#aws api gateway rest api example
Explore tagged Tumblr posts
Text
AWS API Gateway Tutorial for Cloud API Developer | AWS API Gateway Explained with Examples
Full Video Link https://youtube.com/shorts/A-DsF8mbF7U Hi, a new #video on #aws #apigateway #cloud is published on #codeonedigest #youtube channel. @java #java #awscloud @awscloud #aws @AWSCloudIndia #Cloud #CloudComputing @YouTube #you
Amazon AWS API Gateway is an AWS service for creating, publishing, maintaining, monitoring, and securing REST, HTTP, and WebSocket APIs. API developers can create APIs that access AWS or other web services, as well as data stored in the AWS Cloud. As an API Gateway API developer, you can create APIs for use in your own client applications. You can also make your APIs available to third-party…

View On WordPress
#amazon api gateway#amazon web services#api gateway#aws#aws api gateway#aws api gateway http api#aws api gateway http endpoint#aws api gateway http proxy example#aws api gateway http tutorial#aws api gateway http vs rest#aws api gateway lambda#aws api gateway rest api#aws api gateway rest api example#aws api gateway rest api lambda#aws api gateway rest vs http#aws api gateway websocket#aws api gateway websocket tutorial#aws api gatway tutorial
0 notes
Text
Build A Smarter Security Chatbot With Amazon Bedrock Agents

Use an Amazon Security Lake and Amazon Bedrock chatbot for incident investigation. This post shows how to set up a security chatbot that uses an Amazon Bedrock agent to combine pre-existing playbooks into a serverless backend and GUI to investigate or respond to security incidents. The chatbot presents uniquely created Amazon Bedrock agents to solve security vulnerabilities with natural language input. The solution uses a single graphical user interface (GUI) to directly communicate with the Amazon Bedrock agent to build and run SQL queries or advise internal incident response playbooks for security problems.
User queries are sent via React UI.
Note: This approach does not integrate authentication into React UI. Include authentication capabilities that meet your company's security standards. AWS Amplify UI and Amazon Cognito can add authentication.
Amazon API Gateway REST APIs employ Invoke Agent AWS Lambda to handle user queries.
User queries trigger Lambda function calls to Amazon Bedrock agent.
Amazon Bedrock (using Claude 3 Sonnet from Anthropic) selects between querying Security Lake using Amazon Athena or gathering playbook data after processing the inquiry.
Ask about the playbook knowledge base:
The Amazon Bedrock agent queries the playbooks knowledge base and delivers relevant results.
For Security Lake data enquiries:
The Amazon Bedrock agent takes Security Lake table schemas from the schema knowledge base to produce SQL queries.
When the Amazon Bedrock agent calls the SQL query action from the action group, the SQL query is sent.
Action groups call the Execute SQL on Athena Lambda function to conduct queries on Athena and transmit results to the Amazon Bedrock agent.
After extracting action group or knowledge base findings:
The Amazon Bedrock agent uses the collected data to create and return the final answer to the Invoke Agent Lambda function.
The Lambda function uses an API Gateway WebSocket API to return the response to the client.
API Gateway responds to React UI via WebSocket.
The chat interface displays the agent's reaction.
Requirements
Prior to executing the example solution, complete the following requirements:
Select an administrator account to manage Security Lake configuration for each member account in AWS Organisations. Configure Security Lake with necessary logs: Amazon Route53, Security Hub, CloudTrail, and VPC Flow Logs.
Connect subscriber AWS account to source Security Lake AWS account for subscriber queries.
Approve the subscriber's AWS account resource sharing request in AWS RAM.
Create a database link in AWS Lake Formation in the subscriber AWS account and grant access to the Security Lake Athena tables.
Provide access to Anthropic's Claude v3 model for Amazon Bedrock in the AWS subscriber account where you'll build the solution. Using a model before activating it in your AWS account will result in an error.
When requirements are satisfied, the sample solution design provides these resources:
Amazon S3 powers Amazon CloudFront.
Chatbot UI static website hosted on Amazon S3.
Lambda functions can be invoked using API gateways.
An Amazon Bedrock agent is invoked via a Lambda function.
A knowledge base-equipped Amazon Bedrock agent.
Amazon Bedrock agents' Athena SQL query action group.
Amazon Bedrock has example Athena table schemas for Security Lake. Sample table schemas improve SQL query generation for table fields in Security Lake, even if the Amazon Bedrock agent retrieves data from the Athena database.
A knowledge base on Amazon Bedrock to examine pre-existing incident response playbooks. The Amazon Bedrock agent might propose investigation or reaction based on playbooks allowed by your company.
Cost
Before installing the sample solution and reading this tutorial, understand the AWS service costs. The cost of Amazon Bedrock and Athena to query Security Lake depends on the amount of data.
Security Lake cost depends on AWS log and event data consumption. Security Lake charges separately for other AWS services. Amazon S3, AWS Glue, EventBridge, Lambda, SQS, and SNS include price details.
Amazon Bedrock on-demand pricing depends on input and output tokens and the large language model (LLM). A model learns to understand user input and instructions using tokens, which are a few characters. Amazon Bedrock pricing has additional details.
The SQL queries Amazon Bedrock creates are launched by Athena. Athena's cost depends on how much Security Lake data is scanned for that query. See Athena pricing for details.
Clear up
Clean up if you launched the security chatbot example solution using the Launch Stack button in the console with the CloudFormation template security_genai_chatbot_cfn:
Choose the Security GenAI Chatbot stack in CloudFormation for the account and region where the solution was installed.
Choose “Delete the stack”.
If you deployed the solution using AWS CDK, run cdk destruct –all.
Conclusion
The sample solution illustrates how task-oriented Amazon Bedrock agents and natural language input may increase security and speed up inquiry and analysis. A prototype solution using an Amazon Bedrock agent-driven user interface. This approach may be expanded to incorporate additional task-oriented agents with models, knowledge bases, and instructions. Increased use of AI-powered agents can help your AWS security team perform better across several domains.
The chatbot's backend views data normalised into the Open Cybersecurity Schema Framework (OCSF) by Security Lake.
#securitychatbot#AmazonBedrockagents#graphicaluserinterface#Bedrockagent#chatbot#chatbotsecurity#Technology#TechNews#technologynews#news#govindhtech
0 notes
Text
Enhancing Security in Backend Development: Best Practices for Developers
In today’s rapidly evolving digital environment, security in backend systems is paramount. As the backbone of web applications, the backend handles sensitive data processing, storage, and communication. Any vulnerabilities in this layer can lead to catastrophic breaches, affecting user trust and business integrity. This article highlights essential best practices to ensure your backend development meets the highest security standards.
1. Implement Strong Authentication and Authorization
One of the primary steps in securing backend development services is implementing robust authentication and authorization protocols. Password-based systems alone are no longer sufficient. Modern solutions like OAuth 2.0 and JSON Web Tokens (JWT) offer secure ways to manage user sessions. Multi-factor authentication (MFA) adds another layer of protection, requiring users to verify their identity using multiple methods, such as a password and a one-time code.
Authorization should be handled carefully to ensure users only access resources relevant to their role. By limiting privileges, you reduce the risk of sensitive data falling into the wrong hands. This practice is particularly crucial for applications that involve multiple user roles, such as administrators, managers, and end-users.
2. Encrypt Data in Transit and at Rest
Data encryption is a non-negotiable aspect of backend security. When data travels between servers and clients, it is vulnerable to interception. Implement HTTPS to secure this communication channel using SSL/TLS protocols. For data stored in databases, use encryption techniques that prevent unauthorized access. Even if an attacker gains access to the storage, encrypted data remains unreadable without the decryption keys.
Managing encryption keys securely is equally important. Store keys in hardware security modules (HSMs) or use services like AWS Key Management Service (KMS) to ensure they are well-protected. Regularly rotate keys to further reduce the risk of exposure.
3. Prevent SQL Injection and Other Injection Attacks
Injection attacks, particularly SQL injections, remain one of the most common threats to backend technologies for web development. Attackers exploit poorly sanitized input fields to execute malicious SQL queries. This can lead to unauthorized data access or even complete control of the database.
To mitigate this risk, always validate and sanitize user inputs. Use parameterized queries or prepared statements, which ensure that user-provided data cannot alter the intended database commands. Additionally, educate developers on the risks of injection attacks and implement static code analysis tools to identify vulnerabilities during the development process.
4. Employ Secure API Design
APIs are integral to backend development but can also serve as entry points for attackers if not secured properly. Authentication tokens, input validation, and rate limiting are essential to preventing unauthorized access and abuse. Moreover, all API endpoints should be designed with security-first principles.
For example, avoid exposing sensitive information in API responses. Error messages should be generic and not reveal the backend structure. Consider using tools like API gateways to enforce security policies, including data masking, IP whitelisting, and token validation.
