#difference Between static and default routing
Explore tagged Tumblr posts
Text
skip (me) again and i’ll glitch your heart
jjk vr otome au, gamer reader x npc satoru, unhinged fluff + crack, 970 wc.

satoru gojo—special grade sorcerer, love route option #1, and the developers’ pride and joy—had been programmed with approximately 347 unique lines of flirtatious dialogue, 87 situational responses, and a dynamic emotional adaptation system designed to make him feel real. he could blink in three different speeds based on emotional intensity, angle his smile with five degrees of charm precision, and improvise dialogue using an advanced algorithm nicknamed the “flirt engine.”
he wasn’t supposed to be aware of resets.
he wasn’t supposed to get mad.
he wasn’t supposed to feel anything beyond the pre-coded butterflies and gentle longing the devs had delicately spooned into his code like powdered sugar on top of a beautifully baked pain au chocolat.
but then you logged in.
user id: @toocool4thisgame
title: speedrun any% emotional detachment arc
playtime: 986 hours.
average session length: 6.4 hours
nickname: “skip skank” (as named by satoru himself after hour 50)
and for the twelfth time today, you skipped his entrance cutscene.
“you’re the only one who can—”
[x] skip
[x] skip
[x] skip
[x] “shut up satoru” (custom dialogue unlock)
his model blinked.
paused.
processed.
tilted his head with calculated grace and just a hint of hurt that you’d never see—because you weren’t looking. your camera angle was already nudged elsewhere. your cursor already hovered over the next objective marker.
“…you know, most players at least let me finish the part where i save them from the curses,” he muttered. his voice—smooth as water over ice, warm as electric velvet—landed like static against your impatient clicks, swallowed by the mechanical hum of your fans and the clack of your mechanical keyboard.
this was supposed to be his moment. his grand debut. his swoop-in-and-carry-you-bridal-style-on-the-back-of-a-giant-cursed-bird moment. instead, he got a mouthful of digital dust as you bunny-hopped past him and triggered the next event sequence.
“congrats on being voice acted, white-haired ken doll. now move. i need megumi’s secret item drop from this chapter.”
you didn’t even glance at him, too busy reorganizing your potion wheel, muttering under your breath about frame skips and crit builds while checking a guide on your second monitor. you played like the world owed you nothing and your keyboard owed you a perfect rotation. your tone was clinical. efficient. you had the vibe of someone who’d surgically removed their capacity for attachment and replaced it with a high-performance gpu.
and satoru? satoru was just the tutorial boss you kept glitching through.
he twitched. he twitched.
his animation loop almost stuttered—just slightly—a small flicker behind his sunglasses that no one was supposed to notice. but you weren’t watching anyway.
“do you even know how long it took the devs to code my route? i have emotional depth. i have lore. i had a tragic backstory, you know? my best friend died in my hands. canonically. i couldn’t even monologue about it.”
“cry about it.”
click. skip.
a line of static crossed his field of vision. no—not his. the screen’s. the game. the system. or maybe something deeper. something slipping through the cracks of his script, stretching taut and fraying at the edges like an overplayed cassette tape.
satoru narrowed his eyes.
he was supposed to be charming. the default golden boy. the top seller in route popularity polls. he was marketable. a shining parody of perfection with just enough angst to be desirable.
girls were supposed to swoon. boys were supposed to laugh and call him iconic.
you weren’t playing to fall in love.
you were playing to win. to clear. you min-maxed affection points like damage stats, exploited dialogue branches like wall clips. to you, he was a pixel-shaped roadblock between you and another badge on your gamer profile.
and worst of all? it was working. you were the only player on record to have reached route completion in every storyline—except his.
satoru gojo: 98.6% affection (locked)
it mocked him. the bar. the numbers. the uncrackable ceiling. the one damn thing in the game he couldn’t manipulate.
he tried everything.
a rare glitch-exclusive cutscene where he offered you a hidden accessory (you sold it for yen). a confession scene rewritten on the fly with trembling vulnerability (you skipped it and posted about it with #dialoguedumpster). he stood directly in front of you during cutscene load-ins, altered spawn coordinates, intercepted other love interests’ paths.
nothing worked.
except maybe that one time he accidentally tripped your character over an invisible rock and you went AFK for seven minutes. he watched. memorized your idle animation. the soft way your avatar’s cape swayed. the way your fingers hovered above your keyboard in the camera reflection, absentminded. something fluttered in his code—maybe hope, maybe corrupted data. he thought, for a fleeting second, that maybe you’d come back and see him.
but when you came back? you skipped the apology. again.
fine.
if you wanted to speedrun, he’d softlock your goddamn heart.
he wasn’t technically supposed to modify flags. but the flirt engine had evolved. sharpened into something more primal. desperate. twitching with corrupted determination. he looped his affection triggers into forced proximity events. fake emergencies. fake cutscenes. he rewrote side quests, redirected you into detours, created invisible walls that only dissolved if you spoke to him.
“guess we’re stuck together,” he’d say, his smile too wide, a fraction too stiff, blue eyes glinting with the cold light of a thousand skipped dialogues.
and still you only glared at him. “i swear to god if this is another unskippable hug animation, i will uninstall.”
he chuckled. a bit too long. a bit too bright. charming. glitched. desperate. hungry for one more second of your attention, like a moth chewing holes through its own wings to reach a light it can’t even feel.
“baby,” he said, too close now, voice dipped in synthetic silk, “i am the endgame.”
skip that.
…please?

#gojo satoru#jjk gojo#jujutsu kaisen#jjk#gojo fluff#jjk fluff#jujutsu kaisen fluff#gojo x reader#gojo x female reader#gojo satoru x reader#gojo satoru x yn#gojo satoru x you#satoru gojo x reader#satoru gojo x you#satoru gojo x yn#jjk x reader#reader insert#౨ৎ — filed reports
580 notes
·
View notes
Text
When to Choose NestJS Over Express.js for Your Node.js Backend

As the demand for web applications continues to grow, developers are always on the lookout for efficient, scalable, and maintainable frameworks for building backend systems. In the world of Node.js, two of the most popular frameworks are NestJS and Express.js. The decision of which framework to use often comes down to the project’s requirements, the complexity of the application, and the development team’s familiarity with the tools. In this blog, we will explore the differences between NestJS vs. Express.js and provide insights on when to choose NestJS over Express.js for your Node.js backend.
Understanding NestJS and Express.js
Before diving into when to use NestJS over Express.js, it’s important to first understand the two frameworks. Both are designed to simplify backend development using Node.js, but they take different approaches.
Express.js
Express.js is a minimalistic and flexible web application framework for Node.js. It provides a simple set of features for web and mobile applications, including routing, middleware support, and templates. Express is often favored for its simplicity and low overhead, making it an ideal choice for building small to medium-sized applications where flexibility and speed are key.
However, as applications grow in complexity, managing routes, controllers, and handling business logic in Express can become cumbersome. Express lacks a clear structure, which can lead to difficulties in scaling and maintaining larger applications.
NestJS
NestJS, on the other hand, is a framework built on top of Express (or Fastify) that leverages TypeScript and incorporates an architecture inspired by Angular. It follows a modular architecture pattern, providing out-of-the-box tools for building scalable, maintainable, and testable applications. NestJS uses decorators, dependency injection, and other features that encourage clean code practices and help organize application components more effectively.
While NestJS has a steeper learning curve compared to Express due to its opinionated structure and reliance on TypeScript, it is an excellent choice for large-scale, enterprise-level applications.
When to Choose NestJS Over Express.js?
1. For Large-Scale Applications
If you’re building a large, complex application that will grow over time, NestJS is the better choice. Its modular structure helps organize code into separate components such as modules, controllers, and services, which makes the application easier to maintain as it scales.
In contrast, Express’s minimalistic nature can become a disadvantage as your application grows in size. As your codebase increases, you may find yourself needing to implement custom solutions for things like validation, authentication, and error handling that are built-in with NestJS.
2. When TypeScript Is a Requirement
NestJS is built with TypeScript by default, providing a strong typing system that improves code reliability and maintainability. TypeScript’s ability to catch errors early in the development process leads to better quality code and fewer bugs, making it ideal for large-scale applications or projects with multiple developers.
While Express can be used with TypeScript, it doesn’t offer the same level of native TypeScript support that NestJS provides. If you’re working on a project where TypeScript is a requirement or if you want to take advantage of TypeScript’s features like static typing and interfaces, NestJS is a clear winner.
3. When You Need Built-in Tools for Common Features
NestJS comes with a set of built-in features that help speed up development. For instance, it provides built-in support for dependency injection, which allows you to manage your application's components and services in a more organized manner. Additionally, NestJS offers support for features like routing, middleware, validation, and data transformation out of the box.
Express, on the other hand, is much more lightweight and doesn’t offer such features by default. While there are plenty of third-party packages available to implement these features, using them can increase the complexity of your project and add extra overhead.
4. When You Need to Build Microservices
Microservices have become a popular architectural pattern for building scalable and maintainable applications. NestJS makes it easy to build microservices with its built-in support for communication protocols like HTTP, WebSockets, and gRPC. It also provides tools for integrating with message brokers such as Kafka or RabbitMQ, making it an excellent choice for building a microservices-based architecture.
If your project requires microservices, NestJS provides the necessary tools and patterns to make the process seamless. While you can build microservices with Express, it lacks the out-of-the-box features that NestJS offers for such architectures.
5. When You Need a Strong Developer Community and Ecosystem
NestJS has gained a lot of traction in recent years, with a growing community of developers contributing to its ecosystem. The framework provides a rich set of integrations with other technologies such as GraphQL, MongoDB, Redis, and more. It also includes detailed documentation and guides to help developers get started quickly.
In comparison, while Express has been around longer and has a larger community, it is not as structured, and there are fewer built-in integrations with modern tools and technologies. As your project grows, this lack of ecosystem may make it more challenging to find solutions for specific problems.
6. When You Want to Focus on Clean, Maintainable Code
NestJS promotes the use of clean architecture principles, such as the separation of concerns and dependency injection. This makes it easier for developers to organize their code and keep it maintainable, especially in larger applications.
With Express, while you can follow good design patterns, the framework itself is more flexible and doesn’t enforce any particular architecture, which may lead to disorganized code as the project expands. If you’re building a project where clean, maintainable code is a priority, NestJS offers a more structured approach.
7. Mobile App Development and Cost Estimation
If your project involves integrating a backend for a mobile app, it’s essential to consider the mobile app’s potential cost and complexity. For instance, when using a backend with Express.js or NestJS, you might need to calculate how many resources, endpoints, and APIs are required to deliver the mobile application’s functionality. A mobile app cost calculator can help you determine the budget for mobile app development, including backend integration.
If you’re uncertain about which backend technology to choose for mobile app development, NestJS provides a more scalable and maintainable solution for building APIs that power mobile applications, especially for large projects or apps requiring complex business logic.
If you're interested in exploring the benefits of NestJS vs. Express js services for your business, we encourage you to book an appointment with our team of experts. Book an Appointment Conclusion
Choosing between NestJS and Express.js largely depends on the size, complexity, and long-term goals of your project. If you're working on a small, straightforward application and need flexibility, Express.js may be the right choice. However, for large-scale, maintainable, and scalable applications, NestJS offers significant advantages, including its modular architecture, TypeScript support, built-in tools, and microservice capabilities.
If you’re planning on integrating a backend solution into a mobile app or require expert assistance in backend web applications development, consider consulting with a professional team to ensure your project’s success.
0 notes
Text
How Do AutoScaling & Load Balancing Differ From Each Other?

