#devsecops engineer certification
Explore tagged Tumblr posts
Text
The GSDC Certified DevSecOps Engineer (CDSOE) is a certification highly coveted by those with expertise in developing, deploying, and maintaining secure software solutions using the latest devsecops methodologies. It is intended for seasoned devsecops professionals with advanced knowledge and skills in areas such as automation, continuous integration and delivery, risk management, compliance, and security testing.
The certification exam evaluates the candidate's capacity to create, implement, and oversee secure software pipelines that comply with the highest industry standards.The GSDC Certified DevSecOps Engineer certification is a valuable asset for those who wish to demonstrate their proficiency in the devsecops field and stand out in the job market.
#gsdc devsecops certification#devsecops certification#devsecops certification gsdc#certified devsecops engineer#devsecops engineer certification
0 notes
Text
SAST, DAST & DevSecOp
Job title: SAST, DAST & DevSecOp Company: Ciel HR Job description: and DevSecOps Automation Certification (GCSA), Certified DevSecOps Engineer (CDE) Compulsory: Certified Ethical Hacker (CEH), B… Expected salary: Location: Maharashtra – Bangalore, Karnataka Job date: Wed, 04 Jun 2025 05:54:28 GMT Apply for the job now!
0 notes
Text
Many organizations have well-thought-out, documented processes for managing secrets that work well enough as long as requests are infrequent. In the context of app development, “secrets” might refer to any information that is used by both machines and humans to verify access to restricted environments such as credentials, keys, tokens, and certificates. When every person on the dev team and any app, software, microservice and container needs to be granted permission to perform a given action, we can understand how important proper “management” can be. As your organization grows and the number of applications, components, cloud endpoints and systems you support increases, the process of managing secrets becomes increasingly complex and time-consuming. If your team is among the majority of organizations that have begun to adopt a DevSecOps approach, much of this burden falls upon you. It’s easy to become quickly overwhelmed when supporting hundreds of containers and developers to ensure that secrets are managed and distributed securely. Accessing Secrets for Machines When developers need secrets for their applications, they must make a request through a defined process, such as creating a ticket or sending an email. The DevSecOps team then provides the requested secrets or updates the developer's access to the central repository where the secrets are stored. While this process frequently ensures the security of sensitive information, it can also introduce challenges and complexities in distributing and managing secrets, such as the overhead needed for an infrastructure team to manage thousands of credentials with requests coming in nonstop anytime a change is required. In an attempt to preserve an organization's security, engineers who might not be familiar with a specific application end up handling a high volume of identical tasks on a daily basis. And as a rule of thumb, any time there's a manual process combined with an overwhelming workload, you're running a high risk of errors compromising the security of sensitive information and your organization's efficiency. These seemingly minor errors can have severe consequences in high-stakes deployments of new features. For example, an extra space or a typo can cause a deployment to fail, leading to a slower time-to-market and potentially impacting business operations. Additionally, as snafus occur and process friction rises, you risk losing the trust of development teams. They never know ahead of time if their secret will work correctly in a production-level environment and may worry about its potential impact on end users. In this case, the secrets are impossible to validate. Your secrets may have worked in all lower testing environments and even an inactive production environment... but when it's time to deploy changes to production, a failure still occurs. Guiding Principles In the aforementioned scenario, the manual process for managing secrets directly opposes the core principles of effective secret management. As a DevSecOps engineer, it's essential to strive for automation in all aspects of the job, including the distribution of secrets. To address this challenge, it's crucial to implement the Zero Trust principle. This means that all access to secrets must be verified and authenticated before granting access... or, as we like to call it, "guilty until proven innocent." On top of Zero Trust, other fundamental principles, like Just-in-Time credentials and continuous monitoring, are also key to success. In the fast-paced world of DevOps, machines access information much more quickly than humans do, making automation of secret generation, rotation, and management essential to reducing the risk of human error. Also, real-time monitoring, alerting, and reporting capabilities are essential to quickly detect and respond to any potential incidents or issues related to secrets. Let's go back to our example and start to unpack the steps needed to align with industry best practices for secrets management.
