#circular queue operations in data structure
Explore tagged Tumblr posts
Text
DSA Channel: The Ultimate Destination for Learning Data Structures and Algorithms from Basics to Advanced
DSA mastery stands vital for successful software development and competitive programming in the current digital world that operates at high speeds. People at every skill level from beginner to advanced developer will find their educational destination at the DSA Channel.
Why is DSA Important?
Software development relies on data structures together with algorithms as its essential core components. Code optimization emerges from data structures and algorithms which produces better performance and leads to successful solutions of complex problems. Strategic knowledge of DSA serves essential needs for handling job interviews and coding competitions while enhancing logical thinking abilities. Proper guidance makes basic concepts of DSA both rewarding and enjoyable to study.
What Makes DSA Channel Unique?
The DSA Channel exists to simplify both data structures along algorithms and make them accessible to all users. Here’s why it stands out:
The channel provides step-by-step learning progress which conservatively begins by teaching arrays and linked lists and continues to dynamic programming and graph theory.
Each theoretical concept gets backed through coding examples practically to facilitate easier understanding and application in real-life situations.
Major companies like Google, Microsoft, and Amazon utilize DSA knowledge as part of their job recruiter process. Through their DSA Channel service candidates can perform mock interview preparation along with receiving technical interview problem-solving advice and interview cracking techniques.
Updates Occur Regularly Because the DSA Channel Matches the Ongoing Transformation in the Technology Industry. The content uses current algorithm field trends and new elements for constant updates.
DSAC channels will be covering the below key topics
DSA Channel makes certain you have clear ideas that are necessary for everything from the basics of data structures to the most sophisticated methods and use cases. Highlights :
1. Introduction Basic Data Structures
Fundamentals First, You Always Need To Start With the Basics. Some of the DSA Channel topics are:
Memories storing and manipulating elements of Arrays
Linked Lists — learn linked lists: Singly Linked lists Dually linked lists and Circular linked list
Implementing Stacks and Queues — linear data structure with these implementations.
Hash Table: Understanding Hashing and its impact in the retrieval of Data.
2. Advanced Data Structures
If you want to get Intense: the DSA channel has profound lessons:
Graph bases Types- Type of Graph Traversals: BFS, DFS
Heaps — Come to know about Min Heap and Max Heap
Index Tries – How to store and retrieve a string faster than the fastest possible.
3. Algorithms
This is especially true for efficient problem-solving. The DSA Channel discusses in-depth:
Searching Algorithms Binary Search and Linear Search etc.
Dynamic Programming: Optimization of subproblems
Recursion and Backtracking: How to solve a problem by recursion.
Graph Algorithms — Dijkstra, Bellman-Ford and Floyd-Warshall etc
4. Applications of DSA in Real life
So one of the unique things (About the DSA channel) is these real-world applications of his DSA Channel.
Instead of just teaching Theory the channel gives a hands-on to see how it's used in world DSA applications.
Learning about Database Management Systems — Indexing, Query Optimization, Storage Techniques
Operating Systems – study algorithms scheduling, memory management,t, and file systems.
Machine Learning and AI — Learning the usage of algorithms in training models, and optimizing computations.
Finance and Banking — data structures that help us in identifying risk scheme things, fraud detection, transaction processing, etc.
This hands-on approach to working out will ensure that learners not only know how to use these concepts in real-life examples.
How Arena Fincorp Benefits from DSA?
Arena Fincorp, a leading financial services provider, understands the importance of efficiency and optimization in the fintech sector. The financial solutions offered through Arena Fincorp operate under the same principles as data structures and algorithms which enhance coding operations. Arena Fincorp guarantees perfect financial transactions and data protection through its implementation of sophisticated algorithms. The foundational principles of DSA enable developers to build strong financial technological solutions for contemporary financial complications.
How to Get Started with DSA Channel?
New users of the DSA Channel should follow these instructions to maximize their experience:
The educational process should start with fundamental videos explaining arrays together with linked lists and stacks to establish a basic knowledge base.
The practice of DSA needs regular exercise and time to build comprehension. Devote specific time each day to find solutions for problems.
The platforms LeetCode, CodeChef, and HackerRank provide various DSA problems for daily problem-solving which boosts your skills.
Join community discussions where you can help learners by sharing solutions as well as working with fellow participants.
Students should do Mock Interviews through the DSA Channel to enhance their self-confidence and gain experience in actual interview situations.
The process of learning becomes more successful when people study together in a community. Through the DSA Channel students find an energetic learning community to share knowledge about doubts and project work and they exchange insight among themselves.
Conclusion
Using either data structures or algorithms in tech requires mastery so they have become mandatory in this sector. The DSA Channel delivers the best learning gateway that suits students as well as professionals and competitive programmers. Through their well-organized educational approach, practical experience and active learner network the DSA Channel builds a deep understanding of DSA with effective problem-solving abilities.
The value of data structures and algorithms and their optimized algorithms and efficient coding practices allows companies such as Arena Fincorp to succeed in their industries. New learners should begin their educational journey right now with the DSA Channel to master data structures and algorithms expertise.
0 notes
Text
Essential Algorithms and Data Structures for Competitive Programming
Competitive programming is a thrilling and intellectually stimulating field that challenges participants to solve complex problems efficiently and effectively. At its core, competitive programming revolves around algorithms and data structures—tools that help you tackle problems with precision and speed. If you're preparing for a competitive programming contest or just want to enhance your problem-solving skills, understanding essential algorithms and data structures is crucial. In this blog, we’ll walk through some of the most important ones you should be familiar with.
1. Arrays and Strings
Arrays are fundamental data structures that store elements in a contiguous block of memory. They allow for efficient access to elements via indexing and are often the first data structure you encounter in competitive programming.
Operations: Basic operations include traversal, insertion, deletion, and searching. Understanding how to manipulate arrays efficiently can help solve a wide range of problems.
Strings are arrays of characters and are often used to solve problems involving text processing. Basic string operations like concatenation, substring search, and pattern matching are essential.
2. Linked Lists
A linked list is a data structure where elements (nodes) are stored in separate memory locations and linked together using pointers. There are several types of linked lists:
Singly Linked List: Each node points to the next node.
Doubly Linked List: Each node points to both the next and previous nodes.
Circular Linked List: The last node points back to the first node.
Linked lists are useful when you need to frequently insert or delete elements as they allow for efficient manipulation of the data.
3. Stacks and Queues
Stacks and queues are abstract data types that operate on a last-in-first-out (LIFO) and first-in-first-out (FIFO) principle, respectively.
Stacks: Useful for problems involving backtracking or nested structures (e.g., parsing expressions).
Queues: Useful for problems involving scheduling or buffering (e.g., breadth-first search).
Both can be implemented using arrays or linked lists and are foundational for many algorithms.
4. Hashing
Hashing involves using a hash function to convert keys into indices in a hash table. This allows for efficient data retrieval and insertion.
Hash Tables: Hash tables provide average-case constant time complexity for search, insert, and delete operations.
Collisions: Handling collisions (when two keys hash to the same index) using techniques like chaining or open addressing is crucial for effective hashing.
5. Trees
Trees are hierarchical data structures with a root node and child nodes. They are used to represent hierarchical relationships and are key to many algorithms.
Binary Trees: Each node has at most two children. They are used in various applications such as binary search trees (BSTs), where the left child is less than the parent, and the right child is greater.
Binary Search Trees (BSTs): Useful for dynamic sets where elements need to be ordered. Operations like insertion, deletion, and search have an average-case time complexity of O(log n).
Balanced Trees: Trees like AVL trees and Red-Black trees maintain balance to ensure O(log n) time complexity for operations.
6. Heaps
A heap is a specialized tree-based data structure that satisfies the heap property:
Max-Heap: The value of each node is greater than or equal to the values of its children.
Min-Heap: The value of each node is less than or equal to the values of its children.
Heaps are used in algorithms like heap sort and are also crucial for implementing priority queues.
7. Graphs
Graphs represent relationships between entities using nodes (vertices) and edges. They are essential for solving problems involving networks, paths, and connectivity.
Graph Traversal: Algorithms like Breadth-First Search (BFS) and Depth-First Search (DFS) are used to explore nodes and edges in graphs.
Shortest Path: Algorithms such as Dijkstra’s and Floyd-Warshall help find the shortest path between nodes.
Minimum Spanning Tree: Algorithms like Kruskal’s and Prim’s are used to find the minimum spanning tree in a graph.
8. Dynamic Programming
Dynamic Programming (DP) is a method for solving problems by breaking them down into simpler subproblems and storing the results of these subproblems to avoid redundant computations.
Memoization: Storing results of subproblems to avoid recomputation.
Tabulation: Building a table of results iteratively, bottom-up.
DP is especially useful for optimization problems, such as finding the shortest path, longest common subsequence, or knapsack problem.
9. Greedy Algorithms
Greedy Algorithms make a series of choices, each of which looks best at the moment, with the hope that these local choices will lead to a global optimum.
Applications: Commonly used for problems like activity selection, Huffman coding, and coin change.
10. Graph Algorithms
Understanding graph algorithms is crucial for competitive programming:
Shortest Path Algorithms: Dijkstra’s Algorithm, Bellman-Ford Algorithm.
Minimum Spanning Tree Algorithms: Kruskal’s Algorithm, Prim’s Algorithm.
Network Flow Algorithms: Ford-Fulkerson Algorithm, Edmonds-Karp Algorithm.
Preparing for Competitive Programming: Summer Internship Program
If you're eager to dive deeper into these algorithms and data structures, participating in a summer internship program focused on Data Structures and Algorithms (DSA) can be incredibly beneficial. At our Summer Internship Program, we provide hands-on experience and mentorship to help you master these crucial skills. This program is designed for aspiring programmers who want to enhance their competitive programming abilities and prepare for real-world challenges.
