#List of Journal Management Software
Explore tagged Tumblr posts
Text
Peer Review Software vs. Traditional Peer Review
In the academic publishing world, the peer review process plays a pivotal role in ensuring the quality, integrity, and credibility of research before it reaches the public. Historically, this process has been manual and often painstakingly slow. However, with the rise of peer review software, there is now a revolutionary way to handle manuscript submissions, reviews, and revisions.
In this blog, we will delve into the comparison between traditional peer review and peer review software, examining why peer review software is increasingly being seen as the better option for modern journals.
Understanding the Traditional Peer Review Process
The traditional peer review process has been the cornerstone of academic publishing for centuries. Typically, once an author submits their manuscript to a journal, the editor assigns it to one or more experts in the field for review. These reviewers critically evaluate the manuscript's quality, relevance, and originality, providing detailed feedback for the author and the editor to consider.
Steps in the Traditional Peer Review Process:
Kryoni JMS and Stream Space offer a unique, integrated solution that addresses the unique challenges of academic publishing. Our platforms provide:
Submission: The author submits the manuscript to the journal.
Reviewer Assignment: The journal editor manually assigns the manuscript to reviewers based on their expertise.
Reviewing: Reviewers read the manuscript and provide feedback on its quality, validity, and significance.
Decision: Based on the reviews, the editor decides (accept, reject, or revise) and communicates it to the author.
Revisions: If revisions are requested, the manuscript goes back to the author, who makes changes and resubmits it for further review.
While this process has served journals well for many years, it is not without its challenges.
The Drawbacks of Traditional Peer Review
While the traditional peer review system is deeply rooted in academic publishing, it has several limitations that can hinder its effectiveness and efficiency.
Lengthy Turnaround Time: The process of traditional peer review can be incredibly time-consuming. Manuscripts may sit in the queue for weeks or even months as reviewers take time to read and provide feedback. Moreover, delays are common, as finding available reviewers can sometimes take longer than expected. As a result, the time from submission to publication can be extensive.
Limited Transparency: Traditional peer review often operates behind closed doors, with the identities of reviewers remaining anonymous. While this anonymity is intended to ensure impartiality, it can also contribute to a lack of accountability and transparency. In some cases, this system can lead to biased decisions or conflicts of interest that are difficult to detect.
Reviewer Fatigue: Reviewers are often volunteers and may already have a heavy workload. This can lead to reviewer fatigue, which in turn affects the quality of the feedback provided. Reviewers may also take longer than necessary to complete their assessments, further slowing down the process.
Administrative Burden: For journal editors, managing the peer review process manually is a daunting task. They must track submissions, assign reviewers, monitor progress, and send reminders. These tasks are repetitive and prone to error, which can add considerable strain on editorial staff.
Why Peer Review Software Is a Better Solution
In contrast to traditional methods, peer review software offers a comprehensive, streamlined approach that addresses many of the challenges mentioned above. This software simplifies the process for authors, reviewers, and editors alike, making it the ideal solution for modern academic publishing
Speed and Efficiency: One of the most significant advantages of peer review software is the speed at which it can accelerate the review process. By automating key functions such as reviewer assignment, reminders, and submission tracking, peer review software significantly reduces the time required to move a manuscript through the review pipeline. Automated workflows mean that editors can spend less time managing logistics and more time on quality control.
Enhanced Transparency and Accountability: Many peer review software platforms offer transparent workflows, allowing reviewers and authors to see the status of a manuscript in real-time.
Better Collaboration: Peer review software fosters improved collaboration between authors, reviewers, and editors. The integrated platform allows all stakeholders to communicate directly within the system, eliminating the need for scattered emails and documents. This real-time collaboration ensures that feedback is clear, concise, and actionable, helping authors to make more informed revisions.
Scalability: As journals grow and receive an increasing number of submissions, managing the review process manually becomes impractical. Peer review software is highly scalable, able to handle large volumes of submissions simultaneously. This scalability allows journals to process submissions efficiently, even as they expand in scope.
Reduced Administrative Workload: Peer review software automates much of the administrative work traditionally handled by editors and journal staff. From assigning reviewers to sending reminders, tracking the status of submissions, and managing reviewer feedback, the software reduces manual labour. As a result, editorial teams can focus on high-level decision-making and quality assurance, rather than getting bogged down in repetitive tasks.
Higher Quality Reviews: Because peer review software can track reviewer performance and allow for easy reassignment, journals are able to maintain high standards for their reviewers. With robust feedback mechanisms and detailed tracking of review quality, journals can ensure that only qualified experts are providing feedback. Additionally, software can help prevent issues like duplicate reviews or missed deadlines, further enhancing the quality of the review process.
How Peer Review Software Enhances the Publishing Workflow
The automation, transparency, and improved collaboration offered by peer review software lead to a smoother and faster publishing workflow. The software not only shortens review cycles but also improves the overall quality of the final published content. Here's a look at the typical workflow for journals using peer review software:
Automated Submission Management: Authors submit manuscripts directly into the system, which automatically sorts and categorizes them for easy review.
Reviewer Assignment & Management: The system matches manuscripts with appropriate reviewers based on expertise and availability, sending automated notifications to all parties.
Collaborative Reviewing: Reviewers submit their feedback via the platform, allowing for easy communication with the editor and author
Final Decision & Communication: The editor uses the feedback from reviewers to decide, and the results are communicated to the author, who can then make revisions and resubmit.
Track Changes & Revisions: Authors submit revised versions of their manuscript, and the process continues until the manuscript is ready for publication.
Why Peer Review Software Is the Future of Academic Publishing
Peer review software is not just a tool; it’s a game changer in academic publishing. It accelerates the review process, increases transparency, and enhances collaboration, all while reducing administrative burdens. For journals seeking to improve the speed and quality of their publishing workflows, adopting peer review software is essential.
Kryoni Advanced Peer Review Solutions: Revolutionizing the Publishing Process
We understand the complexities and challenges of academic publishing, which is why our peer review software is designed to streamline and optimize every aspect of the review process. With Kryon’s innovative technology, journals can:
Efficient Review Process: Accelerate the review cycle with automated tasks, reducing time spent on administrative work.
Flexible Workflow Customization: Tailor workflows to fit your journal’s unique needs, allowing for personalized processes that match your editorial structure.
Reviewer Expertise Matching: Automatically match manuscripts with reviewers based on their expertise and availability, ensuring the right feedback from qualified professionals.
AI Scope Check: Utilize artificial intelligence to assess the scope and relevance of the manuscript, ensuring it aligns with the journal’s focus areas.
Plagiarism Checking: Integrate advanced plagiarism detection tools to maintain academic integrity and avoid content duplication.
By choosing Kryoni peer review software, your journal can modernize its publishing process, improve turnaround times, and enhance the quality of its content. Don’t let traditional review methods hold you back—upgrade to Kryoni peer review software for journals and experience the future of academic publishing.
#academicpublishing#List of Journal Management Software#Manuscript Submission Software#Academic Journal Publishing Software#Manuscript Management System#Best Peer Review System for Journals#Editorial Management Software#Journal Peer Review Software
0 notes
Text
How to Write Character Goals More Effectively
As writers, creating character goals can sometimes feel overwhelming, especially when we're on the spot trying to decide what drives them. To help, I’ve compiled a list of goals to inspire your character-building process and add depth to your story.
