#basically it automates your piracy
Explore tagged Tumblr posts
Text
And if you're technologically confident, look up the 'arr' collection. Running a home server with those, paired with Jellyfin, an open source Plex alternative, is a remarkably good system.




#basically it automates your piracy#works with torrent trackers and usenet#install casaos on a raspberrypi or nucbox and youre golden
121K notes
·
View notes
Text
How I ditched streaming services and learned to love Linux: A step-by-step guide to building your very own personal media streaming server (V2.0: REVISED AND EXPANDED EDITION)
This is a revised, corrected and expanded version of my tutorial on setting up a personal media server that previously appeared on my old blog (donjuan-auxenfers). I expect that that post is still making the rounds (hopefully with my addendum on modifying group share permissions in Ubuntu to circumvent 0x8007003B "Unexpected Network Error" messages in Windows 10/11 when transferring files) but I have no way of checking. Anyway this new revised version of the tutorial corrects one or two small errors I discovered when rereading what I wrote, adds links to all products mentioned and is just more polished generally. I also expanded it a bit, pointing more adventurous users toward programs such as Sonarr/Radarr/Lidarr and Overseerr which can be used for automating user requests and media collection.
So then, what is this tutorial? This is a tutorial on how to build and set up your own personal media server using Ubuntu as an operating system and Plex (or Jellyfin) to not only manage your media, but to also stream that media to your devices both at home and abroad anywhere in the world where you have an internet connection. Its intent is to show you how building a personal media server and stuffing it full of films, TV, and music that you acquired through indiscriminate and voracious media piracy various legal methods will free you to completely ditch paid streaming services. No more will you have to pay for Disney+, Netflix, HBOMAX, Hulu, Amazon Prime, Peacock, CBS All Access, Paramount+, Crave or any other streaming service that is not named Criterion Channel. Instead whenever you want to watch your favourite films and television shows, you’ll have your own personal service that only features things that you want to see, with files that you have control over. And for music fans out there, both Jellyfin and Plex support music streaming, meaning you can even ditch music streaming services. Goodbye Spotify, Youtube Music, Tidal and Apple Music, welcome back unreasonably large MP3 (or FLAC) collections.
On the hardware front, I’m going to offer a few options catered towards different budgets and media library sizes. The cost of getting a media server up and running using this guide will cost you anywhere from $450 CAD/$325 USD at the low end to $1500 CAD/$1100 USD at the high end (it could go higher). My server was priced closer to the higher figure, but I went and got a lot more storage than most people need. If that seems like a little much, consider for a moment, do you have a roommate, a close friend, or a family member who would be willing to chip in a few bucks towards your little project provided they get access? Well that's how I funded my server. It might also be worth thinking about the cost over time, i.e. how much you spend yearly on subscriptions vs. a one time cost of setting up a server. Additionally there's just the joy of being able to scream "fuck you" at all those show cancelling, library deleting, hedge fund vampire CEOs who run the studios through denying them your money. Drive a stake through David Zaslav's heart.
On the software side I will walk you step-by-step through installing Ubuntu as your server's operating system, configuring your storage as a RAIDz array with ZFS, sharing your zpool to Windows with Samba, running a remote connection between your server and your Windows PC, and then a little about started with Plex/Jellyfin. Every terminal command you will need to input will be provided, and I even share a custom #bash script that will make used vs. available drive space on your server display correctly in Windows.
If you have a different preferred flavour of Linux (Arch, Manjaro, Redhat, Fedora, Mint, OpenSUSE, CentOS, Slackware etc. et. al.) and are aching to tell me off for being basic and using Ubuntu, this tutorial is not for you. The sort of person with a preferred Linux distro is the sort of person who can do this sort of thing in their sleep. Also I don't care. This tutorial is intended for the average home computer user. This is also why we’re not using a more exotic home server solution like running everything through Docker Containers and managing it through a dashboard like Homarr or Heimdall. While such solutions are fantastic and can be very easy to maintain once you have it all set up, wrapping your brain around Docker is a whole thing in and of itself. If you do follow this tutorial and had fun putting everything together, then I would encourage you to return in a year’s time, do your research and set up everything with Docker Containers.
Lastly, this is a tutorial aimed at Windows users. Although I was a daily user of OS X for many years (roughly 2008-2023) and I've dabbled quite a bit with various Linux distributions (mostly Ubuntu and Manjaro), my primary OS these days is Windows 11. Many things in this tutorial will still be applicable to Mac users, but others (e.g. setting up shares) you will have to look up for yourself. I doubt it would be difficult to do so.
Nothing in this tutorial will require feats of computing expertise. All you will need is a basic computer literacy (i.e. an understanding of what a filesystem and directory are, and a degree of comfort in the settings menu) and a willingness to learn a thing or two. While this guide may look overwhelming at first glance, it is only because I want to be as thorough as possible. I want you to understand exactly what it is you're doing, I don't want you to just blindly follow steps. If you half-way know what you’re doing, you will be much better prepared if you ever need to troubleshoot.
Honestly, once you have all the hardware ready it shouldn't take more than an afternoon or two to get everything up and running.
(This tutorial is just shy of seven thousand words long so the rest is under the cut.)
Step One: Choosing Your Hardware
Linux is a light weight operating system, depending on the distribution there's close to no bloat. There are recent distributions available at this very moment that will run perfectly fine on a fourteen year old i3 with 4GB of RAM. Moreover, running Plex or Jellyfin isn’t resource intensive in 90% of use cases. All this is to say, we don’t require an expensive or powerful computer. This means that there are several options available: 1) use an old computer you already have sitting around but aren't using 2) buy a used workstation from eBay, or what I believe to be the best option, 3) order an N100 Mini-PC from AliExpress or Amazon.
Note: If you already have an old PC sitting around that you’ve decided to use, fantastic, move on to the next step.
When weighing your options, keep a few things in mind: the number of people you expect to be streaming simultaneously at any one time, the resolution and bitrate of your media library (4k video takes a lot more processing power than 1080p) and most importantly, how many of those clients are going to be transcoding at any one time. Transcoding is what happens when the playback device does not natively support direct playback of the source file. This can happen for a number of reasons, such as the playback device's native resolution being lower than the file's internal resolution, or because the source file was encoded in a video codec unsupported by the playback device.
Ideally we want any transcoding to be performed by hardware. This means we should be looking for a computer with an Intel processor with Quick Sync. Quick Sync is a dedicated core on the CPU die designed specifically for video encoding and decoding. This specialized hardware makes for highly efficient transcoding both in terms of processing overhead and power draw. Without these Quick Sync cores, transcoding must be brute forced through software. This takes up much more of a CPU’s processing power and requires much more energy. But not all Quick Sync cores are created equal and you need to keep this in mind if you've decided either to use an old computer or to shop for a used workstation on eBay
Any Intel processor from second generation Core (Sandy Bridge circa 2011) onward has Quick Sync cores. It's not until 6th gen (Skylake), however, that the cores support the H.265 HEVC codec. Intel’s 10th gen (Comet Lake) processors introduce support for 10bit HEVC and HDR tone mapping. And the recent 12th gen (Alder Lake) processors brought with them hardware AV1 decoding. As an example, while an 8th gen (Kaby Lake) i5-8500 will be able to hardware transcode a H.265 encoded file, it will fall back to software transcoding if given a 10bit H.265 file. If you’ve decided to use that old PC or to look on eBay for an old Dell Optiplex keep this in mind.
Note 1: The price of old workstations varies wildly and fluctuates frequently. If you get lucky and go shopping shortly after a workplace has liquidated a large number of their workstations you can find deals for as low as $100 on a barebones system, but generally an i5-8500 workstation with 16gb RAM will cost you somewhere in the area of $260 CAD/$200 USD.
Note 2: The AMD equivalent to Quick Sync is called Video Core Next, and while it's fine, it's not as efficient and not as mature a technology. It was only introduced with the first generation Ryzen CPUs and it only got decent with their newest CPUs, we want something cheap.
Alternatively you could forgo having to keep track of what generation of CPU is equipped with Quick Sync cores that feature support for which codecs, and just buy an N100 mini-PC. For around the same price or less of a used workstation you can pick up a mini-PC with an Intel N100 processor. The N100 is a four-core processor based on the 12th gen Alder Lake architecture and comes equipped with the latest revision of the Quick Sync cores. These little processors offer astounding hardware transcoding capabilities for their size and power draw. Otherwise they perform equivalent to an i5-6500, which isn't a terrible CPU. A friend of mine uses an N100 machine as a dedicated retro emulation gaming system and it does everything up to 6th generation consoles just fine. The N100 is also a remarkably efficient chip, it sips power. In fact, the difference between running one of these and an old workstation could work out to hundreds of dollars a year in energy bills depending on where you live.
You can find these Mini-PCs all over Amazon or for a little cheaper on AliExpress. They range in price from $170 CAD/$125 USD for a no name N100 with 8GB RAM to $280 CAD/$200 USD for a Beelink S12 Pro with 16GB RAM. The brand doesn't really matter, they're all coming from the same three factories in Shenzen, go for whichever one fits your budget or has features you want. 8GB RAM should be enough, Linux is lightweight and Plex only calls for 2GB RAM. 16GB RAM might result in a slightly snappier experience, especially with ZFS. A 256GB SSD is more than enough for what we need as a boot drive, but going for a bigger drive might allow you to get away with things like creating preview thumbnails for Plex, but it’s up to you and your budget.
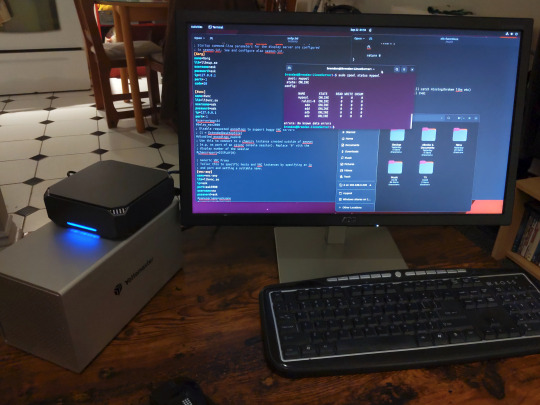
The Mini-PC I wound up buying was a Firebat AK2 Plus with 8GB RAM and a 256GB SSD. It looks like this:

Note: Be forewarned that if you decide to order a Mini-PC from AliExpress, note the type of power adapter it ships with. The mini-PC I bought came with an EU power adapter and I had to supply my own North American power supply. Thankfully this is a minor issue as barrel plug 30W/12V/2.5A power adapters are easy to find and can be had for $10.
Step Two: Choosing Your Storage
Storage is the most important part of our build. It is also the most expensive. Thankfully it’s also the most easily upgrade-able down the line.
For people with a smaller media collection (4TB to 8TB), a more limited budget, or who will only ever have two simultaneous streams running, I would say that the most economical course of action would be to buy a USB 3.0 8TB external HDD. Something like this one from Western Digital or this one from Seagate. One of these external drives will cost you in the area of $200 CAD/$140 USD. Down the line you could add a second external drive or replace it with a multi-drive RAIDz set up such as detailed below.
If a single external drive the path for you, move on to step three.
For people with larger media libraries (12TB+), who prefer media in 4k, or care who about data redundancy, the answer is a RAID array featuring multiple HDDs in an enclosure.
Note: If you are using an old PC or used workstatiom as your server and have the room for at least three 3.5" drives, and as many open SATA ports on your mother board you won't need an enclosure, just install the drives into the case. If your old computer is a laptop or doesn’t have room for more internal drives, then I would suggest an enclosure.
The minimum number of drives needed to run a RAIDz array is three, and seeing as RAIDz is what we will be using, you should be looking for an enclosure with three to five bays. I think that four disks makes for a good compromise for a home server. Regardless of whether you go for a three, four, or five bay enclosure, do be aware that in a RAIDz array the space equivalent of one of the drives will be dedicated to parity at a ratio expressed by the equation 1 − 1/n i.e. in a four bay enclosure equipped with four 12TB drives, if we configured our drives in a RAIDz1 array we would be left with a total of 36TB of usable space (48TB raw size). The reason for why we might sacrifice storage space in such a manner will be explained in the next section.
A four bay enclosure will cost somewhere in the area of $200 CDN/$140 USD. You don't need anything fancy, we don't need anything with hardware RAID controls (RAIDz is done entirely in software) or even USB-C. An enclosure with USB 3.0 will perform perfectly fine. Don’t worry too much about USB speed bottlenecks. A mechanical HDD will be limited by the speed of its mechanism long before before it will be limited by the speed of a USB connection. I've seen decent looking enclosures from TerraMaster, Yottamaster, Mediasonic and Sabrent.
When it comes to selecting the drives, as of this writing, the best value (dollar per gigabyte) are those in the range of 12TB to 20TB. I settled on 12TB drives myself. If 12TB to 20TB drives are out of your budget, go with what you can afford, or look into refurbished drives. I'm not sold on the idea of refurbished drives but many people swear by them.
When shopping for harddrives, search for drives designed specifically for NAS use. Drives designed for NAS use typically have better vibration dampening and are designed to be active 24/7. They will also often make use of CMR (conventional magnetic recording) as opposed to SMR (shingled magnetic recording). This nets them a sizable read/write performance bump over typical desktop drives. Seagate Ironwolf and Toshiba NAS are both well regarded brands when it comes to NAS drives. I would avoid Western Digital Red drives at this time. WD Reds were a go to recommendation up until earlier this year when it was revealed that they feature firmware that will throw up false SMART warnings telling you to replace the drive at the three year mark quite often when there is nothing at all wrong with that drive. It will likely even be good for another six, seven, or more years.

Step Three: Installing Linux
For this step you will need a USB thumbdrive of at least 6GB in capacity, an .ISO of Ubuntu, and a way to make that thumbdrive bootable media.
First download a copy of Ubuntu desktop (for best performance we could download the Server release, but for new Linux users I would recommend against the server release. The server release is strictly command line interface only, and having a GUI is very helpful for most people. Not many people are wholly comfortable doing everything through the command line, I'm certainly not one of them, and I grew up with DOS 6.0. 22.04.3 Jammy Jellyfish is the current Long Term Service release, this is the one to get.
Download the .ISO and then download and install balenaEtcher on your Windows PC. BalenaEtcher is an easy to use program for creating bootable media, you simply insert your thumbdrive, select the .ISO you just downloaded, and it will create a bootable installation media for you.
Once you've made a bootable media and you've got your Mini-PC (or you old PC/used workstation) in front of you, hook it directly into your router with an ethernet cable, and then plug in the HDD enclosure, a monitor, a mouse and a keyboard. Now turn that sucker on and hit whatever key gets you into the BIOS (typically ESC, DEL or F2). If you’re using a Mini-PC check to make sure that the P1 and P2 power limits are set correctly, my N100's P1 limit was set at 10W, a full 20W under the chip's power limit. Also make sure that the RAM is running at the advertised speed. My Mini-PC’s RAM was set at 2333Mhz out of the box when it should have been 3200Mhz. Once you’ve done that, key over to the boot order and place the USB drive first in the boot order. Then save the BIOS settings and restart.
After you restart you’ll be greeted by Ubuntu's installation screen. Installing Ubuntu is really straight forward, select the "minimal" installation option, as we won't need anything on this computer except for a browser (Ubuntu comes preinstalled with Firefox) and Plex Media Server/Jellyfin Media Server. Also remember to delete and reformat that Windows partition! We don't need it.
Step Four: Installing ZFS and Setting Up the RAIDz Array
Note: If you opted for just a single external HDD skip this step and move onto setting up a Samba share.
Once Ubuntu is installed it's time to configure our storage by installing ZFS to build our RAIDz array. ZFS is a "next-gen" file system that is both massively flexible and massively complex. It's capable of snapshot backup, self healing error correction, ZFS pools can be configured with drives operating in a supplemental manner alongside the storage vdev (e.g. fast cache, dedicated secondary intent log, hot swap spares etc.). It's also a file system very amenable to fine tuning. Block and sector size are adjustable to use case and you're afforded the option of different methods of inline compression. If you'd like a very detailed overview and explanation of its various features and tips on tuning a ZFS array check out these articles from Ars Technica. For now we're going to ignore all these features and keep it simple, we're going to pull our drives together into a single vdev running in RAIDz which will be the entirety of our zpool, no fancy cache drive or SLOG.
Open up the terminal and type the following commands:
sudo apt update
then
sudo apt install zfsutils-linux
This will install the ZFS utility. Verify that it's installed with the following command:
zfs --version
Now, it's time to check that the HDDs we have in the enclosure are healthy, running, and recognized. We also want to find out their device IDs and take note of them:
sudo fdisk -1
Note: You might be wondering why some of these commands require "sudo" in front of them while others don't. "Sudo" is short for "super user do”. When and where "sudo" is used has to do with the way permissions are set up in Linux. Only the "root" user has the access level to perform certain tasks in Linux. As a matter of security and safety regular user accounts are kept separate from the "root" user. It's not advised (or even possible) to boot into Linux as "root" with most modern distributions. Instead by using "sudo" our regular user account is temporarily given the power to do otherwise forbidden things. Don't worry about it too much at this stage, but if you want to know more check out this introduction.
If everything is working you should get a list of the various drives detected along with their device IDs which will look like this: /dev/sdc. You can also check the device IDs of the drives by opening the disk utility app. Jot these IDs down as we'll need them for our next step, creating our RAIDz array.
RAIDz is similar to RAID-5 in that instead of striping your data over multiple disks, exchanging redundancy for speed and available space (RAID-0), or mirroring your data writing by two copies of every piece (RAID-1), it instead writes parity blocks across the disks in addition to striping, this provides a balance of speed, redundancy and available space. If a single drive fails, the parity blocks on the working drives can be used to reconstruct the entire array as soon as a replacement drive is added.
Additionally, RAIDz improves over some of the common RAID-5 flaws. It's more resilient and capable of self healing, as it is capable of automatically checking for errors against a checksum. It's more forgiving in this way, and it's likely that you'll be able to detect when a drive is dying well before it fails. A RAIDz array can survive the loss of any one drive.
Note: While RAIDz is indeed resilient, if a second drive fails during the rebuild, you're fucked. Always keep backups of things you can't afford to lose. This tutorial, however, is not about proper data safety.
To create the pool, use the following command:
sudo zpool create "zpoolnamehere" raidz "device IDs of drives we're putting in the pool"
For example, let's creatively name our zpool "mypool". This poil will consist of four drives which have the device IDs: sdb, sdc, sdd, and sde. The resulting command will look like this:
sudo zpool create mypool raidz /dev/sdb /dev/sdc /dev/sdd /dev/sde
If as an example you bought five HDDs and decided you wanted more redundancy dedicating two drive to this purpose, we would modify the command to "raidz2" and the command would look something like the following:
sudo zpool create mypool raidz2 /dev/sdb /dev/sdc /dev/sdd /dev/sde /dev/sdf
An array configured like this is known as RAIDz2 and is able to survive two disk failures.
Once the zpool has been created, we can check its status with the command:
zpool status
Or more concisely with:
zpool list
The nice thing about ZFS as a file system is that a pool is ready to go immediately after creation. If we were to set up a traditional RAID-5 array using mbam, we'd have to sit through a potentially hours long process of reformatting and partitioning the drives. Instead we're ready to go right out the gates.
The zpool should be automatically mounted to the filesystem after creation, check on that with the following:
df -hT | grep zfs
Note: If your computer ever loses power suddenly, say in event of a power outage, you may have to re-import your pool. In most cases, ZFS will automatically import and mount your pool, but if it doesn’t and you can't see your array, simply open the terminal and type sudo zpool import -a.
By default a zpool is mounted at /"zpoolname". The pool should be under our ownership but let's make sure with the following command:
sudo chown -R "yourlinuxusername" /"zpoolname"
Note: Changing file and folder ownership with "chown" and file and folder permissions with "chmod" are essential commands for much of the admin work in Linux, but we won't be dealing with them extensively in this guide. If you'd like a deeper tutorial and explanation you can check out these two guides: chown and chmod.
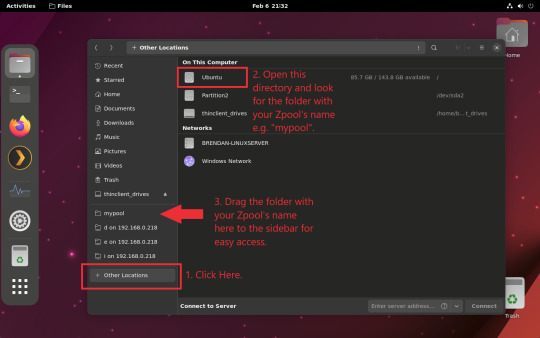
You can access the zpool file system through the GUI by opening the file manager (the Ubuntu default file manager is called Nautilus) and clicking on "Other Locations" on the sidebar, then entering the Ubuntu file system and looking for a folder with your pool's name. Bookmark the folder on the sidebar for easy access.
Your storage pool is now ready to go. Assuming that we already have some files on our Windows PC we want to copy to over, we're going to need to install and configure Samba to make the pool accessible in Windows.
Step Five: Setting Up Samba/Sharing
Samba is what's going to let us share the zpool with Windows and allow us to write to it from our Windows machine. First let's install Samba with the following commands:
sudo apt-get update
then
sudo apt-get install samba
Next create a password for Samba.
sudo smbpswd -a "yourlinuxusername"
It will then prompt you to create a password. Just reuse your Ubuntu user password for simplicity's sake.
Note: if you're using just a single external drive replace the zpool location in the following commands with wherever it is your external drive is mounted, for more information see this guide on mounting an external drive in Ubuntu.
After you've created a password we're going to create a shareable folder in our pool with this command
mkdir /"zpoolname"/"foldername"
Now we're going to open the smb.conf file and make that folder shareable. Enter the following command.
sudo nano /etc/samba/smb.conf
This will open the .conf file in nano, the terminal text editor program. Now at the end of smb.conf add the following entry:
["foldername"]
path = /"zpoolname"/"foldername"
available = yes
valid users = "yourlinuxusername"
read only = no
writable = yes
browseable = yes
guest ok = no
Ensure that there are no line breaks between the lines and that there's a space on both sides of the equals sign. Our next step is to allow Samba traffic through the firewall:
sudo ufw allow samba
Finally restart the Samba service:
sudo systemctl restart smbd
At this point we'll be able to access to the pool, browse its contents, and read and write to it from Windows. But there's one more thing left to do, Windows doesn't natively support the ZFS file systems and will read the used/available/total space in the pool incorrectly. Windows will read available space as total drive space, and all used space as null. This leads to Windows only displaying a dwindling amount of "available" space as the drives are filled. We can fix this! Functionally this doesn't actually matter, we can still write and read to and from the disk, it just makes it difficult to tell at a glance the proportion of used/available space, so this is an optional step but one I recommend (this step is also unnecessary if you're just using a single external drive). What we're going to do is write a little shell script in #bash. Open nano with the terminal with the command:
nano
Now insert the following code:
#!/bin/bash CUR_PATH=`pwd` ZFS_CHECK_OUTPUT=$(zfs get type $CUR_PATH 2>&1 > /dev/null) > /dev/null if [[ $ZFS_CHECK_OUTPUT == *not\ a\ ZFS* ]] then IS_ZFS=false else IS_ZFS=true fi if [[ $IS_ZFS = false ]] then df $CUR_PATH | tail -1 | awk '{print $2" "$4}' else USED=$((`zfs get -o value -Hp used $CUR_PATH` / 1024)) > /dev/null AVAIL=$((`zfs get -o value -Hp available $CUR_PATH` / 1024)) > /dev/null TOTAL=$(($USED+$AVAIL)) > /dev/null echo $TOTAL $AVAIL fi
Save the script as "dfree.sh" to /home/"yourlinuxusername" then change the ownership of the file to make it executable with this command:
sudo chmod 774 dfree.sh
Now open smb.conf with sudo again:
sudo nano /etc/samba/smb.conf
Now add this entry to the top of the configuration file to direct Samba to use the results of our script when Windows asks for a reading on the pool's used/available/total drive space:
[global]
dfree command = /home/"yourlinuxusername"/dfree.sh
Save the changes to smb.conf and then restart Samba again with the terminal:
sudo systemctl restart smbd
Now there’s one more thing we need to do to fully set up the Samba share, and that’s to modify a hidden group permission. In the terminal window type the following command:
usermod -a -G sambashare “yourlinuxusername”
Then restart samba again:
sudo systemctl restart smbd
If we don’t do this last step, everything will appear to work fine, and you will even be able to see and map the drive from Windows and even begin transferring files, but you'd soon run into a lot of frustration. As every ten minutes or so a file would fail to transfer and you would get a window announcing “0x8007003B Unexpected Network Error”. This window would require your manual input to continue the transfer with the file next in the queue. And at the end it would reattempt to transfer whichever files failed the first time around. 99% of the time they’ll go through that second try, but this is still all a major pain in the ass. Especially if you’ve got a lot of data to transfer or you want to step away from the computer for a while.
It turns out samba can act a little weirdly with the higher read/write speeds of RAIDz arrays and transfers from Windows, and will intermittently crash and restart itself if this group option isn’t changed. Inputting the above command will prevent you from ever seeing that window.
The last thing we're going to do before switching over to our Windows PC is grab the IP address of our Linux machine. Enter the following command:
hostname -I
This will spit out this computer's IP address on the local network (it will look something like 192.168.0.x), write it down. It might be a good idea once you're done here to go into your router settings and reserving that IP for your Linux system in the DHCP settings. Check the manual for your specific model router on how to access its settings, typically it can be accessed by opening a browser and typing http:\\192.168.0.1 in the address bar, but your router may be different.
Okay we’re done with our Linux computer for now. Get on over to your Windows PC, open File Explorer, right click on Network and click "Map network drive". Select Z: as the drive letter (you don't want to map the network drive to a letter you could conceivably be using for other purposes) and enter the IP of your Linux machine and location of the share like so: \\"LINUXCOMPUTERLOCALIPADDRESSGOESHERE"\"zpoolnamegoeshere"\. Windows will then ask you for your username and password, enter the ones you set earlier in Samba and you're good. If you've done everything right it should look something like this:

You can now start moving media over from Windows to the share folder. It's a good idea to have a hard line running to all machines. Moving files over Wi-Fi is going to be tortuously slow, the only thing that’s going to make the transfer time tolerable (hours instead of days) is a solid wired connection between both machines and your router.
Step Six: Setting Up Remote Desktop Access to Your Server
After the server is up and going, you’ll want to be able to access it remotely from Windows. Barring serious maintenance/updates, this is how you'll access it most of the time. On your Linux system open the terminal and enter:
sudo apt install xrdp
Then:
sudo systemctl enable xrdp
Once it's finished installing, open “Settings” on the sidebar and turn off "automatic login" in the User category. Then log out of your account. Attempting to remotely connect to your Linux computer while you’re logged in will result in a black screen!
Now get back on your Windows PC, open search and look for "RDP". A program called "Remote Desktop Connection" should pop up, open this program as an administrator by right-clicking and selecting “run as an administrator”. You’ll be greeted with a window. In the field marked “Computer” type in the IP address of your Linux computer. Press connect and you'll be greeted with a new window and prompt asking for your username and password. Enter your Ubuntu username and password here.
If everything went right, you’ll be logged into your Linux computer. If the performance is sluggish, adjust the display options. Lowering the resolution and colour depth do a lot to make the interface feel snappier.
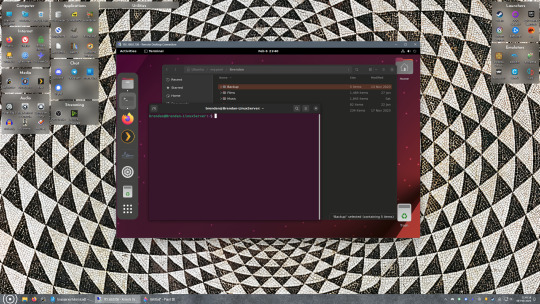
Remote access is how we're going to be using our Linux system from now, barring edge cases like needing to get into the BIOS or upgrading to a new version of Ubuntu. Everything else from performing maintenance like a monthly zpool scrub to checking zpool status and updating software can all be done remotely.

This is how my server lives its life now, happily humming and chirping away on the floor next to the couch in a corner of the living room.
Step Seven: Plex Media Server/Jellyfin
Okay we’ve got all the ground work finished and our server is almost up and running. We’ve got Ubuntu up and running, our storage array is primed, we’ve set up remote connections and sharing, and maybe we’ve moved over some of favourite movies and TV shows.
Now we need to decide on the media server software to use which will stream our media to us and organize our library. For most people I’d recommend Plex. It just works 99% of the time. That said, Jellyfin has a lot to recommend it by too, even if it is rougher around the edges. Some people run both simultaneously, it’s not that big of an extra strain. I do recommend doing a little bit of your own research into the features each platform offers, but as a quick run down, consider some of the following points:
Plex is closed source and is funded through PlexPass purchases while Jellyfin is open source and entirely user driven. This means a number of things: for one, Plex requires you to purchase a “PlexPass” (purchased as a one time lifetime fee $159.99 CDN/$120 USD or paid for on a monthly or yearly subscription basis) in order to access to certain features, like hardware transcoding (and we want hardware transcoding) or automated intro/credits detection and skipping, Jellyfin offers some of these features for free through plugins. Plex supports a lot more devices than Jellyfin and updates more frequently. That said, Jellyfin's Android and iOS apps are completely free, while the Plex Android and iOS apps must be activated for a one time cost of $6 CDN/$5 USD. But that $6 fee gets you a mobile app that is much more functional and features a unified UI across platforms, the Plex mobile apps are simply a more polished experience. The Jellyfin apps are a bit of a mess and the iOS and Android versions are very different from each other.
Jellyfin’s actual media player is more fully featured than Plex's, but on the other hand Jellyfin's UI, library customization and automatic media tagging really pale in comparison to Plex. Streaming your music library is free through both Jellyfin and Plex, but Plex offers the PlexAmp app for dedicated music streaming which boasts a number of fantastic features, unfortunately some of those fantastic features require a PlexPass. If your internet is down, Jellyfin can still do local streaming, while Plex can fail to play files unless you've got it set up a certain way. Jellyfin has a slew of neat niche features like support for Comic Book libraries with the .cbz/.cbt file types, but then Plex offers some free ad-supported TV and films, they even have a free channel that plays nothing but Classic Doctor Who.
Ultimately it's up to you, I settled on Plex because although some features are pay-walled, it just works. It's more reliable and easier to use, and a one-time fee is much easier to swallow than a subscription. I had a pretty easy time getting my boomer parents and tech illiterate brother introduced to and using Plex and I don't know if I would've had as easy a time doing that with Jellyfin. I do also need to mention that Jellyfin does take a little extra bit of tinkering to get going in Ubuntu, you’ll have to set up process permissions, so if you're more tolerant to tinkering, Jellyfin might be up your alley and I’ll trust that you can follow their installation and configuration guide. For everyone else, I recommend Plex.
So pick your poison: Plex or Jellyfin.
Note: The easiest way to download and install either of these packages in Ubuntu is through Snap Store.
After you've installed one (or both), opening either app will launch a browser window into the browser version of the app allowing you to set all the options server side.
The process of adding creating media libraries is essentially the same in both Plex and Jellyfin. You create a separate libraries for Television, Movies, and Music and add the folders which contain the respective types of media to their respective libraries. The only difficult or time consuming aspect is ensuring that your files and folders follow the appropriate naming conventions:
Plex naming guide for Movies
Plex naming guide for Television
Jellyfin follows the same naming rules but I find their media scanner to be a lot less accurate and forgiving than Plex. Once you've selected the folders to be scanned the service will scan your files, tagging everything and adding metadata. Although I find do find Plex more accurate, it can still erroneously tag some things and you might have to manually clean up some tags in a large library. (When I initially created my library it tagged the 1963-1989 Doctor Who as some Korean soap opera and I needed to manually select the correct match after which everything was tagged normally.) It can also be a bit testy with anime (especially OVAs) be sure to check TVDB to ensure that you have your files and folders structured and named correctly. If something is not showing up at all, double check the name.
Once that's done, organizing and customizing your library is easy. You can set up collections, grouping items together to fit a theme or collect together all the entries in a franchise. You can make playlists, and add custom artwork to entries. It's fun setting up collections with posters to match, there are even several websites dedicated to help you do this like PosterDB. As an example, below are two collections in my library, one collecting all the entries in a franchise, the other follows a theme.

My Star Trek collection, featuring all eleven television series, and thirteen films.
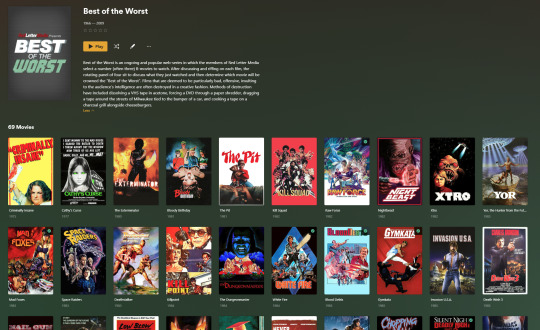
My Best of the Worst collection, featuring sixty-nine films previously showcased on RedLetterMedia’s Best of the Worst. They’re all absolutely terrible and I love them.
As for settings, ensure you've got Remote Access going, it should work automatically and be sure to set your upload speed after running a speed test. In the library settings set the database cache to 2000MB to ensure a snappier and more responsive browsing experience, and then check that playback quality is set to original/maximum. If you’re severely bandwidth limited on your upload and have remote users, you might want to limit the remote stream bitrate to something more reasonable, just as a note of comparison Netflix’s 1080p bitrate is approximately 5Mbps, although almost anyone watching through a chromium based browser is streaming at 720p and 3mbps. Other than that you should be good to go. For actually playing your files, there's a Plex app for just about every platform imaginable. I mostly watch television and films on my laptop using the Windows Plex app, but I also use the Android app which can broadcast to the chromecast connected to the TV in the office and the Android TV app for our smart TV. Both are fully functional and easy to navigate, and I can also attest to the OS X version being equally functional.
Part Eight: Finding Media
Now, this is not really a piracy tutorial, there are plenty of those out there. But if you’re unaware, BitTorrent is free and pretty easy to use, just pick a client (qBittorrent is the best) and go find some public trackers to peruse. Just know now that all the best trackers are private and invite only, and that they can be exceptionally difficult to get into. I’m already on a few, and even then, some of the best ones are wholly out of my reach.
If you decide to take the left hand path and turn to Usenet you’ll have to pay. First you’ll need to sign up with a provider like Newshosting or EasyNews for access to Usenet itself, and then to actually find anything you’re going to need to sign up with an indexer like NZBGeek or NZBFinder. There are dozens of indexers, and many people cross post between them, but for more obscure media it’s worth checking multiple. You’ll also need a binary downloader like SABnzbd. That caveat aside, Usenet is faster, bigger, older, less traceable than BitTorrent, and altogether slicker. I honestly prefer it, and I'm kicking myself for taking this long to start using it because I was scared off by the price. I’ve found so many things on Usenet that I had sought in vain elsewhere for years, like a 2010 Italian film about a massacre perpetrated by the SS that played the festival circuit but never received a home media release; some absolute hero uploaded a rip of a festival screener DVD to Usenet. Anyway, figure out the rest of this shit on your own and remember to use protection, get yourself behind a VPN, use a SOCKS5 proxy with your BitTorrent client, etc.
On the legal side of things, if you’re around my age, you (or your family) probably have a big pile of DVDs and Blu-Rays sitting around unwatched and half forgotten. Why not do a bit of amateur media preservation, rip them and upload them to your server for easier access? (Your tools for this are going to be Handbrake to do the ripping and AnyDVD to break any encryption.) I went to the trouble of ripping all my SCTV DVDs (five box sets worth) because none of it is on streaming nor could it be found on any pirate source I tried. I’m glad I did, forty years on it’s still one of the funniest shows to ever be on TV.
Part Nine/Epilogue: Sonarr/Radarr/Lidarr and Overseerr
There are a lot of ways to automate your server for better functionality or to add features you and other users might find useful. Sonarr, Radarr, and Lidarr are a part of a suite of “Servarr” services (there’s also Readarr for books and Whisparr for adult content) that allow you to automate the collection of new episodes of TV shows (Sonarr), new movie releases (Radarr) and music releases (Lidarr). They hook in to your BitTorrent client or Usenet binary newsgroup downloader and crawl your preferred Torrent trackers and Usenet indexers, alerting you to new releases and automatically grabbing them. You can also use these services to manually search for new media, and even replace/upgrade your existing media with better quality uploads. They’re really a little tricky to set up on a bare metal Ubuntu install (ideally you should be running them in Docker Containers), and I won’t be providing a step by step on installing and running them, I’m simply making you aware of their existence.
The other bit of kit I want to make you aware of is Overseerr which is a program that scans your Plex media library and will serve recommendations based on what you like. It also allows you and your users to request specific media. It can even be integrated with Sonarr/Radarr/Lidarr so that fulfilling those requests is fully automated.
And you're done. It really wasn't all that hard. Enjoy your media. Enjoy the control you have over that media. And be safe in the knowledge that no hedgefund CEO motherfucker who hates the movies but who is somehow in control of a major studio will be able to disappear anything in your library as a tax write-off.
1K notes
·
View notes
Text
Twitch Revenue Sharing: An Unrealistic Proposal
It’s been years since Phil Fish wanted YouTubers to pay him money for playing FEZ on YouTube. The prevailing counter-argument is that exposure is better than no exposure, and having people play your games on Twitch or YouTube without licensing your work for public performance means other people will see and buy it, leading to increased sales, and more revenue than you could have possibly gotten from a licensing deal. In my experience, this is not true. I understand the analogy to piracy of music and AAA games, but even that is an argument about economics of scale, not about morals.
In my own experience, this doesn’t even happen with free games. On the analytics of my own games, I saw that having YouTubers play them did almost nothing to page views or free downloads. A thousand views in one day don’t translate into one additional download, maybe three page views. The only significant effect was that one YouTube video about one of my games got small many MineCraft YouTubers to make copycat videos. A spike in downloads corresponded one-to-one with the number of YouTube videos with under a hundred views on small channels run by teenage boys.
I don’t think adding an EULA to my games that explicitly covers public performance would do anything. I could consult a lawyer to make it legally enforceable, but I could not enforce it in practice. Twitch and YouTube have cornered the market on gaming content, and even though Nintendo don’t like it when you play their games as a public performance YouTube turn a blind eye. What game developers need isn’t the copyright, what we need is the cooperation of YouTube and Twitch to allow us to enforce our copyrights. Twitch and Youtube have basically cornered the market.
We could have a chance if instead of trying to legislate or enforce public performance rights for games, we could just pressure YouTube and Twitch into codifying something into their terms of service. I know it won’t happen in practice. I don’t know what to do about YouTube. Youtube would rather ban a game from their site or negotiate a rather one-sided deal, and many YouTube videos exist in a grey area between fair use and entertainment.
I know what to do about Twitch though. I know what kind of deal I would want from them, anyway: When a streamer sets the game, a percentage of the revenue goes to the game developer. This could be 10%-30% of the ad revenue, and 2% of cheers and subscriptions, (out of Twitch’s cut of cheers and subscriptions). If the game is set to “IRL“ or “Just Chatting“, the revenue works the way it does today. There would be a lot of gnashing of teeth about PayPal donations (outside of twitch’s hands) and gifted subscriptions (do they count over the whole month, or for the moment they are gifted?), but I think this system would be fair, and a marked improvement over the status quo.
With YouTube, there is a lot more “long tail“ revenue, and videos are sometimes critique, or machinima, or edited with clips from different games. YouTube ad revenue is straightforward, but the copyright question is thorny. Twitch is live-streamed gaming, so copyright-wise and morally it’s a lot easier to just enable revenue sharing by default for twitch streams of the game, and every twitch stream has to have a game category listed (or arts and crafts, beaches, IRL, just chatting, game shows, demos, game development...).
If we managed to implement such a scheme, it would probably be through some kind of EU copyright directive. On balance, it would be terrible, because large conglomerates like Amazon, Alphabet, Apple and Microsoft would fight it every step of the way and try to make it not worth it for developers, algorithmically punishing developers of games that take a cut. It would also be terrible because it involves automated copyright enforcement. The only way this could turn out favourably for game developers is of the EU commission and US congress simultaneously threatened Amazon/Twitch with regulation, because Twitch already has streams categorised by game.
But if we somehow managed to get Twitch to cut in the developers, I think this would align the incentives between developers and streamers. We wouldn’t have to awkwardly say “but the people who watch the stream might buy the game for themselves.“ Even a story-based game with no replay value after you know the endings would have all the incentives aligned between streamers, stream audiences, and developers.
5 notes
·
View notes
Text
Why Your Business Needs a Marine Insurance Policy and Warehouse Insurance Today

Damage to merchandise gives rise to a lot of risk in operating a business-whether you are importing and exporting the goods or even just storing inventory. This risk exists with transport and others with storage, not just one. If you think basic insurance will do for you, you better get ready for a rude shock. Marine Insurance Policy and Warehouse Insurance are 2 specialized protections that simply cannot be ignored.
Here's why both are essential-and putting them off could kill your business faster than you think.
1. Marine Insurance Policy: Your First Line of Defense
The Marine Insurance Policy is not limited to sea-covered shipments; it also concerns air, road, and rail transport. Though "marine" pops in most people's heads and only ocean freight comes up, that couldn't be further away from the truth. It's all about the movement of goods.
Reasons why you need to secure it:
Cargo Damage: Things go wrong sometimes. Ships sink, planes crash, trucks overturn... a total loss on marine insurance means you take the complete loss.
Theft and Piracy: Piracy isn't just a myth of the 17th century in this world such as we know it today. It is a real threat in regions like Southeast Asia and parts of Africa.
Weather Disasters: Weather can be very unpredictable. Storms, floods, and other natural events can destroy shipments almost instantaneously.
Global Compliance: Many international trade agreements and contracts now require businesses to have marine insurance to be able to close deals.
Forward-thinking tip: Where global supply chains are concerned, complexity shall only increase. The Marine Insurance Policy is no longer an option; it is mandatory if you want to remain competitive abroad.
2. Warehouse Insurance-The Safety Net You Forgot About
Now let us assume your cargo has arrived in great condition. But what happens when it sits in the warehouse for weeks? Fire, flood, burglaries, and even employee theft could take a chunk out of your investment. This is where Warehouse Insurance comes in.
The reasons why Warehouse Insurance is so critical:
Fire and Water Damage: Electrical fires and flooding are among the major causes of warehouse losses. Standard property insurance may not fully protect against losses on stored goods.
Inventory Loss: Theft does happen. Employee theft occurs frequently and often goes unnoticed for months.
Third-party liability: If the goods stored for another person are damaged, you are liable. Warehouse insurance usually has third-party coverage.
Business Continuity: Any major incident with the warehousing operation could stop operations for months. Insurance assists you in rebuilding faster.
Forward-thinking tip: As the warehouse automates and smart logistics come into play, goods value (and vulnerability) is soaring. If your insurance is not evolving alongside it, then you are preparing for failure.
3. No More "Maybe Later" Thinking
Insurance works only if you give some thought to it; most companies come to that conclusion only when the damage has occurred. That is naive and downright irresponsible. Marine Insurance Policy and Warehouse Insurance are no longer optional-now it is a must-have wherever you are moving consignments across continents or keeping them in a facility for months.
Conclusion:
Run a business without these shields, and you're just a lawsuit, fire, or storm away from bankruptcy. Protect a little now to save a lot later. When calamity bangs on your door, prepare; the successful marginal businesses will be those that have prepared in a world of increasing risks and razor-sharp margins.
0 notes
Text
sorry to burst your bubble but that's literally how piracy works. it's usually a bit more sophisticated and automated than the process you described but it basically works exactly like this
hbo max blocks screenshots even when I use the snipping tool AND firefox AND ublock which is a fucking first. i will never understand streaming services blocking the ability to take screenshots thats literally free advertising for your show right there. HOW THE HELL IS SOMEBODY GONNA PIRATE YOUR SHOW THROUGH SCREENSHOTS. JACKASS
124K notes
·
View notes
Text
The Importance of DMCA Takedown Services in Protecting Your Digital Assets

In today’s digital age, our lives are intricately woven into the fabric of the internet. We share, create, and consume an unprecedented amount of digital content every day. From personal photos and videos to business presentations and creative works, our digital assets hold immense value.
However, the open nature of the internet also makes these assets vulnerable to theft, misuse, and unauthorized distribution. This is where DMCA (Digital Millennium Copyright Act) takedown services come into play, acting as a crucial line of defense for protecting your digital assets.
Understanding the DMCA
Before we delve into the significance of DMCA takedown services, it’s essential to grasp the basics of the DMCA itself. Enacted in 1998, the DMCA is a U.S. copyright law that provides a legal framework to protect digital content and the rights of content creators. It addresses various issues related to digital media, including copyright infringement, digital piracy, and online distribution of copyrighted materials.
One of the most powerful tools provided by the DMCA is the ability for copyright holders to issue takedown notices. These notices, often referred to as DMCA takedown notices, are requests to remove or disable access to copyrighted material that has been uploaded or shared without authorization on online platforms. When issued correctly, these notices can swiftly and effectively protect the rights of content creators.
The Importance of DMCA Takedown Services
Protection of Intellectual Property: Your digital assets are valuable intellectual property. Whether you are an individual artist, a photographer, a musician, or a business owner, your creations have a monetary and emotional value. DMCA takedown help safeguard your intellectual property rights by swiftly addressing instances of copyright infringement.
Preserving Revenues: Unauthorized distribution of digital assets can result in lost revenue. For businesses, this can translate into substantial financial losses. DMCA services aid in removing infringing content from websites, ensuring that your content is monetized as intended.
Brand Reputation: Reputation is invaluable in the digital world. If your digital assets are misused or associated with harmful content, it can tarnish your brand’s image. DMCA services help protect your brand’s reputation by removing content that is damaging or false.
Legal Compliance: Complying with copyright laws is not only ethical but also a legal requirement. Failing to take action against copyright infringement could weaken your legal standing in the event of a dispute. DMCA services ensure that you are actively protecting your copyrights and adhering to legal obligations.
Time and Resource Efficiency: Issuing takedown notices can be a time-consuming process, involving legal documentation and communication with multiple parties. Takedown services specialize in handling these tasks efficiently, allowing you to focus on your creative endeavors or business operations.
Global Reach: The internet transcends geographical boundaries, making it challenging to tackle copyright infringement worldwide. DMCA takedown services are equipped to deal with international infringements, ensuring that your digital assets are protected on a global scale.
How DMCA Takedown Services Work
DMCA takedown services simplify the process of protecting your digital assets. Here’s a simplified overview of how they work:
Identification: You or the service provider identifies instances of copyright infringement. This could be through automated tools, manual monitoring, or user reports.
Documentation: The service provider prepares DMCA takedown notices, including all required legal information, to submit to the hosting platform or website where the infringing content is located.
Submission: The service provider submits the DMCA notices to the appropriate online platforms or web hosting providers on your behalf.
Monitoring and Follow-up: The service provider monitors the progress of takedown requests, following up if necessary to ensure compliance.
Reporting: You receive reports detailing the status and outcomes of the takedown requests, allowing you to track the protection of your digital assets.
Conclusion
In a world where digital assets are under constant threat of unauthorized use and distribution, DMCA takedown services have emerged as indispensable protectors of creative works and intellectual property. Whether you are an individual content creator or a business owner, the importance of safeguarding your digital assets cannot be overstated.
Blog Resource : https://lexdmca.com/casestudy/the-importance-of-dmca-takedown-services-in-protecting-your-digital-assets/
#dmca#copyright#dmca takedown#dmca takedown notice#brand protection#copyright enforcement#copyright infringement#copyright service
0 notes
Text
My basic pessimistic take is that as [writing, visual artists, video game design, music, video essays, etc, etc] simultaneously become more accessible to aspiring creators and easier to share, the result will almost inevitably be an utter supply glut far in excess of what there's really societal demand for - at least, demand on the level to actually sustain so many artists at, like, a living wage.
Piracy and automation sure as shit won't help, of course, but, like, steam and ao3 are already full of heartfelt passions projects which have far more hours of labor put into creating them then will ever be spent consuming them.
Which is absolutely fine as far as hobby projects go - creation should be done for its own sake, write for an audience of yourself and your two best friends, etc, etc - but it's not a great economic environment for the aspiring artist without a preexisting fanbase or a marketing department behind them.
Anyway UBI when etc etc.
328 notes
·
View notes
Note
Do have some advice on how to defend against the pirates before they even though your work? After hearing what happened to your story; I’ve become very afraid of what will happen to mine…
Hello!
In this case, I suspect that the pirated works were bot-scraped, so there really isn't much you can do to prevent theft if your writing is posted online. I searched up a number of the stolen titles on AO3 to see if I could identify a common thread to figure out what types of stories were at risk, but they had little in common. Among the 500+ titles in the publisher's catalogue, there were stories from many different fandoms, works over 300K words, works under 20K words, works that were complete, and works that were incomplete and still updating on AO3! The only things the stories seemed to have in common at all were 1) they were in fairly mainstream fandoms (AAA video games, popular TV shows, major franchises like Marvel), and 2) they had a lot of readers on AO3. It's likely the pirates chose some arbitrary number of views or kudos and just swiped the top X number of works in several major fandoms. Additionally, the ebook formatting was a hot mess and all the covers used the same basic template, which makes me think much of the process may have been automated.
As I explained in my follow-up post, this sort of scheme is actually relatively common in the publishing world, too -- only it's even worse there. Pirates will acquire and reupload an ebook from a successful self-published or small-press author, then serve a fraudulent DMCA notice on the legitimate author to get the original version of the book removed from Amazon, so the only copy of the book available for purchase is the pirated one! Amazon's DMCA team gives the benefit of the doubt to whoever files the first complaint, so it can be difficult (and costly, if legal representation is required) for authors to prove ownership and get their accounts reinstated. At least with works stolen from AO3, there's a clear timestamped source we can send in to prove that the online work long predates the existence of the pirated one.
Some people have started account-locking their work on AO3 to try to restrict who can view it, but realistically, that doesn't provide much protection from this kind of piracy (thieves can make a free AO3 account, too!). The best defense is just to be aware that this sort of thing can happen, do a search on a couple of your most popular works every once in a while to make sure your stories aren't being reposted/sold, and share news of/report piracy any time you see it so the authors can file a complaint and get the pirated copy taken down.
19 notes
·
View notes
Text
Okay, here we go! I'm gonna try and put this in order from least to most technical knowledge required. I'm not responsible if you accidentally create SkyNet etc.
Level 1: browser extensions
This one is basically impossible to get wrong, or at least to get wrong badly enough that it causes any problems.
Get Firefox, or a Firefox fork like Waterfox. If you use a fork, make sure it's one that will let you use add-ons. On a PC, pretty much any Firefox fork will take add-ons, but on mobile devices, many don't. Iceraven is one that does.
Get the add-ons uBlock Origin, YouTube Sponsorblock (if you use YouTube), and FBCleaner (if you use Facebook).
uBlock Origin comes with a built-in list of filters to block ads and trackers, but you can add your own filters to block any specific element of a website you don't like. You know those goddamn floating frames on fandom.com sites that block half the screen? Now you can zap 'em.
Sponsorblock uses crowdsourced timestamps to automatically skip sponsor spots and self-promotion in YouTube videos. Never listen to anyone say "hit like and subscribe" or "Raid Shadow Legends" again.
FBCleaner hides all content from your feed except posts from people, groups, and pages you've actually chosen to follow.
Level 2: leaving enshittified services
The software that's become standard over the years in a lot of fields is steadily selling more of your data, showing you more ads, and pushing you to buy more expensive subscriptions. Time to tell them to get fucked.
Dump Adobe apps for Affinity or Krita. Drop Microsoft for LibreOffice. Change your default search engine from Google to DuckDuckGo or Qwant. Use OpenStreetMaps instead of Google or Apple Maps.
Level 3: network-level DNS fuckery
DNS, or Domain Name Service, is the thing that tells your computer where www.website.com is actually located. By hacking your network's DNS you can force it to tell your devices that ad-hosting domains don't exist at all. Some of the steps on this one can get pretty technical, but because you're doing all the difficult stuff on a dedicated device, you can't really fuck up anything that seriously.
Get yourself a Raspberry Pi (a cheap older one like a model 3B will work just fine for this purpose), and follow a guide like this one to get it set up running AdGuard Home. AdGuard, like uBlock, has built-in filter lists, but you can also add your own if there are specific domains you want to block.
Once it's up and running, you'll need to change the DNS settings on your router to point to your AdGuard service. This is different for every router but will always start with logging into the admin panel with a password printed on a little sticker somewhere on the router.
With that done, every time a device on your home network looks for ads.website.com, it'll get back a message that says "sorry, can't find it", so it won't be able to load any ads.
Level 4: Android-specific DNS fuckery
Because AdGuard runs on your home network, it can't block ads on your phone when you're away from home - and what's worse, your phone will sometimes remember the addresses it got when you were out and about, and ads will get past your AdGuard wall even when you're home.
To avoid this, get AdAway for DNS-based ad-blocking directly on your phone. The easy, but less seamless, way of using AdAway is the "local VPN mode", which doesn't require you to do any mucking about with your phone's operating system.
Level 5: automated media piracy
The best way to stop seeing ads on all your streaming services is to stop using streaming services. There are loads of ways to do this, but the best ones involve setting up what's called an "arr stack" (Google that for setup guides) along with nzbget and a usenet account. Most of the time you'll want to set this stuff up on a dedicated device - an old laptop gathering dust in the closet is a great option, or you can grab something used from a charity shop or a local electronics recycler.
The great thing about usenet is that unlike with torrents, you don't have to do any sharing from your computer, so you're in a lot less legal jeopardy - legally speaking, distributing pirated content is waaayyy more serious than accessing it. I pay about £3 a month for a secure, high-bandwidth usenet service.
Once you start getting your own collection of media on your own computer, use the open-source media library manager Jellyfin to browse and play things from basically any device.
Oh, and don't be a dick. Pirate all you want from big corporations, but please pay independent small-time creators for their work.
Level 6: fucking with Android
Android phones are a lot more locked-down than they used to be, but depending on the device you own you can still do a lot of messing around under the hood. Note that if you get something wrong while doing this, there is always the possibility that it will turn your device into a paperweight.
Before you buy a device, check where it sits on the Bootloader Unlock Wall of Shame. Once you've bought it, check the xda-developer forums for guides on how to unlock it and "root" it (gain admin access) with Magisk.
Once Magisk is installed, you can add modules to do all sorts of cool stuff, including using AdAway in "root mode" which makes it basically invisible.
You can also install YouTube ReVanced, which will do all the ad- and sponsor blocking stuff we took care of in your Windows browser a few paragraphs ago. Be careful: there are a lot of fake sites out there pretending they're associated with the ReVanced project which might be injecting malware into their downloads. This Reddit post has the official instructions and links.
Also, try out the modded version of Facebook from APKmoddone, which will block most of the same shit as the FBcleaner add-on from earlier. There's always a possibility that modified apps like this are doing something dodgy, but I've never had any issues with this one personally.
Level 7: fucking with Windows
This one is scary because it can seriously fuck up your shit if something goes wrong, but some really cool people have actually made it very simple to strip all the bloat, ads, and spyware out of Windows. The tool I use is ReviOS. Start reading at https://www.revi.cc/docs. Basically, you'll need to download a tool called AME Wizard and the ReviOS "playbook" that tells AME what to do. Read the documentation before you do any of this.
Level 8: switching to Linux
I'm not going to pretend this is an option for everyone. Half the software I use on a weekly basis isn't available on Linux. But if you can switch? Do it. These days, Ubuntu - one of the most popular flavours of Linux - is built with people switching from Windows in mind, and a lot of things will be pretty intuitive. It also has great documentation and a huge community you can go to for help if you're confused about stuff.
And that, friends, is a comprehensive approach to banishing the demons of capitalism from your home!
genuinely wild to me when I go to someone's house and we watch TV or listen to music or something and there are ads. I haven't seen an ad in my home since 2005. what do you mean you haven't set up multiple layers of digital infrastructure to banish corporate messaging to oblivion before it manifests? listen, this is important. this is the 21st century version of carving sigils on the wall to deny entry to demons or wearing bells to ward off the Unseelie. come on give me your router admin password and I'll show you how to cast a protective spell of Get Thee Tae Fuck, Capital
67K notes
·
View notes
Text
The morality and effect of pirating RWBY related content.
Recently there has been a lot of discussion on the morality and the effect that the decision to encourage piracy of RWBY and its related content. Not without reason in my opinion, morally the question of piracy is complicated, just like any kind of resistance or wish of change.
I am firmly in the pro-piracy camp as i have indicated before, but i want to make this thread to explain why and why some of the arguments i have seen in opposition to piracy are not well thought out.
Many people have indicated that if we do not support RWBY, there might be no volume 10. And that is correct. As such i have to pose a question. What is more important to you? Your own comfort and watching RWBY no matter what? Or people who work on the show and are exploited while doing so? At least in my opinion the more moral and selfless thing is to refuse a product that one CAN refuse if it is made through exploitative labour.
Others begun to ask however, why RWBY then? There are other exploitative corporations, especially since we live in a capitalist society. Why RT? Why RWBY? Because RWBY and RT is entertainment. While humans do need entertainment and enrichment in our lives, RWBY is not the only source of that. Nor is it necessary to our lives. RWBY is not food, it is not clothing. One can justify the exploitation or harm that is caused by food production/clothing and the like because these are necessary, and because there is no ethical consumption under capitalism. RWBY does not fall under this umbrella.
Why RWBY and RT specifically though? Because they are an example of a rotten company. Sexual abuses, worker exploitation, constant lies about "changing". And because RT is a relatively small company that we CAN affect the actions of. We cannot fix the entire exploitative system of the industry, but we can at least fix this company, or help fix it. We can engage in harm reduction. Even if we cant fix EVERYTHING we can at least NOT contribute to harm.
Some have argued that by pirating we will not enact change, that we need to "encourage" RT to get better. And that is categorically wrong. That is NOT how corporations work. The only language that corporations speak in is MONEY. Nothing else. A good example of this is Activision-Blizzard. Did you know that they almost entirely automated their "ticket" system that is used to report bugs in-game? Almost every player that has used it acknowledges it as an useless system and asks why it isnt changed. The answer is simple. Because they still pay money to the company. Why would Blizzard pay money to fix a problem that is not a "deal-breaker" for people who play the game? The players will complain and then still play. The same applies to RT. If you keep buying RT first they wont need to change. Because if you are willing to pay them money despite all of the revalations, why should they care about fixing anything?
"But what about the crew members?"
"What about them?"
I jest of course, i am not so callous as to ignore the workers of RT. If RWBY or RT fails it does mean that the employees of RT would most likely lose their jobs entirely. However, and im going to say it very simply, that is neither our moral responsibility, nor business.
What this is, is a very disgusting manipulative tactic.
We have to buy a product no matter what or people lose their jobs? Does noone else see how fucked up such logic is? How exploitative it is? It is guilt tripping at its basic.
And may i ask where the line is then if you do agree with such a view? How much abuse do you think is "alright" just so that the workers could keep their jobs. And how exactly will change be achieved if one can be guilt-tripped into stopping it before it goes on.
Corporations make products. We are not responsible for buying them or the consequences of NOT buying them. We have NO obligation to corporations NOR their workers. The corporations have obligations to their workers.
I would advise people to not surrender to such manipulation.
At the end of the day. All of this is your choice and a question that you have to answer to yourself. Do you think supporting RT is worth it? Or do you not think so? Those are the questions you have to answer to yourself individually.
2 notes
·
View notes
Text
Gmail Account Creator Pro

Power BI account using gmail doesn't work 05:00 PM I downloaded and installed PowerBI last week and gave my email address and information to the create account forum. An intuitive application that allows users to create Gmail accounts without having to configure the settings online, quickly and with minimum effort GMail Account Creator is a lightweight Windows. With this software you can create a single account in under 10 seconds, and 10 accounts in under 2 minutes. Obviously this saves you loads of time. GYC Automator - GYC Automator is Gmail account creator, Yahoo account creator, Craigslist and Backpage account creator - all in one powerful tool. Forget filling lengthy forms to create email accounts.
On this page
How to Create Mutliple Gmail Accounts. Gmail is a free webmail service offered by Google that supports sending and receiving emails as well as chatting to other Gmail users. The 10GB of free storage offered by the service means you can store all your mails and attachments online. You can create multiple Gmail accounts. Download gmail account creator.exe for free. Communication downloads - MASS Gmail Account Creator by Easytech Software Solutions and many more programs are available for instant and free download.
Description
Gmail Account Creator is a software which allows you create unlimited Gmail email accounts in seconds. It will automate the process of creating Gmail accounts. Feature list: * Setup Auto-Responder automatically * Setup Forwarding automatically * Use random or custom names * Enable POP3 automatically
Rate:
Release Date:05/18/2012
License:Shareware
Category:E-Mail Tools
Developer:Account Creator
Downloads:3653
Size:793 Kb
Price: -
To free download a trial version of Gmail Account Creator, click here To visit developer homepage of Gmail Account Creator, click here
Advertisement
Jiffy Gmail Account Creator
System Requirements
Gmail Account Creator requires Win98, WinME, WinNT, 4.x, Windows2000, WinXP, Windows2003, Windows, Vista, Starter, Windows, Vista, Home, Basic, Windows, Vista, Home, Premium, Windows, Vista, Business, Windows, Vista, Enterprise, Windows, Vista, Ultimate, Windows, Vista, Home, Basic, x64, Windows, Vista, Home, Premium, x6.
Gmail Account Creator v.1.0 Copyright
Shareware Junction periodically updates pricing and software information of Gmail Account Creator v.1.0 full version from the publisher using pad file and submit from users. Software piracy is theft, Using crack, password, serial numbers, registration codes, key generators, cd key, hacks is illegal and prevent future development of Gmail Account Creator v.1.0 Edition. Download links are directly from our publisher sites. Links Gmail Account Creator v.1.0 from Bittorrent, mediafire.com, uploadfiles.com, hotfiles.com rapidshare.com, megaupload.com, netload.in, storage.to, depositfiles.com and other files hosting are not allowed. The download file is obtained directly from the publisher, not from any Peer to Peer file sharing applications such as Shareaza, Limewire, Kazaa, Imesh, eDonkey, eMule, Ares, BearShare, Overnet, Morpheus, BitTorrent Azureus and WinMX.
Review This Software
More Gmail Account Creator Software
Advertisement
MASS Gmail Account Creator v.1.0.7
MASS GmailAccountCreator is a light weight and very easy to use application that will help you to create multiple Gmail accounts with ease.
Category: Miscellaneous
Developer: Easytech Software Solutions - Download - Price: $14.00
gmail account creator - generate gmail account - email form filler - gmail account - email account
Gmail Account Creator v.1.0
GmailAccountCreator is a software which allows you create unlimited Gmail email accounts in seconds. It will automate the process of creating Gmail accounts. Feature list: * Setup Auto-Responder automatically * Setup Forwarding automatically *
Category: E-Mail Tools
Developer: Account Creator - Download - Price: -
email - creator - cash - advance - debt
Yahoo Account Creator v.1.0.0.0
Fully automatic yahoo accountcreator . Make as many accounts as you want and need with our fast yahoo accountcreator
Category: Dial Up Networking
Developer: BuildBacklinksCheap.com - Download - Buy: $14.99
yahoo email account creator - create yahoo account - yahoo id maker - email account creator - yahoo accounts
MASS Hotmail Account Creator v.1.0.51
MASS Hotmail AccountCreator is a light weight and very easy to use application that will help you to create multiple Hotmail accounts with ease.
Category: Miscellaneous
Developer: Easytech Software Solutions - Download - Price: $14.00
hotmail account creator - generate hotmail account - email form filler - hotmail account - email account
MASS Facebook Account Creator v.1.0.69
MASS Facebook AccountCreator is a light weight and very easy to use application that will help you to create multiple Facebook accounts with ease.
Category: Miscellaneous
Developer: Easytech Software Solutions - Download - Price: $14.00
facebook account creator - generate bulk facebook account - email form filler - facebook account - email account
Bulk Cpanel Email Account Creator v.1
Create bulk CPanel email accounts.
Category: Wizards & Components
Developer: Webmaster Bots - Download - Free
cpanel email creator - bulk email creator - cpanel email account creator - cpanel email account generator - bulk cpanel email account
GYC Automator v.3.0
GYC Automator is a Gmailaccountcreator, Yahoo! accountcreator and Craigslist accountcreator - all in one powerful tool. Forget filling lengthy forms to create email accounts. Just setup what and how you want to fill signup forms,
Gmail Account Creator Pro Apk
Category: Miscellaneous
Developer: ADDiFF Solutions - Download - Free
Gmail Extract Email Addresses Software v.7.0
This software offers a solution to users who want to extract email addresses from their Gmailaccount. There is a feature to choose which folder to extract from (Inbox, All Mails, Drafts, Sent Mail, Spam, Starred or Trash).
Category: E-Mail Tools
Developer: Sobolsoft - Download - Buy: $19.99
extract gmails from gmail account - gmail inbox email extract - email extractor for gmail - extraction - extracting
Account Chef v.1.0
Account Chef is an unlimited email accountcreator software. With this application, you can get bulk email account in just one click.
Category: Auction Tools
Developer: Account Chef - Download - Buy: $79.00
account chef - bulk email account creator - bulk email maker - email account robot - email bot
ToolsGround EML to Gmail Migration v.1.0
ToolsGround EML to Gmail Program provides dual mode for adding EML files to the software panel. Users can export EML files in bulk into Gmailaccount. EML files of Windows Live Mail, eM client, Zoho Mail, Thunderbird, etc. are supported.
Category: File and Disk
Developer: ToolsGround - Download - Buy: $29.00
eml to gmail migration - eml to gmail converter - eml to gmail - eml files to gmail account - import eml to gmail
Photobucket Blaster v.1.0
Photobucket Blaster is your fully automated Photobucket accountcreator and image uploading software.
Category: Personal and Home
Developer: Photobucket Blaster - Download - Buy: $99.95
photobucket account creator - pb account creator - image uploading software - photobucket creator - pb creator
Gmail Extract Email Data Software v.7.0
This software offers a solution to users who want to extract specific text data in their Gmailaccount. Functions allow you to extract all text, certain lines, text between two sets of characters or extract by line number.
Category: Dial Up Networking
Developer: Sobolsoft - Download - Buy: $19.99
extracting emails - lines - g mail - webmail - attachments
Update: December 14, 2020 (7:20AM ET): You’re not alone! Gmail and several other Google services are all suffering from service disruptions and account authentication issues right now. You can read the full story over here — we’ll update that post as we know more.
Original article: May 10 2019 (12:00 AM ET):Gmail is one of those services that you don’t really think about until it’s gone. Is Gmail not working for you today? When it hits the fan, you need to get it fixed, but how? We’re here to help, as we break down the five most common Gmail issues and how to fix them.
Gmail not working? Check Google Status Dashboard
Is Gmail not working for you? First of all, click this link, then bookmark it, then tattoo it onto your left bicep, just in case. This is the link to Google’s app status Dashboard. If there is ever an outage, suspected outage, or credible report of an outage of any Google service — so anytime Gmail’s not working — this site will let you know. On the page, you’ll see a list of all the apps in Google Suite, and a list of dates leading up to the current date. Orange dots indicate there is or was trouble. You can go back about two months to see old outages too, if need be. Otherwise, if you’re having trouble with any Google app, this should be your first stop — after this article, that is.
Nuclear option
This is a little tongue in cheek, but often when you’re having trouble with your Google account, removing the account from your mobile device and setting it back up again will resolve a lot of problems. The beauty of a Google account is that everything is stored in Google’s servers — your mail, your documents, your movies and videos, etc. All of those will come back, once you reset up your account. It is a nuclear option of sorts, but it’s also the easiest way to wipe everything and bring it all back. It’s nuclear, but simple.
To do so, go into your settings area -> Accounts -> Google -> (tap the account you want to remove) -> tap the ellipsis in the upper right corner -> Remove account. Keep in mind that the process may be slightly different depending on your device and Android version.
Forgot password
One of the most common reasons someone loses access to their Gmail account is because they have forgotten their password. Not everyone can use the passphrase “MargaretThatcheris100%sexy,” so we get it. Fortunately, Google has a number of tools you can use to recover that password. Fair warning — it’s not a lot of fun. Have you ever noticed that any time you forget your password on another service, like Netflix, the recovery option is almost always to have it emailed to you? Well, that won’t work if you’re trying to log into an email account.
First, it’s critical that you set up alternative contact methods attached to your Google account. Log in to your Gmail account, click your profile pic in the upper right corner, and then select “Manage your Google account.” Tap the “Security” tab and locate the “Ways we can verify it’s you” option. Next, make sure the two options — Recovery Email and Recovery Phone — are filled out. These are the recovery methods you can use to get access to your account back.
Two-step verification issues
Two-step verification is one of the best methods you can use to secure your account. Briefly, two-step verification adds a second layer to your security by requiring a second acknowledgment of a login attempt. For example, if you log into your Gmail account, you’ll receive a text message with a code you must enter in order to proceed. But things don’t always go smoothly. Sometimes, the code doesn’t get there. What then?
First, you need to make sure you’re in an area with good signal. Google sends 2-step authentication codes via SMS, so if you’re in an area with strong Wi-Fi but not good cell signal — I’m looking at you, downtown Chicago — that could be part of the problem.
If so, you can use the Google Authenticator app. Simply download the app on your phone. Once installed, you’ll be asked how to verify the account. The easiest is with a QR code. On your computer, go to the two-step authentication page, and scroll down to Authenticator App. Click on that and follow the steps to scan the QR code. Once scanned, you’ll get a code in the app. Enter that code into the “Verify” box on your computer, and it will link the phone to your account. From then on, you’ll use the Authenticator app to log in, rather than SMS codes.
If that won’t work, you can also opt to receive a call on your backup phone. Of course, this will still not work if you’re in an area with a bad signal. However, you can choose for this to be a landline. The downside to that choice is that you have to be at the place where the landline is, but it is an option.
Finally, if all else fails, you can also use backup codes. Backup codes are generally used for occasions when you lose your phone, or cannot receive authentication codes by any other means.
These need to be generated in advance. Backup codes are sets of codes you can use to log into your account in lieu of your two-step verification. Backup codes come in sets of 10. These are one-time use codes — they become inactive as soon as you use them. If you generate a set of codes, all unused codes from your last batch are deactivated. Spoiler alert: I generated a new set of codes after taking that screenshot.
To generate a set of codes, visit the two-step verification page and scroll down to the backup codes area. Click on “Get new codes.” This will generate a text file for you to download, which will be called “Backup-codes-<yourusername>.txt.
If you want to use the backup code to sign in, go to the Gmail sign-in page and enter your username/password. When asked for the two-step authentication, click “More options” and then click “Enter one of your 8-digit backup codes.” Enter your code, and you’re good to go!
Sync issues
Bulk Gmail Account Creator
Gmail can fail to sync for a lot of different reasons, and a failure to sync can manifest itself in a number of ways. You may not have all of your messages, you may be failing to send email, you may receive an “account not synced” error message, or the app itself may just be slow. In any of these cases, you can try several steps to get things back up and running.
Update the Gmail app. Sometimes an older, outdated version of the app can have trouble getting mail from Google. Making sure you have the latest and greatest version of the Gmail app will resolve a lot of sync issues.
Restart your device. Have you tried turning it off and on again? Yes, it’s a cliché, but it works a surprising number of times.
Verify your connectivity. Yes, it’s a stupid question, but we have to ask. You can avoid a lot of unnecessary troubleshooting if you make sure you have a good signal, aren’t in Airplane mode, etc.
Check your Gmail settings. Should you have to make sure sync is on? No. But you do. Accidental taps happen, and if Gmail sync gets turned off, nothing gets synced. Open the Gmail app, and tap the menu button in the upper left corner -> Settings. Tap on your account and make sure you’ve checked “Sync Gmail.”
Clear your Gmail app data. Open your device’s Settings app -> Apps & Notifications -> App Info -> Gmail -> Storage -> Clear Data -> Ok. Once you’re done with that, restart your device and see if that did the trick. Most of the time that will work.
Missing messages
If your Gmail is missing emails that you know are in there, the most likely cause is that you accidentally deleted or archived them. You can check this easily enough by clicking on the Trash folder in Gmail. Most often you can find the trash folder by clicking “More” in the folders area, then clicking “Trash.” If the email is in there, it may be archived. In the area where you clicked “More,” look for “All Mail.” That will show you all mail, whether archived or not.
You can also search for mail by typing in the search box. In the “All Mail” folder, search for archived email, but remember that it won’t search the Trash folder. Most of the time, your email will be in the trash or archived — I’m no stranger to that myself. If you find the email in either place, click on it to open it, then click the folder icon at the top, then choose “Move to Inbox.” That will restore the email to your inbox and you’ll be able to see it normally.
Bonus! Gmail won’t load (browser only)
If you’re logging into Gmail with a web browser, and the web page will not load for you, there are a few things you need to try to get things back up and running again. First, you’ll want to make sure you’re using a supported web browser. You can find a list of supported web browsers in Google’s help site. It’s fair to say that most modern web browsers will work, but Opera users will be out of luck, I’m afraid.
Often, browser extensions or applications can interfere with Gmail as well. A quick way to check on this is by trying out Gmail in the web browser’s private or incognito mode. If Gmail works there, try disabling browser extensions one-by-one until you find the culprit.
Sometimes cookies or temporary files can break Gmail as well. The same test — using incognito mode — is a quick way to test that behavior as well. If Gmail works in incognito mode, but disabling extensions didn’t help, clearing your cache and cookies should do the trick.
Finally, you might want to try disabling any Google labs you have running. The easiest way to do that is to visit this website. This will automatically disable any labs you have running so you can test the Gmail client without them. If it works, again, try disabling all labs, and re-enabling them one at a time. If Gmail fails again, you have your culprit.
Anything else?
Gmail is one of those services that usually just works, and it’s wonderful. It is an awful feeling when it goes down. Hopefully, some of these tips have helped get you back on track. If there’s anything you’ve run into that you can’t figure out, let us know. Of course, if there’s something we haven’t covered that you’d like to see, hit us up in the comments. If you have any other tips, feel free to drop us a note in the comments, and we’ll be sure to update the article in the future.
Other Gmail-related content:

1 note
·
View note
Text
Adobe acrobat dc free trial

#Adobe acrobat dc free trial how to#
#Adobe acrobat dc free trial pdf#
#Adobe acrobat dc free trial full#
#Adobe acrobat dc free trial full#
If you don't cancel your trial before the 7 days are over, you're then charged $14.99 a month, though Adobe will refund you in full if you cancel within 14 days. But its free trial can't be downloaded without giving payment info, as though you were actually buying it. Trial version requires credit card info and physical address: Granted, Adobe products have been historically prone to piracy, which is one of the reasons why the company's moved to a subscription model. You can also give Adobe a phone number that it can call if you need to recover your account. Alternatively, you can opt to receive the code via email, but authentication apps are still the ideal method. Secure log-in options available: Adobe offers two-step verification to confirm your log-in, although it sends a text via SMS instead of sending a code to an authentication app, the latter of which is more secure because the verification code is a lot more difficult to intercept. This is a lot handier than having to manually move a file from one device to another, and a more reliable method of file retrieval.
#Adobe acrobat dc free trial pdf#
Syncs with iPhone and Android version: "DC" stands for Document Cloud, which works basically like Google Docs - once you're logged into your Adobe cloud account on your PC, you can start editing a PDF there and read it later on an iPhone or Android device that has the Acrobat Reader mobile app installed and set up. It streamlines getting a signed document back and lets you track what's signed and what isn't. Semi-automated signature requests: If your job has you frequently sending out documents and forms to be signed, the Send for Signature feature may be a lifesaver. Then each change can be tagged as "Accepted," "Rejected," "Cancelled," or "Completed." Like Google Docs, this change tracking tool can genuinely streamline your workflow and help you avoid mistakes in the final product. Acrobat will actually analyze the text and highlight changes. If you're just editing the occasional document, this won't be a big deal, but it should be handy for people who have to wrangle a lot of PDFs on a regular basis.ĭocument comparison: This is more than just looking at two files side-by-side. Adobe Acrobat does the same thing with PDFs. With this function, you could track all of your open web pages at a glance, without cluttering your task bar. Tabbed viewing: When the Mozilla Firefox web browser first appeared, one of its major distinctions was tabbed browsing. The website also has a User Guide, which is basically an online manual. Clicking on the "?" icon in the upper right opens up a web page with seven more videos for beginners, and seven for experienced users, all ranging from one minute to 13 minutes in length.
#Adobe acrobat dc free trial how to#
If you say that you're a beginner, the app will show you a few major features, walk you through exporting a PDF to Microsoft Word, show you how to scan a document, and even play a one-minute video about editing PDFs. Substantial tutorial info: During the download process, you're asked about your level of familiarity with Acrobat. Is it worth the high entry fee? Let's find out. From the beginning, Adobe Acrobat has been the default app for tackling this task, and Pro DC is the company's top-of-the-line version. A variety of apps and programs can read PDF files, but if you want to create or edit a PDF, things can get complicated.

0 notes
Link
The first step toward a sound and secure RPA infrastructure begins with an understanding of the core Architectural components of the solution, their operations, and the requirements for secure RPA platform.
Securing RPA Platform
Security measures to be considered while designing secure RPA platform. Below mentioned are few steps Automation Anywhere takes for ensuring all of the data is protected.
Multi-layer identification and authentication
A security level let you determine how strong the identity of user is or if he is really the user he claims to be. It is very clear that a user logged from company network is more trustworthy then someone logged in from the internet.
It is necessary for fixing security in order that humans and bots must be authenticated before accessing or performing actions within the RPA platform
Automation anywhere offers flexibility to have single or multi-factor authentications and application credentials in the Control Room, which manages and monitors all processes of the infrastructure. This involves integration with Microsoft Active Directory using LDAP, Active Directory using Kerberos and native authentication using the embedded Credential Vault for identity and access management
You can also use an external third-party-privileged access system (Burp suite, Nessus Scanner, Open Web Application Security (OWASP), Black Duck) or support for SAML 2.0 based single sign-on (SSO)
Multi-Level Authentication allows you to define, assign levels to your users and protect your services based on below strategies:
Contextual-based
Credential-based
Authenticator-based Encryption
Encryption
Encryption can ensure a basic level of security for all sensitive data so that it remains hidden from unauthorized users. Encryption is vital because it allows you to securely protect data that you simply don’t want others to possess access.
Many RPA tools allow for the configuration and customization of encryption methods, from securing specific types of data to safeguarding against the interposing of network communication
Encryption is majorly effective when implemented with a comprehensive information security plan
RPA provides file and text encryption
Access control
Though RPA replaces humans with bots, people still need to work with bots to schedule, run, and view and edit their processes. To successfully and securely do that, security admins must be ready to specify who does what — access control for humans and bots alike is critical. Access control for humans and bots is critical.
Audit logs
RPA platforms, provides comprehensive audit logging, monitoring, and reporting capabilities.
Extensive audit logging is performed for 185+ activities on Automation Anywhere platform. Comprehensive and continuous audit logging capabilities within the Enterprise room enable you to spot and alert abnormal activities like bot performance errors, misuse by employees, malicious code so on
It ensures enterprise-level security and audit compliance
Full audit trails enable you to make quicker and cleaner audit reports, and make sure that you’ll retrace the steps that led to a selected problem, be it a mistake within the robot’s performance, malicious code or other misuse by an employee
Bot-specific security
It is important that the bot code be secured from piracy. Because bots mimic users, they interact with applications using keyboard and mouse peripheral inputs.
How can I secure my RPA environment?
For leveraging the cyber security your organization approach should provide the following:
Integrity
Traceability
Confidentiality
Control
How can RPA improve your security organization?
Decrease time to detect and respond to incidents, helping minimize risk exposure to an attack
Minimize employee turnover due to lack of challenge or career progression by permitting employees to focus on higher value tasks
Make intelligent decisions quickly, leading to high-quality and consistent outcomes
“Milind Bibodi is a consultant at Systems Plus. The content of this blog is personal & for information purposes only, and is subject to change. Reader discretion is advised”
0 notes
Text
Why Test Automation Services Are Important Factor?

Testing is essential since most of us make mistakes. A few of those mistakes aren't significant, but a few are costly or might be life-threatening. We must check everything we create since things can go wrong; individuals can make mistakes at any given moment.
What's Testing Necessary?
The outcomes are categorized as insignificant or devastating, based on the effects of the mistake.
The need for rigorous testing along with their related documentation through the program development life cycle appears due to the below reasons:
· To Recognize flaws
· to Lessen defects in the part or system
· Boost the general quality of the machine
There may also be a necessity to do software testing to follow lawful requirements or industry-specific criteria.
The points below reveals the Importance of analyzing for a Trusted and Simple to Use software product:
· Test automation services is essential as it finds defects/bugs prior to the delivery to the customer, which ensures that the quality of the program.
· By way of instance, suppose you're using a Web Banking program to transfer the sum for your buddy account. Thus, you begin the trade, receive a successful trade message, and also the sum also deducts from the accounts. Nonetheless, your friend affirms that his/her account hasn't obtained any credits nevertheless. Likewise, your accounts is also not representing the reversed trade. This will certainly make you mad and leave you as a unsatisfied client.
· It's due to the improper testing of the internet banking software prior launch. Thorough testing of this site for all potential user operations would result in early identification of this issue. Therefore, an individual could fix it before discharging it into the public to get a smoother experience.
From the preceding example, we could observe that because of the existence of flaws , the machine failed to perform the necessary operation and did not fulfill the customer's requirements. Suitable testing techniques employed to every test degrees , together with a proper degree of evaluation experience, ensures a complete decrease in the frequency of these applications failures.
Let us take a look at how the testing could contribute to the achievement of the overall job:
Involvement of testers in-demand reviews and consumer narrative refinement- Involving testers through the demand phase guarantees identification of a number of their requirement flaws even prior to their execution. It considerably reduces the fixing price. Additionally, the tester profits significant job insight at this phase. That, in turn, assists him in the implementation stage of the job. Furthermore, it is going to aid in lessening the danger of basic design flaws and permits the identification of mistakes at an early period. What's more, in addition, it enhances the quality of integration situations and leads to a greater grade of flaws. It enables testers to perform more effective testing against client requirements. Testers also know places which are deemed risky by the programmer in order that they can correct their priorities so. This assists in replicating the bugs there and then, without moving via a protracted defect management procedure.
Testers Assessing and validating the application prior to its launch - This assists in discovering errors that otherwise might have gone undetected, and encourage the practice of removing the flaws that led to the failures. The implementation of evaluations at different levels increases the chance that the program will have fewer mistakes and meet up with the client's needs.
But without assessing software components under different anticipated and unanticipated conditions, the staff can't guarantee these facets. Consequently, testing is done to check every software component big and small.
To comprehend Software analyzing significance, let us look to the below tips:-
Thus, do not begin from scratch : Occasionally we examine a completely developed software product contrary to the consumer requirement and discover that some simple functionality was lost. It might occur due to a error in the demand gathering or even the coding stage. Then to mend such kinds of mistakes, we might need to begin the advancement again from scratch. Repairing such sorts of errors becomes really dull, time-consuming, rather pricey. Because of this, it's always desired to check the applications in its development period.
Assessing the simplicity of use of this software: simplicity of use is a very simple notion; it defines how readily the intended users may use the final product. The program testing ensures the building of the program product in a manner that fulfills the consumer's expectations concerning compliance with the needs at a comfortable, decent, and simplistic method.
Verification of all facets of the applications - it's possible to verify all of the facets of the applications in applications testing, like checking the fundamental functionalities in addition to analyzing a platform for unexpected problems. Sudden ailments can be out of a wrong data type or because of a piracy attack. Consequently, testing makes certain the system can take care of these situations quite well. Therefore, if we find a mistake beforehand, we've got the choice to fix them. It may prevent complaints when the software or program has attained clients.
Computer software tests help hasten development- computer software tests help programmers find mistakes and situations to replicate the error, which then enables them to repair it quickly. Anyway, software testers may operate in parallel with the development group, thus understanding that the layout, hazard regions, etc. in detail. This knowledge exchange involving testers and programmers accelerates the whole development procedure.
Conclusion:
In conclusion, the value of software testing is crucial. Software testing is a vital part of software product development since it enhances functionality and functionality. The principal advantage of testing is that the identification and subsequent elimination of these mistakes. But, testing helps programmers and testers to evaluate expected and actual results to be able to enhance quality. In case the software creation occurs without testing it, then it might be useless or occasionally harmful for clients. Therefore, a tester must put on a exceptional hat that shields the trustworthiness of the application and makes it more safe to use in real life situations.
0 notes
Text
What is the purpose of IoT?

IoT or internet of things lately we hear this word quite often. Words like cyber-attacks, hacking, we can hear it too together with IoT. Despite this, fears of piracy and cyber-attacks on the internet and IoT applications will grow much faster in the coming years. In the end we can say the scope of the future IoT or the future of IoT is very bright. There will be lots of IoT devices coming soon.
IoT or the Internet of Things is primarily a full system of all interconnected computing devices, having all mechanical and digital machines. When objects or living things have UID or Unique Identification, IoT and IoT applications can transfer data automatically without including human-to-human interactions and human-to-computer interactions in between.
Internet of Things or IoT objects can be either artificial hearts in humans or biochip transponders in farm animals or sensors containing cars. All of these things are important for human survival. Along with the increase in the organization so that the needs of the organization that can make work run easier in an efficient way.
How many IoT devices are there now?
According to Gartner:
In 2017 there were 8.4 billion devices connected to IoT worldwide. While in 2018 it increased to 9.2 billion. It is hoped that by 2020 IoT-connected devices worldwide will be 20.8 billion.
It's hard to secure smart things that have a base attached to this, including items such as TVs, refrigerators, and security cameras. We can expect that there will be a 31% increase in IoT applications and IoT connected devices this year. While this can also reach 10 billion or more, which is more than the world's population.
IoT is useful because it makes our work easy and very less time-consuming. Come on, taking into account the smartphones that we use, make our lives so easy and a lot of our work can be done with just a fingertip.
IoT has facilitated human life. Imagine a hospital connected to all smart devices. All data collected from the device saves the patient information and then carries out analysis on any machine that the doctor or authority wants to examine. Make life easy and orderly, make the hospital run as optimal as possible.
This clearly shows the seriousness, and how important IoT is today.
Is the IoT device safe?
Basic and important questions that are on everyone's mind. Are all IoT devices that we use safe and protected? But people still haven't found much to secure the Internet of Things device.
Cisco, one of the largest network companies, told the Global IoT device supply chain that requires the most powerful and higher vigilance regarding quality control. Due to the lack of proper rules, regulations and IOT security standards, hacking of IOT and IOT applications is very common and dangerous.
