#Application Security
Text
Threats: What Every Engineer Should Learn From Star Wars
Okay, I know this isn't a general purpose security topic, but hey, I've seen a lot of Tumblr users admit to being in software dev over the years ;) Adam Shostack, well known in the security space on a variety of topics, particularly threat modeling, has a new book out. The twist? Looking at the concept of threats to software through the lens of Star Wars.
I haven't read this one myself yet so no book review right now, but it looks fun!
6 notes
·
View notes
Text
Guarding Against Threats: Advanced Techniques for Application Security Testing
Explore advanced techniques in #applicationsecuritytesting to safeguard against evolving cyber threats and ensure the integrity of your software infrastructure.

#application security#application security testing#penetration testing services#cybersecuritytestingsolutions#cyber security#application testing
0 notes
Text
What are the Main Types of Security Vulnerabilities When Working With Open Source Components? - Technology Org
New Post has been published on https://thedigitalinsider.com/what-are-the-main-types-of-security-vulnerabilities-when-working-with-open-source-components-technology-org/
What are the Main Types of Security Vulnerabilities When Working With Open Source Components? - Technology Org
The vulnerabilities inherent in open-source components warrant due consideration, given their potential threats. As we work to unravel the primary security risks associated with open-source components, particularly in software development, we will present viable solutions for mitigating these risks. While open-source software can benefit the rapid development of systems, it also exposes projects to innate security risks. This is true, particularly if they are managed incorrectly. A detailed understanding of the security vulnerabilities is sacrosanct.
Artificial intelligence (AI) – artistic interpretation. Image credit: Pixabay, free license
Nowadays, open-source components, as part of software development, are indispensable. Widespread use has led to increased exposure to security flaws. Many instances exist, notably the Heartbleed bug in OpenSSL and the gaping vulnerabilities in ApacheLog4J. Both of these examples highlight the critical nature of safe and secure operations with open-source libraries. These vulnerabilities compromised millions of systems worldwide, ensuring that vigilance becomes a top priority within the open-source ecosystem.
For example, Synopsys Cybersecurity Research Centre discovered that 84% of companies are vulnerable to open-source code in their systems. This is especially true with JavaScript – the most widely used code framework. The report was based on 1700 audits and 17 industries globally, and it revealed that at least one known open-source vulnerability existed in the code bases. That statistic was 4% higher than the previous year.
Unknown Source Code Quality
Quality is not a blanket standard. It varies between systems, processes, and software applications. Therefore, the quality of open-source code varies widely. Without thorough vetting, it can be disingenuous to incorporate open-source components with poorly written code, unoptimized code, or gaping holes in the security infrastructure. Setting a standard, raising the benchmark of excellence, and enforcing compliance across the board is imperative.
Risks Associated with Licensing
One has to walk a fine line between understanding security vulnerabilities, and the legal aspects that may impact the viability and sustainability of a project. License risks are not a direct security threat, but misuse or abuse of open-source licenses can result in legal challenges and disputes. These will indirectly impact the security of projects underway.
Insecure Dependency Risk
Many open-source projects rely on various open-source frameworks and libraries. As expected, the absence of standards can result in introduced vulnerabilities. To maintain excellence, regular updates are imperative. By the same token, all security-related issues must be promptly addressed and corrected.
Ineffectual Security Practices in Development
The design and development stage of open-source software and projects is often mired in security practices. This is especially true if these projects do not follow rigorous security protocols. This can lead to clearing vulnerabilities, including cross-site scripting (XSS), SQL injections, or even cross-site request forgery (CSRF). If any of these, where similar vulnerabilities are introduced into the open source projects, they can pose tremendous challenges.
Insufficient Documentation and Updating
Open source components invariably suffer from inadequate documentation vis-a-vis security practices. Similarly, they may lack timely updates for known vulnerabilities. These loopholes present gateways for nefarious actors, allowing infiltration and disruption of systems. Once exposed, the open-source software is highly vulnerable to attack. Security flaws must be identified, addressed, and corrected as quickly as possible.
