#Ledger Nano Number
Text
Table of ContentsIntroductionUnderstanding the Basics of Hardware Wallets: A Beginner's Guide to Cold Storage SecurityChoosing the Right Hardware Wallet for Your Needs: A Comprehensive Comparison of Top OptionsStep-by-Step Guide to Setting Up and Using a Hardware Wallet: Securing Your Crypto Assets with EaseQ&AConclusionSecure Your Crypto with Ease: The Most User-Friendly Hardware WalletIntroduction**The Most User-Friendly Hardware Wallet: Easiest Options for Beginners to Cold Storage Security**
In the realm of cryptocurrency, safeguarding your digital assets is paramount. Hardware wallets, physical devices designed to store private keys offline, offer an unparalleled level of security against cyber threats. However, navigating the complexities of hardware wallets can be daunting for beginners. This guide introduces the most user-friendly hardware wallets, empowering beginners with the knowledge to secure their cryptocurrencies with ease.Understanding the Basics of Hardware Wallets: A Beginner's Guide to Cold Storage Security**The Most User-Friendly Hardware Wallet: Easiest Options for Beginners to Cold Storage Security**
When it comes to securing your cryptocurrency, hardware wallets offer an unparalleled level of protection. These physical devices store your private keys offline, making them immune to online attacks. However, not all hardware wallets are created equal. For beginners, finding a user-friendly option is crucial.
**Trezor Model T**
The Trezor Model T is widely regarded as one of the most beginner-friendly hardware wallets on the market. Its large touchscreen and intuitive interface make it easy to navigate and manage your assets. The Model T also supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, and Litecoin.
**Ledger Nano X**
Another excellent choice for beginners is the Ledger Nano X. This compact device features a Bluetooth connection, allowing you to manage your cryptocurrencies from your smartphone. The Nano X also has a large OLED display and supports over 1,800 cryptocurrencies.
**SafePal S1**
The SafePal S1 is a budget-friendly option that offers a surprisingly user-friendly experience. Its simple design and clear instructions make it easy for beginners to set up and use. The S1 supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, and Binance Coin.
**CoolWallet Pro**
For those who prefer a more portable option, the CoolWallet Pro is a great choice. This credit card-sized device features a built-in display and Bluetooth connectivity. The CoolWallet Pro supports over 100 cryptocurrencies and offers advanced security features such as fingerprint authentication.
**Choosing the Right Wallet**
When choosing a hardware wallet, consider your experience level, the number of cryptocurrencies you own, and your budget. If you're a beginner, the Trezor Model T or Ledger Nano X are excellent options. For those on a tighter budget, the SafePal S1 is a great choice. And if portability is a priority, the CoolWallet Pro is a solid option.
**Conclusion**
Hardware wallets are an essential tool for securing your cryptocurrency. By choosing a user-friendly option, beginners can easily protect their assets from online threats. The Trezor Model T, Ledger Nano X, SafePal S1, and CoolWallet Pro are all excellent choices for those new to cold storage security.Choosing the Right Hardware Wallet for Your Needs: A Comprehensive Comparison of Top Options**The Most User-Friendly Hardware Wallet: Easiest Options for Beginners to Cold Storage Security**
When it comes to securing your cryptocurrency, hardware wallets offer an unparalleled level of protection. However, navigating the complexities of these devices can be daunting for beginners. To simplify the process, we've compiled a list of the most user-friendly hardware wallets that make cold storage security accessible to all.
**Trezor Model T**
The Trezor Model T is renowned for its intuitive interface and ease of use. Its large
touchscreen display and clear navigation menu make it a breeze to set up and manage your crypto assets. Additionally, the Trezor Suite software provides a comprehensive suite of features, including advanced security options and support for multiple cryptocurrencies.
**Ledger Nano X**
The Ledger Nano X is another top-rated hardware wallet that prioritizes user-friendliness. Its compact design and Bluetooth connectivity make it highly portable, allowing you to manage your crypto on the go. The Ledger Live app offers a user-friendly interface and supports a wide range of cryptocurrencies, making it a versatile choice for beginners.
**SafePal S1**
The SafePal S1 is a budget-friendly hardware wallet that doesn't compromise on ease of use. Its simple design and straightforward interface make it ideal for those new to cold storage. The SafePal app provides a user-friendly platform for managing your crypto assets and offers support for a growing number of cryptocurrencies.
**CoolWallet Pro**
The CoolWallet Pro stands out as the only hardware wallet with a built-in e-ink display. This unique feature allows you to view your crypto balances and transaction history without connecting to a computer or smartphone. Its sleek design and intuitive interface make it a pleasure to use.
**BitBox02**
The BitBox02 is a Swiss-made hardware wallet that combines security with user-friendliness. Its open-source firmware and transparent design provide peace of mind, while its intuitive interface and clear instructions make it easy to set up and use. The BitBoxApp offers a user-friendly platform for managing your crypto assets.
**Choosing the Right Wallet for You**
When selecting a hardware wallet, consider your technical proficiency, the number of cryptocurrencies you hold, and your budget. If you're a beginner looking for a user-friendly and secure option, the Trezor Model T, Ledger Nano X, or SafePal S1 are excellent choices. For those seeking a portable and versatile wallet, the Ledger Nano X or CoolWallet Pro are ideal. And if security and transparency are your top priorities, the BitBox02 is a solid choice.
By choosing a user-friendly hardware wallet, you can enjoy the peace of mind that comes with knowing your cryptocurrency is securely stored offline. These devices empower beginners to take control of their digital assets and protect them from theft and unauthorized access.Step-by-Step Guide to Setting Up and Using a Hardware Wallet: Securing Your Crypto Assets with Ease**The Most User-Friendly Hardware Wallet: Easiest Options for Beginners to Cold Storage Security**
In the realm of cryptocurrency, safeguarding your digital assets is paramount. Hardware wallets, physical devices that store your private keys offline, offer an unparalleled level of security against cyber threats. However, navigating the complexities of hardware wallets can be daunting for beginners.
Enter the most user-friendly hardware wallets, designed to simplify the process of securing your crypto assets. These devices prioritize ease of use, intuitive interfaces, and beginner-friendly features.
**Trezor Model T**
The Trezor Model T is renowned for its sleek design and user-friendly interface. Its touchscreen display and intuitive navigation make it a breeze to set up and manage your crypto assets. The Model T supports a wide range of cryptocurrencies and offers advanced features such as passphrase protection and multi-factor authentication.
**Ledger Nano X**
The Ledger Nano X is another top-rated hardware wallet known for its portability and ease of use. Its Bluetooth connectivity allows you to manage your assets from your smartphone, making it convenient for on-the-go transactions. The Nano X supports a vast array of cryptocurrencies and features a secure chip that protects your private keys from unauthorized access.
**SafePal S1**
The SafePal S1 is an affordable and user-friendly hardware wallet designed specifically for beginners. Its simple interface and step-by-step instructions make it easy to set up and use.
The S1 supports a range of popular cryptocurrencies and offers a built-in exchange for convenient trading.
**Setting Up Your Hardware Wallet**
Setting up your hardware wallet is a straightforward process. Simply follow the instructions provided by the manufacturer. Typically, you will need to:
* Connect your hardware wallet to your computer or smartphone.
* Create a PIN code for security.
* Generate a recovery seed phrase, which is a set of words used to recover your wallet in case of loss or damage.
* Transfer your crypto assets to your hardware wallet.
**Using Your Hardware Wallet**
Once your hardware wallet is set up, you can use it to securely store, send, and receive cryptocurrencies. To send crypto, simply connect your wallet to your computer or smartphone, enter the recipient's address and the amount you wish to send, and confirm the transaction. To receive crypto, provide the sender with your wallet's public address.
**Conclusion**
Choosing the right hardware wallet is crucial for securing your crypto assets. By opting for a user-friendly device like the Trezor Model T, Ledger Nano X, or SafePal S1, beginners can easily safeguard their digital wealth with confidence. Remember to follow the setup instructions carefully and store your recovery seed phrase securely. With a hardware wallet, you can enjoy the peace of mind that comes with knowing your crypto assets are protected from cyber threats.Q&A**Question 1:** What is the most user-friendly hardware wallet for beginners?
**Answer:** Ledger Nano X
**Question 2:** What makes the Ledger Nano X easy to use?
**Answer:** Large touchscreen, Bluetooth connectivity, and a user-friendly interface
**Question 3:** What are the benefits of using a hardware wallet like the Ledger Nano X?
**Answer:** Enhanced security, offline storage, and support for multiple cryptocurrenciesConclusion**Conclusion:**
The most user-friendly hardware wallet for beginners seeking cold storage security is the Ledger Nano X. Its intuitive interface, mobile app integration, and extensive coin support make it an accessible and secure option for storing cryptocurrencies offline. Other beginner-friendly hardware wallets include the Trezor Model T, SafePal S1, and CoolWallet Pro, each offering varying features and price points to suit different needs. By choosing a reputable hardware wallet and following best practices for secure storage, beginners can effectively protect their digital assets from theft and unauthorized access.
0 notes
Text
How to Set Up a Crypto Wallet

