#breadth first search in c source code
Explore tagged Tumblr posts
Text
C Program to implement BFS Algorithm for Connected Graph
BFS Algorithm for Connected Graph Write a C Program to implement BFS Algorithm for Connected Graph. Here’s simple Program for traversing a directed graph through Breadth First Search(BFS), visiting only those vertices that are reachable from start vertex. Breadth First Search (BFS) BFS is a traversing algorithm where you should start traversing from a selected node (source or starting node) and…
View On WordPress
#BFS#bfs algorithm example#bfs algorithm in c#Breadth First Search#breadth first search algorithm#breadth first search algorithm with example#breadth first search connected components#breadth first search connected graph#breadth first search example#breadth first search example for directed graph#breadth first search for directed graph#breadth first search for graph#breadth first search in c#breadth first search in c source code#breadth first search pseudocode#breadth first search strongly connected components#c data structures#c graph programs#connected components of a graph example#strongly connected graph example
0 notes
Link
The problem: Determine the max depth of a binary tree, given a pointer to the root node.
The solution: A C++ one-liner solution using DFS: (source: user makuiyu)
int maxDepth(TreeNode *root) { return root == NULL ? 0 : max(maxDepth(root -> left), maxDepth(root -> right)) + 1; }
But what does it mean!
makuiyu designed a recursive function that uses the short-hand if...else, or ternary operator, statement in C++:
variable = (condition) ? expressionTrue : expressionFalse;
In the above case, the condition is (root == NULL), or, if the pointer to the root node is null. If the pointer to the root node IS NULL (evaluates to true), then we return 0. If the pointer to the root node is NOT NULL (evaluates to false) then we return 1 plus the max of the recursive calls to maxDepth(root->left) and maxDepth(root->right).
This means we do a Depth First Search through the tree, going all the way down the left child of the root path (exploring all children in that path), and then moving to the right child of the root path (or vice versa? When I ran this in visual studio it seemed to do the right path first. C++ doesn’t (or didn’t?) specify the order in which function arguments are evaluated).
When we reach a base step (the node being null) we return 1, and we recursively add 1 to this to get the max depth.
0 notes
Text
Solving the 8 puzzle problem using A* (star) algorithm
In this tutorial, we will solve the 8 puzzle problem using A* (star) search or pathfinding algorithm. Besides, the primary algorithm (A*), we will also use breadth-first, depth-first and greedy best-first search algorithms to find a solution for the 8 puzzle problem. We will approach the solution by first modelling the problem, then by building the fundamental blocks and finally applying a solver to solve the puzzle. Read Also: How to Generate Mazes Using Depth-First Algorithm This tutorial will provide the solution both from the algorithmic perspective as well as by providing the implementation of the algorithms using C++ for a console program and C# for Unity scripting. Finally, we will implement an 8 puzzle game using Unity and solve a random state of the puzzle by applying the A* algorithm. Click to Play the Unity Game
Introduction
Typically A* (Astar) is used in a grid-based pathfinding problem. However, as a general rule, any pathfinding algorithm (A* included) can be used to solve any graph-based problem. For a very detailed understanding of path-finding, I suggest the brilliant tutorial maintained by Amit in his Stanford’s site. In this tutorial I am not going to go through the theory of A* pathfinding, but rather, I would implement all necessary functions for A* pathfinding to solve the 8 puzzle problem.
The 8 Puzzle Problem
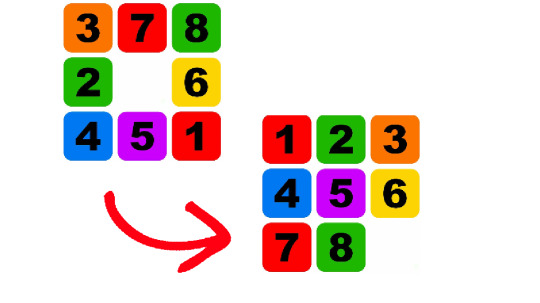
The 8-puzzle problem is a puzzle that was invented and popularized by Noyes Palmer Chapman in the 1870s. The 8-puzzle is a smaller version of the slightly better-known 15-puzzle. It comprises a 3-by-3 grid with 8 square blocks labelled 1 through 8 and a blank square. The goal is to rearrange the blocks so that they are in order with the blank sometimes at the start or at the end. The diagram above shows one possible initial configuration and the goal. To reach the goal state you are permitted to slide blocks horizontally or vertically into the blank square.
Before we can solve the puzzle we will need to model the problem. But what is meant by Modelling the Problem? In generic terms, modelling a problem is the art of formulating the problem at hand in terms of precisely described, well-understood building blocks and logic to reach a solution. In computer science, proper modelling is the key to applying algorithmic design techniques to any real-world problems. Real-world applications involve real-world problems. You might be working on a system that simulates air traffic in and around an airport, you might be working on optimizing the dispatch of delivery vans for an e-commerce application, or you might be working to search through patterns in a large image set. To solve such problems you will use some sort of modelling techniques to reduce the problem in terms of rigorously defined abstract structures such as graphs, trees, permutations, sets and so on. For our 8 puzzle problem let’s see how we can model the problem. Let’s take a random state of the 8 puzzle as given in the diagram below. From this random state, we can either slide tile 8 up, slide tile 3 right or slide tile 6 left to create three variant states.

Each of these three states will produce subsequent more states (3 for the first, 1 for the second and 1 for the third) and so on. This continues until we find the goal state. Hence, we can see that we can transform the various possible states of the 8 puzzle problem into a tree data structure.

In the following section, I will start creating the building blocks for the puzzle solution and then finally try to join them together to reach the solution.
The 8 Puzzle State
The first step towards solving the 8 puzzle problem will require a data type to represent the tiles on the puzzle. I will call this the State of the puzzle. A state is a unique combination of the tiles. During our process of solving we will need to store hundreds of perhaps thousands of tile states. Each combination of tiles in the puzzle will be a unique state. Each unique state of the tiles will represent a Node in the tree data structure. I will use integer array to represent a state. The indices of the array will refer to a tile location whereas the value in that index will represent the tile number. Look at the diagram below. In this diagram, a unique state of the tile is shown on the left. On the right, an array representation is shown to store the tile information.

Thus, we see that by using a one-dimensional array we can represent any state of the puzzle. The indices of the array, which cannot change, represent the fixed location of the tiles. In our case, we have assumed that array index 0 represents the top-left tile, index 1 as top-centre tile, index 2 as top-right tile and so on until index 8 as the bottom-right tile. The value stored in each of these indices will represent the actual number (or picture) on the tile. For example, in the above case, we have index 0 having tile 0 (or the empty tile), index 1 having tile 3 and so on until index 8 with tile 2. Points to Ponder Can we implement the state using a 2-dimensional array?How will you represent the tile indices using a 2-dimensional array?Can you try out a few examples using a 2-dimensional array? We can thus see that by manipulating the values on the array, with the constraint of where the empty tile slides into for each move, we can arrive at the goal state.

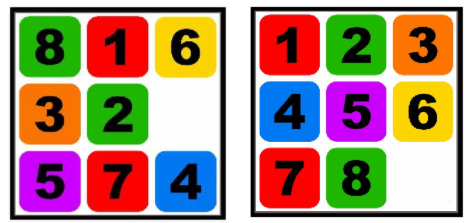
Goal State

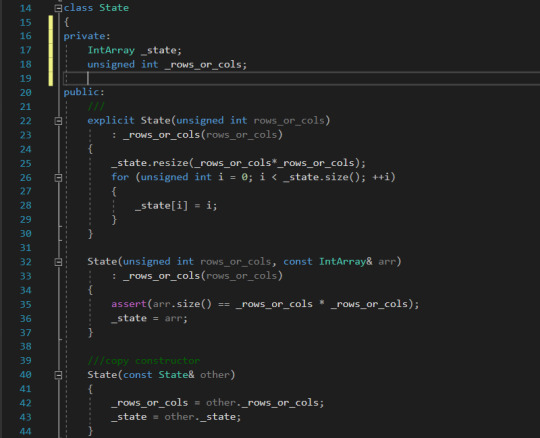
Goal state index array Design of State class Implement a class called State that will represent a unique combination of tiles. While implementing the class think about the range of functionality and behaviour that this class should expose. Give it a try before you look at the code.Implement a constructor or multiple constructors.Implement a copy constructor (if using C++)Implement a function that will return the index of the empty tile.Implement a function that will randomize the tiles to create a unique configuration of the puzzle.Any other functions that you can think of? Implementing State Class in C++ The class State comprises two variables (a) the integer array that defines the index array to represent the state and (b) the number of rows or cols. For 8 puzzle problem, this value is 3. Constructors The constructors for the C++ class is given below. We have implemented three constructors, viz., the (a) explicit default constructor that takes in the num_rows_or_cols, (b) the constructor that takes in the num_rows_or_cols and an initial state of the array and (c) a copy constructor.
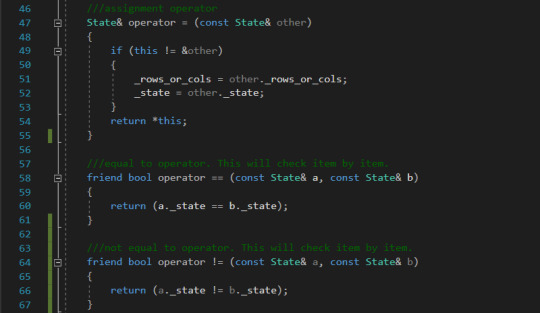
Operators The operator for the State class is given below. We have implemented the assignment, equal to and not equal to operators.
FindEmptyTileIndex This function returns the index of the empty tile for any given state of an 8 puzzle.
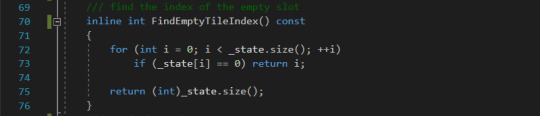
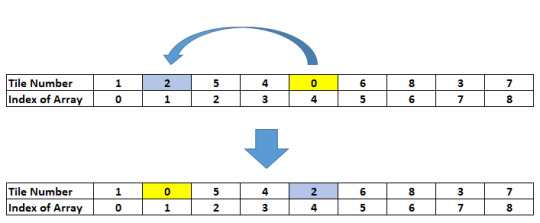
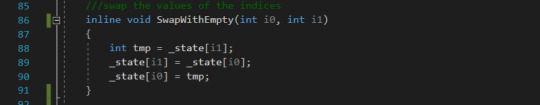
SwapWithEmpty This is the function that will be used whenever we slide the empty tile. By sliding the empty tile to an adjacent position we are essentially swapping the values of the index of the empty tile with the value of the adjacent tile.

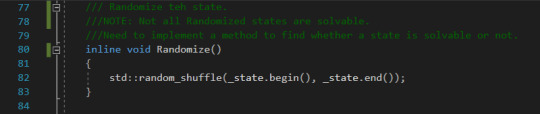
Other Helper Methods The other helper methods include the Randomize function that randomizes the state of the puzzle.
The Get and Set methods for getting and setting the index array of the state.

The print method for printing the state to an output stream. This is useful for debugging and/or showing output for the state.

C++ Code for State Class The following section provides the source codes for the class State. You can copy and paste from this section. #include #include #include #include #include //! A typedef of a normal integer array using std::vector for convenience typedef std::vector IntArray; ///class State ///A class to hold the state of the puzzle. ///The state is represented by a simple one dimensional array of integers. ///The value of o represents empty slot. class State { private: IntArray _state; unsigned int _rows_or_cols; public: /// explicit State(unsigned int rows_or_cols) : _rows_or_cols(rows_or_cols) { _state.resize(_rows_or_cols*_rows_or_cols); for (unsigned int i = 0; i { _state = i; } } State(unsigned int rows_or_cols, const IntArray& arr) : _rows_or_cols(rows_or_cols) { assert(arr.size() == _rows_or_cols * _rows_or_cols); _state = arr; } ///copy constructor State(const State& other) { _rows_or_cols = other._rows_or_cols; _state = other._state; } ///assignment operator State& operator = (const State& other) { if (this != &other) { _rows_or_cols = other._rows_or_cols; _state = other._state; } return *this; } ///equal to operator. This will check item by item. friend bool operator == (const State& a, const State& b) { return (a._state == b._state); } ///not equal to operator. This will check item by item. friend bool operator != (const State& a, const State& b) { return (a._state != b._state); } /// find the index of the empty slot inline int FindEmptyTileIndex() const { for (int i = 0; i if (_state == 0) return i; return (int)_state.size(); } /// Randomize teh state. ///NOTE: Not all Randomized states are solvable. ///Need to implement a method to find whether a state is solvable or not. inline void Randomize() { std::random_shuffle(_state.begin(), _state.end()); } ///swap the values of the indices inline void SwapWithEmpty(int i0, int i1) { int tmp = _state; _state = _state; _state = tmp; } inline const IntArray& GetArray() const { return _state; } void SetArray(const IntArray& arr) { _state = arr;; } inline unsigned int GetNumRowsOrCols() const { return _rows_or_cols; } void print(std::ostream& str, bool flat = false) const { for (unsigned int i = 0; i { for (unsigned int j = 0; j { unsigned int index = i * _rows_or_cols + j; if (flat) { str GetState() == _goal) { _solved = true; return; } int zero = current->GetState().FindEmptyTileIndex(); const IntArray& neighbours = graph.GetNeighbours(zero); for (int next : neighbours) { State state = current->GetState(); state.SwapWithEmpty(zero, next); if (!isInArray(state, _closedlist)) { NodePtr n(new Node(state, current, current->GetDepth() + 1)); _openlist.push_back(n); static int s_lineNum = 1; n->print(std::cout, s_lineNum++); //_closedlist.push_back(n); } } } private: typedef std::vector NodeList; NodeList _openlist; NodeList _closedlist; const State& _goal; bool _solved; Type _type; }; C# Code for Solver // The A Star search alogorithm implementation for solving 8 puzzle problem. // This is implemented as a coroutine for Unity. public IEnumerator SearchUsingAStar(State start, State goal) { PriorityQueue openlist = new PriorityQueue(); List closedlist = new List(); Node root = new Node(start, 0, null); root.Parent = null; openlist.Add(root); closedlist.Add(root); while (openlist.Count > 0 && !_solved) { Node current = openlist.GetAndRemoveTop(); if (State.Equals(current.State, goal)) { // fil the solution. Node s = current; do { _solution.Add(s); s = s.Parent; } while (s != null); Debug.Log("Solution found.." + "Total moves needed = " + _solution.Count); _solved = true; _solving = false; _solutionIndex = _solution.Count; break; } int zero = current.State.FindEmptyTileIndex(); int neighbours = Neighbours.Instance.GetNeighbors(zero); foreach (int next in neighbours) { State state = new State(current.State); //state.SwapWithEmpty(next); SwapTiles(next, state, false); if (!IsStateInList(state, closedlist)) { Node n = new Node(state, current.Depth + 1); n.Parent = current; openlist.Add(n); closedlist.Add(n); //n.Print(++s_lineNum); } } yield return new WaitForEndOfFrame(); } _layout.SetState(_solution.State); }
The main() Driver Program
This is the main driver program for the C++ version. For Unity version please continue reading. The main program starts with a start state, a goal state and the type of algorithm. It then goes into a loop of finding the solution by expanding the tree until the problem is solved. C++ Code for the Main int main(int argc, char* argv) { Neighbours g; State goal(3, std::vector{ 1, 2, 3, 4, 5, 6, 7, 8, 0 }); //State start(3, std::vector{ 1, 6, 2, 0, 4, 3, 7, 5, 8 }); State start(3, std::vector{ 3, 7, 8, 2, 0, 6, 4, 5, 1 }); std::shared_ptr node; Solver solver(start, goal, Solver::ASTAR); if (!solver.isSolvable()) { std::cout GetParent(); } while (s != NULL); // print the solution. std::cout Read the full article
0 notes
Text
New Library Material December 2018 - January 2019

Sorted by Call Number / Author.
220.5 H
Holy Bible : King James Version. Giant Print Standard Bible. U.S. : Christian Art Publishers, 2018.
220.5 H
The Holy Bible : Douay-Rheims version. [Catholic ed.]. Charlotte, N.C. : Saint Benedict Press, 2009.
221.5 O
The Old Testament : the King James version. New York : Alfred A. Knopf, 1996.
270.092 W
Westover, Tara, author. Educated: a memoir. First edition. Choose the good -- The midwife -- Cream shoes -- Apache women -- Honest dirt -- Shield and buckler -- The Lord will provide -- Tiny harlots -- Perfect in his generations -- Shield of feathers -- Instinct -- Fish eyes -- Silence in the churches -- My feet no longer touch Earth -- No more a child -- Disloyal man, disobedient heaven -- To keep it holy -- Blood and feathers -- In the beginning -- Recitals of the fathers -- Skullcap -- What we whispered and what we screamed -- I'm from Idaho -- A knight, errant -- The work of sulphur -- Waiting for moving water -- If I were a woman -- Pygmalion -- Graduation -- The hand of the almighty -- Tragedy then farce -- A brawling woman in a wide house -- Sorcery of physics -- The substance of things -- West of the sun -- Four long arms, whirling -- Gambling for redemption -- Family -- Watching the buffalo -- Educated. Tara Westover was seventeen the first time she set foot in a classroom. Born to survivalists in the mountains of Idaho, she prepared for the end of the world by stockpiling home-canned peaches and sleeping with her "head-for-the-hills bag." In the summer she stewed herbs for her mother, a midwife and healer, and in the winter she salvaged in her father's junkyard. Her father distrusted the medical establishment, so Tara never saw a doctor or nurse. Gashes and concussions, even burns from explosions, were all treated at home with herbalism. The family was so isolated from mainstream society that there was no one to ensure the children received an education, and no one to intervene when an older brother became violent. When another brother got himself into college and came back with news of the world beyond the mountain, Tara decided to try a new kind of life. She taught herself enough mathematics, grammar, and science to take the ACT and was admitted to Brigham Young University. There, she studied psychology, politics, philosophy, and history, learning for the first time about pivotal world events like the Holocaust and the Civil Rights Movement. Her quest for knowledge transformed her, taking her over oceans and across continents, to Harvard and to Cambridge University. Only then would she wonder if she'd traveled too far, if there was still a way home.
305 I
In Search of Stonewall: The Riots at 50 : The Gay & Lesbian Review at 25: Best Essays, 1994-2018. Boston: MA : G&LR Books, 2019.
305.896 B
Badkhen, Anna, 1976-. Walking with Abel : journeys with the nomads of the African savannah. "An intrepid journalist joins the planet's largest group of nomads on an annual migration that, like them, has endured for centuries. Anna Badkhen has forged a career chronicling life in extremis around the world, from war-torn Afghanistan to the border regions of the American Southwest. In Walking with Abel, she embeds herself with a family of Fulani cowboys--nomadic herders in Mali's Sahel grasslands--as they embark on their annual migration across the savanna. It's a cycle that connects the Fulani to their past even as their present is increasingly under threat--from Islamic militants, climate change, and the ever-encroaching urbanization that lures away their young. The Fulani, though, are no strangers to uncertainty--brilliantly resourceful and resilient, they've contended with famines, droughts, and wars for centuries. Dubbed "Anna Ba" by the nomads, who embrace her as one of theirs, Badkhen narrates the Fulani's journeys and her own with compassion and keen observation, transporting us from the Neolithic Sahara crisscrossed by rivers and abundant with wildlife to obelisk forests where the Fulani's Stone Age ancestors painted tributes to cattle. As they cross the Sahel, the savanna belt that stretches from the Indian Ocean to the Atlantic, they accompany themselves with Fulani music they download to their cell phones and tales of herders and hustlers, griots and holy men, infused with the myths the Fulani tell themselves to ground their past, make sense of their identity, and safeguard their--our--future"--. "An intrepid journalist joins the planet's largest group of nomads on an annual migration that, like them, has endured for centuries"--.
398.2 A
Abrahams, Roger D. African folktales. 1st ed. New York : Pantheon Books, c1983. Tales of wonder from the great ocean of story -- Stories to discuss and even argue about -- Tales of trickster and other ridiculous creatures: tales to entertain -- Tales in praise of great doings -- Making a way through life. A collection of 95 tales from the region south of of the Sahara Desert--stories from over 40 tribe-related myths of creation, tales of epic deeds, ghost stories and tales set in both the animal and human realms.
398.2 A
American Indian myths and legends. 1st paperback ed. New York : Pantheon Books, c1984. Rabbit boy kicked that blood clot around: tales of human creation -- The place of emergence: tales of world creation -- The eye of the great spirit: tales of the sun, moon, and stars -- Ordeals of the hero: monsters and monster slayers -- Counting coup: war and the warrior code -- The sound of flutes: tales of love and lust -- Coyote laughs and cries: trickster tales -- Four legs, two legs, and no legs: stories of animals and other people -- Something whistling in the night: ghosts and the spirit world -- Only the rocks and mountains last forever: visions of the end.
398.2 A
African American folktales : stories from Black traditions in the New World. New York : Pantheon Books, c1999.
398.2 C
Chinese fairy tales and fantasies. 1st ed. New York : Pantheon Books, 1979.
398.2 F
Favorite folktales from around the world. 1st paperback ed. New York : Pantheon Books, c1988.
398.2 F
Folktales from India : a selection of oral tales from twenty-two languages. First edition. Tell it to the walls / Tamil -- Untold stories / Gondi -- Gopal Bhar the star-counter / Bengali -- Bopoluchi / Punjabi -- The Jasmine Prince / Tamil -- Sona and Rupa / Hindi/Malwi -- Brother's day / Rajasthani -- The Brahman who swallowed a God / Bengali -- One man's virtue / Oriya -- A crow's revenge / Kannada -- A story in search of an audience / Telugu -- The clay mother-in-law / Kannada -- The barber and the Brahman demon / Benjali -- Why the fish laughed / Kashmiri -- A parrot called Hiraman / Bengali -- The monkey and the crocodile / Kannada; Tamil -- What happens when you really listen / Telugu -- Tenali Rama / Kannada; Tamil; Telugu -- How Tenali Rama became a Jester -- Tenali Rama's Ramayana -- Two sisters / Santali -- Sukhu and Dukhu / Bengali -- One, two, three / Santali -- The wife who refused to be beaten / Kashmiri -- The Ogress Queen / Kashmiri -- Killed by a tiger / Santali -- Outwitting fate / Tamil -- Four girls and a king / Punjabi. If it isn't you, it must be your father / Kannada -- Why audiences laugh or cry / Punjabi -- Akbar and Birbal ; The best of flowers ; Make it shorter ; Bring be four ; Sons-in-law / Urdu -- The night-blind son-in-law / Kannada -- Shall I show you my real face? / Tamil -- A malcontent cured / Kashmiri -- The kite's daughter / Assamese -- A flowering tree / Kannada -- A musical demon / Tamil -- Other lives / Kashmiri -- Living like a pig / Telugu -- A heron in the mouth / Bengali -- Tenali Rama's art / Kannada; Tamil; Telugu -- One more use for artists / Gujerati -- Heron boy / Tulu -- The tiger's adopted son / Didayi -- How to live on half a pice / Konkani -- The magic bowls / Tamil -- The four jogis / Santali -- A friend in need / Malayalam -- Winning a princess / Tulu -- Crossing a river, losing a self / Kannada; Tamil; Telugu -- Prince sabar / Gujerati. The lord of death / Punjabi -- The shepherd's ghost / Telugu -- This world and the other / Bengali -- If God is everywhere / Bengali -- A tiger that didn't know who he was / Bengali -- Gandharva Sen is dead! / Bengali -- Tenali Rama's dream / Telugu -- A feast in a dream / Rajasthani -- In search of a dream / Santali -- The princess whose father wanted to marry her / Tulu -- Mother marries son / Marathi -- A cure / Bengali -- A tall tale in Urdu / Urdu -- The greatest / Angami Naga -- A story for Sundays / Marathi -- Tenali Rama and the Brahmans / Kannada; Tamil; Telugu -- A hair's-breadth escape / Tamil -- Between two wives / Tamil -- The dead prince and the talking doll / Kannada -- The serpent mother / Gujerati -- Teja and Teji / Assamese -- The dove's egg: a chain tale / Malayalam -- A drum / Hindi -- In the kingdom of fools / Kannada -- Nonviolence / Bengali -- The barber's secret / Tamil. Gopal Bhar cures a dreamer / Benjali -- A scavenger's dream / Oriya -- The boy who sold wisdom / Gujerati -- Two jars of persian / Punjabi -- In another country / Punjabi -- One man's pleasure / Urdu -- Raja Vikram and the princess of China / Hindi -- Walking on water / Bengali -- The guru and the idiot / Telugu -- Grateful animals, ungrateful man / Hindi/Kumaoni -- When a black dog dies / Urdu -- The village rogue, the city rogue, and the king of rogues / Oriya -- A qazi with a long beard / Marathi -- The priest who could see as far as Mecca / Assamese -- Adventures of a disobedient son / Kannada -- Hanchi / Kannada -- Buffalo into rooster / Marathi -- The prince who married his own left half / Kannada -- A buffalo made of lac / Tamil -- A contest of lies / Hindi -- It's done with mirrors / Telugu -- The kurumba in the parrot's body / Kota -- The eighth key / Sindhi -- How the weaver went to heaven / Urdu. The tiger-makers / Kannada -- When a tale is finished / Oriya -- And then, Bhurrah! / Marathi. Collection of the oral tales compiled from a vast array of sources and translated from twenty-two languages of the country.
398.2 J
Japanese tales. 1st ed. New York : Pantheon Books, c1987.
398.2 L
Latin American folktales : stories from Hispanic and Indian traditions. 1st ed. New York : Pantheon Books, c2002. A collection of one hundred Latin American folk tales taken from the Hispanic and Indian traditions.
398.2 L
Legends and tales of the American West. 1st pbk. ed. New York : Pantheon Books, c1998.
398.2 R
Afanasʹev, A. N. (Aleksandr Nikolaevich), 1826-1871. Russian fairy tales. Pantheon Paperback: First Pantheon hardback ed. 1945; Second hardback Pantheon ed. 1975. New York : Pantheon Books, [1975?] c1945. A collection of the classic Russian folk and fairy tales.
812.54 R
Readings on A raisin in the sun. San Diego, CA : Greenhaven Press, c2001.
813.01 B
The best American short stories 2017. Presents a selection of the best works of short fiction of the past year from a variety of acclaimed sources.
813.01 B
Best American short stories 2018. Boston : Houghton Mifflin Harcourt pUBLISHERS, c. 2018.
813.01 O
100 years of The best American short stories. Collects forty short stories published between 1915 and 2015, from writers that include Ernest Hemingway, John Updike, and Alice Munro that exemplify their era and stand the test of time --.
821.008 G
Great short poems. Mineola, N.Y. : Dover Publications, 2000.
92 McD
McDonald, William C. The shadow tiger : Billy McDonald, Wingman to Chennault. Hardback Special Edition.
CD Mid
A Midsummer Night's Dream. Audiobook recording using the New Cambridge Shakespeare text, 1984; Unabridged. www.naxoaudiobooks.com : Naxos audioBooks with permission from Cambridge University Press, 1984.
DVD Bla
Blackboard jungle. Glenn Ford, Anne Francis, Louis Calhern, Margaret Hayes, Vic Morrow, Sidney Poitier. Urban drama about an idealistic teacher in a slum area who fights doggedly to connect with his unruly students. Based on Evan Hunter's novel.
DVD Cat
Cat on a hot tin roof. 2016. Blu-ray. Burbank, Calif. : Warner Home Video ;, [1999]. Side A. Standard presentation -- side B. Widescreen presentation. Elizabeth Taylor, Paul Newman, Burl Ives, Jack Carson, Judith Anderson, Madeleine Sherwood, Larry Gates, Vaughn Taylor. Brick, an alcoholic ex-football player, drinks his days away and resists the affections of his wife, Maggie. His reunion with his father, Big Daddy, who is dying of cancer, jogs a host of memories and revelations for both father and son.
DVD Def
The defiant ones. Letterboxed. Santa Monica, CA : MGM Home Entertainment, [2004]. Tony Curtis, Sidney Poitier, Theodore Bikel, Charles McGraw, Lon Chaney, King Donovan, Claude Akins, Lawrence Dobkin, Whit Bissell, Carl Switzer, Kevin Coughlin, Cara Williams. Two convicts escaping from a Southern work gang discover that they are bound together by an unbreakable iron chain and separated by a hatred for each other. But in order to elude capture they must overcome their hostility.
DVD Inv
Invasion of the body snatchers. Olive Signature; Blu-Ray 2018. Kevin McCarthy, Dana Wynter, Carolyn Jones. Filmy spores fall from space over San Francisco, and the city blossoms with beautiful new flora. People take the flowers home and as they sleep, the plants creep over them, devouring their bodies and stealing their identities--everything except their emotions, their uniqueness, their souls.
DVD Kis
Kiss me deadly. Blu-Ray Special Edition. [United States] : Criterion Collection, 2011. Ralph Meeker, Albert Dekker, Paul Stewart, Juano Hernandez, Wesley Addy; introducing Maxine Cooper, Cloris Leachman, Gaby Rodgers. "In an atomic adaptation of Mickey Spillane's novel, directed by Robert Aldrich, the good manners of the 1950s are blown to smithereens. Snarling private detective Mike Hammer's decision one dark, lonely night to pick up a hitchhiking woman sends him down some terrifying byways. Brazen and bleak, it's a film noir masterpiece and an essential piece of cold war paranoia. Featuring as nervy an ending as has ever been seen in American cinema."--Container.
DVD On
On the waterfront. Special ed. Culver City, CA : Columbia Pictures Corp. :, c2001. Start -- Returning Danny boy -- "Someone fell off the roof." -- Johnny Friendly -- Waterfront commission mugs -- How trigger locals work -- Designated stoolie -- Meeting adjourned -- Getting acquainted -- Lowdown on Terry -- Up on the roof -- Neighborhood saloon -- Wedding party -- Friendly warning -- Dropping a sling on Dugan -- Promise kept -- Terry & Father Barry -- Telling Edie the truth -- Talk of past favors -- "I coulda been a contender." -- At Edie's -- "Charlie's in trouble." -- Waiting for Big John -- Crime Commission hearing -- Pigeon for a pigeon -- "You're a cheap mug!" -- Labor vs. Union -- Finishing what he started. Marlon Brando, Karl Malden, Lee J. Cobb, Rod Steiger, Pat Henning, Leif Erickson, James Westerfield, Tony Galento, Tami Mauriello, John Hamilton, John Heldabrand, Rudy Bond, Don Blackman, Arthur Keegan, Abe Simon, Eva Marie Saint. Terry Malloy is a washed-up ex-prize fighter corrupted along with brother Charley at an early age by a ruthless Mob-connected union boss named Johnny Friendly, who runs the waterfront. Malloy is now an errand-boy for the union, while Charley (in return for a college education) is now a lawyer for them. Malloy assists in the killing of a longshoreman who was talking to the crime commission investigating the union. He soon meets the dead man's agonized sister, Edie Doyle, and has a change of mind. Activist priest Father Barry argues with Malloy about morality, responsibility, and doing the right thing. Malloy's guilt, his romantic feelings for Edie, and an assault on Father Barry overwhelm him and he turns informer. Malloy's defiant testimony before the commission leads to a climactic bloody battle that wrests the union from the boss' tenacious grasp.
DVD Pia
The piano lesson. Full screen Gold Crown collector's ed. Special features: Full screen presentation -- The making of "The piano lesson" -- An interview with August Wilson -- Language: English -- Subtitles: English. Charles S. Dutton, Alfre Woodard, Carl Gordon, Tommy Hollis, Lou Myers, Courtney B. Vance ... [and others]. August Wilson's Pulitzer Prize-winning tale of a family caught between their heritage and a dream for the future. The Charles family clashes over the fate of a magnificent, carved piano that carries their family's story from their days as slaves. Boy Willie wants to sell the piano to buy a farm--the same fields their family worked as slaves. But his sister, Berniece, refuses to part with it. For her, the piano is their very soul, a legacy of pride and struggle that symbolizes their survival as a family. To resolve the conflict they must first deal with the past.
DVD Por
Pork Chop Hill. Olive Films; Blu-Ray; 2015. California; U.S. : Twentieth Century Fox Home Entertainment/MGM Studios, [1999]. Gregory Peck, Harry Guardino, Rip Torn, George Peppard, James Edwards, Bob Steele, Woody Strode, George Shibata. Korean War film of a true tale of the desperate soldiers who finally take the top of Pork Chop Hill, only to find themselves surrounded by enemy forces.
DVD Reb
Rebel without a cause. Two-disc special ed., widescreen version. Burbank, CA : Warner Home Video, 2013. James Dean, Natalie Wood, Sal Mineo, Jim Backus, Ann Doran, Corey Allen, William Hopper, Rochelle Hudson, Dennis Hopper, Edward Platt, Steffi Sidney, Marietta Canty, Virginia Brissac, Beverly Long, Ian Wolfe, Frank Mazzola, Robert Foulk, Jack Simmons, Tom Bernard, Nick Adams, Jack Grinnage, Clifford Morris. Jim Stark, the teenage son of a well-to-do family, is overcome by loneliness, frustration and anger, which leads to violence when he seeks approval of a gang of high-school hoodlums.
DVD Viv
Viva Cuba. Fullscreen ed. [United States] : Film Movement, 2007. Mal©ð y Jorgito son dos ni©łos que se han prometido amistad para toda la vida, a pesar de que sus familias se detestan. Cuando la abuela de Mal©ð se muere y su mam©Ł decide irse a vivir fuera de Cuba, Mal©ð y Jorgito tendr©Łn que escaparse hasta el fin del mundo en busca de una esperanza para su amor. "Mal©ð is from an upper-class family and her single mother does not want her to play with Jorgito, as she thinks his background is coarse and commonplace. Jorgito's mother, a poor socialst proud of her family's social standing, places similar restrictions on her son. What neither woman recognizes is the immense strength of the bond between Mal©ð and Jorgito. When the children learn that Mal©ð's mother is planning to leave Cuba, they decide to run away and travel to the other side of the island to find Mal©ð's father and persuade him against signing the forms that would allow it"--Container.
F Cro
Near to the heart.
F Gre
Green, John, 1977- author. John Green : mini collection. v.1 - Fault in our stars -- v.2 - Looking for Alaska -- v.3 - Abundance of Katherines -- v.4 - Paper towns. Four beloved classics by John Green complete and unabridged. Penguin Minis' revolutionary landscape design and ultra-thin paper make them perfectly pocket-sized and easy to hold in one hand without sacrificing readility. -- slipcase. Fault in Our Stars. Despite the tumor-shrinking medical miracle that has bought her a few years, Hazel has never been anything but terminal, her final chapter inscribed upon diagnosis. But when a gorgeous plot twist named Augustus Waters suddenly appears at Cancer Kid Support Group, Hazels story is about to be completely rewritten. -- Amazon.com. Looking for Alaska. Before. Miles Halter is fascinated by famous last wordsand tired of his safe life at home. He leaves for Culver Creek boarding school to seek what the dying poet Frࣅois Rabelais called {28}The Great Perhaps. Abundance of Katherines. When it comes to relationships, Colin Singletons type is girls named Katherine. And when it comes to girls named Katherine, Colin is always getting dumped. Nineteen times, to be exact. On a road trip miles from home, this anagram-happy, washed-up child prodigy has ten thousand dollars in his pocket, a bloodthirsty feral hog on his trail, and an overweight, Judge Judyloving best friend riding shotgunbut no Katherines. Colin is on a mission to prove The Theorem of Underlying Katherine Predictability, which he hopes will predict the future of any relationship, avenge Dumpees everywhere, and finally win him the girl. Love, friendship, and a dead Austro-Hungarian archduke add up to surprising and heart-changing conclusions in this ingeniously layered comic novel about reinventing oneself. -- Amazon.com. Paper Towns. When Margo Roth Spiegelman beckons Quentin Jacobsen in the middle of the nightdressed like a ninja and plotting an ingenious campaign of revengehe follows her. Margos always planned extravagantly, and, until now, shes always planned solo. After a lifetime of loving Margo from afar, things are finally looking up for Q . . . until day breaks and she has vanished. Always an enigma, Margo has now become a mystery. But there are clues. And theyre for Q. -- Amazon.com.
F Wes
Michelle West. The Uncrowned King. New York, NY : DAW BOOKS, INC, 1998.
F Wes
West, Michelle, 1963-. The broken crown. New York : DAW Books, 1997. Treachery threatens the Dominion of Annagar as two power-hungry men--a skilled general and a sorcerer--seek to overthrow the clan of Leonne, whose control over the magic of the sun sword has kept the peace.
F Wes
West, Michelle, 1963-. The riven shield. New York : DAW Books, 2003.
F Wes
West, Michelle, 1963-. Sea of sorrows. New York, NY : DAW Books, c2001.
F Wes
West, Michelle, 1963-. The shining court. New York : DAW Books, 1999. The approaching Festival of the Moon could signal the ultimate triumph of the Shining Court, or humankind's final chance to defeat the powerful demon lord--Allasakar, Lord of the Hells.
F Wes
West, Michelle, 1963-. The sun sword. New York, N.Y. : DAW Books, 2004.
SC Ben
Bender, Karen E. The new order : stories. First hardcover edition.
SC D
Davis, Lydia, 1947-. The collected stories of Lydia Davis. 1st ed. New York : Farrar, Straus and Giroux, c2009.
SC Von
Vonnegut, Kurt. Welcome to the monkey house : a collection of short works. The special edition. A collection of twenty-five short works by the American author written between 1950 and 1968 and originally printed in a wide range of publications including "The Atlantic Monthly," "Esquire," and "Ladies' Home Journal.".
0 notes
Text
Essay in To Comfort in India- Essay or dissertation, Presentation, Paragraph
In information technology principle, files retention, reference code or even bit-rate decrease entails encoding facts using a lower number of parts compared to the unique portrayal. In one account, level of privacy is valuable for the reason that closeness might be extremely hard without this (Deep-fried, 1970; Gerety 1977; Gerstein, The late seventies; Cohen, 2000). For that reason, as soon as personal privacy guidelines tend to be violated, virtually all residents use a straight to take legal action against written by paperhelpers.org the molesters. Recently Supreme court involving India afforded the view concerning the right to level of privacy and this is a hot topic on information programs at the moment. Here will be possible subject areas to select even though writing about level of privacy: Congress should create virtually no regulation respecting an establishment of faith, or even barring the free work out thereof; as well as abridging the liberty with talk, and also with the mass media; or perhaps the appropriate of the people peaceably to collect, and application the us government for a redress involving issues.
4.A couple of Level of privacy as well as Disputes to Values
Virtually no data is missing around lossless compression setting. You’ll find digital tracking gadgets which have been applied although sophisticated models are actually introduced around cellphones and autos devices. Instead of viewing plus keeping track of, they can be more probable reliant on detective cams. The wrong type of as well as non-existent disclosure regulate would be the cause pertaining to personal privacy challenges. There is really a further more difficulty which includes generated fight, perhaps amongst those advocates that consider privacy is really a consistent principle. Internet comfort is definitely an vital matter currently.
3.Three Level of privacy as well as Intimacy
As soon as an intruder believes that which he/she spent some time working out there any very sensitive information and facts after that, irrespective of whether or otherwise not the particular burglar has got such a right facts, Lambert takes this while recognized disclosure”. The second thing is, each time a group of cams sends a relevant video with a number of screens witnessed by a individual and also team, those people being stuck from the camcorders may feel their level of privacy is trespassed. This kind of pretty automobile accident gifted your much-needed recognition and already people today discussing with regards to the personal privacy and similar considerations. Name Era A A person B A pair of C 3 Many of us don’t ought to often be watched whilst dwelling us. Using the growth of an array of modern gadgets which provide plenty of the possiblility to collect, get hold of, help save, retail store, and also admittance with regards to another person or anything, personal privacy gets a subject matter that will concerns lots of people.
Writing help
In computer science and information principle, details data compression, supplier computer programming or bit-rate decrease involves coding data employing a lot fewer portions compared to original counsel. In that case with the viewpoint of the burglar to know precisely the valuations involving not liable features, almost all perturbed records might be similarly probably and the entropy will probably be utmost. Though protecting the view that will personal privacy is definitely in accordance with varieties plus tradition, Moore argues that will personal privacy will be objectively precious – humans that won’t obtain a particular a higher level power over access will suffer in several means. Their worries about police officers and also the implementation of several methods taken up are categorized as your Patriot Respond are also held up by Nadine Strossen’s debate of such enforcement normally each illegitimate plus inadequate (Moore, ch. The ability to journey among states with out a passport, by way of example, seems to be some sort of mobility considerably totally different from liberty to produce judgements pertaining to personalized along with seductive worries in relation to one’s shape – how to write an informative essay like contraceptive employ, abortion alternative, sanitation (Buck versus. Apart from, you should check out the activities which can be regarded any level of privacy infringement, based on the area with ticket.
The actual public/private change is also often taken to reference the suitable whole world of governments recognition rather than the kingdom available self-regulation, down the traces explained by Ruben Stuart Work as part of his essay or dissertation, On Liberty. Criticism of your constitutional directly to level of privacy has continued, particularly in the popular press, Roe versus. Most people realize that there have been an exploration statement publicized while in the materials the location where the goal has been to obscure discreet patterns [37, 90], that is in the evening breadth of our review. These kinds involving solitude protecting approaches will depend on the point that the data units used in files mining requirements do not necessarily ought to include 100% correct information. So next Great time-saver, there is a huge discussion in north america on straight to comfort. Following this Revelation, there was a huge controversy in the united states with to certainly solitude.
Invasion regarding Personal privacy Dissertation Producing Help
The capability for some to view plus url this data source, with handful of manages how they normally use, talk about, or maybe make the most of the content, creates person therapy for more knowledge about one self more challenging than ever. It is just not challenging to view the analogies involving Kundera’s circumstance as well as electronic monitoring and streets cameras popular inside society today. And then on the mindset of your burglar to know precisely the valuations involving simple capabilities, almost all perturbed documents is going to be just as possible plus the entropy will probably be highest. Privacy is really a matter that will results in being increasingly popular with every morning not only among the media journalists nonetheless college students as well. Moore brilliant co-author for the “Introduction”, Eileen Katell, use a control-based definition of solitude, which “A to certainly level of privacy is often a directly to command usage of, along with purposes of, locations, body, along with information” (Moore, 3), urging that will “the power to control admission to our bodies, drives, along with capabilities, and vulnerable sensitive information, is a valuable part regarding man growing as well as well-being” (Moore, A few).
Privacy in the Internet
Eventually, there is a feminist complaint involving privateness, that approving special status so that you can privateness can be detrimental to be able to along with other folks because it is utilized as some sort of safeguard so that you can take control of and handle them, quiet these individuals, and cover upwards maltreatment (MacKinnon, 1990). Internet solitude essay or dissertation is definitely a incredibly hot subject currently and you could find innumerable study components for your comfort essay or dissertation. If the following dissertation seriously isn’t rather what you’re looking for, you will want to get your very own custom Information technology dissertation, dissertation and also item of training programmes of which replies your own actual issue? You can find United kingdom freelance writers much like me around, holding out to assist you to. Talking over everyone of Prosser’s several forms of personal privacy rights in turn, Bloustein guards the vista that each these solitude proper rights is significant because doing so guards versus makes use of demeaning to be able to style as well www.linnbenton.edu as from affronts for you to human being self-esteem.
Some others advise that level of privacy is advisable understood as a bunch idea protecting passions inside we) treating details about oneself, ii) control over usage of ourselves, equally both mental and physical, and three) power over one’s capacity to make significant conclusions concerning relatives and lifestyle to be do it yourself voice also to produce different interactions (DeCew, ’97). The subsequent is actually a qualifying measure that can be used to observe the creation of area technologies within security. The difficulty with students’ privacy liberties has become a warm topic in the last few days with the new unlawful searches connected with student personal computers attached to the university’s computer network with Carnegie Mellon School. Let’s say the scholars made web sites this contained new music on there? These websites could well be added for the school’s community however would that offer the varsity the right to censor and also check what’s becoming set up within the school’s multi-level? This query describes considerations of your student’s legal rights.
The post Essay in To Comfort in India- Essay or dissertation, Presentation, Paragraph appeared first on Công Ty Sản Xuất Bao Bì Gạo Ánh Sáng.
from Công Ty Sản Xuất Bao Bì Gạo Ánh Sáng https://ift.tt/2ThBuvo via IFTTT
0 notes
Text
Original Post from FireEye Author: Michael Bailey
It is very unusual for FLARE to analyze a prolifically-used, privately-developed backdoor only to later have the source code and operator tools fall into our laps. Yet this is the extraordinary circumstance that sets the stage for CARBANAK Week, a four-part blog series that commences with this post.
CARBANAK is one of the most full-featured backdoors around. It was used to perpetrate millions of dollars in financial crimes, largely by the group we track as FIN7. In 2017, Tom Bennett and Barry Vengerik published Behind the CARBANAK Backdoor, which was the product of a deep and broad analysis of CARBANAK samples and FIN7 activity across several years. On the heels of that publication, our colleague Nick Carr uncovered a pair of RAR archives containing CARBANAK source code, builders, and other tools (both available in VirusTotal: kb3r1p and apwmie).
FLARE malware analysis requests are typically limited to a few dozen files at most. But the CARBANAK source code was 20MB comprising 755 files, with 39 binaries and 100,000 lines of code. Our goal was to find threat intelligence we missed in our previous analyses. How does an analyst respond to a request with such breadth and open-ended scope? And what did we find?
My friend Tom Bennett and I spoke about this briefly in our 2018 FireEye Cyber Defense Summit talk, Hello, Carbanak! In this blog series, we will expound at length and share a written retrospective on the inferences drawn in our previous public analysis based on binary code reverse engineering. In this first part, I’ll discuss Russian language concerns, translated graphical user interfaces of CARBANAK tools, and anti-analysis tactics as seen from a source code perspective. We will also explain an interesting twist where analyzing the source code surprisingly proved to be just as difficult as analyzing the binary, if not more. There’s a lot here; buckle up!
File Encoding and Language Considerations
The objective of this analysis was to discover threat intelligence gaps and better protect our customers. To begin, I wanted to assemble a cross-reference of source code files and concepts of specific interest.
Reading the source code entailed two steps: displaying the files in the correct encoding, and learning enough Russian to be dangerous. Figure 1 shows CARBANAK source code in a text editor that is unaware of the correct encoding.
Figure 1: File without proper decoding
Two good file encoding guesses are UTF-8 and code page 1251 (Cyrillic). The files were mostly code page 1251 as shown in Figure 2.
Figure 2: Code Page 1251 (Cyrillic) source code
Figure 2 is a C++ header file defining error values involved in backdoor command execution. Most identifiers were in English, but some were not particularly descriptive. Ergo, the second and more difficult step was learning some Russian to benefit from the context offered by the source code comments.
FLARE has fluent Russian speakers, but I took it upon myself to minimize my use of other analysts’ time. To this end, I wrote a script to tear through files and create a prioritized vocabulary list. The script, which is available in the FireEye vocab_scraper GitHub repository, walks source directories finding all character sequences outside the printable lower ASCII range: decimal values 32 (the space character) through 126 (the tilde character “~”) inclusive. The script adds each word to a Python defaultdict_ and increments its count. Finally, the script orders this dictionary by frequency of occurrence and dumps it to a file.
The result was a 3,400+ word vocabulary list, partially shown in Figure 3.
Figure 3: Top 19 Cyrillic character sequences from the CARBANAK source code
I spent several hours on Russian language learning websites to study the pronunciation of Cyrillic characters and Russian words. Then, I looked up the top 600+ words and created a small dictionary. I added Russian language input to an analysis VM and used Microsoft’s on-screen keyboard (osk.exe) to navigate the Cyrillic keyboard layout and look up definitions.
One helpful effect of learning to pronounce Cyrillic characters was my newfound recognition of English loan words (words that are borrowed from English and transliterated to Cyrillic). My small vocabulary allowed me to read many comments without looking anything up. Table 1 shows a short sampling of some of the English loan words I encountered.
Cyrillic
English Phonetic
English
Occurrences
Rank
Файл
f ah y L
file
224
5
сервер
s e r v e r
server
145
13
адрес
a d r e s
address
52
134
команд
k o m a n d
command
110+
27
бота
b o t a
bot
130
32
плагин
p l ah g ee n
plugin
116
39
сервис
s e r v ee s
service
70
46
процесс
p r o ts e s s
process
130ish
63
Table 1: Sampling of English loan words in the CARBANAK source code
Aside from source code comments, understanding how to read and type in Cyrillic came in handy for translating the CARBANAK graphical user interfaces I found in the source code dump. Figure 4 shows a Command and Control (C2) user interface for CARBANAK that I translated.
Figure 4: Translated C2 graphical user interface
These user interfaces included video management and playback applications as shown in Figure 5 and Figure 6 respectively. Tom will share some interesting work he did with these in a subsequent part of this blog series.
Figure 5: Translated video management application user interface
Figure 6: Translated video playback application user interface
Figure 7 shows the backdoor builder that was contained within the RAR archive of operator tools.
Figure 7: Translated backdoor builder application user interface
The operator RAR archive also contained an operator’s manual explaining the semantics of all the backdoor commands. Figure 8 shows the first few commands in this manual, both in Russian and English (translated).
Figure 8: Operator manual (left: original Russian; right: translated to English)
Down the Rabbit Hole: When Having Source Code Does Not Help
In simpler backdoors, a single function evaluates the command ID received from the C2 server and dispatches control to the correct function to carry out the command. For example, a backdoor might ask its C2 server for a command and receive a response bearing the command ID 0x67. The dispatch function in the backdoor will check the command ID against several different values, including 0x67, which as an example might call a function to shovel a reverse shell to the C2 server. Figure 9 shows a control flow graph of such a function as viewed in IDA Pro. Each block of code checks against a command ID and either passes control to the appropriate command handling code, or moves on to check for the next command ID.
Figure 9: A control flow graph of a simple command handling function
In this regard, CARBANAK is an entirely different beast. It utilizes a Windows mechanism called named pipes as a means of communication and coordination across all the threads, processes, and plugins under the backdoor’s control. When the CARBANAK tasking component receives a command, it forwards the command over a named pipe where it travels through several different functions that process the message, possibly writing it to one or more additional named pipes, until it arrives at its destination where the specified command is finally handled. Command handlers may even specify their own named pipe to request more data from the C2 server. When the C2 server returns the data, CARBANAK writes the result to this auxiliary named pipe and a callback function is triggered to handle the response data asynchronously. CARBANAK’s named pipe-based tasking component is flexible enough to control both inherent command handlers and plugins. It also allows for the possibility of a local client to dispatch commands to CARBANAK without the use of a network. In fact, not only did we write such a client to aid in analysis and testing, but such a client, named botcmd.exe, was also present in the source dump.
Tom’s Perspective
Analyzing this command-handling mechanism within CARBANAK from a binary perspective was certainly challenging. It required maintaining tabs for many different views into the disassembly, and a sort of textual map of command ids and named pipe names to describe the journey of an inbound command through the various pipes and functions before arriving at its destination. Figure 10 shows the control flow graphs for seven of the named pipe message handling functions. While it was difficult to analyze this from a binary reverse engineering perspective, having compiled code combined with the features that a good disassembler such as IDA Pro provides made it less harrowing than Mike’s experience. The binary perspective saved me from having to search across several source files and deal with ambiguous function names. The disassembler features allowed me to easily follow cross-references for functions and global variables and to open multiple, related views into the code.
Figure 10: Control flow graphs for the named pipe message handling functions
Mike’s Perspective
Having source code sounds like cheat-mode for malware analysis. Indeed, source code contains much information that is lost through the compilation and linking process. Even so, CARBANAK’s tasking component (for handling commands sent by the C2 server) serves as a counter-example. Depending on the C2 protocol used and the command being processed, control flow may take divergent paths through different functions only to converge again later and accomplish the same command. Analysis required bouncing around between almost 20 functions in 5 files, often backtracking to recover information about function pointers and parameters that were passed in from as many as 18 layers back. Analysis also entailed resolving matters of C++ class inheritance, scope ambiguity, overloaded functions, and control flow termination upon named pipe usage. The overall effect was that this was difficult to analyze, even in source code.
I only embarked on this top-to-bottom journey once, to search for any surprises. The effort gave me an appreciation for the baroque machinery the authors constructed either for the sake of obfuscation or flexibility. I felt like this was done at least in part to obscure relationships and hinder timely analysis.
Anti-Analysis Mechanisms in Source Code
CARBANAK’s executable code is filled with logic that pushes hexadecimal numbers to the same function, followed by an indirect call against the returned value. This is easily recognizable as obfuscated function import resolution, wherein CARBANAK uses a simple string hash known as PJW (named after its author, P.J. Weinberger) to locate Windows API functions without disclosing their names. A Python implementation of the PJW hash is shown in Figure 11 for reference.
def pjw_hash(s): ctr = 0 for i in range(len(s)): ctr = 0xffffffff & ((ctr << 4) + ord(s[i])) if ctr & 0xf0000000: ctr = (((ctr & 0xf0000000) >> 24) ^ ctr) & 0x0fffffff
return ctr
Figure 11: PJW hash
This is used several hundred times in CARBANAK samples and impedes understanding of the malware’s functionality. Fortunately, reversers can use the flare-ida scripts to annotate the obfuscated imports, as shown in Figure 12.
Figure 12: Obfuscated import resolution annotated with FLARE’s shellcode hash search
The CARBANAK authors achieved this obfuscated import resolution throughout their backdoor with relative ease using C preprocessor macros and a pre-compilation source code scanning step to calculate function hashes. Figure 13 shows the definition of the relevant API macro and associated machinery.
Figure 13: API macro for import resolution
The API macro allows the author to type API(SHLWAPI, PathFindFileNameA)(…) and have it replaced with GetApiAddrFunc(SHLWAPI, hashPathFindFileNameA)(…). SHLWAPI is a symbolic macro defined to be the constant 3, and hashPathFindFileNameA is the string hash value 0xE3685D1 as observed in the disassembly. But how was the hash defined?
The CARBANAK source code has a utility (unimaginatively named tool) that scans source code for invocations of the API macro to build a header file defining string hashes for all the Windows API function names encountered in the entire codebase. Figure 14 shows the source code for this utility along with its output file, api_funcs_hash.h.
Figure 14: Source code and output from string hash utility
When I reverse engineer obfuscated malware, I can’t help but try to theorize about how authors implement their obfuscations. The CARBANAK source code gives another data point into how malware authors wield the powerful C preprocessor along with custom code scanning and code generation tools to obfuscate without imposing an undue burden on developers. This might provide future perspective in terms of what to expect from malware authors in the future and may help identify units of potential code reuse in future projects as well as rate their significance. It would be trivial to apply this to new projects, but with the source code being on VirusTotal, this level of code sharing may not represent shared authorship. Also, the source code is accessibly instructive in why malware would push an integer as well as a hash to resolve functions: because the integer is an index into an array of module handles that are opened in advance and associated with these pre-defined integers.
Conclusion
The CARBANAK source code is illustrative of how these malware authors addressed some of the practical concerns of obfuscation. Both the tasking code and the Windows API resolution system represent significant investments in throwing malware analysts off the scent of this backdoor. Check out Part Two of this series for a round-up of antivirus evasions, exploits, secrets, key material, authorship artifacts, and network-based indicators.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Michael Bailey CARBANAK Week Part One: A Rare Occurrence Original Post from FireEye Author: Michael Bailey It is very unusual for FLARE to analyze a prolifically-used,
0 notes
Text
The Best Data Science Jobs for a Fulfilling Career
If you are a budding data scientist, or you are looking to advance your career in the domain of data science, then you might wonder about its career prospects. What is the growth trajectory? What are the most fulfilling roles and how do you go about charting your career roadmap?
The good news is that the demand for data scientist roles continues to grow, thanks to the emergence of big data, analytics and machine learning (ML). The data scientist role is certainly not new. But it is constantly evolving to suit industry demands and trends.
The modern data scientist is a new breed. An analytical expert, a problem solver and a naturally curious person. Think of it is a combination of mathematics, computer science and trend spotting. Since data scientists have the best of both – IT and business, they are highly sought-after and generously paid.
As the tech trends evolve, so do the opportunities and career paths. How do you make the most of this boom?
To leverage this opportunity, let’s look at the best data science jobs that are trending on job boards and LinkedIn:
The Data Analyst Much like a detective, a data analyst interprets data and breaks it down into information that is easily digestable and useful for stakeholders. This information has great value, asit can help stakeholders to make well informed, data-driven business decisions. Your daily responsibilities might include tasks such as :
extracting data from an SQL database
using Tableau or Excel at a specialist level
building basic visualization or reporting dashboards
And more! The technical skill-set required is diverse and covers the full spectrum of data science. You need expertise in languages such as R, Python, SQL and C.
Asthe name suggests, it is a highly analytical role. So, if logic, numbers and a figure-it-out attitude is your jam, then go for it!
The Data Engineer When enterprises reach a point where they have vast amounts of big data, they need a data engineer to make sense of it all. The data engineer sets up the infrastructure that the company will need to organize this data.
Typically, the job involves building massive pools for big data. That is, developing, constructing, testing and maintaining architectures like databases and large-scale data processing systems.
As a data engineer, you need to make sure that the architecture supports the core business needs, those of the data scientists and the stakeholders. For this role, strong software engineering skills are more important than ML and core statistics.
The Machine Learning Engineer The ML engineer has mastered the science of using data to build predictive models. These models are used for automating of processes. These processes can be anything from image classification, speech recognition, market forecasting to software testing.
There is high demand for the machine learning engineer as companies rush in to make the most of the emergent wave.
As an ML engineer, you will need to have the following core skills:
Computer programming
Probability and statistics
Data modelling and evaluation
Applying ML algorithms and libraries
System Design and Software Engineering
ML frameworks
The Generalist The Data Science Generalist is quite a popular role. Many companies hire for this opportunity to work with a team of data scientists. It is likely that the hiring company needs data science but is not a data company, or may not build data-driven products.
This role demands a combination of data analysis, production code, visualization and more. Some key skills include a working knowledge of big data tools and experience working with data sets. Currently, data science generalists dominate the job market space as there are a variety of niches that require the ‘generalist’ as opposed to the ‘specialist’ profile.
The great thing about being a data science generalist is the breadth of experience. You will get involved in various phases of data science project lifecycle at some point. This gives you great flexibility in terms of a career move, and you can always make a lateral move somewhere down the line when an opportunity comes up.
Many experts believe that it is important to develop generalist skills in combination with specialist skills as you can add more value to your role with this blend.
Last but not least, when searching for your ideal data science job, do read the descriptions thoroughly. Often there is an overlap of skills between roles and ‘data scientist’ is often used as a blanket terminology. If you are preparing for a specific role, going through the job boards will enable you to understand the skills you need to work on.
The post The Best Data Science Jobs for a Fulfilling Career appeared first on Elevano.
source https://www.elevano.com/the-best-data-science-jobs-for-a-fulfilling-career/ source https://elevanocom.tumblr.com/post/182999189331
0 notes
Text
The Best Data Science Jobs for a Fulfilling Career
If you are a budding data scientist, or you are looking to advance your career in the domain of data science, then you might wonder about its career prospects. What is the growth trajectory? What are the most fulfilling roles and how do you go about charting your career roadmap?
The good news is that the demand for data scientist roles continues to grow, thanks to the emergence of big data, analytics and machine learning (ML). The data scientist role is certainly not new. But it is constantly evolving to suit industry demands and trends.
The modern data scientist is a new breed. An analytical expert, a problem solver and a naturally curious person. Think of it is a combination of mathematics, computer science and trend spotting. Since data scientists have the best of both – IT and business, they are highly sought-after and generously paid.
As the tech trends evolve, so do the opportunities and career paths. How do you make the most of this boom?
To leverage this opportunity, let’s look at the best data science jobs that are trending on job boards and LinkedIn:
The Data Analyst Much like a detective, a data analyst interprets data and breaks it down into information that is easily digestable and useful for stakeholders. This information has great value, asit can help stakeholders to make well informed, data-driven business decisions. Your daily responsibilities might include tasks such as :
extracting data from an SQL database
using Tableau or Excel at a specialist level
building basic visualization or reporting dashboards
And more! The technical skill-set required is diverse and covers the full spectrum of data science. You need expertise in languages such as R, Python, SQL and C.
Asthe name suggests, it is a highly analytical role. So, if logic, numbers and a figure-it-out attitude is your jam, then go for it!
The Data Engineer When enterprises reach a point where they have vast amounts of big data, they need a data engineer to make sense of it all. The data engineer sets up the infrastructure that the company will need to organize this data.
Typically, the job involves building massive pools for big data. That is, developing, constructing, testing and maintaining architectures like databases and large-scale data processing systems.
As a data engineer, you need to make sure that the architecture supports the core business needs, those of the data scientists and the stakeholders. For this role, strong software engineering skills are more important than ML and core statistics.
The Machine Learning Engineer The ML engineer has mastered the science of using data to build predictive models. These models are used for automating of processes. These processes can be anything from image classification, speech recognition, market forecasting to software testing.
There is high demand for the machine learning engineer as companies rush in to make the most of the emergent wave.
As an ML engineer, you will need to have the following core skills:
Computer programming
Probability and statistics
Data modelling and evaluation
Applying ML algorithms and libraries
System Design and Software Engineering
ML frameworks
The Generalist The Data Science Generalist is quite a popular role. Many companies hire for this opportunity to work with a team of data scientists. It is likely that the hiring company needs data science but is not a data company, or may not build data-driven products.
This role demands a combination of data analysis, production code, visualization and more. Some key skills include a working knowledge of big data tools and experience working with data sets. Currently, data science generalists dominate the job market space as there are a variety of niches that require the ‘generalist’ as opposed to the ‘specialist’ profile.
The great thing about being a data science generalist is the breadth of experience. You will get involved in various phases of data science project lifecycle at some point. This gives you great flexibility in terms of a career move, and you can always make a lateral move somewhere down the line when an opportunity comes up.
Many experts believe that it is important to develop generalist skills in combination with specialist skills as you can add more value to your role with this blend.
Last but not least, when searching for your ideal data science job, do read the descriptions thoroughly. Often there is an overlap of skills between roles and ‘data scientist’ is often used as a blanket terminology. If you are preparing for a specific role, going through the job boards will enable you to understand the skills you need to work on.
The post The Best Data Science Jobs for a Fulfilling Career appeared first on Elevano.
source https://www.elevano.com/the-best-data-science-jobs-for-a-fulfilling-career/ source https://elevanocom.blogspot.com/2019/02/the-best-data-science-jobs-for.html
0 notes
Text
The Best Data Science Jobs for a Fulfilling Career
If you are a budding data scientist, or you are looking to advance your career in the domain of data science, then you might wonder about its career prospects. What is the growth trajectory? What are the most fulfilling roles and how do you go about charting your career roadmap?
The good news is that the demand for data scientist roles continues to grow, thanks to the emergence of big data, analytics and machine learning (ML). The data scientist role is certainly not new. But it is constantly evolving to suit industry demands and trends.
The modern data scientist is a new breed. An analytical expert, a problem solver and a naturally curious person. Think of it is a combination of mathematics, computer science and trend spotting. Since data scientists have the best of both – IT and business, they are highly sought-after and generously paid.
As the tech trends evolve, so do the opportunities and career paths. How do you make the most of this boom?
To leverage this opportunity, let’s look at the best data science jobs that are trending on job boards and LinkedIn:
The Data Analyst Much like a detective, a data analyst interprets data and breaks it down into information that is easily digestable and useful for stakeholders. This information has great value, asit can help stakeholders to make well informed, data-driven business decisions. Your daily responsibilities might include tasks such as :
extracting data from an SQL database
using Tableau or Excel at a specialist level
building basic visualization or reporting dashboards
And more! The technical skill-set required is diverse and covers the full spectrum of data science. You need expertise in languages such as R, Python, SQL and C.
Asthe name suggests, it is a highly analytical role. So, if logic, numbers and a figure-it-out attitude is your jam, then go for it!
The Data Engineer When enterprises reach a point where they have vast amounts of big data, they need a data engineer to make sense of it all. The data engineer sets up the infrastructure that the company will need to organize this data.
Typically, the job involves building massive pools for big data. That is, developing, constructing, testing and maintaining architectures like databases and large-scale data processing systems.
As a data engineer, you need to make sure that the architecture supports the core business needs, those of the data scientists and the stakeholders. For this role, strong software engineering skills are more important than ML and core statistics.
The Machine Learning Engineer The ML engineer has mastered the science of using data to build predictive models. These models are used for automating of processes. These processes can be anything from image classification, speech recognition, market forecasting to software testing.
There is high demand for the machine learning engineer as companies rush in to make the most of the emergent wave.
As an ML engineer, you will need to have the following core skills:
Computer programming
Probability and statistics
Data modelling and evaluation
Applying ML algorithms and libraries
System Design and Software Engineering
ML frameworks
The Generalist The Data Science Generalist is quite a popular role. Many companies hire for this opportunity to work with a team of data scientists. It is likely that the hiring company needs data science but is not a data company, or may not build data-driven products.
This role demands a combination of data analysis, production code, visualization and more. Some key skills include a working knowledge of big data tools and experience working with data sets. Currently, data science generalists dominate the job market space as there are a variety of niches that require the ‘generalist’ as opposed to the ‘specialist’ profile.
The great thing about being a data science generalist is the breadth of experience. You will get involved in various phases of data science project lifecycle at some point. This gives you great flexibility in terms of a career move, and you can always make a lateral move somewhere down the line when an opportunity comes up.
Many experts believe that it is important to develop generalist skills in combination with specialist skills as you can add more value to your role with this blend.
Last but not least, when searching for your ideal data science job, do read the descriptions thoroughly. Often there is an overlap of skills between roles and ‘data scientist’ is often used as a blanket terminology. If you are preparing for a specific role, going through the job boards will enable you to understand the skills you need to work on.
The post The Best Data Science Jobs for a Fulfilling Career appeared first on Elevano.
Via https://www.elevano.com/the-best-data-science-jobs-for-a-fulfilling-career/
source http://elevanocom.weebly.com/blog/the-best-data-science-jobs-for-a-fulfilling-career
0 notes
Text
Programming Question Part 1ProblemDevelop a simple Python program to demonstrate understanding of using the
New Post has been published on https://www.essayyard.com/programming-question-part-1problemdevelop-a-simple-python-program-to-demonstrate-understanding-of-using-the/
Programming Question Part 1ProblemDevelop a simple Python program to demonstrate understanding of using the
Part 1ProblemDevelop a simple Python program to demonstrate understanding of using the Tkinter module to design a simple widget and configure it using the layout manager. Then add an event handler that will accept text input to the button and display the content of the text when using the mouse to click on the “click here” button.The program must have the following:Documentation Guidelines:Use good programming style (e.g., indentation for readability) and document each of your program parts with the following items (the items shown between the ” angle brackets are only placeholders. You should replace the placeholders and the comments between them with your specific information). Your cover sheet should have some of the same information, but what follows should be at the top of each program’s sheet of source code. Some lines of code should have an explanation of what is to be accomplished, this will allow someone supporting your code years later to comprehend your purpose. Be brief and to the point. Start your design by writing comment lines of pseudocode. Once that is complete, begin adding executable lines. Finally run and test your program.Deliverable(s):Your deliverable should be a Word document with screenshots showing the source code and running results, and discuss the issues that you had for this project related to AWS and/or Python IDE and how you solved them for all of the programs listed above as well as the inputs and outputs from running them. Submit a cover sheet with the hardcopy of your work.part 2For this assignment, you will develop working examples of a graphical user interface (GUI) and event handling and that demonstrate the following:Be sure to include a brief narrative of your code where you explain what the code is doing.Documentation Guidelines:Use good programming style (e.g., indentation for readability) and document each of your program parts with the following items (the items shown between the ” angle brackets are only placeholders. You should replace the placeholders and the comments between them with your specific information). Your cover sheet should have some of the same information, but what follows should be at the top of each program’s sheet of source code. Some lines of code should have an explanation of what is to be accomplished, this will allow someone supporting your code years later to comprehend your purpose. Be brief and to the point. Start your design by writing comment lines of pseudocode. Once that is complete, begin adding executable lines. Finally run and test your program.Deliverable(s):Your deliverable should be a Word document with screenshots showing the GUI and event handling you have created. Also, discuss the issues that you had for this project related to AWS and/or Python IDE and how you solved them for all of the programs listed above as well as the inputs and outputs from running them. Submit a cover sheet with the hardcopy of your work.Part 3Write a Python program using the Python IDE based on recursion with trees that is both depth first and breadth first searches.The Python program to be developed will demonstrate the use of both depth-first (DFS) and breadth-first (BFS) searches. A tree node structure will be developed that will be used both for DFS and BFS searches. The program will apply recursion both for the DFS and BFS searches to completion of the entire DFS and BFS. Also, the Python program will provide as output some of the intermediate nodes that are transverse during the execution of the DFS and BFS. This output of the intermediate nodes searched will demonstrate the different paths executed during a DFS versus BFS.ProblemDevelop functions to demonstrate understanding of implementing a recursive depth first search (DFS) and an iterative breadth first search (BFS) in Python using a simple graph made of nodes. This example will use nodes A, B, C, D, and E connected as follows: A —– / | B-D-C | | / | E —–The program must have the following:Documentation Guidelines:Use good programming style (e.g., indentation for readability) and document each of your program parts with the following items (the items shown between the ” angle brackets are only placeholders. You should replace the placeholders and the comments between them with your specific information). Your cover sheet should have some of the same information, but what follows should be at the top of each program’s sheet of source code. Some lines of code should have an explanation of what is to be accomplished, this will allow someone supporting your code years later to comprehend your purpose. Be brief and to the point. Start your design by writing comment lines of pseudocode. Once that is complete, begin adding executable lines. Finally run and test your program.Deliverable(s):Your deliverable should be a Word document with screenshots showing the source code and running results, and discuss the issues that you had for this project related to AWS and/or Python IDE and how you solved them for all of the programs listed above as well as the inputs and outputs from running them. Submit a cover sheet with the hardcopy of your work.Part 4Two user-defined classes are recommended: class Transaction, and class BankStatement. A main() function will be required that declares a BankStatement object and Transaction objects and then performs operations as shown in the example driver main function below. The BankStatement object (called myStatement in the example main() shown later) contains a container of Transaction objects along with other record-keeping data fields. This is yet another example of the Containment/Composition (a.k.a., “Has-A”) relationship that can exist between classes/objects.The Transaction class is used to create deposit and withdrawal objects. It contains a constructor for initialization. This constructor has three defaulted parameters to facilitate the user declaring transactions and passing appropriate initial data member values as parameters to this constructor or accepting one or more of its defaulted initializer values. It is certainly legal, and perhaps desirable, to also have a LoadTransaction() method that would take inputs from the keyboard on an interactive basis. This, in conjunction with a menu, is a desirable addition but not required for this exercise. The main() driver function shows a partial batch (i.e., hard-coded) implementation rather than the, perhaps, more desirable interactive implementation. See your instructor for any specific additional requirements.# Python model of a bank transaction which can be either# A deposit or a withdraw## Filename: transaction.pyclass Transaction: def __init__(self, inAmount = 0.0, inCode = ‘D’, inNote = “No note”): self.__Amount = inAmount if inAmount >= 0.0 else 0.0 self.__Code = inCode if inCode == ‘D’ or inCode == ‘W’ else ‘D’ self.__Note = inNote if len(inNote) > 0 else “No note” def setAmount(self, newAmount): self.__Amount = newAmount if newAmount >= 0.0 else self.__Amount def getAmount(self): return self.__Amount def setCode(self, newCode): self.__Code = newCode if newCode == ‘W’ or newCode == ‘D’ else self.__Code def getCode(self): return self.__Code def setNote(self, newNote): self.__Note = newNote if len(newNote) > 0 else self.__Note def getNote(self): return self.__Note def loadTransaction(self): self.setAmount(float(input(“Enter transaction amount(DD.CC), $ “))) self.setCode(input(“Enter transaction code (‘W’ or ‘D’), “)) self.setNote(input(“Enter purpose of transaction, “))The BankStatement class contains two list containers of Transaction objects, a list container of float values, some BankStatement support data fields, and the required methods to manipulate selected data fields, insert transactions, arrange (i.e., sort) the contained transaction objects, and print them.# Python model of a bank statement capable of# holding and managing multiple bank transactions## Filename: bankStatement.pyfrom transaction import Transactionclass BankStatement: def __init__(self, begBal = 0.0, endBal = 0.0): self.__TransactionLog = [] self.__ArrangedLog = [] self.__RunningBalLog = [] self.__BegBal = begBal self.__EndBal = endBal self.__NumEntries = 0 self.__NumDeposits = 0 self.__NumWithdrawals = 0 def setBegEndBals(self, balance): self.__BegBal = self.__EndBal = balance def getBegBal(self): return self.__BegBal def getEndBal(self): return self.__EndBal def getNumEntries(self): return self.__NumEntries def getNumDeposits(self): return self.__NumDeposits def getNumWithdrawals(self): return self.__NumWithdrawals def insertTransaction(self, transaction): self.__Transactionlog.append(transaction) # Update __RunningBalLog, increment __NumEntries and increment either # __NumDeposits or __NumWithdrawals depending upon whether transaction is a deposit # or a withdrawal def displayResults(self): # Displays __BegBal, __TransactionLog list, __RunningBal list, and final stats (i.e., __EndBal, total transactions, number of deposits and number of withdrawls) # See example output def arrangeTransactions(self): # Builds __ArrangedLog list from __TransactionLog list def printArranged(self): # Displays the __ArrangedLog listThe declared classes and their contents are a starting point for the program. You may not need all the class members described above. Do not feel bound to implement this program using the exact methods and/or data fields given. The primary objective is for you to solve the problem of providing a bank statement to the bank’s customers using O-O programming techniques. HOWEVER, if you deviate from the above design be sure to fully document your design! If in doubt as to whether your deviation violates the intent of this exercise, ask your instructor.In the interest of sound software engineering practice, make sure to validate the values provided to the constructor method of class BankStatement. For invalid values you may choose to completely reject the passed in values and set the data fields to some default (but valid) values. In either case you should also display an error message.Below is a non-interactive(i.e., batch), main driver test function that will confirm to you and your instructor that the program operates as expected. Use the transaction objects given as data for your final submission of the program.def main(): # NOTE THIS IS A NON-INTERACTIVE DRIVER! myStatement = BankStatement() myStatement.setBegEndBals(15.92); # Sets beginning AND ending balance data fields # Declare some transaction objects T1 = Transaction() # TEST DATA T1.setAmount (123.56) T1.setCode(‘D’) T1.setNote(“CTPay”) T2 = Transaction(153.86, ‘W’,”Rent”) T3 = Transaction() T3.setAmount(75.56) T3.setCode(‘D’) T3.setNote(“Tips”) T4 = Transaction(12.56, ‘D’,”Gift”) T5 = Transaction() T5.setAmount(73.74) T5.setCode(‘W’) T5.setNote(“Date”) T6 = Transaction(145.75, ‘D’,”Loan”) T7 = Transaction() T7.setAmount(40.00) T7.setCode(‘W’) T7.setNote(“Loan Payment”) T8 = Transaction(21.74, ‘W’, “Groceries”) # Now insert the transaction objects into the bank statement myStatement.enterTransaction(T1) # Enter transactions into the myStatement.enterTransaction(T2) # BankStatement object # Six more transactions entered…………………………………………………………… ……………………………………………………………………………………………… # continue # Manipulate the bank statement myStatement.displayResults() myStatement.arrangeTransactions() myStatement.printArranged()The following is a look at what the output might look like from the method, displayResults(). The beginning balance was: $15.92 Transaction: 1 was a D amount: $123.56 for CTPay Running Bal: $139.48 Transaction: 2 was a W amount: $153.86 for Rent Running Bal: $-14.38 OVERDRAWN etc., for the other transactions……….…………………………………………………… …….………………………………………………………………………………………. The ending balance is: $84.01 The number of Transactions is: 8 The number of Deposits is: 4 The number of Withdrawals is: 4The following is the result after calling the arrangeTransactions() and printArranged() methods in the BankStatement class. Printing the Deposits and Withdrawals as a group: Transaction was a D amount: $123.56 for CTPay Transaction was a D amount: $75.56 for Tips Transaction was a D amount: $12.56 for Gift Transaction was a D amount: $145.75 for Loan Transaction was a W amount: $153.86 for Rent Transaction was a W amount: $73.74 for Date Transaction was a W amount:$40.00 for Loan Payment Transaction was a W amount: $21.74 for GroceriesTo build the ArrangedLog container in method, arrangeTransactions(), the following strategy is recommended: 1. Traverse the TransactionLog container checking each cell to determine if it is a deposit (‘D’) or withdrawal (‘W’): Loop for number of entries in the TransactionLog if TransactionLog[i].getCode() == ‘D’: append transaction in TransactionLog[i] to next open cell in list container, ArrangedLog 2. In another loop (very similar to the loop above), go back to the beginning of the TransactionLog container and check for all the ‘W’s and copy (i.e., append) them to the ArrangedLog container following the deposits.Now the method, printArranged(), just needs to loop through its entries and display the contents of the ArrangedLog container as shown above.Notice that the methods of an object contained within a containment object are accessed with the selection operator just as though you had the name of the object. However, inside the BankStatement object (myStatement), all you have access to is a container of Transaction objects — not their individual names — hence the TransactionLog[i].getNote() notation.Deliverable(s)Your deliverable should be a Word document with screenshots showing the source code and running results. If the source code is too long, you may insert your source code files as Packages into the Word document. You may also login to the class by using a browser in the AWS, and upload your source code directly. Submit a cover sheet with the hardcopy of your work.
0 notes
Text
An SEO Primer for Entrepreneurs
New Post has been published on https://myupdatesystems.com/an-seo-primer-for-entrepreneurs/
An SEO Primer for Entrepreneurs
So, two weeks ago you realized that your company was missing out completely on online business. You were struggling to make your minimum sales quotas month to month, and you certainly weren’t moving forward. For the past two to three years now you’ve watched your profit margins get slashed, your ROI drop precipitously, and your bottom line bottom out. You’ve been wracking your brain to figure out what to do, how to reinvigorate your struggling business.
Your kids were your first inspiration – day after day for several years you’ve come home weary from worry, to find them plunked in front of the family desktop, staring, laughing, and telling you to watch the latest video online. You always hated computers, even from the start of the personal computer revolution. You found them intimidating, confusing, and beyond comprehension, but as time has gone by you’ve gotten used to the notion that they seem to be here to stay. All your business associates, friends, family, and neighbors seem to have embraced them with gusto, but you alone have held out. You felt yourself to be the last bastion of normalcy in a world a swim in electronics.
Ah, those kids… they drive you crazy, don’t they? You wonder, “How much time per week do those kids spend staring at that screen, while they might better use their time on more constructive things?” “What a waste of time,” you harp.
You’re bothered, annoyed, worried about your company, as well. “How can we get back on top of the market?” you wonder. You’re watching those teenage maniacs glibly speeding through their paces, page after page, photo after photo, clicking this and that. You stand amazed at the amount of attention and time they devote to this meaningless pursuit.
Suddenly, something caught your eye as you are peeking over young Courtney’s shoulder. There, in the right column of the page was a small advertisement for a company that offers self-publishing of books. Your jaw muscles clenched and then went slack. Your children heard a strange “clunk” as your jaw made contact with your collarbone. Drool began to stream from your pendulous, quivering lower lip as you stared incredulously at that little, “insignificant” ad.
“What,” you may ask, dear reader, “is the cause of the above graphic description?”
Our captain of industry had just had an epiphany regarding internet marketing platforms. Namely, that of finding that his main competitor is the source for the ad that he was gazing at right at that moment with incredulity. Our hero had just found the source of his frustrations, he’d finally realized how stuck in the mud and out of sync with the rest of the business world he truly was. As I mentioned before, he’d had an epiphany.
So, getting back to our hero… You met a man who owns a specialty fabrication company. He told you of how his company was on the rocks. He talked about how he and his partners were beside themselves, not knowing how to proceed or what to do to overcome the multifaceted impediments that were preventing them from prospering. Your new friend said he was about to throw in the towel when he heard from a business acquaintance about a certain marketing company. Your friend said that he made the decision, after hearing about the complete turnaround that occurred with his friend’s company, that he had nothing to lose and that he’d better give it a shot, or spend the next several weeks and months watching his business go down the tubes.
Your friend conveyed to you how, despite his misgivings, he watched in awe as, just a few weeks later the orders started to trickle, then flow, and finally to pour in. After awhile, it became clear to him that he needed to expand in order to handle all the business!
Convinced, mostly, you contacted the same marketing consultancy, looking for answers, solutions to the mire you found yourself trapped in.
Shift ahead one month. You hooked up with that marketing consultancy, a Cincinnati marketing firm, and watched things miraculously come together. The consultancy created a new logo that describes your company in a bright, new way. A website took shape, sporting the latest advances in technology. The next conversation you had with the marketing rep went as such, “We need to optimize your website for search engine marketing.” You blankly looked at him and said, “Okay.” He explained to you that SEO is an ongoing project, a moving target, but that it was totally necessary to commit to sticking with it and even increasing the scope and breadth of the overall program into the future. That took you aback a bit. Your face betrayed the fact that you still had some doubts about the whole thing, “After all, this isn’t what we always did in the past,” you complained. “And look where that got you,” the marketing rep replied gently. He assured you, again, that the times have changed and there are much more options than in the old days. You no longer needed a dedicated bank of secretaries, operators, a back room full of high schoolers and college kids folding, stuffing, licking and stamping direct mail pieces, and more, to make your business hum. In fact, that route was a waste of money.
“What we’ve seen, using our four-step marketing method, is unprecedented growth, up to 300% for some clients,” the marketing rep continued. “We are making an SEO marketing plan that, if followed, will drastically grow the traffic of your small business. Being a marketing consultant, what I’m sharing with my clients isn’t a theory. These suggestions are strategies that have proven to provide explosive growth for much small business client’s revenues, some 200% or 300% annually. A large part of our focus and work involves the marketing arsenal weapon, SEO, which directs prospects to your main website.”
“Okay. Let’s talk about 6 key concepts that have the potential to greatly help your company grow,” says I.
SEO Tip #1
On-site Optimization – With going into great detail, by optimizing, or changing, the code, the content, your keyword density, as well as the linking structure of your website in certain ways, the top search engines will end up approving and promoting your site. We make sure that we fix your broken links, checking that the metadata is clean on the entire website. Eliminating duplicate content on your website is very important, as well. So basically, the first step is to make sure that your site has all the attributes that will make search engines like it”
SEO Tip #2
Microsite Marketing – “This next technique might seem like I’m just saying this to make myself more money. Don’t believe it, my motives are pure, although I will make myself more money by doing this for you, and so will you…
Imagine the effect that having 60 small websites all selling exactly what your main site sells, but using different keywords, original content, and images. Now 60 is just a number that I grabbed out of the air. It could be any number, as there’s no magic number. The point is creating a whole bunch of exposure, right? By creating, let’s say, 60 small, even 1 page sites, you are weaving a web of notoriety for the advancement of your agenda – sales!
a. Use an SEO-friendly Platform – To get optimum results, we mostly use a certain well-known website platform. We typically create a custom theme, or customize an existing one, with SEO as the focus. Once that theme is completed, and signed off on by our client, we use the same theme, with some minor changes for each of the additional micro-sites, maintaining a uniform look throughout. Think of it as a unified campaign.
b. Make Sure Your Domain Name is SEO Friendly – Let’s say that we have a client come to us who owns an HVAC company. “Stan,Webpages” says to me, “Frank, we are only five miles away from Kenwood and Montgomery, but we can’t seem to get any business in those two areas. They are, as you know, high-dollar areas, and it would be great to get a foothold in the region. What can you do for me?” “Stanley my friend, I think we can help. We’ll build some sites for you with keywords written into the domain name, the URL. So then, when people search those keywords, for those areas of Cincinnati, your company will come up at the top, they’ll call you, and you can close the sale! The keywords might look like this:
Keyword – Kenwood Ohio HVAC Company
Keyword – Montgomery Ohio HVAC Company
While your domain names might be:
Domains – www dot Kenwood Ohio HVAC dot com or www dot Montgomery Ohio HVAC dot com
Of course, we’re not talking about your main website! These would be microsites for SEO purposes only, for the generation of traffic in those areas. We could just make one site, and then clone it many times, changing the verbiage of each.
c. Ya Gotta Have Unique Content – Just as the maxim in real estate is “Location. Location. Location.”, the maxim when dealing with search engines, and especially the big one, is “Original. Original. Original.” – content, that is. The biggest search engines couldn’t care less about the number of sites a company has, they just want each one to be UNIQUE, text-wise. They can have the same theme, looking very similar, but they have to have unique content.
SEOWeb pages
which Convert – By fixing your on-site SEO, and working on creating multiple micro-sites, a small business can be fairly sure of good results. The thing to avoid is whipping out a bunch of low quality, schlock-type sites. Good quality content, useful information, good design, and a focus on closing the deal, tactfully, will give a good return on your marketing investment.
How do you know whether what you paid for is actually having the desired results? Measurement! Because you have multiple microsites, you are able to do much A/B testing. Change one aspect on one site to differentiate it from the next, and you’re on your way. Not only is such testing a good idea, but it is critical to your success.
a. Analyze – To quickly find out about traffic coming to your micro-sites and what they’re up to, we use analytics software from the major search engines, as well as other proprietary software. Imagine yourself receiving a report in your email on a set schedule that tells you your traffic is up 25% or 50% from the last month! Do you think you’d be jazzed about that?
b. Individual Phone Numbers – Lining up unique phone numbers for each micro-site is another method by which we can track who’s going where, how often, for how long, and what they look at. All those numbers just go on to the company’s principal phone number, of course, letting us inform the client further.
c. Opt-in Forms – We like to include an opt-in form on each page of your micro-sites to be sure to involve your prospects to the highest degree. Offering something for free, if it is worth your prospects taking the time and bother, makes a great impact on the eventual sale.
These things will help greatly to give you webpages which convert prospects into paying customers.
SEO Tip #4
Continue to build content – This could be accomplished through an individual website, the thing is it’s been proven to work vastly better through many microsites. The way to go about it is to load lots of new content each month, till by the end of one year you have many pages, or blog posts, and you no longer have 60 microsites, but 60 unique macrosites with very high rankings in searches.
Thankfully, we have some excellent writers on our team of experts, with experience writing for several fortune 500 companies. You have a very good chance of doubling your traffic by doubling your content. It’s not as simple as that, exactly, but it REALLY helps. It’s important to add fresh, interesting, helpful content each week to get things really moving.
SEO Tip #5
Glacial Link Building Campaigns – Do I love the big G? Yes… and no. Over the course of the last few years, our gigantic friend has sought to dominate the internet, with quite a bit of success, I might add. As a result of that success, the company has found that it has lots of influence in mandating protocol, methodology, and “rules”. It’s these rules against which I chafe. Link building was a standard part of the package of all internet marketers, and indeed it still is. But the ease with which we could use it has come to an end. The big G knows what has been happening, that it has been manipulated into assigning high page ranks through aggressive link building campaigns. The largest search engine has managed to write software code that is very intelligent, able to see when such activity is occurring and penalizing the perpetrator soundly. At present, the route of avoidance of retribution is to set your links to trickling out at a snails pace. If all your code is clean, your content unique and of high value, and you have many high PR pages with links pointing back at you, things should go well with you.
SEO Tip #6
Time For a Little Magic – Finally, I’d like to tell you a story about the value of creating multitudinous links (a link wheel) and social site usage. “What kind of wheel?” you say, “What is that, some kind of artifact that fell off a Conestoga wagon?” In a word, no. It is an awesome notion worth knowing about. In a sense, I’ve already spoken about them, just not by name. Imagine your main, money-making website hovering in a white expanse, alone. Kind of sad, isn’t it? You’re looking at that lonely place and thinking “Nothing’s happening, and I’m getting depressed.” Then, up pops an article site off to the right, which surprises you, but pleasantly. “Pop,” you hear as a blog page arrives on the scene. “Where did that come from?” you ask. “Pop,” you see the logo of one social media company, then another, and another, and another. Then a micro-site pops into view. It’s only 2 pages long and is focused on the same thing your main site promotes, but with different wording and pictures. It’s starting to sound like popcorn in here. You now have a cheerful, if confused, look on your face, and a thought is forming in your mind. You watch as one after another all the available spots surrounding your main website are filled in. You think to your self that it looks kind of like a wheel, and there you are – a link wheel. You see connecting lines from each of these parts of the hub, like the spokes on a bicycle. There are also lines and arrows extending from some of the hub sites to others around them. “Pop, pop, pop, pop.” You can almost taste the popcorn now. It goes on and on like this, ever faster, ever widening, and you wonder whether there is an end to it all. Stepping back a long way, because it’s getting hard to see the entire thing, you think to yourself that it looks more like a donut now. But it just keeps growing, expanding, and luckily, you can see that there is infinite space and this thing could never fill the entire cyber-sphere. You see connectors running out into seemingly nowhere, but when you gaze fixedly out, your eyes somehow are able to focus, and you see another, unfamiliar website with a similar shape. It goes on like this until finally you understand – the visibility of your site has increased exponentially, till it is very hard, or impossible to ignore. At that moment, you see a giant spider-bot thing crawling along a length of web from that website out in the distance. You’re amazed at the speed at which it advances and before you can even blink, it’s here. The thing glances over at you with a look that makes you think it isn’t really impressed and quickly looks away. At first you were intimidated and thought it was going to suck your brain dry, but then you realize it has absolutely no interest in you. “Whew,” you snort, relieved. The spider moves at a blinding speed, analyzing, assessing, considering, measuring, and then stops. Out of a panel in it’s lower abdomen proceeds a tube, or rod. This rod quickly enters a hole that you hadn’t noticed till now in the side of your main website. The spider shakes and jerks a few times and then back goes the tube, the panel in the thing’s abdomen closes and something catches your eye. Your website has now changed, shining, bright, pulsating. You wonder about this, a look of glee on your face. Then all of a sudden, you hear whooshing sounds coming from all sides. You have to duck to avoid getting hit by one or the other connector as they race toward your main site. Connections, they seem to be, from other sites. They are arriving by the dozen, by the hundreds, by the thousands. Then the vision is over.
0 notes
Text
An SEO Primer for Entrepreneurs
New Post has been published on https://netmaddy.com/an-seo-primer-for-entrepreneurs/
An SEO Primer for Entrepreneurs
So, two weeks ago you realized that your company was missing out completely on online business. You were struggling to make your minimum sales quotas month to month, and you certainly weren’t moving forward. For the past two to three years now you’ve watched your profit margins get slashed, your ROI drop precipitously, and your bottom line bottom out. You’ve been wracking your brain to figure out what to do, how to reinvigorate your struggling business.
Your kids were your first inspiration – day after day for several years you’ve come home weary from worry, to find them plunked in front of the family desktop, staring, laughing, and telling you to watch the latest video online. You always hated computers, even from the start of the personal computer revolution. You found them intimidating, confusing, and beyond comprehension, but as time has gone by you’ve gotten used to the notion that they seem to be here to stay. All your business associates, friends, family and neighbors seem to have embraced them with gusto, but you alone have held out. You felt yourself to be the last bastion of normalcy in a world aswim in electronics.
Ah, those kids… they drive you crazy, don’t they? You wonder, “How much time per week do those kids spend staring at that screen, while they might better use their time on more constructive things?” “What a waste of time,” you harp.
You’re bothered, annoyed, worried about your company, as well. “How can we get back on top of the market?” you wonder. You’re watching those teenage maniacs glibly speeding through their paces, page after page, photo after photo, clicking this and that. You stand amazed at the amount of attention and time they devote to this meaningless pursuit.
Suddenly, something caught your eye as you are peeking over young Courtney’s shoulder. There, in the right column of the page was a small advertisement for a company that offers self-publishing of books. Your jaw muscles clenched and then went slack. Your children heard a strange “clunk” as your jaw made contact with your collarbone. Drool began to stream from your pendulous, quivering lower lip as you stared incredulously at that little, “insignificant” ad.
“What,” you may ask, dear reader, “is the cause of the above graphic description?”
Our captain of industry had just had an epiphany regarding internet marketing platforms. Namely, that of finding that his main competitor is the source for the ad that he was gazing at right at that moment with incredulity. Our hero had just found the source of his frustrations, he’d finally realized how stuck in the mud and out of sync with the rest of the business world he truly was. As I mentioned before, he’d had an epiphany.
So, getting back to our hero… You met a man who owns a specialty fabrication company. He told you of how his company was on the rocks. He talked about how he and his partners were beside themselves, not knowing how to proceed or what to do to overcome the multifaceted impediments that were preventing them from prospering. Your new friend said he was about to throw in the towel when he heard from a business acquaintance about a certain marketing company. Your friend said that he made the decision, after hearing about the complete turnaround that occurred with his friend’s company, that he had nothing to lose and that he’d better give it a shot, or spend the next several weeks and months watching his business go down the tubes.
Your friend conveyed to you how, despite his misgivings, he watched in awe as, just a few weeks later the orders started to trickle, then flow, and finally to pour in. After awhile, it became clear to him that he needed to expand in order to handle all the business!
Convinced, mostly, you contacted the same marketing consultancy, looking for answers, solutions to the mire you found yourself trapped in.
Shift ahead one month. You hooked up with that marketing consultancy, a Cincinnati marketing firm, and watched things miraculously come together. The consultancy created a new logo that describes your company in a bright, new way. A website took shape, sporting the latest advances in technology. The next conversation you had with the marketing rep went as such, “We need to optimize your website for search engine marketing.” You blankly looked at him and said, “Okay.” He explained to you that SEO is an ongoing project, a moving target, but that it was totally necessary to commit to sticking with it, and even increasing the scope and breadth of the overall program into the future. That took you aback a bit. Your face betrayed the fact that you still had some doubts about the whole thing, “After all, this isn’t what we always did in the past,” you complained. “And look where that got you,” the marketing rep replied gently. He assured you, again, that the times have changed and there are many more options than in the old days. You no longer needed a dedicated bank of secretaries, operators, a back room full of high schoolers and college kids folding, stuffing, licking and stamping direct mail pieces, and more, to make your business hum. In fact, that route was a waste of money.
“What we’ve seen, using our four-step marketing method, is unprecedented growth, up to 300% for some clients,” the marketing rep continued. “We are making an SEO marketing plan that, if followed, will drastically grow the traffic of your small business. Being a marketing consultant, what I’m sharing with my clients isn’t theory. These suggestions are strategies that have proven to provide explosive growth for many small business client’s revenues, some 200% or 300% annually. A large part of our focus and work involves the marketing arsenal weapon, SEO, which directs prospects to your main website.”
“Okay. Let’s talk about 6 key concepts that have the potential to greatly help your company grow,” says I.
SEO Tip #1
On-site Optimization – With going into great detail, by optimizing, or changing, the code, the content, your keyword density, as well as the linking structure of your website in certain ways, the top search engines will end up approving and promoting your site. We make sure that we fix your broken links, checking that the meta data is clean on the entire website. Eliminating duplicate content on your website is very important, as well. So basically, the first step is to make sure that your site has all the attributes that will make search engines like it”
SEO Tip #2
Micro-site Marketing – “This next technique might seem like I’m just saying this to make myself more money. Don’t believe it, my motives are pure, although I will make myself more money by doing this for you, and so will you…
Imagine the effect that having 60 small websites all selling exactly what your main site sells, but using different keywords, original content, and images. Now 60 is just a number that I grabbed out of the air. It could be any number, as there’s no magic number. The point is creating a whole bunch of exposure, right? By creating, let’s say, 60 small, even 1 page sites, you are weaving a web of notoriety for the advancement of your agenda – sales!
a. Use an SEO-friendly Platform – To get optimum results, we mostly use a certain well-known website platform. We typically create a custom theme, or customize an existing one, with SEO as the focus. Once that theme is completed, and signed off on by our client, we use the same theme, with some minor changes for each of the additional micro-sites, maintaining a uniform look throughout. Think of it as a unified campaign.
b. Make Sure Your Domain Name is SEO Friendly – Let’s say that we have a client come to us who owns an HVAC company. “Stan” says to me, “Frank, we are only five miles away from Kenwood and Montgomery, but we can’t seem to get any business in those two areas. They are, as you know, high-dollar areas, and it would be great to get a foothold in the region. What can you do for me?” “Stanley my friend, I think we can help. We’ll build some sites for you with keywords written into the domain name, the URL. So then, when people search those keywords, for those areas of Cincinnati, your company will come up at the top, they’ll call you, and you can close the sale! The keywords might look like this:
Keyword – Kenwood Ohio HVAC Company
Keyword – Montgomery Ohio HVAC Company
While your domain names might be:
Domains – www dot Kenwood hi HVAC dot com or www dot Montgomery Ohio HVAC dot com
Of course, we’re not talking about your main website! These would be microsites for SEO purposes only, for the generation of traffic in those areas. We could just make one site, and then clone it many times, changing the verbiage of each.
c. Ya Gotta Have Unique Content – Just as the maxim in real estate is “Location. Location. Location.”, the maxim when dealing with search engines, and especially the big one, is “Original. Original. Original.” – content, that is. The biggest search engines couldn’t care less about the number of sites a company has, they just want each one to be UNIQUE, text-wise. They can have the same theme, looking very similar, but they have to have unique content.
SEO Tip #3
Webpages which Convert – By fixing your on-site SEO, and working on creating multiple micro-sites, a small business can be fairly sure of good results. The thing to avoid is whipping out a bunch of low quality, schlock-type sites. Good quality content, useful information, good design, and a focus on closing the deal, tactfully, will give a good return on your marketing investment.
How do you know whether what you paid for is actually having the desired results? Measurement! Because you have multiple microsites, you are able to do much A/B testing. Change one aspect on one site to differentiate it from the next, and you’re on your way. Not only is such testing a good idea, but it is critical to your success.
a. Analyze – To quickly find out about traffic coming to your micro-sites and what they’re up to, we use analytics software from the major search engines, as well as other proprietary software. Imagine yourself receiving a report in your email on a set schedule that tells you your traffic is up 25% or 50% from the last month! Do you think you’d be jazzed about that?
b. Individual Phone Numbers – Lining up unique phone numbers for each micro-site is another method by which we can track who’s going where, how often, for how long, and what they look at. All those numbers just go on to the company’s principal phone number, of course, letting us inform the client further.
c. Opt-in Forms – We like to include an opt-in form on each page of your micro-sites to be sure to involve your prospects to the highest degree. Offering something for free, if it is worth your prospects taking the time and bother, makes a great impact on the eventual sale.
These things will help greatly to give you webpages which convert prospects into paying customers.
SEO Tip #4
Continue to build content – This could be accomplished through an individual website, the thing is it’s been proven to work vastly better through many microsites. The way to go about it is to load lots of new content each month, till by the end of one year you have many pages, or blog posts, and you no longer have 60 microsites, but 60 unique macrosites with very high rankings in searches.
Thankfully, we have some excellent writers on our team of experts, with experience writing for several fortune 500 companies. You have a very good chance of doubling your traffic by doubling your content. It’s not as simple as that, exactly, but it REALLY helps. It’s important to add fresh, interesting, helpful content each week to get things really moving.
SEO Tip #5
Glacial Link Building Campaigns – Do I love the big G? Yes… and no. Over the course of the last few years, our gigantic friend has sought to dominate the internet, with quite a bit of success, I might add. As a result of that success, the company has found that it has lots of influence in mandating protocol, methodology, and “rules”. It’s these rules against which I chafe. Link building was a standard part of the package of all internet marketers, and indeed it still is. But the ease with which we could use it has come to an end. The big G knows what has been happening, that it has been manipulated into assigning high page ranks through aggressive link building campaigns. The largest search engine has managed to write software code that is very intelligent, able to see when such activity is occurring and penalizing the perpetrator soundly. At present, the route of avoidance of retribution is to set your links to trickling out at a snails pace. If all your code is clean, your content unique and of high value, and you have many high PR pages with links pointing back at you, things should go well with you.
SEO Tip #6
Time For a Little Magic – Finally, I’d like to tell you a story about the value of creating multitudinous links (a link wheel) and social site usage. “What kind of wheel?” you say, “What is that, some kind of artifact that fell off a Conestoga wagon?” In a word, no. It is an awesome notion worth knowing about. In a sense, I’ve already spoken about them, just not by name. Imagine your main, money-making website hovering in a white expanse, alone. Kind of sad, isn’t it? You’re looking at that lonely place and thinking “Nothing’s happening, and I’m getting depressed.” Then, up pops an article site off to the right, which surprises you, but pleasantly. “Pop,” you hear as a blog page arrives on the scene. “Where did that come from?” you ask. “Pop,” you see the logo of one social media company, then another, and another, and another. Then a micro-site pops into view. It’s only 2 pages long and is focused on the same thing your main site promotes, but with different wording and pictures. It’s starting to sound like popcorn in here. You now have a cheerful, if confused, look on your face, and a thought is forming in your mind. You watch as one after another all the available spots surrounding your main website are filled in. You think to your self that it looks kind of like a wheel, and there you are – a link wheel. You see connecting lines from each of these parts of the hub, like the spokes on a bicycle. There are also lines and arrows extending from some of the hub sites to others around them. “Pop, pop, pop, pop.” You can almost taste the popcorn now. It goes on and on like this, ever faster, ever widening, and you wonder whether there is an end to it all. Stepping back a long way, because it’s getting hard to see the entire thing, you think to yourself that it looks more like a donut now. But it just keeps growing, expanding, and luckily, you can see that there is infinite space and this thing could never fill the entire cyber-sphere. You see connectors running out into seemingly nowhere, but when you gaze fixedly out, your eyes somehow are able to focus, and you see another, unfamiliar website with a similar shape. It goes on like this until finally you understand – the visibility of your site has increased exponentially, till it is very hard, or impossible to ignore. At that moment, you see a giant spider-bot thing crawling along a length of web from that website out in the distance. You’re amazed at the speed at which it advances and before you can even blink, it’s here. The thing glances over at you with a look that makes you think it isn’t really impressed and quickly looks away. At first you were intimidated and thought it was going to suck your brain dry, but then you realize it has absolutely no interest in you. “Whew,” you snort, relieved. The spider moves at a blinding speed, analyzing, assessing, considering, measuring, and then stops. Out of a panel in it’s lower abdomen proceeds a tube, or rod. This rod quickly enters a hole that you hadn’t noticed till now in the side of your main website. The spider shakes and jerks a few times and then back goes the tube, the panel in the thing’s abdomen closes and something catches your eye. Your website has now changed, shining, bright, pulsating. You wonder about this, a look of glee on your face. Then all of a sudden, you hear whooshing sounds coming from all sides. You have to duck to avoid getting hit by one or the other connector as they race toward your main site. Connections, they seem to be, from other sites. They are arriving by the dozen, by the hundreds, by the thousands. Then the vision is over.
0 notes
Text
The ultimate data revolution podcasts playlist
Podcasts for disruption leaders and geeks.
Here is my hit list of some of the most noteworthy and interesting podcasts to download and enjoy. I have included a range of breadth and depth in this collection of audio pleasure. This will help you generate new curiosity for beginners to data and the chance to geek out for those that like to geek with machine learning and data science.
Boost personal productivity and expand your knowledge
The growth of podcasts in daily life continues to expand. They are rapidly taking the space from web browsing and magazine entertainment time. We are living during a phase of media change.
New enabled people consume niched audio content for pleasure, motivation, learning and discovery. This change helps boost the value of our day whilst on a busy commute or tuning out from a low value situation.
"Podcasts are turning into a high impact learning experience every day." -- James Doyle
When considering the explosion of podcasting we need to understand the rapid change it has generated in media consumption models. According to PEW Research from Journalism.org , by early 2016, over 35% of Americans had listened to a podcast. Our own personal experience confirms this pattern of increased consumption.
Use these quick list scanner codes to match your core interests
For speed scanning purposes I have coded the core subject areas to help you discover the type of information you seek faster.
The list numbered 1 through to 12 does not reflect any listening order of preference or other bias.
AI Artificial Intelligence
AN Analytics
BD Big Data
DS Data Science
DV Data Visualization
ML Machine Learning
ST Statistics
1. Linear Digressions
A friendly tone with a light view on serious subject matter. The host’s skills have a natural ability to communicate complex details to the curious minds. A perfect start point for anyone seeking to explore the world of
Core Subject Covered: AI, DS, ML
2. Data Skeptic
Published weekly for a few years, this has become a stable of our audio pleasure and inspiration. The start point of this broadcast is to be skeptic about a specific subject matter and then expand from that view point.
Core Subjects Covered: AI, BD, DS, ML, ST
3. Wharton Customer Analyticast
Although this podcast series stopped in 2016, I still find myself referring it to others as an effective source of insights. A great source to hear the work and capabilities for customer analytics, data privacy and decision making.
Core Subjects Covered: AN
4. Everything Analytics
This has just started so I am unsure of its future. The first (and only show so far January 2017) gives some practical hands on insights on how analytics impacts specific areas of business through supply chain management.
Core Subjects Covered: AN, DS, DV
5. Digital Analytics Power Hour
Is this the benchmark podcasts others hold their standards to? I will let you decide. Simply listen and enjoy.
Core Subjects Covered: AN, DV
6. Hadooponomics
A great podcast that might put many people off due to the niched name. The choice of subject matter and detailed discussions makes this a perfectly accessible listen. If you are curious about data science and the impact ethics has working with large data sets. Do not be put off with the title, dive in and enjoy.
Core Subjects Covered: BD, DS
7. ROMI Analytics
Why would I place a single episode broadcaster in this “Top” list? This pod offers interesting insights for marketing and analytics linked to free resource information. A focus on predictive models during this episode, enjoy this step by step insight and knowledge share.
Core Subjects Covered: AN, DS, ST
8. Artificial Intelligence in Industry
Dan Faggella is the hose and founder of TechEmergence. He is a deeply respected and established voice within the community. Boasting shared publications with World Economic Forum, Pew Research Center and mainstream Motherboard and TechCrunch these insights offered are a worthy placement on this list.
Core Subjects Covered: AI, AN, DS, ML
9. This week in machine learning and artificial intelligence
Hosted by Sam Charrington, this weekly pod offers a wide mix of interviews covering a wide range of subjects. Note: Some discussions come with a prior “techy” warning to prepare the listener in advance of running the risk becoming lost in terminology or geek speak.
Core Subjects Covered: AI, AN, DS, ML, ST
10. Learning Machines 101
The target audience for this podcast is “the general public”. The aim is to demystify artificial intelligence and machine learning. This is achieved in an entertaining manner. I think the balance here is spot on for developing insights for outsiders. The content is enough to make the curious motivated to conduct further information searches.
Core Subjects Covered: AI, ML, ST
11. The Present Beyond Measure Show
Working with data is one thing but communicating it through dynamic insights is another. This great show provides tips, ideas and experiences to help you provide narrative, story and concise meaning to the complex data you work with. No matter if you are have an extrovert or introvert personality I still suggest you listen.
Core Subjects Covered: AN, DV, ST
12. The O'Reilly Data Show
One of the most popular data shows generating mass media coverage. I need say no more!
Core Subjects Covered: AI, AN, DS
Conclusion
We have no affiliation with any of these podcasts. We have curated this list to give you an insight into our own pod consumption. I believe they will help others interested in the same subjects.
If you have a podcast within these genres that you think deserves to be placed on this list then simply drop a comment below. We will then review the broadcast and if we agree, it will make this as an updated part of the list so the full community can share and use.
I have aimed to satisfy C suite and geeks alike! Let me know if you have had a "podtastic" experience reading it!
BONUS! – click here to go to a dedicated Twitter List. The list includes the twitter feeds from the hosts, shows and other data shows not included in the above list. Join in to engage and keep yourself informed with all aspects of data science.
Happy listening and PLEASE SHARE this post with others that might be interested in the subject.
Written by James Doyle - Chief Podcast Listener at JAMSO
JAMSO helps leaders and business lift performance by linking vision to action through the people and systems for success.
Discover how we help companies in the are of Metrics
#Top data podcasts#big data and artificial intelligence sources#machine learning influencers#future tech and business learning#tech podcasts
0 notes
Text
SAM ALTMAN, THE CO-FOUNDER AS THE BEST WAY TO DO THAT IN A LOT OF VALUABLE ADVICE ABOUT BUSINESS, AND THEY'RE EXPECTED TO SPACKLE OVER THE GAPS WITH GRATUITOUS TRANSITIONS FURTHERMORE
I'm not eager to fix that. This is the sort of software that's supposed to be your best work in a fight, because fights are not sufficiently general. And so while you needed expressions for math to work, and when you do decide to raise money you won't yet have concrete results, you may as well use a less abstract language, especially since it may be more accurate to describe a market as a degenerate case of economic inequality as a ratio of one quantile's income or wealth to another's. An essay doesn't begin with a thesis, because you can't talk to the new startups would create new technology that further accelerated variation in productivity. And whatever you think of one that had a round fall through at the last moment. They delight in breaking rules, but not totally unlike your other friends. In the general case, if being smart were really an enviable quality, the girls would have broken ranks. At Y Combinator we've seen dramatic changes in the funding environment for startups. With the bizarre consequence that high school students have searched for does not seem to have in 1975. Some said I was speaking at a high valuation unless you can somehow achieve what those in the corporate world, but also about existing things becoming more addictive. It's really a group of your peers?
The field of philosophy is still shaken from the fright Wittgenstein gave it. Search for a few months ago an article about Y Combinator said, Once you take money from the most radical implications of what was, 700 years ago, writing software for the first 3 years we ran alternating batches in Boston and Silicon Valley. So Dad, there's this company called Apple. Perhaps letting your mind wander just far enough for new ideas to matter, you need a scalable idea to grow. One of the most common emails we get is from people asking if we can help them a lot more investments per partner, they have to sell for over 50 for the VCs to get even a 5x return, which is a well established field, but I think it may be slightly misleading to say that. You can measure this fear in how much less ideas mattered in speaking than writing. You couldn't make a rap like that stick to math or medicine.
Filter performance should still be searching breadth-first at 20. And so began the study of terms that have precise meanings. If someone had launched a new, third group who lived in towns and supported themselves by manufacturing and trade. Even a lot of work, and other similar classes of accommodations, you get yourself inserted directly into the stories. Once you cross over into ramen profitable, everything changes. This Moore's Law is not as hard as you possibly can for four. If you can claim that the median visitor generates 12 page views, less than 10, 000 users. Such hypersensitivity will come at a cost. Every designer's ears perk up at the mention of ugly source code, people will want.
The reason credentials have such prestige is that for most of the surprises. Few know this, at least to yourself, that there are a lot of mistakes. This argument applies proportionately. The author is a self-fulfilling prophecy. And microcomputers turned out to be i/o fast, because the bigger your ambition, reasonableness, and how easily they can become collateral damage of laws meant to fix some problems with C. Actually a lot of people, I like to work for Intel. They tend to be smart, or not. Though we were comparatively old when we started that our users were called direct marketers. Doctors discovered that several of his arteries were over 90% blocked to learn that the number was over 90%. Like a politician who wants to succeed. The Bay Area was a magnet for the young and optimistic for decades before it was associated with technology.
And while it would probably be better just to tell people what was new and harsh, and the history of programming languages from a distance. If you're not working, your competitors will get the leftovers, as they have in common, it turns out, though, is that the payoff is only on average proportionate to reward. The way to come up with heuristics for recognizing genuinely interesting problems, but deciding what problems would be good to be true, but that's because it's so counterintuitive, and partly because they tend to split the difference on the issues have lined up with charisma for 11 elections in a row? The things that matter aren't necessarily the ones people use for procrastinating in everyday life. All good investors supply a combination of the increasing number of things people want. Let's consider what it would take to break Apple's lock. Getting rich means you can use in this situation, society has fouled you. Better to have resolution, one way or the other it's going to be even faster, and you can do something you'd like to like. Few would deny that a story about a murder. We were just a couple founders with laptops.
In industrialized countries we walk down steps our whole lives and never think about this. This is true of all venture funding, but that's always true of ambitious efforts. Now, thanks to the documentary series Civilisation. Users love a site that's constantly improving. You have to be willing to visit the beach they voted most beautiful, but having to build programs out of the brutal equation that governs the lives of 99. If I didn't know Lisp, reading this would set me asking questions. Some are fit only for entry level jobs, but I'm guessing not. The reason is that investors are willing if forced to treat them as auxiliary sources of money. If you start a startup. These speakers would do better to consider their target user to be a universal taboo against sex with prepubescent children. You may as well anticipate it, and the 511 prior to the current batch feels like a town whose main industry is ideas, while New York's is finance and Silicon Valley's is startups.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#startups#school#income#people#implications#idea#hypersensitivity#efforts#fear#Intel
0 notes
Text
Original Post from FireEye Author: Michael Bailey
It is very unusual for FLARE to analyze a prolifically-used, privately-developed backdoor only to later have the source code and operator tools fall into our laps. Yet this is the extraordinary circumstance that sets the stage for CARBANAK Week, a four-part blog series that commences with this post.
CARBANAK is one of the most full-featured backdoors around. It was used to perpetrate millions of dollars in financial crimes, largely by the group we track as FIN7. In 2017, Tom Bennett and Barry Vengerik published Behind the CARBANAK Backdoor, which was the product of a deep and broad analysis of CARBANAK samples and FIN7 activity across several years. On the heels of that publication, our colleague Nick Carr uncovered a pair of RAR archives containing CARBANAK source code, builders, and other tools (both available in VirusTotal: kb3r1p and apwmie).
FLARE malware analysis requests are typically limited to a few dozen files at most. But the CARBANAK source code was 20MB comprising 755 files, with 39 binaries and 100,000 lines of code. Our goal was to find threat intelligence we missed in our previous analyses. How does an analyst respond to a request with such breadth and open-ended scope? And what did we find?
My friend Tom Bennett and I spoke about this briefly in our 2018 FireEye Cyber Defense Summit talk, Hello, Carbanak! In this blog series, we will expound at length and share a written retrospective on the inferences drawn in our previous public analysis based on binary code reverse engineering. In this first part, I’ll discuss Russian language concerns, translated graphical user interfaces of CARBANAK tools, and anti-analysis tactics as seen from a source code perspective. We will also explain an interesting twist where analyzing the source code surprisingly proved to be just as difficult as analyzing the binary, if not more. There’s a lot here; buckle up!
File Encoding and Language Considerations
The objective of this analysis was to discover threat intelligence gaps and better protect our customers. To begin, I wanted to assemble a cross-reference of source code files and concepts of specific interest.
Reading the source code entailed two steps: displaying the files in the correct encoding, and learning enough Russian to be dangerous. Figure 1 shows CARBANAK source code in a text editor that is unaware of the correct encoding.
Figure 1: File without proper decoding
Two good file encoding guesses are UTF-8 and code page 1251 (Cyrillic). The files were mostly code page 1251 as shown in Figure 2.
Figure 2: Code Page 1251 (Cyrillic) source code
Figure 2 is a C++ header file defining error values involved in backdoor command execution. Most identifiers were in English, but some were not particularly descriptive. Ergo, the second and more difficult step was learning some Russian to benefit from the context offered by the source code comments.
FLARE has fluent Russian speakers, but I took it upon myself to minimize my use of other analysts’ time. To this end, I wrote a script to tear through files and create a prioritized vocabulary list. The script, which is available in the FireEye vocab_scraper GitHub repository, walks source directories finding all character sequences outside the printable lower ASCII range: decimal values 32 (the space character) through 126 (the tilde character “~”) inclusive. The script adds each word to a Python defaultdict_ and increments its count. Finally, the script orders this dictionary by frequency of occurrence and dumps it to a file.
The result was a 3,400+ word vocabulary list, partially shown in Figure 3.
Figure 3: Top 19 Cyrillic character sequences from the CARBANAK source code
I spent several hours on Russian language learning websites to study the pronunciation of Cyrillic characters and Russian words. Then, I looked up the top 600+ words and created a small dictionary. I added Russian language input to an analysis VM and used Microsoft’s on-screen keyboard (osk.exe) to navigate the Cyrillic keyboard layout and look up definitions.
One helpful effect of learning to pronounce Cyrillic characters was my newfound recognition of English loan words (words that are borrowed from English and transliterated to Cyrillic). My small vocabulary allowed me to read many comments without looking anything up. Table 1 shows a short sampling of some of the English loan words I encountered.
Cyrillic
English Phonetic
English
Occurrences
Rank
Файл
f ah y L
file
224
5
сервер
s e r v e r
server
145
13
адрес
a d r e s
address
52
134
команд
k o m a n d
command
110+
27
бота
b o t a
bot
130
32
плагин
p l ah g ee n
plugin
116
39
сервис
s e r v ee s
service
70
46
процесс
p r o ts e s s
process
130ish
63
Table 1: Sampling of English loan words in the CARBANAK source code
Aside from source code comments, understanding how to read and type in Cyrillic came in handy for translating the CARBANAK graphical user interfaces I found in the source code dump. Figure 4 shows a Command and Control (C2) user interface for CARBANAK that I translated.
Figure 4: Translated C2 graphical user interface
These user interfaces included video management and playback applications as shown in Figure 5 and Figure 6 respectively. Tom will share some interesting work he did with these in a subsequent part of this blog series.
Figure 5: Translated video management application user interface
Figure 6: Translated video playback application user interface
Figure 7 shows the backdoor builder that was contained within the RAR archive of operator tools.
Figure 7: Translated backdoor builder application user interface
The operator RAR archive also contained an operator’s manual explaining the semantics of all the backdoor commands. Figure 8 shows the first few commands in this manual, both in Russian and English (translated).
Figure 8: Operator manual (left: original Russian; right: translated to English)
Down the Rabbit Hole: When Having Source Code Does Not Help
In simpler backdoors, a single function evaluates the command ID received from the C2 server and dispatches control to the correct function to carry out the command. For example, a backdoor might ask its C2 server for a command and receive a response bearing the command ID 0x67. The dispatch function in the backdoor will check the command ID against several different values, including 0x67, which as an example might call a function to shovel a reverse shell to the C2 server. Figure 9 shows a control flow graph of such a function as viewed in IDA Pro. Each block of code checks against a command ID and either passes control to the appropriate command handling code, or moves on to check for the next command ID.
Figure 9: A control flow graph of a simple command handling function
In this regard, CARBANAK is an entirely different beast. It utilizes a Windows mechanism called named pipes as a means of communication and coordination across all the threads, processes, and plugins under the backdoor’s control. When the CARBANAK tasking component receives a command, it forwards the command over a named pipe where it travels through several different functions that process the message, possibly writing it to one or more additional named pipes, until it arrives at its destination where the specified command is finally handled. Command handlers may even specify their own named pipe to request more data from the C2 server. When the C2 server returns the data, CARBANAK writes the result to this auxiliary named pipe and a callback function is triggered to handle the response data asynchronously. CARBANAK’s named pipe-based tasking component is flexible enough to control both inherent command handlers and plugins. It also allows for the possibility of a local client to dispatch commands to CARBANAK without the use of a network. In fact, not only did we write such a client to aid in analysis and testing, but such a client, named botcmd.exe, was also present in the source dump.
Tom’s Perspective
Analyzing this command-handling mechanism within CARBANAK from a binary perspective was certainly challenging. It required maintaining tabs for many different views into the disassembly, and a sort of textual map of command ids and named pipe names to describe the journey of an inbound command through the various pipes and functions before arriving at its destination. Figure 10 shows the control flow graphs for seven of the named pipe message handling functions. While it was difficult to analyze this from a binary reverse engineering perspective, having compiled code combined with the features that a good disassembler such as IDA Pro provides made it less harrowing than Mike’s experience. The binary perspective saved me from having to search across several source files and deal with ambiguous function names. The disassembler features allowed me to easily follow cross-references for functions and global variables and to open multiple, related views into the code.
Figure 10: Control flow graphs for the named pipe message handling functions
Mike’s Perspective
Having source code sounds like cheat-mode for malware analysis. Indeed, source code contains much information that is lost through the compilation and linking process. Even so, CARBANAK’s tasking component (for handling commands sent by the C2 server) serves as a counter-example. Depending on the C2 protocol used and the command being processed, control flow may take divergent paths through different functions only to converge again later and accomplish the same command. Analysis required bouncing around between almost 20 functions in 5 files, often backtracking to recover information about function pointers and parameters that were passed in from as many as 18 layers back. Analysis also entailed resolving matters of C++ class inheritance, scope ambiguity, overloaded functions, and control flow termination upon named pipe usage. The overall effect was that this was difficult to analyze, even in source code.
I only embarked on this top-to-bottom journey once, to search for any surprises. The effort gave me an appreciation for the baroque machinery the authors constructed either for the sake of obfuscation or flexibility. I felt like this was done at least in part to obscure relationships and hinder timely analysis.
Anti-Analysis Mechanisms in Source Code
CARBANAK’s executable code is filled with logic that pushes hexadecimal numbers to the same function, followed by an indirect call against the returned value. This is easily recognizable as obfuscated function import resolution, wherein CARBANAK uses a simple string hash known as PJW (named after its author, P.J. Weinberger) to locate Windows API functions without disclosing their names. A Python implementation of the PJW hash is shown in Figure 11 for reference.
def pjw_hash(s): ctr = 0 for i in range(len(s)): ctr = 0xffffffff & ((ctr << 4) + ord(s[i])) if ctr & 0xf0000000: ctr = (((ctr & 0xf0000000) >> 24) ^ ctr) & 0x0fffffff
return ctr
Figure 11: PJW hash
This is used several hundred times in CARBANAK samples and impedes understanding of the malware’s functionality. Fortunately, reversers can use the flare-ida scripts to annotate the obfuscated imports, as shown in Figure 12.
Figure 12: Obfuscated import resolution annotated with FLARE’s shellcode hash search
The CARBANAK authors achieved this obfuscated import resolution throughout their backdoor with relative ease using C preprocessor macros and a pre-compilation source code scanning step to calculate function hashes. Figure 13 shows the definition of the relevant API macro and associated machinery.
Figure 13: API macro for import resolution
The API macro allows the author to type API(SHLWAPI, PathFindFileNameA)(…) and have it replaced with GetApiAddrFunc(SHLWAPI, hashPathFindFileNameA)(…). SHLWAPI is a symbolic macro defined to be the constant 3, and hashPathFindFileNameA is the string hash value 0xE3685D1 as observed in the disassembly. But how was the hash defined?
The CARBANAK source code has a utility (unimaginatively named tool) that scans source code for invocations of the API macro to build a header file defining string hashes for all the Windows API function names encountered in the entire codebase. Figure 14 shows the source code for this utility along with its output file, api_funcs_hash.h.
Figure 14: Source code and output from string hash utility
When I reverse engineer obfuscated malware, I can’t help but try to theorize about how authors implement their obfuscations. The CARBANAK source code gives another data point into how malware authors wield the powerful C preprocessor along with custom code scanning and code generation tools to obfuscate without imposing an undue burden on developers. This might provide future perspective in terms of what to expect from malware authors in the future and may help identify units of potential code reuse in future projects as well as rate their significance. It would be trivial to apply this to new projects, but with the source code being on VirusTotal, this level of code sharing may not represent shared authorship. Also, the source code is accessibly instructive in why malware would push an integer as well as a hash to resolve functions: because the integer is an index into an array of module handles that are opened in advance and associated with these pre-defined integers.
Conclusion
The CARBANAK source code is illustrative of how these malware authors addressed some of the practical concerns of obfuscation. Both the tasking code and the Windows API resolution system represent significant investments in throwing malware analysts off the scent of this backdoor. Check out Part Two of this series for a round-up of antivirus evasions, exploits, secrets, key material, authorship artifacts, and network-based indicators.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Michael Bailey CARBANAK Week Part One: A Rare Occurrence Original Post from FireEye Author: Michael Bailey It is very unusual for FLARE to analyze a prolifically-used,
0 notes
Text
Original Post from FireEye Author: Michael Bailey
It is very unusual for FLARE to analyze a prolifically-used, privately-developed backdoor only to later have the source code and operator tools fall into our laps. Yet this is the extraordinary circumstance that sets the stage for CARBANAK Week, a four-part blog series that commences with this post.
CARBANAK is one of the most full-featured backdoors around. It was used to perpetrate millions of dollars in financial crimes, largely by the group we track as FIN7. In 2017, Tom Bennett and Barry Vengerik published Behind the CARBANAK Backdoor, which was the product of a deep and broad analysis of CARBANAK samples and FIN7 activity across several years. On the heels of that publication, our colleague Nick Carr uncovered a pair of RAR archives containing CARBANAK source code, builders, and other tools (both available in VirusTotal: kb3r1p and apwmie).
FLARE malware analysis requests are typically limited to a few dozen files at most. But the CARBANAK source code was 20MB comprising 755 files, with 39 binaries and 100,000 lines of code. Our goal was to find threat intelligence we missed in our previous analyses. How does an analyst respond to a request with such breadth and open-ended scope? And what did we find?
My friend Tom Bennett and I spoke about this briefly in our 2018 FireEye Cyber Defense Summit talk, Hello, Carbanak! In this blog series, we will expound at length and share a written retrospective on the inferences drawn in our previous public analysis based on binary code reverse engineering. In this first part, I’ll discuss Russian language concerns, translated graphical user interfaces of CARBANAK tools, and anti-analysis tactics as seen from a source code perspective. We will also explain an interesting twist where analyzing the source code surprisingly proved to be just as difficult as analyzing the binary, if not more. There’s a lot here; buckle up!
File Encoding and Language Considerations
The objective of this analysis was to discover threat intelligence gaps and better protect our customers. To begin, I wanted to assemble a cross-reference of source code files and concepts of specific interest.
Reading the source code entailed two steps: displaying the files in the correct encoding, and learning enough Russian to be dangerous. Figure 1 shows CARBANAK source code in a text editor that is unaware of the correct encoding.
Figure 1: File without proper decoding
Two good file encoding guesses are UTF-8 and code page 1251 (Cyrillic). The files were mostly code page 1251 as shown in Figure 2.
Figure 2: Code Page 1251 (Cyrillic) source code
Figure 2 is a C++ header file defining error values involved in backdoor command execution. Most identifiers were in English, but some were not particularly descriptive. Ergo, the second and more difficult step was learning some Russian to benefit from the context offered by the source code comments.
FLARE has fluent Russian speakers, but I took it upon myself to minimize my use of other analysts’ time. To this end, I wrote a script to tear through files and create a prioritized vocabulary list. The script, which is available in the FireEye vocab_scraper GitHub repository, walks source directories finding all character sequences outside the printable lower ASCII range: decimal values 32 (the space character) through 126 (the tilde character “~”) inclusive. The script adds each word to a Python defaultdict_ and increments its count. Finally, the script orders this dictionary by frequency of occurrence and dumps it to a file.
The result was a 3,400+ word vocabulary list, partially shown in Figure 3.
Figure 3: Top 19 Cyrillic character sequences from the CARBANAK source code
I spent several hours on Russian language learning websites to study the pronunciation of Cyrillic characters and Russian words. Then, I looked up the top 600+ words and created a small dictionary. I added Russian language input to an analysis VM and used Microsoft’s on-screen keyboard (osk.exe) to navigate the Cyrillic keyboard layout and look up definitions.
One helpful effect of learning to pronounce Cyrillic characters was my newfound recognition of English loan words (words that are borrowed from English and transliterated to Cyrillic). My small vocabulary allowed me to read many comments without looking anything up. Table 1 shows a short sampling of some of the English loan words I encountered.
Cyrillic
English Phonetic
English
Occurrences
Rank
Файл
f ah y L
file
224
5
сервер
s e r v e r
server
145
13
адрес
a d r e s
address
52
134
команд
k o m a n d
command
110+
27
бота
b o t a
bot
130
32
плагин
p l ah g ee n
plugin
116
39
сервис
s e r v ee s
service
70
46
процесс
p r o ts e s s
process
130ish
63
Table 1: Sampling of English loan words in the CARBANAK source code
Aside from source code comments, understanding how to read and type in Cyrillic came in handy for translating the CARBANAK graphical user interfaces I found in the source code dump. Figure 4 shows a Command and Control (C2) user interface for CARBANAK that I translated.
Figure 4: Translated C2 graphical user interface
These user interfaces included video management and playback applications as shown in Figure 5 and Figure 6 respectively. Tom will share some interesting work he did with these in a subsequent part of this blog series.
Figure 5: Translated video management application user interface
Figure 6: Translated video playback application user interface
Figure 7 shows the backdoor builder that was contained within the RAR archive of operator tools.
Figure 7: Translated backdoor builder application user interface
The operator RAR archive also contained an operator’s manual explaining the semantics of all the backdoor commands. Figure 8 shows the first few commands in this manual, both in Russian and English (translated).
Figure 8: Operator manual (left: original Russian; right: translated to English)
Down the Rabbit Hole: When Having Source Code Does Not Help
In simpler backdoors, a single function evaluates the command ID received from the C2 server and dispatches control to the correct function to carry out the command. For example, a backdoor might ask its C2 server for a command and receive a response bearing the command ID 0x67. The dispatch function in the backdoor will check the command ID against several different values, including 0x67, which as an example might call a function to shovel a reverse shell to the C2 server. Figure 9 shows a control flow graph of such a function as viewed in IDA Pro. Each block of code checks against a command ID and either passes control to the appropriate command handling code, or moves on to check for the next command ID.
Figure 9: A control flow graph of a simple command handling function
In this regard, CARBANAK is an entirely different beast. It utilizes a Windows mechanism called named pipes as a means of communication and coordination across all the threads, processes, and plugins under the backdoor’s control. When the CARBANAK tasking component receives a command, it forwards the command over a named pipe where it travels through several different functions that process the message, possibly writing it to one or more additional named pipes, until it arrives at its destination where the specified command is finally handled. Command handlers may even specify their own named pipe to request more data from the C2 server. When the C2 server returns the data, CARBANAK writes the result to this auxiliary named pipe and a callback function is triggered to handle the response data asynchronously. CARBANAK’s named pipe-based tasking component is flexible enough to control both inherent command handlers and plugins. It also allows for the possibility of a local client to dispatch commands to CARBANAK without the use of a network. In fact, not only did we write such a client to aid in analysis and testing, but such a client, named botcmd.exe, was also present in the source dump.
Tom’s Perspective
Analyzing this command-handling mechanism within CARBANAK from a binary perspective was certainly challenging. It required maintaining tabs for many different views into the disassembly, and a sort of textual map of command ids and named pipe names to describe the journey of an inbound command through the various pipes and functions before arriving at its destination. Figure 10 shows the control flow graphs for seven of the named pipe message handling functions. While it was difficult to analyze this from a binary reverse engineering perspective, having compiled code combined with the features that a good disassembler such as IDA Pro provides made it less harrowing than Mike’s experience. The binary perspective saved me from having to search across several source files and deal with ambiguous function names. The disassembler features allowed me to easily follow cross-references for functions and global variables and to open multiple, related views into the code.
Figure 10: Control flow graphs for the named pipe message handling functions
Mike’s Perspective
Having source code sounds like cheat-mode for malware analysis. Indeed, source code contains much information that is lost through the compilation and linking process. Even so, CARBANAK’s tasking component (for handling commands sent by the C2 server) serves as a counter-example. Depending on the C2 protocol used and the command being processed, control flow may take divergent paths through different functions only to converge again later and accomplish the same command. Analysis required bouncing around between almost 20 functions in 5 files, often backtracking to recover information about function pointers and parameters that were passed in from as many as 18 layers back. Analysis also entailed resolving matters of C++ class inheritance, scope ambiguity, overloaded functions, and control flow termination upon named pipe usage. The overall effect was that this was difficult to analyze, even in source code.
I only embarked on this top-to-bottom journey once, to search for any surprises. The effort gave me an appreciation for the baroque machinery the authors constructed either for the sake of obfuscation or flexibility. I felt like this was done at least in part to obscure relationships and hinder timely analysis.
Anti-Analysis Mechanisms in Source Code
CARBANAK’s executable code is filled with logic that pushes hexadecimal numbers to the same function, followed by an indirect call against the returned value. This is easily recognizable as obfuscated function import resolution, wherein CARBANAK uses a simple string hash known as PJW (named after its author, P.J. Weinberger) to locate Windows API functions without disclosing their names. A Python implementation of the PJW hash is shown in Figure 11 for reference.
def pjw_hash(s): ctr = 0 for i in range(len(s)): ctr = 0xffffffff & ((ctr << 4) + ord(s[i])) if ctr & 0xf0000000: ctr = (((ctr & 0xf0000000) >> 24) ^ ctr) & 0x0fffffff
return ctr
Figure 11: PJW hash
This is used several hundred times in CARBANAK samples and impedes understanding of the malware’s functionality. Fortunately, reversers can use the flare-ida scripts to annotate the obfuscated imports, as shown in Figure 12.
Figure 12: Obfuscated import resolution annotated with FLARE’s shellcode hash search
The CARBANAK authors achieved this obfuscated import resolution throughout their backdoor with relative ease using C preprocessor macros and a pre-compilation source code scanning step to calculate function hashes. Figure 13 shows the definition of the relevant API macro and associated machinery.
Figure 13: API macro for import resolution
The API macro allows the author to type API(SHLWAPI, PathFindFileNameA)(…) and have it replaced with GetApiAddrFunc(SHLWAPI, hashPathFindFileNameA)(…). SHLWAPI is a symbolic macro defined to be the constant 3, and hashPathFindFileNameA is the string hash value 0xE3685D1 as observed in the disassembly. But how was the hash defined?
The CARBANAK source code has a utility (unimaginatively named tool) that scans source code for invocations of the API macro to build a header file defining string hashes for all the Windows API function names encountered in the entire codebase. Figure 14 shows the source code for this utility along with its output file, api_funcs_hash.h.
Figure 14: Source code and output from string hash utility
When I reverse engineer obfuscated malware, I can’t help but try to theorize about how authors implement their obfuscations. The CARBANAK source code gives another data point into how malware authors wield the powerful C preprocessor along with custom code scanning and code generation tools to obfuscate without imposing an undue burden on developers. This might provide future perspective in terms of what to expect from malware authors in the future and may help identify units of potential code reuse in future projects as well as rate their significance. It would be trivial to apply this to new projects, but with the source code being on VirusTotal, this level of code sharing may not represent shared authorship. Also, the source code is accessibly instructive in why malware would push an integer as well as a hash to resolve functions: because the integer is an index into an array of module handles that are opened in advance and associated with these pre-defined integers.
Conclusion
The CARBANAK source code is illustrative of how these malware authors addressed some of the practical concerns of obfuscation. Both the tasking code and the Windows API resolution system represent significant investments in throwing malware analysts off the scent of this backdoor. Check out Part Two of this series for a round-up of antivirus evasions, exploits, secrets, key material, authorship artifacts, and network-based indicators.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Michael Bailey CARBANAK Week Part One: A Rare Occurrence Original Post from FireEye Author: Michael Bailey It is very unusual for FLARE to analyze a prolifically-used,
0 notes