#Manipulating XML with PHP
Explore tagged Tumblr posts
Text
Computer Language
Computer languages, also known as programming languages, are formal languages used to communicate instructions to a computer. These instructions are written in a syntax that computers can understand and execute. There are numerous programming languages, each with its own syntax, semantics, and purpose. Here are some of the main types of programming languages:
1.Low-Level Languages:
Machine Language: This is the lowest level of programming language, consisting of binary code (0s and 1s) that directly corresponds to instructions executed by the computer's hardware. It is specific to the computer's architecture.
Assembly Language: Assembly language uses mnemonic codes to represent machine instructions. It is a human-readable form of machine language and closely tied to the computer's hardware architecture
2.High-Level Languages:
Procedural Languages: Procedural languages, such as C, Pascal, and BASIC, focus on defining sequences of steps or procedures to perform tasks. They use constructs like loops, conditionals, and subroutines.
Object-Oriented Languages: Object-oriented languages, like Java, C++, and Python, organize code around objects, which are instances of classes containing data and methods. They emphasize concepts like encapsulation, inheritance, and polymorphism.
Functional Languages: Functional languages, such as Haskell, Lisp, and Erlang, treat computation as the evaluation of mathematical functions. They emphasize immutable data and higher-order functions.
Scripting Languages: Scripting languages, like JavaScript, PHP, and Ruby, are designed for automating tasks, building web applications, and gluing together different software components. They typically have dynamic typing and are interpreted rather than compiled.
Domain-Specific Languages (DSLs): DSLs are specialized languages tailored to a specific domain or problem space. Examples include SQL for database querying, HTML/CSS for web development, and MATLAB for numerical computation.
3.Other Types:
Markup Languages: Markup languages, such as HTML, XML, and Markdown, are used to annotate text with formatting instructions. They are not programming languages in the traditional sense but are essential for structuring and presenting data.
Query Languages: Query languages, like SQL (Structured Query Language), are used to interact with databases by retrieving, manipulating, and managing data.
Constraint Programming Languages: Constraint programming languages, such as Prolog, focus on specifying constraints and relationships among variables to solve combinatorial optimization problems.
2 notes
·
View notes
Text
JavaScript Frameworks
Step 1) Polyfill
Most JS frameworks started from a need to create polyfills. A Polyfill is a js script that add features to JavaScript that you expect to be standard across all web browsers. Before the modern era; browsers lacked standardization for many different features between HTML/JS/and CSS (and still do a bit if you're on the bleeding edge of the W3 standards)
Polyfill was how you ensured certain functions were available AND worked the same between browsers.
JQuery is an early Polyfill tool with a lot of extra features added that makes JS quicker and easier to type, and is still in use in most every website to date. This is the core standard of frameworks these days, but many are unhappy with it due to performance reasons AND because plain JS has incorporated many features that were once unique to JQuery.
JQuery still edges out, because of the very small amount of typing used to write a JQuery app vs plain JS; which saves on time and bandwidth for small-scale applications.
Many other frameworks even use JQuery as a base library.
Step 2) Encapsulated DOM
Storing data on an element Node starts becoming an issue when you're dealing with multiple elements simultaneously, and need to store data as close as possible to the DOMNode you just grabbed from your HTML, and probably don't want to have to search for it again.
Encapsulation allows you to store your data in an object right next to your element so they're not so far apart.
HTML added the "data-attributes" feature, but that's more of "loading off the hard drive instead of the Memory" situation, where it's convenient, but slow if you need to do it multiple times.
Encapsulation also allows for promise style coding, and functional coding. I forgot the exact terminology used,but it's where your scripting is designed around calling many different functions back-to-back instead of manipulating variables and doing loops manually.
Step 3) Optimization
Many frameworks do a lot of heavy lifting when it comes to caching frequently used DOM calls, among other data tools, DOM traversal, and provides standardization for commonly used programming patterns so that you don't have to learn a new one Everytime you join a new project. (you will still have to learn a new one if you join a new project.)
These optimizations are to reduce reflowing/redrawing the page, and to reduce the plain JS calls that are performance reductive. A lot of these optimatizations done, however, I would suspect should just be built into the core JS engine.
(Yes I know it's vanilla JS, I don't know why plain is synonymous with Vanilla, but it feels weird to use vanilla instead of plain.)
Step 4) Custom Element and component development
This was a tool to put XML tags or custom HTML tags on Page that used specific rules to create controls that weren't inherent to the HTML standard. It also helped linked multiple input and other data components together so that the data is centrally located and easy to send from page to page or page to server.
Step 5) Back-end development
This actually started with frameworks like PHP, ASP, JSP, and eventually resulted in Node.JS. these were ways to dynamically generate a webpage on the server in order to host it to the user. (I have not seen a truly dynamic webpage to this day, however, and I suspect a lot of the optimization work is actually being lost simply by programmers being over reliant on frameworks doing the work for them. I have made this mistake. That's how I know.)
The backend then becomes disjointed from front-end development because of the multitude of different languages, hence Node.JS. which creates a way to do server-side scripting in the same JavaScript that front-end developers were more familiar with.
React.JS and Angular 2.0 are more of back end frameworks used to generate dynamic web-page without relying on the User environment to perform secure transactions.
Step 6) use "Framework" as a catch-all while meaning none of these;
Polyfill isn't really needed as much anymore unless your target demographic is an impoverished nation using hack-ware and windows 95 PCs. (And even then, they could possible install Linux which can use modern lightweight browsers...)
Encapsulation is still needed, as well as libraries that perform commonly used calculations and tasks, I would argue that libraries aren't going anywhere. I would also argue that some frameworks are just bloat ware.
One Framework I was researching ( I won't name names here) was simply a remapping of commands from a Canvas Context to an encapsulated element, and nothing more. There was literally more comments than code. And by more comments, I mean several pages of documentation per 3 lines of code.
Custom Components go hand in hand with encapsulation, but I suspect that there's a bit more than is necessary with these pieces of frameworks, especially on the front end. Tho... If it saves a lot of repetition, who am I to complain?
Back-end development is where things get hairy, everything communicates through HTTP and on the front end the AJAX interface. On the back end? There's two ways data is given, either through a non-html returning web call, *or* through functions that do a lot of heavy lifting for you already.
Which obfuscates how the data is used.
But I haven't really found a bad use of either method. But again; I suspect many things about performance impacts that I can't prove. Specifically because the tools in use are already widely accepted and used.
But since I'm a lightweight reductionist when it comes to coding. (Except when I'm not because use-cases exist) I can't help but think most every framework work, both front-end and Back-end suffers from a lot of bloat.
And that bloat makes it hard to select which framework would be the match for the project you're working on. And because of that; you could find yourself at the tail end of a development cycle realizing; You're going to have to maintain this as is, in the exact wrong solution that does not fit the scope of the project in anyway.
Well. That's what junior developers are for anyway...
2 notes
·
View notes
Text
Adobe Commerce Developer Expert AD0-E725 Practice Exam
The Adobe Commerce Developer Expert (AD0-E725) certification is a prestigious credential that validates your advanced skills in implementing, customizing, and managing Adobe Commerce solutions. Designed for developers with deep expertise in Adobe Commerce (formerly Magento), this exam is a stepping stone to enhancing your career in e-commerce development. This article provides a comprehensive guide to preparing for the AD0-E725 exam, including recommended knowledge, exam objectives, study tips, and an introduction to the Cert007 Adobe Commerce Developer Expert AD0-E725 Practice Exam as a key preparation tool.
Why Pursue the AD0-E725 Certification?
Earning the Adobe Commerce Developer Expert certification demonstrates your ability to leverage Adobe Commerce to its fullest potential, making you a valuable asset to employers and clients. According to industry surveys, certified Adobe Commerce professionals can earn up to 25% more than their non-certified peers, and the certification opens doors to senior roles in e-commerce and web development. Whether you're a developer aiming to stand out in a competitive job market or a consultant seeking to build client trust, the AD0-E725 exam is a worthy investment in your professional future.
Recommended Knowledge and Skills
To excel in the AD0-E725 exam, candidates should possess a robust skill set and practical experience. Here are the key areas of expertise required:
Experience: At least 2 years of hands-on experience with Adobe Commerce, including real-world projects involving customization and optimization.
Programming Proficiency: Strong programming skills, particularly in App Builder, and adherence to Adobe Commerce Coding Standards Technical Guidelines.