The cryptocurrency market has grown significantly in the last few years, and there are promising signs that it will continue to rise. Meanwhile, as enthusiasts make predictions of digital assets, the first step toward taking advantage of these prospects is to create a Bitcoin wallet. This thorough article walks readers through creating a cryptocurrency wallet, stressing its significance, essential features, and how to choose the best wallet based on personal preferences.
Making a Digital Currency Wallet on Software: Your Entryway to Trading
Step 1: Select a Reputable Wallet App
Choosing a trustworthy wallet provider is the first step in creating a software cryptocurrency wallet. There are numerous choices, each with special features and security measures. Careful study is essential before choosing a wallet. Among the best options available are Trust Wallet, Electrum, and Exodus.
Step 2: Download the Wallet App
After selecting a compatible software crypto wallet, the program must be downloaded to your device. This guarantees easy access to your cryptocurrency holdings. To protect against security breaches, it is essential to download the program via legitimate sources, such as the wallet provider's website or the app store.
Step 3: Register for an Account
When creating an account, you must enter your name, email address, and a strong password. Certain wallet apps may also ask for a selfie and a government-issued ID for identity verification.
Step 4: Give Up Your Property
After setting up your software crypto advisor and account, the next step is to move assets. Numerous techniques, such as bank transfers, cryptocurrency exchanges, or transfers from other wallets, might be used to do this. These transfers are made possible by wallet addresses and QR codes, which help users safely manage various assets.
Building a Hardware Wallet: Strengthening Security
Step 1: Choose Your Hardware
Selecting the hardware wallet that best meets your needs requires investigation and comparison shopping. Trezor Model T, Ledger Nano X, and KeepKey are well-liked options with different features and degrees of security.
Step 2: Get and Set Up Software
Once you've chosen a hardware wallet, buy it and install the necessary software. Most hardware wallets provide an installation wizard that walks customers through the procedure. Connecting the hardware wallet to your device ensures a secure connection; the manufacturer's instructions are an essential reference.
Step 3: Exchange Digital Money
Move your cryptocurrency holdings once your hardware wallet has been appropriately configured. Improving security entails connecting your hardware wallet to an exchange or brokerage account. This keeps your digital assets offline
Making a Paper Wallet: An Easy, Affordable Storage Option
Step 1: make use of a wallet generator.
Go to a trustworthy wallet generator website to build a paper wallet. This open-source software creates distinct public and private keys for your cryptocurrency wallet. To minimize the risk of internet attacks, you can save the generator offline as a web archive on your computer.
Step 2: Disconnect for Optimal Security
To ensure the private key generation in an offline environment and lower the danger of internet attacks, make your paper wallet offline for maximum security.
Step 3: Get your key printed and secure.
Please write down the private key and keep it somewhere safe, like a lockbox or safe. Because the paper wallet key unlocks your cryptocurrency cash, keeping it secure is essential
Things You'll Need to Open a Cryptocurrency Wallet Account: Important Things to Know
When opening a Bitcoin wallet account, consider choosing a wallet provider, entering personal information, and having some cryptocurrency to store.
Personal Data Needed:
It would help if you usually supplied your full name, email address, phone number, and residential address to abide by anti-money laundering (AML) and know-your-customer (KYC) rules. You should also be aware of the significance of public and private keys.
Things to Take Into Account When Setting Up a Crypto Wallet: An Introduction for New Investors
Setting up a cryptocurrency wallet can be daunting for beginners, but a few essential elements can help streamline the selection process.
Safety:
Security features, including support for multiple signatures, two-factor authentication, and extensive backup and recovery capabilities, should be given top priority. A wallet with a good reputation and a track record of security is essential.
Charges:
Think about wallet fees and choose open pricing. Specific wallets could impose extra costs for particular functions or transactions.
Count of Cryptocurrencies Accepted:
Make sure the wallet you've chosen can hold the variety of cryptocurrencies you want. The wallet's website provides a detailed list of supported currencies.
Client Support:
User manuals, FAQs, and responsive customer service are all excellent tools. Select a wallet provider that provides dependable support for any questions or concerns.
Managing Profits and Risks with Crypto Trading Courses: A Comprehensive Guide to Mastering the Crypto Wave
Gaining a thorough grasp of cryptocurrency trading is crucial for anyone hoping to profit from the market's rapid growth in the ever-evolving cryptocurrency landscape. Cryptocurrency trading classes are a priceless tool that allows fans to master the art from seasoned experts.
Understanding the complexity of cryptocurrency trading becomes crucial as the market continues its astonishing expansion. These courses give students insights into the leading cryptocurrencies that are now saturating the market and teach them how to analyze market patterns and make calculated transactions. Acquiring knowledge from a bitcoin specialist or advisor via organized classes enables traders and investors to make wise choices, improving their capacity to negotiate the unstable cryptocurrency market successfully.
These courses cover advanced methods and risk management techniques, going beyond the fundamentals of learning cryptocurrencies. Because it's crucial to comprehend the subtleties of the cryptocurrency market, crypto trading courses act as knowledge oases, assisting enthusiasts in navigating the complexities of the market and building a community of knowledgeable investors poised to take advantage of opportunities in this ever-evolving financial landscape. When people start their cryptocurrency journey, it's essential to ensure a comprehensive approach to navigating the fascinating but complicated world of digital assets by pairing the purchase of a secure wallet with a strong foundation in crypto trading through courses.
Conclusion
First step in navigating the world of cryptocurrencies is creating a trustworthy and safe wallet. This tutorial's concerns and processes offer thorough instruction for those new to digital assets, regardless of whether they want to use a paper wallet, software, or hardware. Blockchain Council is a top resource for people learning more about blockchain technology and cryptocurrency trading. The Blockchain Council comprises enthusiasts and subject matter experts and is committed to promoting blockchain technology, products, use cases, and research and development for a better society. Acknowledging blockchain's revolutionary potential, Blockchain Council provides reputable learn crypto trading courses that offer priceless insights into the complex mechanics of the digital asset market.
0 notes
Text
Cryptocurrency Security: Protecting Your Digital Assets in a Cyber-Connected World
In today's digitally-driven age, the widespread adoption of cryptocurrencies has revolutionized the way we perceive and interact with financial assets. The decentralized nature of cryptocurrencies such as Bitcoin, Ethereum, and others offers unparalleled security and convenience, attracting a growing number of investors seeking to diversify their portfolios. However, as the popularity of cryptocurrencies continues to soar, the need for robust security measures to safeguard digital assets has become paramount. This article will explore the crucial aspects of cryptocurrency security, offering valuable insights to protect your investments in this cyber-connected world.
### Understanding Cryptocurrency Security
Cryptocurrency security encompasses a wide range of practices and technologies aimed at safeguarding digital assets from unauthorized access, theft, and other cyber threats. Given the digital and decentralized nature of cryptocurrencies, ensuring the security of your holdings requires a proactive approach and a solid understanding of key security measures.
### Secure Investment: How Do You Invest in Cryptocurrency?
Before delving into the intricacies of cryptocurrency security, it's essential to address the fundamental question of how to invest in cryptocurrencies securely. The process typically involves the following steps:
1. Choose a Reputable Exchange: Select a trusted and well-established cryptocurrency exchange platform to facilitate the purchase, sale, and exchange of digital assets.
2. Secure Your Wallet: Utilize a secure digital wallet to store your cryptocurrency holdings. Hardware wallets, such as Ledger Nano S or Trezor, offer enhanced security through offline storage and encryption, reducing the risk of unauthorized access.
3. Research and Due Diligence: Conduct thorough research and due diligence on the cryptocurrencies you intend to invest in. Understand the underlying technology, market dynamics, and potential risks before committing funds.
### How to Buy and Send Crypto Instantly
Buying and sending cryptocurrencies instantly requires a seamless and secure process to ensure swift transactions without compromising security. Here's a brief overview of the steps involved:
1. Select the Cryptocurrency: Choose the specific cryptocurrency you wish to purchase, considering factors such as market trends, potential for growth, and utility.
2. Choose a Reliable Exchange: Opt for a reputable cryptocurrency exchange that supports instant transactions and offers robust security features.
3. Execute the Transaction: Initiate the purchase of the selected cryptocurrency through the exchange platform, following the specified procedures and security protocols.
4. Secure the Transaction: After purchasing the cryptocurrency, ensure that you securely store the digital assets in a trusted wallet and implement best practices to safeguard your investment.
### Enhancing Cryptocurrency Security
Now that we've covered the basics of investing in and transacting with cryptocurrencies, let's delve into the essential strategies to enhance cryptocurrency security:
1. Utilize Multi-Factor Authentication (MFA): Enable MFA for your cryptocurrency exchange accounts and digital wallets to add an extra layer of protection against unauthorized access.
2. Keep Software and Wallets Updated: Regularly update your cryptocurrency wallet software and associated applications to incorporate the latest security patches and enhancements.
3. Beware of Phishing Scams: Exercise caution when interacting with cryptocurrency-related emails, websites, and communications to avoid falling victim to phishing scams and fraudulent activities.
4. Consider Cold Storage: For long-term storage of significant cryptocurrency holdings, consider utilizing cold storage solutions, such as hardware wallets, which keep the private keys offline and away from potential cyber threats.
5. Stay Informed: Stay abreast of the latest developments and security best practices in the cryptocurrency space by engaging with reputable sources, forums, and communities dedicated to cryptocurrency education and awareness.
### Conclusion
As the allure of cryptocurrencies continues to captivate investors and enthusiasts worldwide, prioritizing robust security measures to protect digital assets has never been more crucial. By implementing the recommended security practices and staying vigilant against evolving cyber threats, you can fortify your cryptocurrency investments and navigate the cyber-connected world with confidence. Remember, the proactive protection of your digital assets is a cornerstone of responsible and sustainable cryptocurrency investment.

0 notes
Text
BOTIFI
Step by Step Guide to Buy BOTIFI Tokens in Presale
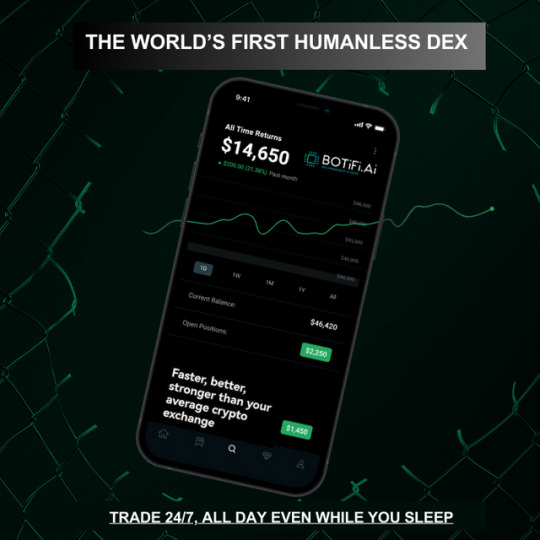
In the fast-paced world of digital marketing, staying ahead is critical. We recently discovered a ton of insights that we believe can change the way you approach your digital marketing strategy. At the heart of Botifi is a treasure trove of knowledge that can redefine your online presence. Get ready as we take you on a journey through key insights and revelations that can skyrocket your digital marketing game.
If you are interested in investing in BOTIFI tokens, it is important to know how to purchase them during the presale. In this blog post, we will explore the various payment options and wallets you can use to earn BOTIFI tokens during the presale.

Payment options
BOTIFI offers a variety of payment options to accommodate a diverse audience. The following payment methods you can use to buy BOTIFI tokens:
Ethereum (ETH) : Ethereum is the native cryptocurrency of the Ethereum blockchain, on which the BOTIFI token is based. Using ETH is an easy choice for many investors. To buy BOTIFI with ETH, you must have ETH in your wallet, and the exchange rate will determine how many BOTIFI tokens you will receive for your ETH.
Tether (USDT): Tether is a stablecoin pegged to the value of the US dollar. The use of USDT can provide price stability during the purchase of BOTIFI tokens, because the value is relatively constant. You can use USDT to buy BOTIFI during the presale.
Binance Coin (BNB) : Binance Coin is the native cryptocurrency of the Binance exchange. You can use BNB to purchase BOTIFI tokens, and like ETH, the number of tokens you will receive will depend on the exchange rate.
Binance USD (BUSD) : Binance USD is a stablecoin issued by Binance. It is designed to maintain a 1:1 peg with the US dollar. If you prefer the stability of stablecoins, you can use BUSD to buy BOTIFI tokens.

Wallet Options
To participate in the BOTIFI pre-sale, you will need a cryptocurrency wallet that supports the Ethereum network, as the BOTIFI token is an ERC-20 token. Here are some wallet options:
Metamask : Metamask is a popular Ethereum wallet that is easy to set up and use. It is available as a browser extension and mobile app, making it convenient for many users.
Trustwallet : Trustwallet is a mobile wallet with a user-friendly interface. It supports various cryptocurrencies and allows you to manage your assets on the go.
MyEtherWallet (MEW) : MyEtherWallet is a web-based wallet that allows you to create and manage Ethereum wallets. This gives you complete control over your private keys, which is important for security.
Ledger Nano S/X : If you prefer a hardware wallet for added security, the Ledger Nano S or X can store your BOTIFI tokens offline, protecting them from potential online threats.

Steps to Buy BOTIFI Tokens
Now that you understand the payment options and wallet choices, let’s summarize the steps to purchase BOTIFI tokens during the presale:
Visit the official BOTIFI website ( https://www.botifi.ai ).
Set up a cryptocurrency wallet compatible with the Ethereum network, such as Metamask, Trustwallet, or MyEtherWallet.
Fund your wallet with the cryptocurrency of your choice, be it ETH, USDT, BNB or BUSD.
Connect your wallet to BOTIFI’s official website to interact with pre-sales.
Join the presale by selecting the number of BOTIFI tokens you wish to purchase.
Confirm the transaction and pay the required fuel fees. Make sure you have enough ETH in your wallet to cover these fees.
Wait until the transaction is confirmed on the Ethereum blockchain. Your BOTIFI tokens will be stored in your wallet once the confirmation is complete.

Tokenomics and pre-sale
Most of the token economics for BOTiFi token issuance are pre-sale stage. Early backers have the opportunity to purchase tokens at favorable prices during the pre-sale, when a certain allocation of tokens is available to them at a cheaper price. The pre-sale has attracted interest due to its exclusivity and incentives, making it a key component of BOTiFi’s token economy.
Pre-sale participants often get additional bonuses, which increases the appeal of making an early purchase. These extras, which increase value for pre-sale participants, may include additional tokens or early access to platform features.
A broad and active community was built from the start thanks to the pre-sale event’s contribution to the initial token distribution. This distribution is important for laying a strong foundation for project development and success.

INTDESTCOIN generates income through a range of services and investments across various sectors, including blockchain, AI, cybersecurity, and renewable energy. The project’s focus on continuous research and development, expertise, and social responsibility bolsters its position in the market, providing a stable foundation for growth.
Unlocking the Potential with Tokenomics:
INTDESTCOIN’s tokenomics strategy encompasses allocations to other investors, a token burning process, team tokens, locked liquidity pools, an ecosystem fund, user acquisition, safety and insurance funds, adviser tokens, and locked tokens. These mechanisms ensure stability, security, and responsible growth for the project.
In Conclusion: A Journey of Innovation:

Buying BOTIFI tokens during the presale is an exciting opportunity to become part of a promising project. Remember to do your research, stay safe, and make informed investment decisions. Happy investing!
Tokenomics and pre-sale
Most of the token economics for BOTiFi token issuance are pre-sale stage. Early backers have the opportunity to purchase tokens at favorable prices during the pre-sale, when a certain allocation of tokens is available to them at a cheaper price. The pre-sale has attracted interest due to its exclusivity and incentives, making it a key component of BOTiFi’s token economy.
Pre-sale participants often get additional bonuses, which increases the appeal of making an early purchase. These extras, which increase value for pre-sale participants, may include additional tokens or early access to platform features.
A broad and active community was built from the start thanks to the pre-sale event’s contribution to the initial token distribution. This distribution is important for laying a strong foundation for project development and success.
In short, Botifi Smart Dex is a must-have platform for cryptocurrency traders. It leverages the power of AI to make informed decisions, offers lightning-speed execution with smart bots, and increases user control and security through smart contracts. Whether you are an experienced trader or a newcomer to the world of crypto, Botifi Smart Dex is a platform that can give you the edge you need.

