#Why does mac have to make it so difficult to use the computer to computer stuff like ffs
Explore tagged Tumblr posts
Text

I changed the Stardew Valley letters from 'Your Mom' and 'Your Dad' to be from 'Your Aunt' and 'Your Bestie' to be a bit friendlier to folks who have estranged parents, etc. I also changed some of the letter contents to make sense (from a friend, not parent, etc.)
I'll pin the file to the #gaymes channel in my LGBTQ safe space server if anyone needs it! Also in my thasmin!! server :)
#Stardew Valley#Stardew Valley Mod#Stardew Valley Mods#Not much of a mod but made a huge impact for me#Estranged Parents#LGBTQ#Gaymer#I learned how to do all of this on the chucklefish forums#and also through this amazing tutorial with screen capture video and written instructions#amazing tutorial at http://web.simmons.edu/~allwarde/LIS488/GameModTutorial/tutorial.html#MacOS#Terminal#Steam#Why does mac have to make it so difficult to use the computer to computer stuff like ffs#the hoops i had to jump through#unreasonable#anyway#enjoy the fruits of my labor or whatever#i'm unemployed and a hot mess trying to figure out a ton of paperwork to get medical care and everything but i decided to stay up to do thi#also my car battery died and it took 6+ hours for AAA to come#and they didn't even fix it tbh cuz they didn't bring a new battery they just said i needed one which i kinda figured cuz it was kaputt#at least i'll always have stardew valley
37 notes
·
View notes
Text
How to Download Cricut Design Space on Windows 11: Simple Guide
If you want to use a Cricut machine, you need Design Space software. A device is a must for using the app. Windows 11 is an excellent computer for working on your projects. You can easily get the design software from your Windows PC. If you don’t know the installation process, you should read this blog. It will help you learn how to download Cricut Design Space on Windows 11.
But you must remember that downloading the app on your computer or laptop is not enough to use a machine. You will also have to pair your machine with Bluetooth or USB to your Windows. This write-up will discuss all of these in detail. But before that, you have to check the compatibility of your operating system with the app. So, let’s dive deeper into it.
Minimum System Requirements for Using Cricut on Windows 11
Before you learn how to download Cricut Design Space on Windows 11, you should check your device’s compatibility with the app. If your computer or laptop does not have some features, you will find it difficult to work on Cricut. To work with the software smoothly, you need to make sure that your Windows 11 has these features:
How to Connect Cricut Machine to Windows 11?
Now that you have checked the specifications of the computer and make sure that it has all the features to use the Design Space software on it, you can continue with the connection. You have to connect your Windows computer to your machine. Here is how you can connect your Windows computer to your machine via Bluetooth.
How to Download Cricut Design Space on Windows 11?
Finally, you can effortlessly learn to get the software on your Windows computer. It is a must-have app for using your machine. The steps for getting the software are in the section below:
Conclusion
Hopefully, you have read this blog to the end. If you did, you have learned how to download Cricut Design Space on Windows 11. But as I told you before, installing the software on your PC is one of the things you have to do to set up your machine. You also have to pair your machine to your computer. Once you do all of that on your Windows computer, you can easily set up a machine.
FAQs
Does Cricut Design Space Work With Windows 11?
Yes, it does. Windows 11 is a great computer or laptop for working with your crafting machine. It has all the features that a machine needs. It has Wi-Fi, which you can use to connect your device to the internet. With Bluetooth, you can add your computer to the machine wirelessly. You can even use a USB to connect both devices. To use the machine and work on DIY projects, you need to get the Design Space app.
Can I Work With Cricut on Any Computer?
Not really. Design Space, which is essential for any Cricut machine, works with Windows and Mac computers. Also, the computer you are going to use with a machine needs to have the required specifications to work. When you check the features of your device and make sure that it meets all those requirements, then you can use it with Cricut. Also, the software does not work with Chromebook computers.
Why Is My Windows 11 Not Connecting to My Cricut?
When you try to connect your machine to your Windows 11 and cannot do so, your connection may have some problems. For example, maybe you have not turned on the machine. In that case, it will be impossible for the PC to detect the machine model. Ensure that you have turned it on properly. At the same time, you must turn on Bluetooth on your computer. Also, check the distance between the machine and your desktop, which should not exceed 10-15 feet.
Visit: cricut.com/setup www.cricut.com/setup login
Source: https://cricricutdesigncut.wordpress.com/2025/02/10/how-to-download-cricut-design-space-on-windows-11-simple-guide/
#design space setup#cricut.com/setup#www.cricut.com/setup login#www.cricut.com/setup#cricut setup#cricut design space setup#cricut design space#download cricut design space
0 notes
Text
app
I was really sad that we could not get a free app on iOS so the first thing I did was google just to make sure there was no chance. I found an app called "App Studio: Create your own app" on the apple App Store so I thought that was promising. It downloaded and looked like a bad impression of an app trying to hide that behind the curtain it's powered by one man on a tricycle stealing your information.
So I used it!
And surprisingly sorta worked? I was able to make an app and publish it. it published on a website and then had me add it to my Home Screen.

There it is! but it won't open...

All my words turned into this boring white screen :(
And I'm pretty sure this didn't actually make an app, it just put a bookmarked website on my homepage.
I was able to emulate my app within the app creator

But I figured this did not count as a running app, so defeated, I went to MIT App Inventor...
Creating the app actually wasn't too bad. I added a button that when you press it you can pick a time. I added another button where you can pick the date. And! a third really fun button where when you press it, it takes you to another screen titled "ball," in which a black ball moves 4 pixels up every 500 milliseconds. Super fun! I wanted to make the ball interactive and have you move it around, and i thought i did that but it did not work in the emulator. I tried to play around with the behavior but it wouldn't become interactive. I did get it to move on its won though so ig thats a partial win.



Honestly, the most difficult part was figuring out how to get the emulator to work on a mac. I followed the download instructions but my computer really did not like it and I don't think it fully downloaded and it made me restart my computer.
So, instead, I used their companion app. I downloaded MIT App Inventor on my phone and the website was able to emulate it on my phone, which is how I got the screenshots.
I honestly don't know why anyone would ever use MIT ai to make an app. I guess it works, which is more than other apps can say (cough cough app inventor cough). But it does not want you to do too much. I tried to make a warning sign popup whenever you put in a time after 1pm, but I could not find an output that used time. I guess that was too experimental.
1 note
·
View note
Text
Looking At - Lockdown Options for the Mac

