#What is vectorization in fintech?
Explore tagged Tumblr posts
Text
What is vectorization in fintech?
What is vectorization in fintech? By Kwami AHIABENU (PhD) The financial sector is heavily data driven. Every day, trillions of data is generated by the global financial system; these data sets are the bedrock of the financial system since they support a variety of applications, especially decision-making. The key challenge remains how to effectively, efficiently and quickly process these large…
0 notes
Text
10 Hot Tips for Logo Design That Make a Real Impact
A logo is often the first visual connection people have with your brand, shaping how they remember you. Whether you are launching a startup or refreshing your identity, a well-designed logo can be the difference between blending in and standing out. Here are 10 hot tips every business owner should know when it comes to great logo design in Sydney:

1. Simplicity is Key
The most impactful logos are straightforward, minimal, and easily identifiable. The most impactful logos are straightforward, minimal, and easily identifiable. Think Nike or Apple. A simple logo communicates your message quickly and looks great across all platforms.
2. Make It Memorable
A logo should leave a lasting impression. Use a unique shape, custom typography, or a clever visual twist to make sure people remember your brand after one glance.
3. Ensure Versatility
Your logo should work on everything, website headers, business cards, billboards, and even merchandise. Design in vector format so it scales without losing quality, and test it in black and white too.
4. Keep It Relevant
Your logo should effectively convey your brand’s quality and industry. A playful café might go for a hand-drawn style, while a fintech startup would benefit from a sleek, modern look.
5. Add Visual Salience
Use contrast, negative space, or bold shapes to draw the eye. A visually striking logo stands out in a crowd and communicates your brand personality with impact.
6. A/B Testing
Test multiple logo versions with real users or customers. You’ll gain valuable feedback on what resonates best before making a final decision.
7. Master Your Typography
Typography isn’t just about choosing a pretty font. The typeface should enhance your brand’s voice, elegant, strong, quirky, or minimal. Don’t mix too many fonts; clarity is crucial.
8. Use Symbols and Icons Thoughtfully
Icons can strengthen your message, but avoid clichés. Use meaningful, well-crafted symbols that align with your brand story. Abstract logos also work well when done right.
9. Research Your Competitors
Look at logos in your industry to identify what works and what doesn’t. This helps ensure your design feels fresh and unique while staying within industry expectations.
10. Conclusion
Great logo design isn’t just art, it's strategy. Aim for clarity, consistency, and connection. If you are unsure where to start, working with a professional logo design agency like LogoDo ensures your brand gets a logo that’s not just beautiful, but truly brand-ready.
Your logo represents your brand’s voice at a glance. Make it count.
Need help crafting a custom logo? Contact LogoDo—we're here to bring your brand vision to life. 10 Hot Tips for Logo Design That Make a Real Impact
#logo design#business branding#logo design in Sydney#logo designer in Sydney#logo design agency in Sydney#best logo design agency in Sydney
1 note
·
View note
Text
Abstrike Empty State Illustrations — Free & High-Quality Designs by IconAdda
Empty state images are required to enhance the user experience in Ui/UX design. When there is no data, the abstrian empty state image offers aesthetic and informative perspectives that guide users to realize the status of the system. To enhance its digital ventures, Iconadda provides an extensive range of free Graphics.
Empty state images: What are they? If there is no data to show on the user interface, there are blank conditions, such as: There were no results for your search. A lack of an Internet connection errors pages (404, 500, etc.) employs beautiful pictures for skill messages rather than a blank screen or alerts for a message or notification. These images enhance the function by providing guidance, by decreasing annoyance and overall the user experience.
Why use abstrike empty state images from Iconadda?
1. High quality and flexible design
Our empty state drawings in Iconadda are drawn with precision to conform to contemporary UI/UX requirements. With either a webapp, mobile app or dashboard, our vector-based images can easily be modified to fit your brand.
2. Free illustrations options

3. Numerous formats to make integration easy
Our abstrike empty state illustrations come in numerous formats like SVG, PNG and more to make it convenient to incorporate them into any design or development process.
4. Ideal for web and mobile applications
At first, these images are compatible with multiple platforms and provide a seamless visual experience. Whether you are creating an e-commerce website, mother-in-law website or fintech app, you can make our empty state graphics interface more user-friendly.
How to use blank state images? User increase on board: Guide users through novel features using impressive views. Reduce error handling: Replace standard error messages with an amicable sketch. Marketing involvement: Users find interest even in any material availed. Easier navigation: Assist users on what to proceed with when meeting empty situations.
Free download of abstrike blank state images from iconadda
At Iconadda we think that big design should be accessible to all. That is why we offer a set of free completely empty state images that you can download and use in your projects right away.
Begin today!
Visit iconadda and discover our extensive library with images, high-quality stickers and icons. You are a UX/UX designer, developer or business masters, our abstragistic empty state images will assist you in designing a spontaneous user experience.
Don’t remember! Download free photos today and add the life of your empty conditions!
#EmptyStateIllustrations #MinimalIllustration #VectorArt #AbstractDesign #ModernIllustration #CreativeVectors #UIUXDesign #FlatIllustrations #WebGraphics #DigitalIllustration #AbstractVectors #IllustrationPack #CleanDesign #DesignResources #UIIllustrations
#EmptyStateIllustrations#MinimalIllustration#VectorArt#AbstractDesign#ModernIllustration#CreativeVectors#UIUXDesign#FlatIllustrations#WebGraphics#DigitalIllustration#AbstractVectors#IllustrationPack#CleanDesign#DesignResources#UIIllustrations
0 notes
Text
Creating a Secure and Fraud-Free Blockchain Gaming Experience
In the wild west of blockchain gaming, security isn't just a feature it's the foundation everything else is built on. As someone who's watched this space evolve from crypto-kitties to complex metaverse economies, I've seen firsthand how security challenges can make or break a game's success.
Let's talk about how developers and players can create safer blockchain gaming experiences without sacrificing the innovation that makes this space so exciting.

The Double-Edged Sword of Blockchain Gaming
Blockchain gaming brings incredible opportunities: true digital ownership, play-to-earn economies, and unprecedented transparency. But these same features create unique security challenges. When in-game assets have real financial value and transactions are irreversible, the stakes get much higher.
I remember talking to a developer who launched one of the early NFT-based games. "We were so focused on the creative mechanics," he told me, "that we didn't realize we were essentially building a financial platform too." This mindset shift is crucial—blockchain game development requires thinking like both a game designer and a fintech security expert.
Security By Design: Building From the Ground Up
The most secure blockchain games bake protection into their architecture from day one, rather than bolting it on later:
Smart Contract Auditing: This isn't optional anymore. Multiple independent audits from reputable firms should be standard practice before any code goes live. I've seen projects delay launches to address audit findings and never regretted it—unlike those who rushed to market with vulnerabilities.
Layered Defense Mechanisms: The best security systems use multiple validation checks at different points. Think of it like airport security—ID checks, scanners, and human verification working together rather than relying on just one system.
Progressive Decentralization: Many successful projects start with some centralized controls that gradually transfer to the community. This allows for quicker responses to security incidents early on while still delivering on the decentralized promise long-term.
Player Protection: Making Security User-Friendly
Security isn't just about code—it's about how players interact with your game:
Intuitive Wallet Integration: Players shouldn't need a computer science degree to keep their assets safe. The games gaining the most traction offer simple wallet connections with clear permissions.
Transaction Verification: Always show players exactly what they're approving in plain language. "Allow access to ALL your tokens forever" should be a red flag that's impossible to miss.
Fraud Detection Systems: Machine learning can identify unusual transaction patterns before they become problems. One game I play implemented this after a phishing attack and has since prevented thousands of suspicious transactions.
Combating Common Attack Vectors
Understanding the threats is half the battle:
Phishing Resistance: Players get targeted through fake websites, Discord messages, and emails claiming to be from your game. Regular education campaigns and verification systems can dramatically reduce successful attacks.
Flash Loan Exploits: These complex attacks manipulate token prices by borrowing large amounts of cryptocurrency within a single transaction. Implementing circuit breakers and value locks can help mitigate this risk.
Front-Running Protection: When transactions wait in the mempool, bad actors can see them and execute their own transactions first. Solutions like commit-reveal schemes or private transaction pools are becoming standard defenses.
Community as Security Partners
Your players are your most valuable security asset:
Bug Bounty Programs: Reward white-hat hackers for finding vulnerabilities before malicious actors do. Some of the strongest security improvements in blockchain gaming have come from community members incentivized to protect rather than exploit.
Transparency Culture: Regular security updates, clear communication about risks, and honest post-mortems after incidents build trust more effectively than pretending problems don't exist.
Community Monitoring: Engaged players often spot suspicious activity before automated systems do. Creating easy reporting channels turns your entire player base into a security team.
Real-World Success Stories
Learning from those who've gotten it right:
Axie Infinity learned hard lessons after their Ronin bridge hack but emerged stronger with multi-signature validation requirements and dramatically improved monitoring systems.
Gods Unchained prioritized secure trading from day one, implementing escrow systems that prevent the most common card-trading scams.
The Sandbox created a phased withdrawal system for high-value transactions, allowing time for verification before assets move out of the ecosystem.
The Road Ahead: Evolving Security Landscape
As blockchain gaming matures, security approaches are evolving:
Insurance Models: Some games now offer optional insurance for high-value assets, creating protection pools funded by small transaction fees.
Standardized Security Frameworks: Industry bodies are developing shared security practices specific to blockchain gaming, similar to PCI standards in financial services.
Reputation Systems: Cross-game identity verification is emerging, making it harder for bad actors to simply move to a new game after being identified.
Final Thoughts
Creating truly secure blockchain games isn't just about protecting assets—it's about building the foundation for this entire industry to thrive. When players trust the ecosystem, they'll invest more time, creativity, and yes, money into these virtual worlds.
The blockchain games that will stand the test of time aren't just the ones with the flashiest graphics or most innovative gameplay—they're the ones that players trust to safeguard their digital lives. By prioritizing security alongside creativity, developers can build experiences that are not just fun to play, but fundamentally reliable.
In this exciting but still-maturing space, security isn't the enemy of innovation—it's what makes sustainable innovation possible.
#game#mobile game development#multiplayer games#metaverse#vr games#nft#blockchain#gaming#unity game development
0 notes
Text
How platformization is transforming cyber security - CyberTalk
New Post has been published on https://thedigitalinsider.com/how-platformization-is-transforming-cyber-security-cybertalk/
How platformization is transforming cyber security - CyberTalk


