#IoT Protocols
Explore tagged Tumblr posts
Text
#IoT Testing#Internet of Things#Device Testing#Functional Testing#Performance Testing#Security Testing#Interoperability Testing#Usability Testing#Regression Testing#IoT Security#Smart Devices#Connected Systems#IoT Protocols#GQATTech#IoT Solutions#Data Privacy#System Integration#User Experience#IoT Performance#Compliance Testing#POS Testing#Point of Sale#Retail Technology#Transaction Processing#System Reliability#Customer Experience#Compatibility Testing#Retail Operations#Payment Systems#PCI DSS Compliance
0 notes
Text
Discover the leading IoT protocols, including MQTT, CoAP, HTTP, AMQP, DDS, and more. Understand how these protocols facilitate communication within IoT ecosystems.
0 notes
Text
Optimize the data & business insights acquired from your connected devices by swiftly expanding the apps with Teksun’s IoT Cloud Integration. Connect with us today with these services and all programmable modules at www.teksun.com
#Cloud Integration#IoT Devices#Data Management#Real-time Data#Cloud Services Data Analytics#Device Connectivity#IoT Protocols#Edge Computing#IoT Security
0 notes
Text
How do self-healing protocols enhance IoT device longevity in harsh environments
TheIoT Communication Protocol Market Size was valued at USD 16.95 Billion in 2023 and is expected to reach USD 23.94 Billion by 2032 and grow at a CAGR of 4.2% over the forecast period 2024-2032.
The IoT Communication Protocol Market is experiencing unprecedented growth, driven by the pervasive integration of connected devices across industries. This market is crucial for enabling the seamless exchange of data between the billions of IoT devices, from smart home appliances to complex industrial sensors, forming the backbone of our increasingly interconnected world. The evolution of communication protocols is vital to unlock the full potential of the Internet of Things, ensuring efficiency, security, and scalability in every deployment.
U.S. Headline: IoT Communication Protocol Market Poised for Significant Expansion Driven by Smart Infrastructure Demands
IoT Communication Protocol Market continues its robust expansion, fueled by advancements in wireless technologies and the rising demand for real-time data exchange. As the Internet of Things ecosystem matures, the emphasis on interoperability, low-power consumption, and enhanced security features in communication protocols becomes paramount. This dynamic landscape necessitates continuous innovation to support the diverse and expanding array of IoT applications that are reshaping industries globally.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6554
Market Keyplayers:
Huawei Technologies (OceanConnect IoT Platform, LiteOS)
Arm Holdings (Mbed OS, Cortex‑M33 Processor)
Texas Instruments (SimpleLink CC3220 Wi‑Fi MCU, SimpleLink CC2652 Multiprotocol Wireless MCU)
Intel (XMM 7115 NB‑IoT Modem, XMM 7315 LTE‑M/NB‑IoT Modem)
Cisco Systems (Catalyst IR1101 Rugged Router, IoT Control Center)
NXP Semiconductors (LPC55S6x Cortex‑M33 MCU, EdgeLock SE050 Secure Element)
STMicroelectronics (STM32WL5x LoRaWAN Wireless MCU, SPIRIT1 Sub‑GHz Transceiver)
Thales (Cinterion TX62 LTE‑M/NB‑IoT Module, Cinterion ENS22 NB‑IoT Module)
Zebra Technologies (Savanna IoT Platform, SmartLens for Retail Asset Visibility)
Wind River (Helix Virtualization Platform, Helix Device Cloud)
Ericsson (IoT Accelerator, Connected Vehicle Cloud)
Qualcomm (IoT Services Suite, AllJoyn Framework)
Samsung Electronics (ARTIK Secure IoT Modules, SmartThings Cloud)
IBM (Watson IoT Platform, Watson IoT Message Gateway)
Market Analysis
The IoT Communication Protocol Market is on a clear upward trajectory, reflecting the global acceleration in IoT device adoption across consumer electronics, industrial automation, healthcare, and smart city initiatives. This growth is intrinsically linked to the demand for efficient, reliable, and secure data transmission. Key drivers include the proliferation of 5G networks, the imperative for edge computing, and the integration of AI for smarter decision-making, all of which heavily rely on robust communication foundations. The market is witnessing a strong shift towards wireless and low-power consumption technologies, with standardized protocols becoming increasingly critical for widespread interoperability.
