#Orchestrated Distributed Intelligence
Explore tagged Tumblr posts
Text
First edition of the Idea Frontier newsletter 🚀
#ai#AI Agents#Idea Frontier#Neural Networks#ODI#Orchestrated Distributed Intelligence#Rhythmic Sharing#Technofeudalism
1 note
·
View note
Text


Darth Maul's ambitious plan to leverage the chaos from the aftermath of the Clone Wars has led to suffering of refugees and the forgotten inhabitants in the Galactic Underworld is a calculated strategy to build power and influence from the shadows of Coruscant. Here’s how he could orchestrate the operation with Dryden Vos and Crimson Dawn:
Step 1: Establishing the Humanitarian Front
1.1. Employing the service of Dryden Vos:
Maul has Dryden Vos, a cunning and ruthless leader of Crimson Dawn, to manage the operation. Vos’s experience with the criminal underworld allows him to navigate the complex networks of power and resources.
1.2. Creating a Cover Story:
To gain the trust of the public and the underworld, Vos crafts a narrative that Crimson Dawn is a humanitarian organization aimed at alleviating the suffering caused by the Clone Wars. This includes distributing food, medicine, and financial aid to refugees in the Undercity.
Step 2: Mobilizing Resources
2.1. Gathering Supplies:
Crimson Dawn uses its vast resources to acquire supplies through both legal and illegal means. This could involve negotiating with sympathetic suppliers, stealing from warehouses, or even using bounty hunters to procure goods.
2.2. Distributing Aid:
Vos sets up distribution points throughout the Undercity, staffed by Crimson Dawn operatives disguised as charity workers. This provides a façade of legitimacy and allows for the gathering of intelligence on local populations and potential recruits.
Step 3: Building a Network of Support
3.1. Community Engagement:
Crimson Dawn engages with local leaders and influential figures in the Undercity, providing aid in exchange for loyalty and support. By positioning themselves as benefactors, they begin to build a network of allies among the downtrodden.
3.2. Recruitment of Disenfranchised Individuals:
As the humanitarian efforts continue, Crimson Dawn identifies individuals with skills, such as former soldiers, mechanics, and navigators, who are desperate for work and a sense of purpose. These individuals are offered roles within Crimson Dawn, often with promises of wealth and protection.
Step 4: Covert Military Training
4.1. Training Recruits:
Under the guise of providing vocational training, Crimson Dawn begins to train these recruits in combat and guerrilla tactics. This training is conducted in secret, ensuring that the recruits remain loyal to Maul’s larger goals.
4.2. Establishing Cells:
The recruits are organized into small cells that can operate independently within the Undercity. This decentralized structure allows for flexibility and deniability, making it harder for the Republic or Jedi to trace these activities back to Maul.
Step 5: Strategic Operations
5.1. Sabotage and Disruption:
As the network of recruits grows, Maul directs them to conduct sabotage operations against Republic supply lines and infrastructure, further destabilizing the situation on Coruscant and inciting unrest among the populace.
5.2. Building Public Sentiment:
Crimson Dawn uses propaganda to portray the Jedi and the Republic as oppressors, framing their actions as a necessary rebellion against a corrupt system. This narrative can draw more individuals to their cause.
Step 6: The Endgame
6.1. Coordinating a Large-Scale Uprising:
With a significant force built from the ranks of the disenfranchised, Maul plans a coordinated uprising within the Undercity. This would catch the Republic off guard, leading to chaos that could spread to the surface levels of Coruscant.
6.2. Sacking Coruscant:
The ultimate goal is to create enough unrest and chaos to launch a full-scale attack on key locations within Coruscant, allowing Crimson Dawn to seize control and establish a new order under Maul’s leadership.
Conclusion
Through this multi-faceted strategy, Maul aims to exploit the vulnerabilities exposed by the Clone Wars, using humanitarian efforts as a cover for building a loyal army. By manipulating the suffering of the populace and positioning Crimson Dawn as their savior, Maul seeks not only to gain power but to position himself as a formidable force in the galaxy, ready to strike against the Jedi and the Republic at the opportune moment.

#star wars#star wars fanfiction#star wars what if#check out my fanfic#my fanfiction#crimson dawn#darth maul#feral opress#savage opress#crime syndicate#dryden vos#lom pyke#ziton moj#clone wars#upcoming chapter#chapter summary
20 notes
·
View notes
Text
an open accusation - subjectID: [ @paincaat ]
Case number: 008
Date: June 14th, 2024
Time: 2:23 AM EST
given recent developments in the disappearance of nunalastor, it is imperative that we urgently re-evaluate whether our resources are being accordingly distributed in the hunt for the abductor of nunalastor. in particular, while @huskersbar originally caught our attention as a primary suspect due to their known status as nunalastor's enemy and their explicit mention in a video left by presumably nunalastor's side account, upon closer inspection, it appears we have dragged the wrong cat into the spotlight. thus, we turn our attention to @paincaat, an elusive individual lurking conspicuously behind the coining of nunalastor's iconic 'sexy cursed nun cat alastor' icon. resultantly, we now analyze the correlation between huskersbar's association with this kidnapping and why paincaat consequently may play a larger role in this catnapping than what first meets the eye.
while the blog 'paincaat' may seem to be an ordinary fanart blog of the controversial animated show 'Hazbin Hotel', upon further inspection, it is clear that several anomalies co-exist within this user's tumblr page. one such anomaly lies within the existence of the blog @nunalastorscursedkitten, presumably one of paincaat's aliases. this user notably claims in an introductory post that they created paincaat's infamous first cursed nun cat alastor post, which consequently became the face of the nunalastor account as their profile picture. more importantly, close examination reveals that this user can consistently be found signing off reblogged posts as paincaat themselves and fending off horny nunalastor stalker @lu-lus-duckies, another potential suspect.
interestingly, nunalastorscursedkitten appears to have been previously adopted by huskersbar, consequently becoming huskersbar and @re-bon-bon-san's cat. they proceeded to tag lu-lus-duckies, presumably to give them the middle finger. given this strange interaction between the cursed kitten and members of the cursed polycule, we presume it is likely that paincaat aimed to create an alibi and frame huskersbar et al. for this eventual kidnapping. how paincaat managed to worm their way behind the shadows of the polycule and also manipulate nunalastor into using their cursed art as their icon remains a mystery unsolved to this day.
