#detect DDoS attacks
Explore tagged Tumblr posts
Text
Firewall Friday: Defending Against DDoS Attacks - How to Keep Your Network Safe
Welcome to Firewall Friday, where we dive into the world of DDoS attacks and equip you with the knowledge to safeguard your network against these digital bullies. But don’t worry, we won’t let these troublemakers ruin our Friday vibes. Instead, we’ll tackle the topic with a humorous tone, using analogies and emojis to make it easy for even the most novice readers to understand. So, put on your…
View On WordPress
#anomaly detection#cloud-based defenses#cybersecurity#DDoS attacks#firewall#intrusion prevention systems#load balancing#network security#rate limiting#traffic analysis
0 notes
Text
Checkerboard
Will add an AO3 link once the ddos attack is over. In the meantime, please enjoy this Gen Rex fic! It's whump. :)
Edit: AO3 Link!
.
One moment, Rex was breaking free of the control collar, as planned. The next–
Caesar hadn't realized that witch could move that fast.
The fight was, in a word, brutal. Rex was good, very good, even Caesar could see that, but against both an equal opponent and the relentless black pawns, even he had limits. Especially when he was avoiding lethal blows. It appeared he hadn't, quite, realized that the black pawns were robots.
That was an oversight on Caesar's part, he'd admit. He knew that Rex had the ability to detect nearby nanites, but he didn't know if that ability was behind the consciousness partition his parents had set up in the onboard AI, and even if it wasn't, well, having the ability to perceive something and understanding the information it gave you were two very different things. Especially under stress.
Black Knight crushed Rex's latest set of smack hands with a nanite-generated hammer, then tipped him over, wrapping him with her whip. He hit the floor hard, but it was obvious he was going to break free momentarily, and possibly even counter with his own whip build, but Black Knight's hammer shifted into a sword, and she brought it down through Rex's shoulder.
"Stop! Stop! What are you doing?" demanded Caesar.
The black pawns moved in, aiming at Rex from point blank range.
"Kill or control," said Black Knight. "That's Providence's current protocol. If we get your brother back under control, we can put ‘cure’ back on the table, but until then… What will it be?" The ultimatum, because that's what it was, was delivered in the same falsely pleasant tone Black Knight gave all her orders in.
Caesar clenched his jaw. Some people might think he was cold and disconnected, that he lacked empathy, feelings, care for anything that wasn’t one of his experiments. Dr. Holiday, for example, had, shortly after Rex’s disappearance, accused Caesar of being a psychopath.
Well. Caesar knew there was something not quite right about him. Never had felt like getting a diagnosis. But he hadn’t cried over his parents’ deaths, and he hadn’t cried over Rex’s disappearance. He certainly hadn’t gotten as emotional as Holiday, or even Six.
But he did love his brother. He knew that love was just the result of neural connections in the brain, coupled with certain chemical reactions, but that didn’t make it less real. He wanted his brother to be healthy and happy. That was love, yes?
But for Rex to be healthy and happy, he also had to be alive.
He met Rex’s eyes. Rex, unlike Caesar, was emotional. Caesar could easily read the pain, fury, and fear on Rex’s face. Fear that quickly slid into terror as Rex realized what Caesar was going to do.
“Dr. Salazar, your decision. You can stop stalling. We neutralized the robot monkey, and even all the Numbers working together couldn’t break into this facility fast enough to keep me and my pawns from terminating this EVO.”
“He-ahhhh!” Rex’s protest was cut off with a sideways jerk of Black Knights blade, ending with a high-pitched whine. There was no blood - Rex, as a rule, didn’t bleed. His nanites had instructions about that. But even so…
“Alright, alright!” said Caesar. “I’ll do it! I’ll just. This isn’t something I can do immediately. I told you Rex’s nanites were different.” He had. Multiple times. Some of those times were even after his six-years-in-fifteen-minutes trip.
“I’d think it’d be a simple matter, considering you worked on him before. And your control of the Omega-1 during your… reappearance.”
“I’d think,” said Caesar, retrieving a set of new control collars and checking their serial numbers, “you’d appreciate the difficulty, considering anything that could easily be done to Rex could easily be done to you.”
Black Knight’s smile grew sharper, showing teeth. “Careful. Dr. Salazar.”
Caesar made sure his tablet computer was synchronized with the main control computer and walked towards Rex. The pawns who weren’t aiming at him were now aiming at Caesar. He held up the collars and his tablet. “I’ve got to start somewhere, right?”
“Let him by,” said Black Knight in an almost magnanimous tone. She had a lot of practice with that one.
“Okay, mijo,” said Caesar, with false cheer, “let’s get started.”
“Don’t do thi–”
His protest was cut off as Black Knight changed the angle of her sword, enlarging the wound. Rex gasp, breath hitching, and Caesar decided the best way to handle this was fast, like ripping off a bandaid. He wrapped the first collar around Rex’s neck.
Predictably, because Rex could be predictable, sometimes, (it was, Caesar thought, probably a result of many of his subconscious thought processes and actions being directed by nanite programs) the skin on his neck lit up with blue lines that crossed over onto the collar and took it apart.
“Don’t–” said Caesar, quickly. “Don’t. There’s a reason I brought more than one, yes?”
“You have fifteen minutes. My arm is getting tired.”
“Please, Rex, just… Let it happen.”
Rex bit his lower lip and glared up at him. Caesar swallowed and checked his tablet, looked at what, exactly, Rex had done to the collar, and made a few adjustments. He had to - he had to get this right.
Despite the whip and despite the sword, Rex still tried to twitch away from the collar. This time, Caesar could hear the activation tone of the nanites. They’d intended to remove some of the audio cues after the nanites got out of the prototype phase, but since things had turned out the way they did, they’d never gotten around to it.
He kept an eye on the tablet, watching the feedback and already making adjustments to the next collar. When the second - or should he count it as the third? - one broke, it was ready to slide into place.
And… There! He’d need some more changes. Just a little more. But this time… Yes! He could stop Rex from breaking this one for long enough to get his foot in the door, at least. And Rex was wearing out.
He had limits. And Caesar wasn’t exactly fighting fair.
He snapped the next collar - hopefully the last one - into place. The program, a construction command for the Omega-1, started running immediately, relaying its results to the tablet. Caesar watched them anxiously, but he didn’t have much faith in that particular program as anything but a delaying tactic. Rex’s self-programming capabilities had taken care of that particular backdoor within the first week of Caesar’s return.
But the program he was loading up now was a bit different. Simple, yes, there wasn’t time for anything complex, but hopefully effective, given Caesar’s special permissions and privileges in the nanite system.
