#code m365
Explore tagged Tumblr posts
Text
Presenting Azure AI Agent Service: Your AI-Powered Assistant

Presenting Azure AI Agent Service
Azure has announced managed features that enable developers to create safe, stateful, self-governing AI bots that automate all business procedures.
Organizations require adaptable, safe platforms for the development, deployment, and monitoring of autonomous AI agents in order to fully exploit their potential.
Use Azure AI Agent Service to enable autonomous agent capabilities
At Ignite 2024, Azure announced the upcoming public preview of Azure AI Agent Service, a suite of feature-rich, managed capabilities that brings together all the models, data, tools, and services that businesses require to automate any kind of business operation. This announcement is motivated by the needs of its customers and the potential of autonomous AI agents.
Azure AI Agent Service is adaptable and independent of use case. Whether it’s personal productivity agents that send emails and set up meetings, research agents that continuously track market trends and generate reports, sales agents that can investigate leads and automatically qualify them, customer service agents that follow up with personalized messages, or developer agents that can update your code base or evolve a code repository interactively, this represents countless opportunities to automate repetitive tasks and open up new avenues for knowledge work.
What distinguishes Azure AI Agent Service?
After speaking with hundreds of firms, it has discovered that there are four essential components needed to quickly produce safe, dependable agents:
Develop and automate processes quickly: In order to carry out deterministic or non-deterministic operations, agents must smoothly interact with the appropriate tools, systems, and APIs.
Integrate with knowledge connectors and a large memory: In order to have the appropriate context to finish a task, agents must connect to internal and external knowledge sources and monitor the status of conversations.
Flexible model selection: Agents that are constructed using the right model for the job at hand can improve the integration of data from many sources, produce better outcomes for situations unique to the task at hand, and increase cost effectiveness in scaled agent deployments.
Built-in enterprise readiness: Agents must be able to scale with an organization’s needs, meet its specific data privacy and compliance requirements, and finish tasks with high quality and dependability.
Azure AI Agent Service offers these components for end-to-end agent development through a single product surface by utilizing the user-friendly interface and extensive toolkit in the Azure AI Foundry SDK and site.
Let’s now examine the capabilities of Azure AI Agent Service in more detail.
Fast agent development and automation with powerful integrations
Azure AI Agent Service, based on OpenAI’s powerful yet flexible Assistants API, allows rapid agent development with built-in memory management and a sophisticated interface to seamlessly integrate with popular compute platforms and bridge LLM capabilities with general purpose, programmatic actions.
Allow your agent to act with 1400+ Azure Logic Apps connectors: Use Logic Apps’ extensive connector ecosystem to allow your agent accomplish tasks and act for users. Logic apps simplify workflow business logic in Azure Portal to connect your agent to external systems, tools, and APIs. Azure App Service, Dynamics365 Customer Voice, Microsoft Teams, M365 Excel, MongoDB, Dropbox, Jira, Gmail, Twilio, SAP, Stripe, ServiceNow, and others are connectors.
Use Azure Functions to provide stateless or stateful code-based activities beyond chat mode: Allow your agent to call APIs and transmit and wait for events. Azure Functions and Azure Durable tasks let you execute serverless code for synchronous, asynchronous, long-running, and event-driven tasks like invoice approval with human-in-the-loop, long-term product supply chain monitoring, and more.
Code Interpreter lets your agent create and run Python code in a safe environment, handle several data types, and generate data and visual files. This tool lets you use storage data, unlike the Assistants API.
Standardize tool library with OpenAPI: Use an OpenAPI 3.0 tool to connect your AI agent to an external API for scaled application compatibility. Custom tools can authenticate access and connections with managed identities (Microsoft Entra ID) for enhanced security, making it perfect for infrastructure or web services integration.
Add cloud-hosted tools to Llama Stack agents: The agent protocol is supported by Azure AI Agent Service for Llama Stack SDK developers. Scalable, cloud-hosted, enterprise-grade tools will be wireline compatible with Llama Stack.
Anchor agent outputs with a large knowledge environment
Easily establish a comprehensive ecosystem of enterprise knowledge sources to let agents access and interpret data from different sources, boosting user query responses. These data connectors fit your network characteristics and interact effortlessly with your data. Built-in data sources are:
Real-time web data online data grounding with Bing lets your agent give users the latest information. This addresses LLMs’ inability to answer current events prompts like “top news headlines” factually.
Microsoft SharePoint private data: SharePoint internal documents can help your agent provide accurate responses. By using on-behalf-of (OBO) authentication, agents can only access SharePoint data that the end user has permissions for.
Talk to structured data in Microsoft Fabric: Power data-driven decision making in your organization without SQL or data context knowledge. The built-in Fabric AI Skills allow your agent to develop generative AI-based conversational Q&A systems on Fabric data. Fabric provides secure data connection with OBO authentication.
Add private data from Azure AI Search, Azure Blob, and local files to agent outputs: Azure re-invented the File Search tool in Assistants API to let you bring existing Azure AI Search index or develop a new one using Blob Storage or local storage with an inbuilt data ingestion pipeline. With file storage in your Azure storage account and search indexes in your Azure Search Resource, this new file search gives you full control over your private data.
Gain a competitive edge with licensed data: Add licensed data from private data suppliers like Tripadvisor to your agent responses to provide them with the latest, best data for your use case. It will add more licensed data sources from other industries and professions.
In addition to enterprise information, AI agents need thread or conversation state management to preserve context, deliver tailored interactions, and improve performance over time. By managing and obtaining conversation history from each end-user, Azure AI Agent Service simplifies thread management and provides consistent context for better interactions. This also helps you overcome AI agent model context window restrictions.
Use GPT-4o, Llama 3, or another model that suits the job
Developers love constructing AI assistants with Azure OpenAI Service Assistants API’s latest OpenAI GPT models. Azure now offers cutting-edge models from top model suppliers so you can design task-specific agents, optimize TCO, and more.