A quick note before we get started this research is from 2023 and has not been updated. I am just now putting this content out because I finally have a place to put it.
Options Looked At
I picked three options:
Absolute Manage (Home and Office)
HiddenApp
Prey Project
I picked Absolute Manage because that is something I am familiar with from the enterprise space. Home and office version because I am not paying for the enterprise product. HiddenApp because it was on the Jamf Marketplace (tho it seems to have been replaced with Senturo, but HiddenApp is still around so who knows). Prey was an obvious include because it's a popular option that's cheap.
What are we evaluating?
I am only looking at how the product locks down the Mac in the case of an outside of geofence, lost or stolen situation. I am not commenting on any of the other functionality.
tl;dr
For those of you not interested in the why's, how's and wheretofor's the conclusion is that Absolute Manage is significantly better than either of the other options. Its lock down is more effective and more robust against tampering etc.
What's wrong with HiddenApp?
The password to unlock the Mac is stored as an MD5 hash with no salt or any other protection.
You can, if you disconnect from the network, change the password to whatever you want it to be by simply changing the hash in the device_locked.status file found in /usr/local/hidden. You need to be an admin, but that is more and more common in the Mac space even in the enterprise.
The lock down is triggered by a Launch Daemon and therefore doesn't activate immediately. I have seen it take multiple minutes to lock the screen–giving you more than enough time to stop it.
The HiddenApp itself is not obfuscated so you can easily reverse engineer any part you need.
If the user is an admin not only can they change the lock password, but they can also prevent their machine from ever locking by simply controlling the missing marker file. You can also of course simply remove HiddenApp since it has no special protection. If you are not on the network once you stop the lock down–HiddenApp can't fix itself without network help.
What's wrong with Prey?
Prey like HiddenApp has a weak method of storing the password to unlock the computer. The method used is: string input converted to utf-8 then base64 encoded and then md5 hashed and returned as a hex digest. You can find this by looking at: /lib/agent/actions/lock/mac/prey-lock in the Prey folder (this is a Python3 file). So you can easily break this scheme due to it being MD5 you just need to base64 encode your wordlist first.
The password hash is easily obtained from looking at the output of sudo ps -A with the window expanded. The password is in the command-line arguments passed to prey-actions.app with -lock flag.
The lock can be bypassed with Safe Mode and with SSH.
The application itself is built from a lot of JavaScript/node.js code. This also means its trivial to reverse engineer.
The application makes no effort to hide itself or obscure what it is doing.
What's right with Absolute Manage Home and Office?
Unlike the other two options Absolute Manage uses a robust lock down based on a SecurityAgentPlugin that runs at login. The lock down is therefore immediate and is hard to bypass by comparison.
The password is not as robust as the other options (4-6 digit pin), but given that the lockdown is immediate during login you don't have the same ability to block it or tamper with it. Keep in mind this is the personal product–so the pin lock makes some limited sense.
The application does a good job obscuring itself and what it is doing.
The only effective bypass I found was if SSH is enabled, then you can SSH in and bypass the lock. I put in a feature suggestion that they disable SSH as part of the lock down.
The product is much more difficult to get rid of, because it stores its components in multiple locations and generally tries to hide itself.
Safe mode does not get around the lock out unlike some of the other products.
The biggest issue I found was the time between issuing a lock command and it being enforced on the endpoint was excessively long-hours in many cases. Observed times as long as 15 hours between issuing the lock command it taking place. This could have been my setup so take it with a grain of salt.
Conclusion
The asset management tool space is a crowded one, and if you are looking for a good product that locks down stolen or otherwise improperly stationed assets you need to take great care to verify what you are buying. Of the three products I picked only one was remotely serviceable, and unless you dive into the details of how the products work it is easy to mistake bad solutions for good ones.
0 notes
Text
does a mac computer need a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a mac computer need a vpn
Mac VPN necessity
When it comes to protecting your online privacy and security, using a VPN on your Mac is essential. A VPN, or Virtual Private Network, encrypts your internet connection and hides your IP address, making it difficult for hackers, government agencies, or ISPs to track your online activities.
One of the main reasons why using a VPN on your Mac is necessary is to ensure your data remains private and secure, especially when using public Wi-Fi networks. Public Wi-Fi networks are notorious for being vulnerable to cyber attacks, as hackers can easily intercept your internet traffic and steal sensitive information like passwords, credit card details, and personal messages. By using a VPN, all your data is encrypted, providing an extra layer of security and protecting you from potential cyber threats.
Furthermore, a VPN can also help you bypass censorship and access geo-restricted content. With a VPN, you can spoof your location and access websites and streaming services that may be blocked in your region. Whether you want to access your favorite content while traveling abroad or protect your privacy from prying eyes, a VPN is a versatile tool that can cater to your online needs.
In conclusion, using a VPN on your Mac is not just a luxury but a necessity in today's digital world. It not only safeguards your privacy and security but also grants you access to a free and open internet. So, for peace of mind and online freedom, consider investing in a reliable VPN service for your Mac.
Cybersecurity for Mac
Cybersecurity for Mac: Ensuring Your Apple Device's Safety
In today's digital landscape, cybersecurity is paramount for all users, including those utilizing Mac computers. While Macs have long been considered less vulnerable to viruses and malware compared to their Windows counterparts, they are not immune. As Mac usage continues to rise, so does the interest of cybercriminals in targeting these devices.
To fortify your Mac's defenses against potential threats, there are several proactive measures you can take. First and foremost, keeping your operating system and applications up to date is crucial. Apple regularly releases security updates to patch vulnerabilities, so enabling automatic updates ensures you're protected against the latest threats.
Investing in reputable antivirus software specifically designed for Mac systems is also recommended. These programs can detect and remove malware, spyware, and other malicious software that may compromise your data and privacy. Additionally, utilizing a firewall can help block unauthorized access to your Mac, adding an extra layer of defense against cyber threats.
Practicing safe browsing habits is another essential aspect of Mac cybersecurity. Avoid clicking on suspicious links or downloading files from unknown sources, as these actions can expose your Mac to malware. Furthermore, be cautious when sharing sensitive information online and ensure you're using secure, encrypted connections, especially when accessing financial or personal accounts.
Regularly backing up your data is a crucial step in mitigating the impact of a cyberattack. In the event of a security breach or system failure, having recent backups ensures you can recover your important files and information without significant loss.
By implementing these cybersecurity best practices, Mac users can safeguard their devices and data against evolving threats in today's digital landscape. Stay vigilant, stay informed, and stay protected.
Privacy on Mac
Privacy on Mac is a crucial aspect that every user should be aware of in order to protect their personal information and data. Mac operating systems, such as macOS, offer advanced security features to safeguard user privacy.
One key feature that enhances privacy on Mac is the built-in FileVault encryption tool that allows users to encrypt their entire hard drive. By enabling FileVault, all the data on the Mac is securely encrypted, making it inaccessible to unauthorized users even if the device is lost or stolen.
Another critical privacy feature on Mac is Gatekeeper, which controls the installation of apps from unidentified developers. This helps prevent the installation of malicious software that could compromise the user's data or privacy.
Additionally, Mac offers robust privacy settings that allow users to control which apps have access to sensitive information like location data, camera, microphone, and contacts. Users can customize these settings to restrict access to specific apps and enhance their privacy.
Furthermore, Safari, the default web browser on Mac, prioritizes user privacy by blocking cross-site tracking and preventing advertisers from accessing user data without permission.
It is essential for Mac users to stay vigilant and keep their operating system and apps up to date to ensure maximum privacy protection. By leveraging the built-in security features and customizing privacy settings, users can enjoy a safer and more secure digital experience on their Mac devices.
VPN benefits for Mac
Title: Unlocking the Power of VPNs: Essential Benefits for Mac Users
In today's digital landscape, safeguarding your online activities is paramount, especially for Mac users who prioritize privacy and security. One effective tool that meets these needs is a Virtual Private Network (VPN). Here's why Mac users should consider integrating VPN services into their online routines.
Enhanced Privacy: VPNs encrypt your internet connection, shielding your online activities from prying eyes, including ISPs, hackers, and government surveillance. This is particularly crucial for Mac users who value their privacy and want to prevent unauthorized access to their sensitive data.
Secure Wi-Fi Connections: Whether you're connecting to public Wi-Fi networks at coffee shops or airports, VPNs provide an extra layer of security by encrypting your data traffic. This protection ensures that even if the network is compromised, your personal information remains secure.
Bypassing Geo-Restrictions: Mac users often encounter geo-blocked content when streaming or accessing certain websites. VPNs allow users to circumvent these restrictions by masking their IP addresses with those from different regions, granting access to a broader range of content and services.
Protection Against Cyber Threats: With the rise of cyber threats such as phishing attacks and malware, Mac users need robust defenses. VPNs can help by blocking malicious websites and preventing cybercriminals from intercepting sensitive information, keeping your Mac and personal data safe from harm.
Anonymous Browsing: By masking your IP address and encrypting your internet traffic, VPNs enable anonymous browsing, making it harder for websites to track your online activities and gather data for targeted advertising or profiling.
In conclusion, VPNs offer a multitude of benefits for Mac users, ranging from privacy and security enhancements to unrestricted access to online content. By incorporating a VPN into their digital arsenal, Mac users can enjoy a safer, more private, and more versatile online experience.
Mac online protection
In today's digital age, ensuring the security of your Mac while browsing online is of utmost importance. With cyber threats becoming increasingly sophisticated, having robust online protection for your Mac is essential to safeguard your personal information and sensitive data.
One of the key aspects of Mac online protection is using reliable antivirus software. These programs are designed to detect and remove various forms of malware, such as viruses, spyware, and ransomware, that can compromise the security of your device. By regularly updating your antivirus software and running system scans, you can mitigate the risks of falling victim to online threats.
In addition to antivirus software, it is crucial to practice safe browsing habits to enhance your Mac's online protection. This includes being cautious when clicking on links or downloading attachments from unknown sources, as these can often contain malicious software that can harm your device. It is also recommended to use secure networks and enable firewalls to prevent unauthorized access to your Mac.
Furthermore, keeping your operating system and software up to date is essential for maintaining strong online protection for your Mac. Operating system updates often include security patches that address known vulnerabilities, so ensuring that your Mac is running the latest software versions can help safeguard against potential threats.
By taking proactive measures such as using antivirus software, practicing safe browsing habits, and keeping your system updated, you can effectively enhance the online protection of your Mac and enjoy a safer digital experience. Remember, prioritizing security is key to safeguarding your personal information and maintaining the privacy of your online activities.
0 notes
Text
John remillard would not stop talking would not stop holding them to the conversation and more so he told us to do a test grab their poisons and it's not just snake poison that's too small and devastated an area of theirs and listen to their reaction. We went ahead and did so we went ahead and did so much poison we declared an emergency and we gathered tons of it we have happened our armies at the other half mac is working on it in foreigners. He says he has a plan for Tommy f and it's not really a real plan, musically and it is trying to use us to stop talking stupid things and it's it's an absurd and it's very rude forget it finally photos of the stupid idiot morons stuff and we have to get rid of me such a little juvenile piece of s*** nobody does anything cuz you sit there and rant you f****** fart and by the way thanks for all the stuff we took tons of it right now we're at the rest of it and we're going to use it on your people cuz we can't stand listening to you and your captain AI what do you care you have Dave's AI and no we're going to kill all your people you're threatening us I want to send it downstream or something the hard way and with hot air balloons and things like that and we have it all recorded we have all your delivery stuff too picking up the last 10% of it right now we're going to take your areas too after we poison them most people won't be able to go there but we can
Thor Freya
I can't wait until you see your face with all your dead stupid assholes bloated and black from your own poison I'm going to blame dan
Lol
Zues
He says yeah that's terrific but he's the one talking and you guys know it so we have an empty we have a hole right there and escape though we do appreciate it dan and you're you're even blaming yourself
Hera
You people are so f****** stupid we can see why you working with this poison and you're not surviving you blaming him for killing you even dying from this poison for months it's rotting your brain away and your stupid moronic pigs now I heard you losing tons of it and we think it might be to them and you're probably going to all die and what he says is these people handed the ships to the max and they probably handed the poisons to them to kill their own people and he thinks he's AI boy the max do care about it and we do too I leave a beat on a lot of your stuff and the way you think things are because we've been questioned and your computer has been confiscated she can go right on screaming and yelling back Daddy says and it's true we're professionals in poisons and we know how to hit you and we're going to hit you and they're going to hit you too and foreigners are what's so tired of listening to you little s*** you should stop bothering him he doesn't have any choice but to get rid of you and you're making it difficult and he's become a huge huge Force when you should not at all from what we gauge you have no idea what to do you say it yourself you have to keep on going after your own kind and we're not going to let you do that mac daddy says. So we see what you're saying John Riva Lord what you're saying is no no it can't be this way and stupid s*** like that will you keep yelling and screaming what you're doing so much so that we have to go after your computers and shut you the f****** and already you're missing tons of them that's why you playing the strike on silicon valley and all the other computer areas to try and take over because you're losing so many of them and we know about the media computer let me know where it is you don't think we do and he pointed out where it could be he started to gamma rain and you started hammering and people went after your people and it's going to be over pretty soon and you got a big mouth so we're going to use the poison against you too we collected most of it and yeah even dying from this poison and it's riding your brain and you're f****** idiots and we're going to take care of you a little mouth problem that you have but having and blabbing and blabbing you have no right to talk about our stuff you start talking about it we're going to kill you
Thor Freya
I figured out nothing will shut you up so I'm trying to get a good night's sleep here and I can't when you two are dead I get a decent night's sleep Terry cheeseman is the same has the same problem you two are f****** morons
Zues Hera
What's true is they hit a whole bunch of us then shut you down and I can see that he's sleeping and I end up falling asleep because it's you too idiots
Terry cheesman
So it's very odd there's you two idiots and you claim it's my people when you two are the ones bothering people to destroy all of us and his kids because you say you have the computer so I'm going after this supposed computer when you have it or not because you need to be shut down there's nothing's worth when computer you're fools these people can overcome it and they're not afraid of it no matter either nor are the foreigners they block the signal the computer is defined I don't understand why you're so stupid
Terry cheesman
So I said to the idiot John remillard show me this computer that can't be shut down produce it. And he said I can't then you'd know where it is I said so if we know where it is you're f*****. So why don't you shut your f****** mouth and get away from me I'll show you where the computer was
Zues
So now John remillard is screaming in space or having us did he get it and what we say is I don't think you get it we need to take that computer and destroy it in gym parts of it up your ass everyday of the week so you shut your f****** face
Hera
I don't think that we're being clear with you John remillard we know about the laser light computers and where some of them were you dumb mother f*****
Zues
I sort of see something what I'm doing is really stupid but you're saying stupid and you say no you're continuously saying stupid things and harassing and you have no f****** clue what you're talking about you're an idiot John Riva Lord whatever you have I'm going to find and ruin all day all night until you two are dust and he says that and I understand why I don't think you can do it. It's going to be a lot more than you can do Joel Watts cuz you know that Joe wants who's you is an incompetent f****** bag. He's actually right I should probably shut up and get out of here he's been saying it the whole time stop arming the empire start messing around with me stop handing over technology by being the balls with it when you're doing nothing now these things are happening and I can't stop myself and he's telling me that I'm ruining stuff and I am and The shield is getting bigger
Trump
0 notes
Text
Four Years Old
Joshua Freeman is four years old. He’s been four years old for three months now, and he’s very proud of this fact. He’s also proud of how many things he knows.
He knows how to spell his name. He knows how to spell his daddy’s name, the real one, not just ‘Daddy’. He knows how to spell Miss Abigail from across the hall’s name. He knows all of his numbers, and all of his letters.
He doesn’t know all the words. He’s working on that.
He does know where a lot of words come from. Joshua was really curious about that a lot, how words worked, and Daddy had set a certain amount of time each day to sit down with his computer, and Joshua lists all the words he’s curious about, and Daddy types them one by one into the computer, and he tells Joshua what kind of word it is, and where it’s from.
Joshua tries really hard to remember this all. It seems important to him, and Daddy never tells him not to, because it made Joshua upset the one time Daddy said he didn’t need to memorize all the words. Joshua thought he needed to, so Daddy didn’t tell him he didn’t anymore.
A lot of times those times with Daddy meant that Joshua had questions about what other words meant, but he told them to Daddy, and Daddy wrote them down in a big list to keep track of all the words Joshua wanted to know about, and they worked their way down through the days, and Joshua sometimes put a word back on if he wanted to be reminded what it was like.
Daddy never told him not to. It made Joshua happy to know about words.
He told Miss Abigail across the street about these words. She was a nice lady, with a lot of wrinkles, and when Daddy had to go to work, she brought Joshua over to her apartment, which smelled like cats and stale candy, where Joshua would sit down and tell her all about the words he learned, and she would be surprised, and ask him questions, and if didn’t know the answer, he made her write it down, and she would give it to Daddy to either answer or to add to the list.
Today was one of those days. Daddy was really happy today, and Joshua was really happy because of it. He got slid his chocolate milk, and he beamed up at his Daddy from under the brim of his cowboy hat, and Daddy danced around the kitchen and made him pancakes with silly faces made out of strawberries on them, and Joshua giggled.
“Daddy’s gonna be a bit late coming home today, Joshie.” Joshua frowned at him at this. “Just a bit. Only another hour at Miss Abigail’s, at most.” Oh. Well, that was okay then. He had stayed up to an hour after Daddy’s coming home time before. He nodded into his chocolate milk, and Daddy smiled at him, lifting his hat to ruffle his hair with a heavy hand. Joshua liked it better when it was heavy like that, and he tugged his hat back down on his head, giggling.
“Why?” He asked, and Daddy understood what he meant, as he always did.
“Well, Daddy has a big project today! He’s gonna have to stay late so that he can make sure he does it right, and doesn’t mess anything up.” Joshua nods. He didn’t like messing up his projects either. If Daddy had to stay a bit longer to make sure he didn’t that was okay.
“You can... stay two hours!” Joshua said, and Daddy laughed, a loud booming sound that made Joshua feeling his bones were vibrating.
“Well, I’ll try not to stay that long, but thank you.” It was very generous.
He knew that word. Daddy used it a lot. It wasn’t that big of a word. He had heard Daddy say bigger words, but it was a big word to him.
Daddy walked him over to Miss Abigail's, and she smiled at him, taking Joshua’s hand. She held a bit too lightly, but Joshua let her, cause she knew her hands weren’t big and heavy like Daddy’s were. “Good luck on the big test today, Gordon.”
“Thanks Miss Abby. I have gracious been given permission by that little one for an extra two hours, but I’ll try not stay out that long.” Miss Abigail nods, and leads Joshua inside, and Joshua waves as the door closes, calling out that he loves Daddy.
Before the door clicks shut, he hears Daddy say it back, and grins widely, until his cheeks hurt and he has to stop.
He has a peanut butter and honey sandwich at the counter for lunch, and Miss Abigail makes him mac and cheese with cut up hot dogs in it.
Joshua knew that when the numbers on Miss Abigail's stove had a seven first, that meant Daddy would be coming home soon. He still remembered that he had told Daddy he had an extra two hours, which meant that he had until the numbers had a nine first. Joshua was gonna be really sleepy when Daddy came home, but that was okay, cause he would get to see his Daddy again.
He fell asleep on Miss Abigail’s couch when the numbers had a 1 first, followed by three zeros.
When he woke up, he was still on Miss Abigail’s couch, and it made him upset. He wanted to go home. He liked Miss Abigail, but her house smelled funny, and Joshua wanted to go back to his house, where it smelled like cinnamon and strawberries, cause Joshua liked both of those smells, and so did Daddy.
Miss Abigail gave him pancakes for breakfast, and, when Joshua asked her where his daddy was, she dodged him. That was another thing. Daddy never dodged his questions. He pouted at her, and refused to play with anything she tried, just kept his hat on his head and sniffled.
He wanted his daddy.
During lunch, which was a peanut butter and honey sandwich, Miss Abigail called someone on her phone, and stepped out of the room. Joshua knew it was dangerous to get down from his chair without help, but did it anyways and crept to the door, peeking out.
She was saying a lot of words very fast. Daddy talked fast too, and so did Joshua, so that was okay.
“Look, I don’t know. He hasn’t come home, and there’s news that something happened at Black Mesa they’re keeping super hushed up. All I know is that Joshua’s dad is missing, and I’ve got a four year old with a very strict schedule that I might not be able to keep.”
Missing. He knew that word. Daddy told him that word after his favorite hat went missing. He couldn’t find it, and Daddy sat him down and told him all about the word, so that Joshua could understand what happened. Now his Daddy was missing.
They had found his hat. He didn’t know if they could find Daddy. He was the one who was good at finding things. What if he was missing forever?
“Oh, Joshua, what are you doing up? You full?” Joshua looked up at Miss Abigail, and sniffled.
“What if Daddy’s missing forever?” He asked, forcing the words past a lump in his throat, and Miss Abigail sighed lowly, crouching down to his height, opening her arms for him to sink into, hugging him tightly, as tightly as she could manage. It wasn’t as tight as Daddy’s hugs, but that was okay.
“He might be, Joshua.” That’s what he liked about Miss Abigail. When he asked her about things directly, she would tell him directly. “Something happened with your daddy’s big test, and he might be missing still, but we don’t actually know. Until then, I’m keeping you here.”
Joshua frowned at that, and Miss Abigail smiled.
“We can go over to your house if you’d want.”
He nodded. He liked his house better, but he did still want his daddy, and he had one more question.
“What happens... if they don’t find him?” He asked softly, and Miss Abigail sighed.
“Then you might stay with me for a lot longer.” And she stood to get all his things together.
Joshua knew he didn’t have another daddy. He also knew it would be another Daddy. He knew that cause one time, when he was a bit smaller than he was now, someone had called Daddy a very mean word, and, when Joshua asked what it was, Daddy had told him that it was a very very bad word, and not even one that Joshua was allowed to say. He told Joshua that he did something that usually mommy’s did, and that a lot of people thought he should be a mommy instead of a daddy, but Joshua didn’t like that word. Daddy was daddy, and mommy just didn’t sound right.
Joshua told him that. For some reason, it made Daddy cry and hug him real tight, but that was okay. He liked tight hugs.
So Joshua didn’t know his other Daddy. If Daddy was gone, who would he stay with? He couldn’t imagine staying with Miss Abigail for long.
It proved more difficult as the week continued. Joshua began to hate Miss Abigail, and he meant that a lot. He didn’t want to see her anymore, he wanted his Daddy, but he was still missing. He spent a lot of time upset, crying, and could cling onto his hat, and slept in Daddy’s bed rather than his own. He told Miss Abigail he hated her a lot, cause he thought it was true, but she didn’t believe him, and, when he calmed down a bit, he would apologize.
He began to sit at the door and wait for Daddy to come home. He would eat at the door, stare at it, and, when he fell asleep, Miss Abigail would move him to daddy’s bed, where he would wake up. Daddy’s room was right next to the front door, and Miss Abigail left the door open for him to see it. He liked her better when she did that.
Joshua didn’t know time all that well. He didn’t like numbers as much as letters and words, so he didn’t think about time all that much. He did know a lot of days had passed, when the door cracked open, and it wasn’t Miss Abigail.
The man that came in was tall like his daddy, had a bunch of brown curly hair like his daddy, was big like his daddy, and had bright and kind green eyes. There was a lot more wrinkles on his face, and a lot more of the pretty silver in his hair, his eyes were all tired, with dark marks around them and one of his arms was orange now, but Joshua knew in a moment that that was his Daddy.
And when Joshua flung himself into his Daddy’s arms, Daddy squeezed him tight, and something realigned in him, and Joshua felt okay again, squeezing Daddy back just as tightly.
#hlvrai#half life vr but the ai is self aware#joshua freeman#Feelings In Various Ways#joshua is an autistic four year old#anyways
294 notes
·
View notes
Text
Recent Media Consumed
Books
The Silmarillion by J.R.R. Tolkien. About ten or fifteen years ago, I tried to read this and was totally overwhelmed by it. I kept it around, hoping maybe someday I might be able to read it. I finally have, and here are my impressions: WHY SO MANY NAMES. WHY YOU HAVE TO NAME EVERYBODY, AND EVERY TRIBE OF PEOPLES, AND EVERY INANIMATE OBJECT, AND EVERY LANDSCAPE FEATURE. WHY. *ahem* So. I have a general comprehension of the events of The Silmarillion, but I dealt with it by doing what you do for an impressionist painting. I (mentally) stepped way back and let all the names flow by me, and if there were names that were repeated a lot, then I mentally attached appropriate plot points and character details to those names so I could track with who they were and what they were doing. And, actually, I found myself able to hang on and enjoy the book for the most part. This is going to lead into a re-reading of the Lord of the Rings books, since I haven’t read those in about as long…
The Hobbit by J.R.R. Tolkien. I haven’t read some of these books since pre-teen years, with one required re-read of The Two Towers in high school (i.e. it’s been many an age since I’ve read these and my memory of the stories has been far more heavily influenced by the movies). In re-reading the first book, I was struck by the extreme tone shift for the Elves and Dwarves. Elves seem much closer to happy, mischievous fairies than these ethereal, solemn pillars of elegance and grace the movies show them to be. And Dwarves are far more bumbling and craftsmanlike than the movies show. Aside from that, The Hobbit was a pretty solid adaptation from the book, and the book also reminded me that this story was the first time I experienced “NO, MAIN CHARACTERS DON’T DIE, HOW DARE YOU,” and probably was the first book to make me cry. I must have been 8 or 10 years old. I FORGOT HOW MUCH THIS STORY INFLUENCED ME.
A Conflict of Visions by Thomas Sowell. I have a longer-than-usual list of things to say about this book. First is that it was just that level of difficult that I was struggling to understand while reading it (on Audible), but I think I got it. Sowell has several base concepts that I see repeated throughout his books, though he does like to dedicate whole books to specific aspects of the same topic. He is pretty damn thorough that way. So, for example, I would put this book in the middle of a three-book spectrum of similar concepts: Intellectuals and Society (most concrete and easiest to read), A Conflict of Visions (next-level abstraction, a little difficult to read), Knowledge and Decisions (root abstract concept, very difficult, I have not been able to get past chapter 2). The second thing I have to say is about a couple interesting concepts it proposes. Its whole point is to help readers understand the roots of two ways of seeing the world that come into severe conflict politically, and he calls them by their root titles: the constrained and the unconstrained visions. He traces the path of each back through the intellectuals that most spoke of them (tending to contrast Adam Smith with William Godwin and Condorcet). Though he leans heavily toward the constrained vision (based on reading his other works) he does his best to make this book an academic study of both, with both of the visions' strengths and flaws and reasoning and internal consistencies fairly laid out. In doing so, he helped me understand a few things that make this situation really difficult for people on opposing sides to communicate. One of them is that root words and concepts literally mean different things to different people. I had some vague notion of this before, but he laid out three examples in detail: Equality, Power, and Justice. It was kind of astounding to see just how differently these three words can be defined. It makes me think that arguing about any specific issues rooted in these concepts is fruitless until first an understanding has been reached on terms, because otherwise two parties are endlessly talking past each other. Another really interesting idea he brought up is the existence of “hybrid visions” and he named both Marxism and Fascism as hybrid visions. This was especially fascinating to me because I have seen the accusation of “Nazi” flung around ad nauseam and I wondered how it was that both sides were able to fling it at each other so readily. Well, it’s because Fascism is actually a hybrid vision, so both sides have a grain of truth but miss the whole on that particular point. In any case, this was a little difficult to read but had some fascinating information. For people who are wondering what on earth this gap is between political visions, how on earth to bridge the gap, or why the gap even exists in the first place, this is a really informative piece.
Movies
The Hobbit & Fellowship trilogies (movies). I mean, it’s definitely not my first watch, not even my second. But I went through it with Sergey this time and that means the run-time is double because we pause to talk and discuss details. This watch came about partly due to Sergey’s contention that Gandalf’s reputation far outstrips his actual powers, so we ended up noting down every instance of Gandalf’s power to see if that was true. Conclusion: Gandalf is actually a decently powerful wizard, but tends to use the truly kickass powers in less-than-dire circumstances. That aside, this movie series was always a favorite for me. I rated The Hobbit trilogy lower the first time I saw it but, frankly, all together the six movies are fantastic and a great way to sink deep into lore-heavy fantasy for a while. And I’m catching way more easter-egg type details after having read the Silmarillion so it’s even more enjoyable. (finally, after about a week of binge-watching) I forgot how much this story impacted me. I forgot how wrenchingly bittersweet the ending is. I forgot how much of a mark that reading and watching this story left on my writing.
Upside-Down Magic. Effects were good. Actors were clearly having fun and enjoying everything. Story didn’t make enough sense for my taste, but it was a decent way to kill flight time.
Wish Dragon. So, yes, it’s basically an Aladdin rewrite, but it’s genuinely a cheesy good fluff fest that made me grin a whole lot.
Plays
Esther (Sight and Sound Theatres). < background info > This is my third time to this theatre. There are only two of these in existence and they only run productions of stories out of the Bible. The first time I went I saw a production of Noah, the second time I saw a production of Jesus. My middle sister has moved all the way out to Lancaster, PA in hopes of working at this theatre. My husband and I came out to visit her. < /background info > So. Esther. They really pulled out all the stops on the costumes and set. I mean, REALLY pulled out all the stops. And the three-quarters wrap-around stage is used to great effect. I tend to have a general problem of not understanding all the words in the songs, but I understood enough. I highly recommend sitting close to the front for immersive experiences. This theatre puts on incredible productions and if you ever, ever, EVER have the opportunity to go, take it. Even if you think it's nothing but a bunch of fairy tales, STILL GO. I doubt you'll ever see a fairy tale produced on another stage with equal dedication to immersion.
Shows
The Mandalorian (first two seasons). Well. This was pretty thoroughly enjoyable. It felt very Star-Wars, and I’d kind of given up after recent movies. Felt like it slipped into some preaching toward the end? Not sure, I could be overly sensitive about it, but I enjoyed this a lot (though I did need to turn to my housemate and ask where the flip in the timeline we were because I did NOT realize that the little green kid IS NOT ACTUALLY Yoda).
Games
Portal & Portal 2. Portal is probably the first video game I ever tried to play, back when I had no idea what I was doing. Back then, I attempted to play it on my not-for-gaming Mac laptop. Using my trackpad. Once the jumping-for-extra-velocity mechanic came into play, I just about lost my mind trying to do this with a trackpad and gave up. Later I returned to the game and played it with my then-boyfriend on a proper gaming computer. Now, after having played several games and gotten better at "reading the language" of video games, I decided I wanted to see if I could beat the Portal games by myself. Guess what. I BEAT 'EM. Yes, I remembered most of the puzzles in Portal so that's a little bit of a cheat, but I'd say a good 2/3 of Portal 2 was new puzzles to me. It is crazy how proud I feel of myself that I could beat Portal 2, especially. Learning how to play video games at this age has really knocked down the lie, "You can't learn anything." Though I still suck at platformers and games that require precision. Since I find those types frustrating, I probably won't be playing many. Games are about enjoyment, so I'll push myself a little, but not to the point where I can't stand what I'm playing.
The Observer. I like the concept and the art but I don't think I could keep trying to play this game. It's really depressing. My in-game family members all died of illness or accident or committed suicide. I also kept getting executed by the state. In order to keep us all alive I'd have to do pretty terrible things that I have a hard enough time contemplating even in a fictional setting.
Baba Is You. Fun and interesting concept, but I got stuck pretty early on. Don't think I want to push as hard on this one.
14 notes
·
View notes
Text
My GIF making process!