With more than 15 years of experience in cyber security, Manuel Rodriguez is currently the Security Engineering Manager for the North of Latin America at Check Point Software Technologies, where he leads a team of high-level professionals whose objective is to help organizations and businesses meet their cyber security needs. Manuel joined Check Point in 2015 and initially worked as a Security Engineer, covering Central America, where he participated in the development of important projects for multiple clients in the region. He had previously served in leadership roles for various cyber security solution providers in Colombia.
In this insightful Cyber Talk interview, Check Point expert Manuel Rodriguez discusses “Platformization”, why cyber security consolidation matters, how platformization advances your security architecture and more. Don’t miss this!
The word “platformization” has been thrown around a lot recently. Can you define the term for our readers?
Initially, a similar term was used in the Fintech industry. Ron Shevlin defined it as a plug and play business model that allows multiple participants to connect to it, interact with each other and exchange value.
Now, this model aligns with the needs of organizations in terms of having a cyber security platform that can offer the most comprehensive protection, with a consolidated operation and easy enablement of collaboration between different security controls in a plug and play model.
In summary, platformization can be defined as the moving from a product-based approach to a platform-based approach in cyber security.
How does platformization differ from the traditional way in which tech companies develop and sell products and services?
In 2001, in a Defense in Depth SANS whitepaper, Todd McGuiness said, “No single security measure can adequately protect a network; there are simply too many methods available to an attacker for this to work.”
This is still true and demonstrates the need to have multiple security solutions for proper protection of different attack vectors.
The problem with this approach is that companies ended up with several technologies from different vendors, all of which work in silos. Although it might seem that these protections are aligned with the security strategy of the company, it generates a very complex environment. It’s very difficult to operate and monitor when lacking collaboration and automation between the different controls.
SIEM and similar products arrived to try to solve the problem of centralized visibility, but in most cases, added a new operative burden because they needed a lot of configurations and lacked automation and intelligence.
The solution to this is a unified platform, where users can add different capabilities, controls and even services, according to their specific needs, making it easy to implement, operate and monitor in a consolidated and collaborative way and in a way that leverages intelligence and automation.
My prediction is that organizations will start to change from a best-of-breed approach to a platform approach, where the selection factors will be more focused on the consolidation, collaboration, and automation aspects of security controls, rather than the specific characteristics of each of the individual controls.
From a B2B consumer perspective, what are the potential benefits of platformization (ex. Easier integration, access to a wider range of services…)?
For consumers, the main benefits of a cyber security platform will be a higher security posture and reduced TCO for cyber security. By reducing complexity and adding automation and collaboration, organizations will increase their abilities to prevent, detect, contain, and respond to cyber security incidents.
The platform also gives flexibility by allowing admins to easily add new security protections that are automatically integrated in the environment.
Are there any potential drawbacks for B2B consumers when companies move towards platform models?
I have heard concerns from some CISOs about putting all or most of their trust in a single security vendor. They have in-mind the recent critical vulnerabilities that affected some of the important players in the industry.
This is why platforms should also be capable of integration through open APIs, permitting organizations to be flexible in their journey to consolidation.
How might platformization change the way that B2B consumers interact with tech companies and their products (ex. Self-service options, subscription models)? What will the impact be like?
Organizations are also looking for new consumption models that are simple and predictable and that will deliver cost-savings. They are looking to be able to pay for what they use and for flexibility if they need to include or change products/services according to specific needs.
What are some of main features of a cyber security platform?
Some of the main features are consolidation, being able to integrate security monitoring and management into a single central solution; automation based on APIs, playbooks and scripts according to best practices; threat prevention, being able to identify and block or automatically contain attacks before they pose a significant risk for an organization…
A key component of consolidation is the use of AI and machine learning, which can process the data, identify the threats and generate the appropriate responses.
In terms of collaboration, the platform should facilitate collaboration between different elements; for example sharing threat intelligence or triggering automatic responses in the different regions of the platform.
In looking at platformization from a cyber security perspective, how can Check Point’s Infinity Platform benefit B2B consumers through platformization principles (ex. Easier integration with existing tools, all tools under one umbrella…etc)?
The Check Point Infinity platform is a comprehensive, consolidated, and collaborative cyber security platform that provides enterprise-grade security across several vectors as data centers, networks, clouds, branch offices, and remote users with unified management.
It is AI-powered, offering a 99.8% catch rate for zero day attacks. It offers consolidated security operations; this means lowering the TCO and increasing security operational efficiency. It offers collaborative security that automatically responds to threats using AI-powered engines, real-time threat intelligence, anomaly detection, automated response and orchestration, and API-based third-party integration. Further, it permits organizations to scale cyber security according to their needs anywhere across hybrid networks, workforces, and clouds.
Consolidation will also improve the security posture through a consistent policy that’s aligned with zero trust principles. Finally, there is also a flexible and predictable ELA model that can simplify the procurement process.
How does the Check Point Infinity Platform integrate with existing security tools and platforms that CISOs might already be using?
Check Point offers a variety of APIs that make it easy to integrate in any orchestration and automation ecosystem. There are also several native integrations with different security products. For example, the XDR/XPR component can integrate with different products, such as firewalls or endpoint solutions from other vendors.
To what extent can CISOs customize and configure the Check Point Infinity Platform to meet their organization’s specific security posture and compliance requirements?
Given the modular plug and play model, CISOs can define what products and services make sense for their specific requirements. If these requirements change over time, then different products can easily be included. The ELA consumption model gives even more flexibility to CISOs, as they can add or remove products and services as needed.
How can platformization (whether through Infinity or other platforms) help businesses achieve long-term goals? Does it provide a competitive advantage in terms of agility, innovation and cost-efficiency?
A proper cyber security platform will improve the security posture of the business, increasing the ability to prevent, detect, contain and respond to cyber security incidents in an effective manner. This means lower TCO with increased protection. It will also allow businesses to quickly adapt to new needs, giving them agility to develop and release new products and services.
Is there anything else that you would like to share with Check Point’s thought leadership audience?
Collaboration between security products and proper intelligence sharing and analysis are fundamental in responding to cyber threats. We’ve seen several security integration projects through platforms, such as SIEMs or SOARs, fail because of the added complexity of generating and configuring the different use cases.
A security platform should solve this complexity problem. It is also important to note that a security platform does not mean buying all products from a single vendor. If it is not solving the consolidation, collaboration problem, it will generate the same siloed effect as previously described.
#ai#AI-powered#America#Analysis#API#APIs#approach#architecture#automation#B2B#Business#business model#change#Check Point#Check Point Infinity Platform#Check Point Software#CISOs#Cloud Security#cloud-delivered#clouds#Collaboration#collaborative#Companies#complexity#compliance#comprehensive#consolidated#consolidation#consumers#cyber
1 note
·
View note
Text
Tea and Soju
Bridging piece between “Are we ever going to talk about this?” and “KIdnapped!Q”. The events here feed into the plot but can be read as a series of drabbles.
Tags: Established relationship, but open secret. Intimacy in plain sight. Bond feeling his age. Mostly fluff with plot points. Tiny bit of angst. Q-Branch being weird.
-------------
Christ, he feels like a teacher on a school trip. “Might I remind the class that the french police are notoriously speed adverse and do not take well to British nationals breaking the law on their home soil?”
--------------------------------------------------
SIS HQ, M’s Office - 12th Floor
Eve hands him his next mission dossier without preamble when he enters the antechamber to M’s office.
“He doesn’t want to see me today?”
Eve shakes her head. “Crisis in Hong Kong. He’s tied up with the station chief all morning. Besides your next assignment is a more or less a straightforward reconnaissance.”
There is no such thing as a straightforward in their world, Bond disagrees in his mind. He flips open the file and takes a seat on the edge of her desk, ”What is it?”
Eve comes around to stand next to him:
“MI6 Persons of interest: First is Marco Sciarra. Formerly linked to Silva on the periphery and several other possible terrorist links. Word has it, he’s meeting with an entrepreneur by the name of Kim Min Jun in Geneva next week. Which brings us to the second person: Mr Kim is connected to one of the Korean Chaebols - grandson to the Chairman,” Eve points to his picture in the file.
Kim Min Jun is a handsome man in his mid thirties. Perfectly coiffed and flawless skinned. The photo looks to be a media shot; designer clothes and posture befitting a princeling from a privileged background. His expression in the picture is cold and slightly imperious.
“You know how it is, the chaebols control nearly all aspects of the Korean economy including politics. So what he’s doing talking to someone like Sciarra piques our interest.”
Curious indeed. “What do we know about Sciarra and the princeling? And why Geneva?”
“Sciarra we know very little except he’s a fixer of sorts. Procuring equipment and expertise for his clients. You’re going to have to fill in the blanks for us when you track him,” Eve is apologetic on behalf of the research team.
“Kim we know more about. He’s dabbling in cryptocurrency at the moment. The Korean government has banned ICOs so many crypto start-ups are registering in friendlier countries. Switzerland has one of the friendliest regulations for fintech startups. Kim is unveiling his ICO (Initial Coin Offering) to investors next week. His new cryptocurrency is called- $PECTRE.”
Considering the concerns around cryptocurrencies and their use, I suppose that’s fitting. Is it really spelled that way?” Bond points at the name on the printed page. -Classy-. He thinks sardonically. Eve chuckles.
The next page his is cover brief. He reads it out loud, “Cover story… CEO Private Security Contractor. Should be easy enough to fill out.” He likes the ‘private security’ covers, its the easiest for him to slip into considering it is essentially the same skillset.
“The timing coincides with the Geneva Motor Show and the EBACE (European Business Aviation Conference & Exhibition) so there will be influx of fat cat corporate and private executives around the city with their private security teams - seems like a good reason to explain you and your Walther’s presence.”
“Hmm… What’s this?” he reads the next paragraph. They have teamed him up with the freshly minted 008. Logical - considering Agent Park is speaks Korean, he can work the Chaebol angle while 007 tracks Sciarra.
Then Bond sees it, the two other cover names belonging to people he knows well - Mr. Collin Mitchel and Mr. Nishant Chowdhary will be joining them on the trip.
Eve can see Bond’s hesitation, “Well, your cover will look rather silly without a ‘fat cat’ of your own to secure won’t it? … M approved their request to attend the auto and aviation show yesterday afternoon, so it’s a happy coincidence. Besides, they can help run your Ops.”
Q will be pleased about his shopping trip getting approved. All that engineering in one place, it was all Q could talk about for days. This mission will take almost three weeks just looking at the timeline, bookended by the two exhibitions. Mr Kim’s ICO launch will happen in between that, but intel has him arriving early for preparations.
Altogether, the mission parameters seem perfect and spending a so much time with Q in picturesque Geneva is something he can only dream of - but it does mean he is weighed down with the task of ensuring security for both the boffins.
It would not have mattered in his younger days; what with his cavalier attitude towards the lives of people he crossed paths with on his missions - to the point that even the previous M rebuked him for it (e.g. Strawberry Fields). This older and wiser 007 can feel the creep of responsibility and the extra precautions he will need to take.
Eve the omniscient seems to sense his emotions, smiles kindly at him - and despite being a decade younger, she tells him, “Time to grow up James.”
——————————
SIS HQ - Cafeteria
Friday afternoon 12:30pm
“So, we finally finished the analysis on Hayden’s phone... I know, its been over a month. There’s been so much going on with the spike in ransomware attacks on UK targets and Hayden hasn’t been the most cooperative.” Mark is sitting opposite Q on the crowded communal cafeteria bench, chewing on his pesto pasta salad.
It is peak lunch hour and the place is chock a block full. Q is still waiting for his lunch, “Anything of interest?”
“It looks like a rooting malware was downloaded into his phone at one point and then removed to avoid detection. We’ve gone though the logs of each app to find what might have been compromised but we still can’t find anything…”
At that moment, Agent 007 appears from behind Q. He drops a brown envelope and an armful of packaged food onto the long table. He then picks out a sandwich and a bottle of iced tea and wordlessly slides it in front of Q. The agent then squeezes himself into the small opening on the bench between Q and the next occupant. He has to sit straddling the bench, perpendicular to the table and angled towards Q in order to fit.
Mark notices that Q doesn’t even flinch at the sudden invasion of his personal space, his attention still on Mark even as he unscrews the top off the bottle and begins to unwrap his sandwich without so much as an acknowledgement of 007.
Taking his cue, Mark continues, “The likeliest target was his email, but they’re mostly administrative, we don’t send classified information through emails. We’re combing the logs to see what could have interested the hackers.”
“Is this about Hayden?” 007 asks, catching up to the conversation while inhaling his massive panini sandwich.
Mark nods, “It’s going to take more time to figure out if the hackers got anything useful out of the whole thing.”
007 considers, “They went though all the trouble of setting up a trap like that - it would have taken months. No one expends resources like that unless they know what they want out of it...”
He shifts the sandwich in his hands, stuffing a piece of chicken that escaped back into the bread before he continues, “They would have known MI6 wouldn’t be so callous with classified information. So perhaps Hayden wasn’t the actual target - he might have just been a vector. A way to get into the system.”
Q finally turns to 007, “But it is unlikely that they would spend time rooting around our systems for information they might find relevant, it would take too long. Not to mention the navigating layers of security. The longer they stay inside the system, the higher chances of being found out.”
“Precisely. If it were me, I’d use the access to engineer it so that my target -gives- me what I’m looking for. Then bugger the hell out of there before they realise it.” Bond emphasises the word ‘gives’ by tapping a forefinger on the table top.
“She managed to slip away, but as I understand, DEF CON was her opportunity to break things off with Hayden - even he mentioned as much. I’m willing to bet their final rendezvous was to allow her to remove the malware from his phone. Think a bout it, why remove the malware unless you’ve already got what you need and you’re covering your tracks?” Bond takes a swig from Q’s iced tea.
“Bond, if it were you, what would you do with the access?” Q asks prompting him further.
“It would depend on what I’m looking for. If we take it that Hayden was not a random target, then consider what his position and clearance will give him access to. I could use social engineering to pose as Hayden and requisition seemingly innocuous information that might point me in a direction or to confirm intel,” Bond takes them thorough his thought process.
Mark thinks out loud, “His emails just contain administrative stuff. Meeting schedules, budgets, department rosters, project timelines… hiring and resignation notices—“
Bond cuts him off before he misses the point, “Put motive aside for the moment and look at the behaviour. If we work on the premise that the information was given to the hacker, try checking his inbox - though it’s likely the hacker would have deleted it. So check his deleted email logs, even if they emptied the bin, I’m sure you have ways around that don’t you?”
The two boffins stare at him for a moment. The type of work they do meant that they are naturally wired as detail oriented and deep technical thinkers, but can sometimes miss the forest for the trees.
Mark swallows the last of his mouthful, expression excited. He picks up his trash and water bottle and starts to extricate himself from the bench, “Good chat 007. I’m going to—,” he makes a flailing gesture in the direction of the lift banks, indicating he was going to get right on it. “I’ll update the both of you later!” he calls back to them almost as an afterthought.
—
Moment later, another SIS employee slides into the vacated seat, grateful to have found an opening. But once she realises who is sitting across from her, she seems to hesitate before nodding politely to Bond and Q who return the gesture.
The general population in SIS are a little wary around the Double-0 agents. Something about knowing definitively that the person you’re facing has taken a life possibly with their bare hands - even if it is in the service of the nation that makes most people uncomfortable.
It is exactly how 007 likes it anyway; keeps the small talk at bay. Bond turns his attention to Q, his voice dropping lower now that it is only two of them in the conversation, mouth inches from Q’s ear, “What are you doing after lunch? Do you have time to talk about Geneva?” he taps the official looking brown envelope on the table.
“Ah, I have a meeting with the people from Aston Martin at Tintagel House. Shouldn’t take long. We can discuss after that?” Q suggests.
Bond perks up like a child trying to guess his Christmas present. “Oh? Am I getting a new car?”
“You realise that there are twelve other agents we have to outfit besides yourself…” Q gives him a pointed look, reclaiming his iced tea that Bond stole.
“Besides, it might end up being an electric car; and we know how you feel about any vehicle we issue you that has anything short of a V8 inside.”
007 at least had the temerity to look sheepish. He recalls the heated argument several years ago with Q-Branch the last time they attempted to send him out with a hybrid car. An argument he may live to regret, now that the technology has progressed so rapidly.
“Can I come with?” Bond asks, trying not to sound too needy by concentrating on wiping his fingers with a paper napkin. It has been over month ago that they agreed to share living arrangements, but he’s been away on mission for half of it so realistically speaking, his wardrobe has spent more time in Q’s bedroom than his person.
“You can wait in the lab. Or… you might even try locating that mythical office of yours. Legend has it you were given one, even if it might be a hot desk.” Q teases him.
—————
Tintagel House, Albert Embankment
In the end, Q relents and lets Bond walk him the short distance to Tintagel House and the rented co-working space that Q-Branch employees use when they need to meet external vendors.
The two representatives from Aston Martin are waiting when they arrive. Q introduces himself as Collin Mitchel from MTech R&D Consulting. Bond’s presence is explained away as ‘private security’ a convenient excuse when he wants to be ‘seen but not heard’.
To the outside world, the four of them - Q (Collin Mitchel), R (Jenny Khoo), S (Nishant Chowdhary), and P (Mark Trent) are Senior Project Managers of MTech, a private engineering R&D firm specialising in IT security and customised equipment solutions.
The little exclusive R&D company is the front that allows Q-Branch to procure components and equipment without being directly involved. Their role as Senior Managers is carefully crafted to position them high enough to have clout when dealing with external contractors but not high enough to warrant any further interest in them personally. A careful balancing act.
This is their cover story for most of their day-to-day lives outside the walls of SIS. The first and most superficial layer of their identities. It is their public persona - the names on their takeaway coffee cups and the names the world would call them.
As for the car, it is not a production car at all. ‘Mr Mitchel’ is custom designing a car to very exacting specifications. They have the chassis pinned down based on the Vantage. And the body will be a custom designed beauty, if the concept drawings are anything to go by - but the engine and other mechanicals have yet to be finalised. Collin is leaning towards electric as the small motors leave more room inside for ‘modifications’. The auto show will give him inspiration for how he can implement the vision.
Bond still doesn’t know who the car is for; Q refuses to say. Aside from the travesty of the electric motor, the renderings of the car seem exactly his style. Surely he is due for a replacement. His poor track record keeping cars in one piece not withstanding, the older V8 Vantage he is usually assigned is looking frankly anaemic at this point.
The meeting ends an hour later. As Q walks them out of the building, the senior rep who’s known Collin for a while now asks a curious question. “Hey Mitchel, seeing that your office is so close the the SIS building, have you ever met an MI6 agent?”
Q is unperturbed by her question. It is a question that comes up often in various forms during small talk. “Well, they’d be shit spies if I can spot them,” is his practiced reply. He takes a peek over her shoulder at Bond who is standing to the side - listening to everything.
“Ha! True… Imagine though, you could be having lunch at the place across the street and sitting next to someone like Jason Bourne.” The rep seems to find the idea titillating.
“Nevermind the spies, imagine the kind of tech they have in there. I read somewhere that they’ve got submersible cars and portable jet-packs..,” the second rep, an engineer, chimes in. “Being the Quartermaster must be the coolest job.”
Again Q unconcerned. The codename has been around for decades, since even before Major Boothroyd. Q himself had heard the name thrown around in engineering school, used to reference the more ridiculous solutions that students came up with.
“Yes, I suppose it would…” Q agrees with the assessment and leaves it at that.
———
SIS HQ, Q-Branch - Lower Ground Floor 1
Agent Marcus Park does not know the ‘rules’ yet. The newly minted Double-0 replaces the outgoing 008 who has miraculously survived to see retirement. Park is of Korean descent, mid 30s, former Captain in the Royal Army…… Tall and lean, at home in street fashion and cleans up well when needed. Tech and social media savvy, he’s the new generation agent - as long as he stays alive long enough.
He’s been measured, photographed, scanned, sampled, pinched, poked and prodded all day in Medical and Q-Branch as they collect the the information they need to customise all the bits that will go into his kit. Marcus thinks the Q-Branch minions know more about him by now than he knows himself. They even know his bone density and which side of his molars he prefers to chew on.
Thankfully by mid afternoon, Nish releases him temporarily to let him have a break. He has taken the opportunity to make himself a cup of tea and have some biscuits. He returns to Nish’s workspace to wait for further instructions carrying his tea in a borrowed novelty Q10 mug.
Nish is typing on his workstation, reviewing Park’s results but seems distracted - stealing surreptitious looks his way. A few other minions slow down as they walk by as well. As the new agent, Marcus is expecting some sort of hazing. Though he’s expecting it to come from the senior Double-0s.
He thinks it is better to get it done with. “I get the feeling something’s up? Is the tea spiked?”
Nish tries to find his words, without making Q-Branch seem like weird people, but just ends up gulping air like a goldfish.
“Earl grey? In the fancy tin?” Marcus prompts.
“No. No… It’s not spiked. That’s the Quartermaster’s tin.”
“Ah, he’s particular about that sort of thing is he?” Mischief. “I won’t tell if you won’t,” he taps the side of his nose.
Josh, the minion occupying the next table waves his arms frantically at Nish from behind 008. He points repeatedly at the CCTV monitor mounted on the column above his workstation. On it, they can see feeds from all levels of Q-Branch, including the lift lobby and main doors of each floor - it is as much for security as well as work safety.
Nish takes a quick peek at the monitor and starts to worry. “Not exactly…. It’s not the tea, and Its not the Quartermaster you should be worried about.“
Okaay… Marcus is starting to think Q-Branch are a weird bunch. He had only been officially introduced to Q in the morning. Marcus has been an agent for several years but stationed overseas. As a field agent, he normally collected his tech from his handlers so never expected that the skinny, floppy haired man-child he’d crossed paths with maybe twice in the SIS bulling was THE Quartermaster. He seemed normal enough from the brief encounter, perhaps bordering on patronising - but that could be just the formality that made it seem so.
“Josh will make you a fresh cup!” Nish snaps his fingers urgently at the other man. Josh rushes up to Marcus to retrieve the mug.
“Oh, don’t trouble yourself. This one is fine.” Marcus waves him away still holding on to the mug. Josh is paralysed, not knowing what to do. He can’t very well wrestle it out of the agent’s hands.
Too late.
”Ah 008. Nish. How is the fitting going?” Q’s voice carries from behind Nish. Nish does not have to turn around to know that 007 is with him. Josh slinks away quickly.
“Quartermaster. It’s going very well. Taking a break, just replenishing the sugar levels,” 008 lifts the mug of tea and the plate of biscuits. If the Quartermaster is that particular about his tea he’s going to try and get a rise out of him.
But Q does not react. Instead it is the man next to him that stills ever so slightly - no that’s not accurate, it was more like an almost imperceptible shift in body language. The body loosing that casual ease, control sliding into place.
A fellow double agent Marcus is sure. Predators know other predators. They study each other for a moment.
Q realises they haven’t been introduced. “Ah 008, have you met 007?”
Both men extend a hand out for a polite shake. Introductions ensue.
Nish uses the opportunity to signal to Josh to check his chat program.
:: Make a fresh pot and get back here with 3 mugs ASAP! ::
Josh flees to the pantry just in time, as the introductions finish. Nish then draws everyones’ attention to the data they have collected so far in the day. And when he runs out of interesting things to say about the data, he tries to shift the conversation to the new car for 008.
“Ah, about 008’s car - how did the meeting with Aston Martin go?” Which was apparently the wrong thing to say.
There is no mistaking the hurt and affront as 007’s eyes go wide and the set of his mouth goes slack.
Q grimaces at Nish and squeezes his eyes shut a moment before turning to face 007. The lowered tilt of his head and the apologetic smile up at 007 tells Nish that there might have been a misunderstanding about it. Oops?
What follows is an uncomfortable summary of the meeting with Aston Martin. With Q trying to convey his excitement about the project without offending 007 further.
Marcus listens attentively, leaning casually on Nish’s worktable, asking appropriate questions and offering his input about the design and potential modifications - all the while taking sips from the mug cupped in his hands. With each consecutive sip, he notices 007’s stare get more intense, eyes like blue chips of ice - Bond seemed to be watching him drink.
Curious. Marcus is confident of his own charms, but he hasn’t even tried anything yet. Surely 007 would be much more discrete than this if he were interested. The senior agent is not conventionally handsome but he has a rugged charm - if you like that sort of thing. Still, it might be an enlightening experience. He catches Bond’s stare and flicks the tip of his tongue against the lip of the mug before taking the next sip.
Bond is not happy. He is still smarting from the disappointment, then he has to listen to 008 ingratiatingly espouse the benefits of going electric with the new car and tolerate his drinking out of Q’s mug. And to top it off, 008 is now -taunting- him??
He doesn’t know when it happened, but Q is so attuned to Bond’s breathing by now he can feel the irritation radiating off the man standing next him. He thinks it is a rather disproportionate response to not getting a new company car for an agent his age - especially when he was never promised one in the first place.