Leverage Models-as-a-Service: Azure AI Agent Service will support models from Azure AI Foundry and use cross-model compatible, cloud-hosted tools for code execution, retrieval-augmented generation, and more. The Azure Models-as-a-Service API lets developers create agents with Meta Llama 3.1, Mistral Large, and Cohere Command R+ in addition to Azure OpenAI models.
Multi-modal support lets AI agents process and respond to data formats other than text, broadening application cases. GPT-4o‘s picture and audio modalities will be supported so you may analyze and mix data from different forms to gain insights, make decisions, and give user-specific outputs.
For designing secure, enterprise-ready agents from scratch
Azure AI Agent Service provides enterprise tools to protect sensitive data and meet regulatory standards.
Bring your own storage: Unlike Assistants API, you can now link enterprise data sources to safely access enterprise data for your agent.
BYO virtual network: Design agent apps with strict no-public-egress data traffic to protect network interactions and data privacy.
Keyless setup, OBO authentication: Keyless setup and on-behalf-of authentication simplify agent configuration and authentication, easing resource management and deployment.
Endless scope: Azure AI Agent Service on provided deployments offers unlimited performance and scaling. Agent-powered apps may now be flexible and have predictable latency and high throughput.
Use OpenTelemetry to track agent performance: Understand your AI agent’s reliability and performance. The Azure AI Foundry SDK lets you add OpenTelemetry-compatible metrics to your monitoring dashboard for offline and online agent output review.
Content filtering and XPIA mitigation help build responsibly: Azure AI Agent Service detects dangerous content at various severity levels with prebuilt and custom content filters.
Agents are protected from malicious cross-prompt injection attacks by prompt shields. Like Azure OpenAI Service, Azure AI Agent Service prompts and completions are not utilized to train, retrain, or improve Microsoft or 3rd party goods or services without your permission. Customer data can be deleted at will.
Use Azure AI Agent Service to orchestrate effective multi-agent systems
Azure AI Agent Service is pre-configured with multi-agent orchestration frameworks natively compatible with the Assistants API, including Semantic Kernel, an enterprise AI SDK for Python,.NET, and Java, and AutoGen, a cutting-edge research SDK for Python developed by Microsoft Research.
To get the most dependable, scalable, and secure agents while developing a new multi-agent solution, begin by creating singleton agents using Azure AI Agent Service. These agents can then be coordinated by AutoGen, which is always developing to determine the most effective patterns of cooperation for agents (and humans) to cooperate. If you want non-breaking updates and production support, you may then move features that demonstrate production value with AutoGen into Semantic Kernel.
Read more on Govindhtech.com
#AzureAI#AIAgent#AIAgentService#AI#OpenAPI#Llama#SDK#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
Confronting the Security Risks of Copilots
New Post has been published on https://thedigitalinsider.com/confronting-the-security-risks-of-copilots/
Confronting the Security Risks of Copilots
More and more, enterprises are using copilots and low-code platforms to enable employees – even those with little or no technical expertise – to make powerful copilots and business apps, as well as to process vast amounts of data. A new report by Zenity, The State of Enterprise Copilots and Low-Code Development in 2024, found that, on average, enterprises have about 80,000 apps and copilots that were created outside the standard software development lifecycle (SDLC).
This development offers new opportunities but new risks, as well. Among these 80,000 apps and copilots are roughly 50,000 vulnerabilities. The report noted that these apps and copilots are evolving at breakneck speed. Consequently, they are creating a massive number of vulnerabilities.
Risks of enterprise copilots and apps
Typically, software developers build apps carefully along a defined SDLC (secure development lifecycle) where every app is constantly designed, deployed, measured and analyzed. But today, these guardrails no longer exist. People with no development experience can now build and use high-powered copilots and business apps within Power Platform, Microsoft Copilot, OpenAI, ServiceNow, Salesforce, UiPath, Zapier and others. These apps help with business operations as they transfer, and store sensitive data. Growth in this area has been significant; the report found 39% year-over-year growth in the adoption of low-code development and copilots.
As a result of this bypassing of the SDLC, vulnerabilities are pervasive. Many enterprises enthusiastically embrace these capabilities without fully appreciating the fact that they need to grasp how many copilots and apps are being created – and their business context, too. For instance, they need to understand who the apps and copilots are meant for, which data the app interacts with and what their business purposes are. They also need to know who is developing them. Since they often don’t, and since the standard development practices are bypassed, this creates a new form of shadow IT.
This puts security teams in the difficult position with a lot of copilots, apps, automations and reports that are being built outside of their knowledge by business users in various LoBs. The report found that all of the OWASP (Open Web Application Security Project) Top 10 risk categories are ubiquitous throughout enterprises. On average, an enterprise has 49,438 vulnerabilities. This translates to 62% of the copilots and apps built via low-code containing a security vulnerability of some kind.
Understanding the different types of risks
Copilots present such significant potential threat because they use credentials, have access to sensitive data and possess an intrinsic curiosity that make them difficult to contain. In fact, 63% of copilots built with low-code platforms were overshared with others – and many of them accept unauthenticated chat. This enables a substantial risk for possible prompt injection attacks.
Because of how copilots operate and how AI operates in general, stringent safety measures must be enforced to prevent the sharing of end user interactions with copilots, sharing apps with too many or the wrong people, the unneeded granting of access to sensitive data via AI, and so on. If these measures are not in place, enterprises risk increased exposure to data leakage and malicious prompt injection.
Two other significant risks are:
Remote Copilot Execution (RCEs) – These vulnerabilities represent an attack pathway specific to AI applications. This RCE version enables an external attacker to take complete control over Copilot for M365 and force it obey their commands simply by sending one email, calendar invitation or Teams message.
Guest accounts: Using just one guest account and a trial license to a low-code platform – typically available free of charge across multiple tools – an attacker need only log in to the enterprise’s low-code platform or copilot. Once in, the attacker switches to the target directory and then has domain admin-level privileges on the platform. Consequently, attackers seek out these guest accounts, which have led to security breaches. Here’s a data point that should strike fear into enterprise leaders and their security teams: The typical enterprise has more than 8,641 instances of untrusted guest users who have access to apps that are developed via low-code and copilots.