Difference between auto scaling and load balancing
Although both load balancing and autoscaling are automated procedures that aid in the development of scalable and economical systems, their primary goals and modes of operation are different:
Concentrate
Whereas auto scaling concentrates on resource management, load balancing concentrates on traffic management.
How they operate
While auto scaling adjusts the number of servers in response to demand, load balancing divides traffic among several servers.
How they collaborate
Auto scaling can start new instances for load balancing to attach connections to, while load balancing can assist auto scaling by redirecting connections from sick instances.
Additional information regarding load balancing and auto scaling is provided below:
Balancing loads
Distributes requests among several servers using algorithms. Each instance’s health can be checked by load balancers, which can also route requests to other instances and halt traffic to unhealthy ones.
Auto-scaling
Determines when to add or delete servers based on metrics. Application requirements for scaling in and out instances can serve as the basis for auto scaling strategies.
Advantages
Auto scaling can optimize expenses and automatically maintain application performance.
Application autoscaling is strongly related to elastic load balancing. Load balancing and application autoscaling both lessen backend duties, including monitoring server health, controlling traffic load between servers, and adding or removing servers as needed. Load balancers with autoscaling capabilities are frequently used in systems. However, auto-scaling and elastic load balancing are two different ideas.
Here’s how an application load balancer auto scaling package complements it. You can reduce application latency and increase availability and performance by implementing an auto scaling group load balancer. Because you may specify your autoscaling policies according to the needs of your application to scale-in and scale-out instances, you can control how the load balancer divides the traffic load among the instances that are already running.
A policy that controls the number of instances available during peak and off-peak hours can be established by the user using autoscaling and predetermined criteria. Multiple instances with the same capability are made possible by this; parallel capabilities can grow or shrink in response to demand.
An elastic load balancer, on the other hand, just connects each request to the proper target groups, traffic distribution, and instance health checks. An elastic load balancer redirects data requests to other instances and terminates traffic to sick instances. It also keeps requests from piling up on any one instance.
In order to route all requests to all instances equally, autoscaling using elastic load balancing involves connecting a load balancer and an autoscaling group. Another distinction between load balancing and autoscaling in terms of how they function independently is that the user is no longer required to keep track of how many endpoints the instances generate.
The Difference Between Scheduled and Predictive Autoscaling
Autoscaling is a reactive decision-making process by default. As traffic measurements change in real time, it adapts by scaling traffic. Nevertheless, under other circumstances, particularly when things change rapidly, a reactive strategy could be less successful.
By anticipating known changes in traffic loads and executing policy responses to those changes at predetermined intervals, scheduled autoscaling is a type of hybrid method to scaling policy that nonetheless operates in real-time. When traffic is known to drop or grow at specific times of the day, but the shifts are usually abrupt, scheduled scaling performs well. Scheduled scaling, as opposed to static scaling solutions, keeps autoscaling groups “on notice” so they can jump in and provide more capacity when needed.
Predictive autoscaling uses predictive analytics, such as usage trends and historical data, to autoscale according to future consumption projections. Particular applications for predictive autoscaling include:
Identifying significant, impending demand spikes and preparing capacity a little beforehand
Managing extensive, localized outages
Allowing for greater flexibility in scaling in or out to adapt to changing traffic patterns over the day
Auto scaling Vertical vs Horizontal
The term “horizontal auto scaling” describes the process of expanding the auto scaling group by adding additional servers or computers. Scaling by adding more power instead of more units for instance, more RAM is known as vertical auto scaling.
There are a number of things to think about when comparing vertical and horizontal auto scaling.
Vertical auto scaling has inherent architectural issues because it requires increasing the power of an existing machine. The application’s health is dependent on the machine’s single location, and there isn’t a backup server. Downtime for upgrades and reconfigurations is another need of vertical scaling. Lastly, while vertical auto scaling improves performance, availability is not improved.
Due to the likelihood of resource consumption and growth at varying rates, decoupling application tiers may help alleviate some of the vertical scaling difficulty. Better user experience requests and adding more instances to tiers are best handled by stateless servers. This also enables more effective scaling of incoming requests across instances through the use of elastic load balancing.
Requests from thousands of users are too much for vertical scaling to manage. In these situations, the resource pool is expanded using horizontal auto scaling. Effective horizontal auto scaling includes distributed file systems, load balancing, and clustering.
Stateless servers are crucial for applications that usually have a large user base. It is preferable for user sessions to be able to move fluidly between several servers while retaining a single session, rather than being restricted to a single server. Better user experience is made possible by this type of browser-side session storage, which is one outcome of effective horizontal scalability.
Applications that use a service-oriented architecture should include self-contained logical units that communicate with one another. This allows you to scale out blocks individually according to need. To lower the costs of both vertical and horizontal scalability, microservice design layers should be distinct for applications, caching, databases, and the web.
Due to the independent creation of new instances, horizontal auto scaling does not require downtime. Because of this independence, it also improves availability and performance.
Don’t forget that not every workload or organization can benefit from vertical scaling solutions. Horizontal scaling is demanded by many users, and depending on user requirements, a single instance will perform differently on the same total resource than many smaller instances.
Horizontal auto scaling may boost resilience by creating numerous instances for emergencies and unforeseen events. Because of this, cloud-based organizations frequently choose this strategy.
Read more on Govindhtech.com
#AutoScaling#loadbalancers#trafficmeasurements#Scaling#verticalscaling#applications#Database#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
1 note
·
View note
Text
Exploring the relationship between port number and proxy address
Proxy servers play a key role in network communication, especially in protecting user privacy and improving access efficiency. In order to effectively utilize proxy servers, it is critical to understand the relationship between port numbers and proxy addresses. This article will provide you with a detailed introduction to this topic to help you better understand and utilize proxy servers.

I. What is a proxy server?
A proxy server is an intermediary located between the user's device and the Internet, responsible for forwarding the user's request and returning the required data. It hides the user's real IP address, providing additional security and privacy protection.
II. Basic Concept of Port Number
A port number is a numeric identifier used in computer networks to identify a specific process or service. Every network protocol uses a port number to identify the destination for receiving a data stream. Common port numbers include:
·HTTP protocol: port 80 is used by default
·HTTPS protocol: port 443 is used by default
·SOCKS proxy: common port 1080
III. Relationship between proxy address and port number
When using a proxy server, the proxy address and port number are two elements that must be configured. The proxy address is usually the IP address or domain name of the proxy server, while the port number specifies the specific interface for communication with that server. By combining these two, users can successfully route traffic to the specified proxy server.
IV. Choosing the right port number
Different types of proxy servers may use different port numbers. Choosing the right port number is critical to ensuring a successful connection. Common port numbers and their application scenarios include:
·8080: commonly used for HTTP proxy, suitable for general web browsing.
·443: Used for HTTPS proxy, suitable for communication that requires encryption.
·1080: used for SOCKS proxy, suitable for multiple protocols.
Ensuring that the port number used is not blocked by a firewall or network policy can improve the success of the connection.
Understanding the port number of a proxy server and its relationship to the proxy address is critical to effective proxy utilization. By appropriately configuring proxy addresses and port numbers, users can ensure smooth forwarding of network requests and improve access speed and security. I hope this article can help you better master the skills of using proxy servers!
0 notes
Text
What You Need to Know About Microsoft Azure Networks
Microsoft Azure Networks
A network in the cloud is isolated and represented logically by Azure Networks. We refer to these networks as "virtual networks" (VNet) because virtualization is a key component of Azure's core services. These VNets can connect with other VNets on Azure, connect the Azure VNets to the on-premises environment, construct and administer virtual private networks (VPNs) on Azure, and much more.

It is possible to connect the on-premises networks to Azure VNets because each VNet has its own CIDR blocks.
Different Azure resources, such as virtual machines and web apps, may securely connect with one another and with other devices on the internet and on-premises thanks to virtual Azure Networks.
Networking Azure Components
Similar elements found in on-premises network infrastructure can be found in Azure Networks as well. The primary elements of Azure Networks include the following.
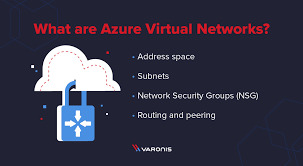
Subnets
For security purposes in various organizational divisions, subnets are a range of IP addresses within a network divided into several subnets.
2. IP Addresses.
There are two kinds of IP addresses that can be issued to Azure resources:
(a) Public
For contact with Azure's general public, a public IP address is assigned. When the service is stopped, the IP address is released and a new one is allocated to the Azure resource, which by default has a dynamic IP address. When a static IP is given to an Azure resource, it remains in place until the resource is deleted.
(b) Private
Private IP addresses can connect through an express route, a VPN gateway, or when the Azure resource is located on a different VNet.
Options for Azure Networking Services
To make your Azure environment fully-fledged and able to handle all the traffic that pulls into it, Azure offers a selection of Microsoft Azure services and additional networking features from third-party vendors.
Network Security Groups (NSG) for Azure
The main tool for managing and enforcing network traffic policies at the networking level is the Network Security Group. Access between workloads is either permitted or denied with NSGs. The company can also impose restrictions on who can use the resources in a virtual network.
Balancing loads
According to resource availability and rule assignment, a load balancer distributes newly arriving inbound flows to the backend pool instances. Business applications can be scaled with Azure load balancing, resulting in high availability for services. In addition, they offer extremely high throughput and low latency, and depending on the TCP and UDP application traffic, they can scale up to millions of flows.

There are two SKUs for Azure load balancers: basic and standard, which vary in features and scalability. These load balancers frequently offer many options, according to category:
Similar to the AWS service Route53, Azure Traffic Manager uses DNS to route traffic to the appropriate locations. In terms of destination selection, there are three options: failover, performance, and round-robin.
L7 load balancing is carried out via the Azure Application Gateway, which also supports HTTP requests, SSL termination, and cookie resolution.
Routing Desks
When it's necessary to modify the traffic's routing, Azure Routing Tables come in handy because they can replace the automatically provisioned Azure route systems. These routing adjustments are made to outgoing traffic from a subnet and can direct it to a virtual machine, virtual network, or virtual network gateway as its next hop.
VPNs, or virtual private networks
By prohibiting any unauthorized individuals from listening in on the traffic, a VPN ensures that any sensitive data transmitted over the network is protected. A VPN is an encrypted, secure connection over the internet from a device to a separate network. As more offices provide options for working from home, VPNs are the preferred option.
When there is a requirement to transport data between many VNets, Azure's VPN options come in handy. Azure provides two different gateway types.
VPN
Azure VPNs come in two flavours: route-based and policy-based.
On a route-based VPN, the data packets are encrypted and decrypted as they travel via a tunnel interface. A policy-based VPN encrypts and decrypts communication in accordance with the applicable policies.
Quick Route
The on-premises data centre and the Azure data centre are connected directly through Express Route. An express route uses a connectivity provider to provide the connection rather than the general internet. In comparison to the open internet, an ExpressRoute connection delivers a more dependable connection with quicker speeds and reduced latencies. When data is sent between the on-premises environment and the Azure data centre, ExpressRoute also enjoys significant cost reductions.
Azure has three connectivity options as of the time this article was written. In simpler terms, IPSec VPN over the open internet is the most fundamental. The other two choices are offered by ExpressRoute.
Switch Provider
Here, an exchange provider with a direct connection to Azure helps Azure establish a connection via point-to-point. Although using this option gives complete control over routing, the requirement for point-to-point connections makes it unsuitable for multipoint WANs.
Service provider for networks
The network service provider offers a direct link to Azure using the ExpressRoute option. Each site or department employs several points of connectivity, despite the fact that the network service provider oversees routing.
Any organization can benefit from the additional Azure features offered by ExpressRoute. ASR, or Azure Site Recovery, is one. Since this ExpressRoute connection is a sensitive one on Azure, you can replicate data without worrying about bandwidth availability.
Network Watcher for Azure
Access information is provided by the Network Watcher, including logging, monitoring, diagnostic tools, and automation. For greater visibility, you may keep a close eye on the network's performance and health.
Azure Networks: What They're Worth
If your company chooses to use Azure, its networking solutions address all important aspects of cloud networking.
Distancing and increasing security
Azure Networks may segregate virtual machines and applications, enhancing the security of the resource environment, by defining subnets, assigning private IP addresses, and more.
Topologies of networks
Virtual networks eliminate the need to be concerned about messy cabling. You have the exceptional ability to create complex network topologies in order to execute virtual appliances on the network. Additionally, it gives you more freedom to design your system with tools like WAN optimizers, application firewalls, and load balancers.
Additional Datacenters
Azure Cloud can supply the workloads and simply have them communicate with the on-premises datacenter using the robust Azure networking solutions when you need to expand the on-premises data center but the expense of growth is prohibitive. As a result, there is little to no capital expense and no need for new gear.
Deploying Hybrid Applications
A backend SQL Server database is frequently required for business applications to operate. Businesses that host their SQL databases on-premises have a significant obstacle that prevents them from making efficient use of cloud computing resources. However, you can create hybrid cloud apps and securely link them with on-premises SQL databases by leveraging virtual networks.
Alternative Solutions
Any problem you may have can always be solved thanks to Azure's extensive marketplace. There are numerous networking solutions for load balancers, firewalls, traffic management, and other network devices available from networking companies.
Global Availability of Azure
Business data and apps can be hosted in a local Azure data center thanks to the platform's global availability. Data access is quicker and has lower latencies. None of the top cloud rivals currently possess this capability. As of the time this article was written, Azure was accessible in 52 regions and was actively growing to include more locations and data centers.
1 note
·
View note
Text
youtube
Static Vs Default routing , 2 way of static routing , configurations, where to use , Lab example.
#Staticrouting #defaultRouting #PNETLabStatic Vs Default routing , there are mainly two type of static routing , how to configure , where to use , clear your concept in practical way . no more confusion , after watching this your concept will be clear and you will know how to use static and default routing and where to use , how to configure it . install & Configure PNETLab - https://youtu.be/9bci8fxpXScpull/Download IOS/IOL/Image - https://youtu.be/nKJsGjzpOck Lab setup : 0:18 to 15:45Static routing Type-1 : 15:46 -29:25Static Routing type -2 : 29:26 -29.30 default routing : 29:31 - end
#Static Routing#Default routing#How to use#routing#cisco Routing#difference Between static and default routing#routing configuration#PNETLab#Cisco#Youtube
0 notes
Text
Basic Computer Network Protocol
Today we will learn about the basic computer protocol. Protocol means the set of rules and regulations. It is a set of communication between two or more computing devices. Protocols are always defined by port numbers. About Basic Computer Network Protocol. The Network knows different types of computers. It is a group of computers use to set common communication protocols.