The second program worked like this: it sent a request for access to Rex’s code interface, tagged with Caesar’s administrator codes. For various ethical and practical reasons (their parents didn’t quite trust Caesar not to use higher-level access for pranks) Caesar had never been given full, unimpeded access to Rex’s nanite programming. But… the admin codes meant that he got a response. A little popup that said nothing but ‘request denied.’ Rex also could accept the request, but, well…
Caesar looked at Rex, whose face was screwed up into an expression of pained but determined confusion. That just didn’t seem likely. Even if the request was handled entirely behind the consciousness partition.
The program didn’t just send one request, though. It sent repeated requests. As many as it could, on a code loop only a few lines long.
The whirr of the nanites became more stressed as they worked on endless access requests. The nanites were tiny, brilliant computers, but they were, in the end, still computers. Computers (and everything, really), as a rule, generated heat when they were working. They’d managed to break physics in so many ways working on the nanite project, but not that one.
Rex began to sweat and pant as his body tried to regulate its internal temperature. Every inhale hitched and every exhale was accompanied by a pained whine. As a rule, Caesar didn’t experience empathy, didn’t feel with other people. Probably a mirror neuron problem. But this? This hurt.
He didn't want to do this.
His tablet beeped.
Their parents hadn’t trusted Caesar not to play pranks on his little brother, but they did trust him to look after Rex’s wellbeing in an emergency. An emergency like a significantly elevated body temperature and a huge hole in his body.
The popup now read, ‘access granted.’
The first thing Caesar did was make a new back door. He was confident that this one, the one he used to get in just now, would be patched within a week. Probably some limit on access-requests-per-minute, even for admins.
Rex’s code was a mess. Six years of unregulated self-modification would do that. Few of the new programs were instantly understandable, even to Caesar. Builds, wifi hacking tools, a series of ‘handshakes’ for various systems, dormant EVO-originating code, probably copied from people and animals he’d cured, active EVO code, from the same, a rather ingenious fix for a problem they’d never solved, back in the nanite project days. But buried underneath all that was the original code for Rex’s nanites. Even the Omega-1.
He brought up the set of programs they’d written after the first time Rex had forgotten everything. It was just a little something to help him recognize them, trust them, in case it happened again. It was why it had been so easy to convince Rex to come with him, when they had met again.
But family wasn’t the only thing on the list anymore. Dr. Holiday, Six, Noah, and even Bobo were there, primarily identified through their nanite loci, rather than the facial, vocal, and code recognition that identified the Salazars. Although, now that he looked, he could see that Rex had appended Caesar’s nanite locus to his ID data.
He went to the part of the code that dictated how much and how the nanites could influence Rex’s thoughts about a given person, and changed a few variables and permissions. He went back to the main list, added in Black Knight, and generated variables for her, too.
There. Rex was controlled. Not, perhaps, the same way all the other EVOs were, but with the values Caesar had just assigned, saying ‘no’ to him or Black Knight would be given roughly the same avoidance priority as self harm, and just being around them should feel vaguely pleasant.
Rex made a tiny noise of protest, but judging by how glazed over his eyes were, and how clammy his skin looked, Caesar doubted he was really aware of what Caesar had just done. He would be, though.
Caesar went back to the main list one more time, and told Rex’s nanites that Rafael and Violeta Salazar were dead. The effect of this was immediate and far more dramatic. Rex started sobbing.
“I’m sorry, I’m sorry.” He really was. But this was the fastest way to get to the other thing he wanted. The consciousness partition. Without their parents, Caesar was now recognized as having the highest level of admin access.
He… hesitated before he deleted it. There were a vast number of reasons it existed. The primary one being to keep ten-year-old Rex from accidentally deleting his liver, but also because the nanite project’s… well, Caesar’s… track record with AIs was not good, and even if this was more of an integrated intelligence, than an artificial one…
But Rex needed this. For that matter, if Caesar’s original plan had worked, and Rex had escaped, and he got Providence to restart the project, and, and, and… Eventually, the partition would have been removed anyway, was the point.
He hit the button and moved on. Medical options. He brought up a list of prearranged medically-related voice commands - it was short, for emergency use only, in case Rex lost control of his nanites while he was ill. He interdicted Rex’s builds, put them behind a voice authorization from a ‘person of trust’ and he desperately hoped Rex would figure out that particular loophole. He told the nanites to take over Rex’s breathing reflex for the moment, because the way he was currently breathing had to be cutting him up on Black Knight’s sword. He–
“That’s been fifteen minutes, Dr. Salazar.”
“Rex,” said Caesar, clearly, “go to sleep.”
Rex’s eyes fluttered closed.
“There you go!” said Caesar, a horrible approximation of a smile on his face. “All under control!”
"Dr. Donevsky," said Black Knight.
Caesar flinched as the doctor approached from the side of the room. He hadn't noticed anyone else come in.
“It won’t be the same as with the other EVOs, his base programming is too different,” said Caesar, now anxious as Donevsky checked Rex’s pulse and reflexes. “You won’t be able to– To puppet him around. There are only a few voice commands he has to follow, but–”
Black Knight raised an eyebrow. “That doesn’t sound like under control.”
“I’ve made him trust us,” said Caesar. “Even more than he trusts Holiday or Six. I’ve made it– You are familiar with Pavlov’s experiments with dogs, aren’t you?” It wasn’t quite what was going on, but, honestly, he didn’t want to explain it to Black Knight.
“He’s really asleep, ma’am,” said Donevsky, stepping back.
“Hm,” said Black Knight. She withdrew her builds. “How long does this last for?”
“Eight hours,” said Caesar. “That’s the recommended amount, after all!”
“Interesting. We’ll give this a trial run.”
Other medical staff, who had been standing at the periphery of the room, came forward. They heaved Rex up onto a gurney and started taking more measurements and readings. Rex stayed entirely limp throughout, like a rag doll. The doctors conferred over their results for a moment, then started to wheel him out of the room. Caesar began to follow.
Black Knight’s hand on his shoulder stopped him.
“I think we have some things to discuss, before you join your brother,” she said.
.
It wasn’t as if Rex had never been stabbed before. He had. Mostly by Van Kleiss and his stupid, stabby, sucky fingers. It sucked, but he could deal with it. Maybe with some complaining and a bit of encouragement from Dr. Holiday or Six, or some well-timed snark from Bobo, but he could deal with it.
On the other hand, the stuff that stabbed him usually wasn’t this big and usually didn’t stay stabbed in him for this long. Benefit of having the most awesome nanites on the planet was that he could safely ignore the whole ‘don’t remove the thing stabbing you or else you might bleed out’ thing… Which he totally hadn’t discovered by ignoring Holiday when she said ‘don’t remove the thing stabbing you or else you might bleed out.’ Good times.
What wasn’t a good time? The fact that the literal backstabbing he was dealing with had come after a metaphorical backstabbing.
(He was pretty sure that when people said siblings were a pain, they didn’t mean like this.)
