#Open source network bandwidth monitoring tool
Explore tagged Tumblr posts
Text

ARM Embedded Remote Controller for Weather Monitoring System
System Overview
A weather monitoring system requires real-time collection of various environmental parameters (e.g., temperature, humidity, wind speed, air pressure, rainfall) and efficient data processing and communication for remote monitoring and analysis. The ARMxy Embedded Remote Controller BL335ARMxy SBC realizes real-time data collection, remote monitoring and intelligent analysis of meteorological monitoring, and is widely used in automatic weather stations, agricultural monitoring, environmental monitoring, etc. with its industrial-grade design, rich interface configuration, and robust protocol support, serves as an ideal core device for building such systems.
Hardware Configuration Plan
Core Hardware Selection
Host Model: BL335B (supports 2 Y-series I/O boards for multi-sensor connectivity).
SOM Module: SOM335 (8GB eMMC + 1GB DDR3, ensuring large-capacity data buffering and processing).
Wireless Communication: Added 4G module (model BL335L) for reliable data transmission in remote areas.
Sensor and I/O Board Integration
Y-series I/O Boards:
Y31: 4-channel single-ended 0/4~20mA analog input for current-type temperature/humidity sensors.
Y33: 4-channel 0~10V analog input for voltage-type pressure sensors.
Y95: 4-channel PWM output + pulse counting for anemometer signal acquisition.
Y63: 4-channel RS485 for Modbus-compatible digital sensors (e.g., rain gauge).
Expandability: Use X-series I/O boards (e.g., X1) to expand RS485 interfaces for additional industrial protocol devices.
Environmental Adaptability
Mounting: DIN35 rail installation for outdoor cabinets or industrial control boxes.
Protection: IP30 dustproof design with custom waterproof housing for harsh weather.
Wide Temperature Range: Operates at -40°C to 85°C for stability in extreme environments.
Software Architecture and Functionality
OS and Development Tools
OS: Ubuntu 20.04, offering open-source toolchains and containerization support.
Development Frameworks:
Node-RED: Graphical programming for data flow logic (e.g., sensor data cleaning, threshold alerts).
Docker: Containerized deployment of MQTT/OPC UA data forwarding services for seamless cloud integration.
Protocol and Data Management
BLIoTLink Protocol Conversion:
Converts Modbus RTU (RS485 sensors) to MQTT for cloud platforms (e.g., Alibaba Cloud IoT).
Supports IEC104 protocol for integration with SCADA systems in meteorological stations.
Edge Computing and Storage:
SQLite for historical data storage; Python scripts for anomaly filtering.
Real-time edge calculations (e.g., average wind speed, temperature/humidity trends) to reduce cloud load.
Remote Maintenance and Monitoring
BLRAT Tool: Remote access for firmware updates or sensor configuration.
Watchdog: Auto-restart for failed services, ensuring 24/7 operation.
Typical Applications
Solar Farm Weather Stations: Monitor irradiance and wind speed to optimize PV panel angles.
Agricultural Networks: Collect soil moisture/temperature for smart irrigation systems.
Transportation Alerts: Upload real-time road icing data for intelligent traffic management.
Key Advantages
High Reliability: Passes GB/T EMC and IP30 tests for harsh industrial environments.
Flexible Expansion: 4000+ module combinations, compatible with diverse sensors and protocols.
Low-Cost Operation: BLRAT reduces on-site maintenance; edge computing minimizes bandwidth usage.
Implementation Recommendations
Sensor Calibration: Use Y-series AO outputs for periodic analog signal calibration.
Power Redundancy: 9-36V wide input voltage; deploy solar + lithium battery solutions.
Data Security: Enable Linux kernel encryption for secure data transmission.
The ARMxy BL335, with its high customization and industrial-grade performance, provides an end-to-end solution for weather monitoring systems—from data acquisition to cloud integration—empowering smart city and green energy initiatives.
0 notes
Text
Powering Connectivity: Modern Networking Solutions

In today’s hyper-connected world, networking solutions are no longer optional — they’re foundational. From small startups to sprawling global enterprises, effective networking infrastructure determines not only operational efficiency but also competitiveness, security, and scalability. As technology evolves, so too must the architecture that connects our systems, data, and people.
What Are Networking Solutions?
At their core, networking solutions encompass the hardware, software, and protocols that enable communication between devices within a network. These solutions range from local area networks (LANs) and wide area networks (WANs) to more complex architectures such as software-defined networking (SDN), cloud networking, and hybrid models that integrate on-premises and cloud-based resources.
Key Components of Modern Networking
Hardware Infrastructure Routers, switches, access points, and firewalls form the physical layer of networking. Choosing the right hardware ensures speed, reliability, and security across an organization’s digital environment.
Network Management Software These tools offer centralized control, allowing administrators to monitor traffic, configure devices, and identify potential threats or bottlenecks. Intelligent software reduces downtime and enhances productivity.
Security Protocols As cyber threats become increasingly sophisticated, secure networking has become paramount. Encryption, intrusion detection systems, and secure access controls are essential elements in any comprehensive solution.
Cloud and Virtual Networking With the rise of cloud computing, virtual networking solutions have gained prominence. These solutions support scalability and remote access while reducing the need for physical infrastructure.
Wireless and Mobile Connectivity Wireless networking continues to advance with technologies like Wi-Fi 6 and 5G, offering faster and more reliable connections, which are essential for mobile workforces and IoT deployments.
Trends Driving Innovation in Networking
Edge Computing Integration Networking is moving closer to data sources with edge computing, reducing latency and improving response times in critical applications such as autonomous vehicles and real-time analytics.
AI-Powered Network Management Artificial Intelligence is increasingly being used to predict network failures, automate troubleshooting, and optimize bandwidth allocation dynamically.
Zero Trust Architecture Instead of assuming devices within a network can be trusted, this model verifies each request as though it originated from an open network, significantly enhancing security.
Network as a Service (NaaS) This model allows businesses to lease network infrastructure and services, offering flexibility, cost savings, and simplified management.

Building a Future-Ready Network
To build a resilient and future-proof network, organizations must adopt a strategic approach. This includes assessing current and future needs, prioritizing cybersecurity, and embracing innovations such as virtualization and automation. Cross-functional collaboration between IT, cybersecurity, and business units is essential to align network capabilities with organizational goals.
Conclusion
Networking solutions are not just technical tools — they’re strategic enablers of growth and innovation. As digital transformation accelerates, investing in robust, scalable, and intelligent networking infrastructure is no longer a luxury but a necessity. The future belongs to those who can stay connected — securely, efficiently, and at scale.
0 notes
Text
Which is the Best ISP Billing Software in India?

In India’s fast-growing digital economy, Internet Service Providers (ISPs) play a vital role in delivering seamless connectivity to businesses and households. Whether you're running a regional broadband company or a nationwide ISP brand, managing customers, billing cycles, and data usage efficiently is crucial. That’s where choosing the Best ISP billing software becomes essential. In this guide, we’ll explore what features define a great ISP billing tool and highlight some of the top solutions available in India today.
Why ISP Billing Software Is Critical for Your Business
Manual billing is outdated, error-prone, and inefficient. A robust ISP billing software automates the process of: - Generating GST-compliant invoices - Tracking bandwidth usage and session logs - Managing prepaid/postpaid plans - Sending payment reminders and processing transactions - Integrating with CRM and network hardware The right solution helps ISPs reduce downtime, avoid revenue leakage, and offer a better experience to subscribers.
Key Features to Look for in the Best ISP Billing Software
Before choosing any billing system, consider these essential features: ✅ Automated Invoicing and Payments: Reduce manual workload and ensure timely billing ✅ Bandwidth and Data Monitoring: Track usage per user for fair billing ✅ User Management and Plan Customization: Support for tiered plans and policy control ✅ Integration: Connect with routers (like MikroTik), CRMs, SMS/email services ✅ Compliance: Ensure adherence to TRAI and GST regulations ✅ Cloud-based vs. On-Premise: Choose based on flexibility and IT capacity
Top 5 ISP Billing Software in India
NetAdmin by NetSoft Solutions
NetAdmin is a leading ISP billing software designed specifically for the Indian broadband market.
- 📌 Features: Online payments, GST billing, network integration, customer self-care portal - ✅ Pros: India-focused, strong support team, TRAI-compliant reporting - ❌ Cons: Slightly dated UI - 💰 Pricing: Custom plans based on user base Best for: Small to mid-sized Indian ISPs seeking local support
24Online by Elitecore (Sterlite Technologies)
24Online has been a trusted name for over a decade, offering a comprehensive AAA (Authentication, Authorization, Accounting) platform.
- 📌 Features: Prepaid/postpaid billing, hotspot management, franchisee billing, RADIUS support - ✅ Pros: Highly scalable, widely adopted by ISPs and hospitality providers - ❌ Cons: Premium pricing for advanced features - 💰 Pricing: Tiered enterprise pricing Best for: Large ISPs or WiFi hotspots needing scalable infrastructure
Splynx
While Splynx is developed in Europe, it’s increasingly popular among Indian ISPs due to its powerful integration capabilities.
- 📌 Features: RADIUS server, CRM, billing automation, API access, VoIP integration - ✅ Pros: Highly customizable, supports MikroTik, Ubiquiti, and other routers - ❌ Cons: Requires technical setup - 💰 Pricing: Starts at ~$49/month Best for: Tech-savvy ISPs who want flexibility and control
Antamedia ISP Billing
This Windows-based solution supports internet cafes, hotspots, and small broadband providers.
- 📌 Features: Bandwidth control, captive portal, pre-paid billing - ✅ Pros: One-time license pricing, ideal for smaller operators - ❌ Cons: Limited scalability, desktop-based (no cloud) - 💰 Pricing: One-time license fee (varies by user/device count) Best for: Café-style networks and local WiFi operators
MikroTik + Third-Party Billing Add-ons
If you’re using MikroTik routers, pairing them with open-source or commercial billing tools (like Radius Manager or Splynx) can create a cost-effective solution.
- 📌 Features: Custom network policies, RADIUS authentication, usage billing - ✅ Pros: Flexible, hardware-level control - ❌ Cons: Technical learning curve - 💰 Pricing: Varies based on software/plugin Best for: ISPs with in-house tech teams who prefer open/custom setups
How to Choose the Right ISP Billing Software
Here are a few questions to guide your decision: - How large is your subscriber base? - Do you need cloud access or prefer local deployment? - Do you require integration with specific hardware like MikroTik or Cisco? - Is your team technically equipped to handle a custom or open-source solution? - Are compliance and tax (GST) reporting features included? If you're a small or mid-sized Indian ISP, NetAdmin and 24Online provide reliable, region-specific support. For advanced customization and integrations, Splynx offers a great balance of features and scalability.
Final Thoughts
Finding the best ISP billing software in India depends on your specific needs, budget, and technical capacity. Whether you’re just starting or scaling nationwide, investing in the right platform can streamline your operations and improve subscriber satisfaction. If you’re an Indian ISP evaluating software, make sure to request demos, explore integrations, and ask for local support options before deciding. 📝 Have you used any of these tools, or do you recommend another one? Let us know in the comments!
FAQs
🔹 What is ISP billing software?
It’s a platform used by Internet Service Providers to manage customer accounts, billings, bandwidth tracking, and plan management.
🔹 Is GST billing supported by Indian ISP software?
Yes, most India-focused platforms like NetAdmin and 24Online offer GST-compliant invoicing.
🔹 Can I use free or open-source tools?
Yes, but they often require technical expertise. Pairing MikroTik with open-source billing platforms can be budget-friendly but complex to manage.
#isp billing software in delhi#aaa solution for isp#best isp billing software#billing software for isp#isp billing software#isp billing solution#isp crm software#isp erp#isp management software#isp radius solution
0 notes
Text
Edge Computing in 2025: Enhancing Real-Time Data Processing and IoT Integration
As someone who's worked in tech through multiple waves of transformation, it's clear: edge computing is no longer a buzzword—it’s the backbone of real-time digital infrastructure in 2025.
Whether you're deploying thousands of IoT sensors in a smart factory or running AI models at the edge in a hospital, the need to process data closer to the source is more critical than ever. Cloud is still important, but latency, bandwidth, and privacy concerns have pushed us to rethink how and where we compute.
Let’s unpack what’s changed—and what edge computing really looks like in 2025.
What Edge Computing Means Today
Back in the day, we pushed everything to the cloud. It worked—for a while. But with the explosion of IoT, AI workloads, and real-time demands, we hit a wall. Edge computing evolved as a response.