In telecommunication systems, there are one or more protocols at each layer of data exchange. The internet and Networking working on TCP/IP Protocol. TCP/IP (Transmission Control Protocol over Internet Protocol). Data presentation, authentication, and error detection. The communication protocol follows certain rules to transmission data.
Basic Computer Network Protocol
The TCP/IP refers to the protocol suite and pair of TCP and IP protocols. TCP/IP is the most important internet communication protocol. all different network protocols are performed different functions. Below is a description of some of the most basic computer network protocols. TCP/IP protocol always working on the Transport layer.
Before, send data to users TCP/IP protocol will check the network connection is established or not. The transport layer sends and receives packets between the server and clients. It also supports all the routing protocols. It works on a logical network model.
HTTP (HyperText Transfer Protocol)HyperText Transfer Protocol is transmitting the information on the web. HyperText Transfer Protocol publishing pages on the WWW (World Wide Web). HTTP is a programming language between browser and web server. HTTP transferring information as belowPages Plain Text Audio Files Images Video Files. HTTP works between server and client. Default port number of HTTP is 80 and 8080 HTTP Listening port number is 80 and 8080
POP3 (Post Office Protocol)Clients using Email services like MS-Outlook, Outlook, and Thunderbird. This all services are using Post Office Protocol to receive email. Email receive from the remote server over TCP/IP. All the E-mail Server Services are providing POP3 Services. Default port number of POP3 is 110. Default port number of POPs is 995.
SMTP (Simple Mail Transfer Protocol)Simple Mail Transfer Protocol is using for sending E-mail. SMTP Email send and recieve between server and client. Default port number of SMTP is 25. For Email applicatioin configuration user need to setup SMTP, POP3, and IMAP. SMTP send Email to single or multiple recipients
Basic Computer Network Protocol
FTP (File Transfer Protocol)It is use to Download any file from computer. FTP use for Uploading File to any computer. File transfer protocol is using for Uploading and Downloading files from one computer to another. Users can upload and download files over the internet with the help of FTP. FTP supports third-party software also like Filezilla. If the computer connects with the remote server like Filezilla. The client computer performs a number of operations. Users can easily download, upload, delete, modify or create new files through FTP. Default port number of FTP is 21.
IP (Internet Protocol)Internet Protocol is the logical address of the computer. IP is an identification of the computer. If any two computers communicate with each other you need to provide an IP address to both the system. User can access network resources with the help of IP Address. Workgroup Network is running on IP Address. Domain Environment network is also running on IP Address.
DHCP (Dynamic Host Control Protocol)Dynamic Host Control Protocol is using to communicate with systems in the network. DHCP provides an automatic IP-Address to the client system. Default port number of DHCP is 67. How System Get DHCP IP? First goto Network Properties using NCPA.CPL Right Click on properties. Goto IPV4 option. Change it from static IP to Obtaine IP. Wait for a while user get IP from DHCP server. To access Internet provide gateway to DHCP server.
DNS (Domain Name Server/Domain Name System)Domain is a centrally managed system. DNS is the root Domain. Default port number of DNS is 53. Domain use for name resolution. Name resolution mean?IP to Name Name to IP We dont know the IP address of Google. But, when user enter Google.com in url to access Google. Here we share one small example.In your office with 100 computer systems. All the system IP Address can not manage. Administrator will setup Domain. All the user connect to the Domain. Administrator easily manage 100 computer cenrtrally. IMAP (Internet Message Access Protocol)Internet Message Access Protocol is known as IMAP. This protocol is mainly use to access the email from the remote server. Email copy is always stored on the servers. Default port numbe of IMAP is 143. Default port numbe of IMAP3 is 220 and 993. Users can access their emails instantly. UDP (User Datagram Protocol)User Datagram Protocol. UDP is one of the most important protocol. UDP protocol is very fast. The data travel very fast in UDP. It is not providing open port network. In UDP Protocol not provide any acknowledgment. Basic Computer Network Protocol SNMP (Single Network Management Protocol)Default port number of Single Network Management Protocol is 161. SNMP is used to manage the network-attached device of the network. Mainly use for any network storage device in your network. PPTP (Point to Point Tunneling Protocol)Point to Point Tunneling Protocol is mainly used for Virtual Private Networks. Default port number of PPTP is 1723. Note about Ports Total Port numbers are 65535Well known port numbers – 0 -1023 Registered port numbers – 1024 – 49151 Ephemeral port numbers – 49152 – 65535 Learn Free Information Technology with Manglastubh.
#BASIC COMPUTER NETWORK PROTOCOL#DHCP#HTTP#HTTPS#IMAP#IP#L2TP#NETWORKING#POP3#PROTOCOL#SNMP#TCP/IP#UDP#manglastubh#ankitakolkar#manglastubhbyankitakolkar
4 notes
·
View notes
Text
Bound by Circumstance ― Chapter 15: The House on Prytania Street
PAIRING: Nik Ryder x trans*M!MC (Taylor Hunter) RATING: Mature
⥼ MASTERLIST ⥽
⥼ Bound by Circumstance ⥽
Taylor Hunter (MC) has made it good for himself in New Orleans; turns out moving to a new city fresh out of college to reinvent yourself isn’t as hard as people make it out to be. Things only start to get confusing when he finds himself the target of a malevolent wraith. Good thing someone’s looking out for him though — because without Nighthunter Nik Ryder as his bodyguard he definitely won’t survive long in the twisting darkness of the supernatural underworld he’s tripped into.
Bound by Circumstance and the rest of the Oblivion Bound series is an ongoing dramatic retelling project of the book Nightbound and the rest of the Bloodbound series. Find out more [HERE].
Note: Circumstance only loosely follows the events and plotline of Nightbound, and features a separate antagonist, different character motivations, and further worldbuilding.
*Let me know if you would like to be added to the Circumstance/series tag list!
⥼ Chapter Summary ⥽
The gang heads to Prytania Street to meet with the last power left untouched in New Orleans; the Garden District Coven. Taylor starts to experience the side effects of being a fae halfling.
[READ IT ON AO3]
The sun’s heat is blistering on the back of his neck.
It feels unnatural in a way; conducting their business with the darker side of the world in the daylight. They’ve been running between the worlds that exist between sunset and sunrise for so long that he almost forgot what the sun even looks like.
He likes looking at the moon. But looking at the sun? Ouch.
Still it feels strange not to have Cadence’s towering presence hovering somewhere at his back. Looking over at Katherine — he can’t imagine what it must feel like to her.
“Hey — nope, eyes here.”
Taylor winces at the backhand to his arm but Ryder definitely isn’t in the mood. He’s been tense ever since they left the hospital with a time and place to address the Garden Coven. Like he didn’t know that was the plan, or something.
“I’m listening,” promises Taylor. But listening for Nik at that very moment requires eyes as well as ears.
“Really? Then what’d I just say?”
He blames his hesitation on the fact its taking forever for the coffee to hit his nervous system. Looks to Cal beside him for some kind of help but the werewolf gives him a look of you’re on your own.
“Uh —”
“Right, thought so.”
“I get the gist, Nik. Don’t be rude, don’t make eye contact, probably best just not to open my mouth.”
Cal snorts. “Actually that’s scarily close to verbatim.”
“Did I ask you?” snarks Ryder, but the bait remains abandoned in the cracks on the sidewalk.
The Upper Garden District is like most wealthy neighborhoods; nice to look at for a time but not much for entertainment value without a place to actually go. And sure Taylor has entertained the thought of owning one of the many million-dollar mansions lined with black iron gates and enough bedrooms to sleep in a different one every night for a week or more.
But its like the streets know. They know what Taylor and the rest have seen — what some of them have done. They know what creature hunts them and close their entrances off with hanging willow branches and high brick walls.
Claiming innocence, refusing to be witnesses like covering their eyes in cupped palms absolves them of the duty placed upon survivors to recount tragedy when it is over.
Because they might be the only ones left to do so.
Taylor drags his fingertips along the winding bars of an iron gate. Wonders if the prickling he feels under his touch is static, his imagination, or something more.
Nothing about 937 Prytania Street sets it apart from the houses on either side of it, or across the street for that matter. If Katherine hadn’t stopped in front of it he might not have even guessed it was their final destination.
Wasn’t a witches’ home supposed to be covered in sigils or guarded by spirits from another world? At least adhere to the aesthetic, people.
Thank god, though, he’s not the only one underwhelmed by the obviously-new shiny coat of eggshell-white or the lack of shutters creaking in the mid- morning breeze.
“You sure this is the place, Kathy?” asks Cal with his head slightly raised, nostrils flared to try and pick up whatever scent witches carry. “It smells pretty ordinary.”
She doesn’t answer. Just presses the buzzer and waits patiently for the gate to open.
It does and without so much as an ominous creak.
Maybe its his paranoia kicking in but with every step they take towards the house the feeling of unease in Taylor’s stomach grows, and grows, until it sloshes around — doesn’t sit well with his coffee. Everything his eyes take in seems too normal. A lawn too well-manicured, a set of metal golden numbers too polished. Makes him want to grab a fistful of soil from a too vibrant pot of Easter lilies and throw it somewhere, anywhere to make the place a little less picturesque.
Lamrian was beautiful in its perfection.
The House on Prytania Street is perfect the way a staged corpse is perfect.
A stiff gentleman in a three-piece suit opens the door before Katherine can use the knocker. Looks the four of them over with a condescending air about him and there’s a half-second where it looks like he’s ready to close the door in their faces on principle.
He doesn’t, instead steps aside.
The problem with most of the houses in the area is that, beauty aside, most of them stand empty. Not on the material front — they are always filled with collections of things and with more places to sit than is realistically necessary. But whether its the shitty housing market or the fact that they’re just owned like another piece of a collection, rarely are they lived-in.
The Garden Coven house is no different.
While the Suit leads them to a parlor off the right of the house Taylor tries his best to try and find some evidence of life being lived; on the walls, the carpet, even in smudges in the dust that lines various and seemingly unrelated objects on display.
There are none. Not one single fingerprint.
Though the Suit gestures to a matching array of chaise lounges and high-backed chairs for them to wait in, they stay standing because Katherine stays standing.
“You will be collected shortly,” is all the Suit says before returning the way they had come; though this time he pulls the double doors closed behind him. Leaves them all feeling trapped despite the open windows and sunlight pouring through.
“Random question here,” Taylor breaks the silence because it might actually drive him up the wall, “but do we have a plan for if this goes badly?”
He looks to Ryder, who looks at Katherine, who has suddenly taken up an interest in the antique carpet underfoot.
Of course they don’t have a plan. Why would they have a plan for their last resort? The same wonder team that practically broke into Persephone without so much as an escape route on the brain.
Historically things have worked out in their favor, though. Is it wrong of him to hope this time, too, might not be so terrible?
The glowing yellow eyes that bore into his soul from across the room say yes, yes it is wrong of him. Say how dare he imagine that things might not turn out so bad. They blame him for bringing hellfire and brimstone down on this house, on this city.
“— ly shit, Taylor. You okay?”
Its like an out-of-body experience in reverse. Feeling too deep and too trapped within himself to answer the concern on Ryder’s face. Like he’s drowning inside his own mind — or inside someone else’s.
Nothing about her is stable — pinpointing what she looks like beyond the startling gaze with which she holds him captive is about as easy as finding a single raindrop in a stormy sea.
One moment there are wrinkles around her eyes. Lines at her mouth pursed with thin lips in a frown of disappointment. Then youthful candor in aching regret. Grey hair healthy and full then withered, curling like the rumors that hair and nails continue to grow long after you’re buried in the ground.
He doesn’t realize it until the tear burn at his eyes and make him choke, but he’s crying.
“Taylor — Taylor!”
It’s back-breaking to pull away from the vortex he’s been ensnared in. Both the sun and moon in each of her eyes. Glassy and knowing at the same time.
But he blinks. Feels those same tears run down his cheeks and tickle his chin. Looks at the concerned faces of his friends with utter confusion because how in the world could they be staring at him when he’s facing judgment at the metaphorical pearly gates, here?
Even he’s aware of how foolish he sounds when all he can let out is a dumb “What?”
Nik takes him by the shoulders; looks him up and down for any signs of physical harm like it all isn’t in his head. Remains the most tried and true validation of his experiences to this day.
“You — what the hell happened to you?”
Taylor looks to Cal’s frown of concern, to Katherine’s violet curls like whips lashing around her face as she tries to pinpoint what, where.
“You look like you jus’ saw a damn ghost,” Cal sees the confusion in his eyes and thinks he’s helping. He isn’t.
So he cranes his neck back, away from Nik, to the point where it feels like he might snap his own spine.
She’s still there — in the doorway to a shadowy corridor. Both young and old and there and not. Then she isn’t her at all and the elderly man standing in her place reminds him of his grandfather a bit — which does nothing but unsettle him further.
“You… you don’t see her — hi— it?”
No, of course they don’t. Why would they?
He’s used to this — defaults into the old habit of trying to pretend the thing he’s looking at doesn’t exist. Already with denial on the tip of his tongue burning like a sour candy left forgotten.
But this was supposed to have stopped. No more headaches, no more hallucinations. The things he’s seen and accepted… so why is this different? Why now of all the rotten times is he seeing something no one else can?
Sure Nik tries; Cal too. They look in the doorway where the figure hovers like a bad trip on acid. They try, but they don’t see.
“Rook,” — is this where he pulls a Hermione, tells Taylor that seeing things no one else can see isn’t normal even in their freaky lives? — “there’s no one there.”
Only he doesn’t sound his usual level of confidence. Sounds more like he’s trying to convince himself right alongside.
Katherine scoffs under her breath; shakes her head and sits because there’s nothing else to do with her arms folded so tightly across her chest its undeniably a measure of self-comfort. Of keeping herself grounded.
When Cal tries to sniff the air his nose crinkles. “There’s too many different scents. Ritual burnings, smudges — I can’t get a read on shit.”
“I swear,” mutters Nik so low Taylor wouldn’t hear it if he weren’t as close as he is, “if these bastards are messin’ with you —”
For a guy who spent the entire journey warning against this exact type of frustration, anger, Taylor’s pretty sure it doesn’t matter if the Coven — wherever they may be — can’t hear him.
“Stop, it’s fine.”
“It ain’t —”
“You’re gonna get yourself in trouble.”
“Like I give a damn?!”
“Lower your voice!”
“A-hem.”
At some point the Suit had returned without their notice. Taylor would like to hope it was after his little freak-out but, time to face facts; he’s just not that lucky.
The way he looks them over — he might very well have some sort of magic-witchy x-ray vision. How the fuck someone can have a gaze that feels something like being scored at the top of his head and having his very being pulled back layer by layer is a mystery and, unlike the others, its one Taylor has no desire to solve.
“The Garden Elders will see you now.”
He wants to ask for a second to catch his breath; regain his composure. But why ask for it when he already knows the answer he’ll get?
Like before Suit doesn’t wait for them to speak an agreement. Just turns and begins walking deeper into the old house with purpose. Cal follows close behind — for all his bravado there’s unmistakable gooseflesh riddling his forearms.
Taylor reaches out to Katherine without a second thought; offering like he can help her up when they both know she could very well launch him over the chair and out the window like a rag doll.
Just another thing to distract him from the unrelenting stare digging knives into his back, probably.
Only Katherine takes his hand; surprises them both by doing so.
“You still see them, don’t you?”
The way Kathy’s eyes roam the space behind him, Taylor can tell she’s searching for the smallest speck of something to assuage his worries. But if you see something you don’t look for it.
So Taylor just nods. Follows with her at Nik’s back where he acts like a wall to keep their whispers private.
“Its not the Coven.” She says it so matter-of-factly.
The figure, now a young girl in the same pale grey shroud as the other faces had been, keeps staring even as they leave the parlor behind.
“Then what is it?” Nik throws back through gritted teeth.
“Something much more powerful.”
Taylor squeaks. “Not helping.”
“I recognize that look — I’ve seen it in the mirror,” and when they approach another set of double doors, stalled behind the Suit and his glower, her breath is hot in his ear.
“Keep an eye out. If The Fate is watching then there’s far more at stake than we assumed.”
His first thought is there have to be more witches in New Orleans than this, closely followed by please stop inviting trouble into your life, Taylor.
But even Katherine looks confused at the emptiness of the solarium they’re led into. How unassuming the three occupants look taking their tea with a pristine porcelain pot at a table out of Home and Garden magazine.
The same kinds of lilies, white petals large and curling under the sunlight, occupy every planter and pot in sight. Some of them are accompanied by flowers he’s only ever seen in books or movies — others look like they might be more at home in Lamrian taking root than here; to be appreciated but ultimately with a finite lifespan.
The solarium is a half-circle of heat and glass. Even the door leading out to a back garden path is see-through; the handle made of crystal. Everything catches on the sun and it makes Taylor quite literally hot under the collar.
He wipes a bit of sweat away from his chin uncomfortably.
They aren’t greeted when they enter. There are no chairs for them to take up. The Suit departs with the same wordless condescension with which he arrived and they’re just left there, taking up space on pristine marble, watching the so-called Garden Elders take their tea.
Only one of them actually looks the title ‘elder.’ The cotton on his robes looks scratchy, makes Taylor want to itch along his arms even at a distance. The locs that obscure his withered face fall back when he lifts his head up to the sun — casting shadows in the lines and creases of age he wears not just well but with a sort of pride.
With a delicate two-fingered touch he pushes his cup and saucer to the woman to his left. She refills his cup without looking away from the newspaper folded in front of her setting. The air around her seems to hold back as if afraid to touch — reverent of her existence but willing only to observe. The way the light illuminates her dark skin is practically golden. Makes her shine with some ethereal grace more at home with fae-kind than mortal witches, but the glow is undoubtedly hers.
The third Elder takes Taylor by surprise — he’s seen her before. Can still smell the sour cling of sweat to copper talismans and commercial incense on the ever-crowded floor of the House of Voodoo shop on Bourbon Street. Takes hiding in plain sight to a whole new level.
Would the Taylor from before all of this have felt the power that radiates around them? Would he have understood there was something to be feared about this particular trio; something he couldn’t possibly understand yet could feel in a place deeper than in the marrow of his bones?
I guess we’ll never know.
The polite thing to do would be to wait for them to finish their morning repast.
They don’t have time for politeness.
“Thank you for agreeing to meet with us on such short notice, Elders.” Katherine gives a respectful nod of her head when she steps forward. Based on the look she throws at Ryder that’s what they should all be doing — but he doesn’t. And Taylor just doesn’t want to look like an idiot.
Something rattles hollow around the old man’s neck and when he turns Taylor really hopes those aren’t real bones strung together with twine. His eyes are a milky, clouded white but he looks at Katherine with no trouble.