Database and Web Knowledge: Familiarity with relational databases (e.g., MySQL) and an understanding of how web browsers and servers interact.
Performance and Delivery: Skills in performance optimization, software analysis, and the build/delivery process for Adobe Commerce solutions.
Feature Utilization: Experience leveraging built-in features to enable solutions without extensive custom development.
Full-Stack Competence: Proficiency in front-end (HTML, CSS, LESS, JavaScript) and back-end (PHP, XML, MySQL) technologies.
These skills form the foundation for tackling the exam’s technical challenges and applying Adobe Commerce in practical scenarios.
Exam Objectives and Content Breakdown
The AD0-E725 exam is structured into four key sections, each focusing on critical aspects of Adobe Commerce development. Understanding the weight of each section helps prioritize your study efforts. Below is the content breakdown:
Section 1: Architecture (38%)
This section carries the highest weight and tests your understanding of Adobe Commerce’s core architecture. Key objectives include:
Effectively using cache in Adobe Commerce.
Demonstrating knowledge of components (e.g., plugins, preferences, observers).
Configuring multiple sites on a single instance and understanding effects/constraints.
Explaining Git patches and Composer file-level modifications.
Understanding security features (e.g., CSP, escaping, form keys, sanitization, reCAPTCHA, input validation).
Explaining the CRON scheduling system and index functionality.
Section 2: External Integrations (14%)
This section focuses on integrating Adobe Commerce with external systems. Objectives include:
Customizing data flow with SaaS services.
Utilizing App Builder and Adobe I/O events/Webhooks.
Section 3: Customizations (32%)
Customization is a core competency for Adobe Commerce developers. This section covers:
Customizing the catalog, checkout, and sales operations.
Programmatically manipulating entity types.
Customizing the admin panel and APIs.
Leveraging message queues (existing and new) and writing integration tests.
Section 4: Cloud (16%)
This section addresses Adobe Commerce Cloud-specific knowledge. Objectives include46:
Explaining Adobe Commerce Cloud architecture.
Setting up and configuring Adobe Commerce Cloud.
Using the Adobe Commerce Cloud CLI tool.
The exam consists of approximately 60 multiple-choice and multiple-select questions, with a passing score of around 62% (37/60). It lasts 1 hour 40 minutes and costs $225 USD.
Study Tips to Pass the AD0-E725 Exam
Preparing for the AD0-E725 exam requires a strategic approach that combines theoretical study, hands-on practice, and community engagement. Here are proven tips to help you succeed:
Review the Official Exam Guide: Start by downloading Adobe’s official blueprint from the Adobe Certification website. This guide outlines each topic area and its weight, helping you focus on high-impact sections like Architecture (38%) and Customizations (32%).
Use Hands-On Practice: Set up a local development environment or use a demo Adobe Commerce instance to practice concepts like plugin development, API customization, and performance optimization. Real-world scenarios solidify your understanding.
Study Adobe Documentation: Dive into Adobe’s official documentation for in-depth knowledge of coding standards, security features, and Cloud architecture. This is especially critical for topics like CRON scheduling and index functionality.
Practice with Realistic Questions: Simulate the exam environment with high-quality practice tests. The Cert007 Adobe Commerce Developer Expert AD0-E725 Practice Exam is an excellent resource (more details below).
Introducing the Cert007 Adobe Commerce Developer Expert AD0-E725 Practice Exam
To boost your confidence and readiness, the Cert007 Adobe Commerce Developer Expert AD0-E725 Practice Exam is a highly recommended preparation tool. Designed to mirror the actual exam, Cert007’s practice tests offer:
Realistic Questions: Questions align with the AD0-E725 exam objectives, covering Architecture, External Integrations, Customizations, and Cloud topics.
Detailed Explanations: Each question includes comprehensive explanations to clarify concepts and reinforce learning.
Simulated Exam Environment: Practice under timed conditions to improve time management and reduce exam-day anxiety.
Up-to-Date Content: Cert007 regularly updates its question bank to reflect the latest Adobe Commerce features and exam changes.
Performance Tracking: Detailed results highlight your strengths and areas needing improvement, allowing you to focus your study efforts effectively.
Final Thoughts
The Adobe Commerce Developer Expert (AD0-E725) exam is a challenging but rewarding opportunity to showcase your expertise in one of the world’s leading e-commerce platforms. By building a strong foundation in the recommended skills, aligning your study with the exam objectives, and leveraging high-quality resources like the Cert007 AD0-E725 Practice Exam, you can approach the exam with confidence. Start your preparation today by reviewing the official exam guide, setting up a practice environment, and incorporating Cert007’s realistic practice tests into your study plan. With dedication and the right tools, you’ll be well on your way to earning the Adobe Commerce Developer Expert certification and advancing your career in e-commerce development.
0 notes
Text
automatisierter UBL-XML-Generator in PHP in Kombination mit FileMaker
Während meiner Arbeit an der serverseitigen PDF-Generierung mit ZUGFeRD wurde mir schnell klar, dass viele Kunden zunehmend auf den UBL-Standard setzen – gerade im internationalen Kontext oder in Verbindung mit elektronischen Rechnungsplattformen. Also habe ich kurzerhand ein eigenes PHP-Skript geschrieben, das auf POST-Daten aus FileMaker oder anderen Quellen reagiert und daraus eine gültige UBL-Rechnung im XML-Format erstellt. Wie so oft war der Aufbau des XML-Dokuments der anspruchsvollste Teil. Viele Details wie Namespaces, Pflichtfelder und ISO-konforme Datums- und Betragsformate mussten exakt stimmen. Außerdem wollte ich vermeiden, dass mein System bei fehlenden Daten abstürzt – darum habe ich Fallbacks eingebaut und ein eigenes Logging-System integriert. Das Skript liest die Rechnungsdaten, Kunden- und Lieferantendaten sowie die Rechnungspositionen ein, berechnet die Summen und schreibt daraus ein vollständiges XML-Dokument nach dem UBL 2.1-Standard, das sich z. B. auch für die XRechnung weiterverwenden lässt. Die resultierende Datei ist kompatibel mit Plattformen wie PEPPOL, eRechnung.gv.at oder Zentralplattformen der ��ffentlichen Hand. Die Daten werden in FileMaker gesammelt, das ganze klassisch über schleifen. Die Daten werden über ein einfaches application/x-www-form-urlencoded-POST-Request übergeben. Alle Felder werden als Key-Value-Paare übermittelt. Die Rechnungspositionen (line items) sind dabei als kompaktes Raw-String-Feld lineItemsRaw codiert, das einzelne Positionen mit | trennt und innerhalb der Position durch ; strukturiert ist. FileMaker bietet zwar mittlerweile solide Funktionen für JSON-Manipulation – aber bei 25+ Feldern und einer schlichten Punkt-zu-Punkt-Kommunikation mit meinem PHP-Skript war mir das einfach zu umständlich. Ich wollte keine JSON-Parser-Bastelei, sondern einfach Daten senden. Daher nutze ich application/x-www-form-urlencoded, was mit curl ohnehin besser lesbar ist und mir in PHP direkt über $_POST zur Verfügung steht. "-X POST " & "--header \"Content-Type: application/x-www-form-urlencoded\" " & "--data " & Zitat ( "invoiceNumber=" & $invoiceNumber & "&invoiceDate=" & $invoiceDate & "&invoiceCurrencyCode=" & $invoiceCurrencyCode & "&invoiceTypeCode=" & $invoiceTypeCode & "&dueDate=" & $dueDate & "&paymentTerms=" & $paymentTerms & "&deliveryTerms=" & $deliveryTerms & "&sellerName=" & $sellerName & "&sellerStreet=" & $sellerStreet & "&sellerPostalCode=" & $sellerPostalCode & "&sellerCity=" & $sellerCity & "&sellerCountryCode=" & $sellerCountryCode & "&sellerTaxID=" & $sellerTaxID & "&lieferschein_nr=" & $lieferschein_nr & "&kunden_nr=" & $kunden_nr & "&buyerName=" & $buyerName & "&buyerStreet=" & $buyerStreet & "&buyerPostalCode=" & $buyerPostalCode & "&buyerCity=" & $buyerCity & "&buyerCountryCode=" & $buyerCountryCode & "&buyerTaxID=" & $buyerTaxID & "&paymentMeansCode=" & $paymentMeansCode & "&payeeFinancialInstitution=" & $payeeFinancialInstitution & "&payeeIBAN=" & $payeeIBAN & "&payeeBIC=" & $payeeBIC & "&paymentReference=" & $paymentReference & "&taxRate=" & $taxRate & "&taxAmount=" & $taxAmount & "&taxableAmount=" & $taxableAmount & "&taxCategoryCode=" & $taxCategoryCode & "&totalNetAmount=" & $totalNetAmount & "&totalTaxAmount=" & $totalTaxAmount & "&totalGrossAmount=" & $totalGrossAmount & "&lineItemsRaw=" & $lineItemsRaw )
