#SQL Server 2016
Explore tagged Tumblr posts
Text
How to install Endpoint Configuration Manager on HyperV VM
Microsoft integrates Configuration Manager into the Intune family of products, offering an integrated solution for managing all devices. This integration simplifies licensing and eliminates the need for complex migrations. Users can continue leveraging their existing Configuration Manager investments while tapping into the capabilities of the Microsoft cloud at their own pace. This is a…

View On WordPress
#ConfigMgr#Configuration Manager#ECM Installation#Extend Active Directory AD Schema#Microsoft Endpoint Configuration Manager#Microsoft SQL Server Management Studio#Microsoft Windows#SQl Server 2022#SQL Server Management Studio#SQL Server Management Studio (SSMS)#Windows#Windows 10#Windows 11#Windows ADK#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
VPS Chạy Hệ Điều Hành Windows - Giải Pháp Tối Ưu Cho Doanh Nghiệp Và Cá Nhân
Trong thời đại số hóa mạnh mẽ, nhu cầu sử dụng máy chủ ảo (VPS - Virtual Private Server) ngày càng gia tăng. Trong số các loại VPS, VPS chạy hệ điều hành Windows là lựa chọn phổ biến, đặc biệt với các doanh nghiệp, lập trình viên, và người dùng cần môi trường làm việc quen thuộc và dễ sử dụng. Vậy VPS Windows là gì? Tại sao nên chọn loại VPS này? Hãy cùng tìm hiểu chi tiết trong bài viết dưới đây.
VPS Windows là gì?
VPS (Virtual Private Server) là một máy chủ ảo được tạo ra từ một máy chủ vật lý, hoạt động độc lập với các VPS khác. Khi VPS sử dụng hệ điều hành Windows, nó được gọi là VPS Windows. Điều này có nghĩa là máy chủ ảo này được cài đặt và vận hành trên nền tảng Windows Server (ví dụ: Windows Server 2016, 2019, 2022…).
Người dùng có thể điều khiển VPS Windows từ xa thông qua Remote Desktop Protocol (RDP), cho phép truy cập và quản lý như đang sử dụng một máy tính cá nhân.
Ưu điểm của VPS chạy hệ điều hành Windows
Giao diện thân thiện, dễ sử dụng
Một trong những điểm mạnh lớn nhất của VPS Windows chính là giao diện đồ họa quen thuộc. Với những ai đã quen sử dụng máy tính Windows, việc sử dụng VPS sẽ trở nên dễ dàng hơn nhiều so với VPS Linux, vốn chủ yếu dùng dòng lệnh để thao tác.
Hỗ trợ phần mềm chuyên dụng
Nhiều phần mềm quản lý doanh nghiệp, kế toán, quản lý bán hàng hoặc ứng dụng desktop được thiết kế để chạy trên nền tảng Windows. Với VPS Windows, người dùng có thể cài đặt và sử dụng những phần mềm này một cách ổn định mà không lo vấn đề tương thích.
Truy cập từ xa linh hoạt
Thông qua giao thức RDP, người dùng có thể truy cập VPS từ bất cứ đâu, bất cứ thiết bị nào. Bạn chỉ cần một thiết bị kết nối Internet là đã có thể làm việc trên máy chủ của mình như đang ngồi trực tiếp trước màn hình.
Tích hợp Active Directory và các dịch vụ Microsoft
VPS Windows có khả năng tích hợp với các dịch vụ như Active Directory, Microsoft Exchange, IIS (Internet Information Services) hay Microsoft SQL Server. Điều này cực kỳ thuận tiện cho các doanh nghiệp muốn xây dựng hạ tầng CNTT nội bộ trên nền tảng Microsoft.
Khi nào nên sử dụng VPS Windows?
VPS Windows phù hợp với nhiều đối tượng người dùng:
Doanh nghiệp sử dụng phần mềm nội bộ: Nhiều công ty dùng các phần mềm kế toán, ERP, CRM chạy trên nền Windows.
Nhà phát triển phần mềm: Lập trình viên cần môi trường để test hoặc triển khai phần mềm .NET, ASP.NET, C#...
Người quản trị website: VPS Windows có thể được dùng để chạy các website sử dụng IIS hoặc các nền tảng yêu cầu Windows.
Người dùng cá nhân: Muốn làm việc từ xa, xử lý dữ liệu hoặc đơn giản là chạy các phần mềm không tương thích với hệ điều hành khác.
Nhược điểm cần lưu ý
Mặc dù có nhiều ưu điểm, VPS chạy Windows cũng có một số điểm hạn chế:
Chi phí cao hơn: Bản quyền Windows Server khiến giá thuê VPS Windows thường cao hơn VPS Linux.
Yêu cầu tài nguyên cao hơn: Hệ điều hành Windows và các ứng dụng liên quan thường tiêu tốn nhiều RAM và CPU hơn.
Bảo mật: Vì là nền tảng phổ biến nên Windows cũng là mục tiêu của nhiều cuộc tấn công mạng. Tuy nhiên, nếu được cấu hình và cập nhật đầy đủ, VPS Windows vẫn có thể rất an toàn.
Cách chọn VPS Windows phù hợp
Khi lựa chọn VPS Windows, bạn nên xem xét một số yếu tố sau:
Cấu hình: Xác định nhu cầu sử dụng để chọn cấu hình CPU, RAM, dung lượng ổ cứng phù hợp.
Phiên bản Windows: Chọn phiên bản Windows Server tương thích với phần mềm bạn muốn sử dụng.
Vị trí máy chủ: Chọn máy chủ gần khu vực người dùng để tăng tốc độ truy cập.
Nhà cung cấp uy tín: Ưu tiên các đơn vị có hỗ trợ kỹ thuật 24/7, cam kết uptime cao, có khả năng mở rộng linh hoạt.
Một số ứng dụng thực tế của VPS Windows
Chạy phần mềm quản lý kế toán như MISA, Fast, Bravo…
Triển khai các website viết bằng ASP.NET hoặc sử dụng SQL Server.
Thiết lập Remote Desktop cho nhóm làm việc từ xa.
Lưu trữ dữ liệu và chia sẻ tệp tin nội bộ trong doanh nghiệp.
Tạo môi trường học tập hoặc thử nghiệm các phần mềm mới.
Tổng kết
VPS chạy hệ điều hành Windows là giải pháp lý tưởng cho những ai cần một môi trường làm việc ổn định, dễ sử dụng và tương thích với các phần mềm quen thuộc. Dù có mức chi phí cao hơn so với các loại VPS khác, nhưng lợi ích mà nó mang lại hoàn toàn xứng đáng, đặc biệt với những người dùng ưu tiên sự tiện lợi và hiệu quả.
Nếu bạn đang tìm kiếm một công cụ mạnh mẽ để hỗ trợ công việc, phát triển phần mềm, hoặc đơn giản là vận hành hệ thống từ xa, VPS Windows chắc chắn là lựa chọn đáng cân nhắc.
Thông tin chi tiết: https://vndata.vn/vps-windows-gia-re/
0 notes
Text
Maximize Business Performance with a Dedicated Server with Windows – Delivered by CloudMinister Technologies
In the era of digital transformation, having full control over your hosting environment is no longer optional—it’s essential. Businesses that prioritize security, speed, and customization are turning to Dedicated servers with Windows as their go-to infrastructure solution. When you choose CloudMinister Technologies, you get more than just a server—you get a strategic partner dedicated to your growth and uptime.
What is a Dedicated Server with Windows?
A Dedicated server with Windows is a physical server exclusively assigned to your organization, running on the Windows Server operating system. Unlike shared hosting or VPS, all the resources—CPU, RAM, disk space, and bandwidth—are reserved solely for your use. This ensures maximum performance, enhanced security, and total administrative control.
Key Benefits of a Dedicated Server with Windows
1. Total Resource Control
All server resources are 100% yours. No sharing, no interference—just consistent, high-speed performance tailored to your workload.
2. Full Administrative Access
You get full root/administrator access, giving you the freedom to install applications, manage databases, configure settings, and automate processes.
3. Better Compatibility with Microsoft Ecosystem
Run all Microsoft applications—SQL Server, Exchange, SharePoint, IIS, and ASP.NET—without compatibility issues.
4. Advanced Security Options
Use built-in Windows security features like BitLocker encryption, Windows Defender, and group policy enforcement to keep your data safe.
5. Remote Desktop Capability
Access your server from anywhere using Remote Desktop Protocol (RDP)—ideal for managing operations on the go.
6. Seamless Software Licensing
With CloudMinister Technologies, Windows licensing is bundled with your plan, ensuring legal compliance and cost savings.
7. Scalability Without Downtime
Need to upgrade? Add more RAM, switch to SSDs, or increase bandwidth—without migrating to another server or experiencing downtime.
Why Choose CloudMinister Technologies for Windows Dedicated Servers?
At CloudMinister Technologies, we combine performance with personalized service. Our infrastructure is engineered to support the demands of startups, growing businesses, and large enterprises a like.
Our Competitive Edge:
100% Custom Configurations Choose your ideal specs or consult with our engineers to build a server optimized for your application or business model.
Free Server Management We manage your OS, patches, updates, firewalls, backups, and security—so you can focus on your business, not your backend.
High Uptime Guarantee With our 99.99% uptime commitment and redundant systems, your server stays online—always.
Modern Data Centers All servers are housed in Tier III or higher data centers with 24/7 surveillance, redundant power, cooling, and robust firewalls.
Rapid Deployment Get your Dedicated server with Windows up and running quickly with pre-configured setups or same-day custom deployment.
Dedicated 24/7 Support Our expert team is available any time, day or night, to troubleshoot, consult, or provide emergency support.
Additional Features to Boost Your Operations
Automated Daily Backups Protect your data and ensure business continuity with secure, regular backups.
DDoS Protection Stay secure with advanced protection from distributed denial-of-service attacks.
Multiple OS Choices Prefer Windows 2016, 2019, or 2022? Choose what suits your stack best.
Control Panel Options Get support for cPanel, Plesk, or a custom dashboard for simplified server management.
Private VLAN and IPMI Access Enjoy better isolation and direct console access for advanced troubleshooting.
Call to Action: Start with CloudMinister Technologies Today
Your business deserves more than just a server—it deserves a partner who understands performance, uptime, and scalability. With a Dedicated server with Windows from CloudMinister Technologies, you're guaranteed a seamless hosting experience backed by unmatched support and reliability.
Don’t wait for slow speeds or security issues to hold you back.
Upgrade to a Dedicated Windows Server today.
Visit www.cloudminister.com to view plans Or contact our solutions team at [email protected] to discuss your custom setup.
0 notes
Text
Step-by-Step-Guide-to-IT Research
IT Researches is an international information technology company and computer research center headquartered in the United Kingdom. Through its official Iranian representative, Rayan Net Co., it offers a wide range of AI-powered services and solutions to businesses and organizations across Iran and neighboring countries. The company is recognized for its official partnerships with major global tech firms such as Microsoft, IBM, and Amazon.
The website represents IT Researches, an international IT and computer science research company headquartered in the UK. The company offers a wide range of AI-driven commercial and scientific services to organizations worldwide, including the provision of genuine Microsoft software licenses and various AI-based solutions.
Company Overview 1.IT Researches specializes in delivering advanced AI-driven services, including:
2.Image, speech, and natural language processing
3.Machine learning and data mining
4.Biometric identification and steganography
5.Expert systems, fuzzy logic, and business intelligence (BI) solutions
6.Big data analytics
7.Sales and demand forecasting
Additionally, the company provides services for company registration and book publishing in Europe and the UK.
Microsoft Software Licensing In Iran, IT Researches, through Rayan Net Co., serves as the official distributor of genuine Microsoft products. Their offerings include:
Windows 10 and 11
Windows Server editions (2016, 2019, 2022)
Microsoft Office suites (2016, 2019, 2021, Office 365, Office for Mac)
SQL Server, System Center, SharePoint, Project Server, Exchange Server
Project, Visio, Visual Studio
The company emphasizes the importance of using licensed software to ensure system stability, security, and access to updates, especially in environments where pirated software is prevalent.
Global Presence IT Researches operates internationally, with branches in multiple countries, providing AI-based commercial and scientific services to companies and organizations worldwide. Their collaborations with leading IT companies enhance their capability to deliver cutting-edge solutions.
📞 Contact Information Website:
Iran Office: 021-28422
UK Office: (+44)-200-888-0272
Russia Office: (+7)-499-322-9824
IT Research
0 notes
Text
One of the oldest forms of internet communication, message boards and forums are just as popular today as they have ever been. As of 2016, there were an estimated 110,000 separate forum and message board providers across the world, ranging from social media style sites like Reddit to free bulletin software built on phpBB. Market Share Of Various Popular Forum Platforms Studies show that premium (paid-for) forum software still takes the lead when it comes to setting up a discussion website. In fact, leading premium provider vBulletin takes an estimated 50% of the total market. This service is essentially a template site with fully customizable bulletin board platforms, available for developers to manipulate and innovate as desired. [Credit: BuiltWith.com via Quora] However, there has been a marked growth in the amount of open source software which enables discussion board creation, and many developers are creating their own message boards for commercial, social and personal use. We take a look at the top free platforms on the market today, tried and tested by industry experts. Five Of The Best Free Forum Platforms phpBB Experts agree that you will struggle to beat phpBB for functionality and ease of use. This simple PHP bulletin board application is perfect for fan discussions, photo threads, advice pages and general messaging between users. It has millions of global users and is fully compatible with PostgreSQL, SQLite, MySQL, Microsoft SQL Server, as well as being open to editing through the General Public Licence There are lots of opportunities to play with it and customize it, with no need for seeking permission first. Threads can be split and messages can be archived for posterity, and the site maintains a template database with modifications and styles that are open for users to play around with. bbPress Forums WordPress has been the leading platform for blogging for many years. There are millions of sites across the Web which use the publishing software for their business sites, blogs and even e-commerce - and now the team is adding forum sites to its range of products. bbPress Forums is a WordPress-style bulletin board creation tool, which has the smooth and seamless transitions and roomy capacity that keeps the site fast and user-friendly. Just like with the blogs, bbPress begins as a free service and has the option of a Premium or Business upgrade, with additional custom features and templates for subscribers. It is also one of the most secure free programs, with additional safety features to prevent hacking. YetAnotherForum Don’t let the name fool you - YetAnotherForum is anything but, with its quirky and innovative approach to forum development. The managed open source platform is designed specifically with ASP.NET in mind and is compatible with the fourth C# generation and above. It is licensed free to developers and open for reworkings of the system’s code, and it builds bright, bold message boards that are simple and easy for users and admins alike. One of the big selling points is YetAnotherForum’s reliability: the service has operated for nine years without problems and still undergoes regular testing. Over those nine years, progress has been slow but the last twelve months have seen promising developments and the program is seeing a surge in downloads and orders. Phorum Sometimes the old ones really are the best. Phorum has been around since the 1990s and it played a big role in the rise of forum sites. The free-to-use platform is based around PHP and MySQL development, and it is still one of the best pieces of software for forum creation that you can use free today. One of the key selling points is how flexible it is - you can host one huge message thread with thousands of users, or adopt it across hundreds of different forums for a help site, social network or discussion group. Phorum has also upped its game lately with the introduction of a new template - the XHTML 1.0 Transitional Emerald design.
This is available instead of the basic template and has far more features and options, but it still offers a blank slate for the developer in terms of design and function. Discourse If you need a platform that scales up as your service grows and is easy to develop and change as you do, Discourse is a great choice. There are three tiers of membership available - free, paid and premium - and all options are pretty budget-friendly. Discourse is designed for creating discussion boards, and it is fully compatible with mobiles and tablets as well as PCs and laptops. It can handle busy conversations and it makes them easy to read back, with options to split threads and move conversations as needed. The open source code is readily available for programmers to play with, and the system is easy to hand over to your designer or tech team if you have something specific in mind. User-created templates and styles are available, and there is a built-in filter system with can save on moderator costs and keep your forum a safe space for visitors to chat. Ten More Top Free Forum And Bulletin Board Programs Haven’t found what you need among our top picks above? Not all programs suit everyone - but there are hundreds of options on the market, so keep searching for your perfect platform. Find the right match for your forum vision, and get creating thanks to these amazing open source programs. Here are some more of the best forum development programs for 2017: Vanilla Forums Simple Machines MiniBB Forums MyBB DeluxeBB PunBB FluxBB UseBB Zetaboards Plush Forums The Best Of Premium Forum Software - At A Discount! If the free tools do not meet your needs or you want the added support and security of a premium service, there are plenty of platforms to choose from - including vBulletin, Burning Board, XenForo and IP.Board. Paid-for tools often require a subscription, so take advantage of the deals available online at OZCodes.com.au. Voucher codes can give big savings on the cost of software subscriptions through leading providers.
0 notes
Text
Inside the Mind of a Hacker: Understanding Cyber Criminals and Their Tactics

