#extracting information from mobile app
Explore tagged Tumblr posts
Text
Medicine Delivery App Data Scraping | Extract Medical & Pharmaceutical Data
Efficient data scraping for medicine delivery apps. Extract medical and pharmaceutical data in the USA, UK, UAE, Australia, Germany, and Spain for valuable insights.
know more:
#Medicine Delivery App Data Scraping Services#Extract Medical & Pharmaceutical Data#extracting information from mobile app#Data scraping from medicine delivery app
0 notes
Text
Realigning Food Delivery Market Moves with Precision Through Glovo Data Scraping

Introduction
This case study highlights how our Glovo Data Scraping solutions empowered clients to monitor food delivery market trends strategically, refine service positioning, and execute agile, data-backed business strategies. Leveraging advanced scraping methodologies, we delivered actionable market intelligence that helped optimize decision-making, elevate competitiveness, and drive profitability.
Our solutions offered a clear strategic edge by enabling end-to-end visibility into the delivery ecosystem to Extract Food Delivery Data. This comprehensive insight allowed clients to fine-tune service models, sharpen market alignment, and achieve consistent revenue growth through accurate competitor benchmarking in the fast-moving food delivery sector.
The Client
A mid-sized restaurant chain operating across 75+ locations with a rapidly expanding digital footprint reached us with a critical operational challenge. Although the brand enjoyed strong recognition, it faced a noticeable drop in customer engagement driven by gaps in delivery service efficiency. To address this, Glovo Data Scraping was identified as a strategic solution, as service inconsistencies directly impacted their revenue goals and competitive position.
With a broad menu and widespread delivery zones, the restaurant struggled to manage delivery logistics, especially during peak hours when quick shifts in demand required fast action. Their manual approach failed to support Real-Time Glovo Data Scraping, leading to missed revenue opportunities and weakening customer loyalty.
Recognizing the need to refine their delivery strategy, the management team saw that without proper visibility into Glovo’s delivery ecosystem, they lacked the insights necessary for efficient operations and practical customer experience management.
Key Challenges Faced by the Client
In their pursuit of stronger delivery market intelligence and a sharper competitive edge, the client faced several operational and strategic hurdles:
Market Insight Shortage
Limited insights into Glovo's platform and competitors made scraping Glovo Delivery Information difficult, preventing effective market analysis necessary for informed business decisions.
Slow Response Adaptation
Reliance on manual weekly evaluations slowed the restaurant chain's ability to act quickly. Without Glovo Delivery Data Extraction, adapting to real-time market changes became a challenge.
Demand Forecasting Gap
Traditional methods failed to account for real-time delivery data. The restaurant chain needed Glovo Product Data Extraction to predict demand and adjust services based on emerging trends accurately.
Manual Process Overload
Labor-intensive processes hindered efficient service decisions. By applying methods to Scrape Glovo For Product Availability And Pricing, the restaurant chain sought automation to optimize service delivery.
Service Consistency Issue
Inconsistent service quality across zones presented a problem. They required Mobile App Scraping Solutions to streamline operations and ensure consistent service delivery across all customer touchpoints.
Key Solutions for Addressing Client Challenges
We implemented cutting-edge solutions to the client's challenges, combining delivery intelligence with advanced analytics.
Delivery Optimization Engine
We built a centralized platform that leverages Real-Time Glovo Delivery Time Data Extraction to collect live data from various restaurants and delivery zones, enabling efficient decision-making.
Competitor Monitoring System
Our system, designed to Extract Restaurant Menus And Prices From Glovo, quickly identifies service gaps when competitors adjust, giving restaurant chains the edge to adapt promptly.
Dynamic Market Signals
By integrating multiple delivery signals, such as peak hours and weather, with Glovo Scraping For Restaurant Delivery Services, we created flexible models that adjust to market fluctuations.
Automated Service Recommender
Using Real-Time Glovo Data Scraping, we implemented an automated engine that generates service suggestions based on customer feedback and competitive positioning, reducing the need for manual input.
Strategic Adjustment Mechanism
Competitor promotions directly influence our service strategies by using tools to Extract Food Delivery Data, optimizing delivery times and fees while ensuring premium offerings remain profitable.
Cloud-Based Monitoring Hub
A robust Mobile App Scraping Solution enables managers to access and update delivery data remotely, facilitating continuous optimization and transforming strategy management into a dynamic process.
Key Insights Gained from Glovo Data Scraping
Service Elasticity Analysis Revealed delivery time sensitivity across different menu items, offering immediate operational optimization opportunities.
Competitive Positioning Patterns Provided insights into neighborhood-specific delivery differences, supporting targeted service improvements.
Pricing Cycle Optimization Illuminated optimal fee adjustment timing for different meal categories, aiding in more strategic revenue management.
Data-Driven Service Decisions Enabled the implementation of adaptive delivery models based on competitive positioning patterns.
Benefits of Glovo Data Scraping From Retail Scrape
Strategic Boost
By utilizing solutions to Scrape Glovo Delivery Information, the client improved delivery strategies, positioning their services for maximum value, enhancing market responsiveness to competitive shifts.
Loyalty Growth
Using competitor service insights, the client predicted market trends and strengthened customer retention, employing to Extract Glovo Product Data to stay ahead of shifts in demand.
Efficient Operations
The client minimized manual efforts by employing advanced Real-Time Glovo Delivery Time Data Extraction, driving faster decisions and better service while ensuring precise positioning and operational success.
Competitive Edge
With advanced techniques to Scrape Glovo For Product Availability And Pricing, the client gained critical insights into market trends, allowing for service adjustments that boosted profitability in competitive delivery sectors.

Retail Scrape's Glovo Data Scraping solutions revolutionized our approach to delivery market positioning. By gaining comprehensive access to Extract Food Delivery Data insights, we rapidly adjusted our strategy, refined our service models, and achieved a remarkable 37% increase in customer retention.
- Operations Director, Leading Multi-Location Restaurant Chain
Conclusion
Maintaining optimal delivery service positioning is crucial in today's competitive food delivery market. Glovo Data Scraping empowers businesses to monitor competitor services, make informed decisions, and improve market competitiveness.
Our customized solutions offer smooth delivery intelligence and actionable insights, allowing businesses to refine their competitive positioning. With in-depth expertise in Glovo Delivery Data Extraction, we equip businesses with the tools to unlock valuable insights for strategic growth.
Our specialists help evaluate market positioning, refine delivery strategies, and boost profit margins through Real-Time Glovo Data Scraping. Contact Retail Scrape today to minimize service inconsistencies, enhance market positioning, and drive long-term revenue with our advanced food delivery intelligence solutions.
Read more >>https://www.retailscrape.com/glovo-food-delivery-data-scraping-for-market-insights.php
officially published by https://www.retailscrape.com/.
#Glovo data scraping#Glovo delivery data extraction#Scrape Glovo delivery information#Real-time Glovo data scraping#Glovo product data extraction#Extract restaurant menus and prices from Glovo#Real-time Glovo delivery time data extraction#Scrape Glovo for product availability and pricing#Glovo scraping for restaurant delivery services#Extract Food Delivery Data#Mobile App Scraping solution
0 notes
Text


Sending him letters:
**Yes, he can receive international mails too! 💚**
- Mail must have his full name (Luigi Nicholas Mangione) and register number (52503-511).
- Mail will be opened and inspected by staff, so content must be kept appropriate or else it will be rejected. Do not talk about the incident. Talk to him like a friend.
These suggestions are collected from @renegadeforjustice (TikTok):
- Use plain paper.
- Use plain black/blue pen or pencil.
- Greeting cards can be included but they have to be as simple as possible (one piece of folded paper without any layer, embossing, glitter, or other extra material).
- Puzzles like crossword and sudoku can also be sent. Make sure to include the answers in a separate paper.
- Mail can include multiple pages.
- If you are not comfortable using your real name, you can use a pen name instead (just make sure it is a simple one with a first and last name).
Sending him packages:
From bop.gov:
“Inmates are not allowed to receive packages from home without prior written approval from the inmate's unit team or authorized staff member at the institution. The only packages an inmate may receive from home are those containing release clothing and authorized medical devices. However, inmates may receive magazines, hard and paperback books directly from the publisher.”
More information from Policy on Incoming Publications:
"At all Bureau institutions, an inmate may receive hardcover publications and newspapers only from the publisher, from a book club, or from a bookstore.”
“At medium security, high security, and administrative institutions, an inmate may receive softcover publications (for example, paperback books, newspaper clippings, magazines, and other similar items) only from the publisher, from a book club, or from a bookstore."
- Books, magazines, and newspapers can only be sent to him by the publisher/bookstore/book club themselves. You cannot mail it to him yourself. When ordering, put Luigi as the recipient.
- If you are going to use Amazon to send him books, there is a “send as a gift” button below the cart that you can click if you want to include a message to him as well.
