#REST API Security
Explore tagged Tumblr posts
Text
Custom REST API Development Solutions | Connect Infosoft
Connect Infosoft offers top-tier REST API development services, catering to diverse business needs. Our seasoned developers excel in crafting robust APIs that power web and mobile applications, ensuring seamless communication between various systems. We specialize in creating secure, scalable, and high-performance REST APIs that adhere to industry standards and best practices. Whether you need API development from scratch, API integration, or API maintenance services, we have the expertise to deliver tailored solutions. Trust Connect Infosoft for cutting-edge REST API development that enhances your digital ecosystem.
#REST API Development Services#Expert REST API Developers#RESTful API Solutions#Custom REST API Development#REST API Integration Services#REST API Security#Scalable RESTful Services#REST API Consulting#REST API Implementation#REST API Best Practices
0 notes
Text
SQL Injection in RESTful APIs: Identify and Prevent Vulnerabilities
SQL Injection (SQLi) in RESTful APIs: What You Need to Know
RESTful APIs are crucial for modern applications, enabling seamless communication between systems. However, this convenience comes with risks, one of the most common being SQL Injection (SQLi). In this blog, we’ll explore what SQLi is, its impact on APIs, and how to prevent it, complete with a practical coding example to bolster your understanding.

What Is SQL Injection?
SQL Injection is a cyberattack where an attacker injects malicious SQL statements into input fields, exploiting vulnerabilities in an application's database query execution. When it comes to RESTful APIs, SQLi typically targets endpoints that interact with databases.
How Does SQL Injection Affect RESTful APIs?
RESTful APIs are often exposed to public networks, making them prime targets. Attackers exploit insecure endpoints to:
Access or manipulate sensitive data.
Delete or corrupt databases.
Bypass authentication mechanisms.
Example of a Vulnerable API Endpoint
Consider an API endpoint for retrieving user details based on their ID:
from flask import Flask, request import sqlite3
app = Flask(name)
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = f"SELECT * FROM users WHERE id = {user_id}" # Vulnerable to SQLi cursor.execute(query) result = cursor.fetchone() return {'user': result}, 200
if name == 'main': app.run(debug=True)
Here, the endpoint directly embeds user input (user_id) into the SQL query without validation, making it vulnerable to SQL Injection.
Secure API Endpoint Against SQLi
To prevent SQLi, always use parameterized queries:
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = "SELECT * FROM users WHERE id = ?" cursor.execute(query, (user_id,)) result = cursor.fetchone() return {'user': result}, 200
In this approach, the user input is sanitized, eliminating the risk of malicious SQL execution.
How Our Free Tool Can Help
Our free Website Security Checker your web application for vulnerabilities, including SQL Injection risks. Below is a screenshot of the tool's homepage:
Upload your website details to receive a comprehensive vulnerability assessment report, as shown below:
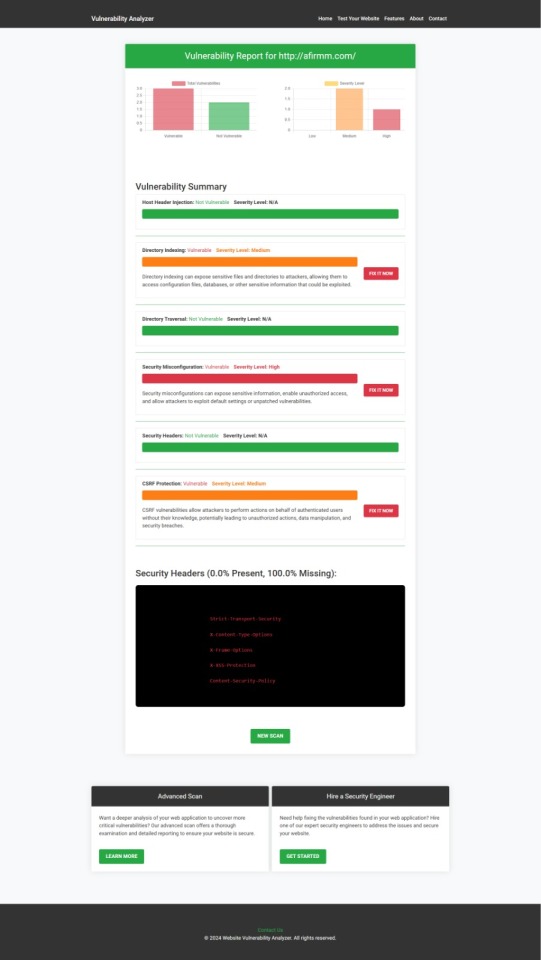
These tools help identify potential weaknesses in your APIs and provide actionable insights to secure your system.