The whole ‘tied up with a dozen guns pointed at him’ thing was bad, also. But it was kind of… Expectedly bad? Like, it wasn’t anything too out of the ordinary for his life, except for the when and where of it. But Caesar trying to mind control him? That was just…
Well. It sucked. What else was he supposed to say? He didn’t know what to say, which was, maybe, why he wasn’t saying anything while Black Knight was giving Caesar some kind of psycho speech about why he needed to be controlled.
He didn’t know why she was bothering with that, honestly. Caesar had already decided to control him. With that stupidly easy to break collar… that Caesar had to know wouldn’t work on him.
Ughhhhh sometimes he hated being the kind of person who gave others the benefit of the doubt.
He looked up and glared at Caesar, hard enough to hide any trace of hope. Not that he really kept a lot of hope as Caesar’s expression went from ‘blank’ to ‘resigned.’
A bunch of words that Dr. Holiday thought he didn’t know went through his brain so fast they sounded like static. Caesar was a weirdo and a space case most of the time, but he also knew Rex, and his nanites, better than anyone else. Caesar had gotten him to build that freaky containment machine on remote control, sans collar. Caesar could screw him over so freaking much.
“Dr. Salazar, your decision. You can stop stalling. We neutralized the robot monkey, and even all the Numbers working together couldn’t break into this facility fast enough to keep me and my pawns from terminating this EVO.”
Robot monkey? Did that mean Bobo wasn’t under control? And he hated it when people talked over him like he was some kind of object. “He-ahhhh!”
Black Knight must have moved her sword by, like, a foot, because Rex’s entire arm and back lit up like they were on fire. In the back of his mind there was something with the general shape and texture of the few times his nanites had talked to him directly. Not that any information got through to Rex. It was probably just them trying to tell him how stabbed he was, so no biggie. He could figure that out on his own. He had this whole biological system called pain and more pain, oh, and get this, yet more pain, to help him figure it out! Wasn’t that wonderful?
“Alright, alright!” said Caesar. “I’ll do it! I’ll just. This isn’t something I can do immediately. I told you Rex’s nanites were different.”
Yeah, no kidding. He was sure Providence’s new evil overlord knew nothing about that at all. It wasn’t like Providence hadn’t been studying them since Rex first got here.
Caesar strode across the room and out of Rex’s immediate line of sight. His attempt to shift his position resulted in a heel being dug into his spine, the whip tightening to the point of crushing the air out of his lungs, and the sword being twisted so viciously his vision whited out for a second.
“....could easily be done to Rex could easily be done to you.”
Okay, maybe more than a second.
“Careful. Dr. Salazar.”
Rex blinked hard, still trying to follow what was going on around him. It could be done to Black Knight, too? All of this? The mind control thing? Something else?
“I’ve got to start somewhere, right?”
“Let him by,” said Black Knight in an almost magnanimous tone. The agents between Caesar and Rex parted.
“Okay, mijo,” said Caesar, with obvious false cheer, “let’s get started.”
Rex tried to catch Caesar’s eyes. If Caesar didn't want to do this, maybe Rex could convince him not to. Sure, he wasn’t at the point of things where he’d rather die than be mind controlled - he wasn’t that noble, and he remembered the follow-up interviews from the Meechum incident - but seriously injured? Imprisoned? Those both sounded way better.
“Don’t do thi–”
Black Knight wrenched her sword to one side, and Rex’s argument was lost to agony. For a split second, he couldn’t breathe, couldn’t think, and when he could the collar was there. He sent his nanites against it, first disabling the code that let it send messages to his nanites, then telling it to disassemble stuff.
Not for the first time, Rex wondered why people didn’t make things more mechanical and less electronic. If there wasn’t an electronic disassembly command, it would be way harder for him to do stuff like this.
He wasn’t going to ask anyone that, though. His life was hard enough as it was. Case in point, his current situation (which was bad).
“Don’t–” said Caesar. “Don’t. There’s a reason I brought more than one, yes?”
What, was that some kind of threat? Rex had heard better.
“You have fifteen minutes. My arm is getting tired.”
… or maybe he was talking to someone else. Again.
“Please, Rex, just… Let it happen.”
Like heck. If Caesar and Black Knight were going to do this to him, he was going to make them work for it. In the spirit of that - and not because he was scared - he tried to pull away when Caesar picked up the next collar and put it on. Not that it did much good. But it didn’t do Caesar any good, either, so there. Ha.
It had been harder, this time, though. Not a lot harder, but enough to make him apprehensive.
He really hoped Black Knight was wrong about that backup. He didn’t think he’d be able to get out of this on his own, and he was liking his chances of holding out against mind control long term less and less.
He broke the next collar, too. That one had been hard, and Rex was starting to feel tired. More tired. His nanites were starting to protest being diverted from the giant gaping hole in his shoulder.
But Caesar already had the next collar around Rex’s neck. Rex told his nanites to take it apart, too, but… they were… busy? He pushed through, overriding whatever was occupying them, and the collar fell off.
Caesar put the next one on.
For a second, Rex zoned out like he had when Caesar had been sending the Omega-1 instructions. When he came back to himself, he felt hot.
Well, he always felt hot. He was hot. Blisteringly good looking, even. But he was physically hot right now. Fever-level hot. Best he could compare it to was when his nanites had been working overtime trying to counteract the chupacabra poison. Except there was no chupacabra poison this time. Probably. What was Caesar doing to him?
He closed his eyes, trying to focus on getting his nanites back under control. There was a feeling like someone knocking, knocking, knocking on the back of his mind until the sound turned to jackhammer black noise. It hurt, and he was rapidly approaching the temperatures where it was hard for him to think. His skin felt slick and sticky, and he started to pant, even as the motion made Black Knight’s sword saw back and forth inside him.
And then the building pressure against him disappeared all at once. He didn’t exactly relax, but he did go limp, unable to maintain the state of tension from before. He was going to pass out, soon, he could tell. He hated passing out.
With difficulty, he opened his eyes to glare blearily at Caesar. He was hunched over his tablet, tapping away at the screen. Traitor. Backstabber. Jerk. It wasn’t as if Rex hadn’t been backstabbed by, like, everyone, except for Holiday, Bobo (except for really minor things), and Six (there had been that time with the Numbers, and the other thing with the memory loss, but, really, that was fine, water under the bridge and all), but family was supposed to be different. You were supposed to be able to trust family. Family wasn’t supposed to try to mind control you for creepy middle-aged women, which is why Rex had to trust that Caesar was doing this for a very good reason.
Rex blinked slowly. There was something wrong with that train of thought. The people you… Caesar wouldn’t mind control him just because. Caesar had betrayed him– But Caesar wouldn’t do that. Had Rex misunderstood something? Somewhere? Was he not working for Black Knight? Except, Black Knight was a good person. He knew that. He trusted her. Good people didn’t just mind control people for no reason. Or stab people for no reason. So, there had to be a reason. But it was so hard to think of one.
… Had he hurt someone?