$dom = new DOMDocument('1.0', 'UTF-8'); $dom->formatOutput = true; $invoice = $dom->createElementNS( 'urn:oasis:names:specification:ubl:schema:xsd:Invoice-2', 'Invoice' ); $invoice->setAttribute('xmlns:cac', 'urn:oasis:names:specification:ubl:schema:xsd:CommonAggregateComponents-2'); $invoice->setAttribute('xmlns:cbc', 'urn:oasis:names:specification:ubl:schema:xsd:CommonBasicComponents-2'); $dom->appendChild($invoice); // Standardfelder setzen $invoice->appendChild($dom->createElement('cbc:UBLVersionID', '2.1')); $invoice->appendChild($dom->createElement('cbc:CustomizationID', 'urn:cen.eu:en16931:2017#compliant#urn:xoev-de:kosit:standard:xrechnung_2.0')); $invoice->appendChild($dom->createElement('cbc:ID', $invoiceNumber)); $invoice->appendChild($dom->createElement('cbc:IssueDate', $invoiceDate)); $invoice->appendChild($dom->createElement('cbc:InvoiceTypeCode', '380')); $invoice->appendChild($dom->createElement('cbc:DocumentCurrencyCode', 'EUR'));
Der Aufbau geht dann weiter über Verkäufer- und Käuferdaten, Zahlungsinformationen, steuerliche Angaben und natürlich die Rechnungspositionen, die als cac:InvoiceLine-Blöcke angelegt werden. Die Daten werden direkt auf dem Server verarbeitet, im Anschluss kann ich die XML-Datei wieder in ein FileMaker-Feld laden (Aus URL einfügen). Da ich mit horstoeko/zugferd arbeite, wird in der Folgeversion noch die Validierung erfolgen. Die derzeit händische, zeigt alle Werte, keine Fehler, keine Warnungen.
0 notes
Text
Preventing XML External Entity (XXE) Injection in Laravel
As cybersecurity threats evolve, XML External Entity (XXE) injection remains a significant vulnerability affecting applications that parse XML input. If left unchecked, attackers can exploit XXE to access sensitive files, execute remote code, or perform denial-of-service (DoS) attacks. Laravel, a popular PHP framework, can also be vulnerable if not properly secured. This blog explores XXE injection, its risks, and how to protect your Laravel application with a coding example.

What Is XML External Entity (XXE) Injection?
XXE injection occurs when an XML parser processes external entities in XML input. Attackers can manipulate these external entities to gain unauthorized access to files, network resources, or even escalate their privileges.
Real-Life Scenario of XXE in Laravel
Suppose your Laravel application accepts XML files for data import or integration. If your XML parser allows external entities, an attacker could upload malicious XML files to exploit your system.
Example Malicious XML Code:
xml <?xml version="1.0"?> <!DOCTYPE root [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]> <root> <data>&xxe;</data> </root>
The above code retrieves sensitive system files (/etc/passwd) by exploiting the external entity xxe.
How to Protect Laravel Applications from XXE?
Here’s a step-by-step guide to securing your Laravel application:
1. Disable External Entity Processing
The first defense against XXE is to disable external entity processing in your XML parsers. For PHP’s libxml, you can disable it globally or for specific instances.
Example Code to Disable External Entity Loading:
php // Disable loading external entities libxml_disable_entity_loader(true); // Securely parse XML $xmlContent = file_get_contents('path/to/xml/file.xml'); $dom = new DOMDocument(); $dom->loadXML($xmlContent, LIBXML_NOENT | LIBXML_DTDLOAD);
2. Use Secure Libraries
Instead of using default XML parsers, consider using secure alternatives like SimpleXML with proper configuration or third-party libraries designed for secure XML parsing.
3. Validate User Inputs
Sanitize and validate all user inputs to ensure they meet your application’s requirements. Reject malformed or suspicious XML files.
Leverage Free Website Security Tools
To ensure your Laravel application is free from vulnerabilities like XXE, perform regular security scans. Our Free Website Security Scanner is designed to identify such vulnerabilities and provide actionable insights.
Example Screenshot: Free Tool in Action

After scanning your application, you’ll receive a detailed report highlighting any vulnerabilities.
Example Screenshot: Vulnerability Assessment Report

How Our Tool Helps with XXE Prevention
Our free tool identifies vulnerabilities like XXE in your Laravel application by simulating real-world attacks. It highlights areas needing immediate action and provides recommendations to secure your app.
Conclusion
XML External Entity (XXE) injection is a critical security risk for Laravel applications. By disabling external entity processing, validating inputs, and using secure libraries, you can mitigate these risks. Additionally, tools like our Free Website Security Checker make it easier to detect and resolve vulnerabilities effectively.
Start your journey toward a more secure Laravel application today!
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#xml
1 note
·
View note
Text
Top Software Certifications By Edchart
Full Stack Web Developer Certificate
Become a flexible developer with Edchart's Full Stack Web Developer Certificate. This certification covers every the the the the front-surrender and all over again-prevent technology, ensuring you may deal with all elements of internet improvement.
Full Stack Developer Certification
Elevate your career with Edchart's Full Stack Developer Certification. This software program application program presents in-intensity knowledge and practical enjoy in growing complete-featured net packages.
MEAN Stack Certification
Specialize within the MEAN Stack (MongoDB, Express.Js, Angular, and Node.Js) with Edchart's MEAN Stack Certification. This certification is right for builders aiming to construct robust, excessive-famous overall performance programs.
.NET Developer Certification
Edchart's .NET Developer Certification is outstanding for those seeking out to excel in Microsoft’s .NET framework, allowing you to create effective and scalable packages.
JavaScript Certification
JavaScript is the spine of present day internet improvement. Edchart's JavaScript Certification guarantees you grasp this important language, starting doors to severa improvement possibilities.
Express Certificate
Master once more-give up development with Edchart's Express Certificate. This certification makes a speciality of Express.Js, a flexible and minimal net software program software framework for Node.Js.
HTML CSS JavaScript Certification
Lay a solid basis with Edchart's HTML CSS JavaScript Certification. Gain records in the essential trio of internet development to create visually attractive and interactive net web sites.
HTML5 CSS3 JavaScript Certification
Stay in advance with Edchart's HTML5 CSS3 JavaScript Certification. Learn the contemporary-day requirements and capabilities to build modern-day, responsive internet internet sites.
XML Certification
Edchart's XML Certification is designed for developers who need to recognize and use XML for information interchange and internet services correctly.
CSS3 Certification for Developers
Enhance your styling abilties with Edchart's CSS3 Certification for Developers. Learn superior strategies to create visually cute and responsive net designs.
PHP Certification
PHP stays a critical language for internet development. Edchart's PHP Certification ensures you may expand dynamic and interactive net net websites with self notion.
CakePHP Certification
Edchart's CakePHP Certification makes a speciality of this powerful PHP framework, permitting you to construct sturdy and scalable applications successfully.
CodeIgniter Certification
Master the slight-weight and stylish CodeIgniter framework with Edchart's CodeIgniter Certification, quality for developing dynamic web sites with PHP.
Yii Framework Certification
Edchart's Yii Framework Certification offers in-intensity information of this immoderate-usual average normal overall performance PHP framework, assisting you bring together massive-scale net programs.
Joomla Certification
Become talented in one of the most popular content fabric manipulate structures with Edchart's Joomla Certification. Develop, control, and keep Joomla-based totally websites effectively.
Magento Certification
Specialize in e-change development with Edchart's Magento Certification. Learn to create effective on line shops the use of the Magento platform.
Zend Framework Developer Certification
Edchart's Zend Framework Developer Certification offers complete schooling in this PHP framework, first rate for building enterprise company agency-degree packages.