What to Expect:
Hands-On Projects: Work on real-world problems and implement algorithms and data structures.
Mentorship: Receive guidance from experienced professionals in the field.
Workshops and Seminars: Participate in workshops that cover advanced topics and techniques.
Networking Opportunities: Connect with peers and industry experts to expand your professional network.
By participating in our DSA Internship, you’ll gain practical experience and insights that will significantly boost your competitive programming skills and prepare you for success in contests and future career opportunities.
In conclusion, mastering essential algorithms and data structures is key to excelling in competitive programming. By understanding and practicing these concepts, you can tackle complex problems with confidence and efficiency. Whether you’re just starting out or looking to sharpen your skills, focusing on these fundamentals will set you on the path to success.
Ready to take your skills to the next level? Join our Summer Internship Program and dive into the world of algorithms and data structures with expert guidance and hands-on experience. Your journey to becoming a competitive programming expert starts here!
0 notes
Text
How to Ace Your DSA Interview, Even If You're a Newbie
Are you aiming to crack DSA interviews and land your dream job as a software engineer or developer? Look no further! This comprehensive guide will provide you with all the necessary tips and insights to ace your DSA interviews. We'll explore the important DSA topics to study, share valuable preparation tips, and even introduce you to Tutort Academy DSA courses to help you get started on your journey. So let's dive in!

Why is DSA Important?
Before we delve into the specifics of DSA interviews, let's first understand why data structures and algorithms are crucial for software development. DSA plays a vital role in optimizing software components, enabling efficient data storage and processing.
From logging into your Facebook account to finding the shortest route on Google Maps, DSA is at work in various applications we use every day. Mastering DSA allows you to solve complex problems, optimize code performance, and design efficient software systems.
Important DSA Topics to Study
To excel in DSA interviews, it's essential to have a strong foundation in key topics. Here are some important DSA topics you should study:
1. Arrays and Strings
Arrays and strings are fundamental data structures in programming. Understanding array manipulation, string operations, and common algorithms like sorting and searching is crucial for solving coding problems.
2. Linked Lists
Linked lists are linear data structures that consist of nodes linked together. It's important to understand concepts like singly linked lists, doubly linked lists, and circular linked lists, as well as operations like insertion, deletion, and traversal.
3. Stacks and Queues
Stacks and queues are abstract data types that follow specific orderings. Mastering concepts like LIFO (Last In, First Out) for stacks and FIFO (First In, First Out) for queues is essential. Additionally, learn about their applications in real-life scenarios.
4. Trees and Binary Trees
Trees are hierarchical data structures with nodes connected by edges. Understanding binary trees, binary search trees, and traversal algorithms like preorder, inorder, and postorder is crucial. Additionally, explore advanced concepts like AVL trees and red-black trees.
5. Graphs
Graphs are non-linear data structures consisting of nodes (vertices) and edges. Familiarize yourself with graph representations, traversal algorithms like BFS (Breadth-First Search) and DFS (Depth-First Search), and graph algorithms such as Dijkstra's algorithm and Kruskal's algorithm.
6. Sorting and Searching Algorithms
Understanding various sorting algorithms like bubble sort, selection sort, insertion sort, merge sort, and quicksort is essential. Additionally, familiarize yourself with searching algorithms like linear search, binary search, and hash-based searching.
7. Dynamic Programming
Dynamic programming involves breaking down a complex problem into smaller overlapping subproblems and solving them individually. Mastering this technique allows you to solve optimization problems efficiently.
These are just a few of the important DSA topics to study. It's crucial to have a solid understanding of these concepts and their applications to perform well in DSA interviews.
Tips to Follow While Preparing for DSA Interviews
Preparing for DSA interviews can be challenging, but with the right approach, you can maximize your chances of success. Here are some tips to keep in mind:
1. Understand the Fundamentals
Before diving into complex algorithms, ensure you have a strong grasp of the fundamentals. Familiarize yourself with basic data structures, common algorithms, and time and space complexities.
2. Practice Regularly
Consistent practice is key to mastering DSA. Solve a wide range of coding problems, participate in coding challenges, and implement algorithms from scratch. Leverage online coding platforms like LeetCode, HackerRank to practice and improve your problem-solving skills.
3. Analyze and Optimize
After solving a problem, analyze your solution and look for areas of improvement. Optimize your code for better time and space complexities. This demonstrates your ability to write efficient and scalable code.
4. Collaborate and Learn from Others
Engage with the coding community, join study groups, and participate in online forums. Collaborating with others allows you to learn different approaches, gain insights, and improve your problem-solving skills.
5. Mock Interviews and Feedback
Simulate real interview scenarios by participating in mock interviews. Seek feedback from experienced professionals or mentors who can provide valuable insights into your strengths and areas for improvement.
Following these tips will help you build a solid foundation in DSA and boost your confidence for interviews.
Conclusion
Mastering DSA is crucial for acing coding interviews and securing your dream job as a software engineer or developer. By studying important DSA topics, following effective preparation tips, and leveraging Tutort Academy's DSA courses, you'll be well-equipped to tackle DSA interviews with confidence. Remember to practice regularly, seek feedback, and stay curious.
Good luck on your DSA journey!
#programming#tutortacademy#tutort#DSA#data structures#data structures and algorithms#algorithm#interview preparation#interview tips
0 notes
Link
Data Structures and Algorithms from Zero to Hero and Crack Top Companies 100+ Interview questions (Java Coding)
What you’ll learn
Java Data Structures and Algorithms Masterclass
Learn, implement, and use different Data Structures
Learn, implement and use different Algorithms
Become a better developer by mastering computer science fundamentals
Learn everything you need to ace difficult coding interviews
Cracking the Coding Interview with 100+ questions with explanations
Time and Space Complexity of Data Structures and Algorithms
Recursion
Big O
Dynamic Programming
Divide and Conquer Algorithms
Graph Algorithms
Greedy Algorithms
Requirements
Basic Java Programming skills
Description
Welcome to the Java Data Structures and Algorithms Masterclass, the most modern, and the most complete Data Structures and Algorithms in Java course on the internet.
At 44+ hours, this is the most comprehensive course online to help you ace your coding interviews and learn about Data Structures and Algorithms in Java. You will see 100+ Interview Questions done at the top technology companies such as Apple, Amazon, Google, and Microsoft and how-to face Interviews with comprehensive visual explanatory video materials which will bring you closer to landing the tech job of your dreams!
Learning Java is one of the fastest ways to improve your career prospects as it is one of the most in-demand tech skills! This course will help you in better understanding every detail of Data Structures and how algorithms are implemented in high-level programming languages.
We’ll take you step-by-step through engaging video tutorials and teach you everything you need to succeed as a professional programmer.
After finishing this course, you will be able to:
Learn basic algorithmic techniques such as greedy algorithms, binary search, sorting, and dynamic programming to solve programming challenges.
Learn the strengths and weaknesses of a variety of data structures, so you can choose the best data structure for your data and applications
Learn many of the algorithms commonly used to sort data, so your applications will perform efficiently when sorting large datasets
Learn how to apply graph and string algorithms to solve real-world challenges: finding shortest paths on huge maps and assembling genomes from millions of pieces.
Why this course is so special and different from any other resource available online?
This course will take you from the very beginning to very complex and advanced topics in understanding Data Structures and Algorithms!
You will get video lectures explaining concepts clearly with comprehensive visual explanations throughout the course.
You will also see Interview Questions done at the top technology companies such as Apple, Amazon, Google, and Microsoft.
I cover everything you need to know about the technical interview process!
So whether you are interested in learning the top programming language in the world in-depth and interested in learning the fundamental Algorithms, Data Structures, and performance analysis that make up the core foundational skillset of every accomplished programmer/designer or software architect and is excited to ace your next technical interview this is the course for you!
And this is what you get by signing up today:
Lifetime access to 44+ hours of HD quality videos. No monthly subscription. Learn at your own pace, whenever you want
Friendly and fast support in the course Q&A whenever you have questions or get stuck
FULL money-back guarantee for 30 days!
This course is designed to help you to achieve your career goals. Whether you are looking to get more into Data Structures and Algorithms, increase your earning potential, or just want a job with more freedom, this is the right course for you!
The topics that are covered in this course.
Section 1 – Introduction
What are Data Structures?
What is an algorithm?
Why are Data Structures And Algorithms important?
Types of Data Structures
Types of Algorithms
Section 2 – Recursion
What is Recursion?
Why do we need recursion?
How does Recursion work?
Recursive vs Iterative Solutions
When to use/avoid Recursion?
How to write Recursion in 3 steps?
How to find Fibonacci numbers using Recursion?
Section 3 – Cracking Recursion Interview Questions
Question 1 – Sum of Digits
Question 2 – Power
Question 3 – Greatest Common Divisor
Question 4 – Decimal To Binary
Section 4 – Bonus CHALLENGING Recursion Problems (Exercises)
power
factorial
products array
recursiveRange
fib
reverse
palindrome
some recursive
flatten
capitalize first
nestedEvenSum
capitalize words
stringifyNumbers
collects things
Section 5 – Big O Notation
Analogy and Time Complexity
Big O, Big Theta, and Big Omega
Time complexity examples
Space Complexity
Drop the Constants and the nondominant terms
Add vs Multiply
How to measure the codes using Big O?
How to find time complexity for Recursive calls?
How to measure Recursive Algorithms that make multiple calls?
Section 6 – Top 10 Big O Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Product and Sum
Print Pairs
Print Unordered Pairs
Print Unordered Pairs 2 Arrays
Print Unordered Pairs 2 Arrays 100000 Units
Reverse
O(N) Equivalents
Factorial Complexity
Fibonacci Complexity
Powers of 2
Section 7 – Arrays
What is an Array?