For starters, the manual generation of secrets must stop and be taken off the plate of the DevSecOps team. There are a couple ways of doing this, which your organization should consider based on its container infrastructure and security requirements. Deploy-Time Secrets These are like access keys or passwords, encrypted and bundled with the application code and stored in the code repository. They are embedded within the code and stored within version control systems like Git. The idea here is to put control in the hands of developers. They can access a tool to request and generate a production secret without ever seeing the value and by simply using a reference to the value. Some key advantages of managing secrets for deploy-time injection: Solid Security - Parameterized values are stored in the source code, so developers only have access to encrypted values. Improved Control - Secrets can be updated or revoked without impacting code. Scalability - Secrets are centrally managed, and developers can begin self-servicing the secrets with the right solutions implemented. Runtime Secrets Runtime secrets, on the other hand, are encrypted, stored and accessed separately from the code and managed by a secure secret management system. These are used at runtime, like user credentials or API keys. Some key advantages of managing secrets for runtime injection: Just-in-Time Access - This minimizes the risk of stand privileges that are easily exploitable. Revoke Access at Any Time - Ensure that sensitive data is only accessed by authorized parties or applications, and that secrets are never hard coded. Dynamic - Your secrets can be updated without performing a redeployment of the application. Using dynamic, parameterized secrets certainly makes sense, whether they’re used upon deployment or in runtime. However, no matter what approach you take, proper use of secrets does involve added layers of complexity. Any time you adopt new tools and processes, and a higher level of developer ownership, you’re necessarily looking at more to manage. You’re also likely to compromise visibility, as monitoring and revocation becomes harder. There are several effective options available for the transformation of deploy-time and runtime secret management. Akeyless, a SaaS platform, offers centralized management and automation for Just-in-Time credentials, secret rotation and access management. Unlike the open-source HashiCorp Vault, Akeyless offers a more scalable approach while providing a Zero Trust level of security for your secrets as they are not visible / accessible to third-party cloud service providers. To Summarize The main difference between deploy-time and runtime secrets is when they are used and how they are stored. Deploy-time secrets are used during the deployment process, while runtime secrets are used while the application runs. Starting out, your organization might opt for deploy-time secret loading, which means a developer will be able to self-service the deployment of secrets as configuration to relevant containers. In our example, this could be a practical first step as they continue the transformation of secret management. Then, eventually, DevSecOps teams are often best off transitioning to runtime secrets by identifying all secrets currently stored in code, migrating them to a secret management system, and updating the code to retrieve secrets at runtime. This process can be complex and time-consuming, but it's essential to ensure the security and privacy of sensitive information in today's fast-paced, dynamic development environments.
0 notes
Text
How to Build a Winning Cloud Transformation Strategy That Actually Drives Business Growth
In today’s hyper-connected digital economy, organizations must continuously evolve or risk falling behind. One of the most impactful ways to drive long-term business growth is by adopting a cloud transformation strategy that aligns with both current operational needs and future scalability goals. Cloud transformation is not just a technology upgrade; it is a business revolution that reshapes how enterprises function, deliver value, and innovate at scale.
Start with Vision-Aligned Objectives
A successful cloud transformation strategy begins with clarity of purpose. Identifying key business objectives, such as faster time-to-market, enhanced customer experiences, cost optimization, or global scalability, and reverse-engineering the cloud framework to support these goals is essential. Rather than lifting and shifting outdated systems into the cloud, the aim should be to reimagine workflows and infrastructures in a way that leverages the inherent flexibility of cloud-native environments.
Embrace a Phased Migration Approach
Attempting a full-scale migration without a structured plan can lead to operational chaos. A phased approach allows for better risk management, employee adaptation, and continuous feedback loops. Begin by classifying workloads based on complexity, criticality, and interdependencies. Low-risk, high-impact applications often make ideal candidates for early-stage migration. With each phase, evaluate and refine both the technical execution and its business impact.
Integrate Cloud Transformation Security Service from Day One
Security is no longer an afterthought; it is the foundation. The rise of distributed cloud infrastructure increases the attack surface, making robust security indispensable. A comprehensive Cloud Transformation Security Service ensures that data integrity, identity access management, and compliance standards are seamlessly integrated into every layer of the transformation journey. From encrypted data transfers to zero-trust architecture, prioritizing cloud security mitigates risk and builds stakeholder trust.
Prioritize Intelligent Automation and AI
To accelerate ROI and minimize human error, integrate intelligent automation into your transformation blueprint. Whether it’s provisioning cloud resources, monitoring network anomalies, or scaling application performance, automation reduces manual intervention and fosters agility. Layering in artificial intelligence allows for predictive analytics, smarter decision-making, and more efficient resource utilization. The synergy of AI and cloud is particularly potent in identifying bottlenecks before they impact business performance.
Build a Culture of Cloud-Native Thinking
Technology alone cannot drive transformation. The people behind the systems must embrace a shift in mindset. Encourage cross-functional collaboration, promote cloud certifications, and instill a DevSecOps culture. This approach empowers teams to rapidly innovate while embedding security and compliance into every development cycle. A cultural transformation ensures that cloud isn’t treated as just an IT function, but as a core business enabler.
Monitor, Measure, and Optimize
Building the strategy is just the beginning its ongoing success hinges on continuous monitoring and optimization. Use key performance indicators (KPIs) tied to business goals to track progress. Metrics such as uptime, latency, user satisfaction, and cost efficiency should be consistently reviewed. Feedback-driven refinement ensures the strategy remains dynamic and responsive to evolving business demands.
Enhance Resilience with a Multi-Cloud Strategy
Single-vendor lock-in can be risky. A multi-cloud or hybrid cloud model allows organizations to harness the strengths of different providers while minimizing dependency. This approach enhances system resilience, geographic redundancy, and compliance flexibility. Multi-cloud environments can be managed efficiently without compromising control or visibility when paired with a unified Cloud Transformation Security Service.
Crafting a winning cloud transformation strategy demands more than just migration; it requires security, scalability, and smart execution. Embedding a strong Cloud Transformation Security Service is key to long-term success. Invensis offers expert cybersecurity solutions, including threat detection, vulnerability assessments, and cloud security audits, to protect and empower your transformation journey.
0 notes
Text

Get ECDE Certified: Build Security Into Every Step of DevOps
Security should be built-in, not bolted on. The Certified DevSecOps Engineer (ECDE) certification equips you with hands-on skills to secure CI/CD pipelines, cloud-native apps, and tools like GitHub and Jenkins. Stay ahead—master DevSecOps today.