Sending money to his commissary account:
To deposit money into his commissary account, you can choose from 3 options:
1.) MoneyGram
You'll need the following information:
Account Number: 52503511MANGIONE
Company Name: Federal Bureau of Prisons
City & State: Washington, DC
Receive Code is always: 7932
Beneficiary: Luigi Nicholas Mangione
a. At a MoneyGram location
Locate the nearest agent by calling 1-800-926-9400 or visiting: www.moneygram.com.
You'll need to complete a MoneyGram ExpressPayment Blue Form (see a sample form).
You can pay with cash.
b. Online
Please visit https://www.moneygram.com/mgo/us/en/paybills and enter the receive code 7932 or Federal Bureau of Prisons.
Enter the Receive Code (7932) and the amount you are sending (up to $300).
First time users will have to set up a profile and account.
A MasterCard or Visa credit card is required.
2.) Western Union
You'll need the following information:
Account Number: 52503511MANGIONE
Attention Line: Luigi Nicholas Mangione
Code City is always: FBOP, DC
a. Online
Please visit www.send2corrections.com
A credit/debit card will be required to complete a payment online.
You can also initiate a payment via mobile app and pay later with cash or payment card, at a Western Union agent location.
b. At a Western Union location
Locate the nearest agent by using our agent locator or by calling 1-800-325-6000.
You can pay with cash. Debit cards are accepted at select locations.
c. Over the phone
Call 1-800-634-3422 and choose option 2.
A credit/debit card will be required.
d. Via Send2Corrections mobile application
Search "Send2Corrections" in the Apple App Store (Apple iOS) or the Google Play Store (Android devices).
3.) Using mail
For detailed information, click on this link.
Information is extracted from bop.gov. Please visit the site if you need any confirmation.
💚F💚R💚E💚E💚💚💚💚L💚U💚I💚G💚I💚
43 notes
·
View notes
Text
In March 2007, Google’s then senior executive in charge of acquisitions, David Drummond, emailed the company’s board of directors a case for buying DoubleClick. It was an obscure software developer that helped websites sell ads. But it had about 60 percent market share and could accelerate Google’s growth while keeping rivals at bay. A “Microsoft-owned DoubleClick represents a major competitive threat,” court papers show Drummond writing.
Three weeks later, on Friday the 13th, Google announced the acquisition of DoubleClick for $3.1 billion. The US Department of Justice and 17 states including California and Colorado now allege that the day marked the beginning of Google’s unchecked dominance in online ads—and all the trouble that comes with it.
The government contends that controlling DoubleClick enabled Google to corner websites into doing business with its other services. That has resulted in Google allegedly monopolizing three big links of a vital digital advertising supply chain, which funnels over $12 billion in annual revenue to websites and apps in the US alone.
It’s a big amount. But a government expert estimates in court filings that if Google were not allegedly destroying its competition illegally, those publishers would be receiving up to an additional hundreds of millions of dollars each year. Starved of that potential funding, “publishers are pushed to put more ads on their websites, to put more content behind costly paywalls, or to cease business altogether,” the government alleges. It all adds up to a subpar experience on the web for consumers, Colorado attorney general Phil Weiser says.
“Google is able to extract hiked-up costs, and those are passed on to consumers,” he alleges. “The overall outcome we want is for consumers to have more access to content supported by advertising revenue and for people who are seeking advertising not to have to pay inflated costs.”
Google disputes the accusations.
Starting today, both sides’ arguments will be put to the test in what’s expected to be a weekslong trial before US district judge Leonie Brinkema in Alexandria, Virginia. The government wants her to find that Google has violated federal antitrust law and then issue orders that restore competition. In a best-case scenario, according to several Google critics and experts in online ads who spoke with WIRED, internet users could find themselves more pleasantly informed and entertained.
It could take years for the ad market to shake out, says Adam Heimlich, a longtime digital ad executive who’s extensively researched Google. But over time, fresh competition could lower supply chain fees and increase innovation. That would drive “better monetization of websites and better quality of websites,” says Heimlich, who now runs AI software developer Chalice Custom Algorithms.
Tim Vanderhook, CEO of ad-buying software developer Viant Technology, which both competes and partners with Google, believes that consumers would encounter a greater variety of ads, fewer creepy ads, and pages less cluttered with ads. “A substantially improved browsing experience,” he says.
Of course, all depends on the outcome of the case. Over the past year, Google lost its two other antitrust trials—concerning illegal search and mobile app store monopolies. Though the verdicts are under appeal, they’ve made the company’s critics optimistic about the ad tech trial.
Google argues that it faces fierce competition from Meta, Amazon, Microsoft, and others. It further contends that customers benefited from each of the acquisitions, contracts, and features that the government is challenging. “Google has designed a set of products that work efficiently with each other and attract a valuable customer base,” the company’s attorneys wrote in a 359-page rebuttal.
For years, Google publicly has maintained that its ad tech projects wouldn’t harm clients or competition. “We will be able to help publishers and advertisers generate more revenue, which will fuel the creation of even more rich and diverse content on the internet,” Drummond testified in 2007 to US senators concerned about the DoubleClick deal’s impact on competition and privacy. US antitrust regulators at the time cleared the purchase. But at least one of them, in hindsight, has said he should have blocked it.
Deep Control
The Justice Department alleges that acquiring DoubleClick gave Google “a pool of captive publishers that now had fewer alternatives and faced substantial switching costs associated with changing to another publisher ad server.” The global market share of Google’s tool for publishers is now 91 percent, according to court papers. The company holds similar control over ad exchanges that broker deals (around 70 percent) and tools used by advertisers (85 percent), the court filings say.
Google’s dominance, the government argues, has “impaired the ability of publishers and advertisers to choose the ad tech tools they would prefer to use and diminished the number and quality of viable options available to them.”
The government alleges that Google staff spoke internally about how they have been earning an unfair portion of what advertisers spend on advertising, to the tune of over a third of every $1 spent in some cases.
Some of Google’s competitors want the tech giant to be broken up into multiple independent companies, so each of its advertising services competes on its own merits without the benefit of one pumping up another. The rivals also support rules that would bar Google from preferencing its own services. “What all in the industry are looking for is fair competition,” Viant’s Vanderhook says.
If Google ad tech alternatives win more business, not everyone is so sure that the users will notice a difference. “We’re talking about moving from the NYSE to Nasdaq,” Ari Paparo, a former DoubleClick and Google executive who now runs the media company Marketecture, tells WIRED. The technology behind the scenes may shift, but the experience for investors—or in this case, internet surfers—doesn’t.
Some advertising experts predict that if Google is broken up, users’ experiences would get even worse. Andrey Meshkov, chief technology officer of ad-block developer AdGuard, expects increasingly invasive tracking as competition intensifies. Products also may cost more because companies need to not only hire additional help to run ads but also buy more ads to achieve the same goals. “So the ad clutter is going to get worse,” Beth Egan, an ad executive turned Syracuse University associate professor, told reporters in a recent call arranged by a Google-funded advocacy group.
But Dina Srinivasan, a former ad executive who as an antitrust scholar wrote a Stanford Technology Law Review paper on Google’s dominance, says advertisers would end up paying lower fees, and the savings would be passed on to their customers. That future would mark an end to the spell Google allegedly cast with its DoubleClick deal. And it could happen even if Google wins in Virginia. A trial in a similar lawsuit filed by Texas, 15 other states, and Puerto Rico is scheduled for March.
31 notes
·
View notes
Text
Limbus Company Update 2025/04/02
New Banners: Now, with a bang and rattle of chains The Middle Little Brother Sinclair Solo Banner had appeared. Also target extraction Don Quixote Banner, hopefully if you pull, you will be lucky to get Little Sister Don for team building. Sinclair kit suggests his preference for envy resonance. There is also new Identity Growth Pack with Uptie Takeoff module and exp tickets.
Change in profile decoration sorting and new sorting options for borders added, now they go by [Claim Date/Release Date/Alphabetical].
Weekly Update Bug fixes: Cinq East Section Don skill effect wasn't activating after first evade, while the coin power should be increased by open per two speed difference. With appearance of new Middle Identity, older ones got a look over and Little Sister Don counter skill description was adjusted to match her in game usage, that had been already established. Fixing the skill was deemed to be appropriate as this ID had been out for a while by now and a fix would weaken her kit. So at 6+ sum Envy resonance (does not need to be consecutive) use "A Just Vengeance" as counter. Fixed clashing ability of a skill in 7.5 - 25 (Nocturnal Sweeping - Sweepers) stage. When the Enkephalin Module recharge message pop up appeared while claiming Refraction Railway Lost and Found rewards, UI could start to malfunction. Choice hint wasn't matching results in choice event in Nocturnal Sweeping MD pack, and certain faction identities now possess bonus to certain choice events. Certain announcer was disabled from use in stage 6 - 41 (The Heartbreaking - Wild Hunt fight with assistance of certain character). Effect used by Middle enemies had been changed from "Vendetta Mark" to "The Middle's Vendetta Mark". Text that loaded on 6th page of Nocturnal Sweeping now loads properly. Adjustment in explanation of event currency for current Intervalo. Volume of certain sounds now can be adjusted for stage 7.5 - 25. In Heishou Pack - Mao Branch Outis uptie story term "reverse-jointed" was corrected to "Digitigrade". And just information about standardization for inconsistent Skill descriptions for EN.