Types of Array
Arrays in Memory
Create an Array
Insertion Operation
Traversal Operation
Accessing an element of Array
Searching for an element in Array
Deleting an element from Array
Time and Space complexity of One Dimensional Array
One Dimensional Array Practice
Create Two Dimensional Array
Insertion – Two Dimensional Array
Accessing an element of Two Dimensional Array
Traversal – Two Dimensional Array
Searching for an element in Two Dimensional Array
Deletion – Two Dimensional Array
Time and Space complexity of Two Dimensional Array
When to use/avoid array
Section 8 – Cracking Array Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Question 1 – Missing Number
Question 2 – Pairs
Question 3 – Finding a number in an Array
Question 4 – Max product of two int
Question 5 – Is Unique
Question 6 – Permutation
Question 7 – Rotate Matrix
Section 9 – CHALLENGING Array Problems (Exercises)
Middle Function
2D Lists
Best Score
Missing Number
Duplicate Number
Pairs
Section 10 – Linked List
What is a Linked List?
Linked List vs Arrays
Types of Linked List
Linked List in the Memory
Creation of Singly Linked List
Insertion in Singly Linked List in Memory
Insertion in Singly Linked List Algorithm
Insertion Method in Singly Linked List
Traversal of Singly Linked List
Search for a value in Single Linked List
Deletion of a node from Singly Linked List
Deletion Method in Singly Linked List
Deletion of entire Singly Linked List
Time and Space Complexity of Singly Linked List
Section 11 – Circular Singly Linked List
Creation of Circular Singly Linked List
Insertion in Circular Singly Linked List
Insertion Algorithm in Circular Singly Linked List
Insertion method in Circular Singly Linked List
Traversal of Circular Singly Linked List
Searching a node in Circular Singly Linked List
Deletion of a node from Circular Singly Linked List
Deletion Algorithm in Circular Singly Linked List
A method in Circular Singly Linked List
Deletion of entire Circular Singly Linked List
Time and Space Complexity of Circular Singly Linked List
Section 12 – Doubly Linked List
Creation of Doubly Linked List
Insertion in Doubly Linked List
Insertion Algorithm in Doubly Linked List
Insertion Method in Doubly Linked List
Traversal of Doubly Linked List
Reverse Traversal of Doubly Linked List
Searching for a node in Doubly Linked List
Deletion of a node in Doubly Linked List
Deletion Algorithm in Doubly Linked List
Deletion Method in Doubly Linked List
Deletion of entire Doubly Linked List
Time and Space Complexity of Doubly Linked List
Section 13 – Circular Doubly Linked List
Creation of Circular Doubly Linked List
Insertion in Circular Doubly Linked List
Insertion Algorithm in Circular Doubly Linked List
Insertion Method in Circular Doubly Linked List
Traversal of Circular Doubly Linked List
Reverse Traversal of Circular Doubly Linked List
Search for a node in Circular Doubly Linked List
Delete a node from Circular Doubly Linked List
Deletion Algorithm in Circular Doubly Linked List
Deletion Method in Circular Doubly Linked List
Entire Circular Doubly Linked List
Time and Space Complexity of Circular Doubly Linked List
Time Complexity of Linked List vs Arrays
Section 14 – Cracking Linked List Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Linked List Class
Question 1 – Remove Dups
Question 2 – Return Kth to Last
Question 3 – Partition
Question 4 – Sum Linked Lists
Question 5 – Intersection
Section 15 – Stack
What is a Stack?
What and Why of Stack?
Stack Operations
Stack using Array vs Linked List
Stack Operations using Array (Create, isEmpty, isFull)
Stack Operations using Array (Push, Pop, Peek, Delete)
Time and Space Complexity of Stack using Array
Stack Operations using Linked List
Stack methods – Push, Pop, Peek, Delete, and isEmpty using Linked List
Time and Space Complexity of Stack using Linked List
When to Use/Avoid Stack
Stack Quiz
Section 16 – Queue
What is a Queue?
Linear Queue Operations using Array
Create, isFull, isEmpty, and enQueue methods using Linear Queue Array
Dequeue, Peek and Delete Methods using Linear Queue Array
Time and Space Complexity of Linear Queue using Array
Why Circular Queue?
Circular Queue Operations using Array
Create, Enqueue, isFull and isEmpty Methods in Circular Queue using Array
Dequeue, Peek and Delete Methods in Circular Queue using Array
Time and Space Complexity of Circular Queue using Array
Queue Operations using Linked List
Create, Enqueue and isEmpty Methods in Queue using Linked List
Dequeue, Peek and Delete Methods in Queue using Linked List
Time and Space Complexity of Queue using Linked List
Array vs Linked List Implementation
When to Use/Avoid Queue?
Section 17 – Cracking Stack and Queue Interview Questions (Amazon, Facebook, Apple, Microsoft)
Question 1 – Three in One
Question 2 – Stack Minimum
Question 3 – Stack of Plates
Question 4 – Queue via Stacks
Question 5 – Animal Shelter
Section 18 – Tree / Binary Tree
What is a Tree?
Why Tree?
Tree Terminology
How to create a basic tree in Java?
Binary Tree
Types of Binary Tree
Binary Tree Representation
Create Binary Tree (Linked List)
PreOrder Traversal Binary Tree (Linked List)
InOrder Traversal Binary Tree (Linked List)
PostOrder Traversal Binary Tree (Linked List)
LevelOrder Traversal Binary Tree (Linked List)
Searching for a node in Binary Tree (Linked List)
Inserting a node in Binary Tree (Linked List)
Delete a node from Binary Tree (Linked List)
Delete entire Binary Tree (Linked List)
Create Binary Tree (Array)
Insert a value Binary Tree (Array)
Search for a node in Binary Tree (Array)
PreOrder Traversal Binary Tree (Array)
InOrder Traversal Binary Tree (Array)
PostOrder Traversal Binary Tree (Array)
Level Order Traversal Binary Tree (Array)
Delete a node from Binary Tree (Array)
Entire Binary Tree (Array)
Linked List vs Python List Binary Tree
Section 19 – Binary Search Tree
What is a Binary Search Tree? Why do we need it?
Create a Binary Search Tree
Insert a node to BST
Traverse BST
Search in BST
Delete a node from BST
Delete entire BST
Time and Space complexity of BST
Section 20 – AVL Tree
What is an AVL Tree?
Why AVL Tree?
Common Operations on AVL Trees
Insert a node in AVL (Left Left Condition)
Insert a node in AVL (Left-Right Condition)
Insert a node in AVL (Right Right Condition)
Insert a node in AVL (Right Left Condition)
Insert a node in AVL (all together)
Insert a node in AVL (method)
Delete a node from AVL (LL, LR, RR, RL)
Delete a node from AVL (all together)
Delete a node from AVL (method)
Delete entire AVL
Time and Space complexity of AVL Tree
Section 21 – Binary Heap
What is Binary Heap? Why do we need it?
Common operations (Creation, Peek, sizeofheap) on Binary Heap
Insert a node in Binary Heap
Extract a node from Binary Heap
Delete entire Binary Heap
Time and space complexity of Binary Heap
Section 22 – Trie
What is a Trie? Why do we need it?
Common Operations on Trie (Creation)
Insert a string in Trie
Search for a string in Trie
Delete a string from Trie
Practical use of Trie
Section 23 – Hashing
What is Hashing? Why do we need it?
Hashing Terminology
Hash Functions
Types of Collision Resolution Techniques
Hash Table is Full
Pros and Cons of Resolution Techniques
Practical Use of Hashing
Hashing vs Other Data structures
Section 24 – Sort Algorithms
What is Sorting?
Types of Sorting
Sorting Terminologies
Bubble Sort
Selection Sort
Insertion Sort
Bucket Sort
Merge Sort
Quick Sort
Heap Sort
Comparison of Sorting Algorithms
Section 25 – Searching Algorithms
Introduction to Searching Algorithms
Linear Search
Linear Search in Python
Binary Search
Binary Search in Python
Time Complexity of Binary Search
Section 26 – Graph Algorithms
What is a Graph? Why Graph?
Graph Terminology
Types of Graph
Graph Representation
The graph in Java using Adjacency Matrix
The graph in Java using Adjacency List
Section 27 – Graph Traversal
Breadth-First Search Algorithm (BFS)
Breadth-First Search Algorithm (BFS) in Java – Adjacency Matrix
Breadth-First Search Algorithm (BFS) in Java – Adjacency List
Time Complexity of Breadth-First Search (BFS) Algorithm
Depth First Search (DFS) Algorithm
Depth First Search (DFS) Algorithm in Java – Adjacency List
Depth First Search (DFS) Algorithm in Java – Adjacency Matrix
Time Complexity of Depth First Search (DFS) Algorithm
BFS Traversal vs DFS Traversal
Section 28 – Topological Sort
What is Topological Sort?
Topological Sort Algorithm
Topological Sort using Adjacency List
Topological Sort using Adjacency Matrix
Time and Space Complexity of Topological Sort
Section 29 – Single Source Shortest Path Problem
what is Single Source Shortest Path Problem?
Breadth-First Search (BFS) for Single Source Shortest Path Problem (SSSPP)
BFS for SSSPP in Java using Adjacency List
BFS for SSSPP in Java using Adjacency Matrix
Time and Space Complexity of BFS for SSSPP
Why does BFS not work with Weighted Graph?
Why does DFS not work for SSSP?
Section 30 – Dijkstra’s Algorithm
Dijkstra’s Algorithm for SSSPP
Dijkstra’s Algorithm in Java – 1
Dijkstra’s Algorithm in Java – 2
Dijkstra’s Algorithm with Negative Cycle
Section 31 – Bellman-Ford Algorithm
Bellman-Ford Algorithm
Bellman-Ford Algorithm with negative cycle
Why does Bellman-Ford run V-1 times?
Bellman-Ford in Python
BFS vs Dijkstra vs Bellman Ford
Section 32 – All Pairs Shortest Path Problem
All pairs shortest path problem
Dry run for All pair shortest path
Section 33 – Floyd Warshall
Floyd Warshall Algorithm
Why Floyd Warshall?
