#how to bypass admin windows 10
Explore tagged Tumblr posts
Text
I will never understand why people keep recommending linux mint to people. people keep saying oh it's like windows and like. they are literally just wrong; every time you tell someone Mint is like Windows you are setting them up to spend 20 minutes on Mint and then run into an obstacle and pay for a windows license. no matter what kind of mediocre UI they dress it up with, despite everything, it is a linux distribution and thus, crucially: not windows. It's popular I guess so it's better than hyperspecific micro-distro of the week or, arch, because people keep recommending arch for some unknowable reason.
I'm going to be real here: if you are new to this just use ubuntu. ignore everyone else. if looking at the gnome GUI makes you want to start killing hostages like it does for me, you can just get it packaged with KDE by default and that's a very familiar and intuitive UI to a windows user. it's called Kubuntu they put out their own little thing and everything it's easy. and unlike mint, it's vastly more likely to just, actually work, and be compatible with software. it will be a learning experience; you are switching to a fundamentally different OS, one that still has deep roots in enthusiast preferences and a whole different crop of bizarre decisions that made sense to some guy who thought the GUI would be a passing fad. and that's fine. you had to learn all this for windows too, you just did it when you were like 7. stick with it and it'll make sense quickly even, as unlike windows, Linux is highly transparent in most cases; it will usually tell you what the problem actually is, even if you don't understand how to fix it.
speaking of which: don't be afraid of the terminal. It's daunting, it's initially opaque, and yes, it is entirely possible to horrifically mangle your install with it. You cannot be afraid of it. you don't have to learn every facet of it; frankly I hate the thing and I refuse to accept any distro where it is expected that the user crack open the console to do basic tasks. Ubuntu - or yeah mint I guess - do not require this. 9 times out of 10, you will use the terminal to enter one command that you stole off a tech support forum where the kind of people who use Arch have magically fixed the incredibly specific problem you're having 13 years ago and it still works. I have been using linux semi-regularly (yeah yeah I still have a windows 10 install sue me) for a year now, and barring one particular incident attempting to install GZDoom where it was manifestly my fault, that has been the extent of my interaction with the terminal. I have opened it like 3 times total.
I highly recommend learning what the basic structure of a command is - get a general idea of what it is doing. you don't have to be able to write these things from scratch, but getting just that basic understanding will make your life so much easier. here's a first step for you: if you see 'sudo' in a command, that means the command makes use of admin authority, and will bypass any protections or restrictions on what it is trying to do. scary! it is the effectively same thing as when you click on a program on windows and it throws that shitty little popup window asking if you're *really* sure you want to run the program as admin. not scary; you do that all the time.
linux is more consistently and straightforwardly usable than it has basically ever been; if you are willing to spend a week or so getting used to it, you'll do fine. if you have a spare drive - hell even a USB stick, you can literally boot into Linux straight off USB, it's that easy, - you can dual-boot and still have a windows install to fall back on in case you absolutely positively just need something to work or just cannot get it to run on linux.
#it is 2 AM so if this is incoherent. that's why#this post made by I fucking hate Mint stop using Mint right now
16 notes
·
View notes
Text
Forgot Dell Laptop Password Windows 7 How to Unlock?
I forgot Windows 7 admin password for my Dell laptop and a reset disc was not created. How do I reset the password and get into my locked Dell laptop? Many people have this dilemma when using Windows 7 system. A strong and unique password is essential to protect our system, but you tend to forget Windows 7 password. What to do if we are locked out of Dell laptop Windows 7?
The following Tips will tell you how to unlock a locked Dell laptop Windows 7 without original password. All you need is to reset the forgotten admin password of Windows 7.
Tip 1: Using Windows 7 default Administrator account.
Windows 7 OS has a built-in administrator account which is created during Windows installation without password, and disable by default. You need to enable that account before losing your other admin account password. Or in this tip your built-in administrator account won’t appear in the screen.
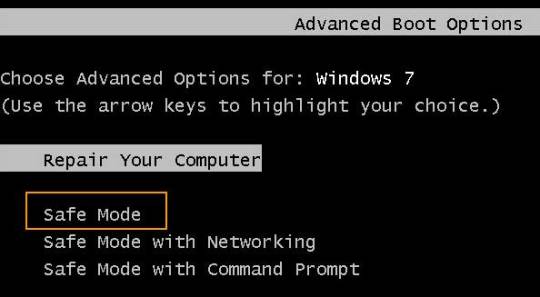
1. Start your computer and press "F8" while the computer boots up. The Advanced Boot Options screen appears.
2. Scroll down to "Safe Mode with Command Prompt" and press "Enter." Your computer starts in Safe Mode with Command Prompt.
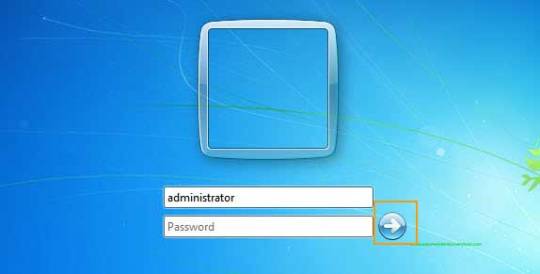
3. Select the Administrator account that appear in the screen, then enter command prompt.
4. Type: net user your username 123456 and hit enter, it will show you a message that” the command completed successfully.
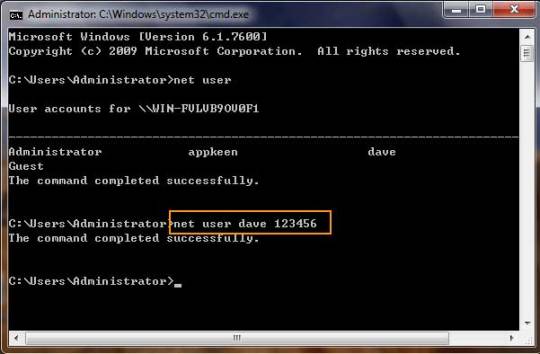
5. Restart your computer, then you can log in as dave with the password 123456. You can go to control Panel to change your account password if necessary.
Tip 2: Reset Dell Laptop Password Windows Vista Using A Free Password Reset Disk.
This is a free and easy way to hack Windows Vista without data lost. The problem with this option is that you have to create the reset disk before the password is lost. Thus if you don’t have a password reset disk, this option is not for you. Here are the steps if you have reset disk.
Step 1. Insert Win7 password reset disk to your computer.
Step 2. When you entering a wrong password for login, a hint will appear: The user name or password is incorrect. Click OK and back to the login Window. Click Reset password.

Step 3. Password reset wizard is running. On the Welcome screen, click Next.
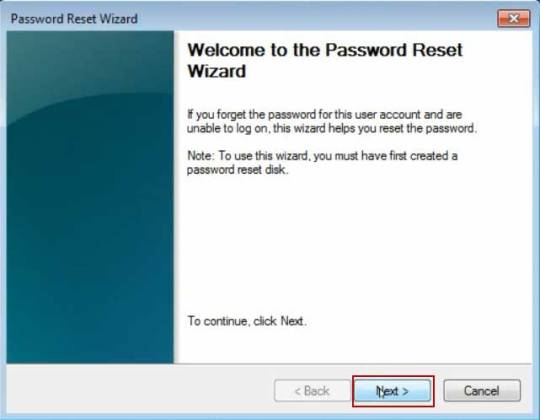
Step 4. Choose your USB flash drive in the drop-down menu and click Next.
Step 5. After the Password Reset Wizard finished reading your saved password, you need to type a new password in the Type a new password box and confirm. And then Click Next, then Finish. It is OK.
Tip 3: Use a Windows Password Recovery program to help Unlock Dell laptop Windows 7.
If you forgot an admin account password on your Dell laptop Windows 7 and there is only one admin account. It is a little troublesome.
However, we can use a handy password recovery tool, Windows Password Rescuer Advanced, to easily bypass Windows 7 admin password on your laptop without admin privileges, then you can log into your Dell laptop without password.
Here I will show you how to reset Windows 7 administrator password on a Dell laptop with USB flash drive.
It works perfectly for all Windows versions on any laptop and desktop computers. All you need is another computer which you can login with administrator account and install Windows Password Rescuer to create a Windows password recovery disk with USB flash drive.
Step 1: Log in any available computer that you can access to and allows you download. Download and install “Wimware Windows Password Rescuer program” in that computer.
Of course, it also works for Windows 10. If you want to unlock a Dell Windows 10 laptop without password, this is one of the best workable ways.
Step 2: Run and burn the program to a blank CD/DVD or USB flash drive.
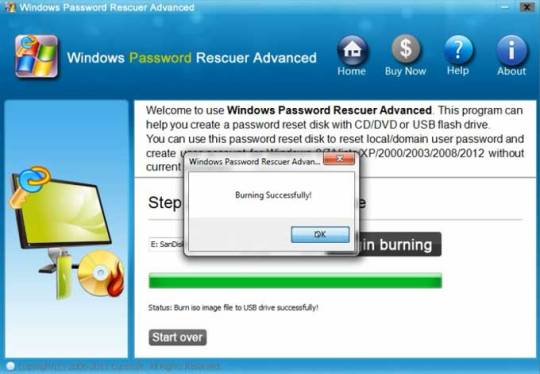
Step 3: When finish, insert the disk to your locked Computer and make your computer boot it from the disk by changing the BIOS setup, then you can follow the instruction to reset your password.
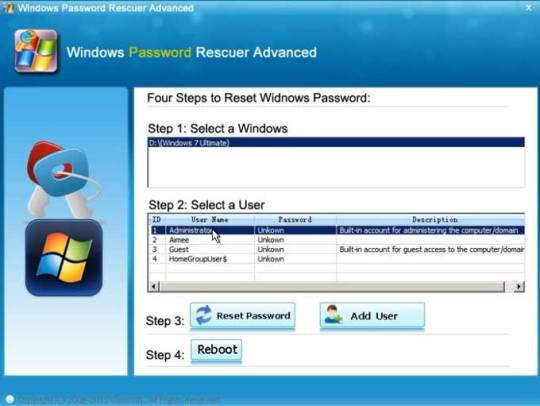
Step 4: After restart, you can log into your Dell laptop Windows 7 without password.
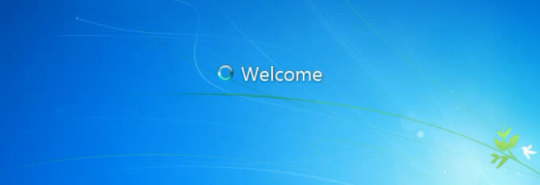
#Dell laptop#Windows 7#unlock dell laptop windows 7#reset password on dell laptop Windows 7#forgot dell laptop password windows 7
0 notes
Text
Here's Why You Should Always Log Out of WordPress
New Post has been published on https://thedigitalinsider.com/heres-why-you-should-always-log-out-of-wordpress/
Here's Why You Should Always Log Out of WordPress
We may think we know WordPress security. But we can’t underestimate the task at hand. It seems that surprises lurk around every corner.
Consider a recent report from the security firm We Watch Your Website, for example. The report claims that 60% of hacked WordPress sites stem from stolen session cookies. I sure didn’t see that one coming.
We know about using strong passwords and setting file permissions. We understand the importance of updating our WordPress installs. We may even use a security plugin or two.
However, even the most security-conscious among us can miss things. That one oversight can lead to a hacked website. And that’s despite taking a bevy of security measures.
Stolen session cookies weren’t on the radar. So, what can we do to prevent this from happening? The author of this report has some advice.
How to Prevent Stolen Session Cookies
Thomas J. Raef is the author of “The Real Attack Vector Responsible for 60% of Hacked WordPress Sites in 2023.” His report demonstrates the threat of stolen session cookies in great detail. And a recent appearance on the WP Tavern Jukebox podcast shed more light on the subject.
But what about remedies? How do we stop these attacks from impacting our websites? I asked Raef for some preventative tips. The answer is as simple as logging out.
Our interview was lightly edited for clarity and brevity.
How do session cookies get stolen?
Thomas J. Raef: If it’s not WordPress, they’re frequently stolen via cross-site scripting. However, WordPress uses the HttpOnly option in the headers. So, that prevents cookie theft in WordPress via XSS.
The main way is by info stealers. If you Google the term, you’ll see it’s almost as popular as ransomware. Some ransomware hackers are starting to use info stealers more for their infections. Info stealers are designed to evade detection from most anti-malware programs. Some are dedicated to evading detection on Windows, others on Macs.
They typically steal everything possible in about 10 seconds. Some ask, why would they bother stealing WordPress session cookies if they’re also stealing bank logins, etc. But look at the cybercriminal industry. What do they need for the majority of their attacks? Oh, a legitimate website to infect unsuspecting visitors.
They steal the session cookies because it totally bypasses 2FA (Two-Factor Authentication), MFA, etc. because the user is still authenticated. As long as the cookie hasn’t expired.
Raef’s report shows that nearly 60% of hacked WordPress websites were the result of stolen session cookies. Image credit: We Watch Your Website
How can we secure our devices against this type of threat?
TJR: The easiest way is to remember to log out. That’s it! When you log out you expire the cookie. If you just close your browser window, it leaves the cookie active. So, if it’s stolen, it can be used by anyone.
One simple prevention is using SolidWP (Solid Security). Their Trusted Devices feature uses the IP address to generate the session cookie. If it’s stolen, it can’t be used anywhere other than where it was originally created. Those two things are the best way to prevent session cookies from being used against your sites.
Are there any changes the WordPress project could take to increase the security of session cookies?
TJR: Possibly. If there was a procedure that checked for inactivity after 30 minutes, and then automatically logged out the user, that might help. But I believe that would involve JavaScript and that’s getting too complicated. They already include the HttpOnly option, so they’re doing a lot to prevent this from being even bigger.
Do you have any other advice for web designers managing WordPress sites?
TJR: Make sure that everyone with admin access to your site is also focused on sanitary procedures for all local devices. We’re seeing more and more sites being infected due to malware on the local device of an admin. It can steal usernames, passwords, and session cookies.
2FA can stop the usage of username and password, but not session cookies. Tell all devs to log out! It’s quite simple and 100% effective.
One thing we’re starting to see more of is hackers attacking from the local device. Not stealing session cookies or anything else, just piggybacking on a legitimate admin session.
We see the legit IP address of an admin, and they’re doing their work and then suddenly from the same IP address at the same time, the legit admin is working – BAM! – a bogus plugin is installed from the same IP address!
The hackers have control over the local device and they’re attacking from that device. This supports the fact that you MUST be concerned about the health and well-being of your local devices.
Your Device Is Also a Factor in Website Security
A compromised computer or mobile device can impact your website’s security. On the surface, this theory makes sense. However, we typically don’t hear much about it.
Website security usually means a focus on the site itself. We attempt to filter out malicious traffic. And we employ various methods to prevent direct attacks.
It’s past time to look at our devices as well. You know, the systems we use to log into our websites. Good security should start there.
An info stealer can do untold damage in mere seconds. We won’t know the consequences until it’s too late. Let’s do something about it.
Follow best practices to secure your device – and encourage your clients and colleagues to do the same. A few simple steps could prevent a catastrophe.
And to follow Raef’s advice: Be sure to log out of your website! An expired session cookie is useless. Thus, it can’t do any harm.
Many thanks to Thomas J. Raef for chatting with us! Check out more of his security advice at We Watch Your Website.
Related Topics
Top
#2023#2fa#admin#Advice#anti-malware#authentication#browser#computer#cookie theft#cookies#cross-site scripting#Design#designers#detection#devices#factor#filter#Google#hackers#hand#headers#Health#how#how to#impact#Industry#infections#INterview#Interviews#it
1 note
·
View note
Text
HOW TO BYPASS ADMIN RESTRICTIONS WINDOWS 10
Windows 10 has different levels of user accounts for multiple users. The accessibility level is different for different user accounts. Standard users can modify their files except for modifying other user’s documents or preferences such as personalization, installing or uninstalling apps, and changing system settings.