Nish thinks this afternoon is headed straight for a disaster. Why is Marcus molesting the mug - it is like waving a red cape in front of an angry bull. Bond is so still it it is foreboding. Where the hell is Josh??!
Josh finally appears with a tray of mismatched mugs filled with tea. He nudges his way in between 007 and 008 using the tea tray as a wedge.
“Oh! Thank you Josh. You didn’t have to…” Q is bewildered; his minions don’t usually make tea for their visitors with the exception of Mallory. It is not encouraged to prevent the double-0s from feeling further entitled.
Josh deliberately picks a spot on the table, right on the small strip of clear space in front of 008 to set the tray down. This forces Marcus to put down the Q10 mug somewhere else and help Josh clear a bigger area to fit and unload the tray.
Nish swipes the mug in the ensuing distraction and sets it on the far end of the worktable away from 008. Bond catches the action and cotton’s on; then decides to take matters into his own hands.
In a bizarre turn of events, 007 proceeds to pick up each fresh mug of tea and offers it to Nish first; then to Josh - who accepts it out of pure shock. And then finally to Marcus - who looks bemused as he accepts it.
Then he leans very close to Q, a hand on the small of his back - voice intimate, “I’ll go get your tea.” Then he leaves for the pantry; collecting the Q10 mug when he rounds the table.
This leaves the four of them (Q, Nish, Josh and Marcus) standing around the worktable in awkward silence. Q just shrugs and smiles tightly, not sure what has gotten into Bond today.
Marcus can tell something happened, and it had to do with tea - but is still not sure exactly what. He has to revise his assessment of Q-Branch and perhaps 007; they are DEFINITELY a weird bunch.
—————————————————————
London to Geneva
The twelve hour drive included several refuel and recharge stops. With 007 in his old V8 Vantage and 008 in a hand me down Audi R8 formerly assigned to 003. Q and Nish on the other hand were enjoying the brand new modified Tesla Model X.
The Tesla was meant to be a support vehicle for handlers or other members of the support team that needed to be closer onsite - a mobile Ops centre of sorts. The large central screen was perfect for video conferencing and the software that controlled most of the car’s functions made it easy to add specialised ‘apps’ that increased its capabilities. The ‘summon’ mode that came stock with the car had been hacked to near true autonomous levels - turning it into a bulletproof infiltration or escape pod that could be summoned remotely if needed.
To top it off, the boot space was now fitted with hot-swappable modules that could contain anything from an armoury, a medical lab, a mini workshop, a surveillance drone launchpad etc. depending on mission parameters. The teams could even use its batteries as a power generator for a limited time.
All in all, another technological marvel courtesy of Q-Branch. But the best thing about it was also the simplest. The fact that the electric motors had enough punch to allow support teams to catch up to, or flee from hot situations.
A fact not lost on the boffins during their test drive to Geneva. While the sport cars that 007 & 008 drove had higher top speeds, the Model X’s acceleration was as advertised - ludicrous.
“Oh my God. This thing is insane! Check the accelerometer, how many Gs did we pull?”
At motorway legal speeds, they were unmatched. Something the boffins took plenty of pleasure doing on the open road - overtaking the agents whenever they had the chance.
Q tuts smugly at them as he pushes the car performance, “Oh hello 007, 008. Mind picking up the pace? We haven’t got all day…”. The dark grey Tesla pulls out from behind the convoy and shoots smoothly past the stunned agents.
Over the 3-way call and the roar of his noisy V8 engine, Bond can hear Nish and Q hooting and cackling like teenagers. Drunk on instant torque - Nish even tried to egg the agents into a race.
“Come on! Last one to Saint Quentin buys dinner!” Nish called out over the connection.
“Where are they? Did we loose them?” Q ribs the agents.
A testament to his growing maturity, 007 refused to take the bait. He could out manoeuvre them easily even with the handicap; but as senior agent on this mission, he’s not about to encourage dangerous driving that will attract the attention the french police and get them pulled over for no good reason.
Agent 008 however, did take the bait - turning the section from Beaune to Saint Quentin into a light game of tag all the while quibbling with the boffins good naturedly.
“Dinner is a broad term. Are we talking Maccies or the Ritz?” Marcus wants clarification. His Audi R8 pulling out into the overtaking lane and closing the distance.
“Ah, there you are 008.” Q catches him in the rearview mirror.
“Mate, the Ritz of course! Risotto with Grana Padano cheese and truffle oil and a bottle of the best Chasselas in the house,” Nish is surfing the menu on his tablet.
Christ, he feels like a teacher on a school trip. “Might I remind the class that the french police are notoriously speed adverse and do not take well to British nationals breaking the law on their homesoil?”
“… wet blanket…” someone mutters over the line.
“This doesn’t have anything to do with 007 having the slowest car of the lot does it?” Marcus goads.
The roar of Bond’s V8 engine barely drowns out their laughter.
By the time they arrived at the next rest stop, Bond had reached the end of his patience. He is not about to let the inexperienced boffins attempt to race a young impetuous double-0 through the twisty alpine roads with its sharp drops up to Geneva.
He forces Nish to switch cars with him. As for Q, he pinned with a strong hand behind the neck like you would a naughty cat by the scruff - and fixed him with a disapproving glare.
That effectively put an end to the game. Bond’s sports car was far less intuitive to drive - unaided by fancy tech and electronics, the performance machine required skill and experience to control. Nish has not much of either with the car, so had to treat it with respect.
Which left Bond driving the Model X with Q as passenger. It is essentially a glorified minivan in his eyes.
“Since when were you the sensible one?” Q grouses, tapping on the navigation screen to check their arrival time.
“Haven’t you been in my ear nagging about it for years?”
“And you chose now to listen to me?”
“We can’t both be irresponsible at the same time.” Now there’s a sobering thought, the havoc the both of them can wreck on the world… maybe that’s why interpersonal relationships are frowned upon, “The world isn’t ready for it.”
Q looks over at Bond and taps some options on the screen. Suddenly the car feels different, just as they are about to merge back onto the motorway. The instant torque that throws him into his seat when he puts his foot on the accelerator catches him by surprise.
Twenty minutes into the drive and Bond has to grudgingly admit that the acceleration was addictive, and the silence a relief to his ears. The seats and suspension far less a strain on his back and the large screen is easier to read. 007 has to face the terrifying possibility that he might be getting… SOFT.
“Admit it, it’s not as bad as you thought it would be.”
“Yes fine, I’m starting to see what all the fuss is about. Can you drift in it?”
“Not quite yet…. We have figured out how to bypass the stability control and add it as a shortcut tile onscreen—,“ Q points to the red ‘Chase Mode’ button on the corner of the main screen.
“—but its a heavy car and no one in Q-branch has managed to get the tail to spin out without nearly killing themselves in the process.” Q grins at him, “You up to the challenge?”
Bond quirks a smile as he puts his foot down on the accelerator to effortlessly and silently overtake a lumbering lorry.
“Sure, when we get home… But what happens if I need to turn the car OFF and ON again in the middle of a chase?” He’s not quite ready to surrender his internal combustion engine for a mobile phone on wheels.
————-------
Geneva Motor Show - Palexpo, Grand-Saconnex
Aston Martin Exhibition Stand
“Bond, if you stand like that next to the Vantage any longer, the press is going to think you’re a hired model.”
The agent is doing his patented man-in-suit ‘pose’ - that blend of deliberate insouciance he’s perfected over the years, feet right distance apart, one hand in his pocket. Hell, his suit is probably more expensive than what some of the actual models here are wearing. If Q was being honest, Bond makes the car look even better.
Q knows what Bond is doing. He’d basically herded Q over to the massive Aston Martin stand and refused to let him leave. Dragging him back to draw his attention to one thing or another whenever Q tried to move on. The bastard is fishing for a new car and not so subtly hinting which one he wants.
“Come over here,” he uses his free hand to gesture to Q, cajoling and demanding at the same time.
Q has to roll his eyes. He comes to stand in front of the information sign next to the car. He knows it already, the recently updated Vantage now has a 4.0 litre twin turbo V8 engine pushing out 503hp, 0-62mph in 3.6 seconds with a price tag that does not even bear thinking.
Q does a bit of mental math, “At that price, not to mention the cost of the additional modifications, we usually want to get more than a single use out of it…” a direct jibe at 007’s track record.
Bond just smiles cheekily and leans in close, “But surely if it meant the difference between if I get home in one piece or… several pieces, it’d be worth it. Consider it safeguarding Her Majesty’s assets.”
-Oh low blow-. That’s emotional blackmail. If they weren’t in public, Q would have smacked him soundly with the stack of glossy brochures he’d been collecting all day.
“Or we could write you off as depreciated assets and be done with it,” that was extra mean, and Q knows it. So he softens the blow by handing Bond the stack of brochures to free his hands and starts to inspect the car - making a show that he is ‘considering’ the request.
He pops open the bonnet to examine the engine setup, walks around checks the tyres and breaks, checks the boot space before climbing in to examine the interior and driver’s setup and controls.
Q is surprised when an Aston Martin executive lands in the passenger seat all of a sudden and introduces himself as the Deputy head of Engineering before drawing Q into a conversation about the car’s performance and clever electronic bits.
In his peripheral vision, Q sees Bond round the car to stand just outside the driver’s door - trapping Q in the driver’s seat. Bond braces and arm on the hood of the car and leans into the cabin, ostensibly to listen to the explanations from the executive.
Lecture completed, Bond finally allows Q to climb back out. Q grudgingly accepts a brochure from one of the marketing reps circling the stand and when he turns to regard Bond, silently asking -Happy now?-.
The man is standing close - he picks the brochure out of Q’s hands, placing it on the very top of Q’s growing collection before handing the entire stack back to the quartermaster. A satisfied smile on his face that conveys -I want one-.
Nish appears just then interrupting their silent repartee, “Q!— I mean Collin.” Nish hisses his name in a not quite whisper. 007 has to suppress the urge to roll his eyes. The boffins keep forgetting to use their cover names.
“Have you seen the concept Lagonda? That thing is ‘effing bonkers!” Nish is holding a champagne flute. “They’ve got drinks too yeah!”
Their priority passes as well as MTech’s connections score them invitations to exclusive launches by select manufacturers. For the boffins, it is Disneyland but with free alcohol. 007 can only hope that they will manage not to get too drunk on ‘gratis’ bubbly by the end of the day.
———
It was not all play and no work for the agents though. The day proved to be a fruitful outing for all of them.
At the Bugatti concept unveiling, 008 spots his mark. Kim Min Jun is watching the event together with the other VIPs. Marcus makes his move, insinuating himself into his small entourage of young, rich, social climbers. He scores an invite to drinks and party that evening at the Mambo in the city.
007 too finds his mark walking the show floor with a stunning woman presumably his wife. He watches as Don Marco and Kim meet briefly upstairs in the invitation only pavilion of the Bugatti stand. 007 takes his opportunity, swiping an unattended marketing pass from a table and goes up to the woman whom he later learns is Donna Lucia Sciarra. From her, he finagles their hotel name and duration of stay whilst giving her a tour of the cars on display.
———----------------------
The Ritz-Carlton, Hotel De la Paix - 2:00am
Bond gets back to the Ritz at 2am. He’d spent the evening with Donna Lucia while her husband was away attending to business. While Lucia wasn’t averse to physical dalliances of her own, she was loyal to her husband and his chosen profession. She had enough understanding of economics to know that her own position and lifestyle depended on it.
Which meant that 007 despite his charms could not get much information out of her other than a hint that Sciarra’s activities revolved around a client (presumably Kim). However the evening did present him with the opportunity to plant trackers and upload a virus into Sciarra’s laptop.
Now back at the Ritz, his room is oddly empty - Q is not in the room nor the connecting one. Neither bed has been slept in, nor was there a note of explanation. He checks his phone in case he missed a message - nothing.
Bond searches his jacket for his earpiece and puts it back in, “Q? Are you there?” No answer, but a moment later a sleepy Nish answers.
“Yes 007? I thought you’d finished with your objective tonight? The virus will continue to monitor and transmit data, but it will take time for HQ to shift through to find anything of interest. Did you need anything else?”
“Where’s Q?” voice carefully neutral.
“Uhh… in his room? He said he had a headache and had me standby on comms tonight. Why?” Nish is starting to sound concerned.
Bond stamps down his rising unease. He’s about to request Nish to check Q’s location when the room lock beeps and the man himself enters, dressed as he was during dinner. Q is swaying on his feet a little, that and the flushed skin indicated that he might be slightly inebriated.
Eyes locked on each other. “Nevermind. False alarm,” he tells Nish and removes the earpiece.
“Where the -hell- were you?” Bond is relived, but can’t keep the irritation out of his voice.
Q is a little taken aback by it. “I…uh… 008 called, needing assistance. It seems Kim Min Jun has few topics of interest outside of the serial partying expected of a socialite. Financial investments is one and the other, engineering. He’s a software engineer by education though his actual coding experience is limited, however he does retain an -intense-“ head tilt to emphasise the world “—interest in the field.”
He’s rambling. Bond knows Q does that when he’s stalling. “What happened?” he asks, more gently this time.
“008 was having difficulty maintaining Kim’s interest, so requested my help. We met up with him at his rented residence for a private party. Sciarra was present as well. Marcus did the requisite drinking, including most of my share, while I did the talking. Mostly about IT security, a little bit about encryption - fundamentals for the most part.”
Q elaborates while walking further into the room. He starts to empty his pockets and removes his jacket. When he’s done, he leans against the hallway wall - clearly tired.
“After a while, Sciarra who hadn’t spoken much the entire night brings out a tablet. He had a game on it, some sort of storm the castle type strategy puzzle. The game is adaptive - machine learning adjusts the game’s response to the skill level of the player in real time. It does not have preset levels or preset game paths like traditional games.”
“I can’t imagine it would be something for commercial release, it’s terrible as a game - it felt more like a simulation. But to the right people, it would be entertaining I suppose. He asked if I could help him solve the game. He’d been struggling for weeks apparently.”
Then more quietly he adds, “Park and I were concerned that if we did not indulge him, Sciarra would leave early… and that would put you in a precarious situation.”
Q braces for Bond’s exasperation, “Q… we’ve discussed this. You are not to put yourself in danger for my sake.” Sleeping with a colleague had its complications.
“At no point this evening was Sciarra or Kim aggressive nor did I feel any immediate danger.. just a general unease.” Q tries to defend himself.
And quickly continues, “We spent close to an hour on it, trying multiple strategies before making significant headway. I wanted to leave after that, so made an excuse about being too drunk for anymore strenuous thinking. Sciarra did not seem inclined, wanting my help to finish it. Kim was more accommodating and let us leave. He seemed pleased though, enough to invite us to the launch of his ICO.”
Bond has a sinking feeling in his stomach. So that’s what Lucia alluded to, when she said her husband was out scouting for opportunities. What was 008 thinking? He’d tossed an unprepared boffin into shark infested seas and chummed the water.
“Invite YOU, you mean… I think their interests rest solely in you at this point.” Despite the disapproval roiling off him, Bond can sense how uncomfortable Q is and steps in close, hands wrapping around his ribcage. Q melts into the comforting touch, resting his hands on the lapels of Bond’s jacket.
“I suppose… James, I’m going confess - I’m feeling somewhat out of my depth in this. Sciarra makes me nervous. And the personal manipulation feels… distasteful. Intellectually I understand the need for it, but it’s so different when you’re in the thick of it, that constant anxiety about being found out.”
“I’m guessing you felt a connection with Kim? The manipulation works best if there is a connection but also feels the worst.” Bond hopes the explanation would help.
Q nods in agreement. “Kim is a good conversationalist, we have overlapping interests, in any other situation we could very well be friends. How do you do this?” It is a rhetorical question. He is beginning to understand what 007 has to do in the line of duty; how this line of work can alter your perception of the world. He recalls Bond’s file and the trauma of Vesper Lynd.
In a moment of drunken paranoia and insecurity of his own, Q’s internal commentary goes into a wild tangent - what if Bond with his training and psychopathic tendencies is toying with him? How would he even begin to tell? Cold creep of horror constricts his chest. What if one day James tells him that he’s done playing house? Itch scratched?
He tries to distract himself by picking at a loose thread sticking out of Bond’s shirt where a button should be, the next one down is missing as well. How unlike Bond, he’s usually so fastidious with his wardrobe— ohh!
“Did she… pop your buttons??” The mental image is not helping his insecurities at the moment. This is nothing, just a couple of buttons - nothing compared to the cuts and bruises Bond comes home wearing all too often. But it is enough to remind Q that as recent as half an hour ago, Bond was in the embrace of someone else. There is even a lingering hint of her perfume.
His expectations in this regard has not changed just because of their as of yet undisclosed relationship. Q can maintain a clinical detachment while reading about and even on occasion listening to 007’s amorous encounters in the line of duty. But he is usually spared the physical aftermath. James always return to him carefully put back and scrubbed clean of evidence so to speak. So to be confronted with it for the first time is jarring, especially in his current state of mind.
Bond feels Q stiffen in the embrace. The gentle idling hands on his chest suddenly ceasing their movements - recoiling slowly into loosely balled fists. He grabs Q’s hands before they slip off his chest.
The action snaps Q out of his spiral of paranoid thoughts, anchoring him. The cold tightness around his chest eases - the warm reality he chooses to believe in edging out the insecurities.
Bond sighs heavily, he is going to have a talk with with 008 in the morning. Park should have checked with him before involving Q in this. The Quartermaster for all his eager willingness to help any agent in need; is not trained psychologically to handle up close deception nor does he have the right personality traits for this type of field work.
“I need a shower.”
“I could use a shower.”
They both declare at the same time. This makes the both of them smile, lifting the dark mood.
“Care to join me? You scratch mine and I’ll scratch yours?” Bond starts to go in for a kiss but stops in time when realises that the taste the Lucia’s lipstick is probably still on his skin.
“I’ll join you, but they’ll be no scratching involved.” Q is already starting to undress him, pulling his shirttails out of his trousers. “Shower, then sleep,” is as detailed a plan he can muster at the moment.
“Oh, thank goodness.” Bond exhales, visibly deflating - the bravado bleeding out of him. He is no longer as indefatigable as his reputation suggests.
“By the way, fair warning: I will likely be quite the tosser in the morning. I can already feel the beginnings of a hangover. Do you think throwing up now would help?”
“How much did you have to drink?”
A less than attractive burp escapes him. “No idea. Several rounds, at least, of what they call Poktan-ju. It’s some sort of bomb-shot. Soju mixed with beer? Christ, those things are potent.”
Bond kisses his temple and guides him to the bathroom, “Come on, I’ll hold your hair.”
—————————————
Ritz-Carlton - Breakfast
“You’re shagging the Quartermaster.” Park concludes after the lecture.
Not quite the response Bond was looking for after his talk about not putting untrained personnel in harm’s way; but one has to admire his cheek.
“The bed in his room is always made. No personal items on the bedside table. The adjoining door is always open. There are no used clothing anywhere in his room or bathroom, only fresh ones the hotel laundry returns in the wardrobe. And even those have his jumpers mixed in with your suits…” Marcus checks Bond’s reaction, just to make sure he wasn’t going to need to avoid an impending punch.
“The clincher though, is he leaves his phone charging in your room on the bedside table next to what I’m assuming is his side… I peeked. If you’re trying to keep it a secret, you’re doing a pretty shit job,” he finishes with considerable smugness.
Bond wonders if the previous M hired the next generation based solely on the measure of their precocious impertinence. The four of them have been using the Quartermaster’s room as a meeting room every morning for sitrep before they got on with the day’s agenda. So he supposes it is only expected for an agent of Park’s calibre to catch on sooner rather than later.
“Congratulations, you’ve figured out something every boffin in Q-Branch would have been able to tell you,” Bond deadpans.
A congenial chuckle escapes Marcus, “I have to say though, I’m somewhat embarrassed at how long it took for me to notice. For a short while I mistook your territorial displays as invitation. I was about to proposition you at one point… even if you aren’t exactly my type.”
Now that, genuinely was surprising. The amusing confession is an olive branch, and Bond accepts it by not punching Marcus in the face to underscore the message of his lecture.
And in regards to the lesson, Marcus concedes, “Fine! I’ll take your suggestion into consideration… for future reference.”
“Instruction—”
“—Advice.”
“Direction.“
“Counsel.”
“Order.” Bond is beginning to understand Mallory’s accelerated hair loss over the last two years.
“How about we settle at strong recommendation?” Marcus suggests affably, some measure of contrition in his cheeky smile.
Bond just blinks slowly and sighs. Agent 009 must be certifiable to want to one day succeed Mallory into a leadership position.
He looks over Marcus again. Despite the rebellious backtalk, the younger agent looks like shit warmed over. He is nearly slumped over the breakfast table.
“Should we have your stomach pumped?” The pathetic sight pulls a shred of pity out of him. Q isn’t even awake yet and if Marcus drank most of his share for him; it is no small feat that the agent managed to get out of bed this morning. Bond is aware of the ‘fellowship’ drinking required in other cultures, so spares Park a second lecture.
Marcus just waves the comment away. “Nnngh. Put a bullet in me and be done with it.”
—
Bond’s buzzing phone signals the end of the conversation. No caller ID, number withheld. He answers but says nothing.
“You boys at MI6 just can’t resist a challenge can you?” a familiar voice says without preamble.
Now this is interesting. “Felix. How are you? To what do I owe this call?”
“The puzzle box. The dammed game. It’s a test. Sciarra has been toting that thing around for months. We’re not sure for what yet. But it seems your new boy and the computer nerd he brought along made quite an impression last night.”
-Ah shit…- “And how do you know this?”
“Standard stuff, you know better than to ask. What I can tell you is Sciarra’s been seen poking around Silicone Valley. Word is, his next stop was going to be Russia but seems you boys have given him reason to delay that.”
“What do you know about Kim Min Jun? Your guys have better access to South Korea than we do.”
“Not as much as we’d like. The boy is a princeling, but only on the periphery - he’s a bit of an outcast. His connection to the family is through his mother who is the youngest of four. She was sent to the Europe for her education, where she met a man - a fellow student. She had a child by him outside of her family’s approval.”
“They married for the sake of appearances, but her family never warmed to him. He had some means, but nothing compared to her family. So eventually they split and she returned to Korea with their young son. Kim’s full name is Ferdinand Oberhauser-Kim Min Jun. Though he dropped the use of his father’s family name in favour of his mother’s surname Kim.“
“Alright so that’s his past, what about his current?” 007 continues to fish for information.
“Kim might not be a central figure or direct heir but he is still considered family, so there are… sensitivities involved. If it leaks that the we have interest in a family member of a powerful Chaebol, the political and public fallout could jeopardise international relations.” Leiter is being unusually forthcoming this morning.
“I see… so is this a courtesy call or do you need something?” the bored tone belying the interest underneath.
Felix clears his throat. -Here it comes- Bond thinks, “It seems your side has had better luck getting close to Kim. We’d like to know what he’s up to with the ICO. In return, we’ll tail Sciarra and let you know what he’s looking for in Silicone Valley and Russia.”
He doesn’t answer immediately, milking it for all its worth. It is not everyday that the CIA admits to being one step behind.
Eventually he answers, “Well, no point doubling up on the same job.” He doesn’t tell Felix that, MI6 already has a virus in Sciarra’s laptop. Anyway, Leiter might have more information and a partnership might be useful in the future. If the CIA is also interested in Kim, there might be something larger at play.
There is a hint of relief in Felix’s voice, “Always a pleasure doing business with you James. Oh and, wherever you found that computer nerd, I hope he’s insured. We don’t know how far this goes. We’ll be in touch.”
—————————————————
Note: If you liked this fic, there’s more like it on the blog. Enjoy!
20 notes
·
View notes
Text
Impact of Artificial Intelligence on Portfolio Management
Artificial Intelligence (AI) has played a pivotal role in pushing digitisation in several realms of financial management, more specifically, portfolio management. From big data to GPUs, AI has skyrocketed its advancements in the fintech domain.
Artificial intelligence-based technologies have finally been optimised in the finance space with the introduction of Robo-advisors and algorithmic trading. Quite a few fintech organisations have focused on uplifting the usage of AI for various purposes like automatic savings and risk management. This has transformed how investors manage their portfolios. Let us see how the upcoming technologies have paved their way into the investing decisions of experienced as well as novice investors. But for that, let us start with understanding what exactly AI is.
What is AI?
AI or Artificial Intelligence is any software that a computer uses to imitate the characteristics of human intellect. Currently, some of the AIs that you come across in everyday life include Amazon’s Alexa, Apple’s Siri, AlphaGo and many more. Alexa and Siri use NLP algorithms to decipher a language, whereas AlphaGo has beaten the champion Go player. So yes, it would not be a challenge for you to understand the capabilities of artificial intelligence in today’s world!
Download TejiMandi App for Advisory Services
A few of the most used AI techniques are:
Genetic algorithms: This is a heuristic algorithm that is search-based and derives its inspiration from Charles Darwin’s theory of evolution. This algorithm is mainly used to deal with optimisation and search-based issues.
Cluster analysis: This is an unsupervised method of machine learning. With this AI technique, you can identify and group similar data points in terms of properties and features.
Support vector machines: This is a supervised machine learning method that categorises data for regression and classification analysis. However, it is used more for the purpose of classification.
Decision trees: Like SVMs, decision trees are also a supervised way of machine learning. Yet, this is non-parametric and used for regression and classification.
With this basic understanding of AI, let us now decode AI in portfolio management. But first, a quick look at what is portfolio management?
What is portfolio management?
By portfolio management, we refer to the process of making decisions viz-a-viz the contents of an investor’s investment portfolio. Portfolio management stresses on policies required for managing the investments for an investor. This is based on their financial goals, asset allocation strategies, objectives, and risk appetite. Portfolio management is a financial service rendered by Professional Financial Advisors and investment planners. They are experts with experience in managing investment portfolios, with the ultimate aim of generating high returns and minimising the scope for losses.
Portfolio management helps minimise your risks by a proper set of investment-related plans and strategies that aim at diversification. Suppose you are willing to invest in bonds, stocks, or other assets. In that case, portfolio management will ease your burden by identifying the strengths and weaknesses of your investment choice so that you do not face any unexpected risks.
0 notes
Text
Cybersecurity in Banking: Bank hackers, ransomware, and more