A weak whine built in the back of his throat. He didn’t remember hurting… But maybe he did? He was so angry about the control collars, but Black Knight and Caesar said they were good, so…? His thoughts felt so sticky and slow. What had he been thinking about before? Caesar and Black Knight had… They had been…?
He was hit with a wave of grief absolutely unlike anything he had ever experienced before. Grief, like something he’d always had, something he’d held so close he couldn’t even see it, being ripped away from him without warning. A piece of his world, just gone, and he didn’t even know what it was, just that he wanted it back, please, please, please.
“I’m sorry, I’m sorry.”
Rex was sorry, too. He didn’t know what he had done, but he wanted this to stop.
And then, something in the back of Rex’s mind opened up, and his thoughts stopped being anything like coherent. He watched, more or less passively, as Caesar turned on emergency medical controls, put his builds on lock, and made the nanites actively regulate his breathing. Which actually did help, a little. Rex may have been hyperventilating.
Black Knight and Caesar started talking, but Rex couldn’t follow anything they were saying at all. It was okay for him to just… zone out a bit, right? He could… obviously, they could take care of things…
“Rex,” said Caesar, dragging Rex’s attention back into the real world, if only for a moment, “go to sleep.”
.
To be continued. :)
83 notes
·
View notes
Text
Defending the Internet: how Cloudflare blocked a monumental 7.3 Tbps DDoS attack
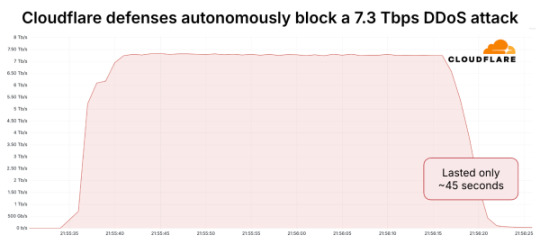
Summary: Cloudflare mitigated a record 7.3 Tbps multivector DDoS attack predominantly composed of UDP floods combined with multiple reflection and amplification techniques, utilising global anycast, real-time packet fingerprinting with eBPF, and distributed heuristic detection to block over 34,000 destination ports without impacting legitimate traffic.
Source: https://blog.cloudflare.com/defending-the-internet-how-cloudflare-blocked-a-monumental-7-3-tbps-ddos/
2 notes
·
View notes
Text
Ostensibly an Islamist terrorist gang, Anonymous Sudan said yesterday it attacked AO3 because it is “against all forms of degeneracy, and the site is full of disgusting smuts and other LGBTQ+ and NSFW things”.
The group posted a further message on its Telegram channel today, saying it will continue to target the site if it comes back online. “We can bypass any detection you put, we will make sure your site goes offline for the longest possible time as your ‘experts’ scratch their heads cluelessly to find a solution,” the criminals wrote.
However, security experts believe Anonymous Sudan is actually a Russian hacking gang posing as a splinter group of the original Anonymous hacktivist collective, aiming to cause trouble for Moscow’s enemies in the West.
[...]
A report from another security business, Flashpoint, goes further, stating: “Evidence suggests that Anonymous Sudan are likely state-sponsored Russian actors masquerading as Sudanese actors with Islamist motivations, as cover for their actions against western, or western-aligned, entities.”
59 notes
·
View notes
Text
Edit: If you guys have any questions feel free to dm them to me or drop them in my ask box !
Hello ! I am sad about ao3 being down, but I would like to offer my insight about what type of DDOS could be affecting it ! Yes this is an excuse to talk about my special interest
For context: I major in Informational Technology, and we have to learn about this, and technology has always been my special interest. I know way too much about this
In this post I will explain what a DDOS is, different types of DDOS attacks, and my theory on which one.
A DDOS (or denial of service attack) is when the servers get so overloaded that they crash and burn.
There are multiple types of DDOS attacks: Zip Bomb, Time Bomb, Fork Bomb, and a Zombie attack. Each one does something different but reach the same result.
Zip Bomb: Will send a compressed file of data to a server, and when they uncompress it, they get fit with 4.5 petabytes (4 503 599 626 321 920 bytes) of data. No computer can even process that !
Time Bomb: Basically what a free trial is, but will implode other things too. Time Bombs will basically count down to when they release the attack to servers with either Zip Bombs, Trojan Horses, or a Worm
Fork Bomb: A malicious file that will get in your servers and start duplicating itself, taking up server resources and slowing them down. Very bad if not caught early on. (I would also like you to know this is also called a Wabbit virus)
Zombie: A hacked computer that has been compromised and can be used by the hacker remotely to do what they want. These are dangerous because they affect multiple systems and then use those systems to overload a server, and they're hard to detect. (If you're scared you have this, run your downloaded files though VirusTotal , it runs files and websites through a lot of antivirus software and can detect anything malicious)
My working theory is that ao3 is under either a Fork Bomb attack or a Zombie Attack (that is the official term for it). Both these DDOS attacks are hard to get rid of, and hard to pinpoint where they started from.
It doesn't mean ao3 is gone forever, but it means it might be down for a little bit. They're working their absolute hardest, and I believe in them <3
#ao3#ao3 down#ddos attack#computer virus#I only know so much about this bc its my special intrest#any of this could be wrong please don't quote me on it
54 notes
·
View notes
Text

#cyberpunk#detailed#futuristic#moody#gritty#urban#decay#reflective#high-tech#dystopia#atmospheric#digital art#cyberpunk 2077
10 notes
·
View notes
Text
What is DoS and DDoS Attacks: Definition, Examples & Detection
2 notes
·
View notes
Text
Going Global: Why International VPS Hosting Matters for Your Website's Success
The internet has shrunk the world, making it easier than ever to reach a global audience. If your website aspires to break geographical barriers and connect with users worldwide, choosing the right virtual private server (VPS) hosting provider becomes crucial. This article delves into the world of VPS hosting with international servers, explaining its significance and guiding you towards making an informed decision.
What is VPS Hosting and Why is it Ideal for Global Websites?
VPS hosting offers a sweet spot between shared hosting and dedicated servers. Unlike shared hosting, where multiple websites share resources on a single server, VPS grants you a dedicated portion of the resources on a physical server. This translates to better performance, security, and control over your website's environment compared to shared hosting. However, VPS remains more cost-effective than dedicated servers, making it a popular choice for websites experiencing growth.
For websites targeting a global audience, international VPS hosting becomes a game-changer. Here's how:
Improved Website Speed and Performance: When users access your website from a location geographically distant from your server, it can lead to slow loading times. By strategically placing your VPS server closer to your target audience, you significantly reduce latency (delay) and ensure a faster, more responsive website experience.
Enhanced Search Engine Optimization (SEO): Search engines like Google prioritize websites that deliver a good user experience. Page loading speed is a critical factor in SEO rankings. International VPS hosting can improve your website's speed in different regions, potentially boosting your search engine ranking and visibility globally.