Market Trends
Proliferation of Wireless Technologies: A dominant shift towards wireless protocols like Wi-Fi, Bluetooth, Zigbee, LoRaWAN, and NB-IoT, preferred for their flexibility and ease of deployment.
5G Integration: The rollout of 5G networks is revolutionizing IoT communication, offering unprecedented speeds, ultra-low latency, and enhanced capacity for real-time applications such, as autonomous vehicles and advanced telemedicine.
Edge Computing Synergy: Growing integration of edge computing with IoT protocols to process data closer to the source, significantly reducing latency and bandwidth consumption, crucial for time-sensitive applications.
Enhanced Security Protocols: A paramount focus on embedding advanced encryption, authentication, and data integrity layers within communication protocols to combat escalating cyber threats and ensure data privacy.
Standardization and Interoperability: A strong industry-wide push for unified communication frameworks to ensure seamless interaction between devices from diverse manufacturers, minimizing vendor lock-in and fostering a more cohesive IoT ecosystem.
AI-Enabled Communications: Increasing integration of Artificial Intelligence into IoT protocols to facilitate smarter decision-making, predictive analytics, and automated optimization of communication pathways.
Market Scope
The IoT Communication Protocol Market's reach is expansive, touching virtually every sector:
Smart Homes & Consumer Electronics: Enabling seamless connectivity for intelligent appliances, smart lighting, voice assistants, and wearables.
Industrial IoT (IIoT) & Manufacturing: Facilitating real-time monitoring, predictive maintenance, and operational efficiency in factories and industrial settings.
Healthcare: Powering remote patient monitoring, connected medical devices, and smart hospital infrastructure for improved patient care and operational insights.
Smart Cities & Utilities: Supporting intelligent traffic management, energy grids, environmental monitoring, and public safety applications.
Automotive & Transportation: Crucial for connected vehicles, intelligent transportation systems, and fleet management, enhancing safety and efficiency.
Agriculture: Enabling precision farming through sensor data for optimized irrigation, crop monitoring, and livestock management.
Forecast Outlook
The future of the IoT Communication Protocol Market appears incredibly promising, driven by relentless innovation and an ever-increasing global demand for connected solutions. Anticipate a landscape characterized by increasingly sophisticated protocols, designed for superior efficiency and adaptive intelligence. The convergence of emerging technologies, such as advanced AI and ubiquitous 5G connectivity, will further accelerate the market's trajectory, fostering an era of truly pervasive and intelligent IoT deployments across all verticals. Expect a future where communication is not just about connectivity, but about seamless, secure, and context-aware interactions that redefine possibility.
Access Complete Report: https://www.snsinsider.com/reports/iot-communication-protocol-market-6554
Conclusion
As we stand on the cusp of an even more interconnected era, the IoT Communication Protocol Market is not merely a segment of the tech industry; it is the fundamental enabler of digital transformation. For innovators, developers, and enterprises alike, understanding and leveraging the evolution of these protocols is critical to building the next generation of smart solutions. This market represents an unparalleled opportunity to shape a future where every device contributes to a smarter, safer, and more efficient world. Embrace these advancements, and together, we can unlock the full, transformative power of the Internet of Things.
Related reports:
U.S.A accelerates smart agriculture adoption to boost crop efficiency and sustainability.
U.S.A. IoT MVNO market: surging demand for cost-effective, scalable connectivity
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text

Discover the top 5 reasons why RS-485 IoT Gateways are essential for efficient and reliable industrial automation systems. Boost performance today!
#RS 485 IoT Gateway Solutions#Industrial IoT Gateway Solutions#industrial iot gateway devices#IOT gateway devices#IIoT gateway devices#MQTT IoT gateway#iot gateway manufacturers#Top IoT gateway companies#IoT gateway company#iot gateway solutions#modbus gateway#rs485 gateway#rs485 protocol#modbus rs485#modbus communication protocol#rs485 iot gateway#modbus protocol#iot gateway
0 notes
Text
Internet of Things (IoT) Technology
The Internet of Things, by its very nature, is a transformative technology that connects ordinary appliances to the Internet, offering an opportunity to collect, share, and act on data. This network as such boasts everything from smart appliances and wearables to industrial machinery and automobiles, therefore leading to better monitoring, control, and more automation for completing environments.