In 2025, edge computing means:
Real-time decisions without cloud dependency
Smarter endpoints (not just data collectors)
Integrated security, orchestration, and AI at the edge
The Shift: From Centralized to Distributed
In practice, this means pushing compute, storage, and intelligence to where the data is generated. It could be:
A camera on a highway
A robotic arm on a factory floor
A health monitor on a patient
This shift reduces latency from seconds to milliseconds—and that can mean the difference between insight and incident.
Real-World Use Cases I’ve Seen
Here are some real-world examples I’ve worked with or seen evolve:
Manufacturing
Quality inspection cameras running AI locally
Predictive maintenance models analyzing vibration data in real time
Healthcare
Edge-based diagnostic devices reducing hospital visit times
Secure, compliant local data processing for patient monitoring
Automotive
Vehicles using onboard compute for real-time navigation and hazard detection
V2X (Vehicle-to-Everything) running on edge networks at traffic lights
Smart Cities
Real-time traffic management using edge video analytics
Waste bins alerting pickups when full—processed on-site
What’s Driving This Shift in 2025?
A few key forces are accelerating edge computing:
5G deployment has made edge even faster and more practical
AI hardware has gotten cheaper and smaller (NVIDIA Jetson, Coral, etc.)
Cloud-native edge tools like KubeEdge and Open Horizon make orchestration manageable
Businesses want real-time insights without sending everything to the cloud
But What About Security?
Security used to be the biggest barrier. In 2025, we're seeing more mature edge security practices:
Zero Trust at the edge
Built-in TPMs and secure boot
AI models detecting threats locally before they propagate
Security at the edge is still a challenge—but it’s more manageable now, especially with standardized frameworks and edge-specific IAM tools.
Final Thoughts
If you’re still thinking of edge computing as a future trend, it’s time to recalibrate. In 2025, edge is mainstream—and it's how smart, connected systems are built.
As someone who’s deployed both cloud and edge architectures, I’ve learned this: the best strategy today isn’t “cloud vs. edge,” it’s “cloud + edge.” You need both to build fast, reliable, scalable systems.
Edge computing isn’t just an optimization—it's a requirement for real-time digital transformation.
#artificial intelligence#sovereign ai#coding#devlog#entrepreneur#linux#html#gamedev#economy#indiedev
0 notes
Text
Download Manager - Persepolis Download Manager
A Comprehensive Guide to Persepolis Download Manager
In the world of internet downloads, having a reliable and efficient download manager can make a huge difference. Persepolis Download Manager is a powerful tool that stands out among various download managers for its simplicity, speed, and open-source nature. Whether you’re downloading a large file or multiple files at once, Persepolis can help you manage, pause, resume, and schedule your downloads with ease.
Here’s everything you need to know about Persepolis Download Manager:
What is Persepolis Download Manager?
Persepolis is an open-source download manager that allows you to accelerate your downloads and manage them with ease. It is compatible with both Linux and Windows operating systems. Persepolis acts as a graphical user interface (GUI) for Aria2, which is a command-line download utility, known for its high-speed downloading capabilities and support for multiple protocols like HTTP(S), FTP, and BitTorrent.
The software was designed to offer a simple, user-friendly experience while maintaining the power of Aria2 behind the scenes. As an open-source project, Persepolis provides users with full control over its functionality and allows for transparency and community contributions.
Key Features of Persepolis Download Manager
Download Acceleration Persepolis helps speed up your downloads by splitting files into multiple segments and downloading them simultaneously, resulting in faster download speeds. This is especially useful when downloading large files or multiple files at once.
Pause and Resume Downloads One of the most useful features of Persepolis is the ability to pause and resume downloads. Whether you’re dealing with an unstable internet connection or need to shut down your system, you can pick up right where you left off, saving you time and bandwidth.
Scheduling Downloads Persepolis allows you to schedule downloads for later. This feature is perfect for those who want to download large files overnight or when network congestion is minimal.
Batch Downloading You can queue up multiple files for downloading at once. Persepolis will manage them in the background, ensuring that each download starts and finishes without requiring manual intervention.
Browser Integration Persepolis integrates seamlessly with popular browsers like Firefox and Chrome. Once the plugin is installed, you can easily add downloads to Persepolis directly from the browser with a single click, bypassing the browser’s built-in download manager.
Support for Multiple Protocols Persepolis supports several protocols, including HTTP(S), FTP, and BitTorrent. This makes it versatile for all kinds of downloads, whether from standard websites or peer-to-peer networks.
User-Friendly Interface Persepolis’s interface is clean and intuitive, making it easy for both beginners and advanced users to navigate. Its simple design ensures that users can start using it right away without needing to read lengthy manuals.
Cross-Platform Being available on both Linux and Windows ensures that a wide range of users can benefit from Persepolis Download Manager. You can use it on your desktop or laptop without worrying about compatibility issues.
Notifications and Alerts Persepolis keeps you updated with progress notifications. When your download completes, you will receive an alert, so you’re always in the loop without needing to constantly monitor the app.
How to Install Persepolis Download Manager?
For Linux:
Using APT (Ubuntu/Debian): Open a terminal and run the following command:bashCopysudo apt install persepolis
From Source: You can also download the source code from the official Persepolis GitHub repository and build it manually if you prefer to customize the installation.
For Windows:
Download the Installer: Visit the official Persepolis website or its GitHub page to download the Windows installer. Simply follow the prompts to complete the installation process.
Install via Windows Package Manager (Winget): You can also install Persepolis using Windows Package Manager by running:bashCopywinget install Persepolis
Why Choose Persepolis?
Open-Source and Free Persepolis is completely free and open-source, meaning that anyone can contribute to its development or use it without any cost. There are no hidden fees or premium features locked behind a paywall.
Lightweight Unlike some other download managers, Persepolis is lightweight, meaning it doesn’t take up much system space or resources, even during active downloads.
Community Support Persepolis has a dedicated community of users and developers who contribute to its improvement. If you encounter any issues, you can easily find help or file a bug report.
Completely Customizable Being open-source, Persepolis is customizable to fit your needs. You can adjust its settings to maximize download performance, adjust the number of segments, or tweak it to work with your preferred browser.
Privacy-Focused Persepolis respects user privacy. Unlike some proprietary download managers, it does not track your downloads or impose unwanted ads.
Troubleshooting Common Issues
While Persepolis is generally reliable, users may encounter some common issues such as:
Slow Downloads If you’re experiencing slow download speeds, ensure that the number of download segments is set to a higher value, as this can help accelerate the process. Additionally, check your internet connection for any interruptions.
Browser Integration Issues If the browser integration isn’t working, ensure that the Persepolis browser extension is installed and properly configured in your browser settings.
Connection Timeouts Sometimes, Persepolis may fail to connect to a server due to connection timeouts. This issue can be solved by adjusting the connection timeout settings or retrying the download.
Conclusion
Persepolis Download Manager is an exceptional tool for managing and accelerating your downloads. Its open-source nature, ease of use, and powerful features make it a top choice for anyone looking to download files more efficiently. Whether you’re a casual user or a power downloader, Persepolis offers all the features you need to streamline your download experience.
So, if you haven’t already, give Persepolis a try and experience how it can improve your downloading workflow. Happy downloading!
Persepolis for Windows > https://github.com/persepolisdm/persepolis/releases
Persepolis for Chromium based Browsers > https://chrome.google.com/webstore/detail/persepolis-download-manag/legimlagjjoghkoedakdjhocbeomojao?hl=en
Persepolis for Mozilla based Browsers > https://addons.mozilla.org/en-US/firefox/addon/persepolis-dlm-integration/
Screenshot: (Multiple themes available)
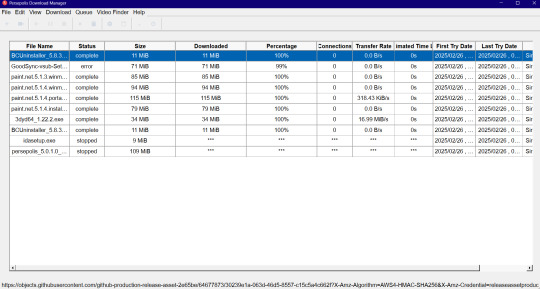
0 notes
Text
Cloud Cost Optimization Strategies: Reducing Expenses Without Sacrificing Performance
As organizations increasingly rely on cloud infrastructure, cloud cost optimization has become a top priority. While cloud services offer flexibility and scalability, they can also lead to unexpected expenses if not managed properly. The challenge is to reduce cloud costs without compromising performance, security, or availability.
This blog explores proven strategies for cloud cost optimization, helping businesses maximize ROI while maintaining efficiency.
1. Understanding Cloud Cost Challenges
Before optimizing costs, it’s essential to understand where cloud spending can spiral out of control:
🔴 Common Cost Pitfalls in Cloud Computing
Underutilized Resources – Idle virtual machines (VMs), storage, and databases consuming costs unnecessarily.
Over-Provisioning – Paying for computing power that exceeds actual demand.
Lack of Monitoring – Poor visibility into usage patterns and billing leads to inefficiencies.
Data Transfer Costs – High egress charges from excessive data movement between cloud services.
Inefficient Scaling – Failure to implement auto-scaling results in overpaying during low-demand periods.
💡 Solution? Implement cloud cost optimization strategies that ensure you're only paying for what you need.
2. Cloud Cost Optimization Strategies
✅ 1. Rightsize Your Cloud Resources
Analyze CPU, memory, and storage usage to determine the appropriate instance size.
Use cloud-native tools like:
AWS Cost Explorer
Azure Advisor
Google Cloud Recommender
Scale down or terminate underutilized instances to cut costs.
✅ 2. Implement Auto-Scaling and Load Balancing
Use auto-scaling to dynamically adjust resource allocation based on traffic demands.
Implement load balancing to distribute workloads efficiently, reducing unnecessary resource consumption.
🔹 Example: AWS Auto Scaling Groups ensure instances are added or removed automatically based on demand.
✅ 3. Optimize Storage Costs
Move infrequently accessed data to low-cost storage tiers like:
Amazon S3 Glacier (AWS)
Azure Cool Storage
Google Cloud Coldline Storage
Delete obsolete snapshots and redundant backups to avoid unnecessary costs.
✅ 4. Use Reserved Instances & Savings Plans
Reserved Instances (RIs) – Prepay for cloud resources to get discounts (e.g., up to 72% savings on AWS RIs).
Savings Plans – Commit to a specific usage level for long-term discounts on cloud services.
💡 Best for: Organizations with predictable workloads that don’t require frequent scaling.
✅ 5. Leverage Spot Instances for Cost Savings
Spot Instances (AWS), Preemptible VMs (GCP), and Low-Priority VMs (Azure) offer discounts up to 90% compared to on-demand pricing.
Ideal for batch processing, big data analytics, and machine learning workloads.
🚀 Example: Netflix uses AWS Spot Instances to reduce rendering costs for video processing.
✅ 6. Monitor and Optimize Cloud Spending with Cost Management Tools
Track real-time usage and spending with:
AWS Cost Explorer & Trusted Advisor
Azure Cost Management + Billing
Google Cloud Billing Reports
Set up budget alerts and anomaly detection to prevent unexpected cost spikes.
✅ 7. Reduce Data Transfer and Egress Costs
Minimize inter-region and cross-cloud data transfers to avoid high bandwidth charges.
Use Content Delivery Networks (CDNs) like Cloudflare, AWS CloudFront, or Azure CDN to reduce data movement costs.
💡 Pro Tip: Keeping data in the same region where applications run reduces network charges significantly.
✅ 8. Optimize Software Licensing Costs
Use open-source alternatives instead of expensive third-party software.
Leverage Bring-Your-Own-License (BYOL) models for Microsoft SQL Server, Oracle, and SAP workloads to save costs.
✅ 9. Implement FinOps (Cloud Financial Management)
FinOps (Financial Operations) integrates finance, engineering, and IT teams to manage cloud spending effectively.
Establish spending accountability and ensure that each team optimizes its cloud usage.
✅ 10. Automate Cost Optimization with AI and Machine Learning
AI-powered cost optimization tools automatically analyze and recommend cost-saving actions.
Examples:
CloudHealth by VMware (multi-cloud cost management)
Harness Cloud Cost Management (AI-driven insights for Kubernetes and cloud spending)
💡 AI-driven automation ensures cost efficiency without manual intervention.
3. Best Practices for Sustainable Cloud Cost Management
🔹 Set up real-time budget alerts to track unexpected spending. 🔹 Regularly review and adjust reserved instance plans to avoid waste. 🔹 Continuously monitor cloud resource usage and eliminate redundant workloads. 🔹 Adopt a multi-cloud or hybrid cloud strategy to optimize pricing across different providers. 🔹 Educate teams on cloud cost optimization to promote a cost-conscious culture.
