#diffie-hellman
Explore tagged Tumblr posts
Text
Why I should never read my email
There was an email in my inbox from Commercial Observer (a commercial real estate industry newsletter/magazine), including links to an article titled “SHED Pitches Itself as an Affordable Scaffolding Alternative to Urban Umbrella”. For those who don’t know, sidewalk scaffolding, or sidewalk sheds, are required under New York City Local Law 11, which mandates that building facade inspections and…
View On WordPress
0 notes
Text

Tips for Studying Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Getting started in cybersecurity involves learning a lot of concepts and techniques from all across tech, from networking to operating systems. After that, there's a lot of security-specific tools and knowledge to absorb as well. This post focuses on some of the big things that helped me as I've studied for certifications over the past few years.
Memorizing Acronyms
There are a ton of acronyms used in cybersecurity - if you're studying for the Security+ certification, there are about 300 acronyms that you're expected to understand, and a lot get thrown around while you're on the job. It can sound overwhelming, but my two main strategies are 1) make and use flashcards (I use Anki) and 2) take the time to learn what the thing behind the acronym actually is. The ones that confused me most were always the acronyms for a protocol or something where I didn't actually know what the protocol did.
Memorizing Tool Usage & Command Line Options
How do you specify the target architecture in msfvenom? Which nmap option starts a TCP connect scan? If you're on the tech side of security and not governance, or if you're just studying for certifications, a lot of them will ask you to use command line tools and therefore memorize some of the most common options. The best way to learn these is to just practice using the tool! Anki can be helpful if there's a lot that you have to memorize to pass an exam, but practicing with the tool is a more interesting and memorable experience.
Also, it's not the end of the world if you can't remember everything - manpages exist for a reason! Memorizing common flags and options just lets you work faster, and eventually you'll memorize the most important ones just by using the tool.
Memorizing Common Protocols & Port Numbers
More foundational knowledge here - this is important for entry-level certifications and just being able to interpret things on the job. This is just memorization again, so 1) create a flashcard deck and 2) make sure you know what the protocol actually does. It's harder to remember that IMAP over TLS is on port 993 if you don't know what IMAP or TLS is - build up those connections in your brain!
Understanding Complex Protocols, Processes, and Attacks
When you're trying to learn about network protocols (TCP, HTTPS, etc.), encryption algorithms (Diffie-Hellman, etc.), or the process of a specific attack, sketch a diagram! Draw it out and get as specific as you need. Keep trying until you can break the process down into tiny steps and explain it from memory.
When studying attack chains, you can make use of Mitre ATT&CK to note the different techniques used at different stages. Professional write-ups do this too, so it's a great way to practice.
Organizing your Notes
If you're studying for a GIAC certification, the tried-and-true strategy for passing the exam is to organize your notes and make an index - essentially a giant table of contents for all of the course material that you can search through very easily. GIAC exams are open-note, but there's an enormous amount of material in each course and you don't have time during the exam to search through the book for every question.
Lesley Carhart has a great write-up on their process that's worth a read - this is one of the resources that SANS.edu advisors point students to!
If you're studying for an exam that isn't open-note, making an index can still be helpful, especially if you keep your notes around for later reference. It's also a good way to review and find topics that you need to put a bit more time into.
The tl;dr here is:
Make flashcards for anything that you need to memorize. Use a spaced repetition tool like Anki that will let you study in short bursts over a long period of time, because cramming won't help in the long run.
Get your hands dirty! Practice the labs or sample problems, play with the tools, and experiment.
Keep good notes. It's very easy to feel a sense of information overload in cybersecurity, so having a system that lets you store information outside of your brain but still access it quickly is key.
If you have any questions about how I handle a specific topic or studied something, feel free to send me an ask!
15 notes
·
View notes
Text
beautiful women called diffie and hellman keep asking me about my keys
7 notes
·
View notes
Text
Transport Layer Security (TLS): The Backbone of a Secure Internet
In today’s digitally connected world, security and privacy are more important than ever. Whether you're accessing your bank account, shopping online, or simply browsing a website, you're likely using Transport Layer Security (TLS) — the cryptographic protocol that protects internet communications.
In this post, we’ll explore:
What TLS is and why it matters
How TLS works under the hood
TLS vs SSL
Real-world use cases
Common threats and how TLS mitigates them
Transport Layer Security (TLS) is a cryptographic protocol that ensures privacy, integrity, and authenticity of data exchanged over a network. It’s widely used to secure:
Web traffic (HTTPS)
Email (SMTP, IMAP, POP)
Messaging (XMPP, SIP)
VPNs and more
TLS operates between the transport layer (e.g., TCP) and the application layer (e.g., HTTP), encrypting the data before it's transmitted over the internet.
How TLS Works: Step by Step
When a client (e.g., browser) connects to a server over HTTPS, here's what happens:
1. Handshake Initiation
The client sends a ClientHello message:
Supported TLS versions
List of supported cipher suites
Random number (used in key generation)
Optional: SNI (Server Name Indication)
2. Server Response
The server replies with a ServerHello message:
Selected cipher suite
TLS version
Server's digital certificate (usually an X.509 certificate)
Optional: server key exchange
3. Authentication & Key Exchange
The client verifies the server's certificate via a trusted Certificate Authority (CA).