Future fix 25/04/10: In Focused Encounters enemies who gain new phases or spawn again, load with details of their passives and skills in locked states. It came as a side effect of getting all information for all enemies. After returning to stage information menu just after one wave, giving access to the information on foes that hadn't been fought yet. There will be fix in game logic for that.
Compensation for errors is 300 Lunacy.
Custom Language Support: From this update onward, custom unofficial translation mods will be supported to make game more accessible. Officially supported languages are (Korean, English, Japanese). It is not explained how it is applicable for mobile application, just via Steam, but by connecting your device to PC and moving files following the guide.
Interested? Please check it out. Detailed and official guide here: https://store.steampowered.com/news/app/1973530/view/533220039674824263
Any other modifications to the game beyond text changes are unwelcome and might harm the game.
O nie… To nie za dobry pomysł by tłumaczyć tyle tekstu…
4 notes
·
View notes
Text
Modded Balatro on Android is possible! (and not easy to do, but here's a tutorial to help you do it).
Part of the fun of PC gaming is being able to mod games, and devices that run Steam games can still use mods BUT android ports cannot. This is due to the fundamental differences between Windows, IOS, and Android.
So modded Balatro on Android was out of the question.
Or so it appeared.
Turns out early on people realized that Balatro uses an engine called Love which is very easy to dissemble and dissect. So before the official Mobile port came out, players were able to extra the Balatro files from Balatro, turn those files into a zip, and then run the game as a zip file through the Android app Love2d.
Eventually this process became automated and if you have an android device in developer mode you can allow the app on a PC to install Balatro and transfer to save files along with it.
Well, as it turns out, this process can also allow you to install a modded version of Balatro, but it's uh, not transparent how it exactly works or what can go wrong.
But I figured it out! And I can show you how.
NOTE:
I will not provide a copy of my modded Balatro. You need to buy Balatro and install it on Steam. Buy a cheap key before you try to outright steal. That's my opinion.
Yes, you will need a PC. The mod files run through Lovely Injector. Lovely Injector supplements the mod data into the Love Engine, so when Balatro runs, Lovely Injector dumps the Mod game data into the game's loading process.
Guess what doesn't exist on Android? Lovely Injector.
Now pathing could change that but god help you if you want to change where lovely Injector pulls mod data.
So you can change that information at will so that it can pull the mod information from the pathing that Android uses. I tried to figure that out but could not do it. But that is a thing you can do.
Now with that out of the way, let's talk about how I figured out how to add modded Balatro.
Okay, so the first step is to download the tools you need. You have balatro of course, so now you require Balatro Mobile Maker and a couple Batch scripts. Also 7-zip
Here's a link to download 7-zip
And here's a link to download Balatro Mobile Maker, a list of compatible Mods, and the Batch files you will also need.
NOW, if you want to edit the textures and music on Balatro follow these steps.
Step 1: Go on nexus or any other website that hosts Balatro mods and download texture and music focused mods.
Step 2: Open Balatro.exe (easily found by right-clicking Balatro from your library and selecting “browse local files”) using 7-zip and extract the resources' folder, you can extract the whole thing if you want to, but it's not necessary.
Step 3: Fire up your art program of choice (it has to have built in transparency, so NO MS Paint.) Open both the default sprites you want to change and the mod sprites you want to use in the change, and just start copying and pasting. Keep in mind that there is a 1x and a 2x of most sprites, but you only require the 1x of a given sprite because once you're done editing you can just can resize that image to the resolution of the 2x and nothing is out of place. Also. If you are editing hologram Joker, make the sprite translucent. I saw several artists screw that up. You just need to make the sprite translucent, and it will work like the original hologram Joker does.
Step 4: Take that edited Sprite sheet and re-open the Balatro.exe file as an archive again. Overwrite the default sprites with your edited ones in the archive and close it. Now, Balatro will run with those edited sprites as the default ones.
Music has the same steps, only difference is that you'll need to change the file type to .OGG and you'll want to rename the music file to whatever track you want to replace. (Note that editing music files this way will result in the soundtrack being slowed down for whatever reason. You can compensate for that by presumably speeding the track up in Audacity)
Step 5: You will power up Balatro Mobile Maker and run it. The program should fetch all the tools it needs to run correctly. It will ask permission for various actions several times, just say yes to the most logical choices, fps 30 can be left blank. You can run the executable wherever for the most part (at least for this process it doesn't matter) and it will find your legal copy of Balatro, unpack, format it into an APK compliant format, and then repack the file to be played as an APK. Now you have a version of Balatro that plays with modified textures and music files.
That's pretty good, but what if you want to enjoy all the fun and interesting modded jokers?
Well, first off, you'll need to temper your expectations. Some of the best Balatro mods also completely overhaul how Balatro works, and the Mobile Maker cannot cope with maintaining that functionality with Android. I provided a folder of all the mods I know won't break the game at boot. Whatever happens after that is out of my hands.
Step 1: Delete whatever mods you have already in your Mod folder (excluding Lovely and Steammodded). Go into the lovely folder and delete the files in the dump folder as well.
Step 2: Drop the mods I provided into the mod folder and run Balatro. Assuming you didn't have any issues with the game finding Lovely or Steammodded you should have booted into the main menu with the Mod tab accessible. Play a new game and do a couple hands. Don't worry about winning the round, just play a couple hands so that instance of your game is saved.
Step 3: Run Balatro Mobile Maker. Run it as normal, but when it gets to the part where it asks if you want to transfer save files, leave it alone and Run Balatrofoldersetup.bat. That will copy and move around a bunch of files needed for the Mod Transfer process. Once you clicked that Bat once, go ahead and tell the Mobile Maker to transfer your save file. When it's done, click on Balatrofoldercleanup.bat to turn things back to normal. If you forget to do that, Balatro on your PC won't run. Don't worry. If you forget to do that, clicking on it at anytime will still work as intended.
Step 4: This is the hardest step. Doing Step 1-4 over again because X thing happens.
If your pc is hooked up to your android device and mobile maker is supposed to be installing it on your Android device (and has the permissions to do so) but doesn't install it. Try again. If the App just plain crashes, move the app to a different folder and try again. I hear it works best in folders where the Balatro.exe file actually is, but I alternated between download folder, Balatro Mod folder, and the actual folder that contains the Balatro game files and there was no real difference.
If the save transfer finishes in a couple seconds, it didn't work. You can confirm it by opening the Balatro game and seeing that it's just default Balatro without the Mod tab. If the save transfer process takes several seconds to actually transfer the data, then it's actually legitimately working. If you boot up and see evidence of your previous game progress and the mod tab, you're in! Enjoy it friend!
Addendum:
Yes, I know that people have gotten Jen's Almanac, Pokermon, and especially Cryptid working on Android, I don't like using the Jen and Cryptid mods because they're just insane and exist for the spectacle.
The Vanilla Joker mods dilute the collection of Jokers making the really powerful cards less likely to show up and making really odd niche cards more likely to get in the way, this adds a bit of challenge. Jen and Cryptid having many face roll jokers eliminates that, however.
Also, a lot of overhaul mods require modifying the shader files to get the game working on Android, and I just don't know where to begin fixing that. I tried the patches and they didn't work.
If you know the solution to "error validating vertex shader code: Line 125 error '/': wrong operand types: no operation '' exists that takes a left-hand operand of type ' global highp float' and a right operand of type ' const int (or there is no acceptable conversion)"
Post it on this web zone, I'm not the only one wanting a solution for that, and no one on the Balatro Mobile Maker GitHub had a solution (that worked).
There are other mods I skipped that probably worked but didn't personally want in my pack, so go to Mirahaze and download whatever mod you like and go through the steps I tried. If you boot up the Android app, and it crashes, specifying that some abbreviated file linked to a specific mod was not found or had trouble installing, get rid of the mod. You could fix it, but if you could do that, you probably didn't need my help to begin with.
2 notes
·
View notes
Text
𝐓𝐨𝐩 5 𝐅𝐮𝐭𝐮𝐫𝐢𝐬𝐭𝐢𝐜 𝐒𝐢𝐝𝐞 𝐇𝐮𝐬𝐭𝐥𝐞𝐬 𝐟𝐨𝐫 𝐓𝐞𝐜𝐡𝐢𝐞𝐬 𝐢𝐧 2025
In today’s fast-paced tech world, side hustles can be a fantastic way for professionals to boost their skills and earn extra income. With advancements in artificial intelligence, remote working, and a growing need for tech solutions, 2025 is filled with exciting possibilities for tech enthusiasts.