IoT involves using embedded sensors, communication protocols, and cloud computing to provide insights for real-time operations and smooth user experiences in various domains, including healthcare, agriculture, transportation, and smart cities.
IoT technology revolutionizes industries through predictive maintenance, effective resource use, and decision-making. For instance, in agriculture, IoT sensors track soil moisture and weather conditions so that irrigation is optimized; in manufacturing, machines are IoT-enabled, providing equipment health insight, and resulting in lower downtime and maintenance costs. Indeed, IoT's explosive growth has also created severe concerns for data security and privacy. Consequently, traditional cybersecurity and secure communication protocol developments continue to advance.
Training in IoT at EmbLogic
The EmbLogic training program focuses on practical, hands-on, real-world experience for engineers in IoT technology. The courses include IoT architecture sensor integration and processing and network protocols. Those participants will engage in hands-on projects about designing and programming IoT solutions. This course is good for anyone wanting to upgrade his technical skills in IoT or join this exciting industry. Sutrusted between pure theoretical knowledge and hands-on application, EmbLogic facilitates the training of engineers regarding near-future available career opportunities in IoT technology.
#Internet of Things (IoT), #IoT technology solutions, #IoT applications, #Smart devices and automation, #IoT network protocols, #Embedded sensors in IoT, #IoT data collection and analysis, #Predictive maintenance IoT, #IoT cloud computing, #IoT security and privacy, #Smart city IoT solutions, #EmbLogic IoT training program.
#Internet of Things (IoT)#IoT technology solutions#IoT applications#IoT network protocols#Embedded sensors in IoT#IoT cloud computing#Smart city IoT solutions
1 note
·
View note
Text
MQTT turns 25 - here's how it has endured
Happy birthday, @[email protected]! 25 years young.
It’s October 2024 and I’m sitting here in my creative maker studio, wearing a bright t-shirt that excitedly bellows “MQTT 25”! To my left is a top-end Bambu Lab X1C 3D printer, that uses MQTT internally for communication. On my wall are a variety of connected gadgets that display data or that light up in response to MQTT notifications. Today is the official 25th anniversary of the publication of…
#1C1A25#787588#C9C4DA#eclipse paho#FCF8FF#history#hivemq#IBM#internet of things#iot#messaging#mosquitto#MQTT#open source#open standards#protocols#Technology
0 notes
Text
What is the need for real-time Ethernet protocols?
The need for real-time Ethernet protocols #Ethernet #Protocol #Sensor #technology #informationtechnology
Real-time Ethernet protocols in automation technology are used for process control instead of Fieldbus systems. Ethernet serves as an effective communication standard on layers 1 and 2 of the ISO/OSI model, facilitating the reading of sensor values and the controlling of actuators by central controllers at various points in a machine or system. In such setups, when they take on control…
0 notes
Text
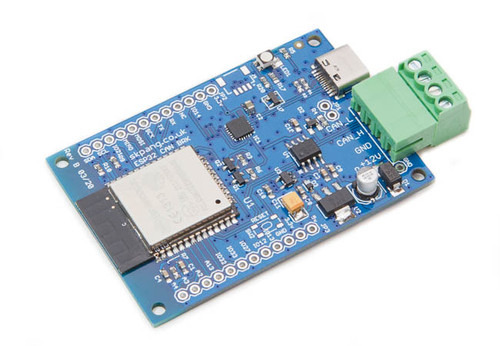
SAE J1939 Protocol Stack Sketch for ESP32 Using the Arduino IDE
The ARD1939 code itself is directly compatible with the ESP32 when used with the Arduino IDE. I am using our ESP32 WiFi, Bluetooth Classic, BLE, CAN Bus Module. This board comes not only with an onboard ESP32 WROOM-32 WiFi, Bluetooth Classic, BLE Module, but also a CAN Bus port with a transceiver.