Conclusion
Effective cloud cost optimization isn’t just about cutting expenses—it’s about achieving the right balance between cost savings and performance. By implementing AI-driven automation, rightsizing resources, leveraging cost-effective storage options, and adopting FinOps practices, businesses can reduce cloud expenses without sacrificing security, compliance, or performance.
Looking for expert cloud cost optimization solutions? Salzen Cloud helps businesses maximize their cloud investment while ensuring performance and scalability.
0 notes
Text
Top Tools for Effective System Monitoring and Maintenance
In today's technology-driven world, businesses and organizations rely heavily on IT systems to ensure smooth operations. With the increasing complexity of modern networks and infrastructures, maintaining system health, preventing downtime, and ensuring security have become paramount. This is where system monitoring and maintenance tools come into play. These tools help IT teams proactively manage system performance, identify issues, and address them before they become critical. In this blog, we’ll explore some of the top tools available for effective system monitoring and maintenance.
1. Nagios
Nagios is one of the most popular and versatile system monitoring tools. It provides comprehensive monitoring solutions for systems, applications, services, and network infrastructure. Nagios offers real-time monitoring with instant alerts and reports, enabling IT teams to address issues before they cause serious downtime.
Key Features:
Real-Time Monitoring: Nagios tracks system resources, services, and network protocols to ensure optimal system performance.
Customizable Alerts: It provides alerts via email, SMS, or other notifications based on thresholds.
Extensive Plugin Support: Nagios supports a wide range of plugins to monitor diverse services and applications.
Scalability: Whether it’s a small office or large enterprise, Nagios can scale to meet the needs of different infrastructures.
Best For: Large enterprises and organizations with complex IT infrastructures.
2. Zabbix
Zabbix is an open-source monitoring solution designed for performance monitoring of networks, servers, cloud services, and applications. Known for its flexibility and scalability, Zabbix allows users to gather detailed insights into system performance, making it easier to detect and resolve issues.
Key Features:
Comprehensive Monitoring: Zabbix monitors a wide range of systems including servers, databases, virtual environments, and cloud services.
Real-Time Alerts: Zabbix sends notifications to users in case of system failure or performance degradation.
Visualization: Custom dashboards and graphs provide clear insights into system performance.
Auto-Discovery: Automatically detects and adds new devices to the monitoring system.
Best For: Organizations that require detailed monitoring and flexible configuration options.
3. SolarWinds
SolarWinds is a well-established name in the IT monitoring space, known for providing easy-to-use tools for network and system management. SolarWinds offers a suite of solutions that can be customized to meet the needs of both small and large organizations.
Key Features:
Network Performance Monitoring: SolarWinds tracks network performance in real-time, including bandwidth usage, device health, and more.
System Monitoring: It offers robust monitoring for operating systems, applications, and server performance.
Centralized Dashboard: SolarWinds has an intuitive and user-friendly dashboard that consolidates all monitoring data in one place.
Customizable Alerts: Alerts are highly customizable to suit the specific needs of the system.
Best For: Organizations looking for an easy-to-use, all-in-one solution for network and system monitoring.
4. Prometheus
Prometheus is a powerful open-source monitoring tool designed for cloud-native environments. It’s ideal for organizations using microservices and containers, especially those relying on Kubernetes. Prometheus focuses on time-series data, providing high-resolution metrics for system monitoring.
Key Features:
Time-Series Data: Prometheus stores metrics in a time-series database, enabling efficient analysis of trends over time.
Integration with Kubernetes: Prometheus is seamlessly integrated with Kubernetes, making it a go-to option for cloud-native environments.
Powerful Query Language: PromQL (Prometheus Query Language) is a flexible query language that enables users to extract and analyze data efficiently.
Alerting: Prometheus offers built-in alerting capabilities to notify users when specific thresholds are breached.
Best For: Companies using microservices, containers, and Kubernetes who need advanced monitoring capabilities.
5. Datadog
Datadog is a cloud-based monitoring tool that offers full-stack observability, which is crucial for businesses operating in multi-cloud or hybrid cloud environments. It provides deep insights into cloud infrastructure, servers, containers, and applications, all from a single platform.
Key Features:
Cloud-Native Monitoring: Datadog is ideal for monitoring dynamic, cloud-based environments and modern infrastructure.
End-to-End Visibility: Monitors everything from network traffic to application performance and cloud services.
Integrated Dashboards: Provides real-time and customizable dashboards that help users visualize system performance.
Anomaly Detection: Datadog’s machine learning-driven anomaly detection helps identify unusual behavior across your infrastructure.
Best For: Enterprises operating in multi-cloud or hybrid environments looking for a comprehensive cloud-based solution.
6. New Relic
New Relic is a popular observability platform that helps businesses monitor their entire stack, from infrastructure to applications. It focuses on performance monitoring for applications and allows businesses to identify bottlenecks and optimize user experience.
Key Features:
Application Performance Monitoring (APM): New Relic offers deep insights into application performance, helping to identify slow transactions and errors.
Distributed Tracing: Tracks requests across microservices, providing visibility into each step of the transaction lifecycle.
Custom Dashboards: Users can create customizable dashboards for specific metrics or use cases.
Integration: New Relic integrates with numerous third-party services and platforms.
Best For: Teams focused on monitoring application performance and user experience.
7. Puppet
Puppet is an automation tool that also supports system monitoring and maintenance. It helps ensure that your IT infrastructure is always configured and maintained according to desired states, automatically applying updates and fixes to prevent issues before they arise.
Key Features:
Configuration Management: Puppet helps maintain the desired state of your systems and ensures configurations are applied consistently across the infrastructure.
Automated Updates and Patches: Puppet automates updates and security patches, reducing manual effort and minimizing downtime.
Reporting and Auditing: Puppet generates detailed reports to help you track changes and ensure compliance.
Best For: Organizations looking for automation combined with monitoring to streamline system maintenance.
8. Checkmk
Checkmk is another open-source monitoring solution that covers both IT infrastructure and application monitoring. It’s known for its easy setup, scalability, and high flexibility, making it a great choice for a wide range of environments.
Key Features:
Infrastructure Monitoring: Provides comprehensive monitoring of network devices, servers, and cloud infrastructure.
Agent and Agentless Monitoring: Supports both agent-based and agentless monitoring methods, making it adaptable to different use cases.
Powerful Dashboards: Checkmk’s dashboards are highly customizable to show exactly what you need to see.
Scalability: Checkmk can scale from small environments to large, complex infrastructures.
Best For: Medium to large businesses requiring an open-source monitoring solution with high scalability.
Conclusion
System monitoring and maintenance are critical for ensuring that your IT infrastructure runs smoothly, securely, and efficiently. Choosing the right tools for the job depends on your specific needs, infrastructure complexity, and business size. Whether you’re managing a small network or a sprawling enterprise, there’s a solution out there to fit your needs.
By leveraging these top tools, you can not only prevent downtime but also optimize system performance, enhance security, and ensure the overall health of your IT infrastructure. With proactive monitoring and regular maintenance, your systems will be more resilient and capable of handling the demands of modern business operations.
for more details please visit
www.qcsdclabs.com
www.hawkstack.com
0 notes
Text
Image Recognition Market Size, Trends, and Business Outlook 2024-2030
The global image recognition market size was valued at USD 53.3 billion in 2023 and is projected to grow at a compound annual growth rate (CAGR) of 12.8% from 2024 to 2030.
This growth is attributed to the increasing volumes of image data, advancements in artificial intelligence (AI) and machine learning (ML), and the growing demand for automation across various sectors are pivotal. In addition, the integration of image recognition in applications such as healthcare, retail, and security enhances operational efficiency and customer engagement. Furthermore, the rise of edge computing and mobile solutions further supports market expansion.
Gather more insights about the market drivers, restrains and growth of the Image Recognition Market
Image recognition technology, powered by machine learning, has been embedded in several fields, such as self-driving vehicles, automated image organization of visual websites, and face identification on social networking websites. One of the most popular applications of image identification is social media monitoring, as visual listening and visual analytics are essential factors of digital marketing. Image recognition is highly used in applications related to safety and security, such as facial recognition used by law enforcement agencies. Furthermore, airports are increasingly using face remembrance technology at security checkpoints.
The growing popularity of high-bandwidth data services and advanced machine learning has led to a higher demand for image recognition technology among people. Establishments in different sectors such as media & entertainment, retail, IT & telecom, and Banking, Financial Services, and Insurance (BFSI) have led to the growing utilization of advanced technologies within their companies, consequently driving the acceptance of image recognition. The system for image recognition assists in recognizing objects, buildings, locations, logos, individuals, and other images. Moreover, advances in image recognition tech enable connecting offline materials such as brochures and magazines with promotional videos, AR experiences, and product details using images from a smartphone.
In addition, an automated system for recognizing images is essential in computer vision, as it can pinpoint an image or attribute within digital photos and videos. It allows users to collect and analyze data in real-time. Information is gathered in complex dimensions and results in numerical or symbolic data. Computer vision, an image recognition component, allows for object recognition, event detection, image reconstruction, learning, and video tracking tasks. Image recognition technology has seen various opportunities arise in areas such as big data analysis and successful branding of products and services, thanks to the expanding use of image databases.
Furthermore, since the database serves as the training material for image recognition solutions, open-source frameworks such as software libraries and software tools form the building blocks of the solution. These frameworks help prepare or train machines to learn from the images available in the database by providing different types of computer vision functions, such as medical screening, obstacle detection in vehicles, and emotion and facial recognition, among others. Some of the leading libraries for image recognition include UC Berkeley's Caffe, Google Tensor Flow, and Torch.
Image Recognition Market Segmentation
Grand View Research has segmented the image recognition market report based on, technique, component, deployment mode, vertical, application, and region.
Technique Outlook (Revenue, USD Million, 2018 - 2030)
• QR/ Barcode Recognition
• Object Recognition
• Facial Recognition
• Pattern Recognition
• Optical Character Recognition
Component Outlook (Revenue, USD Million, 2018 - 2030)
• Hardware
• Software
• Service
• Managed
• Professional
• Training, Support, and Maintenance
Deployment Mode Outlook (Revenue, USD Million, 2018 - 2030)
• Cloud
• On-Premises
Vertical Outlook (Revenue, USD Million, 2018 - 2030)
• Retail & E-commerce
• Media & Entertainment
• BFSI
• Automobile & Transportation
• Telecom & IT
• Government
• Healthcare
• Others
Application Outlook (Revenue, USD Million, 2018 - 2030)
• Augmented Reality
• Scanning & Imaging
• Security & Surveillance
• Marketing & Advertising
• Image Search
Regional Outlook (Revenue, USD Million, 2018 - 2030)
• North America
o U.S.
o Canada
o Mexico
• Europe
o UK
o Germany
o France
• Asia Pacific
o China
o India
o Japan
o Australia
o South Korea
• Latin America
o Brazil
• Middle East and Africa (MEA)
o Saudi Arabia
o South Africa
o UAE
Browse through Grand View Research's Next Generation Technologies Industry Research Reports.
• The global video management software market was valued at USD 9.69 billion in 2023 and is projected to grow at a compound annual growth rate (CAGR) of 19.5% from 2024 to 2030.
• The global 3D Scanning market was valued at USD 3.95 billion in 2023 and is projected to grow at a compound annual growth rate (CAGR) of 9.8% from 2024 to 2030.
Key Companies And Market Share Insights
Some key companies in the image recognition market include Attrasoft, Inc., Blinkfire Analytics, Inc., Kairos AR, Inc., Catchroom, Chooch., Cloudsight, Inc., Google, GumGum, Inc., Hitachi, Ltd.; and others that focus on development with continuous innovations and enhancements.
• Blinkfire Analytics, Inc. specializes in AI-powered visual content analysis for sports, media, and entertainment industries. Blinkfire's proprietary platform uses computer vision and machine learning algorithms to automatically detect, track, and analyze brand exposures, logos, and sponsorships within images and videos, providing valuable insights for brands, teams, and leagues. The company's offerings include sponsorship valuation, brand monitoring, and audience engagement metrics, enabling clients to measure the effectiveness of their marketing efforts and optimize their sponsorship strategies.
• Kairos AR, Inc. provides facial recognition and image analysis solutions, offering products and services that leverage artificial intelligence and machine learning to deliver accurate and efficient image recognition capabilities. Kairos' flagship platform, Kairos Face Recognition, provides real-time facial recognition, identification, and verification, with security, access control, and customer experience applications. The company's other offerings include Kairos Demographics, which analyzes age, gender, and emotions, and Kairos Emotions, which detects and interprets emotional responses. Kairos' solutions are used across various industries, including healthcare, finance, and retail, and are designed to integrate with existing systems and infrastructure, enabling seamless deployment and scalability.
Key Image Recognition Companies:
The following are the leading companies in the image recognition market. These companies collectively hold the largest market share and dictate industry trends.