5. Keep Dependencies Updated and Patched
Third-party libraries and frameworks streamline development but can introduce vulnerabilities if not updated regularly. Outdated software components are a common attack vector. Perform routine dependency checks and integrate automated vulnerability scanners like Snyk or Dependabot into your CI/CD pipeline.
Beyond updates, consider using tools to analyze your application for known vulnerabilities. For instance, dependency management tools can identify and notify you of outdated libraries, helping you stay ahead of potential risks.
6. Adopt Role-Based Access Control (RBAC)
Access management is a critical component of secure backend systems. Role-Based Access Control (RBAC) ensures users and applications have access only to what they need. Define roles clearly and assign permissions at a granular level. For example, a customer service representative may only access user profile data, while an admin might have permissions to modify backend configurations.
Implementing RBAC reduces the potential damage of a compromised user account. For added security, monitor access logs for unusual patterns, such as repeated failed login attempts or unauthorized access to restricted resources.
7. Harden Your Database Configurations
Databases are at the heart of backend systems, making them a prime target for attackers. Properly configuring your database is essential. Start by disabling unnecessary services and default accounts that could be exploited. Enforce strong password policies and ensure that sensitive data, such as passwords, is hashed using secure algorithms like bcrypt or Argon2.
Database permissions should also be restricted. Grant the least privilege necessary to applications interacting with the database. Regularly audit these permissions to identify and eliminate unnecessary access.
8. Monitor and Log Backend Activities
Real-time monitoring and logging are critical for detecting and responding to security threats. Implement tools like Logstash, Prometheus, and Kibana to track server activity and identify anomalies. Logs should include information about authentication attempts, database queries, and API usage.
However, ensure that logs themselves are secure. Store them in centralized, access-controlled environments and avoid exposing them to unauthorized users. Use log analysis tools to proactively identify patterns that may indicate an ongoing attack.
9. Mitigate Cross-Site Scripting (XSS) Risks
Cross-site scripting attacks can compromise your backend security through malicious scripts. To prevent XSS attacks, validate and sanitize all inputs received from the client side. Implement Content Security Policies (CSP) that restrict the types of scripts that can run within the application.
Another effective measure is to encode output data before rendering it in the user’s browser. For example, HTML encoding ensures that malicious scripts cannot execute, even if injected.
10. Secure Cloud Infrastructure
As businesses increasingly migrate to the cloud, backend developers must adapt to the unique challenges of cloud security. Use Identity and Access Management (IAM) features provided by cloud platforms like AWS, Google Cloud, and Azure to define precise permissions.
Enable encryption for all data stored in the cloud and use virtual private clouds (VPCs) to isolate your infrastructure from external threats. Regularly audit your cloud configuration to ensure compliance with security best practices.
11. Foster a Culture of Security
Security isn’t a one-time implementation — it’s an ongoing process. Regularly train your development team on emerging threats, secure coding practices, and compliance standards. Encourage developers to follow a security-first approach at every stage of development.
Conduct routine penetration tests and code audits to identify weaknesses. Establish a response plan to quickly address breaches or vulnerabilities. By fostering a security-conscious culture, your organization can stay ahead of evolving threats.
Thus, Backend security is an ongoing effort requiring vigilance, strategic planning, and adherence to best practices. Whether you’re managing APIs, databases, or cloud integrations, securing backend development services ensures the reliability and safety of your application.
0 notes
Text
Developing Your Future with AWS Solution Architect Associate
Why Should You Get AWS Solution Architect Associate?
If you're stepping into the world of cloud computing or looking to level up your career in IT, the Aws certified solutions architect associate course is one of the smartest moves you can make. Here's why:

1. AWS Is the Cloud Market Leader
Amazon Web Services (AWS) dominates the cloud industry, holding a significant share of the global market. With more businesses shifting to the cloud, AWS skills are in high demand—and that trend isn’t slowing down.
2. Proves Your Cloud Expertise
This certification demonstrates that you can design scalable, reliable, and cost-effective cloud solutions on AWS. It's a solid proof of your ability to work with AWS services, including storage, networking, compute, and security.
3. Boosts Your Career Opportunities
Recruiters actively seek AWS-certified professionals. Whether you're an aspiring cloud engineer, solutions architect, or developer, this credential helps you stand out in a competitive job market.
4. Enhances Your Earning Potential
According to various salary surveys, AWS-certified professionals—especially Solution Architects—tend to earn significantly higher salaries compared to their non-certified peers.
5. Builds a Strong Foundation
The Associate-level certification lays a solid foundation for more advanced AWS certifications like the AWS Solutions Architect – Professional, or specialty certifications in security, networking, and more.
Understanding the AWS Shared Responsibility Model
The AWS Solutions Architect Associate Shared Responsibility Model defines the division of security and compliance duties between AWS and the customer. AWS is responsible for “security of the cloud,” while customers are responsible for “security in the cloud.”
AWS handles the underlying infrastructure, including hardware, software, networking, and physical security of its data centers. This includes services like compute, storage, and database management at the infrastructure level.
On the other hand, customers are responsible for configuring their cloud resources securely. This includes managing data encryption, access controls (IAM), firewall settings, OS-level patches, and securing applications and workloads.
For example, while AWS secures the physical servers hosting an EC2 instance, the customer must secure the OS, apps, and data on that instance.
This model enables flexibility and scalability while ensuring that both parties play a role in protecting cloud environments. Understanding these boundaries is essential for compliance, governance, and secure cloud architecture.
Best Practices for AWS Solutions Architects
The role of an AWS Solutions Architect goes far beyond just designing cloud environments—it's about creating secure, scalable, cost-optimized, and high-performing architectures that align with business goals. To succeed in this role, following industry best practices is essential. Here are some of the top ones:
1. Design for Failure
Always assume that components can fail—and design resilient systems that recover gracefully.
Use Auto Scaling Groups, Elastic Load Balancers, and Multi-AZ deployments.
Implement circuit breakers, retries, and fallbacks to keep applications running.
2. Embrace the Well-Architected Framework
Leverage AWS’s Well-Architected Framework, which is built around five pillars:
Operational Excellence
Security
Reliability
Performance Efficiency
Cost Optimization
Reviewing your architecture against these pillars helps ensure long-term success.
3. Prioritize Security
Security should be built in—not bolted on.
Use IAM roles and policies with the principle of least privilege.
Encrypt data at rest and in transit using KMS and TLS.
Implement VPC security, including network ACLs, security groups, and private subnets.
4. Go Serverless When It Makes Sense
Serverless architecture using AWS Lambda, API Gateway, and DynamoDB can improve scalability and reduce operational overhead.
Ideal for event-driven workloads or microservices.
Reduces the need to manage infrastructure.
5. Optimize for Cost
Cost is a key consideration. Avoid over-provisioning.
Use AWS Cost Explorer and Trusted Advisor to monitor spend.
Choose spot instances or reserved instances when appropriate.
Right-size EC2 instances and consider using Savings Plans.
6. Monitor Everything
Build strong observability into your architecture.
Use Amazon CloudWatch, X-Ray, and CloudTrail for metrics, tracing, and auditing.
Set up alerts and dashboards to catch issues early.
Recovery Planning with AWS
Recovery planning in AWS ensures your applications and data can quickly bounce back after failures or disasters. AWS offers built-in tools like Amazon S3 for backups, AWS Backup, Amazon RDS snapshots, and Cross-Region Replication to support data durability. For more robust strategies, services like Elastic Disaster Recovery (AWS DRS) and CloudEndure enable near-zero downtime recovery. Use Auto Scaling, Multi-AZ, and multi-region deployments to enhance resilience. Regularly test recovery procedures using runbooks and chaos engineering. A solid recovery plan on AWS minimizes downtime, protects business continuity, and keeps operations running even during unexpected events.
Learn more: AWS Solution Architect Associates
0 notes
Text
Accounting and Financial Application Development

In today's fast-paced business environment, accounting and financial applications play a crucial role in managing finances, ensuring compliance, and providing insights for decision-making. Whether you’re developing a personal finance tracker or a comprehensive accounting system for enterprises, understanding the essentials of financial application development is vital. This post outlines key features, technologies, and best practices for building successful financial software.
Core Features of Financial Applications
User Authentication and Authorization: Secure user access and role-based permissions.
General Ledger Management: Track and manage all financial transactions.
Invoicing and Billing: Generate and send invoices, manage recurring payments.
Expense Tracking: Record and categorize business expenses.
Financial Reporting: Generate balance sheets, income statements, and cash flow reports.
Budgeting and Forecasting: Tools for setting budgets and predicting future financial performance.
Integration with Banking Systems: Automate transactions and synchronize with bank statements.