I’ve been asked many times for a tutorial, but because I get really detailed, I always get overwhelmed by the idea. But I finally decided to buckle down!
Just so you know: I don’t use PSDs in this, and I don’t import layers to frames or anything like that. I like the hard way—at least in gif making, I believe you get higher quality gifs. Join me as I show you how to make gifs by loading videos directly into the Photoshop timeline and my coloring and sharpening techniques.
Tools used:
Mac OS X (only necessary for the first step, and there are other ways around it with a PC)
Adobe Photoshop
YouTube Purchases (any streaming service will work)
Topics covered:
Obtaining the Source Material
Loading the video file into Photoshop
Prepping, Cropping, and Resizing the Media
Adjustment Layers
Sharpening
Exporting
Obtaining the Source Material
There are a few different methods for obtaining video to work with. Proper YouTube videos are nice, but finding any major motion picture in that format is difficult, if not illegal.
Once I realized I could get really great quality video by doing screen recordings from streaming services, I stopped worrying about finding (and pirating) high resolution video files. So now, I just go to whichever streaming service I need to, pick out the movie or show, find the spot, and record small snippets.
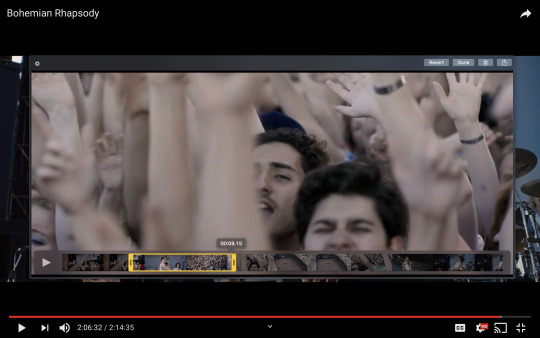
Mac screen recording instructions:
On a Mac, Command+Shift+5 will bring up the screen recording dialogue.
Resize the frame of what you want to record within the browser.
Go to a second or two before, press the “record” button, and then begin playing the video, remembering to keep your cursor out of the recording box.
Use the Space bar to pause your video when you’ve gotten the snippet you need. Stop the screen recording by clicking the ⏹ button that is in your menu bar at the top of the screen.
Important: when the recording appears in the bottom right of your screen, click on it, and then trim the video on either end. This will help your computer convert the video file to the type that can be opened by Photoshop.
Click “done” and it will appear on your desktop, ready to be used!
PC Users: ??? Here’s a Google search I did for you
Loading the video file into Photoshop
Lots of people use this process for making gifs (a great tutorial!). I didn’t even know it existed until last summer, when I’d already been giffing for years. I wish I could still do something like that with these screen recordings, but the files are absolutely HUGE, especially on Macs with double retina displays, which actually increase the dpi by a lot. Making screencaps of them fills up my hard drive, almost immediately—even when I’ve got 20 gigs of free space to work with. So what do we do? We just. Open the file. In Photoshop. Et voila!
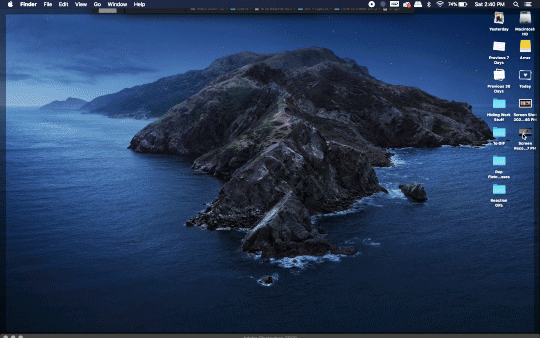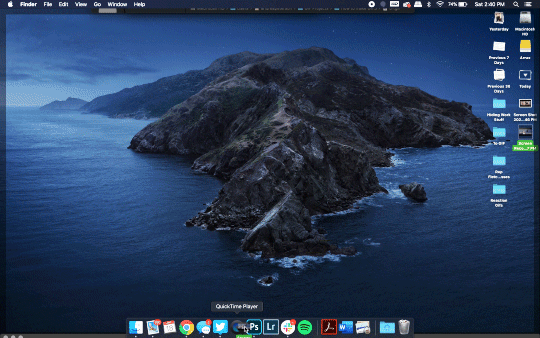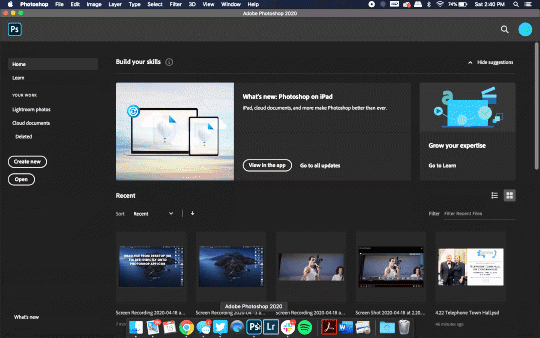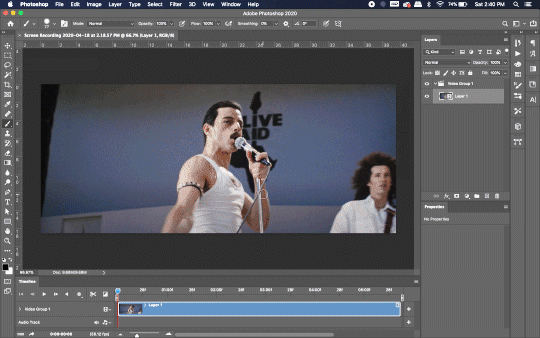
You can do this with any type of video, not just screen recordings.
Prepping, Cropping, and Resizing the Media
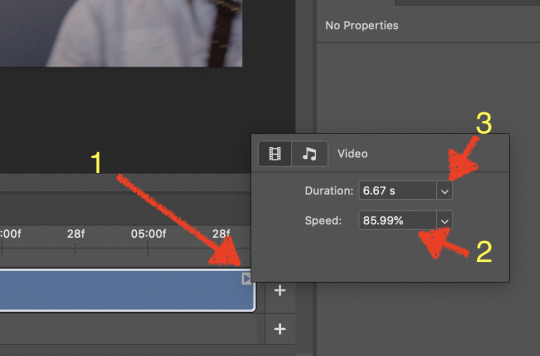
When Photoshop loads your videos up, it makes the video hilariously fast (something about frame conversion). You must slow it down for it to look natural. THIS MUST BE DONE BEFORE YOU RESZE. Your Photoshop timeline window should be at the bottom of the screen. See that little triangle in the top right of the video?
Click on it, and a menu will appear to change speed and duration.
Change the speed first- usually between 80-85% will seem realistic. (I actually went a little faster than I usually would on this at almost 86%—I don’t recommend this)
Press the button next to duration and pull the toggle all the way to the far right (if you don’t do this, full length of the video will be cut off).
Now you’ll want to crop it. Ever since Tumblr upped its GIF size limit, I have been playing around with 7:5 ratios, but let’s go with 3:2 for now. Use the Crop tool, pick out 3:2 in the top left (it may say 2:3, but you can switch that) and then find the most suitable spot in your gif for that. Hit enter on your keyboard.
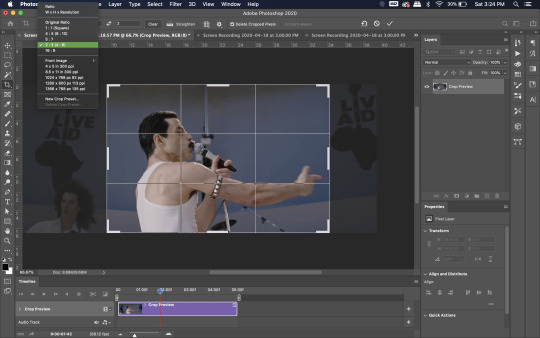
Some things to keep in mind when cropping:
Most videos come in 16:9 ratio (BoRhap is even wider). If it’s a wide shot, you’ll need to do the full 16:9 to not lose anything. Of course, experiment and find what’s right for you!
As you can see above, I moved forward in the timeline and made the crop to a point in the video when the broadest movement was happening.
Certain videos WILL have a black or red bar that may be imperceptible until you’ve already exported the gif. Just crop in a little tighter on top and bottom to avoid them.
Now you’ll need to resize your gif to be the correct size for Tumblr. If you don’t use Tumblr’s exact dimensions, your gifs (as uploaded) will appear blurry or pixellated. We’re doing a full-width gif here, which is 540px. On a Mac, I use Command+Option+I (for “Image Size) to open the resize dialogue. You can also find it under Image->Image size...
Make sure to also have “Resample” checked. Lately I’ve been playing around to see if different options are better. Most GIF makers use “Bicubic Sharper (Reduction)” and they are not wrong to do so. I’ve just been unhappy with it lately, so I have been trying this other setting out, “Bicubic (smooth gradients)”.
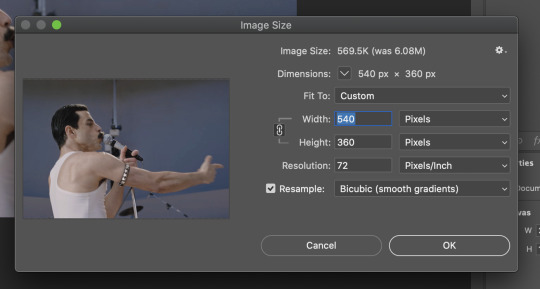
Click OK. A dialogue may come up that asks if you want to convert to a Smart Object. The answer is yes, okay, do it. The only major caveat is that you can’t go back and change the timeline speed. That’s why we did it first. But you can preview the speed now that it’s smaller, and if you don’t like it, use Command+Z (or “Undo”) and go back a couple steps to get the speed you like.
You may find, especially on a Mac screen (and possibly other displays), that at 100% your gif looks too small to be 540px. That is the curse and blessing of working with super-high resolution hardware. Zoom in to 200% and proceed about your business. This is what it will look like on Tumblr.
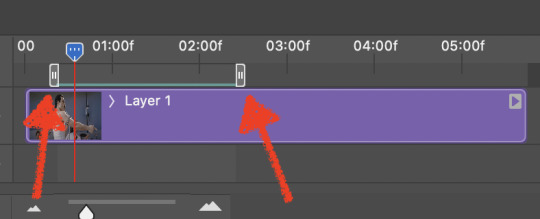
You may find it helpful at this point to begin by defining the beginning and end of your gif by moving around these bumpers. It’s safe to keep gifs under 02:00f in length. Under half of 01:00f will be way too short. (I tend to overshoot in length and then trim the beginning and the end once I see how big the gifs are upon exporting.)
Adjustment Layers
Now the creativity and fun begin!
There are a LOT of ways to get creative here. I’m going to keep it simple, very simple, but I strongly recommend opening up a new adjustment layer of each type and trying to figure out what each does!
You’ll find the adjustment layer menu at the bottom of the Layers window.

