#how to print prime number in c
Explore tagged Tumblr posts
Text
My Esoteric Programming Language Synopsis
Been looking into esoteric programming languages, or programming languages whose purpose is NOT to make a programmer's life easier, but rather to be weird and often confusing. Here are my reviews:
<>< (Fish): This language revolves around the moving a pointer around the program itself, which is read as a 2 dimensional grid of characters. The pointer moves to the right by default, but you can change its direction with the arrow-looking characters (<,>,^,v). You can also reflect the instruction pointer with the mirror-looking characters (|,_,/,\\), which reflect the arrow the direction that makes sense based on what way it is going and the geometry of the characters. On top of this, the language is stack-based. For those who don't recall the first few pages of Homestuck, a stack is a data structure that stores a list of values like an array, except the only accessible datum in the stack is the most recently entered one. Programmers have no business using stacks in the year 2023. Other neat details include the trampoline instruction (!) which jumps over a spot in the grid, and because you need to use a stack, to print a value from code, you need to write it in the code backwards. Also when you get an error, the compiler says "Something smells fishy..." Difficulty 3/10
Brainfuck: Brainfuck was made by a man trying to make the smallest programming language compiler he could. The program instructions rely on an arbitrarily large 1 dimensional array of numbers. Brainfuck has 8 single-character commands, and all other characters are treated as comments. This is a brainfuck program to write "Hello World":
+[-->-[>>+>-----<<]<--<---]>-.>>>+.>>..+++[.>]<<<<.+++.------.<<-.>>>>+.[<->-]<-.>
Difficulty 9/10
Hexagony: Like <><, Hexagony works by sending a pointer along the program, treating it like a grid of characters. The difference is that Hexagony programs are on a hexagonal grid. This is Hello World in Hexagony:

Difficulty 8/10 (I cannot wrap my head around this one)
INTERCAL: Compiler Language With No Pronounceable Acronym, or INTERCAL, was one of the first esoteric programming languages, created in 1972. The language was designed to make common operations needlessly difficult, while adding keywords for other operations to make the whole thing unpleasant to look at. There is a keyword “PLEASE” that doesn’t do anything, although if you don’t include enough “PLEASE” commands, the compiler will give an error stating your program is not polite enough. Unlike most of the programming languages on this list, INTERCAL is too slow when compiled to be used practically. In 1992 a journalist tested the speed of Intercal against C. In C, it took less than a second to compute all the prime numbers up to 65536. In INTERCAL, it took over 17 hours. Difficulty: 8/10 LOLCODE: The syntax of LOLCODE is inspired by “lolspeak,” the English dialect of lolcat captions. Every LOLCODE program begins with “HAI” and ends with “KTHXBYE”. To import library STDIO, use the command “CAN HAZ STDIO?” The underlying structure of LOLCODE is actually fairly standard, which makes this esolang pretty accessible.
Difficulty: 1/10
Malbolge: How do you print “Hello, World” in Malbolge?
(=<`#9]~6ZY327Uv4-QsqpMn&+Ij"'E%e{Ab~w=_:]Kw%o44Uqp0/Q?xNvL:`H%c#DD2^WV>gY;dts76qKJImZkj
Malbolge was designed to be the most difficult programming language in existence. The language determines which of the eight available instructions to execute by adding the current instruction to the current instruction’s index in memory, modulo 94. There are no arithmetic operators except for the *crazy operator*, a Malbolge original that takes two numbers in their ternary form and determines the result digit by digit using an unintuitive table. The crazy operator is not commutative, and is your only arithmetic operation. Whenever an instruction is executed, it is encrypted so that it will not do the same thing next time. Due to the complexity of Malbolge, a turing complete version does not currently exist, limited by the size of programs allowable.
Difficulty: 20/10
3 notes
·
View notes
Text
Step-by-Step Process to Check Exide Battery Manufacturing Date
Keeping track of your car battery's age is essential to ensure its longevity and performance. The manufacturing date gives you crucial information about the battery's lifespan, helping you decide when it’s time for a replacement. In this guide, we’ll walk you through a step-by-step process to check the Exide battery manufacturing date so you can stay on top of your battery’s health and keep your car running smoothly.

Step 1: Locate the Manufacturing Date Code
The first step in the process of checking the Exide battery manufacturing date is to find the date code on your battery. Exide typically prints this code on a label located on the top or side of the battery. However, depending on the model and age of the battery, it could also be embossed directly into the casing or stamped near the terminals.
The manufacturing date is often included in a four or five-character code, and in most cases, it is easy to spot once you know what to look for. For example, you might see a code like “A9” or “C0” printed clearly on the battery label.
Step 2: Decode the Date
Once you’ve located the manufacturing date code, the next step is to decode it. This step is crucial because it gives you the exact month and year the battery was made. The date code typically consists of two parts:
The First Character (Letter): This represents the month the battery was manufactured. For instance, "A" stands for January, "B" for February, "C" for March, and so on up to "L" for December.
The Second Character (Number): This indicates the year. For example, "9" represents 2019, "0" represents 2020, and so forth.
Let’s break it down with an example. If your battery shows "B1":
The "B" stands for February (the second month of the year).
The "1" indicates the year 2021.
Thus, your battery was manufactured in February 2021.
Step 3: Double-Check for Clarity
While most batteries follow the standard code, Exide has been known to vary their format slightly depending on the model. Some newer batteries may display the date more clearly, using a four-digit numerical code like "0522," where the first two digits stand for the month and the last two for the year. In this case, "0522" would mean the battery was made in May 2022.
Always check your battery’s manual or consult Exide’s customer service if you’re unsure how to interpret the code. Knowing how to check Exide battery manufacturing date accurately will give you a better understanding of your battery’s age and condition.
Step 4: Verify with Other Documentation
If the code on your battery is missing, hard to read, or confusing, you can verify the manufacturing date through alternative means. Here’s how:
Check Your Purchase Receipt: Often, the receipt or invoice will include the manufacturing date or at least the date of purchase, which can give you an idea of the battery’s age.
Look at the Warranty Card: The warranty card that comes with your Exide battery may also list the manufacturing date.
Consult Your Dealer: If all else fails, you can take the battery to an authorized Exide dealer. They can look up the manufacturing date using the serial number or other identifiers on the battery.
Step 5: Assess the Battery’s Condition
Now that you know how to check the Exide battery manufacturing date, it’s time to assess whether your battery is still within its prime lifespan. Car batteries generally last between three and five years, depending on usage, climate, and maintenance. If your battery is approaching or exceeding this range, it might be time to consider a replacement.
You should also pay attention to signs of aging, such as:
Difficulty Starting the Car: If your engine takes longer to crank, it could indicate that the battery is losing its charge capacity.
Corrosion on the Terminals: White or blue-green powder around the terminals suggests that the battery might be leaking acid, which can signal the end of its life.
Swollen Battery Case: A swollen or bloated casing often indicates overheating, which can be caused by age or a failing battery.
Why Knowing the Manufacturing Date is Important
Understanding how to check Exide battery manufacturing date ensures that you stay on top of your vehicle’s maintenance and avoid being caught off guard by a dead battery. By checking the manufacturing date, you can plan for a replacement before you encounter problems on the road. It also helps when buying a new battery, as you’ll want to ensure you’re getting a fresh battery rather than one that has been sitting on the shelf for too long.
Conclusion
Following this step-by-step process will make checking the Exide battery manufacturing date quick and easy. By locating, decoding, and verifying the manufacturing date, you’ll have a clear understanding of your battery’s age and its remaining lifespan. Remember, knowing how to check Exide battery manufacturing date is essential for keeping your vehicle running smoothly and avoiding unexpected breakdowns. Make it part of your regular car maintenance routine to stay ahead of potential battery issues.
1 note
·
View note
Text
*Looks both ways*
So, programming. People often think about it as kind of magical, but it's really not. It's just a set of instructions for the computer to follow. Think of it kind of like a very detailed recipe. Instead of saying something like "mix until smooth" it would say something like "mix for three minutes on high or until no more sugar is visible". At the lowest level, the stuff your computer actually runs, its much stupider and simpler than that. Just basic things like "add these two numbers" and "is this number greater than zero?" and "go this many squares (bits) into memory and add 3 to that number". Now, as you might imagine, this is *incredibly* inconvenient to work with. Really what you want to do is ask for the person's username and password and check if that person is allowed to log in. How do you even start working with text? How do you check two pieces of text being equal? How do you hash the password? Text is just numbers to the computer, so I guess you could dive in head first and do a lot of number crunching and work through converting everything to the stupid level the computer understands.
Thankfully, programmers decided that was way too annoying, so we have programming languages, like C, C++, Java and more that abstract away the stupid instructions into much higher level instructions. Instead of saying "add 1 to that number, now save it, now load this number, load that place in memory, now add 1 and load that place in memory, now check if the top two values are equal and write that back to memory, ..." we can just ask it "a == b" (does a equal b). That's already a great improvement, but still leaves much to be desired. What if we want to reverse a list? Or print out the first prime numbers? Or compute the Fibonacci sequence? We would still have to write out all the intermediate steps ourselves.
This is where one of my favorite parts of programming comes into play: functional programming. What I've been talking about up to now is imperative programming. In imperative programming you say *how* to do something, in functional programming you say *what* to do. If I wanted the first prime numbers I just ask it to make a list of all natural numbers and return any that are prime. I don't have to specify how to make the list or how to check that they are prime or anything. It just does it.
Now that's cool in and of itself for convenience, if nothing else, but it gets even better. You see, as you climb into more and more "pure" functional programming, it turns more and more into math. Math about how containers for things work, math operations over functions, math over sequences, sets, and more. (If you want to see a pretty good example, go look at some high level Haskell code.)
I don't know where I was going with that, I just think it's kind of cool. I could say more, but I'm feeling a little crumby and can't be bothered to type it out right now.
INFODUMP TO ME ABOUT LITERALLY ANYTHING IDC
21 notes
·
View notes
Video
youtube
Program to print the numbers up to 1, 2, 3, 4, 5, 300
#Program to print prime number#program to print the numbers up to 1-300#1 2 3 4 5 300#write a program to print prime number between 1 to 100#how to make program of prime numbers#program to print numbers from 10 to 1 using for loop#how to print prime number in c#fortran language#fortran program#learning fortran language
1 note
·
View note
Note
I'm okay with a bunch of disorganized rambling honestly 😂. But if I had to narrow it down then I guess I want to know about main and side characters and how they compare to the original?
I know that tumblr is the Prime Site for disorganized rambling, but I have perfectionism issues. But that is a great question, nonnie, and I will be happy to ramble is a slightly less disorganized fashion.
When reading Maximum Ride as a somewhat-formed adult who discovered they enjoy English classes about 3.5 years ago, I noticed that JP, when writing, doesn't understand consistency. At all. Which means, in many ways, I have a free sandbox to work with.
Spoilers for my rewrite WIP, because I strongly believe that if a story would no longer be good if one had spoilers, then it wasn’t a good story in the first place.
I'm trying to keep the backstories the same, plus or minus the scientific method and a few characters (RIP my OCs. I want to bring you back so bad but it wouldn't fit with the thematic narrative). I've mostly kept their (starting) abilities the same, too. Without further ado, I'm going to introduce some WorldBuilding. (If I'm good at nothing else, I'm good at world building)
First off. Logically.
How are they getting Cable?
How are they getting internet?
How are they getting money to eat and stuff?
JP's answer: handwave it off. Sometimes you need to ignore logistics for the sake of plot. This is an answer I'd accept from an author that I like, such as Julie Kagawa, that makes amazing worlds, characters, and narratives that I will happily handwave a few things that wouldn't work in the real world. James Patterson, on the other hand, did not make any of that; he made a cool concept, some good rough-draft characters, and nothing else, and therefore this is an unforgivable sin.
Wasp's answer: They are not getting any of that.
Introducing Cottagecore.
The house is off the grid. Solar Panels and a wind turbine create electricity. They have their own well. They grow their own food, raise livestock for eggs, milk, and wool, and trap fish for meat. They get money through dumpster diving and pawning. They still have to steal half of the necessities they can’t make themselves. They do have a TV, but it can access about three channels on a clear day. Internet is only a thing when they go to the public library.