Visit: https://www.eccouncil.org/train-certify/certified-devsecops-engineer-ecde/
0 notes
Text
Become a DevOps Master with WiseLearner IT Services

Realize Your Potential in the DevOps World In the fast-changing IT environment, DevOps is a game-changer. DevOps is being adopted by organizations globally to speed up software delivery, enhance collaboration, and provide stable infrastructure. Hence, demand for qualified DevOps experts is on the rise.
At WiseLearner IT Services, we provide a complete DevOps Master Training Program that will prepare you with the knowledge, tools, and hands-on skills to be successful in this fast-moving area.
What Is DevOps Master? A DevOps Master is a professional who is in charge of the whole software delivery pipeline — development and testing all the way through deployment and monitoring. They unite development and operations teams, automate the workflow, and ensure scalable and reliable infrastructure.
With proper training, you can be an organization's star contributor in its digital transformation process.
Why DevOps Master Program at WiseLearner IT Services? Our course is designed for beginners as well as professionals who wish to upgrade their careers. Here's what differentiates us:
Hands-On Learning: Live projects and labs with most-used DevOps tools such as Git, Jenkins, Docker, Kubernetes, Ansible, Terraform, and AWS.
Industry-Specific Curriculum: Study the newest DevOps practices, CI/CD pipelines, containerization, infrastructure as code, and cloud computing.
Trained Trainers: Our trainers have practical industry experience and offer individualized attention throughout your training.
Certification Readiness: Prepare for certificates such as EXIN DevOps Master, Docker Certified Associate, Certified Kubernetes Administrator, and AWS DevOps Engineer.
Flexible Timings: Attend weekday or weekend batches as per your convenience.
Placement Assistance: We help with resume creation, interview preparation, and referrals.
Who Can Join? Software Developers and Testers
System and Cloud Administrators
IT Support Professionals
New Graduates interested in DevOps positions
Anyone interested in automation and cloud technologies
No experience in DevOps? No problem! Our course begins from basics and progresses to advanced material.
Course Highlights DevOps Culture and Practices
Version Control using Git & GitHub
Continuous Integration and Continuous Deployment (CI/CD) using Jenkins
Containerization with Docker and orchestration with Kubernetes
Infrastructure as Code with Ansible and Terraform
Cloud Platforms: AWS and Azure Fundamentals
Monitoring and Logging with Prometheus, Grafana, and ELK Stack
Security in DevOps (DevSecOps) Fundamentals
Take the Leap — Join WiseLearner IT Services Today! Don't miss the opportunity to future-proof your IT career. Become a certified DevOps Master and unlock new exciting job opportunities across the globe.
Come to www.wiselearner.com or reach out to us at [email protected] for more information about joining and batch timings.
WiseLearner IT Services — Your Partner in Professional Growth.
0 notes
Text
DevOps services company in Noida
As businesses in Noida grow rapidly in the digital space, the demand for DevOps services is at an all-time high. Whether you're a startup trying to ship code faster or an enterprise aiming to scale operations, DevOps can transform your entire development and deployment pipeline. But a common dilemma remains: Should you hire a DevOps services company in Noida or work with a freelancer?
This article helps you weigh both options—considering factors like cost, quality, reliability, scalability, and long-term value. By the end, you'll have a clearer understanding of which is the right fit for your business goals.
What Does a DevOps Services Company in Noida Offer?
Before jumping into the comparison, let’s understand what a DevOps services company in Noida typically provides:
End-to-End Automation: CI/CD pipelines, test automation, infrastructure as code (IaC)
Cloud Integration: AWS, Azure, Google Cloud, or hybrid environments
Monitoring & Logging: Real-time system monitoring, alert systems, log analysis
Security & Compliance: DevSecOps practices built into workflows
Scalability: Containerization with Docker, orchestration using Kubernetes
24/7 Support & SLA-based services
Team Collaboration & Agile Practices
These companies usually have multi-domain expertise, large teams, and infrastructure to support businesses of all sizes.
What Do Freelance DevOps Professionals Offer?
Freelancers are individual specialists who may have worked across multiple domains and offer services like:
CI/CD pipeline setup
Script automation
Server configuration and management
Cloud deployments
Performance tuning and basic monitoring
Freelancers are often hired for short-term, project-based work and may work independently or remotely.
1. Expertise and Skill Depth
✅ DevOps Services Company in Noida
Offers a team of experts: developers, cloud architects, DevOps engineers, and QA specialists
Experienced across industries like fintech, e-commerce, healthcare, and logistics
Proven track record with certifications and case studies
✅ Freelancer
Expertise depends on the individual’s experience
May lack broader team collaboration
Might be highly skilled in specific tools but not full-stack DevOps
Verdict: If you're looking for in-depth knowledge, companies offer a more robust and diverse skill set.
2. Project Scope and Scalability
✅ DevOps Services Company in Noida
Capable of handling large-scale and complex projects
Can scale resources up/down based on project needs
Well-versed in compliance, cloud migration, and enterprise integrations
✅ Freelancer
Ideal for small-scale or one-time automation projects
Limited by bandwidth and resources
Scalability is usually restricted to what one person can manage
Verdict: For long-term or complex infrastructure, a DevOps company offers more scalability.