Phalcon Framework Developer Certification
Learn to apply the immoderate-regular performance Phalcon framework with Edchart's Phalcon Framework Developer Certification, quality for developing speedy and inexperienced net applications.
Fuel Framework Developer Certification
Edchart's Fuel Framework Developer Certification covers the light-weight PHP framework Fuel, specializing in its talents and brilliant practices for net development.
Web Framework Certification
Gain facts in various internet frameworks with Edchart's Web Framework Certification. Learn to choose out and implement the proper framework in your duties.
Sencha Framework Certification
Specialize in wealthy net applications with Edchart's Sencha Framework Certification, overlaying the effective Ext JS framework for building statistics-in depth programs.
Front End Framework Certification
Edchart's Front End Framework Certification specializes in famous the front-give up frameworks like React, Angular, and Vue.Js, equipping you with the competencies to bring together modern-day consumer interfaces.
Bootstrap Framework Developer Certification
Learn to create responsive and cell-first internet web sites with Edchart's Bootstrap Framework Developer Certification, mastering the maximum well-known CSS framework.
Bulma CSS Certification
Edchart's Bulma CSS Certification teaches you to apply this contemporary, open-deliver CSS framework, regarded for its simplicity and versatility.
Materialize CSS Certification
Master Google's Material Design necessities with Edchart's Materialize CSS Certification, developing sleek and intuitive consumer interfaces.
Ember.Js Developer Certification
Edchart's Ember.Js Developer Certification covers this powerful JavaScript framework, first-rate for building formidable net packages.
Backbone.Js Developer Certification
Become proficient in Backbone.Js with Edchart's Backbone.Js Developer Certification, permitting you to shape your net applications efficaciously.
Adobe ColdFusion Certification
Edchart's Adobe ColdFusion Certification offers the facts to enlarge dynamic net packages using Adobe's fast software program software development platform.
Software Testing Certification
Ensure tremendous and reliability with Edchart's Software Testing Certification. Learn diverse trying out methodologies and extraordinary practices.
Software Testing Certifications
Edchart's Software Testing Certifications cover numerous trying out methodologies and tool, ensuring you could successfully find out and clear up defects in software applications.
Software Testing Certification for Experts
Advance your abilities with Edchart's Software Testing Certification for Experts, protecting superior locating out strategies and tools.
Manual Testing Certification
Edchart's Manual Testing Certification focuses on the basics of guide sorting out, ensuring you may understand and treatment defects efficiently.
Agile Testing Certification
Adapt to modern development practices with Edchart's Agile Testing Certification, protecting agile methodologies and their application in finding out.
Automation Testing Certification
Edchart's Automation Testing Certification gives understanding in automatic attempting out machine and strategies, important for green and powerful sorting out techniques.
LoadRunner Certification
Master sizable performance attempting out with Edchart's LoadRunner Certification, focusing in this organization-main tool for load trying out applications.
JUnit Certification
Edchart's JUnit Certification ensures capabilities in this well-known Java checking out framework, critical for writing and walking repeatable tests.
JUnit Certifications
Master unit finding out in Java with Edchart's JUnit Certifications. Learn to put in writing down effective tests, automate techniques, and integrate trying out into non-save you integration pipelines.
UFT Certification
Become an professional in automated useful attempting out with Edchart's UFT Certification, masking Unified Functional Testing tools and techniques.
Mobile App Development Certification
Edchart's Mobile App Development Certification covers the necessities of creating and coping with mobile programs in a few unspecified time within the destiny of severa systems.
Android Certifications
Specialize in Android development with Edchart's Android Certifications, shielding the entirety from number one app creation to superior functions.
Android Security Certification
Ensure your packages are strong with Edchart's Android Security Certification, that specialize in tremendous practices and strategies for securing Android apps.
0 notes
Text
web development,
web development,
In the ever-evolving landscape of technology, web development stands as a testament to human innovation and creativity. From the humble beginnings of static HTML pages to the sophisticated realm of full-stack development, the journey of web development has been marked by groundbreaking advancements, paradigm shifts, and endless possibilities. Let's embark on a journey through time and explore the evolution of web development, from its inception to its current state of complexity and dynamism.
The Birth of the Web: HTML and Static Pages At the dawn of the internet age, Tim Berners-Lee introduced the World Wide Web, laying the foundation for modern web development. HyperText Markup Language (HTML) emerged as the language of the web, enabling developers to create static web pages with text, images, and hyperlinks. These early websites were basic and primarily informational, lacking interactivity and dynamic content.
The Rise of Dynamic Content: Introduction of CSS and JavaScript As the demand for more engaging and interactive web experiences grew, cascading style sheets (CSS) and JavaScript emerged as game-changers. CSS allowed developers to enhance the visual appeal of web pages, while JavaScript empowered them to add dynamic functionality and interactivity. This era witnessed the birth of animated effects, client-side form validation, and AJAX (Asynchronous JavaScript and XML), enabling seamless data exchange between the client and server without page reloads.
The Era of Server-Side Scripting: PHP, ASP, and Ruby on Rails With the increasing complexity of web applications, server-side scripting languages like PHP, ASP (Active Server Pages), and Ruby on Rails gained prominence. These languages enabled developers to build dynamic websites capable of processing user input, accessing databases, and generating personalized content on the fly. The server-side scripting era marked a significant shift towards more robust and scalable web development practices.
The Emergence of Content Management Systems (CMS) As the internet became inundated with content, the need for efficient content management solutions arose. Content Management Systems (CMS) like WordPress, Joomla, and Drupal emerged as popular platforms for building and managing dynamic websites with ease. These systems offered customizable templates, plugins, and user-friendly interfaces, democratizing web development and empowering individuals and businesses to create and publish content effortlessly.
The Advent of Front-End Frameworks: Angular, React, and Vue.js In response to the growing demand for richer, more responsive web applications, front-end frameworks like Angular, React, and Vue.js revolutionized the way developers built user interfaces. These frameworks leveraged the power of component-based architecture, virtual DOM manipulation, and reactive data binding to create fast, interactive, and maintainable web applications. With a focus on modularization and reusability, front-end frameworks streamlined the development process and fostered collaboration among developers.
The Era of Full-Stack Development: MEAN, MERN, and Beyond As web applications became increasingly complex, the demand for developers proficient in both front-end and back-end technologies soared. Full-stack development emerged as a holistic approach to web development, encompassing skills in HTML, CSS, JavaScript, server-side scripting, databases, and deployment. Stacks like MEAN (MongoDB, Express.js, Angular, Node.js) and MERN (MongoDB, Express.js, React, Node.js) gained popularity for their versatility, scalability, and efficiency in building modern web applications.
The Future of Web Development: Progressive Web Apps (PWAs) and Beyond Looking ahead, the future of web development holds exciting prospects, with technologies like Progressive Web Apps (PWAs), WebAssembly, and serverless architecture leading the way. PWAs blur the line between web and native applications, offering offline capabilities, push notifications, and app-like experiences across devices. WebAssembly enables high-performance, near-native code execution in the browser, opening doors to a new era of web applications with unprecedented speed and functionality. Serverless architecture abstracts away infrastructure management, allowing developers to focus on writing code and delivering value without worrying about server maintenance.
Conclusion: The evolution of web development is a testament to human ingenuity and innovation. From the humble beginnings of static HTML pages to the sophisticated realm of full-stack mastery, web developers have continuously pushed the boundaries of what's possible on the web. As we embrace new technologies and embrace the challenges of tomorrow, one thing remains certain: the journey of web development is far from over, and the future is brimming with endless opportunities for those daring enough to explore it.
0 notes
Text
Web App Security: A Crucial Component in Your Business Strategy

Web App Security: A Crucial Component in Your Business Strategy
The stark reality facing organizations today is that security threats are ever-increasing, and expanding in complexity faster than ever before. From small-scale businesses to multinational firms, no entity is immune from potential cyber attacks. This crucial aspect can impact not only your business operations but also its reputation and customer trust. Web apps are especially exposed to third party manipulation, as they serve as an important tool for internal users and customers alike. So to highlight the relevance of making them as secure as possible, here’s an overview of why web app security should be high on your list of considerations when devising an optimized business strategy.