Personal Goals
Personal goals contribute to character growth and make them complex and relatable. They also bring your story to life:
- Learn a new language
- Practice mindfulness and meditation
- Develop a growth mindset
- Enhance time management skills
- Become proactive
- Master new technology or software
- Start a new craft or hobby
- Improve public speaking skills
- Build self-confidence
- Refine writing skills
- Practice communication skills
- Acquire a new skill
- Become more organized
- Accept limitations
- Hone decision-making abilities
- Cultivate gratitude
- Stay open to new opportunities
- Improve financial literacy
- Diversify cooking knowledge
- Learn to play an instrument
- Solve problems creatively
- Pick up a new sport
- Start a blog or online journal
- Learn to code or build websites
- Become a mentor
- Practice active listening
- Be more empathetic
- Forgive oneself
- Learn to say no
- Manage stress effectively
- Gain emotional control
- Develop patience
- Strengthen resilience
- Foster optimism
- Embrace change
- Live in the moment
- Enjoy simple pleasures
- Appreciate small things
- Explore creativity
Family and Friends
Improving relationships and family dynamics can add rich layers of character development and bonding moments:
- Plan a family vacation
- Spend quality time with loved ones
- Strengthen relationships
- Organize a family reunion
- Host weekly game nights
- Volunteer together
- Enhance communication skills
- Enjoy outdoor activities together
- Practice patience with others
- Expand the family
Finance
Financial goals can introduce real-world challenges that make your characters more relatable:
- Pay off debt
- Create and stick to a budget
- Invest wisely
- Save money consistently
- Consult a financial advisor
- Achieve financial freedom
- Start a side hustle or part-time job
- Negotiate better deals
- Build financial literacy
Career
Professional aspirations are key to relatable character arcs:
- Earn a promotion or raise
- Change careers
- Become their own boss
- Start a business
- Learn new career-related skills
- Network with peers in their field
- Attend career development seminars
- Volunteer professional skills
- Mentor others
- Improve their resume
Travel
Travel goals add excitement, exploration, and opportunities for plot-building:
- Visit a new country
- Explore their local area
- Embark on a road trip
- Experience a cruise
Conclusion
This list provides a starting point for creating meaningful character goals that enhance their journeys and make your story stand out. Whether you use these ideas or create your own, the key is to craft goals that resonate with your characters' personalities and ambitions.
Happy writing!
#writing community#creative writing#writing tips#writingjourney#fiction writing#charactergoals#character development#plotbuilding#story writing#author life
21 notes
·
View notes
Text
April 11, 2025
HEATHER COX RICHARDSON
APR 12
READ IN APP
On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command.
Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem.
Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors. Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?”
The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.”
The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
—
16 notes
·
View notes
Text

Matt Davies
* * * *
LETTERS FROM AN AMERICAN
April 11, 2025
Heather Cox Richardson
Apr 12, 2025
On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command.
Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem.
Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors. Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?”
The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.”
The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#political cartoons#Matt Davies#The Big Chill#Heather Cox Richardson#Letters from An American#personal data#the right to privacy#identity theft#mistaken identity#SCOTUS#secretary of defense#homeland security#incompetence#data mining#data weaponization
15 notes
·
View notes
Text
I started writing "4 srs" this month and I like how free and accessible writing is, so I'm recommending free software I've experimented with that might help people who want to get into the hobby!
“Specifically Created for Writing Stories”
-------------------------------
Manuskript – Story organizer / word processor. Has an outliner and index card function, along with distraction free mode. Lets you switch between different templates such as a non-fiction mode or a short story.
Bibisco – Novel writing software that includes writing goals, world-building, distraction free mode, and a timeline.
“I Just Want to Write”
---------------------------
LibreOffice – Microsoft 365 alternative, but free! LibreOffice Writer is what I wrote this tumblr post in before I posted it. Also if you copy & paste the text into the Rich Text Editor on AO3, it seems that it actually converts it properly. Nice! No need for scripts.
Note-Taking
-------------------------------
Zim Wiki - note taking application that is very, very lightweight (1.1mb). It functions with a tree structure, so I’d personally recommend it for world-building and character bios. There are built-in plugins that also turn it into a good software for task management (it even has a article on how to use it for GTD) and journalling. See also: CherryTree (2mb), which is a more outdated-looking app, but functions similarly.
Obsidian MD – The Big Boy. markdown note editor that has been adopted by personal knowledge management fans---if it doesn’t do something you want it to do, just look in the community plugins to see if someone has already done it. Some unique non-word processing related usages I’ve found is the ability to create a table of contents dashboard, a image gallery for images, embedding youtube videos and timestamping notes, so forth.
Logseq – A bullet point based markdown note editor that also has PDF annotations, Zotero integration, flashcard creation, and whiteboards. Best used for outlining projects due to the bullet point structure.
Joplin – A modern app comparable to Zim Wiki, it’s basically just a note-taking software that uses folders and tags to sort easier. Looks prettier than Zim Wiki and Cherry Tree
Notion – An online-only website that allows usage of different database types. Free for personal use. Note: I dislike the AI updates that have been making the app lag more. I prefer the others on this list.
Mind Maps
-------------------------------
Freeplane – So much goddamn features, including a ton of add-ons. Looks somewhat ugly, but it works for anyone willing to spend a while learning how to use it.
Mermaid – Text-based diagram creator. Can be used in apps like Joplin, Notion, and Obsidian.
Obsidian’s Canvas – A core plugin for Obsidian, it deserves its own mention in that it allows you to create embedded notes of the mindmap nodes. Thus, if you want to create a 20-page long note and have it minimized to the size of a penny on the mindmap, you could.
Other Things That Might Be Of Interest
Syncthing - A free software that allows you to sync between two or more computers. Have a desktop but also laze around on a laptop in bed, coming up with ideas?? This is your buddy if you don't want to use a online software.
124 notes
·
View notes
Text
Are Game Blogs Uniquely Lost?
All this started with my looking for the old devlog of Storyteller. I know at some point it was linked from the blogroll on the Braid devlog. Then I tried to look at on old devlog of another game that is still available. The domain for Storyteller is still active. The devblog is gone.
I tried an old bookmark from an old PC (5 PCs ago, I think). It was a web site linked to pixel art and programming tutorials. Instead of linking to the pages directly, some links link led to a twitter threads by authors that collected their work posted on different sites. Some twitter threads are gone because the users were were suspended, or had deleted their accounts voluntarily. Others had deleted old tweets. There was no archive. I have often seen links accompanied by "Here's a thread where $AUTHOR lists all his writing on $TOPIC". I wonder if the sites are still there, and only the tweets are gone.
A lot of "games studies" around 2010 happened on blogs, not in journals. Games studies was online-first, HTML-first, with trackbacks, tags, RSS and comment sections. The work that was published in PDF form in journals and conference proceedings is still there. The blogs are gone. The comment sections are gone. Kill screen daily is gone.