Fortunately, the features and benefits of software security tools like Checkmarx Static Application Security Testing (SAST) can provide relief for these exigencies. Companies no longer have to choose between scanning code quickly for security vulnerabilities and completing a thorough review of the open-source components. SAST offers a viable solution in terms of comprehensive security oversight and rapid assessment during developmental processes.
The key features of such breakthrough technology include a mix of elements, notably:
The best fix location
Rapid scanning for vulnerabilities
Ability to scan uncompiled open-source code
Artificial Intelligence query builder and security
Full support in multiple languages and across frameworks
Viewed in perspective, such solutions place the developers in control by reducing noise and finalizing secure code in the software and systems. A credible and trusted security solution makes application development efficient and secure. This balances the need for speed and security. Since it’s also developer-friendly, it easily integrates into work environments and with tools developers already use.
To the uninitiated, these types of tech solutions used for identifying security vulnerabilities, notably open-source components, are akin to using tools and resources that can rapidly identify errors and suggest a best-practice methodology to improve material based on relevance. That’s precisely what top-tier SAST does for software development. It secures code, ramps up the pace of development, and identifies problems as efficiently and effectively as possible.
#ai#application development#Application Security#applications#artificial#Artificial Intelligence#assessment#bases#benchmark#board#bug#code#Companies#compliance#comprehensive#cross-site scripting#cybersecurity#Design#Developer#developers#development#disruption#documentation#Features#framework#Full#gateways#impact#Industries#Infrastructure
0 notes
Text
Check out my recent blog post, "Navigating the Cloud: Addressing Top Security Concerns in Cloud Computing."
0 notes
Text
rock around the security flaw
youtube
dual life - rock and security flaws
0 notes
Text
Continuously Scan Code for Vulnerabilities with Built-in Security Tools
<h2>Leveraging Software Vulnerability Scanning</h2>
<p>Software vulnerability scanners have been used for some time to detect exploits hackers might use during the development process. Traditionally, security teams would run scans after developers completed their work, often returning code to address known issues. Currently, scanning is incorporated earlier in the development cycle and continuous integration (CI) workflows. However, most organizations must customize automation to integrate scanning within their CI tools.</p>
<p>A recent update now provides built-in scanning that automatically runs as part of the CI process. You can configure scanning for individual code repositories. Each time code is pushed to a repository, a scan will run to identify vulnerabilities. Scan results can then be viewed within your account.</p>
<h3>Setting Up Scanning</h3>
<p>Enabling scanning is simple - just turn it on since it's disabled by default. You can start with smaller repositories and expand usage over time across your organization. Or disable scanning for repositories no longer under active development. Once enabled, each code push will trigger an automatic scan.</p>
<h3>Reviewing Scan Results</h3>
<p>After a scan completes, results can be found on the repository page. A summary shows high, medium, and low issues found across scans. Selecting a specific version reveals details for that scan, including a total vulnerability count.</p>
<p>Issues are organized by severity, with higher risks upfront. Same-severity issues are ordered by their Common Vulnerability Scoring System (CVSS) scores, which quantify severity levels. Details include the Common Vulnerabilities and Exposures (CVE) identifier and affected package name/version. The "Fixed In" column notes later versions addressing a vulnerability. Selecting provides additional information on Snyk's site.</p>
<p>Take time to review scan results as part of your development and security workflows. This helps ensure code quality and protects users from known issues. Let me know if any part of the process or results need clarification.
0 notes
Text
Cloud Access Security Broker Market Size to Reach USD 37.2 billion by 2031
According to a new report published by Allied Market Research, titled, “Cloud Access Security Broker Market,” The Cloud Access Security Broker Market Size was at $6.8 billion in 2021, and is estimated to reach $37.2 billion by 2031, growing at a CAGR of 18.8% from 2022 to 2031.
A cloud access security broker is a security policy enforcement point positioned between enterprise users and cloud service providers. CASBs provide flexible enterprise solutions that help ensure cloud app security across authorized & unauthorized applications and managed (and unmanaged devices). These flexible enterprise solutions can combine multiple different security policies, from authentication and credential mapping to encryption, malware detection, and others. Furthermore, key factors that drive the growth of the cloud access security broker market include growing demand for work-from-home and remote working policies during the period of the COVID-19 pandemic aided in propelling the demand for cloud and security solutions, hence empowering the growth of the cloud access security broker industry. However, higher installation costs and maintenance challenges of cloud access security broker platforms can hamper the cloud access security broker market forecast. On the contrary, the integration of advanced technologies such as machine learning and data analytics with cloud access security broker solutions suites is expected to offer remunerative opportunities for the expansion of the cloud access security broker industry during the forecast period.
