#hackingtip
Explore tagged Tumblr posts
Text
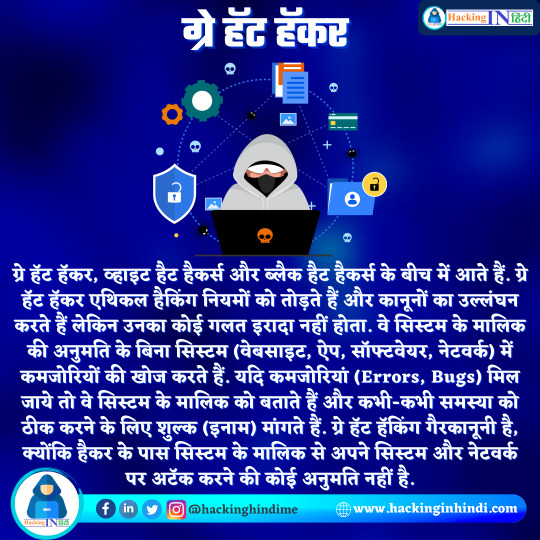
Who Is gray Hat Hacker ? ग्रे हॅट हॅकर कौन है ? Gray hat hackers come in between white hat hackers and black hat hackers. Gray hat hackers break the ethical hacking rules & violate laws but they do not have any harmful intention. They search for weaknesses in a system (website, App, Software, Network) without the permission of the system owner. If problems were found, they Report the owner and sometimes ask for a fee (Bounty) to fix the problem. Gray hat hacking is illegal, as the hacker doesn't have any permission from the system owner to break into their systems & networks.
#hacking#hacker#hack#hacks#hackathon#hackinginstagram#hackinginhindi#hackingtools#hackingtip#hackingtips#hackingtricks#hackingtutorials#hackingtutorial#hackingtutorialseries#hackertools#hackertypes#blackhat#typesofhackers#blackhatorganization#blackhatsociety#blackhathacker#blackhatindia#whitehat#whitehathacker#grayhathacker#grayhat#cybersecurity#cyber#cybersecuritytraining#hacker news
1 note
·
View note
Photo

Edward snowden anime . 🌐www.techyrick.com . . #hackingtips #hackingshit #hackernews #hackingético #hackerofkrypton #hackerkitchens #hackers_empire #hackingnews #hackersstayaway #hackerearth #vinniehackeredits #hackingtools #hackerbrücke #lifehackers #hackingorsecurity #hacker_max #hackerkiralama #brainhacking #hackerz #vinniehackeredit #blackhathacker #whitehathacker #hackermemes #hackercraft #hackertdog #anonymoushackers #whacking #hacking_or_security #hacking #hacker https://www.instagram.com/p/CQkmwyOhmd7/?utm_medium=tumblr
#hackingtips#hackingshit#hackernews#hackingético#hackerofkrypton#hackerkitchens#hackers_empire#hackingnews#hackersstayaway#hackerearth#vinniehackeredits#hackingtools#hackerbrücke#lifehackers#hackingorsecurity#hacker_max#hackerkiralama#brainhacking#hackerz#vinniehackeredit#blackhathacker#whitehathacker#hackermemes#hackercraft#hackertdog#anonymoushackers#whacking#hacking_or_security#hacking#hacker
2 notes
·
View notes
Video
youtube
Illustrator সেরা 3 কৌশল | Top 3 INCREDIBLE tips and Tricks l Bangla tuto...