I followed a link from critical-distance.com to a blog post. That blog is gone. The domain is for sale. In the Wayback Machine, I found the link. It pointed to the comment section of another blog. The other blog has removed its comment sections and excluded itself from the Wayback Machine.
I wonder if games stuff is uniquely lost. Many links to game reviews at big sites lead to "page not found", but when I search the game's name, I can find the review from back in 2004. The content is still there, the content management systems have been changed multiple times.
At least my favourite tumblr about game design has been saved in the Wayback Machine: Game Design Tips.
To make my point I could list more sites, more links, 404 but archived, or completely lost, but when I look at small sites, personal sites, blogs, or even forums, I wonder if this is just confirmation bias. There must be all this other content, all these other blogs and personal sites. I don't know about tutorials for knitting, travel blogs, stamp collecting, or recipe blogs. I usually save a print version of recipes to my Download folder.
Another big community is fan fiction. They are like modding, but for books, I think. I don't know if a lot of fan fiction is lost to bit rot and link rot either. What is on AO3 will probably endure, but a lot might have gone missing when communities fandom moved from livejournal to tumblr to twitter, or when blogs moved from Wordpress to Medium to Substack.
I have identified some risk factors:
Personal home pages made from static HTML can stay up for while if the owner meticulously catalogues and links to all their writing on other sites, and if the site covers a variety of interests and topics.
Personal blogs or content management systems are likely to lose content in a software upgrade or migration to a different host.
Writing is more likely to me lost when it's for-pay writing for a smaller for-profit outlet.
A cause for sudden "mass extinction" of content is the move between social networks, or the death of a whole platform. Links to MySpace, Google+, Diaspora, and LiveJournal give me mostly or entirely 404 pages.
In the gaming space, career changes or business closures often mean old content gets deleted. If an indie game is wildly successful, the intellectual property might ge acquired. If it flops, the domain will lapse. When development is finished, maybe the devlog is deleted. When somebody reviews games at first on Steam, then on a blog, and then for a big gaming mag, the Steam reviews might stay up, but the personal site is much more likely to get cleaned up. The same goes for blogging in general, and academia. The most stable kind of content is after hours hobbyist writing by somebody who has a stable and high-paying job outside of media, academia, or journalism.
The biggest risk factor for targeted deletion is controversy. Controversial, highly-discussed and disseminated posts are more likely to be deleted than purely informative ones, and their deletion is more likely to be noticed. If somebody starts a discussion, and then later there are hundreds of links all pointing back to the start, the deletion will hurt more and be more noticeable. The most at-risk posts are those that are supposed to be controversial within a small group, but go viral outside it, or the posts that are controversial within a small group, but then the author says something about politics that draws the attention of the Internet at large to their other writings.
The second biggest risk factor for deletion is probably usefulness combined with hosting costs. This could also be the streetlight effect at work, like in the paragraph above, but the more traffic something gets, the higher the hosting costs. Certain types of content are either hard to monetise, and cost a lot of money, or they can be monetised, so the free version is deliberately deleted.
The more tech-savvy users are, the more likely they are to link between different sites, abandon a blogging platform or social network for the next thing, try to consolidate their writings by deleting their old stuff and setting up their own site, only to let the domain lapse. The more tech-savvy users are, the more likely they are to mess with the HTML of their templates or try out different blogging software.
If content is spread between multiple sites, or if links link to social network posts that link to blog post with a comment that links to a reddit comment that links to a geocities page, any link could break. If content is consolidated in a forum, maybe Archive team could save all of it with some advance notice.
All this could mean that indie games/game design theory/pixel art resources are uniquely lost, and games studies/theory of games criticism/literary criticism applied to games are especially affected by link rot. The semi-professional, semi-hobbyist indie dev, the writer straddling the line between academic and reviewer, they seem the most affected. Artists who start out just doodling and posting their work, who then get hired to work on a game, their posts are deleted. GameFAQs stay online, Steam reviews stay online, but dev logs, forums and blog comment sections are lost.
Or maybe it's only confirmation bias. If I was into restoring old cars, or knitting, or collecting stamps, or any other thing I'd think that particular community is uniquely affected by link rot, and I'd have the bookmarks to prove it.
Figuring this out is important if we want to make predictions about the future of the small web, and about the viability of different efforts to get more people to contribute. We can't figure it out now, because we can't measure the ground truth of web sites that are already gone. Right now, the small web is mostly about the small web, not about stamp collecting or knitting. If we really manage to revitalise the small web, will it be like the small web of today except bigger, the web-1.0 of old, or will certain topics and communities be lost again?
60 notes
·
View notes
Text
Heather Cox Richardson
April 11, 2025 Heather Cox Richardson Apr 12 On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command. Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
(NOTE: AND MOGRHADDASI IS AN IRANIAN NAME, I BELIEVE!!!!) The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem. Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?” The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.” The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
WILL NO ONE STOP THIS FASCIST FROM MAKING OUR GOVERNMENT INTO AN AUTHORITARIAN DICTATORSHIP? I CANNOT FUCKING BELIEVE WHAT IS HAPPENING BEFORE OUR VERY EYES!!!!!
2 notes
·
View notes
Text
Pinned Post
Side Blog: https://somethingdifferent.wordpress.com/
Software Projects (Fallen Star/Marxist Furry)
Completed Projects
Reddit
A simple picture posting reddit iphone app. A Computer Science University Project at Weber State University for an ios/iphone development class. It uses the reddit api for logging into an account to upload a photo to imgur and posting it to a user defined subredit. It also finds all the images on a subreddit and displays them in a list where the user can click ont one of the items in the list and it will display the image
https://github.com/ballju/iReddit
In Progress
Fallen Star
Converting Gamemaker School Project from Gamemaker 8 to Godot
Playlist Transfer
Transfers Playlists from streaming apps from one service to another. Using C# and .Net framework. It will be a console application.
Mood Tracker
Open-source daily journal and daily tracking of both mood and other important things.
Avatar Sim
Choose your own adventure based on JC’s Avatar
ADHD Tracker
(Private Github Repo for now) An time tracker that using Android TTS to help those with poor time management to keep on track storing tasks by priority
DBT Diary Card
(Private Github Repo for now) An application for generating dbt diary cards for thearpy and personal tracking
videowyrm
A fork of a decentralized movie/tv/anime social tracker based on a book tracking app
Frequently Used Tags
For most of the posts the were posted by me its #original post
#journal
#history #socialism
#song lyrics #song of the day #metal #music #Bandcamp
#hg wells #old movies #colorized #youtube movies #Youtube
#movies
#open source #linux #computer #piracy #tech
#video games #mods #quake
2 notes
·
View notes
Text
week 1 | re-(centering, settling, organizing)
I embrace the new year with a cup of candy cane tea and a bare bullet journal whose only filled page resembles a coloring book. “2025” it announces, shaped from traced out (and colored in) vines that twist over one another to make the edges of the numbers. I have my “Quests” (new year’s resolutions) on one side, below a red (colored in) banner, and “Achievements” (unexpected, but defining experiences and moments in the new year) to the other, but of course, below its banner is empty space.
The hardest thing about new year’s resolutions is accepting that the goals you wrote— potentially scoured Pinterest for, if you’re anything like me, who deemed their ten-goal list (already difficult) too skimpy on paper— require you to start today. Not in a week or a few days.