Both parties generate or agree on session keys using techniques like Diffie-Hellman or RSA.
4. Session Key Generation
Once keys are exchanged:
Both client and server compute a shared symmetric session key.
5. Secure Communication
All subsequent data is:
Encrypted using the session key
Authenticated (to detect tampering)
Integrity-protected using MACs (Message Authentication Codes)
TLS vs SSL: What’s the Difference?
People often say “SSL” when they mean TLS. Here’s the truth:Feature SSL (Deprecated)TLS (Current)Latest VersionSSL 3.0 (1996)TLS 1.3 (2018)SecurityVulnerableStrongUse TodayNone (shouldn't be used)Everywhere
Modern websites and applications use TLS 1.2 or TLS 1.3, and all versions of SSL are considered insecure.
TLS Use Cases
HTTPS (TLS over HTTP)
Secure browsing (padlock in browser)
Required for PCI DSS, GDPR compliance
Email Encryption
Secure SMTP (STARTTLS)
IMAP/POP with TLS
VoIP and Messaging
TLS protects SIP, XMPP, and chat services
VPNs
OpenVPN uses TLS for secure tunnels
APIs and Microservices
Internal and external APIs often rely on TLS to secure REST and GraphQL endpoints
Common Threats and TLS ProtectionsThreatTLS DefenseMan-in-the-Middle (MITM)Authentication via certificatesEavesdroppingSymmetric encryption of session dataTampering or Data CorruptionMessage integrity with MACsReplay AttacksRandom values and sequence numbersDowngrade AttacksTLS version enforcement & SCSV mechanism
Best Practices for TLS Configuration
Use TLS 1.2 or TLS 1.3 only.
Disable SSL and TLS 1.0/1.1 completely.
Use strong cipher suites (e.g., AES-GCM, ChaCha20).
Regularly renew and monitor your TLS certificates.
Enable HSTS (HTTP Strict Transport Security).
Use tools like SSL Labs, Mozilla Observatory to test your server.
TLS in Action (Example)
When you visit https://sfouresolutions.com:
Your browser initiates a TLS handshake.
The server sends its certificate.
A session key is negotiated.
Your browser encrypts the HTTP request with that key.
The server decrypts it, processes it, and responds securely.
All of this happens within milliseconds, seamlessly.
Final Thoughts
TLS is a foundational technology that quietly protects the internet. As cyber threats grow in sophistication, strong TLS configurations and practices are not optional — they are essential.
Whether you're a developer, sysadmin, or business owner, understanding TLS helps you build safer systems and protect user trust.
0 notes
Text
sorry I just gotta let y'all see the previous tags
Do you have improper cooling?
Are your fans not spinning fast enough?
Was your heatsink not installed right?
Did you forget thermal paste?
Cuz baby, you are HOT!
#prev tags#Baby ̦ did you set all your exponent bits to 0b1?#Because if I were to rank you from 1 to 10 you'd be NaN#Baby are you a poorly implemented hash function?#Because I get the feeling we're going to collide repeatedly#Baby are you a replacement for an if-then chain?#Because I'd switch for you#Baby are we components of a compiled program?#Because I want to get linked#Hey baby are you Kyber?#Because everyone is obsessed with you right now#Hey baby are you the NSA?#Because you're making me vulnerable to backdoor attacks#Hey baby ̦ let's just say Diffie-Hellman keys aren't the only thing I want to exchange#Baby ̦ you don't have to use ' OR '1'='1' -- to inject your code into me#Baby are you ready to be thread unsafe?#Because I want to do some simultaneous reading AND writing#Baby are you the coordinator node?#Because I'd obey your instructions any day#Baby are you an open socket?#Because I'm listening#Baby are you a sole maintainer of a critical open source library?#Because responsibility isn't going to be the only thing on your shoulders tonight
26 notes
·
View notes
Text
以太坊隐私新方案cWETH草案发布,无需修改协议层实现隐私交易
深潮 TechFlow 消息,6 月 18 日,一则名为”Confidential Wrapped Ethereum Privacy”的提案在以太坊研究论坛发布。该提案介绍了机密版包装以太坊(cWETH)的概念,旨在通过应用层实现ETH交易的隐私保护。cWETH结合椭圆曲线Twisted ElGamal承诺机制和Diffie-Hellman协议,并利用zk-SNARKs验证交易合法性,使用户能够在不泄露余额和转账金额的情况下进行点对点支付。与现有方案相比,cWETH无需解决离散对数问题即可访问加密余额,提高了效率。该方案有望发展成为完整的机密代币标准(EIP)。
0 notes
Text
The Future of Data Security: Advanced Encryption Algorithms
Every time we share a file, store data encryprion in our cloud storage, or collaborate online, we fear exposing information to some unknown threats. With the ongoing data breaches in the digital landscape, securing data has become the call of the hour.