#illustratortips#illustratortipsandtricks#design#graphicdesign#graphicsdesign#designgraphic#graphicdesignstudent#graphicdesignuiweb#business#motiongraphics#typeposter#visualidentity#grapgicdesign#gridsystem#hackingtips#growthhackingtips#hacking#growthhacking#biohacking#lifehacking#hackingtools#coder#hacker#linux#developers#freeradicals#adaptogen
1 note
·
View note
Text
1 note
·
View note
Photo

все хотят безопасности, но ни одна система не является безопасной💀💀 #hacking #hacker #hackers #anonymous #anonymous2020 #hackingtips (at Москва-Сити) https://www.instagram.com/p/CY4Mn9stKM0/?utm_medium=tumblr
0 notes
Photo

Algo se está cocinando 🧑🍳… porque no todo es Gamming… #newproject #personalproject #stream #streamer #hackingstreaming #darkdevil #hackingtips #fasthacking https://www.instagram.com/p/CS-DTRQln18/?utm_medium=tumblr
0 notes
Photo

TRY THIS LIFE HACK . Mehndi is a natural way to get rid of dandruff. Mix mehndi with curd, lemon juice. Keep the mixture aside for 8 hours then apply it on hair. Let it dry over your hair for 2 hours and then you can wash it away. . Follow @ayushmedi for daily healthy tips.... . Website:- http://www.ayushmedi.com . #ayurvedic #lemon #curd #mhendi #dandruff #dailytips #follow #likes #hackingtips #ayushmedi https://www.instagram.com/p/COHYzi1pPT-/?igshid=156ot0v42prty
0 notes
Photo

10 secrets to going viral on social media!!. . . . Live |comment|share . . . #socialmediahacks #socialmediatips #socialmediatraining #socialmediapost #socialmediacoaching #socialmediaservices #followersinstagram #instagramads #instagrampostideas #instagramgrowthtips #pythoncode #hackingtips #developerslife #webdevelopment #facebookmemes #facebookadsexpert #facebookmarketing #adsราคาถูก #marketingconsultant #marketingstrategy #marketingdigital360 #marketingideas #marketing2021 (at Los Angeles, California USA) https://www.instagram.com/p/CNXIOzWHAe4/?igshid=1coikd1u3j2rp
#socialmediahacks#socialmediatips#socialmediatraining#socialmediapost#socialmediacoaching#socialmediaservices#followersinstagram#instagramads#instagrampostideas#instagramgrowthtips#pythoncode#hackingtips#developerslife#webdevelopment#facebookmemes#facebookadsexpert#facebookmarketing#adsราคาถูก#marketingconsultant#marketingstrategy#marketingdigital360#marketingideas#marketing2021
0 notes
Text
Hacking tips of 2018
Essential OF HACKING
Programmer implies somebody who discovers shortcomings in a PC or PC arrange, however the term can likewise allude to somebody with a propelled comprehension of PCs and PC networks.Hackers might be spurred by a large number of reasons, for example, benefit, dissent, or test. The subculture that has advanced around programmers is frequently alluded to as the PC underground however it is presently an open group. While different employments of the word programmer exist that are not identified with PC security, they are infrequently utilized as a part of standard setting.
Characterizations:-
A few subgroups of the PC underground with various dispositions utilize diverse terms to delineate themselves from each other, or endeavor to reject some particular gathering with which they don't concur. Eric S. Raymond (creator of The New Hacker's Dictionary) advocates that individuals from the PC underground ought to be called saltines. However, those individuals consider themselves to be programmers and even endeavor to incorporate the perspectives of Raymond in what they see as one more extensive programmer culture, a view brutally dismissed by Raymond himself. Rather than a programmer/wafer division, they give more accentuation to a range of various classifications, for example, white cap, dim cap, dark cap and content kiddie.
White Hat:-
A white cap programmer breaks security for non-vindictive reasons, maybe to test their own particular security framework or while working for a security organization which makes security programming. The expression "white cap" in Internet slang alludes to a moral programmer. This grouping likewise incorporates people who perform entrance tests and helplessness appraisals inside a legally binding assention. The EC-Council , otherwise called the International Council of Electronic Commerce Consultants has created affirmations, course product, classes, and web based preparing covering the various field of Ethical Hacking.
Dark Hat:-
A "dark cap" programmer is a programmer who "abuses PC security for little reason past vindictiveness or for individual pick up" (Moore, 2005). Dark cap programmers shape the cliché, unlawful hacking bunches regularly depicted in mainstream culture, and are "the encapsulation of all that general society fears in a PC criminal". Dark cap programmers break into secure systems to decimate information or make the system unusable for the individuals who are approved to utilize the system.