2025 is already a week old, and I have yet to put on my retainers (one of the many habits I swore to start this year); I have been using my creative pursuits as excuses to put off the gritty work of starting my term readings early (to loosen the burden of the start of term) or starting a research database for my lab work (I was supposed to do this…weeks ago); and my tasks for the “ambitious, but not unattainable” days I scheduled preceding the end of break continue to be postponed, dragged onto future days, with previously-schedule tasks rescaled and reordered to compensate for my unproductiveness.
That isn’t to say I have been wasting this break. These past few days I have been easing myself back into a working mindset, doing the tedious, yet needed, tasks to set myself up for actually doing my larger goals: downloading and sorting readings for the term (if available), finding research programs to apply for, labs I would want to reach out to for those research programs, finally responding to neglected emails, and carrying out overdue action items from those message threads. I redid my notion for the year, scrapping the overcomplicated and overwhelming parts of my organization system that I just…didn’t use.
A small aside: I see so many YouTube videos and Instagram reels marketing Notion as a game changing software for productivity, and I would spend hours scouring free templates and downloading them, watching videos on how to format pages or organize my knowledge, and eventually attempting to build my own aesthetic system. Only to almost never use it. I had the same problem with the Hobinichi planner (which I spent a ridiculous amount of money shipping overseas)! Systems require upkeep and consistency, and while I am absolutely one of those types of people that need to write things down to remember them and need organization systems to structure their time and keep their goals in check, I think I fell into the trap of having too many systems in place. I would “touch and go,” skipping between my paper planner, to creating a daily page in notion, that I would inevitably forget to check any of my tasks off from, to sometimes even ripping a page out of my notebooks to create a makeshift to-do list if I felt like it.
Don't get me wrong, Notion is an incredible program to visually organize information and create a workflow! I just wanted to put my entire life into Notion, and the fact of the matter is that...*my* system was not working for me. It didn't make sense for me to split up my life into 20 different pages that I honestly forgot to check and keep up with. I have bursts of motivation, much like the dawn of a new year, to create all these new ways to see and pick apart my life on these programs, but I quickly lose stamina to keep up with all of them.
So, one of my primary goals for 2025 is to simplify and redesign my organization systems (including Notion) to cater to my lifestyle and priorities.
Being in uni with two jobs, being on board for a few student organizations, and studying biomedical engineering, I have found the most success in managing my day primarily with Google Calendar. I even downloaded the “Duration for Google Tasks” extension, so that I can assign tasks for specific time blocks and visually factor in the time estimated for completion into my plans around and beyond class and work schedules. This is how I best visualize my days and prioritize work for the week.
So, I massively simplified my Notion workplace to supplement what my Google ecosystem cannot adequately take care of for me. I almost use it as a control panel/dashboard, with dropdown yearly and quarterly goals; daily, weekly, and monthly habits; a dashboard to keep track of all my applications for internship and research opportunities; and for now, an “everything page” to organize and keep track of miscellaneous notes that I would like to find better homes for later. [A brief snapshot of my Notion page, affectionately also called "ary's garden" is below]

It’s not perfect, but it’s a start!
And as I progress throughout this "quarter" (I set the arbitrary end date of Q1 to Mar 29, 2025), I will keep and adapt what works and discard what doesn't. I just simply no longer have time to waste on systems that do not work for me.
And my bullet journal…will be more of a visual archive than a day-to-day task manager. I might write down some notes or visually plan out projects on its pages (instead of ripped out notebook pages I neatly fold and place into the depths of my backpack, never to be seen again), but it is not a part of my organizational system. It's more an art project than anything, and I am setting it up as such. Vision boards, photos, journal entries, ideas...we will see what I shall fill up this beautiful, blank journal with later, but this year I stop with the monthly and weekly spreads that beg for me to spill my life into its neatly traced boxes and under new list headings. This year, I accept the bujo for what it is: a hobby, that sometimes, I won't have time for.
I will update you all on how these changes impact my day-to-day operations and longer term achievements (or don’t). As I said before, we'll figure it out together!

[Above is a Salem the Cat gif from one of my favorite television shows, Sabrina the Teenage Witch (1996-2003), where he is sporting scholarly glasses sitting atop a book. He looks fabulous and unbothered, as always. Truly the vibe I'm trying to embody this new year]
Nevertheless, I didn’t start of 2025 on magically better footing simply because the calendar marked an ending and beginning or because my motivation shot up at the creation of resolutions. I spent much of this break resting and healing, and frankly, and I spent the first half week of 2025 doing the same. But, as the start of school again looms for the next few days, I actually feel restored and ready to take on the new year with all it promises...and requires of me.
I have applications to finish, readings to absorb, and a life to live. Guess I have to start today :)
Until next week, mis amores,
Ary
#updates#vision board#new years resolution#new year 2025#new years resolutions#organization#studyblr#self improvement#study motivation#study blog#universitylife#studyadvice#stem student#studyspo#college#healing#self healing
6 notes
·
View notes
Note
Hi there! I saw your post on using discord as a tracker for things and I want to say a couple of things.
I use it for ocs and it works somewhat well (I rarely update it, but at least I can remember about those ocs that I have not toyed with in a while), along with some other things. But for day to day tasks I'm not sure of how useful it can be? I can't keep track of things on a physical diary/calendar/whatever the word is for the thing in English and I don't know how a digital version of it might be better? I mean, I tried in the past via phone notes and after a while (a week tops) I just stopped? I suppose it's more of a me issue?
Another thing, as someone who uses a different pw for everything and has the list written on a sheet of paper, wouldn't it be dangerous to have them on discord? Idk leaks, havkers, that jazz, or is the risk so small that it's trascurable?
hi hi!! im glad that little lifehack post works well enough for your OC purposes!!
i'll be honest first though and say that that post DEFINITELY breached containment and i was not expecting it to get that big, i was wholly just talking to myself HAHA. that being said, it's usefulness really depends on if it works well for you and your own brain purposes!!
i also struggle with keeping diaries/journals, so i simply dont use my personal server for it. the only thing i use my personal server for really, is for sending files to myself across devices so i dont have to bother with bluetooth or cloud or stuff like that. and i use channels as categories of What type of thing im sending to myself. for reference, heres some of my channels in my personal server
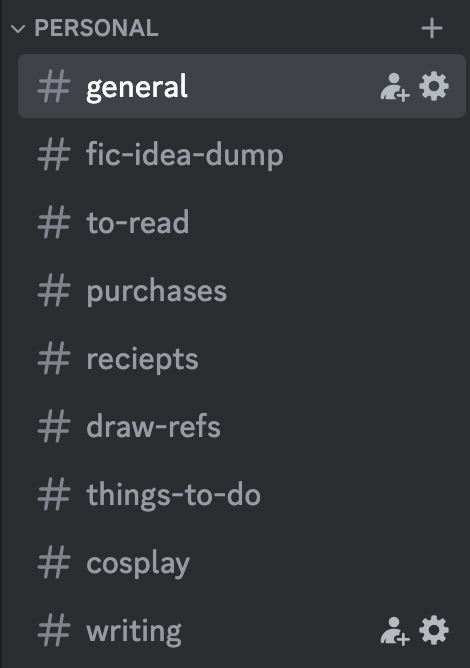
so as u can see i rlly dont use it as a personal diary. at most, i use it as a to do list or a to read list for when im switching between my laptop and my phone
i hope that makes sense? kblskjfbsjdffds
now on the matter of passwords: NEVER USE DISCORD TO STORE YOUR PASSWORDS OR ANY SENSITIVE INFORMATION. im like you, i go old school pen and paper style, but yeah really, not on discord. the threat of hacks or leaks or other stuff is too high.