This post dives into five promising side hustles, supported by data and trends. Techies can capitalize on their expertise and thrive in these areas.
1. Remote IT Support
With businesses shifting to hybrid work models, the demand for remote IT support has skyrocketed. According to a report from the International Data Corporation (IDC), the global IT services market is set to hit $1 trillion by 2025, hinting at tremendous opportunities in this field.
Techies with skills in troubleshooting can offer services to both businesses and individuals. The TechServe Alliance notes that the demand for IT support roles surged over 10% last year, making this a vibrant market.
Starting a remote IT support hustle is easy. Freelancing platforms like Upwork and Fiverr allow techies to find clients quickly. Depending on the complexity of the service, they can earn between $25 and $150 per hour while enjoying the flexibility to work on their own schedule.
2. Cybersecurity Consulting
As cyber threats evolve, companies increasingly prioritize cybersecurity. A report from Cybersecurity Ventures predicts that costs from cybercrime could reach $10.5 trillion annually by 2025. This statistic underscores the growing need for cybersecurity professionals.
Techies with experience in cybersecurity can offer their services to businesses looking to protect sensitive data. A survey by Proofpoint found that 55% of organizations fended off phishing attacks, indicating a strong demand for seasoned professionals.
In this consulting niche, technology experts can earn between $100 and $500 per hour, based on their experience and project complexity. Earning certifications, like the Certified Information Systems Security Professional (CISSP), can significantly boost credibility and income potential.
Minimize image
Edit image
Delete image

3. Software Development and Mobile App Creation
As the world becomes more mobile-first, demand for software and app development is expected to rise. Statista reports that the global app economy may generate over $407.31 billion in revenue by 2026, presenting a lucrative chance for techies skilled in coding.
Developers can enter this space through freelancing or by launching their own projects. Tools like React Native and Flutter allow for efficient cross-platform application development, saving both time and resources.
Freelancers can charge between $50 and $200 per hour based on expertise and project scope. For those willing to turn a side hustle into a full business, the income from app sales and in-app purchases can be enormous.
4. Data Analysis and Visualization
Data remains one of the most valuable assets today, with analytics aiding decision-making. The global data analytics market might reach $300 billion by 2026, creating fertile ground for techies skilled in data analysis.
Freelance data analysts can help companies extract valuable insights from their data. Utilizing tools like Tableau, Power BI, and R can help create compelling visualizations, making their services even more attractive.
Data analysts typically charge between $40 and $150 per hour depending on analysis complexity. Mastering data storytelling enables techies to transform raw data into practical insights, positioning themselves as key assets for businesses.
5. E-Learning Course Creation
The rapid growth of online learning has made creating and selling e-learning courses a sought-after side hustle. The global e-learning market is anticipated to reach $375 billion by 2026, driven by rising demand for skill development.
Techies can harness their knowledge to develop courses on platforms like Udemy or Teachable. Topics can range from programming languages to software tools and emerging technologies, such as AI and machine learning. Statista reported that 42% of online course creators are tech professionals, showing the market's strong bias toward technical education.
Successful courses can generate substantial passive income, sometimes yielding thousands of dollars. Since course creation has low overhead, techies can concentrate on producing high-quality content and devising effective marketing strategies.
Minimize image
Edit image
Delete image

Unlocking New Opportunities in Tech
The side hustles mentioned offer exciting paths for tech-savvy individuals aiming to enhance their skills and income in 2025.
As technology keeps evolving, the need for skilled professionals in IT support, cybersecurity, software development, data analysis, and e-learning will continue to grow.
By leveraging their expertise and using the right platforms, techies can build rewarding side hustles that provide financial perks and opportunities for personal and career growth.
Whether solving challenging problems for clients, creating innovative apps, or imparting knowledge, the potential for side hustles in the tech sector is vast. The key is to find a niche that aligns with personal interests, engage in continuous learning, and embrace the entrepreneurial spirit in this dynamic environment.
In a landscape where technology is at the center of everyday life, techies hold a unique position to lead future innovations. Engaging in these side hustles will not only keep them relevant but also equip them for the challenges and opportunities that lie ahead.
#TechSideHustles#RemoteITSupport#Cybersecurity#SoftwareDevelopment#DataAnalysis#MobileAppDevelopment#Elearning#Freelancing#TechEntrepreneur#FreelanceLife#TechProfessionals#FutureOfWork#TechOpportunities#DigitalTransformation#AI#DataVisualization#Coding#TechConsulting#OnlineLearning#CareerGrowth#TechSkills
2 notes
·
View notes
Text
Optimizing Business Operations with Advanced Machine Learning Services
Machine learning has gained popularity in recent years thanks to the adoption of the technology. On the other hand, traditional machine learning necessitates managing data pipelines, robust server maintenance, and the creation of a model for machine learning from scratch, among other technical infrastructure management tasks. Many of these processes are automated by machine learning service which enables businesses to use a platform much more quickly.
What do you understand of Machine learning?
Deep learning and neural networks applied to data are examples of machine learning, a branch of artificial intelligence focused on data-driven learning. It begins with a dataset and gains the ability to extract relevant data from it.
Machine learning technologies facilitate computer vision, speech recognition, face identification, predictive analytics, and more. They also make regression more accurate.
For what purpose is it used?
Many use cases, such as churn avoidance and support ticket categorization make use of MLaaS. The vital thing about MLaaS is it makes it possible to delegate machine learning's laborious tasks. This implies that you won't need to install software, configure servers, maintain infrastructure, and other related tasks. All you have to do is choose the column to be predicted, connect the pertinent training data, and let the software do its magic.
Natural Language Interpretation
By examining social media postings and the tone of consumer reviews, natural language processing aids businesses in better understanding their clientele. the ml services enable them to make more informed choices about selling their goods and services, including providing automated help or highlighting superior substitutes. Machine learning can categorize incoming customer inquiries into distinct groups, enabling businesses to allocate their resources and time.
Predicting
Another use of machine learning is forecasting, which allows businesses to project future occurrences based on existing data. For example, businesses that need to estimate the costs of their goods, services, or clients might utilize MLaaS for cost modelling.
Data Investigation
Investigating variables, examining correlations between variables, and displaying associations are all part of data exploration. Businesses may generate informed suggestions and contextualize vital data using machine learning.
Data Inconsistency
Another crucial component of machine learning is anomaly detection, which finds anomalous occurrences like fraud. This technology is especially helpful for businesses that lack the means or know-how to create their own systems for identifying anomalies.
Examining And Comprehending Datasets
Machine learning provides an alternative to manual dataset searching and comprehension by converting text searches into SQL queries using algorithms trained on millions of samples. Regression analysis use to determine the correlations between variables, such as those affecting sales and customer satisfaction from various product attributes or advertising channels.
Recognition Of Images
One area of machine learning that is very useful for mobile apps, security, and healthcare is image recognition. Businesses utilize recommendation engines to promote music or goods to consumers. While some companies have used picture recognition to create lucrative mobile applications.
Your understanding of AI will drastically shift. They used to believe that AI was only beyond the financial reach of large corporations. However, thanks to services anyone may now use this technology.
2 notes
·
View notes
Text
Facebook, Zoom convicted in Brazil of illegal access to user data

A court in the Brazilian northeastern state of Maranhão ordered Facebook and Zoom to compensate users for illegally harvesting their data. Both companies will have to pay BRL 20 million (just over USD 4 million) in collective damages and BRL 500 in individual compensation to each concerned user.
In March 2020, Vice’s Motherboard website revealed that the Zoom iOS app was sending user data to Facebook unbeknownst to the user — even if the user didn’t have a Facebook account.
Zoom had implemented the ‘login from Facebook’ button on its iOS app, which allowed the social media behemoth to access and extract user data from Zoom’s platform. Zoom apologized for allowing swaths of data that “included information about devices such as the mobile OS type and version, the device time zone, device OS, device model and carrier, screen size, processor cores, and disk space.”
The judge in the case found that Facebook and Zoom had violated users’ privacy rights by accessing data points that allowed the companies to direct ads, track and analyze user behavior, track conversion rates, and personalize user app experience. Having access to this type of data can be precious for advertisers.
Continue reading.
#brazil#brazilian politics#politics#data rights#facebook#zoom#mod nise da silveira#image description in alt
8 notes
·
View notes
Text
How Google Maps, Spotify, Shazam and More Work
"How does Google Maps use satellites, GPS and more to get you from point A to point B? What is the tech that powers Spotify’s recommendation algorithm?
From the unique tech that works in seconds to power tap-to-pay to how Shazam identifies 23,000 songs each minute, WSJ explores the engineering and science of technology that catches our eye.
Chapters:
0:00 Google Maps
9:07 LED wristbands
14:30 Spotify’s algorithm
21:30 Tap-to-Pay
28:18 Noise-canceling headphones
34:33 MSG Sphere
41:30 Shazam "
Source: The Wall Street Journal
#Tech#Algorithm#WSJ
Additional information:
" How Does Google Map Works?
