#hacktivist
Explore tagged Tumblr posts
Text

Sometimes life is good
10 notes
·
View notes
Text







HACKTIVIST - JOC, Ieper (B) 2016
#concert#live music#music#photography#pictures#concert photography#concertphotography#metal#clubshow#rap#hip hop#hacktivist
3 notes
·
View notes
Text
Zukunkft ● Garden
Christina here. Here’s another one for the bulging how uncool am I file. I was wandering around on Instagram a couple of weeks ago and the Zukunftgarten account caught my eye. Zukunftgarten is a German compound word that translates as future garden. What else could I think but aha! This must be a German solarpunk. Because I live in Germany, I should follow them.
(Ariel jumping in here to tell you that it turns out that Christina cold-called - well, slipped into the DMs of - John Threat aka Corrupt aka legendary hacktivist of the Great Hacker War, in order to interview him for our next podcast episode.
Listener, she had zero clue who he was the entire time and it's an amazing conversation. We can't wait for you to hear it! In the meantime, have an excellent background read on the process...)

View On WordPress
#solarpunk#SolarpunkPresentsPodcast#Art Installation#Zukunft Garden#hacktivist#cyberpunk#anarchism#John Threat#Corrupt#Great Hacker War
3 notes
·
View notes
Photo
I love the idea of every single hacktivist saw this and went " Aw fuck, he's right. This needs to be fixed immediately, can't be dissapointing John Waters.


the only criticism of millennials l accept
395K notes
·
View notes
Text
Hacktivist Released New Single And Video "Bones"
Photo by Shaun Hodson/Loki Films UK djent/grime outfit HACKTIVIST have shared a brand new single and music video titled “Bones“, along with the announcement of a brand new line-up, including guitarist Alex Hek (ex-October Ends) and drummer Stee Cole (protege of Mike Malyan), alongside the already-established vocal powerhouse duo of J Hurley and JJ Olifent. The band’s first release with their…
0 notes
Text
Robert,
Just send it all to Wikileaks. We’re done taking the high road.
Keep at it,
Those of us who give a shit
0 notes
Photo

CrowdStrike faces additional adversities as the cybersecurity company struggles to improve its situation. Despite restoring most affected systems, a recent post reveals that a hacktivist group has caused further trouble. #CrowdStrike #cybersecurity #hacktivist
0 notes
Text
APT44, Cyber Espionage & More In NATO Cyber Threats