in summary:
i rlly didnt expect that post to go big so im unfamiliar with a lot of the issues that are cropping up for many many people
i find the personal server most useful for storing and sending NON-SENSITIVE INFORMATION, like fanfic ideas or my grocery shopping list or links to stuff i wanna read while im stuck in traffic
in general i dont trust any online-connected-to-the-internet method of storing passwords. pen and paper is the way to go, or if youre more tech savvy than i am, maybe you can look into dedicated password manager softwares.
i hope this can help!!
5 notes
·
View notes
Text
List of Quick 2-Year Degree Programs After 12th in India (2025)
The major question is 2 years of degree courses after 12th; most students desire to study, but would like shorter courses so that they can work early. Two-year degree courses are an ideal choice for this. These courses provide you with practical expertise and information in less time than conventional 3- or 4-year degrees.
What Are 2-Year Courses?
There are plenty of 2-year courses such as Medical Lab Technology, Radiography, or X-ray Technology, Fashion Designing or Animation & Multimedia, Business Management or Financial Accounting, Journalism, and Digital Video Production
These are undergraduate courses that are completed in approximately 2 years.
Typical ones are Associate's degrees and a few higher-level diploma programs.
They include general subjects such as science, commerce, arts, and social sciences.
Some courses are concerned with practical and employment-related skills.
Types of 2-Year Degree courses after 12th
Associate's Degree: A widely popular 2-year degree providing general education and attainable through community colleges or universities.
Professional Diplomas: Lesser duration courses in particular areas such as nursing, applied science, or technical skills.
Technical Programs: Competency-based courses in fields like welding, automotive technology, or HVAC
Popular Professional Courses After 12th
Medicine: MBBS (Bachelor of Medicine), BDS (Bachelor of Dental Surgery), Nursing, Pharmacy. These courses lead to careers in healthcare and require a science background (Physics, Chemistry, Biology).
Engineering: Diploma and degree courses in different streams such as Mechanical, Civil, Electrical, and Computer Science. Admission usually requires PCM (Physics, Chemistry, Mathematics) in the 12th and entrance tests such as BITSAT or JEE.
Business Administration: BBA (Bachelor of Business Administration) is favored by students who want to pursue management, marketing, and entrepreneurship. Eligibility normally demands a 12th pass with 50% marks minimum, and admission can be through merit or entrance tests such as CUET or IPU CET.
Journalism and Mass Communication: Media, journalism, digital content creation, and communication courses. These equip students to join news, media houses, and digital websites.
Information Technology: BCA (Bachelor of Computer Applications), etc., courses emphasize computer programming, software development, and IT infrastructure.
Law: Bachelor of Laws (LLB) or integrated law courses after 12th make one eligible for legal careers.
Main Points Regarding Professional Courses
Duration: Typically 3 to 4 years for degree courses; diploma and certificate courses can be shorter (8 months to 2 years).
Eligibility: 12th pass with the concerned subjects and a minimum percentage (typically 45-50%).
Entrance Exams: Most courses require clearing entrance exams such as CUET, MAT, BITSAT, GPAT, CLAT, etc.
Recognition: Programs are recognized by organizations such as UGC, AICTE, PCI (Pharmacy), and BCI (Bar Council of India) to provide quality education.
Career Opportunities: With these courses, students can become employed in hospitals, IT firms, law firms, media organizations, business firms, and more.
UG Diploma Courses in India
Undergraduate (UG) diploma courses are diplomas of shorter durations, typically 1-2 years, offered in areas such as:
Popular UG Diploma Courses in India
Diploma in Computer Science and IT: Includes programming (Python, Java), networking, cybersecurity, and database management. The graduates can be software testers, IT support specialists, or junior developers.
Diploma in Digital Marketing, Graphic Designing, Web Designing, Animation & VFX: Technology and creative-oriented diplomas that prepare candidates for marketing, design, and multimedia sectors.
Diploma in Engineering (Mechanical, Civil, Electrical, etc.): Polytechnic diplomas with emphasis on technical skills and practical training in different branches of engineering.
Diploma in Business Management, Event Management, Journalism: Diplomas that equip students for administrative, marketing, and media work careers.
Diploma in Data Science and Analytics, Artificial Intelligence: Emerging fields with diplomas aimed at data handling, AI technologies, and analytics.
Diploma in Fashion Designing, Hotel Management, Agriculture: Specialized diplomas for the creative and service industry.
Why Opt for 2-Year Courses?
Opting for a 2-year course after the 12th standard is gaining more and more popularity among students due to the following practical reasons:
Early Entry into the Job Market: The courses are shorter than conventional 3- or 4-year degrees, enabling you to acquire work-ready skills and enter the workforce earlier. This is perfect if you wish to start earning early or acquire work experience early on.
Affordable Education: As 2-year programs consume fewer hours, they typically are less expensive in terms of tuition fees and living costs than longer degree courses. This makes education within reach for most students.
Practical and Focused Learning: These courses specialize in experiential skills and real-world knowledge in certain areas such as business administration, digital marketing, medical laboratory technology, and fashion design. Such specialized learning gets you effectively ready for work requirements.
Flexibility and Choice: There are numerous 2-year courses covering various streams like Science, Commerce, Arts, and Technology. You have the option to pick a course according to your hobby and profession.
Career Opportunities and Higher Studies: With a 2-year course, you can find decent job opportunities and even use it as a stepping stone in case you wish to take up higher studies afterwards.
Growing Recognition and Acceptance: As government education agencies such as UGC endorse accelerated and flexible degree courses, 2-year courses are becoming accepted and recognized in India's education system.
Conclusion
2-year Degree courses provide a wise, time-saving opportunity to acquire useful skills, minimize cost and time, and start a professional career with confidence. Most colleges and universities in India provide such courses, but Arya College of Engineering & IT is among the best colleges in Rajasthan.
0 notes
Text
How To Make Sure Information On Your Old Computer Is Really, Truly Deleted
It Isn’t As Simple As Pressing ‘Delete’ And Emptying The Trash. Here’s A Step-By-Step Guide.
— By Sean Captain | June 17, 2025 | The Wall Street Journal (WSJ)

Illustration: Jon Krause
Spring-cleaning season is almost done, and it is time to finally get rid of that old computer. But be very careful before you sell, give away or recycle it.
You could be handing over sensitive information.
Even if you think you deleted everything on it, your old computer may hold lots of personal items you don’t want anyone seeing. In a 2019 study by the University of Hertfordshire (funded by security tech-reviews site Comparitech), researchers purchased 200 used hard drives from the U.S. and U.K. An analysis found data remaining on 59% of the drives, including passport and driver’s license scans, bank statements, utility bills and “intimate photos.”