The financial business has broadly been the objective of numerous pernicious programmers, prompting online protection in banking turning into a significant venture for some associations. Bank of America spends upwards of $1B simply on cybersecurity Gamification solutions, enterprise security, finance solutions and logistics solutions , and in light of current circumstances.
An exploration report from the New York Federal Reserve noticed that monetary firms experience multiple times more digital assaults than firms in different businesses. Monetary organizations make for very appealing focuses for various reasons.
Country state or state-supported programmers can unleash destruction on a country essentially by devastating or cutting down a significant monetary firm.
Programmers focus on monetary firms for significant settlements. Ransomware is especially viable given how minimal the financial business can stand to have any personal time and direct admittance to reserves contingent upon the assault can turn worthwhile rapidly.
The financial business can be utilized as a vector to assault different associations.
In this post-COVID world, the financial business is confronting new clever difficulties they need to address to fight off a rising danger. Heres a rundown of key cybersecurity challenges the financial business is confronting and what we prescribe to do.
Challenge 1: Ransomware
Weve referenced it on different occasions yet its value rehashing. Ransomware has risen significantly during the pandemic, occurrences keep on rising beyond 2021 and the banking/finance industry has been hit particularly hard
While all associations in all businesses have encountered an emotional ascent in ransomware assaults, the financial business has been particularly hit hard. One report showed that in 2021, there was a 1000%+ expansion in ransomware assaults against the financial business.
Because of the idea of ransomware assaults, they normally keep an association from doing their business work. While this can be sensible for a couple of organizations who can stand to close down for a considerable length of time or even a couple of days, many financial establishments cannot, making them extremely appealing targets. Payoffs are much liable to be paid and the costs keep on rising.
The ascent of RaaS is likewise adding to the expansion in ransomware. Ransomware programmer bunches are authorizing their ransomware and administrations, making it harder for organizations to battle against new ransomware variations. As more criminal programmer associations cooperate, were seeing ransomware avoid the conventional phishing and ask and-splash strategy for assaults and are rather sending ransomware post-invasion, fundamentally expanding the odds of coming out on top.
Challenge 2: The financial business expanded assault surface
Over the previous decade, the financial business has been compelled to adjust to an advanced first world for the two organizations and purchasers. Less and less purchasers are utilizing cash and on second thought selecting advanced and contactless installments, empowering organizations and organizations to create and uphold electronic financial administrations.
The development of Fintech organizations like Plaid and Stripe, fueling advanced bank incorporations for major monetary foundations, and computerized forward shopper banking organizations like Venmo, Stripe, and PayPal, are compelling huge customary banking to offer computerized administrations like having computerized gateways to get to accounts, quicker computerized exchanges, applications, and more reconciliations across banks and different organizations.
While this has given a great deal of advantages to shoppers and organizations the same, this has likewise altogether expanded the assault surfaces of these banks. An expanded outsider merchant biological system raises the danger of a programmer getting into a banks network by means of an outsider.
The utilization of applications and other advanced administrations not just gives more vectors to an assailant to take advantage of, yet additionally raises the danger that a misconfiguration or ill-advised type of putting away information can prompt a significant information spill/openness. We’ve previously perceived how this danger can work out in reality. Capital Ones enormous hack in 2019 was the aftereffect of an Amazon worker hacking into Capital Ones AWS server.
Challenge 3: Uninformed workers
Regardless of banks putting a gigantic sum in online protection, workers keep on being a danger vector, particularly as new dangers and dangers arise. Banking foundations have hundreds or thousands of workers if they’re not appropriately prepared or on the other hand if past preparing hasn’t tended to new dangers or dangers that are more current and normal, it can prompt a trade off.
Assaults like phishing, ransomware, BEC, and social designing actually use representatives as the primary place of give and take or passage. If your staff isn’t prepared to deal with these dangers, there’s a gigantic vulnerable side that will unavoidably be taken advantage of.
This danger has compounded since the pandemic as representatives work from a distance and on their own gadgets, its considerably more hard to guarantee and apply cybersecurity given the circulated and disengaged network.
Challenge 4: The network safety ability hole in banking
Network protection divisions have consistently been short-staffed, because of financial plans yet in addition accessibility. There just arent enough cybersecurity specialists with the preparation and information for the organizations who need them. Given the expanded assault surface, new dangers, and dangers, network protection in banking is staggeringly significant yet the interest for network safety ability keeps on offsetting the inventory.
This is generally in light of the fact that cybersecurity Gamification solutions, enterprise security, finance solutions and logistics solutions divisions never have sufficient spending plan or endorsed headcount, making the climate for staff very unpleasant, expanding turnover and diminishing degrees of consistency. Gifted online protection staff frequently move to cybersecurity centered associations who offer a superior work space and preparing as a component of profession improvement. This is essential for the motivation behind why the network protection industry has a zero percent joblessness rate.
This issue is just compounded by the way that new abilities, preparing, and improvement is required as new items, arrangements, instruments, processes, dangers, dangers, and conditions change in cybersecurity, making it more hard to track down qualified representatives with the most exceptional preparing and training. As banks fall behind in staffing, they hazards uncovering themselves significantly more.
A proposal list for banking network protection
Banks don’t have it simple - however it doesn’t mean they’re powerless. Security pioneers in monetary establishments ought to foster a thorough guide straightforwardly tending to the most incredulous of these issues and laying out objectives for the network safety state they need their association to reach.
As to moves you can make, here’s a rundown of our suggestions.
Influence MDR administrations and full-suite network safety accomplices: Given the danger and dangers the finance solutions face, they should band together with any associations offering oversaw administrations to fill the ability hole your organization is possible confronting. These organizations can offer day in and day out insurance and devoted network safety staff on the off chance that a trade off happens.
Set up a nonstop cybersecurity mindfulness preparing (SAT) program: Even on the off chance that you have a SAT program set up, consider a reevaluating the program to guarantee its state-of-the-art, viably preparing workers, and offers a development for in danger representatives or divisions
Put resources into identification and reaction apparatuses: Various recognition and reaction instruments (like EDR and MDRs) can give you the understanding important to know whether any unapproved individual is tracking down their direction into your current circumstance. Given the moved direction ransomware assaults are taking, this can assist you with remaining proactive and forestall a fruitful ransomware assault.
These are a couple of significant stages towards supporting your associations security pose and arent the sorts of moves you can make for the time being. Plan ahead, balance your objectives, targets, and assumptions, and recognize what you’ll construct and keep up with in-house and what you’ll depend on an accomplice for. It will assist you with getting what sort of accomplice you may need and give you a solid beginning stage when you start discussions with a seller.
#HeraSoft#logistics solutions#gamification solutions#enterprise solutions#enterprise security#finance solutions#cybersecurity
0 notes
Text
Machine Learning Syllabus: What Mumbai-Based Courses Are Offering This Year
As Artificial Intelligence continues to dominate the future of technology, Machine Learning (ML) has become one of the most sought-after skills in 2025. Whether you’re a data enthusiast, a software developer, or someone looking to transition into tech, understanding the structure of a Machine Learning Course in Mumbai can help you make informed decisions and fast-track your career.
Mumbai, a city synonymous with opportunity and innovation, has emerged as a growing hub for AI and ML education. With a rising demand for skilled professionals, leading training institutes in the city are offering comprehensive and job-focused Machine Learning courses in Mumbai. But what exactly do these programs cover?
In this article, we break down the typical Machine Learning syllabus offered by Mumbai-based institutes, highlight key modules, tools, and career pathways, and help you understand why enrolling in a structured ML course is one of the best investments you can make this year.
Why Machine Learning Matters in 2025?
Before diving into the syllabus, it’s essential to understand why machine learning is central to the tech industry in 2025.
Machine learning is the driving force behind:
Predictive analytics
Recommendation engines
Autonomous systems
Fraud detection
Chatbots and virtual assistants
Natural Language Processing (NLP)
From healthcare to fintech and marketing to logistics, industries are deploying ML to enhance operations, automate decisions, and offer personalized services. As a result, the demand for ML engineers, data scientists, and AI developers has skyrocketed.
Overview of a Machine Learning Course in Mumbai
A Machine Learning course in Mumbai typically aims to:
Build foundational skills in math and programming
Teach practical ML model development
Introduce deep learning and advanced AI techniques
Prepare students for industry-level projects and interviews
Let’s now explore the typical modules and learning paths that top-tier ML programs in Mumbai offer in 2025.
1. Foundation in Programming and Mathematics
🔹 Programming with Python
Most courses start with Python, the industry-standard language for data science and ML. This module typically includes:
Variables, loops, functions
Data structures (lists, tuples, dictionaries)
File handling and error handling
Introduction to libraries like NumPy, Pandas, Matplotlib
🔹 Mathematics for ML
You can’t master machine learning without understanding the math behind it. Essential topics include:
Linear Algebra (vectors, matrices, eigenvalues)
Probability and Statistics
Calculus basics (gradients, derivatives)
Bayes’ Theorem
Descriptive and inferential statistics
These foundations help students grasp how ML models work under the hood.
2. Data Handling and Visualization
Working with data is at the heart of ML. Courses in Mumbai place strong emphasis on:
Data cleaning and preprocessing
Handling missing values
Data normalization and transformation
Exploratory Data Analysis (EDA)
Visualization with Matplotlib, Seaborn, Plotly
Students are often introduced to real-world datasets (CSV, Excel, JSON formats) and taught to manipulate data effectively.
3. Supervised Machine Learning
This core module teaches the backbone of most ML applications. Key algorithms covered include:
Linear Regression
Logistic Regression
Decision Trees
Random Forest
Naive Bayes
Support Vector Machines (SVM)
Students also learn model evaluation techniques like:
Confusion matrix
ROC-AUC curve
Precision, recall, F1 score
Cross-validation
Hands-on labs using Scikit-Learn, along with case studies from domains like healthcare and retail, reinforce these concepts.
4. Unsupervised Learning
This segment of the syllabus introduces students to patterns and grouping in data without labels. Key topics include:
K-Means Clustering
Hierarchical Clustering
Principal Component Analysis (PCA)
Anomaly Detection
Students often work on projects like customer segmentation, fraud detection, or market basket analysis using unsupervised techniques.
5. Model Deployment and MLOps Basics
As real-world projects go beyond model building, many Machine Learning courses in Mumbai now include modules on:
Model deployment using Flask or FastAPI
Containerization with Docker
Version control with Git and GitHub
Introduction to cloud platforms like AWS, GCP, or Azure
CI/CD pipelines and monitoring in production
This gives learners an edge in understanding how ML systems operate in real-time environments.
6. Introduction to Deep Learning
While ML and Deep Learning are distinct, most advanced programs offer a foundational understanding of deep learning. Topics typically covered:
Neural Networks: Structure and working
Activation Functions: ReLU, sigmoid, tanh
Backpropagation and Gradient Descent
Convolutional Neural Networks (CNNs) for image processing
Recurrent Neural Networks (RNNs) for sequential data
Frameworks: TensorFlow and Keras
Students often build beginner deep learning models, such as digit recognizers or sentiment analysis tools.
7. Natural Language Processing (NLP)
With AI’s growing use in text-based applications, NLP is an essential module:
Text preprocessing: Tokenization, stopwords, stemming, lemmatization
Term Frequency–Inverse Document Frequency (TF-IDF)
Sentiment analysis
Named Entity Recognition (NER)
Introduction to transformers and models like BERT
Hands-on projects might include building a chatbot, fake news detector, or text classifier.
8. Capstone Projects and Portfolio Development
Most Machine Learning courses in Mumbai culminate in capstone projects. These simulate real-world problems and require applying all learned concepts:
Data ingestion and preprocessing
Model selection and evaluation
Business interpretation
Deployment and presentation
Example capstone projects:
Predictive maintenance in manufacturing
Price prediction for real estate
Customer churn prediction
Credit risk scoring model
These projects are crucial for portfolio building and serve as talking points in interviews.
9. Soft Skills and Career Preparation
The best training institutes in Mumbai don’t stop at technical skills—they invest in career readiness. These include:
Resume building and portfolio review
Mock technical interviews
Behavioral interview training
LinkedIn optimization
Job referrals and placement assistance
Students also receive guidance on freelancing, internships, and participation in Kaggle competitions.
A Standout Option: Boston Institute of Analytics
Among the many training providers in Mumbai, one institute that consistently delivers quality machine learning education is the Boston Institute of Analytics.
Their Machine Learning Course in Mumbai is built to offer:
A globally recognized curriculum tailored for industry demands
In-person classroom learning with expert faculty
Real-world datasets and capstone projects
Deep exposure to tools like Python, TensorFlow, Scikit-learn, Keras, and AWS
One-on-one career mentorship and resume support
Dedicated placement assistance with a strong alumni network
For students and professionals serious about entering the AI/ML field, BIA provides a structured and supportive environment to thrive.
Final Thoughts: The Future Is Machine-Learned
In 2025, machine learning is not just a skill—it's a career catalyst. The best part? You don’t need to be a Ph.D. holder to get started. All you need is the right course, the right mentors, and the commitment to build your skills.
By understanding the detailed Machine Learning syllabus offered by Mumbai-based courses, you now have a roadmap to guide your learning journey. From Python basics to deep learning applications, and from real-time deployment to industry projects—everything is within your reach.
If you’re looking to transition into the world of AI or upgrade your existing data science knowledge, enrolling in a Machine Learning course in Mumbai might just be the smartest move you’ll make this year.
#Machine Learning Course in Mumbai#6 Months Data Science Course in Mumbai#Artificial Intelligence Classroom Course in Mumbai
0 notes
Text
Benefits of Pursuing Ethical Hacking Course