1 note
·
View note
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
Battery-operated Remote Terminal Units Market Research, Size, Share, Analysis, Overview and Regional Outlook Study 2017 – 2032
The market for Remote Terminal Units (RTUs) that are battery-operated allows them to function in isolated or off-grid regions where access to a reliable power supply is restricted. RTUs are electronic devices used to monitor and manage remote equipment and processes in many different industries, such as oil and gas, water and wastewater management, power distribution, and telecommunications. Here is a summary of the market for battery-operated RTUs, including information on demand:
Market Overview: Due to a number of circumstances, the market for battery-operated RTUs has been expanding. The need for battery-operated RTUs has been fueled by the necessity for remote monitoring and control capabilities in various industries, particularly in places with weak power infrastructure. These devices enable efficient monitoring and control of remote assets without the requirement for a continual external power source thanks to their dependable and autonomous operation.
Demand Drivers:
1. Real-time monitoring and control of assets: situated in remote or isolating locations are necessary in many businesses. Without the requirement for a sizable power infrastructure or reliance on cable connections, battery-operated RTUs allow for effective data gathering, monitoring, and control of these assets.
2. Applications Off-Grid: In off-grid applications where access to a dependable power supply is restricted or nonexistent, battery-operated RTUs are widely used. Examples include remote water pumping stations in rural areas, environmental monitoring stations, remote weather monitoring stations, and remote oil and gas wellheads.
3. Emergency and Temporary Installations: Whereas immediate deployment is necessary, battery-powered RTUs are also used in emergency and temporary installations. When catastrophe recovery, building projects, or temporary infrastructure installations are taking place, these machines can instantly provide remote monitoring and control capabilities.
4. Environmental Monitoring: Data collection from remote weather stations, air quality sensors, and water quality sensors are all important aspects of environmental monitoring that battery-operated RTUs play a key role in. Continuous monitoring is made possible in remote or environmentally delicate locations by these equipment.
5. IoT Connectivity: The need for battery-operated RTUs has increased as the Internet of Things (IoT) is becoming more widely used in a variety of businesses. These devices are essential parts of IoT networks because they provide seamless data transmission, communication, and control between remote assets and central management systems.
Here are some of the key benefits for Stakeholders:
Remote Monitoring and Control
Flexibility and Mobility
Cost-Effective Deployment
Resilience to Power Outages
Integration with IoT and Smart Grids
Increased Data Accessibility
Environmental Monitoring and Compliance
Rapid Deployment for Emergency Response
Redundancy and Reliability
Scalability and Future-Proofing
We recommend referring our Stringent datalytics firm, industry publications, and websites that specialize in providing market reports. These sources often offer comprehensive analysis, market trends, growth forecasts, competitive landscape, and other valuable insights into this market.
By visiting our website or contacting us directly, you can explore the availability of specific reports related to this market. These reports often require a purchase or subscription, but we provide comprehensive and in-depth information that can be valuable for businesses, investors, and individuals interested in this market.
“Remember to look for recent reports to ensure you have the most current and relevant information.”
Click Here, To Get Free Sample Report: https://stringentdatalytics.com/sample-request/battery-operated-remote-terminal-units-market/10333/
Market Segmentations:
Global Battery-operated Remote Terminal Units Market: By Company • SIEMENS • SENECA • Omniflex • King Pigeon Communication Co.,Limited • Servelec Group • TEKBOX • Micro Sensor Co., Ltd. • Hitachi Group • Remsdaq Ltd Global Battery-operated Remote Terminal Units Market: By Type • GPRS • GSM • Modular • Others Global Battery-operated Remote Terminal Units Market: By Application • Power Industry • Government and Utilities • Industrial Global Battery-operated Remote Terminal Units Market: Regional Analysis The regional analysis of the global Battery-operated Remote Terminal Units market provides insights into the market's performance across different regions of the world. The analysis is based on recent and future trends and includes market forecast for the prediction period. The countries covered in the regional analysis of the Battery-operated Remote Terminal Units market report are as follows: North America: The North America region includes the U.S., Canada, and Mexico. The U.S. is the largest market for Battery-operated Remote Terminal Units in this region, followed by Canada and Mexico. The market growth in this region is primarily driven by the presence of key market players and the increasing demand for the product. Europe: The Europe region includes Germany, France, U.K., Russia, Italy, Spain, Turkey, Netherlands, Switzerland, Belgium, and Rest of Europe. Germany is the largest market for Battery-operated Remote Terminal Units in this region, followed by the U.K. and France. The market growth in this region is driven by the increasing demand for the product in the automotive and aerospace sectors. Asia-Pacific: TheAsia-Pacific region includes Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, China, Japan, India, South Korea, and Rest of Asia-Pacific. China is the largest market for Battery-operated Remote Terminal Units in this region, followed by Japan and India. The market growth in this region is driven by the increasing adoption of the product in various end-use industries, such as automotive, aerospace, and construction. Middle East and Africa: The Middle East and Africa region includes Saudi Arabia, U.A.E, South Africa, Egypt, Israel, and Rest of Middle East and Africa. The market growth in this region is driven by the increasing demand for the product in the aerospace and defense sectors. South America: The South America region includes Argentina, Brazil, and Rest of South America. Brazil is the largest market for Battery-operated Remote Terminal Units in this region, followed by Argentina. The market growth in this region is primarily driven by the increasing demand for the product in the automotive sector.