Just pressing “delete” and emptying the Trash in macOS or the Recycle Bin in Windows won’t do the trick. That’s because your computer maintains an index of where every file resides. Deleting a file erases only its entry in the index, telling your system that it can put new files in that space. But until the system actually does put new files there, the old ones remain accessible. Simple consumer-level file-recovery apps can get at it—never mind professional-grade forensic software.
Here’s how to make sure your data is really gone—even on a computer that won’t start up.
Back-up And Log Out
Start by backing up anything you want to keep. You could drag files onto an external hard drive or use backup software such as the Time Machine app in macsOS. You can also back up to the cloud using Microsoft OneDrive, Apple iCloud, Google Drive, Dropbox or other services. (Don’t empty the Trash or Recycling bin. The wipe process will take care of this.)
Next, log out of applications or games with an online component, so the license is no longer associated with your old computer. Also do this for services like Gmail or Facebook, and web browsers like Chrome that sync your data online—on the admittedly remote chance that an incomplete wipe allows the next owner to access those accounts.
Another step for any type of computer is making sure your files are encrypted—scrambled in a mathematical operation based on very long strings of random numbers and letters called encryption keys. The wiping process will delete the keys to make sure any files that may remain on the machine are unreadable.
What you do next depends on your operating system.
Clearing Out A PC
Windows 10 and the current Windows 11 have a feature called “Reset this PC,” which, with the right settings, thoroughly wipes your data. First, make sure your operating system is up-to-date, as Microsoft recently fixed a bug that sometimes caused the reset process to fail. Press the Windows key, search for “updates” and select “Check for updates.” Install any that are available.
Now check on encryption. In Windows 10 or 11 Home editions, press the Windows key and search for “device encryption settings.” Click “Device encryption settings” on the next screen, then make sure the switch next to “Device encryption” is toggled on. Windows Pro, Enterprise and Education editions have an encryption utility called BitLocker. To enable it, click the Start button, type “bitlocker” and select “Manage BitLocker” from the list of results. (All versions of Windows 10 and 11 also encrypt deleted files.)
Now you’re ready to wipe. Tap the Windows key again, search for “Reset this PC,” then click on it. On the next screen, tap “Reset PC” (Windows 11) or “Get started” (Windows 10), and on the following screen, click “Remove everything.” On the next screen, select “Local reinstall.” (If this doesn’t work, try the “Cloud download” option.) Then click “Change settings,” and on the following screen (under “Clean data?”), toggle the switch to “Yes” and press “Confirm.” On the following screen, press “Next” (Windows 11) or “Reset” (Windows 10). On Windows 11, you will press “Reset” on one more screen. Then let the process run for a few hours.
“Reset this PC” deletes your files, apps and settings, logs you out of your Microsoft account and disables the “Find My Device” feature so the computer is no longer associated with you. Then the serious wiping starts. The encryption keys are deleted, making any encrypted data irretrievably scrambled, and the Clean data option overwrites the ones and zeros that had encoded data on your drive. A clean copy of Windows is also installed.
The MacOS Method
Apple’s “Erase Assistant” feature made its debut in 2021’s macOS 12 Monterey. If your current OS is older, you may be able to update it. To update an older OS to Monterey or a later one, click the Apple menu, then “System Preferences” and “Software Update.” If the update process doesn’t work, jump to “If all else fails” below for another option.
As with Windows, the “Erase All Content & Settings” process should start with encryption. On newer Macs (starting between 2018 and 2020, depending on the model), data is encrypted automatically. Just to be safe, though, turn on a feature called FileVault that adds encryption to older systems and an extra layer to newer ones. Click the Apple icon, then “System Settings” (or “System Preferences” in Monterey). In the next window, click “Privacy & Security” (or “Security & Privacy”), then click FileVault.
Now it is time to wipe. Click again on the Apple icon and “System Settings” (or “System Preferences”), click “General” on the left, then “Transfer or Reset” on the bottom right. Finally, on the next screen, click “Erase All Content & Settings.” (In Monterey, you’ll go there directly from “System Preferences.”)
This process signs you out of Apple services, turns off the “Find My” and “Activation Lock” security measures so that the system is no longer associated with you, and erases all your files, settings, apps and anything else. It deletes the encryption keys, permanently scrambling any data that remains.
If All Else Fails
If your PC or Mac is so old that it can’t run a modern wipe process, you have one more option before seeking pro help. For Windows, several experts recommended the KillDisk app. The $49.95 Professional version runs from a USB drive and overwrites the ones and zeros that encode data on your hard drive with all zeros. Afterward, your computer will no longer boot into Windows unless you reinstall the OS.
For a Mac, your best option is a complex process that Apple describes online.
If these processes sound too complicated, or if your system won’t even turn on, use Apple’s recycling program for Macs or a disposal company that offers hard-drive destruction (or shredding) and recycling for consumers with either type of system. Look for ones that issue a certificate of destruction to verify the process. For instance, Ship ‘N’ Shred accepts drives or whole devices, with prices that include shipping ranging from around $30 to $200.
Modern technology leaves a lot of digital footprints, but at least you can sweep them off your old computer.
— Sean Captain is a Writer ✍️ in New York.
#Technology#Personal Technology#Personal Information#Old Computer 💻 🖥️#Deleting Personal Data#‘Delete’ | Emptying The Trash#Step-By-Step Guide#Sean Captain#The Wall Street Journal (WSJ)
0 notes
Text
Globaling Attribution Software Market Size, Share, Demand, Future Growth, Challenges and Competitive Analysis
Executive Summary Marketing Attribution Software Market :
Marketing Attribution Software Market research report is a resource for getting current as well as upcoming technical and financial details of the industry to 2025. This market report contains market data that can be relatively essential when it comes to dominate the market or make a mark in the market as a new emergent. The purpose of ing Attribution Software Market report is to provide a detailed analysis of industry and its impact based on applications and on different geographical regions. It also strategically analyses the growth trends and future prospects. ing Attribution Software Market report also enlists the leading competitors and provides the insights about the strategic industry analysis of the key factors influencing the industry.
The data and the information concerning the industry are derived from consistent sources such as websites, annual reports of the companies, journals, and others and were checked and validated by the market experts. ing Attribution Software Market report uses a range of steps for collecting, recording, analysing and interpreting market data to make this report all-inclusive. The industry analysis report speaks about the manufacturing process, type and applications. ing Attribution Software Market report also endows with the list of the leading competitors and their moves such as joint ventures, acquisitions, and mergers etc. ing Attribution Software Market business document also makes available statistics on the current state of the industry as a valuable source of guidance and direction for companies and investors interested in this market.
Discover the latest trends, growth opportunities, and strategic insights in our comprehensive ing Attribution Software Market report. Download Full Report: https://www.databridgemarketresearch.com/reports/global-marketing-attribution-software-market
ing Attribution Software Market Overview
**Segments**
- Based on the component, the marketing attribution software market can be segmented into solutions and services. The solutions segment is further categorised into cloud-based and on-premises solutions. The services segment includes professional services and managed services.