Preventing SQLi in RESTful APIs
Here are some tips to secure your APIs:
Use Prepared Statements: Always parameterize your queries.
Implement Input Validation: Sanitize and validate user input.
Regularly Test Your APIs: Use tools like ours to detect vulnerabilities.
Least Privilege Principle: Restrict database permissions to minimize potential damage.
Final Thoughts
SQL Injection is a pervasive threat, especially in RESTful APIs. By understanding the vulnerabilities and implementing best practices, you can significantly reduce the risks. Leverage tools like our free Website Security Checker to stay ahead of potential threats and secure your systems effectively.
Explore our tool now for a quick Website Security Check.
#cyber security#cybersecurity#data security#pentesting#security#sql#the security breach show#sqlserver#rest api
2 notes
·
View notes
Text
Does learning Java increase my salary?
1. Introduction to the Java Job Market
Java is still one of the hottest programming languages out there. Whether you're just starting or have been coding for a while, knowing Java can really help your career. A common question is: Does learning Java boost my paycheck? The answer is yes—companies really want people who know Java because it's so flexible for web, mobile, and big business apps. Key topics include Java programming, Java developers, and job roles related to it.
Key Point: Java skills are in demand across different industries and can help increase your salary.
2. Java's Popularity and Market Demand
Big names like Amazon, Netflix, and Google use Java because it handles large-scale apps well. So, does learning Java increase my salary? Definitely. Employers will pay a premium for those who are good at Java. Key terms include Java software development, full stack, and backend developer.
Key Point: There’s a strong demand for Java devs, which leads to better pay and job security.
3. Java Skills and Salary Growth
Having Java skills gives you an edge. Companies are looking for people who know frameworks like Spring Boot and tools like Maven. Will learning Java increase my salary? For sure. With the right certifications and experience, you can earn more. And signing up for a Java course in Coimbatore can really help solidify your skills.
Key Point: Specialized Java knowledge can lead to promotions and salary increases.
4. Role of Certifications in Salary Hike
Getting a Java certification is a smart way to stand out. A lot of people choose the Java Full Stack Developer Course in Coimbatore for hands-on practice. Certifications prove your skills, and the answer to the question: Does learning Java bump up my salary? Yes.
Key Point: Java certifications help validate your skills and can lead to better pay.
5. Java Job Roles and Their Pay Scales
Java jobs range from junior developers to senior architects, and each level comes with higher pay. A Java training in Coimbatore can get you ready for roles like Full Stack Developer or Software Engineer. Is there a salary increase if you learn Java? Absolutely, especially for specialized roles.
Key Point: There are many roles in Java, and each offers attractive salary packages.
6. Java vs. Other Programming Languages in Salary
Java developers often earn more than those working with less popular languages. Unlike some newer languages, Java jobs tend to be more stable. Does learning Java mean better pay? Yes, compared to other languages, Java usually offers more consistent salaries.
Key Point: Java's long-standing presence in the industry generally means better pay than many newer languages.
7. Full Stack Java Developer Salary Benefits
Full Stack Java Developers are among the best paid in tech. Taking a Java Full Stack Developer Course in Coimbatore can prepare you for the job market. Will learning Java increase my salary? For sure—especially in full stack roles where you need to be skilled in both backend and frontend.
Key Point: Full Stack Java positions offer top salaries and are in high demand.
8. Java's Role in Enterprise Applications
Java is key for many enterprise systems. Learning enterprise-level Java can really answer the question: Does it help me earn more? Yes. A training program in Coimbatore that teaches things like Hibernate and JSP is worth considering.