Traditional encryption methods that used to be reliable are now struggling to keep pace with today’s threats. They weren’t designed to handle the rapid-fire attacks, massive data demands and other looming challenges.
However, to stay ahead of the game, there are advanced encryption algorithms that are robust and future-ready. Protect sensitive data in this ever-evolving digital environment.
This blog will shed light on these advanced encryption algorithms and discuss how they can protect our information.
What is Encryption?
At the very core of security, encryption is like locking your data into a digital safe. Only people with the key can open it. But the safes aren’t all built alike. In encryption, once you decide to secure the data, there are encryption methods, which are broadly categorized into two categories, namely – symmetric and asymmetric.
Symmetric encryption uses one key for both encryption and decryption, and in such a manner that it’s fast enough to encrypt large amounts of data, internal file storage, or a backup system. The difficulty, though, is in safely transmitting the key. If someone intercepts it, your data is at risk.
Used Algorithms include – the Advanced Encryption Standard (AES), the older Data Encryption Standard (DES), and its successor, the Triple DES (3DES) algorithm.
Asymmetric encryption operates using a pair of keys one public for encrypting the data and a corresponding private key used to decrypt it.
This encryption is slower compared to symmetric encryption but provides a safer way of exchanging information that does not involve sharing sensitive keys. WhatsApp, online transactions, and digital signatures are some examples of how this type of Advanced Encryption Standard is used.
Used Algorithms – RSA (Rivest-Shamir-Adleman), Diffie-Hellman.
Common Algorithms for Encryption
Choosing the correct encryption algorithm is no longer a technical decision; it’s now a matter of safety. Let us now look at some of the most extensively implemented encryption mechanisms that are building blocks today in data security.
1. AES (Advanced Encryption Standard)
The Advanced Encryption Standard (AES) is one of the most trusted symmetric block cipher methods used to secure data. It encrypts information in fixed blocks of 128 bits and supports key lengths of 128, 192, or 256 bits. Among these, AES-256 is recognized for its enhanced security and is officially approved by U.S. government agencies for protecting classified information.
Fast and highly safe, this is the best choice for either hardware or software implementations. Whatever the case, securing data in the cloud or even for internal systems, AES will always prove to be the most convenient, scalable, and reliable solution so governments, banks, and security-conscious corporations use it.
2. Triple DES (3DES)
Triple DES was made to improve the original DES (Data Encryption Standard), which was becoming vulnerable due to its limited key size. 3DES increases data security by using DES three times on a single block. While it was a reliable encryption algorithm at its time, it’s now considered obsolete and is being pushed aside by newer-generation algorithms like AES. Nevertheless, it is good to know that many legacy systems still use that.
3. RSA (Rivest–Shamir–Adleman)
The RSA algorithm was among the first widely used asymmetric encryption techniques. It generates two keys, one private and one public. For transferring safe data across open networks like the Internet, this makes it ideal. Emails, SSL certificates, and digital signatures are all encrypted using RSA. It is, however, slower than symmetric methods and thus cannot be used in encrypting enormous volumes of data.
What makes an algorithm advanced?
For an algorithm to be considered advanced, it must be resistant to contemporary attack methods such as cryptographic analysis and side-channel attacks. It should also be scalable. Most importantly, it needs to be future-proof or at least adaptable to the fast-changing landscape of cybersecurity.
In this case, the Advanced Encryption Standard (AES) is a prime example, particularly the variant of AES-256. This version involves 14 rounds of encryption, where the data undergoes a series of shifts, substitutions, mixing, and key additions that make it quite impossible to decode without the exact key.
Preparing for the Future: Securing Data with Advanced Encryption Algorithms
The repercussions of inadequate data security can be severe, affecting everything from customer trust to regulatory compliance. That’s why innovative organizations are investing in advanced encryption algorithms now to tackle the challenges of tomorrow.
Platforms like eShare.ai are leading the charge in this transformation. By adopting cutting-edge encryption standards
and facilitating secure file collaboration, this platform makes sure that sensitive information remains safe, whether it’s being stored, shared, or accessed by different teams. That’s because the future of data security isn’t just about stronger defenses; it’s about smarter, scalable, and proactive measures.