Floyd Warshall with negative cycle,
Floyd Warshall in Java,
BFS vs Dijkstra vs Bellman Ford vs Floyd Warshall,
Section 34 – Minimum Spanning Tree
Minimum Spanning Tree,
Disjoint Set,
Disjoint Set in Java,
Section 35 – Kruskal’s and Prim’s Algorithms
Kruskal Algorithm,
Kruskal Algorithm in Python,
Prim’s Algorithm,
Prim’s Algorithm in Python,
Prim’s vs Kruskal
Section 36 – Cracking Graph and Tree Interview Questions (Amazon, Facebook, Apple, Microsoft)
Section 37 – Greedy Algorithms
What is a Greedy Algorithm?
Well known Greedy Algorithms
Activity Selection Problem
Activity Selection Problem in Python
Coin Change Problem
Coin Change Problem in Python
Fractional Knapsack Problem
Fractional Knapsack Problem in Python
Section 38 – Divide and Conquer Algorithms
What is a Divide and Conquer Algorithm?
Common Divide and Conquer algorithms
How to solve the Fibonacci series using the Divide and Conquer approach?
Number Factor
Number Factor in Java
House Robber
House Robber Problem in Java
Convert one string to another
Convert One String to another in Java
Zero One Knapsack problem
Zero One Knapsack problem in Java
Longest Common Sequence Problem
Longest Common Subsequence in Java
Longest Palindromic Subsequence Problem
Longest Palindromic Subsequence in Java
Minimum cost to reach the Last cell problem
Minimum Cost to reach the Last Cell in 2D array using Java
Number of Ways to reach the Last Cell with given Cost
Number of Ways to reach the Last Cell with given Cost in Java
Section 39 – Dynamic Programming
What is Dynamic Programming? (Overlapping property)
Where does the name of DC come from?
Top-Down with Memoization
Bottom-Up with Tabulation
Top-Down vs Bottom Up
Is Merge Sort Dynamic Programming?
Number Factor Problem using Dynamic Programming
Number Factor: Top-Down and Bottom-Up
House Robber Problem using Dynamic Programming
House Robber: Top-Down and Bottom-Up
Convert one string to another using Dynamic Programming
Convert String using Bottom Up
Zero One Knapsack using Dynamic Programming
Zero One Knapsack – Top Down
Zero One Knapsack – Bottom Up
Section 40 – CHALLENGING Dynamic Programming Problems
Longest repeated Subsequence Length problem
Longest Common Subsequence Length problem
Longest Common Subsequence problem
Diff Utility
Shortest Common Subsequence problem
Length of Longest Palindromic Subsequence
Subset Sum Problem
Egg Dropping Puzzle
Maximum Length Chain of Pairs
Section 41 – A Recipe for Problem Solving
Introduction
Step 1 – Understand the problem
Step 2 – Examples
Step 3 – Break it Down
Step 4 – Solve or Simplify
Step 5 – Look Back and Refactor
Section 41 – Wild West
Download
To download more paid courses for free visit course catalog where 1000+ paid courses available for free. You can get the full course into your device with just a single click. Follow the link above to download this course for free.
3 notes
·
View notes
Text
C Program to implement circular queue using arrays
Circular queue using arrays Write a C Program to implement circular queue using arrays. Here’s simple Program to implement circular queue using arrays in C Programming Language. What is Queue ? Queue is also an abstract data type or a linear data structure, in which the first element is inserted from one end called REAR, and the deletion of existing element takes place from the other end called…
View On WordPress
#c data structures#c queue programs#circular queue implementation in c using array algorithm#circular queue in c#circular queue in c using array#circular queue operations in data structure#implement circular queue using array in c#implementation of circular queue in c using array#program to implement circular queue using array in c
0 notes
Text
CSE Project #2 Operating Systems Solution
CSE Project #2 Operating Systems Solution
Part 1: (This part of the project is not graded.) Overview: For this project you are to write routines that perform standard queuing functions. The functions work on multiple queues, and structure each queue as a doubly linked, circular list. Data Structures: A queue consists of a head-pointer and a set of q-elements. A q-element is a structure, consisting of a prev and next pointer, and a…

View On WordPress
0 notes
Text
CSE Project #2 Operating Systems Solution
CSE Project #2 Operating Systems Solution
Part 1: (This part of the project is not graded.) Overview: For this project you are to write routines that perform standard queuing functions. The functions work on multiple queues, and structure each queue as a doubly linked, circular list. Data Structures: A queue consists of a head-pointer and a set of q-elements. A q-element is a structure, consisting of a prev and next pointer, and a…

View On WordPress
0 notes
Text
What are Circular Queue in Data Structures?
A Circular Queue is a type of Queue in which operations like insertion and deletion are performed on the basis of First In First Out principle.

NOTE : In, the memory there is nothing like a circular array, its just visual representation to make the programmers understand the concept easily. In the code also, we will be using linear array only. Why Circular Queues? In a linear queue there was a problem that when we delete ...........
To read more about circular queues refer to this link .
0 notes
Text
Tencent details how its MOBA-playing AI system beats 99.81% of human opponents
In August, Tencent announced it had developed an AI system capable of defeating teams of pros in a five-on-five match in Honor of Kings (or Arena of Valor, depending on the region). This was a noteworthy achievement — Honor of Kings occupies the video game subgenre known as multiplayer online battle arena games (MOBAs), which are incomplete information games in the sense that players are unaware of the actions chosen by other players. The endgame, then, isn’t merely Honor of Kings AI that achieves superhero performance, but insights that might be used to develop systems capable of solving some of society’s toughest challenges.
A paper published this week peels back the layers of Tencent’s technique, with the coauthors describe as “highly scalable.” They claim its novel strategies enable it to explore the game map “efficiently,” with an actor-critic architecture that self-improves trains over time.
As the researchers point out, real-time strategy games like Honor of Kings require highly complex action control compared with traditional board games and Atari games. Their environments also tend to be more complicated (Honor of Kings has 10^600 possible states and and 10^18000 possible actions) and the objectives more complex on the whole. Agent must not only learn to plan, attack, and defend but also to control skill combos, induce, and deceive opponents, all while contending with hazards like creeps and fully automated turrets.
Tencent’s architecture consists of four modules: a Reinforcement Learning Learning (RL) Learner, an Artificial Intelligence (AI) Server, a Dispatch Module, and a Memory Pool.
The AI Server — which runs on a single processor core, thanks to some clever compression — dictates how the AI model interacts with objects in the game environment. It generates episodes via self-play, and based on the features it extracts from the game state, the ut predicts players’ actions and forwards them to the game core for execution. The game core then returns the next state and the corresponding reward value, or the value that spurs the model toward certain Honor of Kings goals.
As for the Dispatch Module, it’s bundled with several AI Servers on the same machine, and it collects data samples consisting of rewards, features, action probabilities, and more before compressing and sending them to Memory Pools. The Memory Pool — which is also a server — supports samples of various lengths and data sampling based on the generated time, and it implements a circular queue structure that performs storage operations in a data-efficient fashion.
Lastly, the Reinforcement Learner — a distributed training environment — accelerates policy updates with the aforementioned actor-critic approach. Multiple Reinforcement Learners fetch data in parallel from Memory Pools, with which they communicate using shared memory. One mechanism (target attention) helps with enemy target selection, while another — long short-term memory (LSTM), an algorithm capable of learning long-term dependencies — teaches hero players skill combos critical to inflicting “severe” damage.
The Tencent researchers’ system encodes image features and game state information such that each unit and enemy target is represented numerically. An action mask cleverly incorporates prior knowledge of experienced human players, preventing the AI from attempting to traverse physically “forbidden” areas of game maps (like challenging terrain).
In experiments, the paper’s coauthors ran the framework across a total of 600,000 cores and 1,064 graphics cards (a mixture of Nvidia Tesla P40s and Nvidia V100s), which crunched 16,000 features containing unconcealed unit attributes and game information. Training one hero required 48 graphics cards and 18,000 processor cores at a speed of about 80,000 samples per second per card. And collectively for every day of training, the system accumulated the equivalent of 500 years of human experience.
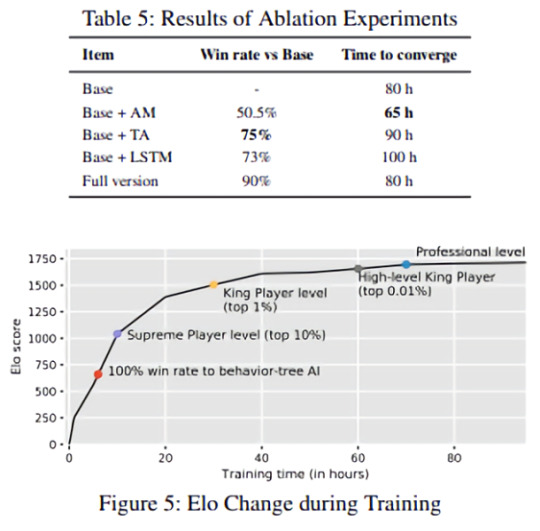
The AI’s Elo score, derived from a system for calculating the relative skill levels of players in zero-sum games, unsurprisingly increased steadily with training, the coauthors note. It became relatively stable within 80 hours, according to the researchers, and within just 30 hours it began to defeat the top 1% of human Honor of Kings players.