3. Cost Comparison
✅ DevOps Services Company in Noida
May have higher upfront costs
However, services are often backed by SLAs, guarantees, and support
Less risk of delays or rework
✅ Freelancer
Typically more affordable for small tasks or short-term contracts
May charge hourly or project-based
Potential hidden costs due to limited availability or lack of documentation
Verdict: Freelancers are cost-effective for small tasks, but companies provide better value for the long run.
4. Reliability and Accountability
✅ DevOps Services Company in Noida
Operates under contracts, SLAs, and strict timelines
Offers dedicated account managers and round-the-clock support
Provides documentation and transition support
✅ Freelancer
May lack structured timelines or dedicated reporting
Risk of unavailability due to other projects or personal issues
Communication gaps or project abandonment are common concerns
Verdict: Companies are far more reliable and accountable for critical operations.
5. Security & Compliance
✅ DevOps Services Company in Noida
Follows industry security protocols
Implements DevSecOps for security throughout the pipeline
Aware of local and global compliance regulations like GDPR, HIPAA, etc.
✅ Freelancer
May not be updated with the latest compliance laws
Risk of data breaches or poor security practices
Documentation and access control might be weak
Verdict: If your business handles sensitive data, go with a DevOps company that ensures proper security.
6. Support & Maintenance
✅ DevOps Services Company in Noida
24/7 technical support
Maintenance packages and performance audits
Disaster recovery plans included
✅ Freelancer
May not be available for emergency fixes
Often moves on after project completion
Support is usually informal and non-committal
Verdict: For continuous operations and support, companies are the better choice.
When to Choose a Freelancer
You have a very limited budget
Your project is short-term and well-defined
You need quick help for small fixes or initial DevOps setup
You already have a team and just need one expert for a specific task
When to Choose a DevOps Services Company in Noida
You need long-term DevOps strategy and execution
Your business requires scalability, security, and continuous support
You're undergoing cloud migration or digital transformation
Your app handles large traffic, sensitive data, or needs high uptime
You value partnership, documentation, and accountability
Final Thoughts
In the digital age, DevOps is no longer optional — it’s a necessity for performance, security, and speed. While freelancers can be a quick fix for small jobs, they often fall short in terms of long-term value, reliability, and scalability. A DevOps services company in Noida brings structured expertise, dedicated teams, and a strategic approach tailored to your business needs.
If you're serious about growth and digital stability, partnering with a trusted local DevOps company might be the smartest step you take.
Need help getting started? Connect with a top-rated DevOps services company in Noida to discuss your goals, challenges, and how automation can drive your next level of growth.
0 notes
Text
10 Exciting Tech Careers You Might Not Know About (But Should in 2025)
Published by Prism HRC – Leading IT Recruitment Agency in Mumbai
Most people who hear the word "tech" immediately think about jobs such as software developer or data analyst. However, the tech sector is much more diversified and changing extremely fast. Some of the coolest and fastest-rising careers are those that fly under the radar in 2025.
If you're looking into a career in tech or considering your next step, here are 10 lesser-known and high-potential jobs to explore.
1. Prompt Engineer
Why it matters: As AI tools such as ChatGPT emerge, prompt engineers are becoming central to enabling businesses to talk to AI more effectively.
Who it's for: Communicators and creatives who know how to direct AI to provide the right responses.
Skills required: AI fundamentals, copywriting, critical thinking, and experimentation.

2. DevSecOps Specialist
Why it matters: Safety isn't something afterthought; security is done with development pipelines from day one from within DevSecOps.
Who it's for: Sysadmins or developers with some interest in cybersecurity.
Skills needed: CI/CD tooling, cloud platforms, scripting, and compliance in security.
3. XR (Extended Reality) Developer
Why it matters: Virtual reality and augmented reality are transforming how we work, learn, and play.
Who it's for: Developers and designers who care for immersive technology.
Skills required: Unity/Unreal Engine, 3D modeling, C#, and UX design.
4. Ethical Hacker/Penetration Tester
Why it matters: With increasing cyberattacks, businesses require experts to hack their defenses within the law.
Who it's for: Intrigued minds with a sense of vulnerability discovery.
Skills required: networking, ethical hacking tools, and certifications such as CEH.
5. AI Trainer/Annotator
Why it matters: Prior to AI getting intelligent, human assistance is required. Trainers train AI to comprehend and react appropriately.
Who it's for: Detail enthusiasts and domain specialists.
Skills required: language skills, data tagging, and pattern identification.
6. Cloud FinOps Analyst
Why it matters: With companies moving to the cloud, cloud cost management has become paramount.
Who it's for: Data analysis and budgeting enthusiasts with a technical spin.
Skills required: cloud billing software, financial projections, and data visualization.
7. No-Code/Low-Code Developer
Why it matters: These platforms enable businesses to create apps in a jiffy without extensive coding expertise.
Who it's for: Devs who aren't from a classical dev background.
Skills needed: tools such as Bubble, Webflow, PowerApps, and Zapier.
8. Data Ethicist
Why it matters: As data becomes more influential, the ethical concerns surrounding it increase.
Who it's for: Philosophers who care about fairness, privacy, and AI accountability.
Skills needed: philosophy or law background, data governance, and tech literacy.
9. Digital Twin Engineer
Why it matters: Digital twins (virtual copies of physical systems) are revolutionizing manufacturing and healthcare.