- On the basis of deployment mode, the market can be divided into cloud and on-premises deployment. Cloud deployment is gaining popularity due to its flexibility, scalability, and cost-effectiveness.
- In terms of organization size, the market is segmented into small and medium-sized enterprises (SMEs) and large enterprises. SMEs are increasingly adopting marketing attribution software to analyze their marketing efforts and optimize their strategies.
- By application, the market can be classified into social media marketing, email marketing, content marketing, search engine marketing, and others. Each application area has specific requirements for marketing attribution to track and attribute conversions accurately.
- Geographically, the global marketing attribution software market is segmented into North America, Europe, Asia-Pacific, South America, and Middle East & Africa. North America is expected to dominate the market due to the presence of major market players and the early adoption of advanced marketing technologies.
**Market Players**
- Google LLC - Adobe - SAP - Oracle - Neustar - Merkle - IRI Worldwide, Inc. - Analytic Partners - Equifax Inc. - Singular - Rockerbox - C3 Metrics - Windsor.ai - LeadsRx - Marketing Evolution
Neustar and Merkle stand out for their data-driven approach to marketing attribution, leveraging advanced data analytics and machine learning techniques to deliver accurate insights for businesses. IRI Worldwide, Inc., Analytic Partners, and Equifax Inc. focus on providing tailored solutions for businesses looking to optimize their marketing campaigns through precise attribution modeling. Singular, Rockerbox, and C3 Metrics are notable players offering innovative attribution solutions that help companies track ROI and optimize their marketing spend effectively.
Windsor.ai and LeadsRx are emerging players in the market, known for their advanced attribution modeling techniques and user-friendly interfaces that appeal to a wide range of businesses. Marketing Evolution is recognized for its AI-powered marketing attribution platform, helping companies drive measurable results and enhance customer engagement through data-driven insights. These market players collectively contribute to the dynamic landscape of the marketing attribution software market, offering a diverse range of solutions to meet the evolving needs of businesses across various industries.
In addition to the established players, new entrants and startups are also entering the market with disruptive technologies and fresh ideas to address the growing demand for effective marketing attribution solutions. As the market continues to evolve, we can expect to see increased collaboration among players, technological advancements, and a focus on delivering more personalized and actionable insights for businesses. With the rising importance of data-driven marketing strategies, the marketing attribution software market is poised for further growth and innovation in the coming years.The global marketing attribution software market is witnessing significant growth and competition among key players looking to secure a competitive advantage through innovative solutions and strategic collaborations. Google LLC, Adobe, SAP, and Oracle are leading the market with their comprehensive marketing tools and analytics solutions tailored to meet diverse business requirements. These major players have successfully integrated advanced analytics and attribution capabilities into their offerings, empowering businesses to make data-driven decisions and optimize their marketing strategies effectively.
Neustar and Merkle are notable for their data-driven approach to marketing attribution, utilizing advanced data analytics and machine learning techniques to provide accurate insights for businesses seeking to enhance their marketing campaigns' performance. IRI Worldwide, Inc., Analytic Partners, and Equifax Inc. are focusing on delivering customized solutions through precise attribution modeling to help businesses achieve their marketing goals efficiently.
Emerging players like Windsor.ai, LeadsRx, and Marketing Evolution are bringing fresh perspectives to the market with their advanced attribution modeling techniques and innovative AI-powered platforms that deliver actionable insights for businesses looking to drive measurable results and enhance customer engagement. These new entrants are disrupting the market landscape and contributing to the market's dynamic evolution, emphasizing the importance of personalized marketing strategies and data-driven decision-making.
As the marketing attribution software market continues to expand, we can anticipate increased collaboration among established players, further technological advancements, and a stronger emphasis on providing personalized and actionable insights to businesses across various industries. With the growing significance of data-driven marketing approaches, the market is poised for continued growth and innovation in the foreseeable future. The influx of new technologies and players into the market will only serve to fuel competition and drive the development of more sophisticated solutions that cater to the evolving needs of businesses in the digital age.
The ing Attribution Software Market is highly fragmented, featuring intense competition among both global and regional players striving for market share. To explore how global trends are shaping the future of the top 10 companies in the keyword market.
Learn More Now: https://www.databridgemarketresearch.com/reports/global-marketing-attribution-software-market/companies
DBMR Nucleus: Powering Insights, Strategy & Growth
DBMR Nucleus is a dynamic, AI-powered business intelligence platform designed to revolutionize the way organizations access and interpret market data. Developed by Data Bridge Market Research, Nucleus integrates cutting-edge analytics with intuitive dashboards to deliver real-time insights across industries. From tracking market trends and competitive landscapes to uncovering growth opportunities, the platform enables strategic decision-making backed by data-driven evidence. Whether you're a startup or an enterprise, DBMR Nucleus equips you with the tools to stay ahead of the curve and fuel long-term success.
Key Questions Answered in This Report: –
How has this ing Attribution Software Marketperformed so far and how will it perform in the coming years?
Which are the key product types available in this ing Attribution Software Market?
Which are the major application areas in theing Attribution Software Market?
What are the key distribution channels in the global ing Attribution Software Market?
What are the key regions in this ing Attribution Software Market?
What are the price trends?
What are the various stages in the value chain of this industry?
What are the key driving factors and challenges in the market?
Browse More Reports:
Global Ankylosing Hyperostosis Market Global Angioplasty Balloons Market Global Anchorage Additives Market Global Amphotericin B Market Global Alum and Calcium Salts Market Global Alternative Proteins Market Global Algae Biofuel Market Global Alcoholic Beverage Processing Equipment Market Global Albuterol Market Global Aircraft Wheels Market Global Aircraft Fairings Market Global Air Runner Market Global AI in Neurology Market Global Agriculture Chemicals Market Global Agave Nectar Market Global Aerial Imaging Market Global Advanced Therapeutics Market Global Adrenoleukodystrophy Treatment Market Global Adnexal Tumor Market Global Acute Myeloid Leukemia Market
About Data Bridge Market Research:
An absolute way to forecast what the future holds is to comprehend the trend today!
Data Bridge Market Research set forth itself as an unconventional and neoteric market research and consulting firm with an unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process. Data Bridge is an aftermath of sheer wisdom and experience which was formulated and framed in the year 2015 in Pune.
Contact Us: Data Bridge Market Research US: +1 614 591 3140 UK: +44 845 154 9652 APAC : +653 1251 975 Email:- [email protected]
Tag
ing Attribution Software Market Size, ing Attribution Software Market Share, ing Attribution Software Market Trend, ing Attribution Software Market Analysis, ing Attribution Software Market Report, ing Attribution Software Market Growth, Latest Developments in ing Attribution Software Market, ing Attribution Software Market Industry Analysis, ing Attribution Software Market Key Player, ing Attribution Software Market Demand Analysis
0 notes
Text
Top Stocks Picks for Intraday Trading
Intraday trading has become a popular strategy among traders looking to capitalize on short-term price movements. It demands quick decision-making, real-time market analysis, and precise entry and exit strategies. Choosing the best stocks for intraday trading can make all the difference between a profitable day and a loss. With market volatility offering frequent trading opportunities, it's essential to focus on stocks with high liquidity and significant price movement potential.
