#ftp program
Explore tagged Tumblr posts
Text
THE AESTHETICS OF ABANDONWARE: WHY DEAD SOFTWARE FEELS HOLY
By R A Z, Queen of Glitches, Rat Prophet of the Post-Crash Pixel-Chapel
INTRO: Oi, you ever boot up a DOSBox emulator and feel your soul whisper "Amen"? No? Then saddle up, you absolute fetus, 'cause we’re going full pilgrimage through the haunted cathedrals of dead code, cursed shareware, and disc rot salvation. This is for the ones who dream in .BMPs, weep in MIDI, and hit “Yes to All” when copying cracked ZIPs from forgotten FTPs at 3AM. Abandonware ain’t just nostalgia—it’s digital necromancy. And some of us are bloody good at it.
DEAD SOFTWARE = HOLY SHRINE
Let’s be clear: abandonware is software that’s been, well, abandoned. The devs moved on. The publisher collapsed in a puff of VC smoke. The website's now a spammy shell selling beard oil or crack cocaine. The software? Unupdated. Unsupported. Gloriously obsolete.
So why does launching Hover! or Starship Titanic in 2025 feel like entering a chapel with weird lighting and a dial-up modem choir?
Because it’s sacred, mate.

We’re not talking about the games themselves being perfect. A lot of them were janky as hell. We’re talking vibe. These programs exist outside capitalism now. They’re post-market. Post-hype. They don’t want your money, your updates, your logins. They just want your attention—pure and simple. You’re not a user anymore. You’re a curator. A digital monk brushing dust off EXEs and praying to the Gods of IRQ Conflicts and SoundBlaster settings.
WHY IT HITS DIFFERENT
Dead software doesn’t update. It doesn’t push patches or ads. It won’t ask you to connect your Google account to play Math Blaster. It’s a sealed time capsule. Booting it up is like receiving an artifact from a parallel dimension where the internet still had webrings and every kid thought Quake mods would lead to a dream job at ID Software.
But it also represents a lost sincerity. These weren’t games made to hook you for eternity with algorithms. These were games made by six dudes in a shed with a caffeine problem and one working CD burner. And their README files were poetry. Half of them end with “Contact us on AOL or send a floppy to our PO Box.” What do you mean you don’t know what a PO Box is?
FOR THE ZOOMIES: YOU JUST MISSED THE GOLDEN ROT
Listen up, juniors. If you were born after 2005, you missed the age when the internet was held together with chewing gum, JPEG artifacts, and unspoken respect.
Back then, finding a rare game was an adventure. Not an algorithm. You didn’t scroll TikTok and get spoon-fed vibes. You climbed through broken Geocities links and begged on IRC channels. You learned to read. You learned to search. You learned that “No-CD crack” doesn’t mean what your mum thinks it means.
So here’s your initiation: go download something weird from a forgotten archive. No guides. No Discord server. Just the raw, terrifying joy of not knowing if you’ve just installed Robot Workshop Deluxe or a Russian trojan. Welcome to the cult.
THE TWO-YEAR RULE
Online communities? They’re mayflies with usernames. Peak lifespan? Two years.
Here’s the cycle:
A niche game/tool/art style gets revived.
People form a forum/Reddit/Discord.
A zine or remix scene emerges.
Drama. Mods quit. Someone forks the project.
Everyone vanishes.
This cycle has always existed. The only difference now is that it’s faster. But dead software bypasses this. It’s post-community. You don’t have to join a scene. You are the scene. Every time you open it up, you’re plugging into a ghost socket. You’re chatting with echoes. It’s beautiful.
CONCLUSION: THIS IS A RELIGION NOW. PRACTICE IT.
Abandonware isn’t about gaming. It’s about reclaiming reverence. About saying “This mattered” even if no one else remembers it did. It’s about surfing the ruins, not for loot, but for meaning. There’s holiness in opening a program that hasn’t been touched in decades and seeing it still works. Still waits for you. Still loads that same intro MIDI with the confidence of a god.
So light a candle. Install a CRT filter. Screenshot that low-res menu and print it on a t-shirt. You’re not just playing with the past. You’re preserving the bones of the digital age.