Who it's for: Engineers and 3D simulation enthusiasts.
Skills needed: IoT, simulation software, modeling, and real-time data analysis.
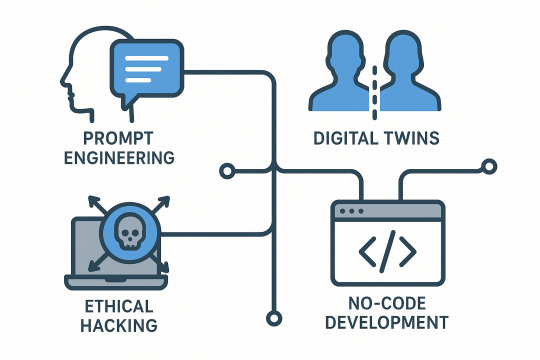
10. Chief Automation Officer
Why it matters: Businesses are automating everything—and require leadership to do it properly.
Who it's for: Tech and operations professionals.
Skills needed: RPA tools, process improvement, change management, and leadership.
Why These Careers Matter in 2025
These jobs are not only "cool" but also they're strategic. They're designing the future of how we live, work, and engage with technology. For job seekers, breaking into these lesser-known industries means fewer competitors, quicker expansion, and an opportunity to dominate niche markets.
If you're seeking advice on how to get into one of these industries, or you're hiring for them, Prism HRC is your go-to partner. We have expertise in bringing today's talent and tomorrow's opportunities together.
- Based in Gorai-2, Borivali West, Mumbai - www.prismhrc.com - Instagram: @jobssimplified - LinkedIn: Prism HRC
#Tech Careers#IT Jobs 2025#Future of Work#Prism HRC#IT Recruitment Mumbai#IT Consulting#Ethical Hacking#Digital Twins#Technology Jobs#Job Market 2025
0 notes
Text
Certified DevSecOps Professional: Career Path, Salary & Skills
Introduction
As the demand for secure, agile software development continues to rise, the role of a Certified DevSecOps Professional has become critical in modern IT environments. Organizations today are rapidly adopting DevSecOps to shift security left in the software development lifecycle. This shift means security is no longer an afterthought—it is integrated from the beginning. Whether you're just exploring the DevSecOps tutorial for beginners or looking to level up with a professional certification, understanding the career landscape, salary potential, and required skills can help you plan your next move.
This comprehensive guide explores the journey of becoming a Certified DevSecOps Professional, the skills you'll need, the career opportunities available, and the average salary you can expect. Let’s dive into the practical and professional aspects that make DevSecOps one of the most in-demand IT specialties in 2025 and beyond.
What Is DevSecOps?
Integrating Security into DevOps
DevSecOps is the practice of integrating security into every phase of the DevOps pipeline. Traditional security processes often occur at the end of development, leading to delays and vulnerabilities. DevSecOps introduces security checks early in development, making applications more secure and compliant from the start.
The Goal of DevSecOps
The ultimate goal is to create a culture where development, security, and operations teams collaborate to deliver secure and high-quality software faster. DevSecOps emphasizes automation, continuous integration, continuous delivery (CI/CD), and proactive risk management.
Why Choose a Career as a Certified DevSecOps Professional?
High Demand and Job Security
The need for DevSecOps professionals is growing fast. According to a Cybersecurity Ventures report, there will be 3.5 million unfilled cybersecurity jobs globally by 2025. Many of these roles demand DevSecOps expertise.
Lucrative Salary Packages
Because of the specialized skill set required, DevSecOps professionals are among the highest-paid tech roles. Salaries can range from $110,000 to $180,000 annually depending on experience, location, and industry.
Career Versatility
This role opens up diverse paths such as:
Application Security Engineer
DevSecOps Architect
Cloud Security Engineer
Security Automation Engineer
Roles and Responsibilities of a DevSecOps Professional
Core Responsibilities
Integrate security tools and practices into CI/CD pipelines
Perform threat modeling and vulnerability scanning
Automate compliance and security policies
Conduct security code reviews
Monitor runtime environments for suspicious activities
Collaboration
A Certified DevSecOps Professional acts as a bridge between development, operations, and security teams. Strong communication skills are crucial to ensure secure, efficient, and fast software delivery.
Skills Required to Become a Certified DevSecOps Professional
Technical Skills
Scripting Languages: Bash, Python, or PowerShell
Configuration Management: Ansible, Chef, or Puppet
CI/CD Tools: Jenkins, GitLab CI, CircleCI
Containerization: Docker, Kubernetes
Security Tools: SonarQube, Checkmarx, OWASP ZAP, Aqua Security
Cloud Platforms: AWS, Azure, Google Cloud
Soft Skills
Problem-solving
Collaboration
Communication
Time Management
DevSecOps Tutorial for Beginners: A Step-by-Step Guide
Step 1: Understand the Basics of DevOps
Before diving into DevSecOps, make sure you're clear on DevOps principles, including CI/CD, infrastructure as code, and agile development.
Step 2: Learn Security Fundamentals
Study foundational cybersecurity concepts like threat modeling, encryption, authentication, and access control.
