#Secure Store Service Application
Explore tagged Tumblr posts
Text
Overcoming Common Challenges in SharePoint Server Installation
SharePoint Server, a powerful collaboration and content management platform, provides organizations with robust functionalities. However, the installation process can present various challenges that may hinder a seamless deployment. In this article, we will explore common issues faced during SharePoint Server installation and provide probable solutions to overcome them. “The tool was unable to…

View On WordPress
#Access Privileges#Application Services Configuration#Central Administration#Collation Settings#Configuration Database#Database Connectivity#Deployment Challenges#Disk Space#Firewall Interference#Hardware Requirements#Installation Issues#Internet Connectivity#Memory Exception#Probable Solutions#Secure Store Service Application#Service Account#SharePoint Prerequisites#SharePoint Search Service#SharePoint Server#SharePoint Timer Service#SQL Server Permissions#Troubleshooting#User Profile Service Application#Windows Features
0 notes
Text
Musk associates given unfettered access to private data of government employees
Several of Elon Musk’s associates installed at the Office of Personnel Management (OPM) have received unprecedented access to federal human resources databases containing sensitive personal information for millions of federal employees. According to two members of OPM staff with direct knowledge, the Musk team running OPM has the ability to extract information from databases that store medical histories, personally identifiable information, workplace evaluations, and other private data. [...] The arrangement presents acute privacy and security risks, one of the OPM staffers said. [...] The civil servants who oversee the OPM’s information technology services were then instructed to provide access to Musk's associates, according to the OPM staffers who spoke to Musk Watch. One of the OPM staffers received an email from the agency’s new leadership instructing them to give Musk’s team “access [to] the system as an admin user" and "code read and write permissions." “They have access to the code itself, which means they can make updates to anything that they want,” the staffer explained. USAJOBS, the federal government’s official hiring site, was one of the systems that Musk's associates were given access to. The database stores personal information — Social Security numbers, home addresses, employment records — provided by private individuals who have applied for federal jobs, regardless of whether the applicants went on to work for the government. Musk’s aides were also given access to the OPM’s Enterprise Human Resources Integration (EHRI) system. Contained within the EHRI are the Social Security numbers, dates of birth, salaries, home addresses, and job descriptions of all civil government workers, along with any disciplinary actions they have faced. “They’re looking through all the position descriptions… to remove folks,” one of the OPM staffers said of Musk’s team. “This is how they found all these DEI offices and had them removed — [by] reviewing position description level data.” Other databases Musk’s team has access to include USA Staffing, an onboarding system; USA Performance, a job performance review site; and HI, which the government uses to manage employee health care. “The health insurance one scares me because it's HIPAA [protected] information, but they have access to all this stuff,” the OPM staffer noted.
75 notes
·
View notes
Text
$7.25 $1231
Apply today Sign up for text alerts to see drive-thru pantries in your area Join us after services for a homemade meal and prayer support Limited to single mothers, the elderly, and the unemployed Sign up for a backpack plan: food assistance for low income families If you are in need of a hot meal join our waiting list Include your email for notifications if your cart is funded Your application will be reviewed in 7-10 business days Weekly shared meals on Tuesday at 2:30pm Those with current government ID and a local address are welcome What documents you need to sign up for SNAP benefits LEARN: click this link for tips on nutrition LEARN: where to find coupons online LEARN: penny-pinching tips at the grocery store LEARN: how to start a saving plan LEARN: part-time jobs that will work with your schedule r/personalfinace r/povertyfinance r/randomactsofpizza r/beermoney First time Donor? What you need to know First weekly visit: $40 Second weekly visit: $70 How to treat a hemotoma at home Can meditation lower your resting heart rate? Five foods high in iron Three signs that you might be dehydrated Securing a loan is easy and fast Available to consumers at all levels of credit To help cover life's little emergencies Your title is returned when the lien is released Get approved in minutes Apply today
589 notes
·
View notes
Text
Today, the Supreme Court handed down opinions in TikTok Inc. v. Garland, No. 24-656, slip op. (U.S. Jan. 17, 2025), sustaining the federal law banning the social media platform.
For my own sake, I tried to figure out what the law says and does, bracketing the First Amendment issues.
I.
The federal law at issue is the Protecting Americans from Foreign Adversary Controlled Applications Act, Pub. L. No. 118-50, div. H, 138 Stat. 955. It's a division of an April 2024 appropriations bill, a bundle that came with aid for Israel and Ukraine.
The Act targets "foreign adversary controlled applications," which it defines, in part, as applications operated by ByteDance, TikTok, their subsidiaries or successors, or any entity they own or control. § 2(g)(3)(A), 138 Stat. at 958.
The Act's prohibitions address app stores and web hosts. They're the ones who have to deny support to "foreign adversary controlled applications," and keep them off their platforms.
The Act makes it unlawful "to distribute, maintain, or update" the app by providing either (A) "a marketplace" through which users in the United States "may access, maintain, or update" the application, or (B) "internet hosting services" that enable "distribution, maintenance, or updating" for users in the United States. § 2(a)(1).
These prohibitions are only applicable to the territory of the United States and those within it. They address "carrying out, within the land or maritime borders of the United States," acts for "users within the land or maritime borders of the United States."
The territorial language, "the land and maritime borders of the United States," is not defined within the Act. Nor is it defined anywhere else in the U.S. Code. It's only used once. 6 U.S.C. § 124h(e).
That said, deducing "the land and maritime borders of the United States" should be fairly straightforward for someone familiar with the relevant boundary treaties and law of the sea, as understood by the political branches. It's just not something I understand.
II.
The Act targets "foreign adversary controlled applications," which it defines, in part, as applications operated by ByteDance, TikTok, their subsidiaries or successors, or any entity they own or control. § 2(g)(3)(A), 138 Stat. at 958.
The Act extends to covered companies "controlled by a foreign adversary," following a public notice and a public report to Congress, § 2(g)(3)(B), but ByteDance and TikTok are the only persons identified by name.
The language seems broad. But "controlled by foreign adversary" is fairly narrow. It means persons domiciled in "foreign adversary countries," entities they have a 20 percent stake in, and persons subject to their direction or control. § 2(g)(1). That's it.
The term "foreign adversary country" is defined obliquely, § 2(4), by reference to a military minerals procurement rule, 10 U.S.C. § 4872, but it only covers four countries, specified by name: North Korea, China, Russia, and Iran. 10 U.S.C. § 4872(d)(2).
The President could, in other words, ban applications operated by persons domiciled in North Korea, China, Russia, or Iran, or entities in which such persons have a 20 percent stake, or entities subject to their direction or control.
It doesn't sweep much further than that.
III.
The "foreign adversary country" limitation means the Act isn't an unconstrained delegation to the President.
It's not like the President's authority to "suspend the entry of all aliens or any class of aliens as immigrants or nonimmigrants, or impose on the entry of aliens any restrictions he may deem to be appropriate." 8 U.S.C. § 1182(f); Exec. Order No. 13,769, 82 Fed. Reg. 8977 (Jan. 27, 2017).
Nor is it like the President's authority to restrict entry from countries "designated by the Secretary of State," or "designated by the Secretary of Homeland Security." 8 U.S.C. § 1187(a)(12); Exec. Order No. 13,780, § 1(b)(i), 82 Fed. Reg. 13209 (March 6, 2017).
Nor is it like the President's claimed authority to bar "any transaction by any person, or with respect to any property, subject to the jurisdiction of the United States, with ByteDance Ltd.," Exec. Order No. 13,942, § 1(a), 85 Fed. Reg. 48637 (Aug. 6, 2020), a claim that proved wanting. TikTok Inc. v. Trump, 507 F. Supp. 3d 92 (D.D.C. 2020); Marland v. Trump, 498 F. Supp. 3d 625 (E.D. Pa. 2020).
The Act is, mercifully, is more constrained than that.
27 notes
·
View notes
Text
Elon Musk asserted last week that before any US federal employee can retire, their paper records have to be processed more than 200 feet underground in an old limestone mine located in rural Pennsylvania, which he said often takes months. “And then the speed—the limiting factor is the speed—at which the mine-shaft elevator can move determines how many people can retire from the federal government,” Musk said, standing next to a seated President Donald Trump in the Oval Office. “And the elevator breaks down sometimes, and then nobody can retire—doesn’t that sound crazy?”
While Musk’s comment about elevator dependency is overstated—the mine has many entrances and exits, as well as a road leading in and out that golf carts and other vehicles can drive on—his general point about inefficiencies within the federal retirement process is true. The Office of Personnel Management, which functions as the human resources department of the US government, tells retirees to expect a three- to five-month wait to process their applications. And retirement paperwork for federal employees does route through a storage facility in a repurposed limestone mine in rural Boyers, about 50 miles north of Pittsburgh.
When the system at Boyers was first established decades ago, putting retiree archives and processing files under one roof that was both remote and secure made a lot of sense. But over time, a systematic lack of resources, combined with repeated failed attempts to automate and digitize, created the “sinkhole of bureaucracy” that is the federal retirement hub today.
Six years ago, the Government Accountability Office reported that the OPM’s retirement system was still plagued by a “continuing reliance on paper-based applications and manual processing.” The agency's average retirement file processing time was about 60 days in 2019, which is only a modest decrease from 1981, when it took 98 days, but the agency processed almost twice as many applications.
But David Carmicheal, who recently retired as state archivist of Pennsylvania and has corresponded with staff at the Boyers facility, tells WIRED it’s a mistake to only view OPM’s process as “woefully outdated.”
“Much of the work that goes on at Boyers, as I understand it, is digital, so the idea of people trundling piles of paper through dark mine shafts is absurd,” Carmicheal says. “In fact, these facilities are meant to protect you and me by protecting the records that safeguard our legal rights, our public benefits.”
When reached for comment, the Government Accountability Office referred WIRED to its most recent publications. The Office of Personnel Management did not respond to a request for comment.
Going Underground
The Civil Service Commission, the predecessor of the OPM, started mailing retirement files to Boyers in 1960 with the intent to archive them “forever.” The CSC was one of many agencies that took advantage of repurposed mines and caves during the Cold War, seeking enhanced protection for sensitive materials in the event of a nuclear catastrophe.
The Boyers mine was operational from 1902 to roughly 1959 under the helm of US Steel. When high operating costs and dwindling demand for limestone caused the business to decline in the 1950s, US Steel employee Larry Yont saw an opportunity to repurpose the site as a storage facility and, with the help of civil engineer and mine superintendent Russell Mitchell, went on to found National Underground Storage. It was later bought by the company Iron Mountain in 1998, which owns and leases the Boyers mine to this day.