Emboldened and Evolving: NATO Cyber Threats snapshot
As NATO members and partners prepare for a landmark summit, the cyber threat must be considered. Empowered state-sponsored actors, hacktivists, and criminals are willing to cross lines and commit acts previously unthinkable to attack the Alliance. Besides military targets, NATO must address hybrid threats including APT44, Cyber Espionage & More harmful cyber activities against hospitals, civic society, and other targets, which could affect contingency resilience. The Ukraine crisis is linked to rising cyber risks, but many will grow separately and simultaneously.
NATO faces clandestine, aggressive cyber actors that gather intelligence, assault key infrastructure, and spread disinformation. Google is closely watching cyber threats, including those in this report, to safeguard its customers and businesses, but this is just a snapshot of a bigger and developing world.
What is Cyber espionage?
Cyber espionage is the act of stealing information without permission over the internet. It’s the digital version of traditional espionage
Cyber espionage
NATO’s enemies have long used Cyber Espionage to gain political, diplomatic, and military insight and acquire defence technologies and economic secrets. However, Alliance intelligence will be crucial in the coming months. This summit represents a transition time, with Mark Rutte as Secretary General and other changes planned to strengthen the Alliance’s defence posture and long-term support for Ukraine. Threat actor Cyber Espionage might weaken NATO’s strategic advantage and inform opponent leadership on how to oppose NATO’s investments and ambitions.
NATO faces global Cyber Espionage from various actors. Many still use simple but successful approaches like social engineering. Others have advanced their tradecraft to become formidable opponents for even the most skilled defenders.
APT29 (ICECAP)
APT29, attributed to the Russian Foreign Intelligence Services (SVR) by various governments, collects diplomatic and political intelligence on Europe and NATO member states. APT29 has committed several high-profile compromises of technology corporations that give public sector access. In the past year, Mandiant has seen APT29 target NATO member technology businesses and IT service providers to compromise government and policy organisations’ third-party and software supply chains.The actor is skilled in cloud environments and adept at disguising their tracks, making them hard to detect, monitor, and expel from infiltrated networks.
In addition to spear-phishing NATO members, APT29 has traditionally targeted diplomatic bodies. The actor has breached European and U.S. executive authorities multiple times. They have also targeted political parties in Germany and the U.S. to gather intelligence on potential government policy.
Cyberespionage from China
Recently, Chinese Cyber Espionage has shifted from noisy, easily identifiable operations to stealth. Technical advances have made defending harder and helped NATO member states attack government, military, and commercial targets.
Chinese Cyber Espionage increasingly uses:
Targeting the network edge and exploiting zero-day vulnerabilities in security devices and other internet-facing network infrastructure to limit defence detection. These operators have lowered their risk of user or control identification by using less social engineering. These hackers exploited 12 zero-days (software or hardware vulnerabilities unknown to the vendor, with no patch or fix available, and can be exploited before they can be addressed) in 2023, several in network edge security products. These devices are suitable beachheads in hacked networks because they lack endpoint detection.
Hiding harmful communications via operational relay box (ORB) networks. Threat actors use proxies to mask their malicious traffic on the internet, but proxy tracking is easy. Large ephemeral ORB networks of shared and hacked proxies are used by actors. These networks are hard to trace and hinder infrastructure intelligence sharing for defenders.
Live off the land to avoid defence detection. Some actors utilise non-malware means to break in. Live-off-the-land tactics exploit legitimate system tools, features, and functionalities to traverse networks and commit crimes. Without malware detection and intelligence sharing, defenders are at a disadvantage.
Not just Chinese threat actors use these methods. Russian actors APT29, APT28, and APT44 have employed them.
Cyberattacks that disrupt and destroy
Cyberattacks are increasing, threatening NATO directly and indirectly. Iranian and Russian state actors have been eager to attack NATO countries in recent years, but they have concealed behind phoney fronts that take credit. Mandiant described a 2022 damaging attack on Albania by a purported hacktivist group called “HomeLand Justice” that the U.S. Government subsequently ascribed to Iranian actors.
While demonstrating their ability to launch complex strikes on extremely sensitive operational technology systems in Ukraine, state actors are compromising NATO countries’ key infrastructure for future disruptions. These actors have the means and motivation to disrupt NATO’s key infrastructure.
In addition to state cyberattacks, hacktivist and criminal disruptions are no longer ignorable. Global hacktivist resurgence has caused major attacks on the public and private sectors, making illegal activity a national security threat.
APT44 Sandworm, Frozenbarents
Highly advanced cyber threat outfit APT44, also known as Sandworm, is thought to be backed by Russian military intelligence.
Espionage, disruption, and disinformation efforts are APT44’s specialties. For over a decade, they’ve carried out disruptive malware attacks including BlackEnergy and Industroyer.
APT44 summary:
APT44 has targeted essential infrastructure, government agencies, and international sports organisations. Since the Russia conflict, Ukraine has been a top target.
Tactics: APT44 has many tools to achieve its goals. Supply chain attacks, phishing emails, and software flaws are examples. They may use wiper malware to delete data and disrupt operations.
The range of APT44’s capabilities makes it worrisome. APT44 conducts espionage, sabotage, and influence operations, unlike many APT groups.
The global devastating hack NotPetya, Pyeongchang Olympic games strikes, and Ukraine outages have all been carried out by APT44. Russian military intelligence-linked actor has carried out technically complicated interruptions of sensitive operational systems and broad-effect damaging strikes. APT44 has carried out most disruptive assaults in Ukraine and minor attacks in NATO nations since the war.
PRESSTEA (Prestige) ransomware was used against Polish and Ukrainian logistics companies by APT44 in October 2022. The malware was unbreakable and damaging, maybe to demonstrate the group’s ability to harm supply routes carrying lethal aid to Ukraine. APT44’s risk-taking in using a disruptive capacity against a NATO member country is evident in this operation.
Hacktivists
Geopolitical flashpoints like the Russian invasion of Ukraine have sparked a global hacktivism revival. Despite focusing on NATO members, these actors have had mixed results. Many surgeries are meant to draw attention and create a false sense of uneasiness but cause no lasting damage.
These actors cannot be disregarded despite their flaws. Their attacks draw media attention in target countries and sometimes have catastrophic effects. One of their preferred methods, distributed denial-of-service (DDOS) attacks, are cosmetic but might be used to greater effect during elections. Hacktivists like pro-Russian organisation Cyber Army Russia Reborn (CARR) are also testing larger strikes on key infrastructure. CARR, which has questionable ties to APT44, has affected U.S., Polish, and French water systems in a series of basic but aggressive acts.
Cybercriminals
Ransomware-related financial disruptions are already disrupting NATO states’ essential infrastructure, causing hospital patient care, energy, and government service failures. Many crooks target this crucial infrastructure despite their promises. Russian-speaking criminals and North Korean state actors seeking espionage funding have regularly attacked U.S. and European healthcare institutions. This threat will likely grow due to these actors’ ability to operate from states with low cyber crime enforcement or extradition agreements and the lucrative nature of ransomware operations.
Information Operations and Disinformation
Information operations have grown in cyber threat activities over the past decade as wars and geopolitical tensions have increased. These operations range from “troll farm” social media manipulation to intricate network intrusions. Russian and Belarusian information operations have targeted NATO member nations to weaken the Alliance’s cohesiveness and goals.
Some Cyber Espionage operators who acquire clandestine intelligence also conduct information operations. In hack-and-leak activities, APT28 and COLDRIVER have used stolen data, while UNC1151 has used infiltration capabilities in more complicated information operations. False and misleading information is used to influence public opinion, foment strife, and advance political goals.
Google vigorously counters these activities across products, teams, and geographies where they break our standards and disrupt overt and covert information operations campaigns. They report quarterly in the TAG Bulletin on YouTube channel disruptions, blogs, AdSense accounts, and URLs deleted from Google News surfaces.
Information Operations of Prigozhin Survive
Former Russian industrialist Yevgeniy Prigozhin’s disinformation empire continues, albeit less efficiently, after his death. These campaigns continue to spread disinformation and pro-Russia narratives on many social media platforms, recently emphasising alternative sites, across multiple regions.
These efforts advocate for NATO’s disarmament and claim it causes global instability. They criticise NATO leaders too. These commercials’ substance is heavily influenced by geopolitical events like Russia’s 2022 invasion of Ukraine and other Russian strategic aims. NATO and its member states’ backing for Ukraine has made the Alliance a major target directly and indirectly by becoming involved in matters against Russia’s strategic interests.
COLDRIVER
Russian Cyber Espionage actor COLDRIVER has been linked to the Federal Security Service. The actor often conducts credential phishing attempts against prominent NGOs and retired intelligence and military leaders. The hack-and-leak operation employed victim mailbox data stolen by COLDRIVER. In 2022, COLDRIVER leaked information to deepen Brexit-related political divides in the UK.
Before that, the actor revealed U.S.-UK trade deals before the 2019 UK election. Originally targeting NATO countries, COLDRIVER expanded in 2022 to include the Ukrainian government and conflict supporters. In March 2022, COLDRIVER campaigns targeted numerous European militaries and a NATO Centre of Excellence for the first time.
Read more on govindhtech.com
#apt44#cyberespionage#natocyber#emboldened#apt29#icecap#chinesecyber#hacktivist#frozenbarents#distributeddenial#ddos#healthcare#Prigozhin#survive#coldriver#technology#technews#news#govindhtech
0 notes
Text
HACKTIVIST #4
Created by: Alyssa Milano Writers: Jackson Lanzing & Collin Kelly Artist: Marcus To Publisher: Archaia Black Label Previously: Hacktivist #3 Yes, I know I’m quite late on this issue. I actually thought I had reviewed this. But as I thinking about getting ready to watch and review Mistresses tonight, which stars Alyssa Milano, it made me think of this series that she created, so I looked it up and…