Why Web App Security is Essential
The necessity of web app security for your business cannot be stressed enough. It goes beyond protecting data — it’s about safeguarding the trust and confidence of your users. Here are just a few reasons why it's essential: Guard Your Reputation: A compromised system can result in leaked user data leading to grave loss of faith amongst clients or customers, so it should be part of your broader risk management strategy. Comply With Legal Requirements: Specific industries have strict regulations for data security. Ignoring these can lead to hefty fines or legal consequences. Defend Company Assets: Protect proprietary data, such as source code files from theft by competitor firms which enhances competition effectively. An ounce of prevention is worth a pound of cure. Taking proactive steps like staying updated on the latest cybersecurity threats, implementing robust protection measures, and educating your staff about best practices will go a long way towards improving your overall app security.

Identifying Potential Threats to Your App
In web app security, the first line of defense is accurate identification. You need to recognize what threats could compromise your app's safety. Here are a few examples: SQL Injection Attacks: These happen when an intruder manipulates your SQL query through insecure user input fields, accessing or manipulating sensitive data in the process. Cross-Site Scripting (XSS): This occurs when attackers inject malicious scripts into websites viewed by other users. Cross-Site Request Forgery (CSRF): In CSRF attacks, unsuspecting users get tricked into executing unauthorized commands intended for higher privileged accounts. Then there are more sophisticated methods such as Server Side Request Forgery and XML external entity injection among many others which you should also watch out for. The good news is that using an online PHP vulnerability scanner helps identify weaknesses that can serve as entry points for these cyber attackers. Such tools continually monitor your site, exposing any flagged vulnerabilities so they can be fixed proactively.
Effective Strategies for Enhancing App Safety
Protection is vital when it comes to handling threats. Here are some strategies that can significantly enhance your web app's safety: Regularly Updating Your Software: Routinely updates, including server operating system and any other software you utilize on your website, provide necessary patches that address known vulnerabilities. Using the HTTPS Protocol: Transferring data via HTTP renders the sensitive user information vulnerable during transit. HTTPS implementations add a layer of security by encrypting this data during transportation. Implementing Strong Password Policies: Encourage users to use complex passwords and change them regularly. This creates an extra level of protection against brute force attacks. Incorporating Firewalls: Web Application Firewalls (WAFs) work as filters or monitors which help defend against exploitations like SQL injection attacks or cross-site scripting. Differing levels of protective actions can be combined into several layers - analogous to a multi-tiered security net around your online business assets. Hence, utilizing an amalgamation of these measures offers greater assurance in defending against potential cyberattacks.
Dealing with Cyber Attacks in Business

Cyber attacks are an unfortunate reality for businesses, and can impact web apps as well as other digital assets, as discussed. But knowing how to respond effectively can minimize damage and speed recovery. Consider the following guidelines: Prompt Incident Reaction: Once an attack occurs, quickly identify what has been impacted. Accelerated responses can help you close loopholes. Data Preservation: Keep a backup of your data on a reputable cloud storage service, as it will support quick revivals after cyberattacks without significant losses. Communication Strategy: Inform impacted users honestly and promptly about any breaches. Transparency helps repair trust. Dealing with a breach involves more than mere technicalities; part of it is managing public relations too. By ensuring transparent engagement with all stakeholders during such crises, you’ll be able to regain trust, rather than watching it all drain away.
Wrapping Up
The short and sweet version of all this is that web app security remains a flagship consideration for companies across the world. Getting to grips with the potential threats, equipping your systems to defend against them and formulating a comprehensive crisis management strategy are all part of smarter business planning. As technology continues to evolve, always stay up-to-date with the latest security measures for protecting your online assets, as failure to do so could result in potentially catastrophic losses both financially and reputation-wise. And since malicious third parties are doing the same, you can’t be caught sleeping on this strategic issue. Read the full article
0 notes
Text
PHP XML
PHP XML Hello and welcome to our blog post about PHP XML! Today, we're going to explore the exciting world of XML and how PHP can help us work with this data format. Learn More Here : : https://phptutorialpoints.in/php-xml/ #php #phptutorial #phptutorialpoints #webdevelopment #webdevelopmenttutorial #phpxml #xmlprocessing #xmlmanipulation #phpdevelopment #xmlparsing #phpxmltutorial #phpxmlhandling
Hello and welcome to our blog post about PHP XML! Today, we’re going to explore the exciting world of XML and how PHP can help us work with this data format. PHP is a powerful tool for working with XML data. It provides a range of functions for reading and manipulating XML data, and it can be used with both SimpleXML and DOM. Whether you are working with XML files or generating XML data…

View On WordPress
#"XML data handling in PHP#Creating XML with PHP#Manipulating XML with PHP#PHP DOM functions for XML#PHP SimpleXML tutorial#PHP XML#PHP XML manipulation#PHP XML parsing#Working with XML in PHP
0 notes
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
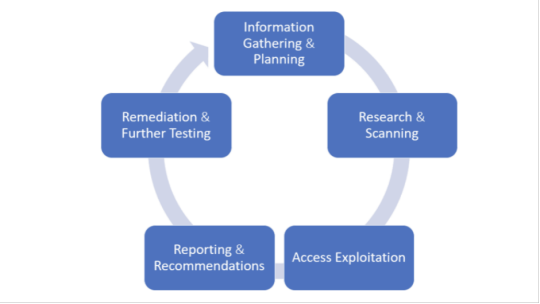
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
Sqlite For Mac Os X

Sqlite For Mac Os X El Capitan
Sqlite Viewer Mac
Sqlite Mac Os X Install
If you are looking for an SQLite Editor in the public domain under Creative Commons license or GPL (General Public License) i.e. for free commercial or non-commercial use. Then here is a shortlist of the SQLite Editor that is available on the web for free download.
SQLite is famous for its great feature zero-configuration, which means no complex setup or administration is needed. This chapter will take you through the process of setting up SQLite on Windows, Linux and Mac OS X. Install SQLite on Windows. Step 1 − Go to SQLite download page, and download precompiled binaries from Windows section. Core Data is an object graph and persistence framework provided by Apple in the macOS and iOS operating systems.It was introduced in Mac OS X 10.4 Tiger and iOS with iPhone SDK 3.0. It allows data organized by the relational entity–attribute model to be serialized into XML, binary, or SQLite stores. The data can be manipulated using higher level objects representing entities. Requirements: Free, ideally open source Browse schema, data. Run queries Bonus if updated in near real time when the file is. SQLite viewer for Mac OS X. Ask Question Asked 5 years, 10 months ago. Active 4 years, 3 months ago. Viewed 504 times 3. I need to inspect an SQLite file on Mac. Since I develop on Windows, Linux and OS X, it helps to have the same tools available on each. I also tried SQLite Admin (Windows, so irrelevant to the question anyway) for a while, but it seems unmaintained these days, and has the most annoying hotkeys of any application I've ever used - Ctrl-S clears the current query, with no hope of undo.
These software work on macOS, Windows, Linux and most of the Unix Operating systems.
SQLite is the server. The SQLite library reads and writes directly to and from the database files on disk. SQLite is used by Mac OS X software such as NetNewsWire and SpamSieve. When you download SQLite and build it on a stock Mac OS X system, the sqlite tool has a.
1. SQLiteStudio
Link : http://sqlitestudio.pl/
SQLiteStudio Database manager has the following features :
A small single executable Binary file, so there is need to install or uninstall.
Open source and free - Released under GPLv2 licence.
Good UI with SQLite3 and SQLite2 features.
Supports Windows 9x/2k/XP/2003/Vista/7, Linux, MacOS X, Solaris, FreeBSD and other Unix Systems.
Language support : English, Polish, Spanish, German, Russian, Japanese, Italian, Dutch, Chinese,
Exporting Options : SQL statements, CSV, HTML, XML, PDF, JSON, dBase
Importing Options : CSV, dBase, custom text files, regular expressions
UTF-8 support

2. Sqlite Expert
Link : http://www.sqliteexpert.com/download.html


SQLite Expert though not under public domain, but its free for commercial use and is available in two flavours.
a. Personal Edition
Sqlite For Mac Os X El Capitan
It is free for personal and commercial use but, covers only basic SQLite features.
But its a freeware and does not have an expiration date.

b. Professional Edition
It is for $59 (onetime fee, with free lifetime updates )
It covers In-depth SQLite features.
But its a freeware and does not have an expiration date.