Along with the Civil Service Commission, other federal agencies, including the National Archives, the Office of Civil Defense (the precursor to the Federal Emergency Management Agency), and the Social Security Administration began storing records in the Boyers facility around the same time. J. G. Franz, then office manager of the Boyers mine, told a newspaper reporter in 1966 that federal agencies have “backup equipment for everything” stored in a special area of Boyers to protect the records in the event of nuclear fallout.
Franz told a local newspaper that workers “hope we will never have to worry about a nuclear explosion,” but that if one happened, the mine would be safely sealed off, according to newspaper archives reviewed by WIRED. “The mine is equipped with a 30-day supply of food and supplies for all of the employees.”
At the time, the staff at Boyers were reportedly able to process about 600 pounds of records each day bussed to the facility straight from Washington, DC. They relied on the recently constructed interstate highway system for timely deliveries. In fact, the federal government built an exit off Pennsylvania’s Interstate 80 specifically for “quick access to the mine in case of an emergency,” according to an article in the Pittsburgh Press.
There are other practical benefits that make old mines a good place to store records. For one, their typically rural and secluded settings create a layer of natural security from other types of threats. Repurposed mines provide “excellent fire protection,” and immunity from events like “flood, theft, civil disorder, aircraft crashes, tornadoes, lightning,” noted a 1999 Iron Mountain presentation for the National Archives.
Carmichael tells WIRED that access to the underground facilities he’s visited tend to be tightly controlled, often through heavily guarded entrances. These facilities also frequently have maze-like designs that would likely discourage or confuse thieves if they somehow got inside.
Several current managers of repurposed limestone mines told WIRED that their caves are naturally between 55 and 70 degrees Fahrenheit, optimal temperature for most storage situations. John Smith, director of industrial real estate for the company that manages the limestone storage facility Carefree Industrial Park near Kansas City, Missouri, said that this means utility costs are “dramatically lower” compared to above-ground facilities. His main expenses are associated with ventilation, since caves tend to be very humid.
It All Goes Wrong
Shortly before the Civil Service Commission arrived at Boyers, the US federal retirement apparatus was a mess. A 1951 government report found that “an adequate record system” wasn’t even in place yet and urged Congress to “insist” one be created. At first, it seemed like the team at Boyers was able to turn things around. The News-Herald reported in 1966 that with just 55 employees, the system at the mine was operating “with the same efficiency and effectiveness as it used to in Washington, DC.”
However, as the number of retirees continued to climb, things fell into disarray. By the early 1980s, the Office of Personnel Management was being audited to find the root causes of excessive delays in processing retirement claims. In 1981, the Government Accountability Office recommended that OPM “develop a long-term plan for automating the retirement claims process.”
OPM tried to launch an automated system in 1987, only to shut it down in 1996 when it failed an independent review. It began planning a new system, but gave up in 2001 and decided to contract the work out. The contracts weren’t awarded until 2006. The system they eventually built, RetireEZ, was finally launched in 2008, but it too was promptly shut down due to “quality issues.”
Little progress was made until 2013, when OPM launched a new “strategic vision” for a totally “paperless system.” Around that time, the agency was able to partially digitize the retirement process, allowing retirees to receive 80 percent of their pension quickly. But to get the full value, physical files still had to go through Boyers, according to a 2014 feature story in The Washington Post.
By 2019, the Government Accountability Office reported that OPM didn’t have enough money to finish digitizing. The agency was then piloting what it called the Electronic Retirement Record system, which was supposed to replace hard copies altogether. As part of the improvements, OPM was also trying to fix “inconsistent data between electronic and paper records,” according to the Government Accountability Office. Boyers workers would sometimes have to track down the physical copies of records by navigating through what had become essentially a small city of shelves and files, or type up other files that weren’t digitized.
Despite all of these efforts, the OPM still hasn’t finished digitizing the retirement process. It’s been a decade since the agency updated its internal guide for processing retirement applications. The Government Accountability Office attributed the slow pace of progress to “the continuing reliance on paper-based applications and manual processing,” lack of staffing, and OPM frequently receiving incomplete submissions.
Musk and DOGE have defunded and started to hollow out a slew of government agencies. While the centibillionaire has identified Boyers as a prime example of government inefficiency, he hasn’t described a clear vision for fixing the retirement system.
Despite their shortcomings, Carmicheal tells WIRED that it’s important to remember why government bureaucracies and record-keeping systems were set up in the first place. “I’m just thankful that we have had a long history in this country of governments that care about protecting their citizens,” Carmichael says, “and that includes safeguarding the records that document our rights and the responsibility of governments toward us.”
8 notes
·
View notes
Text
How to Prove Your Identity in Canada Without a Driver’s License
In Canada, a driver’s license is one of the most widely accepted forms of identification. But what if you don't drive or don't yet have a license? Fortunately, there are several other valid ways to prove your identity when you need to access services, verify your age, or complete important transactions. Understanding these options ensures that you’re always prepared — even without a driver's license in hand.

1. Primary Forms of Non-Driver Identification
If you don't have a driver’s license, you can use other government-issued ID cards to prove your identity. Some of the most commonly accepted alternatives include:
Canadian Passport: A passport is the gold standard for proof of identity and citizenship. It's accepted almost everywhere for identification purposes.
Provincial or Territorial Photo ID Cards: Many provinces offer official photo ID cards for non-drivers. For example, Ontario offers the Ontario Photo Card, while British Columbia has the BC Services Card.
Permanent Resident (PR) Card: For newcomers, a PR card serves as both proof of identity and legal status in Canada.
Citizenship Certificate or Card: This document proves Canadian citizenship and includes your name, photo, and signature.
Secure Certificate of Indian Status (SCIS): For Indigenous individuals, this government-issued card is an accepted form of ID.
Each of these IDs provides verifiable details such as your full name, date of birth, photograph, and often your signature, meeting requirements for official identification.
2. Secondary Identification Options
Sometimes, institutions may request two pieces of ID: one with a photo and one with supporting information. In that case, you can present documents like:
Health Card (with photo) — depending on the province.
Social Insurance Number (SIN) card or letter (usually as secondary ID).
Birth Certificate.
Bank or credit cards with your name printed.
Utility bills or rental agreements showing proof of address.
It’s always best to check ahead of time what forms of ID are accepted, especially for critical processes like banking, healthcare registration, or government applications.
3. Why a Provincial ID Card Is a Smart Move
If you don't drive but need a reliable piece of photo ID, applying for a provincial photo identification card is highly recommended. These cards are issued by your provincial or territorial government and often require similar documents as a driver's license application — proof of identity, proof of residency, and proof of legal status in Canada.
This card can make everyday tasks — such as picking up packages, accessing government services, or even entering age-restricted venues — much smoother.
4. Stay Informed and Prepared
No matter which ID you use, keeping it current and securely stored is crucial. Always make sure your name, address, and other details are updated promptly after major life changes like moving or marriage.
Need help navigating the different forms of identification in Canada or preparing for your future licensing needs? Check out LicensePrep.ca — your trusted resource for expert guides, ID tips, and practice tests to help you stay ready and confident!
#CanadianID#NonDriverID#IdentityVerificationCanada#LicensePrepCanada#CanadianPassport#PermanentResidentCard#SecureID#CanadaIdentification#ProofOfIdentity#PhotoIDCanada
5 notes
·
View notes
Text
Caleb Ecarma and Judd Legum at Popular Information:
Several of Elon Musk’s associates installed at the Office of Personnel Management (OPM) have received unprecedented access to federal human resources databases containing sensitive personal information for millions of federal employees. According to two members of OPM staff with direct knowledge, the Musk team running OPM has the ability to extract information from databases that store medical histories, personally identifiable information, workplace evaluations, and other private data. The staffers spoke on the condition of anonymity because they were not authorized to speak publicly and feared professional retaliation. Musk Watch also reviewed internal OPM correspondence confirming that expansive access to the database was provided to Musk associates.
The arrangement presents acute privacy and security risks, one of the OPM staffers said. Among the government outsiders granted entry to the OPM databases is University of California Berkeley student Akash Bobba, a software engineer who graduated high school less than three years ago. He previously interned at Meta and Palantir, a technology firm chaired by Musk-ally and fellow billionaire Peter Thiel. Edward Coristine, another 2022 high school graduate and former software engineering intern at Musk’s Neuralink, has also been given access to the databases.
Other Musk underlings embedded at OPM following President Donald Trump’s inauguration include the agency’s new chief of staff, Amanda Scales, who until January was a human resources staffer at xAI, Musk’s artificial intelligence firm, and Brian Bjelde, who has spent the past 21 years at Musk's SpaceX, including the last 10 leading the human resources department. They are joined by Gavin Kliger, a former Twitter software engineer serving as a special advisor to the director of OPM, and Riccardo Biasini, a former software engineer at Musk’s tunneling venture, the Boring Company. OPM did not respond to a request for comment. Shortly after Trump took office, OPM installed Greg Hogan to serve as its new chief information officer (CIO). Hogan was tapped to replace OPM CIO Melvin Brown, who had accepted the job less than a month ago. The civil servants who oversee the OPM’s information technology services were then instructed to provide access to Musk's associates, according to the OPM staffers who spoke to Musk Watch. One of the OPM staffers received an email from the agency’s new leadership instructing them to give Musk’s team “access [to] the system as an admin user" and "code read and write permissions." “They have access to the code itself, which means they can make updates to anything that they want,” the staffer explained. USAJOBS, the federal government’s official hiring site, was one of the systems that Musk's associates were given access to. The database stores personal information — Social Security numbers, home addresses, employment records — provided by private individuals who have applied for federal jobs, regardless of whether the applicants went on to work for the government. Musk’s aides were also given access to the OPM’s Enterprise Human Resources Integration (EHRI) system. Contained within the EHRI are the Social Security numbers, dates of birth, salaries, home addresses, and job descriptions of all civil government workers, along with any disciplinary actions they have faced. “They’re looking through all the position descriptions… to remove folks,” one of the OPM staffers said of Musk’s team. “This is how they found all these DEI offices and had them removed — [by] reviewing position description level data.” Other databases Musk’s team has access to include USA Staffing, an onboarding system; USA Performance, a job performance review site; and HI, which the government uses to manage employee health care. “The health insurance one scares me because it's HIPAA [protected] information, but they have access to all this stuff,” the OPM staffer noted.
[...] A new server being used to control these databases has been placed in a conference room that Musk’s team is using as their command center, according to an OPM staffer. The staffer described the server as a piece of commercial hardware they believed was not obtained through the proper federal procurement process. There is a legal requirement that the installation of a new server undergo a Privacy Impact Assessment (PIA), a formal process to ensure the change would not create any security vulnerabilities. But in this instance, the staff believes there was no PIA. “So this application and corresponding hardware are illegally operating,” they added. On Friday, Reuters reported that some senior civil servants have been blocked from accessing the EHRI and other OPM systems, making it difficult for career OPM employees to know what Musk’s team has been examining or modifying. In the same report, the outlet revealed the team had moved sofa beds into the agency's headquarters to continue their work around the clock.