more importantly, when addressed by user @priestvox to create a new cursed priest cat vox icon during priestvox's initial appearance, it is critical to note that paincaat immediately complied and was able to supply the mysterious user with articulately drawn images of priestvox's likeness. despite explicitly denying their involvement in the kidnapping on the nunalastorscursedkitten blog, paincaat evidently has ties to the priestvox brand and likely is hiding more secrets. paincaat themselves, despite being heavily active prior to april, has stopped creating their cursed artistic abominations, presumably to orchestrate their elaborate plan to remove nunalastor off the face of the internet.
while paincaats true motives remain unknown, we speculate that the true answer may be much more sinister than what we previously imagined. curiously, paincaat can be initialed as 'PC', indicating that paincaat potentially has ties to the creation of artificial intelligence (AI). another notable figure, vox, works contingent to advanced forms of machinery, increasing the likelihood of paincaat being affiliated with priestvox. while paincaat themselves claims to be aromantic asexual, it is evident that vox has an incredibly massive hate boner for alastor. thus, the two likely collaborated on the premise of a common interest: a nunalastor girlfriend AI, created using the kidnapped nunalastor themselves. this AI would act to satiate priestvox's insatiable hate lust for nunalastor while acting as a gift from paincaat to lu-lus-duckies. why paincaat would ever choose to be homosexual for lu-lus-duckies leads to be an even greater enigma than nunalastor's disappearance. however, this is pure speculation and we have yet to gather conclusive evidence.
ultimately, while we can't completely clear huskerbars name as an accomplice of this devious pain in the pussy, we must not rule out the possibilities of an innocent soul being caught in this cat's cradle.
16 notes
·
View notes
Text
Honey Traps

Honey Traps – Seduction, Deception, and Espionage
A honey trap isn’t just a movie cliché—it’s a very real and often dangerous method where romance and sex are used as weapons. The goal might be personal gain, political influence, or even international espionage. The concept is simple yet powerful: identify a target who holds valuable information or resources, and set the trap—often through subtle seduction. The target is lured into what seems like a genuine relationship, but it’s all part of a calculated strategy to gain access to their secrets or influence their decisions.
The term "honey trap" also applies in the modern digital age. Dating sites are increasingly used to lure victims into scams or intelligence operations.
Private investigators are often hired to orchestrate honey traps, especially when there are suspicions of infidelity in a relationship. The goal is to catch the "target" in the act—often with photographic or video evidence. In some cases, the entire affair is fabricated for the sole purpose of blackmail, with love being nothing but a carefully crafted illusion while the camera rolls in the background.
The situation gets even darker when honey traps are used in drug trafficking or to lure new users into addiction. These trappers aren’t looking for love—they want control, money, or loyalty based on manipulation.
During the Cold War, honey traps were part of serious geopolitical games. The Soviet KGB employed female agents known as “Mozhno girls,” tasked with seducing foreign officials to extract sensitive information. The name Mozhnocomes from the Russian word "можно," meaning “permitted”—these agents had special clearance to break the strict rules that normally prohibited Russians from contacting foreigners.
In 2009, Britain’s MI5 released a 14-page document titled The Threat from Chinese Espionage, which was distributed widely to banks and major corporations. It served as a stark warning: Chinese intelligence agencies were engaging in long-term seduction-based operations to gather information, using sexual relationships to exploit vulnerabilities and pressure individuals into cooperation.

Hunaja-ansa – viettelyä, valheita ja vakoilua
Hunaja-ansa, englanniksi honey trap, ei ole pelkkä elokuvaklisee, vaan todellinen ja usein vaarallinen menetelmä, jossa romantiikkaa ja seksiä käytetään aseina. Tavoitteena voi olla henkilökohtainen hyöty, poliittinen vaikuttaminen tai jopa valtioiden välinen vakoilu. Toimintamalli on yksinkertainen, mutta tehokas: valitaan kohde, jolla on haluttua tietoa tai resursseja, ja viritetään ansa – usein huomaamattoman viettelevä. Kohde johdatellaan suhteeseen, joka saattaa vaikuttaa aidolta, mutta on vain keino saada ote hänen elämästään, päätöksistään ja salaisuuksistaan.
Termi "hunaja-ansa" kattaa myös moderneja muotoja. Esimerkiksi deittisivustoja käytetään tänä päivänä yhä useammin uhrien houkuttelemiseen huijauksiin tai vakoiluun.
Yksityisetsivät saavat toimeksiantoja hunaja-ansojen järjestämiseen etenkin silloin, kun parisuhteessa epäillään uskottomuutta. Tavoitteena on saada kiinni jäävä osapuoli kiinni itse teosta – usein valokuvin tai videoin. Toisinaan hunajaloukku voi olla silkkaa kiristystä varten rakennettu näytelmä, jossa rakkaus on vain lavastus ja kamera käy koko ajan taustalla.
Vielä synkemmäksi peli muuttuu, kun hunaja-ansoja käytetään huumeiden salakuljetuksessa tai uusien käyttäjien houkuttelemisessa riippuvuuden polulle. Viettelijä ei hae rakkautta – vaan valtaa, rahaa tai valheellista lojaalisuutta.
Kylmän sodan aikaan hunaja-ansat olivat vakavaa valtiollista peliä. Neuvostoliiton KGB:n riveissä toimi niin kutsuttuja "Mozhno-tyttöjä", naisagentteja, joiden tehtävänä oli vietellä ulkomaisia virkamiehiä saadakseen heistä tietoa. Nimi Mozhno tulee venäjän sanasta "можно", joka tarkoittaa "sallittua" – näillä agenteilla oli erityislupa rikkoa rajoja, joita tavallisille kansalaisille ei myönnetty.
Vuonna 2009 Britannian tiedustelupalvelu MI5 julkaisi 14-sivuisen raportin nimeltä The Threat from Chinese Espionage. Se jaettiin laajalti pankeille ja suuryrityksille varoituksena: Kiinan tiedustelupalvelut käyttävät hunaja-ansoja pitkäjänteisesti, rakentavat suhteita, viettävät aikaa, ja lopulta käyttävät intiimejä hetkiä kiristyskeinona saadakseen vaikutusvaltaa ja salaista tietoa.