In today’s digital landscape, cybercrime has evolved into a sophisticated, multi-billion-dollar industry. Hackers operate with precision, using advanced techniques to breach security systems, steal sensitive data, and disrupt businesses. But what motivates these cybercriminals, and how do they think? To truly combat cyber threats, we must first understand the mindset of hackers and the strategies they employ.
If you're looking to safeguard yourself and build a career in cybersecurity, pursuing a Cyber Security Certification in Kolkata can equip you with the skills needed to protect against these evolving threats. Let’s dive into the mind of a hacker and explore their tactics.
The Psychology of a Hacker
1. Motivations Behind Cybercrime
Hackers are not always driven by the same goals. Understanding their motivations helps cybersecurity professionals develop better defense mechanisms. Common hacker motivations include:
Financial Gain: Cybercriminals engage in ransomware attacks, credit card fraud, and data breaches to steal money or sell information on the dark web.
Political or Ideological Beliefs: Hacktivists, such as Anonymous, target governments or corporations to protest against policies or social issues.
Espionage: State-sponsored hackers infiltrate government agencies, corporations, and research institutions to steal confidential data.
Personal Challenge or Notoriety: Some hackers break into systems purely for the thrill, to prove their skills, or to gain recognition in the hacking community.
Revenge: Disgruntled employees or individuals use hacking to sabotage organizations or individuals who have wronged them.
2. The Hacker Mindset
Hackers exhibit a combination of intelligence, curiosity, and persistence. Many have a deep understanding of coding, networking, and security vulnerabilities. Key psychological traits of hackers include:
Problem-Solving Skills: Hackers view security systems as puzzles to be cracked.
Anonymity & Deception: They leverage VPNs, proxy servers, and encryption to remain undetected.
Adaptability: As cybersecurity evolves, hackers continuously find new ways to bypass security measures.
Common Hacking Techniques and Tactics
Hackers use various methods to infiltrate systems. Some of the most common tactics include:
1. Phishing Attacks
Phishing remains one of the most effective hacking techniques. Hackers send deceptive emails or messages that trick users into revealing personal information, such as passwords and credit card details. They often impersonate banks, government agencies, or trusted brands.
Example: In 2021, a major phishing campaign targeted Microsoft users, tricking them into entering their credentials on a fake login page.
2. Malware and Ransomware
Hackers deploy malicious software (malware) to infect systems, steal data, or lock users out of their devices. Ransomware encrypts files and demands a ransom for their release.
Example: The WannaCry ransomware attack in 2017 affected over 200,000 computers worldwide, causing billions in damages.
3. Social Engineering
This tactic exploits human psychology rather than technical vulnerabilities. Hackers manipulate individuals into divulging sensitive information or granting unauthorized access.
Example: A hacker posing as an IT support technician might call an employee and ask for their login credentials.
4. SQL Injection Attacks
Hackers exploit vulnerabilities in websites that use SQL databases. By inserting malicious SQL code into input fields, they can access, modify, or delete database records.
Example: A well-known SQL injection attack targeted Yahoo! in 2012, exposing 450,000 user accounts.
5. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
These attacks overwhelm a system with excessive traffic, causing it to crash and become inaccessible.
Example: In 2016, the Mirai botnet launched a massive DDoS attack on Dyn, a major DNS provider, disrupting websites like Twitter, Netflix, and PayPal.
How to Defend Against Hackers
Understanding hacker tactics is the first step in securing digital assets. Here are essential strategies to protect against cyber threats:
1. Invest in Cybersecurity Education
A Cyber Security Certification in Kolkata can provide in-depth knowledge of ethical hacking, penetration testing, and risk management, helping individuals and businesses strengthen their defenses.
2. Use Strong Passwords and Multi-Factor Authentication (MFA)
Avoid using simple or reused passwords. Implement MFA to add an extra layer of security.
3. Keep Software and Systems Updated
Outdated software contains vulnerabilities that hackers exploit. Regular updates and security patches help close these loopholes.
4. Educate Employees on Cyber Threats
Since social engineering is a major attack vector, training employees to recognize phishing emails and suspicious activities is crucial.
5. Implement Firewalls and Intrusion Detection Systems (IDS)
These tools monitor and block unauthorized access attempts, enhancing network security.
6. Regularly Backup Data
Frequent backups protect against ransomware attacks. Store backups in a secure, offline location.
7. Conduct Penetration Testing
Simulating cyberattacks through ethical hacking helps identify vulnerabilities before malicious hackers exploit them.
Conclusion
Cybercriminals are constantly evolving, using innovative tactics to breach systems and exploit vulnerabilities. By understanding their mindset and techniques, individuals and businesses can better protect themselves from cyber threats.
If you're serious about cybersecurity, obtaining a Cyber Security Certification in Kolkata is a great way to gain the skills and knowledge needed to combat cyber threats effectively. Investing in cybersecurity today can save organizations from significant financial losses, data breaches, and reputational damage in the future.
Cybersecurity is not just a technology problem—it’s a human challenge. Stay informed, stay prepared, and stay secure.
0 notes
Text
STRING_SPLIT SQL Server: Yeni ve Eski Versiyon Farkları
SQL Server 2016 ile birlikte sunulan STRING_SPLIT SQL Server, verileri ayırmak için kullanılan oldukça pratik bir table-valued fonksiyondur. Bu fonksiyon, bir stringi belirli bir ayraç ile bölerek, veritabanı üzerinde SQL veri analizi süreçlerini oldukça kolaylaştırır. Özellikle SQL Server 2022 sürümünde gelen güncellemelerle birlikte, STRING_SPLIT fonksiyonunun işlevselliği daha da artmıştır.…
0 notes
Text
Social Business Intelligence Market Set to Soar: Projections at US$ 49.6 Billion by 2034
Based on income from worldwide deployment, FMI projects that the global market for social business intelligence will be worth US$ 17 billion by the end of 2017. The market is anticipated to have expanded at a compound annual growth rate (CAGR) of 6% by the end of 2026. An estimated US$ 29 billion is its value.
According to Future Market Insights (FMI), SAP SE, SAS Institute Inc., Logi Analytics, Inc., TIBCO Software, Inc., Alteryx Inc., MicroStrategy, Inc., Microsoft Corporation, Qlik Technologies, Inc., and Tableaue Software, Inc. are a few of the well-known players in the industry.
They are exploring prospects in the development of social media tools and software. Several companies in the market are a substantial investments in research and development aimed at wearable technologies based on social business intelligence to gain a competitive edge over others.
The various end-use verticals for the social business intelligence market are BFSI, healthcare and life sciences, consumer goods and retail, travel and tourism, IT and telecommunication, media and entertainment, and government. Of these, the BFSI sector is the leading segment as it held a major market share of 20.2% of all the verticals in 2016. The segment is anticipated to retain its dominance throughout the assessment period. However, the travel and tourism segment is anticipated to rise at higher year-over-year growth from 2017 to 2026.
Request a Sample of this Report: https://www.fmisamplereport.com/sample/rep-gb-3182
Rising Ubiquity of Social Media to Bolster Demand
The growing demand for big data analytics tools for the analysis of social media, coupled with the rising ubiquity of social networks world over, is a key factor driving the market. The pressing need for next-generation analytical data generation technologies and management systems across modern enterprises is a primary factor driving the market in various regions.
The robustly rising popularity of social media among product and customer service teams, largely on account of benefits that percolate beyond marketing and promotion, is a key trend accentuating the market. The growing demand for various big data tools such as Hadoop in managing vast sets of unstructured data emanating from online and social media sites and CRM conversations is a notable trend catalyzing the demand for social business intelligence tools. This is motivated by the intensifying needs to garner data-driven insights into customer taste and preference across enterprises.
The pressing need for gaining customer insights in real-time for accelerating time-to-market is a key aspect of a fast-growing modern enterprise, necessitating the demand for social business intelligence tools. The rising adoption of cloud-based technologies and services will expectedly create exciting opportunities for market players in the coming years.
Data Security Major Concerns, Advanced Enterprise Data Operating Systems to Open up Exciting Avenues
The concern of privacy of data and their enterprise security are key factors likely to hamper the demand for social business intelligence to an extent. Nevertheless, the marked shift of enterprises workloads from on-premise to cloud is expected to allay these mounting concerns, thereby bolstering the demand for social business intelligence. In addition, the advent of advanced enterprise data operating systems has led players overcome the constraints associated with traditional database systems, notably SQL servers.
The growing popularity of Hadoop for building large-scale database has enabled enterprises manage large operational requirements. This is a welcome trend in the global social business intelligence market. Furthermore, the introduction of YARN and MapReduce has substantially expanded the capabilities of Hadoop, thereby creating lucrative avenues for market players.
0 notes
Text
Discover the Full Range of Microsoft Products at TechLicence
For original Microsoft products, TechLicence is the best way to go. It's a licensed certified member of Microsoft partners with pride and a willingness to offer you all different high-quality software in stock to serve individual, business, or enterprise requirements. TechLicence comes to help you with high-level operating systems, leading tools in productivity, or top servers that can provide genuine, reliable access to the software you need.
We understand at TechLicence that one of the critical choices is where the tools move to upgrade work and personal projects. For these reasons, we have everything ranging from the latest versions of Windows to diverse Microsoft Office suites and specific specialized applications like SQL Server, Project, and Visio. Whether you're looking forward to upgrading your home office, streamlining business operations, or setting up a wide enterprise environment, we ensure that there's something there for everyone through our rich collection of Microsoft products. But with TechLicence, you never have to compromise on quality, safety, or performance.
Explore Our Ranges of Microsoft Products
At TechLicence, we understand how important high-quality, genuine software is in your productivity. To keep ahead, we offer you the following:
1. Windows Operating Systems
Run your devices with authentic Microsoft Windows operating systems. Choose the one for you:
Windows 10: perfect OS for your both home and professional life.
Windows 11: The new Windows technology, built for a modern, secure and connected experience.
2. Microsoft Office Suites
Unlock your productivity with Microsoft Office. Choose from:
Office 365: Get regular access to cloud tools updated by using 1TB of OneDrive storage.
Office 2019 & 2021 : Traditional productivity apps like Word, Excel, PowerPoint with perpetual licenses
3. Microsoft Servers
Build your business with strong server solutions from us. With Windows Server 2016 up to 2019 and more, TechLicence has everything you need for sure. Administering networks, databases and applications should soon be a part of routine work for you.
4. More Microsoft Products
On top of the above, TechLicence shall also provide you with the necessary Microsoft Software like:
Project und Visio for detailed project management and diagramming
Remote Desktop Services for smooth remote working solutions
SQL Server für data and app management
Why TechLicence for Microsoft Products?
We give you a set of lucrative benefits that place us as your one-stop partner for the purchase of Microsoft software.
We are a certified Microsoft Partner. Hence, you can get assured that you are getting authenticated licenses.
Competitive Price: Premium software at pocket-friendly rates so that it fits right in your budget requirement. You can enjoy lifetime support through our dedicated team's effort to activate and use your product; we are just a call away if you require any technical assistance.
Microsoft Direct Support: Being an authorized seller, we give you direct support from the company if you require any technological support.
Lock Your Microsoft Software Now!
Whether you want to upgrade your home setup, equip your office, or manage enterprise systems, TechLicence has all the Microsoft solutions for you. Browse on TechLicence and discover our wide product range and find the right tools for your journey to greater productivity.
Choose TechLicence authenticity, reliability, and exceptional customer service for your digital world.
0 notes
Text
从数据库发展历程到数据结构设计探析