Giving the flock a background that’s heavy in farming and livestock rearing shores up the plot holes mentioned above, but in my opinion, ties the flock more tightly to the environment, thus giving them something tangible to lose when they have to leave the E-shaped house. Because they’re not just leaving a house and a safety net— they’re leaving their entire way of life with no promise of getting it back. It also gives them a tangible connection to the earth in case I want to actually pursue the global warming themes.
Main Characters
Maximum “Max” Ride (Birthname: nonexistent)
First off, I'm letting her be Latina, James Patterson.
In the original, Max was very much the headstrong, independent, action girl. Leaning into Strong Female Character (TM), but overall she had a strong, solid foundation and enough character consistency through the first three books for me to not have to just make an entire new character. However, I felt that she was, in some ways, a bit too Action-Girl and Strong and Capable. Yes, Max is incredible and competent, but she’s also fourteen. She’s a child.
In the rewrite, Max’s character is still headstrong, independent, capable, and sometimes not the best at listening to others. All of that’s the same. But she’s that way not because of girlboss energy, but because there’s no one else to do it. She doesn’t want to lead, necessarily. She wants to get some rest and let someone else handle the problems life keeps throwing at her. But she knows if she did that, the responsibility of leader would fall to Fang and Iggy, and she can’t ask that of them. She doesn’t want to place that burden on anyone else (Look, there’s a reason I chose Ayano’s Theory of Happiness as one of her signifier songs, okay?). Her narrative is very much centered around burden, and also around loss. She lost her cultural heritage when she was taken away from her birth family, she lost her childhood to being a leader, she lost a good deal of her friends to the school (RIP my OCs), she lost Jeb, and then she lost her stability. And she’s going to lose a lot more before the end of the story. So a lot of her character arc deals with learning that there are some things she can’t fix, some things that can’t be recovered. She can’t get the E-shaped house back. She can’t get her Little Baby Angel back, even after they rescue her. She can’t get her friends back from the school. And instead of working so hard to recover those or find something to replace them, she has to learn to live with that sense of loss and move on with her life without feeling guilty for leaving things behind. And she has to learn that asking for help and sharing her burden is selfish or weak.
Other changes I made that don’t necessarily fit into her narrative arc, but you asked for rambling so rambling you shall get:
Max hallucinates, because mental illness is also a prominent theme in the rewrite. She doesn’t have a psychotic disorder, but her C-PTSD causes visual/audio hallucinations, especially when she’s stressed or sleep deprived.
Max ends up having a Gender Discovery throughout the story and goes by He/She pronouns eventually. I don’t know when, but it will happen.
As far as genetic modifications/special quirks go, she can fly faster than the rest of the flock, but not 300 miles per hour. She averages about sixty mph with diving speeds of 240. She cannot breathe underwater or shut down her organs on command. She also has the Super Special Power to predict the weather, but that’s not because of genetics, it’s because she has chronic pain in her right arm that gets worse when weather fronts change.
Her favored weapon is her trusty rebar that she picked up from a condemned building. I think she’s going to name it eventually but I don’t know what yet.
Fang (Birth name: Gabriel Xue)
In canon, Fang is characterized in early books by being the “dark, strong, silent type”. He’s probably the most reserved member of the flock, to the point of falling into the Brooding Mystery Man trope in parts of the book. They care a lot, but they’re not the best at conveying that, especially with the younger members of the flock, and at times their high empathy leads them to making mistakes. Despite the high empathy, he’s often compared to a robot due to his lack of expression and external emotions.
Well, first change is that they’re not a man, so jot that down—
If Max’s narrative is centered around burden and loss, I would probably say that Fang’s is centered around humanity and moving on. None of the flock was treated as human while in the school, but Fang was more often than not treated like a wild animal due to “behavioral issues”, and therefore had and continues to have a difficult time considering themselves real and alive, let alone human. This manifests through a several different ways— where in canon Fang definitely had a ‘fight’ reaction, in the re-write they have a ‘freeze’ or ‘shut down’ instinct. They’re selectively mute for multiple reasons (including derealization, jaw pain, the fact that they didn’t learn how to speak until they were 10, and genuinely forgetting it’s something they’re capable of), a period of Cotard’s syndrome, and a tendancy towards self-loathing and self-sacrifice. In short, Fang is still halfway stuck in the mindset that most of the flock grew out of when they escaped in the school, and doesn’t know how to move past it.
Much of their character arc revolves around not necessarily seeing themselves as human, but learning to treat themselves as human even when they don’t feel like one (or even feel real), and knowing that just because they don’t feel human all the time doesn’t mean anyone else can treat them the same. They never start easily expressing their emotions, and they’re always going to be selectively mute, but they learn to accept that those aspects of themself aren’t character flaws or signs that they’re sub-human.
Other additions to Fang’s character include:
They don’t get their hair cut in New York. It stays long through the entire series. They have the longest hair in the flock by the end of the series, and they can wear it in so many styles.
Fang uses they/it pronouns because themes of reclaiming the weapons used against it and, more importantly, Gender.
They’re actually really good at spelling compared to the rest of the flock, because they and Iggy communicate with Print-On-Palm when they’re nonverbal, and they’re nonverbal for some pretty long stretches of time.
They and Max have... zero romantic tension. At all. There is none. The number of times Max calls them her sibling/little sibling in the first arc alone is staggering, and that will not change.
Igneous “Iggy” (Birthname: Jamsetta “Jamie” Griffiths)
I’ve talked about Iggy before. Canon doesn’t give us much to go off of, but from what’s shown, he’s smart, sarcastic, has sharper edges than Fang and Max, and also has a sizable ruthless streak. So that’s what I have to go off of.
The big difference between Iggy and Fang&Max is that Iggy has a much better memory of the School. Most of the flock have areas (months or years) that they don’t remember, or people that they’ve blocked from their mind, but Iggy... doesn’t. So he’s the one that remembers all of the other AVIAN test subjects that were old enough to have names and identities but died due to complications. Max might have the burden of leadership, but he has the burden of memory. And that has lead to both a massive fucking guilt complex, because why did he survive when they didn’t, and, as mentioned above, a ruthless streak that he doesn’t shy away from.
Which is to say, by the end of the story, Iggy has the highest kill count.
I love, love writing Iggy next to Max and Fang. I love writing Iggy next to Gazzy and Nudge. Because, I say this with all of the love of the world, but Iggy is not a good person. He is loyalty and love incarnate, and the world can burn down if he and his siblings are safe. Max and Fang will always try to save as many people as they can. They will wonder what’s wrong with them the first time they kill and don’t have a mental breakdown about it. They are good in a way that Iggy is not. He’s okay with killing Erasers. He’s okay with killing humans. He’s okay with killing people who might not necessarily deserve it, if they show themselves as a threat or are simply in the blast radius. He knows perfectly well that most of those Erasers he’s murdering are four and five and he is okay with that, because a lot of the AVIANs were that age when they died. (Yeah, in the rewrite it’s not Fang who has an issue with Ari; it’s Iggy who wants the 7-year-old wolf-boy dead.)
And this is, of course, juxtaposed with Iggy being really, really good with Nudge and Gazzy (especially in the beginning). Because, again, he actually remembers being a child. He remembers a lot of kids that died and is therefore fiercely protective of the kids that didn’t, as well as fiercely protective of the innocence that he never got. So he’s the one that cooks their favorite foods when they’re having a bad day, always makes time when they want to talk about something, and convinces Max to let them go to that toy store in New York because, yeah, he Max and Fang aren’t kids. They never were. But Nudge, Gazzy, and Angel can be. (And if he has to be a murderer to preserve that, then he’s perfectly okay with that.)
He and Angel don’t get along very well, though. The telepath doesn’t like hanging out with the person with the most clear memories of the school.
Other additions:
Iggy is trans and says trans rights
He also has paranoid episodes, because C-PTSD. Sometimes they’re very helpful. Sometimes they are not.
I actually decided that he’s one of the flock that doesn’t meet their parents. I know in canon he did, but I always found that very clunky because it didn’t add to his character. He was one of the characters who, until it was convenient for the plot, seemed to care the least about his family. I’d much rather give that to a character whose arc would benefit from it.
Iggy! Gets! Older Sibling Rights! Seriously, he’s two months younger than Fang, he is just as capable.
Iggy does not know braille because Jeb decided it wasn’t necessary for him to know. Iggy is also the best speller in the flock, because Print-on-Palm was the only way to talk to Fang for a solid year. Yes he mocks everyone over this.
Iggy is the only member of the flock that enjoys swimming and can take into the air from water. Everyone else in the flock is incredibly jealous.
Nudge (Birthname: Monique Robinson)
If Iggy is defined by his memories, Nudge is his polar opposite. She was seven when she left the School, but she has next to no memories of it. She is missing a lot of time in the first year she escaped. And that causes... a lot of things. It makes her feel disconnected from her older siblings, it gives her the ability to function in society in a way the other’s can’t, it lets her feel less grief over the ones that didn’t make it and she doesn’t remember, it makes her feel guilty that she doesn’t remember what she’s old enough to know.
Basically, in order for me to keep the character of Nudge as I saw her (more extroverted, not afraid of the world, fascinated with humans like her siblings aren’t, desiring to fit in instead of isolate), I had to put a little bit of distance between her and the flock. Of course, she loves them— that will in no way change— but she’s old enough that she should remember the school (and her dead friends) unlike Gazzy and Angel, but she can’t, and she very much fears forgetting the flock if anything happens to them. So she’s trying desperately to keep the flock close and wants desperately to experience the world at the same time, and doesn’t know what to do when she can’t have both. That’s her biggest character conflict throughout the series, along with that in-between area where she’s not quite where her older siblings are but understands so much more than Gazzy and Angel, and where she stands in that.
So yeah. Nudge’s journey is that in looking for belonging in the world, in her family, and in herself.
This is why she’s one of the ones that gets to find her parent, James Patterson.
Other additions include:
She never straightens her hair. Never. Her resources at the E-shaped house aren’t perfect, but she still has learned how to take care of her hair and has a few styles she cycles through.
She becomes the default person Max sics on people when the flock is trying to befriend them. Also their de-facto diplomat around strangers.
As in canon, she does take some time away from the flock to expirience ‘normal life’. This does not last long due to the stress of being separated from her siblings/not being able to help them and [REDACTED]
Nudge is... not the only person in her head. I’m not focusing on it much because she doesn’t actually know and neither does the flock (I don’t know if they ever figure it out during the series, either), but she has dissociative identity disorder. She’s not aware of her alter(s?). Her alter isn’t super aware of her, either.
The alter that I’ve developed is named Oxy and is not super aware of the outside world. In her eyes, she’s still seven and they’re still at the School. She would not recognize the body as her own if she looked in a mirror.
Nudge actually leaves the flock for a while to pursue her dream of living a normal life. She deserves it. She learns how to make muffins and the basics of software development. These things are unrelated.
Gasman (Birthname: No first name, surname “Falk”)
Honestly, writing Gazzy is kind of hard for me. Partially because I’m not great at writing kids, and partially because I feel like he’s a pretty surface-level character in-series that... isn’t super compelling in canon. But even if that’s the case, I try to treat all of my characters with respect, so here we go. In my rewrite, he escaped when he was four, which was half a lifetime ago for him, so his memories are ill-defined. Therefore, he managed to circumvent a lot of the trauma that the rest of the kids have, and not in the way Nudge did, which is by creating an elaborate blockage in her memories.
Which means Gazzy... really doesn’t know how to deal with all of this traumatic stuff happening. So much of his development turns out to be a coming-of-age narrative. Learning how to deal with the horrors of what his siblings grew up with. Learning the fears that they had the entire time. Losing his innocence when everyone around him never had it in the first place, and being so terribly alone because of it. Because, really, how can you explain such a deep loss to people who never had what he had? How can they help in a way that matters?
Also, relationship-wise, I’m slowly deteriorating the relationship between him and Iggy. Slowly. Or, changing it, at least. Gazzy hero-worships Iggy in-series, and for good reason, because Iggy is super cool, especially in the eyes of an eight-year-old, and especially when Iggy has taken care to cultivate parts of his behaviors to be child-friendly. Part of growing up is seeing the flaws in your heroes, and Gazzy has to learn how to deal with it. End of the series Gazzy is much less closer to Iggy than beginning of the series Gazzy, and neither of them are really okay with that, but they learn to live with it, because that’s really all they can do.