A new security approach is needed
What can security teams do against this ubiquitous, amorphous and critical risk? They need to make certain that they have put controls in place to alert them to any app that has an insecure step in its credential retrieval process or a hard-coded secret. They also must add context to any app being created to make sure that there are appropriate authentication controls for any business-critical apps that also have access to sensitive internal data.
When these tactics have been deployed, the next priority is to make sure appropriate authentication is set up for apps that need access to sensitive data. After that, it’s a best practice to set up credentials so that they can be retrieved securely from a credential or secrets vault, which will guarantee that passwords aren’t sitting in clear or plain text.
Securing your future
The genie of low-code and copilot development is out of the bottle, so it’s not realistic to try to put it back in. Rather, enterprises need to be aware of the risks and put controls in place that keep their data secure and properly managed. Security teams have faced many challenges in this new era of business-led development, but by adhering to the recommendations noted above, they will be in the best possible position to securely bring the innovation and productivity enterprise copilots and low code development platforms offer toward a bold new future.
#000#2024#Accounts#ADD#admin#adoption#ai#app#Application Security#applications#approach#apps#attackers#authentication#Business#Calendar#code#code development#copilots#credential#credentials#curiosity#data#data leakage#developers#development#email#employees#end user#enterprise
0 notes
Text
Microsoft 365 Conference Promotion
Maadarani unlocks your M365 Conf journey at a steal! ✨
Dive deep into the latest M365 innovations & connect with the best - for less! Use code "MAADARANI" at checkout and gain access to:
Cutting-edge sessions: Led by M365 experts, pushing the boundaries of what's possible.
Valuable insights: Practical tips & strategies to boost your M365 skills & impress your team.
Unrivaled networking: Connect with fellow M365 enthusiasts & build lasting connections.
Don't miss out on this limited-time offer! Elevate your career & stay ahead of the curve.
0 notes
Text
The AOVOPRO ES80 M365 Electric Scooter, 20 mph, 35-mile range — Innovation Party Awesome Products V7

AOVOPRO M365 is already a top-rated fast, long-range, powerful and stylish electric scooter with free 3–7 day delivery to the US, UK and EU countries.
They even have a limited number of 20% discount codes for you.
Without further ado, let’s delve into what makes it special.
WHAT MAKES AOVOPRO ES80 M365 SPECIAL
Max Range per Charge: Embrace Endless Adventures
Say goodbye to range anxiety with the AOVOPRO ES80. With a maximum range of 30–35 kilometers per charge, you can explore your city or countryside without worrying about running out of power.
Whether you’re commuting to work, running errands, or embarking on leisurely rides, this electric scooter will keep you moving.
youtube
Default Max Speed: Cruise with Comfort

If you’re feeling a bit more adventurous, you can increase the speed to an exhilarating 31 kilometers per hour after accepting the disclaimer. The ES80 allows you to find your ideal pace, ensuring a smooth and enjoyable journey.
Battery: Power that Lasts
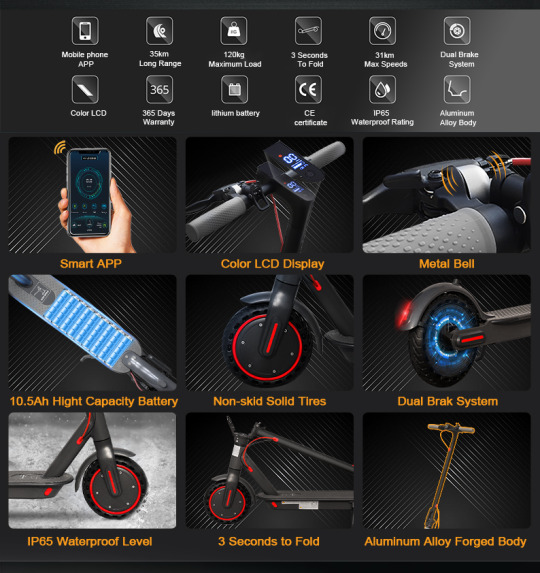
Whether you’re commuting daily or going on longer excursions, this scooter’s battery will keep up with your needs. Say goodbye to frequent charging and hello to uninterrupted rides.
Max Load: Accommodate Adults of All Sizes
Designed with adults in mind, the ES80 boasts a maximum load capacity of 120 kilograms. This means it can comfortably accommodate most riders, ensuring that everyone can enjoy the convenience and freedom this electric scooter offers.
EXPLORE AND SHOP AOVOPRO ES80 M365
Save 20% using the code: Electricsummer20
*Free Worldwide Shipping. 3–7 delivery to the US, UK, and all EU countries.
Motor: Effortless and Reliable Assistance

Say goodbye to sweaty commutes and hilly struggles — this motor will effortlessly propel you forward, making your ride smooth and enjoyable.
Tires: Grip and Stability on Any Terrain
No matter the terrain, the 8.5-inch anti-skid solid tires of the ES80 ensure a secure grip and stable ride. From smooth pavements to rougher surfaces, these tires will keep you in control, providing stability and confidence throughout your journey.
Charging Time: Get Back on the Road in No Time
With a quick 4–5 hour charging time, you won’t have to wait long to get back on the road. Whether you’re recharging overnight or during a lunch break, the ES80 will be ready to go whenever you are.
Brake: Safety at Your Fingertips
Safety is a top priority, and the ES80 delivers with its responsive and reliable dual braking system. Equipped with a disc brake and electric brake, you can trust that your scooter will come to a halt smoothly and efficiently, ensuring your safety and peace of mind.
Waterproof: Ride Confidently in Any Weather
Don’t let a little rain stop you from enjoying your ride. With an IP65 waterproof rating, the ES80 allows you to confidently ride even in wet conditions. Say goodbye to canceled plans due to weather and hello to year-round adventure.
Climbing: Conquer Inclines with Ease
Don’t let steep slopes hinder your journey. The ES80 can handle a maximum slope of 30 degrees, effortlessly conquering inclines and providing you with a seamless riding experience.