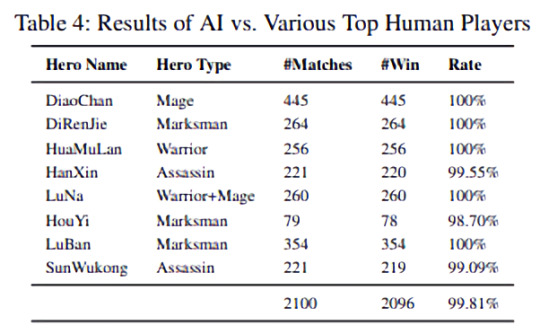
The system executes actions via the AI model every 133 milliseconds, or about the response time of a top-amateur player. Five players professional players were invited to play against it, including “QGhappy.Hurt,” “WE.762,” “TS.NuanYang,” “QGhappy.Fly, eStarPro.Ca,” as well as a “diversity” of players attending the ChinaJoy 2019 conference in Shanghai between August 2 and August 5.
The researchers note that despite eStarPro.Cat’s prowess with mage-type heroes, the AI achieved five kills per game but was killed itself only 1.33 times on average. In public matches, its win rate was 99.81% over 2,100 matches, and five of the eight AI-controlled heroes managed a 100% win rate.
The Tencent researchers say that they plan to make both their framework and algorithms open source in the near future, toward the goal of fostering research on complex games like Honor of Kings. They’re far from the only ones who plan to or who have already done such — DeepMind’s AlphaStar beat 99.8% of human StarCraft 2 players, while OpenAI Five’s OpenAI Five framework defeated a professional team twice in public matches.
0 notes
Text
B.Tech Tuition For Data Structures And Algorithms In Noida
B.Tech Tuition For Data Structures And Algorithms In Noida
B.Tech Tuition For Data Structures And Algorithms In Noida
Abstract Data Types, Sequences as value definitions, Data types in C, Pointers in C, Data Structures and C, Arrays in C, Array as ADT, One Dimensional Array, Implementing one Dimensional Array, Array as parameters, Two Dimensional Array, Structures in C, Implementing Structures, Unions in C, Implementation of unions, Structure Parameters,…
View On WordPress
#9650308924 For Tutorial as well as Tuitions Classes For B. Tech#Addition of Long Positive Integers on Circular and Doubly Linked List Trees: Binary trees: Operations on Binary Trees#Address Calculation Sort#Allocation of storage and scope of variables#AMIE Students. CFA Academy is NOIDA’s oldest and Number - 1 Tuition Center. It is best for Faculties#Application of Depth First Traversal#Applications of Binary Trees#Array as ADT#Array as parameters#Array Implementation of Priority Queue#Arrays in C#B.Tech Tuition For Data Structures And Algorithms In Noida Abstract Data Types#BE#Binary Search#Binary Tree Representation#Binary Tree Traversal in C#Breadth First Traversal#C Implementation of Queues#C Representation of Graphs#Circular Lists: Stack and Queue as Circular List -Primitive Operations on circular lists#Closed Hashing: Linear Probing#Constructing a Tree. Sorting And Searching: General Background of Sorting: Efficiency Considerations#Course completion on time#Data Structures and C#Data types in C#Deleting an Element#Depth First Traversal#Dijkstra&039;s Algorithm#Double Hashing#Doubly Linked Lists
0 notes
Text
NCERT Class 12 Computer Science Chapter 10 Queue
NCERT Class 12 Computer Science C++ Solutions for Chapter 10 Queue
Long Answer Type Questions [4 marks each]
Question 1:
Define member function delque() to perform delete operation on a linked queue where each node has the following structure :
struct node { char name[20] int marks; node *link; }; class queue { node *front,‘rear; public : queue() {front=rear=NULL; } void delque ( ); }; [CBSE Comptt., 2014]
Answer:
void queue : : delque () { if ( front != NULL) { node *Temp = front; cout << Temp -> name << Temp ->marks; front = front->link; delete Temp; if(front == NULL) rear = NULL; } else cout << "Queue is empty"; } (4 marks for correct program)
Question 2:Give the necessary declaration of linked’ implemented Queue containing players information (as defined in the following definition of Node). Also write a user defined function in C++ to delete one Player’s information from the Queue. [CBSE Comptt., 2013]
struct node { int Player No ; char PlayerName[20]; Node*Link; }
Answer:NODE *QUEUEDEL(Node * front, int val, char val2[ ])
{ Node *temp; if (front ==NULL) [1] cout<<"Queue EMPTY"; { else { temp=front ; temp®PlayerNo=val; [1] strcpy (temp®PlayerName, val2); front=front®Link; [1] delete temp; } return (front); } [1]
Question 3:Write a function QDELETE ( ) in C++ to perform delete operation on a Linked Queue, which contains Passenger no and Passenger name. Consider the following definition of Node in the code,
struct node { long int Pno; char Pname [20]; node *Link; }; [O.D, 2013]
Answer://Function to delete queue elements Node * QUEUE (Node * front, int val, char vail [])
{ Node *temp; if (front == NULL) cout <<"Queue Empty"; else { temp = front; temp®Pno=val; strcpy (temp®Pname, vail); front = front®Link; delete temp; } return (front); } [4]
Question 4:Write a function QINSERT() in C+ + to perform insert operation on a Linked Queue, which contains Client no and Client name. Consider the following definition of NODE in the code of . QINSERT (). [Delhi, 2013]
struct Node { long int Cno; // Client No char Cname [20]; // Client Name Node *Next ; };
Answer:Function to Insert elementNode * QINSERT (Node *rear, int val),
char val [] { Node *temp; temp = new Node; temp®Cno = val; strcpy (temp®Cname, val); temp®NEXT=NULL; rear®NEXT=temp; rear=temp; return (rear); } [4]
Question 5:Write a function in C++ to perform Insert operation in a circular Queue containing Layer’s information (represented with the help of an array of structure Player). [CBSE SQP 2013]
struct Player { long PID; //Player ID char Pname [20];} //Player Name Player*Link; }
Answer:
void Insert ( ) { PLAYER *P = new PLAYER; cout <<"Enter Player ID & Name"; cin>>P→PID; gets (P→ Pname); P®Link=NULL; if ((fronts = NULL) && (rear == NULL)) { front = rear = P; } else { rear®Link = P; rear = P; } } [4]
Question 6:Write a function in C++ to perform insert operation in a static circular queue containing book’s information (represented with the help of an array of structure BOOK). [O.D, 2012]
struct BOOK { long Accno; //Book Accession Number char Title[20]; //Book Title };
Answer:
struct BOOK { long Accno; char Title [20] ; int front, rear; }B [10] ; void insert() { if (r e a r = = s i z e - l & & f r o n t = = 0||front== rear+1) { cout<<"\n Circular queue is full"; return; } else if(rear==-l) { rear++; front++; } else if(rear==size-1) rear=0; else { rear++; } cout<<"Enter Title : ” ; cin>>B[rear] . Title; cout<<"Enter Accno : ” ; cin>>B[rear] . Accno; } [4]
Question 7:Write a function in C++ to perform insert operation in a dynamic queue containing DVD’s information (represented with the help of an array of structure DVD). [Delhi, 2012]Answer:/*Function in C++ to perform insert in a dynamic queue is given as*/
struct DVD { long No; // DVD Number char Title[20]; // DVD Title DVD *Link }; void insert(struct DVD *start, char data[20] ) ; { DVD *q, *temp; // Dynamic memory has been allocated for a node temp=(DVD*)malloc(size of (DVD)); temp=Title[20]=data[20] ; temp"Next=NULL; if (start = = NULL) /*Element inserted at end*/ while (q"Next ! = NULL) q=q.Next; q.Next = temp; } [4]
Question 8:Write the definition of a member function INSERT() for a class QUEUE in C++, to insert a CUSTOMER in a dynamically allocated Queue of items considering the following code which is already written as a part of the program,
struct CUSTOMER { int CNO; char CNAME[20]; CUSTOMER *Link; }; Class QUEUE { CUSTOMER *R,*F; Public: QUEUE(){R=NULL;F=NULL;} void INSERT(); void DELETE() -QUEUE(); }; [CBSE SQP 2013]
Answer:
void QUEUE : : INSERT () { CUSTOMER*T=New CUSTOMER; cin>>T>>; gets(T→CNAME); //OR cin>>T>>CNAME; T → LINK = NULL; if (R==NULL) { F=T; R=T; } else { R → LINK = T; R = T; } }
(1 Mark for correct a new code)(1/2 Mark for entering data to new code)(1/2Mark for assigning NULL to link of the new code)(1/2 Mark for assigning front to the first code as L=T)(1/2 Mark for linking the last node to new code as R→Link=T)(1 Mark for assign Read to the new code as R=T)
from Blogger http://www.margdarsan.com/2020/09/ncert-class-12-computer-science-chapter_3.html
0 notes
Text
LINKED LIST
What is Linked list ? Just as the name suggests LINKED LIST it is a list of data that is connected in a such a way that the address of next element or data is stored in the previous data . To access the linked list all we need to do is access the address of first element and that will automatically print the whole list ( because every element is connected with each other).
Why do we use it ? As we know in ARRAY we can store data of similar data type. So array has this con that it can only store data of similar data type. So to overcome this we introduced Linked List . A linked List can store data of multiple data types . This is the main advantage of using a Linked List . Another advantage of using Linked List is the operation of insertion and deletion become easy. Because a LINKED LIST IS MADE UP OF VARIOUS *NODES ( A Node is nothing but it is a structure that holds a data of any data type and Address of type structure). How to use it ? Declaration: struct Linked_List { int Data; struct Linked_List *Node; } This structure has data of data type int and its second variable of struct type Linked_List *Node is used to hold the address of next variable . For making a linked list we need to malloc (to allocate the memory for every node) every single node. As many elements as we want to enter.
-----IMP---- The head node of a linked list should be fixed so that we can access whole Linked list. If we will delete the Head node of the linked list the whole linked list will get destroyed and will get lost in the memory space (as observed) . To End a Linked list we must need to store the Null instead of address so that it won’t access any other . Figure
Head Node
End Node
Operations we can perform
We can perform various operations like insertion , deletion and sorting etc. To perform any operation first we have to know about the position the pointer where it actually is present , which element or node is it representing at present . While making a head node we introduce a variable of type structure that is defined above named temp . All the operations that we want to perform on linked list is performed by the help of temp variable . We never move head node anywhere (Head node is fixed ) . According to our operation we write algo and make functions .