0 notes
Text
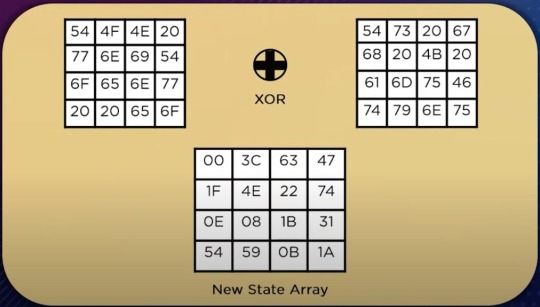
Dairy 24/4/25
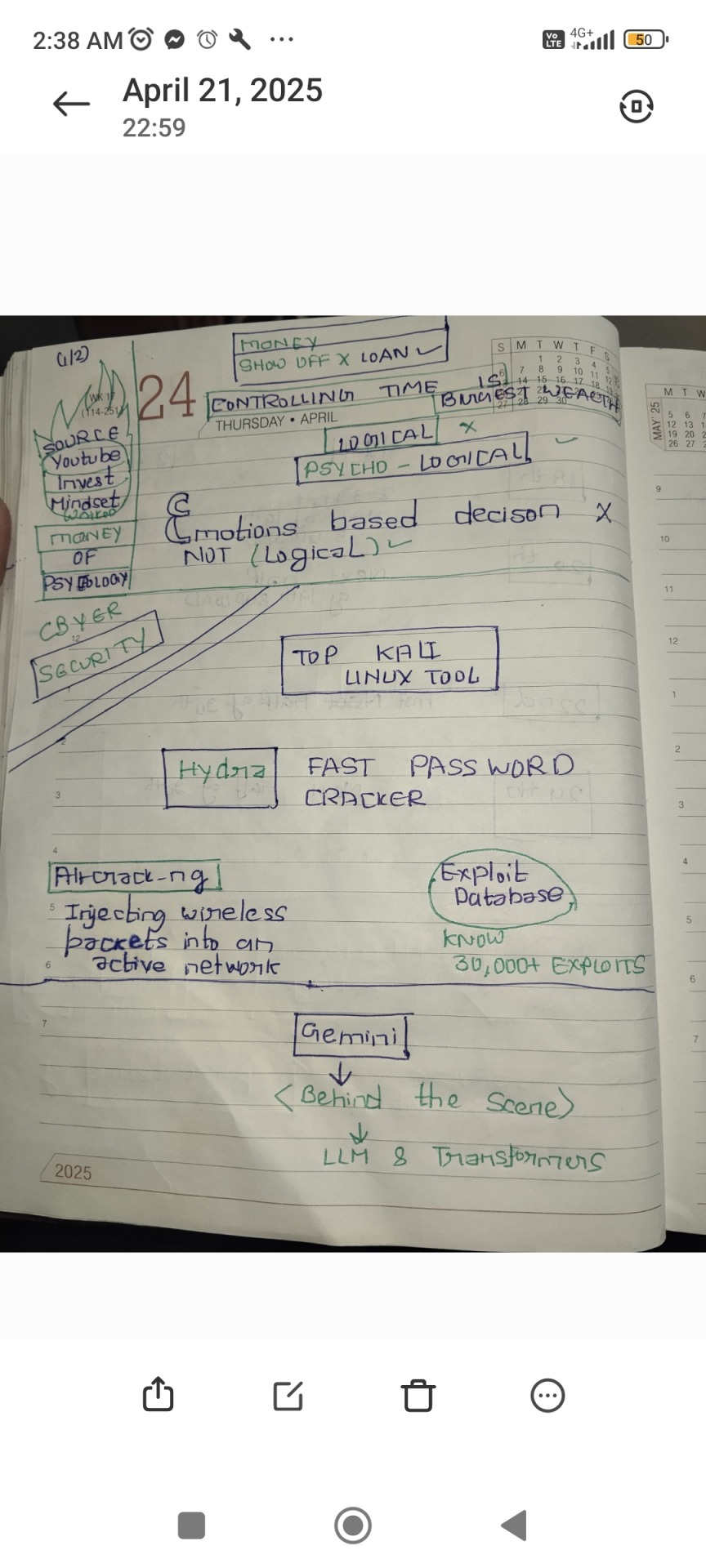


The goal of dmitry is rangefinder is to find out which IP's are used by target used servers.
Gray Hat Python Book : Page 27 Elipse and Pydev is required.
Silenceonthewire page 33 smart cards are here thanks to the contribution of Diffie, Hellman, Rivest, Shamir, and Adleman.
MetaspoitGuide page 29 Threat Modeling : 1) Use the information you acquired in the intelligence gathering phase to identify existing vulnerabilities in the system. u Development of general tools specialization, test procedures, test criteria, test sets and test hardware.
Python for Forensic and system engineer python setup. py install install nmap package
LLM Models Page 16
Self Attention Allows the model to weight different part of sequence to each other in Pararell without processing token at one time
Hallo : Hello. Hallo, wie geht's : How are you? Gute Morgen : Good Morning.
Hotel, Identify, iilusion and Insult same in French and English.
un aeropuerto = an aeroplane. el pecho = chest
hallunicate = ai system produces false information.
contact : [email protected] Till 26/4/25 1) English for IELTS, SPEAKING, Duolingo coaching, 2) AI and Analytics Training. 3) Mathematics Class 1 to Graduation.