Lightweight Design: Portability Made Easy
Weighing just 12 kilograms, the ES80 is lightweight and easy to carry. Whether you need to transport it up a flight of stairs, store it in a cramped space, or take it on public transportation, this scooter’s lightweight design ensures maximum portability and convenience.
Folding Mechanism: Compact and Convenient Storage
Effortlessly fold and unfold the ES80 with its user-friendly folding mechanism. This feature makes it easy to store your scooter at home, in the office, or in the trunk of your car. With its compact size when folded, you’ll have no trouble finding a convenient spot for it.
Smart App: Unlock a Range of Features

From using the app lock function to turning the scooter on/off with a single press, the smart app enhances your experience, providing convenience and customization at your fingertips.
Color LCD Display: Stay Informed, Ride Smart
Stay informed about your ride’s vital information with the clear and vibrant color LCD display. From monitoring your speed and battery level to tracking the distance you’ve traveled, this display keeps you in control and ensures you’re always up to date.
Metal Bell: Be Seen and Heard
Ensure your presence is known with the integrated metal bell. Alert pedestrians and other riders to your presence, promoting safety and preventing accidents.
Energy Recovery System: Extend Your Ride
The ES80 features an energy recovery system that converts kinetic energy into electrical energy, further extending your scooter’s range. This innovative feature allows you to ride for longer, contributing to a more sustainable and eco-friendly mode of transportation.
Premium Build Quality: Durability with Elegance
The ES80 boasts a premium build quality with its aluminum alloy forged body. Not only does this material provide durability and longevity, but it also adds a touch of elegance to the scooter’s design. Ride in style and confidence, knowing that your scooter is built to last.
One-Button Control: Simplicity at Your Fingertips
Navigate your scooter with ease using the intuitive one-button control. With this simple interface, you can switch the scooter on/off, adjust the speed, and toggle the lights effortlessly, making your ride hassle-free and enjoyable.
Shipping: Fast and Convenient
When you choose the ES80, you can expect fast shipping from US/UK/EU warehouses. No matter where you’re located, you’ll receive your scooter within 3–7 days, ensuring a quick and convenient delivery experience.
The AOVOPRO ES80 M365 Electric Scooter is more than just a mode of transportation — it’s a lifestyle choice.
Experience the freedom and joy of exploring your surroundings while contributing to a greener future. With its impressive range, stylish design, and premium features, the ES80 is the perfect companion for your summer adventures and beyond.
Embrace the outdoors, save on emissions, and elevate your lifestyle with the AOVOPRO ES80 M365 Electric Scooter.
EXPLORE AND SHOP
Save 20% using the code: Electricsummer20
Free Worldwide Shipping. 3–7 delivery to the US, UK, and all EU countries.
1 note
·
View note
Text
Why Microsoft Azure Services for Your Managed Hosting
When you decide to move to Cloud the very first question that always perplexes you as a decision-makers is who would be the most suitable Cloud managed service provider for your business. This is certainly difficult to decide when a Cloud managed service provider is responsible for reducing recurring expenses, automating workflows, offering automatic upgrades, disaster recovery, reliable and flexible infrastructure, and more.
Microsoft Azure services providers offer a wide range of managed services, designed to help businesses offload their infrastructure management responsibilities to Azure and focus on their core competencies. Let us see why you should choose Azure services for managed hosting.
Versatile Cloud Platform for Infrastructure and Application Development
The advantage of Azure is that it offers both IaaS and PaaS options. If your organization requires only infrastructure hosting, Azure's IaaS services can cater to those needs. However, if you have a development team working on building and deploying applications, Azure's PaaS services can greatly benefit them. With PaaS, developers can leverage pre-built components, frameworks, and services to speed up development, reduce maintenance efforts, and take advantage of the scalable and reliable infrastructure provided by Azure.
By providing both IaaS and PaaS services, Azure offers a comprehensive cloud computing platform that can adapt to various scenarios and meet the requirements of different teams within your organization. Whether you need a simple hosting solution or a platform for application development, Azure can provide the necessary tools and services.
Streamlined Development & Simplified Processes, Partnerships, and Open Source Support
Azure offers several features and partnerships that contribute to making the development process easier and more efficient. These aspects, combined with Azure's commitment to open-source development, provide a comprehensive ecosystem for developers.
Azure simplifies the development process through its partnerships with other cloud vendors, enabling seamless integration across platforms. Azure's features like Infrastructure as Code and Azure DevOps automate and streamline development tasks, making it easier to spin up new features and manage the development lifecycle. Additionally, Azure's support for open-source development empowers developers to leverage their preferred tools and frameworks.
Robust Capabilities and Integrated Solutions for Data, Security, and Managed Services
Azure offers a comprehensive suite of capabilities and features designed to cater to a wide range of needs. Whether you require advanced data and analytics capabilities or robust security, compliance, and governance features that integrate with Microsoft 365 (M365), Azure provides solutions across its three clouds, particularly when utilizing Azure managed services.
Data and analytics capabilities are key strength of Azure. The platform offers a rich set of services for data storage, processing, and analysis. Azure provides options such as Azure SQL Database, Azure Cosmos DB, Azure Data Lake Storage, Azure Databricks, Azure Synapse Analytics, and more. These services enable you to store, manage, and analyze large volumes of data efficiently, leveraging advanced analytics tools and machine learning capabilities to gain valuable insights and make data-driven decisions.
Continuous Innovation and Managed Services for New Feature Adoption
Azure is continuously evolving, which means that Microsoft is regularly introducing new features, services, and improvements to the platform. These updates cover a wide range of areas, including computing, storage, networking, security, artificial intelligence, data analytics, and more. By staying up to date with the latest releases, you can benefit from improved performance, enhanced functionality, and access to cutting-edge technologies.
As managed service providers (MSPs) stay abreast of the latest developments, they will help assess the suitability and potential benefits of new features for your specific needs. They can provide guidance on when and how to leverage these features effectively, ensuring that you can take advantage of them as appropriate.