Further information
Website: https://www.botifi.ai/
Youtube: https://www.youtube.com/@BOTiFi_Ai
Twitter: https://twitter.com/BoTiFi_Ai
Instagram: https://www.instagram.com/botifi_ai
White Paper: https://docsend.com/view/2kf4zukhs5fb59bh
Telegram: https://t.me/BOTiFi_Ai
Reddit: https://www.reddit.com/r/Botifi_Ai
Forum Username:Saddang
Forum Profile Link:https://bitcointalk.org/index.php?action=profile;u=3460665
0 notes
Text
How to Buy BOTIFI Tokens in Presale: Payment Options and Wallets
If you're interested in investing in BOTIFI tokens, it's crucial to know how to purchase them during the presale. In this blog post, we'll explore the various payment options and wallets you can use to acquire BOTIFI tokens during the presale.

Payment Options
BOTIFI offers a range of payment options to accommodate a diverse audience. Here are the payment methods you can use to buy BOTIFI tokens:
Ethereum (ETH): Ethereum is the native cryptocurrency of the Ethereum blockchain, on which BOTIFI tokens are based. Using ETH is a straightforward choice for many investors. To buy BOTIFI with ETH, you'll need to have ETH in your wallet, and the exchange rate will determine how many BOTIFI tokens you'll receive for your ETH.
Tether (USDT): Tether is a stablecoin pegged to the value of the US dollar. Using USDT can provide price stability during the purchase of BOTIFI tokens, as its value remains relatively constant. You can use USDT to buy BOTIFI during the presale.
Binance Coin (BNB): Binance Coin is the native cryptocurrency of the Binance exchange. You can use BNB to purchase BOTIFI tokens, and like ETH, the number of tokens you'll receive will depend on the exchange rate.
Binance USD (BUSD): Binance USD is a stablecoin issued by Binance. It's designed to maintain a 1:1 peg with the US dollar. If you prefer the stability of a stablecoin, you can use BUSD to buy BOTIFI tokens.

Wallet Options
To participate in the BOTIFI presale, you'll need a cryptocurrency wallet that supports the Ethereum network, as BOTIFI tokens are ERC-20 tokens. Here are a few wallet options:
Metamask: Metamask is a popular Ethereum wallet that is easy to set up and use. It's available as a browser extension and a mobile app, making it convenient for a wide range of users.
Trustwallet: Trustwallet is a mobile wallet with a user-friendly interface. It supports a variety of cryptocurrencies and allows you to manage your assets on the go.
MyEtherWallet (MEW): MyEtherWallet is a web-based wallet that allows you to create and manage Ethereum wallets. It provides you with full control over your private keys, which is important for security.
Ledger Nano S/X: If you prefer a hardware wallet for added security, the Ledger Nano S or X can store your BOTIFI tokens offline, protecting them from potential online threats.

Steps to Buy BOTIFI Tokens
Now that you're familiar with the payment options and wallet choices, let's summarize the steps to purchase BOTIFI tokens during the presale:
Visit the official BOTIFI website (https://www.botifi.ai).
Set up a cryptocurrency wallet compatible with the Ethereum network, such as Metamask, Trustwallet, or MyEtherWallet.
Fund your wallet with the cryptocurrency of your choice, whether it's ETH, USDT, BNB, or BUSD.
Connect your wallet to the official BOTIFI website to interact with the presale.
Join the presale by selecting the number of BOTIFI tokens you wish to purchase.
Confirm the transaction and pay any necessary gas fees. Ensure you have enough ETH in your wallet to cover these fees.
Wait for the transaction to be confirmed on the Ethereum blockchain. Your BOTIFI tokens will be deposited in your wallet once the confirmation is complete.

Buying BOTIFI tokens during the presale is an exciting opportunity to be a part of a promising project. Remember to do your research, stay secure, and make informed investment decisions. Happy investing!
#BOTIFIAI #AIRDROP #Crypto #BTC
More Information
Website: https://www.botifi.ai/
Youtube: https://www.youtube.com/@BOTiFi_Ai
Twitter: https://twitter.com/BoTiFi_Ai
Instagram: https://www.instagram.com/botifi_ai
Whitepaper: https://docsend.com/view/2kf4zukhs5fb59bh
Telegram: https://t.me/BOTiFi_Ai
Reddit: https://www.reddit.com/r/Botifi_Ai
Bitcointalk username: Fenyliu
Bitcointalk profile link: https://bitcointalk.org/index.php?action=profile;u=2215277
BSC address: 0x2BB0de3082c1E212aE95Fa2Bf21c332209FBF68b
0 notes
Text
How to create an eth wallet for erc20 tokens
In this guide, we will tell you how to create a wallet for Ethereum, how to send and receive crypto to it.

What is an Ethereum (eth) wallet
Ethereum is a digital currency that needs to be stored somewhere. For this purpose, crypto wallets were created, which are used to send and receive cryptocurrency, trade, and pay for goods and services online.
Any storage for ether has a set of private keys. A private key is a secret code of letters and numbers that designates certain coins as the personal property of the user. Their complexity certainly doesn’t make it easy for users to remember. ERC20 token generator is exactly what crypto wallets are for. When you send Ethereum coins to your wallet, it stores all the keys associated with them, allowing you to access them without having to enter your private key each time.
Types of Ethereum wallets
Cryptocurrency storage can be divided into two main categories: cold and hot.
Cold:
Hardware crypto wallets. Such devices look like flash drives and are considered the safest storage for ETH coins. This is because they store private keys in such a way that even when connected to a virus-infected device, they remain safe. Because they operate offline, hackers cannot hack into them and steal Ethereum.
Paper crypto wallets. Such repositories are nothing more than a public and private key generated from a website. Their advantages are that they work offline and are free, and they are very easy to create. The disadvantages include the fact that, unfortunately, they are susceptible to physical damage and cannot be used to pay for goods on the spot.
Hot:
Desktop crypto wallets. Such applications are installed on a computer and work with operating systems such as Windows, Mac and Linux. Due to the fact that they have access to the Internet, they are less secure than cold wallets, but their advantage is that they are functional and free.
Browser crypto wallets. In fact, such storage facilities are simply sites where you can register a personal account and transfer Ethereum to it. The advantage of such crypto wallets is the convenience and speed of logging into the system: only the login and password for the account are required. However, this is not the most secure solution if you plan to store a large amount of Ethereum.
Mobile wallets. This includes storage in the form of an application for a smartphone or tablet. Among the advantages, of course, are convenience, ease of use and the fact that they can be installed simply from Google Play or the Apple Store for free.
In each category there are virtual wallets for Ethereum, which are considered the most reliable and convenient — we will look at them in more detail.
Hardware wallets
The market for hardware storage for cryptocurrencies is dominated by two brands — Trezor and Ledger, which also offer models for storing Ethereum. Popular options:
Trezor One — supports more than 1,000 cryptocurrencies, including ether, has a monochrome display with two buttons, costs about $65;
Trezor T — supports more than 1000 cryptocurrencies, including ETH, has a color touch screen, costs $170;
Ledger Nano S — PIN-protected, can install from 3 to 20 applications depending on their size, supports several cryptocurrencies, including ether and ERC-20 tokens, comes in six color options: black, yellow, pink, green, blue and metallic, costs about $70;
Ledger Nano — supports up to 100 applications simultaneously, is equipped with Bluetooth, which allows you to connect it to the Ledger Live Mobile application to access ETH coins from a computer or smartphone, costs about $130;
KeepKey — performs the same functions as devices from Ledger or Trezor: stores keys offline, allows you to make backups and generate 12-character keys to restore access to the crypto on another device, costs about $140.
Mobile wallets
There are not many mobile Ether storage products on the market developed or approved by the Ethereum team. The proven and most popular mobile wallet is Jaxx, which works on all devices and gives the owner complete freedom and flexibility in trading Ethereum. The application has an intuitive interface and a wide range of functions. Its feature is a new data encryption system using the AES-256 algorithm, enhanced by 5000 password hashing cycles according to the PBKDF2 standard.
Desktop wallets
Current crypto wallets for storing ether with installation on a computer:
Guarda — supports more than 40 blockchains and thousands of their tokens, a coin exchange function and the ability to purchase any cryptocurrency using a bank card;
Exodus — supports about 100 cryptocurrencies, including Ethereum, does not store any personal data belonging to clients, and requires an Internet connection to access assets;
Atomic Wallet — supports more than 300 cryptocurrencies, allows you to manage ETH and other than create ERC20 token , buy and exchange ether for other cryptocurrencies inside the wallet.
Browser wallets
Among the popular and proven browser-based crypto wallets for storing Ethereum:
MetaMask — designed for both Ethereum and other tokens based on it, has a simple and intuitive interface, stores keys on the user’s computer, is available for browsers Chrome, Opera, Mozilla and others;
MyEtherWallet — suitable for Ethereum and all ERC20-based tokens, offers the user a client interface with the ability to connect a cold wallet.
The disadvantage of browser versions is the lack of Russian language in the interface, which makes their use somewhat difficult for Russian-speaking users, but not critical.
How to create an Ethereum (eth) wallet
Each type of storage requires its own registration, but if hardware storage needs to be purchased, and paper storage needs to be simply printed, then mobile, desktop and browser applications have approximately the same creation procedure. Therefore, let’s look at the process of creating a wallet for Ethereum using the example of the browser version of MyEtherWallet.
To register a crypto wallet you need to follow a few simple steps:
Visit the official MyEtherWallet website — enter a strong password of at least 9 characters and generate a wallet by clicking “By Keystore File”.
Download the keystore file. You have two ways to do this. You can upload a .JSON file with an encrypted version of the private key, compatible with myetherwallet. You can also store an unencrypted version of your private key by downloading it as a .JSON file or copying it from a website. Try to save this file in the safest place possible, preferably on a USB drive or mobile phone.
Open a crypto wallet. To do this, you need to use the keystore file by selecting the appropriate item in the menu, and then pressing “Enter”.
Get the wallet number. Once the vault is unlocked, you will be able to select ETH coins or other ERC-20 tokens to use, as well as copy the wallet number to send and receive crypto.
You can now send and receive Ethereum coins and other tokens from your personal crypto wallet. Simply click “Send Ether and Tokens”, select the type of private key you want to use (keystore/JSON file), and select your wallet file.
How to send ETH coins and ERC-20 tokens from a wallet
To send crypto, you need to specify the address of the wallet to which the ether will be sent and the amount, then click “Generate transaction” and then “Send”. Managing ERC20 token development in MyEtherWallet is as easy as managing ETH. After logging into your wallet, click the orange “Show all tokens” button to see the entire list of supported tokens in their abbreviated form. Now click on any token to download it and include it in MyEtherWallet. If the token is not yet supported by MEW, you can add it yourself by entering the required information.
How to top up your Ethereum wallet
There are several ways to transfer coins to your MyEtherWallet wallet:
through payment services;
through cryptocurrency exchangers;
through other official Ethereum wallets.
No matter what wallet you use, keep your private key in a safe place. We recommend downloading applications for storing ETH coins only from official developer sites and purchasing hardware wallets from manufacturers.
#create erc20 token#erc20 token generator#erc20 token development#erc20 development#ethereum development
0 notes
Text
What Is A HD Wallet? How To Work HD Wallet?

A HD wallet, or hierarchical deterministic wallet, is a type of cryptocurrency wallet that uses a specific algorithm to generate a unique sequence of addresses and private keys, making it easy to manage multiple cryptocurrencies and ensure secure transactions. The use of HD wallets has become increasingly popular in the cryptocurrency world due to their enhanced security features and ability to create an unlimited number of addresses.
In this type of wallet, a single seed phrase is used to generate a hierarchical structure of private keys, allowing for easy backup and restoration of funds. HD wallets provide a convenient and secure way for users to manage their digital assets and have become an essential tool for cryptocurrency enthusiasts and investors.