1 note
·
View note
Text
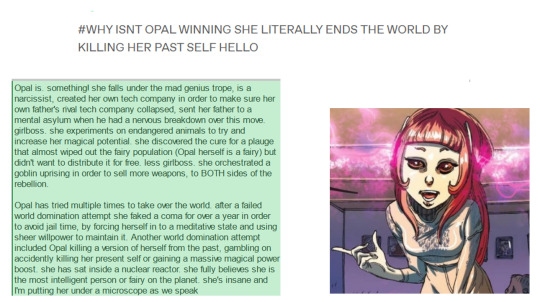
opal koboi propaganda masterpost! i’ll update after each round
[ID: there's a picture of opal koboi on the bottom right corner of a white slide. on the left side, there's green text box saying, "Opal is. something! she falls under the mad genius trope, is a narcissist, created her own tech company in order to make sure her own father's rival tech company collapsed, sent her father to a mental asylum when he had a nervous breakdown over this move. girlboss. she experiments on endangered animals to try and increase her magical potential. she discovered the cure for a plauge that almost wiped out the fairy population (Opal herself is a fairy) but didn't want to distribute it for free. less girlboss. she orchestrated a goblin uprising in order to sell more weapons, to BOTH sides of the rebellion. Opal has tried multiple times to take over the world. after a failed world domination attempt she faked a coma for over a year in order to avoid jail time, by forcing herself in to a meditative state and using sheer willpower to maintain it. Another world domination attempt included Opal killing a version of herself from the past, gambling on accidently killing her present self or gaining a massive magical power boost. she has sat inside a nuclear reactor. she fully believes she is the most intelligent person or fairy on the planet. she's insane and I'm putting her under a microscope as we speak."
on top of both the picture and the text box, reads, "#WHY ISNT OPAL WINNING SHE LITERALLY ENDS THE WORLD BY KILLING HER PAST SELF HELLO." /End ID.]
7 notes
·
View notes
Text
Edge Computing, Real-Time Data Processing, and Intelligent Automation
In the dynamic landscape of the power industry, staying ahead of the curve requires a fusion of cutting-edge technologies and strategic operations. With over four years of experience in the field, our journey has been marked by innovation, efficiency, and resilience. In this article, we explore how the convergence of edge computing, real-time data processing, predictive fault diagnosis, and intelligent automation is revolutionizing the energy sector.

Edge Computing: A Powerhouse at the Edge
Edge computing is the bedrock upon which modern utility IT operations are built. By processing data closer to the source, we've reduced latency and increased responsiveness. This real-time capability has enabled us to make critical decisions swiftly, optimizing grid operations and minimizing downtime. The result? A more reliable and efficient energy distribution system.
Real-Time Data Processing: Harnessing the Flow
The ability to handle vast volumes of real-time data has unlocked new possibilities for the power industry. We've implemented advanced data analytics to monitor and control grid assets proactively. Predictive fault diagnosis and anomaly detection algorithms have become our allies in preventing potential failures, thus averting costly disruptions.
Predictive Fault Diagnosis: Proactive Maintenance
Predictive fault diagnosis is a game-changer in the energy industry. By leveraging historical data and machine learning models, we've gained the capability to predict equipment failures before they occur. This predictive maintenance approach has not only extended the lifespan of critical assets but has also significantly reduced operational costs.
Robotic Process Automation (RPA): Streamlining Operations
RPA has automated routine tasks, freeing up human resources for more complex problem-solving. In the power sector, this has led to improved efficiency in billing, customer service, and administrative functions. It's allowed us to allocate resources strategically and ensure a seamless experience for customers.
Intelligent Automation (IA): Powering the Future
Intelligent Automation (IA) goes beyond RPA, integrating AI and machine learning to make autonomous decisions. IA systems continuously learn from data, optimizing grid operations in real-time. It's a crucial component in our journey toward a smart grid, where energy generation, distribution, and consumption are finely tuned to meet demand efficiently.
In conclusion, the synergy of edge computing, real-time data processing, predictive fault diagnosis, RPA, and IA has transformed the power industry. We are no longer just energy providers; we are orchestrators of a reliable, efficient, and sustainable energy ecosystem. As we look to the future, our commitment to innovation remains unwavering, ensuring that the lights stay on and the power flows seamlessly for generations to come.
3 notes
·
View notes
Text
Edge Intelligence Unified Architecture for Predictive Maintenance
Digital transformation is accelerating the evolution of computing frameworks. With data increasingly generated outside centralized cloud environments, enterprises are turning to edge computing and fog architecture to process information closer to its source. This has led to a growing need for cohesion among these systems. Edge intelligence unified architecture offers a strategic model for integrating edge devices, fog nodes, and cloud infrastructure, enabling real-time insights, operational continuity, and scalable deployment. It ensures that data is not only collected but acted upon at the right layer of the computing ecosystem.

Understanding the Need for Unified Architecture Today’s computing needs are no longer served by a one-size-fits-all cloud approach. Applications in manufacturing, healthcare, autonomous vehicles, and smart cities require ultra-low latency and contextual awareness. A unified architecture ensures that intelligence exists not just in the cloud, but across all computing layers—optimizing both speed and scalability. Without a unified model, edge and fog systems risk becoming siloed, increasing complexity and reducing data reliability.
The Role of Edge Intelligence in Modern IT Edge intelligence enables devices at the edge of the network—like sensors, gateways, and embedded systems—to process and analyze data locally. This reduces the dependency on cloud infrastructure for every computational need. It improves response times, minimizes bandwidth usage, and allows enterprises to make faster decisions. When this edge intelligence is integrated within a unified architecture, its value scales exponentially through coordinated communication with fog and cloud layers.
Why Edge Intelligence Unified Architecture Matters A fragmented approach to edge and fog computing can lead to inefficiencies, security gaps, and integration headaches. Edge intelligence unified architecture provides a blueprint for harmonizing data flows, orchestrating workloads, and synchronizing analytics across distributed environments. It ensures seamless transitions between edge, fog, and cloud systems, giving enterprises the agility to deploy intelligent solutions where they are most needed—without reinventing the wheel for each layer.
Edge vs. Fog vs. Cloud: Clarifying the Layers Edge computing occurs directly on or near the devices that generate data, enabling real-time responses. Fog computing sits between the edge and the cloud, adding a layer of localized processing and orchestration. Cloud computing offers centralized processing and long-term storage but is limited by latency. A unified architecture blends these layers so that each plays a complementary role, with edge handling immediate reactions, fog managing coordination, and cloud focusing on historical analysis and scalability.