Step 3: Get Hands-On With Tools
Use open-source tools to practice integrating security into DevOps pipelines:
# Example: Running a static analysis scan with SonarQube
sonar-scanner \
-Dsonar.projectKey=myapp \
-Dsonar.sources=. \
-Dsonar.host.url=http://localhost:9000 \
-Dsonar.login=your_token
Step 4: Build Your Own Secure CI/CD Pipeline
Practice creating pipelines with Jenkins or GitLab CI that include steps for:
Static Code Analysis
Dependency Checking
Container Image Scanning
Step 5: Monitor and Respond
Set up tools like Prometheus and Grafana to monitor your applications and detect anomalies.
Certification Paths for DevSecOps
Popular Certifications
Certified DevSecOps Professional
Certified Kubernetes Security Specialist (CKS)
AWS Certified Security - Specialty
GIAC Cloud Security Automation (GCSA)
Exam Topics Typically Include:
Security in CI/CD
Secure Infrastructure as Code
Cloud-native Security Practices
Secure Coding Practices
Salary Outlook for DevSecOps Professionals
Salary by Experience
Entry-Level: $95,000 - $115,000
Mid-Level: $120,000 - $140,000
Senior-Level: $145,000 - $180,000+
Salary by Location
USA: Highest average salaries, especially in tech hubs like San Francisco, Austin, and New York.
India: ₹9 LPA to ₹30+ LPA depending on experience.
Europe: €70,000 - €120,000 depending on country.
Real-World Example: How Companies Use DevSecOps
Case Study: DevSecOps at a Fintech Startup
A fintech company integrated DevSecOps tools like Snyk, Jenkins, and Kubernetes to secure their microservices architecture. They reduced vulnerabilities by 60% in just three months while speeding up deployments by 40%.
Key Takeaways
Early threat detection saves time and cost
Automated pipelines improve consistency and compliance
Developers take ownership of code security
Challenges in DevSecOps and How to Overcome Them
Cultural Resistance
Solution: Conduct training and workshops to foster collaboration between teams.
Tool Integration
Solution: Choose tools that support REST APIs and offer strong documentation.
Skill Gaps
Solution: Continuous learning and upskilling through real-world projects and sandbox environments.
Career Roadmap: From Beginner to Expert
Beginner Level
Understand DevSecOps concepts
Explore basic tools and scripting
Start with a DevSecOps tutorial for beginners
Intermediate Level
Build and manage secure CI/CD pipelines
Gain practical experience with container security and cloud security
Advanced Level
Architect secure cloud infrastructure
Lead DevSecOps adoption in organizations
Mentor junior engineers
Conclusion
The future of software development is secure, agile, and automated—and that means DevSecOps. Becoming a Certified DevSecOps Professional offers not only job security and high salaries but also the chance to play a vital role in creating safer digital ecosystems. Whether you’re following a DevSecOps tutorial for beginners or advancing into certification prep, this career path is both rewarding and future-proof.
Take the first step today: Start learning, start practicing, and aim for certification!
1 note
·
View note
Text
#devsecops foundation certification#certified devsecops foundation#devsecops certification#devsecops certificate#certified devsecops#gsdc devsecops certification#devsecops certification gsdc#certified devsecops engineer#devsecops engineer certification
0 notes
Text
SAST, DAST & DevSecOp
Job title: SAST, DAST & DevSecOp Company: Ciel HR Job description: and DevSecOps Automation Certification (GCSA), Certified DevSecOps Engineer (CDE) Compulsory: Certified Ethical Hacker (CEH), B… Expected salary: Location: Maharashtra – Bangalore, Karnataka Job date: Tue, 08 Apr 2025 06:44:32 GMT Apply for the job now!
0 notes
Text
Master Cloud Security Coaching with Gritty Tech
Understanding Cloud Security Coaching
In the digital era, cloud adoption is accelerating faster than ever. However, this surge also brings escalating security risks. Gritty Tech's Cloud Security Coaching is crafted to empower individuals and enterprises with the expertise needed to protect their cloud assets. Our program delivers practical, comprehensive training to help you master the complexities of cloud security For More…
The Growing Importance of Cloud Security
With businesses increasingly relying on cloud services, security breaches can have devastating consequences. Outdated security models are insufficient against modern threats. Gritty Tech's coaching equips you with cutting-edge skills to safeguard data, ensure compliance, and maintain stakeholder trust.
What Gritty Tech Offers in Cloud Security Coaching
At Gritty Tech, our Cloud Security Coaching is a dynamic, hands-on experience designed to:
Strengthen foundational and advanced cloud security skills
Identify security vulnerabilities and mitigate risks
Deploy cloud infrastructure following security best practices
Navigate global compliance standards
We customize learning paths to fit your current skill level, whether you are a beginner or an experienced professional.
Core Elements of Gritty Tech's Coaching
Cloud Basics and Security Architecture
Kick-start your journey with a solid understanding of cloud principles and the shared responsibility model, forming the backbone of secure cloud architecture.