Notes:
I’m keeping the mimickry! It plays a bit of a bigger role because that’s how Gazzy learned to talk. I’m debating whether or not he has his own voice or if he just borrows the flock’s as he sees fit. He also uses it to scream really loudly and occaisonally burst the eardrums of Erasers.
At one point he cosplays as Jessica Jones. No you don’t get any more context than this.
He has a horrible sense of fashion.
I’m changing his name eventually because it sucks. He’s either going to change it to Gannet, Garrison, or Ivy Mike temporarily, and permanently to Zephyr. (I never said I was going to make his name GOOD, because he’s eight, but it’s changing. You’re welcome.)
Angel (Birthname: No first name, surname “Falk”)
It’s just... a completely different character, at this point. I’ve changed so many things about her in an attempt to make her consistent and act like a six-year-old and work in the whole “telepath before she has a solid sense of identity”, so it’s a different character. Also, I’m tired of writing coherently or in paragraphs, so have some interesting facts.
She has epilepsy! Super severe epilepsy! I think she might also develop juvenile MS in the future because her brain has so many scars from being a fucking six-year-old telepath. There’s no way she could get out of that unscathed.
She has more memories of the school than Gazzy, but only because she keeps accidentally reading the minds of Max, Fang, and Iggy. On a related note, she interacts with Iggy as little as possible.
The mind reading means that she has a hard time developing as a normal child with a normal sense of identity or reality. She can’t tell how much people are individual people and how much they’re just extensions of her. Conversely, she can’t tell how much of herself is actually her instead of the thoughts/opinions/identities of someone else. It’s... kinda fucked? But also super not-her-fault.
She’s albino because white wings. Also, because I thought it was cool. This also means that her vision sucks, though. Also she has the biggest straw sunhat and the most stylish sunglasses a six-year-old can have.
She’s responsible for Max shaving her hair off.
She has the highest swear count because I think it’s funny. She’s the only person allowed to say the fuck word in writing. Everyone else can only say ‘hell’ and the occasionally ‘damn’ but she can say whatever she wants for dramatic and comedic value.
She is NOT THE FUCKING VOICE, J*MES P*TTERSON.
Honorable Mentions
Jeb
I’m skipping Jeb because of how little I care about him. He’s a little bitch, next character.
Ari
STILL HASN’T BEEN REVEALED AS AN ERASER. I’ve been writing for 50,000 words and he’s over here saying ‘nope nope not yet, not dramatic enough’. He’s had speaking lines but has refused to make himself known to Max. I am so frustrated with this seven-year-old wolf-child that I’ve already considered how I would kill him, if I decide I want to kill yet another child in my writing.
So, my main thoughts for Ari is that he... really just drew the short end of the stick in every possible way. While Jeb didn’t sign him up for Eraser expirimentation, he didn’t do anything to stop it, and pretty much cut his losses when he realized this expiriment made a wreck of his ‘perfect, unflawed’ son, because Jeb doesn’t consider children of any species to actually be humans. So, Ari really hates his dad, which makes things complicated, because he also really loves his dad and really wants his approval.
Which means that he also really hates Max, because she’s the child that always got Jeb’s time and attention, even when Ari was human. I think, on some level, he knows that trying to tear Max down to a less-favored level isn’t actually going to help his situation— infighting for the love of an abusive parent won’t make them any less abusive— but he’s also seven, and his development is already severely stunted due to becoming an Eraser, and he doesn’t see ‘leaving ITEX’ as an option like the Flock does. ITEX is his everything. It’s all he’s ever known, and they tell him he’s doing the right thing, and he wants them to love him. He wants his father to love him. He knows that if he ever questions ITEX, his father will never love him. So it must be his older sister that’s ruining his life and being a horrible child, and once Ari drags her back down to his level, Jeb will realize who the best child is and love him properly again.
Ari, on an even deeper level, does care for Max quite a bit, because she’s his older sister and he wants that to mean something in a way that ‘Jeb being his father’ obviously doesn’t. He wants what she made for herself, and he hates the Flock because she loves them and obviously doesn’t love him.
Ari, if anything, is the product of neglect, and both loves and hates everyone who shows a chance of caring about him. And he’s seven, so he can’t notice these patterns, let alone break them.
So. Notes!
He doesn’t look like an adult. I thought that was gross and unnecessary. He’s seven, but he looks closer to thirteen or fourteen. Still young enough that he looks like every Eraser’s little brother, and the Erasers high-key treat him like it.
On a related note, he’s the only Eraser who can talk. The others don’t have the mental capacity or vocal structure to replicate human speech, but they can understand language (at about the level of a two or three year old) and are very good at nonverbal communication. This is why Ari managed to climb the ranks despite only having three years of “service” and also looking like a tween.
He doesn’t have an expiration date because that is SUCH a stupid plot point.
I’m giving him a chainsaw! I don’t know how, I don’t know when, but he deserves to have a chainsaw and GODDAMN I will give it to him.
Emergency and Gene
The OCs that I love and also killed pre-series. They don’t have any scenes, because they’re dead, but their deaths greatly effected Max, Fang, and Iggy, and they are very commonly referenced. Their voices are probably Max’s most common hallucination, to the point where she sometimes pretends they’re ghosts that she can talk to. They’re not ghosts. They’re dead.
Dr. Valencia Martinez
I’m actually keeping her pretty close to canon— loving, supportive, the type of person to take in a gsw victim with minimal questions. The difference is that rather than kindness fueling her actions, it’s incredible guilt. She has three goals surrounding Max: Give her as much support in any way she can, teach her as much about chicane culture as possible, and never let Max know that she’s her birth parent.
(She’s probably going to fail at AT LEAST two of those, but it’s the thought that counts.)
Notes:
She has a pet fox named Robin Hood that she rescued from an exotic animal salesman that got arrested.
I think I’m going to kill her. I don’t know yet, but it’s on the table.
Anne Walker
Y’know, the fake FBI Agent. Who’s not actually a fake in my story because I hated that plot point. She’s genuinely an FBI agent who put the Flock into pseudo-witness-protection in order to build a case against the Institute of Higher Living, accidentally got attached to her prime witnesses, raised them for a few months, realized a [SPOILER] and promptly had to let them get the hell out dodge.
I really like the Anne Walker that lives in my head. She is a VITAL part of the Flock’s development, their mental/emotional recovery, and adding to their safety net to fall back on. She serves them as their first adult role model, and is the first adult to show them what parent/child are supposed to look like from a healthy perspective. Though she has several fuck ups, she becomes someone that the Flock genuinely trusts and loves, which makes it all the more difficult for them to leave when [REDACTED].
Notes:
She and Max do butt heads initially, because Max is paranoid and also afraid of becoming uneeded. This ends up being incredibly important because Max needs to learn how to live and find meaning in life without being the designated Leader/Parent/Big Sister
Anne, at one point, sits the entire flock down to teach them about consent, which was something no one ever talked about with them before. She goes in talking specifically about consent in a romantic/sexual sense (because they’re fourteen and that’s something they need to know), but quickly turns into a full-fledged no, people are NOT allowed to do that to you, what the FUCK.
She’s responsible for giving the flock a laptop. It’s because Angel is online schooled (bc telepathy makes actually learning difficult) and was therefore provided with a computer.
Anne is also allowed to swear, but only when it’s funny.
Michael “Grey” Rivers
Aka Grey from the Sewers Aka GR3Y H47 Aka Mike from the Bronx Aka Gifted Child Syndrome Incarnate Aka Would-be-in-MIT-if-his-parents-weren’t-horrible. He’s my son, your honour.
Basically, his backstory boils down to him being a genius, getting into MIT at 14, his (horrible) parents wanting a perfect child who could “make it out” of the Bronx and represent his family/neighborhood/borough to the world. When he inevitably failed their expectations due to stress, a schizophrenic-spectrum disorder that completely alienated him from the rest of his support network, and refusing to take his psych meds because the side effects were horrible and they made it harder to think (and therefore pass his classes), they kicked him out. He fully intends to go back to MIT when he turns 18 and has control of his finances/scholarships/medication/therapy.
So that’s how the flock meets him.
Mike ends up in a very prominent support role for the flock both in technological persuits (helping them track their parents, helping them get information from ITEX, trying to disable Max’s chip and failing multiple times until it becomes a matter of personal honour—), in helping the older members of the flock figure out how to deal with hallucinations/delusions (because he’s actually been to therapy, unlike them), and in being one of the only people who talks to them and helps them without any ulterior motive. He’s not trying to build a case against ITEX/The Institute of Higher Learning, he’s not double crossing them, he’s not plagued with guilt. He just genuinely wants to help them, and they genuinely want to help him, and that’s their first introduction to a healthy, non-codependent relationship.
My many disorganized notes on Michael Rivers:
He’s from specifically Morris Heights, Bronx, NYC.
He would say that his last name is actually Rivera, but his grandparents changed it to Rivers so it would sound more English, and his family has been in America for so long that he doesn’t know much about any Latino heritage he may or may not have. He identifies as African American, not Afro-Latino. He’s just bitter that his family felt the need to change their surname to have better opportunities in New York.
Nudge aggressively befriends him pretty much the moment she meets him, bullies him into teaching her how to code, and he very quickly adopts her as his pseudo-little-sister.
His delusions in the book seemed to involve government conspiracies, but as that’s the one delusion that is proved correct in the book, I’ve decided it would be best if his delusions and reality intersected a bit less if I don’t want to write him having a manic/paranoid episode in the second scene he has screen time. So his delusions are more based on “none of this is real”, “someone is recording everything I do and setting me up to fail” and “my ill-wishes on people can and will come true if I dwell on them too long.”. Government conspiracies are one of things he is skeptical about because he thinks most conspiracies are either “CIA admitted to this twenty years ago” or “antisemitism”.
He’s taking online free college classes that don’t actually give him any college credit, but they have good information and help him feel like he’s working towards something. He plans to double major in computer sciences and electrical engineering, minor in marine biology. He’s wanted to join NOAA since he was twelve and he is nothing if not stubborn.
There you go. These are my characters, now. I have custody.
35 notes
·
View notes
Text
The Peeker’s Compromise: A Fair(er) Netcode Model
Many first person shooters are plagued by a netcode artifact known as the peeker’s advantage. I propose here a technique for correcting this bug, based around normalizing gameplay in such a way that human reflexes and skill decide the outcome of competition (as opposed to network latency or artifacts of varying netcode designs, discussed shortly).
When a player in a first person shooter is moving around the game world they exist in a position on their own game client that is slightly ahead of their position on the server. This is a solution/side-effect of clientside prediction which is ubiquitously used in first person shooters giving the player instantaneous movement and controls that feel like a single player game despite controlling a character that is moving around on a remote server.
If we were to visualize the difference between the clientside player position and the serverside player position it would look like two characters chasing each other. How far apart the two characters are depends (in descending order of usual importance) on how fast movement is in the game, the latency of the player, and the tickrate of the server. But how big are these differences in the actual games of the current era? Are the two states of characters practically overlapping? Or is one several meters behind the other? The answer -- which varies by game and by internet connection -- is that the desynchronization between these two positions is significant. Over amazing internet connections in games with slow moving characters the desynchronization is usually on the order of 1 player length. So imagine any fps game character (valorant, cs:go, apex, overwatch, fortnite, cod, etc) -- and then imagine them creeping or walking around slowly. In this scenario the desync between the two states is such that one could picture the character being followed by its clone, touching. If they move *really* slowly then they’ll be overlapping. However as the characters break into a run their clone will trail them by more -- maybe 2-8 player lengths depending how fast characters are in the game. If a player has a high latency the clone will be ever farther behind in all scenarios except holding still.
Now when a player shoots their gun in all of the above games, the game engines will calculate the shot based on where the player perceives themselves. That means that as you play the game what you see is pretty much what you get. You don’t have to manually correct for lag while aiming in modern shooters -- just aim for the head right where you see it. However this introduces the peeker’s advantage. A defender can hold a corner with their crosshair primed to shoot anything that appears, but an attacker (the peeker) who comes around that corner is ahead of their server position and thus they get to a bit of extra time to "peek” and shoot at the defender before they themselves are visible to the defender. Depending on the actual amount of lag and the game itself the defender perceives themselves as either having been shot insanely quickly right as the attacker appeared, or maybe if the lag is not as bad they perceive themselves as having gotten to trade shots with the attacker, but ultimately they lost. The attacker perceives nothing special -- they just walked around the corner and shot the defender b/c they were playing aggressively and have superior reflexes (or so they think).