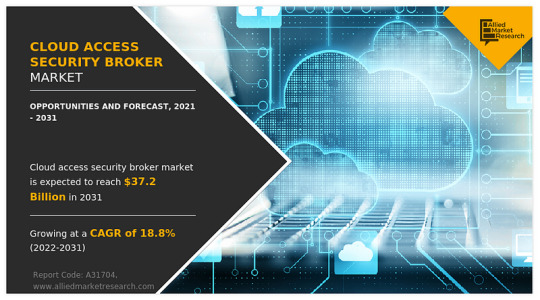
On the basis of enterprise size, the large enterprise segment dominated the overall cloud access security broker market in 2021 and is expected to continue this trend during the forecast period. This is attributed to the complex security requirements of various large corporations needing custom management solutions. However, the SMEs segment is expected to witness the highest growth owing to their growing technological investments and growing innovation, which is expected to further fuel the growth of the global CASB market.
With effective risk and compliance solutions, business enterprises and organizations can ensure that their cloud applications are following industry and regulatory guidelines in various regions, without having to actively dedicate their time to researching the local policies of every region and cloud platform they are operating from. Moreover, cloud risk and compliance management solutions are further divided into policy management, compliance management, audit management, incident management, risk management, and other solutions.
Depending on the industry vertical, the IT and telecom segment dominated the cloud access security broker market share in 2021, and is expected to continue this trend during the forecast period owing to the growing cloud participation of IT and telecom sector companies, incentivizing major businesses of the sector to invest in effective cloud access security broker solutions for their organization. However, the healthcare segment is expected to witness the highest growth in the upcoming years, owing to the rising security standards and government regulatory policies being implemented in the sector.
Region wise, the cloud access security broker market was dominated by North America in 2021, and is expected to retain its position during the forecast period, owing to its highly advanced technology sector which is expected to drive the market for cloud access security broker within the region during the forecast period. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to its growing digital capabilities and a highly competitive market space, which is anticipated to fuel the cloud access security broker market growth in the region in the coming few years.
Inquiry Before Buying: https://www.alliedmarketresearch.com/purchase-enquiry/32154
The alarming increase in COVID-19 cases has compelled many businesses and their employees to adjust to remote working and work-from-home standards, which in turn fueled the adoption of cloud access security broker solutions during the period. Moreover, with the outbreak of COVID-19, businesses had to secure their IT and network assets from cyber threats and data breaches. Moreover, the growing demand for cloud and security during the period drove the demand for the CASB market.
KEY FINDINGS OF THE STUDY
By enterprise size, the large enterprise segment accounted for the largest cloud access security broker market share in 2021.
By region, North America generated the highest revenue in 2021.
By application area, the data security segment generated the highest revenue in 2021.
The key players profiled in the cloud access security broker market analysis are Broadcom Inc., Cisco Systems, Inc., iboss Cybersecurity, Lookout, Microsoft Corporation, Netskope, Palo Alto Networks Inc, Proofpoint Inc, Skyhigh Networks, and Zscaler, Inc. These players have adopted various strategies to increase their market penetration and strengthen their position in the industry and CASB Market Share.
About Us:
Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Portland, Oregon. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of “Market Research Reports Insights” and “Business Intelligence Solutions.” AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
Contact Us:
David Correa
1209 Orange Street
Corporation Trust Center
Wilmington
New Castle
Delaware 19801
USA Int’l: +1–503–894–6022
Toll Free: +1–800–792–5285
Fax: +1–800–792–5285
#Cloud Access Security Broker Market#Cloud Access Security Broker Industry#Cloud Access Security Broker#Governance#Risk#and Compliance#Data Security#Application Security
0 notes
Text
youtube
Tips for Secure Code Review | CybersecurityTv
Secure code review is a crucial part of the software development lifecycle aimed at identifying and mitigating security vulnerabilities in code. It involves manually examining the source code for potential security issues.