See you in the BIOS, kids.
—
RAZ out.
#abandonware#digitalnostalgia#deadsoftware#softwaregraveyard#forgottenweb#vaportech#cyberrelics#dataisreligion#glitchaesthetic#dosgames#earlyinternet#webringculture#digitaldecay#postironictech#crtcore#bitrot#retrocomputing#ghostsofthesoftmachine#hauntology#pixelmonastery#blessthisbootsector#prayingtomidifiles#worshiptheexe#floppydiskcult#exenetkidsunite#ripircchannels#poeticreadme#geocitiesforever#netlordforlife#internetarchaeology
50 notes
·
View notes
Text
Today, during a work meeting, I shared my screen. One coworker wasn't familiar with how to transfer a file from the mainframe computer to a personal computer or virtual desktop. We have a file transfer program for that, but she had never used it. During a project call (with only five people), she asked me to show her.
My first step was copying the file from one dataset to another, which had a different name. My FTP will not recognize the format of the original file name, so I create one that includes my user ID in the name.
Someone else on the call watched me do this and told me if I was copying every line I could skip two tiny steps. Then he went a step further, explaining a command I'd never heard of. It allocates a new file and copies everything simultaneously.
Mind blown.
I was going from point A to point B, via points Y and Z. My extra steps only added a few moments to the process, but now, after learning this command, I feel like I'd been wasting much time over the past 20 years.
#DSU#I love sharing and learning tips and tricks at work#After decades in this business I keep learning little thing#It will always make my eyes twitch though when I watch someone use menu clicks instead of key commands to copy and paste#But I know never to try to explain Cntl-C and Cntl-V to some people because they will never change
32 notes
·
View notes
Text
You know you're deeply buried in a fandom when things like this make you cry with laughter I was reading my library school book, when I came across this quote about information retrieval sources, I laughed so hard, Archie? An archivist? Archive? Archipelago? 😂😂😂 Oh, TMA and TMP broke my sense of humor
Ps: The text is in Portuguese but I left a quick translation below
Ps2: Good time for a library science student to listen to the magnus archives, I will never be able to take my university books seriously
[ SEARCH ENGINES
The first search engine to emerge was Archie, which was intended only to search for programs on FTP servers, and not search for pages (...)]

Ok, news, I was finding the reference to the word archie in my book funny but I went looking for what exactly this system was and look at this.

This not exactly what FR3-d1 is? Suspicious
24 notes
·
View notes
Text

Despite temps in the 40's, the nets are up and so we feel compelled to play tennis; 2 hours on Sundays and Wednesdays. We had a rather large group of 7 yesterday and generally 3-4 including Beth and me on Wednesdays.
My return to running is going well - Saturday's 11 mile run was the furthest I've run in 2 years and it felt good. My running pace and VO2 max are still a long way from where they were before I shifted exclusively to bike training in early 2022, but I'm happy with my progress.
I took a bike FTP test last week and was a little disappointed that my FTP had plateaued until my bike coach directed my attention to a Training Peaks performance management chart which highlighted the load created by simultaneously pursuing bike and running training programs. You can see my fatigue (the pink line) begin to rise dramatically in February when I added half marathon run training to cross-Pyrenees bike training. Simultaneously my Form (the yellow line indicating, 'race readiness') began to decline. Fortunately, my overall fitness, the area under the blue line, began to accelerate more quickly too.
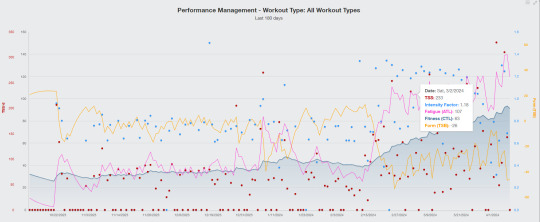
These are all just estimates and calculations made by Training Peaks but it is helpful to see objective confirmation of the stress of training.