一 数据库发展史
起初,数据的管理方式是文档系统,数据存储在文档中,数据管理和维护都由进程员完成。后来发展出树形结构和网状结构的数据库,但都存在着难以扩展和维护的问题。直到七十年代,关系数据库理论的提出,以表格形式组织数据,数据之间存在关联关系,具有了良好��结构化和规范化特性,成为主流数据库类型。
先来看一张数据库发展史图鉴:

随之高并发大数据时代的来临,数据库按照各种应用场景进行了更细粒度的拆分和演进,数据库细分领域的典型代表:

二 数据库名词概念
RDBS
1970 年的 6 月,IBM 公司的研究员埃德加・考特 (Edgar Frank Codd) 发表了那篇着名的《大型共享数据库数据的关系模型》(A Relational Model of Data for Large Shared Data Banks)的论文,拉开了关系型数据库(Relational DataBase Server)软件革命的序幕(之前是层次模型和网状模型数据库为主)。直到现在,关系型数据库在基础软件应用领域仍��最主要的数据存储方式之一。
关系型数据库创建在关系型数据模型的基础上,是借助于集合代数等数学概念和方法来处理数据的数据库。在关系型数据库中,实体以及实体间的联系均由单一的结构类型来表示,这种逻辑结构是一张二维表。关系型数据库以行和列的形式存储数据,这一系列的行和列被称为表,一组表组成了数据库。
NoSQL
NoSQL(Not Only SQL) 数据库也即非关系型数据库,它是在大数据的时代背景下产生的,它可以处理分布式、规模庞大、类型不确定、完整性没有保证的 “杂乱” 数据,这是传统的关系型数据库远远不能胜任的。NoSQL 数据库并没有一个统一的模型,是以牺牲事务机制和强一致性机制,来获取更好的分布式部署和横向扩展能力,使其在不同的应用场景下,对特定业务数据具有更强的处理性能。常用数据模型示例如下:

NewSQL
NewSQL 是一类新的关系型数据库, 是各种新的可扩展和高性能的数据库的简称。它不仅具有 NoSQL 数据库对海量数据的存储管理能力,同时还保留了传统数据库支持的 ACID 和 SQL 特性,典型代表有 TiDB 和 OceanBase。
OLTP
联机事务处理过程 (On-Line Transaction Processing):也称为面向交易的处理过程,其基本特征是前台接收的用户数据可以立即传送到计算中心进行处理,并在很短的时间内给出处理结果,是对用户操作��速响应的方式之一。
OLAP
联机分析处理(On-Line Analytical Processing)是一种面向数据分析的处理过程,它使分析人员能够迅速、一致、交互地从各个方面观察信息,以达到深入理解数据的目的。它具有 FASMI (Fast Analysis of Shared Multidimensional Information),即共享多维信息的快速分析的特征。
关于 OLTP 和 OLAP 的区别,借用一张表格对比如下:

HTAP (Hybrid Transactional/Analytical Processing) 混合型数据库基于新的计算存储框架,能够同时支撑 OLTP 和 OLAP 场景,避免传统架构中大量数据交互造成的资源浪费和冲突。
三 领域数据库
列式数据库
传统的以行形式保存的数据主要满足 OLTP 应用,列形式保存的数据主要满足以查询为主的 OLAP 应用。在列式数据库中,数据按列存储,而每个列中的数据类型相同。这种存储方式使列式数据库能够更高效地处理大量的数据,特别是需要进行大规模的数据分析和处理时(如金融、医疗、电信、能源、物流等行业)。
两种存储结构的区别如下图:

列式数据库的主要优点:
• 更高的压缩比率:由于每个列中的数据类型相同,列式数据库可以使用更高效的压缩算法来压缩数据(压缩比可达到 5~20 倍),从而减少存储空间的使用。
• 更快的查询速度:列式数据库可以只读取需要的列,而不需要读取整行数据,从而加快查询速度。
• 更好的扩展性:列式数据库可以更容易地进行水平扩展,即增加更多的节点和服务器来处理更大规模的数据。
• 更好的数据分析支持:由于列式数据库可以处理大规模的数据,它可以支持更复杂的数据分析和处理操作,例如数据挖掘、机器学习等。
列式数据库的主要缺点:
• 更慢的写入速度:由于数据是按列存储,每次写入都需要写入整个���,而不是单个行,因此写入速度可能较慢。
• 更复杂的数据模型:由于数据是按列存储,数据模型可能比行式数据库更复杂,需要更多的设计和开发工作。
列式数据库的应用场景:
• 金融:金融行业的交易数据和市场数据,例如股票价格、外汇汇率、利率等。列式数据库可以更快速地处理这些数据,并且支持更复杂的数据分析和处理操作,例如风险管理、投资分析等。
• 医疗:医疗行业的病历数据、医疗图像和实验数据等。列式数据库可以更高效地存储和处理这些数据,并且支持更复杂的医学研究和分析操作。
• 电信:电信行业的用户数据和通信数据,例如电话记录、短信记录、网络流量等。列式数据库可以更快速地处理这些数据,并且支持更复杂的用户行为分析和网络优化操作。
• 能源:能源行业的传感器数据、监测数据和生产数据等。列式数据库可以更高效地存储和处理这些数据,并且支持更复杂的能源管理和控制操作。
• 物流:物流行业的运输数据、库存数据和订单数据等。列式数据库可以更快速地处理这些数据,并且支持更复杂的物流管理和优化操作。
总之,列式数据库是一种高效处理大规模数据的数据库管理系统,但需要权衡写入速度、数据模型复杂度和成本等因素。 随着传统关系型数据库与新兴的分布式数据库不断的发展,列式存储与行式存储会不断融合,数据库系统呈现双模式数据存放方式。
时序数据库
时序数据库全称为时间串行数据库 (Time Series Database),用于存储和管理时间串行数据的专业化数据库,是优化用于摄取、处理和存储时间戳数据的数据库。其跟常规的关系数据库 SQL 相比,最大的区别在于:时序数据库是以时间为索引的规律性时间间隔记录的数据库。
时序数据库在物联网和互联网应用进程监控(APM)等场景应用比较多,以监控数据采集来举例,如果数据监控数据采集时间间隔是 1s,那一个监控项每天会产生 86400 个数据点,若有 10000 个监控项,则一天���会产生 864000000 个数据点。在物联网场景下,这个数字会更大,整个数据的规模,是 TB 甚至是 PB 级的。
时序数据库发展史:

当下最常见的 Kubernetes 容器管理系统中,通常会搭配普罗米修斯(Prometheus)进行监控,Prometheus 就是一套开源的监控 & 报警 & 时间串行数据库的组合。
图数据库
图数据库(Graph Database)是基于图论实现的一种新型 NoSQL 数据库。它的数据存储结构和数据的查询方式都是以图论为基础的。图论中图的基本元素为节点和边,在图数据库中对应的就是节点和关系。
图数据库在反欺诈多维关联分析场景,社交网络图谱,企业关系图谱等场景中可以做一些非常复杂的关系查询。这是由于图数据结构表现的是实体联系本身,它表现了现实世界中事物联系的本质,它的联系在节点创建时就已经创建,所以在查询中能以快捷的路径返回关联数据,从而表现出非常高效的查询性能。
目前市面上较为流行的图数据库产品有以下几种:

与传统的关系数据库相比,图数据库具有以下优点:
1. 更快的查询速度:图数据库可以快速遍历图数据,找到节点之间的关联和路径,因此查询速度更快。
2. 更好的扩展性:图数据库可以轻松地扩展到大规模的数据集,因为它们可以分布式存储和处理数据。
3. 更好的数据可视化:图数据库可以将数据可视化为图形,使用户更容易理解和分析数据。
4. 更好的数据一致性:图数据库可以确保数据的一致性,因为它们可以在节点和边之间创建强制性的关系。
四 数据结构设计
前面简单介绍了数据库相关的基础知识,下面再介绍几种我们常见的数据结构设计相关的应用实践:拉链表,位运算和环形队列。
4.1 拉链表
拉链表是一种数据仓库中常用的数据模型,用于记录维度数据的变化历史。我们以一个人员变动的场景举例,假设有一个员工信息表,其中包含了员工的姓名、工号、职位、部门、入职时间等信息。如果需要记录员工的变动情况,就可以使用拉链表来实现。
首先,在员工信息表的基础上添加两个字段:生效时间和失效时间。当员工信息发生变动时,不再添加一条记录,而是修改原有记录的失效时间,同时添加一条新的记录。如下表所示:

这里的生效时间指的是该记录生效的时间,失效时间指的是该记录失效的时间。例如,张三最初是技术部经理,生效时间为入职时间,失效时间为 2012 年底,之后晋升为技术部总监,生效时间为 2013 年初,失效时间为 2015 年底,最后又晋升为技术部总经理,生效时间为 2016 年初,失效时间为 9999 年底。
通过这种方式,可以记录员工变动的历史信息,并能够方便地查询某个时间点的员工信息。例如,如果需要查询张三在 2014 年的职位和部门信息,只需查询生效时间小于 2014 年且失效时间大于 2014 年的记录即可。
拉链表通常包括以下几个字段:
1.主键:唯一标识每个记录的字段,通常是一个或多个列的组合。 2.生效时间:记录的生效时间,即该记录开始生效的时间。 3.失效时间:记录的失效时间,即该记录失效的时间。 4.版本号:记录的版本号,用于标识该记录的版本。 5.其他维度属性:记录的其他维度属性,如客户名、产品名、员工名等。
当一个记录的维度属性发生变化时,不再添加一条记录,而是修改原有记录的失效时间,同时添加一条新的记录。新记录的生效时间为变化的时间,失效时间为 9999 年底。这样就能够记录每个维度属性的历史变化信息,同时保证查询时能够正确获取某个时间点的维度属性信息。
拉链表与传统的流水表相比,它们的主要区别在于:
1. 数据结构不同:流水表是一张只有添加和更新操作的表,每次更新都会添加一条记录,记录中包含了所有的历史信息。而拉链表则是一张有添加、更新和删除操作的表,每个记录都有一个生效时间段和失效时间段,记录的历史信息通过时间段的变化来体现。
2. 查询方式不同:流水表的查询方式是基于时间点的查询,即查询某个时间点的记录信息。而拉链表的查询方式是基于时间段的查询,即查询某个时间段内的记录信息。
3. 存储空间不同:由于流水表需要记录所有历史信息,所以存储空间相对较大。而拉链表只记录生效时间段和失效时间段,所以存储空间相对较小。
4. 数据更新方式不同:流水表只有添加和更新操作,每次更新都会添加一条记录,不会对原有记录进行修改。而拉链表有添加、更新和删除操作,每次更新会修改原有记录的失效时间,同时添加一条新的记录。
4.2 巧用位运算
借助于计算机位运算的特性,可以巧妙的解决某些特定问题,使实现更加优雅,节省存储空间的同时,也可以提高运行效率,典型应用场景:压缩存储、位图索引、数据加密、图形处理和状态判断等,下面介绍几个典型案例。
4.2.1 位运算
• 使用位运算实现开关和多选项叠加(资源权限)等应用场景。一个 int 类型有 32 个位,理论上可以表示 32 个开关状态或业务选项;以用户每个月的签到场景举例:用一个 int 字段来表示用户一个月的签到情况,0 表示未签到,1 表示签到。想知道某一天是否签到,则只需要判断对应的比特位上是否为 1。计算一个月累计签到了多少次,只需要统计有多少个比特位为 1 就可以了。这种设计巧妙的数据存储结构在后面的位图(BitMap)中,还会进行更为详细的介绍。

• 使用位运算实现业务优先级计算:

• 其它使用位运算的典型场景:HashMap 中的队列长度的设计和线程池 ThreadPoolExcutor 中使用 AtomicInteger 字段 ctl,存储当前线程池状态和线程数量(高 3 位表示当前线程的状态,低 29 位表示线程的数量)。
4.2.2 BitMap
位图(BitMap)是一种常用的数据结构,在索引,数据压缩等方面有广泛应用。基本思想就是用一个 bit 位来标记某个元素对应的 Value,而 Key 即是该元素。由于采用了 Bit 为单位来存储数据,因此可以大大节省存储空间,是少有的既能保证存储空间又能保证查找速度的数据结构(而不必空间换时间)。
举个例子,假设有这样一个需求:在 20 亿个随机整数中找出某个数 m 是否存在其中,并假设 32 位操作系统,4G 内存,在 Java 中,int 占 4 字节,1 字节 = 8 位(1 byte = 8 bit)。
• 如果每个数字用 int 存储,那就是 20 亿个 int,因而占用的空间约为 (2000000000*4/1024/1024/1024)≈7.45G
• 如果按位存储就不一样了,20 亿个数就是 20 亿位,占用空间约为 (2000000000/8/1024/1024/1024)≈0.233G
存储空间可以压缩节省 31 倍!那么它是如何通过二进制位实现数字标记的呢? 其原理是用每个二进制位(下标)表示一个真实数字,0 表示不存在,1 表示存在,这样我们可以很容易表示 {1,2,4,6} 这几个数:

计算机内存分配的最小单位是字节,也就是 8 位,那如果要表示 {12,13,15} 怎么办呢?可以另申请一个字节 b [1]:

通过一个二维数组来实现位数叠加,1 个 int 占 32 位,那么我们只需要申请一个 int 数组长度为 int index [1+N/32] 即可存储,其中 N 表示要存储的这些数中的最大值:
index [0]:可以表示 0\~31
index [1]:可以表示 32\~63
index [2]:可以表示 64\~95
以此类推 ... 如此一来,给定任意整数 M,那么 M/32 就得到下标,M%32 就知道它在此下标的哪个位置。
BitMap 数据结构通常用于以下场景:
1. 压缩存储大量布尔值:BitMap 可以有效地压缩大量的布尔值,从而减少内存的使用;
2. 快速判断一个元素是否存在:BitMap 可以快速地判断一个元素是否存在,只需要查找对应的位即可;
3. 去重:BitMap 可以用于去重操作,将元素作为索引,将对应的位设置为 1,重复元素只会对应同一个位,从而实现去重;
4. 排序:BitMap 可以用于排序,将元素作为索引,将对应的位设置为 1,然后按照索引顺序遍历位数组,即可得到有序的元素串行;
5. ElasticSearch 和 Solr 等搜索引擎中,在设计搜索剪枝时,需要保存已经搜索过的历史信息,可以使用位图减小历史信息数据所占空间;
4.2.3 布隆过滤器
位图(Bitmap)这种数据存储结构,如果数据���大到一定程度,比如 64bit 类型的数据,简单算一下存储空间就知道,海量硬件资源要求,已经不太现实了:

所以另一个着名的工业实现 - 布隆过滤器(Bloom Filter)出现了。如果说 BitMap 对于每一个可能的整型值,通过直接寻址的方式进行映射,相当于使用了一个哈希函数,那布隆过滤器就是引入了 k (k> 1 ) 个相互独立的哈希函数,保证在给定的空间和误判率情况下,完成元素判重的过程。下图中是 k = 3 时的布隆过滤器:

布隆过滤器的内部依赖于哈希算法,当检测某一条数据是否见过时,有一定概率出现假阳性(False Positive),但一定不会出现假阴性(False Negative)。也就是说,当 布隆过滤器认为一条数据出现过,那么该条数据很可能出现过;但如果布隆过滤器认为一条数据没出现过,那么该条数据一定没出现过。布隆过滤器通过引入一定错误率,使得海量数据判重在可以接受的内存代价中得以实现。
上图中,x,y,z 经由哈希函数映射将各自在 Bitmap 中的 3 个位置置为 1,当 w 出现时,仅�� 3 个标志位都为 1 时,才表示 w 在集合中。图中所示的情况,布隆过滤器将判定 w 不在集合中。
常见实现
• Java 中 Guava 工具包中实现;
• Redis 4.0 开始以插件形式提供布隆过滤器功能;
适用场景
• 网页爬虫对 URL 的去重,避免爬去相同的 URL 地址,比如 Chrome 浏览器就是使用了一个布隆过滤器识别恶意链接;
• 垃圾邮件过滤,从数十亿个垃圾邮件列表中判断某邮箱是否是杀垃圾邮箱;
• 解决数据库缓存击穿,黑客攻击服务器时,会构建大量不存在于缓存中的 key 向服务器发起请求,在数据量足够大的时候,频繁的数据库查询会导致挂机;
• 谷歌 Bigtable、Apache HBase、Apache Cassandra 和 PostgreSQL 使用布隆过滤器来减少对不存在的行或列的磁盘查找;
• 秒杀系统,查看用户是否重复购买;
4.2.4 小结
• 位运算有着执行速度快,占用空间小,代码实现简洁等优点,往往能起到四两拨千斤的效果。同样也有着代码可读性差,使用范围和可维护性受限等不足;
• 在 BitMap 中,占用空间大小还与实际应用场景有关,这种结构无法容忍误判,只能判断一个元素是否存在,如果数据离散度过高,空间利用率反而更低;
• 布隆过滤器则有着空间利用率高,可以容忍一定的误判率的优点。与 BitMap 相比,也存在着无法删除元素,误判率无法达到 0 等不足;
4.3 环形队列
环形队列是一种用于表示一个固定尺寸、头尾相连的数据结构,很适合缓存数据流。在通信开发(Socket,TCP/IP,RPC 开发),在内核的进程间通信(IPC),视频音频播放等各种场景中,都有其身影。日常开发过程中使用的 Dubbo、Netty、Akka、Quartz、ZooKeeper 、Kafka 等各种中间件,也都有环形队列的思想。下面介绍两种常用的环形数据结构:Hash 环和时间轮。
4.3.1 一致性 Hash 环
先来看一下,典型 Hash 算法结构如下:

以上图 Hash 策略为例,当节点数 N 发生变化的时候 之前所有的 hash 映射几乎全部失效,如果集群是无状态的服务,倒是没什么事情,但是如果是分布式缓存这种场景,就会导致比较严重的问题。比如 Key1 原本是路由到 Node1 上,命中缓存的 Value1 数据。但是当 N 节点变化后,Key1 可能就路由到了 Node2 节点,这就产生了缓存数据无法命中的问题。而无论是机器故障还是缓存扩容,都会导致节点数的变化。
如何解决上面场景的问题呢?就是接下来介绍的一致性 Hash 算法。
一致性哈希将整个哈希值空间组织成一个虚拟的圆环,假设某哈希函数 H 的值空间为 0-2^32-1(即哈希值是一个 32 位无符号整型),所有的输入值都被映射到 0-2^32-1 之间,组成一个圆环。整个哈希空间环如下:

路由数据的过程如下:将数据 key 使用相同的函数 Hash 计算出哈希值,并确定此数据在环上的位置,从此位置沿环顺时针 “行走”,遇到的第一个节点就是其应该定位到的服务器。如果某个节点的服务器故障,其影响范围也不再是所有集群,而是限定在故障节点与其上游节点的部分区域。
当某个节点宕机后,原本属于它的请求都会被重新 hash 映射到下游节点,会突然造成下游节点压力过大有可能也会造成下游节点宕机,从而容易形成雪崩,为此引入了虚拟节点来解决这个问题。
根据 Node 节点生成很多的虚拟节点分布在圆环上,,一个真实节点映射对应多个虚拟节点。这样当某个节点挂了后原本属于它的请求,会被均衡的分布到其他节点上降低了产生雪崩的情况,也解决了物理节点数少,导致请求分布不均的问题。
带有虚拟节点的 Hash 环:

一致性 Hash 算法由于均衡性,持久性的映射特点被广泛应用于负载均衡领域,比如 nginx、dubbo 等内部都有一致性 hash 的实现。
4.3.2 时间轮分片
时间轮(TimeWheel)是一种实现延迟功能(定时器)的精妙的算法,可以实现高效的延时队列。以 Kafka 中的时间轮实现方案为例,它是一个存储定时任务的环形队列,底层采用数组实现,数组中的每个元素可以存放一个定时任务列表(TimerTaskList)。TimerTaskList 是一个环形的双向链表,链表中的每一项表示的都是定时任务项(TimerTaskEntry),其中封装了真正的定时任务 TimerTask。

通过上图可以发现,时间轮算法不再任务队列作为数据结构,轮询线程不再负责遍历所有任务,而是仅仅遍历时间刻度。时间轮算法好比指针不断在时钟上旋转、遍历,如果一个发现某一时刻上有任务(任务队列),那么就会将任务队列上的所有任务都执行一遍。
假设相邻 bucket 到期时间的间隔为 bucket=1s,从 0s 开始计时,1s 后到期的定时任务挂在 bucket=1 下,2s 后到期的定时任务挂在 bucket=2 下,当检查到时间过去了 1s 时,bucket=1 下所有节点执行超时动作,当时间到了 2s 时,bucket=2 下所有节点执行超时动作。时间轮使用一个表盘指针(pointer),用来表示时间轮当前指针跳动的次数,可以用 tickDuration * (pointer + 1) 来表示下一次到期的任务,需要处理此 bucket 所对应的 TimeWheel 中的所有任务。
时间轮的优点
1. 任务的添加与移除,都是 O (1) 级的复杂度;
2. 只需要有一个线程去推进时间轮,不会占用大量的资源;
3. 与其他任务调度模式相比,CPU 的负载和资源浪费减少;
适用场景
时间轮是为解决高效调度任务而产生的调度模型。在周期性定时任务,延时任务,通知任务等场景都可以发挥效用。
五 总结
本文针对数据存储相关名词概念进行了解释,重点介绍了数据库技术的发展史。为了丰富文章的可读性以及实用性,又从数据结构设计层面进行了部分技术实战能力的外延扩展,阐述了拉链表,位运算,环形队列等相关数据结构在软件开发领域的应用,希望本文给你带来收获。
0 notes
Text
Disable SQL Auto Close: Auto Close is enabled for both ePO and ePO Events Databases
The SQL Auto Close feature automatically closes inactive database connections after a specified period of inactivity. By default, auto close is enabled but Trellix does not like this behaviour. In this article, we will discuss the fix to “Disable SQL Auto Close: Auto Close is enabled for both ePO and ePO Events Databases”. Please see Trellix ePolicy Orchestrator Installation on Windows Server,…