How big is the actual peekers advantage? Well it varies by game, but an article put out by Riot Games about Valorant goes into detail about how much the peeker’s advantage affects gameplay, and how their engine attempts to minimize it. It’s a great read: https://technology.riotgames.com/news/peeking-valorants-netcode. But to summarize, using 128 tick servers (very fast) 35 ms of internet latency (fast) and monitor refresh rates of 60 hz (standard) they calculate an advantage of 100 milliseconds after extensive optimization. That’s fast, but is it fast enough? Well back in 2003 I used to be a competitive Counterstrike 1.6 player at around the same time that I was obtaining a psychology degree with a particular interest in human perception (reaction time, how our eyes work, perception of subluminal images that are shown very quickly). I tested the reflexes of myself and all of my teammates. Competitive gaming didn’t have the same structure back then as it does now (everything has a ladder now -- back then it was private leagues), but by modern standards we were probably top 3% ladder players or something like that. Generally speaking there isn’t much of a speed difference in the whole pool of pro-gamers, at least when compared to new players. They are all pretty fast. Response time for watching a corner and clicking as you see a player (already perfectly lined up) fall into the range of 150-190 ms. Tasks that involve moving the crosshair to react quickly (as opposed to having had perfect placement already) slow that down another 50-150 ms. But generally speaking the competition between two similarly fast players with good crosshair placement comes down to very tiny units of time with even 10 ms producing an advantage that is measurable (both Riot and I agree about this). This means that had the server allowed for a double K.O. (which these games do not) we would find that in fact both players were very good and would’ve killed the other just 20-50 milliseconds apart. Valorant and CS:GO don’t work like that however, and instead the game essentially deletes the bullets from one of the players and leaves the other alive. Unfortunately this difference in human reflexes amongst competitive gamers is entirely gobbled up by 100 ms of peeker’s advantage -- meaning that at high skill levels the peeker will very often win and the defender will very often lose. So while the Riot article celebrates the success of engineering that allowed Riot to reduce the peeker’s advantage as much as they did, if you read the fine print you’ll find that the peeker’s advantage remains huge.
I don’t mean to pick on Riot, far from it. They’ve clearly done an amazing job. The other games I mentioned earlier are presumably in the same approximate ballpark, though I can tell you from personal experience that some of them are a fair margin worse. Not all of the games I mentioned use a 128 tick server (only one does). They also have longer interpolation delays and other little engine details that slow things down further. Riot is also an insane company that literally owns/builds the internet just to reduce latency for its players -- so if we want to take away a general sense of how bad the peeker’s advantage is in most games we should assume it to be worse than the scenario described above regarding Valorant.
Now that I’ve discussed at length the peeker’s advantage, allow me to present a related netcode model that attempts to solve these problems: The Peeker’s Compromise. If we delay the time of death on the serverside by the timing difference between the attacker and the victim, then we can allow the defender an equal opportunity to shoot the attacker. The server can then determine the winner (and the remaining damage) based on the performance of the human (instead of using the ~100 ms of engine-related advantage and internet latency). So let’s use some numbers for a hypothetical situation. Let’s say our game has 128 tick server, the players have 35 ms of latency, and 60 hz screens (like the Valoran example from earlier). Right as a player peeks another player they essentially get to shoot 100.6 ms sooner than their victim. As their shots arrive at the server the server might calculate that the victim has died -- but rather than killing the player it will keep them alive for 100.6 ms PLUS their own latency, which in this scenario puts the total at 135.6 ms. If during these 135.6 milliseconds the server receives shots where the defender hits the peeker, it will enter a section of code that attempts to settle this discrepancy. First off, it is entirely possible that after compensating each shot for the difference between the players we find out that one truly was faster than the other -- the game could use this information to decide which one lives and which one dies. It also might make sense to allow damage to legitimately trade kills and to build double K.O. situation into more first person shooters.
Let’s talk about the artifacts of this new and proposed system. In low-latency games with a high tick rate this change would be subtle -- we would just have no more peeker’s advantage. As latency increases all way up to 200 ms we will have a new artifact. Instead of having a more severe peeker’s advantage we’ll end up with a scenario where it looks as if players are taking 1-3 extra bullets beyond what would normally kill them -- although if you stop shooting early they still end up dead a few milliseconds later. The Vandal in Valorant (similar to the AK in cs:go) fires 9.75 shots per second, which is one bullet per 103 ms. So in a best case scenario the player death is delayed by the time it takes to fire one extra shot at full auto, and in a worse case scenario we add 1 bullet per added ~100 ms of waiting done by the engine. It would also make sense to cut off certain shots from being counted from a laggy player (existing systems already do this in their own way).
Gameplay at lower skill levels wouldn’t really be affected one way or the other. It isn’t affected much by the peeker’s advantage either -- players have to know where to aim and thus be involved in legitimate reflex test before we’re down to something so close that milliseconds of delay have an effect. If players are oblivious to each other, or place their crosshairs incorrectly as they come around a corner then the added slow down of the human having to make a new visual-search-decision-plus-adjustment is too slow for any of this to matter. But at higher skill levels there would be some actual changes to gameplay. The most significant change is that players would be able to hold corners -- and if they’re truly faster than the peeker they would win. In such a design it really would make much more sense to allow two players who fire at essentially the same time to kill each other which if adopted would need to be addressed at a game design level. Also games that had an alternate method of very indirectly addressing peeker’s advantage, such as weapon instability during movement as a major element (arma, h1z1, pubg, tarkov, etc), would have more options, and may need to tune existing timings to get the same feeling back.
The underlying netcode behind the peeker’s advantage affects more than the classic peeking situation. It also affects two players picking up an item at the same time (it decides the winner here). And it also is present when you’re playing a game and you duck behind cover and take damage after you should already have been safe (the peeker and the victim are on slightly different timelines). Neither peeker’s advantage nor my proposed peeker’s compromise actually removes lag of the underlying systems of the network connection nor the game engine ticks, both simply *move* delays around such that the controls feel responsive and the latency is suffered elsewhere. There’s a certain physics to the realm of network programming. As I like to half-jokingly say: “Lag is neither created nor destroyed [by compensation techniques.]” So the same problems would still exist, though the Peeker’s Compromise is philosophically different. Where the peeker’s advantage says let the fastest internet and the more aggressive player win, the Peeker’s Compromise says let the more skillful (in terms of accuracy and speed) human win. Outside of a double K.O.esque duel however, this is subjective. Who should pick up an item when both players tried to pick it up at the same time? Well the old method says the one with the better internet gets it, the new method suggests perhaps that we should compensate the timing to remove the internet/engine delay and award it to whomever was faster. But what about getting shot after reaching cover? This is really up to the game designer -- is it more impressive to tag someone barely as they run off? Or more impressive to slide behind a barrier right as you get shot? It’s a design decision. It’s also possible via this proposed system to compromise. The engine design I propose has more data in its context with which to make decisions, courtesy of temporarily allowing ties to occur which get addressed after both players take an action. It could say well that was an amazing shot, AND it was an amazing dodge. After crunching the numbers the decision is to deal a hit but cut the damage in half as a compromise between the feats of the two players.
#netcode#network programming#peeker's advantage#Peeker's Compromise#multiplayer#first person shooter#Riot Games#Valorant#Valve#Counterstrike
4 notes
·
View notes
Text
CAA protests;
okay, i want to talk about something important. let me start off with the fact that i'm not an American and i live in India. so basically, i am asian, brown and also a Muslim.
this in no means is saying that i do not support BLM, i do, i support the protesters and their cause. yes, i signed all the petitions.
i want to use this as a platform to talk about a similar thing that happened in India during November, 2019 - March, 2020, when lakhs of people took to the streets of India (all over the country) to protest against the Citizenship Amendment Act (CAA) being passed by the government. according to which, the government will be discriminating us based on our religion and strip people off their citizenship. yes, you heard that right. so we took to the streets to protest and the police brutality was through the roof. not only did they beat up civilians on the roads but also raided national level universities to beat up the students for protesting against the government. we live in a democracy, it is well within our democratic rights to raise questions and protest. the government is directly responsible to us, the prime minister's office. (its in our constitution, the president is not answerable to the people but the PM is.)
i study law at Aligarh Muslim University (AMU). on the night of 15th December, 2019, police forcefully entered our main gates (they've no jurisdiction inside the gate btw) and beat up students protesting peacefully on the road. 24 consecutive expired poisonous tear gas shells which maimed a student, lathicharge (beating with the police batons), shot with rubber bullets, you name it we went through it. they raided the hostels, and beat up the kids who weren't even part of the protest. they kept hurling abuses at the students and also kept saying "jo log kashmiri hai, un madarchodo ko maro pehle" (the people who look like kashmiri, beat up those mfs first). yes, that's verbatim btw, i'm not exaggerating.
i can go on and on about that night really, so instead you can read what happened in AMU here. i also have the original investigation report by the committee that is mentioned on that site.
other universities faced similar and worse atrocities. you can read how brutally Jamia Milia Islamia (JMI) students were beaten up, here and how local goons who feel that Hinduism is threatened but the presence of Muslims in the country entered another national university, Jawaharlal Nehru University and beat the students up with metal rods, you can read about it here.
and yes, none of the perpetrators of these attacks are arrested. even if they were, they are out on bail now.
we boycotted classes for months but got ZERO justice, instead, now under the guise of lockdown, the government has been arresting the leaders of the protests. lmao, you know the first the government did when lockdown started? they cleaned the graffiti off the walls of the universities which the protesters had made. they cleaned off fucking graffiti which were just quotes by historical figures in the spirits of dissent while the doctors kept begging them for PPE. the government clearly have their priorities set straight.
the women of the country took to shaheen bagh (Delhi) when the students were attacked and sat there in protest for 101 days. even in cold temperatures of below 1°C. mums with their one month old babies sat there, old ladies as old as 80+ sat there too. literate, illiterate both the groups of people sat there and they meant to sit there indefinitely but because of lockdown that wasn't possible and they had to vacate the place. oh, even they were attacked (more than once) by a guy carrying a gun who was ready to shoot at the protesters while the police WATCHED. they fucking stood there and watched. a guy advanced towards the attacker with his hands raised saying “let’s talk calmly” and that fucking privileged jackass shot the protester in the hand. all the while, the police just watched. you can read about it here. (he said "only Hindus will have their way in this country.")
a 4 months pregnant PhD student of Jawaharlal National University has been jailed without any justification. her case is still not being heard before the court and she's being denied basic human rights, living in a prison during a fucking pandemic. an excerpt from the Print, "Zargar, a 27-year-old M.Phil. student from Jamia, is over three months pregnant, and was arrested by the Delhi Police’s special cell on 10 April. She was later denied bail and, on 21 April, charged under the stringent Unlawful Activities Prevention Act (UAPA). She was associated with the Jamia Coordination Committee (JCC), and was part of the anti-Citizenship Amendment Act protests organised by university students in December and January. She was arrested for allegedly leading the anti-CAA protest at Jaffrabad metro station in February."
this is nothing, most of the Muslim people arrested during this protest haven't been released or are simply forgotten. lawyers were not allowed in the police station to bail them or being allowed to talk to them. most lawyers in the country signed up their numbers and other contacting details on the Internet with their locations so that if someone was arrested, they could call them up and the lawyers would bail them out (free of cost).
this discriminating and draconian bill not only affects the muslims but also the people on the lower rungs of the social ladder. i don't believe in caste. i do not agree with the system but it existed widely at a time when i wasn't even born, so there's not much i can do about that. but right now the government is bringing up the caste again, people who are Vaishyas and Shudras will also be stripped off their citizenship while being sent to detention camps. yes, India is already stocked up with their detention centers. so yes, i wasn't there at that time but i am here right now and i refuse to be okay with the government discriminating against us based on caste and religion.
lmao i totally forgot to mention the riot that broke out in February, 2020 which resulted in a recorded deaths (murder) of 53 civilians (mostly Muslims). that's the recorded death count but according to various people who were present in Delhi at the time and witnessed the riots happening, they claim the missing persons report (unreported) is in thousands. and over hundreds were killed. you can read more about the February 2020 Delhi Riots here.
there's so many more incidents that happened, and all the government has done is: NOTHING.
our current PM is the prime suspect of the Gujrat Riots 2002, which was a pogram led by him and it killed over thousands of muslims who lived in gujrat.
i didn't write this here to ask you for help, no, instead i want you guys to read this and remember this. don't forget our voices, because we're all together in this fight and the others to come. forgive but please don't forget.
like faiz ahmed faiz said, "bol k laab, azaad hai tere."