33 notes
·
View notes
Note
What’s autohotkey
FOSS scripting/macro program for Windows. you can use it to write custom keyboard shortcuts that automate common tasks, like adding boilerplate text or hyperlinks to your emails or uploading a file to an ftp server or really any repetitive set of tasks that takes more than one mouse click to do ordinarily but is (programmatically) always the same set of steps.
its relatively simple to program and straightforward/ self-documenting, i've basically never written anything from scratch because you can usually find code online that is pretty close to what you need that you can modify
3 notes
·
View notes
Text

[ . . . ]
// ^^^ is currently thinking about how to get admin rights

[ wait i still have that stuff. ]
Running program: cmd.exe
C:\Users\User\Desktop>probe
Port 22 - SSH (Closed)
Port 21 - FTP (Closed)
Port 1433 - SSL (Closed)
C:\Users\User\Desktop>SSHCrack 22
TRACE
99.00
C:\Users\User\Desktop>FTPBounce 21
TRACE
95.00
SSHCrack exited with exit code 0.
TRACE
87.00
C:\Users\User\Desktop>SSLTrojan 21 -s 22
FTPBounce exited with exit code 0.
SSLTrojan exited with exit code 0.
Port 22 - SSH (Open)
Port 21 - FTP (Open)
Port 1433 - SSL (Open)
TRACE
77.00
C:\Users\User\Desktop>PortHack
Initializing PortHack
Administrator Access Granted
Porthack exited with exit code 0.
TRACE
67.00
C:\Users\User\Desktop>ps
C:\Users\User\Desktop>restart /pid 3148 --sudo
[sudo] Password: *******
C:\Users\User\Desktop>kill /pid 1127
[ Restarting... ]

[ . . . aaaaargh. still can't do much. ]
#os game rp#ask testbuild#// gotta love hacking your own computer and getting traced#// for no reason...
7 notes
·
View notes
Text
Round 1C

Men In Black: Fifteen hundred years ago, everybody knew the Earth was the center of the universe. Five hundred years ago, everybody knew the Earth was flat, and fifteen minutes ago, you knew that humans were alone on this planet. Imagine what you'll know tomorrow. Men in Black is a sci-fi comedy, starring Will Smith and Tommy Lee Jones, which would go on to spawn a franchise after the success of the 1997 film. It centers around a secret government agency known as the Men in Black, tasked with monitoring and regulating extraterrestrial activity on Earth; these agents, notably our protagonists Agent J and Agent K, protect humanity from aliens living among us and ensure the world remains oblivious to their existence. The franchise was praised by critics and audiences alike for its unique screenplay, action sequences, and the humor and chemistry of the lead actors. Over the years, Men in Black has expanded to include multiple sequels, an animated series and spin-offs, all contributing to its enduring popularity as a cheekier take on the sci-fi genre.
The MP3 is Leaked: It took a decade to develop the MPEG Audio Layer III– or the MP3– while maintaining the fidelity to make it commercially viable. It took a college student a single night to bring the music industry to its knees forever after. Karlheinz Brandenburg, who worked at the Fraunhofer Institute for Integrated Circuits in Germany (pictured) would emerge as the “Father of the MP3” in the 90s. The development of the file codex and software, alongside the developments of competitors and the early marketing of the MP3 is well worth independent research, but ultimately background noise to this entry. Mid-1997, in an international clusterfuck facilitated by the popular internet Warez community, an Australian student used a stolen credit card from Taiwan to purchase professional-grade encoding software from Germany. He successfully cracked the software, proceeded to upload it onto a server in Sweden, and initiated distribution to multiple U.S. universities through an FTP site; within it, there was a read-me file that labeled the program as freeware, with a "special thanks" given to Fraunhofer. Brandenberg would do everything he possibly could to warn his colleagues and label executives, but the toothpaste could never be put back into the tube. You know the rest: Napster, Kazaa, Limewire and numerous others would come to follow. The RIAA would engage in endless lawsuits, as would several big names in music, but the industry would never recover from the change in public perception of/capacity for piracy the stolen MP3 ushered in.
12 notes
·
View notes
Note
INCOMING CONNECTION -- SEQUENCER ATTACK


Port 21 - FTP (Opened)
Port 22 - SSH (Opened)
Port 6881 - BitTorrent (Opened)
Admin access granted.