Technology Stack Suggestions
Frontend: React.js, Angular, or Vue.js for creating responsive user interfaces.
Backend: Node.js, Django, or Ruby on Rails for handling business logic.
Database: PostgreSQL or MySQL for relational data storage; MongoDB for NoSQL solutions.
Payment Gateways: Stripe, PayPal, or Square for processing payments.
Cloud Platforms: AWS, Google Cloud, or Azure for hosting and data storage.
Sample User Registration API (Node.js Example)
const express = require('express'); const bodyParser = require('body-parser'); const bcrypt = require('bcrypt'); const app = express(); app.use(bodyParser.json()); let users = []; // Mock database for users // User registration endpoint app.post('/register', async (req, res) => { const { username, password } = req.body; const hashedPassword = await bcrypt.hash(password, 10); users.push({ username, password: hashedPassword }); res.status(201).send({ message: 'User registered successfully!' }); }); app.listen(3000, () => { console.log('Server is running on port 3000'); });
Ensuring Compliance and Security
Data Protection: Implement encryption for sensitive data both in transit and at rest.
Regulatory Compliance: Stay updated with regulations like GDPR, PCI-DSS, and local tax laws.
Audit Trails: Maintain logs of transactions and changes for accountability.
Access Controls: Enforce strong access controls and user permissions.
Best Practices for Financial Application Development
Start with clear requirements gathering and user stories to guide development.
Design a user-friendly interface with intuitive navigation for users of all backgrounds.
Incorporate responsive design to ensure usability across devices (desktops, tablets, mobile).
Implement thorough testing strategies, including unit testing, integration testing, and user acceptance testing.
Continuously gather user feedback for iterative improvements and feature enhancements.
Conclusion
Developing accounting and financial applications requires a blend of technical skills, an understanding of financial principles, and a focus on user experience. By prioritizing security, compliance, and usability, you can build robust applications that empower users to manage their finances effectively. Start with a clear vision, adopt best practices, and stay informed about industry trends to create successful financial software.
0 notes
Text
Building Chatbots with Amazon Lex and Polly
Building Chatbots with Amazon Lex and Polly
Amazon Lex and Polly are AWS services that help developers build conversational AI chatbots with natural language processing and text-to-speech capabilities.
Amazon Lex: A fully managed service for building voice and text-based conversational interfaces powered by automatic speech recognition (ASR) and natural language understanding (NLU).
Amazon Polly: A text-to-speech (TTS) service that converts text into lifelike speech using deep learning technologies.
Step 1: Setting Up Amazon Lex for Chatbot Development
1. Create a Bot in Amazon Lex
Go to the AWS Management Console → Open Amazon Lex.
Click Create Bot → Choose Start with an example or Create your own.
Name your bot (e.g., CustomerSupportBot).
Set IAM permissions (Lex needs permission to call Lambda functions if needed).
2. Define Intents and Utterances
Intent: Defines what the user wants (e.g., BookFlight, OrderPizza).
Utterances: Sample phrases the user might say (e.g., “I want to book a flight to New York.”).
Example of defining an intent for booking a flight:json{ "intentName": "BookFlight", "sampleUtterances": [ "I need to book a flight", "Can you help me find a flight?", "Book a ticket to {Destination}" ] }
3. Define Slots (User Inputs)
Slots capture user input for the intent. Example slots for a flight booking bot:
Slot Name Data Type Required ExampleDestination AMAZON.CityYes" New York"Date AMAZON.DateYes "Next Friday"NumTickets AMAZON.Number No"2"
4. Configure Responses
Add responses for the chatbot:json{ "messages": [ {"contentType": "PlainText", "content": "Where would you like to fly?"} ] }
5. Test the Bot
Use the built-in Test Chat Interface in Amazon Lex.
Deploy it to platforms like Slack, Facebook Messenger, or a website.
Step 2: Enhancing Conversational Experience with Amazon Polly
1. Convert Text to Speech
Amazon Polly provides natural-sounding voices. Example using Python & Boto3:pythonimport boto3polly = boto3.client("polly")response = polly.synthesize_speech( Text="Hello! How can I assist you today?", OutputFormat="mp3", VoiceId="Joanna" )# Save the audio response with open("speech.mp3", "wb") as file: file.write(response["AudioStream"].read())
2. Stream Speech Output in Real Time
Polly allows real-time streaming of responses, making interactions more human-like.
Step 3: Integrating Amazon Lex and Polly for Voice Chatbots
Capture User Speech Input (Lex processes user queries).
Generate Response in Text (Lex determines the response).
Convert Text Response to Speech (Polly speaks the response).
Example integration:pythondef text_to_speech(response_text): polly = boto3.client("polly") speech = polly.synthesize_speech(Text=response_text, OutputFormat="mp3", VoiceId="Matthew") return speech["AudioStream"].read()
Step 4: Deploying the Chatbot on Web & Mobile Apps
Amazon Connect: Integrate the chatbot for customer service.
AWS Lambda: Handle backend logic.
Amazon API Gateway: Expose chatbot as a REST API.
Amazon Lex SDK: Embed the bot into websites and mobile apps.
Conclusion
By combining Amazon Lex for NLP and Amazon Polly for speech synthesis, developers can create intelligent, voice-enabled chatbots for customer service, virtual assistants, and interactive applications.
WEBSITE: https://www.ficusoft.in/aws-training-in-chennai/
0 notes
Text
Cost and Time to Build a Laundry App Like Washio
On-demand laundry services are among the fastest growing refereed here on 13.7% per annum. This growth indicates a demand for convenience and quality in everyday tasks. Washio is the shining star in this space and sets the bar for competitors with its easy laundry pickup app. Below, I have explained how much it costs and what time frame is needed to develop a laundry app like Washio enabling getting the exact investment needed for budding entrepreneurs to materialize.
Key Features of a Laundry App Like Washio
User Registration and Profile Management A seamless onboarding process is vital for user retention.
Service Selection and Scheduling Allow users to choose services like washing, dry cleaning, and ironing, along with scheduling pickups and deliveries.
Real-Time Tracking Integrate GPS tracking to update users about their laundry status and driver location.
Payment Gateway Integration Secure and multiple payment options enhance user trust.
Push Notifications Keep users informed about updates, offers, and service statuses.
Admin Panel Manage orders, payments, and analytics efficiently.
Development Costs: A Detailed Analysis
Frontend Development
Cost of Hiring: Frontend developers typically charge between $30 to $150 per hour, depending on location and experience. On a project basis, costs can reach $10,000 to over $50,000.
Technology Stack: The choice of technology impacts costs significantly. Frameworks like React Native and Flutter allow for cross-platform development, reducing time and expense.
Successful Examples: Apps like Laundry Locker use React Native, making them budget-friendly while providing a robust user experience.
Backend Development
Cost of Backend Development: Building the backend can range from $15,000 to $80,000. Costs include server setup and database management.
Scalability Considerations: Apps must handle varying user loads. Planning for scalability can increase initial costs.
Cloud Platforms: Using services like AWS or Google Cloud can incur monthly fees from $50 to $500 or more, depending on usage.
Third-Party Integrations
Payment Gateways: Integrating platforms like Stripe or PayPal costs around $1,000 - $5,000.
Mapping Services: Google Maps integration can cost between $500 to $3,000.
Other Services: Features like SMS notifications may incur additional costs, potentially around $500 to $1,500.
Time Commitment: Project Timeline
Planning and Design Phase
Market Research and Analysis: Expect to spend 2-4 weeks understanding the market and competitors.
UI/UX Design: Designing the app interface may take 3-6 weeks for wireframes and prototypes.
Example Timelines: Projects similar to this typically spend 1-2 months in planning and design.
Tech Stack for a Laundry App
Frontend: React Native, Flutter
Backend: Node.js, Python (Django/Flask)
Database: PostgreSQL, MongoDB
APIs: RESTful APIs, GraphQL
Payment Gateway: Stripe, PayPal
Cloud Services: AWS, Firebase
Conclusion
Developing a laundry app like Washio requires careful planning of features, budget, and timeline. By partnering with an experienced app development company, you can ensure a high-quality, user-friendly app that meets your business goals. While the cost and time depend on the app's complexity, investing in such an app promises high returns in today’s on-demand service market.
Ready to build your laundry app? Get in touch with expert developers to bring your vision to life.
For more info visit us: https://deorwine.com/blog/build-laundry-app-like-washio/
Contact Us:
Website: https://deorwine.com
Email id: [email protected]
Skype: deorwineinfotech
For Any Query Call Us: +91-9116115717
#laundry app features#on demand laundry app development#laundry app development company#laundry app development cost#mobile application development#mobile app development company#laundry app development#app development
0 notes
Text
Building Scalable Applications with AWS Lambda: A Complete Tutorial

Are you curious about AWS Lambda but not sure where to begin? Look no further! In this AWS Lambda tutorial, we'll walk you through the basics in simple terms.