#protests#caa protests#cab protests#anti caa#anti caa protests#i know i used the blm tag but you've to realize i'm not trying to take away any attention#or jump on the bandwagon#i just want you guys to know this#like yes this happened too#this is also an example of draconian goverment#and peak police brutality#if you're wondering yes i did go to the protests#the ones staged in my university as well in my state#when i came back home because our university went into a lockdown and 16k students were evacuated due to that night's incident#i came back home but that never stopped me from joining in protests#make your voice heard#use the platform#speak up#choosing to keep quiet during a time of dissent is equivalent to choosing the governemnt#let that sink in and remember it
22 notes
·
View notes
Photo

BB King
The Best Of BB King (ABC Label)
@ 1973 US Pressing
****
In spite of 1972 being one of the stalest years in the history of popular music, the spate of reissues from all the major record companies and countless minor ones picks up more speed all the time, and the results (uneven as they are) are generally encouraging. All four of these albums represent attempts both at recapitulating the contributions of three black titans and cashing in on the belated widespread recognition of those contributions. Curtis Mayfield had a long string of hits with the Impressions but it took Super Fly to make him a household name. Ray Charles may have been bigger in the late Fifties and early Sixties than he is now, but he was more vital then, too. His earlier work deserves the endless repackaging. As for B.B. King, I can still remember the first time I saw a couple of kids in a department store line, audibly opting to chance $3.50 on an album called Lucille because some Limey speedfreaks had made it hip, and I’m sure that both they and I are glad they did, but B.B. King’s career didn’t begin when the royalties began pouring in from flash guitar covers and he was invited to tour with the Rolling Stones, so a thoughtful collection of vintage King is imperative.
Ray Charles doesn’t have as many hits these days as he used to, but he’s more renowned than ever before anyway. He’s become something of a national institution, like the Duke Ellington of R&B; even Pres Nixon has made an official declaration of Charles fandom. But the Pres ain’t exactly the type to do back-flips for “What’d I Say” or “The Right Time,” and Ray’s been hacking his way ever deeper into the tissue veldts of MOR for a full decade now. He still makes a good record every once in a while, but in his prime he was raunchy enough to split your skull and rock you into fundamentalist frothing fits. He created rock ‘n’ roll as much as Berry or Little Richard or anybody; he practically drew up the blue-prints for an entire era of gritty Stax R&B, and nobody ever wrenched their way deeper into the soaring terror of the blues. If you want to hear him really rip the joint apart and put it back together again with a cry, go back to those great Atlantic sides. The essence is on three albums: The Genius of Ray Charles. The Genius Sings the Blues and The Greatest Ray Charles. Or, for a fantastic overview, Atlantic’s four-record compilation The Ray Charles Story. Ray’s move from Atlantic to ABC made him rich and, initially at least, the musical rewards were probably as bountiful as ever and an idiomatic breakthrough besides. In search of a buck-grabbing formula, ABC sent him through albums like The Genius Hits the Road (“Georgia on My Mind,” “Mississippi Mud,” “Carry Me Back to Old Virginny” etc.), and miraculously he came up with brilliant, deeply soulful amalgams of gospel roots and mainstream pop. But the real turning point was a record called Modern Sounds in Country & Western Music, which was released about 12 years ago, at which time it promptly became the Number One album in America and changed the face of the milder strains of radio pop as irrevocably as his early work had done for rock ‘n’ roll. All through the Sixties the marriage of C&W to blues or bluesy euphemisms reigned, and whether you picked up on Glenn Campbell or Lee Hazelwood or any one of the rest of the multitude exploiting this new form, it all began with Ray Charles.
Ray himself exploited his innovation till the power of the original purveyor began to pale, and not everything on All-Time Great Country & Western Hits is great. But enough of the prime is here to make it worthwhile, especially if you haven’t picked up any of the many previous Charles reissues. “I Can’t Stop Loving You” was his first big move at this amalgam, and it’s still as tearfully puissant today as it was in 1961. Add the occasional C&W standard rendered in R&B style fully as uncompromising as any early Charles (the boiling “You Are My Sunshine” being the earliest and most potent example here), and you have a record as profound and essential as anything out today.
Lots of people think the Super Fly soundtrack the best soul album of 1972, but those unfamiliar with the Impressions owe it to themselves to discover what Curtis Mayfield was up to in the times before the most vital expression of black music was almost forced to deal with heroin death. “Freddie’s Dead” is already a Seventies standard, and His Early Years with the Impressions is a fine reminder that Mayfield possessed a consistent gift for creating hits destined to become classics all through his career. The vocal harmonies of the Impressions could be as mellow a balm as anything by Smokey Robinson and, like Robinson, Mayfield was never saccharine.
In fact, this late rehearsing of his past achievements impresses you firmly, even if you missed it first time around, with the fact that Mayfield was a groundbreaker in the nascent status of black popular music as a direct expression of the changes in black consciousness. When “Keep On Pushing” was a hit it was fairly easy to find shadings of meaning in its lyrics which formed as clear a link between the oldest gospel message and something far more topical, as it was to revel in the perfect evolutionary link between the purely musical freight carried out of church and the AM soul stylings which reached their summit in the mid-Sixties.
“It’s All Right” illuminates the same historic junction, and “We’re A Winner” takes it out of the realm of ambiguity, straight across the threshold of blatant backbeat radio anthem. Meanwhile, if you’re only familiar with things like “Gypsy Woman” in the eviscerated cover versions of white fluff-boys, get ready to be moved to the shoals of your soul by a whole other, more masterful and authentic type of vocal dramatics.
Again, the packaging is pretty bland, and another caveat is that lots of this stuff has been observed in the original albums selling for far less in bargain bins around the country (plus the fact that lots of those original packages were a joy in their very crassness, like that great Keep On Pushing cover observed among Dylan’s most conspicuously prized possessions on the Bringin’ It All Back Home jacket). But if Super Fly was your introduction to Curtis, you’ll want to make a point of picking this up before his pre-soundtrack solo albums, which qualitatively fall way below both what preceded and followed them.
B.B. King has in his belated flush of success become almost as frustrating for the aficionado of the Real Shit as Ray Charles. B.B. plays Vegas now, no fault there, and hits both the colleges and TV talk shows. So he’s finally out of the scuffle, at late long last. Unfortunately, his music has also gotten less interesting with each successive album. Vintage King wasn’t just something for punks to prove they could tell a good blues guitar solo from a bad one; it was stark, evil stuff. Troubled and troubling.
The difference between these two B.B. albums is the difference between chills and chips, between hearing a raw edge that makes Back in the Alley more than just a good colorful title, and satisfying your curiosity about how B.B. King would work in the context of a standard Leon Russell Hollywood camp meeting. And it’s not just a matter of backalleys vs. proximity to pop-stars: There is just no way a cut from the legendary Live at the Regal album, which molded countless Sixties guitarists and stands alongside things like James Brown at the Apollo as one of the all-time classic in-person R&B disks, there is no way something like that is not gonna shut down a pleasantly perfunctory session cut at Cook County Jail two or three years after Johnny Cash made it both righteously hip and fiscally sound to jam for jailbirds.
Actually, the chronological distance between the two albums is not all that great. Back in the Alley begins in 1964 and leaves off just short of where The Best of B.B. King picks up, but the difference in mood and meat is sufficient to make the choice clear, even if Best Of does have the incredible “The Thrill Is Gone.” It’s the fine line between a man playing with total commitment to an audience he has probably had for years which can savor his peaks and bear an off night, and a man playing for people who’ve been sold his legend and will love anything because they know they’re supposed to. But you don’t have to be any kind of connoisseur to tell the difference.
Rolling Stone 1973
4 notes
·
View notes
Text
Digital Wall Tiles - 6 Phenomenal Benefits of Choosing it for Your Home
Digital wall tiles have become the 'darling' for homeowners and architectures in the past few years. As people realize that home is more than just a 'place to live,' they have started spending more bucks on it besides taking a personal interest.
The house wall designs are no longer limited to green or yellow colors. Now there are plenty of ideas available in the market on how to decorate house walls. One such way is using digital wall tiles instead of wall colors. There are many reasons to choose glazed vitrified tiles (GVT) for your home, office, outdoor, or other space. Let us learn about each of its benefits in brief.

A. Versatility
Versatility is one of the prime features of digital wall tiles. The advanced tile printing technology allows transforming regular tiles into an artistic masterpiece that ultimately helps provide a stunning look to your space.
Using tile printing technology, we can design and print anything on the tile surface such as photos, artwork, various surface textures etc.
B. Durability
Digital wall tiles are the best option for wall tiles. Compare to other wall tiles, glazed vitrified tiles offer higher durability. It can withstand higher temperatures and moist weather. These tiles are also prone to wear and tear.
The higher durability of the tiles will not only save you from the frequent hassle of replacement and repairing, but it will also save you from the wastage of your hard-earned money.
C. Aesthetic Appeal
It is not exaggerated to say that digital wall tiles have indeed kickstart an aesthetic revolution in the wall designs industry. Just like floor tiles, you now have multiple design and pattern option in glazed vitrified tiles too.
You can literally create and design numbers of patterns and motifs using these wall tiles. Its sleek and stylish texture will add an aesthetic appeal to every space wherever you use them– from kitchen to bathroom to storage to outdoors.
D. Multiple Finishes
Along with various designs, Digital wall tiles also have multiple finishes. The three key finishes are Gloss, Matt and Silky. Gloss tiles are reflective in nature. It creates a shining, mirror-like layout. The matt tiles are relatively less glossy compared to gloss tiles, though it looks natural and stunning.
On the other hand, a silky finish is mostly used for sophisticated colors such as black, blue, white etc., to add elegance to space.
E. Well Complement With Surrounding
Digital wall tiles go well with almost all kinds of architecture, be it contemporary, modern or traditional. The digital tiles' ability to transform its surface in all kinds of texture and design allows them to complement its surroundings.
Based on the place's interior or exterior, you can plan the glazed vitrified tiles' design and texture to ensure it blends well.
F. Ease of Maintenance
Last but not least, digital wall tiles are easy to maintain. You don't need a special treatment to maintain its shining and durability. Even basic maintenance will do the wonder. Clean it with vinegar added water once a month. Gently use the scrub to remove tough stains.
We hope that this list of benefits has helped you understand why you should always choose digital wall tiles over wall colors or regular wall tiles.
YGC is a reputed manufacturer & exporter of a range of ceramic products, including glazed vitrified tiles, porcelain tiles, nano tiles, parking tiles and sanitary ware. The company also manufactures and supplies re-plastic sheets, PP woven bags and PVC laminates, among other PP products. Visit their website to know more about their products and service.
1 note
·
View note
Text
Week 7 Morning Lecture

Midsem
First we looked at some questions on the midsem. Apparently there was quite a good outcome overall (subjectively according to Richard), and most people did worst on questions 5 and 10.
Question 5. National Security Guy for the President Missiles Richard reasons that the answer is in fact Type 1/Type 2 Error that you would be most worried about. Although the rest of the answers would be things that you would be concerned about, the main worry is that you launch when you shouldn’t (False Positive) and can’t take back the launch or you can’t launch when you need to (False Negative).
An attacker therefore could identify that only the President is able to command the launch as a single point of failure and then take him out, thereby dearming the whole nation of their firepower. In that instance, if any other nation were to attack America, then they wouldn’t be able to order missiles out because only the President has the capability to, who is now dead.
Ironically, the movie Dr Strangelove that we watched later in the evening session had a great display of this example - where a general was able to exploit the system and direct an attack on Russia which could not be recalled without the secret passcode.