Identity and Access Management (IAM)
Gain mastery over:
Least privilege principles
Role-Based Access Control (RBAC)
Single Sign-On (SSO) and federated identity management
Data Protection Strategies
Secure sensitive information with:
Encryption methods for data at rest and in transit
Key Management Systems (KMS)
Data classification and secure backup solutions
Securing Cloud Networks
Adapt to the new cloud perimeter by learning:
Virtual Private Cloud (VPC) architecture
Network segmentation and firewall configurations
Threat detection and response strategies
DevSecOps Integration
Embed security across your development lifecycle with training on:
Infrastructure as Code (IaC) security
Secure CI/CD pipelines
Automated vulnerability scanning
Governance, Risk, and Compliance
Understand the essentials of:
GDPR, HIPAA, PCI DSS, and ISO 27001 compliance
Risk assessments and governance policies
Preparing for audits
Incident Management
Prepare for potential breaches with:
Incident detection and response
Cloud forensics techniques
Business continuity and disaster recovery planning
Gritty Tech's Exclusive Benefits
Tailored Coaching Plans: Personalized paths based on your goals
Practical Exercises: Real-world attack and defense simulations
Expert Mentorship: Learn from seasoned cloud security professionals
Certification Readiness: Extensive prep for top industry certifications
Lifetime Learning Access: Continuous updates and resource availability
Ideal Candidates for Cloud Security Coaching
Our coaching is perfect for:
IT professionals transitioning to the cloud
Cybersecurity analysts and engineers
Cloud architects and developers
Organizations seeking workforce upskilling
Platforms and Tools Covered
Gritty Tech provides in-depth training on platforms like:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform (GCP)
Oracle Cloud Infrastructure (OCI)
We also dive into tools such as Kubernetes, Terraform, HashiCorp Vault, and more.
Practical Experience through Labs and Projects
We emphasize action through:
Interactive labs
Capture the Flag (CTF) exercises
Real-world project simulations
These experiences bridge the gap between theory and practice.
Success Stories from Gritty Tech
Our alumni have advanced careers in leading global companies, securing critical cloud environments and leading security initiatives.
Staying Ahead with Gritty Tech
Gritty Tech continuously updates its courses to include:
Latest threat intelligence
New regulatory requirements
Cutting-edge tools and methodologies
Certification Training Support
We thoroughly prepare you for:
AWS Certified Security - Specialty
Azure Security Engineer Associate
Google Professional Cloud Security Engineer
Certified Cloud Security Professional (CCSP)
You’ll receive study materials, mock exams, and coaching guidance throughout your certification journey.
Learning Models at Gritty Tech
Flexible options to suit your needs:
Live Online Sessions
Self-Paced Learning
Corporate Onsite Training
Choose what fits your schedule and learning style.
Pricing and Enrollment
Gritty Tech offers:
Individual Training Packages
Corporate Team Training
Enterprise-Level Custom Solutions
Contact Gritty Tech today for a tailored quote based on your needs.
Frequently Asked Questions
Do I need prior cloud experience?
No. Our beginner to expert tracks ensure everyone can start and progress confidently.
What is the course duration?
Courses vary from intensive 4-week tracks to comprehensive 6-month programs.
Will I receive a certificate?
Yes. You will get a Gritty Tech completion certificate and support toward industry certifications.
Is lifetime access included?
Yes. All learners enjoy lifetime access to materials and updates.
What support is available?
Gritty Tech offers 24/7 learner support via multiple communication channels.
Why Choose Gritty Tech for Cloud Security Coaching?
Choosing Gritty Tech means choosing a future where cloud security is second nature. Our practical approach, expert coaching, and continuous learning resources ensure you not only learn but excel.
Secure your cloud future today with Gritty Tech's Cloud Security Coaching — where knowledge meets resilience. Connect with us now and start building your cloud security expertise!
0 notes
Text
The Benefits of Working in a DevOps Environment
Why DevOps is Transforming the IT Industry

Experience the power of DevOps training in Bangalore—streamline development and operations with Eduleem.
DevOps has revolutionized software development by fostering a culture of collaboration between development and operations teams. It enables faster deployment, improved efficiency, and continuous monitoring—crucial for modern IT organizations.
By enrolling in a DevOps training course in Bangalore, professionals can gain in-depth knowledge of automation, cloud computing, and continuous delivery pipelines. Learning from an industry-recognized DevOps institute in Bangalore prepares individuals to handle real-world challenges in AWS, Azure, and GCP environments.
Top Benefits of Working in a DevOps Environment
1️⃣ Faster Software Development & Deployment
Continuous Integration & Deployment (CI/CD) enables teams to release software updates quickly and reliably.
Automated pipelines reduce manual intervention, minimizing deployment failures.
2️⃣ Enhanced Collaboration & Efficiency
DevOps fosters a culture of shared responsibility between developers, operations, and security teams.
Reduces bottlenecks in software development and deployment cycles.
3️⃣ Improved Security & Compliance
Integrates security practices into the development lifecycle (DevSecOps).
Ensures compliance with industry regulations and cloud security best practices.
4️⃣ Automation for Increased Productivity
Reduces human errors by automating infrastructure provisioning, monitoring, and scaling.
Speeds up software delivery through tools like Jenkins, Docker, Kubernetes, and Terraform.
5️⃣ Better Career Growth & High-Paying Jobs
Companies actively seek DevOps professionals with expertise in cloud platforms.
The demand for DevOps engineers is increasing, making it a highly lucrative career path.
Master AWS & Cloud Computing—Your Ultimate Guide Looking to enhance your cloud computing skills? Check out our AWS Certified Solutions Architect—Associate Exam: Preparation Guide and get certified today!