• Attrasoft, Inc.
• Blinkfire Analytics, Inc.
• Catchroom
• Chooch.
• Cloudsight, Inc.
• Google
• GumGum, Inc.
• Hitachi, Ltd.
• Honeywell International Inc.
• Kairos AR, Inc.
• LTU Tech
• NEC Corporation
• Qualcomm Technologies, Inc.
• DEEPSIGNALS
• Calrifai, Inc.
• Wikitude, a Qualcomm company
Recent Developments
• In April 2023, Chooch launched ImageChat, a solution that enables enterprises to create detailed computer vision models using text prompts. Trained on over 11 billion parameters and 400 million images, ImageChat can identify more than 40 million visual details. This innovative tool offered users to generate captions and keywords for images and videos and interact with visual content to gain deeper insights. Combining AI Vision with large language models, ImageChat enhances data reliability and accuracy, making it ideal for object detection and detailed reasoning applications.
Order a free sample PDF of the Image Recognition Market Intelligence Study, published by Grand View Research.
#Image Recognition Market#Image Recognition Market size#Image Recognition Market share#Image Recognition Market analysis#Image Recognition Industry
0 notes
Text
10 Best Network Monitoring Tools (June 2024)
New Post has been published on https://thedigitalinsider.com/10-best-network-monitoring-tools-june-2024/
10 Best Network Monitoring Tools (June 2024)
Effective network monitoring is crucial for maintaining the performance and reliability of today’s complex IT environments. With the right tools, network administrators can proactively identify and resolve issues before they impact end-users. In this blog post, we’ll explore some of the best network monitoring solutions available, including both cloud-based platforms and open-source options.
Auvik is a cloud-based network monitoring and management platform designed to give IT teams full visibility and control over their networks. It automates many complex and time-consuming network management tasks, allowing administrators to work more efficiently. By providing real-time network mapping, detailed device information, and intelligent alerts, Auvik enables IT professionals to proactively monitor network health and quickly troubleshoot issues.
One of Auvik’s standout capabilities is its ability to automatically discover and inventory all devices on the network within minutes of deployment. It creates dynamic, interactive topology maps that visualize physical and logical connections between devices. Auvik also provides in-depth traffic analysis to easily identify who is on the network, what they are doing, and where their traffic is going. With features like automated config backups and an intuitive dashboard to access key network data from anywhere, Auvik is a comprehensive tool to streamline network management.
Key features of Auvik include:
Automated network discovery and inventory that provides a complete view of all network devices
Dynamic network mapping to visualize physical and logical network topology
Intelligent network traffic analysis to monitor bandwidth usage and identify traffic patterns
Automated configuration backups and easy restore to quickly recover from network issues
Extensive integrations with popular IT platforms and a powerful API to build custom workflows
Visit Auvik →
SolarWinds is a leading provider of powerful and affordable IT management software. Their flagship product for network monitoring is called Network Performance Monitor (NPM). NPM is designed to provide comprehensive network monitoring capabilities that allow IT professionals to quickly detect, diagnose, and resolve network performance issues and outages.
SolarWinds NPM can automatically discover network devices and start monitoring them within hours of deployment. It provides real-time visibility into the health and performance of routers, switches, firewalls, load balancers, wireless access points, and any other SNMP-enabled devices. NPM uses a web-based interface with customizable dashboards, views, and charts to present critical performance metrics at a glance. It also includes advanced alerting capabilities to notify administrators of issues before they impact end-users.
In addition to NPM, SolarWinds offers several other tools that extend its network monitoring capabilities. NetFlow Traffic Analyzer provides detailed visibility into bandwidth usage by application, protocol, and IP address group. Network Configuration Manager automates network configuration and change management. IP Address Manager streamlines IP address management with integrated DHCP and DNS servers. Taken together, these tools provide a comprehensive and scalable network monitoring solution.
Key features of SolarWinds network monitoring tools include:
Automated network discovery and mapping to quickly inventory devices and visualize topology
Customizable dashboards, views, and reports to present key performance metrics and health data
Over 1200 pre-built templates for monitoring Cisco, HP, Dell, Juniper, and other network device vendors
Advanced alerting with dynamic baseline thresholds and dependencies to reduce false alarms
PerfStack performance analysis dashboard for easy cross-stack data correlation and root cause identification
Visit SolarWinds →
LogicMonitor
LogicMonitor is a SaaS-based infrastructure monitoring platform that provides unified visibility into complex and hybrid IT environments. It offers comprehensive monitoring capabilities across networks, servers, cloud resources, applications, and more. By collecting metrics, logs, and traces through an agentless collector architecture, LogicMonitor delivers real-time insights into the health and performance of the entire technology stack.
One of LogicMonitor’s key strengths is its ability to automatically discover and monitor devices within minutes of deployment. It creates dynamic topology maps to visualize relationships between critical resources. LogicMonitor also leverages AI and machine learning for advanced capabilities like anomaly detection, forecasting, and intelligent alerting. With customizable dashboards, pre-configured alert thresholds, and extensive integrations, LogicMonitor optimizes digital experiences while consolidating tools and reducing operational overhead.
Key features of LogicMonitor include:
Automated discovery and monitoring of devices, cloud resources, and applications
Dynamic topology mapping to visualize relationships and dependencies
AI-driven insights for anomaly detection, forecasting, and smart alerting
Customizable dashboards and reporting for tailored views of key metrics
Extensive integrations with 2000+ technologies and open API for custom data sources
Visit LogicMonitor →
Nagios
Nagios is a powerful open-source IT infrastructure monitoring tool that enables organizations to identify and resolve problems before they impact critical business processes. Originally developed under the name NetSaint in 1999, Nagios has evolved to become one of the most widely used monitoring platforms, with thousands of projects and plugins extending its core functionality. Nagios runs natively on Linux and other Unix-like systems but can also be deployed on Windows using virtualization.
At its core, Nagios is designed to monitor hosts, services, and network devices. It uses a server-client architecture where plugins run on remote hosts to collect data and send it back to the Nagios server for processing. When issues are detected, Nagios can send alerts via email, SMS, or other notification channels to IT staff, allowing them to quickly respond to outages or performance problems. Nagios also provides a web-based interface for viewing monitoring status, generating reports, and managing configuration.
Beyond its core monitoring engine, the Nagios ecosystem includes several other tools to extend its capabilities. Nagios XI provides an enterprise-grade web interface, advanced visualizations, and features like capacity planning and audit logging. Nagios Fusion allows centralized viewing of multiple Nagios instances. Nagios Log Server enables log monitoring and analysis, while Nagios Network Analyzer provides NetFlow-based traffic analysis.
Key features of Nagios include:
Comprehensive monitoring of IT infrastructure components including servers, network devices, applications, and services
Flexible, plugin-based architecture that allows monitoring of virtually any resource
Centralized view of monitoring status via web interface with user-specific views and dashboards
Proactive alerting via multiple channels to ensure rapid response to issues
Extensible ecosystem with add-ons for log monitoring, network analysis, configuration management, and more
Visit Nagios →
Zabbix
Zabbix is a mature and feature-rich open-source network monitoring solution designed for monitoring the availability and performance of IT infrastructure components including servers, network devices, virtual machines and cloud services. It provides a centralized monitoring system that enables real-time monitoring of thousands of metrics collected from servers, network devices and applications.
One of Zabbix’s key strengths is its flexibility and extensibility. It can monitor a wide range of devices and systems using multiple methods including Zabbix agent, SNMP, IPMI, JMX and custom checks. Zabbix also provides powerful data visualization capabilities including custom graphs, network maps, dashboards and reports. With features like anomaly detection, predictive analytics and auto-discovery of devices, Zabbix helps IT teams proactively monitor their infrastructure and quickly troubleshoot issues.
Key features of Zabbix include:
Distributed monitoring with support for remote Zabbix proxies for monitoring across multiple locations
Agentless monitoring using multiple protocols including SNMP, IPMI, JMX, SSH and Telnet
Powerful data visualization with custom graphs, network maps, dashboards and slideshows
Flexible alerting with customizable escalation scenarios and multiple notification channels
Auto-discovery for automatic registration of new devices and application of appropriate monitoring templates
Visit Zabbix →
Datadog is a comprehensive cloud-based monitoring and analytics platform designed to provide real-time visibility into modern IT environments. It enables organizations to monitor their entire infrastructure, including servers, databases, applications, network devices, and cloud services. By collecting, searching, and analyzing metrics, traces, and logs across fully distributed architectures, Datadog empowers IT teams to proactively detect and resolve performance issues before they impact end-users.
Datadog supports over 600 technologies and services out-of-the-box. This allows seamless data collection from various sources, providing a holistic view of the IT ecosystem. Datadog also offers customizable dashboards, intelligent alerts, and collaboration features, enabling teams to efficiently monitor, troubleshoot, and optimize their systems. With its scalable architecture and flexible deployment options, Datadog caters to businesses of all sizes, from startups to large enterprises.
Key features of Datadog include:
Real-time monitoring of servers, containers, databases, and cloud services, with auto-discovery and detailed performance metrics
End-to-end tracing of requests across distributed systems, identifying bottlenecks and optimizing application performance
Centralized log collection, indexing, and analysis, with powerful search and filtering capabilities
Visibility into network traffic, analyzing communication between services, containers, and cloud environments
Customizable dashboards for visualizing key metrics in real-time
Visit Datadog →
AdRem NetCrunch is a comprehensive network monitoring and management solution designed to provide real-time visibility into IT infrastructure. It offers a wide range of features to streamline network monitoring, including auto-discovery of devices, performance monitoring, customizable dashboards, and an intuitive alerting system. NetCrunch runs on Windows and provides an agentless approach to monitoring, making it easy to deploy and scale.
NetCrunch automatically discovers and maps network devices, creating a dynamic, interactive network atlas. This allows IT teams to visualize their network topology, identify dependencies, and quickly locate the root cause of issues. NetCrunch supports monitoring of various devices and systems, including servers, network devices, applications, virtual environments, and cloud services.
Key features of AdRem NetCrunch:
Agentless monitoring using protocols like SNMP, WMI, and SSH
Automatic network discovery and interactive topology mapping
Customizable dashboards and alerts for tailored network insights
Supports monitoring of servers, network devices, VMs, and cloud services
Extensive reporting and integration with IT management platforms
Visit NetCrunch →
Observium is an open-source network monitoring and management platform that offers auto-discovery capabilities to automatically detect and monitor devices on the network, including servers, switches, routers, and more. Observium supports a wide range of device types and operating systems, such as Cisco, Windows, Linux, HP, Juniper, Dell, and others.
Observium boasts a user-friendly web interface, which presents network data through customizable dashboards, graphs, and reports. It collects data using SNMP and stores it using RRD (Round-Robin Database), enabling efficient storage and retrieval of historical performance metrics. Observium also provides alerting features to notify administrators of potential issues or performance degradations.
Key features of Observium:
Automatic discovery of network devices for easy setup and monitoring
Support for a wide range of device types and operating systems
Customizable dashboards and graphs for data visualization
Alerting system to notify administrators of potential issues
Scalable architecture to monitor large and complex network environments
Visit Observium →
Domotz is a comprehensive cloud-based network monitoring and management software designed for MSPs, IT professionals, and enterprises. It provides real-time visibility and control over IT infrastructure, enabling users to work more efficiently, increase productivity, and resolve issues faster. Domotz offers a user-friendly interface and automated features such as network discovery, topology mapping, and device inventory.
Domotz can monitor a wide range of devices, including servers, workstations, printers, routers, switches, firewalls, and IoT devices, regardless of the manufacturer. It supports various monitoring protocols like SNMP, WMI, and SSH. Domotz also provides secure remote access to devices for troubleshooting, as well as network configuration management with backup and restore capabilities.
Key features of Domotz:
Automated network discovery, inventory, and topology mapping
Supports monitoring of diverse devices across multiple sites and networks
Secure remote access for troubleshooting and issue resolution
Network configuration management with backup, restore and change alerts
Intuitive web-based interface with customizable dashboards and reporting
Visit Domotz →
AKIPS
AKIPS is a powerful and scalable network monitoring software designed to provide comprehensive visibility into large enterprise network infrastructures. It offers a fully-featured, fast, and cost-effective solution for monitoring network performance, enabling network engineers to proactively identify and resolve issues before they impact business operations. AKIPS can monitor over one million interfaces and 500,000 flows per second from a single server, making it one of the most scalable network monitoring tools on the market.
One of the standout features of AKIPS is its ability to provide real-time insights and historical data down to one-minute granularity for up to three years. This allows network administrators to quickly identify the root cause of issues and make informed decisions. AKIPS also offers automated device discovery, adaptive polling, syslog and SNMP trap management, NetFlow analysis, and configuration management capabilities, providing a comprehensive toolkit for network monitoring and management.