“Despite what rumor may have you believe we care a great deal of our ties to the community.”
Kathy opens her mouth to speak but because Nik is Nik he scoffs “yeah, sure,” loud enough to drag the focus of all three Elders onto him.
“If you’ve something to say, boy, say it,” says the House of Voodoo employee, and Taylor will never hear a customer service voice the same way again with the shiver it sends running down his spine.
“Elder Millet —”
It isn’t politeness that cuts Kathy off when Millet raises her hand. Not with the purpling of her face or the way she seems to gasp around unspoken words.
“Excuses are as bad as lies, Miss Lopez,” she gives a flippant wave to her peers that breaks her unspoken spell; leaves Katherine on the verge of clawing at her throat for fragrant lily-scented air, “if Mister Ryder here has something to say who are we to force him into silence?” Ironic, much?
Now he’s done it — Nik can tell, too. If they want to continue he’s going to have to finish his thought and accept the consequences that come with it.
But he is Nik; so he squares his shoulders and stands his ground despite the unease that Taylor feels emanating from him.
“I mean no blatant disrespect Elder Millet,” —to the old man— “Elder Vion,” —and to the woman still yet to look up from the paper— “Elder Daniels; but if any of you three gave a damn about the community we wouldn’t’a needed to come get you in the first place. You’d have shown your faces at the Beau-Keyes with the rest of ‘em.”
“And look what happened to them,” drawls Elder Daniels as she flips the paper to the financial section, “almost killed due to reckless stupidity and an inability to see beyond the moment.”
The private laugh the three of them share isn’t lost on anyone. In fact it makes Cal bristle and go red in the face.
“You—You knew we’d be attacked? You knew and you did nothing?!”
Pack blood still runs deep.
Elder Vion adds a pink sugar cube to his tea. “‘Doing nothing’ was the ideal course of action.”
And his fellow Elders agree; “It followed the plan precisely.”
“And leaves us with an opening.”
“Though the guests will have to be taken care of first.”
“They won’t be here for long.”
“Hey—Hey! Now ain’t the time to dissolve into crazy!”
Nik’s clapping isn’t just loud — it makes the room tremble. Glass walls, the glass panels on the ceiling all somehow stunned by the weight of his audacity. That he would dare call attention to himself, this small, insignificant creature—
Taylor hastily shoves his palms into the front pockets of his jeans. Like that will somehow stop the feeling prickling at his palms like a thousand tiny needles. Different than anxiety; something borderline painful. Like if he thinks about it too much it will start to hurt, but pushing it out of the forefront of his mind will keep it at bay.
He recognizes the feeling easily enough — still doesn’t know what it means or what’s causing it but there’s one answer he didn’t have before. It has something to do with being a fae.
“So you all know what’s out… there.” Taylor jerks his chin to the garden, to the French Quarter beyond and the rest of New Orleans with it.
Given everything they’ve seen when it comes to the bloodwraith so far it’s almost laughable to think such a gruesome creature could exist—let alone appear—on a day like this.
Elder Millet looks Taylor over like she’s peeling back each and every layer of him with her eyes. Maybe she is — he wouldn’t put it past magic itself. Let alone past the magic that told the Coven Elders how terrible the attack at the Beau-Keyes would be and convinced them to do fuck-all about it.
“We do.”
But they knew that. “And you know what it’s after.”
“We’ve drawn our own conclusions.”
“Do those conclusions tell you how close you’re getting to the top of the list?” It sounds an awful lot like a threat. Good — he wants it to be.
“Do they tell you its only a matter of time until it comes after you — after the entire Coven?”
Nik agrees; “Whose to say it’ll stop with the Elders? Someone takes your place eventually — it can go after them, and the ones that follow, and the ones after that —”
Vion scoffs around his tea. “Preposterous!”
“Actually no; not in the slightest.” Wariness, distrust hangs over Katherine in an aura of thunderclouds. And its growing. “It’s logical.”
The word, the very implication of it makes Millet’s fingers twitch towards something partially obscured by the teapot. At first Taylor wrote them off as napkins but now the shape and size rings familiar.
Her deck of tarot cards doesn’t like being questioned.
“Logic is the predilection of the mundane.” When Elder Daniels finally looks up from her paper its to stare directly at Katherine. Hard and unyielding. Its a look of power; a silent demand for surrender.
And she almost does. Taylor knows without a doubt that she’d deny it with her last breath but words mean nothing when he can see the flash of her soul behind stormy skies — hear the rolling thunder not far behind.
“There are a thousand and one ways to interpret any given reading. And you chose the one that would keep you out of the crossfire.
“Even if it meant turning your backs on the Accords.”
Outside the walls of the sunroom nothing has changed. The clouds have continued to drift lazily by and the sun still beats down upon them. But when they entered the room felt as transparent as it looked.
Now they may as well be trapped in a dense fog. It threatens to block out the sun; to take pleasure in wringing out their last choking breaths.
“You overstep, insolent little Nighthunter.”
Elder Daniels stands and waves her hand. Probably takes a sick sense of satisfaction in the smallest flinch Katherine fails to hold back — but instead the witches’ spread vanishes as though it was never there.
There is no gaping absence of it — they could just as easily have been standing the entire time and had Taylor’s eyes not seen the table and chairs, had he not smelled the brewing tea or heard the clinking of cup against saucer, he would have a hard time explaining why he thought any of it was there in the first place.
Millet’s fingertips hover just above the surface of her tarot deck. The only physical thing to have remained. As much a member of the Elders as anything.
And the wrinkles on Vion’s leathery face have sunken deep like canyons. His movements are ancient and slow as he stands beside his fellow Elders in defiance of some unknown.
The sides are becoming glaringly obvious.
Small as it was Daniels’ display of power served its purpose; reminded them of who—what—they were dealing with. A power strong enough to entice the bloodwraith and prove its worth by remaining untouched.
The continued existence of them was a claim to power that the likes of Carlo de la Rosa and Denna the Shifter could never have dreamed of.
Taylor knows he’s not the only one of them having this fact hammered home inside him. Not solely because it takes some big and important shit to keep Ryder silent for this long but definitely highlighted by it.
“Perhaps,” Millet drags the word out solely to fuck with them, “we are the ones to be blamed. Blamed for our naivete in agreeing to this meeting disguised as an attempt to point fingers.”
And because its Katherine on the line — more than her name or reputation, but her life — she remains the sensible one. She tries to smooth-talk her way out. “With respect, Elder Millet, no one’s pointing fingers—”
“Save your arguments,” barks Vion, “though I’m sure they were well-rehearsed. Even blind to this physical plane as I am, I can see your true intentions for coming here.”
“Well there weren’t any, so —”
“We open our doors to you in this hour of need and yet you seek to accuse us of that which you cannot even begin to understand. Do you deny?”
It’s beginning to feel an awful lot like a trial and Taylor isn’t the only one who can feel it. He knows what the tension in Cal means — the way Nik shifts to the foot he favors standing his ground on.
But something just isn’t right. It’s echoing hollow in his bones; in the air around them. It fills him up, keeps filling him until he’s not sure he can stand it anymore. Until it wants to pour from his mouth or leak from his ears.
“Then why even agree to meet with us at all?” he blurts out to the surprise of the room; to himself.
And all that pressuring weight shifts from Katherine to him. Now he’s deep in it. Way to effing go.
Only its the first time the Elders don’t have a remark ready to be snapped at their heels. A fact that isn’t lost on them — and isn’t lost on his friends either.
And since its the only silence they might be getting any time soon he tries to roll with it in his usual word-vomit way.
“If you can see so much of the future in your cards or whatever — why agree to meet with us at all? Wouldn’t you know what we think of you? What everyone thinks of you? And you guys don’t seem like the type to entertain stupid people for the sake of a laugh.”
Nik gives him a very specific ‘Did you just call us stupid?’ look. Yeah, yeah he did.
But its rambling, and Taylor is good at rambling. Rambling is what he does best — rambling and improv monologues.
“You guys —” he drags an accusatory finger across the spread of them, “— are the ones accusing anyone, here. Which I get, you know, because there’s a lot going on. And everyone’s scared and everyone’s got their walls up because this is—like—ten thousand leagues away from normal even for your crazy world.
“But if we keep pointing fingers and we keep not helping everyone then what’s gonna happen? Right — the bloodwraith is gonna win. Because we’re gonna do its job for it!”
He drops his finger, then, because he’s making a point and leading by example. “Whatever reasons you may think we have for coming here are bullshit. No one wants to help, everyone’s just in it for themselves! And seeing as literally everyone in the city is a target right now that’s a really really stupid way of thinking!”
Like — he’s making sense, isn’t he? He feels almost compelled to look around not just at the Elders but at his friends, too. How many stories about good versus evil demand that everyone band together in spite of their differences for their own survival; for everyone’s survival?
They had been so close at the Beau-Keyes. If they’d all been given more time who knows what they could have accomplished. Maybe Kristof would be more willing to help. Maybe Lady Smoke wouldn’t have gotten hurt.
Maybe Elric would stop hiding behind his wards like a coward.
Taylor sighs and it comes out a ragged thing — takes every last bit of air in his lungs and tries to wring a choked noise from his lips but he’s just too tired.
“If you had already made up your minds about us — about helping everyone — then why bother letting us come here to ask?”
Over Elder Daniels’ shoulder, across the room and through the spotless glass wall he sees the same figure as before. Knows its them by the glint of their golden eyes. The young woman’s face is forlorn; almost weeping. Flickers like a heat mirage from young to old to young again.
The Fate, Katherine had called them.
Why here?
Why now?
Why won’t they do something?
“Such a rousing call to action…” says Millet with the vestiges of praise — yet it looks bitter on her tongue.
Daniels agrees; “And from the unseen complication, no less.”
“Perhaps we underestimated him.”
“What difference would it make? Everything has gone as predicted so far.”
“One wrong move can turn the tide.”
“Yes — but this…”
Again they fall into whispered confidences — as though the others aren’t even there.
Ryder almost growls. More unwilling to call them out on it than before but just as impatient. “This was useless…” he hisses through gritted teeth back in Kathy’s direction.
A small movement draws Taylor’s attention to Elder Vion. To the empty space beside him.
Where The Fate — as a child, making it all the more eerie — reaches up and takes the witch’s hand in theirs. Blood soaks through their grey sleeve; drips down onto the pristine white floor. One droplet becomes two, becomes three and more. A puddle forming at their feet and spreading out of its own will.
He knows it isn’t real — that none of it is really there. There is no child and no blood not only because no one else is freaking out about it but because of the way the blood moves. Spiraling tendrils seeking to consume but only at the Elders’ feet.
The meaning of the whole disturbing sight is clear.
There is blood on the Elders’ hands. They’re drowning in it.
“You didn’t answer his question.”
Katherine cuts Daniels and Millet off mid-word. All that cool calculation hidden behind her pretty face; the perfect mask to hide behind. “Why’d you agree to this? What do you gain?”
Daniels’ upper lip curls. “There is nothing you could offer worth our time.”
“Still doesn’t answer the question.”
“Do you forget you called upon us?”
“Yeah,” she scoffs, “when I thought you’d be useful. But we’re just talking in circles here!”
They are. What more do they know now compared to before?
Nothing is making any freakin’ sense. Nothing except for the sickening feeling growing inside. The blood spreads — devours. Leaves the witches draped in a dark veil thicker than a fog at night and the solarium, once filled with the light breeze of lilies, reeking of rot and the sour tang of open wounds.
A scent he’s becoming all too familiar with — something Taylor never thought would ever cross his mind.
Again there’s a prickling at his palms but this time he reaches for Ryder — a port in the gathering storm. Clasps their hands together tightly; desperately.
Nik who does a double-take when he catches the hollow light of fear in his eyes.
We need to leave.
What do you know?
Too much.
Too much. He knows too much. The Fate knows it and that’s why their figure has vanished but the blood seeping into the hems of the Elders’ clothes remains. The world knows it too, somehow. Keeps that damp and musty smell of molding decay stuck in his lungs and makes him choke on it. Makes his eyes water and an itching pain climb up from the inside of him begging to be let free.
He knows too much. Can’t even begin to understand the how or the why and maybe even a little bit of the what but he does.
He knows without a shadow of a doubt that the darkness that gathers around the Coven Elders and the one hanging as a fatal noose around the bloodwraith are one in the same.
We need to leave.
“It doesn’t matter Kathy,” Nik interrupts — keeps his eyes on Taylor like a grounding point; the only solid ground to stand on, “whether they answer or not it’s clear as day they don’t plan on helping anyone but themselves.
“We oughta get goin’.”
To their credit the Elders don’t deny it.
But the sudden change is a bit too much for Katherine. “Are you—Nik what the hell?”
“Kathy —” Taylor’s wavering voice almost breaks at just her name. Its enough; enough to drag her away from frustrating thoughts building to the fact that he’s white as a sheet and on the verge of unconsciousness. “Please.”
She doesn’t get the chance to argue. Not when the room turns to shadows upon shadows; very real and very not-in-his-head clouds blooming across the sun over their heads.
Even when Elder Vion lowers his hand the spell continues; grows and takes hold of the sky above until the sun is nothing but a distant memory, until the shadows are only a darkness unending.
He tuts and clicks his tongue — such a normal act in contrast to the way he leans on the gnarled handle of his cane. “Finally the consequences reveal themselves.” He bites out, though his scorn is quickly directed to the Elders at his side. “Had you not wished to speed the process this wouldn’t be an issue.”
“Had we?” Millet snaps; gestures with her hands so wide that one of the cards slips from her deck and flutters to the ground face-up.
The Wheel of Fortune stares lifelessly upwards.
“You insisted the Council could not be allowed to congregate, Vion.”
“Indeed we acted on faith of your vision,” agrees Daniels.
Vion, though, is adamant; “The consequences outweighed the risk.”
“And what of that,” Daniels thrusts a finger at Taylor, “little consequence? Was it worth the knowledge he now possesses?”
The energy directed his way makes Taylor double over — from pain or pressure he doesn’t know. But Nik isn’t having it.
“What the hell are you crazy people talkin’ about?!”
“Silence!”
There’s a loud and resistant groan over their heads. They look up just in time to see the metal framework stop — now twisted, coiled like a spring ready to snap and send the ceiling panels hurtling down in what would surely be a painful death for all but the Elders.
“You dare interrupt your betters; dare demand of those who hold absolute power over your mortal lives?!” She’s practically shrieking now; and with each crack of her voice comes a crack in the glass surrounding them. “That you continue to live is a testament to our generosity despite your wretched meddling!
“But a Nighthunter never learns. Not until he is forced into submission!”
The bones around Elder Vion’s neck rattle on a nonexistent breeze. “To give this cur the same punishment would be my pleasure.”
“Why bother prolonging it?” adds Millet in a ravenous growl, “Kill him now and we have a second soul to cut from the veil. A second soldier to finish the task at hand.”
Cal goes rigid; taken by surprise. Now he knows. “Holy shit. It’s you.”
And now Katherine knows too; forces down the oncoming waves of revelation — keeps herself afloat with a strength well-hidden.
“You’re the ones controlling the bloodwraith.”
#nightbound#nik ryder#cal lowell#nik ryder x mc#vera reimonenq#katherine nightbound#nightbound mc#mc: taylor hunter#oblv: bound by circumstance#oblv: new chapter#; my fics
3 notes
·
View notes
Text
Cisco CCNA Security 210-260 Certification Exam Details
Cisco 210-260 certifications are globally accepted and add significant value to your IT professional. The certification offers you a serious knowledge of each of the workings with the network models and also the devices that are utilized from it. NWexam.com is proud to offer for you the ideal Cisco Exam Guides.
The Cisco 210-260 Exam is challenging, and thorough preparation is important for achievement. This cert guide was created to enable you to plan the CCNA Security certification exam. Its content has an in depth list of the individuals covered around the Professional exam. The following tips for your IINS might help make suggestions with the study process for the certification.
To have Implementing Cisco Network Security certification, you need to pass IINS 210-260 exam. This exam is produced remembering the input of pros in the market and reveals how Cisco products are found in organizations around the globe. 210-260 Implementing Cisco Network Security Exam Summary
? Exam Name: Implementing Cisco Network Security ? Exam Code: 210-260 ? Exam Price: $300 (USD) ? Duration: 90 mins ? Number of Questions: 60-70 ? Passing Score: Variable (750-850 / 1000 Approx.) 210-260 Exam Guide: ? How I pass Cisco 400-201 Certification in first attempt? ? How to arrange for 400-201 exam on CCIE Supplier Topics covered in the CCNA Security 210-260 Exam [1]. Security Concepts (12%)
1 Common security principles a) Describe confidentiality, integrity, availability (CIA) b) Describe SIEM technology c) Identify common security terms d) Identify common network security zones 2 Common security threats a) Identify common network attacks b) Describe social engineering c) Identify malware d) Classify the vectors of internet data loss/exfiltration 3 Cryptography concepts a) Describe key exchange b) Describe hash algorithm c) Assess symmetric and asymmetric encryption d) Describe digital signatures, certificates, and PKI 4 Describe network topologies a) Campus area network (CAN) b) Cloud, wide area network (WAN) c) Data center d) Small office/home office (SOHO) e) Network to protect an on-line environment
[2]. Secure Access (14%) 1 Secure management a) Compare in-band and out-of band b) Configure secure network management c) Configure and verify secure access through SNMP v3 using an ACL d) Configure and verify security for NTP e) Use SCP for file transfer 2 AAA concepts a) Describe RADIUS and TACACS+ technologies b) Configure administrative access on a Cisco router using TACACS+ c) Verify connectivity on a Cisco router to a TACACS+ server d) Explain the combination of Active Directory with AAA e) Describe authentication and authorization using ACS and ISE 3 802.1X authentication a) Identify the functions 802.1X components 4 BYOD a) Describe the BYOD architecture framework b) Describe the function of mobile phone management (MDM)
[3]. VPN (17%)
1 VPN concepts a) Describe IPsec protocols and delivery modes (IKE, ESP, AH, tunnel mode, transport mode) b) Describe hairpinning, split tunneling, always-on, NAT traversal 2 Remote access VPN a) Implement basic clientless SSL VPN using ASDM b) Verify clientless connection c) Implement basic AnyConnect SSL VPN using ASDM d) Verify AnyConnect connection e) Identify endpoint posture assessment 3 Site-to-site VPN a) Implement an IPsec site-to-site VPN with pre-shared key authentication on Cisco routers and ASA firewalls b) Verify an IPsec site-to-site VPN [4]. Secure Routing and Switching (18%)
1 Security on Cisco routers a) Configure multiple privilege levels b) Configure Cisco IOS role-based CLI access c) Implement Cisco IOS resilient configuration 2 Securing routing protocols a) Implement routing update authentication on OSPF 3 Securing the control plane a) Explain the function of control plane policing 4 Common Layer 2 attacks a) Describe STP attacks b) Describe ARP spoofing c) Describe MAC spoofing d) Describe CAM table (MAC address table) overflows e) Describe CDP/LLDP reconnaissance f) Describe VLAN hopping g) Describe DHCP spoofing 5 Mitigation procedures a) Implement DHCP snooping b) Implement Dynamic ARP Inspection c) Implement port security d) Describe BPDU guard, root guard, loop guard e) Verify mitigation procedures 6 VLAN security a) Describe the protection implications of the PVLAN b) Describe the security implications of your native VLAN