Google Maps is a unique web-based mapping service brought to you by the tech giant, Google. It offers satellite imagery, aerial photography, street maps, 360° panoramic views of streets, real-time traffic conditions, and route planning for traveling by foot, car, bicycle, or public transportation.
A short history of Google maps:
Google Maps was first launched in February 2005, as a desktop web mapping service. It was developed by a team at Google led by Lars and Jens Rasmussen, with the goal of creating a more user-friendly and accurate alternative to existing mapping services. In 2007, Google released the first version of Google Maps for mobile, which was available for the Apple iPhone. This version of the app was a huge success and quickly became the most popular mapping app on the market. As time has passed, Google Maps has consistently developed and enhanced its capabilities, including the addition of new forms of map data like satellite and aerial imagery and integration with other Google platforms like Google Earth and Google Street View.
In 2013, Google released a new version of Google Maps for the web, which included a redesigned interface and new features like enhanced search and integration with Google+ for sharing and reviewing places.
Today, Google Maps is available on desktop computers and as a mobile app for Android and iOS devices. It is used by millions of people around the world to get directions, find places, and explore new areas.
How does google maps work?
Google Maps works by using satellite and aerial imagery to create detailed maps of the world. These maps are then made available to users through a web-based interface or a mobile app.
When you open Google Maps, you can search for a specific location or browse the map to explore an area. You can also use the app to get directions to a specific place or find points of interest, such as businesses, landmarks, and other points of interest. Google Maps uses a combination of GPS data, user input, and real-time traffic data to provide accurate and up-to-date information about locations and directions. The app also integrates with other Google services, such as Google Earth and Google Street View, to provide additional information and features.
Overall, Google Maps is a powerful tool that makes it easy to find and explore locations around the world. It’s available on desktop computers and as a mobile app for Android and iOS devices.
Google uses a variety of algorithms in the backend of Google Maps to provide accurate and up-to-date information about locations and directions. Some of the main algorithms used by Google Maps include:
Image recognition: Google Maps uses image recognition algorithms to extract useful information from the satellite and street view images used to create the map. These algorithms can recognize specific objects and features in the images, such as roads, buildings, and landmarks, and use this information to create a detailed map of the area.
Machine learning: Google Maps uses machine learning algorithms to analyze and interpret data from a variety of sources, including satellite imagery, street view images, and user data. These algorithms can identify patterns and trends in the data, allowing Google Maps to provide more accurate and up-to-date information about locations and directions.
Geospatial data analysis: Google Maps uses geospatial data analysis algorithms to analyze and interpret data about the earth’s surface and features. This includes techniques like geographic information systems (GIS) and geospatial data mining, which are used to extract useful information from large datasets of geospatial data.
Overall, these algorithms are an essential part of the backend of Google Maps, helping the service to provide accurate and up-to-date information to users around the world.
Google Maps uses a variety of algorithms to determine the shortest path between two points:
Here are some of the algorithms that may be used:
Dijkstra’s algorithm: This is a classic algorithm for finding the shortest path between two nodes in a graph. It works by starting at the source node and progressively exploring the graph, adding nodes to the shortest path as it goes.
A* search algorithm: This is another popular algorithm for finding the shortest path between two points. It works by combining the benefits of Dijkstra’s algorithm with a heuristic function that helps guide the search toward the destination node.
It’s worth noting that Google Maps may use a combination of these algorithms, as well as other specialized algorithms, to determine the shortest path between two points. The specific algorithms used may vary depending on the specifics of the route, such as the distance, the number of turns, and the type of terrain. "
Source: geeksforgeeks.org - -> You can read the full article at geeksforgeeks.org
#mktmarketing4you#corporatestrategy#marketing#M4Y#lovemarketing#IPAM#ipammarketingschool#ContingencyPlanning#virtual#volunteering#project#Management#Economy#ConsumptionBehavior#BrandManagement#ProductManagement#Logistics#Lifecycle
#Brand#Neuromarketing#McKinseyMatrix#Viralmarketing#Facebook#Marketingmetrics#icebergmodel#EdgarScheinsCultureModel#GuerrillaMarketing #STARMethod #7SFramework #gapanalysis #AIDAModel #SixLeadershipStyles #MintoPyramidPrinciple #StrategyDiamond #InternalRateofReturn #irr #BrandManagement #dripmodel #HoshinPlanning #XMatrix #backtobasics #BalancedScorecard #Product #ProductManagement #Logistics #Branding #freemium #businessmodel #business #4P #3C #BCG #SWOT #TOWS #EisenhowerMatrix #Study #marketingresearch #marketer #marketing manager #Painpoints #Pestel #ValueChain # VRIO #marketingmix
Thank you for following All about Marketing 4 You
youtube
2 notes
·
View notes
Text
Hotel App Data Scraping Services | Extract Hotel Room Prices
Efficient hotel app data scraping services to extract hotel room prices in the USA, UK, UAE, China, India, Australia, Germany, and Spain. Get the best rates today!
know more:
0 notes
Text
Phonepe fake payment

In the digital age, mobile payment platforms have revolutionized the way we handle financial transactions. PhonePe has gained immense popularity among these platforms for its user-friendly interface and secure payment options. However, with the increase in digital transactions, there has also been a parallel increase in fraudulent activities, and one of the most common scams is the “PhonePe Fake Payment” scheme. In this article, we shed light on the intricacies of this threat by searching for keywords like phonepe fake payment, fake phonepe screenshot, fake phonepe transaction, “fake phonepe customer service number, and “fake phonepe”.
What is Phonepe fake Payment:

PhonePe fake payments refer to fraudulent transactions carried out on the PhonePe platform to deceive users. Scammers use various tactics to trick individuals into paying for goods or services that do not exist. These scams often involve the creation of fake payment receipts and screenshots, leading victims to believe that they have completed a transaction. 1. **Fake PhonePe transactions: How do they happen?** Scammers take advantage of users' trust in digital payment platforms. A common method involves creating a fake payment link that appears legitimate. Unsuspecting users, thinking they are making a genuine transaction, transfer money to the scammer. Additionally, fraudsters may pose as sellers on online marketplaces, and convince buyers to make advance payments through PhonePe. Once the money is transferred, the scammer disappears and the victim is left with no recourse. 2. **Fake phonepe Payment Generator: The Art of Deception** To further their schemes, scammers often create fake PhonePe screenshots and receipts. These fabricated documents mimic authentic documents provided by the platform, making it challenging for users to differentiate between genuine and fake transactions. Victims, upon receiving these fraudulent screenshots, are misled into believing that the payment has been successfully processed. 3. **Fake PhonePe Customer Care Number: A Gateway to Exploitation**

Another strategy adopted by scammers is the use of fake PhonePe customer service numbers. Victims who encounter problems or have doubts about a transaction can seek customer support. Unfortunately, they may stumble upon a fraudulent customer service number that leads them to criminals posing as PhonePe representatives. These fraudsters then extract sensitive information or trick users into making additional payments. PhonePe Detecting and Avoiding Fraudulent Payments:
1. **Verify Payment Link and QR Code** Before making any payment ensure that the payment link or QR code is valid. PhonePe generates secure and unique links for each transaction. Use caution if you receive a link from an unfamiliar source or from outside the official app. 2. **Recheck Transaction Details** Carefully review the transaction details, including payee information and amount. Scammers may slightly alter the details to trick users into making unexpected payments. 3. **Be suspicious of advance payment** Avoid making advance payments, especially to unknown vendors or for goods/services that have not been delivered. Legitimate sellers on online platforms will usually use official payment channels within the app. 4. **Use two-factor authentication** Enable two-factor authentication (2FA) on your PhonePe account for an extra layer of security. This ensures that even if scammers obtain your login credentials, they will not be able to complete unauthorized transactions without a second authentication step. 5. **Contact Official PhonePe Support** If you are concerned about a transaction or facing any issues, use the official customer support channels provided by PhonePe. Avoid relying on random customer service numbers found from online searches to avoid falling victim to scams. Conclusion: While digital payment platforms like PhonePe offer convenience and efficiency, users should remain alert to the growing wave of scams, including the infamous PhonePe fake payment schemes. By understanding the tactics adopted by scammers and implementing preventive measures, users can keep themselves safe from fraudulent transactions and protect their hard-earned money in the digital sphere. Read the full article
#fakephonepe#fakephonepecustomercarenumber#fakephonepescreenshot#fakephonepetransaction#phonepefakepayment
2 notes
·
View notes
Text
Demystifying Python: Exploring 7 Exciting Capabilities of This Coding Marvel
Greetings aspiring coders! Are you ready to unravel the wonders of Python programming? If you're curious about the diverse possibilities that Python offers, you're in for a treat. Let's delve into seven captivating things you can achieve with Python, explained in simple terms from the best Python Training Institute.