#code review#code review best practices#code review tips#code reviews#CybersecurityTV#business news#stock market#cybersecurity#cybersecurity tv#application security#secure code review#secure coding#security#secure code warrior#secure code#secure code review tutorial#secure code video#developer security#developer skills#applications security#software security#developer training#skills development#appsec programs#CybersecurityTv#Youtube
0 notes
Text
Why Application Security is Important in Ghana 2023

Insist on the importance of robust security measures:
Ghana is awed by technology and digital advancements in a time that is rapidly evolving in technology. A better understanding of security in applications is becoming increasingly vital as the country grows increasingly dependent upon technology. This blog reviews the essential part that application security is playing in safeguarding Ghana's future digital.
Ghana's Changing Cyber Threat Environment:
Cyberattacks have been increasing significantly in Ghana across a variety of areas. The vulnerabilities are often used by hackers and malicious actors, which pose serious risks for both businesses and individuals. This highlights the urgent need for robust security measures in applications.
The Importance of Ghana's Application Security:
The most important security measure against cyber-attacks is the security of your application. Financial losses, data breaches as well as reputational harm are just a few examples of the negative outcomes that be the result of ignoring security measures. Security for applications should be more stressed for Ghana's digital transformation to achieve its goals.
Top Ghanaian Application Security Risks:
Applications operating in Ghana are susceptible to numerous common security vulnerabilities. This could include poor data encryption, obsolete software, or insufficient security processes for authentication. To ensure that security breaches do not occur again it is vital to take action on these threats early.
Implementing Strong Security Measures for Application into Practice.
Businesses must take preventative steps to ensure the robust security of applications. To protect digital assets, it is necessary to put the right access restrictions in place as well as regularly upgrading software and performing thorough security assessments.
The Function of Organisations and the Government in Promoting Application Security:
Everyone has a responsibility to enhance the security of applications. To ensure that security standards are adopted and made be made available to the public and acquainted with by the Ghanaian authorities and other organizations need to cooperate. campaigns to educate the public about cybersecurity concerns, for instance, will help in creating an environment that is safe for online use.
Ghana's Future Application Security:
Security of applications is an ever-changing field. Utilizing cutting-edge technologies such as machine learning and artificial intelligence aids in identifying and reducing the risk of threats in the coming. To stay the pace of cyber adversaries Continuous improvement and adaptation to new challenges are crucial.
Conclusion:
As part of Ghana's digital transformation security of applications is of paramount importance. To ensure a secure and efficient digital environment it is essential to secure digital assets and sensitive personal information. We can make an advanced secure, prosperous, and secure Ghana when we cooperate.
#Application Security#Application Security Risks in Ghana#Importance of Application Security in Ghana
0 notes
Link
NoSQL injection is a type of web application security vulnerability that targets non-relational databases. This article will explain what it is, how it works, and offer preventative measures to keep your data safe. By following best practices such as input validation and parameterized queries, you can minimize the risk of NoSQL injection attacks and protect your organization's valuable information.
#sqlinjection#sqli#nosqlinjection#web application security#vulnerability#injectionattacks#Application Security
0 notes
Text
youtube
Tips for Secure Code Review | CybersecurityTv
Secure code review is a very critical but complex process. Not many have experience on how to get started with reviewing the code. In this episode, I have attempted to simplify the process and educate on what you will need to get started, and how you should approach the code review with the checklist. I hope this will be useful to many security professionals.
#code review#code review best practices#code review tips#code reviews#CybersecurityTV#business news#stock market#cybersecurity#cybersecurity tv#application security#secure code review#secure coding#security#secure code warrior#secure code#secure code review tutorial#secure code video#developer security#developer skills#applications security#software security#developer training#skills development#appsec programs#Youtube
0 notes
Text
0 notes
Text
Emerging trends: How to protect your Software Defined Vehicle - CyberTalk
New Post has been published on https://thedigitalinsider.com/emerging-trends-how-to-protect-your-software-defined-vehicle-cybertalk/
Emerging trends: How to protect your Software Defined Vehicle - CyberTalk


Micki Boland is a global cyber security warrior and evangelist with Check Point’s Office of the CTO. Micki has over 20 years in ICT, cyber security, emerging technology, and innovation. Micki’s focus is helping customers, system integrators, and service providers reduce risk through the adoption of emerging cyber security technologies. Micki is an ISC2 CISSP and holds a Master of Science in Technology Commercialization from the University of Texas at Austin, and an MBA with a global security concentration from East Carolina University.