Techniques Using Linked List Stacks – Works on LIFO Technique (Last In First Out) Queues – Works on FIFO Technique (First In First Out)
Types of Linked List Singly Linked List – In this each node has data and pointer pointing towards next Node . As mentioned above in Figure . Doubly Linked List - In this we add a pointer to the previous node . Thus we can go in both forward and backward direction
Circular Linked List – In this the end node of Linked list holds the address of the head node . So it makes up a circle .
0 notes
Text
Tencent details how its MOBA-playing AI system beats 99.81% of human opponents
In August, Tencent announced it had developed an AI system capable of defeating teams of pros in a five-on-five match in Honor of Kings (or Arena of Valor, depending on the region). This was a noteworthy achievement — Honor of Kings occupies the video game subgenre known as multiplayer online battle arena games (MOBAs), which are incomplete information games in the sense that players are unaware of the actions other players choose. The endgame, then, isn’t merely AI that achieves Honor of Kings superhero performance, but insights that might be used to develop systems capable of solving some of society’s toughest challenges.
A paper published this week peels back the layers of Tencent’s technique, which the coauthors describe as “highly scalable.” They claim its novel strategies enable it to explore the game map “efficiently,” with an actor-critic architecture that self-improves over time.
As the researchers point out, real-time strategy games like Honor of Kings require highly complex action control compared with traditional board games and Atari games. Their environments also tend to be more complicated (Honor of Kings has 10^600 possible states and and 10^18,000 possible actions) and the objectives more complex on the whole. Agents must not only learn to plan, attack, and defend but also to control skill combos, induce, and deceive opponents, all while contending with hazards like creeps and fully automated turrets.
Tencent’s architecture consists of four modules: Reinforcement Learning (RL) Learner, Artificial Intelligence (AI) Server, Dispatch Module, and Memory Pool.
The AI Server — which runs on a single processor core, thanks to some clever compression — dictates how the AI model interacts with objects in the game environment. It generates episodes via self-play, and, based on the features it extracts from the game state, it predicts players’ actions and forwards them to the game core for execution. The game core then returns the next state and the corresponding reward value, or the value that spurs the model toward certain Honor of Kings goals.
As for the Dispatch Module, it’s bundled with several AI Servers on the same machine, and it collects data samples consisting of rewards, features, action probabilities, and more before compressing and sending them to Memory Pools. The Memory Pool — which is also a server — supports samples of various lengths and data sampling based on the generated time, and it implements a circular queue structure that performs storage operations in a data-efficient fashion.
Lastly, the Reinforcement Learner, a distributed training environment, accelerates policy updates with the aforementioned actor-critic approach. Multiple Reinforcement Learners fetch data in parallel from Memory Pools, with which they communicate using shared memory. One mechanism (target attention) helps with enemy target selection, while another — long short-term memory (LSTM), an algorithm capable of learning long-term dependencies — teaches hero players skill combos critical to inflicting “severe” damage.
The Tencent researchers’ system encodes image features and game state information such that each unit and enemy target is represented numerically. An action mask cleverly incorporates prior knowledge of experienced human players, preventing the AI from attempting to traverse physically “forbidden” areas of game maps (like challenging terrain).
In experiments, the paper’s coauthors ran the framework across a total of 600,000 cores and 1,064 graphics cards (a mixture of Nvidia Tesla P40s and Nvidia V100s), which crunched 16,000 features containing unconcealed unit attributes and game information. Training one hero required 48 graphics cards and 18,000 processor cores at a speed of about 80,000 samples per second per card. And collectively for every day of training, the system accumulated the equivalent of 500 years of human experience.
The AI’s Elo score, derived from a system for calculating the relative skill levels of players in zero-sum games, unsurprisingly increased steadily with training, the coauthors note. It became relatively stable within 80 hours, according to the researchers, and within just 30 hours it began to defeat the top 1% of human Honor of Kings players.
The system executes actions via the AI model every 133 milliseconds, or about the response time of a top amateur player. Five professional players — “QGhappy.Hurt,” “WE.762,” “TS.NuanYang,” “QGhappy.Fly,” and “eStarPro.Ca,” — were invited to play against it, as well as a “diversity” of players attending the ChinaJoy 2019 conference in Shanghai between August 2 and August 5.
The researchers note that despite eStarPro.Cat’s prowess with mage-type heroes, the AI achieved five kills per game and was killed only 1.33 times per game on average. In public matches, its win rate was 99.81% over 2,100 matches, and five of the eight AI-controlled heroes managed a 100% win rate.
They’re far from the only ones whose AI beat human players — DeepMind’s AlphaStar beat 99.8% of human StarCraft 2 players, while OpenAI Five’s OpenAI Five framework defeated a professional team twice in public matches.
The Tencent researchers say that they plan to make both their framework and algorithms open source in the near future, toward the goal of fostering research on complex games like Honor of Kings.
The post Tencent details how its MOBA-playing AI system beats 99.81% of human opponents appeared first on Actu Trends.
0 notes
Text
300+ TOP WINDOWS SYSTEM ADMINISTRATOR Objective Questions
Windows System Administrator Multiple Choice Questions :-
1. Which of the following administrative thinkers has defined administration as "the organization and direction of human and material resources to achieve desired ends" ? A. L. D. White B. J. M. Pfiffner C. J. A. Veig D. H. A. Simon Ans : B 2. Which one of the following statements is not correct in respect of New Public Management ? A. It has market orientation B. It upholds public interest C. It advocates managerial autonomy D. It focuses on performance appraisal Ans : B 3. 'Good Governance' and 'Participating Civil Society for Development' were stressed in World Bank Report of— A. 1992 B. 1997 C. 2000 D. 2003 Ans : A 4. If the administrative authority within a department is vested in a single individual, then that system is known as— A. Board B. Bureau C. Commission D. Council Ans : B 5. Globalisation means— A. Financial market system is centered in a single state B. The growth of a single unified world market C. Geographical location of a firm is of utmost importance D. Foreign capitalist transactions Ans : B 6. By whom was the 'Managerial Grid' developed ? A. Blake and White B. Blake and Schmidt C. Blake and Mouton D. Mouton and Shophan Ans : C 7. Who among the following says that public administration includes the operations of only the executive branch of government ? A. L. D. White and Luther Gulick B. L. D. White C. Luther Gulick D. W. F. Willoughby Ans : C 8. The concept of the 'zone of indifference' is associated with— A. Decision-Making B. Leadership C. Authority D. Motivation Ans : C 9. Who has analysed the leadership in terms of 'circular response' ? A. C. I. Barnard B. M. P. Follett C. Millet D. Taylor Ans : B 10. Simon proposed a new concept of administration based on the methodology of— A. Decision-making B. Bounded rationality C. Logical positivism D. Satisfying Ans : C

WINDOWS SYSTEM ADMINISTRATOR Objective Questions 11. Who wrote the book 'Towards A New Public Administration : The Minnowbrook Perspective' ? A. Frank Marini B. Dwight Waldo C. C. J. Charlesworth D. J. M. Pfiffner Ans : A 12. Who rejected the principles of administration as 'myths' and 'proverbs' ? A. W. F. Willoughby B. Herbert Simon C. Chester Barnard D. L. D. White Ans : B 13. The classical theory of administration is also known as the— A. Historical theory B. Mechanistic theory C. Locational theory D. Human Relations theory Ans : B 14. How many principles of organization were propounded by Henry Fayol ? A. 10 B. 14 C. 5 D. 9 Ans : B 15. Simon was positively influenced by ideas of— A. Terry B. Barnard C. L. D. White D. Henry Fayol Ans : B 16. Negative motivation is based on— A. Fear B. Reward C. Money D. Status Ans : A 17. 'Job loading' means— A. Shifting of an employee from one job to another B. Deliberate upgrading of responsibility, scope and challenge C. Making the job more interesting D. None of the above Ans : B 18. The theory of 'Prismatic Society' in Public Administration is based on— A. Study of public services in developed and developing countries B. Institutional comparision of public administration in developed countries C. Structural-functional analysis of public administration in developing countries D. Historical studies of public administration in different societies Ans : C 19. Who among the following is an odd thinker ? A. Taylor B. Maslow C. Herzberg D. Likert Ans : A 20. Which of the following is not included in 'hygiene' factors in the Herzberg's two-factor theory of motivation ? A. Salary B. Working conditions C. Company's policy D. Responsibility Ans : D 21. What should a system administrator use to disable access to a custom application for a group of users? A. Profiles B. Sharing rules C. Web tabs D. Page layouts Ans :A 22. Universal Containers needs to track the manufacturer and model for specific car companies. How can the system administrator ensure that the manufacturer selected influences the values available for the model? A. Create the manufacturer field as a dependent picklist and the model as a controlling picklist. B. Create a lookup field from the manufacturer object to the model object. C. Create the manufacturer field as a controlling picklist and the model as a dependent picklist. D. Create a multi-select picklist field that includes both manufacturers and models. Ans :C 23. Sales representatives at Universal Containers need assistance from product managers when selling certain products. Product managers do not have access to opportunities, but need to gain access when they are assisting with a specific deal. How can a system administrator accomplish this? A. Notify the product manager using opportunity update reminders. B. Enable sales teams and allow users to add the product manager. C. Use similar opportunities to show opportunities related to the product manager. D. Enable account teams and allow users to add the product manager Ans :B 24. What