Section 1: Targeting
The programmer figures out what system to break into amid this stage. The objective might be specifically noteworthy to the programmer, either politically or by and by, or it might be picked indiscriminately. Next, they will port output a system to decide whether it is helpless against assaults, which is simply trying all ports on a host machine for a reaction. Open ports—those that do react—will enable a programmer to get to the framework.
Section 2: Research And Information Gathering
It is in this phase the programmer will visit or contact the objective somehow with expectations of discovering key data that will enable them to get to the framework. The primary way that programmers get wanted outcomes from this stage is from "social designing", which will be clarified underneath. Beside social building, programmers can likewise utilize a strategy called "dumpster jumping". Dumpster plunging is the point at which a programmer will truly seek through clients' trash with expectations of discovering archives that have been discarded, which may contain data a programmer can utilize straightforwardly or in a roundabout way, to enable them to access a system.
Section 3: Finishing The Attack
This is the phase when the programmer will attack the preparatory focus on that he/she was wanting to assault or take. Numerous "programmers" will be gotten after this point, baited in or snatched by any information otherwise called a honeypot (a trap set up by PC security staff).
Dark Hat:-
A dark cap programmer is a blend of a Black Hat and a White Hat Hacker. A Gray Hat Hacker may surf the web and hack into a PC framework for the sole reason for informing the director that their framework has been hacked, for instance. At that point they may offer to repair their framework for a little charge.
World class Hacker:-
A societal position among programmers, first class is utilized to depict the most talented. Newfound endeavors will flow among these programmers. Tip top gatherings, for example, Masters of Deception gave a sort of validity on their individuals.
Content Kiddi:-
A content kiddie (or skiddie) is a non-master who breaks into PC frameworks by utilizing pre-bundled computerized devices composed by others, as a rule with small comprehension of the hidden idea—henceforth the term content (i.e. a prearranged plan or set of exercises) kiddie (i.e. kid, youngster—an individual lacking information and experience, youthful).
Hamza Bendelladj used to perform this . In case you dont know about him , read here at
http://gadgetteacher.com/hamza-bendelladj-robin-hood/
Neophyt:-
A novice, "n00b", or "beginner" is somebody who is new to hacking or phreaking and has no learning or experience of the workings of innovation, and hacking.
Blue Hat:-
A blue cap programmer is somebody outside PC security counseling firms who is utilized to bug test a framework preceding its dispatch, searching for misuses so they can be shut. Microsoft additionally utilizes the term BlueHat to speak to a progression of security preparation occasions.
Hacktivis:-
A hacktivist is a programmer who uses innovation to declare a social, ideological, religious, or political message. As a rule, most hacktivism includes site disfigurement or foreswearing of-benefit assaults. Country state Intelligence offices and cyberwarfare agents of country states.
Assault:-
An average approach in an assault on Internet-associated framework is:
1. System list: Discovering data about the expected target.
2. Powerlessness investigation: Identifying potential methods for assault.
3. Abuse: Attempting to bargain the framework by utilizing the vulnerabilities found through the weakness investigation.
Keeping in mind the end goal to do as such, there are a few repeating apparatuses of the exchange and methods utilized by PC lawbreakers and security specialists.
Security Exploit:-
A security misuse is a readied application that exploits a known shortcoming. Normal cases of security misuses are SQL infusion, Cross Site Scripting and Cross Site Request Forgery which manhandle security gaps that may come about because of substandard programming practice. Different endeavors would have the capacity to be utilized through FTP, HTTP, PHP, SSH, Telnet and some site pages. These are exceptionally normal in site/area hacking.
Systems
Defenselessness Scanner:-
A defenselessness scanner is an apparatus used to rapidly check PCs on a system for known weaknesses.Hackers additionally usually utilize port scanners. These verify which ports on a predefined PC are "open" or accessible to get to the PC, and some of the time will identify what program or administration is tuning in on that port, and its adaptation number. (Note that firewalls safeguard PCs from gatecrashers by restricting access to ports/machines both inbound and outbound, yet can at present be dodged.)
Watchword Cracking:-
Watchword breaking is the way toward recouping passwords from information that has been put away in or transmitted by a PC framework. A typical approach is to more than once attempt surmises for the secret key.
Bundle Sniffer:-
A bundle sniffer is an application that catches information parcels, which can be utilized to catch passwords and other information in travel over the system.