The security of IoT devices is in the hands of the manufacturers. The manufacturer must ensure that all Internet of Things devices must be safe and secure to use. Safety is something most businesses miss. According to the survey:
Only 30% of 1000 respondent companies said that they took certain steps to secure all Cellular Applications and IoT devices. At the same time, the rest of the IoT device markers do not build up any security breaches.
We can even take many examples such as cloud-based websites like Netflix, Spotify and Reddit suddenly become unavailable in October 2016. The attack occurred when unknown hackers or destroyers began to gain control of IoT-based applications such as CCTV cameras, digital video recorders .
With this type of instance, we can say that our data and IoT devices are not as safe as they should.
What device is IoT?
Today, if we look around us, we can see that most of the IoT-based devices. So, we list all the popular IoT devices, which are addictive now.
First, out of all Smart Home Automations, we examine carefully, most homes opt for Home Automation. As a matter of safety, and those who want houses that are built automatically and smartly.
Voice Assistant, there is no home that does not have Amazon-Alexa or Google Echo in their home. People began to feel this voice assistant as part of life.
Smart Bands or Fitness Bands.
GPS tracker
Smart Smoke Alarm
Smart Locks
Camera Bell
Amazon Dash Button
IoT-based Security System
Home Wifi System mesh
This device is the most widely used IoT based product. However, there are more devices out there, which people use. It can easily be said how IoT has become an important part of everyone's life.
It is clear that the future of IoT is vast and will increase, without pause, people will be more dependent on the Internet of Things. Although we can even predict that in the near future, people can't even imagine their lives without an IoT device.
What is the scope of IoT in the future?
The future of IoT or where and what progress we can see in the future of IoT or after 25 years. You can see the top five themes that can be seen in the future from IoT listed below:
People will be addicted to Tech connections
The survey shows that the use of IoT-based devices will increase rapidly. This will affect people over the coming decades. There will be some magic things that will make people addicted to the device and people can't refuse to leave it. Its convenience and benefits will make people interested in the device.
In the future, we can even hope that people will choose connectivity over security. As connected with the community, friends and new technology with comfort will become more critical. People will even start storing all of their information data about themselves and their families on this device, and they start trading safety and security for convenience. Users will start making all rational decisions by risking their security and safety.
Children, adults, everyone will be addicted, and the house will be a big IoT device. While humans will not be able to overcome all this.
Conclusion:
IoT has the potential to dramatically increase the availability of information and is likely to transform companies and organizations in almost every industry throughout the world.
Thus, finding ways to increase the strength of IoT is expected factors become the strategic goals of most technology companies, regardless of their industrial focus.
Fusion Informatics leads the IoT development company Indianapolis, where our IoT development team helps build applications that allow your customers to experience a user-friendly experience in every aspect. Our application works smoothly without strong and innovative errors combined with smart Artificial Intelligence, which helps increase sales and productivity.
For more details visit:
AI Company in san Francisco
Best Mobile App Development Companies Los Angeles
Top blockchain app development company in Indianapolis
best mobile app development companies san Francisco
0 notes
Text
The Rise of the ‘Liberaltarian’
Tech industry millionaires are moving the Democratic Party to the left on almost every issue except government regulation. Unions beware.
Political economists Neil Malhotra and David Broockman have documented a new species of political animal: the liberaltarian.
Malhotra, the Edith M. Cornell Professor of Political Economy at Stanford Graduate School of Business, and Broockman, a former Stanford GSB professor who recently moved to the University of California, Berkeley, set out to quantify the political beliefs of one of the most powerful groups of businesspeople in the country: successful technology entrepreneurs.
What they discovered flies in the face of much received wisdom about the politics of America’s technology elites.
When it comes to trade, taxation, and social issues, wealthy founders are more liberal than all but the most ardent progressives. But when it comes to regulation, they are more conservative than most Republicans, and in fact look more like libertarians. That unique combination of attitudes has powerful implications for how they might wield their growing political power to mold government policy.
Broockman and Malhotra discuss the origins of their research, how they conducted it, and what it tells us about the future of American politics.
What prompted this research?
Broockman: We’re both really interested in using tools for understanding public opinion to explore how the economic elites who are gaining power in our society think about American politics.
Malhotra: We were speaking with a former TechCrunch journalist at the Battery, a club for Silicon Valley movers and shakers, and we realized that while there’s been a lot of talk about the political beliefs of Silicon Valley elites — and by that we mean technology elites across the country — we have no hard data on what they actually believe when it comes to politics and policy.
Broockman: For example, some people say Silicon Valley is really libertarian, while others say technology entrepreneurs are just like loyal Democrats and are far to the left on social issues. We thought this is an increasingly important topic to understand in American politics.
How so?
Broockman: History is replete with examples of wealthy businesspeople, such as railroad executives and Wall Street bankers, who have changed the course of American politics through their tremendous political influence. And many of the most valuable firms in the U.S. are now technology firms. They have hundreds of thousands of employees, and their founders are amassing ever greater political influence. But while many researchers have thought about the way people on Wall Street view politics, there’s been much less research concerning Silicon Valley. We wanted to think more clearly about what the Silicon Valley elite thinks and collect some data on it.
Malhotra: We’re at a unique moment in American history. Forces like income inequality, globalization, and automation are going to dramatically change the way society and politics function. We’d love to go back in time and ask the railroad executives how they changed policymaking in the run-up to the Gilded Age, and that’s exactly what we had the chance to do here: to ask technology elites how they actually think about politics, and to explore what that means for politics and policy at this inflection point in American history.
But why focus on technology entrepreneurs in particular? What makes them special beyond sheer economic clout?
Broockman: Our analysis wasn’t motivated only by their economic power. Many other firms have that: They have lots of employees, they can donate a lot of money to political candidates and parties, they can decide where to put jobs. What makes Silicon Valley different from the railroads or Wall Street banks is that they also have a lot of eyeballs; Americans spend a lot of time looking at their smartphones every day. We saw the impact of this several years ago in the fight over the Stop Online Piracy Act and the PROTECT IP Act, which many tech firms opposed. Google put a little text on its homepage saying, “Please contact your senator,” and Congress was inundated with calls and dropped the bills overnight.
Malhotra: They’re also unique in that they have access to so much data. We’re just beginning to understand the concept of data as capital, but the power to capture so much data about what everyone is doing — and to leverage that data for political influence — should not be underestimated.
Who exactly did you target, and how?
Malhotra: We merged data from Crunchbase, a professionally run database of individuals in the technology industry that contains information on the size of firms and how many rounds of funding they’ve received, with contact information for more than 4,200 founders and CEOs. Then we emailed them all a survey.
Broockman: More than 600 people who have founded successful companies responded. Most are millionaires, and their companies have raised more than $19.6 billion in venture capital.
Malhotra: At the same time, we surveyed more than 1,100 members of the elite donor class — the people who donate large amounts of money to political campaigns — and more than 1,600 ordinary citizens. So we had three very diverse groups of people answering the same exact questions about politics.
What kinds of questions did you ask?
Broockman: Traditionally, when people talk about politics they think in terms of left and right, or about economic issues and social issues. We wanted to break things down a little more, so we divided the issues we wanted to address into four domains.
The first, redistribution, involved questions like, “Should we tax wealthy people to fund universal social programs?”
The second, regulation, involved questions such as, “Should we require companies to treat gig workers as regular workers or not?” and “How much should the government be involved in structuring and regulating marketplaces?”
The third category involved social issues: abortion, gay marriage, the death penalty.
And the fourth concerned globalism, which involves issues like trade and immigration that have an impact on the welfare of people around the world.
What did you learn?
Malhotra: The big finding is that technology elites are basically liberal on every dimension you could imagine except regulation. They are more liberal than traditional Democrats on the redistributive dimension, the social dimension, and the globalist dimension. But they’re as conservative as Republican donors on the regulatory dimension. And this is especially interesting because no other group of people we surveyed had this particular constellation of political beliefs.
Tech elites are more liberal than traditional Democrats on the redistributive dimension, the social dimension, and the globalist dimension. But they’re as conservative as Republicans on the regulatory dimension.
Neil Malhotra
Specifically, tech elites are not easily categorized as libertarians when it comes to economic issues, because they believe in the redistribution of income for things like health care, education, and poverty reduction. But at the same time, they believe that government should not be regulating business. So their overall approach is unique: Let the markets operate how they should and redistribute income after the fact. Some people have called this new type of political animal the “liberaltarian.”
As founders and CEOs, couldn’t their antipathy to government regulation simply be explained by self-interest?
Broockman: I’m sure that at least some of their political views have to do with self-interest. But we showed that their values and predispositions — in particular, a favorable predisposition toward markets and entrepreneurs, and a negative predisposition toward government control — are important too.
Malhotra: We ran an experiment where we divided people into two groups. We asked Group A if the price of an Uber car should go up when there’s a lot of demand. This is a classic example of surge pricing or price discrimination, and most ordinary people in our survey, whether Democrat or Republican, were very divided on the issue — about half of people in both parties said that you should raise prices on Uber cars when there’s a surge in demand. But basically 100 percent of technology elites said it’s OK for Uber to raise prices during a surge, which is what you would expect people who firmly believe in free markets to say: Yes, the price should rise to meet the demand.
Now, you might say that’s simply a matter of self-interest. They want Uber to raise its rates because they want the technology industry to do better. But remember that there were two groups. And Group B got a question that addressed the same core concept of price discrimination but had nothing to do the technology industry; namely, is it OK to raise the prices of flowers on Mother’s Day or Valentine’s Day, when demand is higher?
Again, ordinary people split roughly 50/50 on this question. But almost 100 percent of technology elites still thought that it was OK to surge price flowers on Valentine’s Day or Mother’s Day. This shows that there are some genuine values at work, and not just a desire to increase profit margins in the tech industry.
Broockman: In political disagreements, we often assume that our opponents are speaking in bad faith. But our research shows that while their views might be informed by self-interest, many technology entrepreneurs genuinely believe as a matter of principle that markets should be freer and that entrepreneurs and enterprises — whether they are florists or companies like Uber — should have a freer hand in labor markets.
That finding is supported by a survey we conducted of Stanford undergraduates. When we compared students majoring in the natural sciences to students majoring in computer science – many of whom we know will go on to found tech firms — we saw these same differences in values and predispositions. So it seems that these patterns are already present when people are still in their late teens and early 20s, before they’ve founded companies or thought about stock options.
So you’ve got this unique group of people who are super-liberal in most respects but super-conservative when it comes to regulation. They’re also rapidly accumulating political power, and they tend to support the Democratic Party. What does all that mean for American politics?
Malhotra: Historical research has found that political parties usually change when important groups within those parties agree with them on most things but disagree with them on a few things — and then shape the parties in their direction. This pattern has emerged over and over again in American history. So our research suggests that as technology elites become more important to Democratic Party fundraising, they are going to double down and promote traditional Democratic interests when it comes to social policy, redistribution, foreign policy, and immigration, but move the party toward the right when it comes to regulation.
Broockman: We’re already starting to see signs of tension within the Democratic Party overregulation of labor markets. Take Uber again: Should gig workers for Uber be treated like regular workers or as contractors? Labor unions, which have historically held considerable influence within the Democratic coalition, believe it’s important that gig workers receive all of the protections of traditional employees. Whereas technology entrepreneurs say, “No, we shouldn’t be regulating how these companies treat their workers; we should allow them freedom in the marketplace.”
Such tensions within the Democratic Party are going to become increasingly common as the big tech-sector donors to Democratic campaigns start to say, “Actually, we disagree with the labor unions that are endorsing you. We think you should take a different position on this issue.”
How might the growing political power of tech elites — and the differences between their political beliefs and those of ordinary citizens — affect society at large?
Malhotra: The gap between elites and masses is a major political concern. Since World War II, there’s been an agreement of sorts that some power would shift to elites, who would then look out for everybody’s interests. But increasingly we’ve seen populist movements arising in the United States and around the world as people have realized that wages have stagnated even as expenses have gone up, in real terms, on things like health insurance and college tuition, and that their children are going to have a worse of standard of living than their own. So there’s a lot of discussion about how our democratic institutions can survive without cooperation between masses and elites.
But up until now, there really was no data on what elites actually believe. More work needs to be done so that we can understand the potential political fault lines both in the United States and abroad.
Broockman: We’re trying to understand the areas of disagreement between the elites and the masses. What policies do elites in both parties agree upon that the general public might oppose?
That produces some counterintuitive but important findings. For example, the technology entrepreneurs we surveyed were among the strongest supporters of universal health care. Understanding that can prevent us from leaping to simple conclusions like, “When the wealthy get more power, there will be less redistribution.” That might not be true if the wealthy people come out of the tech industry.
source https://scienceblog.com/516890/the-rise-of-the-liberaltarian/
0 notes