ADreward(AD)Gate.io startup listing after free airdrop, Huobi Prime voting Follow Us:)
Website: https://adreward.io
Telegram: https://t.me/ADreward
Twitter: https://twitter.com/a_dreward
What Is A HD Wallet?
A HD wallet, or Hierarchical Deterministic wallet, is a type of cryptocurrency wallet that uses a specific algorithm to generate a sequence of private and public keys. This sequence of keys is derived from a single seed phrase or master key, which makes it easy for users to manage multiple addresses and transactions from one central location.
The term "hierarchical" refers to the tree-like structure of the keys, with each key being derived from its parent key. This allows for the creation of an almost infinite number of unique addresses, without the need to manually generate and manage each key individually.
HD wallets are considered to be more secure than traditional wallets, as they allow for the creation of new addresses for each transaction, preventing the reuse of addresses and reducing the risk of hacking. Additionally, HD wallets often include features such as multi-signature authentication and integration with hardware wallets, providing an additional layer of security.
Overall, HD wallets offer a convenient and secure way for cryptocurrency users to manage their assets, without the need for complicated key management or the risk of compromised private keys.
How To Work HD Wallet?
An HD (Hierarchical Deterministic) wallet is a type of cryptocurrency wallet that uses a hierarchical structure to generate a unique set of addresses for every transaction. HD wallets are designed to provide greater security and privacy compared to traditional wallets by ensuring that each transaction is conducted through a unique and untraceable address.
To use an HD wallet, follow these steps:
Choose an HD wallet: There are many different HD wallet options available, so it's important to choose one that meets your needs. Popular options include Ledger Nano S, Trezor, and Electrum.
Set up your wallet: Once you've chosen your wallet, follow the instructions provided to set it up. This usually involves creating a new wallet, generating a seed phrase (a series of random words), and creating a password to secure your wallet.
Add cryptocurrency to your wallet: To use your HD wallet, you'll need to add cryptocurrency to it. This can typically be done by transferring funds from an exchange or another wallet.
Generate a new address: To receive cryptocurrency, you'll need to generate a new address within your HD wallet. This can usually be done by selecting the "receive" option within your wallet and generating a new address.
Send cryptocurrency: To send cryptocurrency from your HD wallet, select the "send" option within your wallet and enter the recipient's address and the amount you wish to send.
Backup your wallet: To ensure that you don't lose access to your funds, it's important to backup your HD wallet regularly. This can usually be done by saving your seed phrase to a secure location.
By following these steps, you should be able to effectively use an HD wallet to store and transact cryptocurrency securely and privately.
FAQ Related To HD Wallet:
What is an HD wallet and how does it work?
An HD wallet, also known as a Hierarchical Deterministic wallet, is a type of cryptocurrency wallet that generates a new address for each transaction. This is achieved through the use of a hierarchical structure of private and public keys, which are derived from a master seed. This means that you can create multiple addresses for your cryptocurrency without the need to create new private keys every time. Additionally, HD wallets are more secure than traditional wallets, as they are less vulnerable to hacking and theft.
How do I set up an HD wallet?
To set up an HD wallet, you will first need to choose a compatible wallet provider. Many popular wallets such as Ledger, Trezor, and Exodus offer HD wallet functionality. Once you have selected your wallet, you will need to create a master seed, which is a long string of random words that will be used to generate your private keys. This seed should be kept safe and not shared with anyone. Once you have created your seed, your wallet will automatically generate a hierarchy of private and public keys, which you can use to send and receive cryptocurrency.
Are HD wallets more secure than traditional wallets?
Yes, HD wallets are generally considered to be more secure than traditional wallets. This is because they use a hierarchical structure of private and public keys, which reduces the risk of hacking or theft.
Additionally, because HD wallets generate a new address for each transaction, it is more difficult for someone to track your transactions or identify your wallet address. However, it is still important to take proper security measures, such as keeping your master seed safe and using two-factor authentication, to ensure the security of your cryptocurrency holdings.
Conclusion:
In conclusion, HD wallets have revolutionized the way we manage our cryptocurrency assets. With the ability to generate a practically infinite number of unique addresses, along with increased security measures, HD wallets have become the preferred choice for crypto users looking to manage their funds in a safe and convenient manner.
#gateiostartup#adreward#huobi#AD#Adtoken#Gate_io#adreward.io_airdrop#adrewardtoken#adrewardforgamers#adrewardformarketer
0 notes
Text
The Ultimate Crypto Wallet List: Top 5 in 2023
The purpose of a crypto wallet is to provide a secure place to store your cryptocurrencies and to allow you to spend them. There are a number of different types of cryptocurrency wallets, and each one is designed for a different type of user.
Here are the five cryptocurrency wallets likely to be the most popular in 2023: Ledger Nano S plus, Trezor Model T Wallet, Coinbase wallet, Crypto Defi Wallet, and Exodus Crypto Wallet.
How do you use a crypto wallet?
To utilize a cryptocurrency wallet, you must first create an account. This is accomplished by entering your name, email address, and password. You will then be handed a one-of-a-kind key to unlock your wallet.
After you have made an account, you must enter your wallet address.

This is a one-of-a-kind string of characters that corresponds to the email address you used to set up your account. Your wallet address may be found on the same page where you established your account.
Why are crypto wallets important?
Crypto wallets are vital for both individuals and firms wishing to use cryptocurrency. A digital platform that allows users to store, transmit, and receive cryptocurrency is known as a crypto wallet. It usually includes a graphical user interface for managing transactions and storing keys.
Crypto wallets are useful because they allow users to keep their cryptocurrency offline. This is significant because it enables users to protect their cryptocurrency from hackers. Furthermore, crypto wallets enable users to transfer and receive cryptocurrency without relying on a third party.
Crypto wallets are also beneficial to companies since they enable them to accept cryptocurrency as payment.
Different Types of Crypto Wallets
There are many different types of crypto wallets, and each has its own advantages and disadvantages. Before using a crypto wallet, it's important to understand the different types and choose the one that's right for you.
There are a few types of crypto wallets that are available on the market.
Cold Crypto Wallet
Wallet stored in an offline computer, such as a USB drive or hard drive. Cold wallets are the most secure type of crypto wallets because they are not connected to the internet and cannot be hacked.
Hardware wallets: Hardware wallets are physical devices that store your private keys offline and allow you to make transactions without having to connect to the internet. Hardware wallets are generally considered the safest way to store cryptocurrencies because they're not connected to the internet or any third-party servers. You can even use them on multiple devices at once.
Paper wallets: Physical representations of public addresses and private keys. You can print out a paper wallet for Bitcoin or Ethereum and store it in a safe place. This way, you will have an advantage when it comes to cyberattacks as people don't know about your wallet details unless someone steals it from you or hacks into it via malware infection (which is highly unlikely)

Hot Crypto Wallet
The wallet is stored online, such as in a web browser or on an exchange’s website. Hot wallets are not as secure as cold wallets because they can be hacked
Mobile wallets: The most popular and easiest to use. They are convenient because you can access them on any mobile device and easily import your existing crypto assets. Mobile wallets often have good security features such as 2FA (two-factor authentication) and PIN codes.
Web Wallets: Online applications that store your private keys online, but they do not hold any cryptocurrency themselves. They send and receive cryptocurrency from a digital wallet address created by the application when you use it. This type of wallet allows you to access your funds from anywhere in the world using an internet connection, as long as you have an active internet connection
Desktop Wallets: Desktop wallets are similar to web wallets in that they allow users to manage their digital assets using a web interface. However, desktop wallets are more secure than web wallets because there is no reliance on an internet connection for transactions between the client application and server
Conclusion
If you are looking for a digital wallet that can store different types of cryptocurrencies, you might want to consider a cold wallet. A cold wallet is a wallet that does not require a connection to the internet. This is great for securely storing your cryptocurrencies offline.
However, not all digital wallets are created equal. Some are more secure than others. For example, a hot wallet is a digital wallet that is connected to the internet. This is because hot wallets are typically used to store cryptocurrencies that are being traded on exchanges.
#nft crypto#crypto#cryptocurrency news latest#blockchain network#nft marketplace#blockchain#cryptocurrencies#etherum#crypto atms#bitcoin#crypto wallet#coinbase#trezor
1 note
·
View note
Text
Ledger live desktop app

#Ledger live desktop app install#
#Ledger live desktop app drivers#
#Ledger live desktop app update#
#Ledger live desktop app android#
The Ledger company constantly monitors security, updates firmware and comes up with new useful features. FIDO2 is the latest generation of the U2F protocol.
#Ledger live desktop app drivers#
U2F is an open authentication standard that enables internet users to securely access any number of online services with one single security key instantly and with no drivers or client software needed. During installation, the authenticity of the firmware is checked to avoid installing malware.
#Ledger live desktop app update#
The manufacturer is constantly improving the security system, so it is important to constantly update the firmware from the official website. Most often, recovery seeds are stored on paper, but the safer way to store them on special backup devices such as Cryptosteel. It is imperative that you keep them in a safe place. This is a wallet-generated list of words that are used to regain access to your device. This PIN code will need to be entered each time Ledger device is synchronized with Ledger Live application. This tool can protect your wallet from unauthorized access. PIN (Personal Identification Number) can be up to 8 digits long. To protect users’ funds, the following security measures are available in Ledger crypto wallets: The security section is one of the most important sections of this Ledger review. It should be remembered that bitcoins can only be sent to a bitcoin address, like other cryptocurrencies, respectively. Important! Carefully check the addresses to which you are sending your funds. The transaction must be verified on the Ledger device. Select the cryptocurrency account, recipient address, fee and amount. To send cryptocurrency go to the “Send” section. Delivery usually takes 2-5 days, but for an additional fee, you can get the wallet faster. The price of the Nano X wallet already includes free worldwide shipping (for Nano S – from 8 EUR). Choose a model on the Ledger website, make a payment and order the device. Buying Onlineīuy a hardware wallet Ledger exclusively on the official website if you want to be sure that you will receive an original device.īuying a used device, or making a purchase on any other unofficial sites, you run the risk of getting a fake. This makes Ledger an indispensable device for storing, buying and selling cryptocurrency. Secret keys are stored and transactions are performed in a secure area, so you can safely conduct cryptocurrency transactions even if your computer or mobile phone is infected with spyware. The Ledger Nano X has a built-in battery and connects to mobile devices via bluetooth. Ledger connects to a computer or mobile phone using a cable (Nano X: USB-C, Nano S: OTG cable is ordered additionally).
#Ledger live desktop app install#
Ledger Nano X is a premium model which is best suited for active and professional investors with a wide variety of crypto assets.īoth wallets can install apps via Ledger Live from a list of 5500+ crypto assets. It also comes with a modern USB-C connector for desktops and mobile devices. The wallet’s steel outer casing protects it from external damage. The device has an enlarged OLED display with 128×64 resolution and more convenient navigation, compared to the Nano S. The wallet’s private keys are stored on a secure ST33J2M0 microchip with CC EAL5+ certification and the BOLOS operating system. You’ll get access to all smart services – DeFi apps, NFTs and more – in one powerful app. Then use Ledger Live to grow your portfolio by buying, exchanging and lending crypto. Increased internal memory allows you to install up to 100 applications on the device and store any of the 5500+ coins. Manage your crypto portfolio with mobile, no wires. The device is equipped with a 100 mAh Li-On battery to control the hardware wallet via bluetooth. The Ledger Nano X is the company’s second model, which designed specifically for mobile devices. Price: 59 EUR (check price with shipping)
#Ledger live desktop app android#
Smartphones Android 7+.īox: Ledger Nano S hardware wallet, USB cable You will need an OTG kit to connect your Nano S to your desktop or smartphone.Ĭompatibility: 64-bits desktop computer (macOS, Linux, Windows) excluding ARM Processors. No battery required.Ĭonnectivity: USB Micro-B. Materials: Brushed stainless steel and plastic.

0 notes
Text
Ledger live app erc20

#Ledger live app erc20 how to#
#Ledger live app erc20 series#
#Ledger live app erc20 download#
Buterin argued to the bitcoin core developers that Bitcoin and blockchain technology could benefit from other applications besides money and that it needed a more robust language for application development : 88 that could lead to attaching real-world assets, such as stocks and property, to the blockchain. Įthereum co-founder Vitalik Buterin in 2015Įthereum was initially described in late 2013 in a white paper by Vitalik Buterin, a programmer and co-founder of Bitcoin Magazine, that described a way to build decentralized applications.
#Ledger live app erc20 series#
Additionally, many other cryptocurrencies operate as ERC-20 tokens on top of the Ethereum blockchain and have utilized the platform for initial coin offerings.Ī series of upgrades called Ethereum 2.0 includes a transition to proof of stake and aims to increase transaction throughput by using sharding. Ethereum also allows users to create and exchange NFTs, which are unique tokens representing ownership of an associated asset or privilege, as recognized by any number of institutions. Decentralized finance (DeFi) applications provide a broad array of financial services without the need for typical financial intermediaries like brokerages, exchanges, or banks, such as allowing cryptocurrency users to borrow against their holdings or lend them out for interest. Ethereum allows anyone to deploy permanent and immutable decentralized applications onto it, with which users can interact. In 2014, crowdfunded development work began went live on 30 July 2015. Additional founders of Ethereum included Gavin Wood, Charles Hoskinson, Anthony Di Iorio and Joseph Lubin. Įthereum was conceived in 2013 by programmer Vitalik Buterin. Among cryptocurrencies, Ether is second only to Bitcoin in market capitalization. Ether ( ETH or Ξ) is the native cryptocurrency of the platform. London / 5 August 2021 8 months ago ( )Įthereum is a decentralized, open-source blockchain with smart contract functionality. That covers everything you need to know when sending ERC20 tokens from your Ledger Nano S to another address.Ethereum Foundation, Hyperledger, Nethermind, OpenEthereum, EthereumJS Click on the Etherscan link at the right side of the page to check the status of your transaction. Check to make sure the details at the bottom of the pop-up are correct. Click “Send Transaction” and a pop-up will appear with the details. Your recipient’s address is in the Signed Transaction data. MyEtherWallet will then show you Raw Transaction and Signed Transaction data. If everything looks okay, confirm using your Ledger. Click “Generate Transaction.” Your Ledger will ask you to confirm the amount and the recipient address as well as the fees. If you haven’t already, go to Settings -> Contract data on your Ledger Nano S and set it to “Yes.” This allows you to transact ERC20 tokens in addition to Ethereum. If you don’t have enough Ethereum in your wallet to cover this amount, your transaction will not go through. *NOTE: You must pay the gas fee in Ethereum. We recommend using the default – it’s highly unlikely that the transaction will use the entire amount. MyEtherWallet defaults this differently for each transaction. You should now be able to see the token balance directly in MyEtherWallet, and it should be an option in the send drop-down. Find the token you want to send and “Click to Load” it. Scroll down to the “Token Balances” section on the right side. If you don’t see your token there, you have a couple of additional steps (9.1-9.4). Select which token you want to send from the drop-down. On the next page, enter the recipient’s address and the amount you wish to send. For the HD derivation path, choose “Ledger (ETH).” Select whichever address contains the coins you want to send. Next, a pop-up will appear with HD derivation path options and addresses. Select “Ledger Wallet”, and click “Connect to Ledger Wallet.” Click “Send Ether & Tokens” at the top of the page. You should manually type out the URL each time you visit to avoid phishing scams. Also on the Ledger, Navigate to Settings -> Browser Support, and set it to “Yes”.
#Ledger live app erc20 download#
If missing from your Ledger, download the app from the Ledger Manager. On your Ledger Nano S, open the Ethereum app. Step 0. The classic first step – connect your Ledger to a computer and put in your pin code. How to Send ERC20 Tokens From a Ledger Nano S If you haven’t configured your Ledger yet, take a look at our Setup Guide.
#Ledger live app erc20 how to#
In this article, we’ll show you how to send ERC20 tokens from a Ledger Nano S to another address. Thankfully, the first few steps are identical to what you did when receiving the tokens. To send these tokens, you’ll have to use MyEtherWallet. Just as with receiving ERC20 tokens, sending them using a Ledger is a little more complicated than sending Bitcoin or Ethereum.