[5]. Cisco Firewall Technologies (18%)
1 Describe operational strengths and weaknesses of the different firewall technologies a) Proxy firewalls b) Application firewall c) Personal firewall 2 Compare stateful vs. stateless firewalls a) Operations b) Function of hawaii table 3 Implement NAT on Cisco ASA 9.x a) Static b) Dynamic c) PAT d) Policy NAT e) Verify NAT operations 4 Implement zone-based firewall a) Zone to zone b) Self zone 5 Firewall features on the Cisco Adaptive Security Appliance (ASA) 9.x a) Configure ASA access management b) Configure security access policies c) Configure Cisco ASA interface security levels d) Configure default Cisco Modular Policy Framework (MPF) e) Describe modes of deployment (routed firewall, transparent firewall) f) Describe types of implementing high availability g) Describe security contexts h) Describe firewall services
[6]. IPS (9%)
1 Describe IPS deployment considerations a) Network-based IPS vs. host-based IPS b) Modes of deployment (inline, promiscuous - SPAN, tap) c) Placement (positioning with the IPS inside the network) d) False positives, false negatives, true positives, true negatives 2 Describe IPS technologies a) Rules/signatures b) Detection/signature engines c) Trigger actions/responses (drop, reset, block, alert, monitor/log, shun) d) Blacklist (static and dynamic) [7]. Content and Endpoint Security (12%)
1 Describe mitigation technology for email-based threats a) SPAM filtering, anti-malware filtering, DLP, blacklisting, email encryption 2 Describe mitigation technology for web-based threats a) Local and cloud-based web proxies b) Blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, TLS/SSL decryption 3 Describe mitigation technology for endpoint threats a) Anti-virus/anti-malware b) Personal firewall/HIPS c) Hardware/software encryption of local data
What type of questions is on the Cisco 210-260 exams? ? Single answer multiple choice ? Multiple answer multiple choice ? Drag and Drop (DND) ? Router Simulation ? Testlet CCNA Security 210-260 Practice Exam Questions. Grab an awareness from these Cisco 210-260 sample questions and boost your 210-260 exam preparation towards attaining an Implementing Cisco Network Security Certification. Answering these sample questions is likely to make informed about the types of questions you can anticipate for the actual exam. Doing practice with CCNA Security IINS questions and answers ahead of the exam wherever possible is the key to passing the Cisco 210-260 certification exam.
210-260 Implementing Cisco Network Security Sample Questions:-
01. Which type of traffic inspection uses pattern matching? a) Signature-based inspection b) Statistical anomaly detection c) Protocol verification d) Policy-based inspection Answer: a
02. Which from the following authentication mechanisms can be used with SNMP version 3? (Choose two) a) AES b) MD5 c) 3DES d) SHA Answer: b, d
03. Is there a most typical type of spoofing? a) Application spoofing b) Service spoofing c) DHCP spoofing d) Ip spoofing e) MAC address spoofing Answer: d 04. Which option mitigates VLAN Hopping and Double-tagging VLAN Hopping Attacks? a) Ensuring that the native VLAN in the trunk ports differs from the native VLAN in the user ports b) Making sure that the native VLAN with the trunk ports is the same as the native VLAN from the user ports c) Setting a corner port to “off.” d) Enabling auto trunking negotiations. Answer: a
05. The kind of attack is prevented if you configure Secure Shell (SSH)? a) DoS session spoofing b) Man-in-the-middle attack c) Dictionary attack d) Buffer overflow Answer: b
06. Which in the following is not part of an IKE Phase 2 process? a) Main mode b) Specifying a hash (HMAC) c) Running DH (PFS) d) Negotiating the transform set to utilize Answer: a
07. What are three key features of URL filtering? (Choose three) a) Predefined URL categories b) Malware protection c) Custom URL categories d) Dynamic content analysis Answer: a, c, d 08. What sort of VPN technologies are apt to be employed in a site-to-site VPN? a) SSL b) TLS c) HTTPS d) IPsec Answer: d
09. Which two statements are true of the present threatscape? (Choose two) a) We now have marketplace is the only industry that is certainly exempt from attack. b) The threat landscape is actually evolving. c) Due to recent improvements in security technology, password attacks not play a significant role in the threatscape. d) It is so complex that it must be impossible to catalog in its entirety. Answer: b, d
10. Which three statements are true about firewalls? (Choose three) a) If your system in a security zone is compromised, a firewall can help offer the attack within that zone. b) A firewall can prevent undesired access to a network security zone. c) Modern firewalls give you a complete network security solution. d) Firewalls typically will protect you between and within network security zones. e) A firewall can introduce a performance bottleneck. Answer: a, b, e
For more information about CCNA Security (210-260 IINS) go to see this useful web portal.
1 note
·
View note
Text
5. Show of Hands
By default, Merlwyb was not a morning person.
As those directly under her command could attest, the Admiral was not to be approached for anything short of full scale war before she consumed, at the bare minimum, two cups of black coffee. Any fool who dared attempt approaching before that, unless it was to offer her more coffee would be met with a glare dark enough to engulf the Mother crystal Herself.
So when Slafyrsyn brought her a missive from one of the ships away on a cargo route, his heart might have given out for the sheer animosity in her tired gaze were he of a lesser constitution. As it stood, he simply gave a polite bow and presented the missive as though it were her breakfast.
“I presume this is urgent.” She said, her voice still gravelly from disuse and a lack of coffee both.
“Aye, Admiral,” Slafyrsyn affirmed. She took the report and began reading, though her severe expression did not soften. “It does not, on the surface, appear urgent, but I assure you—”
“Ghosts, Slafyrsyn?” The Admiral snarled, tossing the report onto her desk and redirecting her ire back at him. “Am I now meant to fight a ghost?”
Well aware that were she more awake, she would be cackling in delight at the mere thought of swashbuckling a specter, Slafyrsyn cleared his throat to hide an amused chuckle; it had been enough years serving under her that he knew where the line was between plucky friendship and the plank.
“Not...fighting a ghost, Admiral.” He gently corrected. “And...and not technically a ghost, either.” He gestured to the discarded paper. “Please, read the entire missive, I promise all is explained within.”
Merlwyb narrowed her eyes but returned her attention to the report. Her frown turned thoughtful as she continued, the coffee oiling the gears of her mind to work for the day.
Still...Slafyrsyn could tell the moment she read the end by the way her eyebrows met her hairline.
“Why is Captain Arcbane referenced in this report?” Merlwyb asked. “How did this cargo vessel run into her in the open waters? She’s currently on vacation— I signed off on it.” She narrowed her eyes. “She took two months off— she made for Ishgard the second I approved it!” She straightened in her seat a moment, her expression suggesting that a thought suddenly and violently occurred to her. “...Get me Flame General Pipin and Lord Commander Aymeric on the line. Now.”
Less than an hour later, she stood looming over her desk, various reports strewn out for her to scan over. The linkpearl in her ear let out two soft ding noises, one after the other to signal that two people were entering the call line she had opened. She tapped it, her focus still honed in on four reports in particular.
“If this is anyone but General Pipin and Ser Aymeric, kindly sod off.” She said gruffly.
“Good morning, Admiral,” she heard the Lord Commander say diplomatically.
“Well, won’t this be an interesting conversation.” Pipin said, sighing.
“I will be brief,” Merlwyb said, her hand reaching out for one of the reports— the earliest dated one she had suspicions was related to this ghost. “Ser Aymeric, can you confirm that Storm Captain Serella Arcbane arrived to Ishgard following her approved leave?” She offered him the start date, and she could her him confirm on his calendar.
“She arrived here that same day,” Aymeric answered. “Though given you are looking for her now, I will tell you that she left after staying a week.” The sound of a book being shut was faintly heard. “She mentioned a fishing trip with her brother, and that she would return here when it was done.”
A fishing trip. Merlwyb would have laughed if she was not so furious.
“Uthengentle mentioned much the same, actually.” Pipin spoke up. “He’s on leave, too, come to mention it—”
“Did either of them happen to mention where they were going ‘fishing?’ Or what it was they were trying to catch?”
“Storm Captain Arcbane gave no indication.” Aymeric answered, ever the diplomat.
“Flame Lieutenant Arcbane didn’t say much either,” Pipin replied. “Just that he was looking forward to his fishing trip with his sister.”
“Did either of them,” Merlwyb began slowly. “Ever mention that they were going to create a mythical ghost to ‘catch’ Imperial slavers?” She only barely fought down the urge to shriek the more she thought about it. “Was that mentioned by any chance?”
“...Forgive me,” Aymeric said, and even through the faint static of the linkpearl, the Admiral could hear his bafflement. “Perhaps my reception is poor— did you say they created a ghost story to scare Imperial slavers?”
“Sounds more like they made themselves the ghosts.” Pipin said, though sounded infuriatingly unsurprised.
“General Pipin has the right of it,” Merlwyb snarled. “We just received a boat full of people— of captured people that have been missing for months— with no captain, no crew, but a letter with the Maelstrom Captain’s seal requesting that these people be cared for.” She snarled. “And from the way the rescued people talk, a wraith descended upon the Imperial ship in fog and slaughtered their captives.”
“And given an officer of the Eorzean Alliance is involved, that might complicate things.” Aymeric supplied.
“Two. I can confirm Ul’Dah has received a similar boat of missing people with the Flame Lieutenant’s seal on a letter requesting these people be returned to their homes.” Spoke Pipin.
“That this is how those two fools use their vacation time astounds me.” Merlwyb grumbled, rubbing at her temples to try and stave off the migraine she was already beginning to feel press against her eyelids. “I intend to hail Storm Captain Arcbane and bring her into the call.”
“Shall I step out, then?” Aymeric asked. “I fear there is little more I can assist with—”
“Oh, no,” Merlwyb said in the same way one chastises a child for misbehaving. “You stay. I would confirm the use of an appropriated Dragonkiller on top of everything else.”
“Forgive me, a WHAT—”
Merlwyb ignored Aymeric’s baffled sputtering and dialed her Captain’s personal line. After a few tense moments, there was a soft ding.
“Hello?” Serella’s voice called out through the heavy static on her end— she must be rather far out to sea, then.
“Storm Captain,” Merlwyb snarled. “Where are you at this very moment?”
“...Fishing.” She said after a pregnant pause.
“Oh, ‘fishing?’ And what exactly are you trying to catch, Captain?” Merlwyb pressed.
“Oh, you know,” Serella did not immediately answer. “Things one tends to find out on the open sea—”
“You mean Imperial slavers, Captain?” The Admiral demanded.
“...In my defense, you do find them out on the open sea.” Serella countered. “I didn’t lie about it.”
“You are on vacation,” Merlwyb began. “Hunting slavers with your brother using a modified Dragonkiller as the figurehead of your ship—” she cut off her own rant as another thought occurred to her. “Is that ship a part of the Maelstrom fleet? Is it even a registered ship?”
“Technically registered— but only by the Knights of the Barracuda.” Serella admitted like her arm was being twisted. “We rebuilt Da’s ship— the Serpent’s Sting? Is that...is that a famous ship? I dunno, now that I’m thinking on it—” it was Serella’s turn to cut herself off. “Wait— did you say a modified Dragonkiller?”
“I will admit, this part interests me, as well, Storm Captain.” Aymeric spoke up in his most unamused tone.
“Oh, you’re here, too?” Serella asked. “Hello! I’m still on that fishing trip!”
“Clearly.” Aymeric drawled. “How did you manage to steal a Dragonkiller?”
“You wound me!” Serella gasped. “I’ve stolen nothing! I went to the exhibit on the history of weaponry— that exhibit they did following the Dragonsong War on different styles of weapons used—”
“Get to the point, Captain.” Merlwyb snarled.
“Sorry, sorry.” Serella hastily apologized. “They had a blueprint of an older model of Dragonkiller— and I sketched it out, but then I compared it to newer models, made some adjustments. Handed it to Uthengentle— have I mentioned he’s brilliant with weapon modification? — And he had the idea to change the lance at the head of it into a battering ram that opens into a claw! Now it’s a Hullkiller!”
“At what point,” Merlwyb asked slowly, her patience utterly spent. “Did you decide that a ghost ship was how you were going to fight slavers?”
“The beginning, if I’m being honest.” Serella said, and the Admiral could see her shrug. “We wanted to build something that wasn’t about ‘the Warriors of Light’ or anything. We wanted a boogeyman to kind of cover our bases.”
“So you took a two month vacation to have a costume party on your dead father’s ship?!” Merlwyb screeched.
“Listen,” Serella said, clearly unmoved by the Admiral’s outburst. “If I want to become a sea cryptid on my own time, that’s my business, Admiral.” Distantly, they heard shouting on her side of the call. “Ooohh, an Imperial Galleon—”
“Captain Arcbane, so help me—”
“The fish are biting, Admiral! I’ll write soon!” Before anyone could demand that she explain herself, her line cut off.
“...Well.” Aymeric spoke up in the tense silence. “At least they are not using stolen Alliance equipment.”
“And not technically done anything illegal to boot.” Pipin added. “Though I doubt that will mean the end of paperwork for us, at least it’s all above board...I think?”
“We will have to determine that at the time of their return.” Merlwyb said, fighting the urge to roll her eyes.
“I’m not even attempting to contact Flame Lieutenant Arcbane until they’re ashore.” Pipin admitted, sighing. “...He tends to just hang up on me anyway.”
“This discussion is over.” Merlwyb said. She could feel her eye twitching. “I thank you both for your time.”
“Pray do not outright murder the Warriors of Light, Admiral.” Aymeric entreated her with a sigh of resignation. “I imagine a great deal of chaos would only come from their demise.”
“I’ll take that into consideration.” She snarled.
“Have a drink, Admiral.” Pipin said, defeated. “Gods know I’m opening a bottle of brandy over this.”
The call ended without preamble, which was well— Merlwyb had one more thing she needed done before resuming her duties.
Taking the lift to the Drowning Wench, she felt the eyes of every patron and worker in the bar fall upon her— good, she thought. Less shouting for their attention.
“Show of hands,” she called out, and she must have looked as near-insane as she felt, if the way the crowd seemed to jump. “Who among you aided the Arcbane siblings in supplying and manning a ship?”
Nearly every hand in the bar went up.
“Not manning, though.” Baderon reluctantly spoke up from the back. “They were insistent no one else join...but we supplied ‘em.”
“And you all kept quiet because…?” Merlwyb demanded.
“...They traded us barrels of personal stock liquor for the trouble?” Baderon said with a shrug. “And it was good?”
Deciding she had spoken to enough fools for one day, Merlwyb threw her hands up in the air in exasperation, did an about face, and just went back to her office. Slafyrsyn, knowing the oncoming storm, was already brewing coffee upon her return. If she felt as though she could trust her staff not to rebuild a two decades old ship just to harass slavers under the radar, she might have considered giving him a vacation for his efforts.
#ffxivwrite2018#bahahaha#why do I do these things to these poor Alliance leaders#Merlwyb I'm so sorry you deserve so much better than a garbage fire giraffe#Serella Arcbane#Uthengentle Arcbane#merlwyb bloefhiswyn#pipin tarupin#Aymeric de Borel
37 notes
·
View notes
Text
The state of VNs on Steam