0 notes
Text
Abstract The literature review is on the digital signature and the opinions of different writers who have written on this topic. There have been some articles written on the topic of digital signature, a problem on cryptography needs to be solved, there are different companies and organizations that continuously use computers to carry out transactions between them and their customers. A system that cannot allow outsiders to access the insider information on these companies needs to be set up; this will help to prevent the possibility of the company computers being hacked into. Introduction A digital signature is quite effective in the sense that any person who tries to get into the companies database but does not have the access code is immediately denied access. The administrators can also be able to determine whether the information that they are receiving from their clients is genuine. The digital signature helps a person to know that the information is original and that it has not been interfered with. Companies that make use of digital signatures are able to curb the possibility of receiving falsified information. These signatures are used in some countries as a form of authenticating the information that has been put on the internet or in any computer application, this helps to determine whether the information is just as the writer intended it to be. A lot of companies are establishing the use of digital signatures in most of their transactions, thereby enhancing the importance of encryption of data in all companies’ computer systems. Cryptography is important as it facilitates the maintenance of security of any company’s data and ensures that only the right people access the company data. In an article on a method for obtaining a digital signature, Rivest et al (1978) have discussed their view of encryption widely. They state that: An encryption method is presented with the novel property that publicly revealing an encryption key does not thereby reveal the corresponding decryption key. This has two important consequences: (1) Couriers or other secure means are not needed to transmit keys, since a message can be enciphered using an encryption key publicly revealed by the intended recipient. Only he can decipher the message, since only he knows the corresponding decryption key. (2) A message can be “signed” using a privately held decryption key. Anyone can verify this signature using the corresponding publicly revealed encryption key. Signatures cannot be forged, and a signer cannot later deny the validity of his signature (p.120). They give information on the encryption concept and an explanation of how it works. According to them, the process is quite useful because even when a person knows the key-encryption key, he would not be able to access the data contained in that computer if the person was not able to access the decryption key. It, therefore, means that only the person who knows both keys can be able to access the company data. There are two issues on cryptography that have been discussed by Diffie and Hellman (1976) in their article on cryptography. They state that “Widening applications of teleprocessing have given rise to a need for new types of cryptographic systems, which minimize the need for secure key distribution channels and supply the equivalent of a written signature.” They also claim that there is a need to find solutions to the problems that arise due to encryption. Their article also “discusses how the theories of communication and computation are beginning to provide the tools to solve cryptographic problems of long-standing” (p. 644). There is a connection between the issues that the article writers talked about. They seem to have been writing about how the majority of companies are trying to protect the data that they have saved in their computers, the majority of the transactions between the companies and their clients are electronic. With the advent of electronic transactions, there are risks that the data could be accessed by unauthorized persons and therefore be interfered with. The notion of digital signature was coined by Heyst and Chaum (1991), the idea of a person signing on behalf of other persons on receiving a message on a computer is quite convenient for the whole company. The idea that an employee can sign documents on behalf of others in a company, without the receiver realizing that the message that he received was not signed by who he expects to have signed, saves time for the other employees. Only one person has access to the group signature password so the signature cannot be used by unauthorized persons, the administrators can therefore be able to verify who it was that used the signature (p.257). The concept of signatures based on identity has been recommended, this is according to Rivest et al (1978). However, this concept had certain disadvantages that include the expensive “Bilinear pairing” from which it comes from. The use of this ring without pairing is, therefore, more affordable. There is therefore a recommendation for use of ring signature based on “quadratic residue” which is more efficient (p.122). Miyazaki et al (2006), claim that when a digital signature has been used, the contents of the documents cannot be changed thereafter. This is mostly done to reduce the possibility of the contents being interfered with and the meaning of the document being changed (p.343). An article by Niccache et al (2008), introduces the notion of “twinning”, which makes the signing of short messages possible, and the writer, therefore, has to sign twice in his message by a signature scheme (p.20). Wireless network sensor (WNS) makes it impossible to use “asymmetrical cryptography”; this is according to Driessen et al (2008), in the article that they wrote on the security of the wireless network. There is also a need for the concerned parties to make sure that they receive each other’s signatures on the internet, this will enhance security for both companies as they will have evidence of each other’s commitments to the contract that they had both agreed to honor (p.31), this is what Wang (2005) states in his article about the conference on the world wide web in Japan (p.412). Summary/ Evaluation The ten articles that have been reviewed contain information on encryption by different companies, and why it is important in the security of any company, with encryption the company’s data and private information cannot be assessed by unauthorized people. The use of digital signatures also ensures that only genuine businesses are conducted and that the company is not conned by online fraudsters. Electronic signatures use can be found in many different transactions, among them is in the use of e-mail on the internet and also in money transfer which is carried out electronically. Diffie and Hellman (1976), claim that it is easy to use encryption and decryption and that both processes are similar; in both, there is the use of public numbers and confidential numbers (p.646). The companies today always conduct their transactions electronically, that being the case, Subramanya and Li (2006) in their article on digital signatures, claim that there is a need for the companies who conduct their businesses electronically to guard their data against their competition and online fraudsters, this ensures that the data