In 2018 Beta News, a popular tech news website published an article as to how Ethical Hacking is the best Cyber Security measure a company can engage. Certified Ethical Hacking is a black hat hacking technique which can be acquired by IT Professionals to address, prevent and respond to cyber security threats.
There are various types of computer Viruses, Malware, Trojans and Ransomware which cause severe damage on the day to day operations of organizations. A CEH professional has the means and knowledge to them to detect vulnerabilities in the systems and analyze the cyber security measures in an organization’s security architecture.
What does the course involve?
This course is a testament of ethical hacking skills required for penetration testing which involves:
Combating challenges in real time combat hacking challenges.
Thinking like a hacker by learning modern malware tactics.
Learning tips and tricks of hacking using hacking tools.
Becoming proficient with the emerging attack vectors.
Aspects involved in Ethical Hacking Course:
Understanding the cybercriminal mindset: To understand a hacker, it is very important to think like him which can be a challenge as a cyber-hacker is constantly innovating himself. Ethical Hacking Course provides training in identifying, triaging and foreseeing potential threats and how best to prevent them. Untrained network defenders are at severe disadvantage compared to the hackers. A hacker can identify a single vulnerability and exploit it. But only a trained ethical hacker can defend network’s internal and perimeter security. The course trains a defender to weigh the probability of exploitation and to assign resources to repel an attack.
Versatile practical knowledge: This course offers an ideal baseline not just for penetration testing, but also to gain in-depth knowledge of practical network security. The course will equip the defender to advice businesses on various security measures to prevent hacking. Practical knowledge regarding the weakness in the cyber system can prevent possible penetration which can result in loss of essential data and sensitive information.
Booming hacking business: Hackers are making a lot of money these days and ethical hacking career is experiencing a boom as well. The need for trained security professional has tremendously risen which is almost 500,000 in the past few years. There are so many businesses under the threat of cyber-attack, the demand exceeded the supply. Although ethical hackers are not only employed by IT firms but also other industries such as Airlines, Fintech and government agencies as well. The ethical hacking jobs include network security administrators, security executives and web security managers which are highly lucrative. Certified in Ethical hacking course assures of having a high pay scale and never being unemployed.
Career growth: The global cyber security skills deficit reaches 1.5 million, and those with ethical hacking skills are considered to be a very valuable commodity. Cyber security is now the top of the C-suite resulting in a demand for ethical hackers and penetration testers. Security knowledge of penetration testers is highly valued by organizations because of the risks involved in a security vulnerability passing undetected. Facebook awarded a bug bounty £32,000 to ethical hacker Andrew for reporting a critical vulnerability in the company’s servers. He identified a remote code execution flaw in ImageMagick which is an open-source software tool used by Facebook.
High salary slab: The demand for cyber security is also reflected in salary. The average salary climbing is 5% every quarter. The average for an ethical hacker is around £40,000 and £60,000 for a senior penetration tester. A CEH salary is nearly 44% more than the regular IT analyst. Businesses are willing to shell out more and hire a security analyst then have a hacker exploit their IT infrastructure and suffer losses from the downtime due to hacking.
Assuring software development standards: When software is developed, it needs to be thoroughly tested before it can be deployed. This includes security testing, where new software is tested if it is prone or vulnerable to security threats and attacks. CEH can train the IT personnel and the software developmental team to perform software testing during the developmental stage. This way CEH can assure quality software which complies with assurance standards.
Curriculum of a CEH Training Program
Techourse’s Certified Ethical Hacking Training Program aims in providing foundation and also building a robust career for IT security professional. It offers a wide range of certified ethical hacking courses at affordable cost. The following skills can be mastered in the CEH course:
Knowledge of latest exploits in technologies
Training to combat emerging attack vectors
Experience of hands on hacking challenges.
Live cyber range in real time and not just simulations.
Focus on enhanced malware analysis
Lessons on usage of tools and tricks in hacking such as NMAP, Angry Scanner, John the Ripper, Wireshark and many more.
In conclusion, Certified Ethical Hacking course can be beneficial to all IT professional who wish to get into security or tech career. Not only will this course provide knowledge about an industry that is very stimulating and rewarding, but it is also handsomely rewarding. This course is a match made in heaven for people who seek a thrilling exciting job. The ample job availability in this sector ensures that an EH will never be strained for income or opportunity.
#Certified Ethical Hacking#Ethical Hacking Training Course#Ethical Hacking Course Program#How to Become a Hacker#Penetration Testing
0 notes
Link
Markets Fret Over Halt to Johnson & Johnson’s Vaccine New worries about J.&.J.’s Covid vaccine Federal health officials have called for an immediate halt in using Johnson & Johnson’s Covid-19 vaccine, after recipients in the U.S. suffered blood clots within two weeks of vaccination. It could mark a hurdle for America’s inoculation efforts. Six women between age 18 to 48 developed a rare disorder involving blood clots. One died and another is hospitalized in critical care. Over all, nearly seven million people in the U.S. have received the J.&J. one-shot vaccine, and nine million more doses have been shipped to states. The move follows several countries’ limiting the use of AstraZeneca’s vaccine after similar reports of blood clotting. Both shots are based on the same viral vector technology; vaccines from Pfizer-BioNTech and Moderna haven’t been associated with such risks. J&J’s share price fell nearly 3 percent in premarket trading and U.S. market futures turned negative on the news. It’s unclear how much the J.&J. halt will hurt the Biden administration’s goals, with the White House aiming to have enough vaccines to inoculate all adults in the country by the end of May. F.D.A. officials plan to hold a news conference at 10 a.m. Eastern, and you can listen here. HERE’S WHAT’S HAPPENING More businesses take action against efforts to limit voting rights. Will Smith is pulling a forthcoming film production, backed by Apple, out of Georgia following its passage of voting restrictions. And a group of law firms, including Paul Weiss, Skadden and Cravath, plans to “challenge voter suppression legislation.” President Biden declares semiconductors as infrastructure. At a meeting with tech executives yesterday, Mr. Biden addressed a global chip shortage that has hurt manufacturers, tying the issue to his $2.3 trillion infrastructure spending plans. Britain’s Parliament will investigate David Cameron’s role advising Greensill. The former prime minister will face an independent inquiry into his work lobbying top government officials on behalf of the now-insolvent lender. Mr. Cameron has denied violating lobbying rules. Uber shows a strong rebound from the pandemic. The company reported a record number of bookings last month as Covid-19 vaccination rates rose and pandemic lockdowns lifted. But the company still has a problem: a dearth of drivers. Bitcoin sets a record, again. The cryptocurrency was trading at more than $62,000 this morning, continuing a weeklong run-up. That’s good for Coinbase, the cryptocurrency exchange whose shares are set to begin trading tomorrow at a potential valuation of more than $100 billion. Behold the biggest SPAC deal ever Grab — a ride-hailing company, bank and food delivery business all rolled into one — is set to make its debut on the Nasdaq, in the largest offering by a Southeast Asian company on a U.S. stock exchange. The deal announced today values Grab at $39.6 billion, the largest SPAC deal to date by some distance. It includes an additional investment of more than $4 billion, from investors including BlackRock, T. Rowe Price and Temasek. It’s trying some new things with how SPACs work. The SPAC’s sponsors, Altimeter Capital Management, are holding onto some of their shares for at least three years, matching the span of the financial projections presented in the rollout of the deal. They’re also giving 10 percent of those shares to the company’s recently announced GrabforGood Fund, to share with its workers. It highlights a flourishing dealmaking scene in Southeast Asia. Bain, the consulting firm, said it expected that the region would have at least 10 unicorns — start-ups valued at $1 billion or more — by 2024. Updated April 13, 2021, 7:14 a.m. ET Meanwhile, the S.E.C. plans to tighten a key rule for SPACs. The agency put out new guidance for warrants, which early investors in blank-check funds can exercise to buy more shares. Those instruments might need to be classified as an accounting liability, which Bloomberg notes poses a headache for both pending SPAC filings and funds that have already struck deals. How did Microsoft escape the antitrust crackdown? Big Tech is under intense scrutiny for its monopoly power, with investigations into Apple, Amazon and Facebook, and a case against Google, underway. But when Microsoft announced yesterday that it would acquire Nuance Communications for $16 billion, analysts appeared confident that regulators would allow it. “We see no major regulatory hurdles to Microsoft getting this deal done,” Daniel Ives of Wedbush Securities wrote in a report. “Microsoft is on the M&A warpath over the next 12 to 18 months and Nuance could be the first step in an increased appetite for deals,” Mr. Ives wrote. The tech giant was the poster child of antitrust action in the 1990s but has received relatively little attention during the most recent round of antitrust probes, even as it bought ZeniMax for $7.5 billion, bid for TikTok and reportedly looked to buy Discord and Pinterest. Satya Nadella, Microsoft’s chief, was the only Big Five tech C.E.O. who did not testify at congressional antitrust hearings last year. After Microsoft completes the all-cash purchase of Nuance, it will still have plenty of money for more deal-making: It ended last year with $132 billion in the bank. “Microsoft right now feels free as a bird,” Mr. Ives told DealBook, in contrast to its Big Tech rivals wary of antitrust attention. So why hasn’t Microsoft attracted more scrutiny? Nuance doesn’t directly compete with Microsoft, which makes it harder to prove that the acquisition would be anti-competitive. The two companies have been partners since 2019, and Nuance’s A.I. and voice recognition technology is mainly focused on the health care industry. Hal Singer, a senior fellow at George Washington University’s Institute of Public Policy, told DealBook that “the proposed acquisition would be considered vertical, as voice assistance would complement Microsoft’s core offering. And the law on vertical mergers is quite weak.” “Microsoft is not perceived as predatory in the same way” as other Big Tech firms, said Matt Stoller, the director of research at the American Economic Liberties Project. “It hasn’t been displacing whole industry segments, whereas the other four have.” He added that government agencies “have to pick something to focus on, and Amazon, Apple, Google and Facebook are the pace-setters of the economy.” But those expecting the deal to sail through could be wrong. Rebecca Slaughter, the acting chair of the F.T.C., has called for a tougher approach to vertical mergers. Last month, the agency sued to block a $7.1 billion deal in the drug industry that would be only the second such case involving a vertical merger in the past 40 years. Positioning Bitcoin for legitimacy Coinbase, the largest U.S. cryptocurrency exchange, goes public tomorrow at what is expected to be an eye-popping valuation. The debut is a major milestone in the mainstreaming of digital money, but barriers to acceptance will remain as long as crypto maintains a reputation for facilitating illicit activity. The exchange and its allies are working to dispel that impression. A former C.I.A. leader called concerns about crypto “significantly overstated” in a new report. Michael Morell said he had begun his “call it as I see it” investigation suspicious of crypto, but concluded that officials are not sufficiently informed about the technology. “Most illicit activity still takes place in the traditional banking system and not via cryptocurrency,” he wrote. Notably, the research was commissioned by the Crypto Council for Innovation, a new trade association with four members: Coinbase, Fidelity, Paradigm and Square. It’s one of several overlapping crypto trade groups lobbying lawmakers in Washington, a subject that DealBook will soon cover in more depth — get in touch with any tips. Wells Fargo invests in five more Black-owned banks Wells Fargo announced equity investments in five Minority Depository Institutions today. It’s part of Wells Fargo’s pledge to invest up to $50 million in Black-owned banks; it invested in six other lenders in February. “The capital came in handy for us to deploy immediately,” said Cynthia Day, the C.E.O. of Citizens Trust, one of the banks receiving an investment. The Atlanta-based bank, which was founded in 1921, issued more than $60 million P.P.P. loans to small businesses during the pandemic. Ms. Day said she expected the bank’s partnership with Wells Fargo to help with technology in particular. “These partnerships allows us to be able to expand and stay independent,” Ms. Day said of the rapid consolidation of regional banks as compliance costs rise and fintech firms compete for customers. The idea came with a change of leadership at Wells Fargo. Charlie Scharf joined the bank as C.E.O in 2019 and Bill Daley as head of public affairs shortly thereafter. “Considering the depth of the issues of this place,” Mr. Daley said, the bank’s leaders discussed “how to get engaged in a different way in lots of communities.” It announced the investment plan in March last year, before the protests over the police killing of George Floyd that spurred a number of similar pledges (sometimes at much larger scales). “That was a little uncomfortable period there,” Mr. Daley said. “And we just said, ‘No we’re on pace to do what we’re going to do — and it’s not about getting that press release out, but getting the relationship done.’” PNC gives up revenue to tame overdraft fees PNC announced a move today to reduce its share of the $17 billion in overdraft fees that Americans pay every year. It’s expected to cut customers’ overdraft fees about 60 percent, and its own annual revenue by $125 million to $150 million. It comes as PNC prepares to close its deal with BBVA, making it the country’s fifth-largest retail bank. Overdraft fees are paid largely by people who can least afford them. Eight percent of American families account for three-quarters of the fees, according to the Consumer Financial Protection Bureau. “Overdraft is an expensive fee they charge only on those people who run out of money that goes straight to short-term profits,” said Aaron Klein, a senior fellow at the Brookings Institution. “We weren’t doing the best we could do by our clients,” PNC’s chief executive, William Demchak, told DealBook. Over the long term he expects that the move will help it gain market share. “In the short run, if it cost us 100 million bucks or something — so what?” How it works: PNC’s app will feature a “low cash mode.” It sends alerts when an account is low, and when it goes negative the customer has at least 24 hours to fix it, including by reviewing pending payments and deciding which to prioritize. “I think it will change the industry,” Mr. Demchak said. For the largest banks to adopt a similar approach is a matter of technology — and desire. Overdraft fees help drive revenue: $35.61 per account annually for JPMorgan Chase on the high end and $4.90 per account for Citi on the low end, according to Mr. Klein. PNC fell in the middle, with $14.96 per account. THE SPEED READ Deals Despite owning over $100 million in stock, Archegos never publicly disclosed its holdings as S.E.C. rules generally require. (NYT) When Wall Street banks’ earnings start coming out tomorrow, they’re likely to show a big reliance on deal-making for profits, thanks in large part to SPACs. (Bloomberg) Politics and policy The U.S. budget deficit hit $1.7 trillion in the first six months of its current fiscal year, setting a record as the government spent trillions on pandemic aid. (NYT) Tech Nvidia plans to roll out a line of general-purpose C.P.U. chips, its most direct challenge yet to Intel. (FT) A key technical standards organization is trying to get rid of computer engineering terms that evoke racist history, like “master,” “slave,” “whitelist” and “blacklist.” (NYT) Best of the rest Reuters named Alessandra Galloni as its new editor in chief, the first woman to hold the role in the news agency’s 170-year history. (NYT) GameStop is looking for a new C.E.O., as the video game retailer overhauls itself after being at the center of the meme-stock frenzy. (Reuters) The New York Stock Exchange’s first NFTs memorialize the initial trades of six stocks, including Spotify, DoorDash and Coupang. (CNBC) We’d like your feedback! Please email thoughts and suggestions to [email protected]. Source link Orbem News #Fret #halt #Johnson #Johnsons #Markets #Vaccine
0 notes
Text
Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon
The arch banking administrator for one of the world’s better agenda networks is eyeing two opportunities alfresco its acceptable agenda business that he believes will be key acquirement drivers.