1. Craft Dynamic Websites:
Python serves as the backbone for numerous websites you encounter daily. Utilizing robust frameworks such as Django and Flask, you can effortlessly fashion web applications and dynamic websites. Whether your ambition is to launch a personal blog or the next big social platform, Python is your reliable companion. If you want to learn more about Python from the Beginner to Advance level, I will highly recommend the best Python course in Bangalore
2. Automate Mundane Tasks:
Say goodbye to repetitive tasks! Python comes to the rescue with its automation prowess. From organizing files to sending emails and even extracting information from websites, Python's straightforward approach empowers your computer to handle these tasks autonomously.
3. Master Data Analysis:
For those who revel in manipulating numbers and data, Python is a game-changer. Libraries like NumPy, Pandas, and Matplotlib transform data analysis into an enjoyable and accessible endeavor. Visualize data, discern patterns, and unlock the full potential of your datasets.
4. Embark on Game Development:
Surprising as it may be, Python allows you to dip your toes into the realm of game development. Thanks to libraries like Pygame, you can bring your gaming ideas to life. While you may not be creating the next AAA blockbuster, Python provides an excellent starting point for game development enthusiasts.
5. Explore Artificial Intelligence:
Python stands out as a juggernaut in the field of artificial intelligence. Leveraging libraries such as TensorFlow and PyTorch, you can construct machine learning models. Teach your computer to recognize images, comprehend natural language, and even engage in gaming – the possibilities are limitless.
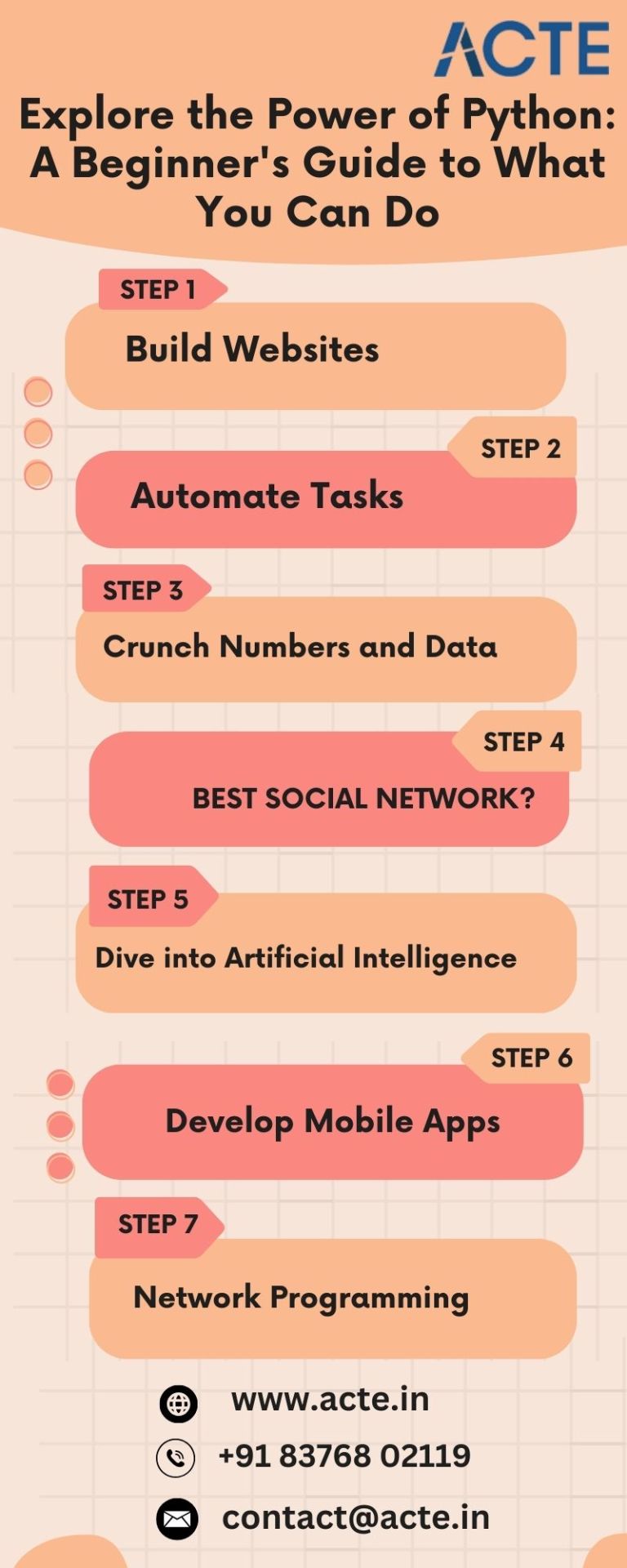
6. Craft Mobile Applications:
Yes, you read that correctly. Python empowers you to develop mobile applications through frameworks like Kivy and BeeWare. Now, you can turn your app concepts into reality without the need to learn an entirely new language for each platform.
7. Mastery in Network Programming:
Python emerges as your ally in the realm of networking. Whether you aspire to create network tools, collaborate with APIs, or automate network configurations, Python simplifies the intricacies of networking.
In essence, Python can be likened to a versatile Swiss Army knife for programmers. It's approachable for beginners, flexible, and applicable across diverse domains. Whether you're drawn to web development, data science, or AI, Python stands as the ideal companion for your coding journey. So, grab your keyboard, start coding, and witness the magic of Python unfold!
2 notes
·
View notes
Text
Angel City FC Launches Performance Optimization Solution From Kitman Labs

Kitman Labs, the global enterprise SaaS platform providing the only single, centralized operating system for performance intelligence in the elite performance industry, today announced a new relationship with LA-based, NWSL club, Angel City Football Club. On the heels of the NWSL’s deployment of the Performance Medicine Solution from Kitman Labs as its league-wide advanced EMR, Angel City FC will expand the use of iP: Intelligence Platform across the club to include Performance Optimization.
Angel City FC will now be able to combine performance data - including game, training, gym, physical testing and more - with player-level medical data for a complete, real-time assessment of each athlete. All data is captured in a single, interactive system - eliminating data and information silos, enabling cross-Departmental communication and supporting informed, data-led decision-making. Both players and practitioners will be able to access and input data through a dedicated Coach and Player App to allow for real-time data capture and on pitch application.
“Communication, collaboration and cohesion are critical for the success of any elite sports organization. By combining both the medical data from our new advanced EMR with our performance data, our staff, coaches and players are now equipped with the analytics and actionable intelligence necessary to work together to unlock optimal performance outcomes across the squad,” said Sarah Smith, Head of Medical and Performance at Angel City FC.
"The purpose of The Intelligence Platform is to unify data, people and processes,” said Stephen Smith, CEO and Founder of Kitman Labs. “Elite sports organizations are inundated with data - typically incomplete, captured in various departments throughout an organization and largely under used and under leveraged. Angel City FC now has the ability to centralize and mobilize their data and extract the full value of that data to support evidence-based decision-making at every level of the organization.”
Kitman Labs has an established track record of working with top leagues, teams and athletes across a variety of sports, including soccer, basketball, rugby, and American football. The company's technology is currently being used by leagues and teams within some of the world's most elite sports organizations, including the National Football League (NFL), Premier League, Major League Soccer (MLS), National Women’s Soccer League (NWSL) and Irish Rugby Football Union (IRFU).
This launch follows other recent business strategy moves Kitman Labs has undertaken including two strategic acquisitions of The Sports Office and Presagia Sports. The combined companies represent the industry’s largest network of elite and youth organizations (1000+), creating the industry’s largest dataset of talent, performance, and medical data for all stages of the athlete lifecycle.
2 notes
·
View notes
Text
Pegasus Spyware – Everything You Need to Know

The name "Pegasus" conjures images of a majestic, winged horse from Greek mythology. In the realm of cybersecurity, however, Pegasus represents something far more sinister: one of the most powerful, invasive, and controversial surveillance tools ever created. This isn't the stuff of spy thrillers; it's a real-world threat that has impacted individuals and raised serious concerns about privacy, human rights, and government accountability globally.
So, what exactly is Pegasus spyware, and why does it command such notoriety?
What is Pegasus Spyware?
At its core, Pegasus is a highly sophisticated, intrusive spyware developed by the NSO Group, an Israeli cyber-arms firm. Its primary function is to covertly infiltrate mobile phones (both iOS and Android devices) to extract vast amounts of data and activate device functions without the user's knowledge or consent. NSO Group maintains that it sells Pegasus exclusively to government intelligence and law enforcement agencies for the sole purpose of investigating terrorism and serious crime.
How Does Pegasus Work? (Its Terrifying Capabilities)
What sets Pegasus apart from typical malware is its unparalleled stealth and potency:
Zero-Click Exploits: This is the most alarming feature. Pegasus can infect a device without any interaction from the target. This means you don't need to click a suspicious link, open an attachment, or even answer a call. It can exploit vulnerabilities in popular apps like iMessage, WhatsApp, or even network protocols, making detection incredibly difficult.