Key Point: Skills in enterprise Java can set you up for well-paying jobs.
9. Local Training Institutes and Career Impact
Joining a local Java course in Coimbatore can boost your earnings. These programs offer hands-on projects and guidance from experts. So, does learning Java help with salary? Yes—local training can lead to quicker job growth.
Key Point: Local Java training can speed up your skills and help with job placements.
10. Final Thoughts and Brand Mention
In summary, does learning Java increase my salary? Yes, through certifications, full stack skills, and local training. Consider a reputable place like Xplore It Corp for training in Coimbatore, offering courses designed to meet job market needs.
Key Point: Xplore It Corp provides practical Java courses that can help you earn more.
FAQs:
1. Does learning Java help me earn more with no experience?
Yes. Even beginners can get better job offers after certified Java training.
2. What’s the average salary after a Java course in Coimbatore?
Freshers typically earn around ₹3-5 LPA, and pay can increase significantly after 1-2 years.
3. Is a Java Full Stack Developer Course in Coimbatore worth it?
Definitely. Full stack developers are in demand and usually earn 20-30% more.
4. How long before I see salary benefits after Java training?
Usually, you can expect to see salary increases within 6-12 months after completing the course.
5. Can I switch to Java and expect a pay increase?
Yes. Many people move from non-tech jobs to Java and see a boost in their salary.
#Java programming#Java developer#Java applications#Core Java#Java certification#Java frameworks#Spring Framework#Java full stack#Java backend developer#Java software development#Java training course#Java job roles#Object-oriented programming#Java IDE#Java runtime environment#Java REST API#J2EE#Java vs Python#Java vs JavaScript#Secure Java coding#Java deployment#Java enterprise solutions#Java bootcamp#Java multithreading#Java performance optimization
0 notes
Text
Best Practices for Securing ColdFusion REST APIs with OAuth2 and JWT
#Best Practices for Securing ColdFusion REST APIs with OAuth2 and JWT#Securing ColdFusion REST APIs with OAuth2 and JWT
0 notes
Text
Top 5 OWASP API Security Risks and How to Mitigate Them
APIs are essential but highly targeted attack vectors. The OWASP API Security Top 10 outlines critical risks and mitigation strategies:
Broken Object Level Authorization (BOLA)
APIs often expose endpoints that attackers manipulate to access unauthorized resources.
Mitigation: Implement strict authorization checks and ensure unique object IDs are validated server-side.
Broken Authentication
Weak authentication mechanisms can allow attackers to compromise accounts.
Mitigation: Enforce strong authentication methods, including multi-factor authentication (MFA), and use secure token management practices.
Excessive Data Exposure
APIs sometimes expose unnecessary data in response payloads.
Mitigation: Ensure responses only contain required fields, and sensitive information is masked or omitted.
Lack of Rate Limiting
API testing without rate-limiting are vulnerable to brute-force and denial-of-service attacks.
Mitigation: Apply rate limits and implement CAPTCHA mechanisms to prevent automated abuse.
Security Misconfiguration
Misconfigured headers, permissions, or outdated components create vulnerabilities.
Mitigation: Regularly review configurations, apply security patches, and follow secure coding practices.
Conclusion
Understanding and addressing these risks is vital to securing APIs. Proactive testing and adherence to OWASP guidelines ensure robust defenses against potential threats.