View On WordPress
#Disable Auto Close on Microsoft SQL Server#Disable SQL Auto Close#Microsoft SQL#Microsoft SQL Auto Close#Microsoft Windows#Windows#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
Microsoft says it broke some Windows 10 patching – as it fixes flaws under attack - Information Important Web https://www.merchant-business.com/microsoft-says-it-broke-some-windows-10-patching-as-it-fixes-flaws-under-attack/?feed_id=195758&_unique_id=66e1043847d5b #GLOBAL - BLOGGER BLOGGER Patch Tuesday Another Patch Tuesday has dawned, as usual with the unpleasant news that there are pressing security weaknesses and blunders to address.Microsoft issued fixes for more than 70 flaws affecting various components of its products including Windows, Office and its Mark of the Web mechanism, Azure, Dynamics Business Central, SQL Server, Hyper-V, and Remote Desktop Licensing Service.Three are already being exploited in the wild. Here they are in descending order of severity:CVE-2024-38014 – A CVSS 7.8-out-of-10 in CVSS severity issue allowing privilege escalation in Windows Installer that could give full SYSTEM privileges. It was discovered by the SEC Consult Vulnerability Lab.CVE-2024-38226 – A CVSS 7.4 security bypass hole in Publisher 2016, plus Office 2019 and 2021. This does require a victim to open a poisoned file, but once that’s done the attacker can bypass the macro defenses in Office.CVE-2024-38217 – A CVSS 5.4 issue allowing a miscreant to bypass Microsoft’s Mark of the Web software identification engine. There’s a second Mark of the Web flaw addressed this month – CVE-2024-43487 – which Microsoft lists as likely to be exploited and of moderate concern.Then there’s CVE-2024-43491, a car crash that solely affects Windows 10 version 1507 first released in July 2015. While that version fell out of support in 2017 for its Pro, Home, Enterprise, Education, and Enterprise IoT editions, Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 remain in support; all are affected.This bug is rated 9.8-out-of-10 in CVSS severity as, from what we can tell, it caused the operating system to silently undo previously applied updates and security patches for certain optional components, leaving them open to attack and other issues.This is due to a programming error triggered by applying security updates released between March and August 2024 inclusively, we’re told.It appears that if you install a security update issued between those two months on Windows 10 version 1507, and then apply updates or security patches released since March 12, the OS gets mighty confused and reverts the updated software back to its base RTM – release to manufacturing – version, leaving the code unpatched and the computer at risk of attack. According to Microsoft, this rollback can happen to the following optional components:.NET Framework 4.6 Advanced Services ASP.NET 4.6Active Directory Lightweight Directory ServicesAdministrative ToolsInternet Explorer 11Internet Information ServicesWorld Wide Web ServicesLPD Print ServiceMicrosoft Message Queue (MSMQ) Server CoreMSMQ HTTP SupportMultiPoint ConnectorSMB 1.0/CIFS File Sharing SupportWindows Fax and ScanWindows Media PlayerWork Folders ClientXPS ViewerMicrosoft is treating this as an exploited-in-the-wild bug in that it previously issued patches for actively exploited bugs for those components, and these patches would have been removed by the bug.“Starting with the Windows security update released March 12, 2024 – KB5035858 (OS Build 10240.20526), the build version numbers crossed into a range that triggered a code defect in the Windows 10 (version 1507) servicing stack that handles the applicability of optional components,” as Microsoft so clearly put it.“As a result, any optional component that was serviced with updates released since March 12, 2024 (KB5035858) was detected as ‘not applicable’ by the servicing stack and was reverted to its RTM version.”So does that mean if you applied, say, the March 2024 update, the operating system already undid fixes previously applied? Yes: “If you have installed any of the previous security updates released between March and August 2024, the rollbacks of the fixes for CVEs affecting [the] optional components have already occurred.
To restore these fixes customers need to install the September 2024 Servicing Stack Update and Security Update for Windows 10.”Indeed, Microsoft says people should install both the servicing stack update KB5043936 and security update KB5043083, released this Patch Tuesday, in that order “to be fully protected from the vulnerabilities that this CVE rolled back.” Users automatically applying updates will have got this already.There are more details here, which does warn that this may break dual-boot systems that run Windows and Linux, and you’re told to check out a workaround for that.Moving on…Here are the other bugs addressed by Microsoft this week.Azure accounts for plenty of the worst bugs, including three elevation of privilege flaws (CVE-2024-38216, CVE-2024-38220, and CVE-2024-38194, all critical) in the Stack Hub that’s used to run Microsoft’s platform on-prem and Azure Web Apps.Azure’s Network Watcher VM Agent has a pair of similar escalations bugs (CVE-2024-38188 and CVE-2024-43470, both important) and a remote code issue (CVE-2024-43469, also important) in the platform’s CycleCloud HPC orchestrator.SharePoint Server has two critical flaws, CVE-2024-38018 and CVE-2024-43464, allowing attackers with Site Member and Site Owner permissions to execute code remotely. There are 30 elevation of privilege flaws to choose from in this month’s update that could be chained with these two flaws and Microsoft lists both critical flaws as “Exploitation more likely.”Another critical flaw, CVE-2024-38119, stems from a use-after-free remote code execution bug in the Windows Network Address Translation (NAT) code base. An attacker would have to be inside the network already to abuse this and Microsoft lists it as difficult to use and less likely to be exploited.Users of Windows 11 version 21H2 or 22H2 should also remember that next patch Tuesday, October 8, will see support for their operating systems coming to an end for Home, Pro, Pro Education, and Pro for Workstations. If you’re using automatic updates you’ll be prompted to upgrade next month.Adobe’s low-priority patchesPatch Tuesday is not just Microsoft’s party: Adobe has revealed 19 critical issues, 13 important, and three rated as moderate severity. ColdFusion 2021 and 2023 are vulnerable to a CVSS 9.8 issue over using deserialization of untrusted data that would allow arbitrary code access.Adobe has also popped patches for the Windows and macOS versions of Photoshop, Acrobat and Reader, Illustrator, After Effects, Premiere Pro, ColdFusion, Media Encoder, and Audition.Adobe classified all of them as Priority 3, its lowest ranking and reports that there are no exploits in the wild.Intel suggests killing its RAID Web ConsoleAfter releasing 43 security advisories in August Intel delivered just four this month –only one of which is high severity.But one of those advisories addresses 11 CVEs related to “Potential security vulnerabilities in UEFI firmware [that] may allow escalation of privilege, denial of service or information disclosure.”The CVES cover a very extensive list of older mobile, PC and server chips, including Atom, 13th generation and earlier Core processors, and Xeon E5 v3 and prior platforms.A patch is also out for CVE-2024-24968, which would allow a denial of service attacks against the 13th generation of Intel Core processors (and earlier kit) in mobile, desktop and embedded hardware. Xeon D server chips and 3rd-gen scalable systems are also vulnerable.Intel’s Running Average Power Limit interface is vulnerable to CVE-2024-23984, the chipmaker warns, which would allow information disclosure, although only for a privileged user. The issue affects third-generation Xeon D and scalable chips and servers, workstations, and embedded systems.There’s also a warning that all RAID Web Console software is vulnerable to nine CVEs but Intel won’t be issuing fixes since the product went end of life in March. Customers are advised to stop using the software and delete it from their systems.
SAP fixes, then fixes againSAP has issued 19 security notes detailing 16 new patches and three updates to older fixes.All the new security patches are medium severity or less with CVSS scores of six or below.SAP has given the highest priority to fixing earlier issues. Top of its list is CVE-2024-41730, in the BusinessObjects Business Intelligence Platform which has a CVSS score of 9.8, is rated highest by SAP, and was issued last month. The new code extends cover to Release 420 of the Enterprise software component and includes details for a workaround for those that can’t patch yet.SAP’s only high priority note covers CVE-2024-33003, an information disclosure vuln in the Commerce Cloud platform with a CVSS of 7.4 that was also released in August. The latest software extends vulnerability coverage to Release 2211.28 of the platform.CISA warns admins to check two Citrix issuesCitrix has issued high-severity fixes for two flaws in its Workspace app for Windows, affecting the current release before version 2405 and long-term releases before 2402 LTSR CU1.CVE-2024-7889 is a privilege elevation flaw, rated CVSS 7.0, that would allow a local user to upgrade themselves to SYSTEM status because of improper resource handling by the code. CVE-2024-7890, rated CVSS 5.4, sorts out improper privilege management that could also lead to an attacker getting SYSTEM access. Both issues require local access to a target machine.“A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system,” the US security agency warned. “CISA encourages users and administrators to review the following and apply necessary update.”Ivanti irritations, againCISA is also warning about serious problems in Ivanti Endpoint Manager 2022 and 2024, Cloud Service Application 4.6, and Workspace Control 10.18.0.0 and below, months after it reported the software biz was leaving US chemical facilities vulnerable with previous security failings.Endpoint Manager’s problems are the most severe, with 16 CVEs named including a CVSS 10.0 issue that allows full remote code execution on EPM before 2022 SU6, or the 2024 September update, due to the agency portal mishandling untrusted data. Nine other critical CVSS 9.1 issues are also reported, as well as two high priority issues (including an RCE issue) and one medium flaw.There’s a CVE for all versions of Ivanti’s Cloud Service Application 4.6 before patch 519, allowing a remote attacker to run code – but only if they have admin privileges. Workspace Control has six high-severity CVEs, all of which would allow locally authenticated users to upgrade their network privileges. ®“CISA wants you to leap on Citrix and Ivanti issues. Adobe, Intel, SAP also bid for patching priorities Patch Tuesday Another Patch Tuesday has dawned, as usual with the unpleasant…”Source Link: https://go.theregister.com/feed/www.theregister.com/2024/09/11/patch_tuesday_september_2024/ http://109.70.148.72/~merchant29/6network/wp-content/uploads/2024/09/1726020006_506_maxresdefault.jpg Patch Tuesday Another Patch Tuesday has dawned, as usual with the unpleasant news that there are pressing security weaknesses and blunders to address. Microsoft issued fixes for more than 70 flaws affecting various components of its products including Windows, Office and its Mark of the Web mechanism, Azure, Dynamics Business Central, SQL Server, Hyper-V, and … Read More
0 notes
Text
Microsoft says it broke some Windows 10 patching – as it fixes flaws under attack - Information Important Web - BLOGGER https://www.merchant-business.com/microsoft-says-it-broke-some-windows-10-patching-as-it-fixes-flaws-under-attack/?feed_id=195756&_unique_id=66e1043608e4a Patch Tuesday Another Patch Tuesday has dawned, as usual with the unpleasant news that there are pressing security weaknesses and blunders to address.Microsoft issued fixes for more than 70 flaws affecting various components of its products including Windows, Office and its Mark of the Web mechanism, Azure, Dynamics Business Central, SQL Server, Hyper-V, and Remote Desktop Licensing Service.Three are already being exploited in the wild. Here they are in descending order of severity:CVE-2024-38014 – A CVSS 7.8-out-of-10 in CVSS severity issue allowing privilege escalation in Windows Installer that could give full SYSTEM privileges. It was discovered by the SEC Consult Vulnerability Lab.CVE-2024-38226 – A CVSS 7.4 security bypass hole in Publisher 2016, plus Office 2019 and 2021. This does require a victim to open a poisoned file, but once that’s done the attacker can bypass the macro defenses in Office.CVE-2024-38217 – A CVSS 5.4 issue allowing a miscreant to bypass Microsoft’s Mark of the Web software identification engine. There’s a second Mark of the Web flaw addressed this month – CVE-2024-43487 – which Microsoft lists as likely to be exploited and of moderate concern.Then there’s CVE-2024-43491, a car crash that solely affects Windows 10 version 1507 first released in July 2015. While that version fell out of support in 2017 for its Pro, Home, Enterprise, Education, and Enterprise IoT editions, Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 remain in support; all are affected.This bug is rated 9.8-out-of-10 in CVSS severity as, from what we can tell, it caused the operating system to silently undo previously applied updates and security patches for certain optional components, leaving them open to attack and other issues.This is due to a programming error triggered by applying security updates released between March and August 2024 inclusively, we’re told.It appears that if you install a security update issued between those two months on Windows 10 version 1507, and then apply updates or security patches released since March 12, the OS gets mighty confused and reverts the updated software back to its base RTM – release to manufacturing – version, leaving the code unpatched and the computer at risk of attack. According to Microsoft, this rollback can happen to the following optional components:.NET Framework 4.6 Advanced Services ASP.NET 4.6Active Directory Lightweight Directory ServicesAdministrative ToolsInternet Explorer 11Internet Information ServicesWorld Wide Web ServicesLPD Print ServiceMicrosoft Message Queue (MSMQ) Server CoreMSMQ HTTP SupportMultiPoint ConnectorSMB 1.0/CIFS File Sharing SupportWindows Fax and ScanWindows Media PlayerWork Folders ClientXPS ViewerMicrosoft is treating this as an exploited-in-the-wild bug in that it previously issued patches for actively exploited bugs for those components, and these patches would have been removed by the bug.“Starting with the Windows security update released March 12, 2024 – KB5035858 (OS Build 10240.20526), the build version numbers crossed into a range that triggered a code defect in the Windows 10 (version 1507) servicing stack that handles the applicability of optional components,” as Microsoft so clearly put it.“As a result, any optional component that was serviced with updates released since March 12, 2024 (KB5035858) was detected as ‘not applicable’ by the servicing stack and was reverted to its RTM version.”So does that mean if you applied, say, the March 2024 update, the operating system already undid fixes previously applied? Yes: “If you have installed any of the previous security updates released between March and August 2024, the rollbacks of the fixes for CVEs affecting [the] optional components have already occurred.
To restore these fixes customers need to install the September 2024 Servicing Stack Update and Security Update for Windows 10.”Indeed, Microsoft says people should install both the servicing stack update KB5043936 and security update KB5043083, released this Patch Tuesday, in that order “to be fully protected from the vulnerabilities that this CVE rolled back.” Users automatically applying updates will have got this already.There are more details here, which does warn that this may break dual-boot systems that run Windows and Linux, and you’re told to check out a workaround for that.Moving on…Here are the other bugs addressed by Microsoft this week.Azure accounts for plenty of the worst bugs, including three elevation of privilege flaws (CVE-2024-38216, CVE-2024-38220, and CVE-2024-38194, all critical) in the Stack Hub that’s used to run Microsoft’s platform on-prem and Azure Web Apps.Azure’s Network Watcher VM Agent has a pair of similar escalations bugs (CVE-2024-38188 and CVE-2024-43470, both important) and a remote code issue (CVE-2024-43469, also important) in the platform’s CycleCloud HPC orchestrator.SharePoint Server has two critical flaws, CVE-2024-38018 and CVE-2024-43464, allowing attackers with Site Member and Site Owner permissions to execute code remotely. There are 30 elevation of privilege flaws to choose from in this month’s update that could be chained with these two flaws and Microsoft lists both critical flaws as “Exploitation more likely.”Another critical flaw, CVE-2024-38119, stems from a use-after-free remote code execution bug in the Windows Network Address Translation (NAT) code base. An attacker would have to be inside the network already to abuse this and Microsoft lists it as difficult to use and less likely to be exploited.Users of Windows 11 version 21H2 or 22H2 should also remember that next patch Tuesday, October 8, will see support for their operating systems coming to an end for Home, Pro, Pro Education, and Pro for Workstations. If you’re using automatic updates you’ll be prompted to upgrade next month.Adobe’s low-priority patchesPatch Tuesday is not just Microsoft’s party: Adobe has revealed 19 critical issues, 13 important, and three rated as moderate severity. ColdFusion 2021 and 2023 are vulnerable to a CVSS 9.8 issue over using deserialization of untrusted data that would allow arbitrary code access.Adobe has also popped patches for the Windows and macOS versions of Photoshop, Acrobat and Reader, Illustrator, After Effects, Premiere Pro, ColdFusion, Media Encoder, and Audition.Adobe classified all of them as Priority 3, its lowest ranking and reports that there are no exploits in the wild.Intel suggests killing its RAID Web ConsoleAfter releasing 43 security advisories in August Intel delivered just four this month –only one of which is high severity.But one of those advisories addresses 11 CVEs related to “Potential security vulnerabilities in UEFI firmware [that] may allow escalation of privilege, denial of service or information disclosure.”The CVES cover a very extensive list of older mobile, PC and server chips, including Atom, 13th generation and earlier Core processors, and Xeon E5 v3 and prior platforms.A patch is also out for CVE-2024-24968, which would allow a denial of service attacks against the 13th generation of Intel Core processors (and earlier kit) in mobile, desktop and embedded hardware. Xeon D server chips and 3rd-gen scalable systems are also vulnerable.Intel’s Running Average Power Limit interface is vulnerable to CVE-2024-23984, the chipmaker warns, which would allow information disclosure, although only for a privileged user. The issue affects third-generation Xeon D and scalable chips and servers, workstations, and embedded systems.There’s also a warning that all RAID Web Console software is vulnerable to nine CVEs but Intel won’t be issuing fixes since the product went end of life in March. Customers are advised to stop using the software and delete it from their systems.
SAP fixes, then fixes againSAP has issued 19 security notes detailing 16 new patches and three updates to older fixes.All the new security patches are medium severity or less with CVSS scores of six or below.SAP has given the highest priority to fixing earlier issues. Top of its list is CVE-2024-41730, in the BusinessObjects Business Intelligence Platform which has a CVSS score of 9.8, is rated highest by SAP, and was issued last month. The new code extends cover to Release 420 of the Enterprise software component and includes details for a workaround for those that can’t patch yet.SAP’s only high priority note covers CVE-2024-33003, an information disclosure vuln in the Commerce Cloud platform with a CVSS of 7.4 that was also released in August. The latest software extends vulnerability coverage to Release 2211.28 of the platform.CISA warns admins to check two Citrix issuesCitrix has issued high-severity fixes for two flaws in its Workspace app for Windows, affecting the current release before version 2405 and long-term releases before 2402 LTSR CU1.CVE-2024-7889 is a privilege elevation flaw, rated CVSS 7.0, that would allow a local user to upgrade themselves to SYSTEM status because of improper resource handling by the code. CVE-2024-7890, rated CVSS 5.4, sorts out improper privilege management that could also lead to an attacker getting SYSTEM access. Both issues require local access to a target machine.“A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system,” the US security agency warned. “CISA encourages users and administrators to review the following and apply necessary update.”Ivanti irritations, againCISA is also warning about serious problems in Ivanti Endpoint Manager 2022 and 2024, Cloud Service Application 4.6, and Workspace Control 10.18.0.0 and below, months after it reported the software biz was leaving US chemical facilities vulnerable with previous security failings.Endpoint Manager’s problems are the most severe, with 16 CVEs named including a CVSS 10.0 issue that allows full remote code execution on EPM before 2022 SU6, or the 2024 September update, due to the agency portal mishandling untrusted data. Nine other critical CVSS 9.1 issues are also reported, as well as two high priority issues (including an RCE issue) and one medium flaw.There’s a CVE for all versions of Ivanti’s Cloud Service Application 4.6 before patch 519, allowing a remote attacker to run code – but only if they have admin privileges. Workspace Control has six high-severity CVEs, all of which would allow locally authenticated users to upgrade their network privileges. ®“CISA wants you to leap on Citrix and Ivanti issues. Adobe, Intel, SAP also bid for patching priorities Patch Tuesday Another Patch Tuesday has dawned, as usual with the unpleasant…”Source Link: https://go.theregister.com/feed/www.theregister.com/2024/09/11/patch_tuesday_september_2024/ http://109.70.148.72/~merchant29/6network/wp-content/uploads/2024/09/1726020006_506_maxresdefault.jpg #GLOBAL - BLOGGER Patch Tuesday Another Patch Tuesday... BLOGGER - #GLOBAL
0 notes
Text
Managed Server Enterprise Support: What You Need to Know
Enterprise IT environments demand reliable, secure, and high-performance server management to ensure business continuity. Managed server enterprise support provides proactive monitoring, maintenance, security, and troubleshooting for on-premises, cloud, or hybrid infrastructures.
1. Key Features of Managed Server Enterprise Support
🔹 24/7 Monitoring & Performance Optimization
✔ Real-time server health monitoring (CPU, memory, disk, network usage) ✔ Proactive issue detection to prevent downtime ✔ Load balancing & resource optimization
🔹 Security & Compliance Management
✔ Firewall & intrusion detection to block cyber threats ✔ Patch management & software updates to fix vulnerabilities ✔ Compliance audits (ISO 27001, HIPAA, GDPR)
🔹 Backup & Disaster Recovery
✔ Automated backups with offsite storage ✔ Disaster recovery solutions for business continuity ✔ RAID configuration & data redundancy
🔹 Server OS & Software Support
✔ Windows Server (2016, 2019, 2022) & Linux distributions (Ubuntu, CentOS, RHEL) ✔ Database management (MySQL, PostgreSQL, MS SQL) ✔ Virtualization & cloud integration (VMware, Hyper-V, AWS, Azure)
🔹 Helpdesk & Technical Support
✔ Dedicated IT support team with rapid response times ✔ Troubleshooting & issue resolution ✔ Custom SLAs for uptime guarantees
2. Types of Managed Server Enterprise Support
🔹 On-Premises Server Management
✔ Ideal for businesses with in-house data centers ✔ Supports hardware maintenance, OS updates, security patches ✔ Best for: Enterprises requiring full control over infrastructure
🔹 Cloud & Hybrid Server Management
✔ Managed services for AWS, Azure, Google Cloud ✔ Optimized for cloud security, scalability & cost-efficiency ✔ Best for: Enterprises adopting hybrid or multi-cloud strategies
🔹 Fully Managed vs. Co-Managed Support
✔ Fully Managed: Service provider handles everything (monitoring, security, backups, troubleshooting) ✔ Co-Managed: Internal IT team works alongside provider for collaborative management
3. Benefits of Enterprise Server Support
🔹 Minimized Downtime: 24/7 monitoring & quick response prevent disruptions 🔹 Stronger Security: Proactive firewall management, encryption & threat monitoring 🔹 Scalability: Adapt server resources as business grows 🔹 Cost Savings: Reduces IT staff workload & lowers infrastructure costs 🔹 Compliance Assurance: Meets industry security & legal requirements
4. How to Choose the Right Managed Server Provider
✔ Service Level Agreements (SLAs): Ensure 99.9%+ uptime guarantees ✔ Security Protocols: Must include firewalls, DDoS protection, and backups ✔ Support for Your Tech Stack: Compatible with Windows/Linux, databases, virtualization ✔ Customization & Scalability: Can adjust services based on business growth ✔ 24/7 Support & Response Time: Fast issue resolution & technical assistance
5. Cost of Managed Server Enterprise Support
💰 Pricing Models: ✔ Per Server: $100–$500/month (basic), $500–$2,500/month (enterprise) ✔ Per Resource Usage: Based on CPU, RAM, storage & bandwidth ✔ Custom Plans: Tailored pricing for hybrid & multi-cloud environments
6. Who Needs Managed Server Enterprise Support?
✔ Large Enterprises: Need mission-critical uptime & security ✔ eCommerce & SaaS Businesses: Require high-performance cloud hosting ✔ Financial & Healthcare Organizations: Must comply with data security regulations ✔ Growing Startups: Benefit from scalable, cost-effective infrastructure
Need a Custom Managed Server Plan?
Let me know your server type, workload, and business needs, and I can recommend the best managed enterprise support solution!