In this highly informative Cyber Talk interview, Check Point expert Micki Boland provides an analysis of Software Defined Vehicles, describing their advantages and flaws, along with actionable security best practices that can keep software safe.
Help our readers understand what benefits the Internet Connected Software Defined Vehicle provides to drivers, automakers and public transportation systems:
For a variety of stakeholders, the continued development of connected vehicles offers several key benefits. I’ll briefly outline them below:
1. Driver’s perspective:
Improved driving experience by optimizing routes.
Enhanced personal safety through real-time information about road hazards, construction zones, and weather-related dangers.
Access to rapid emergency services and roadside assistance on demand.
2. Vehicle manufacturer’s perspective:
Ability to offer road hazard services and monitor vehicle telemetry data.
Delivery of software updates for infotainment and onboard systems.
Monitoring of vehicle health and providing consumers with access to vehicle statistics.
Enhances vehicle safety with features like crash avoidance systems.
3. Public transportation systems and public safety:
Communication with intelligent transportation systems to improve infrastructure.
Integration with smart city infrastructure to enhance public safety and reduce traffic-related fatalities.
Connected vehicles are not just a concept; they are a reality. Many vehicles already transmit telemetry data to auto makers and third parties, allowing for software updates and remote monitoring. Additionally, across the globe, efforts are underway to establish communication between vehicles and traffic management systems, contributing to the development of smart cities.
Is my Software Defined Vehicle vulnerable to hijacking, vehicle theft and the hacking of systems and software? Is it also capable of invading my privacy?
Threat actors are actively seeking to hijack core system functions in order to steal cars. You may have seen recent media reports about two auto manufacturers susceptible to hijacking via the vehicle USB port. This is a TikTok challenge and has resulted in vehicle thefts and crash deaths. One manufacturer is offering financial compensation to owners suffering from vehicle theft.
It does not stop there. Sam Curry, a web application security researcher, published fascinating results in a January 2023 report (here). Sam and team found many automotive vulnerabilities related to everything from the telematic (telemetry) platforms, automotive APIs and infrastructure, including cloud infrastructure and DevOps platforms, customer accounts, and the vehicles themselves. Hackers have breached Tesla infotainment systems and even injected code into vehicle headlights!
Attacking the vehicle has long been the subject of hacker conferences. In real life, hacks range from manipulating the vehicle: unlocking it, engine start/stop, flashing headlights, finding vehicle location by VIN number to track vehicle, hijacking the vehicle owner’s online account, hacking telemetry APIs to stealing data. Additionally, commercial fleet management platforms have been the subject of hacks that exploit vulnerabilities in the web and that exploit vulnerabilities in the APIs hosting these applications.
Hackers inject code into vehicle headlights: https://www.thedrive.com/news/shadetree-hackers-are-stealing-cars-by-injecting-code-into-headlight-wiring
Hackers breached Tesla Infotainment system: https://www.securityweek.com/tesla-hacked-twice-at-pwn2own-exploit-contest/
At present, why aren’t Internet Connected Software Defined Vehicles sufficiently secure?
Securing connected vehicles is a critical concern for the cyber security industry, auto makers and suppliers, third party fleet management providers, 5G network providers, and 5G device makers — all of which are involved in various aspects of the Internet Connected Software Defined Vehicle ecosystem. To tackle this multifaceted challenge, the automotive industry is taking a comprehensive approach, with a focus on cyber security, standards, architecture, communication protocols, and the perspectives of auto manufacturers.
Where are we really when it comes to Software Defined Vehicle cyber security?
1. Cyber security focus:
The U.S. places significant emphasis on Software Defined Vehicle cyber security, with the automotive sector and its partners actively engaged.
Events like the Annual Automotive Cybersecurity Detroit Conference bring together key industry stakeholders, including manufacturers, government bodies, standards organizations, and Tier 1 suppliers.