Reduced Content Delivery Network (CDN) Costs: CDNs are geographically distributed networks of servers that cache your website's content and deliver it to users from the closest server location. While CDNs are a powerful tool, they can come with additional costs. By strategically placing your VPS servers in key regions, you can potentially reduce your reliance on a CDN, saving on costs without compromising performance.
The Power of Geographically Distributed Servers
Many VPS hosting providers offer servers located in various countries and continents. This allows you to choose the server location(s) closest to your target audience. Imagine your website catering to users in Europe and Asia. By opting for a VPS provider with servers in Frankfurt (Germany) and Singapore, you can cater to both regions effectively.
Choosing the Right VPS Hosting Provider with International Servers
With a plethora of VPS hosting providers offering international servers, selecting the right one can be overwhelming. Here are some key factors to consider:
Server Locations: Ensure the provider offers servers in the regions where your target audience resides. Look for a good balance between coverage and cost.
Server Performance: Consider factors like CPU core count, RAM capacity, and storage space. Choose a plan that aligns with your website's resource requirements.
Network Connectivity: A reliable and high-bandwidth network is essential for fast content delivery. Look for providers with strong network infrastructure and uptime guarantees.
DDOS Protection: Distributed Denial-of-Service (DDoS) attacks can cripple your website. Choose a provider offering DDoS protection to safeguard your online presence.
Security Features: Look for a provider with robust security measures in place, including firewalls, intrusion detection/prevention systems, and regular backups.
Customer Support: Reliable and responsive customer support is invaluable. Opt for a provider with 24/7 support channels, such as phone, live chat, or email.
Pricing: VPS hosting plans vary significantly in price. Compare plans based on features, server specifications, and location before making a decision. Consider providers like Nexonhost, known for offering good value for money on VPS plans.
Remember, there's no "one size fits all" solution. Evaluate your specific needs, target audience, and budget to find the best fit.
Beyond Server Location: Additional Considerations
While server location is crucial, other factors also influence your website's global reach. Here are some additional considerations:
Content Localization: If you cater to diverse audiences, consider translating your website content into their native languages. This can significantly improve user engagement.
Cultural Sensitivity: Be mindful of cultural nuances in your website design and content. Colors, symbols, and even humor can have different meanings across cultures.
Payment Gateway Integration: Make sure your website accepts payments from your target audience's preferred payment methods.
Conclusion: Reach the World with International VPS Hosting
By choosing the right VPS hosting provider with strategically placed international servers, you can equip your website to thrive in the global marketplace. Remember, a global audience requires a global approach. Invest in the right tools and resources to connect with users worldwide and achieve your online success goals.
2 notes
·
View notes
Text
Are you facing security challenges in Online Survey?

Online surveys can face several security challenges, including:
Data Privacy: Ensuring the confidentiality of respondents' data is crucial. Unauthorized access to personal information collected in surveys can lead to privacy breaches.
Data Integrity: Maintaining the accuracy and consistency of survey data is essential. Malicious actors might attempt to manipulate or corrupt data, impacting the reliability of survey results.
Survey Fraud: Individuals may attempt to manipulate survey results by providing false information or submitting multiple responses (known as ballot stuffing), compromising the survey's integrity.
Phishing Attacks: Fraudulent emails or survey links may be used to trick respondents into providing sensitive information or downloading malware.
DDoS Attacks: Distributed Denial-of-Service attacks can disrupt survey platforms by overwhelming servers with excessive traffic, causing downtime and hindering survey completion.
To address these challenges, survey administrators often implement various security measures:
Encryption: Utilizing encryption techniques to protect data transmission and storage.
Authentication: Requiring user authentication to prevent unauthorized access to surveys and data.
Firewalls and Anti-Malware: Employing security software and firewalls to mitigate the risk of cyber threats.
Captchas and IP Blocking: Implementing measures to prevent automated responses and restrict multiple submissions from the same IP address.
Anonymity and Confidentiality: Ensuring respondents' anonymity and safeguarding their sensitive information.
Regular Security Audits: Conducting periodic security audits to identify vulnerabilities and enhance overall security.
While these measures can mitigate risks, no system is entirely immune to security threats. Survey administrators must stay vigilant, update security protocols regularly, and adhere to best practices to protect the integrity and privacy of survey data.
To know more:
online market research platform
fraud prevention solution
fraud detection and reporting tool
Online Project Management Platform
#market research#onlineresearch#samplemanagement#panelmanagement#datacollection#fraud detection#datainsights
2 notes
·
View notes
Text
Shards of the Nexus: DDOS
read it on the AO3 at https://ift.tt/qUraM54
by Realityhelix
In honor of the recent AO3 attack, here’s a bunch of extremely short smut vignettes with all our favorite Riddlers. Lbr, none of these people are straight.
A note: Swag and Unswag are not brothers! They are the same man split into two different possible life paths. That story comes later. They refer to themselves as twins because they look nearly identical.
A WARNING!: Nash is underage! But I also remember what it was like to be seventeen. Anyway, I’ve put his little drabble at the end so you can skip it if you want. But I absolutely did warn you!
Words: 1454, Chapters: 1/1, Language: English
Series: Part 14 of Shards of the Nexus
Fandoms: DCU
Rating: Explicit
Warnings: Underage
Categories: Multi
Characters: Arkham!Riddler, Puzzles!Riddler, Swag!Riddler, Unswag!Riddler, Detective!Riddler, Narci!Riddler, YJ!Riddler, Nash!Riddler, Helix(oc), Lust(OC), Bruce Wayne, Jervis Tetch
Relationships: Arkham/Puzzles, Swag/Helix/Unswag, Detective/Jervis, YJ/Bruce, Nash/Lust
read it on the AO3 at https://ift.tt/qUraM54
1 note
·
View note
Text
Comprehensive Cyber Security Services to Safeguard Your Digital Assets
Understanding Cyber Security Services
What are Cyber Security Services?
Cyber security services encompass a broad range of measures designed to protect computer systems, networks, and data from cyber threats. These services can include risk assessment, threat detection, prevention strategies, and mitigation techniques tailored to an organization’s specific needs. In an increasingly digitized world, businesses of all sizes must consider various aspects of cyber security to safeguard their digital assets from theft, damage, or unauthorized access. By leveraging professional cyber security services, organizations can effectively bolster their defenses against evolving cyber threats.
The Importance of Cyber Security Today
As the reliance on digital technology grows, so does the importance of robust cyber security measures. According to recent studies, cybercrime has seen a staggering increase, with attacks becoming more sophisticated and pervasive. In 2022 alone, global cybercrime damages were projected to exceed $6 trillion, emphasizing the need for businesses to invest in comprehensive cyber security strategies.
Moreover, current regulations and compliance mandates require organizations to protect sensitive data. Breaches can lead to significant financial penalties and reputational damage. Thus, implementing effective cyber security services is not only essential for preventing attacks but also for ensuring compliance with applicable laws.