Key one-line features of AKIPS:
Scalable architecture monitoring over 1 million interfaces from a single server
Real-time insights and 3 years of historical data at 1-minute granularity
Automated network discovery and adaptive polling optimizing SNMP traffic
Advanced syslog, SNMP trap management and alerting for proactive issue detection
NetFlow analysis with up to 500k flows/sec and configuration management tools
Visit AKIPS →
The Bottom Line
Choosing the right network monitoring tool is essential for keeping your IT infrastructure running smoothly. Whether you opt for a comprehensive cloud-based platform, a flexible open-source solution, or a combination of tools, having real-time visibility into your network’s performance is crucial. Consider your organization’s specific needs, budget, and existing IT ecosystem when selecting a monitoring solution. By implementing the right tool or combination of tools, you can proactively identify and resolve issues, optimize network performance, and ensure a seamless experience for your end-users.
#000#2024#agent#ai#alerts#Analysis#Analytics#API#applications#approach#architecture#audit#auvik#backup#backups#Best Of#Blog#box#Business#change#change management#charts#Cisco#Cloud#cloud services#Collaboration#communication#comprehensive#Containers#dashboard
0 notes
Text
Innovations in Surveillance Technology: What’s New in Surveillance Kits
In the ever-evolving landscape of security and surveillance, technological advancements continue to redefine the capabilities and possibilities of monitoring and safeguarding environments. Surveillance kits, comprising a variety of tools and devices, play a pivotal role in this domain, offering enhanced functionalities and features to meet the increasing demands of modern security challenges. Let’s delve into the latest innovations in surveillance technology and uncover what’s new in surveillance kits.
Evolution of Surveillance Kits:
Surveillance kits have come a long way from their humble beginnings, evolving into sophisticated systems capable of providing comprehensive monitoring solutions. Traditionally, surveillance kits consisted of basic cameras, recording devices, and monitors. However, recent innovations have propelled these kits into the realm of smart technology, integrating advanced features such as artificial intelligence (AI), high-definition imaging, remote access, and seamless integration with other security systems.
Key Innovations:
AI-Powered Analytics:
One of the most significant advancements in surveillance technology is the integration of AI-powered analytics into surveillance kits. These systems can analyze vast amounts of data in real-time, enabling intelligent features such as facial recognition, object detection, and behavior analysis. AI algorithms can differentiate between normal and suspicious activities, alerting security personnel to potential threats proactively.
High-Resolution Imaging:
The shift towards high-resolution imaging has revolutionized surveillance capabilities, allowing for clearer and more detailed footage. Surveillance kits now feature ultra-high-definition cameras with resolutions up to 4K and beyond, providing unparalleled clarity even in low-light conditions. This level of image quality enhances identification accuracy and facilitates forensic analysis, making it easier to identify individuals and objects of interest.
Remote Monitoring and Control:
Modern surveillance kits offer seamless integration with mobile devices and cloud-based platforms, enabling remote monitoring and control from anywhere in the world. Users can access live video feeds, review recorded footage, and adjust camera settings remotely via smartphone apps or web interfaces. This flexibility ensures constant vigilance and enables rapid response to security incidents, regardless of location.
Edge Computing:
Edge computing has emerged as a game-changer in surveillance technology, allowing data processing to be performed at the edge of the network, closer to the data source. Surveillance kits equipped with edge computing capabilities can analyze video streams in real-time, reducing latency and bandwidth requirements. This enables faster response times and more efficient use of network resources, making surveillance systems more responsive and reliable.
Integration with IoT Devices:
The Internet of Things (IoT) has opened up new possibilities for surveillance kits by enabling seamless integration with a wide range of IoT devices. Surveillance systems can now communicate with sensors, alarms, access control systems, and other IoT devices to create a cohesive security ecosystem. This interconnectedness enhances situational awareness and enables automated responses to security events, improving overall efficiency and effectiveness.
Future Trends:
Looking ahead, the future of surveillance technology promises even more exciting innovations. Advancements in areas such as machine learning, 5G connectivity, drone surveillance, and augmented reality are poised to further revolutionize the capabilities of surveillance kits. As these technologies continue to mature and converge, we can expect surveillance systems to become even more intelligent, adaptive, and interconnected, empowering organizations to enhance security and mitigate risks effectively.
Conclusion:
Innovations in surveillance technology have transformed surveillance kits into powerful tools for safeguarding people, assets, and environments. From AI-powered analytics to high-resolution imaging and remote monitoring capabilities, these advancements are reshaping the landscape of security and surveillance. As we embrace the opportunities presented by emerging technologies, the future of surveillance holds immense promise for creating safer and more secure societies. Source: https://headsettactical.wordpress.com/2024/05/11/innovations-in-surveillance-technology-whats-new-in-surveillance-kits/
0 notes
Text
do i really need a vpn with kodi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i really need a vpn with kodi
Kodi VPN necessity
Title: The Essentiality of a Kodi VPN: Protecting Your Streaming Experience
In the realm of digital entertainment, Kodi has emerged as a powerhouse platform, offering a vast array of streaming options for users worldwide. However, as the popularity of Kodi continues to soar, so do concerns regarding online privacy and security. This is where a Kodi VPN (Virtual Private Network) becomes not just a luxury but a necessity.
First and foremost, a Kodi VPN serves as a shield for your online activities. By encrypting your internet connection and routing it through a secure server, a VPN ensures that your browsing history, streaming habits, and personal information remain confidential. This is crucial in today's age of rampant cyber threats and data breaches, where hackers and malicious entities are constantly on the prowl for vulnerable targets.
Moreover, a VPN can unlock a world of content on Kodi that may otherwise be restricted due to geographic limitations or censorship. With servers located across the globe, a VPN allows you to bypass regional restrictions and access a wider range of streaming services and content libraries. Whether you're craving the latest Hollywood blockbusters, international TV shows, or niche documentaries, a VPN opens the door to limitless entertainment possibilities.
Additionally, a Kodi VPN can enhance your streaming experience by mitigating buffering and throttling issues. Internet service providers (ISPs) often throttle bandwidth for streaming services, leading to frustrating lags and interruptions. By masking your online activities, a VPN prevents ISPs from monitoring and throttling your connection, ensuring smooth and uninterrupted streaming sessions.
In conclusion, investing in a Kodi VPN is not just a matter of convenience but a crucial step towards safeguarding your online privacy, accessing unrestricted content, and optimizing your streaming experience. Whether you're a casual viewer or a dedicated cinephile, a VPN is an indispensable tool for navigating the ever-evolving landscape of digital entertainment.
VPN benefits for Kodi
A VPN offers numerous benefits for Kodi users, enhancing their streaming experience while maintaining online privacy and security. Kodi is a popular media player that allows users to access a wide variety of content, including movies, TV shows, and live sports events. However, using Kodi without a VPN can expose users to several risks, making a VPN an essential tool for a smooth and secure streaming experience.
One of the primary benefits of using a VPN with Kodi is the ability to bypass geo-restrictions. Many streaming services and add-ons on Kodi are restricted to specific regions, limiting the content available to users. By connecting to a VPN server in a different country, Kodi users can access geo-blocked content and enjoy a more extensive library of shows and movies.
In addition to overcoming geo-restrictions, a VPN can also protect users' online privacy and security. By encrypting internet traffic and masking IP addresses, a VPN ensures that Kodi users remain anonymous while streaming content. This prevents ISPs, hackers, and governments from monitoring users' online activities and data, reducing the risk of cyber threats and privacy breaches.
Furthermore, a VPN can improve streaming performance on Kodi by reducing buffering and lagging. By connecting to a VPN server closer to the content source, users can enjoy faster streaming speeds and smoother playback, enhancing their viewing experience.
Overall, using a VPN with Kodi offers numerous benefits, including access to geo-blocked content, enhanced online privacy and security, and improved streaming performance. By investing in a reliable VPN service, Kodi users can maximize their entertainment options while safeguarding their digital footprint.
Security advantages with Kodi VPN
Using a VPN (Virtual Private Network) with Kodi can provide several security advantages for users. Kodi is a popular media player and streaming platform, but like any online activity, it comes with its own security risks. By utilizing a VPN while using Kodi, users can enhance their online security and protect their privacy.
One of the main benefits of using a VPN with Kodi is encryption. A VPN encrypts the user's internet connection, making it more difficult for hackers, ISPs, or any other third parties to intercept the data being transmitted. This is crucial when streaming content on Kodi, as it helps protect sensitive information such as login details, personal data, and browsing history.
Moreover, a VPN can help users bypass geographic restrictions and censorship. By connecting to a VPN server in a different location, users can access content that may be blocked in their region. This is particularly useful for Kodi users who want to stream content from different countries without any limitations.
Additionally, using a VPN with Kodi can help prevent ISP throttling. Internet service providers often throttle the connection speeds of users who engage in high-bandwidth activities like streaming. By encrypting the connection and hiding the user's online activities from the ISP, a VPN can help maintain consistent streaming speeds and improve overall performance.
In conclusion, employing a VPN with Kodi offers a layer of security and privacy protection that every user can benefit from. By encrypting data, bypassing restrictions, and preventing ISP throttling, users can enjoy a safer and more enjoyable streaming experience while using Kodi.
Reasons to use VPN with Kodi
Using a Virtual Private Network (VPN) with Kodi can significantly enhance your streaming experience while safeguarding your privacy and security. Here are several compelling reasons to utilize a VPN with Kodi:
Access Geo-Restricted Content: Many streaming services impose geo-restrictions, limiting access to certain content based on your location. By connecting to a VPN server in a different country, you can bypass these restrictions and unlock a wider range of shows, movies, and live sports events on Kodi.
Protect Your Privacy: Without a VPN, your internet service provider (ISP) can track your online activities, including your Kodi usage. By encrypting your internet connection, a VPN ensures that your browsing history remains private, shielding you from potential surveillance or data collection.
Enhanced Security: Public Wi-Fi networks pose security risks, making your personal information vulnerable to hackers and cybercriminals. When using Kodi on such networks, a VPN encrypts your data, making it virtually impossible for malicious actors to intercept or access your sensitive information.
Prevent Bandwidth Throttling: Some ISPs engage in bandwidth throttling, deliberately slowing down your internet connection when they detect high data usage, such as streaming videos on Kodi. By encrypting your traffic with a VPN, you can prevent your ISP from monitoring your activities and avoid throttling, ensuring smooth and uninterrupted streaming.
Avoid Copyright Enforcement: While Kodi itself is legal, some third-party add-ons may provide access to copyrighted content without proper authorization. Using a VPN adds an extra layer of anonymity, reducing the risk of copyright infringement notices or legal consequences associated with unauthorized streaming.
In conclusion, integrating a VPN with Kodi offers numerous benefits, including access to geo-restricted content, enhanced privacy and security, protection against bandwidth throttling, and mitigation of copyright enforcement risks. By investing in a reliable VPN service, you can enjoy a safer and more versatile streaming experience with Kodi.
Kodi VPN importance
Using a VPN with Kodi is a crucial step to enhance privacy and security while streaming your favorite content online. Kodi, a popular open-source media player software, offers a vast library of entertainment options, including movies, TV shows, music, and more. However, the unrestricted nature of Kodi's content sources may expose users to potential security risks.
By employing a VPN (Virtual Private Network) while using Kodi, users can encrypt their internet connection and mask their IP address. This encryption ensures that all data transmitted between the user's device and the VPN server is secure and protected from prying eyes. It also helps in bypassing geo-restrictions and accessing content that may be blocked in certain regions.
Furthermore, using a Kodi VPN adds an extra layer of anonymity, preventing third parties, such as government agencies, internet service providers, or hackers, from monitoring your online activities. This is especially important for users who want to maintain their privacy and safeguard their personal information from being exposed.
In addition to privacy and security benefits, a VPN can also improve streaming performance on Kodi by reducing buffering and lagging issues. By connecting to servers located closer to the content source, users can experience faster streaming speeds and smoother playback.
In conclusion, incorporating a VPN with Kodi is essential for ensuring a safe, secure, and unrestricted streaming experience. Whether you are accessing copyrighted content or simply prioritizing your online privacy, using a VPN can offer peace of mind and enhance your overall entertainment experience.
0 notes
Text
does vpn help with kodi streaming
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn help with kodi streaming
VPN for Kodi streaming
Title: Enhancing Your Kodi Streaming Experience with VPN
In the digital age, Kodi has emerged as a popular media player, allowing users to stream a wide range of content, from movies and TV shows to live sports and music. However, as with any online activity, privacy and security are paramount concerns. This is where a Virtual Private Network (VPN) can play a crucial role in enhancing your Kodi streaming experience.