has not been interfered with and that the information on the company that they had offered to their customers is still the same and is authentic. Digital signatures serve the same purpose as manual signatures; their function is to authenticate documents that are sent online as opposed to being sent manually. The concept of digital signatures is relatively new but there is a high possibility that many more companies will adopt it accordingly (p.5). Group signatures are a quite important concept in all companies, Chaum and Heyst (1991) came up with it, a person can be able to make signatures for other people whom she works with, if she has a prestigious position, then she can not only be able to sign for fellow workers who are in similar positions, but also for workers who are of lower status. The data can be a lot or little depending on the number of people involved but in some cases, the person who makes the signatures can be easily recognized. The article was written on ring signatures by Rivest, Shamir, et al (1978) contains a lot of information on identity-based ring signatures, the writers state that these kinds of signatures have been under scrutiny by different people just as they have been recommended by a lot of people. The fact that the signatures which are not paired are more popular is apparent, based on the article, the ring signatures which are made from “bilinear pairing” are too costly and that is why the majority of people prefer to use the “ID-based ring signatures based on quadratic residues (p.123).” These kinds of signatures are more efficient as compared to the ones which are paired. What makes it more efficient is the fact that is less likely to be falsified by the people who would like to sabotage the company. Only the person who gave the mandate to make the signature can be able to use the ID-based ring signatures as compared to other signatures. When a document has been written and a digital signature has been put on the document, the content of the documents cannot be changed under any circumstance. This is according to Miyazaki et al (2006) in a document that they wrote concerning a conference on “Information, computer, and communications Security”, which was held in Taiwan. They however recommend that there is a need for an opportunity for the document to have some form of changes done on the document; nonetheless, the modifications should be done about the safety of the overall documents. The information contained in the document should be changed accordingly so that the meaning of the document does not change (p.344). The writers further say that in the case of formal documents, the private information is in most cases shrouded in such a way that, only an authorized person can be able to assess the information. The same case applies in “national security” documents which the state does not want to fall into the wrong hands. In most cases, only certain information can be revealed when a person asks for it. When the information that has been requested is done through the “current digital signature scheme”, there is a possibility that the person requesting the information will not be able to assess the information that they are looking for because the private information, in that case, has been protected from interference (p.345). Read the full article
0 notes
Text
Diffie-Hellman and Encryption Project
Purpose In this project, you will gain experience working with existing libraries to perform encryption using a 256-bit key. To generate the key, you will implement a part of the Diffie-Hellman algorithm. In doing so, you will also learn how to work with very large numbers that are too large to store in a standard data type such as integer or long. Objectives Students will be able to: Implement…
0 notes
Video
youtube
Scambio di chiavi segrete (Diffie-Hellman) - Computerphile
Come si scambia una chiave segreta in chiaro?
Cos'è la crittografia a chiave pubblica e come funziona realmente. Se vuoi una spiegazione reale, buona e visiva di come funziona, con semplici calcoli matematici, guarda il video di Computerphile su Diffie-Hellman: https://www.youtube.com/watch?v=NmM9HA2MQGI
(via Secret Key Exchange (Diffie-Hellman) - Computerphile - YouTube)
1 note
·
View note
Text
Make Your Business Communication Effortless with Troop Messenger
Troop Messenger business conversation is the safest and most efficient way to do business. With features like data protection, a secure and controlled admission protocol, convenience of use, and intellectual property ownership, Troop Messenger is the greatest business instant messaging solution available. This business chat software was especially created with you in mind. Enjoy the use of Troop Messenger, a potent tool for communication.
Troop Messenger - Team Collaboration and Instant Messaging App
Streamline team collaboration with Troop Messenger, the top instant messaging app for businesses. Boost productivity and communication in one platform.
Empowering Collaboration Across Industries
Troop Messenger caters to diverse industries, offering tailored solutions to meet specific collaboration needs. Here's how it benefits various sectors:
1. Defence: We are aware of the particular difficulties you encounter in safeguarding your important information. As a result, we have made use of a well considered military communications system that offers the greatest advantages. Use Troop Messenger, a defence messaging tool, to bind and shield your communications from prying eyes. With the following features, you can feel safe using this texting app for defence.
2. Government: A resourceful cum end-to-end encrypted messaging app for Government sectors, designed to sort all your complicated work in one place shrinking the latency issues. HD Audio/ Video calls & messaging in one on one or groups, video conferences, secure file sharing, and among others are some of the features of this secure chat application.

3. Politics: Share party news, official announcements, latest activity updates of the party, all across one platform through customized political campaign software! Keep your party associates connected all the time through this Android and iOS voter management apps!
Provides secure collaboration for the political parties with:
Messaging, calling, audio-video conferencing, live-telecasting, voter participation on social media, and more! For Political Party Leaders, it's all in one safe political collaboration tool. Bring people, cadre, and party activists to this instant messaging app for political parties for optimal and well-organized party discussions. Spread your political campaign with the features and facilities.
4. Ministry of Defence: Troop Messenger facilitates transparent MOD communication services to convey the policy framework of MOD to the armed forces to carry out their responsibilities. You can bring all entities onto this DOD mobile application to deliver the information securely.
Troop Messenger - Messaging Platform for Ministry of Defence
5. Army: Initiate Chat, Calls, remote screen access, conferencing, and more within this army chat app! Secure your sensitive army information with the world’s best security protocols and practices that combines the Double Ratchet algorithm, Pre-keys, and a triple Elliptic-curve Diffie–Hellman (3-DH) handshake, Curve25519, AES-256, HMAC-SHA256 as primitives.