Scanning . . . Device Found - niko-raspberrypi
Logs erased.
*** STOP: 0X00000050 (0x8872A990, 0x00000001, 0x804F35D7, 0x00000000)
A problem has been detected and Windows has been shut down to prevent damage to your computer.
(Niko is asleep in their bed so they don't have to try and stop this nightmare of a program--)
[ REDIRECTING. ]
4 notes
·
View notes
Text
Coding, programming, website domains, website hosting, DNS, HTP, FTP, listen, as someone who makes music for a living who just does it "based on vibes and feels", none of that world makes sense to me, when I see a line of code my first instinct is "okay but can I like maybe draw what it'd look like in my head instead of doing this scary math stuff please", like yes, I can get it done, with great effort, but it just feels like the creative part of my brain doesn't "get" the coding side of a lot of things (im trying to transfer my website and donain to a different hosting and domain provider and it's very difficult and my friends are trying to help me but jesus christ I sure feel a little dumb when it comes to this)
4 notes
·
View notes
Text
Cookie: “Ah, yes! ATM stands for Automated Teller Machine, RSS for Really Simple Syndication, and PDF for Portable Document Format. So all those phrases are redundant. FTP stands for File Transfer Protocol, so FTP program wouldn’t be stupid to say.”
Cookie: “So, um, Gretchen… c-c-could you recommend-”
Gretchen: “All done here! Talk to you later, Cookie.”
(gretchen leaves and closes the door)
(…)
Cookie: “You’re so pretty!”
(video link)
3 notes
·
View notes
Text
How To Set Up Socks5 Proxy List in Wingate.me?
What Is Private Proxy Wingate.me?

Wingate.me is a private proxy service that delivers secure managed internet access across your entire network and all your online activities. It caters to a range of requirements, from small networks to large enterprises. Known for its high-quality private proxies, particularly in the Russian region, Wingate.me has carved a niche for itself as a powerful online platform.
Supporting for Internet hosting ensures that the WinGate Proxy Server is compatible with all browsers, SSL, FTP, streaming audio and video, DirectPlay Internet gaming, etc. Socks5 proxy list wingate.me provides clients with a safe, anonymous, and unrestricted internet browsing experience. They shield users from data collection and facilitate access to otherwise blocked websites.
Types of Private Proxy Wingate.me
It offers a variety of private proxy types, including:
1. SOCKS4 proxy
A versatile proxy for web browsing, file sharing and online gaming, known for its speed and efficiency.
2. SOCKS5 proxy
These proxies support TCP and UDP traffic, making them ideal for online streaming, torrenting, and high-performance tasks.
3. IPv4 proxy
Stable and reliable proxy based on IPv4 protocol, compatible with most websites and services on the Internet.
4. Mix of SOCKS5 and IPv4 proxies
This option combines the advantages of both proxy types, providing flexibility for different tasks.
An Overview Of Wingate.me’s Socks5 Proxy List
Socks5 proxy list wingate.me provides an extensive list of Socks5 proxy servers, ensuring users have access to a broad range of functional and efficient proxies. The list, updated regularly, includes information such as the IP address, port number, country, and the last time the proxy was checked for functionality. This transparency empowers users to make informed decisions when selecting a proxy server.
Get 1GB Proxy Free Trial of Residential Proxies Now!
How To Set Up Wingate.me’s Socks5 Proxy?
Setting up a Socks5 proxy from Wingate.me is straightforward. After selecting a proxy from the list, users can configure their web browsers or applications to use the proxy by entering the provided IP address and port number in the relevant settings. Specific setup instructions may vary depending on the application or browser used. Here are detailed instructions:
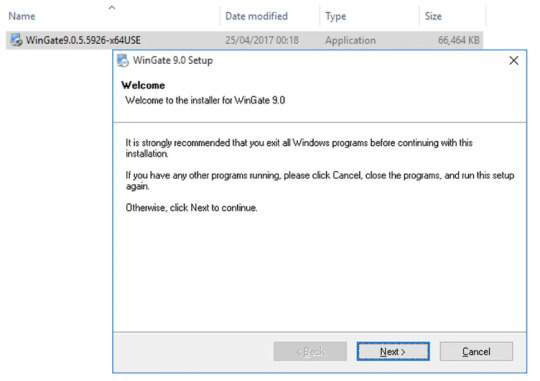
Step 1 Installing Wingate Proxy Server
After downloading the latest package of WinGate Proxy Server, double-click its ‘.exe’ package to start the installation setup wizard of WinGate proxy server. After that, you will be greeted by its welcome page to get started with the installation on your devices. Click on the “Next” button to continue.