First and foremost, a VPN encrypts your internet connection, ensuring that your online activities remain private and secure. This is particularly important when streaming content through Kodi, as it prevents your Internet Service Provider (ISP) from monitoring your activity and potentially throttling your connection speed.
Moreover, a VPN enables you to bypass geographic restrictions and access geo-blocked content on Kodi. By connecting to a server in a different location, you can unlock a world of content that may not be available in your region. Whether you're looking to stream a specific movie or catch up on a TV show that's only available in certain countries, a VPN opens up a plethora of entertainment options.
Additionally, using a VPN can help you avoid ISP-imposed bandwidth throttling, which can slow down your connection speed and hinder your streaming experience. By encrypting your traffic and routing it through a secure server, a VPN prevents your ISP from identifying and selectively slowing down your Kodi streaming activities.
Furthermore, a VPN adds an extra layer of security by masking your IP address and location. This not only protects your privacy but also helps prevent malicious actors from tracking your online activities or targeting you with unwanted advertisements.
In conclusion, integrating a VPN into your Kodi streaming setup can significantly enhance both the security and versatility of your viewing experience. By encrypting your connection, bypassing geo-blocks, and safeguarding your privacy, a VPN ensures that you can enjoy seamless and unrestricted access to your favorite content on Kodi.
Kodi streaming without VPN
Title: The Risks of Kodi Streaming Without VPN
In the world of digital entertainment, Kodi stands out as a popular media player and streaming platform, offering access to a vast array of content. However, many users may not be aware of the potential risks associated with streaming on Kodi without a Virtual Private Network (VPN). While Kodi itself is legal and serves as a versatile tool for accessing media, the sources from which users stream content can often be less reputable.
One of the primary concerns of streaming on Kodi without a VPN is privacy. Without encryption provided by a VPN, internet service providers (ISPs) and even government agencies can potentially monitor users' online activities. This means that streaming content on Kodi without protection could expose users to surveillance, jeopardizing their privacy and security.
Moreover, streaming copyrighted content without proper authorization is illegal in many jurisdictions. While Kodi itself does not host any content, it provides access to third-party add-ons and repositories that may offer copyrighted material without the appropriate licenses. Without the anonymity provided by a VPN, users who engage in illegal streaming activities on Kodi may face legal consequences, including fines or even criminal charges.
Additionally, without a VPN, users may also encounter geo-restrictions that limit access to certain content based on their geographical location. By masking their IP address with a VPN, users can bypass these restrictions and access content that may otherwise be unavailable in their region.
In conclusion, while Kodi offers a convenient platform for streaming media, users should be aware of the risks associated with streaming without a VPN. By using a VPN, users can protect their privacy, bypass geo-restrictions, and mitigate the legal risks associated with streaming copyrighted content.
Benefits of using VPN for Kodi
Using a Virtual Private Network (VPN) with Kodi can offer a range of benefits, enhancing your streaming experience while also prioritizing your online privacy and security. Kodi, an open-source media player software, allows users to access a variety of content, including movies, TV shows, and music. Here are some key advantages of incorporating a VPN into your Kodi setup:
Access Geo-Restricted Content: One of the primary benefits of using a VPN with Kodi is the ability to bypass geographical restrictions. By connecting to a VPN server located in a different country, you can access content that may be blocked or restricted in your region. This opens up a world of entertainment options, giving you access to a wider range of movies, TV shows, and live streams.
Protect Privacy and Anonymity: VPNs encrypt your internet connection, making it virtually impossible for third parties to monitor your online activities. This is particularly important when streaming content through Kodi, as it ensures that your viewing habits remain private. By masking your IP address and encrypting your data, a VPN helps safeguard your anonymity and protects against potential surveillance or data tracking by ISPs, government agencies, or malicious actors.
Enhance Security: Public Wi-Fi networks, commonly used for streaming content on devices like Amazon Fire Stick or Android TV, can be vulnerable to hackers and cyberattacks. By using a VPN, you create a secure tunnel for your internet traffic, preventing unauthorized access to your personal information and sensitive data. This added layer of security is crucial for safeguarding your digital identity and protecting against potential threats, such as malware, phishing attempts, and identity theft.
Prevent Throttling: Some internet service providers (ISPs) engage in throttling, deliberately slowing down internet speeds for certain types of online activities, including streaming. By using a VPN, you can bypass ISP throttling and enjoy consistent, high-speed streaming with Kodi. This ensures a smooth and uninterrupted viewing experience, regardless of your ISP's policies or network congestion.
In conclusion, incorporating a VPN into your Kodi setup offers numerous benefits, including unrestricted access to geo-blocked content, enhanced privacy and anonymity, improved security, and prevention of ISP throttling. By prioritizing your online privacy and security, a VPN empowers you to enjoy a seamless and worry-free streaming experience with Kodi.
VPN encryption for Kodi
VPN Encryption for Kodi
If you are an avid Kodi user looking to enhance your online privacy and security, utilizing a VPN with strong encryption is crucial. Kodi is a popular open-source media player software that allows users to stream content from various sources. However, due to the nature of online streaming and copyright regulations, using a VPN with Kodi can provide an added layer of protection.
VPN encryption technology ensures that your internet traffic is secure and cannot be intercepted by third parties such as hackers, government agencies, or internet service providers. When you connect to a VPN server, your data is encrypted and transmitted through a secure tunnel, making it difficult for anyone to eavesdrop on your online activities.
By using a VPN with Kodi, you can hide your IP address and location, which helps protect your anonymity and privacy while streaming your favorite movies, TV shows, or live sports events. Additionally, VPN encryption can help bypass geo-restrictions imposed by streaming services or ISPs, allowing you to access content that may be not available in your region.
When choosing a VPN for Kodi, look for providers that offer strong encryption protocols such as OpenVPN or IKEv2, as well as a strict no-logs policy to ensure your online activities remain private. It is also essential to select a VPN with fast connection speeds and unlimited bandwidth to enjoy seamless streaming without buffering or lag.
In conclusion, using a VPN with robust encryption is a smart choice for Kodi users who prioritize their online security and privacy. With the right VPN solution, you can enjoy a worry-free streaming experience while keeping your personal information safe from prying eyes.
Kodi streaming privacy with VPN
When it comes to streaming on Kodi, maintaining privacy and security is of utmost importance. Using a Virtual Private Network (VPN) can significantly enhance your online streaming experience by providing an additional layer of protection.
Kodi is a popular open-source media player that allows users to stream a wide range of content, including movies, TV shows, and live sports. While Kodi itself is legal, some third-party add-ons may offer pirated content, making it crucial to safeguard your online privacy while using the platform.
By utilizing a VPN while streaming on Kodi, you can encrypt your internet connection, making it nearly impossible for third parties to monitor your online activities. This added level of security not only protects your personal data from hackers and cybercriminals but also prevents your Internet Service Provider (ISP) from tracking your online behavior.
Moreover, using a VPN can help you bypass geographical restrictions and access geo-blocked content on Kodi. By connecting to a server in a different location, you can enjoy a broader range of streaming options without worrying about regional limitations.
Overall, incorporating a VPN into your Kodi streaming setup can offer peace of mind and a more immersive viewing experience. With enhanced privacy, security, and access to geo-restricted content, a VPN is a valuable tool for any Kodi user looking to make the most of their streaming activities.
0 notes
Text
does opera vpn work with utorrent
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does opera vpn work with utorrent
Opera VPN compatibility with uTorrent
When it comes to using a VPN service with uTorrent, compatibility is key to ensure that your online activities remain secure and anonymous. Opera VPN is a popular choice for many users due to its ease of use and built-in privacy features. However, some users may wonder if Opera VPN is compatible with uTorrent, a widely used torrenting client.
Opera VPN can be a good option for securing your internet connection and keeping your online activities private. It encrypts your data and masks your IP address, making it difficult for third parties to track your online behavior. This can be beneficial when using uTorrent to download and share files, as it adds an extra layer of security to your torrenting activities.
In terms of compatibility, Opera VPN should work with uTorrent in most cases. You can simply enable the VPN within the Opera browser and then open uTorrent to start torrenting. However, it's important to note that some users have reported experiencing slower download speeds when using Opera VPN with uTorrent. This can be a common issue with free VPN services, as they may have limited server options and bandwidth.
If you encounter any issues with Opera VPN and uTorrent compatibility, you may need to troubleshoot by trying different server locations or considering a premium VPN service that offers faster speeds and more reliable connections. Overall, Opera VPN can be a decent choice for adding an extra layer of security to your uTorrent activities, but it's essential to keep in mind the potential limitations and performance drawbacks that may arise.
uTorrent functionality with Opera VPN
uTorrent is a popular BitTorrent client that allows users to download and share files over the internet. One of the concerns that users may have while using uTorrent is their online privacy and security. To address this issue, many users opt to use a Virtual Private Network (VPN) while torrenting.
Opera, a web browser known for its built-in features, offers a free VPN service to its users. By integrating Opera VPN with uTorrent, users can enhance their online privacy and security while downloading torrents. Opera VPN provides encryption and masks users' IP addresses, making it difficult for third parties to track their online activities.
When uTorrent functionality is combined with Opera VPN, users can benefit from increased anonymity and protection against potential cyber threats. By routing their internet traffic through Opera's secure servers, users can prevent their Internet Service Providers (ISPs) from monitoring their torrenting activities. This can be particularly useful in regions where torrenting is restricted or monitored closely.
Furthermore, Opera VPN allows users to bypass geographical restrictions and access torrent sites and content that may be blocked in their region. This can be advantageous for users looking to download legal torrents, such as open-source software or public domain media, that may not be readily available in their location.
In conclusion, integrating uTorrent functionality with Opera VPN can provide users with an added layer of privacy, security, and accessibility while torrenting. By taking advantage of these tools, users can enjoy a safer and more unrestricted torrenting experience.
Opera VPN effectiveness for uTorrent
Title: Assessing the Effectiveness of Opera VPN for uTorrent
Opera VPN, a popular choice for internet users seeking privacy and security online, often sparks curiosity about its compatibility and effectiveness with torrenting clients like uTorrent. While Opera VPN offers a layer of encryption and anonymity, its suitability for torrenting warrants scrutiny.
One of the primary concerns when using a VPN for torrenting is the ability to mask one's IP address effectively. Opera VPN, like other VPN services, assigns users a different IP address, concealing their true location and identity from prying eyes. However, the reliability of this IP masking feature is crucial for maintaining anonymity while torrenting.
Another aspect to consider is the impact of VPN usage on download and upload speeds, particularly when engaging in torrenting activities. Opera VPN may introduce some degree of latency due to rerouting internet traffic through its servers, potentially affecting download speeds on uTorrent. Users should conduct speed tests to assess any significant performance drop and determine if it aligns with their torrenting needs.
Moreover, the jurisdiction and logging policies of Opera VPN are essential considerations for users concerned about privacy. Opera VPN claims a no-log policy, indicating that it does not collect or store users' browsing data. However, verifying the accuracy of these claims and understanding the legal framework governing Opera VPN's operations can provide users with added assurance regarding their privacy while torrenting.
Ultimately, the effectiveness of Opera VPN for uTorrent depends on various factors, including IP masking reliability, impact on download speeds, and privacy assurances. Users should evaluate these factors alongside their torrenting requirements and preferences to determine if Opera VPN is a suitable choice for their torrenting endeavors. Conducting thorough research and considering user reviews can also provide valuable insights into the real-world performance of Opera VPN for uTorrent users.
uTorrent optimization with Opera VPN
Title: Optimizing uTorrent Performance with Opera VPN: A Comprehensive Guide
uTorrent, a popular BitTorrent client, offers efficient file sharing capabilities, but optimizing its performance can significantly enhance your downloading experience. Pairing uTorrent with Opera VPN can further augment its functionality, providing users with enhanced privacy and security while torrenting.
Opera VPN, a built-in feature of the Opera browser, encrypts your internet connection, safeguarding your online activities from prying eyes. By integrating Opera VPN with uTorrent, users can enjoy anonymity and prevent potential throttling or monitoring by ISPs.
To optimize uTorrent with Opera VPN, follow these steps:
Install Opera Browser: Begin by downloading and installing the Opera browser if you haven't already. Opera VPN is seamlessly integrated into the browser, making it convenient to enable and manage.
Enable Opera VPN: Launch Opera and navigate to the settings menu. Locate the "Privacy & Security" section and enable the VPN feature. Once activated, Opera VPN encrypts your internet connection and masks your IP address.
Configure uTorrent Settings: Open uTorrent and access the preferences menu. Navigate to the "Connection" tab and configure the proxy settings to route traffic through the Opera VPN. Input the proxy details provided by Opera VPN to establish a secure connection.