View On WordPress
#1#3#4#Alyssa Milano#Archiai Black Press#Collin Kelly#computer hacking#David Cutler#Hacktivist#Jackson Lanzing#Marcus To#social activism#social networking
1 note
·
View note
Text
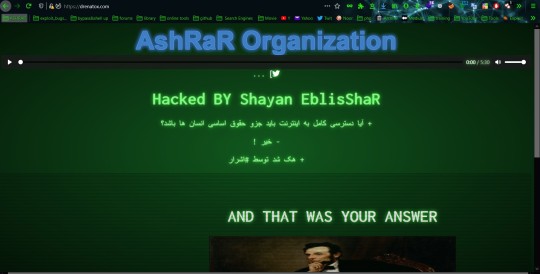
#shayan akbari#شایان سوشیانت#ahrar universal org#شایان اکبری#احرار#hacktivist#shayan hacker#hacker#shayan eblisshar#ابلیس شر#هک سایت#دیفنس#هک#هکینگ#هکر#اشرار تیم
0 notes
Text
you know shit's fucked when you start daydreaming about high profile political protests instead of fictional characters. anyway, don't buy anything Feb 28.
#like what if every winner at the oscars just delivered a 1 sentence rebuke of musk or trump#as their opening line#or simply spent their whole time on it until the music played#or what if there were no jokes at all#just statements of ludicrous fact#what if hacktivists killed every cybertruck by injecting malware into the next software update while musk is busy taking over the u.s. gov#you KNOW he has to have some disgruntled employees#what if trump and luigi went head to head in a national poll abt who would run the country better#what if ... got any for me?#american dystopia#what if elon's next hat had something sewed into it to make his hair fall out
34 notes
·
View notes
Text
JET MY BABY I'LL MISS YOU SO MUCH
The only way I'm dealing with this is headcanoning that Jet is working with Garcia.
#I've always headcanoned that Jet trained herself/was inspired by The Black Queen aka Garcias hacktivist handle anyway#Jet is one of my favorite characters I'm devastated#The Squad is gonna be such a sausage fest without out you sweetie#Pray for Ayanna in this sea of testosterone#organized crime#law and order organized crime#organized crime spoilers#oc spoilers#l&o oc#jet slootmaekers#criminal minds#penelope garcia#peacock
9 notes
·
View notes
Text
“The database has not been compromised as such,” Lan Wangji replies. “Rather, it is being held hostage. It will be breached if we do not pay the ransom.”
oh ny god did wwx become a hacker in the dark years after lwj broke up w him
#he wouldn't do THIS tho#I could see him as a hacktivist. or just releasing embarrassing info abt corrupt politicians. or having fun#im just desperate for this fic to have anything interesting happen#cor.txt
7 notes
·
View notes
Text
what is the fucking point of paying for streaming when streaming keeps adding on more ad breaks and then charges me more money to have NO ads
#every day in every way i am closer to becomign a fucking hacktivist#this is about amazon in case y'all are wondering#shut up alix no one cares
25 notes
·
View notes
Text