Common Types of Cyber Threats
Cyber threats come in many forms, each capable of jeopardizing an organization’s security framework. Some of the most common types include:
Malware: Malicious software, such as viruses, spyware, and ransomware, designed to disrupt or gain unauthorized access to systems.
Phishing: Social engineering attacks that trick individuals into providing sensitive information, often masquerading as trusted entities.
DDoS Attacks: Distributed denial-of-service attacks aim to overwhelm a network or service with traffic, rendering it unusable.
Insider Threats: Risks derived from employees or contractors who misuse their access to company data, either maliciously or through negligence.
Key Components of an Effective Cyber Security Strategy
Risk Assessment and Management
A comprehensive risk assessment is fundamental to cyber security strategies. This process involves identifying potential vulnerabilities within an organization’s IT infrastructure and evaluating the potential impact of different types of threats. Organizations must continuously monitor their risk landscape, adapting their security approaches accordingly.
Effective risk management involves implementing controls to mitigate identified risks. This can range from technological solutions, such as firewalls and intrusion detection systems, to administrative controls like user access policies and incident response protocols.
Endpoint Protection and Monitoring
With the rise of remote work and mobile devices, protecting endpoints—such as laptops, smartphones, and tablets—has become crucial. Endpoint protection services provide real-time monitoring and management, offering threat detection and response capabilities tailored to each device.
An effective endpoint protection strategy may include anti-virus software, encryption, and secure user authentication methods to protect sensitive information and maintain overall system integrity.
Incident Response Planning
Incident response planning is an essential component of any cyber security strategy. A well-defined incident response plan outlines the steps an organization must take when a security breach occurs, minimizing damage and recovery time. Key aspects of incident response planning include:
Establishing a Response Team: Designating knowledgeable personnel to manage and coordinate responses is crucial.
Developing Communication Plans: Clear internal and external communication strategies can aid in maintaining transparency with stakeholders during an incident.
Conducting Simulations: Regular drills and simulations help ensure that all team members are prepared to act when a real incident occurs.
How to Choose the Right Cyber Security Services Provider
Evaluating Technical Expertise and Solutions
When selecting a cyber security services provider, organizations should prioritize technical expertise. It’s important to assess the provider’s experience, certifications, and the range of services offered. Potential clients should look for providers with a proven track record of effectively addressing cyber threats relevant to their industry.
Additionally, providers should offer tailored solutions rather than one-size-fits-all packages, enabling businesses to implement security measures that address their unique challenges.
Client Testimonials and Case Studies
Client testimonials and case studies can provide valuable insights into a provider’s effectiveness. Organizations should seek feedback from current and past clients to gauge satisfaction levels and overall service quality. Examining case studies can also reveal how a provider has successfully addressed specific challenges similar to those faced by prospective clients.
Understanding Service Level Agreements (SLAs)
Service Level Agreements (SLAs) are contracts that define the expected level of service between a provider and a client. It is crucial to review SLAs carefully, as they establish performance metrics, response times, and responsibilities in case of security incidents.
Organizations should ensure that SLAs align with their own security needs and expectations to hold providers accountable for maintaining high security standards.
Best Practices for Cyber Security in Your Organization
Regular Training and Awareness Programs
One of the most effective ways to bolster cyber security is through regular training and awareness programs for employees. Equipping staff with knowledge about potential threats, safe practices, and the importance of cyber security can significantly reduce the likelihood of breaches caused by human error. Programs should include topics like recognizing phishing attempts, securely handling sensitive data, and the importance of strong passwords.
Engaging employees through interactive training sessions, workshops, or simulations can enhance learning and retention of critical cybersecurity practices.
Implementation of Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security beyond just passwords. By requiring users to provide two or more verification factors to gain access, organizations can significantly reduce the risk of unauthorized access. For instance, MFA can involve a combination of something the user knows (like a password), something they have (like a mobile device), or something they are (biometric verification).
The implementation of MFA is particularly important for remote access and sensitive systems to enhance security posture against unauthorized users.
Conducting Regular Security Audits
Regular security audits are essential for identifying vulnerabilities and ensuring compliance with security policies. These audits can help organizations systematically evaluate their IT assets, uncover weaknesses, and assess the overall effectiveness of their cyber security practices.
Audits should cover aspects such as network security, data protection measures, and incident response capabilities. Engaging third-party auditors can provide an impartial view and may uncover issues that internal teams might miss.
Measuring the Effectiveness of Cyber Security Services
Key Performance Indicators (KPIs) to Track
To measure the effectiveness of cyber security services, organizations should establish key performance indicators (KPIs) that align with their security objectives. Common KPIs include:
Incident Response Time: The average time taken to identify and respond to security incidents.
Number of Incidents: Tracking the frequency of security breaches within a defined period to assess trends and patterns.
User Awareness Levels: Measuring employee understanding and adherence to security protocols through assessments or simulations.
Feedback Loops and Continuous Improvement
Establishing feedback loops is critical for continuous improvement in cyber security. By soliciting feedback from internal stakeholders and external providers, organizations can identify areas of weakness and opportunities for enhancement. Regular review sessions can facilitate updates on security policies, new threat intelligence, and evolving business needs to refine the overall strategy.
Case Studies of Successful Implementations
Examining case studies of successful cyber security implementations provides practical insights into best practices and effective strategies. For example, a healthcare provider may document how they applied multi-factor authentication and employee training to significantly decrease phishing incidents. By sharing success stories, organizations can learn from others’ experiences and implement strategies that align with their security goals.
1 note
·
View note
Text
API Security Market
API Security Market size is estimated to reach $6.3 billion by 2030, growing at a CAGR of 25.4% during the forecast period 2023–2030.
🔗 𝐆𝐞𝐭 𝐑𝐎𝐈-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐢𝐧𝐬𝐢𝐠𝐡𝐭𝐬 𝐟𝐨𝐫 𝟐𝟎𝟐𝟓-𝟐𝟎𝟑𝟏 → 𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐍𝐨𝐰
API security market is rapidly expanding as organizations increasingly rely on APIs to enable digital services, integrate systems, and streamline operations. With this growth comes rising threats, including data breaches, injection attacks, and unauthorized access. API security focuses on protecting these interfaces through authentication, authorization, encryption, traffic monitoring, and threat detection. Key sectors such as finance, healthcare, and e-commerce are driving demand for robust API protection. As businesses adopt microservices, cloud computing, and mobile applications, the need for advanced API security solutions grows.
🚀 𝐊𝐞𝐲 𝐌𝐚𝐫𝐤𝐞𝐭 𝐃𝐫𝐢𝐯𝐞𝐫𝐬 𝐟𝐨𝐫 𝐀𝐏𝐈 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲:
📈 𝐑𝐚𝐩𝐢𝐝 𝐆𝐫𝐨𝐰𝐭𝐡 𝐨𝐟 𝐀𝐏𝐈𝐬 𝐀𝐜𝐫𝐨𝐬𝐬 𝐈𝐧𝐝𝐮𝐬𝐭𝐫𝐢𝐞𝐬
The explosion of cloud services, mobile apps, and IoT devices has led to a surge in API usage, increasing the need for robust API protection.