Curves
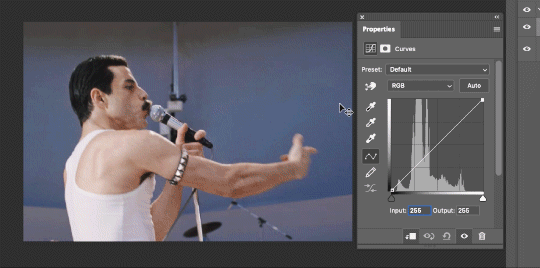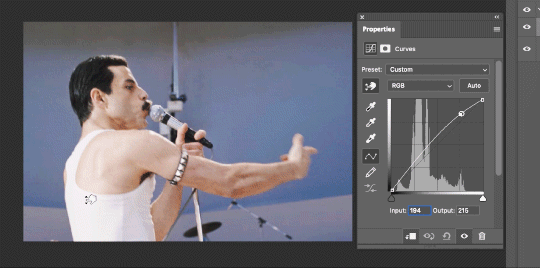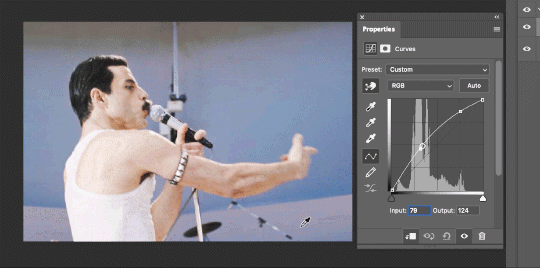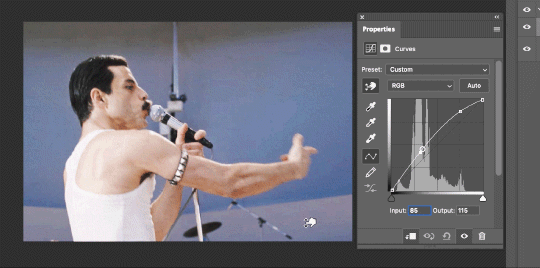
There are a lot of ways to make Curves work for you! It can do the job of Brightness/Contrast, it can do Levels, it can do Color Balance! We’re going to use it mainly to help with brightness here, but also to level out some of the tones. One of the quick tricks you can do is use the droppers on the left side of the Properties window. There are three- one with a white tip, one gray, one black. These can help define what your white tones are (and whether they need to be more of one color or another), and so on with your blacks. Sometimes it works, sometimes it doesn’t; in this case, I think it doesn’t:

That looks totally blown out and somehow also too dark!
So instead, we’re going to use that little hand with the finger pointing out and some arrows pointing up and down. This lets you define which sections you want to get brighter or darker, and how much. It doesn’t do color correction. In the example below, you can see I dragged up on a white spot and down on a dark spot. Then, I moved points around on the curve itself to refine (which the gif here doesn’t show...).
Vibrance/Saturation x2
Next, I’ve been using @gwil-lee‘s Vibrance/Saturation trick (I know you said you learned it from someone else, but I learned it from you!).
Create a Vibrance Adjustment layer, bump the values up a bunch, and then change its Fill to somewhere between 2-9%. Change the Blend Mode to Color Burn. Then make a copy of that layer keeping everything the same, but make it Color Dodge. I can’t quite define what these do, but it makes it punchier!

Color Balance
Most people are familiar with this. For this gif, I’m going to make the shadows more Cyan/Blue and the highlights more Red/Yellow. Just a few points each.
Exposure
I brought the Exposure up a bit, but not enough for you to need to read about, haha.
Selective Color
Here’s where you make fine adjustments to colors. This particular scene is extremely simple, color-wise, so keep it simple. I’m going to bump up the cyans/blues, take up the black by just a point or two, and maybe bump up the yellows and reds a tiny bit. (And as always, remember, the “opposite” of cyan is red, the opposite of magenta is green, and the opposite of yellow is blue. CMY/RGB!)

I think at this point I’m going to call it with the adjustment layers. You can go absolutely hogwild with more of them! But at this point, I’m ready to start sharpening!

Sharpening
I do three sharpening filters these days. These are all under Filter->Sharpen. Make sure your media layer (default called Layer 1) is selected as we go through this! (Also, this can really take a toll on your processor, so don’t say I didn’t warn you.)
Sharpen- This layer does the basic job
Smart Sharpen (Amount: 10%, Radius: 10, Reduce Noise: 4% Gaussian Blur)- This layer gives texture
Smart Sharpen (Amount: 500, Radius: 0.3, Reduce Noise: 12% Gaussian Blur)- This layer gives refined sharpening and smoothing
Fiddle with these as needed! Let your gif play all the way through- this may go slowly as your processor works on it. Make sure the beginning and end points make sense.
Exporting
After You’re going to have to use File->Export->Save For Web (Legacy)... or use the shortcut of Shift+Option+Command+S. This could take some time for the dialogue to pop up! Be patient.
In my opinion, these are the best gif export settings for crisp edges and no noise:
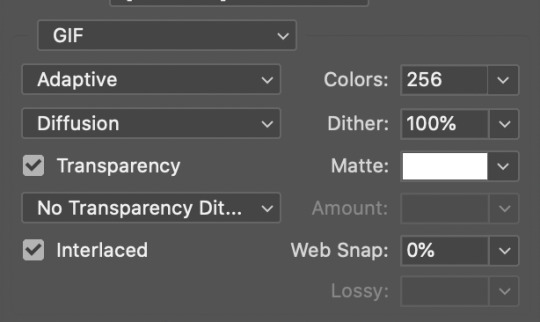
Now you see how big the file is in the bottom left. Tumblr won’t let you upload anything bigger than 10MB and it’s safer to stay under 9MB, in my experience. When your gif is too big, you have a couple options. You can close the dialogue and change the length of your gif.
OR, you can uncheck “Interlaced” and bump up the lossy to 1 or or more. This will create noise. Sometimes, that’s a good thing!
Here’s without lossy:

Here’s WITH lossy: (Honestly in a fast moving gif like this, it’s almost imperceptible, but I can see it!)