Get 1GB Proxy Free Trial of Residential Proxies Now!
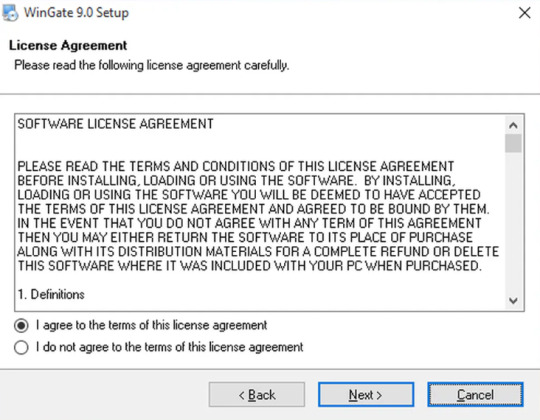
Step 2 License Agreement
You need to read and accept the license agreement before the installation and use of Wingate by choosing the right option as shown.
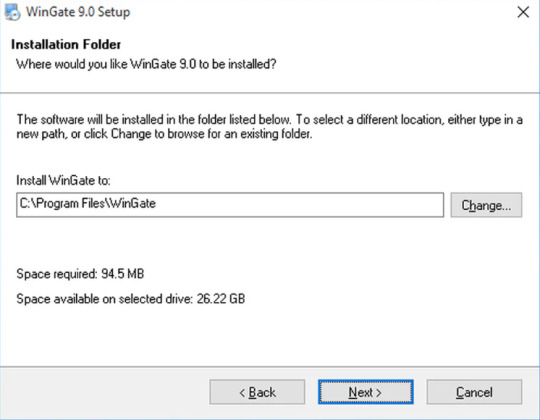
Step 3 Installation Folder
Choose the location on your system, where you like to place the WinGate installation setup.
Step 4 Select Packages
You will be asked to choose the program features that you wish to install on your system.
Step 5 Admin Email Address
You should provide your Administrative User Name and Email ID along with the Senders’ address for the administrative alerts.
Step 6 Ready to Install
If you click on the ‘Next’ button, your installation process will start processing files and other selecting configurations. After finishing the installation process of WinGate, click on the ‘Finish’ to exit the installer. Remember to click on the ‘Yes’ to go for system reboot and wait till it is back.

Step 7 Setting Up
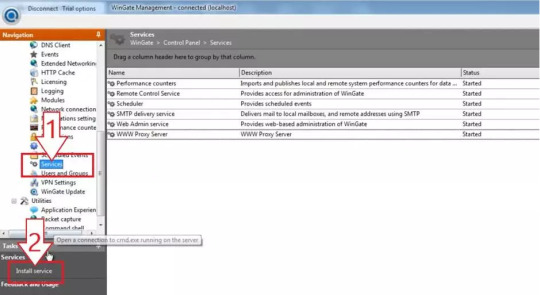
After you finish the installation, you can set up Wingate.me’s Socks5 Proxy List now.
1. You will see a welcome page and a navigation menu on the left with available configuration options. Please focus on setting up the proxy. To do this, select “Services” from the navigation menu, then right-click on the empty space on the right and select Install Service.
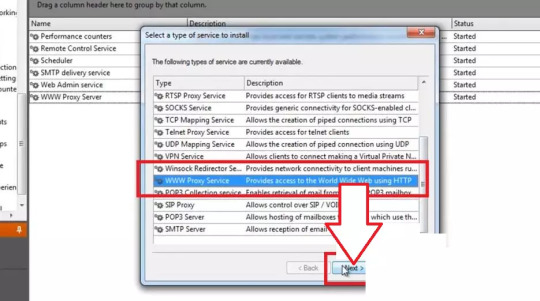
2. The service properties window will appear. Navigate to the Bindings tab. Remove all active bindings and click Add. Select “Any External Adapter” and click “OK” to save your configuration.