Real-World Impact: How DevOps Helps Businesses
Companies like Netflix, Amazon, and Google have adopted DevOps methodologies to achieve rapid innovation and scalability. Here’s how DevOps transforms businesses:
📌 Netflix: Uses CI/CD automation to release new features hundreds of times a day. 📌 Amazon: Implements DevOps best practices to handle millions of daily transactions seamlessly. 📌 Google: Uses containerization (Docker & Kubernetes) to scale its cloud infrastructure efficiently.
If you want to build a future-proof career, enrolling in the best DevOps training in Bangalore will help you gain expertise in automation, cloud computing, and CI/CD pipelines.
How Eduleem’s DevOps Course Can Help You Succeed
Eduleem offers the best DevOps training in Bangalore, designed for both beginners and experienced professionals. Our training includes:
🔥 Hands-on Labs: Work on real-world DevOps projects with AWS, Azure, and GCP. 🔧 Live Practical Sessions: Master CI/CD tools, Kubernetes, Docker, and Terraform. 📜 Globally Recognized Certification: Gain expertise from the best DevOps institute in Bangalore. 🚀 Career Support & Placement Assistance: Get placed in top IT companies!
Whether you're aiming to become a DevOps engineer, cloud architect, or automation specialist, learning from the best institute for DevOps in Bangalore can set you apart from the competition.
Conclusion: Take Your Career to the Next Level with Eduleem
A DevOps career offers immense growth opportunities, high salaries, and job stability. If you’re ready to transform your future, getting trained at the best DevOps training institute in Bangalore is your first step toward success.
🎯 Enroll in Eduleem’s DevOps Course Today!
#aws#azure#devops#cloudsecurity#cloudsolutions#DevOpsTraining#CloudComputing#Automation#DevOpsCourse#BestDevOpsTraining#CI_CD#AWS#Azure#GCP#Eduleem
0 notes
Text
How to Hire DevSecOps Developers: A Step-by-Step Guide

Cybersecurity has become a paramount concern for the majority of the businesses and is a top priority in the majority of the development processes. The demand for DevSecOps developers has outgrown because they embed security in every stage of the software development lifecycle to reduce risks and improve overall system resilience.
Data protection and uptime are vital for your SaaS business which is why you need to have a skilled DevSecOps team for ensuring security, scalability, and compliant applications. For this let’s understand what are the right skills, hiring process, and recruitment strategies you must consider when you hire software engineers for this purpose.
A Step-by-Step Hiring Guide to Building a Strong and Secure DevSecOps Team
State your hiring requirements
List the primary duties and competencies that your DevSecOps developer must possess before you begin your search. Take into account:
Proficiency in cloud security - familiarity with AWS, Azure, or Google Cloud.
Knowledge of automation and CI/CD: familiarity with Kubernetes, Jenkins, and GitLab CI/CD.
Comprehending security frameworks like NIST, SOC 2, and GDPR is essential for threat modelling and security compliance.
The hiring process is streamlined and the right talent is drawn in when these requirements are clearly stated.
Use reputed platforms to source talent
Although it can be difficult to find great talent, the following platforms can help:
Job portals: Indeed, Glassdoor, and LinkedIn for full-time roles; freelance platforms: Upwork and Toptal for contract-based recruiting.
IT staffing agencies: specialized companies that offer talent that is ready for employment after pre-screening applicants. Uplers is a hiring platform that unlike IT staffing agencies provides you AI-vetted top talent from India in a 4-step process.
Without having to spend months on hiring, SaaS organizations can discover skilled DevSecOps developers more rapidly by collaborating with such hiring platforms.
Screen and evaluate candidates
Make sure you carry out comprehensive evaluations to ensure you recruit the top talent:
Technical interviews: Assess their familiarity with cloud security best practices and DevSecOps tools.
Practical exercises: Evaluate their proficiency in automating security checks in CI/CD pipelines.
Assessment of soft skills: Verify excellent problem-solving and teamwork capabilities.
Long-term success for SaaS organizations depends on hiring DevSecOps developers who can comprehend the challenges of protecting cloud-based apps.
Offer competitive compensation and benefits
Offering competitive pay and benefits is crucial given the growing demand for DevSecOps expertise. Take into account:
Flexibility in remote work: Many DevSecOps engineers choose remote positions.
Opportunities for continuous learning: Discuss certifications and training such as CISSP or AWS Security.
Alluring benefits packages: Offering competitive pay helps you retain top developers.
Hiring software engineers that can work with DevSecOps experts on secure coding techniques may also be necessary if you require more backend help. You could also use free tools like the Uplers salary benchmarking tool to compare, contrast, and adjust your compensation offering with the industry standards.
Onboarding and retention strategies
Long-term success is ensured by a seamless onboarding process for DevSecOps developers:
Establish clear security policies and workflows to incorporate them into your team.
Assign mentors to assist them in understanding internal security procedures.
Promote ongoing development via security research and training.
Retaining top security staff lowers risks, improves compliance, and increases system resilience for SaaS organizations.
Summing Up
Integrating security into your software development process requires hiring the best DevSecOps developers. You may create a robust DevSecOps team by establishing clear requirements, using IT staffing companies, and carrying out in-depth assessments.
Investing in qualified experts guarantees long-term security and efficiency. Having a proactive security plan is essential for SaaS organizations; and no longer a choice.
0 notes