What Makes a Stock Ideal for Intraday?
When selecting stocks for intraday trading, several factors should be considered. These include volume, volatility, and price trends. High-volume stocks ensure easy entry and exit, while price volatility creates room for profit margins. Stocks that are news-sensitive or sector-specific often show consistent price movements within a trading day, offering traders valuable opportunities. Traders should always review technical indicators such as moving averages, RSI, and MACD before making decisions. Combining these indicators with sound risk management increases the chances of success in intraday trades.
Identifying the Best Stocks for Intraday
Many traders often wonder how to identify the best stocks for intraday. The key is to focus on stocks that have shown consistent performance over the last few days and have some news impact or corporate announcements. Blue-chip stocks, banking sector equities, and technology-related scrips tend to be active throughout the trading session. These stocks not only exhibit steady movement but also react sharply to market sentiments and global cues. Monitoring market trends, pre-market data, and financial news can help narrow down the list of potential stocks.
Analyzing Stocks for Intraday Today
Each trading day presents a fresh set of opportunities and challenges. Therefore, identifying the right stocks for intraday today becomes a crucial task for day traders. Real-time screeners and market analysis tools come in handy when scanning the market for high-performing stocks. Stocks showing sudden volume spikes, unusual price movements, or breaking key technical levels often become prime candidates for intraday trades. Additionally, tracking sector rotation and institutional buying activity can reveal valuable insights into potential trade setups for the day.
Risk Management and Discipline in Intraday
Intraday trading is not just about spotting the right stock; it’s equally about timing and discipline. Setting stop-loss levels and target prices before entering a trade is essential to protect capital. Traders should never let emotions drive their decisions. Even the best stocks for intraday trading can lead to losses if approached recklessly. Practicing proper position sizing and maintaining a trade journal can improve consistency and reduce impulsive trades. It’s wise to exit trades if market conditions change suddenly or if a pre-set target is achieved early.
Tools and Resources to Support Intraday Trading
The success of intraday trading also depends on the tools used for analysis. Charting software, price action scanners, and live news feeds offer critical data points in real time. Many traders rely on intraday screeners that filter and suggest stocks for intraday today based on parameters like price breakout, volume change, or RSI divergence. These tools save time and increase efficiency by highlighting only those stocks that meet specific trading criteria. With access to the right tools and a disciplined approach, intraday trading can be highly rewarding.
In conclusion, mastering intraday trading requires a solid understanding of market behavior, careful stock selection, and consistent use of technical tools. For those looking to streamline their trading experience and access high-probability stock ideas, visiting intradayscreener.com can offer a powerful edge in identifying the best stocks for intraday success.
For more info:-1.facebook
2.instagram
0 notes
Text
Complete Guide to Career Options: After 12 Science Courses List with Top Choices in 2025
Completing 12th grade in the science stream opens the door to a wide range of career opportunities. Whether you're from the PCB (Physics, Chemistry, Biology) or PCM (Physics, Chemistry, Mathematics) background, there are numerous high-paying, in-demand, and future-ready fields to choose from. If you’re searching for the best after 12 science courses list, this guide is here to give you a detailed breakdown of options, career scope, and what suits your interests best.
🔹 Why Science Stream Offers a Wide Career Scope?
Science students are at an advantage because they can switch to commerce or arts fields if they wish — but students from other streams can’t always shift into science. From medicine and engineering to research and business, the science stream is a launchpad to almost every career path.
📘 After 12 Science Courses List: Complete Overview
Here's the most updated after 12 science courses list for 2025, divided into Medical, Non-Medical, and Other emerging fields.
🔬 Medical (PCB) Stream Courses
MBBS (Bachelor of Medicine & Bachelor of Surgery)
Duration: 5.5 years
Career: Doctor, Surgeon, Specialist
Entrance Exam: NEET
BDS (Bachelor of Dental Surgery)
Duration: 5 years
Career: Dentist, Oral Surgeon
BAMS (Ayurvedic Medicine)
Duration: 5.5 years
Career: Ayurvedic Doctor, Wellness Expert
BHMS (Homeopathy)
Duration: 5.5 years
Career: Homeopathic Doctor
B.Sc. Nursing
Duration: 4 years
Career: Nurse, Hospital Management
BPT (Bachelor of Physiotherapy)
Duration: 4.5 years
Career: Physiotherapist, Sports Therapy Expert
Pharmacy (B.Pharm / D.Pharm)
Duration: 4 years / 2 years
Career: Pharmacist, Drug Researcher
B.Sc. Biotechnology / Microbiology / Biochemistry
Duration: 3 years
Career: Researcher, Lab Analyst, Geneticist
Veterinary Science (BVSc)
Duration: 5.5 years
Career: Animal Doctor, Livestock Consultant
⚙️ Engineering & Non-Medical (PCM) Stream Courses
B.Tech / B.E. (Engineering)
Popular Branches: Computer Science, Mechanical, Civil, AI, Robotics
Entrance Exam: JEE Main, State CET
B.Arch (Architecture)
Duration: 5 years
Career: Architect, Urban Planner
Exam: NATA
B.Sc. in Physics / Chemistry / Maths / IT
Duration: 3 years
Career: Data Scientist, Analyst, Educator
Merchant Navy / Nautical Science
Duration: 3–4 years
Career: Marine Engineer, Ship Officer
Commercial Pilot Training
Duration: 18–24 months
Career: Pilot
Requirement: Physics & Maths in 12th
💻 Emerging & Interdisciplinary Courses
BCA (Bachelor of Computer Applications)
Duration: 3 years
Career: Software Developer, IT Analyst
B.Sc. in Data Science / AI / Cybersecurity
Duration: 3 years
Career: Data Analyst, AI Engineer, Security Expert
Forensic Science
Duration: 3 years
Career: Crime Lab Analyst, Legal Advisor
B.Sc. Agriculture / Forestry / Horticulture
Duration: 4 years
Career: Agri-Scientist, Food Technologist
Environmental Science / Oceanography / Geology
Duration: 3 years
Career: Environmental Officer, Researcher
🎓 Professional Courses Open to All Science Students
Hotel Management
Mass Communication & Journalism
Fashion Designing / Interior Designing
BBA (Bachelor of Business Administration)
Law (Integrated BA-LLB)
These options are excellent for science students who wish to explore beyond the technical field and enter creative or business-related domains.
📌 How to Choose the Right Course?
Here’s how to filter your after 12 science courses list and choose the right one:
Interest & Passion – Don’t choose MBBS or B.Tech just because others are doing it. Ask yourself what truly excites you.
Entrance Requirements – Understand the exams you need to crack (like NEET, JEE, NATA).
Career Scope – Choose fields with long-term growth and stability.
Budget & Duration – Consider how long the course is and whether it fits your financial situation.
✅ Final Words
There’s no doubt that science opens up more career options than any other stream. But the best course is the one that matches your passion and strengths. Use this detailed after 12 science courses list as a starting point and then research deeper based on your interest. Whether it's becoming a doctor, an engineer, a data scientist, or even a pilot — the future is full of opportunities for science students.
0 notes