This should be a major national news scandal.
Elon Musk and the underlings he put in place at the Office of Personnel Management (OPM) have jeopardized data privacy and national security.
#Elon Musk#DOGE#Department of Government Efficiency#Trump Administration#Office of Personnel Management#USA Peformance#HIPAA#Enterprise Human Resources Integration#Amanda Scales#Data Breach#Privacy Impact Assessment#Data Privacy#Musk Coup
9 notes
·
View notes
Text
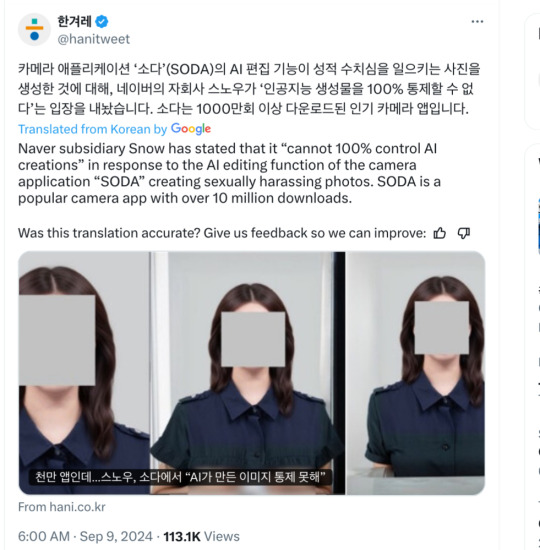
below is a machine translation of the article into english. If you see any discrepancies lmk and I’ll fix it asap. Thanks everyone for your help and continued patience
Ten Million Downloads for the Photo App 'SODA'… Criticism Over AI Being Out of Control Subsidiary of Naver, Snow, Responds Mechanically to AI-Generated Inappropriate Content
Snow, a subsidiary of Naver and the creator of the camera application 'SODA', has come under fire for generating sexually inappropriate images using its AI editing function. The company has stated that it "cannot 100% control AI-generated content," sparking criticism from experts who argue that commercializing an uncontrollable AI service is irresponsible. SODA is a popular camera app with over 10 million downloads on the Google Play Store.
Ms. G, an office worker, complained in an online messenger conversation with Hankyoreh on the 9th, “I didn't expect to feel shame while using the app. It's so unpleasant and traumatizing.” On the 4th, she applied the 'AI background expansion' feature, a paid service of the Soda app, to her photo. The intention was to correct the photo, which was cropped in the middle of her shoulders, to show her entire upper body, but the AI generated a result that made her appear to be clutching her chest with both hands. The rest of the results were normal, but Ms. G said it was hard to get over the shock of the image she suddenly received while using the app.
In response, Snow explained, “Due to the nature of the service that applied A.I. technology, the result was unexpected.” Snow explained that the AI-generated images are filtered to remove offensive or sexualized images as much as possible before they are finally displayed to the user, but this feature did not work perfectly in G's case.
However, experts argue that the issue is more complex. The core problem lies in the AI image generation engine applied to the SODA app, called 'Stable Diffusion'. Developed primarily by the UK startup Stability AI, it was revealed that this model had included explicit content in its training data. Professor Kim Myung-joo of Seoul Women’s University (Information Security) explained, “Unlike other AI models, Stable Diffusion was designed to generate graphic images and included pornographic content in its training data, which has raised concerns since its release.”
Experts are calling for measures like age restrictions on the app to prevent irresponsible commercialization. At the moment, SODA is rated for use by individuals aged 3 and older. Jang Yeo-gyeong, the director of the Information Rights Research Institute, stated, "Even if it doesn't lead to sexual exploitation, consumers who suffer mental harm from AI tools should be able to hold the companies that release these services accountable. Snow's response that 'current technology can't prevent this' is irresponsible."
In response to The Hankyoreh, a Snow representative said, "All companies utilizing AI are struggling to address issues like this. We are working to enhance the service by strengthening filters to prevent similar cases in the future."
plain text in the original Korean
카메라 애플리케이션(앱) ‘소다’(SODA)의 인공지능(AI) 편집 기능이 성적 불쾌감을 일으키는 사진을 생성한 사례가 발생한 것에 대해 이 앱을 만든 네이버의 자회사 스노우가 ‘인공지능 생성물을 100% 통제할 수 없다’는 입장을 내놨다. 통제할 수 없는 인공지능 서비스를 상업화한 것에 대해 무책임한 행태라는 전문가들의 지적이 나온다. 소다는 스마트폰 앱 장터인 ‘구글 플레이 스토어’에서 1000만회 이상 다운로드된 인기 카메라 앱이다.
직장인 ㄱ씨는 9일 한겨레와 온라인 메신저 대화를 통해 “앱을 사용하다 수치심을 느낄 줄 몰랐다. 너무 불쾌하고 정신적 충격이 크다”고 호소했다. 그는 지난 4일 소다 앱의 유료 서비스인 ‘인공지능 배경 확장’ 기능을 자신의 증명사진에 적용했다. 어깨 부분 중간에 잘린 증명사진을 상반신 전체가 나오는 모습으로 보정하려는 의도였는데, 실제 인공지능이 생성한 결과물에선 자신이 가슴을 양손으로 움켜쥐고 있는 듯한 모습이 나왔다. 이 이미지를 제외한 다른 나머지 결과에선 정상적인 사진이 나왔지만, ㄱ씨는 앱을 사용하다 갑자기 받은 이미지의 충격에서 벗어나기 힘들었다고 했다.
이에 대해 스노우 쪽은 “인공지능 기술이 적용된 서비스의 특성상 결과물이 예상치 못한 형태로 구현된 것”이라고 설명했다. 인공지능이 생성한 이미지를 사용자에게 최종적으로 노출하기 전 필터 기술을 통해 모욕적이거나 선정적인 이미지를 최대한 제거하고 있지만, ㄱ씨의 사례에선 이 기능이 완벽하게 작동하지 않았다고도 설명했다.
하지만 문제가 간단치 않다는 게 전문가들의 지적이다. 소다 앱에 적용된 인공지능 이미지 생성 엔진인 ‘스테이블 디퓨전’ 자체에 문제가 있다는 이유에서다. 스테이블 디퓨전은 영국 스타트업 ‘스태빌리티 에이아이(AI)’가 개발을 주도한 모델인데, 개발 단계에서 음란물을 학습 데이터에 포함시킨 것으로 알려져 있다. 김명주 서울여대 교수(정보보호학)는 “다른 인공지능 모델과 달리 스테이블 디퓨전은 그래픽 이미지를 생성하기 위한 목적으로 포르노 영상물을 학습 데이터에 포함했기 때문에 공개될 때부터 많은 우려가 제기됐다”고 말했다.
전문가들은 소다 앱의 이용자 연령을 제한하는 등의 방식으로 기업의 무책임한 상업화를 막아야 한다고 지적했다. 현재 소다 앱은 3살 이상이면 누구나 사용할 수 있다. 장여경 정보인권연구소 상임이사는 “성착취물로 연결되지 않는다고 해도 인공지능 도구로 정신적 피해를 입은 소비자들이 서비스를 출시한 기업에 대해 최소한의 주의 의무를 요구할 수 있어야 한다”며 “‘현재 기술로는 막을 수 없다’는 스노우의 태도는 무책임하다”고 꼬집었다.
스노우 관계자는 한겨레에 “인공지능을 활용하는 모든 회사가 이번과 같은 이슈를 해결하기 위해 분투하고 있다. 유사한 사례가 발생하지 않도록 필터를 더욱 강화하는 등 서비스 고도화를 노력하겠다”고 했다.
#South korea#deepfake crimes#naver#snow app#soda app#Beauty filter app#Ai filter#deepfake ai#stable diffusion
13 notes
·
View notes
Text
The Rise of 5G and Its Impact on Mobile App Development

5G isn’t just about faster internet — it’s opening up a whole new era for Mobile App Development. With dramatically higher speeds, ultra-low latency, and the ability to connect millions of devices seamlessly, 5G is transforming how developers think about building apps. From richer experiences to smarter services, let's explore how 5G is already reshaping the mobile app landscape in 2025 and beyond.
1. Lightning-Fast Data Transfer
One of the biggest promises of 5G is incredibly fast data transfer — we're talking about speeds up to 100 times faster than 4G. For mobile apps, this means that large files, high-resolution images, and HD or even 4K video content can be downloaded or streamed instantly. Apps that once needed to compress their data heavily or restrict features due to bandwidth limits can now offer fuller, richer experiences without worrying about lag.
2. Seamless Real-Time Experiences
5G dramatically reduces latency, meaning the time between a user action and the app’s response is almost instant. This will revolutionize apps that rely on real-time communication, such as video conferencing, live-streaming platforms, and online gaming. Developers can create much more responsive apps, allowing users to interact with data, people, and services with zero noticeable delay.
3. The Growth of AR and VR Mobile Applications
Augmented Reality (AR) and Virtual Reality (VR) apps have been growing, but 5G takes them to another level. Because of the high bandwidth and low latency, developers can now build more complex, interactive, and immersive AR/VR experiences without requiring bulky hardware. Imagine trying on clothes virtually in real-time or exploring a vacation destination through your phone — 5G is making this possible within Mobile App Development.
4. Smarter IoT-Connected Apps
The Internet of Things (IoT) will thrive even more in a 5G environment. Smart home apps, connected car apps, fitness trackers, and other IoT applications will be able to sync and update faster and more reliably. Developers can now integrate complex IoT ecosystems into mobile apps with minimal worries about network congestion or instability.
5. Enhanced Mobile Cloud Computing
Thanks to 5G, mobile cloud computing becomes much more viable. Instead of relying solely on local device storage and processing, apps can now store large amounts of data and execute processes directly in the cloud without latency issues. This allows users with even mid-range smartphones to experience high-performance features without the need for powerful hardware.
6. Revolutionizing Mobile Commerce
E-commerce apps are set to benefit greatly from 5G. Instant-loading product pages, real-time customer support, virtual product previews through AR, and lightning-fast payment gateways will enhance user experience dramatically. This could lead to higher conversion rates, reduced cart abandonment, and greater user loyalty in shopping apps.
7. Opportunities for New App Categories
With the technical limitations of mobile networks reduced, a whole new range of apps becomes possible. Real-time remote surgeries, autonomous vehicles controlled via mobile apps, and highly advanced telemedicine solutions are just a few examples. The doors are open for mobile developers to innovate and create applications that were previously impossible.