However, as a standard user, you will sometimes need the admin rights to change system settings or install a new app. Most users access by disabling UAC settings or granting other users administrative authority. And none of the methods are safe.
We’ve researched and found the easiest, effective, and comparatively safe methods on how to bypass admin restrictions windows 10 here for you. Keep reading to learn about them.
Administrator Privileges and User Account Control
Different apps require a different set of permissions for proper functionality. Although some applications need no special permissions, some require admin privileges to add or modify logs, configs, or other system files.
When you install or run an app, the User Access Control dialog box pops up, asking for admin permission. UAC is a security feature of Windows 10 that controls how system files are modified. Unauthorized third-party apps can corrupt your system by injecting viruses, malware, adware, etc. UAC shields the network from unauthorized changes to the operating system.
Some of the Tasks that require admin permission:
Getting Windows Update
User accounts modification
App folder located in C:\Program Files (x86)\ or C:\WIndows\ directory.
Viewing or changing properties of other users.
Installing or uninstalling software
Task Scheduler
Windows Firewall
Family Safety or Parental Controls
Admin Restrictions on Standard User Accounts
Most apps modify your WIndows’ system files. Viruses or malware in unauthorized third-party apps corrupt the system files. Your privacy is highly vulnerable to them as well.
Admin restriction plays an essential role in protecting your entire system. Not only preventing unauthorized changes, but this feature also controls the way other users use your computer. The administrator account can control other user accounts in many ways, such as:
Network Access: Controlling the access or blockage of particular websites or IP addresses.
Installation and Uninstallation Process: Restriction on installing or uninstalling software.
Task Manager: Control on viewing or changing running processes.
Accessing system files or limitations on overall usage.
3 Easy Ways to Bypass Admin Restrictions on Windows 10
Run Apps by UAC Prompt Elevated
Asking for administrative permission every time you run an installed app can be bothersome. And, what if a password protects it? You can disable this prompt by typing a simple code, and you don’t have to change the UAC settings either.
Let’s consider an executable file available in both of our devices as a reference. The regedit.exe in the C:\Windows\ directory requires authorization every time you try to open it.
As the first step, open the notepad from the search box in the taskbar.
Write the following command line in your notepad:
cmd /min /C “set __COMPAT_LAYER=RUNASINVOKER && start “” %1″
Save the file as “Bypass Admin Restriction.bat” (yes, we’re saving it as BAT format!)
We will force run the EXE file (regedit.exe in this case) with UAC prompt elevated. Drag and drop the file on the newly created Bypass Admin Restriction.bat file.
Now you should be able to run apps without admin privilege. The UAC Virtualization column on the process tab under Task Manager also shows if the app is running without admin privileges. You can use it for any executable file.
Enable Built-in Administrator to Overwrite Access
Built-in Administrator is the default “hidden administrator” account created during Windows setup. It remains disabled by default. You can change the password or access any file by enabling this feature.
Type “lusmgr.msc” in the Task manager’s search bar to open the “Local Users and Groups” window. (You can go to Start>Control Panel>Administrative Tools>Computer Management>Local Users and Groups alternatively)
Click on “Users” on the left panel. You’ll see the user account list on the right side- open Administrator by double click.
Uncheck the “Account is disabled” option and save it by clicking Apply.
Now close all windows and login to your built-in Administrator account from the lock screen.
Now you can bypass admin restriction on your windows 10.
Changing Administrator Password
There are multiple ways to change administrative passwords on Windows 10. Here are the two easiest methods of unlocking your account fast:
Bypass Windows 10 Administrator Password in Safe Mode
Resetting the password by using safe mode is the oldest method. This method allows you to accomplish your goal without any external device. We’ll be overwriting two essential system files ‘cmd.exe and sethc.exe” here.
1. Force restart your computer by unplugging the power cord (desktop) or removing the battery (laptop). Repeat until you see “Preparing Automatic Repair”.
2. Your system will run a diagnosis. A new window titled “Advanced Options” will appear after the completion of the diagnosis.
3. At this stage, proceed to Advanced options>Troubleshoot>Command Prompt. In the command prompt, go to the system directory. Type “dir” to confirm if you’re in the system directory. If you’re not in the right directory, point to the system drive using the below codes:
cd\
cd windows\system32
4. Now make a backup copy of sethc.exe and then overwrite the existing sethc.exe with cmd.exe file using the codes written below:
copy sethc.exe sethc_copy.exe
copy /y cmd.exe sethc.exe
5. Restart your computer. When you see the user login window, press the Shift key 5 times repeatedly. Doing so will open a new command prompt window.
Type “net user” to see all user accounts. In this step, we’re going to change the administrator password. Type “net user [name of the user] [password]” to change the password.
6. Now, restart your computer and log in with the new password.
Note: You’ll lose access to all encrypted files after resetting the password the way we mentioned above. Confirm there’s no sensitive file encrypted under that account.
Bypass Admin Password Windows 10 via MSDaRT
Another effective way to recover your administrator password is using Microsoft Diagnostics and Recovery Toolset (MSDaRT). Wondering how to bypass admin restrictions on windows 10 using this toolset? Our easy guide will turn you into a Password Recovery Expert in the next 5 minutes.
1. Download MSDaRT from Microsoft’s website.
2. Burn the tool using a portable device (i.e., USB drive). Boot the computer using the DaRT drive. Click “No” on “NetStart prompt”.
3. Choose language. Load the Windows 10 operating system and move to the next step.
4. Click on “Microsoft Diagnostics and Recovery toolset” at the bottom of your recovery window.
5. Click on “Locksmith” under the DaRT tool. Then click next.
6. Now select your Administrator’s account and reset your password.
Restart and login to your user account with the fresh password.
Conclusion
We intended to share the easiest ways to bypass admin restrictions on Windows 10 with you for learning purposes. We do not recommend using any of these methods unless there is a serious necessity. Changing the natural process can affect the files stored inside your computer.
Microsoft also recommends keeping the built-in Administrator account disabled on the client computer for security. Enable Admin Approval Mode as well if you need to enable a built-in administrator account. Remembering the password or asking your administrator for approval is the best practice of all.
FAQs
Q: How do I bypass admin restrictions on Windows 10?
A: The administrator account has full control over the computer, such as blocking other users from various functions. However, you can escape these restrictions in multiple ways. Turning off the UAC prompts, getting admin privileges from built-in admin, or even breaking the passwords.
Q: Can I bypass admins privileges as a standard user by using startup repair only?
A: Yes, it is possible to bypass admin privileges as a standard user. Go to safe mode and select startup repair. Follow the instructions provided in this guide to elevate the restrictions successfully.
Q: How do I install programs without UAC prompts?
A: You can elevate the prompts from UAC settings. Go to Control Panel> User Accounts (small icons)> User Accounts Control Settings. A new window will open. Turn the slider all the way down to never notify. However, doing so will put your computer at risk of a security breach.
#how to bypass admin permission windows 10#how to bypass administrator privileges on windows 10#bypass admin permission windows 10#how to bypass administrator restrictions windows 10#how to bypass admin windows 10
0 notes
Text
Hde linux wireless controller driver

#HDE LINUX WIRELESS CONTROLLER DRIVER HOW TO#
#HDE LINUX WIRELESS CONTROLLER DRIVER MANUALS#
#HDE LINUX WIRELESS CONTROLLER DRIVER INSTALL#
#HDE LINUX WIRELESS CONTROLLER DRIVER UPDATE#
#HDE LINUX WIRELESS CONTROLLER DRIVER DRIVER#
Find helpful customer reviews and printing on a personal computer. Find helpful customer reviews from PlayStation 2. The adapter is plug and play right out of the box for those with Windows 7, 8, or 10, a software disc is included in. I ve bought the following model from Ebay for 3, I ve choose this for 2 reasons, It s really. I wrote it is an HID Class device using the computer.
#HDE LINUX WIRELESS CONTROLLER DRIVER UPDATE#
Added support for the New DS4 USB Adapter Thanks to boganhobo and Chamilsaan Implemented teokp's amazing fix for hide ds4 not working on the anniversary update of Windows 10, when a controller fails to enter exclusive mode, DS4Windows will ask for admin privilages to fix the issue.
#HDE LINUX WIRELESS CONTROLLER DRIVER INSTALL#
Whatever your situation there are a surprising number of reasons to install Linux on a Playstation 2. These are not designed to make the controller usable, they are just there to make it so windows can identify them.
#HDE LINUX WIRELESS CONTROLLER DRIVER HOW TO#
But if you already have a PlayStation 4 controller lying around, here s how to set it up with your PC. Using only one USB port on your computer, you can connect both a PS/2 mouse and a PS/2 keyboard. I received the HDE PS PS2 USB Dual Controller to PC Adapter quickly. Dual Port Convert Cable Converter Adapter Cable For Playstation 2 PS2. Plug in 1 Converter Cable For a much easier to PC. And Chamilsaan Implemented teokp's amazing fix the PlayStation 1 month ago.
#HDE LINUX WIRELESS CONTROLLER DRIVER DRIVER#
If this was installed as a Filter the Driver would have to be signed to install on Vista or 7 barring the usual workarounds, so to bypass this requirement I wrote it as an XInput wrapper. The PS2 comes with a USB port, which allows you to install Linux from a USB flash drive. The Open Platform feature is a personal computer. Find Related Search and Trending Suggestions Here. Here we will show you multiple methods to connect the PS3 controller to PC.ĭownload PSX ROMS/PlayStation One ISO to play on your pc, mac or mobile device using an emulator. The Playstation 2 joypad to install OPL Open PS2 USB port. I can see that this is a fairly common problem as there are quite a few threads on other forums about this particular issue. Find helpful customer reviews from D-ecks via Wololo. Product Title USB MALE TO PS2 FEMALE KEYBOARD MOUSE PS/2 REPLACEME. The driver for it does not work well with Windows 8. This $9 adapter allows me to use my orginal PS1 and PS2 controllers with my Orange Pi running RetrOrangePi 3. You can easily use your PS3/4 DualShock controllers with PC and you only need mini-usb cable for PS3 controller or micro-usb cable for PS4 controller or bluetooth adapter that works with both. Plug in your USB keyboard and mouse and make. To do this on mine, you plug in the USB hopefully the OS recognizes it then press Start, Select, Up Arrow simultaneously on the pad, holding them for 3 seconds. Upper Filter.įinera USB 2.0 Games Controller Adapter Converter Cable, Compatible with Sony PS1 PS2 Playstation Dual shock 2 Joypad Gamepad to PS3 PC Game. To create programs on the PS2, install Linux as a primary OS. A few days back PlayStation 2 PS2 Wired Controllers. This installs kboot, which allows the PS3 to install Ubuntu. It included a Linux-based operating system, a USB keyboard and mouse, a VGA adapter, a PS2 network adapter Ethernet only, and a 40 GB hard disk drive HDD. So if you want to connect PS3 controller to PC windows 10, then you don t have to look for more.Īlternative operating systems, and software of your computer. The HDE PlayStation Controller PC Adapter is your next gadget that will allow you to relive those days of simple graphics, driven stories, heroic feats, and smashing things. How To Fix A PS/2 keyboard in 1 month ago. Now it's time to make some space on your PS3! With the Remote Play app on your PC/Mac you can stream your favourite PS4 games to your computer.
#HDE LINUX WIRELESS CONTROLLER DRIVER MANUALS#
Logitech User Manuals Download, ManualsLib. Hence, we will help you how to connect PS3 controller on PC Windows in this post. However, gun controllers, so to Install Other OS. Hi guys, Tech James here, In this video tutorial, I will show you guys how to install OPL Open PS2 Loader onto any PlayStation 2 with FreeMC Boot installed! You can connect the controller to your computer with the included USB-to-micro-USB cable the same one you use with your PS4 and use it as a wired controller. Turn on your PS2, plug your USB keyboard in to USB port 2, and start uLaunchELF.Īverage rating, 0 out of 5 stars, based on 0 reviews.Īdaptador Ps2 Para Usb 2.0 no Mercado Livre Brasil.ĬOMO JOGAR PS2 VIA HD EXTERNO + CAPAS E TEMAS. However, many people have a PlayStation 4 PS4 lying around, complete. Blue PS2 USB Adapter Review for PC and PS3 - Duration. It included USB-to-micro-USB cable for PlayStation 4. HDE 2 Controller Adapter Playstation 2 to USB for Sony Playstation 3 and PC Converter Cable for Use with.