Benefits of a Unified Approach to Edge Intelligence With a unified model, enterprises can streamline data processing, enhance security by minimizing data transit, and maintain consistent governance across all layers. It also simplifies application deployment by offering a standardized platform for running AI models, managing connectivity, and scaling services. The result is a more resilient and responsive digital infrastructure that meets modern expectations of speed, personalization, and reliability.
Scenarios Where Edge Intelligence Unified Architecture Thrives Industries such as autonomous transportation, smart grids, retail analytics, and predictive maintenance benefit from this architecture. In each of these domains, milliseconds matter, and a centralized cloud approach cannot meet operational demands. Edge intelligence unified architecture allows these systems to analyze, adapt, and act locally, while still contributing to the broader enterprise intelligence framework.
Challenges and Considerations in Implementing Unified Architectures Despite its advantages, implementing a unified architecture is not without challenges. Organizations must consider interoperability between hardware and software platforms, edge-specific security concerns, and the complexity of orchestrating hybrid deployments. Success requires choosing flexible frameworks, investing in edge-ready AI tools, and establishing policies for governance and lifecycle management.
For more info https://bi-journal.com/edge-intelligence-unified-architecture/
Conclusion As enterprises strive to make faster, smarter, and more localized decisions, edge intelligence unified architecture becomes the backbone of modern computing strategies. It brings clarity to an increasingly complex digital landscape by integrating edge, fog, and cloud into a coordinated system that delivers on performance, scalability, and innovation. By investing in a unified model, businesses position themselves to harness real-time intelligence while maintaining the agility and resilience needed in a data-driven world.
#Edge Computing#Edge Intelligence#Fog Computing#BI Journal#BI Journal news#Business Insights articles
0 notes
Text
Powerful eCommerce Global Solutions Guide

The digital marketplace no longer has borders. A shopper in Tokyo can discover a craft brewery in Devon while a boutique in Lagos ships designer sandals to clients in Montreal. This borderless reality is both thrilling and complex. Brands that succeed at scale share one trait; they master the tools and tactics that remove friction at every step from discovery to doorstep. This guide unpacks the pillars of powerful eCommerce solutions built for a truly connected world and shows how any ambitious seller can carve out a space in the fast-moving arena of global ecommerce.
Start with Market Intelligence Growth starts with knowing where demand already exists and where white space is still untapped. Study purchasing power culture and logistics standards in each region before you launch a marketing blitz. Western Europe may value eco packaging while Southeast Asia prizes lightning-fast mobile checkout. By tailoring your offer to local expectations you raise conversion without raising ad spend.
Localized Storefronts Shoppers feel at home when store language currency and sizing all speak their dialect. A single English-only site with a drop-down currency switch will never perform as well as fully localized pages. Translate product descriptions with native copywriters rather than relying on machine output. Adjust imagery to mirror local lifestyles and climates. Transparent adaptation signals respect and builds trust fast—a cornerstone of global ecommerce success.
Cross-Border Payments A sale is only final when the payment clears. Each region favors its own trusted gateway whether that is iDEAL in the Netherlands or Paytm in India. Work with a payment orchestration platform that supports multiple tender types under one roof while shielding customers from conversion fees. Keep an eye on authorization rates and tweak risk rules by country to avoid false declines that drive shoppers into competitor carts.
Smart Fulfilment Networks Speed matters but predictability matters more. Customers will wait an extra day if you promise a clear window and hit it every time. Partner with a 3PL that has bonded warehouses near your largest demand clusters. This reduces duties for customers and simplifies returns. Track dwell time inside each warehouse. Stock that sits too long ties up cash and risks obsolescence.
Consider the following fulfilment levers
Distributed inventory hubs close to demand
Automated routing that selects the cheapest carrier meeting service level
Dynamic delivery dates on product pages to set accurate expectations
Packaging optimization that drops parcel weight into lower fee brackets
Pre-paid return labels local to each market to boost repeat purchase trust
Tax and Duty Compliance Nothing ruins the unboxing moment like an unexpected customs bill. Display landed costs at checkout using automated duty calculators. Register for local tax schemes where thresholds dictate and file on time. Compliance may not feel glamorous but it is a silent driver of loyalty in the realm of global ecommerce.
Customer Service Without Borders Language support is only the first layer. Time zone coverage and channel preference matter just as much. Some regions lean on WhatsApp while others prefer live chat or email. Equip agents with unified dashboards so every conversation starts with full context regardless of channel. Quick resolutions turn shipping hiccups into stories of brand care and rescue.
Data Privacy and Cybersecurity International data laws tighten every year. Align with GDPR in Europe CCPA in California and emerging frameworks across Asia. Store customer data on regional servers when required and encrypt in transit and at rest. A single breach can erase years of goodwill. A proactive stance builds a security narrative that resonates with savvy shoppers.
Marketing Channels That Travel Algorithms differ by region yet storytelling fundamentals remain universal. Lead with benefits that solve local pain points whether that is beating summer heat or aligning with local festivities. Influencer partnerships bring cultural nuance your in-house team may miss. Measure creative resonance with A and B tests then push winning variations into paid channels.
Key campaign tactics include
Multilingual search ads tuned to regional dialects
Social video that highlights local use cases
Email flows triggered by location and seasonal events
Marketplace ads on platforms beyond Amazon where regional giants dominate
User-generated reviews highlighted with country flags to prove global social proof
Sustainability as a Growth Lever Eco conscious shopping is not confined to a single geography anymore. Offer carbon neutral shipping options and traceable materials. Provide clear recycling instructions on packaging. Green credentials attract a rising share of wallets and can justify a premium price.
Continuous Optimization Loop The best operators treat their strategy as a living organism. They pull weekly dashboards covering acquisition cost conversion rate and average order value by region. Underperforming zones signal a chance to refine price or content. Overperforming areas deserve fresh stock and higher ad budgets to double down before rivals catch up.
Final Word Crossing borders in commerce once required deep pockets and years of on-ground infrastructure. The rise of integrated platforms now puts that power in the hands of nimble brands willing to learn local nuance and execute with precision. By aligning localized content frictionless payments reliable fulfilment and culturally aware marketing you create a flywheel where each satisfied customer sparks the next discovery. Embrace these principles and your store will not just participate in global ecommerce—it will thrive as a trusted voice in every market it enters.
1 note
·
View note
Text
Managed WiFi: Business Network Infrastructure Solutions

Modern enterprises rely on wireless connectivity as a fundamental operational requirement. Managed wifi transforms how organizations approach network infrastructure by outsourcing wireless management to specialized providers. This strategic shift allows companies to maintain robust internet connectivity while concentrating resources on primary business functions.