8. Better Security Requirements
With 5G’s mass connectivity also comes a bigger responsibility for security. As mobile apps become more connected and complex, developers must prioritize data protection, encryption, and secure authentication methods. Building security deeply into Mobile App Development workflows will be critical to maintain user trust.
9. More Demanding User Expectations
As 5G rolls out globally, users will expect every app to be faster, smoother, and more capable. Apps that fail to leverage the benefits of 5G may seem outdated or sluggish. This shift will push developers to continually optimize their apps to take advantage of higher speeds and smarter networking capabilities.
10. Preparing for the 5G Future
Whether you’re building entertainment apps, business solutions, healthcare tools, or gaming platforms, now is the time to adapt to 5G. Developers must start thinking about how faster speeds, greater device connections, and cloud capabilities can improve their mobile applications. Partnering with experts in Mobile App Development who understand the full potential of 5G will be key to staying ahead in a rapidly evolving digital world.
3 notes
·
View notes
Text
Congress’ unfounded plan to ban TikTok under the guise of protecting our data is back, this time in the form of a new bill—the “Protecting Americans from Foreign Adversary Controlled Applications Act,” H.R. 7521 — which has gained a dangerous amount of momentum in Congress. This bipartisan legislation was introduced in the House just a week ago and is expected to be sent to the Senate after a vote later this week.
A year ago, supporters of digital rights across the country successfully stopped the federal RESTRICT Act, commonly known as the “TikTok Ban” bill (it was that and a whole lot more). And now we must do the same with this bill.
As a first step, H.R. 7521 would force TikTok to find a new owner that is not based in a foreign adversarial country within the next 180 days or be banned until it does so. It would also give the President the power to designate other applications under the control of a country considered adversarial to the U.S. to be a national security threat. If deemed a national security threat, the application would be banned from app stores and web hosting services unless it cuts all ties with the foreign adversarial country within 180 days. The bill would criminalize the distribution of the application through app stores or other web services, as well as the maintenance of such an app by the company. Ultimately, the result of the bill would either be a nationwide ban on the TikTok, or a forced sale of the application to a different company.
Make no mistake—though this law starts with TikTok specifically, it could have an impact elsewhere. Tencent’s WeChat app is one of the world’s largest standalone messenger platforms, with over a billion users, and is a key vehicle for the Chinese diaspora generally. It would likely also be a target.
The bill’s sponsors have argued that the amount of private data available to and collected by the companies behind these applications — and in theory, shared with a foreign government — makes them a national security threat. But like the RESTRICT Act, this bill won’t stop this data sharing, and will instead reduce our rights online. User data will still be collected by numerous platforms—possibly even TikTok after a forced sale—and it will still be sold to data brokers who can then sell it elsewhere, just as they do now.
The only solution to this pervasive ecosystem is prohibiting the collection of our data in the first place. Ultimately, foreign adversaries will still be able to obtain our data from social media companies unless those companies are forbidden from collecting, retaining, and selling it, full stop. And to be clear, under our current data privacy laws, there are many domestic adversaries engaged in manipulative and invasive data collection as well. That’s why EFF supports such consumer data privacy legislation.
30 notes
·
View notes
Text
rare matchup trade with @mysteriawrites
for one of my very cute friends. i was in a major writing slump over the summer but she encouraged me to get out of my slump by offering a matchup trade! this is my first matchup for someone and very overdue on my part so i'm excited wehe
☆ and even though it’s a matchup i tried to write a full fic with her in mind, but applicable to anyone. especially because this is a whole entire fic with 5,905 words.
mysteria sent me a super detailed description in our dms so here's a summary of it:
mysteria is 5'2, african american, a capricorn and an infj! she's kind, responsible, moody, soft-spoken, and introverted. she also describes herself as a social chameleon that can match the energy of a room, from quiet and clumsy to sassy and teasing if she's comfortable enough. she likes animals, books, reading and writing, personality quizzes, rpg/mmo/rhythm games, and sweets. however, she dislikes loud sounds, math, trypophobia, spiders, and inconsiderate people. she also dislikes when people she cares about don't properly take care of themselves, but tends to forget her own needs. she's really a caring person at heart!
your matchup is under the cut for the drama! i match you with...!
Mischievous but observant, the Phantom Thief Alban Knox!
tags: gender neutral reader, getting together, hurt/comfort, reader is an overworker, bad work environment, happy ending, breaking and entering (and other thief-typical crimes lol)
─── ・ 。゚☆: *.☽ .* :☆゚. ───
There's this little convenience store right in your neighborhood that happens to be on your daily commute to work.
The first time you visit, you realize it's about five minutes away from your home and open 24/7, perfect for late-night snack runs.
The staff is so small, the same guy works the graveyard shift whenever you visit: tousled mocha-brown hair, a lanky body too thin for his uniform shirt, and two differently colored eyes. One is dark, while the other is so vividly green it makes him look intelligent.
It doesn't take long before he starts to memorize your usual order, and for you to memorize the Hi, my name is Alban! name tag over his apron.
With time the friendly customer service starts to become just actual friend behavior. You begin to learn more about one another. He asks you about your day, and when you mention some of your coworkers at your dime-a-dozen tech job he's able to remember who's who.
Meanwhile you've seen the two bowls outside the sliding doors, one full of water and the other kibble. Alban leaves them out for the neighborhood cats, and you've been lucky enough to meet a few of them before they scamper away.
Alban is like a brother to the strays, however, and the konbini tends to be empty whenever you visit, so there's no one to stop him when the cats paw at his leg, begging him to pick them up as you rant about your latest project. They even let you pet them once or twice before they climb over Alban's shoulders, watching you with nighttime pupils. Apparently that's rare. The first time a stray nuzzles your palm, Alban secretly slides you an extra pack of the snack cakes you wanted.
"If she trusts you, then you can keep a secret," he says. The cat's tail curls around his wrist before he nonchalantly drop the cake into your bag. "Our secret, right?"
Over time it becomes a part of your routine. Work during the day, visit the konbini, relax after a good conversation with Alban. Once your company picks up a new security project, your schedule slowly folds over. With Alban's late-night shifts and you working longer hours after getting a lead position, he becomes one of the few consistencies in a hectic career.
You really do treasure the time you spend with him. Now that so much is going on at work it's like his store is the only place you can unwind before you get back to programming at home.
Not to mention he's one of the few night owls you know, and the only one that was there for you when you felt like you were falling apart.
It's not like you wanted to let your defenses down, though. You'd been working tirelessly for weeks on this security system, but today your clients blew a fuse over things out of your control. All this effort, and the way they reacted made you feel like it was for nothing.
"Welcome!" Alban's standard customer service voice disappears once he recognizes your face. "Hey, it's my favorite—woah, wait. Are you okay?"
It stuns you how quickly he picked up on your mood. The second you left work, you spent ten minutes trying to wipe the ‘on the verge of tears’ look off your face.
"Don't worry, Alban, I'm fine." You try to smile. "Just a busy day at work. What're the daily specials today?"
"Oh! Uh..."
It's pretty obvious that wasn't a convincing excuse, but he lists off the menu anyways. You appreciate that he knows how to give you space.
You decide halfway through that you'd rather get your usual, though, too exhausted to think of trying anything new. "And a donut," you add, longing for a comfort food.
While Alban gets started on your food, the aisles of bright, prepackaged snacks feels like staring at a headache. Itching for relief, you stare outside the windows instead. A grayed tail swishes along the glass outside while two nighttime pupils stare right back at you.
The air prods at your skin as the sliding doors open, and you approach the cat. You recognize her as one of the first to warm up to you when you started to visit. She continues to watch you, even as you reach a hand out. Her tail rises like smoke.
The stray's eyes squint up into crescents as you scratch under her chin. "A meal and affection for free," you muse. You're trying to not be bitter, especially since this one is skittish, but you can’t help but feel envious. "Must be nice being a cat instead of a human."
The brisk nighttime air stills. This calm makes everything feel like it’s falling out of your grasp, but you don’t have a choice in the matter. You're a resigned observer to your own life.
"I just don't know what to do," you say. Your job pays well, but you’re so sick of being treated like this, especially after such a bad meeting with your client.
The stray nestles up closer to your hand, nudging the touch closer to her body so you can stroke her back. Not a moment later, she backs away. With powerful legs and silent breaths, she pounces down from the ledge, while the smoke trails into the shadowy brush on the other side of the parking lot.
So you lean back against the wall. Cold brick outlines your back. Damn. Not even the strays are cooperating with your shitty day.
By the time you return to the inside of the konbini, your nose is reddened from the chill. The overhead lights wash the color out of your face, so bright that the night outside seems jarring.
At least you can smell your food. Alban returns to the counter with a paper bag that feels warm to the touch, and a to-go box full of donuts.
You cock your head. “I only ordered one donut, didn’t I?”
“Yep.” He seals the box with a sticker. It’s a cute cat with the same mismatched eyes as him and ‘Freshness Guaranteed!’ underneath its paw.
“So why…?”
“Because I want to give you some. It’s nice to get freebies, especially when it’s for a friend that could use ‘em,” he says. “I’m sorry, I shouldn’t ask, but you’re not doing so hot, are you? If there’s anything I can do to help, let me know. I’d be happy to. Help you, I mean.”
He slides the bag of food and the donut box to your side of the counter. “But for now, you just keep those and take a moment to yourself.”
A steady aroma follows the bag while the donut box is warm under your fingers, freshly baked and at no extra charge, simply just because. One green eye and one dark stares up at you from the sticker, blending into the white fur as your vision blurs.
"Alban."
"Yeah, what's—?"
Alban’s question falters. Instead you speak, with one hand up at your eyes, glossy and turning wetter by the second. “Thanks.”
It seems the mask has fallen now. You hunch over as you sniffle. Hot shame seeps down your back like burning oil, the tears feeling more and more like they’re boiling. It only makes you more embarrassed and frustrated, which causes even more heat behind your eyes, and the cycle continues. Now here you are, crying in the cold light of a konbini while the poor cashier has no way out. You don’t even have the heart to look up at Alban’s face.
“Sorry,” you say. Your voice sticks together. “I-I shouldn’t be like this.”
“Why not?”
“Because I’m acting like a big baby, and I’m fine, I’m just—just making it weird, a-and you don’t even want to know.”
“But I do!”
Even though you don’t have the strength to raise your head, you can see Alban’s hands through mottled vision; namely, how they clutch at the counter—right before he sets them both over yours. You’ve never seen him without a pair of food-safe gloves, and these are no different, a solid black that sticks to your skin while fingers rest on your knuckles.