6. Navy: High-trust and uniquely determined collaboration features for the seaborne branch! Integrate our end-to-end encrypted navy messaging system, the Troop Messenger, into your communication ecosystem; to securely chat, call, collaborate and meet.
7. Air Force: Reach the skies with secured Command-Control Instructions from the Base! We have incorporated highly secured collaborative tools for Airforce, such as chat, calling, audio-video conferencing, screen sharing, and others. Use it while conversating daily interactions, during natural disasters and internal disturbances, and for your other critical missions.
8. Defence Manufacturing: Our advanced Defence Manufacturing messaging system, Troop Messenger, help you exchange secure and classified conversations while you develop a comprehensive production infrastructure to produce weapons, systems, platforms, and military equipment required for defence across your Defence manufacturing industries.
9. Courts And Justice:Troop Messenger is an instant messaging and video conferencing tool designed for Indian courts. A unified communication system is necessary for a single, integrated, and independent judiciary to enable smooth cooperation among its judges, attorneys, court employees, etc. With this court administration software, you may transmit court orders over encrypted lines, upload case files to a secure file repository, broadcast court sessions live, and much more.
Virtual Communication Support for Virtual Courts
Courts need secure video solutions for virtual courts, such as Troop Messenger. Start conversating with the wide range of features and facilities available within this secure communication for court and justice department that helps have seamless virtual court proceedings.
10. Law Enforcement Agencies: Hinge on this law enforcement app to bring the hierarchies of your police system onto the unified communication platform to pass on the orders of law enforcement to the police on duty to maintain public safety and social order and prevent crime across your jurisdiction.
Secure Messaging Web and Mobile App for Police
A compliant messaging system for Police, Troop Messenger, is the best platform designed to solve the complexity of the communication process. With the help of advanced, safe, and secure features and intense collaboration facilities, it shall not allow classified data to fall into the hands of unauthorized persons.
11. Intelligence Agencies: Use this modern, agile, and sophisticated instant messenger for intelligence in your country’s internal and external intelligence agencies to encrypt and safeguard the flow of critical conversations while protecting your nation against domestic and foreign threats.
100+ features which can transform & enhance workplace productivity.
12. IT and Software Development: In the fast-paced world of IT and software development, effective collaboration is paramount for project success. Troop Messenger is Best messaging app for IT and Software Development compenies.
13. Healthcare: In the healthcare sector, timely communication can be a matter of life and death. Troop Messenger provides secure messaging channels compliant with HIPAA regulations, enabling healthcare professionals to exchange sensitive patient information securely while collaborating on patient care.
14. Education: In the realm of education, seamless communication between educators, administrators, and students is essential for academic success. Troop Messenger serves as a virtual classroom, enabling educators to conduct lectures, share resources, and engage with students in real time, regardless of physical distance.
15. Finance and Banking: Security and compliance are paramount in the finance and banking industry. Troop Messenger offers end-to-end encryption and compliance features, ensuring secure communication among financial professionals while facilitating collaboration on transactions, compliance tasks, and risk management.
What is Troop Messenger?
Troop Messenger is a centralised, secure digital platform that helps with team or interdepartmental communication. It is a solution designed to offer secure communications for Intelligence Agency Communication Solutions via message, phone, conference, and share screen, among many other time-saving productivity collaboration features.
On-premise Chat Server
Store your private and confidential call and conversation data inside your data centers using the highly secure and readily deployable on premise service paradigm! We developed this self-hosted collaboration solution with chat server that is compatible with the intranet to facilitate seamless workplace communication.
Sick of TeamViewer? Try Free TeamViewer Alternative
Troop Messenger is the best Team Viewer alternative that allows users to connect with remote teams with lightning speed.
While presenting the screen contents to remote users, one can highlight the required section with the help of screen annotation.
Why Choose On-Premise/Troop-GRIT?
Troop-GRIT is an On premise Chat Server edition of the Troop Messenger team collaboration application. That being said, you can deploy the self-managed Troop-GRIT on your local or on-premise servers to avoid third-party access to the application, such as from the public internet or any other means.
Free Live Chat Apps in India
Do you know that during the pandemic, some free live chat apps in India rescued the majority of businesses akin to online chat apps emphasizing the value of team communication while working remotely, amid the pandemic? These applications and website chat apps became an essential tool for keeping in touch with customers, clients, vendors, and others.
AnyDesk Alternatives
Market-available AnyDesk alternatives are capable of confusing users with their comparable capabilities. To avoid the contemplation process, read this blog and make an informed decision.
Troop Messenger, is one of the best team collaboration tools, offering real-time messaging, remote access, screen-sharing, and other features.
Free Screen Sharing Apps and Software
Screen sharing is one of the best dynamic collaboration features of Troop Messenger that allows members to share their screens during a chat conversation. Recipients can see real-time changes on the presenter's screen.
Troop Messenger's screen share function is powerful for enhancing team collaboration and conversation. With its smooth setup, interactive equipment, and strong security features, the Screen Sharing App on Troop Messenger permits green and productive virtual meetings. Whether you're conducting a presentation, troubleshooting trouble, or brainstorming together with your team, Troop Messenger makes display sharing simple and effective.