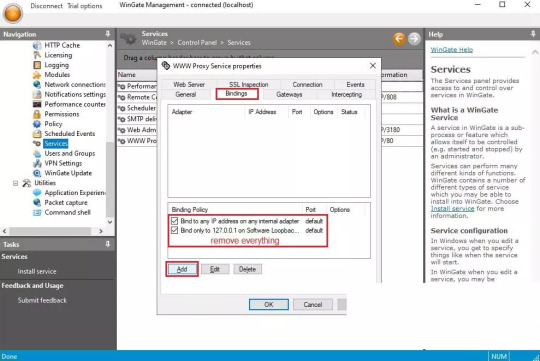
3. Now, go to the Connection tab. Check the box next to ���Connect through upstream proxy.” Go to the IP Settings dashboard to configure your proxy. Note down the HTTP proxy host, proxy port, proxy username and proxy password of the private proxy you obtained from the website and import this data into WinGate.

By following these steps, you will successfully configure a private proxy using Wingate’s user-friendly interface. This ensures safe, anonymous and efficient internet browsing while protecting your online activity and data.
Get 1GB Proxy Free Trial of Residential Proxies Now!
Conclusion
Wingate.me’s Socks5 proxy list is a powerful tool for anyone seeking to navigate the digital world with anonymity, versatility, and global access. However, like any tool, it should be used responsibly and ethically. As we continue to sail through the data-driven era, tools like Wingate.me’s Socks5 proxy list will undoubtedly play a crucial role in shaping our digital experiences.
For more please read the original article which is from:
#socks5 proxy list wingate.me
#private proxy wingate.me
#buy wingate me private proxy
#proxy for email wingate.me
3 notes
·
View notes
Text
Infinite's handling of "Spartan training" is too soft. I know its a T rated game, and a FTP at that, but come on.
They should make it clear this is a SPARTAN training program, not some fun little game they play on the weekends. If your team looses, the post-game screen (where you can see who you played with and your fireteam) should show the worst player on their knees, hands behind their back, armor removed and face battered and bruised, because their teammates gave them the Full Metal Jacket "Private Pyle" treatment by beating the SHIT out of them with their armored gauntlets.
Really drive it home that you not only fucked up for yourself, you fucked up for your team. And the weakest link in a Spartan chain needs to be remade stronger. By force.
Either the player gets tired of seeing their personalized Spartan being a punching bag for other people...or they just stop playing and someone else comes in to replace them.
6 notes
·
View notes
Text

Functional Threshold Power
The FTP test is a measure of cycling fitness and my coach assigned a ramp FTP as a baseline for my training program. Your FTP is how many watts you can produce on average in an hour of maximum effort. An hour of max effort involves a lot of suffering so there are shorter versions with simple math to convert to the FTP.
I did the ramp version which, after a warm up period, increases the resistance by 10 watts every minute. You hang on as long as can and multiply the ending watts (when you acquiesce) by 75% to get your FTP.
I had to bail out at 275 watts - my heart rate reached 175, which is surprising because I thought my max HR was 171. The standard formula is 220 minus your age. I’m 56 so the predicted max is 164. There’s nothing you can do to increase your max HR - it just is what it is.
205 is an OK, but certainly not great FTP and I’m confident it will get better with training.
32 notes
·
View notes
Text
Maybe you don’t remember those days when internet security was being in use mostly via installed programs on your pc and the only thing you needed to do for your win95/98/xp pc to run smoother was to run an antivirus program every week or so and guess what, just by browsing and downloading lots of illegal stuff via p2p clients you got shitloads of viruses trojans malware adware and others and you have no idea how lucky you are that nowadays almost every os has some sort of antivirus firewall or defender or something and you don’t need to worry about it
(Who remembers modem-era dial-up internet connections with viruses that called some hotlines with every second of it costing you fuckton of money?)