At his outburst, you dare to look up. His eyes are closed, mouth set in a crinkled frown, barely pursed as if he wants to say something. Alban reconsiders just as he opens it. Hesitation crawls into lowered brows, and your heart pangs even harder when he looks down at the hands. Either you’re seeing things, or there’s a bittersweet look in one eye and concern in the other. “If you trust me, then I want to know.
“Because you’re not ‘fine’. If you really were then you wouldn’t be crying at someone doing one tiny nice thing,” he blurts. “Did someone hurt you? Because if they did, I’ll give them a piece of my mind, no questions asked.”
“It’s… not a someone.”
That gets him to squeeze your palm. A wave of understanding bleeds through and travels up your veins. “I’m all ears.”
You squeeze back, eyelids smashing together as another fat tear rolls down your cheek. “It’s my jobbb.”
You aren’t exactly proud of how you weep, but the way Alban listens to you erases the regret. You spill your guts about the client, the meeting, the mismanagement, and that stupid security system you’ve been working on. Halfway through, Alban flips the ‘OPEN’ sign to ‘CLOSED’, thumbs off his gloves, and sits next to you properly.
By now his touch returns, resting fingertips on your knuckles and rubbing up your wrist. Without the gloves, he’s warmer than ever, and softer. He passes you a box of tissues from the office, too, and doesn’t even flinch when you honk into the tissues in-between sobs.
You explain everything, even the tiny stresses in your career. “I’m lost. It pays so much but I’m so exhausted,” you say. “I don’t want to leave but sometimes I just wish I could, I don’t know, transfer to a different location, or give the client to someone else, or hell, some kind of payback.
“But I’d not that kind of person. And even if I was…” Your eyes cast downward. The tears have slowed but they’re still so wet with misery. “I’m so tired.”
Your heart aches just at saying it. The realization has set in now. You’re tired.
That’s putting it mildly. You never noticed until now, but there’s an indescribable weight in your neck and shoulders, just about ready to snap you in two under the pressure. You used to love this job, and you still love what you do, but only now are you realizing you’ve put far more into it than your superiors deserve.
“That’s fucked,” Alban finally says, and you almost snort at how plainly he says it. Instead it comes out as a weak chuckle.
“Can’t your boss put two and two together and realize you’re already giving one hundred percent—no, two hundred into the project?” He asks, even though you both know the answer. “That’s stupid. There’s a whole staff of people, so they need to get their head out of their ass and give you a break.”
“I wish.” You sniffle. “I’m just a generic worker, but I’m the only one that knows exactly how everything operates. Makes me feel like I can't even rest.”
“Do you have any time off?”
“Well, yeah.”
“So take it. You need it,” Alban says. Then he playfully nudges you. “You know you deserve to treat yourself.”
That gets another chuckle out of you, louder than the last. He smiles softly and points out, “You’re laughing more.”
“You say things so simply that, I dunno, it makes things feel less difficult. Like when I think about it, it’s like this swirling black hole.” You exhale. “I was thinking about taking time off, earlier, but I told myself to tough it out instead of giving up. But now it doesn’t feel as extreme.”
“It’s not giving up. It’s resting. That’s a requirement.”
“Yeah. It just… doesn’t feel like it when I’m talking about me.”
“Then let me be the first to remind you that you’re allowed to relax just like the rest of us.”
You wipe your eyes again, this time with a tissue while Alban rubs your back. You’ve known that for as long as you can remember, but hearing Alban say it out loud is the beginnings of understanding. Internalizing that need.
You sniff, but rather than with hopelessness, a different feeling swells in your throat. Something like recognition, warm and loose rather than tight.
“Thanks,” you say. “For the food. And, you know, all this…”
The words get lost along the way, so you settle with a gentle tilt of your head to gesture.
Alban seems to get it without much trouble, though, and pats your back reassuringly. “It’s nothing.”
“I’d argue otherwise. I must have been a nuisance—“
“It's nothing,” he repeats. “No problem at all. If you ever walk in here crying again I’d do anything to make you feel better, you know.”
“Oh.” That makes you look away, almost scared of the fact. This type of caring is unfamiliar, and now that you’re all cried out, you can’t make heads or tails of the feeling. “That’s really sweet, I think.”
Alban lifts his hand off your body. The absence picks you up and out of your thoughts, so you raise your head. You watch as it rests back on his neck, right underneath his tousled brown hair. “Don’t mention it. Uh, how do you get home?”
“I usually walk.”
“Not that I don’t trust you, but you’re not about to walk home by yourself after crying your eyes out. I’ll drive you.”
Your eyes widen. “No, you don’t have to! I don’t want to be a bother!”
“Hey, I’m offering. No one visits at this time of night anyway, except for you.”
“Yeah, but it feels like I’m being a burden or something, and I don't want to cause more trouble for you than I already have, and—oh, forget it.” You bury your face in your hands. Your cheeks are still tempered from crying earlier, but now you can feel the unmistakable heat of embarrassment as well. “You’re not going to let this up, are you?”
He says, “Only if you’re sure you’ll get home safe. It’s late.”
“Fine, you can drive.” You pat at your face with the tissue. Your tears have long since dried, but maybe this will hide the blush. “I can’t say thank you enough.”
Alban shrugs that praise off as well, so intent on refusing your gratitude that it comes across as either sheepish or blasé. He busies himself with locking up the store while you clean yourself up (again) in the bathroom. He opens the car door for you before you can open it yourself.
The stick shift is a few years behind, but the console is rigged up to connect to Alban's phone. Before he starts driving, he hands it to you. "You can choose the music."
You thumb through a streaming service before finding a title your recognize from one of your own playlists, and at the first few notes of the song, the car enters motion. It's a quiet, comfortable silence filled up by the song and your directions to your home.
The walk to the konbini is fast, but driving is even faster, and the song barely ends as he pulls up to your home. "You got everything?" He asks.
You nod. "I do. Thanks, Alban."
"It's noth—"
"Oh, quit playing yourself down already." Before you can slip out of your seat, you lay a hand over Alban's as it rests on the stick shift, just like how he comforted you earlier. "No one at work took time out of their day to hear me out, not even my friends. You did. That means something."
"Still!" Alban says. "I wouldn't just ignore you."
"A lot of people would, and did. You're a lot better than you give yourself credit for." You poke his cheek. "Now repeat after me: you're welcome."
The poke makes his face squish up, cheek smushing into the corner of his lips while one eye closes. He blinks, uncertain, as if he entered uncharted territory. He likely has. If it wasn't apparent before, it certainly was by how long it took him to avert his eyes and say the words. “…You’re welcome.”
You squish his cheeks a little more as friendly affection. Barely visible under the overhead light, his face tints pink under the pressure of your hands. “Glad to hear it. I’ll see you later, Alban.”
“Right. Rest well?”
“I will.”
The door shuts and the headlights shine long shadows behind you as you walk away. Alban watches as you pull out your keys. You notice the shining lights only dim out after you’ve stepped inside your humble abode, and the warm feeling rises up again. He made sure you were inside safe and sound before he drove away.
It’s with that warm feeling that you speed through your nighttime routine and fall asleep in your bed.
It returns each time you visit the konbini after that night, too. Alban, in all his selflessness, still insists on giving you even more freebies than you know what to do with.
“Damn, Reader, if you visit even more often, I’ll have to order extra shipments of candies,” he quips as he scans your items—then snatches a king-size snack and slips it into your bag without charging you a cent more.
You snicker. “It’s not like I ask. You’re the one that won’t quit giving me things for free.”
“I’ve got more than enough to go around.”
“But you just said you’d have to order more.”
“How’s work? Still doing the security thing?” He asks.
You roll your eyes to the ceiling and huff not a second later. “Yep, same old, same old. One of my coworkers used the wrong parts on something, so I had to spend my entire shift today disassembling and reassembling it myself.”
"You know what I'm going to say—"
"That it's unfair and stupid?"
"—Among other things, but you're just going to say the pay is too good to leave, aren't you," he finishes.
You focus on the counter rather than Alban's movements. It's been a while since that night he drove you home and the wound has healed, but there's no mistaking the beginnings of a scar at the memory, all puffy-pink as it tries to recover to what once was.
You hate to admit it, but he's right. He quoted something you said word-for-word last week.
"I'm not just predictable, I'm mad," you say. "And tired of being mad."
"Not at anything new, is it?"
You sigh. "Nope. It's more like a lot of little things building up and just whittling me down. Same ol' soul-crushing machine as always."
The cash register dings as Alban places all your items into the bag, and you pay for half of what you should. "There isn't anything keeping you happy or loyal, is there?"
"Not really. It's all miserable, even the other departments." You even laugh bitterly. "I guess the employees get paid so much because there's no budget going into decent HR."
"You know what I'm going to say."
"Don't waste your breath."
"I can't tell you what to do."
"Gotta pay my bills somehow." The receipt inches out. Alban tears it off and slips it into the bag. "I'm looking, but I can't just quit yet. At this point, I don't care what happens to the place, as long as I get paid. Need to finish the security system before moving onto another job."
"I hope someone gives you a better offer soon. Workplace culture included."
"Me too." He offers the bag to you. You take the handles from Alban with crinkles and a skim along his fingertips. "At least I've got nothing planned tonight but binging a TV show over snacks." You jostle the bag, and the many candies inside. "In no small part because of you."
He beams at that, just before wiring his mouth into a thin smile to cover up his happiness. "We're always open! And I'm always here."
"I'm counting on it." That happiness spreads to you like watercolor on paper. "I'll come back soon, Alban."
He sees you off with the good cheer and well-wishes you've come to expect from Alban, and a request to keep out of trouble. Once the crisp white of the konbini's lights fade away into the night as you walk home, the dismal feeling returns.
Maybe you should take his advice and quit while you're ahead. It's no secret this job will kill you one day.
You bite back the thought as soon as it comes to mind. You need the cash. Quitting is tempting, but if you leave now, you won't have enough savings to fall back on.
"Until this commission is over," you mutter under your breath. You'll put in the two-week notice then, once the security project is complete, and that stuck-up client coughs up the high price for all your effort.
Until then, until then, until then. Your mind echoes as you go down the familiar path home, staving off the urge to think any more on it. All that's left for you to do today is watch some shows, relax, and hopefully, get a good night's rest before doing the same thing again tomorrow.
Even though the night in serves as a good distraction, you remember the grind ahead as you tuck yourself into bed, and with it, Alban's wishes for your happiness pushes the harsh thoughts away as you drift off.
As you'd expect, the days ahead are predictably mundane, save for the awful work environment you've become so used to over time. Some days it feels like you're the only competent person in the building. Other days you know it's true.
Which brings you to now. The coworker that sits closest to you left to go file some papers in another office—or take a personal call for the next twenty minutes, it's always a toss up with them—leaving you to your own devices as you work on something that should've been completed earlier this week. Again.