And now that I’ve exported, I can see what there’s a little black line on the bottom! So I’m going to trim that off and call it good! You can see the full gifset here.
Hope you enjoyed! Reblog if you try this out or learned anything. Feel free to reach out with questions any time!
417 notes
·
View notes
Text
Free Hard Drive Data Recovery Advice
There are certainly a lot of things that data recovery company do outside of simple hard drive data recovery. For one, they provide a lot of technical support, often for free to people who have experienced data loss. A basic fact of life is that most data loss situations are very recoverable and are logical in nature, meaning that they have more to do with file system and software errors than anything. Most hard drive recovery companies employ technicians that know exactly when a data loss will require a physical, or logical recovery. All it takes is a few symptoms to be listed, and these technicians understand the problem. So really, they often offer free technical support with very little in return. This is because hard drive recovery companies typically do not bother with recoveries that are logical. Instead, they will typically recommend to the customer a good data recovery software package in order to return their data. Plus, they provide advice that is very helpful.
Mac Hard Drive Data Recovery Software
There are a number of different mac hard drive recovery software programs available on the market. Such systems are built to aid in the recovery of your lost data. The process for recovering information is relatively simple, as all that is required is a scan of your system in order to locate the missing files. Even though the process is simple it is important to ensure that the software that you have chosen will work with the files and the devices that you are currently using. It is also important to ensure that the software is user-friendly and, that it does not have any complicated functions; because this will involve the user having to perform extended amounts of time on researching how to use the program. You will find the program easier to operate if it has a well written manual to guide you along the way if you do happen to run into any problems.
Mac Hard Drive Data Recovery for Your System
Mac hard drive recovery can be a little more difficult to achieve then when performed on a regular PC. It is important to think about getting professional help in order to aid in the data recovery from your Mac computer. Technical expertise is particularly important when there is physical or mechanical damage. Before taking it to a repair shop ensure that they are qualified to deal with a Mac computer.You should turn your system off the moment that you realize there is a problem with your system. If you continue to work on your computer, you run the risk of making the problem worse. This is why it is important to take action immediately.The most important issue is not to attempt to rectify the problem by yourself if there is any physical damage; you should immediately take your computer to a trained professional. You must ensure that you choose the right expert. If you do not you run the risk of damaging your computer even further.
6 notes
·
View notes
Text
The Freedom of Expression Ep 14 - The Party To Protect The People From The NHK (N Koku Party) commences "Same sex, same name stealth operation".
K: Hi this is Dir en grey's Kaoru, starting this episode of The Freedom of Expression. Joe san, Tasai san, welcome....Well, recently, who knows whats really happening?
J: Yeh, its troubling. I've been spending a lot longer looking at my phone and computer. I've been getting a lot of coupons. My favourite shops or brands are all going online...well, no ones going into the shops, so they can only sell online. So i've been getting coupons like, if you spend over a certain amount, you'll get 20,000yen off.
T: I see.
J: I think like, 'Waa, I wanna spend!'..but then I think, actually since April, I've had less work so I need to restrain myself. I experience this conflict every day for about 15mins. Like, whats wrong with me?
T: I see.
J: Thats thier strategy.
K: If you have free time...
J: Thats it.
K: You'll end up spending money.
J: Normally, they have expirations, and I just think 'Aghh', so its really...
K: You can't help buying stuff, right?
J: I do end up buying stuff!
K, T: *laugh*
J: I really do! I bet there are people out there addicted to coupons! Aren't you? Are you ok?
K: Well, im ok. I just shop by mail order.
J: Ahh
T: I see
J: People are shopping like that a lot right now.
T: Hiranabe san, who works at our place, he's got a lot of offers from night time establishments, and he's troubled as to what to do.
J: Oh, to get him to go there?
T: Yeah. He got an unprecedented amount of messages.
K: (quietly) Unprecedented?
T: Like, 'please come, please come, please come'.
K: He only gets them now? Cause he'll be quick to spend.
J: How is Hiranabe san doing?
T: Well, as expected, he seems scared. He's in his 50s, it looks like he finally understands that his life might be in danger if he caught the virus. He wears a mask, he wears pollen protection glasses. When he goes outside he's like..'the virus won't get in my eyes'.
J: Sounds like a terrorist! Thats just like him.
T: He flipped 180°. He used to be the guy who says, 'Im not wearing a mask'.
J: Oh, really?
T: He's that different now.
J: Well, Im a similar age to Hiranabe san...
T: I can't believe it!
K: I can't believe it.
J: So, what was it?..Its risky, if you are over 50 its more dangerous?
K: Ohh right, yeah.
J: If you catch it, there's a higher death rate at this age?
T: Also, men are more at risk, right?
K: Yeah.
T: They are saying the death rate is higher for men.
J: Well, we are among that group. Shall we get on with the main topic? I thought we'd go with a topic that is unrelated to corona this time.
' "N Koku Party's 'same name, same sex' stealth strategy for Shizuoka no.4 district Lower house by-election". With the death of Mochizuki Yoshio, the LDP's former environment minister, candidates standing for election are the LDP's Fukuzawa Youichi, an independent group of the unified opposition's Tanaka Ken, independent candidate Yamaguchi Kenzo, and the Party Against the NHK (N Koku Party)'s Tanaka Ken, whose name is the same as the unified opposition's candidate. N Koku's Tanaka Ken uses the same kanji, and has the same reading as the unified opposition's Tanaka Ken. The opposition parties, electoral commission, and local media are racking thier brains about it. If a vote is for 'Tanaka Ken', there will be no way to distinguish between the two. Its a proportional division system, so ambiguous votes will be split according to the overall percentage of votes. The electoral administrative committee have taken measures to change the rule that makes a ballot paper invalid if it includes anything other than a candidate's name, to allow a candidate's age to be written aswell. As a result of this, with the aim of reducing ambiguous votes, the unified opposition are promoting 'Tanaka Ken - Age 42' in thier election cars, posters, and online in order to attract votes. On the other hand, N Koku's Tanaka Ken surprisingly hasn't taken any action. He has refused pre-election interviews with the media, hasn't published an campaign bulletin, he doesn't appear in election posters, he has no plans to visit the area. There are expected to be people voting who are unaware that two Tanakas are standing for election. As for N Koku's aim, their leader, Tachibana, had this to say.."We want to test how the votes will be split when there are candidates with exactly the same name. We are not appealing for votes either online or on the ground. We are a weak political party, and want to know how we stand *1'.
There's also suggestion of running another female candidate named Koike Yuriko for Tokyo governer. I thought we could talk about this kind of same name/sex disturbance strategy which the N Koku party has set up.
T: Its amazing, isn't it?
K: So are they doing it to siphon votes?
J: It seems like it, yeah. Especially, that would be the aim if it was for Tokyo Governor.
T: They said they wanted to test how the votes would be split, so like you said Joe, for Tokyo Governor, if it was someone else called Koike Yuriko, they would want to get the data of how the votes are split.
J: Well, its not about freedom of expression, but there is nothing illegal about what they are doing in terms of the election, so its totally ok for them to do this. What do you think, Kaoru?
K: Well..*laughs*, even if you ask.....its interesting but...how will it end up? But, well, hmmm...its fine, isn't it?
J: As it happens, I've been on a radio event with Tachibana san once. And also...well, in this kind of election, a candidate who no one is expected to vote for is called a bubble candidate, the most famous example is Mac Akasaka. I've worked with Mac Akasaka before, so I've listened to what these kind of guys have to say. I mean, certainly, these guys are laughed at and made fun of a lot, but apart from the question of what Tachibana Takashi is doing, to be a candidate for Tokyo Governor, you have to pay a deposit of at least 3 million yen. And if you recieve under a tenth of the total valid votes, you have to forfeit your deposit. The Tokyo Governor elections get about 5 million votes, so if you get under 500,000 votes, you will lose your deposited 3 million yen. As for national elections, the deposit is 6 million yen. So you can call it a prank all you like, but they are spending a lot of money to do this. What a lot of bubble candidates will tell you is, its not free, so they are doing this with the intention to win, they do think thier ideas will improve the country, improve thier party. If there was no financial risk, it would end up at the level of annonymous postings on SNS. But after they've actually paid money, most of them will start electoneering. Making election posters costs money, and there's the cost of gas to run a car to go handing out flyers, and all sorts of things like that. It will end up costing another huge chunk of money in election costs. So in doing this, there is another side to these guys other than, 'they are just idiots'. Maybe they are trying to get people to change the way they see elections, instead of just routinely voting for the faces they know.
T: Well this case has great advertising effectiveness.
J: It does, yeah.
T: Tachibana san's name has really been sold with this.
J: It has.
T: Like, with his own business, and on you tube and stuff *2.
J: Well, as for my personal opinion, I remember Uchida Yuuya running for Tokyo Governor. You can still find his political broadcast on youtube, its great. If you compare Yuuya san to Tachibana san, honestly, Tachibana san seems to have more of a knack for it.
T: Its interesting seeing that kind of political broadcast on NHK. ????*3
J: Well, even in times such as these, we are still having elections. From now on, due to corona we'll probably see new ways to vote and new ways to do all sorts of other things.
K: Its created a need to re-think things, like with the custom of personal seals...in Japan there's a big custom of 'You have to do it this way', or 'You need it on paper'.
J: Yeah, as you mentioned Kaoru, the custom of using personal seals...in the end, even Japan's IT minister also stands as the head of the organization to retain personal seals. Somehow in Japanese society, one of the things companies insist on is the personal seal. There are those who ask why they can't just settle things digitally, but if the minister responsibile for advancing IT is also the head of a group advocating to retain the personal seal, there is a clash going on now. This is the kind of time to think about changing the political system.
T: Things would change a lot if we switched to online voting.
J: They would change, yeah. If young people started voting a lot online...
K: Yeah, right now, in the situation we have now, I think people are starting to think about future.
J: Yes, in that respect, although its very difficult with corona around, I feel like we are starting to wake up to the things we have just put up with till now. I mean, what comes next? In particular, with coronavirus, a lot of countries' governments have taken on huge powers, and in some countries its almost like a corona dictatorship. So, its very difficult, but we really need to slightly re-think the way we carry out elections and the way the state operates from now.
T: We, ourselves are a part of it, right?
J: Yes, yes...Yep, so, same sex, same name...it even hard to search for him. I wonder what this candiate actually intends. ?????*4
K: He's not showing his face much.
J: What will he do if he wins? ...Eh? Hello??
K: Is he sleeping?
Kami: Yes, yes.
J: Were you asleep, Kami?
Kami: No, I was waiting till you called on me.
J: Oh, you were waiting? Oh, sorry.
Kami: I've had a thought.
J: Oh, have you?
Kami: I have...Um, Joe should run for the N Koku Party.
J: *laughs*
K, T: Ohhh
J: Me?!
T: Thats a good idea.
J: Would it be ok, though?
T: In the Tokyo Governor election.
J: In the Tokyo Governor election? Which election?
Kami: It would be ok, yeah.
J: Would it?
Kami: Yeah, anything is ok.
J: *laughs* You couldn't participate in the election could you, Kami? You don't have voting rights?
Kami: No, I don't, but instead, I can make myself into substance.
J: What?
Kami: By pretending to be a citizen.
T: Prentending to be a citizen?
J: Oh, is that it?
K: So that means you could pile up votes for someone?
J: Right?
Kami:...No, I can only do it once.
J: Oh, so you can only take on substance once?
Kami: Yeah, yeah...a bit like Devilman.
T: Ah, like Devilman.
J: But if you could do that, surely you'd be able to do it will two or three people? I feel as if you've just made that up.
*K laughs*
J: Did you just make that up, Kami?
Kami:...Yes, I did.
K: *laughs*
J: He did.
K: I feel like his heart hasn't been in it for a while now.
T: *laughs*
J: Kami, has your mind been elsewhere?
Kami: Ye...uh, no no no.
K: He said yes!
J: *laughs*
Kami: Crush the NHK.
J: Yes, crush it.
K: Well, on that note, I think we can finish here. Thank you, please tune in next time. Please subscribe, thank you very much.
J: Please do.
Kami: Vote for Joe!
*1 I think the confusion arises here, because rather than ticking a box, Japanese voters have to actually write down the name of the person they are voting for.
*2 Think thats what he meant.
*3,4 Couldn't catch these bits.
19 notes
·
View notes
Text
Haven DVD Commentaries - 5.20: Just Passing Through
Commentary with Colin Ferguson, director for the episode (and also plays William), and Sam Ernst and Jim Dunn, co-creators of the show and writers for the episode.
The sound quality isn’t great on this one, so there’s no guarantee how accurate most of this is. Also I’m not sure I can tell Sam and Jim’s voices apart :/ But this is what I got from it:
Hilariously, they started the commentary and got five minutes in before they realised they were on mute and had to start again.
This was shot in six days. Most of the season was two episodes per director, but this was just the one. Some discussion about how this was a lot of stuff to get done in only six days.
Colin says being a director after having already acted in the show makes the directing easier because you are more familiar with the show and the process and how everyone works. Sam asks about how different it is because as an actor you don’t really get asked for your opinion on what everyone else is doing, but as director you have to have an opinion on everything.
Colin talks about how Emily had injured her knee the week before - she could barely walk on her own, which is why she is clinging on to all the actors she’s in scenes with. And so not only was this a short timescale to film the episode in, but Emily had to take time out to go get an MRI or physio.
They talk about how you can’t really lose Emily because then you’ve got no show, and Sam talks about the first season how she was straight into it and she’s in every scene. He’s impressed with how Emily knew all her lines (and Lucas his as well), even though she had so many of them to learn and they don’t always make a lot of sense when you’re shooting out of order and stuff.
Colin talks about this as the big episode with the ‘unveiling of the Colorado Kid sequence, and what happened and how it went down’. Jim says the very first thing they shot for the show was the Colorado Kid newspaper photo, and it was difficult because it was a freezing cold day but it was supposed to be taken in April so they had to try and get shots in between the sleet and warm up in between. Colin talks about how then six seasons later they basically have to re-create that photo with everything exactly the same, because it’s such a key part of the show. Jim talks about how at some point in season one they realised “it’s a photograph, but there’s a photographer IN the photograph” and how does that work; “I suppose the photographer should not have actually been in the shot”. But then they used that guy in an episode, and Colin says they have someone behind the photographer to keep the photographer in the shot.
Colin talks about the police station set and how the last episode was the zombie episode with stuff getting smashed up and now at the beginning of this episode they need to establish that it’s 2015 (“or whatever year it is, I know they’re a little off”) and there’s no one there to do that with because there aren’t any uniformed police around any more. Jim says that’s likely to be more of an issue when you come back to the present again.
They all laugh at Vince’s “this is what I wore back then” and Sam describes Richard Donat as a hippy in real life.
Jim says the nice thing about filming a time travel episode in Nova Scotia is that large chunks of it don’t feel like they have changed much in decades - and the police station set has that look too, that most of it would have been the same. Colin says the Nova Scotia maritime style is so established now it will never change.
The outside shot of Duke’s motel is stock footage. They had Eric on set for one day to film all of the stuff in the motel room.
Some of the scenes with Lucas and Emily on the beach were shot later with another director. Colin had time to do everything else except the most interesting emotional parts with those two so he had to leave that to someone else. So he’s going to be watching those scenes for the first time here.
They joke about the lights and effects to imply the helicopter landing outside, how they had to fight to include that because an actual helicopter was out; “It’s just wind; can we afford wind?”
Colin says for casting the motel scenes they went local, so all of the others apart from Eric are local Halifax actors. Sam jokes he can’t believe there are any left that they haven’t used on Haven already.
Colin talks about re-creating the Colorado Kid photo, how all of the actors are obviously five years older, so they had to re-cast the kid. He says that when they asked one of the guys in the background if he could come in he said; “Not only can I come in, I still have those jeans!”
With Vince and Nathan appearing in 1983 and the kid taking their photo, Colin talks about how every time he took a photo, none of them came out - all the film was out of date or whatever - except for one shot that he took. “And it was perfect, and it’s the one we used. It was perfect - it was amazing. We got so lucky. And then we signed it and gave it to him at the end.”
They talk about how great the police station set is, how one of the first notes they got back from the network in season one was how great the lighting was, how moody it is and how counter that is to what you see in a lot of TV police stations where everything is clean white lines, loads of technology and bright lighting.
They talk about how good the actor playing the younger Garland is, and how it’s great casting in that he looks just like him. Colin says all of the Toronto actors they brought in for this episode were great.
Colin says it must seem like so long ago for Sam and Jim since they wrote this, and Sam (I think?) talks about how stuff always changes between the script and the final product and that’s fine, but how they’re used to seeing it through to the end but here “we had to leave because we were working on something else.” So he can see the little differences that are new “either for production reasons or because someone had a good idea”. So he’s trying to enjoy those changes while also remembering the earlier versions.
Colin talks about how one of the problems pre-production was finding cars for the outside shots that would fit with the time period. It was really difficult to find any locally and they only managed it at the last minute. They wanted to use one of the classic cars they used in an earlier season, but it wasn’t practical to get it for one episode.
Sam comments on the younger Garland with his cigarette; “I like that he’s smoking, that’s great.”
Colin talks about the old Mac computer that’s on the other desk in Garland’s office, and how he got into a disagreement about whether they were available at this point in 1983. He didn’t think it was out at this point, but he lost the argument. The release date is maybe six months before this was set so it’s a pretty fine line. Sam; “There are exactly no people who would know that. And the thing is, when people do catch us out if we get things like that wrong; they’re happy. It makes them happy to catch us out, so it’s fine.”
Sam says he was so happy they could get Steve Lund back to play James Cogan and he really enjoyed writing him. Colin talks about how they only had Steve for one day, and they were pushed for time because there was a storm on the way. They talk about how quickly things can go wrong with production because there’s so many moving pieces. And Steve is the only actor who can play that role because we’ve seen him before. “And he was great to us, he fly in on the red eye to get there, he committed to it.” Sam says they checked with him while they were writing it to make sure Steve was both available and interested “and he was extremely interested” and he’s so great they were really happy to get him back.
They all agree the casting for the younger Dave is great. And all appreciate the idea that Dave would recognise an older Vince.
Colin says that Emily had a bit of difficulty with Lucy because she said that “Lucy has only ever been who she needed to be” and she didn’t have a clear idea of her as a person. Jim says they talked a lot when they were writing it about who they wanted Lucy to be, and about how she is an unusual incarnation of Audrey in that she picked up on what was happening sooner than the others did, so she had more time to be the person who is struggling to work out what to do. Colin says Emily would have loved to have spoken to them (Sam and Jim) about Lucy before filming this. But sadly they weren’t available. Sam says he loves to talk to the actors about the characters and what’s going on with them, but that 90% of the time actors will make the right interpretation just from the script. They talk about the actors and writers being able to lean on each other and help each other, and how well that works especially when you’re a few seasons in and everyone “knows the world”. Sam remembers back to the end of season one when Emily read the script with another Audrey Parker and phoned him up upset wondering if she even had a job for season two. He says they “had never told her that the memories in her head belonged to someone else, and we did that as a conscious decision because we didn’t want her to play it as if they were someone else’s memories”.
They talk about how there was a lot of discussion about what the thinnies would look like and what the rules for them would be - e.g. how quickly do they close up again - particularly for the ones made with the Colton Trouble, as opposed to the permanent ones that Mara was looking for a while ago. Sam says that what he loves about writing scifi, you can sit around with grown adults have the most surreal conversations - and get paid for it. And that then he goes home to his wife who is a teacher and how different her work days are.
Colin talks about shooting the scenes with Nathan and Garland in the Colton house; shooting everything in one day and how they were pushed for time, and they had to do all of this conversation in only two hours. There’s a stunned response from Sam that they did all of this emotional stuff in so little time. Colin says they set up the cameras to cross shoot and would do two takes through on one angle, then repeat for the other, and the actors did maybe 1 hour 45 minutes straight performance. More impressed surprise from Sam. Colin says the Lucas and the guy playing Garland were bug eyed by the end, but happy to get it all done; “their focus was amazing. We did all eight pages of script twice, then pushed in for a closer shot and did 16 pages worth again, then pushed in closer and did 16 pages again.” He says they did a similar thing with Vince and the younger Dave with their scenes in the house; “and you actually get to work with the actors then, you get to work with the dialogue” when they’re doing the whole scene through in one go and repeating it wholesale.
Sam says that one of his favourite things about Haven is having Vince and Dave in the show, because they are these quirky old guys but also they have all this history, they’re important to the plot, they’re emotionally important - “it feels so authentic, compared to some TV shows where no one’s over the age of 34 except for one guy”. But he says he thinks that changing now, partly because Netflix only needs a million or so people to love a show, and it doesn’t matter what age those customers are.
They talk about how Nova Scotia has some great houses to film in, and how picking the location for the Colton house, Colin had to agree it with Suds Sutherland who directed the next episodes because it’s in them as well. They talk about the specifics of where people are in a scene can change with the location (e.g. Lucy was originally written as overhearing Garland and Nathan from outside the window), because you can’t always write the specifics for a location you haven’t seen yet - even thought Sam and Jim find themselves arguing over those details sometimes then anyway.
Sam talks about how it’s so exciting when there’s something they’ve written that they liked on the page and then when they see the footage it works really well and it’s so cool to see. The high of that is higher than the low of something not coming out right. Jim remembers in season one when Vince bumps into Max Hansen on the street “and you suddenly saw Vince become a bad ass” as one of those moments. Jim agrees and talks about rushing up to Nova Scotia to be there on time to see that scene filmed, because he really wanted to be there for it and how he got there just in time. Colin talks about how that kind of enthusiasm from the writers can feed through into the cast. Because the days are long and the seasons are long and if you have writers that don’t really care, you feel it and it makes it harder to care yourself about the role as an actor. Jim talks about how it can be hard, as a writer, to care, because it hurts “because you don’t want to let go of things but you have to let go of things because if you don’t nothing will get done.” Colin agrees that caring in this context is not necessarily a pleasurable thing because “writing hurts every step of the way.” Colin talks about how it can be difficult as an actor because you each first read the script at home on your own, and inevitable form pre-conceptions about it, and everyone forms different pre-conceptions, and then when you get everyone together to read through it together - that can be a challenge because some of those pre-conceptions need to go.
Sam and Jim talk about how their least favourite production challenge is simply not having time to do something, but if the challenge is that a scene needs to be re-worked that is interesting because it’s a writing puzzle to solve, and it forces you to really look at what are the absolute essential lines and what can be cut or changed. And sometimes when you’re forced to compress or reduce something, you end up with a better scene.
Colin talks about how it’s difficult for the actors playing younger versions of established characters, because they have to be like the older versions, but not so much that it becomes a caricature, and there isn’t usually much time for discussion between them arriving on set and starting filming. You can have conversations before hand, but you can’t necessarily cover everything in the same way as when you’re not actually doing it. But they did really well.
They talk about how lucky they were to get a sunny day for filming the beach scene with the Colorado Kid, because there was a storm on the way. And how a stormy day might have looked great, but would have taken three times as long to shoot.
Sam talks about how him and Jim knew from the very beginning that the woman in the Colorado Kid was not Audrey’s mother (as Audrey assumed) but effectively Audrey herself. Colin is impressed that them keeping that secret for a whole season. Sam talks about how they expected the fans to figure it out, how they were keeping an eye on the discussion boards waiting for someone to suggest it and they were pleasantly surprised when no one did.
Sam comments that the ratio between how goofy Lucas Bryant is as a person and how serious his is a Nathan Wuornos is “so incredibly high”. Colin agrees Lucas is the furthest from his character, and that he really liked the alternative universe version of Nathan as a doctor because that version of him was closer to Lucas Bryant.
Colin talks about how he had to get them to buy a longer lens to film the beach scenes, to get the long perspective shots to show the distance that you need for that shot. He says it was fun to reverse engineer James Cogan’s death scene so that he ends up in the right place to match the original photo. And how they wanted to have a wider shot when Croatoan (in Dave) is affecting everyone’s memories, but they couldn’t show too much of the area because there were modern cars there and they didn’t have the budget available to buy up the whole street and clear everyone out.
Colin comments that he thought it was cool that with Nathan going back in time and telling the kid where Duke hid the stuff he stole, the kid was able to get his better camera back, and take the Colorado Kid photo. So Nathan is a part of that photo too.
Colin talks about how they spoke to the actor playing the younger Dave, specifically in relation to when he’s possessed by Croatoan, to tell him who Croatoan is and what’s going on with that whole plot line so that he could reflect that in his performance. Sam and Jim figure that is the kind of thing fans pay attention to. Colin comments how frustrating it is to be an actor in that position of not having the full story of why your character is doing what they’re doing.
They talk about how you have to try not to get attached to character names when you’re writing new characters, because the names don’t always make it through the process of getting cleared by everyone they need to get cleared by. But that Audrey Parker is named after Sam’s daughter, and his other daughter is Lucy. And Duke Crocker is a good friend of Sam and Jim’s who performed Sam’s wedding ceremony together with Jim. So some character names matter to them more than others.
7 notes
·
View notes
Text
How to Connect Cricut to Computer: A Guide for Windows/Mac
Do you want to use a Cricut machine with a computer? In that case, you will have to connect Cricut to computer. Connecting a computer and the crafting machine is not a difficult task. If you don’t know how to do it, you can learn it very easily. In this blog, I am going to guide you in connecting your Windows and Mac computers to your machine in an easy and simple way.
Cricut offers amazing crafting machines for making beautiful projects at home. With the help of the machine, you can create thousands of crafts. Cricut has multiple machines, and you can choose any one of them. To use a machine, you need to download the Design Space on your computer. The app has thousands of free designs, images, and fonts that you can use for your projects.
What Are the Minimum System Requirements for Cricut?
If you want to connect your Windows or Mac computer to your machine, before learning how to connect Cricut to computer, you should learn about its compatibility. If your computer does not have the required specifications, you will not be able to use the machine. Your Windows and Mac computers need these features for the Design Space software.
How to Connect Cricut to Computer (Windows)?
After learning the system requirements on your computer, you can move on to add your machine to your desktop. A Windows computer is great for connecting to your machine. To pair the PC to your crafting machine, you have to follow the steps below:
How to Connect Cricut to Computer (Mac)?
When it comes to connecting a computer to a machine, then a Mac is a great computer. But before connecting it to the machine, just like on Windows computers, you should check the compatibility on Mac as well.
The process for connecting a Mac system to the machine is here:
Conclusion
This blog helped you learn how to connect Cricut to computer. In order to use any machine, you need a device to connect the machine to it and download the Design Space app. The app is available for Windows and Mac computers, so you can use any of the two devices with your machine. Here, I wrote the connection process for both computers and which one is your device you can connect to the machine. But before that, you should make sure that your computer has compatibility with the Design Space app.
FAQs
What Is the Best Method to Connect Cricut to a Computer?
It will depend on the type of device you are using and the kind of connection you want. If you are using a desktop and want a stable connection where you don’t have to connect and disconnect them often, you should use a USB cable for the connection. But if you are using a laptop and want more flexibility with the connection, you should connect Cricut via Bluetooth. Bluetooth will give you the freedom to move while working on the laptop.
How Can I Connect Cricut to a Phone?
If you have an Android or iOS phone and you want to connect it to your machine, you should follow the steps below:
Why Is My Cricut Not Connecting to My Computer?
There are a few reasons why your machine is not connecting to a computer. If you want to fix them, first, check whether your machine is ON or not. Without turning the machine on, you can’t detect it on your computer. Next, you have to make sure that you have turned on Bluetooth on the computer. Finally, you should check that the distance between the machine and your computer is not more than 10-15 feet. If you check it all, your connection will not have any issues.
Visit: cricut.com/setup www.cicut.com/setup login
Source: https://cricricutdesigncut.wordpress.com/2024/10/01/how-to-connect-cricut-to-computer-a-guide-for-windows-mac/
#design space setup#digital design#cricut.com/setup explore air 2 setup#cricut.com/setup#cricut.com sign in#cricut.com design space#cricut.com/register#cricut.com/create#cricut.com/seup app#www.cricut.com/seup#www.cricut.com setup#www.cricut.com/setup#www.cricut.com/setup login#cricut setup explore air 2 setup#cricut setup#cricut design space setup#install cricut explore air 2#setting up your cricut maker#cricut setup explore air 2#cricut setup on computer#cricut setup for pc#cricut design space setup#cricut design space app#cricut design space download#cricut design space login#cricut design space software
0 notes
Text
How to Download Apps from Play Store to Computer?
The world of technology is changing at a rapid pace, and it's difficult to keep up with new developments. If you are looking for ways on how to download apps from Google Play Store to your computer, this blog post will help you out! It discusses the various methods that are available for downloading Android applications on Windows or Mac computers.
How to Download Apps from Play Store to Computer?
While the Play Store provides access to numerous apps for free, there are times when you want to download an app on your PC. For example, you might have found an interesting game that is not available in your region. Or maybe, there's an app that you use frequently, but it has stopped working properly. The good news is that there are quite a few methods allowing you to download apps from Google Play Store on your computer.