Features :
Visual SQL Query Builder : with auto formatting, sql parsing, analysis and syntax highlighting features.
Powerful restructure capabilities : Restructure any complex table without losing data.
Import and Export data : CSV files, SQL script or SQLite. Export data to Excel via clipboard.
Data editing : using powerful in-place editors
Image editor : JPEG, PNG, BMP, GIF and ICO image formats.
Full Unicode Support.
Support for encrypted databases.
Lua and Pascal scripting support.
3. Database Browser for SQLite
Link : http://sqlitebrowser.org/
Database Browser for SQLite is a high quality, visual, open source tool to create, design, and edit database files compatible with SQLite.
Database Browser for SQLite is bi-licensed under the Mozilla Public License Version 2, as well as the GNU General Public License Version 3 or later.
You can modify or redistribute it under the conditions of these licenses.
Features :
You can Create, define, modify and delete tables
You can Create, define and delete indexes
You can Browse, edit, add and delete records
You can Search records
You can Import and export records as
You can Import and export tables from/to text, CSV, SQL dump files
You can Issue SQL queries and inspect the results
You can See Log of all SQL commands issued by the application
4. SQLite Manager for Firefox Browser
Link : https://addons.mozilla.org/en-US/firefox/addon/sqlite-manager/
This is an addon plugin for Firefox Browser,
Features :
Manage any SQLite database on your computer.
An intuitive hierarchical tree showing database objects.
Helpful dialogs to manage tables, indexes, views and triggers.
You can browse and search the tables, as well as add, edit, delete and duplicate the records.
Facility to execute any sql query.
The views can be searched too.
A dropdown menu helps with the SQL syntax thus making writing SQL easier.
Easy access to common operations through menu, toolbars, buttons and context-menu.
Export tables/views/database in csv/xml/sql format. Import from csv/xml/sql (both UTF-8 and UTF-16).
Possible to execute multiple sql statements in Execute tab.
You can save the queries.
Support for ADS on Windows
Sqlite Viewer Mac
More Posts related to Mac-OS-X,
More Posts:
Sqlite Mac Os X Install
Facebook Thanks for stopping by! We hope to see you again soon. - Facebook
Android EditText Cursor Colour appears to be white - Android
Disable EditText Cursor Android - Android
Connection Failed: 1130 PHP MySQL Error - MySQL
SharePoint Managed Metadata Hidden Taxonomy List - TaxonomyHiddenList - SharePoint
Execute .bin and .run file Ubuntu Linux - Linux
Possible outages message Google Webmaster tool - Google
Android : Remove ListView Separator/divider programmatically or using xml property - Android
Unable to edit file in Notepad++ - NotepadPlusPlus
SharePoint PowerShell Merge-SPLogFile filter by time using StartTime EndTime - SharePoint
SQLite Error: unknown command or invalid arguments: open. Enter .help for help - Android
JBoss stuck loading JBAS015899: AS 7.1.1.Final Brontes starting - Java
Android Wifi WPA2/WPA Connects and Disconnects issue - Android
Android Toolbar example with appcompat_v7 21 - Android
ERROR x86 emulation currently requires hardware acceleration. Intel HAXM is not installed on this machine - Android

1 note
·
View note
Text
Php training course
PHP Course Overview
PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML.
PHP can generate the dynamic page content
PHP can create, open, read, write, and close files on the server
PHP can collect form data
PHP can send and receive cookies
PHP can add, delete, modify data in your database
PHP can restrict users to access some pages on your website
PHP can encrypt data
With PHP you are not limited to output HTML. You can output images, PDF files, and even Flash movies. You can also output any text, such as XHTML and XML.
PHP Training Course Prerequisite
HTML
CSS
Javascript
Objectives of the Course
PHP runs on different platforms (Windows, Linux, Unix, Mac OS X, etc.)
PHP is compatible with almost all servers used today (Apache, IIS, etc.)
PHP has support for a wide range of databases
PHP is free. Download it from the official PHP resource: www.php.net
PHP is easy to learn and runs efficiently on the server-side
PHP Training Course Duration
45 Working days, daily 1.30 hours
PHP Training Course Overview
An Introduction to PHP
History of PHP
Versions and Differences between them
Practicality
Power
Installation and configuring Apache and PHP
PHP Basics
Default Syntax
Styles of PHP Tags
Comments in PHP
Output functions in PHP
Datatypes in PHP
Configuration Settings
Error Types
Variables in PHP
Variable Declarations
Variable Scope
PHP’s Superglobal Variables
Variable Variables
Constants in PHP
Magic Constants
Standard Pre-defined Constants
Core Pre-defined Languages
User-defined Constants
Control Structures
Execution Control Statements
Conditional Statements
Looping Statements with Real-time Examples
Functions
Creating Functions
Passing Arguments by Value and Reference
Recursive Functions
Arrays
What is an Array?
How to create an Array
Traversing Arrays
Array Functions
Include Functions
Include, Include_once
Require, Require_once
Regular Expressions
Validating text boxes,emails,phone number,etc
Creating custom regular expressions
Object-Oriented Programming in PHP
Classes, Objects, Fields, Properties, _set(), Constants, Methods
Encapsulation
Inheritance and types
Polymorphism
Constructor and Destructor
Static Class Members, Instance of Keyword, Helper Functions
Object Cloning and Copy
Reflections
PHP with MySQL
What is MySQL
Integration with MySQL
MySQL functions
Gmail Data Grid options
SQL Injection
Uploading and downloading images in Database
Registration and Login forms with validations
Pegging, Sorting,…..
Strings and Regular Expressions
Declarations styles of String Variables
Heredoc style
String Functions
Regular Expression Syntax(POSIX)
PHP’s Regular Expression Functions(POSIX Extended)
Working with the Files and Operating System
File Functions
Open, Create and Delete files
Create Directories and Manipulate them
Information about Hard Disk
Directory Functions
Calculating File, Directory and Disk Sizes
Error and Exception Handling
Error Logging
Configuration Directives
PHP’s Exception Class
Throw New Exception
Custom Exceptions
Date and Time Functions
Authentication
HTTP Authentication
PHP Authentication
Authentication Methodologies
Cookies
Why Cookies
Types of Cookies
How to Create and Access Cookies
Sessions
Session Variables
Creating and Destroying a Session
Retrieving and Setting the Session ID
Encoding and Decoding Session Data
Auto-Login
Recently Viewed Document Index
Web Services
Why Web Services
RSS Syntax
SOAP
How to Access Web Services
XML Integration
What is XML
Create an XML file from PHP with Database records
Reading Information from XML File
MySQL Concepts
Introduction
Storage Engines
Functions
Operators
Constraints
DDL commands
DML Commands
DCL Command
TCL Commands
Views
Joins
Cursors
Indexing
Stored Procedures
Mysql with PHP Programming
Mysql with Sqlserver(Optional)
SPECIAL DELIVERY
Protocols
HTTP Headers and types
Sending Mails using PHP
Email with Attachment
File Uploading and Downloading using Headers
Implementing Chating Applications using PHP
and Ajax
SMS Gateways and sending SMS to Mobiles
Payments gateways and How to Integrate them
With Complete
MVC Architecture
DRUPAL
JOOMLA
Word Press
AJAX
CSS
JQUERY (Introduction and few plugins only)
1 note
·
View note
Text
Best way to prepare for PHP interview
PHP is one among the programming languages that are developed with built-in web development functions. The new language capabilities contained in PHP 7 ensure it is simpler for developers to extensively increase the performance of their web application without the use of additional resources. interview questions and answers topics for PHP They can move to the latest version of the commonly used server-side scripting language to make improvements to webpage loading without spending extra time and effort. But, the Web app developers still really should be able to read and reuse PHP code quickly to maintain and update web apps in the future.
Helpful tips to write PHP code clean, reliable and even reusable
Take advantage of Native Functions. When ever writing PHP code, programmers may easily achieve the same goal utilizing both native or custom functions. However, programmers should make use of the built-in PHP functions to perform a number of different tasks without writing extra code or custom functions. The native functions should also help developers to clean as well as read the application code. By reference to the PHP user manual, it is possible to collect information about the native functions and their use.