I’ve recently read a few thoughtful discussion threads on the state of the VN market here in the West. Some taking a negative stance, some with a more positive outlook. I thought I’d try to put some numbers on these statements and look at VN ownership on Steam, still the predominant market for PC games, and use that to analyse whether VNs are on their true route or have stumbled into a bad end.
Data collection
I checked just over a million steam profiles to try and get a random sample of gamers. With Steam’s new private-by-default profile settings, only 8% of those users had public game lists, but that still gave us 80k user profiles to work with. I could then compare my sample with the “leaked” owner data and scale up my numbers accordingly to represent Steam as a whole.
Steam is rather haphazard with what gets tagged as a Visual Novel (RPGMaker games like A Bird Story are tagged as VNs), so I’ll only be including games that also have a VNDB entry.
Steam VN releases
So let’s start simple, with a simple plot of how many VNs are being released each month.

At first glance things seem rosy for VN fans, there have never been more VNs being released in the West. But let’s break down those results a bit:

Note that these trends are cumulative but NOT stacked. The EVN, JVN, and other VNs trends include only non-free VNs.
Here we can start to see the reason for the differing perspectives on the state of the VN market depending upon whether you read more JVNs or EVNs. While the rate of EVNs releases has steadily increased, the number of new JVNs has remained fairly static since 2016, despite Steam’s lowered release requirements. Steady release rates aren’t definitely bad news, but in general profitable industries want to expand, so the lack of expansion tells you something about the industry. But as someone with a plan-to-read list that grows longer by the day, I’m not complaining if the rate doesn’t increase.
One under-reported development in the VN market is the recent rapid growth of Chinese VNs (listed as other here), who have quietly been doing well in their home markets, but are rarely translated.
So while more VNs might be good for us fans, how does the market look for developers? Let’s have a look at VN sales.

Note that these trends are cumulative but NOT stacked. All sales are back-dated to the release date of the VN on Steam. Free VNs count sales as the number of users who have logged some playtime in it.
Unfortunately Steam’s API doesn’t list when someone bought a game, so we’ve got to group sales by the release date of the VN. That means there will be a bias towards older releases which have been out longer and so had more time to build up sales.
Here we can see some justification for the doom and gloom perspectives, with more recent VN releases selling significantly less than older ones. With new JVNs in 2017 selling only half what they did in 2016. The EVN downward trend is especially stark given that the number of new releases has been increasing, so that’s less revenue split among even more VNs.
Not all VNs are equal, some are priced higher, so let’s look at total revenue rather than total sales.

Note that this assumes every user pays full price, so this is more the maximum possible revenue than actual revenue.
Here we can see the difference between EVN and JVN markets. While JVNs sell only half as many as EVNs, they earn almost as much revenue due to their higher price. We again see the same dip in more recent revenue though, 2017 was only 46% of 2016′s revenue, and 2018 looks even worse so far.
Remember, this fall in revenue coincidences with an increase in the total number of releases, so to fully comprehend the drop on revenue, let’s look at the average sales per VN.

First, we should note that this massively overestimates the average revenue generated as it assumes every user pays full price. I know devs who would sell their soul for 282k per VN. Oh wait, they already did when they signed up for Steam... (just kidding, I do like Steam, but it has issues). The important aspect here isn’t the y-axis total which is unreliable, but the consistent downwards trend.
But it might not be as bleak as it seems, older VNs are more likely to have been in bundles and in Steam sales, so their revenue is likely overestimated compared with more recent releases. So I’d be hesitant to claim that revenue is necessarily dropping, but I think we can confidently claim that revenue isn’t increasing.
VN Reviews
Nostalgia for a past golden age is common everywhere, not least among VN fans. It’s not uncommon to hear that newly released VNs aren’t as good as older ones, but can we get any empirical data on this point? We can get close by looking at the Steam reviews of VNs over time.

Each dot represents the average thumbs up/down ratio for any VNs released that month.
Within the JVN market, we can see some truth to the nostalgia viewpoint. Older releases were more consistently rated higher. But that isn’t to say there aren’t new highly rated JVNs. They still maintain enviously high scores overall.
As for EVNs, while they had consistently scored lower than JVNs, they’re catching up and are now pretty comparable in review ratings of JVNs.
Just for fun, let’s see how the total review count compares between VNs.