AWS Lambda is like having a magic wand for your code. Instead of worrying about servers, you can focus on writing functions to perform specific tasks. It's perfect for building applications that need to scale quickly or handle unpredictable workloads.
To start, you'll need an AWS account. Once you're logged in, navigate to the Lambda console. From there, you can create a new function and choose your preferred programming language. Don't worry if you're not a coding expert – Lambda supports many languages, including Python, Node.js, and Java.
Next, define your function's triggers. Triggers are events that invoke your function, such as changes to a database or incoming HTTP requests. You can set up triggers using services like API Gateway or S3.
After defining your function, it's time to test and deploy. Lambda provides tools for testing your function locally before deploying it to the cloud. Once you're satisfied, simply hit deploy, and Lambda will handle the rest.
Congratulations! You've now dipped your toes into the world of AWS Lambda. Keep experimenting and exploring – the possibilities are endless!
For more detailed tutorials and resources, visit Tutorial and Example.
Now, go forth and build amazing things with AWS Lambda!
0 notes
Text
"6 Ways to Trigger AWS Step Functions Workflows: A Comprehensive Guide"
To trigger an AWS Step Functions workflow, you have several options depending on your use case and requirements:
AWS Management Console: You can trigger a Step Functions workflow manually from the AWS Management Console by navigating to the Step Functions service, selecting your state machine, and then clicking on the "Start execution" button.
AWS SDKs: You can use AWS SDKs (Software Development Kits) available for various programming languages such as Python, JavaScript, Java, etc., to trigger Step Functions programmatically. These SDKs provide APIs to start executions of your state machine.
AWS CLI (Command Line Interface): AWS CLI provides a command-line interface to AWS services. You can use the start-execution command to trigger a Step Functions workflow from the command line.
AWS CloudWatch Events: You can use CloudWatch Events to schedule and trigger Step Functions workflows based on a schedule or specific events within your AWS environment. For example, you can trigger a workflow based on a time-based schedule or in response to changes in other AWS services.
AWS Lambda: You can integrate Step Functions with AWS Lambda functions. You can trigger a Step Functions workflow from a Lambda function, allowing you to orchestrate complex workflows in response to events or triggers handled by Lambda functions.
Amazon API Gateway: If you want to trigger a Step Functions workflow via HTTP requests, you can use Amazon API Gateway to create RESTful APIs. You can then configure API Gateway to trigger your Step Functions workflow when it receives an HTTP request.
These are some of the common methods for triggering AWS Step Functions workflows. The choice of method depends on your specific requirements, such as whether you need manual triggering, event-based triggering, or integration with other AWS services.
#AWS#StepFunctions#WorkflowAutomation#CloudComputing#AWSManagement#Serverless#DevOps#AWSLambda#AWSCLI#AWSConsole#magistersign#onlinetraining#cannada#support#usa
0 notes
Text
How to deploy an application and make it publicly available to the Internet on AWS
Your application must run on a server, which listens to traffic on an Internal port. Expose it to the Internet with a Reverse Proxy (something that catches traffic from outside through a certain port, say 443 or 80, and directs it to something listening inside your server, on a local port such as 3000).
Apache can be used as a reverse proxy, but there are myriad other ways to do it. NGINX is a very good one. Traefik also works as a reverse proxy if you're into golang.
Then, you would have to make sure that your server is not behind a firewall that blocks traffic on ports 80 or 443. In AWS the equivalent of this is to enable certain security groups on your VPC.
If you control your Network Gateway (router), you'd need to port forward traffic from the Internet, on ports 80/443/etc. onto your reverse proxy server.
At this point you should be able to access your content by sending HTTP requests to :80 or :443 from anywhere on the internet (WARNING: EC2 instances have internal and public (external) IP addresses. Do not confuse the EC2-specific internal address with your public address).
You don't control the "Network Gateway" so to say in AWS, so you may want to do the following: fall back onto their managed services to procure ingress.
Your mileage may vary but simply setting up an ELB is the recommended course of action in AWS. Yes, I know that AWS ELB is intended for scalability scenarios, but you can effectively set an ELB with just one sole entry.
You can create a Classic (L6) or Application (L7) Elastic Load Balancer, which will allow you to configure rules to port forward. You can also setup redundancy and high availability through this, but that's advanced territory. Which level you need, is usually up to you because balancing at different levels of the OSI level allows you to do certain tricks or not. For example, you can balance depending on the contents of the HTTP request headers if you use an L7 (Application) load balancer; L6 usually implies that the load balancing is performed at the router (DNS) level.
The LB will produce a generic "URL" that you will use to access your server.
Another AWS managed service, "API gateway" can also do this for you so you don't have to. You can create either a REST API or HTTP API on AWS API Gateway, which basically handles Ingress to your infrastructure with a few extra niceties baked in on top.
Finally, you probably want to configure things so you can access your application using a domain name of your choice. This is achieved through configuring the A and C records for your domain with an internet-wide DNS provider. AWS has this, with Route 53 --you can use a different DNS provider too, most domain name registrars provide this service too.
0 notes
Text
Going Serverless: how to run your first AWS Lambda function in the cloud
A decade ago, cloud servers abstracted away physical servers. And now, “Serverless” is abstracting away cloud servers.
Technically, the servers are still there. You just don’t need to manage them anymore.
Another advantage of going serverless is that you no longer need to keep a server running all the time. The “server” suddenly appears when you need it, then disappears when you’re done with it. Now you can think in terms of functions instead of servers, and all your business logic can now live within these functions.
In the case of AWS Lambda Functions, this is called a trigger. Lambda Functions can be triggered in different ways: an HTTP request, a new document upload to S3, a scheduled Job, an AWS Kinesis data stream, or a notification from AWS Simple Notification Service (SNS).
In this tutorial, I’ll show you how to set up your own Lambda Function and, as a bonus, show you how to set up a REST API all in the AWS Cloud, while writing minimal code.
Note that the Pros and Cons of Serverless depend on your specific use case. So in this article, I’m not going to tell you whether Serverless is right for your particular application — I’m just going to show you how to use it.
First, you’ll need an AWS account. If you don’t have one yet, start by opening a free AWS account here. AWS has a free tier that’s more than enough for what you will need for this tutorial.
We’ll be writing the function isPalindrome, which checks whether a passed string is a palindrome or not.
Above is an example implementation in JavaScript. Here is the link for gist on Github.
A palindrome is a word, phrase, or sequence that reads the same backward as forward, for the sake of simplicity we will limit the function to words only.
As we can see in the snippet above, we take the string, split it, reverse it and then join it. if the string and its reverse are equal the string is a Palindrome otherwise the string is not a Palindrome.
Creating the isPalindrome Lambda Function
In this step we will be heading to the AWS Console to create the Lambda Function:
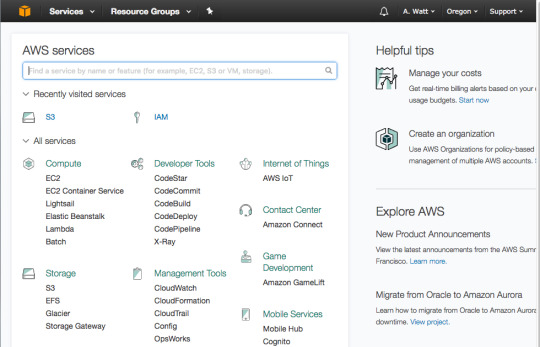
In the AWS Console go to Lambda.

And then press “Get Started Now.”
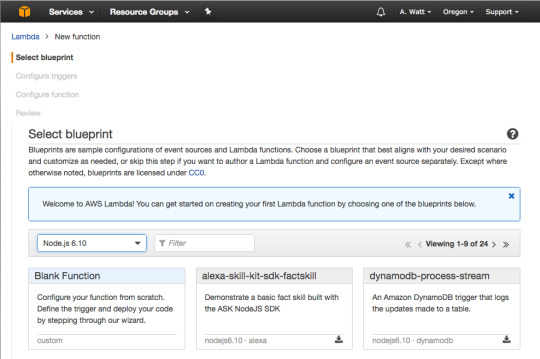
For runtime select Node.js 6.10 and then press “Blank Function.”
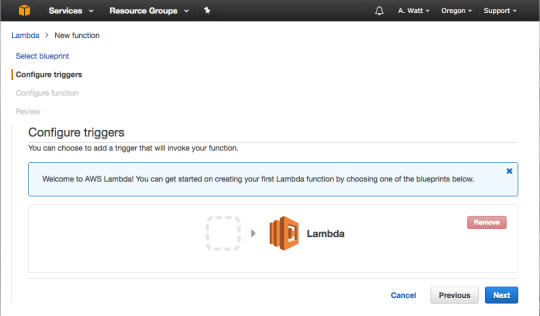
Skip this step and press “Next.”