#api test automation#rest assured api testing#api automation#api automation testing tools#api test tool#api automation tools#rest api automation#api security testing#rest api testing automation#best tool for api automation#api testing in automation#automation testing for api
0 notes
Text
Conectando uma Aplicação Spring Boot com Banco de Dados MySQL
O que é o Spring Boot e como ele facilita o desenvolvimento de aplicações Java O Spring Boot é uma extensão do popular framework Spring, projetado para simplificar o processo de desenvolvimento de aplicações Java. Ele elimina a necessidade de configurações complexas e torna o processo de desenvolvimento mais rápido e eficiente. Com Spring Boot, você pode criar aplicações prontas para produção…
#application.properties#autenticação spring boot#conexão com mysql#configurar banco de dados spring boot#controller spring boot#criar aplicação spring boot#criar banco de dados mysql#h2 database#jdbc spring boot#mysql#persistir dados spring boot#repository jpa#repository spring boot#rest api spring boot#spring boot#spring boot configuração#spring boot crud#spring boot exemplo#spring boot exemplo com mysql#spring boot security#spring boot tutorial#spring data jpa#tutorial spring boot mysql#user entity
0 notes
Text
Implementing Throttling and Rate Limiting in Django REST Framework
Introduction:In today’s API-driven world, ensuring that your API is secure and efficient is crucial. One way to achieve this is by implementing throttling and rate limiting in your Django REST Framework (DRF) applications. Throttling controls the rate at which clients can make requests to your API, helping to prevent abuse and ensuring that your server resources are not overwhelmed by excessive…
0 notes
Text

Voice Call Software - SMPPCenter.com | OBD Voice Call Solutions
Discover SMPPCenter.com's advanced OBD voice call software. Rent or buy licensed software to send OTP voice calls, connect with HTTP vendors, use Text to Speech, and more. Engage globally with high throughput, secure platform, and comprehensive management tools.
#voice call software#OBD voice call#SMPPCenter.com#OTP voice call#Text to Speech#HTTP vendor integration#Restful API#audio libraries#retry mechanism#local block numbers filtering#no downtime#high throughput TPS#NCPR scrubbing#secured platform#global engagement
0 notes
Text
How Can Legacy Application Support Align with Your Long-Term Business Goals?
Many businesses still rely on legacy applications to run core operations. These systems, although built on older technology, are deeply integrated with workflows, historical data, and critical business logic. Replacing them entirely can be expensive and disruptive. Instead, with the right support strategy, these applications can continue to serve long-term business goals effectively.

1. Ensure Business Continuity
Continuous service delivery is one of the key business objectives of any enterprise. Maintenance of old applications guarantees business continuity, which minimizes chances of business interruption in case of software malfunctions or compatibility errors. These applications can be made to work reliably with modern support strategies such as performance monitoring, frequent patching, system optimization, despite changes in the rest of the system changes in the rest of the systems. This prevents the lost revenue and downtime of unplanned outages.
2. Control IT Costs
A straight replacement of the legacy systems is a capital intensive process. By having support structures, organizations are in a position to prolong the life of such applications and ensure an optimal IT expenditure. The cost saved can be diverted into innovation or into technologies that interact with the customers. An effective support strategy manages the total cost of ownership (TCO), without sacrificing performance or compliance.
3. Stay Compliant and Secure
The observance of industry regulations is not negotiable. Unsupported legacy application usually fall out of compliance with standards changes. This is handled by dedicated legacy application support which incorporates security updates, compliances patching and audit trails maintenance. This minimizes the risks of regulatory fines and reputational loss as well as governance and risk management objectives.
4. Connect with Modern Tools
Legacy support doesn’t mean working in isolation. With the right approach, these systems can connect to cloud platforms, APIs, and data tools. This enables real-time reporting, improved collaboration, and more informed decision-making—without requiring full system replacements.
5. Protect Business Knowledge
The legacy systems often contain years of institutional knowledge built into workflows, decision trees, and data architecture. They should not be abandoned early because vital operational insights may be lost. Maintaining these systems enables enterprises to keep that knowledge and transform it into documentation or reusable code aligned with ongoing digital transformation initiatives.
6. Support Scalable Growth
Well-supported legacy systems can still grow with your business. With performance tuning and capacity planning, they can handle increased demand and user loads. This keeps growth on track without significant disruption to IT systems.
7. Increase Flexibility and Control
Maintaining legacy application—either in-house or through trusted partners—gives businesses more control over their IT roadmap. It avoids being locked into aggressive vendor timelines and allows change to happen on your terms.
Legacy applications don’t have to be a roadblock. With the right support model, they become a stable foundation that supports long-term goals. From cost control and compliance to performance and integration, supported legacy systems can deliver measurable value. Specialized Legacy Application Maintenance Services are provided by service vendors such as Suma Soft, TCS, Infosys, Capgemini, and HCLTech, to enable businesses to get the best out of their current systems, as they prepare to transform in the future. Choosing the appropriate partner will maintain these systems functioning, developing and integrated with wider business strategies.