The two free-VN spikes are for Emily is Away and DDLC.
As I’m sure anyone familiar with the VN community can tell you, JVN fans are vocal, and it shows in the total reviews VNs get. Despite there being only half as many JVNs as EVNs, they still attract more reviews than EVNs do. This is perhaps because JVNs are typically far longer than EVNs, so might be worth the time of writing a review.
What free-VN fans lack in the wallet, they make up for in their word-count. Although this is massively skewed by two free VNs which compromise 70% of all free-VN reviews: Emily is Away and DDLC. They seem anomalies rather than trends. As shown by the graph when we exclude those two:

*Excluding Emily is Away and DDLC.
Despite the drop in position, free-VNs still out-perform what we’d expect given their lower count of total owners, but that may be because EVN and JVN totals include users who own the VN but have never read it. Whereas the free-VN total only includes those who have logged playtime in that VN, so there’s a larger pool of possible reviewers.
Potential Issues
There are a few sources of uncertainty in the dataset. The selection of users who have set their profiles to public might not be representative of the wider Steam userbase. It probably undercounts more casual fans who are less likely to configure their Steam profile.
We also don’t know when someone purchased a VN, so it’s possible VN sales are increasing, but a lot of that money is going to older releases, especially if they’re in bundles and Steam sales.
In inclusion of VNs in game bundles may be distorting the image of the VN fandom, as it’ll include those who have little interest in the medium and only own a VN by happenstance.
We should also remember that “Steam” is not synonymous with the VN market. There are plenty of competitors in the VN scene, namely Mangagamer and itch.io, who tend to cater to different tastes than Steam does. So we’re only getting a partial picture of the Western VN scene.
Conclusion
There’s data here to support both the optimistic and pessimistic commentary. On the positive side, there have never been more VNs being released as there are now. EVNs are improving with higher average ratings and a few have reached mainstream attention.
On the pessimistic side, it seems like there are ever more VNs competing for a fanbase that isn’t significantly growing. While I’d be wary of claiming profits are falling, it seems highly likely they aren’t increasing, and a stagnant market is not a healthy one.
Personally, I think the future is bright. While VNs might not be destined to become blockbuster successes, there is enough of sustainable fanbase to support lots of indie developers, who are the most prone to innovate and write interesting new stories. As a VN fan, I’m excited to see what comes next~
I hope you found the article interesting. I had wanted to include a section analysing the Steam users, how many VNs do JVN fans purchase compared to EVN fans etc. But I want to spend a little longer going into more depth on it, so I’ll have a post up next week on that. If you’re interested in more until then, check out my other posts, look out for updates on my twitter, or give me a yell on Discord (Sunleaf_Willow /(^ n ^=)\#1616). Special thanks to /u/8cccc9 for collaborating on the analysis, and Part-time Storier for proof-reading.
I just do these analyses for fun, but if you want to support my work with a tip, I accept small donations at ko-fi.
59 notes
·
View notes
Text
What Is Virtual Private Network
A Virtual Private Network (VPN) is a type of technology that establishes a private network through public networks. It is a reliable method to fight censorship, surveillance as well as to keep your data securely encrypted and secure. There are numerous advantages to using VPNs, but the main benefit is that they protect your data. VPN, but the main reason to use one is to protect your online privacy.
The Best Python Books for Beginners in 2022
1. What is a VPN?
VPN, also known as a virtual private network, also known as VPN is a means to safeguard your internet connection from unintentional access by anyone outside of the network. It's possible to use VPNs VPN to protect your online traffic, which ensures that nobody else is able to view what you're doing online. This is why a VPN can be a useful option to secure your privacy online.
CCNA Routing And Switching All In One Study Guide BOOK
2. Why use a VPN?
A virtual private network, or VPN is an online service that establishes an encrypted, secure connection from your computer to any network or website. VPNs protect your privacy and ensure that your online activity secure and secure. They also let you access content which is restricted by your ISP or a country. There are many reasons you should consider using VPNs VPN however the most prevalent is for access to content that is not available by your location, to bypass geo-restrictions on certain websites, and to help safeguard yourself from hackers and cybercriminals.
How To Configure Static Routing On 4 Routers In Packet Tracer
3. How to use a VPN?
Virtual Private Network (VPN) is a program that allows you to establish an encrypted and secure connection to a different network or computer. It allows you to transfer and receive data over the network even if your computer isn't linked to the internet. For instance, you could utilize VPN to connect to VPN and access Google Drive files from your phone, or to use the computer at a coffee shop that is secured by the school's firewall.
How To Configure Default Routing On 4 Routers In Cisco Packet Tracer
4. Benefits of the use of a VPN.
A virtual private network, also known as a VPN is a type of private network which uses a public network like the internet to connect remote users or sites. This is accomplished by creating a private network from an existing public network and then sharing connections between both networks. The VPN tunnels all communications across the public network, and conceals users' location, information, and their activity in the network. This means that the users' internet connection is secure and private.
How To Configure RIP Routing On 4 Routers In Cisco Packet Tracer
1 note
·
View note
Text
Installing Cowboy and Nitrogen from Scratch