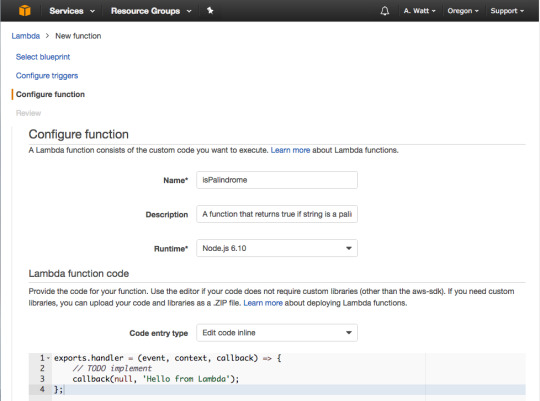
For Name type in isPalindrome, for description type in a description of your new Lambda Function, or leave it blank.
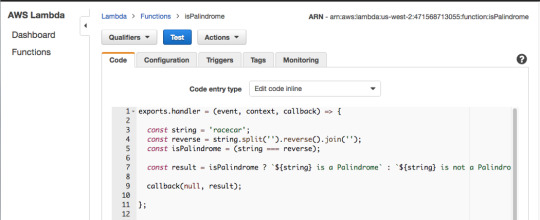
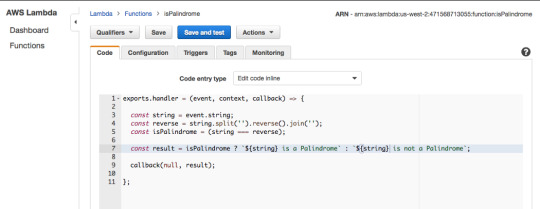
As you can see in the gist above a Lambda function is just a function we are exporting as a module, in this case, named handler. The function takes three parameters: event, context and a callback function.
The callback will run when the Lambda function is done and will return a response or an error message.For the Blank Lambda blueprint response is hard-coded as the string ‘Hello from Lambda’. For this tutorial since there will be no error handling, you will just use Null. We will look closely at the event parameter in the next few slides.
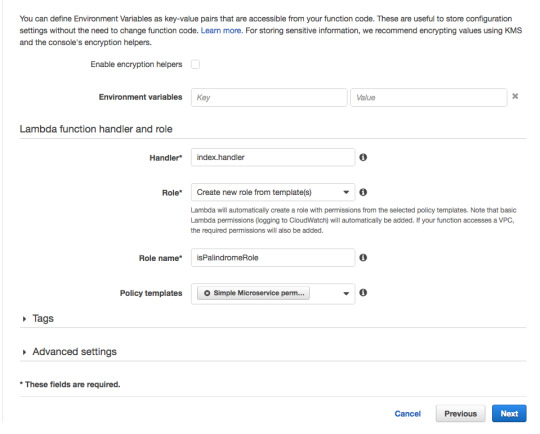
Scroll down. For Role choose “Create new Role from template”, and for Role name use isPalindromeRole or any name, you like.
For Policy templates, choose “Simple Microservice” permissions.
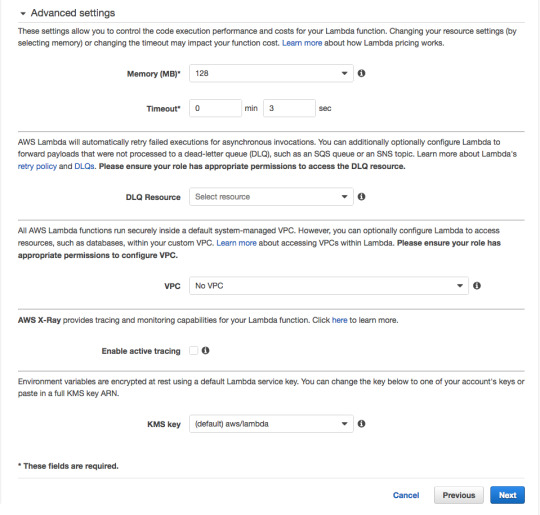
For Memory, 128 megabytes is more than enough for our simple function.
As for the 3 second timeout, this means that — should the function not return within 3 seconds — AWS will shut it down and return an error. Three seconds is also more than enough.
Leave the rest of the advanced settings unchanged.
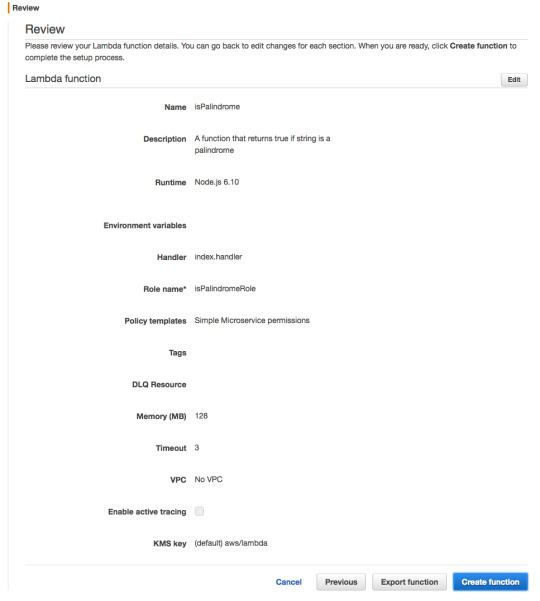
Press “Create function.”
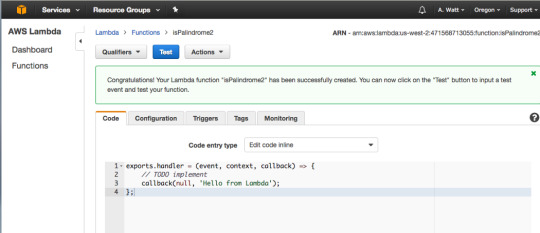
Congratulations — you’ve created your first Lambda Function. To test it press “Test.”
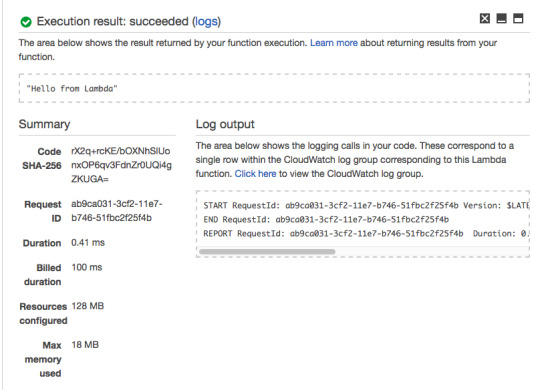
As you can see, your Lambda Function returns the hard-coded response of “Hello from Lambda.”
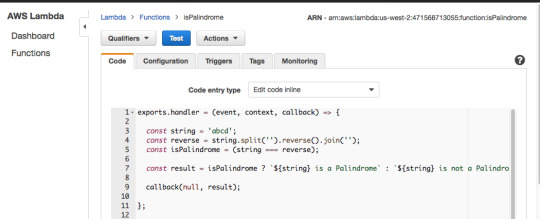
Now add the code from isPalindrome.js to your Lambda Function, but instead of return result use callback(null, result). Then add a hard-coded string value of abcd on line 3 and press “Test.”
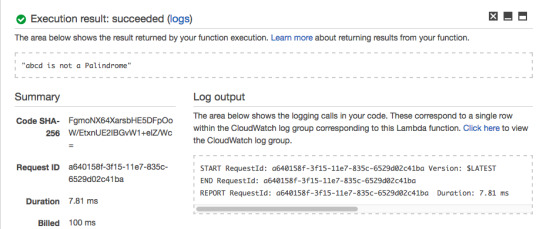
The Lambda Function should return “abcd is not a Palindrome.”
For the hard-coded string value of “racecar”, The Lambda Function returns “racecar is a Palindrome.”
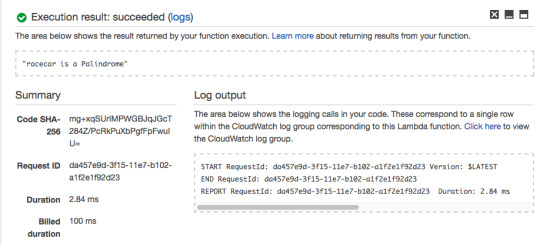
So far, the Lambda Function we created is behaving as expected.
In the next steps, I’ll show you how to trigger it and pass it a string argument using an HTTP request.
If you’ve built REST APIs from scratch before using a tool like Express.js, the snippet above should make sense to you. You first create a server, and then define all your routes one-by-one.
In this section, I’ll show you how to do the same thing using the AWS API Gateway.
Creating the API Gateway
Go to your AWS Console and press “API Gateway.”

And then press “Get Started.”
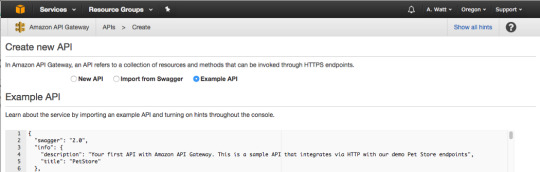
In Create new API dashboard select “New API.”
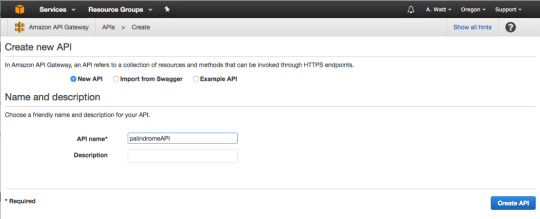
For API name, use “palindromeAPI.” For description, type in a description of your new API or just leave it blank.
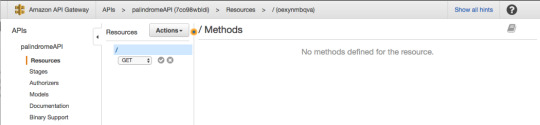
Our API will be a simple one, and will only have one GET method that will be used to communicate with the Lambda Function.
In the Actions menu, select “Create Method.” A small sub-menu will appear. Go ahead and select GET, and click on the checkmark to the right.
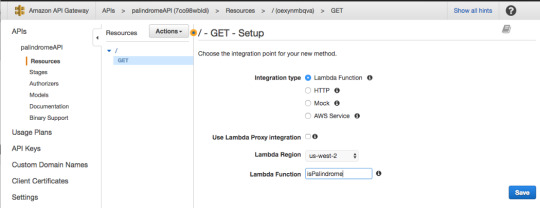
For Integration type, select Lambda Function.
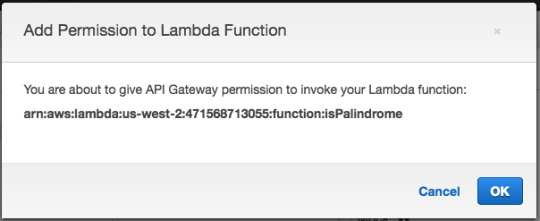
Then press “OK.”
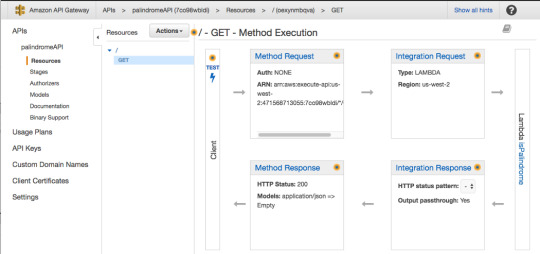
In the GET — Method Execution screen press “Integration Request.”
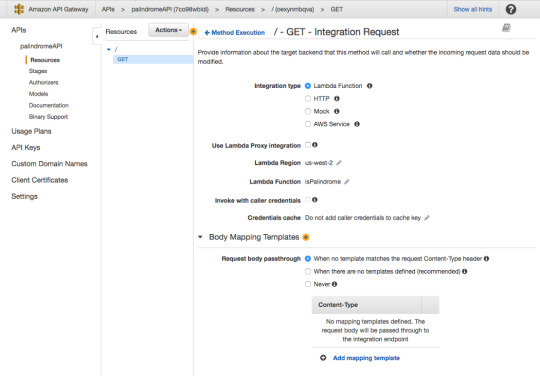
For Integration type, make sure Lambda Function is selected.
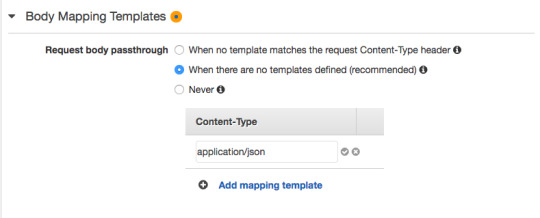
For request body passthrough, select “When there are no templates defined” and then for Content-Type enter “application/json”.
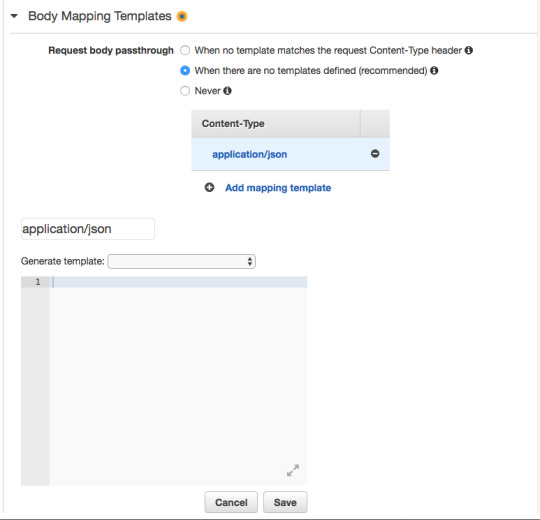
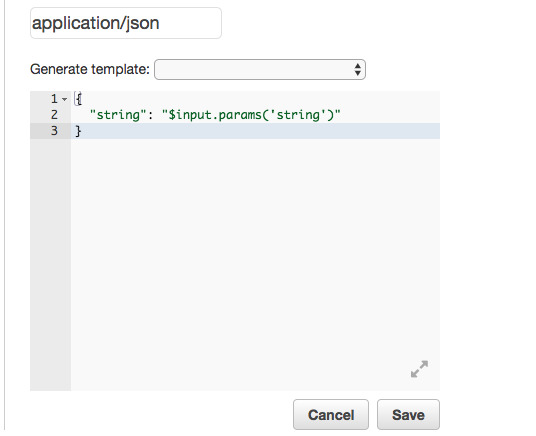
In the blank space add the JSON object shown below. This JSON object defines the parameter “string” that will allow us to pass through string values to the Lambda Function using an HTTP GET request. This is similar to using req.params in Express.js.
In the next steps, we’ll look at how to pass the string value to the Lambda Function, and how to access the passed value from within the function.
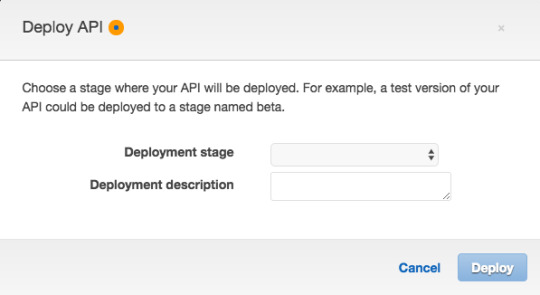
The API is now ready to be deployed. In the Actions menu click “Deploy API.”
For Deployment Stage select “[New Stage]”.
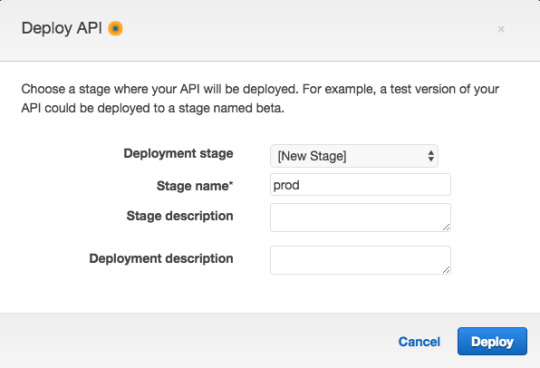
And for Stage name use “prod” (which is short for “production”).
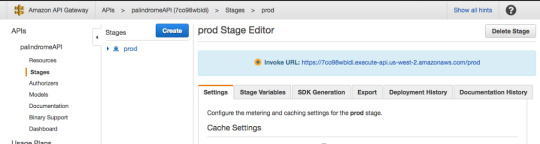
The API is now deployed, and the invoke URL will be used to communicate via HTTP request with Lambda. If you recall, in addition to a callback, Lambda takes two parameters: event and context.
To send a string value to Lambda you take your function’s invoke URL and add to it ?string=someValue and then the passed value can be accessed from within the function using event.string.
Modify code by removing the hard-coded string value and replacing it with event.string as shown below.
Now in the browser take your function’s invoke URL and add ?string=abcd to test your function via the browser.
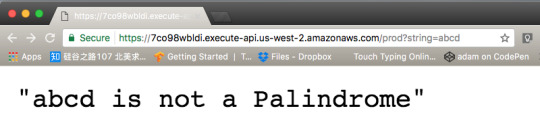
As you can see Lambda replies that abcd is not a Palindrome. Now do the same for racecar.
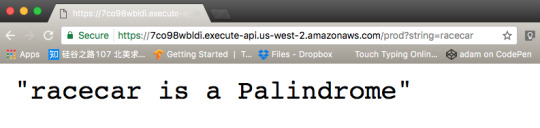
If you prefer you can use Postman as well to test your new isPalindrome Lambda Function. Postman is a great tool for testing your API endpoints, you can learn more about it here.
To verify it works, here’s a Palindrome:
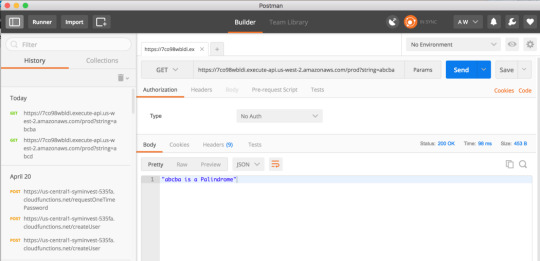
And here’s a non-palindrome:
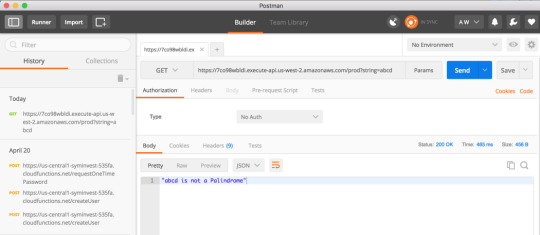
Congratulations — you have just set up and deployed your own Lambda Function!
Thanks for reading!
5 notes
·
View notes
Text
6 ESSENTIAL SKILLS FOR AWS DEVELOPERS
AWS is the 500-pound gorilla in the room of cloud stages. Regarding piece of the pie, AWS claims a greater amount of the cloud market than its nearest four rivals joined. The pervasiveness of a solitary stage implies that when engineers are on the lookout for a new position, there's an amazingly decent possibility that they'll discover "AWS" under the ideal abilities for designer jobs. By having a firm comprehension of AWS improvement, you'll separate yourself and become profoundly esteemed in your group or organization. The measure of administrations and usefulness in AWS can be overpowering; this article reduces the most fundamental abilities you should know as an AWS designer.

1. Deployment
So you've composed a web application, presently what? Sending web applications to AWS is perhaps the most essential, and probably the most profound expertise to know as an AWS engineer. There are different approaches to convey to AWS, yet they keep on developing as new strategies arise and more established ones are the sunset. On account of this advancement, the accompanying outline of AWS arrangement strategies ought to be checked to ensure there aren't fresher techniques recommended.
In the first place, you ought to be agreeable to physically convey a web application to an EC2 occurrence. Understanding this establishment will permit you to expand on it and conceivably make your own mechanized sending scripts.
Then, you should know CloudFormation well and see how to utilize that to send an application, yet in addition, stand up your application framework. You ought to likewise be acquainted with Elastic Beanstalk and the work it accomplishes for you. The jury is as yet out on whether EB is the awesome most exceedingly terrible help for conveying applications to AWS, yet it is utilized at a ton of organizations so realizing it is a smart thought.
At last, compartments are turning out to be increasingly mainstream, so realizing how to convey applications with Elastic Container Service (ECS) for Docker or Elastic Kubernetes Service (EKS) for Kubernetes is getting increasingly fundamental.
2. Security
The force of AWS is at times a two-sided deal. In spite of the fact that it permits you to do a ton, it likewise doesn't hold your hand. Acting naturally dependent and understanding the intricate details of the AWS Security Model and IAM is fundamental. Regularly, the most well-known bugs and issues that emerge in AWS come from a misconception of IAM by engineers. Getting very acquainted with how Roles and Policies work will upgrade all aspects of your AWS work.
Privileged insights the board is likewise another interesting subject that emerges regularly. AWS dispatched another assistance a year ago—properly called Secrets Manager—that truly removes the intricacy from overseeing and recovering any insider facts (like API keys, passwords, and so on) in your web applications.
3. AWS SDK
The AWS Software Development Kit (SDK) is the manner by which your application will communicate with AWS in the code. The API layer is totally gigantic in the SDK; even as an expert, you will continually discover new things that can be cultivated with it. Being acquainted with the SDK will deliver profits, on the grounds that interfacing with AWS won't be new to you. It's regular for engineers to not realize where to begin when pulling down an article from an S3 pail or associating with a DynamoDB table. Try not to be that designer. Get some involvement in SDK and perceive that it is so natural to utilize perhaps the most impressive advancements on the planet.
4. Databases
Data sets are a fundamental piece of each web application and AWS has various choices for fulfilling that utilization case. The issue is sorting out which information base assistance is ideal for your application. Without seeing every one of the alternatives and a portion of the advantages and disadvantages, you risk picking some unacceptable choice and blocking your application's development.
Investigate the current alternatives accessible in RDS. Aurora proceeds to improve and add new layers of similarity with MySQL and PostgreSQL. Attempt to comprehend why you should utilize Aurora rather than different alternatives. DynamoDB keeps on being a well-known decision for fast and straightforward NoSQL data set requirements. Perhaps the best part is its REST-based API, which implies no long-running data set association is required. At last, DocumentDB is the new child on the AWS information base scene, giving MongoDB similarity. Assuming DynamoDB doesn't work for your archive data set requirements, DocumentDB may get the job done.
5. Debugging
Assuming you're a designer, you know how baffling hitting a detour can be. However, you additionally likely ability a lot simpler it will manage barriers after you have some experience defeating them. AWS is the same in such a manner. Each time you conquer an issue in AWS, it just makes investigating and fixing the following issue that a lot simpler. Tragically, there's no guide to troubleshooting. It truly takes getting in there and acquiring experience with AWS. Albeit most issues you'll experience will probably be either identified with IAM consents or VPC bases access rules (for example Security Groups), there's simply no substitution for getting into the stage and creating. You'll run into issues and uncover yourself. Consider that experience when you experience your next issue to have the option to investigate it successfully.
6. Serverless
Serverless administrations in AWS, like Lambda and API Gateway, are taking care of an ever-increasing number of designer's issues nowadays. Getting when and for what reason to utilize them is a fundamental ability for each AWS engineer. Serverless engineering is extraordinary for specific sorts of usefulness and you ought to do research and evaluate this kind of design. Since Serverless is a new methodology, it's not generally comprehended by more prepared designers. By acquiring some involvement in this new innovation worldview, you can separate yourself in your group and in your organization. An open-source structure that makes building applications on Serverless engineering such a ton simpler is the Serverless Framework. By using Cloud Formation and the AWS SDK, this system permits you to utilize straightforward design records to construct incredible Serverless innovations. Perceive how your AWS consultant in India abilities stacks up.
1 note
·
View note
Text
AWS Place Autocomplete API

The AWS Place Autocomplete API provides a slew of data that can be used to help you find what you're looking for. From street addresses to local languages, the API can help you find what you're looking for. You can also use the API to validate addresses. For example, it can provide latitude and longitude to the address you've input.
The API supports more than five million address types. In addition to providing street addresses, the API can provide you with other useful information, such as the nearest metro stations, airports, and gas stations. There are also several widgets that can help you get what you need with the shortest amount of effort. These widgets can also show you only the data you really need.
As with any REST API, you can customize the experience with parameters that will help you find what you're looking for. For example, you can limit the results to only those of a certain type, or filter them by location. It is also possible to optimize the experience by using field masks. Using the proper field masks can reduce the API's response time by as much as 50%.
Although it's not the most performant, the AWS Places API does have its merits. Some of the aforementioned functionality can be augmented with an API gateway. If you don't have a gateway already set up, you can create one with just a few clicks. To do this, you'll need an App ID and a geocodesuggest path.
youtube
SITES WE SUPPORT
Blogspot – Address auto complete api
SOCIAL LINKS
Facebook Twitter LinkedIn Instagram Pinterest
0 notes
Text
Blog #9

What did you do this past week?
I implemented the back end API for our website and set up a hosting environment for it on AWS Elastic Beanstalk. I also updated our Postman documentation to include example JSON responses.
What's in your way?
Currently nothing is in the way of my work.
What will you do next week?
I will support the rest of my team on the leftover front-end tasks where need be. I will also get us started on the technical report and any other last minute requirements for phase II.
What did you think of Paper #9. The Dependency Inversion Principle?
I think the dependency inversion principle is important because, like many of the papers we've read so far, it emphasizes the importance of a maintainable and portable design. When coding in Java, I see a lot of these principles being used in Java's standard library classes. For example, a PrintWriter requires an abstract Reader where Reader can either be a BufferedReader or FileReader. Both readers have the necessary functions that PrintWriter depends on to do what it needs to do.
What was your experience of the relational algebra, select, and project? (this question will vary, week to week)
I am familiar with select since it is one of the many queries used in relational databases to get data. Again through relational databases, I had an idea of what relational algebra is, but I never studied it in depth. I had never heard of the project function before.
What made you happy this week?
I hung out with my friends at a small get-together.
What's your pick-of-the-week or tip-of-the-week?
In addition to setting up your back end hosting environment with Elastic Beanstalk, you also need AWS API Gateway to actually publish your API endpoint and route it through your custom domain name. I did not know this existed but thankfully my roommate had used it before so she helped me a lot.
0 notes
Text
Whmcs theme Customization

WGS provides outstanding as well as fully featured modules that enable you to add on some more functionalities into your WHMCS. Our team has also work experience creating customised WHMCS modules as per the particular business requirements. With WHMCS template customization service, we'll create a custom theme that allows you to seamlessly integrate WHMCS with your hosting company's brand.
We build the customised WHMCS functionality depending on the requirements of the clients. Our expert team of WHMCS will serve as a valuable source of the information.
Services We Offer Custom WHMCS Domain Registrar ModuleCustom WHMCS HookProvisioning ModulesCustom WHMCS Addon ModuleWeb Hosting Company Set UpCustom WHMCS Payment Gateway ModuleWHMCS does comes with default payment gateways but when it comes to any specific payment gateway, we are ready for that. We just need API documentation of that gateway and rest leave it upto us. You can check our already developed payment gateway in our product section, might be the one you are looking for. 1. HostX 2. HostCluster 3. ClientX The Last Saying
Whether you need a software installed or any number of customization, you can contact us here by filling this form.
We offer a full range of design and development services. As our client, you’ll be in touch with our experienced project management and leadership teams, with updates provided and questions answered at every phase of the project
Already we have developed the Registrar module for AWS route 53, Ficora, Switch EPP, .SGNIC etc and you can rely on us if you want to develop any specific domain registrar module.
When it comes to developing custom WHMCS hooks, we are best in it and have developed many hooks in past and can update default WHMCS functionality as per your requirement.
Provisioning Modules or you can say server modules are our expertise. Just have a look at our products and you can get an idea what we can do. One of our top server modules are WGS vmware module, WGS SO you start module.
Provisioning Modules or you can say server modules are our expertise. Just have a look at our products and you can get an idea what we can do. One of our top server modules are WGS vmware module, WGS SO you start module.
If you just have an idea and want to set up a web hosting company, you are at the right place. We set up hosting companies from scratch and have expertise from development, server side support, marketing. Get in touch and we will give you a brief overview of what we can do and let you know our past successful clients stories.
As a hosting provider, you must create a website that represents your company. It should be visually appealing, completely functional, and quick enough to set a good example for your future clients. The web hosting theme you select is critical to this happening.
WHMCS is also worth your consideration when it comes to developing and modifying websites. The tools and functionality included with web hosting template that allow you to quickly launch or maintain your web hosting website.
In this article, we will explore two of the greatest web hosting templates that may easily help you grow your business.
HostX is a well-known, multi-purpose, and versatile WHMCS Template. Because WHMCS is not SEO-friendly, you will need to handle SEO for your website with a third-party application. HostX's 'SEO Manager' function allows you to manage SEO efforts with a few clicks. It is also a full bundle that includes the front end, client area, and order form template.
Furthermore, the pre-built pages make theme tweaking a breeze. What else? HostX WHMCS Web Hosting Template also has built-in SEO tools to help you optimise your web hosting site and increase its search engine performance.
Features:
Page Manager
Top Menu
SEO Manager
Dynamic Testimonial
Live Timer on Offer
Live Chat
HostCluster is a popular web hosting template that integrates with WHMCS to provide you complete control over your website. With over 10 demonstrations and several style options, it is one of the most adaptable WHMCS templates, capable of handling practically any feature, including crypto hosting, domain registration, and so on.
Its pre-built components allow you to create a website from the ground up. Isn't that a more efficient option? It also includes a drag-and-drop visual composer, as well as a front-end and back-end.
Features:
Page Manager
Top Menu
SEO Manager
Dynamic testimonials
Live Timer on Offer
Live Chat
ClientX
WHMCS template allows you to personalize the color and layout of your web hosting website. This web hosting theme includes a variety of stylish and engaging WHMCS layouts.
This is the theme for you if you are a novice. It provides simple recommendations to help you use it in layman's terms. This web hosting theme is also compatible with over 200 WHMCS plugins.
Another important part of this WHMCS theme is that it is updated on a regular basis, leaving a lot of room for customization for businesses.
Features:
Eye-Catching Home Page
Social Signup
Multiple menu styles
RTL supported
Custom Orderform
Domain registration page
So, these are our top recommendations in the field of best web hosting templates. While there are many more, identifying the best is what makes the difference. We have provided the following selection of WHMCS templates with exceptional features and tools to assist you in building, customising, and controlling your web hosting website.
0 notes
Text
How to Build a Secure Backend: Common Security Practices for Developers

How to Build a Secure Backend:
Common Security Practices for Developers Building a secure backend is critical for protecting user data, ensuring application integrity, and maintaining trust.
Cyberattacks and data breaches can have severe consequences, so implementing robust security practices is non-negotiable for developers.
This blog will cover essential security measures every backend developer should follow.
Secure Authentication and Authorization
Authentication and authorization are foundational to backend security. Weak implementations can expose your application to unauthorized access.
Best Practices: Use strong password policies (e.g., minimum length, complexity).
Hash passwords with algorithms like bcrypt, Argon2, or PBKDF2. Implement multi-factor authentication (MFA) for added security.
Use access control mechanisms like Role-Based Access Control (RBAC).
Pro Tip: Avoid storing passwords in plaintext and always use secure hash functions.
2. Validate and Sanitize Inputs
Unchecked user inputs can lead to injection attacks like SQL injection, command injection, or cross-site scripting (XSS).
Best Practices: Validate all inputs for expected formats, lengths, and data types. Sanitize inputs to remove malicious characters.
Use parameterized queries or Object-Relational Mapping (ORM) to prevent SQL injection.
Example
(SQL Injection Prevention):
python
# Using parameterized queries
cursor.execute
(“SELECT * FROM users WHERE email = %s”, (user_email,))
3. Secure APIs APIs are often targeted by attackers, making their security paramount.
Best Practices:
Require authentication for all API endpoints.
Use HTTPS to encrypt data in transit.
Implement rate limiting and throttling to prevent abuse.
Validate API inputs to ensure only valid data is processed.
Use API gateways for centralized security and monitoring.
Pro Tip: Avoid exposing sensitive information in API responses.
4. Protect Against Cross-Site Request Forgery (CSRF) CSRF attacks trick authenticated users into performing unwanted actions.
Best Practices: Use CSRF tokens for all state-changing operations. Set SameSite attributes on cookies to prevent cross-origin requests. Require user re-authentication for sensitive operations.
5. Encrypt Data Encryption ensures that sensitive data remains secure, even if intercepted.
Best Practices:
Use TLS (HTTPS) for data in transit.
Encrypt sensitive data at rest using AES-256 or similar algorithms. Rotate encryption keys periodically.
6. Implement Logging and Monitoring Regular logging and monitoring can help detect and respond to security incidents promptly.
Best Practices: Log user activities, authentication events, and errors.
Use centralized logging systems like ELK Stack or Splunk. Monitor logs for suspicious activities with tools like SIEM (Security Information and Event Management).
7. Keep Dependencies Updated Outdated libraries and frameworks are common attack vectors.
Best Practices: Regularly update dependencies to their latest stable versions.
Use tools like Dependabot or npm audit to detect vulnerabilities.
Avoid unnecessary dependencies to reduce the attack surface.
8. Secure Configuration Management Misconfigured servers or applications can lead to severe security issues.
Best Practices: Disable unused services and ports.
Restrict sensitive environment variables (e.g., API keys, database credentials).
Store secrets securely using vaults like HashiCorp Vault or AWS Secrets Manager.
9. Conduct Regular Security Testing Testing helps identify and fix vulnerabilities before they are exploited.
Best Practices: Perform static application security testing (SAST) and dynamic application security testing (DAST).
Conduct regular penetration testing. Use automated tools like OWASP ZAP or Burp Suite for vulnerability scanning.
Conclusion
A secure backend is the backbone of any robust application.
By following these security practices, developers can minimize vulnerabilities and safeguard their applications against attacks.
Remember, security is not a one-time task; it’s an ongoing process that requires constant vigilance and updates.
Building a secure backend is both an art and a science — start implementing these practices today to ensure your application remains secure and trustworthy.
0 notes