One-Click Exploits (Historical): While less common now, earlier versions of Pegasus often relied on highly targeted phishing attempts delivered via SMS or email, tricking the user into clicking a malicious link that would then install the spyware.
Deep Data Extraction: Once installed, Pegasus gains full control over the device. It can:
Read all your messages (SMS, WhatsApp, Telegram, Signal, etc.), even if they are end-to-end encrypted.
Access your photos, videos, call logs, contacts, emails, and Browse history.
Collect real-time GPS location data.
Steal data from virtually any app installed on the phone.
Covert Device Control: It can secretly activate your phone's microphone and camera, effectively turning your personal device into a 24/7 surveillance tool, recording conversations and surroundings.
Persistence & Evasion: Pegasus is designed to remain undetected. It can hide its traces, operate stealthily in the background, and even re-infect the device after a reboot. It can also self-destruct if it detects a risk of discovery or if its operational period expires.
Who is Pegasus Designed to Target?
NSO Group publicly states that Pegasus is sold only to legitimate governments for combating serious crime and terrorism. However, numerous investigations and leaked documents suggest a far broader and more concerning application:
Journalists: Investigating corruption or human rights abuses.
Human Rights Activists: Advocating for civil liberties and government accountability.
Political Dissidents & Opposition Leaders: Critical voices against ruling regimes.
Lawyers, Academics, and Business Executives: Individuals perceived as threats or holding valuable information.
The "Pegasus Project," a collaborative investigation by Amnesty International and Forbidden Stories in 2021, revealed a leaked list of over 50,000 phone numbers believed to be potential targets of NSO Group clients globally, sparking widespread outrage.
The Controversies and Global Impact
The revelations surrounding Pegasus have ignited significant international debate and legal challenges:
Erosion of Privacy: It highlights the alarming capability of state actors to conduct pervasive surveillance, fundamentally eroding individual privacy and digital rights.
Targeting of Dissent: The alleged use against journalists and activists has raised serious questions about its role in suppressing dissent and undermining democratic processes.
Lack of Accountability: The opaque nature of NSO Group's client list and the lack of robust oversight mechanisms have made it difficult to hold governments accountable for potential misuse.
Legal Battles: Tech giants like Apple and Meta (WhatsApp) have filed lawsuits against NSO Group, accusing them of hacking their platforms.
Blacklisting: The U.S. Commerce Department blacklisted NSO Group in 2021, restricting its ability to acquire certain U.S. technologies, citing evidence that its tools have been used to conduct "transnational repression."
How to Detect Pegasus (An Uphill Battle for the Average User)
Detecting Pegasus is exceedingly difficult for the average user because it is designed to be stealthy and leave minimal traces.
Subtle Indicators: While signs like unusual battery drain, device overheating, or strange network activity could be indicators, they can also be caused by normal app behavior or device issues.
Specialized Tools: Organizations like Amnesty International have developed tools like the Mobile Verification Toolkit (MVT) which can analyze forensic traces on iOS and Android devices. However, using MVT requires technical expertise and often involves creating a full backup of your device for analysis.
Professional Forensics: For definitive detection, a digital forensics expert is typically required to conduct a deep analysis of the device's operating system and network activity.
How to Protect Yourself (Mitigation, Not Absolute Immunity)
While no device is 100% immune, especially if you are a high-value target for a state actor, you can significantly reduce your risk:
Keep Your Devices Updated: This is your strongest defense. Immediately install operating system (iOS, Android) and app updates. These patches often fix the very vulnerabilities (zero-days) that Pegasus and similar spyware exploit.
Be Extremely Wary of Suspicious Links/Messages: Even though zero-click exploits exist, many attacks still rely on a single click. Exercise extreme caution with links received via SMS, email, or messaging apps, even if they appear to come from a known contact. Verify directly via a different channel.
Reboot Your Phone Regularly: Frequent reboots (daily, if possible) can sometimes disrupt certain types of ephemeral zero-click infections that do not establish persistence on the device. Attackers would have to re-infect the device.
Enable Multi-Factor Authentication (MFA): While Pegasus aims to bypass authentication, MFA on your critical accounts (email, banking, social media) adds a layer of security, making it harder for attackers to use stolen credentials. Prioritize app-based MFA or security keys over SMS-based MFA.
Use Strong, Unique Passwords: For all your online accounts.
Avoid Unnecessary Apps: Only install apps from official app stores (Google Play Store, Apple App Store) and delete any apps you don't actively use.
Be Skeptical of Unexpected Communications: If a message or call is unusual or creates undue urgency, pause and verify it through an independent channel.
Consider "Lockdown Mode" (iOS): For iPhone users, Apple's Lockdown Mode (available on iOS 16 and later) offers extreme, optional protection designed for individuals who might be targets of highly sophisticated cyberattacks like Pegasus. It significantly restricts certain functionalities to reduce the attack surface.
Network Security: Ensure your Wi-Fi network is secure (WPA2/WPA3) and consider using a reputable VPN service.
Pegasus spyware represents the cutting edge of surveillance technology, posing unique and formidable challenges to individual privacy and digital security. Its very existence underscores the critical need for stronger international regulations on cyber-arms trade, greater transparency from governments, and a robust commitment to digital hygiene from every individual. While the fight against such advanced threats is ongoing, informed vigilance remains our most potent weapon.
The name "Pegasus" conjures images of a majestic, winged horse from Greek mythology. In the realm of cybersecurity, however, Pegasus represents something far more sinister: one of the most powerful, invasive, and controversial surveillance tools ever created. This isn't the stuff of spy thrillers; it's a real-world threat that has impacted individuals and raised serious concerns about privacy, human rights, and government accountability globally, including right here in India.
So, what exactly is Pegasus spyware, and why does it command such notoriety?
What is Pegasus Spyware?
At its core, Pegasus is a highly sophisticated, intrusive spyware developed by the NSO Group, an Israeli cyber-arms firm. Its primary function is to covertly infiltrate mobile phones (both iOS and Android devices) to extract vast amounts of data and activate device functions without the user's knowledge or consent. NSO Group maintains that it sells Pegasus exclusively to government intelligence and law enforcement agencies for the sole purpose of investigating terrorism and serious crime.
How Does Pegasus Work? (Its Terrifying Capabilities)
What sets Pegasus apart from typical malware is its unparalleled stealth and potency:
Zero-Click Exploits: This is the most alarming feature. Pegasus can infect a device without any interaction from the target. This means you don't need to click a suspicious link, open an attachment, or even answer a call. It can exploit vulnerabilities in popular apps like iMessage, WhatsApp, or even network protocols, making detection incredibly difficult.
One-Click Exploits (Historical): While less common now, earlier versions of Pegasus often relied on highly targeted phishing attempts delivered via SMS or email, tricking the user into clicking a malicious link that would then install the spyware.
Deep Data Extraction: Once installed, Pegasus gains full control over the device. It can:
Read all your messages (SMS, WhatsApp, Telegram, Signal, etc.), even if they are end-to-end encrypted.
Access your photos, videos, call logs, contacts, emails, and Browse history.
Collect real-time GPS location data.
Steal data from virtually any app installed on the phone.
Covert Device Control: It can secretly activate your phone's microphone and camera, effectively turning your personal device into a 24/7 surveillance tool, recording conversations and surroundings.
Persistence & Evasion: Pegasus is designed to remain undetected. It can hide its traces, operate stealthily in the background, and even re-infect the device after a reboot. It can also self-destruct if it detects a risk of discovery or if its operational period expires.
Who is Pegasus Designed to Target?
NSO Group publicly states that Pegasus is sold only to legitimate governments for combating serious crime and terrorism. However, numerous investigations and leaked documents suggest a far broader and more concerning application:
Journalists: Investigating corruption or human rights abuses.
Human Rights Activists: Advocating for civil liberties and government accountability.
Political Dissidents & Opposition Leaders: Critical voices against ruling regimes.
Lawyers, Academics, and Business Executives: Individuals perceived as threats or holding valuable information.
The "Pegasus Project," a collaborative investigation by Amnesty International and Forbidden Stories in 2021, revealed a leaked list of over 50,000 phone numbers believed to be potential targets of NSO Group clients globally, sparking widespread outrage. Countries like India were also implicated in allegations of using Pegasus against journalists, activists, and politicians.
The Controversies and Global Impact
The revelations surrounding Pegasus have ignited significant international debate and legal challenges:
Erosion of Privacy: It highlights the alarming capability of state actors to conduct pervasive surveillance, fundamentally eroding individual privacy and digital rights.
Targeting of Dissent: The alleged use against journalists and activists has raised serious questions about its role in suppressing dissent and undermining democratic processes.
Lack of Accountability: The opaque nature of NSO Group's client list and the lack of robust oversight mechanisms have made it difficult to hold governments accountable for potential misuse.
Legal Battles: Tech giants like Apple and Meta (WhatsApp) have filed lawsuits against NSO Group, accusing them of hacking their platforms.