2. Automotive standards for cyber security for the lifecycle of Software Defined Vehicles:
ISO/SAE provides essential standards for cyber security engineering in road vehicles.
ISO/SAE 21434:2021 offers a comprehensive framework for managing cyber security risks throughout the vehicle lifecycle, from concept to decommissioning.
3. Auto maker perspectives:
Auto manufacturers face complex challenges in ensuring Internet Connected Software Defined Vehicle safety, cyber security, and privacy throughout a vehicle’s lifecycle.
Key considerations include evolving threats, increased connectivity, complex software ecosystems, Over The Air (OTA) updates, telematics, and data privacy.
What are the remaining challenges in this dynamic and complex systems?
1. Evolving threat landscape: To protect people from evolving vehicle threats, we must continually evolve threat prevention initiatives, which can be tough.
2. Increasing connectivity: Extensive vehicle connectivity expands the attack surface, requiring robust security measures at all entry points.
3. Complex software ecosystem: Managing and securing diverse software components in modern vehicles is essential to prevent vulnerabilities and compatibility issues.
4. OTA updates and patch management: Secure delivery and installation of OTA updates necessitate establishing secure channels and ensuring update authenticity and integrity.
5. Software defined vehicles: The concept of Software Defined Vehicles introduces further security considerations in regards to safeguarding software integrity; not only for auto makers, but also for third party providers of infotainment, telemetry, mapping software, etc.
6. Telematics and data privacy: Telematics systems raise privacy concerns, demanding secure data handling and transmission.
7. Collaboration and standards: Industry-wide collaboration and standards are crucial to effectively address Internet Connected Software Defined Vehicle cyber security complexities and challenges.
Addressing these complexities requires continuous investment in cyber security research, rigorous testing, partnerships with experts, and adherence to industry best practices to ensure the safety, security, and privacy of Internet Connected Software Defined Vehicles.
Can you explain Over The Air (OTA) updates for Software Defined Vehicles?
The hallmark feature of a Software Defined Vehicle is the capacity for Over The Air (OTA) updates. OTA updates are essential for keeping the vehicle’s software up-to-date (similar to patch management for computer systems). These updates are facilitated through the vehicle’s Vehicle Identification Number (VIN) and are applicable to both traditional and electric vehicles.
They are delivered in various ways, including through embedded 5G or tethering with the owner’s mobile device. OTA updates encompass infotainment system enhancements, security updates, feature improvements, and system fixes. Communication during OTA transactions involves data exchange between the vehicle, the auto manufacturer, and third parties, and integration with the vehicle owner’s mobile application and customer web portal.
Can you provide some recommendations to help protect my Internet Connected Software Defined Vehicle?
You can take steps to dramatically reduce the risk to your Software Defined Vehicle as it relates to safety, security, and privacy.
1. Protect the mobile devices connecting to your Software Defined Vehicle with a mobile threat prevention tool, like Check Point Harmony Mobile. If you are connecting your mobile device to your Software Defined Vehicle, you need good mobile threat prevention to block malicious applications, smishing, malicious links, and to defend against man-in-the-middle attacks. And be sure to extend mobile threat prevention to any devices connecting to your 5G mobile WiFi hotspot and/or your vehicle’s embedded 5G mobile WiFi hotspot.
2. Conduct a thorough review your security and privacy settings for your Software Defined Vehicle. Typically, this is done from your vehicle’s command center, mobile application, and online vehicle portal. Understand security and privacy settings, as well as the cadence for security and privacy-related software updates. Limit the amount of information that you share with your auto manufacturer and third parties. Again, your VIN is privileged information and so is your vehicle location.
3. Securely manage your vehicle mobile application. Software Defined Vehicles come with a mobile application associated with the car’s VIN, enabling the owner to view vehicle location and system status’, to request roadside service, and to inform maintenance programs of issues.
Review your mobile application settings and privacy warnings. Know that in many instances, the Software Defined Vehicle owner has limited control of the settings regarding what information is to be shared with the auto maker and its designated third parties. From a physical security perspective, never remote start your vehicle with your mobile application unless you have control of your vehicle’s physical security.