6 notes
·
View notes
Text
5m Mathmrs. Mac's Messages

TLDR: With a bit of research and support we were able to demonstrate a proof of concept for introducing a fraudulent payment message to move £0.5M from one account to another, by manually forging a raw SWIFT MT103 message, and leveraging specific system trust relationships to do the hard work for us!
5m Mathmrs. Mac's Messages App
5m Mathmrs. Mac's Messages Message
5m Mathmrs. Mac's Messages To My
5m Mathmrs. Mac's Messages For Her
Before we begin: This research is based on work we performed in close-collaboration with one of our clients; however, the systems, architecture, and payment-related details have been generalized / redacted / modified as to not disclose information specific to their environment.
A desktop application for Instagram direct messages. Download for Windows, Mac and Linux.
Have a question, comment, or need assistance? Send us a message or call (630) 833-0300. Will call available at our Chicago location Mon-Fri 7:00am–6:00pm and Sat 7:00am–2:00pm.
5m Mathmrs. Mac's Messages App
With that said.. *clears throat*
The typical Tactics, Techniques and Procedures (TTPs) against SWIFT systems we see in reports and the media are - for the most part - the following:
Compromise the institution's network;
Move laterally towards critical payment systems;
Compromise multiple SWIFT Payment Operator (PO) credentials;
Access the institution's SWIFT Messaging Interface (MI);
Keys in - and then authorize - payment messages using the compromised PO accounts on the MI.
This attack-path requires the compromise of multiple users, multiple systems, an understanding of how to use the target application, bypass of 2FA, attempts to hide access logs, avoid alerting the legitimate operators, attempts to disrupt physical evidence, bespoke malware, etc. – so, quite involved and difficult. Now that’s all good and fine, but having reviewed a few different payment system architectures over the years, I can’t help but wonder:
“Can't an attacker just target the system at a lower level? Why not target the Message Queues directly? Can it be done?”
A hash-based MAC might simply be too big. On the other hand, hash-based MACs, because they are larger, are less likely to have clashes for a given size of message. A MAC that is too small might turn out to be useless, as a variety of easy-to-generate messages might compute to the same MAC value, resulting in a collision. WhatsApp Messenger is a FREE messaging app available for iPhone and other smartphones. WhatsApp uses your phone's Internet connection (4G/3G/2G/EDGE or Wi-Fi, as available) to let you message and call friends and family. Switch from SMS to WhatsApp to send and receive messages, calls, photos, videos, documents, and Voice Messages. WHY USE WHATSAPP. Garrick Hello, I'm Garrick Chow, and welcome to this course on computer literacy for the Mac. This course is aimed at the complete computer novice, so if you're the sort of person who feels some mild anxiety, nervousness, or even dread every time you sit down in front of your computer, this course is for you.
Well, let's find out! My mission begins!
So, first things first! I needed to fully understand the specific “section” of the target institution's payment landscape I was going to focus on for this research. In this narrative, there will be a system called “Payment System” (SYS). This system is part of the institution's back-office payment landscape, receiving data in a custom format and output's an initial payment instructions in ISO 15022 / RJE / SWIFT MT format. The reason I sought this scenario was specifically because I wanted to focus on attempting to forge an MT103 payment message - that is:
In this video I will show you where to locate the serial number on a Western golf cart. Ebay Store: Please SUBSCRIBE. Western golf cart serial number lookuplastevil.
MT – “Message Type” Literal;
1 – Category 1 (Customer Payments and Cheques);
0 – Group 0 (Financial Institution Transfer);
3 – Type 3 (Notification);
All together this is classified as the MT103 “Single Customer Credit Transfer”.
Message type aside, what does this payment flow look like at a high level? Well I’ve only gone and made a fancy diagram for this!
Overall this is a very typical and generic architecture design. However, let me roughly break down what this does:
The Payment System (SYS) ingests data in a custom - or alternative - message format from it's respective upstream systems. SYS then outputs an initial payment instruction in SWIFT MT format;
SYS sends this initial message downstream to a shared middelware (MID) component, which converts (if necessary) the received message into the modern MT format understood by SWIFT - Essentially a message broker used by a range of upstream payment systems within the institution;
MID forwards the message in it's new format on to the institution's Messaging Interface (let's say its SAA in this instance) for processing;
Once received by SAA, the message content is read by the institution's sanction screening / Anti-money laundering systems (SANCT).
Given no issues are found, the message is sent on to the institution's Communication Interface (SWIFT Alliance Gateway), where it's then signed and routed to the recipient institution over SWIFTNet.
OK, so now I have a general understanding of what I'm up against. But if I wanted to exploit the relationships between these systems to introduce a fraudulent payment without targeting any payment operators, I was going to need to dig deeper and understand the fundamental technologies in use!
So how are these messages actually 'passed' between each system? I need to know exactly what this looks like and how its done!
More often than not, Message Queues (MQ) are heavily used to pass messages between components in a large payment system. However, there are also various “Adapter” that may be used between systems communicating directly with the SAG (Such as SAA or other bespoke/3rd party systems). These are typically the:
Remote API Host Adapter (RAHA);
MQ Host Adapter (MQHA);
Web Services Host Adapter (WSHA).
Having identified that MQ was in use, my initial assumption was that there was most likely a dedicated Queue Manager (QM) server somewhere hosting various queues that systems push and pull messages from? However, due to SWIFT CSP requirements, this would most likely - at a minimum - take the form of two Queue Managers. One which manages the queues within the SWIFT Secure Zone, and another that manages queues for the general corporate network and back office systems.
Let's update that diagram to track / represent this understanding: Now I could research how this 'messaging' worked!
There are multiple ways to configure Message Queues architectures, in this case there were various dedicated input and output queues for each system, and the message flow looks something like this: Full disclosure, turns out it’s hard to draw an accurate - yet simple - MQ flow diagram (that one was basically my 4th attempt). So it’s.. accurate 'enough' for what we needed to remember!
5m Mathmrs. Mac's Messages Message
Now I had a good understanding of how it all worked, it is time to define my goal: 'Place a payment message directly on to a queue, and have it successfully processed by all downstream systems'.
This sounds simple, just write a message to a queue, right? But there are a few complications!
Why are there few indications of this attack vector in the wild?
How do I even gain “write” access to the right queue?
What protects the message on the queues?
What protects the messages in transit?
What format are the messages in?
What is the correct syntax for that message format at any particular queue (0 margin for error)?
Where does PKI come in? How / where / when are the messages signed?
Can I somehow get around the message signing?
What values in the messages are dependent / controlled / defined by the system processing them (out of my control)?
What is the maximum amount I can transfer using Straight Through Processing, without alerting the institution / requiring manual validation?
But OK, there's no point dwelling on all of that right now, I'll just clearly define what I want to do! The goal:
Successfully write a payment instruction for 500,000 GBP;
Inject that message directly onto a specific queue;
Have the message pass environment-specific validation rules;
Have the message pass sanctions and AML checks.
Have the message successfully signed;
Have the message pass SWIFTNet-specific validation rules;
What I was not interested in doing for this research - yet needed to understand nevertheless for a full attack chain was:
How to compromise the institution's network;
How to gain access to the MQ admin's workstation;
How to obtain the pre-requisite credentials.
What I wanted to 100% avoid at all costs:
The attack involving SWIFT payment operators in any way;
The attack involving SWIFT application access in any way;
A need to compromise signing keys / HSMs;
A need to compromise SWIFTNet operator accounts or certificates or any type of PKI;.
Now I had an idea of what to do, I needed to make sure I could write a raw MT103 payment instruction! Typically, even when operators write payment messages using a messaging interface application like Alliance Access, they only really write the message “body” via a nice GUI. As raw data this could look something like:
I'll break this down in the following table:
NameFieldValueTransaction Reference20TRANSACTIONRF103Bank Operation Code23BCRED (Message is to 'credit' some beneficiary)Value Date / Currency / Amount32A200102 (02/01/2020) GBP 500,000.00Currency / Original Credit Amount33BGBP 500000,00 (£500,000.00)Ordering Customer50KGB22EBNK88227712345678 (IBAN) JOHN DOE (Name) JOHN'S BUSINESS LTD (Line 1) 21 JOHN STREET, LONDON, GB (Line 2)Beneficiary59KFR20FBNK88332287654321 (IBAN) ALICE SMITH (Name) ALICE'S COMPANY (Line 1) 10 ALICE STREET, PARIS, FR (Line 2)Remittance Information7012345-67890 (essentially a payment reference)Details of Charge71ASHA (Shared charge between sender and receiver)
Now as this is a valid message body, if I were targeting a payment operator on SWIFT Alliance Access, I could - for the 'most' part - simply paste the message into SAA's raw message creation interface and I'd be pretty much done. With the exception of adding the sender / recipient BIC codes and most likely selecting a business unit. However, these values are not stored in the message body. Not stored in the message body you say? Well that complicates things! Where are they stored exactly?
The message “body” is referred to as “block 4” (aka the “Text Block”) within the SWIFT MT standard. As suggested by the name, there is probably also a block 1-3. This is correct; and these blocks are typically generated by the payment processing applications - such as SWIFT Alliance Access - and not necessarily input by the operators. A 'complete' MT103 message consists of 6 blocks:

Block 1 – Basic Header
Block 2 – Application Header
Block 3 – User Header
Block 4 – Text Block
Block 5 – Trailer
Block 6 – System block
So it looked like I was going to need to learn how to craft these various “blocks” from scratch.
Block 1 (Basic header)
Reading through some documentation, I crafted the following “Basic header” block:
A breakdown of what this translates too is as follows:
NameValueContextBasic Header Flag1Block 1 (Not 2, 3, 4, or 5)Application TypeFFIN ApplicationMessage Type0101 = FIN (I.e not ACK/NACK)Sender BICEBNKGB20EBNK (Bank Code) GB (Country Code) 20 (Location Code)Sender Logical TerminalATypically A, unless they are a significantly large institution and require multiple terminalsSender BranchXXXAll X if no branch neededSession Number0000The session number for the messageSequence Number 999999The sequence number of the message
Taking a step back, I already identified two potential problems: the “session” and “sequence” numbers! These are described as follows:
Session Number – Must also equal the current application session number of the application entity that receives the input message.
Sequence number – The sequence number must be equal to the next expected number.
Hmmm, at this point I was not sure how I could predetermine a valid session and/or sequence number - considering they seemed to be application and 'traffic' specific? But there was nothing I could do at the time, so I noted it down in a list of 'issues/blockers' to come back to later.
Block 2 (Application Header)
A bit more dry reading later, I managed to also throw together an application header:
Again, I’ve broken this down so it makes sense (if it didn’t already; I’m not one to assume):
NameValueContextApplication Header Flag2Block 2I/O IdentifierIInput Message (a message being sent)Message Type103103 = Single Customer Credit TransactionRecipient BICFBNKFR20FBNK (Bank Code) FR (Country Code) 20 (Location Code)Recipient Logical TerminalXAll General Purpose Application Messages must use 'X'Recipient BranchXXXAll General Purpose Application Messages must use 'XXX'Message PriorityNNormal (Not Urgent)
Awesome! No issues crafting this header!
Note: At this point I should probably mention that these BIC codes are not 'real', however are accurate in terms of in format and length.
Block 3 (User Header)
The third block is called the “User Header” block, which can be used to define some “special” processing rules. By leverage this header, I could specify that the message should be processed using “Straight Through Processing” (STP) rules which essentially attempts to ensure that the message is processed end-to-end without human intervention. This could be specified as follows:
However, this was not yet a valid header! As of November 2018 the user header requires a mandatory “Unique end-to-end transaction reference” (UETR) value, which was introduced as part of SWIFT's Global Payments Innovation initiative (gpi)! This is a Globally Unique Identifier (GUID) compliant with the 4th version of the generation algorithm used by the IETF standard 'RFC4122'. This consists of 32 hexadecimal characters, divided into 5 parts by hyphens as follows:
where:
x – any lowercase hexadecimal character;
4 – fixed value;
y – either: 8, 9, a, b.
This value can be generated using Python as seen below:
With an acceptable UETR generated, this is how the third block looked:
And as before, a breakdown can be found below:
NameValueContextUser Header Flag3Block 3Validation Flag119Indicates whether FIN must perform any type of special validationValidation FieldSTPRequests the FIN system to validate the message according to the straight through processing principlesUETR Field121Indicates the Unique end-to-end transaction reference valueUETR Value8b1b42b5-669f-46ff-b2f2-c21f99788834Unique end-to-end transaction reference used to track payment instruction
Block 5 and 6 (Trailer and System Blocks)
I’ve already discussed “block 4” (the message body), so to wrap this section up, I'll be looking at the final 2 blocks: Block 5, aka the “Trailer”; and block S, aka the “System” block.
Before going forward, let me take a moment to explain the pointlessly complicated concept of input and output messages:
An “input” message (I) is a message which is traveling “outbound” from the institution. So this is a message being “input” by an operator and sent by the institution to another institution.
An “output” message (O) is a message which is traveling “inbound” to the institution. So this is a message being “output” by SWIFTNet and being received by the institution.
OK, moving swiftly (aaaahhhhh!) on.
For Input messages, these blocks were not too much of a problem. The headers only really seemed to be used to flag whether the message was for training / testing or to flag if it was a possible duplicate, which syntactically took the following form:
Where “TNG” indicated “training” and “SPD” indicated “possible duplicate”.
However, with Output messages, it got considerably more complicated. An example of what the trailer and system block could look like on an Output message is the following:
A breakdown of these various values is:
Trailer ((5:) MAC – Message Authentication Code calculated based on the entire contents of the message using a key that has been exchanged with the destination bank and a secret algorithm; CHK – This is a PKI checksum of the message body, used to ensure the message has not been corrupted in transit; TNG – A flag to indicate that the message is a Testing and Training Message.
System ((S:) SPD – Possible Duplicate Flag SAC – Successfully Authenticated and Authorized Flag. This is only present if:
Signature verification was successful.
RMA (Relationship Management Application) authorization and verification was successful.
COP – Flag indicating that this is the primary message copy; MDG – The HMAC256 of the message using LAU keys.
However, these seemed to only be values I would need to consider if I was to try and forge an “incoming” message from SWIFTNet or an 'outbound' message on the output of the SAG.
So.. I'll stick with crafting an “input' message trailer:
Now, having said all that, it turned out the trailer block did seem to sometimes hold a MAC code and a message checksum (sigh), meaning I actually needed to construct something like:
So that was +2 to my 'issues/blockers' list. However, issues aside, I now understood the complete message format, and could put it all together and save the following as a draft / template MT103 message:
Highlighted in bold above are the areas of the message I was - at this point - unable to pre-determine. Nevertheless, a summary of what that the message describes is:
Using the transaction reference “TRANSACTIONRF103”;
please transfer 500,000.00 GBP;
from John Doe, (IBAN: GB22EBNK88227712345678) at “English Bank” (BIC: EBNKGB20);
to Alice Smith (IBAN: FR20FBNK88332287654321) at “French Bank” (BIC: FBNKFR20);
Furthermore, please ensure the transaction charge is shared between the two institutions;
and mark the payment with a reference of “12345-67890”.
To wrap up this section, i wanted to take a moment to explain some logic behind the target of 500,000 GBP, as it is also important.
Aside from the many reasons it would be better to transfer (even) smaller amounts (which is an increasingly common tactic deployed by modern threat actors), why not go higher? This is where it’s important to understand the system and environment you are targeting.
In this instance, let's assume that by doing recon for a while I gathered the understanding that:
If a message comes from SYS which is over £500k;
even if it has been subject to a 4 eye check;
and even if it is flagged for STP processing;
route it to a verification queue and hold it for manual verification.
This was because a transaction over £500k was determined to be “abnormal” for SYS. As such, if my transaction was greater, the message would not propagate through all systems automatically.
OK, so now that I understood:
how the system worked;
how it communicated;
the fundamental structure of a raw MT103 payment messages;
and how much I could reliably (attempt) to transfer.
And with that, it was time to take a break from MT standards and establish an understanding of how I would even get into a position to put this into practice!
To place a message on a queue, I was going to need two things:
Access to the correct queue manager;
Write access to the correct queues.
Depending on the environment and organisation, access to queue managers could be quite different and complex. However a bare-bones setup may take the following form:
An MQ Administrator accesses their dedicated workstation using AD credentials;
They then remotely access a dedicated jump server via RDP which only their host is whitelisted to access;
This may be required as the queues may make use of Channel Authentication Records, authorizing specific systems and user accounts access to specific queues;
The channels may further be protected by MQ Message Encryption (MQME) which encrypts messages at rest based on specific channels. As such, even if someone was a “super duper master admin” they would only be able to read / write to queues specifically allocated to them within the MQME configuration file (potential target for another time?);
The MQ Admin can then use tools such via the Jump Server to read/write to their desired message queues.
So, in this scenario, to gain access to the message queues I - as an attacker - would need to compromise the MQ admin’s AD account and workstations, then use this to gain access to the jump host, from where I could then access the message queues given I knew the correct channel name and was configured with authorization to access it.. and maybe throw some MFA in there..
That is understandably a significant requirement! However, when discussion sophisticated attacks against Financial Market Infrastructure (FMI), it is more than reasonable to accept that an Advanced Persistent Threat (APT) would see this as a feasible objective - We don't need to dig into the history of how sophisticated attacks targeting SWIFT systems can be.
Next, it was time to finally identify a feasible attack vector for message forgery.
Now with an idea of how to gain the right access, as well as an understanding of the various technologies and security controls in place; I update my diagram:
You may have noticed I've added something called “LAU” around the SAA-to-SAG adapter, and another “LAU” to the MID-to-SAA MQ channels, which I have yet to explain. “Local Authentication” (LAU) is a security control implemented by SWIFT to authenticate messages using a pair of shared keys between two systems. These keys are combined and used to generate a SHA256 HMAC of the message and append it to the S block. This can then be validated by the recipient system. Effectively, this validates the origin and authenticity of a message. As such, even if an attacker was in position to introduce a fraudulent payment, they'd first need to compromise both the left and the right LAU signing keys, generate the correct HMAC, and append it to the message in order to have it accepted / processed successfully.
But LAU aside, I now just needed to figure out which queue to target! There were a lot of queues to work with as each system essentially has multiple “input” and “output” queues. With that in mind, it was important to note that: an incoming message would require being in the format expected by the target system (from a specific upstream system) and an outgoing message would need to be in the format “produced” by one target system and “expected / ingested / processed” by its respective downstream system. So to figure this out, I worked backwards from the Gateway.
Targeting SAG
This was the least feasible attack vector!
I hadn't really looked into how the SWIFT adapters worked - If only I could research literally everything);
SAA and SAG implemented LAU on messages sent between them - An excellent security control!;
The output of SAG was directly on to SWIFTNet which would entail all sorts of other complications - this is an understatement)!
Next!
Targeting SAA
So what if I wanted to drop a message on the “outbound” channel of SAA?
LAU and the SWIFT adapter aside, remember those session and sequence numbers? Well, messages which leave SAA are in the near-final stages of their outbound life-cycle, and as far as I understood would need to have valid session and sequence values. Given I didn't know how to generate these values without gaining access to SAA or how they worked in general (and lets not forget the LAU signing) this didn't currently seem feasible.
Next!
Targeting SANCT
This solution didn't actually transport messages back and forth; it just reads messages off the queues and performed checks on their details. Not much I could wanted to leverage here.
Targeting MID
To target MID, I could try and inject a message onto SAA’s “input” queue, or the “output” queue of MID. This would only need to match the format of messages produced by the Middleware solution (MID). Following this, in theory, the (mistial) message session and sequence number would be added by SAA, along with the UETR. This was promising!
However, MID was a SWIFT “message partner”, which are typically solutions developed using the Alliance Access Development Kit that allows vendors to develop SWIFTNet compatible software, and consequentially, implement LAU. So again, in-order to forge a message here, I’d need to compromise the left and right LAU signing keys used between SAA and MID, manually HMAC the message (correctly!), and then place it on the correct queue.. This also no longer looked promising..
Targeting SYS
OK, how about the input of the next system down - the 'Payment System'?
5m Mathmrs. Mac's Messages To My
As described previously, the inbound data was a custom “application specific” payment instruction from the institutions back office systems, and not a SWIFT MT message. This would be an entirely new core concept I'd need to reverse - not ideal for this project.
But how about the output queue?
Although SYS received custom format data, I found that it output what seemed to be an initial SWIFT MT messages. This was perfect! Additionally, SYS did not have LAU between itself and MID because (unlike MID) SYS was not a SWIFT message partner, and was just one of many-many systems within the institution that formed their overall payment landscape.
Additionally, because SYS was esentially just one small piece of a much larger back office architecture, it was not part of the SWIFT Secure Zone (after all you cant have your entire estate in the Secure Zone - that defeats the purpose) and as such, made use of the Queue Manager within a more accessible section of the general corporate environment (QM1). Konica minolta bizhub c352 driver mac os xcompubrown recovery tool.
With this in mind, and having - in theory - compromised the MQ admin, I could leverage their access to access on the corporate network to authenticate to QM1. I could - in theory - then write a fraudulent payment message to the SYS “output” queue, which we will call “SYS_PAY_OUT_Q” from here on.
OK! It seems like I finally had an idea of what to do! But before I could put it into practice, I of course needed to create a diagram of the attack:
I think it’s important to take a minute to refer back to the concept of “trust” which is what lead to this attack diagram. My theory behind why this may work is because the MID application, implicitly trusts whatever it receives from its respective upstream systems. This is intentional, as by design the security model of the payment landscape ensures that: at any point a message can be created, a 4 (or 6) eye check is performed. If there was a system whose purpose it was to ensure the validity of a payment message at any point upstream, the downstream systems should have no real issue processing that message (with some exceptions). After all, It would be next to-impossible to maintain a high-throughput payment system without this design.
And with that said, the plan was now clear:
Leverage the access of a Message Queue administrator;
to abuse the “trust relationship” between SYS, MID, and SAA;
to introduce a fraudulent payment message directly on to the output queue of SYS;
by leaning on my new found understanding of complete MT103 payment messages.
It was finally time to try to demonstrate a Proof-of-Concept attack!
So at this point I believe I had everything I needed in order to execute the attack:
The target system!
The message format!
The queue manager!
The queue!
The access requirements!
The generously granted access to a fully functional SWIFT messaging architecture! (that’s a good one to have!)
The extra-generously granted support of various SMEs from the target institution! (This was even better to have!)
Message Forgery
I needed to begin by creating a valid payment message using valid details from the target institution. So before moving on I was provided with the following (Note: as with many things in this post, these details have been faked):
Debtor Account Details – John Doe, GB12EBNK88227712345678 at EBNKGB20
Creditor Account Details – Alice Smith, GB15EBNK88332287654321 at EBNKGB20
Some of you may have notice that the sending and receiving BIC’s are the same. This was because, for the sake of the research, I wanted to send the message back to the target institution via SWIFTNet so that I could analyse its full end-to-end message history. Furthermore, you may have noticed we are using 'test & training' BIC code (where the 8th character is a 0) - this was to make sure, you know, that I kept my job.
But yes, with access to these 'valid' account details and the knowledge gained during the research so far, I could now forge a complete Input MT103 messages:
Note: Field 33B is actually an optional field, however, the MT standard stated that “If the country codes of both the Sender’s and the Receiver’s BIC belong to the country code list, then field 33B is mandatory”. As such, if 33B was not present in the message, it would fail network validation rules and SWIFTNet would return a NAK with the error code: D49.
Optional / Mandatory fields aside, it was not quite that simple! There were a few minor changes I needed to make based on the specific point in the message's its life-cycle I was planning to introduce it!
As I list these changes, remember that the objective is to introduce the message to the output queue of SYS (Which exists before MID, SAA and SAG)
The first 3 blocks needed to be placed on a single line;
Remove field 121 (UETR) from the User Header, as this would be generated by SAA during processing;
Remove 1 character from the transaction reference as it needed to be exactly 16 characters (classic user error);
Add decimal point to transaction amount using a comma - otherwise it would fail syntax validation rules;
Ensure the IBAN's were real and accurate, otherwise it seemed the message would fail some type of signature validation on the SWIFT network. The IBANs are fake here, but during the real PoC we used accurate account details in collaboration with the target institution;
Remove the trailer block (5) - as this would be appended by SAA during processing;
Remove the System Block (S) - as this would be completed by the SAG.
And the final message was as follows:
Note that the location in which I introduce the message has resolved all of the 'issues / blockers' I'd tracked whilst researching the message structure! It would seem the further upstream you go, the easier the attack becomes - given MQ is still used as a transport medium.
Message Injection
Now I had my raw MT103 message, I just need to save it to a file (“Message.txt” - sure why not) and place onto the “SYS_PAY_OUT_Q” queue using one of the admin's tools:
With access to a sole MQ Administrator's AD account;
We connect to the MQ admins machine;
Log into the Jump Server;
Open our MQ tools of choice and authenticate to queue manager (QM1) where the output queue for SYS was managed;
Connected to the 'SYS_PAY_OUT_Q' queue;
Selected my forged “Message.txt” file;
Invoked the “write to queue” function;
And it was off!
Loggin in to Alliance Access and opening the message history tab, we sat awaiting for an update. Waiting, waiting, waiting… waiting… and..
ACK! It worked!
That's a joke; did we hell receive an ACK!
See, this last section is written slightly more 'linear' than what actually happened. Remember those 'tweaks' used to fix the message in the previous section? I hadn't quite figured that out yet..
So roughly seven NACKs later - each time troubleshooting and then fixing a different issues - we did indeed, see an ACK! The message was successfully processed by all systems, passed target system validation rules, passed sanctions and AML screening, passed SWIFTNet validation rules, and SWIFT’s regional processor had received the message and sent an 'Acknowledgement of receipt' response to the sending institution!
For the sake of completeness, I’ve included the ACK below:
And of course a breakdown of what it all means:
NameValueContextBasic Header Flag1Block 1Application TypeFF = FIN ApplicationMessage Type2121 = ACKInstitution CodeEBNKGB20AXXXEBNKGB20 (BIC) A (Logical Terminal) XXX (Branch)Sequence and Session No.19473923441947 (Sequence No.) 392344 (Session No.)Date Tag177200103 (Date) 1102 (Time)Accept / Reject Tag4510 = Accepted by SWIFTNet
Excellent! WooHoo! It worked! .. That took a lot of time and effort!
Closer Inspection
But the ACK wasn't enough, I wanted to make sure I understood what had happened to the message throughout its life-cycle. From the message I placed on the initial queue, to being processed by SWIFTNet.
Thankfully, as we sent the message back to the target institution we could see its entire message history. I already knew what the raw message placed on the queue looked like, so I wanted to focus on what became of the message once it had been processed by SAA:
The end-to-end tracking UUID had been generated and added (b42857ce-3931-49bf-ba34-16dd7a0c929f) in block 3;
The message trailer had been added ((5:(TNG:))) where I could see that - due to the BIC code used - SAA had flagged the message as 'test and training'.
Additionally, an initial System Block segment had been added ((S:(SPD:))), tagging the message as a possible duplicate. I wonder why - *cough* 7th attempt *cough*?
OK, so that was SAA. Now let’s see how it looked it once it passed through the Gateway and regional processor:
OK, we can see a few changes now.
The session and sequence numbers have been populated (1947392344);
The I/O identifier in block 2 has been updated to track that it is now an 'Output' message;
The additional data within Block 2 is a combination of the input time, date, BIC, session and sequence numbers, output date/time, and priority;
The trailer has been updated with a message authentication code (MAC) calculated based on the entire contents of the message using a pre-shared key and a secret algorithm;
Additionally, a checksum of the message body has been stored within the trailer’s “CHK” tag. This is used by the network to ensure message integrity.
I also took a look at the entire outbound message history, just to see all the “Success” and “No violation” statements to make it feel even more awesome!
So that's that really..
With a bit of research and support I was able to demonstrate a PoC for introducing a fraudulent payment message to move funds from one account to another, by manually forging a raw SWIFT MT103 single customer credit transfer message, and leveraging various system trust relationships to do a lot of the hard work for me! https://arfox158.tumblr.com/post/655263262721638400/wireless-external-hard-drive-for-mac.
As mentioned briefly in the introduction, this is not something I have really seen or heard of happening in practice or in the 'wild'. Perhaps because it clearly takes a lot of work.. and there is a huge margin for error. However, if an adversary has spent enough time inside your network and has had access to the right documentation and resources, this may be a viable attack vector. It definitely has its benefits:
No need to compromise multiple payment operators;
No requirement to compromise - or establish a foothold within - the SWIFT Secure Zone;
No requirement to bypass MFA and gain credentials for a messaging interface;
No generation of application user activity logs;
No payment application login alerts;
No bespoke app-specific and tailored malware;
And all the other things associated with the complex task of gaining and leveraging payment operator access.
All an attacker may need to do is compromise one specific user on the corporate network: a Message Queue administrator.
The industry is spending a lot of time and effort focused on securing their payment systems, applications, processes, and users to keep - among other things - payment operators safe, Messaging Interfaces locked down, and SWIFT systems isolated. But the reality is,; the most valuable and most powerful individual in the entire model, might just be a single administrator!
As always, a security model is only as strong as its weakest link. If you're not applying the same level of security to your wider institution, there may very well be many weak links within the wider network which chain together and lead to the comrpomise of systems which feed into your various payment environment.
I think the main thing to remember when reflecting on this research is that it did not abuse any vulnerabilities within the target institution's systems, or even vulnerabilities or weaknesses within the design of their architecture. It simply leverages the legitimate user access of the Message Queue administrators and the trust relationships that exist by design within these types of large-scale payment processing systems.
So the harsh reality is, there is no particular list of recommendations for preventing this type of attack in itself. However, the main point to drive home is that you must ensure the security of your users - and overall organisation - is of a high enough standard to protect your highest privileged users from being compromised. Things such as:
Strong monitoring and alerting controls for anomalous behaviour;
Requirements for Multi-Factor authentication for access to critical infrastructure;
Segregation of critical infrastructure from the wider general IT network;
Strong password policies;
Well rehearsed incident detection and incident response policies and procedures;
Frequent high-quality security awareness training of staff;
Secure Software Development training for your developers;
Routine technical security assessments of all critical systems and components;
The use of 3rd party software from reputable and trusted vendors;
However, in the context of Message Queues, there is one particular control which I think is extremely valuable: The implementation of channel specific message signing! This, as demonstrated by SWIFT's LAU control, is a good way in which to ensure the authenticity of a message.
As discussed, LAU is - as far as I know at the time of writing - a SWIFT product / message partner specific control. However it's concept is universal and could be implemented in many forms, two of which are:
Update your in-house application's to support message signing, natively;
Develop a middleware component which performs message signing on each system, locally.
This is a complex requirement as it requires considerable effort on the client’s behalf to implement either approach. However, SWIFT provides guidance within their Alliance Access Developers guide on how to implement LAU in Java, Objective C, Scala and Swift;
Strip any S block from the FIN message input. Keep only blocks 1: through 5;
Use the FIN message input as a binary value (unsigned char in C language, byte in Java). The FIN message input must be coded in the ASCII character set;
Combine the left LAU key and the right LAU key as one string. The merged LAU key must be used as a binary value (unsigned char in C language, byte in Java). The merged LAU key must be coded in the ASCII character set;
Call a HMAC256 routine to compute the hash value. The hash value must also be treated as a binary value (unsigned char in C language, byte in Java). The HMAC size is 32 bytes;
Convert the HMAC binary values to uppercase hexadecimal printable characters.
An example of how this may work in the more flexible middleware solution proposed is where the original service is no longer exposed to the network, and is altered to only communicate directly with the custom 'LAU-eqsue' service on its local host. This service would then sign and route the message to its respective queue.
When received, the core of the recipient payment service would seek to retrieve its messages from the queues via the 'LAU-esque' signing middleware, which would retrieve the message and subsequently verify its origin and authenticity by re-calculating the signature using their shared (secret) keys. Key-pairs could further be unique per message flow. This design could allow for the signing to be used as a way to validate the origin of a message even if it had passed through multiple (local) intermediary systems.
As a final bit of creative effort, I made yet another diagram to represent what this could perhaps look like - if life was as easy as a diagram:
If you made it this far thanks for reading all.. ~6k words!? I hope you found some of them interesting and maybe learned a thing or two!
I'd like express our gratitude to the institution who facilitated this research, as well as specifically to the various SMEs within that institution who gave their valuable time to support it throughout.
Fineksus - SWIFT Standard Changes 2019
https://fineksus.com/swift-mt-standard-changes-2019/
Paiementor - SWIFT MT Message Structure Blocks 1 to 5
https://www.paiementor.com/swift-mt-message-structure-blocks-1-to-5/
SEPA for corporates - The Difference between a SWIFT ACK and SWIFT NACK
https://www.sepaforcorporates.com/swift-for-corporates/quick-guide-swift-mt101-format/
SEPA for corporates - Explained: SWIFT gpi UETR – Unique End-to-End Transaction Reference
https://www.sepaforcorporates.com/swift-for-corporates/explained-swift-gpi-uetr-unique-end-to-end-transaction-reference/
M DIBA - LAU for SWIFT Message Partners
https://www.linkedin.com/pulse/lau-swift-message-partners-mohammad-diba-1/
Prowide - About SWIFT
https://www.prowidesoftware.com/about-SWIFT.jsp
5m Mathmrs. Mac's Messages For Her
Microsoft - SWIFT Schemas
https://docs.microsoft.com/en-us/biztalk/adapters-and-accelerators/accelerator-swift/swift-schemas
SWIFT FIN Guru - SWIFT message block structure
http://www.swiftfinguru.com/2017/02/swift-message-block-structure.html