Question 10. The Merkle Puzzle Question As revealed, Richard got this answer wrong, the original intended answer was something that could be broken feasibly by a person the night before the exam (Lachlan) and an attacker would not be able to in a reasonable amount of time. This is essentially the idea of Merkle puzzles - where on average, the bad guy has to do a work factor of around 1/500000 (half a million) before they crack the right one.
The originally intended answer was RSA 512 since it was the best answer out of all the options. The other options were as reasoned:
One Time Pad - Uncrackable
Caesar Cipher - Too easy
Vigenere Cipher - Too easy
RSA 2048 - Too hard (takes too long)
SHA256 - A hashing algorithm, irreversible
However it was noted that the RSA cracked would be done using the PUBLIC KEY for ALL OF THEM. Therefore an attacker would only have to crack one for the private key and then be able to crack the rest instantly!
What is proof of liveness? There were some additional security terms that were introduced in the exam which I hadn’t encountered before. One of which is this idea of proof of liveness, which essentially is a indicative check if a person is on the other side of the handshake or not. In modern senses this is like a challenge response, where the person requests access and gets given something to solve to prove they are alive.

Diffie-Hellman (Key Exchange)
From last week we talked about being able to communicate security with someone whom you’ve never met over the internet. However, for a computer, who only knows 0s and 1s, the only form of verification is through shared secrets (something you are, something you know and something you have). However, this poses an issue with someone on the other side of the world
how can you securely communicate the KEY used in order to communicate privately?
The answer is Diffie-Hellman key exchange!
Originally conceptualised by Ralph Merkle (this guy wow lmaooo) and named after Diffie and Hellman, the Diffie-Hellman is a method to securely exchange keys over a public channel. DH is one of the earliest implementations of a public-key protocol in cryptography.
The basic mathematics behind DH is that it utilises exponentiation and modulus in order to obtain Confidentiality. In the lectures, Richard simply covered a simplification using only exponentiation:
Richard and another person (let’s call him Frank) agree on a base number (e.g. 5). This is assumed public information, so it’s fine if everyone knows. Now then Richard and Frank each think of a secret number which they don’t tell anyone
Richard’s number = 7
Frank’s number = 3
Now they simply take the base and raise it to their secret number
Richard: 5^7 = 78125
Frank: 5^3 = 125
Then they simply send each other the result of this calculation (or the last few digits if you were to imagine it was modded). Although this example seems quite trivial to break, imagine if the base and the secrets were 20 digits long! Then it would be a lot harder to reverse the base and secret.
This occurs because of the Mathematical loss of information which makes it easy to encrypt and hard to reverse, also known as the Discrete Logarithm Problem, and is the reason why DH is so effective. (See: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/discrete-logarithm-problem)
In this case, the base and the result of the calculation are PUBLIC, while the kept secrets are PRIVATE.
Next to add another layer of security, Richard then takes the result sent by Frank publicly and raises that number to his secret number - and Frank does the same with Richard’s result.
Richard: 125^7 = 4E14
Frank: 78125^3 = 4E14
The resultant numbers from both operations are thereby EQUAL because of the COMMUTATIVE PROPERTY of powers. In this way by getting the same result, Richard and Frank are able to verify that they are indeed communicating with each other through a public protocol - and they can settle on the end result as the key for their communication.
The reason this works so well is because just through the initial messages, it’s impossible to find out from them what they key is. Since the key was never actually transmitted in messages, listening in on the communication won’t help an attacker! You’re not actually sending any information during the key exchange, but creating one together :)
We do this exactly in practice, where we mix up the information we are sending so that whoever is listening in is unable to decipher the secret from the message. This is called FORWARD SECRECY/SECURITY, which means that even if in future, if someone were to go back and uncover your old messages, they would still be encrypted and unable to be read.
Note: this doesn’t however provide Authentication because you can’t actually verify if it is really Frank or Richard from the other side. You can only tell through this that you’re still sending it to the same person, and that your line is confidential.

Sources: https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
https://security.stackexchange.com/questions/45963/diffie-hellman-key-exchange-in-plain-english
https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/diffie-hellman-key-exchange-part-2
Krak de Chevaliers
Krak de Chevaliers was a multi-layered fortress run by the Knights Templar in 1144CE (many years ago). This boi was STACKED, with a strong defence system (Defence in Depth) and prime location perched atop a hill - and as such was considered for many years virtually IMPREGNABLE, being the largest Crusader castle during the 12th century.
Many attacks were held against this fortress, and a few got through past the first wall, but none were able to reach the inner before being eviscerated. It was THAT GOOD.

The design of this boi is ingenious, with every line of physical defence covered. First it has several concentric layers that wear down attacks during their sieges. Then there are moats and several stages in which armies have to be split up due to the restrictions in entry points. Furthermore, they’ve got towers to lay hellfire to any attackers, with an elevated view for the inner wall which is both hard to penetrate being up so high as well as advantageous to provide a vantage point to provide support to the outer wall defences. Then you’ve got sloped points that are vulnerable for attackers and good for the defenders as well as sharp purposeful right angled walls so that there are minimal areas to cover against fire.
In the end however, the fortress did eventually fall to Muslim hands and the knights surrendered after a forged letter was sent through ordering them to lay down. So in the end, humans were the issue and despite all the complex defence mechanisms in place, even the mighty Krak de Chevaliers fell to SOCIAL ENGINEERING.
Sources:
https://www.ancient.eu/Krak_Des_Chevaliers/

Vulnerabilities
Let’s go over a few terms real quicc:
Vulnerability: a potential weakness in something
Exploit: taking advantage of a weakness (the application)
Software Bug: a mistake in something
Memory Corruption Memory Corruption refers to when a bad guy is able to modify and change what happens in memory (i.e. modifying address, contents stored in memory, etc). Through this the make programs do things that they aren’t originally supposed to.
One form of memory corruption is a Buffer Overflow which we saw last week (https://insecure.org/stf/smashstack.html) covered by Aleph One. This memory corruption happens on the Stack where a buffer can be written to past its given size and as such, data gets overwritten on the stack.
The vulnerability of this lecture is FORMAT STRINGS :) Now the thing with vulnerabilities is that it’s quite like the flu. Once someone discovers the vulnerability, they quickly discover that it’s everywhere. Every program and piece of code has it. Once word gets out, the big companies quickly work to patch it, but with smaller institutions and businesses (which is the vast majority of the population), don’t bother with it for a while; because of laziness or cost benefits, etc.
A simple way to illustrate the format string vulnerability is through a simple C program. You may be familiar with the function printf()from first year computing. The thing with printf()is that by good practice, you should be using formats as the first argument in the print function ( printf(%s, “Hello World”)). However we know from experience that this is NOT the case. Programmers are lazy and simply write the string as the first argument without specifying a format in the first place. In fact, pretty much every tutorial every will start with just telling you to pass the string “Hello World” directly into the function.
The issue then again lies in the case where a user is allowed to enter input and a programmer then prints whatever they enter to stdout.
For example, the program:
reads in an input
that input is stored in a variable name.
then the program simply executes printf(name);
Sure, the program is harmless when the user enters what we expect them to, however what if a format argument is passed (i.e. %d, %s, %n, %t, etc)?
Well if the user entered something like the string “Richard%x”:
printf()will take the letters Richard
print that out
and identify %x and look for the NEXT ARGUMENT to substitute into %x
However, in the above input, there is no next argument like in the case of %s, “Hello World’. So the program will then look to the next item on the stack and use that in place for %x. Thereby this format string attack can be used to gather information about what is stored on the stack, and you can decipher what was done in the previous functions.
While this may seem quite harmless, with just gathering information - this isn’t the extent of a format string attack. In fact, there are many many MANY formats you can use and each of them do a variety of things in C.
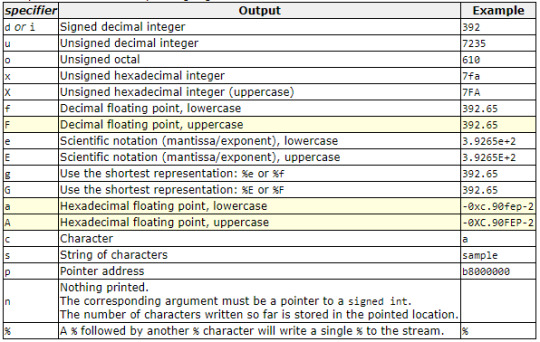
(this C++ but it the same lol)
From above %n is frighteningly scary because it actually WRITES TO MEMORY, storing the number of characters written to the pointed location. Now this can have extremely dangerous effects and is what we are so scared of when it comes to format strings attacks and memory corruption!
In practice, this is however quite difficult to do, but very much possible. It does take a certain amount of luck and preparation in order to successfully perform a truly devastating format string attack, however, Richard likens the situation with vulnerabilities to SWISS CHEESE.
If you take a block of swiss cheese and you slice it up in a few pieces, then rearrange it multiple times and try to line them those pieces up together, once in a while those holes will line up and you can stick your finger right through. It’s very much like this in reality. The bugs are the little holes which seem so small and insignificant on their own, with little format string reads from memory and buffer overflows. But if you pair all those attacks together, once in a while those bugs align and an attack is successful!

More Terms to Know
Shell Code
Let’s say you’re attacking a system, and you’ve gotten in - but you’re unsure what you want to attack at the moment. Well what you can do is simply generate a nice private shell externally on your computer which has access to their system remotely. This is what is known as shell code - writing code that generates an external shell which you have control over.
NOP Sled
NOP is a command in machine code that literally makes the CPU do nothing for a few cycles. So a NOP sled is simply just a sequence of these instructions to make the CPU slide to the desired destination. Therefore an attacker is able to utilise a NOP sled by making the program go to a specific address where they may have stored malicious code! The ingenious aspect of a NOP sled is that they are used to increase the attack area over a huge range of memory. That way the chances that the program lands anywhere in the NOP sled increases, and it trickles down to wherever they want to run. This deals with the issue of memory being randomised and allocated everywhere.
In Assembly, this is literally just:
NOP; NOP; NOP; NOP; NOP; NOP; NOP; // etc etc lmaoo
*Interestingly you can find programs which try and exploit this by simply Googling a sequence of NOP commands and you’ll land upon matching ones with NOP sleds :) (https://github.com/snoack/python-goto/commit/2b0f5e5069cbb88776b0d070d6608e4064735d96)
There are also other ways in which you can make a program ‘do nothing’. For example, making a program add 1 and subtract 1 continually to a register.
Sources:
https://www.oreilly.com/library/view/practical-malware-analysis/9781593272906/ch20s07.html
Responsible Disclosure
Let’s say you’re a bug bounty hunter, and you happen across a bug in some licensed software. What is the right way to go about alerting the developer/company? Normally companies will have some sort of feedback form in which you can submit reports on bugs and how to reproduce them. However if this isn’t the case, normally you should do some research about the bug you’ve encountered and generate a report to send to the company. In this way you’re first giving them time to fix it. In the instance that nothing gets done after you’ve informed them, you should slowly escalate the problem up the chain. The most important thing is to NOT LET THE BAD GUYS HAVE IT (unless you are one of them or ludicrous amounts of money is involved).
Assets
Assets are a very hard thing to define, but identifying what is important to protect is incredibly important because it allows you to prioritise your assets and how you can go about setting up defences.
In the lecture, Richard showed us the starting clip from the movie ‘Team America’ where a satirical team of over-the-top terrorist fighting Hollywood personalities went above and beyond to protect what they believed was the MOST IMPORTANT asset; the lives of the French civilians. In the following clip, we can see them using all force necessary (minus the hand to hand combat from Karate Kid) to put down the terrorists, but in the process they destroy some of the most monumental pieces of French history (notably the Louvre, Eiffel Tower, etc).
Video: https://www.youtube.com/watch?v=HIPljGWGNt4
One could argue that they did more harm than good than if they just let the terrorists blow up the citizens, however it’s really a matter of perspective as those people may value the historical assets over the human lives. This really is a tough question of ethics, but ultimately I think a good point is brought up here. History, no matter how beautiful and valuable, dims in the preciousness that is human life. If human life is taken out, there is a destruction of potential in the future - whereas historical artefacts can be recreated. History will be made anyway, so it’s arguable, but human life is ultimately the most precious asset.