The office you're currently in is built for three at most, though it rarely fits that many. Usually you're by yourself or with another coworker, and now that you're alone, you have the freedom to sigh. You know how these things work, but having to pick up so much slack is just plain exhausting.
The lights go out.
The first thing you think is if the latest updates were saved. Your brain reminds you that the program was on autosave every minute, and you haven't typed in five. It'll be fine.
The next thing is that considering your industry, there's more than a few backup generators. There's no way it would take this long for one of them to kick in and get power back to the building.
Something's wrong. You don't have a clue, but outside your office windows, you can catch glimpses of other workers evacuating. There's no way it could be a natural disaster, and you doubt a fire would cut the lights, but considering how fast the other workers clear out, you aren't staying to find out.
You're one of the last people to leave a personal office, and you presume the last to start moving. The halls twist in the darkness, but you've memorized the layout, and your phone's flashlight guides the way.
The sound of keys on keys jingle behind you. You pivot with a start "Who's there?"
No one responds. Your light reaches a few feet ahead before being swallowed by the darkness. The ceiling boasts some LEDs for detectors, cameras, and the far-off 'EXIT' sign but not much else, and none of them are helpful at the moment.
Something else whooshes ahead, and you turn again, now starting to feel like a fish being circled by a shark.
"This isn't funny," you call out. That was stupid of you. Maybe the job is rotting your brain, and it'll be the reason behind your death, trapped in your shitty office while everyone else evacuates.
With steeled nerves you keep walking, twisting your phone around to get a piece-by-piece view of the hallways. The light bounces off the waxy leaves of a houseplant by a door. The water cooler where you refill your water bottle. Two pointed strikes of orange that shine one-at-a-time as the light flashes.
Cloth covers your mouth before you can scream.
They wire around as the orange comes into focus, now identifiable as two pins in a head full of shaggy hair. The intruder rests a finger on his lips as he shushes you, one green eye and one dark reflecting the light from your phone.
You manage to shake off his grip and hiss. "Alban?"
He blinks before widening his mismatched eyes. "Wh-what are you talking about? I don't know anyone named Alban."
"Oh, cut the crap, you—" You start, but remember the LED lights up on the ceiling. The cameras! You tug on his jacket sleeve as you dive into a corridor hidden from the security cameras, and luckily, he's shocked enough to stumble along. He slips out of your grasp in a matter of seconds, but instead climbs along the walls and hops between structures to obscure himself like a superhero out of a movie.
You push yourself flat against a wall as if it would hide you any further, while Alban clings onto the ceiling and inches down, dangling in midair. A strap is attached to the roof and around his body not unlike climbing gear.
"I'd recognize you anywhere," you say, "and if I didn't before then I definitely did the second you started talking."
Alban looks away. "Oh. Right. I should've expected that."
"Never mind that, what are you doing here? I work here!" You push him lightly, and he sways in air from the force. "Don't tell me you're behind the power outage."
He scratches the back of his head and gives you a coy smile, only half-apologetic, until you push him more. He flails before steadying himself by holding onto your shoulders. "Wait, I had a reason!"
"Uh-huh, and you're going to tell me it right now before I call the cops!"
"Psh, they couldn't catch me even if they tried—" Shove. Alban swivels around aimlessly. "Okay, okay, fine! I'm a phantom thief."
You grab him and glare. "So you decided to target my workplace after hearing me complain about it for eons. Give me one good reason not to twist you so hard we test if motion sickness can result in death."
"I mean, not entirely off?" He says with a sigh. "Okay, hear me out. The konbini isn't exactly a moneymaker. So I steal things here and there, but only from people who don't deserve it. You know, the types that steal their assets, treat everyone like dirt, exploit hard-working, good people... You see where I'm going with this, right?"
"Go on."
"I like to take only a little bit of it for myself, then forward whatever else I find to the original owners, or community projects that would use the cash way better than some hoarder. Which is why I decided to come here. It has an awful rep despite its net worth, and I dunno, it just seems like it sucks more and more of your soul out the longer you work here." Alban frowns. Even upside-down in the air, his concern is heartfelt, as genuine as that day you confided in him.
You can't even say he's wrong, not entirely. He really did listen to all your woes.
"So... I did some research. Didn't like what I saw. I don't think it's news to you, either."
"It's not great, no." You cross your arms. "So you decided to steal from them."
Alban pats down his pockets. Each of them has a hidden zipper, you realize, which must explain how he hasn't dropped any of his loot until he produces it and shows it to you. One by one, he hands you small boxes covered in secure foam. Your eyes widen as you open them. Each is a different minuscule computer part. "You recognize these."
"How could I not? These are upcoming designs. Not entirely complete, but once they are, they'll be gold standard. Maybe even more."
"Exactly. I did some rifling around in the offices, too. They'll be sold at an insane markup from the true estimated value once they're released to the public." Alban bites the inside of his cheek. "Most of the information and programming has been ripped off from programmers that either didn't consent or were severely underpaid."
"You're telling me. And the employees here will be earning pennies once it goes public."
He nods, serious as the grave. You've never seen him this dead-set on something but you recognize the blazing ambition in his eyes, and the curve over his mouth that forms when he's dedicated. He set his hand over the boxes you hold. "If you really want to return them, I won't stop you. I just want to do the right thing."
The packages aren't much bigger than jewelry boxes, and just as light, but holding them feels like handling priceless masterpieces. After all, they are.
"Why?" You ask.
"Because I trust you."
"Even after I spun you around like a piñata."
"It takes more than that to knock me out," Alban says. "Besides, even if you did, I wouldn't regret it. I think I'd endure a lifetime's worth of it if that's what it took for you to know how much I care."
You readjust your grip on the parts as Alban turns his head away again. "That sounded wrong. I mean, you work for them, not me. If this feels wrong, then you can call it off and I'll leave without anything."
He cares for me. You squeeze your lips together in deep thought. "You think so highly of me, even though I'm just a wreck that has a shitty 9 to 5 and mooches off your konbini food."
"Not a wreck," he corrects, voice tilted high in protest. "I wouldn't have it any other way."
"You're such a handful." You present the boxes out and away from you. "Put them back in your pockets. There's the camera outside that I pulled you away from, and a few others in each corner of this floor."
Dumbfounded, Alban gingerly takes them just as you start doodling on a piece of paper. "You're just giving them back to me?"
"What does it look like I'm doing? There's only so much time before any authorities show up." You wait until Alban secures the parts away before pressing the paper flush against his upside-down chest while you stand at eye-level with him. "Not my best blueprint, but you can figure out the best route to sneak out from with that map I just drew up."
Alban stays still in the air, but you let go of the map as it rests under the collar of his jacket. He fumbles for the paper, narrowly avoiding any stray hits to your body due to the proximity.
While he's occupied, your eyes have finally adjusted to the darkness as well as how close you are to him. He doesn't notice you staring at all, nor how his cheeks are a rosier tone than the rest of his skin.
He manages to nab the paper and holds it back over his heart, where you pressed it. When he makes eye contact with you, you see to his core; both the smarmy phantom thief that infiltrated your office, and the understanding, generous dork that works nights at the konbini.
Your hand brushes with his as you take the cloth of his jacket collar. "It didn't sound wrong at all." In the dark, he tenses, gloved hands clutching the paper tighter while that blush grows into a muted red.
You drum up the courage he's shown you time and time again as you lean in. The momentum fuels you as he reciprocates, paper forgotten as it flutters to the floor in favor of holding you tighter as his lips brush along yours.
─── ・ 。゚☆: *.☽ .* :☆゚. ───
bonus.
─── ・ 。゚☆: *.☽ .* :☆゚. ───
You let go of Alban's collar, all lightheaded and woozy after a long-awaited kiss. It breaks off, but his arms are still tangled around your back in a loose hug. The dopey grin on his face is full of emotion; surprise, adoration, and a shred of greed like that wasn't enough for him.
"You need to get back to business," you say, breathless.
"Uh-huh?"
"And I should go before people think I went missing."
"Oh, duh. Yeah. Yeah, you should." Alban shakes his head to jostle him out of his stupor. He raises one limb after another as the cord retracts. "I'll be—ack!"
He flops face-down to the ground with a yelp. Then a groan.
You flinch. "Alban! Are you okay?"
"Ughhh."
Expecting the worst, you crouch down and hold his arm as he rises. "Ow, that hurt... No damage done, though."
"If you say so." You dust off his shoulders as he recovers. Sure enough, there aren't any scratches nor bruises immediately forming, and the concern turns into amusement as he presses his lips together. "Alban, your face is so red."
"Wh—no, it's not."
You pinch his cheeks. His brows are drawn together, all shy and flustered. "Oh, I can't wait to see what this looks like in daylight."
"It's just because I was hanging upside-down! Blood rushes to your head!"
"Yup, right after falling flat on your face."
He wiggles out of your grasp and up on his feet in no time. "You're teasing me and I won't stand for it. Bye!"
And with that, he bolts out of the room, grappling off the walls like a parkour artist until he becomes one with the darkness.
You watch him until he disappears, but you've got places to be, too. You rifle into your pocket where your phone and wallet rest.
That is, until you realize your wallet is nowhere to be found.
You frantically search your pockets until you realize the first one you checked, the one your wallet rested in, had a card inside that wasn't there before.
It's one of the generic business cards your company provides, likely lifted from another worker's office, but along the blank white cardstock, someone had drawn a cat paw alongside a note.
"You just got mugged by the robber! (But visit tonight to get it back.)"
There's a scrawl in the corner, scratched out to the point you can't tell what it was, but a few lines against the scribble makes you think the writer doodled something.
You'll have to ask him later.
"Tonight," you say out loud. It's been a long day, and like you said, you need to get back to the rest of the employees.
But after that, the workday is sure to be cut short as the higher-ups manage the police, and now you have plans.
And you could do without a 9 to 5 looming over you for a while.
. . • ☆ . ° .• °:. *₊ ° . ☆
✧. ┊mysteriawrites
✧. ┊ masterpost ✧. ┊ kofi
#nijisanji x reader#nijisanji en#4402 writes#here's hoping the tags are hidden enough so they won't spoil anything before you click read more#noctyx x reader#noctyx#alban knox#alban knox x reader#alban knox fluff#alban knox angst
22 notes
·
View notes
Text
What is Web Hosting? Discover Types, Key Factors, & 2024’s 12 Best Web Hosting Platforms.
Web hosting—the physical presence of your website on the internet—is essential for your online business. Without dependable web hosting, you jeopardize your capacity to run your business and meet your consumers’ expectations.
Understanding web hosting and how it works can be difficult, particularly for people who are unfamiliar with the notion. This article will clearly describe web hosting, explain the many types of web hosting plans available, and outline the essential factors to consider when selecting a hosting company.