Test Connection: After configuring the settings, perform a connection test within uTorrent to ensure that traffic is routed through Opera VPN successfully. Verify your IP address to confirm anonymity and encryption.
Optimize Download Speed: Experiment with different server locations within Opera VPN to find the optimal connection speed for torrenting. Additionally, prioritize torrents with higher seed-to-peer ratios for faster downloads.
By following these steps, users can effectively optimize uTorrent performance with Opera VPN, enhancing both security and download speeds. Remember to prioritize safety and legality when torrenting, and always use VPNs responsibly.
Opera VPN and uTorrent performance
When it comes to using Opera VPN with uTorrent, there are a few things to consider regarding performance. Opera VPN offers users a way to enhance their privacy and security while browsing by encrypting their internet connection. This can help protect users' data from potential threats such as hackers or surveillance.
However, when using Opera VPN with uTorrent, users may experience a decrease in download and upload speeds. This is because VPNs can introduce additional latency and connection overhead due to the encryption process. As a result, users may find that their uTorrent downloads take longer or that their overall performance is impacted.
One way to potentially improve performance is to select a VPN server that is closer to your physical location. This can help reduce the distance that data needs to travel, which may improve speeds. Additionally, ensuring that your VPN and uTorrent settings are optimized for performance can also help mitigate any slowdowns.
It's important to keep in mind that using a VPN with uTorrent can also have legal implications, as some ISPs may restrict or monitor torrent traffic. Users should always review their local laws and ISP terms of service before engaging in any torrenting activities.
Overall, while Opera VPN can provide added security and privacy benefits, users may experience performance trade-offs when using it with uTorrent. By understanding these potential impacts and optimizing settings where possible, users can strike a balance between security and performance while torrenting.
0 notes
Text
do i need vpn kodi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need vpn kodi
VPN benefits for Kodi
Title: Unlocking the Full Potential of Kodi with VPN: Benefits and Usage Tips
Kodi, the open-source media player software, offers a vast world of entertainment possibilities, from streaming your favorite movies and TV shows to accessing live sports and music. However, maximizing your Kodi experience often requires overcoming geo-restrictions, protecting your online privacy, and ensuring smooth, uninterrupted streaming. This is where a Virtual Private Network (VPN) steps in as an indispensable tool for Kodi users.
One of the primary benefits of using a VPN with Kodi is bypassing geo-blocks. Many streaming services and content providers impose geographic restrictions, limiting access to certain regions. With a VPN, you can connect to servers in different countries, effectively masking your IP address and tricking websites into believing you're accessing content from an allowed location. This means you can enjoy unrestricted access to your favorite shows and movies regardless of your physical location.
Moreover, privacy and security are paramount when streaming content online. A VPN encrypts your internet traffic, shielding your browsing activity from prying eyes, including your Internet Service Provider (ISP) and potential hackers. This ensures that your online activities remain private and secure, preventing third parties from monitoring or intercepting your data.
Additionally, a VPN can help prevent buffering and throttling, common issues faced by Kodi users. By connecting to high-speed servers offered by VPN providers, you can enjoy smoother streaming experiences and eliminate lags caused by ISP throttling.
However, when using a VPN with Kodi, it's essential to choose a reputable provider that offers fast servers, strong encryption, and a strict no-logs policy to ensure your privacy and security are maintained. Furthermore, selecting a server location close to your physical location can help minimize latency and optimize streaming performance.
In conclusion, integrating a VPN with Kodi enhances your streaming experience by providing access to geo-restricted content, ensuring privacy and security, and improving streaming performance. By harnessing the power of VPN technology, Kodi users can unlock a world of entertainment without compromising their online safety and privacy.
VPN necessity on Kodi
Title: Why VPN is Essential for Kodi Users
In the realm of digital entertainment, Kodi stands as a versatile and powerful media player, offering access to a vast array of content from various sources. However, while Kodi itself is legal and widely used, the add-ons and third-party plugins it supports may present potential risks to users. This is where the necessity of a Virtual Private Network (VPN) becomes evident for Kodi users.
A VPN serves as a crucial tool for safeguarding privacy and security while using Kodi. Here's why:
Privacy Protection: When streaming content on Kodi, users may inadvertently expose their IP address to third-party sources, including hackers, ISPs, and copyright trolls. A VPN encrypts internet traffic, masking the user's IP address and making their online activities virtually untraceable.
Bypassing Geo-Restrictions: Many Kodi add-ons and streaming sources are geo-blocked, meaning they're only accessible from specific regions. By connecting to a VPN server in a desired location, users can bypass these restrictions and unlock a broader range of content.
Throttling Prevention: Internet service providers (ISPs) often throttle bandwidth for streaming services, leading to slower connections and buffering issues. A VPN encrypts data traffic, preventing ISPs from monitoring and throttling Kodi streams, resulting in smoother playback and improved performance.
Enhanced Security: Public Wi-Fi networks pose significant security risks, as they are susceptible to hacking and snooping. By using a VPN, Kodi users can ensure their data remains encrypted and protected from potential threats while connected to unsecured networks.
In conclusion, while Kodi offers a wealth of entertainment options, it's essential for users to prioritize their privacy and security. By utilizing a VPN, Kodi enthusiasts can enjoy unrestricted access to content while safeguarding their online activities from prying eyes and potential threats.
Kodi VPN advantages
Title: Unlocking Boundless Entertainment: The Advantages of Using a Kodi VPN
In the realm of digital entertainment, Kodi stands tall as a versatile media player that offers a plethora of streaming options. However, to fully leverage its potential and ensure seamless streaming without restrictions, pairing Kodi with a Virtual Private Network (VPN) proves to be a game-changer. Here are the key advantages of using a Kodi VPN:
Bypassing Geo-Restrictions: Content availability varies based on geographical regions, limiting your access to certain shows, movies, or live streams. With a VPN, you can bypass these restrictions by connecting to servers in different countries, granting you access to a broader range of content libraries.
Enhanced Privacy and Security: VPNs encrypt your internet traffic, shielding your online activities from prying eyes such as ISPs, hackers, or government surveillance. By encrypting your connection, a Kodi VPN ensures that your streaming habits remain private and secure, safeguarding your sensitive information from potential threats.
Preventing Throttling: Internet service providers (ISPs) often throttle the bandwidth of users engaged in high-bandwidth activities like streaming. By using a VPN, you can mask your online activities, preventing ISPs from throttling your connection speed and ensuring smooth, uninterrupted streaming on Kodi.
Protection Against Malicious Add-ons: Kodi's open-source nature makes it susceptible to malicious add-ons that may compromise your device's security. By routing your Kodi traffic through a VPN server, you add an extra layer of protection against such threats, reducing the risk of malware infections or data breaches.
Accessing P2P Streaming Safely: Many Kodi add-ons rely on peer-to-peer (P2P) streaming, which can expose your IP address to potential risks. A VPN masks your real IP address, allowing you to engage in P2P streaming anonymously and safely, without worrying about your online identity being exposed.
In conclusion, integrating a VPN with Kodi amplifies your streaming experience by unlocking geo-restricted content, ensuring privacy and security, thwarting throttling efforts, and safeguarding against potential threats. With these advantages in mind, embracing a Kodi VPN opens the door to a world of boundless entertainment possibilities.
Importance of VPN for Kodi
Using a VPN for Kodi is crucial for ensuring a secure and private streaming experience. Kodi is a popular open-source media player that allows users to stream a wide range of content, including movies, TV shows, live TV, and sports. However, the use of Kodi can also expose you to various security risks, such as hackers, government surveillance, and ISP monitoring.
By using a VPN (Virtual Private Network) for Kodi, you can encrypt your internet connection and protect your online activities from prying eyes. A VPN creates a secure tunnel between your device and the internet, making it difficult for anyone to intercept your data or track your online behavior. This is especially important when streaming content on Kodi, as it helps to prevent hackers from accessing your personal information or monitoring your viewing habits.
Furthermore, a VPN for Kodi enables you to bypass geo-blocks and access content that may be restricted in your region. Many streaming services and add-ons on Kodi are subject to geographic restrictions, meaning you may not be able to watch certain content based on your location. With a VPN, you can connect to servers in different countries and mask your IP address, allowing you to access geo-blocked content and enjoy a more diverse streaming experience on Kodi.
In conclusion, using a VPN for Kodi is essential for protecting your privacy, enhancing your online security, and accessing geo-restricted content. With the increasing threats to online privacy and security, investing in a reliable VPN service can help you enjoy a safer and more unrestricted streaming experience on Kodi.
Reasons to use VPN on Kodi
Using a Virtual Private Network (VPN) while streaming content on Kodi offers several important benefits that every user should consider. Kodi is a popular media player that allows users to access a wide range of online content, but using a VPN can enhance the overall experience and provide added security and privacy. Here are some compelling reasons to use a VPN on Kodi:
Anonymity: When you connect to a VPN server, your real IP address is hidden, making it difficult for anyone to track your online activities. This level of anonymity is crucial for maintaining privacy while streaming content on Kodi.
Bypassing Geo-Restrictions: VPNs allow you to bypass geographical restrictions on certain content by connecting to servers in different locations. This means you can access region-locked content on Kodi that would otherwise be unavailable in your area.
Security: VPNs encrypt your internet connection, shielding your data from potential hackers or cybercriminals. This is particularly important when streaming content on Kodi, as it adds an extra layer of security to protect your personal information.
Avoiding Throttling: Internet service providers (ISPs) often throttle the bandwidth of users streaming content on Kodi to manage network traffic. By using a VPN, your traffic is encrypted, making it difficult for ISPs to detect and throttle your connection speed.
Protection from Malware: Some third-party Kodi addons may contain malware or be used for malicious purposes. A VPN can help block these threats by providing a secure connection to the internet.
In conclusion, using a VPN with Kodi is a smart choice for anyone looking to enhance their streaming experience while also prioritizing their online security and privacy. By taking advantage of the benefits that VPNs offer, Kodi users can enjoy a safer and more versatile entertainment platform.
0 notes
Text
what is vpn on firestick
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn on firestick
VPN setup on Firestick
Setting up a VPN on your Firestick can enhance your streaming experience by providing privacy, security, and access to geo-restricted content. While Firestick does not natively support VPN installation, you can still configure it to work with most VPN services. Here’s a step-by-step guide to help you set up a VPN on your Firestick:
Choose a VPN Service: Start by selecting a reliable VPN provider that offers a dedicated app for Firestick. Ensure the VPN has fast servers and robust security features.
Subscribe to the VPN: Sign up for a subscription plan with the VPN provider of your choice. Most VPNs offer multiple subscription options, including monthly, yearly, and multi-year plans.
Install the VPN App on Firestick: On your Firestick home screen, navigate to the search bar and type in the name of your chosen VPN. Select the VPN app from the search results and click on “Download” to install it.
Launch the VPN App: Once the installation is complete, open the VPN app on your Firestick. Sign in using your credentials provided by the VPN provider.
Connect to a Server: After logging in, you’ll be presented with a list of server locations. Choose a server location based on your preferences, such as accessing geo-blocked content or optimizing for speed.
Enable VPN Connection: Click on the “Connect” button to establish a VPN connection. Once connected, your Firestick will be protected by the VPN, and your internet traffic will be encrypted.
Verify Connection: To ensure that the VPN is working correctly, you can verify your new IP address using online tools or by accessing geo-restricted content that was previously unavailable.
Adjust Settings (Optional): Explore the settings within the VPN app to customize your experience further. You can often configure options like auto-connect, protocol selection, and split tunneling.
By following these steps, you can easily set up a VPN on your Firestick, allowing you to enjoy a secure and unrestricted streaming experience.
Benefits of VPN on Firestick
Using a VPN (Virtual Private Network) on your Firestick device can offer numerous benefits, enhancing your streaming experience and safeguarding your online activities. Here are some key advantages:
Enhanced Privacy and Security: By using a VPN, your internet traffic is encrypted, making it nearly impossible for hackers, ISPs, or government agencies to intercept or monitor your online activities. This ensures that your sensitive information, such as passwords, credit card details, and browsing history, remains secure.
Bypass Geo-Restrictions: Many streaming services impose geographical restrictions on their content, limiting access to certain regions. With a VPN, you can bypass these restrictions by connecting to servers in different countries, allowing you to access a wider range of content on your Firestick from anywhere in the world.
Avoid ISP Throttling: Some ISPs throttle the internet connection of users who engage in high-bandwidth activities, such as streaming video. By using a VPN, your traffic is encrypted, preventing your ISP from monitoring your online activities and thus avoiding potential throttling, which can result in smoother streaming and faster download speeds.