1 note
·
View note
Photo

Dial Ledger Nano Support Number +1-877-595-1809 and get all your issues solved within no time
1 note
·
View note
Text
Best 10 ERC20 Wallets To Store Ethereum Tokens in Upcoming Days.
The Ethereum blockchain supports a large number of ERC20-compliant tokens and smart contracts, so you need to be very diligent and careful when choosing a wallet to store ERC20 tokens.

ERC20 tokens are only used on the Ethereum platform. The term ERC20 stands for “Ethereum Request for Comment,” and 20 is a unique ID number that distinguishes this token standard from other tokens. ERC20 tokens follow a set of rules and regulations on the Ethereum platform. ERC20 compliant tokens or smart contracts bring certain benefits to their users. There are very few wallets that support ERC20 token development, which makes it difficult to choose the best ERC20 wallet for you.
The Ethereum blockchain supports a large number of ERC20-compliant tokens and smart contracts, so you need to be very diligent and careful when choosing a wallet to store ERC20 tokens.
Key points to remember when choosing an ERC20 wallet:
The wallet should support ERC20 tokens.
Control the private key of the wallet.
The user interface should be simple and easy to use.
Check out the safety features.
A back-up team is available 24/7 in case any issues arise.
Active community platform for further wallet development.
List of best ERC20 wallets:
The list of best ERC20 wallets includes hardware wallets, web wallets, and mobile wallets for storing Ethereum ERC20 tokens. Now let’s take a look at some of the best ERC20 wallets for Ethereum tokens:
Cornerstone Wallet:
If security and control of your crypto assets is a priority for you, then the Keystone hardware wallet should be at the top of your list. This stylish device allows you to store private keys for over 5,000 cryptocurrencies (including ERC20 tokens) offline on a separate secure chip. Since it does not require an internet connection, the risk of hacking is eliminated. With this wallet, you have complete control over your private keys, ensuring complete control over your funds.
Designed to cater to both beginners and experienced users, the wallet offers an easy-to-use interface and step-by-step setup process that makes getting started simple. Advanced users will appreciate features such as plausible deniability, coercion PINs, and the Shamir secret sharing algorithm for key sharing. To send or receive funds, you simply connect your Keystone wallet to a web wallet or exchange and enter your PIN. The device immediately signs the transaction and returns you to your online wallet. Additionally, for enhanced security, all data on the device is deleted after each session.
Whether you’re interested in investing in popular coins like Bitcoin or Ethereum, or exploring new projects, Keystone Wallet provides a secure place to store all your valuable digital assets. This hardware wallet costs less than $200 and offers bank-grade security and an intuitive user experience.
Ledger Nano S/Ledger Nano X:
The Ledger Nano S is a hardware wallet that easily plugs into any USB port. It supports multiple coins and tokens. You can use this button to view and check all your transactions and the balance in your wallet. It is backed by a strong support team and is constantly under development, with more currencies to be included in the future. The security features of the Ledger Nano are quite strong. It is protected by a password, PIN, and seed key, making it one of the most popular and secure wallets on the ERC20 platform. Buy Ledger Nano S Wallet
The Ledger Nano X is an upgraded version of the Nano S wallet, adding some extra features. It has a USB Type-C port instead of a micro USB connection slot. It comes with Bluetooth for easy connection with your mobile devices. There are also subtle changes to the physical buttons available on the device.
My Ethereum wallet:
MyEther Wallet is an open source web wallet with a user interface that is very easy to use. It is completely safe as it is an offline wallet and no user’s personal information or data is stored in its servers. Users have full control over their private keys, so it is very secure. MEW is a hot wallet, so it is recommended not to store large amounts of funds in this wallet. However, it can be used with the Ledger Nano S, in which case it is completely safe and allows for the storage of larger amounts of funds. MyEther wallet can also be used to store coins on Trezor and Ledger Nano via its web browser.
Metamask:
MetaMask is a web wallet that is completely free to use. MetaMask browser allows you to store, send and manage your ERC20 development tokens. Users have full control over the wallet’s private keys. Users can smoothly switch between their web browser and the Ethereum network. Users can also securely access DApps and smart contracts through the wallet.
Trust wallet:
Trust is a mobile wallet. It also supports ERC20 tokens and ERC223 tokens. Users here don’t need to worry about security as all their private keys are stored locally. It supports multiple tokens such as Ethereum, Ethereum Classic, EOS, Callisto, Otum, BAT, Augur and other ERC20 tokens. Trust has also partnered with the Kyber network, allowing it to trade with other exchanges.
Visit at : ERC20 Token Development service
Lumi Wallet:
Launched in 2017, Lumi Wallet is an easy-to-use cryptocurrency wallet suitable for both new and experienced users. Lumi Wallet is a layered deterministic wallet that uses a 12-word master seed key. The wallet is available on the web as well as on mobile platforms supporting Android and iOS. Lumi Wallet is a multi-currency wallet that supports Bitcoin, Ethereum, Bitcoin Cash, EOS and ERC20 tokens. Users can exchange tokens within the Lumi wallet as it has the Changelly exchange built-in.
Coinbase Wallet:
Coinbase is one of the most secure cryptocurrency wallets for storing ERC20 tokens. It securely stores all your digital collectibles and assets. Your private keys are protected with biometric authentication capabilities. The wallet allows you to buy or sell your crypto assets through other exchanges in the cryptocurrency market.
Mist:
Mist is often considered the official wallet of Ethereum, as it is supported and developed by developers of the Ethereum blockchain. Mist is a desktop wallet that has built-in Shape-Shift trading functionality, allowing users to easily swap tokens from the wallet. In fact, it is one of the most secure wallets with the added multi-signature feature.
Guarda Wallet:
Guarda is a multi-currency non-custodial wallet that provides support for Ethereum and Ethereum-based tokens. ERC20 token storage is available on multiple platforms — web, desktop, Chrome extension and mobile devices (iOS and Android). Because Guarda is a custodial-free service, users have full control over their funds — private keys are never shared with any third parties. In addition to providing secure and cross-platform ERC20 token management, Guarda also allows users to exchange tokens through the built-in exchange service and even create their own ERC20 through an add-on service (Guarda Token Generator).
The default ERC20 token list is located in the “Tokens” section of the Ethereum wallet. Some of the key features of the ERC20 token wallet on Guarda include:
Secure Backup Cryptocurrency and Custody-Free Storage Policy
Built-in purchasing and redemption services
Widely supported cryptocurrencies
Cross-platform operation — all wallets can be easily synced between available versions
Currency-specific features for supported coins
Ledger Nano S integrated
Atom wallet:
Atom wallet is a desktop wallet. It is by far one of the best wallets as it supports all ERC20 token generator. Users have full control over their private keys and seeds as they are stored on the device itself and are not shared across the browser or server. Users are still advised to store their seed password securely for future use. Atomic wallet is also available for Android phones. iOS version coming soon. Another unique feature of the Atomic wallet is that it has its own official coin called AWC.
0 notes
Text
Exactly how to protect your electronic assets as an individual
You've got your hands on your initial cryptocurrency pocketbook. Congratulations! It's vital to shield your digital possessions when you end up being a cryptocurrency trader. Here are a few pointers you can comply with to boost the protection of your budgets.
Probably one of one of the most complicated comes in the direction of the end of the trip: where do you store your freshly acquired cryptocurrency and also what's the difference between a hot budget and also a cool budget?
Understanding Your Wallets
best digital currency exchange purses are made use of to save the general public as well as personal secrets of your account, monitor the equilibrium, conduct transactions in sending as well as obtaining the money, as well as various other features with the blockchain. Wallets are divided into 2 kinds: warm budgets and also chilly pocketbooks. Hot purses are accounts on cryptocurrency exchanges, or accounts based on on-line internet sites. Cold pocketbooks are accounts stored on an offline means: software, hardware, or paper. As a result, in order to shield private information from ending up being subjected in public and also vulnerable to cyberpunks, traders are suggested to use cool pocketbooks. For cool wallets, account tricks needed to access the cryptocurrencies are only used when trading happens and detached after that. Having and keeping a physical cold wallet in a safe place makes certain that just you have access to your account and all your funds.

When you are reviewing warm purse vs cool pocketbook, you require to take into consideration the equilibrium of access and security that you need. It's worth remembering that you don't need to definitively select either a warm budget or a cool purse remedy, you can keep a portion of your funds in each to alleviate risk while preserving availability as required.
Cold purse discussed
For any cryptocurrency possessions that you do not require instant accessibility to, it's best to keep them offline in a cool pocketbook. Keeping high degrees of security is key in crypto.
There are various selections of cool pocketbook, such as a hardware pocketbook or a paper budget. An equipment pocketbook is an external tool like a Ledger Nano S or Trezor that stores your personal keys. You must push a switch to complete a purchase, so hackers can not take control. Hardware wallet accessibility is secured behind a password or pin. In general, the funds kept on an equipment wallet are rather easily accessible, as long as you have access to the pocketbook.
A paper pocketbook is a print out of the private key and pubic address on a sheet of paper or another material. This is normally considered as a dangerous type of cold storage, since you can lose the paper or someone could conveniently discover it and accessibility your funds.
Another cold storage option is to use a protected crypto exchange like Liquid, where all consumer funds are stored in cold storage, so if you don't intend to take care of the cold store process for your funds, you can aim to Liquid to ensure your funds are totally secure, type of like a wardship service.
Hot pocketbook described
Hot wallets are extra common, but they are greater danger. There are a number of popular hot purses for the Ethereum network which work on your web internet browser, such as MyEtherWallet. If you download a purse to your desktop computer or your phone, that is additionally a warm purse because it is linked to the web.
The majority of exchanges use hot purses at the very least to some extent. This permits fast access to customer funds. Nevertheless, it likewise implies if you are storing your funds on an exchange with these practices, those funds could be in danger. The wallets are connected to the Internet, so they are always being targeted by harmful people as well as hackers.
Selecting between hot or cold purse
There's no basic answer to this concern. Every cryptocurrency user requires to review their requirements. If you are mosting likely to only hold, cold storage is the method to go. If you are preparing to carry out large trades in the near future, consider a hot pocketbook. If you are going to do a bit of both, or if you want to trade yet mitigate risk, shop funds in both hot and cold storage space.
Keeping crypto in a warm budget doesn't necessarily indicate it's harmful, it simply implies your funds are much more in jeopardy to hacking. Use the various sort of pocketbooks to minimize threat as long as you can, while preserving the access you require. If need any help keeping you funds safely, seek to Liquid. We've obtained you covered.
Tips for Keeping Your Wallets Secure
As soon as you have your funds kept in your personal purse( s), you are self-responsible for keeping your exclusive tricks safely to protect your cryptocurrency funds. Keep reading to find out exactly how you can keep your funds safe.
Usage Two-Factor Authentication
Enabling two-factor verification (2FA) on your purse is a straightforward yet efficient method to shield your sensitive information as you sign right into your account. You can pick to make use of the Google Authentication mobile application with a six-digit code that revitalizes every minute, or a biometric recognition, such as touch ID from your fingerprint.
Different Your Funds
It's a good idea to position your funds in numerous wallets rather than one location. You should keep your funds independently in a hot pocketbook for short-term usage in trading and also trading, and on a minimum of one chilly budget to safely keep your funds over time. Once you finish your deals, you should not keep your funds in the exchange in an extended amount of time.
Be Cautious of Phishing Websites and Emails
A myriad of phishing Google Ads and also e-mails are coming to be progressively fancy as well as convincing. You must always verify the address of the web sites and also e-mails of the exchanges before you enter your details to log right into your account. Take note of whether sites have proper HTTPS certificates, as opposed to only HTTP, as well as a lock symbol next to the address.
Only Use a Secure Wifi Connection
Public WiFi links could make you subjected to malicious stars. Make certain that you are making use of a risk-free and dependable WiFi connection with a strong encryption like WPA-2 protocol when you make deals on exchanges or make use of tools with information from your wallets.
Check the Address
Prior to you make any type of repayment transaction, ascertain the crypto address to make sure you are sending out funds to the appropriate place. This is to prevent the situation where malicious programs edit and paste a hacker's address as the recipient of your transaction.
Make Use Of a Separate Non-Public Email Address for Your Accounts
Also when you maintain your funds in cold storage, some cyberpunks can still handle to break your wallets. You ought to make use of an e-mail address separate from your typical personal or job usage, set a solid password and enable 2FA for your e-mail address log-in.
On A Regular Basis Update Your Device Software
In order to stop your devices from potential malware attacks, installing anti-virus software application is a great relocate to take. Having regular software program updates and infection scans can make your gadgets less at risk to such attacks.
It's crucial for you to understand just how to manage your cryptocurrencies securely and safely. These are several of the ideas will certainly aid you end up being much more wise in improving your online security and protecting your purses.
1 note
·
View note
Text
Fiction is the lie through which we tell the truth
Warnings: noncon sex (oral, m&f, intercourse)
This is dark!Steve and explicit. 18+ only.
Summary: The reader is a fic writer and her number one fan can’t get enough.
Note: This is probably the most meta shit I’ve written but for all the fic writers out there, this one if for you. Hope y’all get the good d you deserve but until then, here’s this!
Please let me know what you think in a reblog/reply! <3 please and thank you.