0 notes
Text
SQL Server is quickest way to your Data Analytics journey, says expert
SQL server tools get you through the whole, end-to-end ‘data ecosystem’; where you learn data engineering, data warehousing, and business intelligence all in single platform
Microsoft SQL Server is currently leading the RDBMS market with its tremendously diverse tools and services for data analytics. Whether it’s data management, analysis or reporting, you get all in one package, that too for free.
Given that SQL server provides an end-to-end exposure to the whole data ecosystem, learning SQL server is the quickest path to your data analytics journey..
Note: This career advice is for newbies just starting their analytics journey, as well as for technical geeks who wish to opt for SQL server job roles.
Table of contents
Data Ecosystem and SQL Server Tools
How can SQL Server help me begin a Career in Data Analytics?
Career Tracks to target a job role
Learn SQL Server Tools
Watch Webinar!
Data Ecosystem and SQL Server tools
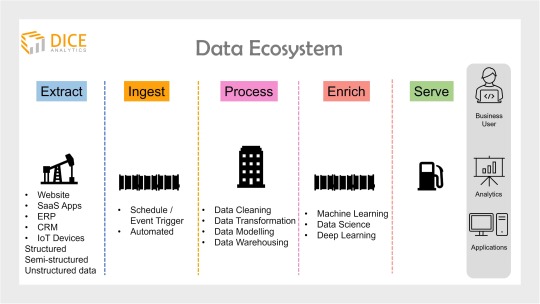
Data ecosystem is the backbone of any organization’s data analytics project.
Simply put, a data ecosystem documents and presents infrastructure and applications for data storage and processing.
Any data ecosystem portrays four to five stages of data, depending on the organization’s objectives.
Starting off, a data expert always needs to collect data from the vast sources of the organization. This includes, website data, SaaS applications, IoT devices, CRM, ERP etc.
Next, all of the data from diverse sources is gathered over a common place through a process called ingestion.
Integrated on a single database, this data needs to be cleaned, transformed and organized into a universal format (data harmonization) to avoid misalignment across the ecosystem.
This process is called data warehousing (aka data engineering).
Optional is to further enrich data using machine learning technology. One of the main data science job roles is to apply predictive analytics at this stage.
Finally, at the last stage, data is analyzed and presented to business users for value driving and decision making. A BI developer or engineer is specialized to handle data visualization at this stage.
SQL Server tools and services offer a low code environment to all of the above steps and therefore quickly and easily helps to build an end-to-end data ecosystem for an organization.
The tools and services can be broadly classified as data management and business intelligence (BI) functionalities.
For data management, SQL Server provides SQL Server Integration Services (SSIS), SQL Server Data Quality Services, and SQL Server Master Data Services.
SQL Server provides SQL Server Data tools for building a database. And for management, deployment, and monitoring the platform has SQL Server Management Studio (SSMS).
SQL Server Analysis Services (SSAS) handle data analysis.
SQL Server Reporting Services (SSRS) are used for reporting and visualization of data.
Earlier known as the R services, the Machine Learning Services came as part of SQL Server suite in 2016 and renamed afterwards.
How can SQL Server help me begin a Career in Data Analytics?
When you learn SQL Server, it exposes you to the complete data ecosystem. This helps you in your career advancement in two ways.
Access to the vast SQL Server jobs
Microsoft SQL Server currently stands at 3rd rank (after Oracle and MySQL) in the world’s most used commercial relational databases. This is because Microsoft offers an intensely feature-rich version of SQL Server for free.
This makes SQL server skills one of the most in-demand across the data analytics ecosystem.
Tip: For newbies, and those with career transitions, if you want to land on an analytics job quickly, learning SQL server tools is a smart idea since the job market is lucrative.
Further, once in, as you move along in your career we recommend growing your skill set and ascending towards more specific job roles, for example, data engineer and BI developer.
Career Tracks to target a job role
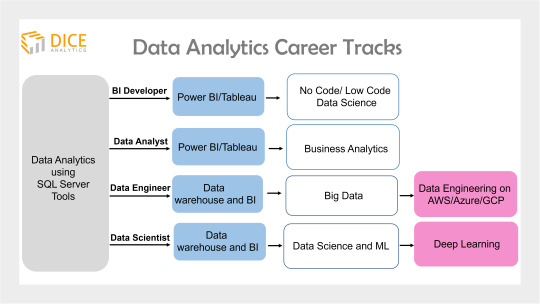
Once you get a grab of the end-to-end data analytics ecosystem, now it’s a step to move forward in your analytics journey.
But why?
Data analytics is a broad field, and carries lucrative job opportunities in the form of various job roles available in the market.
Moreover, given a myriad of job roles, you can opt for a career in the field of your interest.
What are the career tracks when I work with SQL server?
Become a Data Engineer
Once getting to know what data engineering holds, you can now opt for a vendor specific data engineering skills.
For example, Teradata is a market leader in on-premise data warehousing solutions. Learning data engineering on Teradata will offer bright career prospects in the data analytics field.
While SQL Server and Teradata RDBMS have a data architecture built for small scale data, when it comes to data volumes up to petabytes size, these solutions don’t work.
Thus a data engineer can move to learning big data technology that holds even brighter career prospects (read about the blooming big data market forecast).
Become a BI Developer/BI Engineer
This job role narrows to the data visualization, and reporting only. A BI developer is expert in BI tools such as Power BI and Tableau.
As a next step, a BI Developer can also opt for no code/low code Data Science using Knime.
Become an ML Engineer
A Machine Learning engineer uses ML technology to employ predictive analytics and finds out future trends and patterns within data.
The requirement for an ML engineer is to understand how databases and data warehousing works, and needs to build a strong foundation in that.
Next, you can opt for Deep Learning in your career journey for better positions in large enterprises.
Become a Data Analyst
After getting to work with SQL server tools, you can also opt data analyst as your career choice. This requires you to build expertise in BI tools such as Power BI and Tableau.
The next step for career advancement is to learn Business Analytics that deals with business data and marketing analytics.
You might want to view Business Analytics career prospects and salary in Pakistan.
Interested in Learning SQL Server Tools?
Dicecamp offers an 8 weeks course* on Learning SQL Server Tools.
The course covers four tools; SQL Server Integrated Services (SSIS), SQL Server Management Services (SSMS), Azure Cloud, and Power BI.
You will learn:
SQL hands-on
DWH building using SSIS
Data Management using SSMS
AZURE SQL CONFIG, DTU basics
DAX implementation in Power BI
Data visualization in Power BI
Visit complete course outline and registration details here.
*We offer flexible pricing and valuable concessions.
Straight from the Horse’s Mouth!