Blacklisting: The U.S. Commerce Department blacklisted NSO Group in 2021, restricting its ability to acquire certain U.S. technologies, citing evidence that its tools have been used to conduct "transnational repression."
How to Detect Pegasus (An Uphill Battle for the Average User)
Detecting Pegasus is exceedingly difficult for the average user because it is designed to be stealthy and leave minimal traces.
Subtle Indicators: While signs like unusual battery drain, device overheating, or strange network activity could be indicators, they can also be caused by normal app behavior or device issues.
Specialized Tools: Organizations like Amnesty International have developed tools like the Mobile Verification Toolkit (MVT) which can analyze forensic traces on iOS and Android devices. However, using MVT requires technical expertise and often involves creating a full backup of your device for analysis.
Professional Forensics: For definitive detection, a digital forensics expert is typically required to conduct a deep analysis of the device's operating system and network activity.
How to Protect Yourself (Mitigation, Not Absolute Immunity)
While no device is 100% immune, especially if you are a high-value target for a state actor, you can significantly reduce your risk:
Keep Your Devices Updated: This is your strongest defense. Immediately install operating system (iOS, Android) and app updates. These patches often fix the very vulnerabilities (zero-days) that Pegasus and similar spyware exploit.
Be Extremely Wary of Suspicious Links/Messages: Even though zero-click exploits exist, many attacks still rely on a single click. Exercise extreme caution with links received via SMS, email, or messaging apps, even if they appear to come from a known contact. Verify directly via a different channel.
Reboot Your Phone Regularly: Frequent reboots (daily, if possible) can sometimes disrupt certain types of ephemeral zero-click infections that do not establish persistence on the device. Attackers would have to re-infect the device.
Enable Multi-Factor Authentication (MFA): While Pegasus aims to bypass authentication, MFA on your critical accounts (email, banking, social media) adds a layer of security, making it harder for attackers to use stolen credentials. Prioritize app-based MFA or security keys over SMS-based MFA.
Use Strong, Unique Passwords: For all your online accounts.
Avoid Unnecessary Apps: Only install apps from official app stores (Google Play Store, Apple App Store) and delete any apps you don't actively use.
Be Skeptical of Unexpected Communications: If a message or call is unusual or creates undue urgency, pause and verify it through an independent channel.
Consider "Lockdown Mode" (iOS): For iPhone users, Apple's Lockdown Mode (available on iOS 16 and later) offers extreme, optional protection designed for individuals who might be targets of highly sophisticated cyberattacks like Pegasus. It significantly restricts certain functionalities to reduce the attack surface.
Network Security: Ensure your Wi-Fi network is secure (WPA2/WPA3) and consider using a reputable VPN service.
Pegasus spyware represents the cutting edge of surveillance technology, posing unique and formidable challenges to individual privacy and digital security. Its very existence underscores the critical need for stronger international regulations on cyber-arms trade, greater transparency from governments, and a robust commitment to digital hygiene from every individual. While the fight against such advanced threats is ongoing, informed vigilance remains our most potent weapon.
0 notes
Text
How Real-Time Expense Management Software Reduces Fake Claims and Misuse
Transparency in finances and control over them are essential. When it comes to running costs, every rupee matters. But what happens when expense claims are undesirable, receipts disappear, and payment fake claims avoids detection? That's where Employee Expense Management Software makes the change.
Manual expense processing is vulnerable to a wide range of errors, from small inaccuracies to major financial errors. However, companies are already reversing the trend against expenditure fake claims and regaining control over budgets thanks to automation and real-time tracking.
A real-time expense management system can save time and money while protecting your company from fake claims and maintaining financial integrity.
The Problem with Traditional Expense Handling
Before automation, companies went through spreadsheets, piles of paper receipts, and just faith in employees. Employees prepared expense reports on their own, then managers approved them reading every single row. The finance staff was in charge of checking and processing all that material with no reference.
Such was:
Time-consuming
Error-prone
Vulnerable to manipulation
Some common misuse cases were:
Submitting the same receipt multiple times
Exaggerating miles traveled or travel-related claims
Claiming personal expenses as business-related
Tampering receipts
Such actions often destroy the confidence between management and employees along with creating expenses. It is well recognized that fake claims situations cannot be followed in real-time; instead, they take weeks to uncover a scam or, in the worst cases, never be noticed.
Real-Time Expense Management Software to the Rescue
Real-time Expense Management Software emerged as a digital platform that is automated, streamlined, and tracks employee expenses in real time. The best Expense Management Software digitizes receipts and uses smart features that can provide complete visibility and control.
youtube
Here are the benefits for which businesses will realize their advantage in monitoring expenses despite fake claims and misuse minimization:
1. Instant Data Capture Leaves No Room for Tampering
Modern Expense Management Systems come with mobile apps that allow employees to upload receipts instantly—often just by clicking a photo. The software then auto-extracts the needed information (amount, vendor, date) and requires no manual input.
This makes it almost impossible for:
Receipts to be edited
Old claims to be reused
False details to be added
Also, it timestamps every submission, giving Employee live tracking and verification of the claim submission.
For example, if an employee today claims an unnecessary expense, the system can flag it for an inconsistent date or a missing document.
2. Automated Approval Workflows Add Layers of Control
With the many levels of approval that automated expense-management software allows, it reduces incidents where oversight might allow the approval of fraudulent claims. You might choose:
Who reviews what kind of expense
Approval limits by roles
Any automatic flags for suspicious or high-value entries
This way, managers and finance will receive notifications on approval actions instantly, ensuring faster yet more secure approvals.
3. Customized Policies Prevent Rule Bending
Every company has its own rules governing travel, meals, lodging, or client entertainment. A real-time expense management system lets the payment policy of the company flow straight into the software.
If employees:
Exceed spending limits
Select unapproved vendors
Submit non-compliant claims
They'll get real-time alerts. Thus, the policy discourages misuse on the front end instead of engaging it on the back with money already spent.
4. Mileage and Distance Automation Ends Guesswork
Travel claims are one of the most manipulated expenses in the expense report. With GPS tracking, Expense Management Software automatically saves mileage and travel routes.
No more guessing distances and inflating kilometers. Employees start and stop trips in the app, which then records accurate data for reimbursement.
5. Transparent Audit Trails for Every Transaction
A real-time system enables the creation of one of the most preferred audit trails for any transaction. Every action occurs from document submission to approval and subsequent processing. It is timestamped with the user details.
This enables:
Clear accountability
Easy reference during audits
Reduced chances of duplicate or fake entries
Finance teams can cross-examine any transactions, understanding who did what and when thus eliminating the paper shuffle.
6. Real-Time Reports and Insights
As they say, you cannot fix what you do not see. Thus, good Expense Management Software must feature custom reporting tools that will shed light on trends, red flags, and unusual behaviors.
For instance:
A team member is regularly spending more than others in the same role.
Some vendors are a bit too overused.
Last-minute or backdated claims are too frequent.
These insights can help an organization plug a budget leak, renegotiate contracts with vendors, or investigate the possibility of fake claims.
7. Mobile Access for Quick Submissions
With mobile-first Expense Management Systems, employees can submit expenses on the go, and those chances of lost receipts or forgotten claims go away. Real-time access keeps them posted on the status of their claims and ensures the absence of confusion and mistrust.
And as everything gets logged instantly, there is no need for the finance team to chase after employees for documents or explanations. It saves time for everybody.
8. Promotes a Culture of Honesty and Accountability
When employees understand that every submission goes through a track-through check-and-logging procedure, they are less likely to play the system. Hence, a transparent process promotes:
Increased Accountability
Greater Compliance
Higher Morale Across Teams
Instead of micromanaging every reimbursement, businesses can focus on creating clear guidelines and let field sales automation bear the burden.
youtube
How to Choose the Right Expense Management Software
Not all tools are the same. Thus, in selecting the right Expense Management Software for your organization, view the following features:
Real-time expense tracking
Receipt scanning and data extraction
Customizable approval flows
Alerts for policy enforcement
Integration into payroll or accounting tools
Mileage-tracking through GPS
Cloud syncing and mobile access
It should be the adaptation of the right platform for your workflow, not the reverse.
Conclusion: Invest in Visibility, Not Just Software
In an increasingly financially disciplined era, real-time Expense Management Software moves from being a nice-to-have to a must-have. It facilitates cost control and fake claims prevention, along with transparency without placing too much pressure on employees.
Whether you're a startup or a business, a solid Expense Management System gives protection to your finances and eases operations in making Tag Direct your online partner in expense management.
TrackOlap empowers your business with control over business spending through Software in Expense Management. Automate reimbursements, protect against fake claims and enjoy real-time visibility on every transaction. With intelligent functionalities such as distance tracking, receipt scanning, and custom reports, TrackOlap helps streamline expense workflows and raise financial accuracy. Simplifying and improving your expense processes begins today TrackOlap for business management more effectively!
#expense management software#expense management#expense management system#expense management process#expense management app#expense management tool#Youtube
0 notes