You let out a sigh of relief and hit ‘post’. It was almost pathetic but it was the best part of your day, or most days. Having something to share with others was nice. The fact that they enjoyed your work and your boredom-induced work made it worth the frustration.
It wasn’t real writing. You knew that. Fanfiction was a genre to be laughed at. You didn’t admit it to anyone but there was a sense of pride to go along with the shame.
That part of you was kept online. The darker parts; the lust, the angst, the fear. It all went hand in hand and no one would guess that the bookshop assistant was stevies-doll. It felt almost scandalous to have a virtual alter ego.
You closed your laptop and checked the time. More than enough to get ready for work. Plain blouse, grey pants, mary jane flats. You were the typical bookish girl with dreams that would never come true.
The bus was late. Oh well. You’d still be there in time you’d just have to forego your usual espresso. Afternoons were draining and you often needed the boost to keep from nodding off in the last hour. You really weren’t sure why the shop stayed open so late; not many came out after five for books but traffic was relatively steady in the hipster village.
Nina met you with a frown. She preferred you at least ten minutes earlier. Tardiness had seen several other clerks fired and you had been the only to make it more than a year in the shop. Three in fact. This place was like a second home. A garden of ideas to plant the seeds of your mind.
When Nina left, you rearranged the desk. You moved aside her ledger and replaced it with your notebook, two pens to the right of it. In between the chime of the door and the rare customer queries you did most of your writing. When you reached a block you’d read, but today you felt particularly inspired.
The world was saved again. The news reports had shown footage of the daring rescue. As grim as the situation was, you couldn’t help but fantasize. The first avenger with his golden hair and sharp jawline was every woman’s Adonis. At least, you thought he was the very picture of perfection.
It wasn’t obsession. That was your mantra. You often argued with yourself. As much as you thought of the great Steve Rogers, it was only admiration. It wasn’t the possessive infatuation often found on social media. It was a hobby. An escape from the world.
You bent over the notebook. The shop was empty. The dulcet tones of indie folk floated along the shelves. You set pen to paper and waited for the ring to draw you away from the world behind your eyes.
You leaned on the counter and scribbled the first line in ink. That was always the hardest part. Then again, the beginning was always more exciting than the end.
‘The day the earth went dark, there was but one beacon left to shine…’
-
It was amusing at first. The thought of another person spending so much time writing about him. That someone would fabricate an entire universe in which he was entirely different. Somewhere out there was a woman who wore the pseudonym ‘stevies-doll’.
Steve knew he should have been perturbed by the fact. The idea of another so consumed by him that they would post almost every other day about him. He couldn’t remember how he stumbled on the small blog. A decent following but nothing close to viral.
The first story he read was cute. It even made him feel warm. The second was very much the same. He clicked through to another, this one more serious. Grey and daunting. A few more and he stumbled upon one he found most interesting, the letters NSFW emblazoned across the top. He googled the acronym and clicked back to the tab. Excited almost.
When he finished, he was warm in another way. Hot, almost. The things he read, the idea of him doing them, was almost arousing. Of course, he had never done any of it. Had never been more than the perfect gentlemen. Sweet and doting. That was how love should be. But that wasn’t love, no, that story was sex. Pure, unadulterated fucking.
He forced himself away from the computer after that. He needed to sleep. He had intended to browse his email quickly but he often found himself in the oddest rabbit-holes. That was definitely the deepest. He shook his head and chuckled. It was funny.
The next morning he awoke and went about his usual routine. He was out the door by seven. Off to save the world. Or wait around for it to need saving. At Stark Tower, he listened to Tony with his eyes on his phone. It wasn’t anything important. Some recounting about how he had scared Pepper with a nano-spider.
Steve gave a half-hearted chuckle and Tony went back to his screen. “Tough audience,” He muttered to Bruce who merely shook his head.
Steve leaned against a stool and squinted at his phone. He stared at the google search. Why had he typed it in? Somewhere in the tedium of Tony’s chatter, he had keyed in the name. He hit the first link and his phone loaded slowly.
His own face stared back at him. The banner was a press photo he had taken over a year ago. His bright eyes were staunch beneath the mask as he stared off into the distance. She had posted again. His thumb hovered over ‘read more’. Did he dare?
He looked up to make sure he was not being observed. The two scientists were too distracted to care about his online activity. He stood straight and cleared his throat. “I’m gonna hit the gym,” He lied. A grumble from both scientists as they squinted at the floating screens. “Right, have fun.” Steve said dryly as he left them to their work.
He stepped out in the hall and pressed his thumb to the screen. He bent his head over the phone as he walked blindly down the halls. Neither Tony or Bruce noticed through the window that he had gone entirely the wrong way. Steve didn’t either as his eyes flitted over the screen.
‘The day the earth went dark, there was but one beacon left to shine…’
-
You couldn’t believe how much your blog had grown in the last few months. You didn’t know if it betrayed your unexciting life or your one-track mind. Both, maybe. But it made your everyday responsibilities a little less tedious.
And the messages were even better than the hit count. Several had messaged to say they loved your work and went so far as to call you an inspiration. It was flattering but it was easy to remember who you were. No Stephen King or JK Rowling. You wrote silly one shots with limited development.
Today your inbox had been steady. Every time you found yourself bored at work, you opened the app and you had another message. Most of them short or even just emojis but nice nonetheless. And there was one you were waiting to answer
So long and in depth you had to give it more than just a thanks. You opened it several times and reread it.
‘Your story is really interesting. I think the way your portray Steve is believable. In this type of writing you rarely find anything realistic but your writing feels genuine if not entirely accurate. I would say you capture the essence of Steve perfectly and his actions at least make sense.
I always enjoy your updates and even look forward to them...especially the NSFW ones. ;)’
It was one of the few users who didn't use the anonymous feature and also left a complete comment. It was refreshing and you had come to look forward to their commentary. They went by CapUSA. Another Steve fangirl who was surprisingly inactive outside your blog. Her page was almost a clone of your own. They liked every post, reblogged, and commented. What more could a writer ask for?
Original characters maybe and not just fantasies of someone who’d never know of her existence. You closed your laptop and sighed. It felt like time. You could feel the block at the back of your head. The little thrill you got was wearing off and it felt like a phase better left to fade with your emo days in high school and that month in university when you dyed your hair purple.
You readied for work. Back on days that week. Opening was always easier. It didn’t feel so drawn out. Nina would be in at one and you’d keep her company until four. It meant little time for writing. Maybe that was for the better. You needed to start planning. For the future. For something truly your own. A fantasy so detached from reality that it would make market and maybe even a dime.
That was your dream. You didn’t want to be the listless fangirl forever. Ugh, how you hated to even call yourself a fangirl. No post today, you resigned. Maybe none tomorrow. You’d have to work up the courage to announce your hiatus. Life was calling and for once a sliver of genuine inspiration.
And the bookstore. It was Shakespeare’s birthday, which conveniently was also his death day. This meant two for one on all of his works. Nina also hired actors to stand outside the shop and re-enact famous scene from the playwright’s repertoire. They wouldn’t arrive till noon but you had a lot of set-up to do. Enough to keep you from thinking of the disappointed messages that would fill your inbox.
-
Steve scrolled through the pale pink blog for the dozenth time that morning. It had been two weeks since stevies-doll posted. The longest two weeks of his life. He wasn’t sure when it had become a staple in his life. A ritual almost. He’d read her latest fic as he laid down and try to clear his head of blood and grime. Lose himself in the person she dreamed he was. The man he had come to envy. Fictional but all too real in his head.
But there was nothing. At first he re-read and read again. But that grew old. He knew almost every story by heart at this point. He could recite the intro line to most and he fell asleep as his imagination reconstructed the things he had never done.
Her banner flashed across his sight when he woke, the image of his blue eyes staring beyond him. He’d come to think of her Steve as an altar ego. The beast buried deep inside of him. He was tired of being the nation’s golden child. Their unwavering moral beacon. He wanted to be him and she had helped him figure out who he truly was.
But she was gone. No green dot above her name in the chat window, her last post dated fourteen days ago, her blog like a time capsule. The ice that had preserved him for seventy years. Where was she?
Then a thought struck him. A devious one. He had been on enough missions to know his way around a computer. He considered himself quite savvy after living nearly a decade ahead of his time. It was simple enough. He tracked down many a drug pin this way and they were often concealed behind walls of encryption. He doubted she had more than a store-bought antivirus, if that.
He climbed out of bed and booted his computer. His leg shook impatiently and he tossed his phone just beneath the corner of the monitor. He rubbed his palms together as the home screen loaded and he clicked on the browser.
Her IP was simple enough to find. Right-click, inspect. When he found it, he felt his heart jump. This was a line. A very clear one. If he did this, there was no going back. He let go of the mouse and leaned his chin in his hands. He stared at her page, split by the window of code, and his jaw ticked.
He hit back and went to the messenger. He clicked on her name and his fingertips ran over the space bar. He didn’t know what to say. He’d send her little asks about her fics but he never messaged her directly. Would she respond?
‘Hey,’ He typed slowly, his fingers sped up with each key, ‘I’m a fan of your work. I think it’s excellent. I just wanted to check in and see if you were still writing for this blog.’
He hit enter and waited. He focused on the grey dot beside her name. If she saw this, it likely wouldn’t be until morning. He checked the time and sighed. It was late. He had an early briefing with Tony and he should try to sleep.
He hovered the cursor over the x but the dot turned green and he paused. The little ‘...’ blipped in the bottom of the chat box and the ding of her reply was music to his ears.
‘Hey, sorry. I know I’ve been quiet lately. I’ve just been so busy with work. I’m a bit behind at the moment. Thank you though for following me. I always enjoy your comments :)’ He read it several times before he could reply. Before he could even think of the words to.
‘It’s okay. We all have responsibilities. Take your time.’ He wanted to tell her to hurry up but who knew? She might be someone important, like a lawyer or teacher. He could wait. As long as there was hope.
‘Thanks. I appreciate that. Really.’ That response was quicker. Curt, almost.
‘I don’t want to overstep but are you okay?’ His cheeks were hot.
‘Ah, you know, life.’
He scratched his chin as he leaned back in his chair. Slowly he sat forward and typed. It took him three tries to get it right. Concerned but not pushy. ‘Anything you wanna talk about?’ He waited. The three dots appeared then faded. Several times before her answer blipped up.
‘I don’t wanna trouble you but I appreciate you asking. Nothing I won’t get over.’
‘Ok, no problem. Just know that if you need it, I could listen. It’s could to talk about stress.’ He laughed at himself. He should take his own advice. He had a horrible habit of letting things pile up until he burst at the seams.
‘Thanks again. I’ll ttyl. I gotta get some sleep. Have a good one.’
‘You, too,’ He replied a bit too quickly. ‘Talk to you then.’
-
You were ready to post again. It had been almost a month since your last fic and you had been reluctant to return. You couldn’t help checking in daily to see your notifications and scroll mindlessly through your own content. And your offline writing had come to a halt. You were stuck and you didn’t know how else to cope but fall back on what you knew.
Your new friend had helped too. CapUSA had quickly become a stalwart of your blog. She, or he, you still weren’t sure, spoke to you almost everyday. They encouraged you to try one more fic as you mulled over a certain prompt. Why not? It would be like a writing exercise. Maybe it would help you with your original writing. Take some of the pressure off.
And you didn’t just talk about writing. You talked about the bookstore and Nina’s incessant complaints. You talked about the stresses of your lives. Friends, or lack thereof. Cap seemed a popular person and recounted stories of the latest drama. A close knit group of friends who acted more like adversaries. It was amusing and made your forget that your life was rather empty.
You hit post and smiled. That familiar rush rolled over you and you snapped closed your laptop. You were already dressed and ready for work. You crammed in the quick editing session before the bus was due and now you’d have to run for it.