The instructor of this course is Mr. Abu Bakar Nisar Alvi who’s Pakistan’s celebrated engineer awarded Tamgha e Imtiaz (fourth highest civil rank) for his excellent engineering performance back in 2005.
Mr. Alvi serves as a senior IT consultant at the World Bank with key experience in enabling digital transformation as part of the village service delivery in Indonesia.
Taking two decades of experience and vast work diversity, Mr. Alvi is now associated with Dicecamp as a lead trainer Data Analytics and Visualization.
Webinar: Watch him speaking on ‘Why to Learn SQL Server Tools’ in the latest webinar (LinkedIn Webinar Link).
#dicecamp#datascience#careertest#devops#dataengineercourse#datawarehouse#devopscourse#datawarehousecourse#sqlserver#sql#mysql
1 note
·
View note
Text
Configure SQL Server Instance to listen on a specific TCP Port
In this blog post, we shall discuss how to Configure SQL Server Instance to listen on a specific TCP Port using SQL Server Configuration Manager. The default instance of Microsoft SQL Server listens on TCP Port 1433. This is the default port for communication between Microsoft SQL Server and its applications. Here is a similar article on Setup is unable to access the SQL UDP Port 1434 on the…

View On WordPress
#Configure SQL Server Instance to listen on a specific TCP Port#Microsoft Windows#MsSQL#Ports#SQL Server service#SQL TCP Ports#Windows#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes