#bfs algorithm in c
Explore tagged Tumblr posts
Text
Artificial Intelligence at Humber College - Final Presentation
youtube
#portfolio#AI#artificial intelligence#steering behavior#steering behaviour#decision making#decision-making#decisionmaking#pathfinding#path finding#path-finding#A star#A-star#Dijkstra algorithm#breadth-first search#breadth first search#BFS#c++#computer programming#coding#code#programming#data structures
0 notes
Text
Mastering Data Structures: A Comprehensive Course for Beginners
Data structures are one of the foundational concepts in computer science and software development. Mastering data structures is essential for anyone looking to pursue a career in programming, software engineering, or computer science. This article will explore the importance of a Data Structure Course, what it covers, and how it can help you excel in coding challenges and interviews.
1. What Is a Data Structure Course?
A Data Structure Course teaches students about the various ways data can be organized, stored, and manipulated efficiently. These structures are crucial for solving complex problems and optimizing the performance of applications. The course generally covers theoretical concepts along with practical applications using programming languages like C++, Java, or Python.
By the end of the course, students will gain proficiency in selecting the right data structure for different problem types, improving their problem-solving abilities.
2. Why Take a Data Structure Course?
Learning data structures is vital for both beginners and experienced developers. Here are some key reasons to enroll in a Data Structure Course:
a) Essential for Coding Interviews
Companies like Google, Amazon, and Facebook focus heavily on data structures in their coding interviews. A solid understanding of data structures is essential to pass these interviews successfully. Employers assess your problem-solving skills, and your knowledge of data structures can set you apart from other candidates.
b) Improves Problem-Solving Skills
With the right data structure knowledge, you can solve real-world problems more efficiently. A well-designed data structure leads to faster algorithms, which is critical when handling large datasets or working on performance-sensitive applications.
c) Boosts Programming Competency
A good grasp of data structures makes coding more intuitive. Whether you are developing an app, building a website, or working on software tools, understanding how to work with different data structures will help you write clean and efficient code.
3. Key Topics Covered in a Data Structure Course
A Data Structure Course typically spans a range of topics designed to teach students how to use and implement different structures. Below are some key topics you will encounter:
a) Arrays and Linked Lists
Arrays are one of the most basic data structures. A Data Structure Course will teach you how to use arrays for storing and accessing data in contiguous memory locations. Linked lists, on the other hand, involve nodes that hold data and pointers to the next node. Students will learn the differences, advantages, and disadvantages of both structures.
b) Stacks and Queues
Stacks and queues are fundamental data structures used to store and retrieve data in a specific order. A Data Structure Course will cover the LIFO (Last In, First Out) principle for stacks and FIFO (First In, First Out) for queues, explaining their use in various algorithms and applications like web browsers and task scheduling.
c) Trees and Graphs
Trees and graphs are hierarchical structures used in organizing data. A Data Structure Course teaches how trees, such as binary trees, binary search trees (BST), and AVL trees, are used in organizing hierarchical data. Graphs are important for representing relationships between entities, such as in social networks, and are used in algorithms like Dijkstra's and BFS/DFS.
d) Hashing
Hashing is a technique used to convert a given key into an index in an array. A Data Structure Course will cover hash tables, hash maps, and collision resolution techniques, which are crucial for fast data retrieval and manipulation.
e) Sorting and Searching Algorithms
Sorting and searching are essential operations for working with data. A Data Structure Course provides a detailed study of algorithms like quicksort, merge sort, and binary search. Understanding these algorithms and how they interact with data structures can help you optimize solutions to various problems.
4. Practical Benefits of Enrolling in a Data Structure Course
a) Hands-on Experience
A Data Structure Course typically includes plenty of coding exercises, allowing students to implement data structures and algorithms from scratch. This hands-on experience is invaluable when applying concepts to real-world problems.
b) Critical Thinking and Efficiency
Data structures are all about optimizing efficiency. By learning the most effective ways to store and manipulate data, students improve their critical thinking skills, which are essential in programming. Selecting the right data structure for a problem can drastically reduce time and space complexity.
c) Better Understanding of Memory Management
Understanding how data is stored and accessed in memory is crucial for writing efficient code. A Data Structure Course will help you gain insights into memory management, pointers, and references, which are important concepts, especially in languages like C and C++.
5. Best Programming Languages for Data Structure Courses
While many programming languages can be used to teach data structures, some are particularly well-suited due to their memory management capabilities and ease of implementation. Some popular programming languages used in Data Structure Courses include:
C++: Offers low-level memory management and is perfect for teaching data structures.
Java: Widely used for teaching object-oriented principles and offers a rich set of libraries for implementing data structures.
Python: Known for its simplicity and ease of use, Python is great for beginners, though it may not offer the same level of control over memory as C++.
6. How to Choose the Right Data Structure Course?
Selecting the right Data Structure Course depends on several factors such as your learning goals, background, and preferred learning style. Consider the following when choosing:
a) Course Content and Curriculum
Make sure the course covers the topics you are interested in and aligns with your learning objectives. A comprehensive Data Structure Course should provide a balance between theory and practical coding exercises.
b) Instructor Expertise
Look for courses taught by experienced instructors who have a solid background in computer science and software development.
c) Course Reviews and Ratings
Reviews and ratings from other students can provide valuable insights into the course’s quality and how well it prepares you for real-world applications.
7. Conclusion: Unlock Your Coding Potential with a Data Structure Course
In conclusion, a Data Structure Course is an essential investment for anyone serious about pursuing a career in software development or computer science. It equips you with the tools and skills to optimize your code, solve problems more efficiently, and excel in technical interviews. Whether you're a beginner or looking to strengthen your existing knowledge, a well-structured course can help you unlock your full coding potential.
By mastering data structures, you are not only preparing for interviews but also becoming a better programmer who can tackle complex challenges with ease.
3 notes
·
View notes
Text
the devs in the wildmender discord have been begging for game reviews b/c of steam ranking algorithmics stuff so i'm debating actually writing one (w/ my bf's steam account lol) but that involves actually putting my thoughts in order about the game
i mean i guess i've played it for 200+ hours so there's not really a question of me getting my money's worth out of it. it's just that... there's very clearly a mechanical push-and-pull happening. this is a gardening game. to make the plants have any level of 'reasonable fidelity' they made it so plants drop seeds and sometimes those seeds will germinate and sprout into new plants. but because plants grow so fast and there aren't really any things that kill plants, most players have their gardens totally overcome by unrestrained growth. the devs have had to patch down plant spread multiple times, first by making biome-specifying plants not produce their own seeds (so they don't spread biome plants out into infinity) and then by lowering the rate of seed germination and making germinated seeds start out as 'tired'
also, 'tired' is a weird corner of the plant simulation. the way plants work is they'll grow to maturity and then start producing & dropping seeds on a timer. after a few rounds of seeds they'll become 'tired', which slows the timer, and a few rounds after that they'll become 'exhausted', which means they won't produce seeds anymore; they essentially become decorative (you can remove tired & exhausted statuses by manually fertilizing them)
all of this speaks to a plant simulation system that can't really deal with the chaos of nature. which on some level is fine; ecological simulations are notoriously complex, and wildmender already has one of the more in-depth plant life simulations i've seen in a commercial game. but the more involved it gets the more clear it is that there's something vital missing, & i don't even know really what that would look like? it's not like i'd want to see pest insects in the game, although that would be interesting
(there's a whole aside i could make here about how 'nature' is treated as inherently productive in the game. all the plants you get do something; all of them 'improve' the area somehow in a way that makes it more suitable for human exploitation. there's no... massive tangles of gorseberry brambles that slows you and damages your health if you try to move through them, but provides critical habitat for birds. the one plant that's annoying (tumbleweeds) you only ever see in the dead, tumbling form. invasive plants are considered simulation bugs, instead of nature taking its natural course. this is a game about maximizing your productive forces. and in fact, as above, when the natural growth processes in the game as it currently exist end up making something annoying to the player, it ends up getting nerfed to be more suitable.
i think ultimately this is a flaw in the fundamental concept of 'cozy', 'wholesome' games, so it feels bad to pick on the game for that; that's not even something the game is trying to do! it's just something i don't like. this is a game where you can half-cut down a tree to harvest wood. and, like, sure it would be neat if the game used its semi-procedural tree models to actually implement pollarding, but that would make it more visually clear that what you're doing is managing an industrial tree farm rather than tending a garden.
basically, i like the game despite its 'cozy' aesthetic and not because of it, so i'm maybe not the target audience here.)
all of that is a lot of words that are only vaguely aligned with what the game is actually about, though. like the game blurb says, it's a 'gardening' game, not a serious afforestation agroforestry simulation. but i really do wish the plant simulation was more involved. more plants, more variants, more complex soil simulation (add in soil acidity! give me hydrangeas that bloom in different colors!), more complex biome specifications. other animals, preferable ones without instrumental uses and ideally ones that make the landscape actively obnoxious. i want to have to avoid a lake because there are roosting geese there that will attack. maybe just packing a lot more Stuff into the game would help with the feeling of it being overly-simplistic? but maybe that issue is more deeply-rooted and also impossible to really solve, in part b/c my complaint here is so vague and unclear.
that's a lot of demands for a small indie game, tho. anyway i found it to be worth the $25 i spent on it.
4 notes
·
View notes
Video
youtube
LEETCODE PROBLEMS 1-100 . C++ SOLUTIONS
Arrays and Two Pointers 1. Two Sum – Use hashmap to find complement in one pass. 26. Remove Duplicates from Sorted Array – Use two pointers to overwrite duplicates. 27. Remove Element – Shift non-target values to front with a write pointer. 80. Remove Duplicates II – Like #26 but allow at most two duplicates. 88. Merge Sorted Array – Merge in-place from the end using two pointers. 283. Move Zeroes – Shift non-zero values forward; fill the rest with zeros.
Sliding Window 3. Longest Substring Without Repeating Characters – Use hashmap and sliding window. 76. Minimum Window Substring – Track char frequency with two maps and a moving window.
Binary Search and Sorted Arrays 33. Search in Rotated Sorted Array – Modified binary search with pivot logic. 34. Find First and Last Position of Element – Binary search for left and right bounds. 35. Search Insert Position – Standard binary search for target or insertion point. 74. Search a 2D Matrix – Binary search treating matrix as a flat array. 81. Search in Rotated Sorted Array II – Extend #33 to handle duplicates.
Subarray Sums and Prefix Logic 53. Maximum Subarray – Kadane’s algorithm to track max current sum. 121. Best Time to Buy and Sell Stock – Track min price and update max profit.
Linked Lists 2. Add Two Numbers – Traverse two lists and simulate digit-by-digit addition. 19. Remove N-th Node From End – Use two pointers with a gap of n. 21. Merge Two Sorted Lists – Recursively or iteratively merge nodes. 23. Merge k Sorted Lists – Use min heap or divide-and-conquer merges. 24. Swap Nodes in Pairs – Recursively swap adjacent nodes. 25. Reverse Nodes in k-Group – Reverse sublists of size k using recursion. 61. Rotate List – Use length and modulo to rotate and relink. 82. Remove Duplicates II – Use dummy head and skip duplicates. 83. Remove Duplicates I – Traverse and skip repeated values. 86. Partition List – Create two lists based on x and connect them.
Stack 20. Valid Parentheses – Use stack to match open and close brackets. 84. Largest Rectangle in Histogram – Use monotonic stack to calculate max area.
Binary Trees 94. Binary Tree Inorder Traversal – DFS or use stack for in-order traversal. 98. Validate Binary Search Tree – Check value ranges recursively. 100. Same Tree – Compare values and structure recursively. 101. Symmetric Tree – Recursively compare mirrored subtrees. 102. Binary Tree Level Order Traversal – Use queue for BFS. 103. Binary Tree Zigzag Level Order – Modify BFS to alternate direction. 104. Maximum Depth of Binary Tree – DFS recursion to track max depth. 105. Build Tree from Preorder and Inorder – Recursively divide arrays. 106. Build Tree from Inorder and Postorder – Reverse of #105. 110. Balanced Binary Tree – DFS checking subtree heights, return early if unbalanced.
Backtracking 17. Letter Combinations of Phone Number – Map digits to letters and recurse. 22. Generate Parentheses – Use counts of open and close to generate valid strings. 39. Combination Sum – Use DFS to explore sum paths. 40. Combination Sum II – Sort and skip duplicates during recursion. 46. Permutations – Swap elements and recurse. 47. Permutations II – Like #46 but sort and skip duplicate values. 77. Combinations – DFS to select combinations of size k. 78. Subsets – Backtrack by including or excluding elements. 90. Subsets II – Sort and skip duplicates during subset generation.
Dynamic Programming 70. Climbing Stairs – DP similar to Fibonacci sequence. 198. House Robber – Track max value including or excluding current house.
Math and Bit Manipulation 136. Single Number – XOR all values to isolate the single one. 169. Majority Element – Use Boyer-Moore voting algorithm.
Hashing and Frequency Maps 49. Group Anagrams – Sort characters and group in hashmap. 128. Longest Consecutive Sequence – Use set to expand sequences. 242. Valid Anagram – Count characters using map or array.
Matrix and Miscellaneous 11. Container With Most Water – Two pointers moving inward. 42. Trapping Rain Water – Track left and right max heights with two pointers. 54. Spiral Matrix – Traverse matrix layer by layer. 73. Set Matrix Zeroes – Use first row and column as markers.
This version is 4446 characters long. Let me know if you want any part turned into code templates, tables, or formatted for PDF or Markdown.
0 notes
Text
im on my train and im bored so let's do this fully, by that i mean completing the maze with the shortest path
the first step is to isolate the path. bumping the contrast is good enough, but a cleaner way to do this is to do a simple thresholding, this makes the image binary (i.e., black and white) and makes the later processes simpler
i picked the threshold manually (value 200), we just need to make the maze look visible
since we wanna find a path (along the white line) from start to finish, we'd like the line to not be so thick, preferrably just one pixel thick, so we have a clearer path to walk on later. this process is called thinning in computer vision
the thresholding result and the thinning result are the below two images



now we walk from bottom to top (either way is fine). we simply do a breadth-first-search (BFS) to find the shortest path, where the nodes are the white pixels and the edges are the link between the neighbors

when the BFS reaches the other side, we can backtrack and get the result path



the time complexity of the maze solving BFS itself should be roughly O(number of white pixels), and the number of pixels is definitely under 1e8 (100,000,000), by the rule of thumb in comp sci field this program should be done under 1 second and there's really no need for further optimization
the code btw
Also two things to note:
1. There are algorithms to generate a valid maze, the (probably) most famous one is called Eller's algorithm, which basically guarentees that if you bucket fill the path at the start it will fill the whole maze. Thats probably why the original post's method didnt really reduce the search space
2. There are also algorithms to complete a maze with simple rules, for example the also famous hand-on-wall rule, where you just use one hand to touch the wall, keep following the wall until you reach the end. It does need some condition on the maze and almost definitely not the shortest path to solve the maze, but yeah you could try if you run out of options
edit: if you are actually looking at the code, tbh all (x, y) shouldve been written as (r, c) (meaning row & column) instead. oh well, im not gonna edit that now
SOBBING

ok so someone in a server im in sent this maze and told another friend to solve it, and i said i'd solve it my plan was simple, i was just going to use the bucket tool to fill in at least the main path from the start to the end.. there was an issue though

the image wasnt very high res so this anti aliasing made the bucket tool not play nicely. i figured i'd just use a levels adjustment layer to bump up the contrast and that worked well!

and so I covered the start and end with red, then used the bucket tool to fill in the rest. ..the maze had no disconnected parts, and my levels adjustment made the seal and ball at the top and bottom become uhh..

FUCKING. EVIL MAZE. JUMPSCARE
207 notes
·
View notes
Text
include <iostream>
using namespace std;
class node{
public:
node* next;
int val;
node(int k){
val=k;
next=NULL;
}
class q{
public:
node* head;
node* tail;
q(){
head=NULL;
tail=NULL;
}
push(int k){
if (q->head==NULL){
q->head=k;
q->tail=k;
#include <iostream>
#include <algorithm>
#include <vector>
#include <queue>
#include <climits>
using namespace std;
class graph{
int v;
vector<vector<int>> a;
graph(int vertex):v(vertex),a(vertex){}
void insert_edge(int u,int v){
a[u].push_back(v);
a[v].push_back(u);
}
void dfs(int s,vector<bool>& vis){
vector<bool> visited(v,false);
vector<int> st;
visited[s]=true;
st.push_back(s);
while(!st.empty()){
int c=st.back();
st.pop_back();
cout<<c<<" ";
for(int n:a[c]){
if(!visited[n]){
visited[n]=true;
st.push_back(n);
}
}
}
}
void bfs(int s){
vector<bool> visited(v,false);
queue<int> q;
visited[s]=true;
q.push(s);
while(!q.empty()){
int c=q.front();
q.pop();
cout<<c<<" ";
for(int n:a[c]){
if(!visited[n]){
visited[n]=true;
q.push(n);
}
}
}
}
bool connected(){
vector<bool> visited(v,false);
dfs(0,visited);
for(bool vi:visited){
if(!v){
return false;
}
}
return true;
}
bool directed(){
for(int i=0;i<v;i++){
for(int j:a[i]){
if(find(a[j].begin(),a[j].end(),i)==a[j].end()){
return true;
}
}
}
return false;
}
};
#practicing writing code without an editor because they don't let us use one for lab ijbol#and i apparently can't get off tumblr
0 notes
Text
Background:
Holy shit bitcoin is really just a worldwide game that got value because enough people agreed to play.
This is my favorite article on the topic so far and the one that explains it most clearly. But yeah, it works because of artifical scarcity and people willing to spend money on processors to guess/”solve” the right hexadecimal value to mine coin. Which means that Ethan got incredibly lucky that he decided to play this game back in 2012 (while I was busy being suicidal what am i DOING).
Several coins like this exist, and it looks like dogecoin is the second most popular cryptocurrency.
Environmental impact:
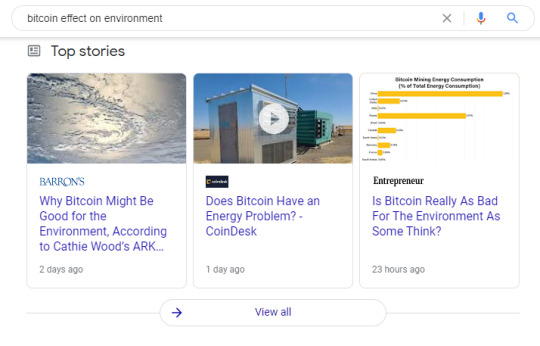
Ooooh why are the top articles funded by powerful financing groups that have a lot to gain from bitcoin staying in circulation. Ladies, ladies please.
“Studies indicate that the annual carbon emissions from the electricity generated to extract and process Bitcoin are equivalent to the amount emitted by New Zealand or Argentina.
The publication indicated that there are still disagreements about how big the carbon footprint of cryptocurrencies is, "but nobody disputes that it is big." Also, because of the way the industry works, the more popular Bitcoin becomes, the higher its carbon footprint”
source
So a solution is that bitcoin can still exist with a switch to sustainable energy practices. The issue is that most folks are still using electricity off of our current grid which produces carbon emissions. the foundation is bad, not bitcoin mining. The issue is that our current carbon emitting foundation is also the most consistent source of energy (talking America rn. I know Europe and Canada are ~different~ and we’re all jealous lads).
“One additional potential risk from the growth of bitcoin mining (and other proof-of-work systems as well) is the increasing energy usage required by the computer systems running the mining algorithms. While microchip efficiency has increased dramatically for ASIC chips, the growth of the network itself is outpacing technological progress. As a result, there are concerns about the environmental impact and carbon footprint of Bitcoin mining. There are, however, efforts to mitigate this negative externality by seeking cleaner and green energy sources for mining operations (such as geo-thermal or solar), as well as utilizing carbon offset credits. Switching to less energy-intensive consensus mechanisms like proof-of-stake (PoS), which Ethereum is planning to do, is another strategy; however, PoS comes with its own set of drawbacks and inefficiencies.”
source
“For example, Jack Dorsey, CEO of Twitter, promised to invest $ 10 million in developing cleaner technologies for the production of the cryptocurrency. In turn, Aker Solutions, an international engineering company based in Oslo (Norway), will build Bitcoin mining facilities that use renewable energy.”
source
Another common concern is that it is a waste of electricity. Meh. You can argue that TV is a waste of electricity.
Ways to Benefit:
"I've done the math. Forget mining. Is there a less onerous way to profit from cryptocurrencies?"
As mentioned above, the easiest way to acquire bitcoin is to simply buy it on one of the many exchanges. Alternately, you can always leverage the "pickaxe strategy." This is based on the old saw that during the 1849 California gold rush, the smart investment was not to pan for gold, but rather to make the pickaxes used for mining. Or, to put it in modern terms, invest in the companies that manufacture those pickaxes. In a cryptocurrency context, the pickaxe equivalent would be a company that manufactures equipment used for Bitcoin mining. You may consider looking into companies that make ASICs equipment or GPUs instead, for example.
^^^
In conclusion:
Bitcoin is only bad for the environment because of the framework it sits on. A switch to renewable sources could remedy the very very real environmental impact that bitcoin has. The trick would be convincing mining pools that investing in solar, wind, geothermal, etc is a good idea. Or providing an incentive to switch to renewable sources.
This means that
a) calls need to be made to your government official to make a penalty for mining pools giving off a certain carbon emission. might be hard to regulate tho since mining pools are spread throughout the country and bitcoin ensures a good amount of privacy in transactions.
b) Pressure the mining pools themselves to reduce the carbon footprint or suffer further public backlash (looking at Malaysia incident). This seems to be the current popular path.
c) Market renewable energy as more efficient than the current system.
No, no girlie, think about who you are appealing to. These are likely businessmen or redditors. Both are likely to forget that people are an asset or are likely to undervalue humans. They wont do anything until the environment affects them. Their values align with being the strongest and most affluent there is.
...I would have to think about this. These folks tend to be high risk, high reward (like my bf) And rn the high risk high reward thing is to keep mining and keep playing with climate change cuz they usually think renewable isnt as good or easy cuz its not right there yet. This is a marketing problem, isnt it. Omg Im cringing as I say it but I deadass think that time would be better spent lobbying Elon Musk about this.
1 note
·
View note
Text
C Program to implement BFS Algorithm for Connected Graph
BFS Algorithm for Connected Graph Write a C Program to implement BFS Algorithm for Connected Graph. Here’s simple Program for traversing a directed graph through Breadth First Search(BFS), visiting only those vertices that are reachable from start vertex. Breadth First Search (BFS) BFS is a traversing algorithm where you should start traversing from a selected node (source or starting node) and…
View On WordPress
#BFS#bfs algorithm example#bfs algorithm in c#Breadth First Search#breadth first search algorithm#breadth first search algorithm with example#breadth first search connected components#breadth first search connected graph#breadth first search example#breadth first search example for directed graph#breadth first search for directed graph#breadth first search for graph#breadth first search in c#breadth first search in c source code#breadth first search pseudocode#breadth first search strongly connected components#c data structures#c graph programs#connected components of a graph example#strongly connected graph example
0 notes
Text
Les nouveautés de la semaine (05/12/22)
A la une : Le masque sanitaire sous toutes ses coutures / sous la direction de Franck Cochoy, Gérald Gaglio, Anaïs Daniau
Cote de rangement : GN 419 .5 M 265723 / Domaine : Anthropologie

"En 2020, quand la Covid nous est tombée sur la tête, les masques sanitaires nous sont aussi tombés sur le nez. Cela dit, Covid et masques sont-ils indissociables ? Le masque n’a-t-il pas des origines plus anciennes ? Est-il désormais devenu un article de mode ? Le masque sanitaire standard a-t-il muté en de multiples « variants » ? Comment se saisir des masques selon qu’on les destine à des enfants, à des « premiers de corvée », à des soignants ou à des commerçants ? Le masque a-t-il été porteur de préoccupations environnementales selon qu’il est jetable ou fait maison ? Comment discours savants et profanes sur la « vérité » des masques s’articulent-ils ?
Cet ouvrage foisonnant apporte des réponses à ces questions et à bien d’autres encore. Il mobilise pour cela un riche éventail de données : archives historiques, témoignages, entretiens, articles de presse, discussions en ligne, etc.
Il est le produit d’un travail collectif de sociologues des sciences et des techniques, des marchés, de la santé et de l’action publique. Le masque sanitaire y est abordé sous toutes ses coutures afin d’explorer les nombreux enjeux qu’il a suscités, et de nous aider ainsi à mieux apprivoiser cet intrus venu soudain envahir mais aussi protéger le cours de nos vies." - Quatrième de couverture
------------------
Sociologie
Petite philosophie de la chaussette / Jean-Claude Kaufmann
Cote de rangement : GT 2128 K 265725
La fabrique du muscle / Guillaume Vallet
Cote de rangement : GV 546 .5 V 265734
La guerre des générations aura-t-elle lieu ? / Frédéric Monlouis-Félicité
Cote de rangement : HM 726 M 265724
Le soin des choses : politiques de la maintenance / Jérôme Denis, David Pontille
Cote de rangement : HM 846 D 265728
Algorithmic intimacy : the digital revolution in personal relationships / Anthony Elliott
Cote de rangement : HM 1106 E 265735
L'histoire mondiale des riches / Fabrice d'Almeida
Cote de rangement : HT 635 D 265731
------------------
Sciences politiques
A world of insecurity : democratic disenchantment in rich and poor countries / Pranab Bardhan
Cote de rangement : JC 423 B 265739
Democracy in hard places / edited by Scott Mainwaring and Tarek Masoud
Cote de rangement : JC 423 D 265742
On revolutions : unruly politics in the contemporary world / Colin J. Beck, Mlada Bukovansky, Erica Chenoweth, George Lawson, Sharon Erickson Nepstad, and Daniel P. Ritter
Cote de rangement : JC 491 B 265746
Social media, freedom of speech, and the future of our democracy / edited by Lee C. Bollinger and Geoffrey R. Stone
Cote de rangement : JC 591 B 265743
Hostile forces : how the Chinese communist party resists international pressure on human rights / Jamie J. Gruffydd-Jones
Cote de rangement : JC 599 .C6 G 265745
Russia's path to the high-Tech battlespace / Roger N. McDermott
Cote de rangement : U 43 .R9 M 265740
------------------
Communication
La guerre qu'on ne voit pas venir / Nathalie Loiseau
Cote de rangement : HV 6773 .15.C97 L 265727
------------------
Méthodologie
Explaining research : how to reach key audiences to advance your work / Dennis Meredith
Cote de rangement : Q 223 M 265741
------------------
Environnement
Sustainability : a history / Jeremy L. Caradonna
Cote de rangement : GE 195 C 265737
La condition terrestre : habiter la Terre en communs / Sophie Gosselin, David gé Bartoli
Cote de rangement : GF 41 G 265729
------------------
Informatique
Algocratie : vivre libre à l'heure des algorithmes / Arthur Grimonpont
Cote de rangement : QA 76 .9.A43 G 265732
Applied bayesian statistics / Scott M. Lynch
Cote de rangement : QA 279 .5 L 265736
------------------
Gestion
The burnout challenge : managing people's relationships with their jobs / Christina Maslach and Michael P. Leiter
Cote de rangement : BF 481 M 265738
#Nego : qu'oseriez-vous négocier si vous n'aviez pas peur ? / Eric Blondeau
Cote de rangement : BF 637 .N4 B 265730
------------------
Économie
Solving social dilemmas : ethics, politics, and prosperity / Roger D. Congleton
Cote de rangement : HB 846 .8 C 265744
------------------
Santé
Face à l'antibiorésistance : une écologie politique des microbes / Charlotte Brives
Cote de rangement : QR 177 B 265733
------------------
Philosophie
Le siècle des égarés / Julia de Funès
Cote de rangement : BD 236 D 265726
---------------------------------------
Tous ces ouvrages sont exposés sur le présentoir des nouveautés de la BSPO. Ceux-ci pourront être empruntés à domicile à partir du 19 décembre 2022.
#anthropologie#Sociologie#SciencesPolitiques#Communication#Méthodologie#Environnement#Informatique#Gestion#Economie#Santé#Philosophie
0 notes
Text
list of vertices visited. In the problem
list of vertices visited. In the problem
Write a C++ program called BFS.cpp that implements the Breadth-First Search (BFS) algorithm . Your program should read an input file name and a starting node from a user. After that, your program should display the list of vertices visited. In the problem, you can assume that the number of vertices in the input file is less than or equal to 25. [Hint: Since the maximum number of vertices is less…
View On WordPress
0 notes
Text
list of vertices visited. In the problem
list of vertices visited. In the problem
Write a C++ program called BFS.cpp that implements the Breadth-First Search (BFS) algorithm . Your program should read an input file name and a starting node from a user. After that, your program should display the list of vertices visited. In the problem, you can assume that the number of vertices in the input file is less than or equal to 25. [Hint: Since the maximum number of vertices is less…
View On WordPress
0 notes
Text
list of vertices visited. In the problem
list of vertices visited. In the problem
Write a C++ program called BFS.cpp that implements the Breadth-First Search (BFS) algorithm . Your program should read an input file name and a starting node from a user. After that, your program should display the list of vertices visited. In the problem, you can assume that the number of vertices in the input file is less than or equal to 25. [Hint: Since the maximum number of vertices is less…
View On WordPress
0 notes
Text
list of vertices visited. In the problem
list of vertices visited. In the problem
Write a C++ program called BFS.cpp that implements the Breadth-First Search (BFS) algorithm . Your program should read an input file name and a starting node from a user. After that, your program should display the list of vertices visited. In the problem, you can assume that the number of vertices in the input file is less than or equal to 25. [Hint: Since the maximum number of vertices is less…
View On WordPress
0 notes
Text
Nodebox network data

#Nodebox network data software#
#Nodebox network data license#
#Nodebox network data license#
The dagre-d3 library acts as a front-end to Dagre, providing actual rendering using D3.ĭash Cytoscape : a Component Library for Dash aimed at facilitating network visualization in Python, wrapped around Cytoscape.js.ĭracula Graph library : a JavaScript library released under the MIT License to display and layout interactive connected graphs and networks, along with various related algorithms from the field of graph theory. D3 combines visualization components and a data-driven approach to DOM manipulation.ĭagre-d3 : a JavaScript library released under the MIT License to lay out directed graphs on the client-side. It includes graph theory algorithms, from BFS to PageRank.ĭ3.JS : a JavaScript library for manipulating documents based on data using HTML, SVG, and CSS. It is used in commercial projects and open-source projects in production and designed for users first, for both front-facing app use-cases and developer use-cases. The core layout is based on a complete rewrite in JavaScript of the C++ LibCola library.Ĭytoscape.js : a graph library written in pure JS with a permissive open source license (MIT) for the core Cytoscape.js library and all first-party extensions. It works well with libraries like D3.js, svg.js, and Cytoscape.js. It visualizes data in a circular layout.Ĭola.JS : an open-source JavaScript library released under the MIT License for arranging your HTML5 documents and diagrams using constraint-based optimization techniques.
#Nodebox network data software#
It is an open source library available under GPLv3 License developed in the Helikar Lab.Ĭircos : a software package in Perl for visualizing data and information. You can use it with canvas, SVG, or even positioned HTML elements.ĬcNetViz : a lightweight JavaScript library for large network graphs visualization using WebGL. Arbor provides a force-directed layout algorithm plus abstractions for graph organization and screen refresh handling, leaving the actual screen-drawing to you. Most customization of the application takes place by overriding default configurations, rather than direct implementation via JavaScript.Īrbor.JS : a JavaScript graph visualization library released under MIT license using web workers and jQuery. The latest version of AfterGlow 1.6.5 was released on 07/08/13.Īlchemy.js : a JavaScript graph drawing application built in d3 to get up and running with graph visualization applications. It reads CSV files and converts them into a Graph. Graph visualization of the "Cosmic Web" dataset, study of the network of galaxies List of graph visualization librariesĪfterGlow : a script written in Perl that assists with the visualization of log data.

1 note
·
View note
Text
Prolog program for block world problem

Prolog is highly used in artificial intelligence(AI). LISP (another logic programming language) dominates over prolog with respect to I/O features.Ģ. Makes it easier to play with any algorithm involving lists.ġ. Doesn’t need a lot of programming effort.Ģ. The above fact, so output was 'Yes', otherwiseĮxplanation : As our knowledge base does notĬontain the above fact, so output was 'No'.ġ. Recursion : Recursion is the basis for any search in program.Įxplanation : As our knowledge base contains Backtracking : When a task fails, prolog traces backwards and tries to satisfy previous task.ģ. Unification : The basic idea is, can the given terms be made to represent the same structure.Ģ. So, a typical prolog fact goes as follows :įormat : relation(entity1, entity2. Their relation is expressed at the start and outside the parenthesis. Entities are written within the parenthesis separated by comma (, ). Facts contain entities and their relation. Prolog facts are expressed in definite pattern. So, Knowledge Base can be considered similar to database, against which we can query. We get output as affirmative if our query is already in the knowledge Base or it is implied by Knowledge Base, otherwise we get output as negative. These facts constitute the Knowledge Base of the system. Formulation or Computation is carried out by running a query over these relations. Core heart of prolog lies at the logic being applied. In prolog, logic is expressed as relations (called as Facts and Rules). Unlike many other programming languages, Prolog is intended primarily as a declarative programming language. It has important role in artificial intelligence. Differences between Procedural and Object Oriented Programming.Arrow operator -> in C/C++ with Examples.Modulo Operator (%) in C/C++ with Examples.Inorder Tree Traversal without Recursion.Tree Traversals (Inorder, Preorder and Postorder).Breadth First Search or BFS for a Graph.Unique paths covering every non-obstacle block exactly once in a grid.Print all possible paths from top left to bottom right of a mXn matrix.Count all possible paths from top left to bottom right of a mXn matrix.Count number of ways to reach destination in a Maze.The Knight’s tour problem | Backtracking-1.Warnsdorff’s algorithm for Knight’s tour problem.Printing all solutions in N-Queen Problem.Difference between Informed and Uninformed Search in AI.Understanding PEAS in Artificial Intelligence.Uniform-Cost Search (Dijkstra for large Graphs).Introduction to Hill Climbing | Artificial Intelligence.ISRO CS Syllabus for Scientist/Engineer Exam.ISRO CS Original Papers and Official Keys.GATE CS Original Papers and Official Keys.

0 notes
Text
BFS Algorithm
Breadth-First Search Algorithm
Breadth-First Search Algorithm or BFS is the most widely utilized method.
BFS is a graph traversal approach in which you start at a source node and layer by layer through the graph, analyzing the nodes directly related to the source node. Then, in BFS traversal, you must move on to the next-level neighbor nodes.
According to the BFS, you must traverse the graph in a breadthwise direction:
· To begin, move horizontally and visit all the current layer’s nodes.
· Continue to the next layer.
Breadth-First Search uses a queue data structure to store the node and mark it as “visited” until it marks all the neighboring vertices directly related to it. The queue operates on the First In First Out (FIFO) principle, so the node’s neighbors will be viewed in the order in which it inserts them in the node, starting with the node that was inserted first.
Read More
Why Do You Need Breadth-First Search Algorithm?
There are several reasons why you should use the BFS Algorithm to traverse graph data structure. The following are some of the essential features that make the BFS algorithm necessary:
· The BFS algorithm has a simple and reliable architecture.
· The BFS algorithm helps evaluate nodes in a graph and determines the shortest path to traverse nodes.
· The BFS algorithm can traverse a graph in the fewest number of iterations possible.
· The iterations in the BFS algorithm are smooth, and there is no way for this method to get stuck in an infinite loop.
· In comparison to other algorithms, the BFS algorithm’s result has a high level of accuracy.
In this tutorial, next, you will look at the pseudocode for the breadth-first search algorithm.
Pseudocode Of Breadth-First Search Algorithm
The breadth-first search algorithm’s pseudocode is:
Read More
Bredth_First_Serach( G, A ) // G ie the graph and A is the source node
Let q be the queue
q.enqueue( A ) // Inserting source node A to the queue
Mark A node as visited.