#BusinessContinuity#DigitalTransformation#ITStrategy#EnterpriseIT#BusinessOptimization#TechLeadership#ScalableSolutions#SmartITInvestments
3 notes
·
View notes
Text
What Are Direct Carrier Appointments? 5 Vital Insights for Agencies
Gaining a strong grasp of direct carrier appointments can significantly elevate how your insurance agency operates.
In simple terms, it’s a formal relationship where an insurer authorizes an agency to sell its policies directly — cutting out the middle layers.
But why is this such a big deal, and how does it shape your agency’s future?
Here are five key insights into direct appointments and why they’re so beneficial for your business.
Request a Demo

Insight #1: Direct Carrier Appointments Offer Wider Product Access One of the most valuable benefits of a direct appointment is the immediate access to a broader range of the carrier’s insurance products.
This enables your agency to provide clients with more tailored options, accommodating varied coverage needs and preferences.
Such diversification strengthens your service portfolio, makes your agency more appealing to a broader audience, and positions you more competitively in the marketplace.
Over time, this enhanced market access contributes to stronger revenue generation and business stability.
Insight #2: Direct Appointments Can Improve Earnings When working directly with carriers, agencies often avoid the layers of commissions that come with using intermediaries or aggregators.
This means you can receive a higher portion of the premium revenue, leading to better profit margins per policy.
With increased commission percentages and potential for negotiating favorable rates, your agency’s income per client improves — supporting financial growth over the long term.
This revenue advantage is key to building a scalable and profitable business model.
Insight #3: Carriers Require Agencies to Meet Eligibility Standards Insurers typically evaluate agencies before granting direct appointments, ensuring the partnership is secure and mutually beneficial.
Common criteria may include years of operational history, proof of production capabilities, and compliance with regulatory standards.
Meeting these benchmarks shows that your agency is trustworthy, productive, and capable of representing the carrier’s interests responsibly.
These requirements help maintain quality and safeguard the insurer's brand and policyholders.
Insight #4: Access to Unique Products Can Set You Apart With a direct appointment, you may gain access to exclusive insurance plans or services that aren’t distributed through indirect channels.
These exclusive offerings allow you to provide value that competitors may lack — fulfilling niche market needs and attracting high-intent clients.
Your agency becomes a go-to source for specialized or higher-tier solutions, strengthening your position as a trusted advisor in the industry.
This exclusivity enhances your credibility and helps retain loyal clients looking for premium options.
Insight #5: Appointments Must Be Actively Maintained Receiving a direct appointment is just the start — agencies must work consistently to keep it active.
That includes hitting required production targets, delivering top-tier service, following carrier policies, and ensuring that records stay updated — including changes to staff.
Failure to maintain performance or compliance can jeopardize the relationship and result in losing the appointment and its benefits.
Ongoing communication and alignment with the carrier are key to keeping the partnership strong and sustainable.

Manage Appointments Easily with Agenzee Meet Agenzee — your all-in-one insurance compliance platform that redefines how agencies handle licenses and appointments.
No more juggling spreadsheets or missing renewal dates. Agenzee helps your agency stay efficient and compliant with features like:
All-in-One License & Appointment Dashboard
Automated Alerts Before License Expiry
Simplified License Renewal Tools
New Appointment Submission & Tracking
Termination Management Features
CE (Continuing Education) Hour Tracking
Robust REST API Integration
Mobile Access for Producers on the Go
With Agenzee, your agency can minimize administrative burdens and maximize focus on growth.
Request a free demo and see how easy compliance management can be!
2 notes
·
View notes
Text
Crafting Web Applications For Businesses Which are Responsive,Secure and Scalable.
Hello, Readers!
I’m Nehal Patil, a passionate freelance web developer dedicated to building powerful web applications that solve real-world problems. With a strong command over Spring Boot, React.js, Bootstrap, and MySQL, I specialize in crafting web apps that are not only responsive but also secure, scalable, and production-ready.