Access to Restricted Apps and Websites: In some regions, certain apps and websites may be blocked or censored. With a VPN, you can access these restricted platforms on your Firestick by connecting to servers located in countries where they are available.
Protection Against Malware and Phishing: VPNs can provide an additional layer of security by blocking malicious websites and preventing malware or phishing attacks. This is particularly important when downloading third-party apps or accessing unknown sources on your Firestick.
In conclusion, using a VPN on your Firestick offers a range of benefits, including enhanced privacy, access to geo-restricted content, improved streaming performance, and protection against online threats. By investing in a reputable VPN service, you can enjoy a safer and more versatile streaming experience on your Firestick device.
VPN apps for Firestick
Title: The Top VPN Apps for Firestick: Enhancing Privacy and Security
As streaming services continue to dominate the entertainment landscape, ensuring privacy and security while using platforms like Firestick has become increasingly important. Virtual Private Network (VPN) apps offer a solution by encrypting internet connections, masking IP addresses, and allowing users to access geo-blocked content. Here are some top VPN apps tailored specifically for Firestick users:
ExpressVPN: Known for its blazing-fast speeds and robust security features, ExpressVPN offers a dedicated Firestick app. With servers in over 90 countries, it enables seamless streaming of content from around the world while maintaining user privacy.
NordVPN: Renowned for its extensive server network and strict no-logs policy, NordVPN provides a user-friendly Firestick app. Its advanced security features, such as Double VPN and CyberSec, offer enhanced protection against online threats.
Surfshark: With unlimited simultaneous connections and a user-friendly interface, Surfshark is an excellent choice for Firestick users seeking affordability and reliability. Its CleanWeb feature blocks ads and malware, ensuring a smooth streaming experience.
CyberGhost: Offering specialized servers for streaming and torrenting, CyberGhost is tailored for Firestick users who prioritize content accessibility. Its user-friendly app interface and robust encryption protocols make it a popular choice for enhancing privacy.
IPVanish: Designed with Firestick compatibility in mind, IPVanish boasts high-speed connections and unlimited bandwidth. Its SugarSync integration allows users to secure their files while enjoying unrestricted access to streaming platforms.
Before selecting a VPN app for Firestick, users should consider factors such as server coverage, speed, and privacy features. By choosing one of these top VPN apps, Firestick users can enjoy a safer and more versatile streaming experience without compromising their privacy and security.
VPN troubleshooting on Firestick
Title: Troubleshooting VPN Issues on Firestick: A Comprehensive Guide
Using a VPN on your Firestick can enhance your streaming experience by providing privacy, security, and access to geo-restricted content. However, like any technology, VPNs can sometimes encounter issues. Here’s a guide to troubleshooting common VPN problems on your Firestick:
Check Internet Connection: Ensure that your Firestick is connected to the internet and that your Wi-Fi signal is strong. A weak connection can cause VPN issues.
Restart Firestick and Router: Sometimes, a simple restart can resolve connectivity issues. Power off your Firestick and router, then turn them back on after a few minutes.
Update VPN App: Make sure that your VPN app is up to date. Developers regularly release updates to fix bugs and improve performance.
Switch Servers: If you’re experiencing slow speeds or difficulty connecting, try switching to a different server within the VPN app. Sometimes, certain servers can become overcrowded or experience technical issues.
Check VPN Settings: Double-check your VPN settings to ensure they are configured correctly. Pay attention to protocols, encryption levels, and any additional features that may impact performance.
Clear App Cache: If your VPN app is acting up, clearing its cache can help resolve glitches. Go to Settings > Applications > Manage Installed Applications, select your VPN app, and choose the option to clear cache.
Reinstall VPN App: As a last resort, uninstall and reinstall the VPN app on your Firestick. This can resolve any underlying issues with the app itself.
By following these troubleshooting steps, you can resolve most VPN issues on your Firestick and enjoy a seamless streaming experience. If problems persist, reach out to your VPN provider’s customer support for further assistance.
VPN security for Firestick
Title: Enhancing Firestick Security with VPN: A Comprehensive Guide
In the age of digital advancement, streaming devices like Firestick have become an integral part of our entertainment setup. However, with the convenience of accessing various streaming platforms comes the risk of exposing your sensitive data to potential threats. This is where VPN (Virtual Private Network) comes into play, offering a robust layer of security for Firestick users.
First and foremost, VPN encrypts your internet connection, making it virtually impossible for hackers or ISPs to intercept your data. This encryption ensures that your online activities, including streaming, remain private and secure.
One of the primary concerns for Firestick users is geo-restrictions imposed by streaming services. By using a VPN, you can bypass these restrictions and access content from anywhere in the world. Whether it's unlocking region-locked shows or accessing streaming platforms not available in your country, VPN empowers you with unrestricted access.
Moreover, VPNs offer anonymity by masking your IP address. This means your online identity remains hidden, protecting you from potential surveillance or tracking by third parties.
Choosing the right VPN for your Firestick is crucial. Look for VPN providers that offer dedicated Firestick apps, ensuring seamless integration and ease of use. Additionally, prioritize VPNs with strong encryption protocols, no-logs policy, and a wide server network for optimal performance.
However, it's essential to note that while VPNs enhance security and privacy, they may impact your internet speed slightly due to encryption overhead. Nevertheless, the trade-off between speed and security is worth it, especially when safeguarding your sensitive information.
In conclusion, VPN is a must-have tool for Firestick users looking to enhance their security and privacy while enjoying seamless streaming experiences. By encrypting your connection, bypassing geo-restrictions, and ensuring anonymity, VPNs provide comprehensive protection against online threats. So, safeguard your Firestick today with a reliable VPN and enjoy worry-free streaming!
0 notes
Text
does a vpn hide internet activity from hotels
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn hide internet activity from hotels
VPN encryption methods
In the realm of online security and privacy, Virtual Private Networks (VPNs) serve as essential tools for safeguarding sensitive data and maintaining anonymity on the internet. One crucial aspect of VPNs that ensures the protection of user information is encryption. Encryption methods employed by VPNs are designed to scramble data, making it unreadable to anyone without the proper decryption key. Here, we delve into the various VPN encryption methods commonly utilized today.
AES (Advanced Encryption Standard): AES is widely regarded as one of the most secure encryption algorithms available. It operates by encrypting data in blocks of 128 bits, with key lengths of 128, 192, or 256 bits. AES encryption is highly robust and is often the preferred choice for VPN providers.
RSA (Rivest-Shamir-Adleman): RSA encryption relies on public-key cryptography, utilizing both public and private keys for encryption and decryption. While RSA is effective for key exchange and authentication, it is less commonly used for bulk data encryption due to its relatively slow processing speed compared to symmetric encryption algorithms like AES.
OpenVPN: OpenVPN is an open-source VPN protocol that supports various encryption algorithms, including AES and RSA. It is highly configurable and can adapt to different security requirements and network conditions, making it a popular choice among VPN users and providers alike.
IPsec (Internet Protocol Security): IPsec is a suite of protocols used to secure internet communications at the IP layer. It employs encryption algorithms like AES and 3DES (Triple Data Encryption Standard) to ensure confidentiality, integrity, and authenticity of data transmitted over a VPN connection.
WireGuard: WireGuard is a relatively new VPN protocol known for its simplicity and efficiency. It utilizes modern cryptographic techniques such as the Noise protocol framework and Curve25519 for key exchange, offering fast and secure connections.
In conclusion, VPN encryption methods play a crucial role in safeguarding online privacy and security. By understanding these methods, users can make informed decisions when choosing a VPN service that meets their security needs.
Hotel network monitoring
Hotel network monitoring is a critical aspect of maintaining the efficiency and security of a hotel's IT infrastructure. With the increasing demand for seamless connectivity and the growing threat of cyber attacks, having a robust network monitoring system in place is a top priority for hotel management.
One of the key benefits of hotel network monitoring is the ability to proactively identify and address potential issues before they escalate into major problems. By continuously monitoring the network for anomalies and irregularities, hotel IT teams can quickly pinpoint and resolve issues such as network congestion, bandwidth limitations, and security breaches. This proactive approach helps ensure uninterrupted service for guests and staff, ultimately leading to higher levels of guest satisfaction and operational efficiency.
In addition to improving network performance, monitoring systems also play a crucial role in safeguarding sensitive guest data and hotel assets. By monitoring network traffic and detecting suspicious activities, hotel IT teams can effectively prevent data breaches and unauthorized access to the network. This not only protects the integrity of the hotel's operations but also helps maintain compliance with data protection regulations.
Furthermore, hotel network monitoring enables IT teams to track network usage patterns and trends, allowing them to optimize network resources and plan for future expansions. By analyzing data generated by monitoring tools, hotel management can make informed decisions about network upgrades, hardware investments, and security measures.
In conclusion, hotel network monitoring is a vital tool for ensuring the reliability, security, and performance of a hotel's IT infrastructure. By investing in a comprehensive monitoring system, hotels can enhance guest experiences, protect sensitive data, and drive overall business success.
Privacy implications of hotel Wi-Fi
Hotel Wi-Fi is a convenient amenity that allows guests to stay connected while traveling, but it also comes with privacy implications that travelers should be aware of. When connecting to a hotel Wi-Fi network, users are often required to input personal information such as their name, email address, or room number. This data can be intercepted by cybercriminals if the network is not properly secured, putting guests at risk of identity theft or fraud.
Additionally, hotel Wi-Fi networks are often unencrypted, making it easier for hackers to access sensitive information such as login credentials or financial details. By monitoring network traffic, cybercriminals can potentially intercept passwords, credit card numbers, and other confidential data transmitted over the network.
Furthermore, hotels may track users' online activities while connected to their Wi-Fi network. This data can be used for various purposes, such as targeted advertising or monitoring guest behavior. Guests should be cautious about the type of information they access or share while using hotel Wi-Fi to prevent their online activities from being monitored by the hotel or third parties.
To protect their privacy while using hotel Wi-Fi, guests can take several precautions. Using a virtual private network (VPN) encrypts internet traffic and adds an extra layer of security, making it difficult for hackers to intercept sensitive data. Guests should also avoid accessing or sharing sensitive information, such as financial details or personal data, while connected to the hotel Wi-Fi network.
In conclusion, while hotel Wi-Fi offers convenience for travelers, it also poses privacy risks that users should be mindful of. By taking precautions and being cautious about the information they access or share while connected to hotel Wi-Fi, guests can protect their privacy and data from potential cyber threats.
VPN effectiveness against hotel tracking
When staying at a hotel, many travelers are unaware that their online activities can be tracked by the hotel's network. This tracking can include monitoring the websites you visit, your search history, and even your personal information. To protect your online privacy and data security while using a hotel's Wi-Fi network, using a VPN (Virtual Private Network) can be highly effective.
A VPN encrypts your internet connection, creating a secure and private tunnel for your data to pass through. This means that even if the hotel is monitoring their network, they won't be able to see what you are doing online. Your internet traffic is rerouted through the VPN server, masking your IP address and location, making it difficult for anyone to track your online activities.
Additionally, using a VPN can also help bypass any restrictions or censorship that the hotel may have placed on certain websites or content. By connecting to a VPN server located in a different region, you can access geo-blocked content and enjoy a more open internet experience.
Overall, VPNs are highly effective in protecting your online privacy and security when using hotel Wi-Fi networks. They provide an extra layer of security and encryption that helps keep your personal information safe from potential tracking or hacking attempts. So next time you travel, make sure to use a reliable VPN service to stay safe and secure online.
VPN usage legality in hotel networks
Using a VPN (Virtual Private Network) on hotel networks raises questions about legality and ethical use. Hotels typically provide Wi-Fi networks for guests, but the terms of service often restrict certain activities, including the use of VPNs. However, the legality of VPN usage in hotels depends on various factors, including the hotel's policies, local laws, and the VPN provider's terms of service.
In many countries, there are no specific laws prohibiting the use of VPNs in hotels. However, hotels may have their own policies against VPN usage to ensure network security and compliance with local regulations. These policies may be outlined in the terms and conditions that guests agree to upon check-in. Violating these policies could result in consequences such as having your internet access restricted or being asked to leave the hotel.
From an ethical standpoint, using a VPN on a hotel network without permission could be considered questionable. Hotels may have legitimate reasons for restricting VPN usage, such as protecting their network from cyber threats or complying with government regulations. By bypassing these restrictions, guests could potentially expose the hotel's network to security risks or violate local laws unintentionally.
Before using a VPN on a hotel network, it's essential to review the hotel's policies regarding internet usage and VPNs. Additionally, guests should ensure that their VPN provider's terms of service permit usage in hotels and comply with local laws. Ultimately, while using a VPN on a hotel network may provide privacy and security benefits, it's crucial to do so responsibly and in accordance with the hotel's rules and regulations.
0 notes