𝙲𝙷𝙰𝚁𝙶𝙸𝙽𝙶 ⇢🔋
#I had a photoshoot of him with the hacktivist set#just different boots#oc : damian#cp2077#cp 2077#cyberpunk 2077 phantom liberty#cyberpunk 2077#male v#game photo#cyberpunk 2077 photomode#cp77#masc v#cyberpunk 2077 v#cyberpunk 2077 oc#cyberpunk photomode
19 notes
·
View notes
Text
hey hey, for anyone who may be unfamiliar with some of my fandoms.
four of my all-time fave TRANS CHARACTERS PLAYED BY TRANS ACTORS:


Ian Alexander (they/them/he, transmasc nb) as Buck Vu (bi, he/him, trans boy) in The OA.


Elliot Page (he/they, transmasc nb) as Viktor Hargreeves (bi, he/him, trans man as of s3) in The Umbrella Academy.


Laverne Cox (she/her, trans woman) as Sophia Burset (ambiguous lesbian, she/her, trans woman) in Orange Is The New Black.


Jamie Clayton (she/her, trans woman) as Nomi Marks (lesbian, she/her, trans woman) in Sense8.
#trans positivity#trans pride#representation matters#trans actors playing trans characters#feel free to add others if you have them!#let's all go back to the days where instead of starting discourse#we recced each other new fandoms instead#ambers.txt#I know I have a lot of transfem followers here - if you have not seen Sense8 you NEED TO OMG. I love her so much.#trans woman lesbian hacktivist yessss
8 notes
·
View notes