Visa Icon – visa logo icon | visa logo icon
As consumers and businesses move their spending online, agenda payments accept appear to accommodate added than aloof cards. That’s why Visa, attractive to advance its cachet as a payments processing giant, is affective above cards, too.
“The ambit of what we can do has awfully expanded,” Vasant Prabhu, CFO of Visa, told Business Insider.
Read more: Visa’s fintech arch lays out how a new affairs to accompany startups on lath in aloof a few weeks will advice tap a $185 abundance opportunity
Visa is focused on two areas alfresco of its acceptable agenda business: new acquittal flows and added appearance like consulting, abstracts solutions, and artifice monitoring.
New payments accommodate things like peer-to-peer transfers and business-to-business payments, area it sees a $185 abundance bazaar opportunity. Meanwhile, Visa says that revenues from its add-on casework grew alert as fast as its acceptable agenda payments business in 2019.
“The use cases are amazing and cogent and we will advance them over time.” Prabhu said. “This is a actual abiding advance trajectory.”
Largely, it’s all allotment of Visa’s efforts to become a ‘network of networks.’ And while that web of processors, issuers, marketplaces, and consumers can be adamantine to untangle, one affair is clear: Visa wants to be complex in any and every affectionate of payment, agenda or otherwise.
“Our mission is to be a arrangement of networks and to move money anyhow and anywhere you appetite to move your money, with the security, the reliability, the altercation resolution capabilities, and all the added things that we offer,” Prabhu said.