Why I Started Freelancing
After gaining experience in full-stack development and completing several personal and academic projects, I realized that I enjoy building things that people actually use. Freelancing allows me to work closely with clients, understand their unique challenges, and deliver custom web solutions that drive impact.
What I Do
I build full-fledged web applications from the ground up. Whether it's a startup MVP, a business dashboard, or an e-commerce platform, I ensure every project meets the following standards:
Responsive: Works seamlessly on mobile, tablet, and desktop.
Secure: Built with best practices to prevent common vulnerabilities.
Scalable: Designed to handle growth—be it users, data, or features.
Maintainable: Clean, modular code that’s easy to understand and extend.
My Tech Stack
I work with a powerful tech stack that ensures modern performance and flexibility:
Frontend: React.js + Bootstrap for sleek, dynamic, and responsive UI
Backend: Spring Boot for robust, production-level REST APIs
Database: MySQL for reliable and structured data management
Bonus: Integration, deployment support, and future-proof architecture
What’s Next?
This blog marks the start of my journey to share insights, tutorials, and case studies from my freelance experiences. Whether you're a business owner looking for a web solution or a fellow developer curious about my workflow—I invite you to follow along!
If you're looking for a developer who can turn your idea into a scalable, secure, and responsive web app, feel free to connect with me.
Thanks for reading, and stay tuned!
2 notes
·
View notes
Text
Web to Mobile: Building Seamless Apps with .NET"
.NET is a effective, flexible, and open-supply developer platform created with the aid of Microsoft. It enables the creation of a huge range of applications—from computing device to cellular, net, cloud, gaming, and IoT. Over the years, .NET has evolved substantially and has become one of the maximum extensively used frameworks inside the software improvement enterprise.
Dot Net Programming Language

A Brief History of .NET
The .NET Framework become first delivered through Microsoft in the early 2000s. The original cause turned into to offer a steady item-oriented programming surroundings regardless of whether code became stored and finished locally, remotely, or via the internet.
Over time, Microsoft developed .NET right into a cross-platform, open-supply framework. In 2016, Microsoft launched .NET Core, a modular, high-performance, cross-platform implementation of .NET. In 2020, the company unified all its .NET technologies beneath one umbrella with the discharge of .NET five, and later persisted with .NET 6, .NET 7, and past.
Today, the unified platform is actually called .NET, and it allows builders to build apps for Windows, macOS, Linux, iOS, Android, and greater using a single codebase.
Key Features of .NET
1. Cross-Platform Development
One of the maximum tremendous features of present day .NET (publish .NET Core) is its ability to run on a couple of platforms. Developers can construct and deploy apps on Windows, Linux, and macOS with out enhancing their codebases.
2. Multiple Language Support
.NET supports numerous programming languages, together with:
C# – the maximum extensively used language in .NET development
F# – a purposeful-first programming language
Visual Basic – an smooth-to-analyze language, regularly used in legacy programs
This multilingual capability allows developers to pick out the nice language for their precise use cases.
3. Extensive Library and Framework Support
.NET offers a comprehensive base magnificence library (BCL) and framework libraries that aid the whole lot from record studying/writing to XML manipulation, statistics get entry to, cryptography, and extra.
Four. ASP.NET for Web Development
ASP.NET is a part of the .NET platform specially designed for net improvement. ASP.NET Core, the cross-platform model, permits builders to build scalable internet APIs, dynamic web sites, and actual-time packages the usage of technology like SignalR.
5. Rich Development Environment
.NET integrates seamlessly with Visual Studio, one of the most function-wealthy integrated development environments (IDEs) available. Visual Studio offers capabilities together with IntelliSense, debugging tools, challenge templates, and code refactoring.
6. Performance and Scalability
.NET is thought for high performance and scalability, especially with its guide for asynchronous programming using async/wait for and its Just-In-Time (JIT) compilation.
7. Secure and Reliable
.NET presents sturdy safety features, including code get entry to security, role-based protection, and cryptography training. It also handles reminiscence management thru rubbish series, minimizing reminiscence leaks.