Visit Report Page for More Details: https://stringentdatalytics.com/reports/battery-operated-remote-terminal-units-market/10333/
Reasons to Purchase Battery-operated Remote Terminal Units Market Report:
• To obtain insights into industry trends and dynamics, including market size, growth rates, and important factors and difficulties. This study offers insightful information on these topics.
• To identify important participants and rivals: This research studies can assist companies in identifying key participants and rivals in their sector, along with their market share, business plans, and strengths and weaknesses.
• To comprehend consumer behaviour: these research studies can offer insightful information about customer behaviour, including preferences, spending patterns, and demographics.
• To assess market opportunities: These research studies can aid companies in assessing market chances, such as prospective new goods or services, fresh markets, and new trends.
In general, market research studies offer companies and organisations useful data that can aid in making decisions and maintaining competitiveness in their industry. They can offer a strong basis for decision-making, strategy formulation, and company planning.
About US:
Stringent Datalytics offers both custom and syndicated market research reports. Custom market research reports are tailored to a specific client's needs and requirements. These reports provide unique insights into a particular industry or market segment and can help businesses make informed decisions about their strategies and operations.
Syndicated market research reports, on the other hand, are pre-existing reports that are available for purchase by multiple clients. These reports are often produced on a regular basis, such as annually or quarterly, and cover a broad range of industries and market segments. Syndicated reports provide clients with insights into industry trends, market sizes, and competitive landscapes. By offering both custom and syndicated reports, Stringent Datalytics can provide clients with a range of market research solutions that can be customized to their specific needs
Contact US:
Stringent Datalytics
Contact No - +1 346 666 6655
Email Id - [email protected]
Web - https://stringentdatalytics.com/
#Battery-operated Remote Terminal Units#RTU Market#Remote Monitoring#Wireless RTU#Industrial Automation#Battery-powered RTU#IoT (Internet of Things)#Energy Efficiency#Data Collection#Telemetry#Remote Control#Battery-powered Sensors#SCADA (Supervisory Control and Data Acquisition)#Energy Management#Off-grid Applications#Renewable Energy#Battery Technology#Remote Sensing#Communication Protocols#Edge Computing#Connectivity Solutions#Remote Data Acquisition#Condition Monitoring#Asset Management.
0 notes
Text
Innovations in Electrical Switchgear: What’s New in 2025?

The electrical switchgear industry is undergoing a dynamic transformation in 2025, fueled by the rapid integration of smart technologies, sustainability goals, and the growing demand for reliable power distribution systems. As a key player in modern infrastructure — whether in industrial plants, commercial facilities, or utilities — switchgear systems are becoming more intelligent, efficient, and future-ready.
At Almond Enterprise, we stay ahead of the curve by adapting to the latest industry innovations. In this blog, we’ll explore the most exciting developments in electrical switchgear in 2025 and what they mean for businesses, contractors, and project engineers.
Rise of Smart Switchgear
Smart switchgear is no longer a futuristic concept — it’s a necessity in 2025. These systems come equipped with:
IoT-based sensors
Real-time data monitoring
Remote diagnostics and control
Predictive maintenance alerts
This technology allows for remote management, helping facility managers reduce downtime, minimize energy losses, and detect issues before they become critical. At Almond Enterprise, we supply and support the integration of smart switchgear systems that align with Industry 4.0 standards.