Back on afternoons. It was rainy and you were soaked by the time you got to the shop. The weather always helped traffic and you ducked behind the counter where Nina was tending to the line with Cara, a new addition. The curly-haired blonde reminded you of old Hollywood. Her high cheekbones and rose lips rivaled Monroe’s.
“Do you want me to start early?” You asked as you tucked your bag under the counter between them.
“You better. I’m gone in ten and Cara’s only on til three.” Nina muttered. “We got a new shipment. Boxes are at the end of the aisles. We’ve not had a chance to touch ‘em.”
“Okay, I’ll get right on it,” You pin your name tag on and stepped back around the counter. She was in one of her moods and all the better that you avoid her until she left. You went to the end of the history aisle and opened the box against the wall.
‘You working?’ The vibration drew your attention from re-arranging the non-fiction section. The message floated in a bubble on your lock screen. You smiled. This faceless stranger felt like more. Of course, virtual friendships were often fleeting.
You glanced down the aisle, both Nina and Cara were squinting at the computer as a customer waited patiently for them to figure out their conundrum. You swiped away the lock and typed swiftly with your phone hidden behind your leg.
‘Closing. Here all night.’
‘Oh :( you got company at least?’
‘For a couple more hours. But no shortage of work. :/’
‘Damn. Should I leave you alone?’
‘Up to you. My responses might be sporadic. Boss isn’t very pleasant today.’
‘Cool. I just read your new fic.’
‘Yeah? Sorry I haven’t checked my notifications just yet.’
‘No problem. I left a comment is all.’
‘What are you up to?’
‘Taking a break from driving. I should actually get back to it. It’s a long trip.’
‘Where are you going?’
‘To see a friend.’
‘Ah, ok. Well, drive safe.’
‘I will ;) See ya later.’
‘ttyl :)’
-
‘Nina’s Nook’. Steve read the crooked moniker several times over. He couldn’t believe he was actually there. That she was inside. He made good time on the road. An eight hour trip in six. Of course, he hadn’t exactly abided the speed limit. His impatience had turned to recklessness. So unlike him.
The sky was dim. The summer nights came later and later. She’d be done in an hour. The streets were dying down and the door hadn’t chimed in almost as long. He felt nervous all of a sudden. He tried to shrug of his anxiety and took a breath.
She wouldn’t know it was him. Well, she might recognize him but she wouldn’t know he was CapUSA. He couldn’t wait to see her reaction. Steve Rogers in her bookshop. In this town. It would be a story she would recount for the rest of her life. An encounter she would never forget.
Oh, he’d make sure she remembered it.
He crossed the street. A single car passed as he stepped up on the curb. It was much quieter than New York. No honking, no shouts, no hissing sewers. He liked it. It was quaint. He stood before the door and peeked through the glass. There was no one behind the desk. But the sign read open and the lights shone in welcome.
He pushed down the handle and slowly opened the door. The bell announced his entrance and a small voice called from the corner of the shop. “One moment, please.” He heard the shuffle of books and light footsteps. She emerged from the far shelves and his lips parted at the sight of her.
He had seen her before. Her few photos on Facebook and Instagram. He had found those shortly after he ferreted out her IP. He couldn’t see much but her privacy settings allowed him a glimpse into her real life. Her smile was nicer than in her pictures.
“Sorry, I was--” She stopped short as she saw him. She blinked. He closed his mouth as hers fell open. Her voice was higher when she spoke next. “I was just sorting some stuff out. I--How can I help you?”
“Um, a friend recommended a book to me and I was passing by, I thought maybe by chance… you might have it.” He kept his voice even. The same one he used for his press conferences.
“Do you have a title?” She asked. He could see her fingers tremble. The guilt as her eyes rounded. She was thinking of all the things she had wrote about him. He was thinking of those too.
“Jeez, you know, I’ve totally forgotten but the author was, uh…” He pretended to think and his eyes drifted down her body. Her flowered blouse was boxy but her pants hugged the curves of her hips and legs. She clasped her hands together and the gesture pushed her chest together between her arms. “Margaret Archer--er, Atwood.”
“Hmm, she’s done a lot. Do you know what it’s about?” She pulled her hands apart and wiped her palms on her dark pants. His eyes followed the movement. He wanted his hands there. Wanted to feel her thighs against him.
“Something about an apocalypse...um, a character named...Snow--Snow something.” He acted like he coudn’t remember. Couldn’t recall that it was stevies-doll who had recommended the very book.
“Oh, Oryx and Crake, I think it is. It’s an interesting one.” She smiled, proud to have figured out the riddle. “If you will, it should be with our most popular books.”
She hesitated as she passed him. He followed her as she went to the shelf just beside the counter. She hovered her finger before the titles as she read them. She bent as she got lower. He admired her ass as she did. He tucked his hands in his pocket before he could reach out.
“Yeah, I think it’s in sci-fi.” She stood and peeked over her shoulder. “It’s just over here.” She led him down the narrow aisle to the end. “Starts just here so Atwood…” She scanned the shelf, “Here.” She pulled out the book and held it out to him. “We have it in hardcover too.”
He took it and felt the raised letters on the cover. “Thanks.” He didn’t even acknowledge the book in his hand. The aisle was so tight she was trapped between him and the wall. She gave a sheepish smile and he turned to press his back to the shelf. “Sorry. Go ahead.”
She nodded and squeezed past him. Her chest brushed against his torso and she pretended not to notice. Once past him, she cleared her throat. “If you need any help, I’ll be up front.” She turned before he could respond and her watched her go. He never would’ve guessed the mousy shop assistant would have such a lurid imagination.
-
You were in disbelief. It couldn’t be. Steve Rogers in your book shop? No, you were dreaming. Or was it a nightmare? Oh god, why had you written all that stuff? You needed to delete. Now. You could hear him. The floor creaked as he moved slowly down the aisle. You hoped he would’ve taken the book and gone. The longer he stayed, the worse you felt. Your cheeks were on fire.
Your phone vibrated. You swiped the screen and found a new message from CapUSA. You sighed and rubbed your eyes. You should just pretend you didn’t see it. You unlocked the phone and read the message.
‘Hey, how’s work?’
‘It’s fine.’ You answered. What could you say? Who would believe that Steve Rogers had walked in your door?
‘I just was thinking about your last fic.’
‘Oh yeah?’ You peeked over at the far aisle. The floor no longer whined with his weight.
‘Yeah, I’d love to re-enact the last scene.’
‘Sorry?’ You sent the message and it went unanswered. ‘I don’t get it. What do you mean?’
‘The one with the girl on her knees. Begging to be fucked.’
‘Okay? I still don’t understand.’ Your heart jumped. This was really weird.
‘Or maybe and I could fuck you on that counter you’re standing behind.’
You hit close and locked the phone. You dropped it and looked around the shop. You rushed out from behind the counter and glanced out the window. You turned the latch and the floorboards groaned. You turned and pressed yourself to the door. You forgot he was there.
How could you forget something like that?
“Sorry, uh, we’re closing up,” You felt around for the lock, “I was just--”
“That’s okay. I think I’m just about done.” He slapped the book against his palm and placed it on the corner of the counter. He set his phone on top of it with a flourish. “Why don’t you flip the sign and we can get started.”
“What are you--”
“Do you prefer I call you by your real name or stevies-doll?” He leaned against the counter and smirked. “Or I can just call you doll. I know you like that.”
“No,” You exhaled shakily, “Y-you can’t be…”
“You’re not happy to see me?” He asked. He didn’t sound like the hero you saw on the news. Barely looked like him now. His pupils dilated to darken his blue eyes and the shadows of the shop cast his face in sinister tones. “You can call me Stevie if you like.”
“I...What I wrote, it was just...” You spluttered. “I’m s-sorry.”
“You don’t have to be.” He pushed himself away from the counter. “I’m not mad. Intrigued really.”
He stepped closer and your ears pounded as the adrenaline coursed through your veins. You turned and fumbled with the lock. The door opened an inch before his hand slammed it shut again. He easily flipped the lock back into place and spun the sign with a flick of his thumb.
“You can close early and we can have some fun...maybe inspire a new fic.” His arm was around your waist and you grabbed onto his thick wrist.
“They’re just stories.” You kicked as he pulled you away from the door. He tugged the blind down over the window. “Stupid fantasies.”
“Well, consider this a dream come true, doll,” He spun and let you go. You collided with the desk and gasped as the air was knocked from your lungs. “I think you remember this scene.”
“What do you want?” You clung to the desk as you turned to him.
“You know, I’m everything people think I am. Straight-laced, valiant, boring.” He planted his feet and stared you down. “Or was...until I found your blog.” His tongue ran across his bottom lip. “It gets lonely on the road. At first, your blog was like a secret companion. It gave me something to look forward to but then it made me think. So many things I never even knew I was missing out on.”
“Please, I don’t know what you want from me,” Your voice cracked. Your fear surged and left you shaking against the counter.
“I want…” He tilted his head and his eyes flashed, “You.” He paused and pushed his shoulders back. “On your knees.” Your eyes rounded, “Oh yes,” He raised a finger, “Naked.”
You stared at him. You were frozen in place. The counter your only support from melting into a puddle. His nostrils flared as he exhaled; long and drawn out.
“Don’t make me repeat myself,” He snarled and his hand balled into a fist.
You gulped and held yourself with one hand against the counter as you bent to unlace your oxfords. You kicked them off with your socks and mustered your strength. You stood on your own and unbuttoned your shirt. You kept your eyes on the aged carpet stretched across the hardwood.
You dropped the blouse onto your shoes and unzipped your fly. The wool trousers slid halfway down without help and you untangled your legs from them. You added them to the heap and stood straight.
“Look at me,” Steve ordered. Your eyes snapped over to him. “Good.” You reached back and he raised a hand. “Stop...I wanna do it.”
He waved you forward and slowly you stepped away from the counter. He bared his palm in a gesture for you to halt and you hung your head. “Eyes up.” He corrected as he came closer. He walked around you and stopped just behind you.
His thick fingers touched the band of your bra and ran along it until they met at the hooks. He carefully unclasped it and the cups fell loose. He tickled your arms as he pushed the straps down them. He took it and flung it away from him. His hands came up to cup your tits and he pushed himself flush to your back.
“You always wrote so vividly of me but...I never knew how beautiful you truly were...how good you feel.” He squeezed and slowly lowered his hands. He dragged them to the side of your panties and slipped his fingers beneath the elastic. He bent as he guided the panties down your legs. “God, that ass.”
You shivered and his hands cradled your ass. He ran his rough palms along your cheeks and up your back. They settled on your shoulders and he pushed down firmly. “On your knees.”
He stepped back and you unsteadily got to your knees. He walked another circle around you. You could hear his dusky breaths. Glimpsed how his hand ran over the front of his jeans.
“Now ask, like a good girl,” He stopped before you and stared down with a smirk. “Go on, doll, I know you want it.”
You closed your eyes and swallowed. You grit your teeth and gather what was left of your wits. A story. That’s all this was. The letters could be backspaced and no one would know better of it.
“Please,” You recalled the last scene you had posted. The tingle which had flowed through you as you hit the button. What had she said? You opened your eyes. “Please, I want to...I want to make you happy.” You shuddered as the words whisked from you. “Can I?”
“Can you...what?” He taunted.
“Can I suck your dick?” It was barely a whisper.
“Oh, well, since you asked so nicely,” His hands were on his belt as he spoke. “But I have a different scene in mind for tonight. A new one.” He unbuckled his belt and cracked his neck. “I want you on the counter. On your back.”
You made to stand and his hand went to your head. He held you down.
“Crawl.”
You weakly dropped forward and turned. You crawled on hands and knees as he followed, stopping just in front of the desk as you followed his pointed finger to the other side. You stood and lifted yourself onto the counter and laid on your back. He guided your head over the side as he pulled you close and his hands found your tits again. He tweaked your hard nipples and you bit your lip.
He rescinded his hands and finished unzipping his pants. You tried not to watch as he pushed his pants down, his briefs too. The blur focused and you gaped at the size of him. He gripped himself and you snapped your mouth shut. He grabbed your chin and squeezed.
“Now, now, don’t act like this isn’t what you wanted,” He pressed his cock to your mouth and you were forced to open as his fingers threatened to crush your jaw.
He slid inside and your gasp was stifled as he met the back of your throat. He forced himself further and you threw your arms out. A clatter of books and papers as you swept them off the counter. He lingered at his limit and wiggled his hips. You arched your back as you choked and he grabbed your tit, kneading it as he slowly pulled out.
He pushed back in just as you gulped down air and you writhed atop the desk. He thrust in and out of your mouth. You gagged and groaned. The noises only fueled his fervour and he sunk in over and over until your head pulsed. The spit smeared around your lips and his balls.