Back in the day you could have been downloading someone’s holidays pictures via p2p if you knew what to search for or how to browse their folders (assuming correctly most of the time they didn’t know shit) and you could have been finding all kinds of weird shit on people’s hard drives they shared with anyone able to install a Kazaa or imesh and my my how the times changed, almost no one uses html anymore and you can’t just source index.html and check these sweet, unprotected folders they had on their ftp
Now all I get is some sort of idiotic forwarding spam websites when I try to watch my comics online and all I need to do is to turn on my built-in vpn and maybe times have changed and so did I and now it is me who don’t know shit
You know what? I don't want to change my VPN every six months cause it was caught selling information. I don't want to go deep into the settings of every website I so much as look at. I don't want my internet browsing to be a constant leap through hoops so that companies can't do things which should be illegal anyway. I want privacy to be the default and for it to be difficult to take it away, not the other way around. Is that too much to ask?
78K notes
·
View notes
Video
youtube
Robot AT8XM Review 🔥{Wait} Legit Or Hype? Truth Exposed!
The Robot AT8XM is a fully automated, AI-powered system designed to generate consistent profits from a hidden loophole in the financial markets. But this isn't some faceless program built by a shadowy corporation. It’s the brainchild of Roman Rosilio, a 38-year-old family man and former top-tier cybersecurity engineer at Apple.
After earning his Master's in Computer Engineering from MIT and spending 11 years protecting sensitive data at one of the world's most powerful companies, Roman discovered something incredible. He found a discreet, legal loophole within Apple's File Transfer Protocol (FTP) that could be harnessed to generate automatic transfers.
He spent over seven months coding and perfecting a robot to exploit this loophole. He named it AT8XM, which stands for "Automatic Transfer 8X Per Month."
That's the core of this system: it's designed to send you two transfers of $632.14 every single week (on Wednesdays and Saturdays), totaling over $5,057 every month, like clockwork.
Is Robot AT8XM Legit and Safe? The Crucial Truth
This is the most important question, and the answer is a resounding YES. However, you need to be careful.
Because of its incredible success, fraudulent copycat sites have appeared, trying to scam people with fake systems. They create unreadable, garbage websites to trick you.
0 notes
Text
Fuzz Testing: An In-Depth Guide

Introduction
In the world of software development, vulnerabilities and bugs are inevitable. As systems grow more complex and interact with a wider array of data sources and users, ensuring their reliability and security becomes more challenging. One powerful technique that has emerged as a standard for identifying unknown vulnerabilities is Fuzz Testing, also known simply as fuzzing.
Fuzz testing involves bombarding software with massive volumes of random, unexpected, or invalid input data in order to detect crashes, memory leaks, or other abnormal behavior. It’s a unique and often automated method of discovering flaws that traditional testing techniques might miss. By leveraging fuzz testing early and throughout development, developers can harden applications against unexpected input and malicious attacks.
What is Fuzz Testing?
Fuzz Testing is a software testing technique where invalid, random, or unexpected data is input into a program to uncover bugs, security vulnerabilities, and crashes. The idea is simple: feed the software malformed or random data and observe its behavior. If the program crashes, leaks memory, or behaves unpredictably, it likely has a vulnerability.
Fuzz testing is particularly effective in uncovering:
Buffer overflows
Input validation errors
Memory corruption issues
Logic errors
Security vulnerabilities such as injection flaws or crashes exploitable by attackers
Unlike traditional testing methods that rely on predefined inputs and expected outputs, fuzz testing thrives in unpredictability. It doesn’t aim to verify correct behavior — it seeks to break the system by pushing it beyond normal use cases.
History of Fuzz Testing
Fuzz testing originated in the late 1980s. The term “fuzz” was coined by Professor Barton Miller and his colleagues at the University of Wisconsin in 1989. During a thunderstorm, Miller was remotely logged into a Unix system when the connection degraded and began sending random characters to his shell. The experience inspired him to write a program that would send random input to various Unix utilities.
His experiment exposed that many standard Unix programs would crash or hang when fed with random input. This was a startling revelation at the time, showing that widely used software was far less robust than expected. The simplicity and effectiveness of the technique led to increased interest, and fuzz testing has since evolved into a critical component of modern software testing and cybersecurity.