Mocking Attack (Phishing):-
A mocking assault includes one program, framework, or site effectively taking on the appearance of another by misrepresenting information and in this way being dealt with as a put stock in framework by a client or another program. The motivation behind this is as a rule to trick projects, frameworks, or clients into uncovering classified data, for example, client names and passwords, to the aggressor.
Rootkit:-
A rootkit is intended to cover the trade off of a PC's security, and can speak to any of an arrangement of projects which work to subvert control of a working framework from its honest to goodness administrators. Ordinarily, a rootkit will cloud its establishment and endeavor to keep its expulsion through a subversion of standard framework security. Rootkits may incorporate swaps for framework doubles with the goal that it ends up noticeably outlandish for the true blue client to recognize the nearness of the gatecrasher on the framework by taking a gander at process tables.
Social Engineering:-
At the point when a Hacker, regularly a dark cap, is in the second phase of the focusing on process, he or she will normally utilize some social designing strategies to get enough data to get to the system. A typical practice for programmers who utilize this procedure, is to contact the framework director and assume the part of a client who can't access his or her framework.
Trojan Horses:-
A Trojan stallion is a program which is by all accounts doing a certain something, yet is really doing another. A trojan steed can be utilized to set up a secondary passage in a PC framework with the end goal that the interloper can obtain entrance later. (The name alludes to the steed from the Trojan War, with adroitly comparative capacity of deluding safeguards into bringing an interloper inside.)
Infections:-
An infection is a self-duplicating program that spreads by embeddings duplicates of itself into other executable code or archives. In this way, a PC infection acts in a path like a natural infection, which spreads by embeddings itself into living cells. While some are innocuous or simple deceptions most PC infections are viewed as vindictive.
Worm:-
Like an infection, a worm is additionally a self-imitating program. A worm contrasts from an infection in that it spreads through PC systems without client intercession. Not at all like an infection, it doesn't have to append itself to a current program. Many individuals conflate the expressions "infection" and "worm", utilizing them both to depict any self-proliferating program.
Key Loggers:-
A key lumberjack is an instrument intended to record ('log') each keystroke on an influenced machine for later recovery. Its motivation is for the most part to enable the client of this instrument to access secret data wrote on the influenced machine, for example, a client's watchword or other private information. Some key lumberjacks employments
1 note
·
View note
Text
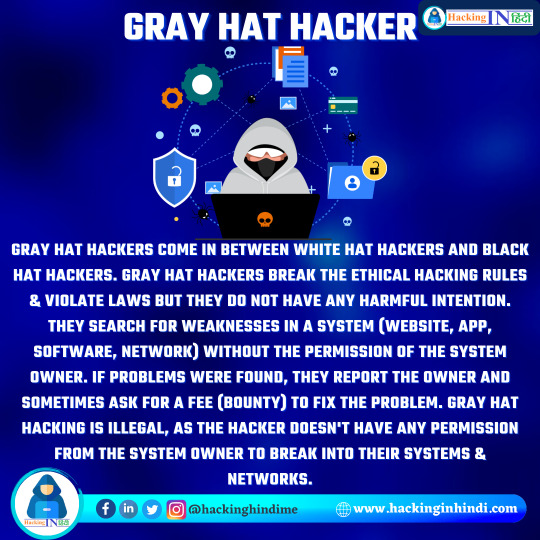
Who Is gray Hat Hacker ? ग्रे हॅट हॅकर कौन है ?
Gray hat hackers come in between white hat hackers and black hat hackers. Gray hat hackers break the ethical hacking rules & violate laws but they do not have any harmful intention. They search for weaknesses in a system (website, App, Software, Network) without the permission of the system owner. If problems were found, they Report the owner and sometimes ask for a fee (Bounty) to fix the problem. Gray hat hacking is illegal, as the hacker doesn't have any permission from the system owner to break into their systems & networks.