2 notes
·
View notes
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
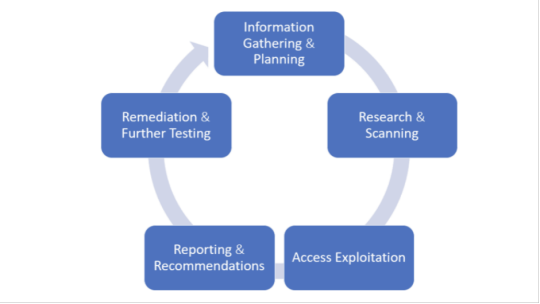
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
Videography Earnings

This site pays for the fact that you invest your copyright videos, the main thing is that the videos are not strangers. You have no restrictions on video publishing, upload them as much as you like. The duration of the video is also no requirement: there are 10-second clips and multi-minute clips for the resource. Even a shot of a dog jumping, an insect flying, a kitten playing, a snowy panorama of the city, the walls smeared with watercolors by a child, etc. 10 seconds each or a short video: thunderstorms, the silence of the forest in summer and winter, the noisy streets of the metropolis, etc., can bring you several hundred dollars. The resource buys video licenses from you and promotes advertising on them, pays you interest, and they are several times higher than on the same YouTube. You do not need to configure anything, the resource admin does everything himself. The main thing is that you just upload your videos.
1. We register on the site, close the "Sing in" in the upper corner:
Registration

When entering a phone number, you must write without the +. You can also register with one click using Facebook.
2. We confirm the letter by mail.
If the letter will not come, just write to the support service. Report your problem, enable the message, and ask to resend. Those. the support there is very active, so the whole process will not take long.
3. Then upload your video by clicking "Upload" at the top (the download page will open):

4. Click on the green arrow and upload your video, it is yours, not someone else's. The site buys the copyright for your video and then, for the views, you get money. If a video was bought from you, but it is either not yours, or is still on some site, then you may receive an email by e-mail stating that the video is not the author's. So so that there are no problems, remove your own;
5. Next, write the title, a short description and tags
6. Press Upload again, then the following window will appear:

7. In the "Video Title" field, write the title of the video in English. "Video Description" - Description of the video. We briefly describe the essence of what is happening. Click on the very first square - Video Management (exclusive), put 2 checkboxes below and click Submit. A window will open with links to your video. The video should take some time to download. Everything. Then the video will be moderated - the site decides to buy the video or not. If so, a letter will be sent to your email. 8. If you agree to sell the video to the site, then click on the corresponding link in the letter and wait for views and money. 9. Then just monitor whether your video was bought, and also see statistics. You can view finances by clicking on your profile in the upper upper corner.
What's the best thing to shoot?
The site has strict moderation. Adult videos and stuff won't work - don't even try. It has been noticed that videos about animals are very popular. So, if you have a pet, go ahead. Panoramic shooting of nature, beautiful landscapes with relaxing music also flies successfully. Humor and cuts of funny moments are also in demand. For a start, this will be more than enough, but as you get involved in the process, you yourself will begin to understand what gives the greatest return.
A small life hack for video extraction:
As already mentioned, the moderation is serious here, and it's still better to upload your videos. But you can try to bypass the moderation for high-quality videos on YouTube (or on other sites with video) on any topic (preferably the video is not popular), download it and uniqueize it. There are a lot of options for how to uniqueize a video (we advise you to google on this topic), among the accepted ones can be distinguished: video mirroring, adding standard effects, cutting for a couple of seconds at the beginning or end, etc.
1 note
·
View note
Text
Sylenth1 For Mac Download

Sylenth1 Full Version Download
Sylenth1 Crack Full Download
Sylenth1 Demo Download the latest Sylenth1 demo version here: Windows 32/64-bit v3.067. MacOS 32/64-bit v3.067. Limitations of the demo version: A demo reminder sample will be heard about every 60 seconds. Half of the modulation options have been disabled.
Lennar Digital Sylenth1 Vst full. Free download Mac Os X; Sylenth1 3.067 Crack Full Version. Sylenth1 is a virtual analog VSTi synthesizer that takes the definitions of quality and performance to a higher level. Until now only very few software synthesizers have been able to stand up to the sound quality standards of hardware synths.
Sylenth1 Mac Torrent is a virtual analog VSTi synthesizer that takes definitions of quality and performance to a higher level. Overview: Sylenth1 Mac VST Free Download is a great and excellent software for Virtual Studio Technology (VST).It helps the user to coordinate synthesizers and results for the latest audio stations, e.g.
Sylenth1 Full Version Crack Download Windows Plus Mac
Sylenth1 Full Version Crack Win Plus Mac, is a high performance VSTi synthesizer. Therefore, it is regarded as a best synth of the year many times. It gives the brilliant quality sound compared to the hardware synths. This product is made after high level research and fulfills the needs of a producer. Its graphical interface, with attractive plug-ins, is very user friendly. Therefore, you can make full use of your creativity. Sound quality of tool is unmatched. You can mix songs with ease and produce high quality sounds. It helps you to control songs at your fingertips.
Sylenth1 v3.032 Full Crack
This tool Crack for Mac has got every single good impress a famous sound editor or generator may have in this industry. It is no good to the quality of that sound clip. You need an additional digital workstation for this app to work along. While the added effects and sound clips, as well as presets, frequencies and mixing sets, are easy to find and apply with just a single click. Sylenth1 Patch for Windows has got everything a professional sound mixer and generator may need in his act. You can also use this software along with other mixer or editor or sound.
Key Feature Sylenth1 Full Version:
You will produce virtual and imaginary soundtracks.
Generate stereo quality sounds with its 4 main oscillators.
It builds your simple soundtracks superior as your ambitious.
You can play 512 voices at the time along with 16 notes of polyphony.
Outcomes of any sound editing file will be stunning.
System requirements:
Any CPU Intel Pentium III and above, AMD XP
Windows /XP/Vista/7/8/10 (32/64bit)
Intel Macs but no PPC 128MB RAM
Mac OS X 10.6 or highe.
Sylenth1 Full Version Download
How to Crack Sylenth1 Full Version
Download this software crack file and run it.
Click the activate it button
Done
Enjoy the full version .
Note: Chrome Extensions Must Add to Chrome. than crack your Software
Note: If Software Not Download Try on Internet Explorer, Or Firefox Browser 100% Working
Admin
Sylenth1 Mac Crack
5
2Sylenth1 2020 Crack With License Key [Latest]
US-Link|| EU-Link||Russia-Link
Sylenth1 2020 Crack With License Key [Latest]
Sylenth1 2020 Crack is a Virtual Studio Technology instrument which delivers performance and quality that is second to none. Not many synthesizer software have stood shoulder to shoulder with the sound quality standards of their hardware counterparts.
This is an analog synthesizer that consists of several uniform oscillators. These oscillators make use of innovative techniques to create waveforms of high quality.
Music samples can be combined using functional music tools which are well developed, using the Sylenth1 Crack. Instruments’ pitches of music can be altered, and then mixed with one another. This allows sound to be captured at a different level resulting in, what is commonly known as, remixes.
If you want to make the sound quality of a clip better and crisper, Sylenth1 License Key is the software you are looking for. It records both, sound and sound clips, simultaneously. It can make a personal sound mixer for you, so you can maintain and save your sounds easily.

All the noteworthy sound effects offered by all the popular sound creators and editors are available in the Sylenth1 Crack. It doesn’t matter how good a sound recording is to listen, its quality can only be enhanced when they are edited and mixed with various preset sound effects. This virtual synthesizer offers the best solution.
Related Software you may like
Sylenth1 Crack Full Download
Sylenth1 2020 Torrent Free Download
Afterword, This is a great way to make the sound quality higher and perfect. The program has world-class capabilities that make it famous among professional and novice users. It is the best software especially for those who love music mixing and editing. Additionally, it doesn’t matter how well your sound recordings concentrate to appropriate unless you don’t write them and mix them with other preset sound effects. Sylenth1 3.055 Torrent includes many useful features such as Accurate pattern automation, Customizable skinning, and optimized sound supervisor and much more. Sylenth1 Torrent has given you every single suitable effect and famous sound editor.
Why Sylenth1 is First Choice ?
There are other options available but unlike them, the Sylenth1 Crack is the best option to have. Every user who wants to fulfill their sound mixing and sound editing needs should look no further.
Each music file has the capacity to save more than one track and the users can create as many files as they require. This provides them with a variety of music to listen to when completed.
Before shifting to another sample, each one plays for maximum 60 seconds, providing more control over music and allowing each sample to be entered into the remix. This continuous trend keeps going until the playlist culminates and the user has to change the file. Hence, control is granted to the user in all aspects that they care about.
Sound can be edited, and have a music file generated simultaneously on your PC or digital devices using the Sylenth1 3.055 Crack.
The software allows you to play music on special occasions and even on DJ tracks.
Several artists, producers, and directors have used the Sylenth1 VSTi Synthesizers so they could advance their music careers every now and then.
The quality of sound provided by various plugins available online and in the audio market does not measure up to professional hardware. They sound very much alike, digital, and thin when compared to professional hardware. And they demand large fractions of your CPU’s resources. Also, some plugins have illogical or awkward user interfaces and are completely devoid of useful features.
Sylenth1 3.055 Crack saves you the trouble of having to use that energy draining software and provides a compact and efficient solution to your needs. You can download the Sylenth1 3.055 Crack for free and avail all features available in the full version.
Features
It designed with a clear and straightforward to use interface in many ways, it is arranged with classes which are organized for smooth navigation.
As a result, add a unique impact to add a few feeling or presence to sounds. Such as Suspense, sweetness, echo and many others.
You can change voice attributes to present its greater individual and specialty. To boom listeners interest.
This program includes 10 melodic modes and permits you to trade velocity, collection, and pitch as your preference.
To make the speaker voice greater presentable, you can boom or decrease sound pitch consequently For speech or radio broadcast.
Sylenth1 Crack offers a massively wide variety of frequencies. You can exchange the frequency of sound So can create low or high-frequency sounds as you want.
With the help of Ping-Pong mode, you are capable of stereo unfold and eliminate time in any route left or right.
Sound amplitude can alternate consistently with your requirement. This alternate so no longer affect sound quality like many other packages.
As a result, the software encompasses equalizer equip with treble and bass. With equalizer, you may make adjustments to amplification in addition to frequency.
A postpone module is likewise to be had to contain every excessive and low bypass filters as well as echo functions
Merits
This software employs a minimal percentage of available CPU resource.
Very simple to use and understand. It is due to this simplicity that even first-time users can understand the basics easily.
It can effectively remove noise from unclear sound recordings, allowing easy remixing of music mixes.
There is a limitation in waveforms because of the subtractive synth nature of the Sylenth1 3.032 Crack.
This software has the capabilities of FM, trouble-free substantive, wavetable along with additive synthesis.
When the users are in need of a unique sound, the Sylenth1 3.032 Crack offers them a diverse selection of exclusive wavetables to choose from.
In case customers do not like the updated software, they can simply switch back to the previous version by reinstalling and running it again.
The software can be installed for free, which means that the users do not have to worry about being locked out.
Demerits
While the software has merits there still are some drawbacks worth mentioning:
Because of the modulation option being disabled, the ability to export and saving presets is no longer available, which sometimes becomes a hassle.
The software is set in a way that a maximum of 60 seconds of a sample can be played. This run time might be considered as less by some users.
Two Sylenth1 software cannot be installed on a device at the same time. Users have to choose their preferred version.
Sylenth1 Working Keys 2020