🔐 𝐑𝐢𝐬𝐢𝐧𝐠 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐡𝐫𝐞𝐚𝐭𝐬
APIs are a frequent target for attacks like data leaks, DDoS, injection, and broken authentication, driving demand for advanced security solutions.
☁️ 𝐖𝐢𝐝𝐞𝐬𝐩𝐫𝐞𝐚𝐝 𝐂𝐥𝐨𝐮𝐝 𝐀𝐝𝐨𝐩𝐭𝐢𝐨𝐧
As businesses migrate to cloud-based services and microservices architectures, securing API communication becomes mission-critical.
📱 𝐏𝐫𝐨𝐥𝐢𝐟𝐞𝐫𝐚𝐭𝐢𝐨𝐧 𝐨𝐟 𝐌𝐨𝐛𝐢𝐥𝐞 & 𝐖𝐞𝐛 𝐀𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬
APIs power user-facing and backend services, making their security essential to ensure data integrity and user trust.
🏥 𝐆𝐫𝐨𝐰𝐭𝐡 𝐢𝐧 𝐒𝐞𝐧𝐬𝐢𝐭𝐢𝐯𝐞 𝐃𝐚𝐭𝐚 𝐓𝐫𝐚𝐧𝐬𝐚𝐜𝐭𝐢𝐨𝐧𝐬
Industries like finance and healthcare rely heavily on APIs to exchange personal and financial information, increasing the need for strong compliance-driven API protection.
𝐋𝐢𝐦𝐢𝐭𝐞𝐝-𝐓𝐢𝐦𝐞 𝐎𝐟𝐟𝐞𝐫: 𝐆𝐞𝐭 $𝟏𝟎𝟎𝟎 𝐎𝐟𝐟 𝐘𝐨𝐮𝐫 𝐅𝐢𝐫𝐬𝐭 𝐏𝐮𝐫𝐜𝐡𝐚𝐬𝐞
𝐓𝐨𝐩 𝐊𝐞𝐲 𝐏𝐥𝐚𝐲𝐞𝐫𝐬:
FortiVenture | Zoom | Rakuten | Naspers Limited | Twilio | Activision Blizzard | Recruit Holdings Co., Ltd. | STARLINK | Kazakhtelecom JSC Quantum | TikTok Shop | EPAM Systems | CenturyLink | Facebook Synopsys Inc | Altice USA | Palo Alto Networks | HubSpot | Akamai Technologies | Cadence
#APISecurity #Cybersecurity #CloudSecurity #DataProtection #Infosec #ApplicationSecurity #DevSecOps #ZeroTrust #APIManagement #OAuth

0 notes
Text
Reliable Website Maintenance Services In India | NRS Infoways
In today’s hyper‑connected marketplace, a website is far more than a digital brochure—it is the beating heart of your brand experience, your lead‑generation engine, and your most valuable sales asset. Yet many businesses still treat their sites as “launch‑and‑forget” projects, only paying attention when something breaks. At NRS Infoways, we understand that real online success demands continuous care, proactive monitoring, and seamless enhancements. That’s why we’ve built our Reliable Website Maintenance Services In India to deliver round‑the‑clock peace of mind, bulletproof performance, and measurable ROI for forward‑thinking companies like yours.
Why Website Maintenance Matters—And Why “Reliable” Makes All the Difference
Search engines reward fast, secure, and regularly updated sites with higher rankings; customers reward them with trust and loyalty. Conversely, a sluggish, outdated, or vulnerable site can cost you traffic, conversions, and brand reputation—sometimes overnight. Our Reliable Website Maintenance Services In India go beyond the basic “fix‑it‑when‑it‑breaks” model. We combine proactive health checks, performance tuning, security hardening, and content optimization into a single, cohesive program that keeps your digital storefront open, polished, and ready for growth.
What Sets NRS Infoways Apart?
1. Proactive Performance Monitoring
We leverage enterprise‑grade monitoring tools that continuously scan load times, server resources, and user journeys. By identifying bottlenecks before they escalate, we ensure smoother experiences and higher conversion rates—24/7.
2. Robust Security & Compliance
From real‑time threat detection to regular firewall updates and SSL renewals, your site stays impervious to malware, SQL injections, and DDoS attacks. We align with global standards such as GDPR and PCI‑DSS, keeping you compliant and trustworthy.
3. Seamless Content & Feature Updates
Launching a new product line? Running a seasonal promotion? Our dedicated team updates layouts, landing pages, and plugins—often within hours—to keep your messaging sharp and relevant without disrupting uptime.
4. Data‑Driven Optimization
Monthly analytics reviews highlight user behavior, bounce rates, and conversion funnels. We translate insights into actionable tasks—A/B testing CTAs, compressing heavy images, or refining navigation—all folded into our maintenance retainer.
5. Transparent Reporting & SLAs
Every client receives detailed monthly reports covering task logs, incident resolutions, and performance metrics. Our Service Level Agreements guarantee response times as low as 30 minutes for critical issues, underscoring the “Reliable” in our Reliable Website Maintenance Services In India.
Real‑World Impact: A Success Snapshot
A Delhi‑based B2B SaaS provider reached out to NRS Infoways after repeated downtime eroded user trust and slashed demo bookings by 18 %. Within the first month of onboarding, we:
Migrated their site to a high‑availability cloud cluster
Deployed a Web Application Firewall (WAF) to fend off bot attacks
Compressed multimedia assets, cutting average load time from 4.2 s to 1.3 s
Implemented weekly backup protocols with versioned restores
Result? Organic traffic climbed 27 %, demo sign‑ups rebounded 31 %, and support tickets fell by half—proving that consistent, expert care translates directly into revenue.
Flexible Plans That Scale With You
Whether you manage a lean startup site or a sprawling enterprise portal, we offer tiered packages—Basic, Professional, and Enterprise—each customizable with à‑la‑carte add‑ons like e‑commerce catalog updates, multi‑language support, or advanced SEO audits. As your business evolves, our services scale seamlessly, ensuring you never pay for overhead you don’t need or sacrifice features you do.
Partner With NRS Infoways Today
Your website is too important to leave to chance. Join the growing roster of Indian businesses that rely on NRS Infoways for Reliable Website Maintenance Services In India and experience the freedom to innovate while we handle the technical heavy lifting. Ready to protect your digital investment, delight your visitors, and outpace your competition?
Connect with our maintenance experts now and power your growth with reliability you can measure.
0 notes
Text
Is Your Website Secure? Use Monitoring Tools to Find Out

In today's digital world, your website is more than just an online presence — it's your brand, your storefront, and your reputation. Yet, thousands of websites are compromised daily due to weak security and a lack of proactive monitoring. So, how can you be sure your website is safe?