#hacking#hacker#hack#hacks#hackathon#hackinginstagram#hackinginhindi#hackingtools#hackingtip#hackingtips#hackingtricks#hackingtutorials#hackingtutorial#hackingtutorialseries#hackertools#hackertypes#blackhat#typesofhackers#blackhatorganization#blackhatsociety#blackhathacker#blackhatindia#whitehat#whitehathacker#grayhathacker#grayhat#cybersecurity#cyber#cybersecuritytraining#hacker news
0 notes
Text

#hacker #hacking #hac #hacks #hackers #learnhacking #virus #scan #anonymous #anonymoushackers #villagerweb #hackingtips #hackingtools #hackingnews #hackinstagram #instagram #instagood #instadaily #instatravel #instastudy #studymotivation #study #instalive #learningeveryday #learning #onlineclasses #online #onlinemarketing #onlinestore
#freecertificate
1 note
·
View note
Photo
@hacker_b0t follow us . . 🌐www.techyrick.com . . #hackercraft #quoteshacker #ikeahackers #biohacker #hackerone #häcker #hackermeme #hackingético #whitehathacker #hackingtool #hackerpschorr #vinniehackeredits #hackinglife #hackingtips #househacking #hackingwithswift #hackingthecity #hackingbooks #belajarhacking #hackingmemes #hackerschool #hackermemes #hackingshit #hackingfacts #hackersworld #happyhacking #hackerinstagram #ethicalhackers #hackerkiralama #hacker https://www.instagram.com/p/CQtdxwEgn4T/?utm_medium=tumblr
#hackercraft#quoteshacker#ikeahackers#biohacker#hackerone#häcker#hackermeme#hackingético#whitehathacker#hackingtool#hackerpschorr#vinniehackeredits#hackinglife#hackingtips#househacking#hackingwithswift#hackingthecity#hackingbooks#belajarhacking#hackingmemes#hackerschool#hackermemes#hackingshit#hackingfacts#hackersworld#happyhacking#hackerinstagram#ethicalhackers#hackerkiralama#hacker
0 notes
Photo

Go ahead, show off now! This is usually what people do in the movies 😝. . . Follow 👉 @saiabhijat.tech for latest Updates, Tips & Tricks, Facts, How-tos and Reviews in Tech! . . . #saiabhijattech #satech #tech #technews #techno #technology #latest #news #instatech #instanews #picoftheday #hacker #hacking #cybersecurity #tricks #tipsandtricks #hackingtips #tools #pranks #didyouknowfacts #didyouknow #facts #satech_diduknow #satech_facts — view on Instagram https://ift.tt/2VlG4eF
0 notes
Link
Learn about 30+ best Android hacks and tips for your smartphone in 2019. It will make your Android phone smarter and you can get the best out of your device.
#androidhacks#hackingtips#topmobilehacks#tricksandhacks#bestandroidhacks#bestmobilehacks#techtips#socialmedia#hacking
0 notes
Text

Who Is white Hat Hacker ? व्हाईट हॅट हॅकर कौन है ?
व्हाइट हॅट हॅकर को एथिकल हैकर भी कहा जाता है क्योंकि वह कानूनी तरीको का अनुसरण करता है, और हमलों से बचाने में मदद करने के लिए सिस्टम के मालिक की अनुमति से साइबर सुरक्षा जांच करता है. व्हाइट हॅट हॅकर के पास सिस्टम की सुरक्षा को तोड़ने की अनुमति होती है. व्हाइट हॅट हॅकर सुरक्षा कमजोरियों ( खामियों ) को खोजने के उद्देश्य से पेनेट्रेसन टेस्टिंग और वल्नरॅबीलिटी असेसमेंट करते है ताकी सिस्टम की सुरक्षा कमजोरीयों को ब्लॅक हॅट हॅकर के अटॅक करने से पहले सुधारा जा सके.
#hacking#hacker#hack#hacks#hackathon#hackinginstagram#hackinginhindi#hackingtools#hackingtip#hackingtips#hackingtricks#hackingtutorials#hackingtutorial#hackingtutorialseries#hackertools#hackertypes#blackhat#typesofhackers#blackhatorganization#blackhatsociety#blackhathacker#blackhatindia#whitehat#whitehathacker#grayhathacker#grayhat#cybersecurity#cyber#cybersecuritytraining#hacker news
0 notes