History is Forgotten
Back when Richard was a boy, he recalls the time of the Cold War where Reagan and Gorbachev where locked in a heated battle of chicken. Both nations had nukes pointed at one another, in retaliation of the threat each imposed on one another. However, Richard had a thought:
“If the Russians attack America, and they don’t retaliate, in a few years people will just forget it happened and be happy that they have half a planet left”
While this is quite dark to think about, it is what I believe to be a cold truth. Time precedes all, and no matter how big the disaster or devastating the crime, people forget or stop caring anymore. If you think about all the great big battles that were such a huge deal at the time, now they’re almost so insignificant in the grand scheme of things. In the whole timeline of the Universe, a battle is simply an instant, and in a few hundred years people forget about it all.
Richard likens this phenomenon with the great poem “Ozymandias”, about the history ‘King of Kings’. Such a person with a magnificent statue must have been extremely great and honourable at the time. He might have been the biggest deal in his area, but ultimately time took him as well. And like the poem says, ‘nothing else remains’. Whatever happened with the great Ozymandias, no one knows or cares anymore. History has left him behind in the sands.
Opinion: In time, everything becomes insignificant and nothingness. Perhaps we should preserve what is truly valuable - that which is all precious and important. Although devastating would be the destruction of the Louvre, life is the greatest asset.
Poem:
I met a traveller from an antique land, Who said—“Two vast and trunkless legs of stone Stand in the desert. . . . Near them, on the sand, Half sunk a shattered visage lies, whose frown, And wrinkled lip, and sneer of cold command, Tell that its sculptor well those passions read Which yet survive, stamped on these lifeless things, The hand that mocked them, and the heart that fed; And on the pedestal, these words appear: My name is Ozymandias, King of Kings; Look on my Works, ye Mighty, and despair! Nothing beside remains. Round the decay Of that colossal Wreck, boundless and bare The lone and level sands stretch far away.”
Great reading + animation of ‘Ozymandias’ by Bryan Cranston from Breaking Bad: https://www.youtube.com/watch?v=sPlSH6n37ts
Protecting your Assets
You might value something as the most important asset, whereas an attacker might be after something else. So it’s very easy to protect the wrong thing and put resources into defending the wrong areas.
Richard had a friend who lived in Surry Hills which was a rough neighbourhood back in the day. Very often his car’s window would be smashed open with a brick and his car would be rummaged for money. However, his friend didn’t keep any money inside his car, and so he felt devastated, having to always pay to repair his broken window. To him, the most valuable asset was the car window. So his solution was simply to leave his car window open. That way, attackers would go approach and find that they wouldn’t need to break the window to get in. In the end, it worked!
So when you protect the right assets, you yield the best results. Coke knows that their most valuable asset is not their secret recipe - in fact, probably hundreds of thousands of employees across the globe know the recipe. Coke’s most valuable asset is their BRAND. The Coke brand has become so powerful that it has its own psychological effect on people. In fact, in a blind taste test between Coke and Pepsi, researchers found that Pepsi almost always won. However, when participants knew which was Coke and which was Pepsi, more often than not, they preferred Coke. Even more interesting is the fact that when analysing the brain during this process, researchers found that Pepsi lit up the part of the brain that dealt with taste and senses, whereas Coke lit up the area of the brain to do with Identity.
https://slate.com/business/2013/08/pepsi-paradox-why-people-prefer-coke-even-though-pepsi-wins-in-taste-tests.html

8 notes
·
View notes
Text
Hello everyone!!
I noticed that I gained a lot of new followers recently, and I realized I haven’t really made a post introducing myself like ever lol so I brain dumped 50 random facts about me and hopefully you guys know me better! ^-^
My name is Angela, but I also go by Ang/Angie/Leighann
I’m currently 22! I was born in 1997 (Chinese zodiac is year of the Rat since I was born before the Lunar New Year)
i’m quite short at 4′11″
My Myers-Briggs is INFJ
For those into Astrology: Aquarius sun, Sagittarius moon, Cancer rising
I just graduated last month from UCSB as a psych major with a minor in English literature!
Born and raised in the Bay Area ❤ Hoping to live in SF someday!
I’m ethnically Chinese/Dutch, but both my parents are from Taiwan
I have a HUGE birthmark from my ankle to my thigh (it’s insane haha but it faded a lot throughout the years)
I have 8 piercings! All in my ears (6 lobes, 1 tragus, 1 helix)
Only countries I been to: U.S., Mexico, China, Taiwan. Top of my bucket list include: Iceland, Santorini, Japan, South Korea!
I guess I’m bi? Still figuring it out tbh. But guys my type include: Doctor Mike, Andre Hamann, Nick Bateman. girls my type: Hyoyeon, Seulgi, Maggie Q, Lucy Liu
My fav (American) TV shows are: OITNB, Grey’s Anatomy, Burn Notice, and FRIENDS
My fav kdramas are: Encounter, City Hunter, IRIS, Legend of the Blue Sea
My fav movie is Breakfast at TIffany’s
I listen to a lot of indie/alternative (Foster the People, Lana Del Rey, Naked and Famous, Mumford & Sons), kpop (right now loving Red Velvet, SNSD and Gfriend), and classic 60s - 80s (Beatles, Motown, Frank Sinatra, etc.)
I got into kpop in 2009 but stopped listening around 2013-2016 and started again in 2017. My ult kpop group is pROoOBably SNSD and my (ult) bias is Hyoyeon ❤ PLEASE STAN HER AND LISTEN TO HER NEW SINGLE BADSTER WHEN IT COMES OUT JULY 20 6PM KST!!
I was raised Catholic but now I am spiritual but not religious. I believe in constantly working on becoming a better person and doing good.
My fav colors are: black, white, most shades of light pink, turquoise (or TIffany blue), and recently I’ve been obsessed with yellow! I can’t pick a single one!
My favorite time of day is prob dawn but I haven’t been awake for it in years lol. I do love twilight too because it gives me a weird nostalgic feeling
I speak English and proficient-fluent Mandarin (I prob can’t have a deep conversation about economics or politics or something lol but I grew up speaking it with my parents 24/7). I also took 4 years of Japanese in high school (but i prob forgot most of it welp). I’m going to relearn Japanese/Mandarin and hopefully start learning Korean sometime in the near future! I know the alphabet and some basics from my countless of hours watching kdramas lol
If you’re one of my female friends, I will melt if you call me these: angel, sweetie, beautiful, babe, hun, etc!!
I try to avoid mainstream things that are talked about too much because I really believe that things are overhyped and people can lose their identity by liking things just because other people are. (no hate, but e.g. BTS, Ariana Grande, Game of Thrones, Beyonce).
I LOVEEE receiving and giving handwritten letters
Speaking of, I change my handwriting every few years since I haven’t really found one that stuck yet and I have like 5 different types of handwriting from all caps to very neat print to almost calligraphy-like cursive
Games I play(ed): Pokemon (Silver, Leafgreen, Emerald, Ultra Sun, Alpha Sapphire, and Pokemon Go lol), Animal Crossing (Wild World, New Leaf, Pocket Camp). I also did my fair share of League but stopped before it consumed my life with toxicity. I was a support main who used Nami, Janna, and Thresh!
27 is my favorite number but I really do not know why lmao
My guilty pleasure song is Britney Spears - Toxic and I still haven’t gotten sick of it. Some favorite songs of all time are prob: Aretha Franklin - Day Dreaming, Tears for Fears - Everybody Wants to Rule the World, SNSD - Gee, SNSD - Genie, Amy Winehouse - Valerie
My best subject at school was English and I received an academic excellence award at the end of my junior year out of all the juniors in my grade in American Lit
When I was younger, my first dream job was an artist. then I watched Grey’s and wanted to be a cardiothoracic surgeon. Other dream jobs I had for brief moments: makeup artist, fashion designer, motivational speaker. Now I’m hoping to go to grad school to be an MFT/LPCC!
I love black cats and german shepherds! But I’m more of a cat person
If I could travel back in time I would want to live in 60′s New York or the 90′s.
Biggest turn on: someone who can hold a deep and intellectual conversation with me about meaningful subjects! Biggest turn off: someone who is extremely vapid and has no ambition whatsoever
My fav season is autumn!
The perfume I use is Marc Jacobs Daisy but I think I want to change to Versace Bright Crystal after I finish
I have perfect vision!
I did track during my prime teenage days (long jumper!) and my fastest mile was 7:20. I haven’t ran for years after that and I just started again 7 years later around this March, and I improved from around a 10 min mile in the beginning to my recent fastest at 8:09! I am hoping to get back in the ~7 mins
I also did a little bit of swim team, and I can swim all four strokes (free, back, breast, butterfly) but I mainly raced freestyle and butterfly!
I am literally the least picky eater you will ever meet. Take me to any restaurant and I wouldn’t complain. I also have a decently high tolerance for spicy things. The only food that I ever really tried and disliked is liver and the one thing that I probably wouldn’t ever try is something way out there like snail or scorpion lol
Speaking of food, I love food on the heavier side and tend to over season and over-sauce my foods lol. I love onion, ketchup, ranch, black pepper, soy sauce, korean chili spice (what they use for kimchi)
I can crack all my toes at will (it grosses everyone out xD)
My favorite book of all time is East of Eden by John Steinbeck ❤
My super power of choice if I had one would probably be invisibility
I played piano for 6 years in my childhood and I can still read notes, but veeery slowly lol
I’m kind of VERY unhealthily obsessed with (Japanese) stationery. Moleskine journals, Uni alpha gel, Pilot Dr. Grip, Zebra Mildliners, Staedler Triplus fineliners, Sakura Microns, Uni-ball signo, Pilot Hi-tec-c... yeah... i have all of those and more... yiKEs
My fav holiday is Christmas. I love holiday spirit and Sleigh Ride (I only accept the Ella Fitzgerald version) is literally such a good song??
My favorite non alcoholic drink is prob earl grey boba tea. fav alcoholic drink is whiskey!
I do not have any tattoos, but the top two I am planning are: “♒” behind my left ear, and “英” behind my neck (my mom’s Chinese name, but it also means brave/hero/outstanding person)
city > countryside
How I would describe my fashion style: tomboy, casual, chic, comfortable
2 notes
·
View notes
Text
Lectures - Week 7
Mid Term Exam
Richard went over a couple of the questions from the midterm exam; I wasn’t surprised by the admission that question 10 was impossible. I had that exact same thought regarding how RSA is bust with Merkle puzzles, because breaking one of the puzzles will give you the private key and therefore you break all the puzzles. (free marks!) I still think the answer to number 5 is questionable (lol)... I would argue the case that ‘authentication’ should be accepted as equally valid to ‘type I / type II error tradeoff’. When we refer to ‘authentication’ it is not purely referring to the ability to bruteforce it (you could if you broke into the back panel technically) but also encompasses the idea that the individual entering the code is actually the person intended to possess the code. So in essence, I would say authentication encompasses ‘type I / type II error’ tradeoff, plus a couple of other things. (hence most important)
Diffie-Hellman & Forward Secrecy
I already discussed the ideas behind Diffie-Hellman key exchange here - basically we want two people to agree on a really big prime p and a base b (which is primitive root modulo p). Then each party picks another big number secret which they use to send g^s (mod p) to the other party; because of some cool modulo laws the other party can combine it with their own secret to generate a shared secret. Now the security of this process relies on the fact that the Discrete Log Problem is hard to solve:
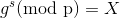
So in this case we know g, p and X and we are trying to work back to find s (i.e. either of the parties’ secrets). For small numbers this might not be too bad, but since we have computers we are dealing with numbers hundreds of digits long.
Richard also touched on the idea of ‘Forward Secrecy�� - basically its a method of protecting multiple data-streams being compromised when a server private key is leaked. This means that we generate separate random secret keys for every client using a non-deterministic algorithm (if they get the algorithm we don’t want them being able to repeat things).
Common Vulnerabilities
When we think of C code, I think the most common vulnerabilities relate to some form of memory corruption - namely the buffer overflow attacks we have been talking about for weeks. (I think I’ve explained them like 5 times but basically overflowing a buffer into the stack variables & return address) Another common one was the format string attack - who knows why they thought they needed the “%x” to read items off the stack and “%n” to dump items on the stack. (FOR A PRINTF()) The other obvious one is dumping user inputs as the first argument to printf. I think the common theme to all of these is pretty obvious - assume the user is going to break everything and therefore validate against everything!