Compare similar functions. To keep the PHP code readable and clean, programmers can utilize native functions. However they should understand that the speed at which every PHP function is executed differs. Some PHP functions also consume additional resources. Developers must therefore compare similar PHP functions and select the one which does not negatively affect the performance of the web application and consume additional resources. As an example, the length of a string must be determined using isset) (instead of strlen). In addition to being faster than strlen (), isset () is also valid irrespective of the existence of variables.
Cache Most PHP Scripts. The PHP developers needs keep in mind that the script execution time varies from one web server to another. For example, Apache web server provide a HTML page much quicker compared with PHP scripts. Also, it needs to recompile the PHP script whenever the page is requested for. The developers can easily eliminate the script recompilation process by caching most scripts. They also get option to minimize the script compilation time significantly by using a variety of PHP caching tools. For instance, the programmers are able to use memcache to cache a lot of scripts efficiently, along with reducing database interactions.
common asked php interview questions and answers for freshers
Execute Conditional Code with Ternary Operators. It is actually a regular practice among PHP developers to execute conditional code with If/Else statements. But the programmers want to write extra code to execute conditional code through If/Else statements. They could easily avoid writing additional code by executing conditional code through ternary operator instead of If/Else statements. The ternary operator allows programmers to keep the code clean and clutter-free by writing conditional code in a single line.
Use JSON instead of XML. When working with web services, the PHP programmers have option to utilize both XML and JSON. But they are able to take advantage of the native PHP functions like json_encode( ) and json_decode( ) to work with web services in a faster and more efficient way. They still have option to work with XML form of data. The developers are able to parse the XML data more efficiently using regular expression rather than DOM manipulation.
Replace Double Quotes with Single Quotes. When writing PHP code, developers are able to use either single quotes (') or double quotes ("). But the programmers can easily improve the functionality of the PHP application by using single quotes instead of double quotes. The singular code will speed up the execution speed of loops drastically. Similarly, the single quote will further enable programmers to print longer lines of information more effectively. However, the developers will have to make changes to the PHP code while using single quotes instead of double quotes.
Avoid Using Wildcards in SQL Queries. PHP developers typically use wildcards or * to keep the SQL queries lightweight and simple. However the use of wildcards will impact on the performance of the web application directly if the database has a higher number of columns. The developers must mention the needed columns in particular in the SQL query to maintain data secure and reduce resource consumption.
However, it is important for web developers to decide on the right PHP framework and development tool. Presently, each programmer has the option to decide on a wide range of open source PHP frameworks including Laravel, Symfony, CakePHP, Yii, CodeIgniter, and Zend. Therefore, it becomes necessary for developers to opt for a PHP that complements all the needs of a project. interview questions on PHP They also need to combine multiple PHP development tool to decrease the development time significantly and make the web app maintainable.
php interview questions for freshers
youtube
1 note
·
View note
Text
Best Institutes for PHP Training in Chandigarh
May 18, 2023
PHP Training in Chandigarh
PHP training is an invaluable resource for individuals seeking to master one of the most popular programming languages used for web development. PHP, which stands for Hypertext Preprocessor, empowers developers to create dynamic and interactive websites. Through PHP training in Chandigarh, aspiring developers gain a comprehensive understanding of PHP syntax, functions, and frameworks, enabling them to build robust and scalable web applications. They learn how to integrate PHP with databases, handle form data, implement security measures, and utilize advanced features to enhance the user experience. With hands-on exercises and real-world projects, PHP training equips individuals with the skills and knowledge necessary to create dynamic web solutions and embark on a successful career in web development.
PHP Training
WHAT IS PHP COURSE IN CHANDIGARH?
A PHP course is a structured educational program designed to teach individuals about the PHP scripting language and its applications in web development. The course typically covers a wide range of topics, including the basics of PHP syntax, variables, data types, control structures, functions, arrays, and file handling. Participants learn how to integrate PHP with databases, such as MySQL, and use it to perform common database operations. Additionally, the course may introduce popular PHP frameworks like Laravel or CodeIgniter, which facilitate the development of complex web applications. Students are often guided through hands-on exercises and projects to reinforce their understanding and gain practical experience. By completing a PHP course, individual s acquire the skills necessary to create dynamic and interactive websites and web applications using PHP as their programming language of choice. php-training-in-chandigarh
SYLLABUS OF PHP COURSE IN CHANDIGARH?
Introduction to PHP
Basics of PHP
1. PHP syntax and variables
Data types and operators
Control Structures and Functions
2. Conditional statements (if, else, switch)
Loops (for, while, do-while)
Functions and function libraries
Arrays and Strings
3. Working with arrays
Array functions
Manipulating strings
String functions PHP Forms and Data Handling
4. HTML forms and PHP form handling
Form validation and data sanitization File uploading and handling Working with Databases
5. Introduction to databases
MySQL database connectivity SQL queries and data manipulation CRUD operations (Create, Read, Update, Delete) Object-Oriented Programming (OOP) in PHP
6. OOP concepts and principles
Classes, objects, and inheritance Encapsulation, polymorphism, and abstraction OOP best practices in PHP Error Handling and Debugging
7. Common errors and debugging techniques
Error handling mechanisms in PHP Exception handling Session Management and Cookies
8. Managing user sessions
Working with cookies Session security considerations PHP Frameworks
9. Introduction to popular PHP frameworks (e.g., Laravel, CodeIgniter)
MVC (Model-View-Controller) architecture Building web applications using a PHP framework Web Services and APIs
10. Consuming web services and APIs
RESTful API development in PHP JSON and XML data handling Security and Best Practices
11. PHP security vulnerabilities and mitigation
Data validation and input sanitization Password hashing and encryption Secure coding practices Deployment and Project Development.
BENEFITS OF DOING PHP TRAINING IN CHANDIGARH
Training from the team of professional PHP developers with years of experience. Training on core Live Projects to get practical exposure of programming. Training on various CMS and framework as per your requirement. Small batches with early morning or late evening and weekend batch availability. Get free personal domain and hosting as we have our own dedicated Web servers. Get more than 2000 solved PHP interview question answers.
TRAININGS RELATED TO PHP TRAINING IN CHANDIGARH
WEB DESIGNING COURSE IN CHANDIGARH web designing course in chadigarh
DIGITAL MARKETING COURSE IN CHANDIGARHdigital marketing course in chandigarh
GRAPHIC DESIGNING COURSE IN CHANDIGARH and many more.graphic designing course in chandigarh
RELEVANT INSTITUTES FOR DOING PHP TRAINING IN CHANDIGARH
1. EXCELLENCE TECHNOLOGY
Excellence technology in Chandigarh is a best institute which provides digital marketing course, web designing course, graphic designing course , full stack course and programming language course and many more. They work on PHP , java , web designing, python etc.excellence-technology
2. EXTECH DIGITAL.
Extech Digital is best for php training in Chandigarh which gives you the facility of doing PHP training in Chandigarh , programming languages, web designing courses , coding languages, digital marketing courses etc . Extech
3. EXCELLENCE ACADEMY.
Excellence academy is a best institute for php training in Chandigarh which also gives all the facility that a php trainer wants. It also provides these courses in Hamirpur and Kangra also.excellence-academy
ABOUT AUTHOR.
Disha is a PHP Expert who is formerly working with Excellence technology for nearly five years. She is well experienced in programming languages.
you can follow her on:instagramfacebook
Comments
Powered by Blogger
Theme images by Michael Elkan
0 notes
Text
Why PHP is the Preferred Choice for Web Application Development
Introduction
There are a variety of programming languages available for developing web applications, however PHP has become the programming language of choice among many developers and enterprises. PHP's versatility, scalability, cost-effectiveness, vast community, and security features make it a popular language among developers for developing online applications. In this blog, we'll look at why PHP is such a popular choice for web application development and how it can help businesses create dynamic and sophisticated web applications.

4 reasons why developers prefer PHP for web application development.
A PHP application development company can provide services like custom software services, web application development, and e-commerce solutions. Here are four reasons developers opt for PHP for web application development.
Scalability and adaptability
PHP's adaptability and scalability are two of its greatest strengths. PHP is a server-side scripting language, meaning it operates on the server instead of the client's computer. This allows for the management of massive volumes of traffic and complicated applications.
PHP is also highly adaptable and can be utilised to create both simple and complicated web applications. It covers a vast array of capabilities and functionalities, including database management, file manipulation, and XML parsing. This makes it a flexible language that may be used to create a wide range of online apps.