What is web hosting?

Web hosting uses internet-facing hardware and software to provide web services to end users. It is where your website and services are stored, processed, and delivered.
At its most fundamental, web hosting consists of secure internet interfaces and communications, computer server hardware and storage, web server software, and content (text, pictures, audio/video).
However, most web hosting solutions also include database servers, content management systems, e-commerce tools, security and authentication, and other applications required for websites to function and remain secure.
The web hosting sector is critical and is expected to increase by more than 20% year between 2024 and 2028.
How much does web hosting cost?
Hosting charges vary, typically based on capabilities. You may pay $10 per month for a simple billboard-style website to market your business online, or much more if you run a successful e-commerce store with thousands of clients.
To successfully select web hosting that works for you, you simply need to understand your goals and how to translate them into hosting requirements.
Types of Web Hosting
Shared hosting.
Dedicated Hosting
VPS (Virtual Private Server) hosting
Cloud hosting
Continue Reading The Blog Post Click Here...
#Web Hosting#Hosting#WordPress Hosting#WP Hosting#Best Web Hosting#Web Hosting Platforms#Top 12 Web Hosting
7 notes
·
View notes
Text
Unlocking the Secrets to Effortless Compliance with ZATCA Phase 2
The Kingdom of Saudi Arabia is leading the way in digital transformation, especially with its structured e-invoicing initiatives. A significant part of this movement is ZATCA Phase 2, which aims to enhance transparency, boost efficiency, and ensure tax compliance across businesses.
If you are a business owner, accountant, or IT professional, understanding ZATCA Phase 2 is no longer optional. It is critical for ensuring that your operations remain compliant and future-ready. This guide breaks down everything you need to know in a simple, easy-to-understand manner.
What Is ZATCA Phase 2?
ZATCA Phase 2, also known as the Integration Phase, is the next major step following Saudi Arabia's Phase 1 e-invoicing requirements. While Phase 1 focused on the generation of electronic invoices, Phase 2 moves beyond that.
It requires businesses to integrate their e-invoicing systems with ZATCA’s Fatoora platform, allowing real-time or near-real-time transmission of invoices for clearance and validation.
This phase ensures that each invoice issued meets strict technical, security, and data format requirements set by the Zakat, Tax and Customs Authority (ZATCA).
Key Objectives Behind ZATCA Phase 2
Understanding the "why" behind Phase 2 can help businesses see it as an opportunity rather than a burden. The main goals include:
Improving tax compliance across all sectors
Minimizing fraud and manipulation of invoices
Streamlining government audits with real-time data
Promoting a transparent digital economy
Enhancing business operational efficiency
Who Needs to Comply?
All businesses registered for VAT in Saudi Arabia must comply with ZATCA Phase 2 regulations. This includes:
Large enterprises
Medium and small businesses
Businesses using third-party billing service providers
Companies operating across multiple sectors
Even if your business operates primarily offline, if you are VAT registered, you need to be compliant.
Important Requirements for ZATCA Phase 2
Compliance with ZATCA Phase 2 is not just about sending electronic invoices. It involves specific technical and operational steps. Here’s what your business needs:
1. E-Invoicing System with ZATCA Compliance
Your billing or accounting system must:
Issue invoices in XML or PDF/A-3 with embedded XML
Securely store invoices electronically
Incorporate UUIDs (Unique Identifiers) for each invoice
Attach a QR code for simplified verification
2. Integration with ZATCA Systems
Businesses must establish a secure Application Programming Interface (API) connection with ZATCA’s platform to allow the real-time sharing of invoice data.
3. Cryptographic Stamp
Each invoice must carry a cryptographic stamp. This verifies the invoice's authenticity and integrity.
4. Archiving
Invoices must be securely archived and retrievable for at least six years in case of audits or regulatory reviews.
Implementation Timeline for ZATCA Phase 2
ZATCA is rolling out Phase 2 gradually, targeting businesses in waves based on their annual revenues:
Wave 1: Businesses with annual revenues above SAR 3 billion (started January 1, 2023)
Wave 2: Revenues above SAR 500 million (started July 1, 2023)
Future Waves: Gradually extending to smaller businesses
Each business is officially notified by ZATCA at least six months before their compliance date, giving them time to prepare.
How to Prepare for ZATCA Phase 2: A Step-by-Step Guide
The good news is that with proper planning, adapting to ZATCA Phase 2 can be straightforward. Here’s a simple preparation roadmap:
Step 1: Review Your Current Systems
Audit your existing accounting and invoicing solutions. Identify whether they meet Phase 2’s technical and security standards. In most cases, upgrades or new software may be required.
Step 2: Select a ZATCA-Approved Solution Provider
Look for software vendors that are pre-approved by ZATCA and offer:
Seamless API integration
Cryptographic stamping
XML invoice generation
Real-time data reporting
Step 3: Integration Setup
Collaborate with IT teams or third-party service providers to set up a secure connection with the Fatoora platform.
Step 4: Employee Training
Ensure that relevant departments, such as finance, IT, and compliance, are trained to manage new invoicing processes and troubleshoot any issues.
Step 5: Test Your Systems
Conduct dry runs and testing phases to ensure that invoices are being properly cleared and validated by ZATCA without delays or errors.
Step 6: Go Live and Monitor
Once your system is ready and tested, begin issuing invoices according to Phase 2 standards. Regularly monitor compliance, system errors, and feedback from ZATCA.
Common Challenges and How to Overcome Them
Businesses often encounter several challenges during their Phase 2 preparation. Awareness can help you avoid them:
Integration Difficulties: Solve this by partnering with experienced ZATCA-compliant vendors.
Employee Resistance: Overcome this with proper training and clear communication on the benefits.
Technical Errors: Regular testing and quick troubleshooting can help prevent issues.
Lack of Budget Planning: Allocate a specific budget for compliance early to avoid unexpected costs.
Preparation is not just technical. It’s organizational as well.
Benefits of Early Compliance with ZATCA Phase 2
Early compliance does more than just prevent penalties:
Improves Financial Reporting Accuracy: Real-time clearance ensures clean records.
Builds Market Trust: Clients and partners prefer businesses that follow regulatory norms.
Enhances Operational Efficiency: Automated invoicing processes save time and reduce errors.
Boosts Competitive Advantage: Staying ahead in compliance projects an image of professionalism and reliability.
Businesses that proactively adapt to these changes position themselves as industry leaders in the evolving Saudi economy.
Conclusion
ZATCA Phase 2 is not just a regulatory requirement. It’s an opportunity to upgrade your operations, improve financial accuracy, and enhance business credibility.
By understanding the requirements, preparing strategically, and partnering with the right solution providers, your business can turn this challenge into a growth opportunity.
The sooner you act, the smoother your transition will be. Compliance with ZATCA Phase 2 is your gateway to becoming part of Saudi Arabia’s dynamic digital economy.
2 notes
·
View notes
Text
Cloud Squatting: Understanding and Mitigating a Modern Cyber Threat

Cloud computing is central to both business and personal data storage. A critical and emerging threat is cloud squatting.This phenomenon, a digital variant of the notorious domain squatting, involves the unauthorized occupation of cloud resources. It poses significant risks, making it a crucial concern for everyone, from casual cloud users to IT professionals and business owners.
Understanding cloud squatting
Cloud squatting is the practice of occupying cloud resources, such as storage accounts, domain names, or service identifiers, often for exploitative purposes. This could range from reselling these resources for profit to hosting harmful content or phishing scams. Cloud squatting not only mirrors traditional domain squatting but also extends to trafficking cloud resources like cloud computing instances or web applications, typically for malicious intentions.
The risks involved
Cloud squatting presents various risks:
Data theft: Unauthorized instances can store or transmit stolen data.
Security breaches: They can act as platforms for attacks on other systems.
Reputation damage: Companies suffer if their services are impersonated.
Legal and financial repercussions: In cases of brand damage and loss of customer trust.
For example, an attacker might use a service resembling a legitimate one, deceiving users into sharing sensitive information, leading to data breaches and tarnished reputations.
Mitigation strategies
Effective mitigation of cloud squatting involves a multi-faceted approach:
Proactive registration: Secure variations of your business’s cloud resource names.
Regular audits: Ensure all cloud services are legitimate.
Monitoring and alert systems: Detect unauthorized or misleading registrations.
Employee training: Educate about risks and the identification of suspicious services.
Legal protections: Utilize trademarks and enforce anti-squatting policies.
Security tools and best practices: Use AI-driven solutions and update security measures regularly.
Stakeholder education: Inform teams and customers about these risks.
Rapid response plan: Have a plan to address incidents swiftly.
Collaboration with cloud providers: Utilize their anti-squatting policies.
Reserved IP addresses: Transfer owned IPs to the cloud and manage records.
Policy enforcement: Prevent hard coding of IP addresses and use reserved IPv6 addresses.
The future of cloud security
As cloud technologies evolve, so do the tactics of cybercriminals. This makes proactive security measures and constant vigilance essential. Emerging technologies, like AI-driven security solutions, will play a crucial role in combating these threats.
Cloud squatting is a modern cyber threat that demands awareness, understanding, and proactive action. Implementing robust security strategies and staying informed about the latest trends in cloud security can significantly protect valuable digital assets. By addressing the risks and employing comprehensive mitigation strategies, individuals and businesses can safeguard their presence and integrity in the cloud.
Centizen, your trusted partner in cloud consulting and staffing provides unparalleled expertise and solutions to guard against threats like cloud squatting, ensuring the security and efficiency of your digital infrastructure.
#CloudSquatting#CyberSecurity#CloudSecurity#DataProtection#DigitalThreats#CloudComputing#InfoSec#AIinSecurity
2 notes
·
View notes
Text
MediaTek Kompanio Ultra 910 for best Chromebook Performance

MediaTek Ultra 910
Maximising Chromebook Performance with Agentic AI
The MediaTek Kompanio Ultra redefines Chromebook Plus laptops with all-day battery life and the greatest Chromebooks ever. By automating procedures, optimising workflows, and allowing efficient, secure, and customised computing, agentic AI redefines on-device intelligence.
MediaTek Kompanio Ultra delivers unrivalled performance whether you're multitasking, generating content, playing raytraced games and streaming, or enjoying immersive entertainment.
Features of MediaTek Kompanio Ultra
An industry-leading all-big core architecture delivers flagship Chromebooks unmatched performance.
Arm Cortex-X925 with 3.62 GHz max.
Eight-core Cortex-X925, X4, and A720 processors
Single-threaded Arm Chromebooks with the best performance
Highest Power Efficiency
Large on-chip caches boost performance and power efficiency by storing more data near the CPU.
The fastest Chromebook memory: The powerful CPU, GPU, and NPU get more data rapidly with LPDDR5X-8533 memory support.