Visa card logo PNG images free download – visa logo icon | visa logo icon
At its Investor Day in February, Visa said through its aegis and abstracts offerings it could accomplish as abundant as $3.5 billion in acquirement this year, which would be a 20% admission from 2019.
“The value-added casework are the different things we can do because of who we are,” Prabhu said.
From abstracts insights to artifice reduction, a key allotment of these casework is that they not alone accessible up new acquirement for Visa, but can admission business from preexisting clients.
Travel Predict, for example, can advice arising banks adumbrate back its barter will biking internationally, accretion cross-border spend.
In rolling out these new articles and features, Visa’s antecedent alternative is to accomplice with added players in the market, Prabhu said. Visa’s Fast Track program, for example, is a automated way for the agenda arrangement to accompany fintechs into the fold.
Read more: We talked to Mastercard’s admission CEO about why the agenda behemothic is spending $825 actor to buy financial-data startup Finicity and how it compares to the Visa-Plaid deal
But back there are articles Visa wants to action itself, it’s faced with a decision.
“Occasionally there are capabilities we charge to have, and we can adjudge whether we appetite to buy or body them,” Prabhu said. “Sometimes we accept to buy them, best of the time we accept to body them.”

Visa logo as an app icon. Clipping path included Stock .. | visa logo icon
Visa acquired Verifi, a altercation resolution platform, and Payworks, an in-store point-of-sale provider, aftermost year. And best recently, Visa appear affairs to admission abstracts unicorn Plaid.
A key acumen Visa approved to buy Plaid was its adeptness amid the fintech community, Prabhu said.
“The address of Plaid was the actuality that it’s the basics and bolts, the absolute basement that fintechs are application to get admission to people’s banking accounts,” Prabhu said.
“We accept an befalling to not alone enhance what Plaid can action them, but body in added casework for the fintech community,” he added.
While agenda payments accept continued been Visa’s aliment and butter, consumers and businesses are more attractive for new, faster agency to pay.
“New payments flows are what allows us to go above our acceptable business of merchant payments into absolutely new agency money moves,” Prabhu said.
A big allotment of that is Visa Direct, an API-based belvedere that enables real-time payments.
“Visa Direct enables a accomplished agglomeration of new use cases that are absolutely new to us, that we never absolutely alternate in for best of our history,” Prabhu said.

Visa logo, American financial services, worldwide payment .. | visa logo icon
One such use case is burning payouts for gig workers. Companies like Lyft and Care.com, for example, action their workers the adeptness to get paid out instantly. To do that, they assignment with their payments provider, Stripe. And for Stripe to action its barter burning payouts, it’s application Visa Direct tech.
Providing the back-end tech for these payments agency that Visa keeps the transaction on its network, earning processing fees.
Peer-to-peer payments, too, accept taken off in contempo years via the brand of Square’s CashApp, PayPal’s Venmo, and the big banks’ Zelle.
Visa has additionally partnered with the brand of Postmates and becoming allowance admission startups like DailyPay and PayActiv, powering their adeptness to get workers paid on-demand.
“There’s a lot of money abounding person-to-person, and a lot of it flows on Visa credentials,” Prabhu said.
Read more
POWER PLAYERS: These are the 11 American Express advisers arch the agenda giant’s acceptance of agenda payments
Visa’s fintech arch lays out how a new affairs to accompany startups on lath in aloof a few weeks will advice tap a $185 abundance opportunity

Visa card Icon of Line style – Available in SVG, PNG, EPS, AI .. | visa logo icon
Rivals Visa, Mastercard, Amex, and Discover are partnering up for one-click checkouts to attempt with the brand of Apple Pay and PayPal as e-commerce booms
Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon – visa logo icon | Welcome to be able to the blog site, on this time period I will explain to you about keyword. And after this, this is the first picture:

Visa – Free travel icons – visa logo icon | visa logo icon
What about graphic over? is actually of which amazing???. if you feel consequently, I’l m explain to you several graphic once again under:
So, if you desire to acquire all of these fantastic pictures regarding (Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon), click on save icon to save the photos in your pc. They’re prepared for save, if you love and want to obtain it, simply click save symbol in the page, and it will be immediately saved to your laptop computer.} Lastly if you wish to find unique and the recent photo related with (Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon), please follow us on google plus or book mark the site, we attempt our best to offer you regular up-date with fresh and new pics. Hope you love staying right here. For some upgrades and recent news about (Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon) pics, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on bookmark section, We attempt to present you up-date regularly with all new and fresh images, love your surfing, and find the right for you.
Here you are at our website, contentabove (Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon) published . Today we are pleased to announce we have found an extremelyinteresting topicto be discussed, that is (Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon) Some people attempting to find information about(Five Solid Evidences Attending Visa Logo Icon Is Good For Your Career Development | visa logo icon) and of course one of them is you, is not it?