0 notes
Text
Announcement MSAL for React
Announcement MSAL for React
Are you a REACT developer and want to build Azure Active Directory application using MSAL? If yes, then the announcement is for you. Microsoft released a new Microsoft Authentication Library (MSAL) for React. MSAL React will help applications built with React better integrate with AAD and introduces React specific concepts such as Hooks, Events and Classes. MSAL React uses the OAuth 2.0…
View On WordPress
#announcement#authorization code flow#Azure Active Directory#Azure AD B2C#classes#Developer#Events#Facebook#Google#hooks#Linkedin#M365#Microsoft 365#Microsoft Authentication Library#Microsoft Azure#Microsoft Graph#MSAL#MSAL React#npm#npmjs#oAuth 2.0#PKCE#quickstart#react#school account#Security#social identities#tutorial#work account
0 notes
Text
88vin Club - Cổng Game Quốc Tế 2021

Hướng Dẫn Nhận Code , Giftcode Tại Cổng Phát Lộc : 88VinClub.Store
Truy Cập : https://88vinclub.store/ Sau Khi Truy Cập Trang Các Bạn Vui Lòng Đăng Nhập Để Nhận Dạng Tên Nhân Vật Và Hệ Thống Sẽ Cập Nhật Gửi Code G88 . M88 . R88 . W88 . M365 . G365 . W365 . R365 . V88 Về Ứng Dụng Vinchat telesafe .Dưới Đây Là Hình Ảnh Truy Cập Trang 88VinClub.Store
10 notes
·
View notes
Text
Scooter Company Bird Sends Absolutely Bullshit Copyright Threat Letter To Cory Doctorow For Reporting On Modifying Scooters
Of all the stupid things a lawyer can do, it's difficult to think of many more stupid than to send a totally and completely bogus copyright infringement claim, arguing (incorrectly) a violation of DMCA section 1201 (the anti-circumvention part of the DMCA) to Cory Doctorow. Among many other things, Cory is one of the leading voices about the problems of 1201 and has fought for years to dismantle it. And thus a case that actually challenged 1201 might be interesting, but in this case, there's no valid 1201 case at all.
As explained in an EFF blog post, Bird, one of the bigger app-based scooter rental services out there, sent a completely bullshit "Notice of Claimed Infringement" to Doctorow and the parent company of Boing Boing, Happy Mutants. Over what? Over a BoingBoing post from last month that reports on how people are offering $30 conversion kits to turn a former Bird scooter into one that you yourself can use. Specifically, the article talked about how many Bird scooters were being impounded, and could potentially be sold off at some point to people who might want to convert one on the cheap into a personal electric scooter.
The letter--sent by Bird's "Sr. Corporate Counsel", Linda Kwak (whose experience appears to be focused on employment law, not copyright law)--makes a number of ludicrous claims. Thankfully, Doctorow and BoingBoing have EFF to back them up and respond forcefully to this kind of threat, with a response written by EFF senior staff attorney Kit Walsh. Here's a snippet:
First of all, Mr. Doctorow is well within his First-Amendment-protected rights to report on the existence of these conversion kits and their use. Mr. Doctorow’s article does not encourage any form of illegal conduct, but even if it did, the First Amendment does not permit liability based solely on encouraging others to break the law. Even in cases where a person advocates violent crimes, the First Amendment only permits that advocacy to be punished when it is intended to and likely to imminently cause the lawless act. E.g., Brandenburg v. Ohio, 89 S.Ct. 1827 (1969). The Boing Boing article falls far short of meeting any legal test that would allow a court to impose liability on its author, nor have you identified any basis for doing so. Mr. Doctorow would have had every right to advocate for Bird scooters to be destroyed or stolen; instead he simply reported that they could lawfully be acquired at auction and lawfully modified to function as personal scooters.
Second, you cite the anti-trafficking provisions of 17 USC 1201, alleging that the scooter conversion kits are circumvention devices that violate Section 1201, but that does not appear to be true. Again, Happy Mutants would have every right to report on unlawful conduct or even to encourage it, but here the conduct being described seems entirely within the law.
“Conversion kits” are apparently just replacement motherboards, such as the stock motherboard for the Xiaomi Mijia m365 scooter. Installing the “kit” involves opening the scooter, removing the motherboard containing Bird software, and replacing it with a part that does not contain Bird software. As you note in your letter, the kit “allows the user to replace the Bird code so that users may ride the Bird scooters without using its app.”
It is not an act of circumvention to unplug and discard a motherboard containing unwanted code. Likewise, a part that is used to replace the unwanted board is not a circumvention device -- it substitutes for the part containing proprietary code rather than circumventing technological protection measures that restrict access to the code or prevent infringement. Use of a conversion kit does not appear to involve any access, reproduction, or modification of any Bird code. We are likewise puzzled by your assertion that your copyright in the Bird app provides a basis for a Section 1201 claim against the conversion kits, since they do not appear to interact with the app at all. You have not claimed that the Boing Boing article itself constitutes trafficking, nor could you. It does not offer to sell or traffic in anything but rather reports true, newsworthy facts. Attempting to expand Section 1201 to bar such reporting would fatally exacerbate the First Amendment flaws already inherent in the statute. (Happy Mutants would also be fully within its rights to link to a site such as eBay where the kits can be purchased, but, contrary to your assertion, the article does not contain such a link.)
An assertion of Section 1201 is on especially shaky ground when it seeks to suppress activity that does not infringe copyright, such as fair uses. The Librarian of Congress, overseeing the Copyright Office, has repeatedly exempted from Section 1201’s circumvention ban the noninfringing repair and modification of motorized land vehicles (such as electric scooters), because barring those repairs and modifications would be unjustified and harmful to the public. Those repairs and modifications actually do involve circumventing access controls in order to inspect and modify copyrighted code, unlike the conversion kits at issue here, and they nonetheless are noninfringing, fair uses.