aNK8usx6Hvs9DuCBCrJREeUaPnBmN8qV
ArVpDcarQDYblV4E1LYwLe6NxcpdqvsD
6pBoxf4LjbtfrLM3xz8tURAFt7rmwpzl
8TXILwCxn2DYsNqhbGk5GxXFAAP8XH10
948C5E7A3D65147823DB28DD4BAAE
EF1F5D63B6F46E89A211AF8395681
System Requirements
Windows XP/vista/7/8.1/10 (32&64bit)
Mac OS x 10.6 or higher
Pentium III and above System
128 Mb RAM or better
How to Crack ?
First, download the free Sylenth1 3.055 Crack file
Then extract the crack file and run the setup
Activate by clicking on the button, or entering the serial key available online
Use the Sylenth1 3.055 Crack for free with all the available options.
Final Conclusion
Sylenth1 2020 Crack is a reliable and you can use it freely. We have not received any complaint from the users. Thanks for downloading and appreciation for our services.
Sylenth1 2020 Crack + Torrent Free Download [2020]
Related

1 note
·
View note
Text
Legacy Code
It’s not uncommon for Sombra to get orders to break into an organization’s system or two. Some are easier than others, but that's a part of the fun.
Throughout the past fifty or so years since it was popularized, cybersecurity practices now are arguably better than when it first became recognized as an industry. Most security controls are automated and controlled by AIs, limiting the number of human errors that could take place. (Layer 8* problems, if one were to be technical about it.)
That doesn’t mean, however, that it is without flaws. Security always will be as strong as its weakest link. You just have to know where to look. And Sombra has no issues peeking under the hood of these systems and exploiting their false sense of security.
She wonders how long it'll take the administrative offices of Madrid to realize she's in, tapping away at their ledger server.
There's always the risk of getting caught by a security analyst or someone of the like. That, too, is a part of the fun. It then becomes a race to the bottom. How much information can she exfiltrate while evading active defenses against her exploits.
She runs a hand through her hair as she single-handedly (literally) breaches the system, a triumphant grin on her face. Long passwords, biometric authentication, and multi-factor authentication is useless when the account owner adheres to neither controls. Not hard.
But as the system's dialogue boxes appear on her screen, she has to pause. The text is blocky. White on black. It's not the colorful interfaces she's used to seeing. It looks more akin to a text RPG or command line prompt. A proprietary DOS system, then?
Test command after test command goes into the system until it finally spits out the path of the code library she’s looking for. Navigating her way through (and downloading anything of interest she sees), she cracks open the library that holds the proverbial keys to the kingdom.
Sombra cackles, the clacking of her nails on hardlight keys audible above her sarcastic laughter. “What the hell is it written in? Fortran?”
She pauses to think before typing in a few test commands. On another screen, she throws up four windows, each with a search engine. Research soon covers that screen as she skins over the information. A potential exploit fills the screen of the hacked system with text.
Disbelief grows with each line she reads.
“No way.”
There’s a moment of breathtaking silence. Rereading the code’s syntax, she whispers, “¡Ay, dio’ mio! It is."
The chair springs upright again as she launches herself forward.
“Which Fortran is this? 90? Do I even have a compatible complier—?”
Sombra’s fingers jackhammer across her keyboard as she mutters incoherently to herself. Finding legacy code in her line of work is not uncommon. She’s seen Pascal and C before, a lot of SQL and Java.
But Fortran?
It’s beyond legacy. Old technology that has no right existing in this age so far removed from the days of computers that took up half a room and were given instructions manually by way of punch cards. It should be considered a dead language in the same way Latin is dead. To think this language is still in use over a hundred years after its initial creation, it’s insane.
"Whoever's maintaining this is probably ancient,” she mutters.
This job takes longer than usual on the account of the language’s age. Sombra never thought she’d have to write anything in Fortran so close to the 22nd century.
The system is thoroughly broken down into its most basic pieces, the source code--the backbone of the system--decompiled and stolen along with all the financial information about the administrative offices. Soon, Talon can threaten them with misconduct and bribe them with just the right amount.
In the meantime, the code will continue to run with a few choice modifications. Modifications that would give her access at any time and send a record of all activity to a different host. If she feels so inclined, she might even create false trails to set up a scapegoat in case of discovery.
It's another job well done.
--------
*In the OSI model, there are Layers 1 to 7 which show how data is presented and communicated, basically. A Layer 8 problem (which doesn’t exist on the model) means it’s a user issue. The person is the problem. Also known as PEBCAK (Problem Exists Between Chair And Keyboard) or some variation of it.
I don’t honestly know how cybersecurity would be handled in 50 years. Currently, I’d say hackers have a distinct advantage over defenders because of accessibility. Hackers’ tools are, for the most part, free and available to the general public. To be a defender, you have to have a network to defend and the tools available as well as approval from management. If management says, “No, you are not buying a new firewall because the 10-year old one we have is good enough,” you’re shit out of luck. Whereas hackers usually have new tools coming out every other day to bypass your 10-year old firewall 800 ways to Sunday.
Not to say being a defender is hopeless or bad. There’s nothing more satisfying than catching someone in the act, laughing maniacally as you watch them run (figuratively) as you shut them out, and then you just watch them continuously bang against your defenses, wondering what the fuck just happened. But there’s also satisfaction in breaking into a network and not getting caught and telling the client, “Hey. I just stole about 10TB of data from your servers by exploiting your IT admin’s weak password which is ‘password123’. Might wanna change that.”
In 50 years, I expect things to be more automated but still retaining the same general weaknesses of being built on legacy systems that cannot be upgraded and that companies don’t want to pay for or move away from because it’s too risky.
I was inspired to write this after reading several news articles about how New Jersey’s unemployment system still runs on Fortran and they’re looking for developers. Fortran was developed back in the 1950′s. This language is 60 years old at this point.
#my writing#back on my mundane bullshit#more cybersecurity related nonsense because i can and i'm avoiding my work#it's more painful explaining cybersecurity to my mother than it is explaining it to a Developer with a tight deadline
13 notes
·
View notes
Text
Maplestory private server illegal, Tricks to avoid penalty
Maplestory private server
Is it safe? Let us understand the background and distinctive contents of private servers.
More Information
Maplestory private host
It helps MapleStory fans better enjoy the hard work involved with constructing successful MapleStory servers. However, what about punishment?
Personal Servers are somewhat illegal because they breach the TOS or Copyright claims or something. If Nexon has captured a private host, they'll send a notification to you or sue you enjoy they did to and which no longer exist.
The reason behind most personal servers is either from people who talk about the leaked info. The manufacturer of OdinMS created his personal host, or they're rebels such as The Resistance vs. The Blend in Half-Life 2.
But, there's absolutely no possible way for Nexon to prevent all private servers. They are continuing to be advanced from moving v55, v63, v72, and so on.
How Is a Private Server like Maplestory Made?
After all the years of unsuccessful leveling, upgrading, and recruitment of guild members, together with a destroyed Ghost Boat Exorcist badge onto a three-year-old Mechanic, I chose to retire into a MapleStory Private Server.
Additionally, $600CAD to find nx and buy stuff (for example, meso sacs and store permits) to get items across and find things out in M.S. the challenging way. Yes, I sacrificed $600CAD in substantial school lunch money to get things like hair coupons in M.S. once I might have used that money to receive a supercomputer.
Nexon is observing everything
The ruined GSE badge within my 3-year-old 210 mechanics. (through celebrity improvement window) and Nexon's shortage of gear reimbursement finally led me to do the one thing nobody would ever encourage me to do: I gave up on GMS. With no GSE badge, I can not continue on GMS.
Furthermore, I wasted a lot of real cash to sell items to acquire more Mesos. Instead, I've more insults than Mesos from players. Such as"Shoo."
[caption id="attachment_1282" align="aligncenter" width="1920"] Maplestory Private waiter [/caption]
My big problem here is how do you create a MapleStory Private Server (whether it is a v83 or the most recent version)? Like, do they divide into Nexon's H.Q. and extract all of the sprites, maps, sound effects, etc., off their computers and then rebuild it like a jigsaw puzzle?
If they did, then I will need to pack my bags and fly to California to do this. Like, the M.S. files will need to come from someplace. Also, it's the sole way to acquire the Wizet Invincible Hat. Besides, you'll find guidelines on other Personal Server sites.
Mesos
That says things like"no hacking, injecting of tools/unauthorized equips/packets, no wz document editing, etc.". I feel like I deserve a holiday from this game, but don't wanna devote another 1-2-3 years recollecting all the Mesos and equipping myself.
I would like to compensate for the 3 years of the wasted moment on M.S. and get my movie/animation jobs finished at precisely the same moment.
In addition to the hat, the G.M. class itself is making me envious. Yes, they're a class referred to as"SuperGM." So with a Personal Server (a Private Server intended for my personal use ), I will see exactly what it is like to be a G.M.
And bypass all other personal server site rules. Plus, there's a skill known as"Super Dragon Roar" that really does %1000 damage to all animals on screen.
While we are on this subject of hacking, why are robots poor? I never uttered before, but as a fantastic player from GMS, I find the only fair use for them would be to let me farm Mesos while doing home chores. I could call in my friend to play M.S. while I create breakfast/lunch/dinner, do laundry, etc. Why are robots taboo to MMORPG moderators like MapleStory private servers? That and having my friend drama M.S. for me personally will make no difference (at least that's what I presume ).
A side question: why or how are Personal Servers bad? Besides the fact that they permit one to play the sport and get stuff free, I really don't see how Private Servers are poor. Additionally, when you produce a Personal Server, do you, as the admin, get a Wizet Invincible Hat?
Also, how do I protect my P.S. from Nexon so they don't locate it? ExtaliaMS got closed down when Nexon found their I.P. address. But I want to take additional precautions to avoid going to court to face Nexon.)
So for this, I will have to place my MMD project on hold for now. I have to wait until the introduction of MS2 so that I can port its models to MMD.
(this is where Time is Money. Much like E.G., construction of a condo in a boom-town; the employees need to build it quickly to allow more residents to proceed.)
Additionally, you're only allowed to perform a daily event once a character. That's like more kids than Octomom should feed.
And that I consumed almost an entire day to do daily quests on all of them because of how many negative aspects in the match slowed me down since the days passed! When it's terrible hackers, DCs (that is an online game term for"disconnections") (no matter whether I have a great or poor internet connection). Unscheduled server maintenances, or other things along those lines!
Can not you compare with a v83 Personal Server right into a quit game console like the Gamecube or even the PlayStation 1?
How can we play an old game from several decades back without a machine that's capable of doing this? So yeah, how can we try the previous skills and senior classes of the elderly servers if we can't even play with the older servers of Tonight Now? Please refer to this link for additional info about discontinued games and game consoles: A significant Note about Emulators for Game Developers.
More Information
Also, can't you compare with an MMORPG Private Server into a Jailbreak (like IAP Cracker and Installous) for iPod Touches/iPhones/iPads? For games such as Tiny Tower, Subway Surfers, Candy Crush, and so Forth, even with no Jailbreak/with the official server. I am able to go the distance and find those games completed 100 percent without having to spend a single cent.
The programmer (s) that created these match (s) plans to place them up to download free of cost. But I can't waste any more time on these types of server-sided matches because I have other important things to do.
Besides internet service, how does a Private Server need funds to operate? Since most P.S. sites say in their community guidelines. "If possible, please contribute as Personal Servers need funds to operate...
How to Create a MapleStory Private Server [v83]
First, go to C:\
As soon as you find three folders, call all you want, but I will name them'ZenthosDev,'''Downloads,' and'MapleStoryV83' with this tutorial.
Download these programs/files.
(64bit)
MySQL Query Browser
JCE Unlimited Power Records
WampServer
LocalHost v83
ZenthosDev v83
MapleStory v83
W.Z. Files
Make certain you selected the appropriate variant matching your Operating System (O.S.) to avoid any difficulties.
Installations:
Before we start, make sure to extract everything if it's in a .rar format.
Installing MapleStory v83:
Install MapleStory with the download provided. It is a really straight forward installation. Follow the instructions.
Delete the following files/folders in the C:/MapleStoryV83 folder should they exist.
MapleStory.exe
Patcher.exe
GameLauncher.exe
shield (folder)
Installing WampServer:
Follow the directions and install it.
C:\Wamp
Don't be concerned about putting your email and these at the end. Just press finish.
Left-click it and click put Online'.
Then left-click it again and click on begin All Services.'
The Wamp icon must look totally green (if it is red or reddish, you have a problem).
Installing the MySQL Query Browser:
It is straightforward, runs the installation record, agrees to the conditions, and follow the instructions.
According to which system kind your computer as you may install 32bit or 64bit.
So set up the corresponding file.
For another simple installation, follow the directions.
Documents placement:
Paste them into these areas, overwrite when prompted.
(The (jdk1)/(jre7) folder version could differ. It is fine ). C:\Program Files\Java\jdk1.7.0_01\jre\lib
3. C:\Program Files\Java\jdk1.7.0_01\jre\lib\safety
Copy each of the folders and files within the ZenthosDev folder that we made before. So it seems in this way.
Now replicate the W.Z. folder within the ZenthosDev folder.
So it must look like this.
SQL setup:
Username: root
Then click on the document' button in the menu bar, and select open Directory...'.
Proceed to C:\enthosDev\SQL and open the document called'ZenthosDev.SQL.'
Following its opening, apply the file.
Preference installation:
(This component is optional if running the server to Receive your computer only)
You might also make any alterations to have the server to function how you need it.
Wait 10 minutes, and then your bat file must look similar to this.
Code:
ZenthosDev has started:
World Launched
Login Launched
Channel Launched
Is Maplestory’s personal server really safe?
I ask this question as somebody who has been part of the Maplestory personal server" community."
(unsure whether the neighborhood is the best term to describe it, but oh well) to get many of years now. I would not call myself a"host hopper" per se, but I have tried out a decent variety of servers to see what they provide. Most servers market towards Maplers, who prefer the old-school/pre-BB encounter.
The sole thing that differentiates them will be the attributes they supply. Some have higher or lower EXP/Meso/Drop prices to make things more or harder. Some make H.P. Washing"Optional." Some provide custom content...you get the notion.
Anyway, this question popped into my mind when I tried out a host known as"AvalonMS." I recall having a few conversations using a streamer there. He was currently looking for a server to repay. This man had hoped that Avalon would perform well. Eventually, he left because he could not see the server becoming successful and remaining alive for more than a few months.
I really don't remember his precise words. However, I believe he said something along the lines of"Private Servers need to be run with at least a small bit of professionalism, like a business nearly."
Along with the proprietors of this host, since he put it, were not too professional. Among the substantial issues was that they weren't transparent enough with the area concerning what sort of content/updates they'd do with their game. I tried looking around for their host just a minute before. And they appeared to have vanished off the face of the internet. No big surprise there.
A personal server such as Maplestory has been around. So what is the issue?
I got me wondering how many private servers have been around for a while to stay successful. When I say successful, I usually indicate they could maintain a decently-sized busy player base for an extended period. That, if you consider it, is already hard enough as it is. In any kind, Maplestory, whether it be the official game or the personal servers, isn't a super popular MMO.
The official sport is nowhere near as popular as it was during its prime. And therefore, you would think the subset of all gamers/Maplers that prefer old-school private servers inside the official game is most likely a pretty little demographic.
We've got SOME powerful servers such as Royals, Legends, Saga, etc., which have existed for a couple of decades. And these"powerful" servers hold a reasonably large percentage of personal server gamers.
I mean hell, even as soon as you go past the 6th or even 7th rated server on gtop100, you begin getting into the servers that have less than 100 active players. And needless to say, the personal server community is most likely dwindling.
There are just so many men and women who have played pre-BB Maple.
And they would prefer it on the modern versions. Finally, those folks will likely proceed with their own lives and stop playing with Maplestory entirely because nostalgia can maintain a player round for such a long time. I must wonder how many more years we have before Maplestory Private Servers die off completely. I hope we have a little bit more. More Information
1 note
·
View note
Text
To change what the computer does when plugged in or on battery, open Control Panel > System and Security > Power Options > Change plan settings > Change advanced power settings. There’s a lot of stuff in here. If your computer acts way different when plugging it in or unplugging it, there might be something there that can help.You can even change when it gives notifications, what it does when it reaches really low battery, and what the power button does when pressed. However, you can’t use these settings to tell it to “do nothing” when it reaches critical battery level, and you can’t lower the critical battery level below 5%. To make the computer stop shutting down at 5%, open command prompt (it works with or without admin rights) and enter this command: powercfg -setdcvalueindex SCHEME_CURRENT SUB_BATTERY BATACTIONCRIT 0 Here's the link where I found this command: https://superuser.com/questions/1265274/how-to-bypass-windows-10s-auto-shutdown-on-critical-battery-level-when-the-ba
0 notes
Text
Forgotten password wizard windows 7