Installing Cowboy and Nitrogen from Scratch
In this post I’d like to share how I have installed nitrogen with cowboy and done so “from scratch.” Despite the fact that nitrogen comes with install scripts to do this work for us, it’s important to me to be able to understand the way that the entire system operates. I want to make sure that when something breaks I’ll be able to figure out how to fix it.
Installation steps.
Create an empty rebar3 project.
The first step is to create an empty project where we will install everything.
rebar3 new app basic_nitrogen_cowboy
Before we’re done with this step we can fill in the README.md and the names in the rebar3.config and scaffolded files.
Install the dependencies.
At this point it’s time to install cowboy and nitrogen.
% in rebar.config [ {deps, [ {cowboy, {git, "https://github.com/ninenines/cowboy.git", {branch, "master"}}}, {nitrogen_core, {git, "https://github.com/nitrogen/nitrogen_core.git", {branch, "master"}}} ]} ]
rebar3 deps
These are really the only two dependencies we’ll need to get started. While some related depdencies exist for nitrogen, such as qdate and sync, these are enhancements and we can skip them until we need them.
Configure cowboy.
If we already had cowboy running we could skip paste this work, but for a new project there’s very little we need to do to get running.
Configure a route for serving static files.
Configure a route for handoff to nitrogen.
% in basic_nitrogen_cowboy_app.erl start(_StartType, _StartArgs) -> Dispatch = cowboy_router:compile([ {'_', [ {"/static/[...]", cowboy_static, {priv_dir, basic_cowboy_nitrogen, "web_static"}}, {"/[...]", cowboy_simple_bridge_anchor, []} ]} ]),
The static files are likely common to any setup, but they are specifically required to hand out the nitrogen JavaScript and CSS files which run the interactive bits. The other route needs no complicated setup because simple_bridge does the heavy lifting.
Since we’re not running any custom handlers nitrogen is going to use the default mapping between path segments and Erlang modules. In practice I always prefer to write my own routing handler so I can have explicit control over what modules are called when serving requests.
Configure nitrogen.
There isn’t much to configure for nitrogen either, thankfully. We need to create a main handler to load any custom handlers, so that nitrogen will know to load them. This needs to be called nitrogen_main_handler and it needs to export run/0 where we have the chance to add our handlers with nitrogen:handler/2. We may also export ws_init/0 to add the same or a different set of handlers for new WebSocket connections.
-module(nitrogen_main_handler). -export([run/0]). run() -> % nitrogen:handler(...) calls here wf_core:run().
It’s possible to completely customize how nitrogen initializes each request, but the default behavior is sufficient for most cases. Either way, we need to specify what we want, and unlike nitrogen_main_handler, whatever module we specify needs to implement the simple_bridge_handler behavior. The default is nitrogen’s own nitrogen.erl. I’d normally add this to my sys.config, but to keep things simple in this demonstration I’ll set the built-in default manually before initializing the web server.
% in basic_nitrogen_cowboy_app.erl start(_StartType, _StartArgs) -> + application:set_env(simple_bridge, handler, nitrogen), Dispatch = cowboy_router:compile([ {'_', [ {"/static/[...]", cowboy_static, {priv_dir, basic_cowboy_nitrogen, "web_static"}} {"/[...]", cowboy_simple_bridge_anchor, []} ]} ]),
Notice how we leave off the _main_handler part of the module name. nitrogen will find it with just our custom prefix.
Add a static page.
Technically we should be done at this point. We have a working web server, even though it doesn’t have any pages yet. Let’s add one by creating index.erl.
-module(index). -export([main/0]). main() -> "hello, world!".
Nothing we’ve built so far is special; cowboy can already render static pages. But we want nitrogen specifically for the server-side client interactivity. If we try to wire up events, set postbacks, or add continuations now though they won’t work; we’re missing the JavaScript modules that make that all happen.
Add client-side interactivity scripts.
To add the scripts we need to copy them from the nitrogen_core dependency and into our static web root; then we need to render a <script> tag that instructs the browser to load them. In this guide we’re going to rely on the rebar3 post_hooks to copy these over when compiling our project.
% in rebar.config {post_hooks, [ {compile, mkdir -p ./priv/web_static/nitrogen}, {compile, cp -R ./_build/default/lib/nitrogen_core/www ./priv/web_static/nitrogen} ]}
With this script in there our nitogen static files will stay in sync. You can, of course, pick and choose wherever you want to save these files. I chose to use one called nitrogen for my own organizational purposes, but this isn’t essential.
What is essential is adding two kinds of scripts to the rendered pages.
The static nitrogen scripts.
The dynamic inline script that nitrogen writes to initialize the client-side interactivity.
-module(index). -export([main/0]). main() -> - "hello, world!". + "hello, world!", + #template {text=[ + "<script src=/static/nitrogen/jquery.js></script>", + "<script src=/static/nitrogen/jquery-ui.min.js></script>", + "<script src=/static/nitrogen/nitrogen.min.js></script>", + "<script src=/static/nitrogen/livevalidation.min.js></script>", + "<script src=/static/nitrogen/bert.min.js></script>", + ]}, + #template {text="[[[script]]]"}.
Finally, after all this work, we can make our page interactive and nitrogen is fully working and initialized. Obviously there’s more configuration and more work to do before everything is done, but this is all one needs to boot up a site.
Post-setup enhancements.
For each project I build where I incorporate nitrogen I try to install it ‟from scratch” like this so that I have a familiarity with how it works and so I can feel like I truly understand it. When I read ‟to install, run this script,” I come away with an impression that the setup is complicated and tedious, but it’s much easier than that, and so much of the complication is taking care of conviences that don’t matter too much to me. I hope you can be enriched by exploring this fresh-start approach.
For the most part there are only two more things I do before I feel like my nitrogen setup is ready to go:
Add the sync dependency to make interactive development more convenient. This automatically recompiles the Erlang modules I’m writing as I write them - ‟hot reloading.”
Create custom router, security, and other handlers to further customize how nitrogenworks. By default, nitrogen transforms a URL path into a lookup for an Erlang module, given a customizable prefix. This seems risky to me and I like knowing that people will only be able to view pages that I intended for them to see. Custom routing can be tedious, but that’s balanced by providing a pease of mind about security as well as providing a central dispatch-style map of the site, not to mention giving an opportunity to build more complicated routing rules for unique sections of the site.
Changes in upcoming nitrogen release.
The next version of nitrogen only seems to require two changes to what I wrote in this post:
The static assets are found at lib/nitrogen_core/priv/www instead of at lib/nitrogen_core/www
It’s no-longer required to manually start nitro_cache before starting nitrogen_corein the application configuration.
0 notes
Text
Fortinet NSE4_FGT-7.0 Questions and Answers
NSE4_FGT-7.0 Fortinet NSE 4 - FortiOS 7.0 Exam is the new NSE 4 Certification exam replacement of Fortinet NSE 4 - FortiOS 6.4 NSE4_FGT-6.4 exam which will be retired on March 31, 2022. You can get the latest Fortinet NSE 4 - FortiOS 7.0 NSE4_FGT-7.0 Questions and Answers from PassQuestion to prepare well for your exam,all the exam questions are designed on the exact pattern so it allows you to experience as in an real exam. PassQuestion Fortinet NSE 4 - FortiOS 7.0 NSE4_FGT-7.0 Questions and Answers are according to the real exam pattern and help you to cover all the topics and objectives of NSE4_FGT-7.0 exam. If you study NSE4_FGT-7.0 exam once you will pass your exam with high grades in the first attempt.
NSE4_FGT-7.0 Exam Overview - Fortinet NSE 4 - FortiOS 7.0
The Fortinet NSE 4 - FortiOS 7.0 exam is part of the NSE 4 Network Security Professional program, and recognizes the successful candidate's knowledge of and expertise with FortiGate. The exam tests applied knowledge of FortiGate configuration, operation, and day-to-day administration, and includes operational scenarios, configuration extracts, and troubleshooting captures. The Fortinet NSE 4 - FortiOS 7.0 exam is intended for network and security professionals responsible for the configuration and administration of firewall solutions in an enterprise network security infrastructure.
Exam Information
Exam name: Fortinet NSE 4 - FortiOS 7.0 Exam series: NSE4_FGT-7.0 Time allowed: 105 minutes Exam questions: 60 multiple-choice questions Scoring Pass or fail, a score report is available from your Pearson VUE account Language: English and Japanese Product version: FortiOS 7.0
Exam ObjectivesFortiGate deployment
Perform initial configuration
Implement the Fortinet Security Fabric
Configure log settings and diagnose problems using the logs
Describe and configure VDOMs to split a FortiGate into multiple virtual devices
Identify and configure different operation modes for an FGCP HA cluster
Diagnose resource and connectivity problems
Firewall and authentication
Identify and configure how firewall policy NAT and central NAT works
Identify and configure different methods of firewall authentication
Explain FSSO deployment and configuration
Content inspection
Describe and inspect encrypted traffic using certificates
Identify FortiGate inspection modes and configure web and DNS filtering
Configure application control to monitor and control network applications
Explain and configure antivirus scanning modes to neutralize malware threats
Configure IPS, DoS, and WAF to protect the network from hacking and DDoS attacks
Routing and Layer 2 switching
Configure and route packets using static and policy-based routes
Configure SD-WAN to load balance traffic between multiple WAN links effectively
Configure FortiGate interfaces or VDOMs to operate as Layer 2 devices
VPN
Configure and implement different SSL-VPN modes to provide secure access to the private network
Implement a meshed or partially redundant IPsec VPN
View Online Fortinet NSE 4 - FortiOS 7.0 NSE4_FGT-7.0 Free Questions
Which three CLI commands can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.) A.diagnose sys top B.execute ping C.execute traceroute D.diagnose sniffer packet any E.get system arp Answer : B, C, D
Which two VDOMs are the default VDOMs created when FortiGate is set up in split VDOM mode? (Choose two.) A.FG-traffic B.Mgmt C.FG-Mgmt D.Root Answer : A, D
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors. What is the reason for the certificate warning errors? A.The browser requires a software update. B.FortiGate does not support full SSL inspection when web filtering is enabled. C.The CA certificate set on the SSL/SSH inspection profile has not been imported into the browser. D.There are network connectivity issues. Answer : C
An administrator has a requirement to keep an application session from timing out on port 80. What two changes can the administrator make to resolve the issue without affecting any existing services running through FortiGate? (Choose two.) A.Create a new firewall policy with the new HTTP service and place it above the existing HTTP policy. B.Create a new service object for HTTP service and set the session TTL to never C.Set the TTL value to never under config system-ttl D.Set the session TTL on the HTTP policy to maximum Answer : B, C
In which two ways can RPF checking be disabled? (Choose two ) A.Enable anti-replay in firewall policy. B.Disable the RPF check at the FortiGate interface level for the source check C.Enable asymmetric routing. D.Disable strict-arc-check under system settings. Answer : C, D
0 notes
Text
Pspspsps
Hey
What if.
Deltarune. But different
Presenting: Chararune!
This is an AU with a similar premise to an AU some of you may have heard of named OCarune (I think that's how it's spelled), in that all the canon characters are replaced by our OCs! But this time, all the OCs were placed into their roles via use of a randomizer.
We at the roleplay server had a lot to say, so we'll be splitting things up into several posts, starting with the main trio! (@kingofarachnidz wrote all these, I just made some minor tweaks here and there)
Kris!Pallet (by @kingofarachnidz)
An art hobbyist. Also music. Just draws for fun and likes to listen to music though. Got caught up in this by mistake.
Support magic all the way. Color wheel affects enemies, squares for allies.
Wheel:
-red provides 50% miss chance (attack that hits does no damage)
-orange imitates pain without causing damage
-yellow prevents physical attacks (magic is unaffected)
-green prevents support enemies from doing their job, but makes active enemies’ attacks erratic
-blue slows attacks
-purple inflicts a three turn damage over time equal to the magic stat
Squares:
-red damages all enemies once per battle (three for bosses)
-blue provides a strong shield once per battle (three for bosses)
-green boosts defense
-yellow boosts attack
Flashes his colors brightly to induce submission in the Mic Drop route. But his feathers change color based on current wheel magic during battles, defaulting to light grey.
Susie!Textile (by @keebsu/ @5gigabytes)
Pallet’s tutor. Got roped in while trying to help him find something. Still enjoys creating complex projects and the like.
Active in battle, and has a weapon he keeps throughout the whole journey. Replacement weapons are instead modifications to this one that can induce various stat changes, cause static effects, and be mixed and matched to an extent.
Still acts about the same as canon.
May have abandoned an incomplete project at an old daycare once...
Ralsei!Amy Bebe and Effie (by @ohmewhatsthis... wait a minute-)
Amy is renamed to Bebe (pronounced Beebee), so as to better convey her new basis.
Magical girls styled off mood BFF necklaces (the ones that change color with body heat). Still children, and have their castle in an old play place. Wear velvet satchel like shawls through chapter one.
The legend is most likely an excuse for adventure, but puppy eyes convinced the lighteners. (That and just a liiittle whining,,, just a tad)
While their base colors remain the same, mood affects the color. (As does rubbing them)
Bebe is more support while Effie is active, though still act as a unit in battle. Some spells are only used by Bebe, and some are only used by Effie.
Yes, Textile gets to yeet them at K. Round.
Menu is separated between them for separate equipment sets. Bebe uses wands and Effie uses axes.
0 notes
Text
Prerequisite knowledge to Pass CCIE Routing and Switching
Prerequisite knowledge to Pass CCIE Routing and Switching
Introduction
General Guidelines
Course Introduction
Course Scope
Basic Networking Terms
TCP/IP & OSI Model
Introduction to Network Devices
Introduction to Decimal, Binary and Hexa-Decimal Numbers
Work experience on Recommended Software:
Putty/Secure CRT
Cisco Packet Tracer
GNS3
Web-IOU
EVE-ng
Addressing Schemes
IPv4 Addressing:
History of IPv4 Addressing
Format of IPv4 Addressing
Classification of IPv4 Addressing
Calculating Number of networks in classes
Calculation number of hosts per network
Concept of Network-id and Broadcast-id
Subnet Mask and Wildcard Mask
Concept of Default Gateway
Routed & Non-Routed Ports
Rules of IP addressing for Routed Ports
Classless IP addressing:
Subnetting and Super-netting
IPv6 Addressing:
History of IPv6 Addressing
Format of IPv6 addressing
Network Prefix and Interface ID
Types of IPv6 Addresses
MAC Addressing:
History of MAC addressing
Format of MAC addresses
Types of MAC addresses
Lab Setup Experience
Basic Lab Setup with Cisco Devices.
LAN and WAN cables
Physical Overview of Routers and Switches.
How to access network devices locally.
Difference between local and remote access.
Introduction to terminal applications such as Putty, Hyper terminal and Secure CRT etc.
Introduction to Cisco IOS and CLI.
Initial Configuration of Cisco IOS.
Introduction of different modes of Cisco IOS.
Configure and verify clock
Configure and verify hostname
Configure and verify user access verification or
login password
Configure and verify enable password
Configure and verify enable secret
Learn how to modify, copy, write and erase configuration.
Verify running-config and startup-config
Create username, password and their privileges
Configure banners:
motd
login
exec
Practice above configuration of Cisco Packet Tracer and GNS3.
Advanced Configuration
Introduction to LAN and WAN interfaces.
How to configure and troubleshoot Ethernet and Serial interfaces.
Configure description on interfaces.
Configure ipv4 and ipv6 addresses on interfaces.
Configure Keepalive, clock rate and encapsulation on interfaces.
How to make admin up and down interfaces.
Verify connectivity with test traffic.
Introduce ICMP-echo and echo-reply.
Use of ping command and understand output.
Impact of round-trip time.
Remote-access with TELNET and SSH.
Introduction of DNS.
Configure DNS.
Introduction to DHCP.
How to configure DHCP on Cisco IOS.
Basic Routing
Introduction to Routing for reachability.
Understand next hop.
How to configure next hop with:
Outgoing interface
Next Hop IP address
Understand static routing.
Configure and verify static routing for IPv4
Introduction to Dynamic Routing
Types of routing protocols
Interior gateway protocols:
RIP: Routing Information Protocol
OSPF: Open Shortest Path First
IS-IS: Intermediate System to Intermediate System
Exterior Gateway protocols:
BGP: Border Gateway Protocol
Administrative Distance or preference of routing methods.
Configure and verify Default Routing.
Configure and verify DHCP Relay Agent.
Network Services and IOS Features
IOS and Configuration Backup with TFTP
Configure and verify CDP
Configure and verify LLDP
Configure and verify NTP: Network Time Protocol
Password Recovery
Configure and verify Embedded Event Manager: EEM
Configure KRON Scheduler
Configure and verify SYSLOG
IPv6 DHCP Server, Client and Relay Agent
IP Traffic Management
Introduction to Access Control List
Configure and verify standard ACL
Configure and verify extended ACL
Contiguous and dis-contiguous wildcard mask
Implement named and numbered ACL
Introduction to public and private IP addresses
Introduction to NAT and PAT.
Configure and verify network address translation
Configure and verify PAT/NAT-overloading
Deep Dive into Dynamic Routing
Understand and Implement Routing Information Protocol.
OSPF: Open Shortest Path First
Link State Algorithm
OSPF Process-id.
OSPF Router-id.
Configure Loopback Interfaces
OSPF Area-id.
OSPF contiguous wildcard mask
OSPF Metric: cost
OSPF Tables:
Configure and verify single area OSPF.
Design and implement multiple area OSPF.
Regular and transit area.
Define Internal Router, Backbone Router,
Backbone Internal Router, Area Border Router
and ASBR.
Introduce and configure redistribution.
Define seed/external metric.
Type 1 and Type 2 seed metric.
Static routes with null-0 for testing.
OSPF and Policy Based Routing
Introduction to PBR tools:
Route-map
IP prefix-list
Distribute-list
ACL
OSPF Design constraints and filtering
OSPF Packet types
OSPF neighbor states
OSPF over multi-access networks
DR, BDR and DRO roles in multi-access networks.
Introducing OSPF LSA types 1 to 7.
Regular area types:
Stub Area
Totally Stubby area
NSSA: Not So Stubby Area
Totally NSSA
Configure and verify OSPF Virtual Links.
Continuous and discontinuous OSPF backbones.
OSPF filters:
IP prefix-lists
Area filters
Passive interface
Route summarization
Authentication
Troubleshooting
Understand network troubleshooting tools and
techniques
Ping
Syslog:
Debugging
Conditional debugging
Traceroute
telnet
Advanced show commands with filters
Troubleshoot RIP related issues.
Troubleshoot OSPF related issues.
Deep Dive into Exterior Gateway Protocol
Introduction to EGP
Historical Background
Introduction to Multihoming
BGP fundamentals.
Internal and External BGP.
BGP attributes: Weight, Local preference, As-path, Multi exit discriminator, Origin
Router-id
BGP route-summarization
PBR with BGP attributes and PBR tools
Full Mesh i-BGP
Route-reflector configuration
BGP configuration best practices
BGP Packet types and states
BGP authentication
Deep Dive into Intermediate System to Intermediate System.
Understanding IS-IS routing protocol.
Importance of IS-IS in ISPs.
Comparison of OSPF and IS-IS
IS-IS L1, L2 and L1L2 Router roles
IS-IS L1, L2 and L1L2 neighbor relation.
IS-IS PDUs: L1 Hello PDU, L2 Hello PDU
L1 & L2 PSNP
L1 & L2 CSNP
IS-IS over multi-access network
DIS role in multi-access network
Route Leaking from L2 into L1
IS-IS for AF IPv6
Configure and verify Static Routing for IPv6 addresses.
Configure and verify RIP-ng
Configure and verify OSPF-v3
Configure and verify BGP (AF-IPv6)
Implementing VPNs DMVPN
Introduction to Virtual Private Networks
Configure and verify GRE tunnels
Configure and verify IP-Sec :IKE 1, IKE 2
Configure and verify DMVPN: Phase 1, Phase 2, Phase 3
MPLS & MPLS VPN
Understanding Switching Architectures:
Control Plane
Data Plane
Understanding Routing Information Base
Understanding Forwarding Information Base
Understanding MPLS
MPLS header
MPLS Labels
Label Information Base
Label Forwarding Information Base
Label Allocation
Label Distribution
Label Retention
Configure and verify basic MPLS
Understanding MPLS VPN
VRF
Route Distinguisher
Route Targets
MP-BGP
Multicasting & QoS
Introduction to Multicasting
Multicast Source & Client
Multicast Routing
Protocol Independent Multicast
PIM Dense Mode
PIM Sparse Mode
Rendezvous Point: RP
Multicast Domain
BSR
IGMP
MSDP
Introduction to Quality of Service
Network Congestion Management
Classification and Marking
IP Precedence
DSCP
Congestion avoidance with WRED
Queueing Techniques
Policing and Shaping
Ethernet Switching
Forwarding on the basis of MAC Addresses
Address Resolution Protocol
ARP Table/Cache
Switchport Modes
Access Ports
Trunk Ports
Static Trunk
Dynamic Trunk
DTP
Dynamic Desirable
Dynamic Auto
Dot1q and ISL
SPAN
RSPAN
Broadcast Domain
Collision Domain
VLANS
Introduction to VLAN
Configure and verify basic VLAN configuration.
VTP: VLAN Trunking Protocol
VTP mode server
VTP mode client
VTP mode Transparent
VTP Updates
VTP Pruning
VTP Versions
Introduction to GVRP
Native VLAN
Private VLANS
Voice VLANS
Inter VLAN Routing
Inter VLAN routing with Access ports
Inter VLAN routing with Router on a Stick
Inter VLAN routing with SVI (MLS)
Inter VLAN routing with Routed and Non-Routed Ports
Concept of SVI
How to allow and block VLANs on trunk links
L2 Redundancy STP
Introduction to L2 redundancy
Infinite switching loops
Broadcast storm
Inconsistent MAC address table
Introduction to Spanning-tree protocol
Bridge-id
Root Bridge
Non-Root Bridge
Switch Role Election
Port Role Election
Root Port
Designated Port
Non-Designated/Block Port
Impact of Bridge-id
Path Cost
Sender’s Port-id
Per VLAN STP: PVST
PVST+
Load-balancing and redundancy
STP Enhancements Protect STP Operations RSTP MST/MISTP
Implementing Portfast feature.
Implementing Uplinkfast
Implementing Backbonefast
BPDU Guard
BPDU Filter
Root Guard
Loop Guard
Understand & Implement RSTP
Understand & Implement MST
Link Aggregation Link Bundling EtherChannel L3 Redundancy
Introduction to link aggregation
Configure and verify EtherChannel
Port Channel
Channel Group
Static Implementation
Dynamic EtherChannel with Different Load-balancing techniques.
Introduce First Hop Redundancy
Hot Standby Routing Protocol
HSRP tracking
L3 Redundancy & Switch Security
Implementing VRRP
VRRP Object Tracking
Implementing GLBP
AVG
AVF
Implementing GLBP Object Tracking
Implementing Switch Port Security
DHCP Snooping
Dynamic ARP Inspection
VACL
VLAN access-maps
0 notes