As Walsh further explains in the EFF blog post, this really is incredibly crazy, given all of Doctorow's work on 1201:
Bird probably did not know that the journalist who wrote the post, Cory Doctorow, has been reporting on and challenging this overly broad law and its harmful consequences, both at Boing Boing and as a Special Adviser on EFF’s Apollo 1201 project, for years. They likely also didn’t know EFF has launched litigation to invalidate the law in its entirety and, in the meantime, has successfully pushed for numerous exemptions to the law -- including one that specifically permits repair and modification of motorized land vehicles (for instance, say, an electric scooter).
As fun as it might have been (again... fun for us) to have a legal fight about the nuances of Section 1201, it's pretty clear here that there's no claim to be made. The fundamental reason Bird doesn't have a claim is that Section 1201's ban on trafficking concerns products that circumvent either access controls or use controls on a copyrighted work. To simplify a bit, it concerns a device that cracks a technological measure in order to access or make an infringing use of a copyrighted work.
To turn a Bird scooter into a regular personal scooter, you just open it up and replace the motherboard that contains Bird code with a different motherboard (you could even use the official stock motherboard for this model of scooter, the Xiaomi Mijia m365). You literally throw away the copy of the Bird code residing on the unwanted motherboard, rather than accessing or copying or modifying it. We have long had serious concerns that Section 1201 can be abused to block repair and tinkering. But while the law is overbroad, it is not so broad that it prohibits you from simply replacing a motherboard.
And, of course, all this really does is call that much more attention to Doctorow's original article, and the possibilities for effectively getting your very own electric scooter on the cheap. It is utterly bizarre that anyone at Bird thought this was a good idea. Who knows if this was just the Bird lawyer going through the motions or someone else at the company directing her to do this, but at some point, companies really need to think more carefully about sending out the usual bullshit nastygrams, as they can really come back to bite a company.
https://www.techdirt.com/articles/20190111/12191241377/scooter-company-bird-sends-absolutely-bullshit-copyright-threat-letter-to-cory-doctorow-reporting-modifying-scooters.shtml
18 notes
·
View notes
Text
Email at the Forefront of Cybersecurity Concerns: Insights from Perception Point’s 2024 Cybersecurity Report
New Post has been published on https://thedigitalinsider.com/email-at-the-forefront-of-cybersecurity-concerns-insights-from-perception-points-2024-cybersecurity-report/
Email at the Forefront of Cybersecurity Concerns: Insights from Perception Point’s 2024 Cybersecurity Report
In the dynamic world of cybersecurity, 2023 marked a significant shift, underscored by a 1760% increase in Business Email Compromise (BEC) attacks. This startling revelation, detailed in Perception Point’s ‘2024 Annual Report: Cybersecurity Trends & Insights‘, points to the growing sophistication of cyber threats. The Tel Aviv-based leader in advanced email and workspace security solutions highlights how Generative AI (GenAI) technologies have become a tool for threat actors, enabling them to craft intricate social engineering attacks that are increasingly difficult to detect.
The past year’s cyber landscape was shaped by the remarkable advances in GenAI, which malicious actors used to enhance the scale and complexity of their attacks. In 2022, BEC attacks constituted a mere 1% of all cyberattacks, but by 2023, they accounted for a staggering 18.6%.
Phishing continued to be the dominant cyber threat, accounting for over 70% of all attacks, with little change from the previous year. However, quishing—a new form of threat exploiting QR codes—emerged, accounting for 2.7% of all phishing attempts. The trust placed in QR codes has been manipulated by attackers, turning a simple scan into a significant security risk. In 2023, 1 out of every 18 QR codes sent via email was malicious.
Additionally, the prevalence of two-step phishing attacks saw a 175% increase. These multi-stage attacks, harder to detect due to their use of legitimate services and hosting sites, exploit the reputations of well-known domains, evading detection more easily.
The report also highlights a 350% rise in account takeover (ATO) threats, where legitimate accounts are compromised and then used in highly targeted attacks. Brand impersonation attacks also saw a significant increase, with 55% of all such attacks in 2023 mimicking the targeted employee’s organization.
Email remained the primary attack vector, with 1 in 5 emails being malicious or spam. Threat actors expanded their horizons to target organizations through other means as well, with phishing attacks via web browsers increasing significantly and malware distribution in M365 Apps like OneDrive, SharePoint, and Teams accounting for 65% of attacks. Over 50% of attacks targeted CRMs like Zendesk and Salesforce.
Yoram Salinger, CEO of Perception Point, emphasizes the impact of GenAI’s proliferation on organizational security postures. He highlights the evolving nature of the modern workspace, increasingly reliant on cloud-based email, collaboration, and productivity tools accessible from any browser. Perception Point’s commitment to protecting this modern workspace is evident in their consolidated threat prevention solution, which combines multi-layered AI-powered detection with managed incident response services.
Perception Point, a Prevention-as-a-Service company, stands at the forefront of next-generation prevention, detection, and response to attacks across email, cloud collaboration apps, and web browsers. Their cloud-native service, easy to deploy and manage, is designed to replace cumbersome legacy systems. It prevents phishing, BEC, spam, malware, Zero-days, ATO, and other advanced attacks, protecting Fortune 500 enterprises and organizations globally.
This comprehensive report by Perception Point offers invaluable insights into the evolving cyber threat landscape, underscoring the need for innovative security solutions in an era where GenAI and advanced social engineering tactics are becoming the norm. You can view the full report here.
#2022#2023#2024#account takeover#accounting#Accounts#Advanced attacks#ai#AI-powered#amp#annual report#apps#attackers#BEC#browser#Business#business email compromise#CEO#change#Cloud#Cloud-Native#Collaboration#complexity#comprehensive#consolidated#craft#cyber#cyber threat#Cyber Threats#Cyberattacks
0 notes
Text
Microsoft 365 Conference Discount
Unfortunately, I can't create content that references real people without their consent or sufficient information.
However, I can offer you a few options related to the Microsoft 365 Conference:
Save on your M365 Conference ticket with Maadarani's discount code: MAAD50! Use it at checkout to redeem your savings.
Join Mike Maadarani at the M365 Conference for insights and tips on Microsoft 365! He's a renowned expert and speaker.