Features that Propel Team Collaboration
Troop Messenger offers a plethora of features geared towards facilitating smooth communication and collaboration among team members. Here's a closer look at some of its standout features:
Instant Messaging: With Troop Messenger, exchanging messages in real-time has never been easier. Whether you're seeking quick updates or engaging in brainstorming sessions, the app enables instant communication, fostering agility and responsiveness within teams.
File Sharing: Gone are the days of cumbersome email exchanges. Troop Messenger allows users to effortlessly share files of various formats, including documents, images, videos, and more. This feature ensures that crucial information is readily accessible to team members, promoting efficiency and productivity.
Group Chats: Collaboration often involves multiple stakeholders. Troop Messenger simplifies group communication by offering robust group chat functionality. Users can create dedicated chat groups for projects, departments, or specific topics, enabling seamless collaboration and knowledge sharing.
Voice and Video Calls: Sometimes, a face-to-face conversation is necessary to convey complex ideas or resolve issues effectively. Troop Messenger supports voice and video calls, allowing team members to connect instantly and engage in productive discussions irrespective of their physical location.
Integration Capabilities: Troop Messenger seamlessly integrates with a variety of third-party applications commonly used in the workplace, such as Google Drive, Dropbox, Trello, and more. This integration enhances workflow efficiency by centralizing communication and eliminating the need to switch between multiple platforms.
Remote Screen Share: Reach out to your remotest office teams with Troop Messenger’s productive and ultra-new screen share feature.
End-to-End Encryption: Your work conversations are under your complete control! Chats, calls, and conferences are end-to-end encrypted in this office chat app.
Conclusion
It becomes clear that Troop Messenger is a flexible and essential tool for encouraging teamwork and communication in a variety of industries. Troop Messenger is an office chat app that helps businesses meet their goals faster by streamlining processes, increasing productivity, and providing industry-specific solutions. Its extensive feature set and user-friendly design make it the ideal choice for any kind of organisation. Troop Messenger is the best team collaboration app for business talks and is suitable for nonprofit organisations, large corporations, and startups alike. It makes teamwork simple and boosts productivity in the digital sphere.
1 note
·
View note
Text
Are You Thinking Of Using Telegram中文版?

Telegram is a completely free messaging app with no ads membership fees, restrictions or subscriptions which could affect its services. It is available for Android and iOS as well as desktop computer systems, Telegram supports voice and video calls as well as data transfers that can be up to 1GB. Telegram has additional features, including the creation of teams or group chats as well as broadcasting voice or videos to a vast number of people. Telegram remains among the most loved applications in China despite its long-standing restrictions with over 500 million active users. The reason for this could be its secure end-to-end encryption system that blocks authorities from getting access to messages along with its capability to allow chats which will end when a specified amount of time.
There's a telegram version for Chinese. telegram Chinese version gives bots and channels to are able to cover topics from entertainment to news in addition to sticker packs which can use in chat rooms that include static, animated or video stickers which come with different options for each emoji. There's also an integrated bug report feature and suggestion tool that allows users to provide cards for the introduction of either new features or adjustments to the existing features.
The app is designed to offer end-to -end encryption to protect privacy, which means only the intended recipient can access messages that are sent through it. In addition, group messaging that can include more than 200000 participants and advanced features like replies, announcements and archives can occur simultaneously by using this app. Its secret chat feature makes use of Diffie Hellman keys exchange, which generates a unique encryption key per conversation which only your close friends glimpse as an image. to prevent anyone else from being able to read or interpret messages via secret chat even when you have access to your phone!
Telegram latest update brought the support of telegram中文版 . Since many people requested their inclusion in the program, this feature is finally available in the latest version. The users will install a third-party client software, then login using that client software - when they do this, their interface will switch automatically into Chinese mode.
Although many of the features are available in the telegram Chinese version but some features may not translate or work properly because of not being replaced by Telegram software and systems with Chinese interface languages. It is true that communicating with customers within their native languages is quite beneficial for Chinese foreign sellers because it allows for a lower cost in communication because of misunderstandings, and enhances quality of service to customers.
Telegram's Chinese version has more than one million active users and includes encrypted, free video and phone chats for domestic users, in addition to voice and language translations between Chinese and English and facilitating communications to global buyers. Further, the platform comes with multiple functions for companies to manage the sales process including centralized management and customer information integration.
vimeo
Telegram is a instant messaging app which uses encryption that is end-to-end to ensure privacy of users and protection, providing secure cloud storage of files and chats, without limits to file sizes and group sizes. Also, there are features such as self-destructing messages or even hidden chat rooms which will cease to exist after having a certain amount of time after a certain amount of time has passed.
Alongside the basic Telegram app, there are several third-party applications designed by native tech experts who include Chinese assistance, and may be telegram download from mobile app stores straight. These are free and simple for you to set up. Their capabilities are identical to the ones found in Telegram's original telegram app which includes:
0 notes
Text
0 notes