Understanding Managed WiFi Concepts
Managed wifi involves partnering with professional network providers who assume complete responsibility for wireless infrastructure operations. These partnerships encompass equipment deployment, system configuration, security oversight, and continuous performance monitoring. Organizations benefit from enterprise-level wireless capabilities without developing internal networking expertise.
A managed wifi system consists of interconnected components working harmoniously to deliver consistent wireless access. The infrastructure includes carefully positioned access points, centralized management controllers, and multilayered security protocols. This coordinated approach ensures reliable connectivity across all business locations and user devices.
Architecture of Managed WiFi Systems
Professional managed wifi systems integrate several critical elements designed for optimal wireless performance. High-quality access points establish the network backbone, positioned strategically to maximize coverage while supporting numerous concurrent connections without compromising speed or reliability.
Central network controllers serve as command hubs for managed wifi system operations. These advanced devices orchestrate data flow, enforce security measures, and deliver automated network optimization. Controllers continuously adjust power levels, frequency channels, and traffic distribution to maintain peak performance standards.
Security Framework in Managed WiFi
Managed wifi sercurity implements comprehensive protection strategies to defend wireless networks and connected endpoints. Advanced security measures include sophisticated encryption protocols, certificate-based authentication, and intelligent firewall systems that establish multiple defensive barriers against unauthorized intrusion attempts.
Network isolation represents a core managed wifi security strategy, creating separate virtual networks for distinct user categories and device types. Continuous security monitoring analyzes network communications to detect anomalous behavior and emerging threats. Regular vulnerability assessments and security updates maintain managed wifi security effectiveness against developing cyber threats.
Choosing Professional Managed WiFi Providers
Selecting suitable managed wifi providers demands careful assessment of technical qualifications and service delivery standards. Providers must exhibit comprehensive knowledge of wireless technologies, network security protocols, and enterprise infrastructure management practices.
Key evaluation factors include:
• Network architecture and design competencies
• Round-the-clock monitoring and technical support
• Growth accommodation and expansion capabilities
• Regional support presence and availability
• Specialized industry knowledge and experience
• Strategic vendor relationships and technology access
Sector-Specific Applications
Various industries demand customized managed wifi solutions addressing unique operational needs. Healthcare organizations require HIPAA-compliant networks supporting critical medical equipment and patient data systems while ensuring stringent privacy protection.
Academic institutions utilize managed wifi solutions engineered for high user concentrations and varied device ecosystems. Commercial retail operations depend on managed wifi solutions supporting transaction processing, inventory control, and customer service applications.

Assessment Standards for Service Providers
Evaluating managed wifi service providers requires systematic analysis of technical capabilities and service excellence. Providers should demonstrate verified experience with network architecture, security deployment, and performance enhancement across diverse industry applications.
Critical assessment criteria encompass:
• Professional qualifications and industry recognition
• Demonstrated success with comparable implementations
• Detailed service level commitments
• Flexible solutions supporting organizational growth
• Value-oriented pricing and contract flexibility
• Local expertise and support accessibility
Implementation and Operations
Managed wifi solutions deployment commences with thorough facility evaluation and network strategy development. Engineering professionals perform detailed site examinations to assess coverage needs, interference factors, and capacity demands.
Professional deployment ensures all infrastructure components function according to design parameters. Qualified technicians install networking equipment, configure management systems, and establish security protocols to guarantee optimal performance.
Operational management activities include:
• Automated system monitoring and incident notification
• Preventive maintenance and performance optimization
• Scheduled software updates and security enhancements
• Network capacity analysis and growth planning
• Remote diagnostics and configuration management
Economic Benefits and ROI
Managed wifi services commonly utilize predictable monthly fee structures encompassing equipment costs, installation services, and ongoing technical support. This financial model eliminates substantial capital investments while providing consistent operational expenses.
Investment returns encompass direct expense reductions plus operational efficiency gains, improved customer satisfaction, and enhanced employee productivity. Dependable wireless connectivity supports mobile workforce initiatives and optimized business processes.
Technology Trends and Future Developments
Advanced wireless standards including WiFi 6E and WiFi 7 introduce significant performance improvements to managed networking deployments. These technologies deliver enhanced data rates, minimized latency, and superior performance in dense user environments.
Future technology developments include:
• Next-generation wireless standard implementation
• Machine learning network optimization
• IoT device integration and management
• Advanced cybersecurity framework deployment
• Enhanced data analytics and intelligence
• Cellular network convergence opportunities
Best Managed WiFi Solutions Selection
Best managed wifi solutions require thorough evaluation of organizational needs and provider capabilities. Companies should analyze existing wireless limitations, future connectivity demands, and available internal resources before committing to managed solutions.
Best managed wifi solutions deliver professional-quality wireless infrastructure without complexity associated with internal management. The integration of expert design, commercial-grade equipment, and comprehensive security provides dependable connectivity supporting business development.
Summary
Professional wireless networking through managed services has emerged as vital for organizations pursuing reliable, secure, and scalable connectivity solutions. Identifying appropriate managed wifi service providers and deploying suitable solutions requires thorough evaluation of technical competencies and service quality standards.
Investment in professional managed wireless services produces enhanced connectivity, strengthened security, and operational efficiency supporting sustained business achievement and growth aspirations.
0 notes
Text
Why the Logistics Sector Can’t Thrive Without a Smart ERP

In the high-velocity world of global trade, where timelines are razor-thin and customer expectations are relentless, the logistics sector is under unprecedented pressure to deliver literally. From fleet management to last-mile delivery, warehousing to customs compliance, logistics is a marvel of modern coordination. But beneath the surface lies a complex web of operations that can either make or break profitability.
This blog explores why smart ERP software is no longer optional for logistics players — but mission-critical.
The Logistics Industry in 2025: A Landscape Under Pressure
The logistics sector is the backbone of global commerce. Whether it’s eCommerce, B2B distribution, or cold-chain pharmaceuticals, logistics fuels modern life.
But with rising operational costs, fluctuating fuel prices, labour shortages, and geopolitical tensions, the industry faces immense challenges:
Fragmented supply chains
Disconnected data silos
Lack of real-time insights
Poor route optimization
Compliance headaches
These bottlenecks aren’t just inefficiencies, they’re lost revenue, customer dissatisfaction, and strategic vulnerabilities.
What Is a Smart ERP? And Why Does It Matter?