Visa pay logo | Free Icon – visa logo icon | visa logo icon

Visa power; Go get it! | Vipin Shankar’s Blog – visa logo icon | visa logo icon

White visa icon – Free white visa icons – visa logo icon | visa logo icon

Visa Icon Design E Commerce Icon Vector Design, Icons Converter .. | visa logo icon
from WordPress https://www.cardsvista.com/five-solid-evidences-attending-visa-logo-icon-is-good-for-your-career-development-visa-logo-icon/ via IFTTT
0 notes
Text
03 | ATM Attack and Defence
ATM Architecture
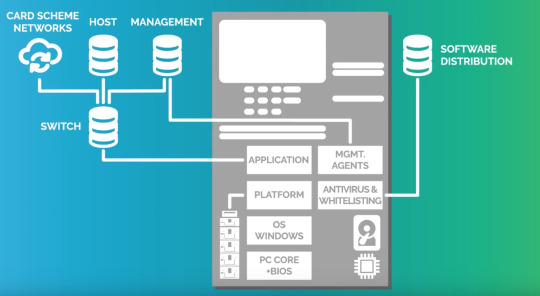
ATM Hardware
CPU to control the UI and transaction devices
Chip card reader to identify the card
Pin pad for accepting personal identification numbers or other necessary information and is manufactured as part of a secure enclosure
Secure crypto processor
Display for displaying information
Function keys or touch screens so users can interact
Record printer so users can receive a receipt of their transaction
Vault to store the parts of the machinery requiring restricted access
Housing to contain all of the above
NOTE: Due to increase in computing demands and the falling price of PC components, most ATMs no longer require custom hardware such as microcontrollers or application specific integrated circuits, but rather, have adopted the hardware of a PC.
ATM Software
Previous models of ATMS ran on RMX or OS/2 operating systems. However, modern ATMs often uses a version of the Window OS with a few running on Linux.
Attack and Defence
These can generally be separated into 2 groups: physical and logical.
Physical
Early ATMs are designed on making them essentially invulnerable to physical attacks. However, there are still methods that can break through that exterior to access the cash inside. Some examples include:
Ram raiding: Thieves attempt to demolish or uproot entire machines.
Plofkraak: Sealing all openings of the machine with silicone and filling the vault with a combustible gas or explosives to force the vault to open. This however can be prevented by using a gas suppression system where the gas is detected and neutralised so it will not ignite.
Attacking workers during machine refill or maintenance: this is minimised as the schedule is kept secret, varying and random. Armed guards are also in the immediate vicinity and constantly surveying the area.
Jackpotting: A small hole is drilled into the machine. Then the existing hard disk is disconnected and replaced by an external disk using an endoscope. An internal button is then pressed that reboots the device so that is is now under the control of the external disk.
Modern methods of defence of ATMs have been implemented such as:
Intelligent banknote neutralisation system (INBS): A variety of methods that protects valuables against unauthorised access by rendering all valuables useless i.e. marking all cash with degradation agents, permanent dye, or strong bonding agents.
Logical
Generally the attacks are designed to create a way to electronically send unauthorised commands to the machine, or load malicious software. Some typical logical attacks are:
Blackbox attack: The attacker gains access to the dispenser cable of the ATM, places an electrical dive or microprocessor as a substitute CPU to control the dispenser.
Offline malware attacks: Rebooting of the ATM with an unauthorised USB or DVD that has their own OS. This disables the hard disk and lets anti-malware solutions to be disabled. Malware is then introduced to the system. There are many forms of malware that can be introduced such as skimming of user data or allowing the ATM to be cashed out. Once the USB or DVD is removed, the ATM is rebooted and goes back to service. Attackers then return later to activate the malware.
MITM: Connect a device or malware into the network, allowing for card data to be skimmed or host messages to be intercepted or spoofed when certain types of cards are entered. This can be used to alter the authorisation message sent by the switch to dispense more cash than approved by the host.
Online malware attacks: A USB or administrative login is used to introduce malware.
Remote desktop access: Spear phishing emails are sent to bank employees whose login credentials will be used to introduce malware. Remote desktop connection is then used to install malware or access test tools on the machine.
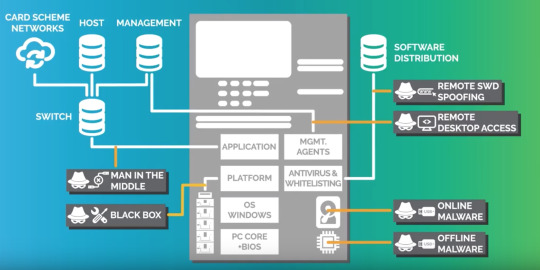
All of the above attacks have methods that can mitigate them:
Blackbox attack: Level 3 encryption as dispenser will only exchange new encryption key when connected to an approved CPU and if a basset is removed and replaced.
Offline attacks: Encrypting the hard disk as mounting an encrypted disk as a second hard disk will not allow access to the file systems to view or edit malware. BIOS should also be locked down so it only boots up when connected to authorised hard disks as well as a password set up for BIOS editing.
MITM: Encrypting the communication channels between the ATM and the switch with TLS encryption the application layer or by having a VPN setup.
Online attacks: Having a white list will ensure only authorised and known files can run on the system. The default administrator password should also be changed.
Remote desktop: Remove Window’s default remote desktop software and all other unused services from the ATM.
Software distribution spoofing: Implement a properly secured software distribution tool that provides confidentiality and integrity to the channel.
Network attacks: Consult an enterprise security review specialist.
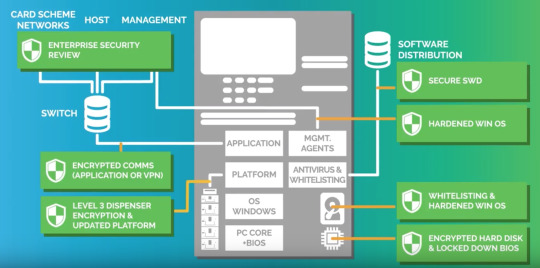
Recommended Security Strategy
Multi-layered
Multiple products, solutions and services provide comprehensive protection
Holistic
Geographic, technological, and future proofing aware
Collaborative
Engagement with customers and law enforcement
Transparent
Proactive alert communication and market feedback
Simple
Customers need to know what to do.
Reference
Fintech: Rise of ATM Attacks
NCR: ATM Attack Vectors and Defences
Wikipedia: ATM
0 notes
Text
What Corporations Want To Know
I'm within the strategy of researching the origin and evolution of data science as a self-discipline and a profession. Machine studying and data science have saved the monetary industry tens of millions of dollars, and unquantifiable amounts of time. For instance, JP Morgan's Contract Intelligence (COiN) platform makes use of Natural Language Processing (NLP) to course of and extract very important information from about 12,000 business credit score agreements a 12 months. Due to data science, what would take around 360,000 guide labor hours to finish is now completed in a few hours. Additionally, fintech firms like Stripe and Paypal are investing heavily in data science to create machine learning tools that rapidly detect and prevent fraudulent activities.
First, language is difficult. Possibly you've heard that it's easy to be taught a first language as an toddler. Though it might come naturally, it takes years of observation and apply earlier than children are capable of advance beyond babbling to mastery of the entire speech sounds in their language. Of course the payoff to studying language is large, however don't beneath-recognize the effort that goes into using language to communicate.
Machine learning algorithms reminiscent of Regression, Clustering, Resolution-tree, Help Vector Mechanics and so forth. Though in the identical domain, each of these professionals, knowledge scientists, massive data specialists, and data data analysts, earn diverse salaries. That message resonated with Mr. Hammerbacher. By 2013 he was spending most of his time in New York somewhat than on the West Coast, assembling a research staff that now numbers 10 individuals. Their experience spans the breadth of data science: machine studying, data visualization, statistics and programming.
Massive data medical imaging: Massive data analytics for healthcare may change the best way photos are read algorithms developed analyzing tons of of hundreds of pictures might identify particular patterns in the pixels and convert it right into a quantity to help the physician with the diagnosis. They even go additional, saying that it may very well be attainable that radiologists will not need to take a look at the pictures, however as a substitute analyze the outcomes of the algorithms that will inevitably examine and remember extra images than they could in a lifetime.
As you'll be able to see from the above image, a Data Analyst usually explains what is going on by processing history of the info. On the other hand, Data Scientist not only does the exploratory evaluation to find insights from it, but in addition makes use of varied superior machine studying algorithms to identify the incidence of a particular occasion sooner or later. A data Scientist will look at the data from many angles, typically angles not identified earlier.
It's changing into fairly widespread to find articles and suppose-pieces that tout the numerous advantages and benefits massive data analytics offer companies and organizations across all industries. What is not as common is a transparent concept of what information and analytics are. For most individuals, these two concepts had been forgotten shortly after university and are used only tangentially. Nevertheless, it's becoming fairly clear that to be truly successful and find the most effective methods to continually keep an edge, understanding analytics is vital.
In his popular ebook ‘Competing on Analytics', Thomas Davenport defines analytics as The in depth use of knowledge, statistical and quantitative evaluation, exploratory and predictive models and reality-primarily based management to drive selections and actions.” To put it in layman's terms, it refers back to the analysis of knowledge to draw hidden insights, to aid in resolution-making”.
For more information visit our site ExcelR Data science courses
0 notes
Text
When is 'Social Credit' Orwellian?
Here is a fascinating brand-new advancement worldwide of 'credit' that pays for fine fodder for reflection. China remains in the process of fine-tuning and rolling out a digitally tracked 'social credit'system that has some individuals considering and other individualsshuddering. (Others, it must be kept in mind, believe the story overblown.) The concept is, in essence, to generalize the organization of the 'credit history, 'with which everyone are
more or less familiar, into something rather wider-- what may be called a'trustworthiness score.'Whereas the very first type of score is produced by application of an algorithm to one's net worth, earning potential, and financial history to ascertain her probability of paying off her financial obligations before a loan provider provides to her, China's alternative is targeted at ascertaining something more like just how' organized 'or'socially adhering'you are where sundry guidelines and social standards are concerned. The first type of score,
simply put, ratings you as a market individual who might seek business credit of some kind, and intends to help potential lenders. The 2nd ratings you far more broadly, as an individual not just in a market, but likewise in society at big. Not just prior defaults or delinquencies on loan payments, however also illegal parking or cigarette smoking in nonsmoking locations will affect your'social credit'score. The sanctions brought by low ratings differ in the 2 cases in a manner that tracks the different scopes of the 2 cases. A low credit score narrows your loaning alternatives: some will not lend to you at all, others will charge greater interest or need security or back-up guarantors. A low 'social credit' score, by contrast, may lead to your being deflected of aircrafts or of high-speed trains. It will likewise be advertised, presumably to help with avoiding and shaming. Forget 'financial personal privacy'-- under social credit history system, you do not enjoy financial or any type of privacy on matters that may be of interest to those thinking about engaging with you in any way.
If you are like me, you're most likely made a little anxious by this system that China is said to be implementing. Why? Is it really that odd?
If you think about it, you'll quickly see that any loan system-- undoubtedly any social system, if it remains in truth a'system'-- is a type of 'social credit'system, and most likely couple of but the most bold of hermits object to the upkeep of such systems in some form or other. Sociality itself would appear to presuppose and depend upon them. Moreover, the decrease of multifactorial'social credit' vectors to rough scalar procedures of merit appears itself to be ubiquitous throughout social systems. We typically'sum 'individuals'up,'in both formal and informal settings, as variably 'good,' 'decent,' 'dependable,' 'reliable,' 'faithful,'etc.-- in families, clubs, work environments, areas, ... you call it. And of course we allow entire industries of 'credit scorers' and other 'reputational intermediaries,' as kept in mind above, to determine who amongst us gets short-lived access to what resources for what purposes, and so on
. And lest there be any error here, this isn't practically scoring debtors anymore, even here in 'the West.' Algorithmic scoring is utilized now in making migration choices and traveler-screening decisions, in working with decisions, in' digital nudging,'in' wise city'security systems, in medical insurance and health shipment systems, and in a quickly growing host of additional applications. Some fintech firms are even now toying with the concept of providing ' social capital scrip,'which would amount to a sort of'spendable social credit'-- standing to social credit rather as currency stands to normal bank credit. Something informs me, nevertheless, that finding out 'we're doing it too now 'doesn't make you feel better about the Chinese case-- or about ours.
What precisely is it, then, that is so troubling about these stories? I think I see 3 possibilities. One source of our worry is presumably the anti-democratic provenance and use of the particular index in concern in China. It is hard to
see it as having
been most likely conceived, built, or deployed by the demos--'the people'-- in any possible sense. And so it looks as though individuals will be denied access to all manner of resource and access on the basis of assessments made not by one another, however by some unchosen manager that's thrust upon them. We might therefore object to the index as being successfully little bit more than a fintech rendition of the old Tang Code, which like most of its follower codes in ancient China was essentially absolutely nothing more than a'book of penalties'administered by an unchosen, unauthorized overlord. Call this the democratic objection. Keep in mind thatthe democratic objection, if meaningful, would rollover to many of the 'Western'cases listed above too, nevertheless. Democratic responsibility is attenuated, if not entirely missing, in all of them. A 2nd source of our concern might be the abnormally large number, and maybe some or a number of the particular options, of vector components that go into the scalar procedure of'social credit'in concern here, at least insofar as the step is then employed formally by'the state' or some other entity instead of informally by members of the community opining informally about one another's dependability. It grates upon liberal sensibilities, for example, to recommend that residents might be denied the capability to acquire rail tickets merely because at some point in the past they were caught cigarette smoking in non-smoking locations-and that they may subsequently regain that capacity by contributing blood or taking part in other' pro-social behaviors.'Surely those credit relations of which a state takes cognizance must be restricted at the very least to our material
efficient and exchange relations, we may object, hence to our dependability as contractual payers-back of what is contractually provided to us. Other indications of virtue, vice, merit or demerit, we may continue, need to be'off limits 'to state functionaries. Call this the classical liberal objection. Here too the objection, if meaningful, should occasion some fret about some of the'Western'cases kept in mind above too. For a few of them include units
of federal government at one level or another-- e.g., DHS, TSA, or local government. We may even stress, as classical liberals, about cases involving 'private 'entities' doing the scoring, a minimum of if they work as monopolists or oligopolists in the appropriate markets, leaving us without alternatives. Finally, some might challenge the' reductiveness'associated with any selected aggregation guideline-- algorithm-- purporting to commensurate and convert a vector of social credit measures into a single scalar such measure. Depending on further requirements of the ground of this objection, it might be a variation on either or both the democratic and the classical liberal objections just noted. Or it may be an objection to reductiveness as such. If the latter, call this the anti-< a href="https://en.wikipedia.org/wiki/Reductionism"target="_ blank"rel= "nofollow noopener noreferrer" data-ga-track="ExternalLink: https://en.wikipedia.org/wiki/Reductionism" > reductionism objection. However in the latter case the objection should then carry over to our casual practices of'sizing individuals up'and characterizing them in shorthand style too. The objection in this case would be, in
other words
, an objection to the inherently reductive notion of putatively unitary'social credit 'as such -and therefore successfully a rejection of sociality itself inasmuch as sociality rests upon open-ended' trust'formed on the basis of numerous distinct qualities of our fellow people and neighborhood members. What, then, to consider all this? I admit that I am unsure of simply which of the three discussed grounds of objection represent my anxiousness with China's new' social credit'system. I do believe, nevertheless, because of the foregoing, that all
three such grounds suggest we ought to be fretted in your home here too. For while ours is maybe somewhat less'centralized'than China's, we seem to have a rapidly establishing, algorithmic' social credit 'system crystalizing< a href="https://kieranhealy.org/files/papers/slam-2.pdf?fbclid=IwAR2O5vBESF37x0MAV1U6N_hpJjek365ls6pHSIOpYDepMKSC9iKadgTbYmo"target="_ blank "rel ="nofollow noopener noreferrer" data-ga-track="ExternalLink: https://kieranhealy.org/files/papers/slam-2.pdf?fbclid=IwAR2O5vBESF37x0MAV1U6N_hpJjek365ls6pHSIOpYDepMKSC9iKadgTbYmo"> here in our own society too.
0 notes
Photo

New Post has been published on https://cryptomoonity.com/community-update%e2%80%8a-%e2%80%8aoctober-2018/
Community Update — October 2018
Community Update — October 2018
Community Update — October 2018
And if you celebrate, Happy Halloween to you! Here’s what we were up to in October.
Technical Update
eWallet Suite
This month, the eWallet Suite team managed to cover quite a bit of ground as well as prepare themselves for Devcon IV.
eWallet Application
As complex as it was, the eWallet settings feature was finalized. The team fixed some bug issues with the preloaded exchange pairs, which weren’t loading properly, improved the transaction flow to our iOS point of sale application, released iOS SDK 1.1.0-beta2 and implemented a support transaction request for an admin module on the Android SDK.
Android Point of Sale Applications
For Android, the version number and endpoint address to the profile and sign in pages were added to the Client Application. A balance detail page was implemented as well as primary token setting ability. To improve navigation flow, the team has switched to the Android Navigation Component. Support for transaction requests on the Client Application has been implemented and a new sub-app dedicated to load testing was added.
iOS Point of Sale and SDK
A number of key features in the merchant Point of Sale application were added, including, but not limited to, the app icon, launch screen, receive funds and top up. Error handling was improved and the team started to add admin endpoints in the iOS SDK. Other support functions added include transaction request/consumption flow in the admin SDK, swift 4.2 in the SDK and Point of Sale applications and base files for the Point of Sale application.
What’s in store…
Next month, the eWallet Suite will be working on the following features:
Admin permission matrix
Transaction auditing
Improving error reporting
Additions to iOS and Android Point of Sale apps
Again, you can always follow the eWallet Suite team’s progress on Waffle board.
For more details, read our eWallet Suite updates here:
eWallet Update October 29, 2018: the “And my axe” edition
eWallet Update October 15, 2018: the “Mr. Stark? I don’t feel so good…” edition
Plasma
Development
This past month, we were focused on getting the Watcher API ready for deployment on our internal testnet. For those who aren’t familiar, the watcher is a critical component for building apps and for securing the network. In other words, anyone building an app will need to deploy their own watcher. We worked on the deployment tooling and carried out performance improvements to the watcher syncing process and detection of faults (invalid blocks, invalid exits, block withholding).
Quantstamp provided preliminary audit feedback revealing a potential attack vector in our Plasma MVP root chain contracts that opens up the possibility that client nodes will consider the child chain invalid and trigger a mass exit. This issue has since been addressed along with other recommendations. We will release audit results once they are finalized.
Research
LearnPlasma
Adding new content to the LearnPlasma website just became a whole lot easier as it is now generated automatically from markdown files.
We invite you to help out with open issues — there are plenty, and community feedback is always welcomed. Also, get paid for contributing to open source work. GitCoin bounties usually get attached onto issues.
Plasma Cash
Our Plasma Cash research continues. We’ve been working with other researchers to simplify atomic swap protocol which builds off Vitalik’s atomic swaps and defragmentation work.
In tackling the problem of large histories in Plasma Cash, we’ve been spending more time with RSA accumulators, which are used to decrease size of proofs users need to send when transferring tokens to each other. We will share updates on this as we get further. In the meantime, people are starting to put these ideas into practice.
Generalized Plasma
Right now, app agnostic plasma chains are the holy grail of plasma research and they are incredibly hard to build. We found ourselves at MIT where we participated in a large research workshop to address some of the underlying problems that make generalized plasma hard. As a first step to formalizing plasma, we spent some time trying to come up with a definition. What is plasma? We then had discussions around how generalized plasma chains should actually represent smart contracts.
For more details on Plasma work, read our updates from the links below. They also include notes from the Plasma Implementers’ calls:
Plasma Update #6 — October 22, 2018
Plasma Update #5 — October 8, 2018
State of the OMG Ecosystem + Roadmap
In our recent blog post, we attempt to summarize the different elements of OmiseGO and the OMG ecosystem, capture key developments over the past months and provide some information on where we’re going — this to provide our audiences some context. It might seem like a repeat of the Official Guide, but this is more succinct and offers updates. Additionally, we included an updated roadmap with key milestones. We’ve been working with community members as well on the OMG project tracker to track progress on a smaller timescale. Do check that out and read the full blog post here.
Omise Holdings in the news
Omise receives investment from Japan’s Global Brain
© 2018 Omise Holdings
Our parent company, Omise Holdings announced that it successfully raised an undisclosed funding amount. As part of the B++ series, the investment is led by Japan’s largest private venture capital, Global Brain, with participation from 31 VENTURES, CVC arm of Mitsui Fudosan and returning Indonesian venture capital, SMDV. Omise Holdings and Global Brain are already in partnership on several ongoing foundational projects including the Ethereum Community Fund (ECF) and blockchain focused co-working space, Neutrino. Read more here. This funding round was carried out by Omise Holdings, but the funds will be used to support all of their projects including OMG.
Past events
Nervos Meet Up, San Francisco, October 8, 2018
© 2018 Nervos Network
We were invited to speak at the Nervos Network meet up in San Francisco alongside SKALE Labs, Celer Network, SpankChain and Alacris. It was an educational evening to say the least. Our Director of Plasma Research was there share insights on the latest developments and breakthroughs in scaling solutions, in particular, Layer 2 solutions that operate on top of existing blockchains.
Watch the full clip here.
Status Hackathon, CryptoLife, October 26–28, 2018, Prague
Plasma 101! We were there alongside Status, MakerDAO, Gitcoin POA Network and MyBit, among others. It was an educational event to say the least. We provided an overview of Plasma, then progressed to Plasma MVP and Plasma Cash.
In classic hackathon style, the venue was open all night; participants broke off into groups to either work on proper hacks, or just absorb that magical hackathon energy as they tried frantically to finish their Devcon4 slides.
DEVCON IV, October 30–2 November, 2018, Prague
We will be at Devcon IV in Prague. If you’re attending, stop by our booth to say hi. This year, we are co-boothing with Hoard Exchange. This year’s agenda is packed with many interesting talks covering a range of topics, workshops and tracks including a talk on the illusion of neutrality in system design by Kelvin; a Plasma talk by Kelvin and David; a live Plasma implementers call; and of course, a very special keynote featuring Stewart Brand and two OMG veterans.
Upcoming events
Singapore Fintech Festival, 12–16 November, 2018
Meetup — Decentralise the future: real world use-cases, 14 November 2018
NODE Tokyo 2018, 19–20 November, 2018
Community Update — October 2018 was originally published in OmiseGO Network on Medium, where people are continuing the conversation by highlighting and responding to this story.
Source
0 notes