Important Assets
Some good tips for ensuring important assets remain up-to-date and relevant include:
Regularly surveying the values of the people involved in what you are protecting
Developing a plan for ascertaining the important components - as humans are often good critics, perhaps a multi-stage review may be appropriate
Periodically revising the current list of assets - organisational values drift and so will the ‘importance’ of each asset
We typically see assets falling under two main categories:
Tangible - physical; usually easy to give a value
Equipment, products, etc
Intangible; usually not valued by physical qualities; hard to assign an appropriate value
Employee morale & security
Customer information
Company secrets
Service availability
It’s important to remember that even though some ‘assets’ of a company may be difficult to value, that doesn’t mean we should completely forget about them!
Web of Trust
One of the biggest issues we have on the internet is answering the question, “how do I know you are who you say you are?” - i.e. authentication. Like how do I know right now that my mindless rambles are actually going to Tumblr and not some other place? Well apart from the fact they’re probably not of high enough value to warrant an attack, we do this through some centralised bodies known as certificate authorities. (more detailed explanation here). The basic idea is a website will register their public key with a certificate authority; they will be given a signature of their key (the websites) with the CA’s private key. When I visit the website they will send me their public key and the signature; since I know the certificate authority, I can verify they approved of this.
The big problem with this is that comes back to the ‘single point of failure’ issue; the matter of the fact is, you only need to compromise one of these bodies and you can bust everyone’s ability to properly authenticate. Also you have to think about the financial incentive behind CAs too - they get money for providing these certificates, so they are probably going to bend the type I / type II error tradeoff more towards letting more people getting certs (rather than stopping bad guys)! The other issue relates to the extended ASCII characters; it’s pretty difficult to spot when a letter like an e is flipped to a é (letter accents) - like if you glanced into your browser and it said www.memés.com, you might not notice you are at the wrong site!
Extended: Bug Bounties
Bounties basically provide a “validity criteria” for finding bugs in software and hardware with a reward (typically monetary) in return. Some services are public such as Bug Crowd and HackerOne, however some like Synack are private. When trying to get the rewards for these bounties it is important to stay in scope, as they often are only giving you permission to test certain regions of a company’s infrastructure. It’s usually a good idea when starting out to look at recently modified assets and publicly disclosed reports; you can work from here. The general process outlined in lectures was as follows:
Find a suitable piece of infrastructure (i.e. from a bounty site)
Review the scope for the bounty
Perform reconnaissance
Hit the target and look for vulnerabilities
Write a report and submit to the company

There are heaps of good resources online to learn the skills required to look for exploits such as one HackerOne. Doing CTFs such as OverTheWire, HackThisSite, etc can also hone your skills for common exploits. However, I still think keeping up-to-date on the latest CVE exploits (and how they work) is useful!
In the lectures, the team went over a strategy called fuzzing; the basic idea is that you repeatedly provide input to each section of a program and monitor for unexpected outputs. You can use software to automatic this process, however you have to know where to look (and inject). Some of the common mutation strategies (when fuzzing) include bit flips, byte flips, arithmetic operations, known integers, dictionaries and mixing the above.
Extended: Penetration Testing
The idea of this testing is good (in theory) in that it forces us to ‘think like an attacker’ and discover vulnerabilities in our systems before another attacker can. They are basically authorised simulated cyberattacks on a computer system to evaluate risks; at the end you should know both strengths and weaknesses. The basic stages of penetration testing are as follows:
Reconnaissance - locate potential vulnerabilities
Planning - think about how to exploit the found vulnerabilities
Exploitation - use appropriate payloads (discovering in planning) to make use the vulnerabilities to compromise the system
Post-exploitation - establish persistence
I think some of the certifications used in pentesting are a bit of a ‘meme’, as well as the tools when they aren’t used as part of a much broader approach. Using tools for recon purposes is fine, but throwing every possible tool at a system just to give a ‘tick of security’ is ridiculous. Some of the tools mentioned:
Metasploit - big database of known vulnerabilities for systems that can be applied
Burp - website scanning
Wireshark - analysis of network traffic (packets, etc)
Kali Linux - linux OS with heaps of exploitation tools
NMap - exploration of open ports on networks (beware of direct printing port lol)
Gobuster - bruteforcing website URLs
Once again, playing around with the tools and knowing the sort of information you can gather with them is definitely useful. Also just having a broader knowledge of the sorts of exploits that exist through research or CTF is good too!
1 note
·
View note
Text
Why one should learn Tally? What is new in Tally Prime?
In India, the demand for Tally courses is steadily rising. We are aware of the term Tally; however, what exactly is Tally and why is it important? You frequently used the term Tally when calculating large numbers or when you were taught how to use the Tally table to solve number problems in school. Tally, on the other hand, is the name of the software that is frequently used by large, medium, and small businesses for accounting and stock management. Because it provides comprehensive business solutions to all, this software is the most difficult to use in today's world. You can complete as much accounting-related work as you like, from filling out GST and TDS forms to managing company payroll, stock management, and budgeting.
What exactly is Tally's ERP version?
ERP is Enterprise Resource Planning in its entirety. Accounting, order management, tax management, payroll, banking, and a variety of other business-related tasks are all handled by this bundle of software. It helps with everything from recording invoices to creating Management Information System (MIS) reports in day-to-day operations.
What is Tally Prime?
The upcoming Tally software version known as Tally Prime will be available soon. The most recent addition to Tally software will be TallyPrime. It is anticipated to launch with the following new features:
Amazing new experience with the same blazing speed that Tally is known for.
Extremely simplified company setup
Enhanced User Experience – without the need to know the navigation path or learn shortcut keys
Ability to do multiple activities in multiple datasets at the same time
New short cut keys harmonized to global usage patterns (e.g. Ctrl C)
Easier and intuitive masters experience
Improved Transaction experience
More Comprehensive experience for and informative business reports
More robust data management and repair
Simplified synchronization, remote access, and security control
Eco-friendly printing capabilities
For a bright career, you can enroll in the Advanced Tally course in Delhi offered by the DSCS Institute. You can learn taxation, stock management, account management, invoice management, and purchase order management through this course. In order to help you advance in your career, we suggest taking the Tally course.
0 notes
Text
C program to print triangle pattern of prime numbers

This program is similar to right triangle star pattern. The only difference is instead of printing star characters we are printing consecutive prime numbers. I will recommend that, first check how to find a number is prime number or not.
#C program to print triangle pattern of prime numbers
0 notes
Text
How to Generate an e-Way Bill Instantly in TallyPrime

For consignments involving the movement of commodities exceeding the declared value, an “electronic waybill,” also known as an “e-way bill,” is necessary. Most states have a threshold value of Rs.50,000, however, others have greater threshold levels. An e-way bill is not a new or recently discovered idea. It has actually been around for a while and was around before GST under several titles. The supplier or carrier must first generate an e-way bill from the website before transporting or sending the goods. When the e-way bill is generated, the supplier has the option to record the individual consignment’s unique number on the document.
Today, the majority of firms create e-way bills by entering the invoice information directly on the portal or using offline tools (JSON). Even though it is a requirement, creating the e-way bills takes time and effort, which makes the entire process of invoicing and shipping difficult. Regardless matter how big or little your organisation is, you must have already experienced this widespread problem.
The most recent version of TallyPrime includes an integrated connected e-way bill solution that generates e-way bills quickly, which helps to reduce the complexity in the present method of generating them and makes the entire process simple and smooth.
You may quickly generate e-way bills with TallyPrime’s internet linked e-way bill solution. Simply enter an invoice as you normally would, and TallyPrime will generate an e-way bill and record the e-way bill number on the invoice.
Let’s first take a look at what an e-way bill is.
What is an e-way bill?
Most businesses today create e-way bills by directly inputting the invoice data on the portal or using offline tools. The process of invoicing and shipping is challenging since, despite being required, preparing the e-way bills requires time and effort.
A connected integrated e-way bill solution that generates e-way bills fast is part of the most recent version of TallyPrime. This makes the process simple and straightforward and helps to lessen the complexity of the current way of generating them.
How to Generate an e-Way Bill in Tally Prime?
You can quickly create an e-Way Bill while keeping a copy of your invoice and printing the QR code and other information. Set the Send e-Way Bill information with e-Invoice option to Yes in your company’s (F11) features if you want to create an e-Way Bill with details.
As per usual, record a GST transaction.
1. Choose the party by clicking on Party A/c name. The screen for dispatch details will now appear.
A. Press Enter after entering the necessary information. It will then display the Party Details screen. This will already be filled in with the data from the party ledger. B. Press Enter to continue with the transaction and, if necessary, update the Party Details.
2. Include additional voucher information, such as the Sales ledger, the Name of the Item, the GST ledger, and so forth.
3. Set the option Provide GST/e-Way Bill to Yes. The Additional Details: Sales Taxable will appear. On the basis of the information entered in this screen, the e-Way Bill will be generated.
4. Press Enter to proceed with the transaction.
5. To save, press Ctrl + A. The generation of an e-Way Bill will be confirmed on a screen. a. Press Enter to continue. The screen for e-Way Bill Login will appear. b. Username and password must be entered. If you do not shut down the computer or reset your password, you will be signed in for the following six hours.
6. Press the Enter key. The e-Way Bill system and TallyPrime will begin exchanging data. Following the information transmission, a confirmation message will show up. A preview of the invoice is available.
7. To view the created e-Way Bill with all the necessary information and the QR Code, press Page Down.
8. The Additional Details screen will also be updated with the e-Way Bill No. and Validity Date. You can press Ctrl+I (More Details) or F12 (Configure) to view additional options for setting your e-Way Bill .
How Tally Prime’s Online Connected e-Way Biils Help You
The fully automated, straightforward e-way bill solution from Tally requires no manual effort. Consider some of the salient characteristics of a connected e-way bill solution.
Instantly Generate and e-Way Bill
There is no longer a need to consider invoicing and e-way bill generation separately given the compliance need of e-way bills in the process of invoicing and shipment. With TallyPrime, you can easily create an online e-way bill by just entering the invoice. The fully integrated solution from TallyPrime reduces complexity by delivering information directly to the portal in the required format and automatically retrieving information about e-way bills.
Generate e-invoice along with e-way bill
The GSTN and e-way bill system are integrated with the e-invoice system (IRP) by design. As a result, it is possible to create both an e-invoice and an e-way bill. Even more freedom is provided by the integrated e-way bill solution from TallyPrime. Depending on your needs, you may decide whether to generate an e-way bill in addition to an e-invoice or solely an e-way bill.
Ability to Generate several e-way bills at once
The connected e-way bill solution from TallyPrime offers the option to generate e-way bills individually or in bulk. In the process of recording the transaction, you have the option to generate an e-way bill for a single invoice, or you can select to generate e-way bills in bulk (for several invoices) from the report. Creating e-way invoices, whether in bulk or just one, couldn’t be easier or faster.
Flexibility to Edit e-way bills online
In rare cases, it is necessary to cancel invoices for which an e-way bill has already been generated. It might be due to a number of things, including a data entry error, an order cancellation, etc. Additionally, you could want to extend the validity of the e-way bill in the event of an extraordinary case, such as a natural disaster, trans-shipment delay, accident, breakdown, etc. Whatever the circumstances, TallyPrime enables you to cancel, extend, and update e-way invoices online without having to manually do these tasks via the portal.
In-depth e-way bill report
You can view all e-way bill transactions and their status with TallyPrime’s connected e-way bill solution thanks to its special e-way bill reports. You can use the report to keep track of the e-way bill status (Pending/cancelled/generated) and to take any necessary actions, such as cancelling or extending a transaction, as needed.
Alternative e-way bill creation methods are supported
If you want to use alternative methods of generating an e-way bill, such as utilising an offline utility, a direct input on the portal, etc., you can do so in emergency situations where internet services are unavailable on a system or for any other reason. These scenarios are completely supported by TallyPrime. Not only does it take into account these situations, but it also automatically obtains information and updates the e-way bill number on the invoice. keeping your books up to date as a result.
The knowledge to find your e-way bill around Tally Prime is incredibly important. Head over to S20’s website to learn more about it. And if you have the hunger to learn more, come visit our Tally institute in Ahmedabad!
0 notes