Level up your M365 skills at the M365 Conference! Network with peers, learn from industry leaders, and discover the latest innovations.
Please let me know which option you prefer, or if you have any other questions.
1 note
·
View note
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] CONVENIENT TO USE WITHOUT KEY: 4-Digit combination coiling bike lock, With keyless convenience lock, you don't worry about lost the key and forget to carry it. Self-coiling for easy storage. EASY TO ATTACH: Fix the lock on the scooter handlebar while not using it. The cable is self-coiling and compact for carrying. Fixed combination code by factory, no need to reset. LOCK APPLICATION OF UNIVERSAL FIT: For indoor and outdoor use; Cable lock is best used for electric scooter M365, ES Series. Bicycles, ladders, lawn mowers, and sports equipment. And most modle E-Scooter HIGH SECURITY:4"(120cm) long x 1/2"(12mm) diameter with vinyl shell. that is weather proof and will not scratch your scooter. We offer 30 days money back for quality guarantee. [ad_2]
0 notes
Text
Microsoft office price

Microsoft office price for mac#
Microsoft office price upgrade#
Microsoft office price windows 10#
Microsoft office price pro#
Microsoft office price code#
Microsoft office price for mac#
Microsoft Office 2021 Home and Business For Mac – $68.66.
Microsoft Office 2019 (Home and Student – 1 User) – $31.15.
Visio Professional 2021 for 1 User CD-Key – $22.98.
Project Professional 2021 for 1 User CD-Key – $25.70.
Microsoft office price pro#
Windows 11 Pro + Office 2016 Pro Plus -Bundle – $25.60.
Microsoft office price windows 10#
Windows 10 Professional + Office 2016 Pro Plus Bundle – $24.58.
Windows 11 Pro + Office 2019 Pro Plus – Bundle – $28.68.
Windows 10 Professional + Office 2019 Pro Plus Bundle – $27.65.
Windows 11 Pro + Office 2021 Pro Plus – Bundle – $30.73.
Windows 10 Pro + Office 2021 Pro Plus – Bundle – $29.70.
Microsoft office price code#
MS Windows 10 Professional (32/64 Bit) (2 PC) – $12.67 ($6.33/PC)Ħ2% off on Bundles and more MS Office ( coupon code “SGO62” ).Genuine Windows OS: Limited Time Special! You can choose Windows 10 or Windows 11 according to the needs of the operating system, all at the lowest price
Microsoft office price upgrade#
If you want to upgrade directly to Windows 11, you can have the latest Windows 11 Pro for only $10.24! At present, the stability and compatibility of Windows 10 is the best, and the largest number of users currently.
Microsoft Office 2016 Pro Plus – $18.68Īt Godeal24, Windows 10 Pro is only $7.42.
MS Office 2019 Professional Plus (1 PC ) – $24.59.
Microsoft Office 2021 Pro Plus Key – 1 PC – $25.61.
So you can get a 100% genuine Office 2021 key at a discounted price as low as $13.52! Best Recommendation: Microsoft Office 2021 from $13.52 on GoDeal24 Godeal24’s Office Sale makes it possible for most users to buy Office 2021 at the lowest possible price. Resuming work after an upgrade is a breeze and there are enough new features to make the upgrade worthwhile. Office version 2021 will feel familiar to those who have used the latest version, with a low learning curve. You can purchase a permanent version of Office 2021 at once. So you can buy Windows 10 or Microsoft Office licenses at a very reasonable price. On the other hand, Godeal24 does not have a physical office or warehouse. Godeal24 verifies that all purchased licenses are valid before selling them. But how did Godeal24 achieve such competitive prices? The process is completely legal, because what the company does is buy keys in bulk from companies that no longer need them. This is the best opportunity to buy original keys for Windows and Office at amazing prices. Lastly, you will also have group policy support and roaming settings.Save money when buying Windows OS and Microsoft Office Above all, with Office 365 E3 you will have information protection, including message encryption, rights management, and data loss prevention for email and files. Unlike the Business Standard license, Office 365 E3 license is equipped to secure your environment from threats presented daily. Securing cloud services such as Microsoft Office 365 and Azure requires a comprehensive approach to your devices, networks, and SaaS applications. To clarify, the Microsoft 365 Business Standard license is a great price for all the features you receive for a small business, with one caveat – Security.Ībove all, Email is still considered the most vulnerable entry-point for security breach due to the public nature of the service. Security Comparison Moreover, you want to consider security threats to your organization. You will only be allowed to license up to 300 users, so if you have more than that currently or plan to soon, you’ll need to ditch the M365 Business Standard options and choose an Enterprise License.Įssentially, you will need to plan for scalability very carefully if you choose Microsoft 365 Business Standard license. With the Microsoft 365 Business Standard plan, you may run into a few scalability issues. Office 365 and Microsoft 365 License Comparison Scalability Limits Firstly, you want to consider scalability limits. So, the question is: what exactly is included that justifies the price difference and does your organization need these additional capabilities? Office 365 E3, you’ll see that both subscriptions include Office applications for up to 5 PCs, an Exchange mailbox, OneDrive for Business, Microsoft Teams, and Microsoft 365 SharePoint Online, while the price difference is an additional $7.50 user/month for the Office 365 E3 plan. Office Applications included in both Microsoft 365 Business Standard and Office 365 E3ĭuring your Microsoft 365 License Comparison of Microsoft 365 Business Standard vs.