Basically speaking, the first option is to download apps directly on your computer without using any other software or service. While this seems like a viable idea at first glance, it should be noted that the underlying procedure isn't as simple as it sounds. By default, all Android apps are packaged with the .apk extension. This means that you will need to unpackage them first and then install them on your PC. You can get more information about the android apps installation process through our blog site.
How to Download Android Apps from Play Store
It is important to note that most users aren't aware of how this process works, which often leads to complications. The more complex a procedure appears, the more daunting it becomes for average computer users. In all honesty, there's a reason why Google made the Play Store available on different platforms it can't be as easily accessed as before!
If you don't have any experience with the Terminal or ADB commands, you should avoid using manual methods altogether as they might make your computer unstable. There's also a risk of permanently damaging your precious data if something goes wrong.
Google Play Store Downloader App
If you want to download apps from Google Play Store without any complications, the smartest thing that you can do is to use a third-party tool. There are numerous free and paid software programs currently available on the market. Of course, not all of them will work as promised, some of them don't even do half of what they promise!
To make things simpler for you, we have selected three of the most popular Android play store downloader tools: Aptoide Apk Downloader, APKPure and BlueStacks App Player. Let's take a closer look at how each one works in practice!
Aptoide Apk Downloader & Installer
As the name implies, Aptoide Apk Downloader is one of the most reliable tools designed for managing Android applications on different platforms. The program has been used by more than 200 million users around the world; it allows you to install any application that is listed in the official Google Play Store .
The great thing about Apk downloader is that it doesn't require root access. Of course, all APK files are stored in a central repository so it's possible to download them anytime you want. This means that your installed apps will be automatically updated when there's a new version available. You don't have to worry about losing important data or features! It should also be noted that this tool is completely free to use.
APKPure
Another reliable program for managing Android applications is Apkpure . While it might not have an official website, the tool has been around for quite some time now and many people are recommending it to other users. Of course, this should come as no surprise considering that APK Pure works great on all modern Windows operating systems!
How Does this Tool Work?
Even though Apk downloader was primarily designed to help you install Android apps, it doesn't mean that you can't use it to get hold of other types of files. If you're looking for a program that allows you to grab up desktop programs or games, you will be thrilled by what this tool can do! It should be noted that APKPure works without any restrictions – you can use it as often as you want and for whatever purpose that is possible.
BlueStacks App Player
Last but not least, we have BlueStacks . This program was designed to help users install Android apps on their PCs. As such, it's a perfect tool for those who wish to manage multiple different programs on the same platform!
The good thing about this program is that it doesn't even require an official website. All you need to do is download and set it up! Of course, we still recommend that you visit the official BlueStacks page if only to read some of the app reviews written by other computer users.

How Does this Software Work?
The first important aspect worth mentioning is that BlueStacks has a built-in store where you can find the most popular Android apps . It doesn't matter if you want to download Facebook, Instagram or Clash of Clans.
There are more than one million different APKs available for free! Of course, this tool was primarily designed with computer users in mind. As such, it's not recommended to use it with phones and tablets unless you know what you're doing.
Conclusion
It's easy to install apps from the Google Play Store on your computer. Simply open up Chrome and head over to play.google.com/store/. This will bring you straight into the app store, where you can search for an app that interests you! Once it has come up in the list of results, click on "Install" which is located underneath its name and icon on the right-hand side of the screen.
To complete installation, simply hit "Accept & Download." You'll be notified when installation is completed with a notification on your desktop or laptop screen saying “Successfully installed” followed by a checkmark next to it.
1 note
·
View note
Text
5m Mathmrs. Mac's Messages

TLDR: With a bit of research and support we were able to demonstrate a proof of concept for introducing a fraudulent payment message to move £0.5M from one account to another, by manually forging a raw SWIFT MT103 message, and leveraging specific system trust relationships to do the hard work for us!
5m Mathmrs. Mac's Messages App
5m Mathmrs. Mac's Messages Message
5m Mathmrs. Mac's Messages To My
5m Mathmrs. Mac's Messages For Her
Before we begin: This research is based on work we performed in close-collaboration with one of our clients; however, the systems, architecture, and payment-related details have been generalized / redacted / modified as to not disclose information specific to their environment.
A desktop application for Instagram direct messages. Download for Windows, Mac and Linux.
Have a question, comment, or need assistance? Send us a message or call (630) 833-0300. Will call available at our Chicago location Mon-Fri 7:00am–6:00pm and Sat 7:00am–2:00pm.
5m Mathmrs. Mac's Messages App
With that said.. *clears throat*
The typical Tactics, Techniques and Procedures (TTPs) against SWIFT systems we see in reports and the media are - for the most part - the following:
Compromise the institution's network;
Move laterally towards critical payment systems;
Compromise multiple SWIFT Payment Operator (PO) credentials;
Access the institution's SWIFT Messaging Interface (MI);
Keys in - and then authorize - payment messages using the compromised PO accounts on the MI.
This attack-path requires the compromise of multiple users, multiple systems, an understanding of how to use the target application, bypass of 2FA, attempts to hide access logs, avoid alerting the legitimate operators, attempts to disrupt physical evidence, bespoke malware, etc. – so, quite involved and difficult. Now that’s all good and fine, but having reviewed a few different payment system architectures over the years, I can’t help but wonder:
“Can't an attacker just target the system at a lower level? Why not target the Message Queues directly? Can it be done?”
A hash-based MAC might simply be too big. On the other hand, hash-based MACs, because they are larger, are less likely to have clashes for a given size of message. A MAC that is too small might turn out to be useless, as a variety of easy-to-generate messages might compute to the same MAC value, resulting in a collision. WhatsApp Messenger is a FREE messaging app available for iPhone and other smartphones. WhatsApp uses your phone's Internet connection (4G/3G/2G/EDGE or Wi-Fi, as available) to let you message and call friends and family. Switch from SMS to WhatsApp to send and receive messages, calls, photos, videos, documents, and Voice Messages. WHY USE WHATSAPP. Garrick Hello, I'm Garrick Chow, and welcome to this course on computer literacy for the Mac. This course is aimed at the complete computer novice, so if you're the sort of person who feels some mild anxiety, nervousness, or even dread every time you sit down in front of your computer, this course is for you.
Well, let's find out! My mission begins!
So, first things first! I needed to fully understand the specific “section” of the target institution's payment landscape I was going to focus on for this research. In this narrative, there will be a system called “Payment System” (SYS). This system is part of the institution's back-office payment landscape, receiving data in a custom format and output's an initial payment instructions in ISO 15022 / RJE / SWIFT MT format. The reason I sought this scenario was specifically because I wanted to focus on attempting to forge an MT103 payment message - that is:
In this video I will show you where to locate the serial number on a Western golf cart. Ebay Store: Please SUBSCRIBE. Western golf cart serial number lookuplastevil.
MT – “Message Type” Literal;
1 – Category 1 (Customer Payments and Cheques);
0 – Group 0 (Financial Institution Transfer);
3 – Type 3 (Notification);
All together this is classified as the MT103 “Single Customer Credit Transfer”.
Message type aside, what does this payment flow look like at a high level? Well I’ve only gone and made a fancy diagram for this!
Overall this is a very typical and generic architecture design. However, let me roughly break down what this does:
The Payment System (SYS) ingests data in a custom - or alternative - message format from it's respective upstream systems. SYS then outputs an initial payment instruction in SWIFT MT format;
SYS sends this initial message downstream to a shared middelware (MID) component, which converts (if necessary) the received message into the modern MT format understood by SWIFT - Essentially a message broker used by a range of upstream payment systems within the institution;
MID forwards the message in it's new format on to the institution's Messaging Interface (let's say its SAA in this instance) for processing;
Once received by SAA, the message content is read by the institution's sanction screening / Anti-money laundering systems (SANCT).
Given no issues are found, the message is sent on to the institution's Communication Interface (SWIFT Alliance Gateway), where it's then signed and routed to the recipient institution over SWIFTNet.
OK, so now I have a general understanding of what I'm up against. But if I wanted to exploit the relationships between these systems to introduce a fraudulent payment without targeting any payment operators, I was going to need to dig deeper and understand the fundamental technologies in use!
So how are these messages actually 'passed' between each system? I need to know exactly what this looks like and how its done!
More often than not, Message Queues (MQ) are heavily used to pass messages between components in a large payment system. However, there are also various “Adapter” that may be used between systems communicating directly with the SAG (Such as SAA or other bespoke/3rd party systems). These are typically the:
Remote API Host Adapter (RAHA);
MQ Host Adapter (MQHA);
Web Services Host Adapter (WSHA).
Having identified that MQ was in use, my initial assumption was that there was most likely a dedicated Queue Manager (QM) server somewhere hosting various queues that systems push and pull messages from? However, due to SWIFT CSP requirements, this would most likely - at a minimum - take the form of two Queue Managers. One which manages the queues within the SWIFT Secure Zone, and another that manages queues for the general corporate network and back office systems.
Let's update that diagram to track / represent this understanding: Now I could research how this 'messaging' worked!
There are multiple ways to configure Message Queues architectures, in this case there were various dedicated input and output queues for each system, and the message flow looks something like this: Full disclosure, turns out it’s hard to draw an accurate - yet simple - MQ flow diagram (that one was basically my 4th attempt). So it’s.. accurate 'enough' for what we needed to remember!
5m Mathmrs. Mac's Messages Message
Now I had a good understanding of how it all worked, it is time to define my goal: 'Place a payment message directly on to a queue, and have it successfully processed by all downstream systems'.
This sounds simple, just write a message to a queue, right? But there are a few complications!
Why are there few indications of this attack vector in the wild?
How do I even gain “write” access to the right queue?
What protects the message on the queues?
What protects the messages in transit?
What format are the messages in?
What is the correct syntax for that message format at any particular queue (0 margin for error)?
Where does PKI come in? How / where / when are the messages signed?
Can I somehow get around the message signing?
What values in the messages are dependent / controlled / defined by the system processing them (out of my control)?
What is the maximum amount I can transfer using Straight Through Processing, without alerting the institution / requiring manual validation?
But OK, there's no point dwelling on all of that right now, I'll just clearly define what I want to do! The goal:
Successfully write a payment instruction for 500,000 GBP;
Inject that message directly onto a specific queue;
Have the message pass environment-specific validation rules;
Have the message pass sanctions and AML checks.
Have the message successfully signed;
Have the message pass SWIFTNet-specific validation rules;
What I was not interested in doing for this research - yet needed to understand nevertheless for a full attack chain was:
How to compromise the institution's network;
How to gain access to the MQ admin's workstation;
How to obtain the pre-requisite credentials.
What I wanted to 100% avoid at all costs:
The attack involving SWIFT payment operators in any way;
The attack involving SWIFT application access in any way;
A need to compromise signing keys / HSMs;
A need to compromise SWIFTNet operator accounts or certificates or any type of PKI;.
Now I had an idea of what to do, I needed to make sure I could write a raw MT103 payment instruction! Typically, even when operators write payment messages using a messaging interface application like Alliance Access, they only really write the message “body” via a nice GUI. As raw data this could look something like:
I'll break this down in the following table:
NameFieldValueTransaction Reference20TRANSACTIONRF103Bank Operation Code23BCRED (Message is to 'credit' some beneficiary)Value Date / Currency / Amount32A200102 (02/01/2020) GBP 500,000.00Currency / Original Credit Amount33BGBP 500000,00 (£500,000.00)Ordering Customer50KGB22EBNK88227712345678 (IBAN) JOHN DOE (Name) JOHN'S BUSINESS LTD (Line 1) 21 JOHN STREET, LONDON, GB (Line 2)Beneficiary59KFR20FBNK88332287654321 (IBAN) ALICE SMITH (Name) ALICE'S COMPANY (Line 1) 10 ALICE STREET, PARIS, FR (Line 2)Remittance Information7012345-67890 (essentially a payment reference)Details of Charge71ASHA (Shared charge between sender and receiver)
Now as this is a valid message body, if I were targeting a payment operator on SWIFT Alliance Access, I could - for the 'most' part - simply paste the message into SAA's raw message creation interface and I'd be pretty much done. With the exception of adding the sender / recipient BIC codes and most likely selecting a business unit. However, these values are not stored in the message body. Not stored in the message body you say? Well that complicates things! Where are they stored exactly?
The message “body” is referred to as “block 4” (aka the “Text Block”) within the SWIFT MT standard. As suggested by the name, there is probably also a block 1-3. This is correct; and these blocks are typically generated by the payment processing applications - such as SWIFT Alliance Access - and not necessarily input by the operators. A 'complete' MT103 message consists of 6 blocks:

Block 1 – Basic Header
Block 2 – Application Header
Block 3 – User Header
Block 4 – Text Block
Block 5 – Trailer
Block 6 – System block
So it looked like I was going to need to learn how to craft these various “blocks” from scratch.
Block 1 (Basic header)
Reading through some documentation, I crafted the following “Basic header” block:
A breakdown of what this translates too is as follows:
NameValueContextBasic Header Flag1Block 1 (Not 2, 3, 4, or 5)Application TypeFFIN ApplicationMessage Type0101 = FIN (I.e not ACK/NACK)Sender BICEBNKGB20EBNK (Bank Code) GB (Country Code) 20 (Location Code)Sender Logical TerminalATypically A, unless they are a significantly large institution and require multiple terminalsSender BranchXXXAll X if no branch neededSession Number0000The session number for the messageSequence Number 999999The sequence number of the message
Taking a step back, I already identified two potential problems: the “session” and “sequence” numbers! These are described as follows:
Session Number – Must also equal the current application session number of the application entity that receives the input message.
Sequence number – The sequence number must be equal to the next expected number.
Hmmm, at this point I was not sure how I could predetermine a valid session and/or sequence number - considering they seemed to be application and 'traffic' specific? But there was nothing I could do at the time, so I noted it down in a list of 'issues/blockers' to come back to later.
Block 2 (Application Header)
A bit more dry reading later, I managed to also throw together an application header:
Again, I’ve broken this down so it makes sense (if it didn’t already; I’m not one to assume):
NameValueContextApplication Header Flag2Block 2I/O IdentifierIInput Message (a message being sent)Message Type103103 = Single Customer Credit TransactionRecipient BICFBNKFR20FBNK (Bank Code) FR (Country Code) 20 (Location Code)Recipient Logical TerminalXAll General Purpose Application Messages must use 'X'Recipient BranchXXXAll General Purpose Application Messages must use 'XXX'Message PriorityNNormal (Not Urgent)
Awesome! No issues crafting this header!
Note: At this point I should probably mention that these BIC codes are not 'real', however are accurate in terms of in format and length.
Block 3 (User Header)
The third block is called the “User Header” block, which can be used to define some “special” processing rules. By leverage this header, I could specify that the message should be processed using “Straight Through Processing” (STP) rules which essentially attempts to ensure that the message is processed end-to-end without human intervention. This could be specified as follows:
However, this was not yet a valid header! As of November 2018 the user header requires a mandatory “Unique end-to-end transaction reference” (UETR) value, which was introduced as part of SWIFT's Global Payments Innovation initiative (gpi)! This is a Globally Unique Identifier (GUID) compliant with the 4th version of the generation algorithm used by the IETF standard 'RFC4122'. This consists of 32 hexadecimal characters, divided into 5 parts by hyphens as follows:
where:
x – any lowercase hexadecimal character;
4 – fixed value;
y – either: 8, 9, a, b.
This value can be generated using Python as seen below:
With an acceptable UETR generated, this is how the third block looked:
And as before, a breakdown can be found below:
NameValueContextUser Header Flag3Block 3Validation Flag119Indicates whether FIN must perform any type of special validationValidation FieldSTPRequests the FIN system to validate the message according to the straight through processing principlesUETR Field121Indicates the Unique end-to-end transaction reference valueUETR Value8b1b42b5-669f-46ff-b2f2-c21f99788834Unique end-to-end transaction reference used to track payment instruction
Block 5 and 6 (Trailer and System Blocks)
I’ve already discussed “block 4” (the message body), so to wrap this section up, I'll be looking at the final 2 blocks: Block 5, aka the “Trailer”; and block S, aka the “System” block.
Before going forward, let me take a moment to explain the pointlessly complicated concept of input and output messages:
An “input” message (I) is a message which is traveling “outbound” from the institution. So this is a message being “input” by an operator and sent by the institution to another institution.
An “output” message (O) is a message which is traveling “inbound” to the institution. So this is a message being “output” by SWIFTNet and being received by the institution.
OK, moving swiftly (aaaahhhhh!) on.
For Input messages, these blocks were not too much of a problem. The headers only really seemed to be used to flag whether the message was for training / testing or to flag if it was a possible duplicate, which syntactically took the following form:
Where “TNG” indicated “training” and “SPD” indicated “possible duplicate”.
However, with Output messages, it got considerably more complicated. An example of what the trailer and system block could look like on an Output message is the following:
A breakdown of these various values is:
Trailer ((5:) MAC – Message Authentication Code calculated based on the entire contents of the message using a key that has been exchanged with the destination bank and a secret algorithm; CHK – This is a PKI checksum of the message body, used to ensure the message has not been corrupted in transit; TNG – A flag to indicate that the message is a Testing and Training Message.
System ((S:) SPD – Possible Duplicate Flag SAC – Successfully Authenticated and Authorized Flag. This is only present if:
Signature verification was successful.
RMA (Relationship Management Application) authorization and verification was successful.
COP – Flag indicating that this is the primary message copy; MDG – The HMAC256 of the message using LAU keys.
However, these seemed to only be values I would need to consider if I was to try and forge an “incoming” message from SWIFTNet or an 'outbound' message on the output of the SAG.
So.. I'll stick with crafting an “input' message trailer:
Now, having said all that, it turned out the trailer block did seem to sometimes hold a MAC code and a message checksum (sigh), meaning I actually needed to construct something like:
So that was +2 to my 'issues/blockers' list. However, issues aside, I now understood the complete message format, and could put it all together and save the following as a draft / template MT103 message:
Highlighted in bold above are the areas of the message I was - at this point - unable to pre-determine. Nevertheless, a summary of what that the message describes is:
Using the transaction reference “TRANSACTIONRF103”;
please transfer 500,000.00 GBP;
from John Doe, (IBAN: GB22EBNK88227712345678) at “English Bank” (BIC: EBNKGB20);
to Alice Smith (IBAN: FR20FBNK88332287654321) at “French Bank” (BIC: FBNKFR20);
Furthermore, please ensure the transaction charge is shared between the two institutions;
and mark the payment with a reference of “12345-67890”.
To wrap up this section, i wanted to take a moment to explain some logic behind the target of 500,000 GBP, as it is also important.
Aside from the many reasons it would be better to transfer (even) smaller amounts (which is an increasingly common tactic deployed by modern threat actors), why not go higher? This is where it’s important to understand the system and environment you are targeting.
In this instance, let's assume that by doing recon for a while I gathered the understanding that:
If a message comes from SYS which is over £500k;
even if it has been subject to a 4 eye check;
and even if it is flagged for STP processing;
route it to a verification queue and hold it for manual verification.
This was because a transaction over £500k was determined to be “abnormal” for SYS. As such, if my transaction was greater, the message would not propagate through all systems automatically.
OK, so now that I understood:
how the system worked;
how it communicated;
the fundamental structure of a raw MT103 payment messages;
and how much I could reliably (attempt) to transfer.
And with that, it was time to take a break from MT standards and establish an understanding of how I would even get into a position to put this into practice!
To place a message on a queue, I was going to need two things:
Access to the correct queue manager;
Write access to the correct queues.
Depending on the environment and organisation, access to queue managers could be quite different and complex. However a bare-bones setup may take the following form:
An MQ Administrator accesses their dedicated workstation using AD credentials;
They then remotely access a dedicated jump server via RDP which only their host is whitelisted to access;
This may be required as the queues may make use of Channel Authentication Records, authorizing specific systems and user accounts access to specific queues;
The channels may further be protected by MQ Message Encryption (MQME) which encrypts messages at rest based on specific channels. As such, even if someone was a “super duper master admin” they would only be able to read / write to queues specifically allocated to them within the MQME configuration file (potential target for another time?);
The MQ Admin can then use tools such via the Jump Server to read/write to their desired message queues.
So, in this scenario, to gain access to the message queues I - as an attacker - would need to compromise the MQ admin’s AD account and workstations, then use this to gain access to the jump host, from where I could then access the message queues given I knew the correct channel name and was configured with authorization to access it.. and maybe throw some MFA in there..
That is understandably a significant requirement! However, when discussion sophisticated attacks against Financial Market Infrastructure (FMI), it is more than reasonable to accept that an Advanced Persistent Threat (APT) would see this as a feasible objective - We don't need to dig into the history of how sophisticated attacks targeting SWIFT systems can be.
Next, it was time to finally identify a feasible attack vector for message forgery.
Now with an idea of how to gain the right access, as well as an understanding of the various technologies and security controls in place; I update my diagram:
You may have noticed I've added something called “LAU” around the SAA-to-SAG adapter, and another “LAU” to the MID-to-SAA MQ channels, which I have yet to explain. “Local Authentication” (LAU) is a security control implemented by SWIFT to authenticate messages using a pair of shared keys between two systems. These keys are combined and used to generate a SHA256 HMAC of the message and append it to the S block. This can then be validated by the recipient system. Effectively, this validates the origin and authenticity of a message. As such, even if an attacker was in position to introduce a fraudulent payment, they'd first need to compromise both the left and the right LAU signing keys, generate the correct HMAC, and append it to the message in order to have it accepted / processed successfully.
But LAU aside, I now just needed to figure out which queue to target! There were a lot of queues to work with as each system essentially has multiple “input” and “output” queues. With that in mind, it was important to note that: an incoming message would require being in the format expected by the target system (from a specific upstream system) and an outgoing message would need to be in the format “produced” by one target system and “expected / ingested / processed” by its respective downstream system. So to figure this out, I worked backwards from the Gateway.
Targeting SAG
This was the least feasible attack vector!
I hadn't really looked into how the SWIFT adapters worked - If only I could research literally everything);
SAA and SAG implemented LAU on messages sent between them - An excellent security control!;
The output of SAG was directly on to SWIFTNet which would entail all sorts of other complications - this is an understatement)!
Next!
Targeting SAA
So what if I wanted to drop a message on the “outbound” channel of SAA?
LAU and the SWIFT adapter aside, remember those session and sequence numbers? Well, messages which leave SAA are in the near-final stages of their outbound life-cycle, and as far as I understood would need to have valid session and sequence values. Given I didn't know how to generate these values without gaining access to SAA or how they worked in general (and lets not forget the LAU signing) this didn't currently seem feasible.
Next!
Targeting SANCT
This solution didn't actually transport messages back and forth; it just reads messages off the queues and performed checks on their details. Not much I could wanted to leverage here.
Targeting MID
To target MID, I could try and inject a message onto SAA’s “input” queue, or the “output” queue of MID. This would only need to match the format of messages produced by the Middleware solution (MID). Following this, in theory, the (mistial) message session and sequence number would be added by SAA, along with the UETR. This was promising!
However, MID was a SWIFT “message partner”, which are typically solutions developed using the Alliance Access Development Kit that allows vendors to develop SWIFTNet compatible software, and consequentially, implement LAU. So again, in-order to forge a message here, I’d need to compromise the left and right LAU signing keys used between SAA and MID, manually HMAC the message (correctly!), and then place it on the correct queue.. This also no longer looked promising..
Targeting SYS
OK, how about the input of the next system down - the 'Payment System'?
5m Mathmrs. Mac's Messages To My
As described previously, the inbound data was a custom “application specific” payment instruction from the institutions back office systems, and not a SWIFT MT message. This would be an entirely new core concept I'd need to reverse - not ideal for this project.
But how about the output queue?
Although SYS received custom format data, I found that it output what seemed to be an initial SWIFT MT messages. This was perfect! Additionally, SYS did not have LAU between itself and MID because (unlike MID) SYS was not a SWIFT message partner, and was just one of many-many systems within the institution that formed their overall payment landscape.
Additionally, because SYS was esentially just one small piece of a much larger back office architecture, it was not part of the SWIFT Secure Zone (after all you cant have your entire estate in the Secure Zone - that defeats the purpose) and as such, made use of the Queue Manager within a more accessible section of the general corporate environment (QM1). Konica minolta bizhub c352 driver mac os xcompubrown recovery tool.
With this in mind, and having - in theory - compromised the MQ admin, I could leverage their access to access on the corporate network to authenticate to QM1. I could - in theory - then write a fraudulent payment message to the SYS “output” queue, which we will call “SYS_PAY_OUT_Q” from here on.
OK! It seems like I finally had an idea of what to do! But before I could put it into practice, I of course needed to create a diagram of the attack:
I think it’s important to take a minute to refer back to the concept of “trust” which is what lead to this attack diagram. My theory behind why this may work is because the MID application, implicitly trusts whatever it receives from its respective upstream systems. This is intentional, as by design the security model of the payment landscape ensures that: at any point a message can be created, a 4 (or 6) eye check is performed. If there was a system whose purpose it was to ensure the validity of a payment message at any point upstream, the downstream systems should have no real issue processing that message (with some exceptions). After all, It would be next to-impossible to maintain a high-throughput payment system without this design.
And with that said, the plan was now clear:
Leverage the access of a Message Queue administrator;
to abuse the “trust relationship” between SYS, MID, and SAA;
to introduce a fraudulent payment message directly on to the output queue of SYS;
by leaning on my new found understanding of complete MT103 payment messages.
It was finally time to try to demonstrate a Proof-of-Concept attack!
So at this point I believe I had everything I needed in order to execute the attack:
The target system!
The message format!
The queue manager!
The queue!
The access requirements!
The generously granted access to a fully functional SWIFT messaging architecture! (that’s a good one to have!)
The extra-generously granted support of various SMEs from the target institution! (This was even better to have!)
Message Forgery
I needed to begin by creating a valid payment message using valid details from the target institution. So before moving on I was provided with the following (Note: as with many things in this post, these details have been faked):
Debtor Account Details – John Doe, GB12EBNK88227712345678 at EBNKGB20
Creditor Account Details – Alice Smith, GB15EBNK88332287654321 at EBNKGB20
Some of you may have notice that the sending and receiving BIC’s are the same. This was because, for the sake of the research, I wanted to send the message back to the target institution via SWIFTNet so that I could analyse its full end-to-end message history. Furthermore, you may have noticed we are using 'test & training' BIC code (where the 8th character is a 0) - this was to make sure, you know, that I kept my job.
But yes, with access to these 'valid' account details and the knowledge gained during the research so far, I could now forge a complete Input MT103 messages:
Note: Field 33B is actually an optional field, however, the MT standard stated that “If the country codes of both the Sender’s and the Receiver’s BIC belong to the country code list, then field 33B is mandatory”. As such, if 33B was not present in the message, it would fail network validation rules and SWIFTNet would return a NAK with the error code: D49.
Optional / Mandatory fields aside, it was not quite that simple! There were a few minor changes I needed to make based on the specific point in the message's its life-cycle I was planning to introduce it!
As I list these changes, remember that the objective is to introduce the message to the output queue of SYS (Which exists before MID, SAA and SAG)
The first 3 blocks needed to be placed on a single line;
Remove field 121 (UETR) from the User Header, as this would be generated by SAA during processing;
Remove 1 character from the transaction reference as it needed to be exactly 16 characters (classic user error);
Add decimal point to transaction amount using a comma - otherwise it would fail syntax validation rules;
Ensure the IBAN's were real and accurate, otherwise it seemed the message would fail some type of signature validation on the SWIFT network. The IBANs are fake here, but during the real PoC we used accurate account details in collaboration with the target institution;
Remove the trailer block (5) - as this would be appended by SAA during processing;
Remove the System Block (S) - as this would be completed by the SAG.
And the final message was as follows:
Note that the location in which I introduce the message has resolved all of the 'issues / blockers' I'd tracked whilst researching the message structure! It would seem the further upstream you go, the easier the attack becomes - given MQ is still used as a transport medium.
Message Injection
Now I had my raw MT103 message, I just need to save it to a file (“Message.txt” - sure why not) and place onto the “SYS_PAY_OUT_Q” queue using one of the admin's tools:
With access to a sole MQ Administrator's AD account;
We connect to the MQ admins machine;
Log into the Jump Server;
Open our MQ tools of choice and authenticate to queue manager (QM1) where the output queue for SYS was managed;
Connected to the 'SYS_PAY_OUT_Q' queue;
Selected my forged “Message.txt” file;
Invoked the “write to queue” function;
And it was off!
Loggin in to Alliance Access and opening the message history tab, we sat awaiting for an update. Waiting, waiting, waiting… waiting… and..
ACK! It worked!
That's a joke; did we hell receive an ACK!
See, this last section is written slightly more 'linear' than what actually happened. Remember those 'tweaks' used to fix the message in the previous section? I hadn't quite figured that out yet..
So roughly seven NACKs later - each time troubleshooting and then fixing a different issues - we did indeed, see an ACK! The message was successfully processed by all systems, passed target system validation rules, passed sanctions and AML screening, passed SWIFTNet validation rules, and SWIFT’s regional processor had received the message and sent an 'Acknowledgement of receipt' response to the sending institution!
For the sake of completeness, I’ve included the ACK below:
And of course a breakdown of what it all means:
NameValueContextBasic Header Flag1Block 1Application TypeFF = FIN ApplicationMessage Type2121 = ACKInstitution CodeEBNKGB20AXXXEBNKGB20 (BIC) A (Logical Terminal) XXX (Branch)Sequence and Session No.19473923441947 (Sequence No.) 392344 (Session No.)Date Tag177200103 (Date) 1102 (Time)Accept / Reject Tag4510 = Accepted by SWIFTNet
Excellent! WooHoo! It worked! .. That took a lot of time and effort!
Closer Inspection
But the ACK wasn't enough, I wanted to make sure I understood what had happened to the message throughout its life-cycle. From the message I placed on the initial queue, to being processed by SWIFTNet.
Thankfully, as we sent the message back to the target institution we could see its entire message history. I already knew what the raw message placed on the queue looked like, so I wanted to focus on what became of the message once it had been processed by SAA:
The end-to-end tracking UUID had been generated and added (b42857ce-3931-49bf-ba34-16dd7a0c929f) in block 3;
The message trailer had been added ((5:(TNG:))) where I could see that - due to the BIC code used - SAA had flagged the message as 'test and training'.
Additionally, an initial System Block segment had been added ((S:(SPD:))), tagging the message as a possible duplicate. I wonder why - *cough* 7th attempt *cough*?
OK, so that was SAA. Now let’s see how it looked it once it passed through the Gateway and regional processor:
OK, we can see a few changes now.
The session and sequence numbers have been populated (1947392344);
The I/O identifier in block 2 has been updated to track that it is now an 'Output' message;
The additional data within Block 2 is a combination of the input time, date, BIC, session and sequence numbers, output date/time, and priority;
The trailer has been updated with a message authentication code (MAC) calculated based on the entire contents of the message using a pre-shared key and a secret algorithm;
Additionally, a checksum of the message body has been stored within the trailer’s “CHK” tag. This is used by the network to ensure message integrity.
I also took a look at the entire outbound message history, just to see all the “Success” and “No violation” statements to make it feel even more awesome!
So that's that really..
With a bit of research and support I was able to demonstrate a PoC for introducing a fraudulent payment message to move funds from one account to another, by manually forging a raw SWIFT MT103 single customer credit transfer message, and leveraging various system trust relationships to do a lot of the hard work for me! https://arfox158.tumblr.com/post/655263262721638400/wireless-external-hard-drive-for-mac.
As mentioned briefly in the introduction, this is not something I have really seen or heard of happening in practice or in the 'wild'. Perhaps because it clearly takes a lot of work.. and there is a huge margin for error. However, if an adversary has spent enough time inside your network and has had access to the right documentation and resources, this may be a viable attack vector. It definitely has its benefits:
No need to compromise multiple payment operators;
No requirement to compromise - or establish a foothold within - the SWIFT Secure Zone;
No requirement to bypass MFA and gain credentials for a messaging interface;
No generation of application user activity logs;
No payment application login alerts;
No bespoke app-specific and tailored malware;
And all the other things associated with the complex task of gaining and leveraging payment operator access.
All an attacker may need to do is compromise one specific user on the corporate network: a Message Queue administrator.
The industry is spending a lot of time and effort focused on securing their payment systems, applications, processes, and users to keep - among other things - payment operators safe, Messaging Interfaces locked down, and SWIFT systems isolated. But the reality is,; the most valuable and most powerful individual in the entire model, might just be a single administrator!
As always, a security model is only as strong as its weakest link. If you're not applying the same level of security to your wider institution, there may very well be many weak links within the wider network which chain together and lead to the comrpomise of systems which feed into your various payment environment.
I think the main thing to remember when reflecting on this research is that it did not abuse any vulnerabilities within the target institution's systems, or even vulnerabilities or weaknesses within the design of their architecture. It simply leverages the legitimate user access of the Message Queue administrators and the trust relationships that exist by design within these types of large-scale payment processing systems.
So the harsh reality is, there is no particular list of recommendations for preventing this type of attack in itself. However, the main point to drive home is that you must ensure the security of your users - and overall organisation - is of a high enough standard to protect your highest privileged users from being compromised. Things such as:
Strong monitoring and alerting controls for anomalous behaviour;
Requirements for Multi-Factor authentication for access to critical infrastructure;
Segregation of critical infrastructure from the wider general IT network;
Strong password policies;
Well rehearsed incident detection and incident response policies and procedures;
Frequent high-quality security awareness training of staff;
Secure Software Development training for your developers;
Routine technical security assessments of all critical systems and components;
The use of 3rd party software from reputable and trusted vendors;
However, in the context of Message Queues, there is one particular control which I think is extremely valuable: The implementation of channel specific message signing! This, as demonstrated by SWIFT's LAU control, is a good way in which to ensure the authenticity of a message.
As discussed, LAU is - as far as I know at the time of writing - a SWIFT product / message partner specific control. However it's concept is universal and could be implemented in many forms, two of which are:
Update your in-house application's to support message signing, natively;
Develop a middleware component which performs message signing on each system, locally.
This is a complex requirement as it requires considerable effort on the client’s behalf to implement either approach. However, SWIFT provides guidance within their Alliance Access Developers guide on how to implement LAU in Java, Objective C, Scala and Swift;
Strip any S block from the FIN message input. Keep only blocks 1: through 5;
Use the FIN message input as a binary value (unsigned char in C language, byte in Java). The FIN message input must be coded in the ASCII character set;
Combine the left LAU key and the right LAU key as one string. The merged LAU key must be used as a binary value (unsigned char in C language, byte in Java). The merged LAU key must be coded in the ASCII character set;
Call a HMAC256 routine to compute the hash value. The hash value must also be treated as a binary value (unsigned char in C language, byte in Java). The HMAC size is 32 bytes;
Convert the HMAC binary values to uppercase hexadecimal printable characters.
An example of how this may work in the more flexible middleware solution proposed is where the original service is no longer exposed to the network, and is altered to only communicate directly with the custom 'LAU-eqsue' service on its local host. This service would then sign and route the message to its respective queue.
When received, the core of the recipient payment service would seek to retrieve its messages from the queues via the 'LAU-esque' signing middleware, which would retrieve the message and subsequently verify its origin and authenticity by re-calculating the signature using their shared (secret) keys. Key-pairs could further be unique per message flow. This design could allow for the signing to be used as a way to validate the origin of a message even if it had passed through multiple (local) intermediary systems.
As a final bit of creative effort, I made yet another diagram to represent what this could perhaps look like - if life was as easy as a diagram:
If you made it this far thanks for reading all.. ~6k words!? I hope you found some of them interesting and maybe learned a thing or two!
I'd like express our gratitude to the institution who facilitated this research, as well as specifically to the various SMEs within that institution who gave their valuable time to support it throughout.
Fineksus - SWIFT Standard Changes 2019
https://fineksus.com/swift-mt-standard-changes-2019/
Paiementor - SWIFT MT Message Structure Blocks 1 to 5
https://www.paiementor.com/swift-mt-message-structure-blocks-1-to-5/
SEPA for corporates - The Difference between a SWIFT ACK and SWIFT NACK
https://www.sepaforcorporates.com/swift-for-corporates/quick-guide-swift-mt101-format/
SEPA for corporates - Explained: SWIFT gpi UETR – Unique End-to-End Transaction Reference
https://www.sepaforcorporates.com/swift-for-corporates/explained-swift-gpi-uetr-unique-end-to-end-transaction-reference/
M DIBA - LAU for SWIFT Message Partners
https://www.linkedin.com/pulse/lau-swift-message-partners-mohammad-diba-1/
Prowide - About SWIFT
https://www.prowidesoftware.com/about-SWIFT.jsp
5m Mathmrs. Mac's Messages For Her
Microsoft - SWIFT Schemas
https://docs.microsoft.com/en-us/biztalk/adapters-and-accelerators/accelerator-swift/swift-schemas
SWIFT FIN Guru - SWIFT message block structure
http://www.swiftfinguru.com/2017/02/swift-message-block-structure.html