Integration with Databases: PHP has excellent integration with popular databases like MySQL and PostgreSQL, making it easy to build dynamic and database-driven web applications.
Cost-effective
Another benefit of PHP is that it is a cost-effective choice for developing online applications. PHP is an open source language, meaning that its source code can be viewed, modified, and distributed by anyone. This has resulted in a strong and active development community of developers that contributes to the language and its ecosystem. This can significantly reduce licence fees and other costs connected with proprietary software.
Moreover, PHP requires fewer hardware and software resources than other programming languages. This allows firms to save money on hardware and software costs. For instance, a company can run a PHP-based web application on a Linux server, which is significantly less expensive than running the same programme on a high-end server running proprietary software.
Large communities and frameworks
PHP has a broad and active developer community. This community provides a plethora of materials and assistance to other PHP developers. Developers can gain access to documentation, tutorials, and other tools that will assist them in learning PHP and developing web apps more efficiently.
There are also other prominent PHP frameworks, including Laravel, Symfony, and CodeIgniter. These frameworks offer ready-made solutions for typical tasks and features, which can help to accelerate the development process. Laravel, for example, includes an authentication system that can save developers a significant amount of time and work.
Stability and security
Security is a significant consideration in online application development, and PHP is a secure language with various security measures built in. PHP, for example, includes routines for dealing with SQL injections and cross-site scripting (XSS) assaults. PHP also offers a number of extensions and libraries that can be used to improve online application security.
PHP is also a stable language that receives frequent upgrades and enhancements. The PHP development community is always trying to improve the language and remedy any bugs or security flaws. As a result, businesses can rely on PHP to provide a solid and secure framework for their web applications.
Popular web applications developed using PHP
Wikipedia
Tumblr
Wordpress
Yahoo
iStockPhoto
Conclusion
PHP is the ideal choice for web application development for a variety of reasons. It is a versatile and scalable language capable of handling high volumes of traffic and complicated applications. It is also a more cost-effective alternative, requiring fewer hardware and software resources than other languages. PHP has a huge and active developer community, as well as various popular frameworks that can help speed up the development process. Finally, PHP is a secure and stable language that the PHP development community is constantly improving. All of these aspects combine to make PHP the preferred language for web application development.
If you are looking for a PHP application development company to develop web apps for your business, look no further than Openspace Services. They are also one of the best DevOps companies in India. They have worked with more than five global firms and have delivered all their projects on time. Their team of talented PHP developers makes sure the applications that are delivered to you are effective and can help your business grow. Visit their website to know more about their services
0 notes
Text
PHP is one amongst the programming languages that were developed with inbuilt net development capabilities. The new language options enclosed in PHP seven any makes it easier for programmers to boost the speed of their net application considerably while not deploying extra resources. They programmers will switch to the foremost recent version of the wide used server-side scripting language to enhance the load speed of internet sites while not swing beyond regular time and energy. however the net application developers still want target the readability and reusability of the PHP code to take care of and update the net applications quickly in future.
12 Tips to write down Clean, rectifiable, and Reusable PHP Code
1) benefit of Native Functions While writing PHP code, the programmers have choice to accomplish identical objective by victimisation either native functions or custom functions. however the developers should benefit of the inbuilt functions provided by PHP to accomplish a spread of tasks while not writing extra code or custom functions. The native functions can any facilitate the developers to stay the appliance code clean and decipherable. they'll simply gather info concerning the native functions and their usage by touching on the PHP user manual.
Another way to check phpstorm key shortcuts
2) Compare Similar Functions The developers will use native functions to stay the PHP code decipherable and clean. however they need to keep in mind that the speed of individual PHP functions differs. Also, bound PHP functions consume extra resources than others. Hence, the developers should compare similar PHP functions, and select the one that doesn't have an effect on the performance of the net application negatively and consume extra resources. as an example, they need to verify the length of a string by victimisation isset() rather than strlen(). additionally to being quicker than strlen(), isset() conjointly remains valid in spite of the existence of variables.
3) Cache Most PHP Scripts The PHP programmers should keep in mind that the script execution time differs from one net server to a different. as an example, Apache net server serve a HTML page abundant quicker than PHP scripts. Also, it has to recompile the PHP script on every occasion the page is requested for. The programmers will simply eliminate the script recompilation method by caching most scripts. They even have choice to scale back the script compilation time considerably by employing a style of PHP caching tools. as an example, the programmers will use memcache to cache an oversized variety of scripts expeditiously, at the side of reducing info interactions.
4) Execute Conditional Code with Ternary Operators It is a typical observe among PHP developers to execute conditional code with If/Else statements. however the developers got to writing extra code to execute conditional code through If/Else statements. they'll simply avoid writing extra code by corporal punishment conditional code through ternary operator rather than If/Else statements. The ternary operator helps programmers to stay the code clean and clutter-free by writing conditional code during a single line.
5) Keep the Code decipherable and rectifiable Often programmers notice it intimidating perceive and modify the code written by others. Hence, they have beyond regular time to take care of and update the PHP applications expeditiously. whereas writing PHP code, the programmers will simply build the appliance simple to take care of and update by describing the usage and significance of individual code snippets clearly. they'll simply build the code decipherable by adding comments to every code piece. The comments can build it easier for alternative developers to form changes to the present code in future while not swing beyond regular time and energy.
6) Use JSON rather than XML While operating with net services, the PHP programmers have choice to use each XML and JSON. however they'll continuously benefit of the native PHP functions like json_encode( ) and json_decode( ) to figure with net services during a quicker and a lot of economical manner. They still have choice to work with XML style of information. The programmers will break down the XML information a lot of expeditiously by victimisation regular expression rather than DOM manipulation.
7) Pass References rather than worth to Functions The intimate PHP programmers ne'er declare new categories and strategies only if they become essential. They conjointly explore ways in which to recycle the categories and strategies throughout the code. However, they conjointly perceive the actual fact that a perform may be manipulated quickly by passing references rather than values. they'll any avoid adding additional overheads by passing references to the perform rather than values. However, they still got to make sure that the logic remains unaffected whereas passing relevancy the functions.
8) flip Error coverage on in Development Mode The developers should establish and repair all errors or flaws within the PHP code throughout the event method. They even have to place overtime and energy to mend the writing errors and problems known throughout testing method. The programmers merely set the error coverage to E_ALL to spot each minor and major errors within the PHP code throughout the event method. However, they need to flip the error coverage choice off once the appliance moves from development mode to production mode.
9) Replace inverted comma with Single Quotes While writing PHP code, programmers have choice to use either single quotes (') or inverted comma ("). however the developers will simply enhance the performance of the PHP application by victimisation single quotes rather than inverted comma. the only code can increase the speed of loops drastically. Likewise, the only quote can any change programmers to print longer lines of data a lot of expeditiously. However, the developers got to build changes to the PHP code whereas victimisation single quotes rather than inverted comma.
10) Avoid victimisation Wildcards in SQL Queries PHP programmers typically use wildcards or * to stay the SQL queries compact and easy. however the employment of wildcards might have an effect on the performance of the net application directly if the info includes a higher variety of columns. The programmers should mention the desired columns specifically within the SQL question to stay information secure and scale back resource consumption.
11) Avoid corporal punishment info Queries in Loop The PHP programmers will simply enhance the net application's performance by not corporal punishment info queries in loop. They even have variety of choices to accomplish identical results while not corporal punishment info queries in loop. as an example, the developers will use a strong WordPress plug-in like question Monitor to look at the info queries at the side of the rows laid low with them. they'll even use the debugging plug-in to spot the slow, duplicate, and incorrect info queries.
12) ne'er Trust User Input The sensible PHP programmers keep the net application secure by ne'er trusting the input submitted by users. They continuously check, filter and sanitize all user info to guard the appliance from varied security threats. they'll any forestall users from submitting inappropriate or invalid information by victimisation inbuilt functions like filter_var(). The perform can check for applicable values whereas receiving or process user input.
However, it's conjointly necessary for the net developers to select the correct PHP framework and development tool. At present, every technologist has choice to choose between a large vary of open supply PHP frameworks as well as Laravel, Symfony, CakePHP, Yii, CodeIgniter and Iranian language. Hence, it becomes essential for programmers to select a PHP that enhances all wants of a project. They conjointly got to mix multiple PHP development tool to scale back the event time considerably and build the net application rectifiable.
1 note
·
View note