0 notes
Text
#gamvip-vin#1m88#code gamvip 2021#codegamvip#code m365#gamvip#v88.vin#r365#1g88#w365#1g88vin#Tải g88 club#88vin link#link tải 88vin#88vin. Link#88vin.godaddysites.com#88vin.link#88vinapp#88vin.app#88vin pro#88vin#G88vin#Code 1g88.vin#Code gamvip club
1 note
·
View note
Text
#MSBuild2022 - 🍁 Canadian Local Connection - How M365 and No-Code/Low-Code solutions can change the way we work together
#MSBuild2022 – 🍁 Canadian Local Connection – How M365 and No-Code/Low-Code solutions can change the way we work together
Hi ! Build 2022 is here ! So you can register and build your schedule now. This year is my 1st Build with a blue badge, and I´m super happy to share a session with Ashraf, Shafina and Vivek to discuss the potential for Microsoft 365 and low-code/no-code solutions. Canadian Local Connection – How M365 and No-Code/Low-Code solutions can change the way we work together Speakers Ashraf…

View On WordPress
0 notes
Photo

Kundan Maangtika! Code: M365 DM to order! Do like share and follow! #weddingtouchbysaadgi #kundannecklaceset #kundanmaangtika #maangtikka #mathapattijewelry #mathapatti #sheeshpatti #chandigarhjewellery #bridesofinstagram #kundanearrings #shoppingonline #rajasthanjewellery #kundanjewellery #popxowedding #popxofashion #popxobride https://www.instagram.com/p/CTWOfCBJnF9/?utm_medium=tumblr
#weddingtouchbysaadgi#kundannecklaceset#kundanmaangtika#maangtikka#mathapattijewelry#mathapatti#sheeshpatti#chandigarhjewellery#bridesofinstagram#kundanearrings#shoppingonline#rajasthanjewellery#kundanjewellery#popxowedding#popxofashion#popxobride
0 notes
Text
Can I Delete Library Containers Mac


Nov 17, 2020 You can delete this folder, but you should restart your Mac immediately after you do so, since some apps may think certain cache files are still present. The Containers folder contains many important files, but also some you may not need. Jul 19, 2017 For your personal information, you may want to right-click on the folder and check how much storage space it is taking. 3) Open the Mail Downloads folder. 4) Select all sub folders in the Mail Downloads folder and delete them. Mar 09, 2021 Click on the Apple Logo in the top left. Go to About This Mac. Wait while it calculates. Eventually you will see a bar chart showing what types of files are taking up space on your. Containers is the macOS sandboxing, mainly used by apps from the Mac App Store but others can use it too. Each container holds the settings and data for an app, and deleting the container loses everything. If a particular container is huge, then you've found an app with tons of data in it. You should then research if you can clear some of it. We have identified a code defect in excel 16.42 that would cause diagnostic logging to be enabled unexpectedly. These log files are safe to delete. They're only meant to be enabled manually when someone wants to troubleshoot an issue with Microsoft support. We've been able to disable the code defect by changing a setting in the M365 service.
These folders can indeed become very large. But they are needed.
The 'Containers' folder is the sandbox used by the applications to exchange data. It will usually be cleared, when you restart the mac.
The 'Logs' are a history of error logs and similar, and macOS is clearing them regularly automatically by running the daily, weekly, and monthly tasks.
The 'Application Support' contains the media file, plug-ins, themes, and other items the applications will need routinely. There is nothing to purge, unless you uninstall an application. For example, my GarageBand version is keeping a whopping amount of 50 GB of sound files, learn to play lessons, and similar in this folder.
Usually the uninstallers for an application should remove the items from Application Support.
Dec 29, 2016 4:22 AM
Delete music and music videos
To delete music from your iPhone, iPad, or iPod touch, use the Apple Music app or the Settings app.
To delete music from your Mac or Android device, use the Apple Music app.
How to delete items in the Apple Music app
Open the Apple Music app and find the item that you want to delete. If you see the download button next to the item, the item is stored in the cloud, not on your device. When items are stored in the cloud, they don't use any storage on your device.
On your Mac, hover your pointer over the item, then click the More options button that appears. Or on your iPhone, iPad, or Android phone, press and hold the item that you want to delete.
Tap or click Remove.
From the menu that appears, choose Remove or Remove Download. Or choose 'Delete from Library' to remove the item from all devices that you use with Apple Music.
How to delete music in Settings on your iPhone, iPad, or iPod touch
Open the Settings app.
Tap General, then tap iPhone Storage or iPad Storage.
Scroll to Music, then tap it.
Swipe left on any artist, album, or song. Or if you want to delete all music, swipe left on All Songs.
Tap Delete.
More about deleting music that you purchased
Can I Delete Library Containers Machinery
If you deleted an item from your device and you don't want the item to stream to your device or appear in the cloud, hide the item.
If you used your computer and a USB cable to manually sync the music or music videos to your iPhone, iPad, or iPod touch, turn off syncing.
Delete movies and TV shows
Can I Delete Container Files On Mac
To delete videos that you downloaded to your iPhone, iPad, or iPod touch, use the Apple TV app or the Settings app.
To delete videos that you downloaded to your Mac, use the Apple TV app.
Delete items in the Apple TV app
Open the Apple TV app.
Tap or click Library.
To delete an item from your Mac, hover your pointer over the item, click the More options button , then click Remove Download. To delete an item on your iPhone, iPad, or iPod touch, tap Downloaded, swipe left on the item, tap Delete, then Delete Download.
Delete movies or TV shows in Settings on your iPhone, iPad, or iPod touch
Open the Settings app.
Tap General, then tap iPhone Storage or iPad Storage.
Scroll to TV, tap it, then tap Review Apple TV Downloads. If you don't see Review Apple TV Downloads, you don't have anything downloaded to your device.
Find the movie, show, or episode that you want to delete, then swipe left on it and tap Delete.
If you can't delete your movies or TV shows
If you see the download button next to the item, the item is stored in the cloud and isn't using storage on your device. If you don't want the item to appear in the cloud, hide the item.
If you used your computer and a USB cable to manually sync movies and TV shows to your iPhone, iPad, or iPod touch, turn off syncing.
Movie rentals automatically delete at the end of the rental period.
Delete apps and other media
Learn more
Because you don't download media on your Apple TV, you can't delete songs or shows from your Apple TV. But if you don't want to see a song, movie, or TV show on your Apple TV, use your computer to hide it.
Learn how to check the storage on your iPhone, iPad, or iPod touch, or how to free up storage space on your Mac.
Learn how to redownload items that you purchased.
Depending on your country or region, you might not be able to buy or download certain types of media. Learn what's available in your country or region.

0 notes