Common Applications Built with .NET
1. Web Applications
With ASP.NET Core, builders can create cutting-edge, scalable internet programs and RESTful APIs. Razor Pages and Blazor are technology within ASP.NET Core that help server-facet and purchaser-facet rendering.
2. Desktop Applications
Using Windows Forms or Windows Presentation Foundation (WPF), builders can build conventional computing device applications. .NET MAUI (Multi-platform App UI) now extends this functionality to move-platform computer and cellular programs.
3. Mobile Applications
Through Xamarin (now incorporated into .NET MAUI), developers can create native mobile applications for Android and iOS the usage of C#.
4. Cloud-Based Applications
.NET is nicely-acceptable for cloud development, in particular with Microsoft Azure. Developers can build cloud-local apps, serverless capabilities, and containerized microservices the usage of Docker and Kubernetes.
5. IoT Applications
.NET helps Internet of Things (IoT) development, allowing builders to construct applications that engage with sensors and gadgets.
6. Games
With the Unity sport engine, which helps C#, developers can use .NET languages to create 2D, three-D, AR, and VR games.
Components of .NET
1. .NET SDK
The Software Development Kit includes everything had to build and run .NET packages: compilers, libraries, and command-line tools.
2. CLR (Common Language Runtime)
It handles reminiscence control, exception managing, and rubbish collection.
Three. BCL (Base Class Library)
The BCL offers center functionalities including collections, record I/O, records kinds, and extra.
4. NuGet
NuGet is the package manager for .NET. It lets in builders to install, manage, and share libraries without problems.
Modern .NET Versions
.NET five (2020): Unified the .NET platform (Core + Framework)
.NET 7 (2022): Further overall performance enhancements and more desirable APIs
.NET 8 (2023): Continued attention on cloud-native, cellular, and web improvement
Advantages of Using .NET
Cross-platform assist – construct as soon as, run everywhere
Large developer network – widespread sources, libraries, and frameworks
Robust tooling – especially with Visual Studio and JetBrains Rider
Active improvement – backed by using Microsoft and open-source community
Challenges and Considerations
Learning curve – particularly for beginners due to its giant atmosphere
Legacy framework – older .NET Framework tasks aren't like minded with .NET Core or more recent variations without migration
Platform differences – sure APIs or libraries might also behave in a different way throughout operating systems
Getting Started with .NET
To begin growing with .NET:
Install the .NET SDK from the legitimate .NET internet site.
Create a new project: Use the dotnet new command or Visual Studio templates.
Write code: Develop your logic the usage of C#, F#, or VB.NET.
#btech students#bca students#online programming courses#offline institute programming courses#regular colleges university#Dot Net Programming Language
2 notes
·
View notes
Text
Integrating Third-Party Tools into Your CRM System: Best Practices
A modern CRM is rarely a standalone tool — it works best when integrated with your business's key platforms like email services, accounting software, marketing tools, and more. But improper integration can lead to data errors, system lags, and security risks.

Here are the best practices developers should follow when integrating third-party tools into CRM systems:
1. Define Clear Integration Objectives
Identify business goals for each integration (e.g., marketing automation, lead capture, billing sync)
Choose tools that align with your CRM’s data model and workflows
Avoid unnecessary integrations that create maintenance overhead
2. Use APIs Wherever Possible
Rely on RESTful or GraphQL APIs for secure, scalable communication
Avoid direct database-level integrations that break during updates
Choose platforms with well-documented and stable APIs
Custom CRM solutions can be built with flexible API gateways
3. Data Mapping and Standardization
Map data fields between systems to prevent mismatches
Use a unified format for customer records, tags, timestamps, and IDs
Normalize values like currencies, time zones, and languages
Maintain a consistent data schema across all tools
4. Authentication and Security
Use OAuth2.0 or token-based authentication for third-party access
Set role-based permissions for which apps access which CRM modules
Monitor access logs for unauthorized activity
Encrypt data during transfer and storage
5. Error Handling and Logging
Create retry logic for API failures and rate limits
Set up alert systems for integration breakdowns
Maintain detailed logs for debugging sync issues
Keep version control of integration scripts and middleware
6. Real-Time vs Batch Syncing
Use real-time sync for critical customer events (e.g., purchases, support tickets)
Use batch syncing for bulk data like marketing lists or invoices
Balance sync frequency to optimize server load
Choose integration frequency based on business impact
7. Scalability and Maintenance
Build integrations as microservices or middleware, not monolithic code
Use message queues (like Kafka or RabbitMQ) for heavy data flow
Design integrations that can evolve with CRM upgrades
Partner with CRM developers for long-term integration strategy
CRM integration experts can future-proof your ecosystem
#CRMIntegration#CRMBestPractices#APIIntegration#CustomCRM#TechStack#ThirdPartyTools#CRMDevelopment#DataSync#SecureIntegration#WorkflowAutomation
2 notes
·
View notes
Text
The Role of Mocking in API Automation Testing
Introduction to Mocking in API Testing
Begin by defining mocking as the process of simulating an API's behavior to isolate testing. Explain its importance in API automation for scenarios where real APIs are unavailable, costly, or unstable.