While ( q is not empty )
B = q.dequeue( ) // Removing that vertex from the queue, which will be visited by its neighbour
Processing all the neighbors of B
For all neighbors of C of B
If C is not visited, q. enqueue( C ) //Stores C in q to visit its neighbour
Mark C a visited
For a better understanding, you will look at an example of a breadth-first search algorithm later in this tutorial.
Example of Breadth-First Search Algorithm
In a tree-like structure, graph traversal requires the algorithm to visit, check, and update every single un-visited node. The sequence in which graph traversals visit the nodes on the graph categorizes them.
The BFS algorithm starts at the first starting node in a graph and travels it entirely. After traversing the first node successfully, it visits and marks the next non-traversed vertex in the graph.
Step 1: In the graph, every vertex or node is known. First, initialize a queue.
Step 2: In the graph, start from source node A and mark it as visited.
Step 3: Then you can observe B and E, which are unvisited nearby nodes from A. You have two nodes in this example, but here choose B, mark it as visited, and enqueue it alphabetically.
Step 4: Node E is the next unvisited neighboring node from A. You enqueue it after marking it as visited.
Step 5: A now has no unvisited nodes in its immediate vicinity. As a result, you dequeue and locate A.
Read More
Step 6: Node C is an unvisited neighboring node from B. You enqueue it after marking it as visited.
Step 7: Node D is an unvisited neighboring node from C. You enqueue it after marking it as visited.
Step 8: If all of D’s adjacent nodes have already been visited, remove D from the queue.
Step 9: Similarly, all nodes near E, B, and C nodes have already been visited; therefore, you must remove them from the queue.
Step 10: Because the queue is now empty, the bfs traversal has ended.
Complexity Of Breadth-First Search Algorithm
The time complexity of the breadth-first search algorithm : The time complexity of the breadth-first search algorithm can be stated as O(|V|+|E|) because, in the worst case, it will explore every vertex and edge. The number of vertices in the graph is |V|, while the edges are |E|.
The space complexity of the breadth-first search algorithm : You can define the space complexity as O(|V|), where |V| is the number of vertices in the graph, and different data structures are needed to determine which vertices have already been added to the queue. This is also the space necessary for the graph, which varies depending on the graph representation used by the algorithm’s implementation.
You will see some bfs algorithm applications now that you’ve grasped the complexity of the breadth-first search method.
Application Of Breadth-First Search Algorithm
The breadth-first search algorithm has the following applications:
· For Unweighted Graphs, You Must Use the Shortest Path and Minimum Spacing Tree.
Read More
The shortest path in an unweighted graph is the one with the fewest edges. You always reach a vertex from a given source using the fewest amount of edges when utilizing breadth-first. In unweighted graphs, any spanning tree is the Minimum Spanning Tree, and you can identify a spanning tree using either depth or breadth-first traversal.
· Peer to Peer Network
Breadth-First Search is used to discover all neighbor nodes in peer-to-peer networks like BitTorrent.
· Crawlers in Search Engine
Crawlers create indexes based on breadth-first. The goal is to start at the original page and follow all of the links there, then repeat. Crawlers can also employ Depth First Traversal. However, the benefit of breadth-first traversal is that the depth or layers of the created tree can be limited.
· Social Networking Websites
You can use a breadth-first search to identify persons within a certain distance ‘d’ from a person in social networks up to ‘d’s levels.
· GPS Navigation System
To find all nearby locations, utilize the breadth-first search method.
· Broadcasting Network
A broadcast packet in a network uses breadth-first search to reach all nodes.
· Garbage Collection
Cheney’s technique uses the breadth-first search for duplicating garbage collection. Because of the better locality of reference, breadth-first search is favored over the Depth First Search algorithm.
· Cycle Detection in Graph
Cycle detection in undirected graphs can be done using either Breadth-First Search or Depth First Search. BFS can also be used to find cycles in a directed graph.
· Identifying Routes
To see if there is a path between two vertices, you can use either Breadth-First or Depth First Traversal.
· Finding All Nodes Within One Connected Component
To locate all nodes reachable from a particular node, you can use either Breadth-First or Depth First Traversal.
Read More
Code Implementation of Breadth-First Search Algorithm
Breadth-First Search Algorithm Code Implementation:
#include<stdio.h>
#include<conio.h>
#include<stdlib.h>
int twodimarray[10][10],queue[10],visited[10],n,i,j,front=0,rear=-1;
void breadthfirstsearch(int vertex) // breadth first search function
{
for (i=1;i<=n;i++)
if(twodimarray[vertex][i] && !visited[i])
queue[++rear]=i;
if(front<=rear)
{
visited[queue[front]]=1;
breadthfirstsearch(queue[front++]);
}
}
int main() {
int x;
printf(“\n Enter the number of vertices:”);
scanf(“%d”,&n);
for (i=1;i<=n;i++) {
queue[i]=0;
visited[i]=0;
}
printf(“\n Enter graph value in form of matrix:\n”);
for (i=1;i<=n;i++)
for (j=1;j<=n;j++)
scanf(“%d”,&twodimarray[i][j]);
printf(“\n Enter the source node:”);
scanf(“%d”,&x);
breadthfirstsearch(x);
printf(“\n The nodes which are reachable are:\n”);
for (i=1;i<=n;i++)
if(visited[i])
printf(“%d\t”,i);
else
printf(“\n Breadth first search is not possible”);
getch();
}
1 note
·
View note