He pulled back and slammed back in suddenly. His motion slowed as he came. He grunted, his breaths stuttered by the staggered rock of his pelvis. You clawed at the counter top and kicked until you could breathe again.
He slipped his cock from between your lips and his cum leaked from your mouth. You sat up and coughed. His hands were on your shoulders again. His fingers danced along your throat as if to ease your struggles.
“Come on, that’s just the first act,” He drew away and you glanced over your shoulder. “Turn around.”
You turned on the desk and he pulled your legs over the edge. He pushed your knees apart and stepped back to admire the view. You dug your nails into the lip of the counter to keep yourself from closing your legs.
“I know you’ve been dying to see this,” He grinned and pulled his shirt over his head.
His cock hung out of his pants. It twitched as he tossed his shirt at you. You caught it. It smelled like him. He shoved his pants down without pause and he hardened again. You dropped his shirt and looked away guiltily.
Had you not written this scene a dozen times over?
He was completely naked when you looked again. He came close, his hands on your knees as he knelt before you. You tried to pull your legs together but he held them apart. He shook his head and tutted.
“Just sit back and enjoy,” He licked his lips. “Trust me, it’s better than you could ever imagine.”
Your shock took over completely. You watched as he bowed his head and you felt his hot breath on your thighs. When his tongue met your pussy you gasped. He delved between your folds and swirled around your clit. Your nails went deeper into the wood and your thighs shook. It felt good. It shouldn’t, though.
He buried his face deeper and you watched his golden locks from above. He reached over blindly, his large hand found yours, and he guided it to the back of his head. He held it there a moment before letting go. You clung to him as he hands glided up your thighs and he framed your vee with thumb and index.
You arched your back and moaned. It was your declaration of surrender. You couldn’t resist it any longer. The heat stirred inside of you, the flames licking at your thighs and back. You urged Steve closer though he couldn’t possibly go any deeper.
His hands slipped down to the outside of your thighs. Your legs closed around his head and held him there. He tipped you slightly and you curled around him as he continued to lap. Your breaths mixed with throaty hums and you fell back.
You had one hand still on his head and the other in your hair as you cried out in a mighty climax. He didn’t stop until you were shaking across the counter. When at last his mouth left you, you shivered. A sudden coolness washed over your body. He stood and you looked at him through the haze.
He grabbed your waist and pulled you to your feet. You wavered and he spun you quickly. You caught yourself on the desk and he slapped your ass. “That’s it,” He purred. “You’re getting it now.”
He nudged your shoulder until you were bent entirely over the counter, your toes barely met the floor. He rubbed your ass and pulled your cheeks apart. His cock poked you as his hand slipped lower and he tickled just below your ass. You squirmed and he chuckled.
He felt around and his cock slipped lower as he bent his knees. He dragged his tip along your folds before prodding at your entrance. He shoved his hand between your legs and forced them apart.
He pushed inside and slowly stretched you around him. Your head shot up at the strain. A mix of pain and pleasure as he got deeper and deeper.
You whined as he bottomed out and his hips bucked almost instinctively. He hit your cervix and you cried out. He eased out and pushed back in. He repeated this again and again, his motion careful. Deliberate. He brought his pelvis flush to your ass and groaned.
“Fuck,” He slapped your ass again.
He drew back and slammed into you all at once. All restraint was lost and he thrust mercilessly. His pace was wild. You reached out to grab at the edge of the counter, your hips hitting the other painfully. The spark had caught and you felt the flame about to burst.
Your orgasm was surprising. More agony than pleasure. You whimpered and pushed your head into the counter as you heaved. You could barely breath as Steve never wavered. He fucked until you until your walls ached. Until they turned numb and you were nothing but a mewling fool before him.
He bent over your, his muscled torso against your sweaty back. He rutted atop you frantically. His hips jerked as his grunts deepened. His breath caught and he swore. He lifted himself off you and you felt the warmth spill down your ass and thigh.
You laid breathless as he panted behind you. He rubbed his cum into your skin with two fingers and you shook. You tried to push yourself up from the desk. He caught your hip and shoved you back down.
“Oh, we’re not even close to the finale,” He pinched your ass and you squeaked. “Not to mention the epilogue.”
-
tags to be added in reblog
#steve rogers x reader#dark!steve rogers x reader#dark steve rogers x reader#fic#steve rogers fic#au#marvel#mcu#captain america#dark!steve rogers#dark steve rogers#steve rogers#dark!fic#dark fic#dark!verse#darkverse
1K notes
·
View notes
Text
The world is pacing towards advancement. With advancement comes the technological development. In order to adapt to the dynamic environment of this era, one needs to stay updated. The survival of businesses today depends upon the continuous and consistent adaptation to the dynamic technological advancement.
Cryptocurrency
Cryptocurrencies are one of the latest introductions in the world of technological advancement. Cryptocurrencies are one of the digital currencies which are present in digital form which cannot be accessed physically but holds all the properties of physical currencies. It is used as a medium of exchange just like physical currencies. The difference is that it is stored in computerized database using asymmetric key called ‘cryptography’ to keep it confidential.
Unlike other digital bank currencies, the control of cryptocurrency is decentralized. It is done through the virtually distributed ledger record termed as blockchain. Blockchains are records of the timestamp and transaction data. The decentralized control implies public financial transaction database distributed on a computer network.
The public key encryption or cryptography guarantees safely running of currencies on that computer network. It is made sure that the transaction requests are kept confidential, the identities are verified and protected and the ‘double’ virtual spending of these currencies is made impossible. The private key is used while spending the crypto currency.
Bitcoins
There are several cryptocurrencies present in the digital world today. Bitcon, Litecon, Tether, XRP, Ethereum, Chainlink, Cardano, Polkadot and Binance coin are some of them. The largest market capital in the digital world is covered by ‘bitcon’.
Bitcon was released in 2009 as open source software by an anonymous individual or group under the name of ‘Satoshi Nakamoto’. Bitcoins promises lower transaction fees compared to other online transaction mediums. It is the digital crypto currency that means it is controlled by decentralized computer networks. It is traded, distributed and stored in digital ledger, blockchain. It has gained popularity in the digital marketplace and therefore inspired other crypto currency creation in the blockcahin space.
Bitcoins are created as a result of reward mechanism termed as mining. The mining is to done through software that tries to solve a difficult math problem. After the solution is known, the miner makes the solution public in the block.
Each bitcoin is a computer file stored in digital wallet, which could be an app in either a smartphone or computer. Bitcoins are stored in crypto wallet, which stores digital assets.
Crypto Wallet
Digital assets need to be stored in the safest way possible. Crypto wallets could be taken as physical wallets which stores digital security keys or crypto currency tokens.
A crypto wallet is basically software that stores the public and private keys of the crypto currency, send and receive the crypto currencies, keep the balances in check and network in the blockchain mechanism. If you want to securely store your digital assets you need to have a crypto wallet. Crypto wallet can be categorized into hot and cold storages.
Hot storage
The crypto wallet that can be accessed anytime as it is online is termed as hot storage. It is preferred by the users who trade frequently and need to monitor their balances. It is connected to the internet and therefore is more vulnerable. Hackers and malwares can affect hot storages.
Hot storages are handy when you opt to use the daily services that includes, online banking, online transfer, online shopping and so on. With convenience comes risk! Hot storages can be made secure with passwords and pins but these security measures are still vulnerable.
If the private key is hacked or stolen the owner might lose all the coins present in the crypto wallet. This is where the ‘cold storages’ comes in.
Cold storage
Cold storage in the physical world implies food storage for a longer period of time. Similarly if the user wants to hold the digital assets for longer period of time, they opt for cold storage. In simple words, cold storage is offline crypto wallet not connected to internet therefore keeping it safe from the vulnerabilities that might include unauthorized access and cyber hacks.
Cold storage therefore is the storage that signs the private keys of the crypto currency offline. A transaction first is transferred to offline device which may be a USB, CD or any hardware device before transacting online. Signing it in the offline device before transferring it online is the main mechanism of cold storage security. Since the private key does not come into contact directly with the online server; the hacker cannot access the key. With cold storage the risk factor is somewhat completely removed but in addition to it, cold storage makes the transaction quite difficult.
Cold storage includes app, website or any hardware device that manages your transaction and stores the private keys. Cryptocurrency users must check the compatibility of the cold storage wallets with the coins they use. Not all digital assets are compatible with all the cold storage wallets available. There are several options to opt from.
Cold Storage Wallets to choose from
When huge amounts are involved, the best and safest mode of storing the cryptocurrencies is using ‘cold storage’ wallets. There are a number of cold storage wallets in the digital marketplace today. Based on the functionality, convenience and security some are more popular than others.
Hardware Wallets
The safest and sturdiest mode is the hard wallet option for storing the cryptocurrencies. The wallet is in the form of electronic device where you can sign the transaction by using your private keys. These signatures are stored offline on your device. If you happen to lose the device the data can be backed up using the device’s backup seed key. With all the above benefits comes the price tag.
The most used hardware wallets used includes:
Ledger nano S
It is the most popular amongst the available hardware wallets. It is USB flash drive which means it is easy to carry. It can contain more than a thousand cryptocurency tokens! It is priced relatively higher for the security and functionality it offers.
Ledger nano X
It is the upgraded version of the Ledger nano S. It has all the features of the Ledger nano S and in addition to it, it also has some upgraded functionalities. It has a larger screen, battery with larger capacity and Bluetooth feature. You can also install more than 100 wallet apps.
Terzor Model T
The terzor model is not as stylish as the Ledger nano series but it is safe and secure mode of storing your cryptocurrencies. The terzor model T is the second model from the terzor series. It has a large touch screen and it comes with a requirement to set a passphrase of pin before you can enter the hardware wallet. This means you do not have to use a mobile or computer device as it is a standalone device. It can contain up to 1100 cryptocurrencies!
CoboVault
It is open source wallet – Secure Element Firmware. You can see how your private keys get derived from the physically generated entropy and how it stays confined to the element.
The pros of the Hardware wallets
· Restorable
· Secure
· Cannot be copied
· Not perishable
The cons of Hardware wallets
· Expensive
· Breakable
· Not a free resource
· Not waterproof
Paper Wallets
The wallets that are used against the safety of cyber hacks and malwares by the involvement of printing the private keys are the paper wallet. It also has a QR code that can be scanned and added to a software wallet to make transactions quicker. For additional safety it is recommended to duplicate an additional copy of the keys and encrypt it.
Pros
· Easy to carry
· Free to use
Cons
· One can see and steal it
· Burnt or torn easily
· Not waterproof
· Not restorable
Sound Wallets
The sound wallets are not so popular cold storage wallet used to store the cryptocurrencies. Sound wallet encrypts the private keys in audio files and stores it in devices like compact discs (CD). The encryptions can be decoded using a spectroscope app.
Pros
· Secure
· �� Restorable
· Price efficient
· Waterproof
Cons
· Not an easy way
Desktop Wallets
The desktop wallet includes the encrypted files of the private key in your desktop computer. The encryption is done in an offline environment. The keys are stored offline on your computer but when you transfer them you connect your machine to the internet.
Pros
· Easy to use
· Price efficient
Cons
· Possibility of physical damage
· Not restorable
The Takeaway
Today cryptocurrencies are becoming popular with the advancement of technology. Not only the business world but even investors consider the cryptocurrencies as investment opportunity. With ever changing technological uncertainty and vulnerability cryptocurrency storage should be given more attention. The most secure mode of storage is the ‘cold storage’.
Choose the cold wallet as per your need, budget, functionality, safety and convenience. Digital assets need to be stored in digital wallets. And cold wallets are the best digital wallet in the digital marketplace. Secure your cryptocurrency today to prevent yourself from the hassle of tomorrow.
#cryptocurreny trading#cryptography#cryptocurrency#bitcoin#digital wallet#digitalbusiness#writing#writer#writingblr
2 notes
·
View notes