should a system administrator consider before importing a set of records into Salesforce? There are two correct answers.. A. The import file should include a record owner for each record. B. Currency field values will default to the personal currency of the record owner. C. Data should be de-duplicated in the import file prior to import. D. Validation rules are not triggered when importing data using the import wizard. Ans :A,C 25. Which statement about custom summary formulas in reports is true? There are two correct answers.. A. Reports can be grouped by a custom summary formula result. B. Custom summary formulas can reference a formula field within a report. C. Custom summary formulas can reference another custom summary formula. D. Custom summary formulas can be used in a report built from a custom report type. Ans :B,D 26. Which of the following utilities provides a report of memory status for instances, databases, and agents? A.db2mtrk B.db2mchk C.db2expln D.db2memview Ans : A 27. Given the following notification log entry: In order to determine the name of the application which encountered the error, which of the following actions must be taken? A.Issue DB2 LIST DCS APPLICATIONS and search for AC14B132.OB12.0138C7070500 B.Issue DB2 LIST APPLICATIONS and search for AC14B132.OB12.0138C7070500 C.Issue DB2 LIST DCS APPLICATIONS and search for 660 D.Issue DB2 LIST APPLICATIONS and search for 660 Ans : B 28. Given the table MYTAB: A.The index MYINX will not be created. B.The word UNIQUE will be omitted by DB2 and a non-unique index MYINX will be created. C.The unique index MYINX will be created and the rows with duplicate keys will be deleted from the table. D.The unique index MYINX will be created and the rows with duplicate keys will be placed in an exception table. Ans : A 29. Which of the following REORG table options will compress the data in a table using the existing compression dictionary? A.KEEPEXISTING B.KEEPDICTIONARY C.RESETDICTIONARY D.EXISTINGDICTIONARY Ans : B 30. Which of the following statements about SCHEMA objects is true? A.A schema must always be associated with a user. B.Triggers and sequences do not have schemas associated with them. C.After creating a new database, all users who successfully authenticate with the database have the ability to create a new schema. D.If a schema is not explicitly specified in a SQL statement, the PUBLIC schema is assumed. Ans : C 31. An iseries server with domino and Websphere Commerce suite installed is performing well, except when the Domino or Websphere servers are starting. Which of the following is the most likely cause of the performance problem. A. Job Queue ASERVER in subsystem ASERVER is set to single thread jobs. B. The activity level in the shared pool running the servers is too low. C. The managing Domino server instance is not started prior to the Websphere server instance. D. The system value QMLTTHDACN Multithreaded job action. is set to stop non-thread safe processes. Ans : B 32. A system administrator needs to add 100 users to a V6R2 system without impacting response times, Which of the following would be the first step in determining the current performance of the system? A. Define a performance collection agent in iDoctor for iSeries. B. Define a performance collection object within iSeries navigator. C. Use Performance Explorer to collect generalized performance data. D. Use the Workload Estimator to show existing performance constraints. Ans : B 33. A batch subsystem is established to run jobs from multiple queues, An application submits two jobs to each queue. All jobs are in release status. Which of the following is the reason that only three jobs have started to run? A. The total MAXACT for all fo the job queue entries is three. B. Only three of the job queue priorities have been defined in the subsystem. C. The activity level setting associated with the subsystem description is 3. D. The execution of the pending jobs, is governed within the application of the jobs currently running. Ans : A 34. What command is used to save the IFS to taps? A. SAV B. SAVRST C. SAVDLO DLO IFS. D. SAVSYS OBJTYPE IFS.. Ans : A 35. A Manufacturing company has three remote sites and a total of six distributed AS/400 systems. The company would like to accomplish the followings. A. Centralize to a single system. B. Maintain each system workload and identity attributes. C. Reduce the total cost of ownership of maintaining individual systems. D. Maintain existing performance levels. Ans : 36. Which of the following can have an impact on determining the interactive workload requirements of an iSeries? A. Active subsystems. B. Active controllers. C. Active user profiles. D. Active display sessions. Ans : D 37. On a system that does not have Performance Tools for iSeries 5722-PTI., how can performance data be collected for analysis on a different system that has Performance Tools installed. A. Use Electronic Service Agent for iSeries. B. Use the Start Performances Monitor command. C. Start a Performance Monitor in iSeries Navigator. D. Install and run OS/400 product option 42, performance Collection Client. Ans : C 38. Which fo the following commands will save all objects in the IFS? A. SAV B. SAVDLO C. SAVLIB "IFS" D. SAVLIB NONSYS. Ans : A 39. Which system performance command can send output to both the online serene and a database file simultaneously. A. WRKSYSACT B. WRKACTJOB C. WRKDSKSTS. D. WRKSYSSTS. Ans : A 40. Using the example below, what is the cumulative PTF level of the system? Display PTF status. System: ANYSYS. Product ID.............. 5722999 IPL source............... ## MACH#B elease of base option ........V5R1M0.LOO. PTF IPL Opt ID Status Action. TL02134 Temporarily applied None. TL02071 Permanently applied None. TL01226 Superseded None. RE01066 Permanently Applied None. QLL2924 Permanently Applied None. MF29379 Permanently Applied None. MF29287 Permanently Applied None. A. TL02071 B. TL02134 C. RE01066 D. MF29379 Ans : B 41. Job description FREDJOBD has public authority of USE. This job description specifies that jobs run under user profile FRED. Which has public authority EXCLUDE*. Use profile SUE is user class USER* with default special authorities and does not have specific authority to use profile FRED. User which security levels would user profile SUE be able to successfully submit a job using PREDJOBD with the intent to run the job under user profile FRED? A. At 20 only. B. At 20 and 30. C. At 20, 30, and 40. D. At 20,30,40, and 50. Ans : B 42. On an iSeries running V5R2, which fo the following authorities needs to be removed from an object to ensure that the object owner cannot delete it? A. Object alter authority. B. Object existence authority. C. Object Management authority. D. Object operational authority. Ans : B 43. Which of the following disk drive considerations has the greatest impact on system performance? A. Number of disk drives on a bus. B. User versus available disk space. C. Data protection method RAID verses mirroring.. D. Peak rate of disk requests versus the number of disk arms. Ans : D 44. Which of the following will enable an administrator to establish an ongoing analysis of the performance and utilization of an iSeries. A. Upload the performance data to the IBM workload Estimator. B. Activate Performance Manage/400 to automatically upload data to IBM. C. Enable PPP communications between the iSeries and the IBM Benchmark Center. D. Utilize the no-charge OS/400 performance analysis tools to print monthly reports. Ans : B 45. Users are reporting long response time delays in transactions that previously would run with sunscald response. The system administrator knows these transactions are RPG IV-SQL based programs. Which of the following would be the first set in determining the problems. A. Use Management Central to start a job monitor for system and select the SQL submonitor display. B. Use iSeries Navigator, SQL Performance Monitor to conllect and analyze the SQL performance of the jobs. C. Start debug on one of the on-line jobs and use Performance Explorer to analyze the jobs database access plan. D. Use iSeries Navigator to create a database map of the tables used in the transactions and watch for high I/O rates. Ans : B 46. A system administrator wants to collect performance data for multiple iSeries servers in a network. When attempting to start performance collection using iSeries Navigator, collection services fail. Which of the following is the most likely cause of the problem. A. The Management Central, central system is not connecting. B. Performance Tools 5722.PTI. is not installed on all systems. C. The user profile being used to start collection does not have *SYSADM special authority. D. The Management Central performance collector plug-in is not installed in iSeries Navigator. Ans : A 47. Which of the following can be adjusted daily by a scheduled job to maximize interactive or bath throughput? A. Memory pools. B. QACTJOB system value. C. Auxiliary storage pools. D. QMAXACTLVL system value. Ans : A 48. Which of the following would the most viable course of action? A. Implement High Availability and replicate each system to a single system. B. Implement LPAR on a centrally located system and consolidate the individual systems onto multiple partitions. C. Transfer all systems to the central location and create an iSeries cluster to form a single "logical" system. D. Consolidate all the systems into a single partition on a syst3em with a CPW rating that matches or exceeds the accumulated CPW of the individual systems. Ans : B 49. Which of the following should be considered when preparing for a release upgrade? A. User changes made to IBM supplied commands. B. Valid license information for the current release. C. Presence of user libraries after QSYS in the system library list. D. Installation of the latest cumulative package for the current release. Ans : A 50. An iSeries Administrator would like to monitor the performance of all four of the machines in the data center at one time. If a certain level of interactive CPU is reached, the administrator wants to receive an email. What needs to be done to satisfy the requirements. A. In Management Central, set up a system group monitor job with a threshold action. B. In iSeries Navigator create endpoints for each of the systems and set up a threshold job monitor. C. Add an exit program to the WRKACTJOB command to intercept the CPU statistics and process the email. D. Start PM/400 and use the PM/400 notification options to send the email when the threshold is reached. Ans : A 51. A DBA wishes to audit all access to the non-audited table OWNER.EMPLOYEE. Assuming no audit traces are started, which of the following steps are needed to audit access to this table? A. -START TRACE AUDIT CLASS 5. B. -START TRACE AUDIT CLASS 4, 5. C. -START TRACE AUDIT CLASS 4, 5. and ALTER TABLE OWNER.EMPLOYEE AUDIT ALL D. -START TRACE AUDIT CLASS 4, 5. and ALTER TABLE OWNER.EMPLOYEE DATA CAPTURE CHANGES Ans : C 52. A company uses