2. Focus on Eco-Friendly and SF6-Free Alternatives
Traditional switchgear often relies on SF₆ gas for insulation, which is a potent greenhouse gas. In 2025, there’s a significant shift toward sustainable switchgear, including:
Vacuum Interrupter technology
Air-insulated switchgear (AIS)
Eco-efficient gas alternatives like g³ (Green Gas for Grid)
These options help organizations meet green building codes and corporate sustainability goals without compromising on performance.
3. Wireless Monitoring & Cloud Integration
Cloud-based platforms are transforming how switchgear systems are managed. The latest innovation includes:
Wireless communication protocols like LoRaWAN and Zigbee
Cloud dashboards for real-time visualization
Integration with Building Management Systems (BMS)
This connectivity enhances control, ensures quicker fault detection, and enables comprehensive energy analytics for large installations
4. AI and Machine Learning for Predictive Maintenance
Artificial Intelligence is revolutionizing maintenance practices. Switchgear in 2025 uses AI algorithms to:
Predict component failure
Optimize load distribution
Suggest optimal switchgear settings
This reduces unplanned outages, increases safety, and extends equipment life — particularly critical for mission-critical facilities like hospitals and data centers.
5. Enhanced Safety Features and Arc Flash Protection
With increasing focus on workplace safety, modern switchgear includes:
Advanced arc flash mitigation systems
Thermal imaging sensors
Remote racking and switching capabilities
These improvements ensure safer maintenance and operation, protecting personnel from high-voltage hazards.
6. Modular & Scalable Designs
Gone are the days of bulky, rigid designs. In 2025, switchgear units are:
Compact and modular
Easier to install and expand
Customizable based on load requirements
Almond Enterprise supplies modular switchgear tailored to your site’s unique needs, making it ideal for fast-paced infrastructure developments and industrial expansions.
7. Global Standardization and Compliance
As global standards evolve, modern switchgear must meet new IEC and IEEE guidelines. Innovations include:
Improved fault current limiting technologies
Higher voltage and current ratings with compact dimensions
Compliance with ISO 14001 for environmental management
Our team ensures all equipment adheres to the latest international regulations, providing peace of mind for consultants and project managers.
Final Thoughts: The Future is Electric
The switchgear industry in 2025 is smarter, safer, and more sustainable than ever. For companies looking to upgrade or design new power distribution systems, these innovations offer unmatched value.
At Almond Enterprise, we don’t just supply electrical switchgear — we provide expert solutions tailored to tomorrow’s energy challenges. Contact us today to learn how our cutting-edge switchgear offerings can power your future projects.
6 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
Future of IoT Communication Protocol Market Size, Share, Analysis, Forecast, and Growth Trends to 2032 in USA
TheIoT Communication Protocol Market Size was valued at USD 16.95 Billion in 2023 and is expected to reach USD 23.94 Billion by 2032 and grow at a CAGR of 4.2% over the forecast period 2024-2032.
IoT Communication Protocol Market is rapidly evolving as industries across the USA accelerate digital transformation and rely heavily on connected devices for automation, monitoring, and data exchange. The demand for seamless, secure, and low-latency communication across IoT ecosystems is driving innovation in protocol development, deployment, and standardization.
U.S. IoT Communication Protocol Market Set for Robust Growth Amid Surge in Connected Devices
The U.S. IoT Communication Protocol Market size was USD 4.76 billion in 2023 and is expected to reach USD 6.0 billion by 2032, growing at a CAGR of 2.64% over the forecast period of 2024–2032.