Why Mocking is Essential in API Automation
Unavailability of APIs
Highlight situations where APIs are under development or dependent systems are inaccessible. Mocking allows testing to continue in parallel.
Handling Rate Limits or Costs
Mention scenarios with third-party APIs that have usage restrictions or incur significant costs. Mocks bypass these limitations.
Isolating API Dependencies
Mocking eliminates issues caused by unstable or unpredictable dependent API testing, ensuring reliable test execution.
Implementing Mocking in API Automation
Tools for Mocking
Introduce popular tools like WireMock, Postman, and Mockoon, which simplify mock creation.
Setting Up Mock APIs
Explain how to create mock endpoints that mimic real API responses with defined status codes, headers, and payloads.
Using Mocks in Automation Frameworks
Show how to integrate mocks into testing workflows for seamless execution.
Benefits of Mocking
Discuss advantages such as improved test stability, faster test execution, and early defect detection.
Conclusion Reiterate that mocking is a critical strategy in API automation, enabling robust testing even in complex or constrained environments.
#api test automation#api automation#api automation tools#api security testing#rest api testing automation#best tool for api automation#api testing in automation#automation testing for api#api testing and automation
0 notes
Text
Alright, Google is zero help with this (every variant of what I'm asking for just floods me with SEO-optimized results for exactly the opposite of what I'm looking for), so...
In my day job, I'm a web developer, mainly. I've got a good deal of experience working with HTML/CSS/JS for front-end UI development, so when I decided to build a content management system for my game project- which is going to be a bunch of pages and menus and buttons and selectors and stuff- it seemed like a natural choice to just build it as a web app, using those skills I already have. It wouldn't be hosted anywhere- the idea would be to just load index.html on localhost and work from a local browser window offline- but I figured I could prototype it pretty quickly with good old-fashioned divs and CSS.
Eeeeexcept I can't do that, actually. The purpose of the app is to manage a directory full of a bunch of structured custom content files- maps, units, sprites, yada yada yada, and lots of small individual changes will happen to a lot of different file resources. Browsers are bad for this, because they rightly have a lot of security protections against webpages accessing the user's filesystem. While I thought the File System API would just let me prompt the user for access to the content folder, and then just work with those files freely from there, that... is apparently a very experimental feature that Firefox doesn't support yet. Seems like a bad choice of thing to rest the entire functionality of the app on.
So what I'm looking for is... is there a framework somewhere for building desktop apps (so I can access local files easily) that uses HTML/CSS/JS for front-end UI development? Something like a browser that's not a browser and doesn't have those inherent security protections to get around?
41 notes
·
View notes
Text
Django REST Framework: Authentication and Permissions
Secure Your Django API: Authentication and Permissions with DRF
Introduction Django REST Framework (DRF) is a powerful toolkit for building Web APIs in Django. One of its key features is the ability to handle authentication and permissions, ensuring that your API endpoints are secure and accessible only to authorized users. This article will guide you through setting up authentication and permissions in DRF, including examples and…
#custom permissions#Django API security#Django JWT integration#Django REST Framework#DRF authentication#Python web development#token-based authentication
0 notes