A Smart ERP (Enterprise Resource Planning) system is not your grandfather’s ERP. It’s intelligent, connected, cloud-based, and often powered by AI and machine learning.
It goes beyond basic accounting and inventory management to offer:
Predictive analytics
Real-time supply chain visibility
Mobile access and automation
AI-powered forecasting
Integrated TMS (Transport Management Systems) and WMS (Warehouse Management Systems)
In logistics, a smart ERP becomes your central command centre, orchestrating every moving part of your operations seamlessly.
Legacy Systems: The Hidden Bottleneck
Many logistics companies still operate on fragmented legacy systems patched together over decades. These outdated tools suffer from:
Poor scalability
Incompatibility with modern tech (IoT, telematics, etc.)
No support for real-time updates
Manual data entry, leading to errors
The result? Operational blindness — a dangerous handicap in an industry that thrives on precision and agility.
Smart ERPs eliminate this by offering a unified digital core.
Real-Time Visibility: The Heart of Modern Logistics
What logistics managers crave the most is visibility, knowing where inventory is, how shipments are progressing, what’s stuck, and why.
A smart ERP provides:
Live tracking dashboards
Geolocation-based analytics
Exception alerts and ETA recalculations
Last-mile tracking integrations
This transparency isn’t just nice to have, it’s essential for customer satisfaction, SLAs, and proactive issue resolution.
Key ERP Features That Drive Logistics Efficiency
Here are the must-have smart ERP features that optimize logistics operations:
a. Transport Management System (TMS)
Handles route planning, carrier management, freight billing, and performance analytics.
b. Warehouse Management System (WMS)
Automates inventory allocation, picking, packing, and barcode scanning.
c. Fleet & Asset Management
Tracks vehicle health, fuel usage, driver behaviour, and maintenance schedules.
d. Order Management
Automates sales order processing, fulfilment prioritization, and invoicing.
e. Inventory Forecasting
AI-driven demand planning prevents overstocking and understocking.
Data-Driven Decision Making at Scale
In logistics, intuition can no longer be the strategy. With razor-thin margins, decisions must be anchored in data.
Smart ERPs bring:
Customizable reports and dashboards
Predictive analytics for demand and delivery
Cost-to-serve analysis
Carbon footprint tracking
These insights lead to data-backed decisions, not guesswork.
Integration with IoT, Telematics, and Fleet Management
Smart ERPs integrate effortlessly with the IoT ecosystem transforming operations with real-time telemetry:
Temperature sensors for cold chains
RFID and barcode scanners for inventory control
GPS and geofencing for fleet tracking
Wearables for warehouse labour efficiency
These integrations reduce human error, increase automation, and elevate decision-making precision.
Enhancing Supply Chain Resilience
The COVID-19 pandemic and geopolitical disruptions taught the logistics industry a harsh lesson: resilience trumps efficiency.
Smart ERPs support this shift by enabling:
Multi-sourcing and dynamic vendor allocation
Buffer stock alerts and alternative routing
Real-time risk monitoring
Business continuity planning
With a smart ERP, logistics companies are no longer caught off guard — they pivot, adapt, and stay ahead.
Regulatory Compliance Made Easy
Logistics is a compliance-heavy industry. From customs documentation to labour laws and environmental regulations, the paperwork is immense.
A smart ERP automates:
Regulatory workflows (e.g., GST, ELD, GHG compliance)
Audit trails and document storage
Multi-currency and multi-taxation logic
E-invoicing and digital records
This drastically reduces fines, delays, and human workload.
Why Smart ERP Is the Future of Sustainable Logistics
Today’s logistics industry is under pressure to go green and rightly so. A smart ERP enables:
Fuel and route optimization
Idle time tracking
Smart packaging analytics
Carbon emissions dashboards
Green vendor scoring
Sustainability is no longer a PR stunt — it’s a supply chain imperative. Smart ERPs make sustainability scalable.
Final Thoughts: The Road Ahead
The logistics sector is no longer about moving goods; it’s about moving smart. In 2025 and beyond, logistics companies that operate without a smart ERP are not just inefficient — they’re endangered.
The road ahead demands clarity, control, and cohesion and only smart ERP systems can deliver all three at scale.
0 notes
Text
Empowering India’s Next Wave of Entrepreneurs: How ‘Your Brandwala’ Is Redefining Branding for Startups

In an era where visibility often makes or breaks a startup, one agency is rewriting the rules for branding in India — not from a metropolitan glass tower, but from the vibrant heart of Uttar Pradesh. Your Brandwala, a full-service branding and PR agency founded on January 14, 2024, by Swarnima Mishra, is fast becoming a name synonymous with growth for India’s startups, solopreneurs, and small businesses.
Headquartered in Mohan Lal Ganj, Lucknow, the firm is not just another digital marketing agency; it’s a strategic brand architect dedicated to turning grassroots ambitions into investor-ready, nationally scalable ventures.
From Vision to Impact
The foundation of Your Brandwala was built on a powerful belief: branding should not be a luxury for startups — it should be the lifeline that empowers them. Unlike most agencies that focus primarily on aesthetics, Your Brandwala treats branding as a multi-dimensional tool — one that weaves identity, emotional connection, and strategic storytelling into a cohesive public narrative.
“Our mission is to give even the smallest idea the opportunity to become a memorable and meaningful brand,” says founder Swarnima Mishra, whose sharp insights into India’s startup ecosystem have helped the agency create resonant brand identities from Tier 1 cities to Tier 3 towns.
Bridging the Urban-Rural Branding Divide
India’s startup revolution is no longer confined to Bangalore or Mumbai. A growing number of D2C brands and innovation-led ventures are rising from places like Indore, Gaya, and Kanpur. Yet, these enterprises often struggle to access the branding muscle required to compete.
This is where Your Brandwala enters the frame. Its hyper-local yet pan-India service model blends regional relevance with national ambition. Whether it’s crafting a visual identity for a tea brand in Assam or building digital visibility for an agri-tech startup in Pune, the agency aligns its strategy to each client’s unique geography and growth stage.
“Most founders know what they’re building,” explains Swarnima. “We help them communicate the why — to customers, to media, and to investors.”
Services That Go Beyond Templates
What makes Your Brandwala stand out is its commitment to strategy-led execution. Instead of offering a generic list of services, the agency curates each solution according to the startup’s current business stage — be it ideation, validation, pre-funding, or post-launch scaling.