IoT Communication Protocol Market is witnessing significant traction as smart devices become mainstream in sectors like manufacturing, healthcare, agriculture, and smart cities. The increasing need for interoperability, scalability, and power efficiency is pushing vendors to enhance protocol designs that support vast, real-time device networks.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6554
Market Keyplayers:
Huawei Technologies (OceanConnect IoT Platform, LiteOS)
Arm Holdings (Mbed OS, Cortex‑M33 Processor)
Texas Instruments (SimpleLink CC3220 Wi‑Fi MCU, SimpleLink CC2652 Multiprotocol Wireless MCU)
Intel (XMM 7115 NB‑IoT Modem, XMM 7315 LTE‑M/NB‑IoT Modem)
Cisco Systems (Catalyst IR1101 Rugged Router, IoT Control Center)
NXP Semiconductors (LPC55S6x Cortex‑M33 MCU, EdgeLock SE050 Secure Element)
STMicroelectronics (STM32WL5x LoRaWAN Wireless MCU, SPIRIT1 Sub‑GHz Transceiver)
Thales (Cinterion TX62 LTE‑M/NB‑IoT Module, Cinterion ENS22 NB‑IoT Module)
Zebra Technologies (Savanna IoT Platform, SmartLens for Retail Asset Visibility)
Wind River (Helix Virtualization Platform, Helix Device Cloud)
Ericsson (IoT Accelerator, Connected Vehicle Cloud)
Qualcomm (IoT Services Suite, AllJoyn Framework)
Samsung Electronics (ARTIK Secure IoT Modules, SmartThings Cloud)
IBM (Watson IoT Platform, Watson IoT Message Gateway)
Market Analysis
The market is driven by the rise of Industry 4.0, smart infrastructure, and cloud-native IoT frameworks. Communication protocols such as MQTT, CoAP, Zigbee, LoRaWAN, and 5G are enabling scalable data exchange between billions of devices. In the USA, enterprise IoT adoption is at an all-time high, fueled by federal smart city initiatives, industrial automation projects, and a thriving tech ecosystem.
Technological advancements, including edge computing and AI integration, demand protocols that are fast, lightweight, and reliable under varying network conditions. Additionally, the push for cybersecurity compliance and seamless integration with cloud platforms is accelerating protocol evolution.
Market Trends
Growing adoption of low-power wide-area networks (LPWAN)
Expansion of 5G networks supporting real-time IoT applications
Integration of edge and fog computing to reduce latency
Rise in secure-by-design protocols for data integrity
Standardization initiatives for cross-platform compatibility
Increased demand for ultra-reliable communication in healthcare and manufacturing
Open-source protocol frameworks gaining popularity among developers
Market Scope
With IoT becoming foundational to digital infrastructure, the scope of the IoT Communication Protocol Market is expanding across every connected environment. Businesses seek robust and adaptive protocols that ensure efficient device-to-device and device-to-cloud communication.
Scalable connectivity across industrial IoT environments
Secure and lightweight protocols for smart healthcare solutions
Energy-efficient communication for battery-powered devices
Dynamic protocol stacks for multi-network integration
Protocol optimization for autonomous vehicles and logistics
Seamless integration with cloud and AI platforms
Real-time communication in mission-critical use cases
Forecast Outlook
The future of the IoT Communication Protocol Market is poised for strong growth as industries prioritize scalable, secure, and energy-efficient connectivity. Protocols tailored to ultra-low latency, enhanced security, and cross-industry compatibility will be pivotal. In the USA, the expansion of smart city programs, autonomous systems, and 5G infrastructure will be key catalysts driving protocol innovation and deployment. Competitive advantage will come to vendors offering modular, standards-aligned solutions adaptable to evolving digital ecosystems.
Access Complete Report: https://www.snsinsider.com/reports/iot-communication-protocol-market-6554
Conclusion
As connectivity becomes the backbone of innovation, the IoT Communication Protocol Market is emerging as a critical enabler of intelligent infrastructure. From smart factories in Detroit to precision agriculture in California, the need for fast, secure, and interoperable communication is reshaping how devices interact and deliver value. The next phase of IoT success lies in protocols that are not only technically advanced but aligned with the fast-changing needs of an increasingly connected America.
Related reports:
Analyze growth opportunities in the U.S. IoT MVNO sector
Track the adoption of Blockchain IoT solutions in the United States
Explore U.S. demand for smart devices and IoT solutions
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Text
Smart Switchgear in 2025: What Electrical Engineers Need to Know

In the fast-evolving world of electrical infrastructure, smart switchgear is no longer a futuristic concept — it’s the new standard. As we move through 2025, the integration of intelligent systems into traditional switchgear is redefining how engineers design, monitor, and maintain power distribution networks.
This shift is particularly crucial for electrical engineers, who are at the heart of innovation in sectors like manufacturing, utilities, data centers, commercial construction, and renewable energy.
In this article, we’ll break down what smart switchgear means in 2025, the technologies behind it, its benefits, and what every electrical engineer should keep in mind.
What is Smart Switchgear?