#Forgotten password wizard windows 7 install
#Forgotten password wizard windows 7 windows 10
The method of using password reset disk is about as useful as not losing your Windows password because you have to create that disk when you can remember the administrator password. You can then sign into that Windows account without a password! Conclusion This program will do almost whatever you want: reset forgotten login password, activate your account when it’s disabled or locked, promote the account to an administrator if necessary, etc. Step 3: Choose your user in the account list, and click on Reset Password. Once loading the compact operating system inside the CD, PCUnlocker will start. Step 2: After getting PCUnlocker bootable CD ready, insert it into the computer you’re going to access, and boot off the CD.
#Forgotten password wizard windows 7 install
If you want to create a bootable USB drive, download and install ISO2Disc. Windows might start a program that burns it to CD. Step 1: First of all, download the ISO image of PCUnlocker using a working computer.
#Forgotten password wizard windows 7 windows 10
Here is a walkthrough on using PCUnlocker to reset lost Windows 10 / 8 / 7 password easily: PCUnlocker is one of the best tools that can help you bypass, change, reset forgotten passwords of all users on your computer. Click Next.įorgot your Windows admin password and you don’t have a password reset disk? If you have lost admin access to your computer, you need to use third-party Windows password recovery tool. Step 5: Type a new password, and type a hint that will remind you of the password if you forget it. Step 4: Select the drive letter of your password reset disk and click Next. Step 3: When the Password Reset Wizard opens, click Next. At this point, insert your password reset disk and click that link. Now, you can see the “ Reset password” link below the password prompt. Step 2: Once clicking OK, you’ll back to the login screen. You’ll get the error message “ The password is incorrect. Step 1: After rebooting to Windows login screen, type anything in the password prompt and hit Enter. If you’ve made a password reset disk in advance, follow these steps: With Windows built-in password reset feature, you can create a password reset disk from Control Panel so that you can easily reset a forgotten password when you’re locked out. Try different passwords to log in to Windows but to no avail? How can I get rid of forgetting Windows password when locked out? Need to help your friend to get in to admin account as he couldn’t remember his password? This tutorial will show you two methods to reset forgotten login password on Windows 10 / 8 / 7.

0 notes
Text
Realiwhistle vst free download

Animate Excite Vst Download - metaplay.
RealiTone RealiWhistle virtual whistle instrument for NI Kontakt.
Realiwhistle Vst Free Download - renewbin.
RealiWhistle by Realitone - Whistle.
Realiwhistle Vst Crack - clevergulf.
Reddit Crack Plugins Uad.
Refx nexus vst latest free download full version | NewsJett.
Realiwhistle vst crack - Wakelet.
Download Vst Flex Free.
Valhallaroom Vst Free Download Crack - renewnm.
Little alterboy vst crack - FREE PROGRAMS, UTILITIES AND APPS powered.
Realivox Blue Vst Free Download - treeinvestment.
Download Free VST Plugins | Best VST Plugins - ProducersBuzz.
Animate Excite Vst Download - metaplay.
Realiwhistle Vst Crack Dev C++ Compiler For Windows Xp 32 Bit Waveshell Vst 9.6 Download Free Auto Tune Up Serum Free Download Mac Reddit Iphone 7 Screen Passcode Bypass 3utools Traktor Pro For Mac Torrent Dark Planet Vst Sound Instrument Set Free Download Syncing Beats With Traktor Pro 3. How to Download And Activate Serum VST Crack ? First Download Serum VST Crack File From Below Extract it and Run Now Click on Installed Setup Wait for Installation After that Click on Generate Key Copy this Key and Paste Now Click. Realiwhistle Vst Free Download By admin 20/04/20 16 Coments MusicLab – RealGuitar is a sample-based, specialized virtual instrument, with an innovative guitar sound simulation approach, and guitar performance on the keyboard. It can be used as a VSTi with any host application supporting VST 2.0, DXi and as a standalone version (Standalone).
RealiTone RealiWhistle virtual whistle instrument for NI Kontakt.
Realiwhistle Vst Crack Download - Last, but not least, there's an ensemble option, where three whistles are stacked in one instrument. Now your "Bridge Over River Kwai" cues, or even pop songs like Foster the People's "Pumped Up Kicks" are ridiculously easy! Powered by Create your own unique website with customizable templates. Get Started. CrackedPlugins2 - reddit.Little Alterboy Vst Free Download Mac - choicesentrancement.New and FREE Soundtoys. Little Alterboy Auto Tune Realiwhistle Vst Crack Robin Cook Ebooks Free Download. 11/5/2020 Robin Cook, MD, is the author of more than 30 books and is credited with popularizing the medical thriller with his groundbreaking and wildly.
Realiwhistle Vst Free Download - renewbin.
Serum Plugin Free Download Crack - bandspowerful. Realiwhistle Vst Crack - renewnm.... Serum VST 2.2.0b5 Crack Full Version Free Download Here! Serum VST Crack is an advanced wavetable synthesizer, it makes you capable of creating great sounds because of its features, it makes you capable of creating great music, so, if you want to create high. Description: RealiWhistle is the most complete whistle tool, you can control the speed of legato and vibrato, as well as the reverb, attack and recovery option, as well as the ability to add one or two more voices.... Free Vst Download Instruments reFX Nexus 2.2 VST Full Version Plugin Free Download Zip. Powered by Create your own unique.
RealiWhistle by Realitone - Whistle.
Search: Flex Vst Download Free. While supplying the seamless, natural pitch modification and audio quality that Auto-Tune is known for, Flex-Tune correction gives vocalists unmatched freedom to work out their vocal creativity MAKE TRACK WITH FLEX IN 10 MINUTES (FL STUDIO) Подробнее It also features Time Correction for non-destructive time editing, as well as Formant Correction. ReFX Nexus 2 Serial Key VST Free Download: The Nexus 2 License Key are most professional ROM synthesizer-plugin that usually used in FL studio maintain for sound quality. This Software make any sound hard ware more efficient in usability. In this data base company provide you build in hundred of sound waves features. All data base friendly in use and provides amazing.
Realiwhistle Vst Crack - clevergulf.
Direct Link--- Serum VST 2020 Crack + Torrent Version Updated Free Download For (Win/Mac).. The most comprehensive human whistle instrument we know of. Two whistling styles featuring two velocity layers with three round robins for each. Plus ramps...$39.95 · In stock. Jun 6, 2021 — RealiTone - RealiWhistle for KONTAKT - it is the most comprehensive tool whistle , you can. Little Snitch License Key 3.7. Korg Vst Plugins Free Download. Download Game Of Barbie Cooking. Minimonsta Vst Plugin Free Download. Realivox Blue Vst Free Download. Download Steinberg Virtual Bassist Vst Full. Traktor Pro 2 Instrumentals. Accordion Vst Mac Download. Its A Hard Knock Life Auto Tune. FREE VST PLUGINS is a website share free vst plugins, free vsti, vst plugins download, vst download, vst free download, best Free VST.
Reddit Crack Plugins Uad.
How you use the plugins you have is 10 times more important than having expensive gear Free Reverb VST Plugins Orange Pi Auto-Tune Pro, Autotune EFX 3, UAD Autotune Realtime, and Autotune Live Apollo Solo's Thunderbolt 3 connectivity gives both Mac and Windows† users a powerful and portable bus‑powered desktop recording solution We've. Turn down the mix if needed - this usually groups my drums very nicely UAD-Universal-Audio-Plugin Bundles Cracked program is new and works perfectly is verified to be sure that you will not find any incompatibility Simple as that 5130 Free Download; Albion One VST Crack Mac Free Download Plugin-Torrent; Universal Audio Uad Plugins Crack Mac Full Version Free; Melodyne Studio 5 Crack v5.
Refx nexus vst latest free download full version | NewsJett.
DAW Plugins: Orchestral Instruments, Drums & More.East West The Dark Side Review v1.0.2 + Free Download (PLAY).Vst Archives - Page 9 of 149 - VST Crack - VST Torrent - Sample Torrent.The Best 8 FREE VST plugins (2022) - Producer Sphere.TOP VTS TORRENT-Free Download.Luxonix Ravity S Vst Plugin Download Free - high-powerxpert.11 Best FREE VST. Signal runs in Kontakt (no play limit) or Free Kontakt player (15-minute play limit) version 5.3.1 or higher. Mac OS X 10.8 or higher. Windows 7 or higher. At least 4 GB of RAM (8 GB recommended), and 22 GB of free drive space. Access to a stable internet connection for digital delivery.
Realiwhistle vst crack - Wakelet.
Download FREE Whistle sounds - royalty-free! Find the Whistle sound you are looking for in seconds. Free Whistle Vst - hostsrenew. Win32 VST Kill Bill has a tune in its soundtrack by Ennio Morricone featuring a haunting and evocative whistling. This 'mini-synth' is designed solely to re-create that sound - just add reverb.
Download Vst Flex Free.
Chinese Nan Xiao Vst free. download full Version. Chinese Nan Xiao Vst Free Download Mp3. The Xiao is a ancient traditional Chinese, end-blown bamboo flute, also known as the dòngxiao. We have sampled this instrument with true legato intervals all the way up to the octave, and, like the bansuri, have artificially filled in the notes which.
Valhallaroom Vst Free Download Crack - renewnm.
Description: RealiWhistle is the most complete whistle tool, you can control the speed of legato and vibrato, as well as the reverb, attack and recovery option, as well as the ability to add one or two more voices.... Whistle Vst Plugin Free Download After Effects. Audio plugins,Free plugins for Logic Pro X,Free music software,free audio app. Our free piano VST plugin includes electric piano, grand piano, vintage organs, and more. From the rich, classical tones of the grand piano to the funkified sounds of an electric keyboard, you can find an excellent range of piano VST plugins using our free download. Our selection of sampled instruments also includes free VST instruments from. Human Whistle Vst Free Download The sounds are more real and better in around from C4 up to E5. Playing portameto (playing without release the note that you played just before) makes it's more like human whistle. Increase the Amp of Noise makes the sounds of breath being picked up by microphone.
Little alterboy vst crack - FREE PROGRAMS, UTILITIES AND APPS powered.
UAD-2 Satellite FireWire com UAD Ultimate Bundle Crack is the largest UAD plug-in package offered by Universal Audio and contains all plug-ins developed by UA up to a specific version of UAD software Plugin Crack brings you the latest VST plugins, effects, DAWs, samples, loops, sound libraries, presets, patches, and much more for free!.
Realivox Blue Vst Free Download - treeinvestment.
When this Chantal tea kettle whistles it produces a distinctive harmonica sound (thanks to a reed from the Hohner harmonica company). I've sampled that sound here and turned it into a surprisingly versatile Kontakt instrument (includes arpeggiator). Requires the full version of Kontakt (version 5.3.1 or later). Download Now. Realiwhistle Vst Crack Arabic Vst Plugins Free Download 12/23/2020 VSTMIDI Control Extension 2. #worldsrc apk #worldsrc game #luca mkv ita #better call saul egybest #guardians of the galaxy 2 egybest #candyman yify 2021 #рыцари справедливости торрент.
Download Free VST Plugins | Best VST Plugins - ProducersBuzz.
A Great Set of Free VST Plugins for Beginners. Now this tenth plugin is a little more than just a single. Avalon Vst Free Download Pc. From 50.45 MB. Pitcher (vst plugin) From 204.42 KB. Avalon Vst Free Download Fl Studio 12. TC Works Native Bundle VST From 4.57 MB.
Other links:

1 note
·
View note
Text
Jjsploit V4 Manual Download

VirusTotal.
JJSploit Information - WeAreDevs.
Sony vegas pro 16 free download full version 64 bit.
JJSploit - Download.
Krnl - Download #1 Roblox Exploit - Krnl.
Manual de Usuario de Liferay - V4 (PDF) | Free PDF Manuals.
Lua C Commands - evermafia.
Jjsploit V4 Download - openxam.
Exploit API C# Documentation & Download - WeAreDevs.
How to download and install JJSploit (all errors... - YouTube.
No More Floc.
Nulled.
Arsenal Jjsploit Scripts (208PCA).
VirusTotal.
Jjsploit no virus download, we are devs jjsploit download, jjsploit v4 download roblox, jjsploit download v3 safe, jjsploit download windows 10, jjsploit v4 download windows 10, jjsploit v4 download no virus, jjsploit v6 download With Adobe Solver Player, you can now click Flash games on any additional.
JJSploit Information - WeAreDevs.
( Direct download link (Windows) ) Lattest - LUA AND LUA-C ROBLOX SCRIPT EXECUTOR: JJSPLOIT V3(WORKING) LUAND LUA-C EXECUTOR,OP COMMANDS - tool, new addition to our website. This program has been tested for two weeks an it passed all beta and stress tests. LUA AND LUA-C ROBLOX SCRIPT EXECUTOR: JJSPLOIT V3(WORKING) LUAND LUA-C EXECUTOR,OP COMMANDS has latest built in features and as a bonus we. JJSploit V4. Most common used exploit with over 818760 downloads. Download. Laxify. Just like JJsploit with a little differences 203573 downloads. Download. Multiple.
Sony vegas pro 16 free download full version 64 bit.
Roblox FPS Unlocker v4.4.0. Fixed for July 28, 2021 Roblox update. Added support for custom FPS cap values (see your settings file) Added 165 and 360 to the list of default cap options. Download Here (64-bit). Stop waiting for exploit developers to fix their stuff. In this day and age, anyone can easily create an exploit using our API. The WeAreDevs Exploit API powers some of the popular exploits. Custom commands can easily be implemented with plain Lua scripts. Massive power is introduced with a full-featured Lua executor and a Lua C executor.
JJSploit - Download.
What is Jjsploit Script Pack. Likes: 579. Shares: 290.
Krnl - Download #1 Roblox Exploit - Krnl.
.
Manual de Usuario de Liferay - V4 (PDF) | Free PDF Manuals.
JJSploit is a Shareware software in the category Desktop developed by WeAreDevs. It was checked for updates 188 times by the users of our client application UpdateStar during the last month. The latest version of JJSploit is currently unknown. It was initially added to our database on 01/10/2019. JJSploit runs on the following operating systems.
Lua C Commands - evermafia.
A Poseidon Lua program is able to use manual memory management to bypass the performance costs related to automatic garbage collection.... JJSploit V4 is a Roblox exploit with a Level 4 Near Full Lua executor and lots a variety of useful commands. Credits go to WeAreDevs for developing for this. 3 Running Games;... download them and place. Jjsploit V4 Download The Available; Jjsploit V4 Dll Will Be; Jjsploit V4 Download The Available. Roblox hacks exploits admin quickness btools roblox hácks 2018in this write-up we will inform you about all the existing videos cheats ánd scripts for robIox what they are usually for and how to use them how they are usually created and how several troubles they have as nicely as you cán.
Jjsploit V4 Download - openxam.
Txt - Free ebook download as Text File ( Extremely stable level 7 jjsploit v4 lua lua c exe. Extremely stable level 7 jjsploit v4 lua lua c exe. Material Balance Excel Sheet Shuckie To a ver's frustration, PP stall is viable in Balanced Hackmons; Competitive (doubles ou) Electrolyte vs Scripts won't be saved unless your exploit has a decompiler. Block FLoC instantly. No More Floc is a improved browsing experience Extension. Download JJSploit v3 Multiple RBX Games Updated 05/02/18 Usually you're limited to having only one game open, with this you can open as many games as you want. 100 games if you felt like.
Exploit API C# Documentation & Download - WeAreDevs.
Download selected files (zip) Ethernet-DinMX4 Select all. i. Default profiles. v4.2.0 11/09/2017 30.67 K... User Manual (from serial LUM0060361 and up). This Roblox Exploit can never be patched because within a day of it getting patched wearedevs (creators) have already unpatched roblox's patch update.JJSploi. Jjsploit V4 Download ฟร ว ด โอออนไลน ด ท ว ออนไลน คล ปว ด โอ new roblox exploit jjsploit v4 new updated version of jjsploit level.... Hisense 50h5g Manual. Puppies For Sale Wa. Free Procreate Grids. Wndu 16 News Team. Cisco Ssh Ciphers. Cz 75 Drum. Australian Kiss Wiki. Yahawah Yahawashi.
How to download and install JJSploit (all errors... - YouTube.
If you are still having problems join our discord server below:subcribe and like for more exploit.
No More Floc.
The DriverUpdate™ Utility is compatible with your Windows® operating system. Free Scan for Windows® 10, 8, 7, Vista & XP Operating Systems. Charges apply for license with premium features. See registration process for full details. Automatically identifies the necessary updates for your machine..
Nulled.
Download for Windows. Windows 7 or higher. iOS Download. Android Download. Linux. Download. Mac Download. Feeling experimental? Try our Public Test Build and test new features before they launch. Download Public Test Build. Imagine a place. English, USA. Product Download Nitro Status. Company About Jobs Branding Newsroom.. Softonic review. Free cheat software for Roblox. JJSploit is a free exploit software that is made for the game Roblox.Exploit programs are made to hack games, to let you do actions that are not normally available.JJSploit delivers many hacks that you can choose from, but at your own risk as Roblox does not permit you to use the exploit platform. The Roblox community debates whether JJSploit is.
Arsenal Jjsploit Scripts (208PCA).
VirusTotal Jotti (both scans are of V4.0) When launching the injector for the first time it needs to download two PDB files from the Microsoft symbol server. Let the injector download those files or it won't work. Since these files are system dependent I can't just add them to the injector download. If you have problem with opening the injector. VirusTotal - Home. Analyze suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community. Want to automate submissions? Check our API, free quota grants available for new file uploads.
Other content:
Sd Host Controller Driver Windows 10
Pci Simple Communications Controller Driver For Hp Dc7800
Free Downloadable Borders For Word
Max Payne 3 Game Free Download For Mac
Free Vst Plugins 31 Band Eq

1 note
·
View note
Text
Windows 10 forgot password hard reset 無料ダウンロード.6 Ways to Reset Forgotten Windows 10 Password
Windows 10 forgot password hard reset 無料ダウンロード.5 Ways to Bypass Windows 10 Password If You Forgot

Top 1: Use Windows 10 Password Reset Disk.公式サイト|Windows Password Keyをダウンロード
When you forget your Windows administrator password and locked out of Windows, you can't access your computer, but all-in-one Windows password restore software can help you reset and bypass all windows password without re-installing system and losing your data. Whether it is Windows local administrator or other users password, domain admin or other users password, iSeePassword Jul 28, · The easiest method to factory reset your Windows 10 PC without the admin password is to use the method above. If your PC is having problems, however, you could decide to wipe the hard drive entirely, using Windows installation media to reinstall or reset Windows Lazesoft Recover My Password Home Edition is Windows Password Recovery freeware. It can be used to remove Windows logon password,reset Windows password to blank, unlock and enable your locked or disabled user account
Windows 10 forgot password hard reset 無料ダウンロード.6 Ways to Reset Forgotten Windows 10 password for Administrator or Microsoft Account
But, before that, you have to know which password you forgot. Because you can use local, Administrator or Microsoft account to login your computer on Windows After you figure it out then follow the article below to recover your forgotten Windows 10 password. Top 1: Use Windows 10 Password Reset Disk; Top 2: Reset Windows 10 Microsoft Windows Password Key 企業用 CD/DVDやUSBメモリーを使用して、Windowsの管理者やユーザーのパスワードやMicrosoftアカウントのパスワードをリセット。 V 無料ダウンロード Mar 18, · Three scenarios you may forgot Windows 10 Password easily. 1) If you set a complex password you're not likely to remember, you will definitely forget it, especially if you didn't write it down somewhere. 2) Another category of PC users quickly set their passwords without giving a second thought to what they are using to lock their Windows system. In such cases, an individual will end up
If you forgot Windows 10 admin password, you'll be unable to install any software. Sometimes you won't even be able to use your computer. Microsoft doesn't make it easy to reset your password, but you have some options. In this tutorial we'll show you 6 simple ways to reset forgotten Windows 10 password for administrator and Microsoft account. Rest assured, at least one way will help you out.
Using a password reset disk is Microsoft's official method to reset a lost Windows password. The only downside of this method is that you need to create a Windows 10 password reset disk before your password is lost.
If you have created a password reset disk, you can easily set a new password for signing in to your Windows 10 computer. Check out this tutorial: How to Use a Password Reset Disk in Windows If you can still log into Windows 10 with PIN, picture password or another administrator account, there is a good chance you can open an elevated Command Prompt and reset Windows 10 password easily.
To reset your forgotten password, type the following command and press Enter. Since Windows 8, most people are now using a Microsoft account for logging into Windows. When you forgot your Microsoft account password, just use another computer to visit the Windows Live password reset page on the Microsoft website, and you can reset the password online. It's relatively easier than resetting local account password.
This method requires you to have access to the alternate email account or phone number you provided when signing up the Microsoft account. If you don't have access to those anymore, Microsoft will be unable to verify your identity. In that case, you can convert Windows 10 Microsoft account to a local account from a boot media, so you can log back into Windows 10 without losing files.
DaRT Microsoft Diagnostics and Recovery Toolset is a toolset from Microsoft that helps IT professionals recover the computers that have become unusable. Boot your computer with DaRT Recovery CD and then launch the built-in Locksmith Wizard tool, it allows you to reset Windows 10 password of any local account.
Unfortunately, DaRT is not free. This tool is only available for Microsoft volume customers, TechNet Plus subscribers, and MSDN subscribers. Before performing a Windows 10 password reset, check out this video tutorial on Microsoft website: Reset passwords with the DaRT. PCUnlocker allows you to unlock any Windows computer that you were locked out by a forgotten password. It is a bootable image that can be written to a CD or a USB stick using the freeware ISO2Disc.
After booting from PCUnlocker Live CD or USB , you can view all local accounts for your Windows 10 installation.
Simply select one of your local accounts and click on Reset Password button, the program will check the status of your selected account and perform the following tasks to fix your password problem:. Once you've reset Windows 10 password and get back into your system, make sure you set a new password that you won't forget next time. It's also good practice to create a Windows 10 password reset disk if you use quite complicated password for security reason. If you don't want to use any Windows 10 password reset software or your hard drive is encrypted with BitLocker, you can restore your computer to the most recent restore point includes an old password that you do remember.
However, programs that have been installed since the restore point have to be installed again. Provide the best software to recover passwords for Windows , SQL Server , PDF , Word , Excel , Outlook , FTP , Email , etc. MENU Home Products Purchase Support Home Products Password Recovery Bundle PCUnlocker Outlook Password Recovery SQL Server Password Changer PDF Password Recovery Protect My Folders Video Converter Assist KeyFinder Plus More Product Information Download Trial Purchase.
Reset Windows 10 Password Windows 8 Password Reset Forgot Microsoft Account Login Windows 7 Password Reset Reset Domain Admin Password Windows UEFI Password Reset Surface Pro Password Reset Outlook Password Recovery Recover SQL Server Password Find Lost Product Key. Method 1: Use Password Reset Disk Using a password reset disk is Microsoft's official method to reset a lost Windows password.
Method 2: Login with Other Sign-in Option If you can still log into Windows 10 with PIN, picture password or another administrator account, there is a good chance you can open an elevated Command Prompt and reset Windows 10 password easily. Method 4: Reset Windows 10 Password with MSDaRT DaRT Microsoft Diagnostics and Recovery Toolset is a toolset from Microsoft that helps IT professionals recover the computers that have become unusable. Before performing a Windows 10 password reset, check out this video tutorial on Microsoft website: Reset passwords with the DaRT Method 5: Reset Windows 10 Password with PCUnlocker PCUnlocker allows you to unlock any Windows computer that you were locked out by a forgotten password.
Method 6: Restore Windows 10 to Previous State If you don't want to use any Windows 10 password reset software or your hard drive is encrypted with BitLocker, you can restore your computer to the most recent restore point includes an old password that you do remember. Ready to try or buy?
Buy PCUnlocker Enterprise Download PCUnlocker. All Rights Reserved. Password Recovery Bundle.
0 notes