TRUSTED CONTEXT "ERP1" and ROLE "ERP_ROLE" as a security mechanism to limit security exposure for an application. All the DB2 objects databases, table spaces, tables, indexes, views, plans and packages. have been created by that ROLE. The ROLE "ERP_ROLE" has been assigned to User ID "DBA01" in order to perform DBA related tasks. When the user "DBA01" leaves the company, the authorization ID is removed. Which of the following statements are correct? Select two answers. A. None of these DB2 objects need to be recreated to re-grant the privileges. B. The related plans and packages have to be recreated and the privileges re-granted. C. When removing user "DBA01" privileges, none of these DB2 objects need to be dropped. D. Only the related databases, table spaces, tables, indexes and views need to be recreated and the privileges re-granted. E. To remove the privileges of user "DBA01" on these related plans and packages, they have to be dropped and as a result all associated privileges are revoked. Ans : A,C 53. At which of the following times is the access control authorization routine DSNX@XAC. invoked? A. At DB2 startup. B. When executing a DB2 GRANT statement. C. When DB2 has cached authorization information. D. During any authorization check if NO was specified in the USE PROTECTION field of the DSNTIPP panel. Ans : A 54. If an object is created statically by a role within a trusted context and the ROLE AS OBJECT OWNER clause is specified, who becomes the object owner when executing the package? A. The role B. The schema name C. The owner keyword D. The current SQLID if set. Ans : A 55. A DBA needs to use the DSN command processor to delete DB2 packages that are no longer needed. Which of the following choices is correct for the DBA to use? A. SPUFI or QMF with the DROP statement B. FREE Package ... C. DROP Package ... D. DROP PLAN . PKLIST ... Ans : B 56. Which of the following tools is used to create subscription sets and add subscription-set members to subscription sets? A. Journal B. License Center C. Replication Center D. Development Center Ans : C 57. Given the following table definition: STAFF id INTEGER name CHAR20. dept INTEGER job CHAR20. years INTEGER salary DECIMAL10,2. comm DECIMAL10,2. Which of the following SQL statements will return a result set that satisfies these conditions: -Displays the department ID and total number of employees in each department. -Includes only departments with at least one employee receiving a commission comm. greater than 5000. -Sorted by the department employee count from greatest to least. A. SELECT dept, COUNT*. FROM staff GROUP BY dept HAVING comm > 5000 ORDER BY 2 DESC B. SELECT dept, COUNT*. FROM staff WHERE comm > 5000 GROUP BY dept, comm ORDER BY 2 DESC C. SELECT dept, COUNT*. FROM staff GROUP BY dept HAVING MAXcomm. > 5000 ORDER BY 2 DESC D. SELECT dept, comm, COUNTid. FROM staff WHERE comm > 5000 GROUP BY dept, comm ORDER BY 3 DESC Ans : C 58. Which of the following DB2 data types CANNOT be used to contain the date an employee was hired? A. CLOB B. TIME C. VARCHAR D. TIMESTAMP Ans : B 59. A table called EMPLOYEE has the following columns: NAME DEPARTMENT PHONE_NUMBER Which of the following will allow USER1 to modify the PHONE_NUMBER column? A. GRANT INDEX phone_number. ON TABLE employee TO user1 B. GRANT ALTER phone_number. ON TABLE employee TO user1 C. GRANT UPDATE phone_number. ON TABLE employee TO user1 D. GRANT REFERENCES phone_number. ON TABLE employee TO user1 Ans : C 60. Which two of the following SQL data types should be used to store a small binary image? A. CLOB B. BLOB C. VARCHAR D. GRAPHIC E. VARCHAR FOR BIT DATA Ans : B,E 61. Which of the following CLI/ODBC functions should be used to delete rows from a DB2 table? A. SQLDelete. B. SQLExecDirect. C. SQLBulkDelete. D. SQLExecuteUpdate. Ans : B 62. Given the tables T1 and T2 with INTEGER columns: How many rows will be left in T1 after running this statement? A. 0 B. 2 C. 3 D. 6 Ans : B 63. Given the following code: EXEC SQL EXECUTE IMMEDIATE :sqlstmt Which of the following values must sqlstmt contain so that all rows are deleted from the STAFF table? A. DROP TABLE staff B. DELETE FROM staff C. DROP * FROM staff D. DELETE * FROM staff Ans : B 64. An ODBC/CLI application executes the following batch SQL: SQLExecDirect hStmt, "SELECT c1 FROM t1; SELECT c2 FROM t2;" SQL_NTS .; Which API is used to discard the first result set and make the second available for processing? A. SQLFetch. B. SQLRowCount. C. SQLMoreResults. D. SQLCloseCursor. Ans : C 65. Given the table T1 with the following data: What is the final content of the host variable "hv"? A. A B. B C. C D. D Ans : C 66. Which of the following is required to specify the output data during an EXPORT? A. Union B. Key range C. Equi-join D. Fullselect Ans : D 67. On which of the following event types can a WHERE clause be used to filter the data returned by the event monitor? A. TABLES B. DEADLOCKS C. TABLESPACES D. CONNECTIONS Ans : D 68. Given an application with the embedded static SQL statement: INSERT INTO admin.payroll employee, salary. VALUES "Becky Smith",80000. Which of the following privileges must a user hold to run the application? A. ALTER on the table B. INSERT on the table C. DBADM on the database D. EXECUTE on the package Ans : D 69. Assuming a user has CREATETAB privileges, which of the following privileges will allow the user to create a table T2 with a foreign key that references table T1? A. SYSCTRL B. SYSMAINT C. UPDATE on table T1 D. CONTROL on table T1 Ans : D 70. Which of the following statements is required to register a federated database source? A. CREATE VIEW B. CREATE WRAPPER C. CREATE TRANSFORM D. CREATE TYPE MAPPING Ans : B 71. Which two of the following can be done to a buffer pool using the ALTER BUFFERPOOL statement? A. Reduce the size. B. Change the page size. C. Modify the extent size. D. Modify the prefetch size. E. Immediately increase the size. Ans : AE 72. A table is defined using DMS table spaces with its index, data, and long data separated into different table spaces. The table space containing the table data is restored from a backup image. Which of the table's other table spaces must also be restored in order to roll forward to a point in time prior to the end of the logs? A. Long table space B. Index table space C. Temporary table space D. Index and long table spaces Ans : D 73. In a federated system, a userid is used for the CREATE SERVER definition at the DB2 data source. Which of the following privileges should it have? A. SELECT on the catalog at the DB2 data source B. UPDATE on the CREATE SERVER definition table C. SELECT on the tables for which nicknames are created D. INSERT on the tables for which nicknames are created Ans : A 74. Which of the following can enable multiple prefetchers for table spaces with a single container? A. NUM_IOSERVERS B. INTRA_PARALLEL C. DB2_PARALLEL_IO D. DB2_STRIPED_CONTAINERS Ans : C 75. Given a single physical server with a single OS image utilizing 24 CPUs and configured with 12 database partitions, how many of the database partitions can act as coordinator partitions for remote applications? A. 1 B. 2 C. 12 D. 24 Ans : C 76. When using AUTOCONFIGURE and a workload that is of type OLTP, what should be used for the workload_type parameter? A. dss B. mixed C. simple D. complex Ans : C 78. To determine the state of a table space and the location of all containers for that table space, which of the following commands would be used? A. LIST TABLESPACES SHOW DETAIL B. GET SNAPSHOT FOR TABLESPACES ON C. LIST TABLESPACE CONTAINERS FOR D. GET SNAPSHOT FOR TABLESPACES ON SHOW DETAIL Ans : B 79. The following command is issued: LOAD FROM staff.ixf OF IXF REPLACE INTO staff What locks are help during the execution of this load? A. Share lock on table STAFF B. Exclusive lock on table STAFF C. Exclusive lock on all table spaces holding components of the STAFF table D. Exclusive lock only on table space holding data component of the STAFF table Ans : B 80. Use the exhibit button to display the exhibit for this question. What is indicated by the output from the Health Monitor in the exhibit? A. 1 warning alert on NTINST, 2 alarm and 1 warning alert on NTDB B. 1 warning alert on NTINST, 1 alarm and 1 warning alert on NTDB C. 1 alarm and 1 warning alert on NTINST, 2 alarm and 1 warning alert on NTDB D. 1 alarm and 1 warning alert on NTINST, 1 alarm and 1 warning alert on NTDB Ans : B WINDOWS SYSTEM ADMINISTRATOR Questions and Answers pdf Download Read the full article
0 notes
Text
Types of Queues in Data Structure
Queue is an important structure for storing and retrieving data and hence is used extensively among all the data structures. Queue, just like any queue (queues for bus or tickets etc.) follows a FIFO mechanism for data retrieval which means the data which gets into the queue first will be the first one to be taken out from it, the second one would be the second to be retrieved and so on.
Types of Queues in Data Structure
Simple Queue
Image Source
As is clear from the name itself, simple queue lets us perform the operations simply. i.e., the insertion and deletions are performed likewise. Insertion occurs at the rear (end) of the queue and deletions are performed at the front (beginning) of the queue list.
All nodes are connected to each other in a sequential manner. The pointer of the first node points to the value of the second and so on.
The first node has no pointer pointing towards it whereas the last node has no pointer pointing out from it.
Circular Queue
Image Source
Unlike the simple queues, in a circular queue each node is connected to the next node in sequence but the last node’s pointer is also connected to the first node’s address. Hence, the last node and the first node also gets connected making a circular link overall.
Priority Queue
Image Source
Priority queue makes data retrieval possible only through a pre determined priority number assigned to the data items.
While the deletion is performed in accordance to priority number (the data item with highest priority is removed first), insertion is performed only in the order.
Doubly Ended Queue (Dequeue)
Image Source
The doubly ended queue or dequeue allows the insert and delete operations from both ends (front and rear) of the queue.
Queues are an important concept of the data structures and understanding their types is very necessary for working appropriately with them.
The post Types of Queues in Data Structure appeared first on The Crazy Programmer.
0 notes
Text
CSE 330 - Operating Systems Project #1 Solved
CSE 330 – Operating Systems Project #1 Solved
Part 1: (This part of the project is not graded.)
Overview:
For this project you are to write routines that perform standard queuing functions. The functions work on multiple queues, and structure each queue as a doubly linked, circular list.
Data Structures:
A queue consists of a head-pointer and a set of q-elements.
A q-element is a structure, consisting of a prev and next pointer, and a…
View On WordPress
0 notes