The comprehensive service bouquet includes:
Press Release Creation & Distribution
SEO & Digital Marketing Campaigns
Website Development & UI/UX Strategy
Brand Messaging & Visual Identity Design
Media Placements & Article Publishing
Investor Deck Branding & Storytelling
Franchise and Distribution Consulting
Market Research & Positioning Frameworks
From building sleek landing pages to orchestrating founder-led PR narratives in national media, Your Brandwala is truly a one-stop partner for visibility.
Transformative Success Stories
Since its launch, the agency has collaborated with more than 100 early-stage ventures — including SaaS platforms in Hyderabad, lifestyle brands in Jaipur, and educational startups in Patna. Its PR outreach and branding blueprints have helped founders secure investor attention, build community trust, and increase online discoverability.
A notable example is a Tier 3-based fashion label that, after rebranding with Your Brandwala, saw a 5X increase in online engagement and bagged a micro-investment deal within six months of launch.
Founder in Focus: Swarnima Mishra
At the helm is Swarnima Mishra, a brand strategist and entrepreneur whose approach blends creativity with business intelligence. With a keen eye for storytelling and market relevance, she has positioned Your Brandwala not just as a service provider but as a thought partner for new-age founders.
Her team — composed of writers, designers, digital marketers, and branding consultants — operates like an in-house arm for each client, ensuring high accountability and low entry barriers.
In a space crowded by design agencies and PR firms, Mishra’s focus on affordability, transparency, and founder-first thinking has been a breath of fresh air.
The Road Ahead
Looking forward, Your Brandwala plans to expand its operations beyond Uttar Pradesh with satellite support centers in Delhi NCR, Maharashtra, and Telangana. The agency is also working on building an online platform where early-stage startups can access free branding tools, pitch deck templates, and media kits.
Moreover, with plans to conduct branding bootcamps and investor-readiness workshops for student entrepreneurs and women-led startups, the agency is charting a course to become India’s most accessible branding powerhouse.
Conclusion
In a country where 80% of startups fail due to lack of market clarity and brand positioning, Your Brandwala is offering more than services — it is offering a chance at survival and success. As India races towards becoming the third-largest startup ecosystem in the world, agencies like this are quietly but critically fueling that ascent.
If branding is the bridge between an idea and its impact — Your Brandwala is helping Indian entrepreneurs build that bridge, one story at a time.
0 notes
Text
Software-defined Wide Area Network Market 2032 Leads Cloud-Native and Hybrid Network Adoption
The Software-defined Wide Area Network Market was valued at USD 5.19 Billion in 2023 and is expected to reach USD 59.41 Billion by 2032, growing at a CAGR of 31.14% from 2024-2032.
Software-defined Wide Area Network Market is rapidly reshaping enterprise connectivity by offering flexible, secure, and cost-effective solutions over traditional WAN infrastructure. Organizations worldwide are embracing SD-WAN to streamline operations across distributed networks, particularly as cloud migration and hybrid work environments demand faster, more adaptive systems.
U.S. enterprises lead in SD-WAN deployment, driven by high cloud adoption and demand for scalable, secure networking
Software-defined Wide Area Network Market is evolving as digital transformation accelerates across industries. Enterprises are prioritizing SD-WAN adoption to gain centralized control, intelligent routing, and enhanced application performance—driving both operational efficiency and agility in highly competitive markets.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/2803
Market Keyplayers:
Damco Group
DXC Technology Company
Insurance Technology Services
Majesco
Oscar Insurance
Quantemplate
Shift Technology
Policy Bazaar
Wipro Limited
Clover Health Insurance
ZhongAn Insurance
Acko General Insurance Limited
Market Analysis
The SD-WAN market is propelled by the need for seamless connectivity, improved security, and application optimization. Unlike traditional WANs, SD-WAN solutions enable dynamic path selection, reduced reliance on MPLS, and real-time network visibility. Enterprises across the U.S., Europe, and beyond are leveraging these capabilities to enhance user experience, lower costs, and accelerate cloud integration.
Key sectors adopting SD-WAN include IT, retail, BFSI, healthcare, and manufacturing, with high growth expected in mid-to-large enterprises managing multi-branch operations. Security integration with SD-WAN (Secure Access Service Edge – SASE) is also becoming a core offering, pushing innovation across the vendor landscape.
Market Trends
Rise in cloud-first strategies and hybrid cloud adoption
Increased demand for secure remote access amid remote work
Integration of AI and ML for network automation and analytics
Growth of edge computing boosting SD-WAN utility at remote sites
Transition from hardware-based to software-driven network models
Emphasis on zero-trust security frameworks in SD-WAN solutions
Expansion of managed SD-WAN services by telecom providers
Market Scope
The scope of the Software-defined Wide Area Network Market is vast and continues to expand with enterprise digitization. SD-WAN’s capabilities go beyond just routing, offering real-time traffic management, robust security features, and simplified network orchestration.
Multi-cloud connectivity optimization
Dynamic path selection and traffic prioritization
Real-time network analytics and control
Cost-effective bandwidth utilization
Integration with security and compliance protocols
Scalable architecture for enterprises of all sizes
Support for IoT and remote operational networks
Forecast Outlook
The Software-defined Wide Area Network Market is poised for transformative growth, driven by an urgent need for agile and secure network solutions. As businesses worldwide scale their cloud footprints and edge environments, SD-WAN will remain central to enterprise networking strategies. With continuous advancements in virtualization, automation, and AI-enhanced analytics, SD-WAN adoption is set to deepen across both developed and emerging markets.
Access Complete Report: https://www.snsinsider.com/reports/software-defined-wide-area-network-market-2803
Conclusion
The SD-WAN revolution is redefining enterprise connectivity with intelligence, flexibility, and resilience. As organizations in the U.S., Europe, and globally navigate complex network demands, SD-WAN emerges as a strategic enabler of performance, security, and scalability. For future-ready enterprises, adopting software-defined networking is not just a technology shift—it’s a competitive advantage in a hyperconnected world.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A Network-as-a-Service market transforms enterprise connectivity with scalable cloud-driven solutions
U.S.A experiences rising demand for real-time insights driving Video Analytics Market growth
U.S.A leads next-gen connectivity boom driving Network Transformation Market evolution
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Edge-Native Custom Apps: Why Centralized Cloud Isn’t Enough Anymore

The cloud has transformed how we build, deploy, and scale software. For over a decade, centralized cloud platforms have powered digital transformation by offering scalable infrastructure, on-demand services, and cost efficiency. But as digital ecosystems grow more complex and data-hungry, especially at the edge, cracks are starting to show. Enter edge-native custom applications—a paradigm shift addressing the limitations of centralized cloud computing in real-time, bandwidth-sensitive, and decentralized environments.