The answer: website monitoring tools. These tools not only check for uptime and performance but also play a critical role in detecting security threats before they cause damage.
Why Website Security Matters
Cyberattacks are increasing in both frequency and sophistication. From malware injections to phishing attacks and DDoS attacks, websites face constant threats. A single vulnerability can lead to:
Data theft or loss
Site defacement
Downtime that hurts SEO and reputation
Loss of customer trust
Legal consequences due to data breaches
What is Website Monitoring?
Website monitoring involves continuous tracking of your site's performance, uptime, and security status. Tools like WebStatus247 provide real-time alerts when something goes wrong — whether it's downtime, slow performance, or suspicious activity.
While performance monitoring focuses on speed and availability, security monitoring looks deeper, detecting:
Unauthorized file changes
Malware injections
Blacklisting by Google or security authorities
SSL certificate issues
Brute-force login attempts
Key Security Features in Monitoring Tools
Here’s how a robust website monitoring tool like WebStatus247 helps protect your site:
1. Real-Time Alerts
Immediate alerts via email, SMS, or app notifications when something suspicious is detected — allowing you to act before your site is compromised.
2. SSL Certificate Monitoring
An expired SSL certificate can break your site’s security and trust. Monitoring tools notify you before expiration to keep HTTPS protection active.
3. Blacklist Checking
Get alerted if your site is added to malware blacklists like Google Safe Browsing, Norton Safe Web, or McAfee Secure.
4. File Integrity Monitoring
Tools compare core files with known safe versions to detect tampering or unauthorized changes — a sign of a breach or malware.
5. Login Page Monitoring
Detect brute-force attacks or unusual login attempts to secure your admin panel from hackers.
How to Get Started
Choose a reliable website monitoring tool like WebStatus247
Set up uptime and performance checks
Enable security features such as SSL, malware scan, and blacklist monitoring
Schedule regular reports and real-time alerts
Take action on alerts immediately to resolve issues before they escalate
Final Thoughts
Your website’s security isn’t something to guess — it’s something to monitor. Don’t wait until your site is hacked or blacklisted to take action. Use a powerful tool like WebStatus247 to stay ahead of threats and keep your site running smoothly and safely.
**Start monitoring today and make security your site
0 notes
Text
How to Make Your WordPress Website Secure and Hack-Proof ?

Your WordPress website is more than just a digital address—it's your brand’s online identity, a lead generation tool, and a customer engagement platform. But it also comes with responsibility. With WordPress powering over 40% of the web, it’s a popular target for cybercriminals.
The good news? You can take simple but effective steps to secure your WordPress site and keep it safe from hackers, malware, and data breaches.
In this guide, we’ll walk you through everything you need to know to secure your WordPress site like a pro. And if you’d rather leave it to the experts, a reliable web design company in Udaipur can set it all up for you.
Why WordPress Security Matters
A hacked website can lead to:
Stolen customer data
Lost SEO rankings
Site downtime
Damaged reputation
Financial loss
Whether you run a personal blog or an eCommerce store, site security is non-negotiable. Prevention is always better—and cheaper—than cure.
Step 1: Use a Reliable Hosting Provider
Your website’s security starts at the server level. Choose a hosting provider that offers:
Malware scanning
Firewall protection
Daily backups
DDoS attack prevention
SSL certificates
Many WordPress-specific hosting services offer built-in security features that make this step much easier.
Step 2: Install a Security Plugin
Security plugins help monitor your site and block threats in real time. Top options include: PluginFeaturesWordfenceFirewall, malware scan, login securityiThemes SecurityFile monitoring, two-factor loginSucuriFirewall + CDN + malware cleanup
These tools help you detect vulnerabilities before hackers do.
Step 3: Keep Everything Updated
One of the most common reasons for WordPress hacks is outdated software. Always:
Update your WordPress core
Update themes and plugins
Remove unused or outdated plugins
Enable auto-updates or set a reminder to check weekly.
Step 4: Use Strong Login Credentials
Weak passwords and usernames like "admin" are an open invitation for hackers.
Secure login best practices:
Use a unique username (never "admin")
Use long, complex passwords
Enable two-factor authentication (2FA)
Limit login attempts with a plugin
Some security plugins even offer CAPTCHA on login forms to prevent brute-force attacks.
Step 5: Enable HTTPS with SSL
An SSL certificate encrypts the data transferred between your server and your visitors. Plus, Google ranks HTTPS sites higher in search results.
Most hosting providers offer free SSL certificates. Once installed, use plugins like Really Simple SSL to force HTTPS across your site.
Step 6: Set User Roles Carefully
If your site allows multiple users (e.g., writers, editors, admins), assign user roles carefully to limit access to backend features.
WordPress roles include:
Administrator (full control)
Editor (edit & publish others’ posts)
Author (can publish own posts)
Contributor (write but can’t publish)
Subscriber (read-only)
Giving full access to untrained users increases security risk.
Step 7: Backup Regularly
Backups are your safety net. If your site gets hacked or corrupted, a recent backup allows you to restore everything quickly.
Use backup plugins like:
UpdraftPlus
BackupBuddy
BlogVault
Set up automatic backups and store them off-site (Google Drive, Dropbox, etc.).
Step 8: Disable File Editing
By default, WordPress allows admins to edit theme and plugin files from the dashboard. Hackers can use this access to inject malicious code.
Disable this by adding the following line to your wp-config.php file:
phpCopy
Edit
define( 'DISALLOW_FILE_EDIT', true );
This small tweak can prevent massive damage.
Step 9: Monitor Activity Logs
Activity logs help you track what’s happening behind the scenes. If something breaks or gets changed, you’ll know who did it and when.
Use plugins like:
WP Activity Log
Simple History
Great for multi-user websites, agencies, and eCommerce sites.
Step 10: Hire a WordPress Security Expert
If security isn’t your strength—or if your site handles sensitive data—it’s wise to hire professionals. A skilled WordPress Development Company in Udaipur can audit your site, set up best practices, and monitor ongoing threats.
They’ll ensure:
Your database is secure
Plugins/themes are safe and optimized
Login systems are reinforced
The site performs fast without vulnerabilities
It’s a one-time setup that delivers long-term peace of mind.
Bonus Tips: Quick Wins for WordPress Security
✅ Rename the default login URL (/wp-admin) using a plugin like WPS Hide Login
✅ Use cloud-based firewalls like Cloudflare for an extra layer of protection
✅ Restrict file permissions (e.g., 755 for folders, 644 for files)
✅ Disable XML-RPC if not in use (it can be a gateway for brute-force attacks)
✅ Regularly scan your site using Sucuri’s free scanner
Final Thoughts
Your website is your brand’s digital asset—protecting it should be a top priority. Thankfully, WordPress makes it easy to lock things down, especially when combined with reliable plugins and smart practices.
0 notes