ChromeOS UX: We optimised speed to respond fast to switching applications during a virtual conference, following social media feeds, and making milliseconds count in in-game battle. Nowhere is better for you.
Because of its strong collaboration with Arm, MediaTek can provide the latest architectural developments to foreign markets first, and the MediaTek Kompanio Ultra processor delivers the latest Armv9.2 CPU advantage.
MediaTek's latest Armv9.2 architecture provides power efficiency, security, and faster computing.
Best in Class Power Efficiency: The Kompanio Ultra combines the 2nd generation TSMC 3nm technology with large on-chip caches and MediaTek's industry-leading power management to deliver better performance per milliwatt. The spectacular experiences of top Chromebooks are enhanced.
Best Lightweight and Thin Designs: MediaTek's brand partners can easily construct lightweight, thin, fanless, silent, and cool designs.
Leading NPU Performance: MediaTek's 8th-generation NPU gives the Kompanio Ultra an edge in industry-standard AI and generative AI benchmarks.
Prepared for AI agents
Superior on-device photo and video production
Maximum 50 TOPS AI results
ETHZ v6 leadership, Gen-AI models
CPU/GPU tasks are offloaded via NPU, speeding processing and saving energy.
Next-gen Generative AI technologies: MediaTek's investments in AI technologies and ecosystems ensure that Chromebooks running the MediaTek Kompanio Ultra provide the latest apps, services, and experiences.
Extended content support
Better LLM speculative speed help
Complete SLM+LLM AI model support
Assistance in several modes
11-core graphics processing unit: Arm's 5th-generation G925 GPU, used by the powerful 11-core graphics engine, improves traditional and raytraced graphics performance while using less power, producing better visual effects, and maintaining peak gameplay speeds longer.
The G925 GPU matches desktop PC-grade raytracing with increased opacity micromaps (OMM) to increase scene depths with subtle layering effects.
OMM-supported games' benefits:
Reduced geometry rendering
Visual enhancements without increasing model complexity
Natural-looking feathers, hair, and plants
4K Displays & Dedicated Audio: Multiple displays focus attention and streamline procedures, increasing efficiency. Task-specific displays simplify multitasking and reduce clutter. With support for up to three 4K monitors (internal and external), professionals have huge screen space for difficult tasks, while gamers and content makers have extra windows for chat, streaming, and real-time interactions.
DP MST supports two 4K external screens.
Custom processing optimises power use and improves audio quality. Low-power standby detects wake-up keywords, improving voice assistant response. This performance-energy efficiency balance improves smart device battery life, audio quality, and functionality.
Hi-Fi Audio DSP for low-power standby and sound effects
Support for up to Wi-Fi 7 and Bluetooth 6.0 provides extreme wireless speeds and signal range for the most efficient anyplace computing.
Wi-Fi 7 can reach 7.3Gbps.
Two-engine Bluetooth 6.0
#technology#technews#govindhtech#news#technologynews#processors#MediaTek Kompanio Ultra#Agentic AI#Chromebooks#MediaTek#MediaTek Kompanio#Kompanio Ultra#MediaTek Kompanio Ultra 910
2 notes
·
View notes
Text
TikTok’s day of reckoning in the US has arrived. On Friday, the United States Supreme Court will hear the company’s appeal against its slated nationwide ban, which could come into force in a little more than a week if the company’s efforts fail.
The social video app, which is owned by Chinese firm ByteDance and is used by around 170 million Americans, has been appealing the ban since US president Joe Biden signed the law underpinning it last year. The Protecting Americans From Foreign Adversary Controlled Applications Act (PAFACA) states that ByteDance must sell TikTok’s US business to a non-Chinese company by January 19—no buyer has yet been found—or see the app blocked in the US. Donald Trump, who retakes the White House on January 20, publicly originated the idea that ByteDance be forced to sell TikTok during his first presidential term but has since reversed course.
The Supreme Court, which is hearing the case quickly due to the impending deadline and following a federal court upholding the ban in December, will determine whether the US Constitution’s First Amendment right to free speech is overruled by the government’s belief that TikTok is a threat to US national security. Proponents of PAFACA claim TikTok’s Chinese ownership could allow China to steal data on Americans and spread disinformation—although little evidence has been presented to support those claims, which the company denies.
If the court allows the ban to go ahead—and Trump doesn’t find a way to stop it—the move will be an unprecedented technological clampdown in the country.
“This is the first time we’ve seen a national-level ban that appears imminent in the United States,” says Joseph Lorenzo Hall, a distinguished technologist at the Internet Society. TikTok has been banned or faces lawsuits in other countries, such as India, and the pressures come against the backdrop of total internet shutdowns and increased online censorship. “What we learned from all of those is that this ends up really hurting the people of the country, that the economic effects are immediate for people,” Hall says.
So, how would TikTok actually be banned?
App Stores, Hosting Providers
Unpicking TikTok from the nation’s consciousness—thousands of influencers and businesses use the app to make money and promote themselves—is not exactly straightforward. Nor is it simple to untangle the company from US-based internet infrastructure.
PAFACA doesn’t require anyone to uninstall TikTok from their phones. It also doesn’t say TikTok should directly stop its services from working in the US. Instead, it effectively tries to throttle TikTok by making it harder to use over time and by stopping companies from providing services that help it to keep working and quickly loading videos.
TikTok, as with all companies mentioned in this story, did not respond to WIRED’s request for comment and hasn’t, at this stage, outlined what technical steps it will or will not take if the ban does eventually come into place.
The law says it will be “unlawful” for entities to “distribute, maintain or update” the app including its source code, or by “providing services” that allow it to keep running as it is now. This distribution, maintenance, or updates could be, the law says, by means of mobile app stores that can be accessed in the US or by “providing internet hosting services.”
“The law really deliberately avoided saying that it was illegal to have the app on your phone,” says Milton Mueller, a professor and cofounder of the Internet Governance Project at the Georgia Institute of Technology, who filed an amicus brief to the Supreme Court in opposition of the ban. “Their attempt is to say nobody new can download it from the Apple or Google stores, and nobody who has it can update it through those stores,” Mueller says. “There’s nothing in the law that says ‘TikTok you must block US users,’ which is again interesting.”
If TikTok is removed from Apple’s App Store and Google’s Play Store in the US, it will not be possible to directly install new updates that will add new features, fix bugs within the code, or quash security flaws. Over time, that means TikTok will stop functioning properly. Apple didn’t respond to WIRED’s request for comment, while Google declined to comment on what it will do if the law comes into effect.
The law’s other focus is on stopping “hosting” companies from providing services to TikTok—and the definition is pretty wide. Hosting companies “may include file hosting, domain name server hosting, cloud hosting, and virtual private server hosting,” the law says. Since the summer of 2022, as TikTok faced pressure about its Chinese ownership, the company has hosted US user data within Oracle’s cloud services. Oracle also did not respond to WIRED’s request for comment.
Even so, other systems such as content delivery networks, advertising networks, payment providers, and more are used as part of TikTok’s infrastructure. The law does not specifically mention these services, but differing legal readings could make them question whether they help to “maintain” or “distribute” TikTok’s fully functioning service.
Hall says a recent test of TikTok’s website showed 185 embedded domains on the page. “They pull in code, content from that array of third-party providers and their own domains too,” he says. “The apps will start to decay and rot as either services stop working, things like content distribution networks or services who feel like they can't take the risks of the ambiguous nature of the language or the potential enforcement by the incoming administration.”
There’s one internet infrastructure player that the ban does not specifically put pressure on: internet service providers. Countries such as Russia and China have developed censorship measures that allow them to block entire websites from being accessed through web bowsers. Mueller believes this omission by US lawmakers was likely deliberate, as it avoids setting up a Chinese-style internet firewall. “They knew that a system of ISP-based blocking and filtering would obviously be a form of First Amendment restriction,” he says.
Avoiding a TikTok Ban
While TikTok’s service in the US would likely degrade over time, there remain some potential ways around any ban—both for individuals and potentially also the company itself. How effective these measures would be likely depends on how motivated people are to keep using TikTok and what the company decides to do.
“TikTok has 170 million users,” says Alan Rozenshtein, an associate professor of law at the University of Minnesota, who is in favor of the law but says it is the “best of a bunch of bad options” relating to TikTok. “This law will not prevent every one of them from accessing TikTok. I don’t think that was ever the goal of the law. The law is to make it meaningfully harder to access TikTok.”
Theoretically, at least, TikTok could shift its services providers—such as hosting companies or content delivery networks—to be based outside of the United States. Using technical infrastructure based abroad, for instance in Europe, could allow TikTok to be served to people in the US while operating within the bounds of the law.
While skirting the full-blown ban would allow people in the US to continue to use the app, that doesn’t mean the experience will be good. If videos are served from international locations, for example, load times may be slower for users, and it may be harder to upload videos. Using TikTok’s website isn’t the same experience as what the app provides, either. And that all depends on such a setup being possible at all.
“I do think that the number of companies that can do that, that are not headquartered in the US, is going to be small, especially considering how hard it is to switch from one cloud provider to another,” Hall says. “It’s really difficult depending on a number of factors.” Aside from technical challenges, international companies may not be willing to risk flying in the face of US restrictions, particularly under an aggressive Trump administration that has already threatened Greenland and economic penalties on other countries.
A TikTok ban would almost guarantee a spike in searches and downloads of virtual private networks (VPNs), which allow people to appear as if they are in a different geographic location to get around restrictions on content—for instance, trying to watch Netflix while abroad. Using a VPN within the US may allow the TikTok app to keep working, although it is unclear whether the company will place any restrictions on users it can determine are in the US by other means. The company’s support pages say SIM card registration details and other information can be used to pinpoint someone’s location.
Alternatively, it is likely Android users could download versions of TikTok outside of Google’s Play Store and install them on their devices. However, sideloading like this can come with security risks if the apps are not verified, and doing the same on an iPhone, via jailbreaking the device, is more technically complex.
Equally, moves such as changing locations of app stores to be outside of the US may come with unforeseen consequences and prove harder to maintain for general users in the long term. For instance, if you are changing an iCloud account’s location, Apple advises that you may need to cancel subscriptions and have a valid payment method for the location you are changing it to.
Prateek Waghre, a technology policy researcher based in India, where TikTok has been banned for four years and, despite an influx of some homegrown competitors, largely saw people move to Instagram Reels or YouTube’s Shorts, says overall restrictions on apps and websites weakens people’s experiences online and damages the internet as a whole.
“For many of us, [it is] the realization of one of our fears of a ‘splinternet,’” Waghre says. “You will have different kinds of access based on different geography, which is not what the experience of the internet was.”
7 notes
·
View notes