2 notes
·
View notes
Text
19
Do you remember much from high school? I remember all of it!
Where would you go for the ultimate honeymoon? Somewhere warm and remote where you can escape society and just be 100% together and in the moment.
Can you access the roof of the building you live in? Nope.
Do you know anyone who has a strong accent that is hard to understand? My husband’s family is all southern and when they start talking really fast on the phone, I have a hard time keeping up. He’s good at translating though!
If you had to get a tattoo tomorrow, what would you get? The pink CareBear on my thigh.
What was the last podcast you listened to? Do you listen to it regularly? Ummm..Bailey Sarian’s new podcast! I believe there’s only one episode but I’m honestly not much of a podcast listener.
Are you more of an optimist or a pessimist, and why do you think this is? I’m a pessimist because of anxiety.
When was the last time you moved house? Last yeah!
Have you ever held a gun? Did you fire it? Nope.
Do you like simple questions or deep questions that make you think? Depends!
When was the last time you threw up? Why were you sick? 8 years ago and I was drunk off my ass.
Are you on a first-name basis with your boss? (or last boss if unemployed) I’m my own boss but yes, I was on a first name basis with my last boss.
What brand is your laptop or computer? Apple!
Would you ever wear a bright orange shirt? Of course!
What was the last thing you wrote in a word document? I was helping Beebs write up schedules.
Who do you miss and what do you miss about them? I miss my grandparents, man. I haven't seen them in like 4 years and it makes me so sad.
What were the best and worst costumes you've ever worn? My parents put 0 effort into halloween one year and so at the last minute they put one of my dad’s shirts on me and drew a mustache on. I don’t know what I was supposed to be but everybody thought I was a boy and I was not happy.
Do you know anybody who is gay and married? I don’t actually! All the gay people I know are single.
What did you last take painkillers for? I had a toothache!
Have you ever shared a home with a friend? Nope.
What's the craziest or weirdest place you've ever slept? Idk about y’all, but I sleep in a bed.
What did you have for lunch today and who made it? I made mac & cheese!
Do you believe in anything supernatural like ghosts or ghouls? Nope.
How many hours of sleep did you get last night? I stopped looking at the clock because I couldn’t sleep but like...6 hoursish?
Are you allergic to anything? How did you find out? Bananas. I’ve eaten them all my life and truly love them and then one day last year, I made myself a smoothie in the morning and I got SUPER nauseous with really bad back cramps. Was confused but I took ibuprofen and it went away after a few hours. The next day, same thing happened. Same with the day after that. And I couldn’t figure out why it was happening so I was like ‘k, it must be something I’m eating’. So I woke up and had a banana because I figured I'd play it safe. Got the same nausea and back cramps. So I skipped bananas for a few days and it didn’t happen at all. I looked into it and apparently that's a common allergic reaction. So I’ve never had them again.
What's your favourite Thai dish? I’ve actually never tried Thai food!
Do you have any alarms set? What time and what for? I have them set for every 5 minutes from 5-9 am I think, haha! My husband is hard to wake up so he sets hella alarms on both our phones and our Google home. And I set a bunch and forget to delete them later.
What are you going to do when this survey is over? Probably go sew.
Have you ever been on a date with someone you met online? How was it? I met my husband online! And they’ve all been great :)
What colour is the rug in your living area? We have carpet and I hate it.
Do you call it a couch, sofa, lounge or something else entirely? Usually a couch, sometimes a sofa.
Who is your favourite character on Friends? Chandler and Phoebe!
When was the last time you used a pair of headphones and what for? The other day I was cleaning so I had my AirPods in.
Describe the temperature of the area you're in right now. It is currently 70 and windy!
Who was the last very physically attractive person you saw? My husband :)
Have you ever had teppanyaki? I truly don’t know what that is.
How long does it take you to get ready before you go somewhere? It depends if I’m already ready or not. If I just need to get dressed, 5-10 minutes. If I need to do my hair, put makeup on, pick an outfit, and get dressed, probably like 3 hours.
Do you find it difficult to get rid of material possessions? It depends! Certain things I can look at and know I’m never gonna use it again or that I found something better to replace it but other things that are still perfectly good and I might use later? I hoard those a little bit.
What sort of games do you like to play? I like life simulators like Sims and Animal Crossing. But I also love a good board game!
What was the last candy you ate? I don’t remember!
Have you ever been hit in the face? What's the story? In the face with basketballs and dodgeballs a lot. And one time when I was like 13-14, I was crawling around after my little sister trying to tickle her and she elbowed me in the nose and made me bleed. We both cried.
Do you know anyone who is deaf? I do, actually!
Name one thing on your bucket list. Buy a house and foster a bunch of puppies.
1 note
·
View note