4. Manage the internet connectivity to your Software Defined Vehicle. Only you should determine when your vehicle accepts Over the Air updates. Whether you synchronize your 5G mobile device to your Software Defined Vehicle or have onboard embedded 5G, your vehicle will seek to connect when there is an internet connection available. Many vehicles support software updates over all available communications methods: embedded 5G, Bluetooth and WiFi.
Make sure you do allow automatic software and feature updates only when your vehicle is idle.
Note: Not only does your vehicle want to auto-initiate system and security updates, but it also runs third party software that wants to auto-install feature and security updates. These third party software sources all have potential vulnerabilities. In my case of a 2023 Ford F350, there are 30 pieces of open source software on board this vehicle.
5. Use Multifactor authentication on your Software Defined Vehicle online portal. Enough said!
6. Mind the physical security of your Software Defined Vehicle. Park your vehicle in well-lit and secure environments if possible. If you have a vehicle on the “most wanted” list, apply the security fixes, park in a garage or in another secure environment. Always use situational awareness. If your vehicle is one that has vulnerabilities, get the fixes or get a wheel lock put in place. Some of the auto makers are providing these for vehicle owners.
#2023#5G#Accounts#air#Analysis#APIs#Application Security#applications#approach#architecture#authentication#automotive#automotive industry#awareness#bluetooth#board#cadence#Cars#challenge#Check Point#CISSP#cities#Cloud#cloud infrastructure#code#Collaboration#command#communication#communications#comprehensive
0 notes
Text
Why Encryption is Essential for App Security and How to Implement It
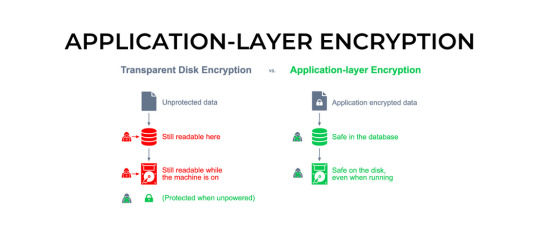
Encryption is essential for app security because it helps protect sensitive data from unauthorized access or interception by hackers or other malicious actors. Encryption involves scrambling data so that it can only be read by someone who has the decryption key or password. This ensures that even if a hacker intercepts the data, they will not be able to read it without the proper key or password.
There are several types of encryption that can be used to secure an app, including symmetric encryption, asymmetric encryption, and hashing. Symmetric encryption involves using the same key to encrypt and decrypt data, while asymmetric encryption uses a public key to encrypt data and a private key to decrypt it. Hashing involves creating a unique digital signature for a piece of data that cannot be reversed or decrypted.
Also Read : Importance of Data Encryption and How It Works
To implement encryption in an app, developers can use encryption libraries or frameworks such as OpenSSL or the Java Cryptography Architecture. They can also use application programming interfaces (APIs) provided by cloud service providers such as Amazon Web Services (AWS) or Microsoft Azure.
The following are some general steps to implement encryption in an app:
Identify sensitive data: Determine which data needs to be encrypted to ensure it remains confidential and secure.
Choose an encryption algorithm: Select an encryption algorithm that is appropriate for the level of security required by the app.
Generate encryption keys: Generate encryption keys for symmetric encryption or public and private keys for asymmetric encryption.
Encrypt the data: Use the chosen encryption algorithm and keys to encrypt the data.
Store the encryption keys securely: Store the encryption keys securely, so they cannot be accessed or intercepted by hackers.
Decrypt the data when needed: Use the appropriate key to decrypt the data when it needs to be accessed by authorized users.
Test and validate: Test the encryption implementation thoroughly to ensure it works as expected and does not introduce any vulnerabilities or weaknesses.
By implementing encryption, developers can help ensure that their app is secure and can protect sensitive data from unauthorized access or interception.
0 notes
Link
Over the forecast period of 2022-2028, Thailand's managed security services market is expected to grow at an impressive CAGR of 11.5%. The managed security services market is a rapidly expanding industry that provides organizations with a range of security solutions to help protect against cyber threats. Cyberattacks and data breaches are on the rise, and organizations need to protect sensitive information more than ever before.
0 notes
Video
youtube
3 Phases of Application Security
1 note
·
View note