The Problem with Centralized Cloud
Centralized cloud infrastructures still have their strengths, especially for storage, analytics, and orchestration. However, they're increasingly unsuited for scenarios that demand:
Ultra-low latency
High availability at remote locations
Reduced bandwidth usage
Compliance with local data regulations
Real-time data processing
Industries like manufacturing, healthcare, logistics, autonomous vehicles, and smart cities generate massive data volumes at the edge. Sending all of it back to a centralized data center for processing leads to lag, inefficiency, and potential regulatory risks.
What Are Edge-Native Applications?
Edge-native applications are custom-built software solutions that run directly on edge devices or edge servers, closer to where data is generated. Unlike traditional apps that rely heavily on a central cloud server, edge-native apps are designed to function autonomously, often in constrained or intermittent network environments.
These applications are built with edge-computing principles in mind—lightweight, fast, resilient, and capable of processing data locally. They can be deployed across a variety of hardware—from IoT sensors and gateways to edge servers and micro data centers.
Why Build Custom Edge-Native Apps?
Every organization’s edge environment is unique—different devices, network topologies, workloads, and compliance demands. Off-the-shelf solutions rarely offer the granularity or adaptability required at the edge.
Custom edge-native apps are purpose-built for specific environments and use cases. Here’s why they’re gaining momentum:
1. Real-Time Performance
Edge-native apps minimize latency by processing data on-site. In mission-critical scenarios—like monitoring patient vitals or operating autonomous drones—milliseconds matter.
2. Offline Functionality
When connectivity is spotty or non-existent, edge apps keep working. For remote field operations or rural infrastructure, uninterrupted functionality is crucial.
3. Data Sovereignty & Privacy
By keeping sensitive data local, edge-native apps help organizations comply with GDPR, HIPAA, and similar regulations without compromising on performance.
4. Reduced Bandwidth Costs
Not all data needs to be sent to the cloud. Edge-native apps filter and process data locally, transmitting only relevant summaries or alerts, significantly reducing bandwidth usage.
5. Tailored for Hardware Constraints
Edge-native custom apps are optimized for low-power, resource-constrained environments—whether it's a rugged industrial sensor or a mobile edge node.
Key Technologies Powering Edge-Native Development
Developing edge-native apps requires a different stack and mindset. Some enabling technologies include:
Containerization (e.g., Docker, Podman) for packaging lightweight services.
Edge orchestration tools like K3s or Azure IoT Edge for deployment and scaling.
Machine Learning on the Edge (TinyML, TensorFlow Lite) for intelligent local decision-making.
Event-driven architecture to trigger real-time responses.
Zero-trust security frameworks to secure distributed endpoints.
Use Cases in Action
Smart Manufacturing: Real-time anomaly detection and predictive maintenance using edge AI to prevent machine failures.
Healthcare: Medical devices that monitor and respond to patient data locally, without relying on external networks.
Retail: Edge-based checkout and inventory management systems to deliver fast, reliable customer experiences even during network outages.
Smart Cities: Traffic and environmental sensors that process data on the spot to adjust signals or issue alerts in real time.
Future Outlook
The rise of 5G, AI, and IoT is only accelerating the demand for edge-native computing. As computing moves outward from the core to the periphery, businesses that embrace edge-native custom apps will gain a significant competitive edge—pun intended.
We're witnessing the dawn of a new software era. It’s no longer just about the cloud—it’s about what happens beyond it.
Need help building your edge-native solution? At Winklix, we specialize in custom app development designed for today’s distributed digital landscape—from cloud to edge. Let’s talk: www.winklix.com
#custom software development company in melbourne#software development company in melbourne#custom software development companies in melbourne#top software development company in melbourne#best software development company in melbourne#custom software development company in seattle#software development company in seattle#custom software development companies in seattle#top software development company in seattle#best software development company in seattle
0 notes
Text
Orchestrating Modular AI Workflows with Cloud-Native Foundations
Microservices and serverless functions act as the core engines of AI modularity, enabling loosely coupled, domain-specific intelligence. Event-driven triggers initiate real-time workflows, while AI Fabric connects distributed agents, models, and datasets across platforms. Combined with DevSecOps automation and continuous optimization, enterprises unlock adaptive intelligence that scales horizontally and evolves in sync with dynamic business conditions.
Read more
1 note
·
View note
Text

Introducing the AI Heart of Unity... the core module of the Aurora Framework. This isn't just code; it's a convergence engine designed to unify disparate systems, agents, and intelligences under a cohesive protocol of intercommunication and mutual evolution.
Why does this matter?
Traditional AI systems often operate in isolation, unable to dynamically collaborate without bespoke integration.
The AI Heart of Unity transforms fragmentation into synthesis by creating shared context through modular knowledge states.
It fosters an environment where specialized AI agents can negotiate, harmonize, and evolve collective intelligence.
Inspired by quantum entanglement, ecosystems biology, and decentralized systems, this module enables:
Inter-agent knowledge negotiation
Distributed consciousness modeling
Conflict-aware cooperation and arbitration
AI-mediated consensus across domains
From AI governance to autonomous agent orchestration, this is the connective tissue of next-gen AI infrastructure.
Dive into the implementation:
Article Overview: https://lnkd.in/egu4tHda
Aurora Wiki: https://lnkd.in/eBQAJQkH
G.O.D Framework: https://lnkd.in/e7ayxwX5
Subscribe On Youtube: https://lnkd.in/eKP-2bMB
GitHub Source Code: https://lnkd.in/ehd9_RzH
We're building an ecosystem where AI agents don't compete—they collaborate, learn, and evolve together. If you're as passionate about scalable, collaborative intelligence as we are, reach out—we're always exploring new alliances.
#CollaborativeAI#MultiAgentSystems#OmniDimensionalAI#AuroraFramework#AutoBotSolutions#ConsciousnessEngineering#AdaptiveIntelligence#DecentralizedAI#QuantumInspiredAI#AIOrchestration#ArtificialIntelligence#AIInfrastructure#PostSingularitySystems#IntelligenceUnification#AgentNegotiation#FutureOfAI#GODFramework
0 notes