Smart switchgear refers to traditional switchgear (devices used for controlling, protecting, and isolating electrical equipment) enhanced with digital technologies, sensors, and communication modules that allow:
Real-time monitoring
Predictive maintenance
Remote operation and control
Data-driven diagnostics and performance analytics
This transformation is powered by IoT (Internet of Things), AI, cloud computing, and edge devices, which work together to improve reliability, safety, and efficiency in electrical networks.
Key Innovations in Smart Switchgear (2025 Edition)
1. IoT Integration
Smart switchgear is equipped with intelligent sensors that collect data on temperature, current, voltage, humidity, and insulation. These sensors communicate wirelessly with central systems to provide real-time status and alerts.
2. AI-Based Predictive Maintenance
Instead of traditional scheduled inspections, AI algorithms can now predict component failure based on usage trends and environmental data. This helps avoid downtime and reduces maintenance costs.
3. Cloud Connectivity
Cloud platforms allow engineers to remotely access switchgear data from any location. With user-friendly dashboards, they can visualize key metrics, monitor health conditions, and set thresholds for automated alerts.
4. Cybersecurity Enhancements
As devices get connected to networks, cybersecurity becomes crucial. In 2025, smart switchgear is embedded with secure communication protocols, access control layers, and encrypted data streams to prevent unauthorized access.
5. Digital Twin Technology
Some manufacturers now offer a digital twin of the switchgear — a virtual replica that updates in real-time. Engineers can simulate fault conditions, test load responses, and plan future expansions without touching the physical system.
Benefits for Electrical Engineers
1. Operational Efficiency
Smart switchgear reduces manual inspections and allows remote diagnostics, leading to faster response times and reduced human error.
2. Enhanced Safety
Early detection of overload, arc flash risks, or abnormal temperatures enhances on-site safety, especially in high-voltage environments.
3. Data-Driven Decisions
Real-time analytics help engineers understand load patterns and optimize distribution for efficiency and cost savings.
4. Seamless Scalability
Modular smart systems allow for quick expansion of power infrastructure, particularly useful in growing industrial or smart city projects.
Applications Across Industries
Manufacturing Plants — Monitor energy use per production line
Data Centers — Ensure uninterrupted uptime and cooling load balance
Commercial Buildings — Integrate with BMS (Building Management Systems)
Renewable Energy Projects — Balance grid load from solar or wind sources
Oil & Gas Facilities — Improve safety and compliance through monitoring
What Engineers Need to Know Moving Forward
1. Stay Updated with IEC & IEEE Standards
Smart switchgear must comply with global standards. Engineers need to be familiar with updates related to IEC 62271, IEC 61850, and IEEE C37 series.
2. Learn Communication Protocols
Proficiency in Modbus, DNP3, IEC 61850, and OPC UA is essential to integrating and troubleshooting intelligent systems.
3. Understand Lifecycle Costing
Smart switchgear might have a higher upfront cost but offers significant savings in maintenance, energy efficiency, and downtime over its lifespan.
4. Collaborate with IT Teams
The line between electrical and IT is blurring. Engineers should work closely with cybersecurity and cloud teams for seamless, secure integration.
Conclusion
Smart switchgear is reshaping the way electrical systems are built and managed in 2025. For electrical engineers, embracing this innovation isn’t just an option — it’s a career necessity.
At Blitz Bahrain, we specialize in providing cutting-edge switchgear solutions built for the smart, digital future. Whether you’re an engineer designing the next big project or a facility manager looking to upgrade existing systems, we’re here to power your progress.
#switchgear#panel#manufacturer#bahrain25#electrical supplies#electrical equipment#electrical engineers#electrical
6 notes
·
View notes
Text

IoT gateways play a crucial role in smart technology ecosystems by aggregating and processing data from various devices, ensuring seamless communication and interoperability.
#RS 485 IoT Gateway Solutions#Industrial IoT Gateway Solutions#industrial iot gateway devices#IOT gateway devices#IIoT gateway devices#MQTT IoT gateway#iot gateway manufacturers#Top IoT gateway companies#IoT gateway company#iot gateway solutions#modbus gateway#rs485 gateway#rs485 protocol#modbus rs485#modbus communication protocol#rs485 iot gateway#modbus protocol#iot gateway
0 notes