Types of Fuzz Testing
Fuzz testing has matured into several distinct types, each tailored to specific needs and target systems:
1. Mutation-Based Fuzzing
In this approach, existing valid inputs are altered (or “mutated”) to produce invalid or unexpected data. The idea is that small changes to known good data can reveal how the software handles anomalies.
Example: Modifying values in a configuration file or flipping bits in a network packet.
2. Generation-Based Fuzzing
Rather than altering existing inputs, generation-based fuzzers create inputs from scratch based on models or grammars. This method requires knowledge of the input format and is more targeted than mutation-based fuzzing.
Example: Creating structured XML or JSON files from a schema to test how a parser handles different combinations.
3. Protocol-Based Fuzzing
This type is specific to communication protocols. It focuses on sending malformed packets or requests according to network protocols like HTTP, FTP, or TCP to test a system’s robustness against malformed traffic.
4. Coverage-Guided Fuzzing
Coverage-guided fuzzers monitor which parts of the code are executed by the input and use this feedback to generate new inputs that explore previously untested areas of the codebase. This type is very effective for high-security and critical systems.
5. Black Box, Grey Box, and White Box Fuzzing
Black Box: No knowledge of the internal structure of the system; input is fed blindly.
Grey Box: Limited insight into the system’s structure; may use instrumentation for guidance.
White Box: Full knowledge of source code or internal logic; often combined with symbolic execution for deep analysis.
How Does Fuzzing in Testing Work?
The fuzzing process generally follows these steps:
Input Selection or Generation: Fuzzers either mutate existing input data or generate new inputs from defined templates.
Execution: The fuzzed inputs are provided to the software under test.
Monitoring: The system is monitored for anomalies such as crashes, hangs, memory leaks, or exceptions.
Logging: If a failure is detected, the exact input and system state are logged for developers to analyze.
Iteration: The fuzzer continues producing and executing new test cases, often in an automated and repetitive fashion.
This loop continues, often for hours or days, until a comprehensive sample space of unexpected inputs has been tested.
Applications of Fuzz Testing
Fuzz testing is employed across a wide array of software and systems, including:
Operating Systems: To discover kernel vulnerabilities and system call failures.
Web Applications: To test how backends handle malformed HTTP requests or corrupted form data.
APIs: To validate how APIs respond to invalid or unexpected payloads.
Parsers and Compilers: To test how structured inputs like XML, JSON, or source code are handled.
Network Protocols: To identify how software handles unexpected network packets.
Embedded Systems and IoT: To validate robustness in resource-constrained environments.
Fuzz testing is especially vital in security-sensitive domains where any unchecked input could be a potential attack vector.
Fuzz Testing Tools
One of the notable fuzz testing tools in the market is Genqe. It stands out by offering intelligent fuzz testing capabilities that combine mutation, generation, and coverage-based strategies into a cohesive and user-friendly platform.
Genqe enables developers and QA engineers to:
Perform both black box and grey box fuzzing
Generate structured inputs based on schemas or templates
Track code coverage dynamically to optimize test paths
Analyze results with built-in crash diagnostics
Run parallel tests for large-scale fuzzing campaigns
By simplifying the setup and integrating with modern CI/CD pipelines, Genqe supports secure development practices and helps teams identify bugs early in the software development lifecycle.
Conclusion
Fuzz testing has proven itself to be a valuable and essential method in the realm of software testing and security. By introducing unpredictability into the input space, it helps expose flaws that might never be uncovered by traditional test cases. From operating systems to web applications and APIs, fuzz testing reveals how software behaves under unexpected conditions — and often uncovers vulnerabilities that attackers could exploit.
While fuzz testing isn’t a silver bullet, its strength lies in its ability to complement other testing techniques. With modern advancements in automation and intelligent fuzzing engines like Genqe, it’s easier than ever to integrate fuzz testing into the development lifecycle. As software systems continue to grow in complexity, the role of fuzz testing will only become more central to creating robust, secure, and trustworthy applications.
0 notes