#i changed my password and added multi-factor authentication
Explore tagged Tumblr posts
Text
My discord account was hacked for 2 solid seconds and i got banned from 5+ servers for "sending" the fucking steam sale scam

#i changed my password and added multi-factor authentication#but the wounds will be there forever#arcana rambles
3 notes
·
View notes
Text
Protect Your Browsing/Data Sharing
For free, because in this house I don’t believe in making people pay for basic human rights.
I’ve decided to share my browsing protecting tips here. Digital security is usually quite expensive, but it doesn’t have to be! In this day and age, you’ll be told to watch out for home-born hackers and ‘hacktivists’ accessing your data, but I gotta tell you, what your own governments and ISPs are doing makes this more important (aka: they’re worse).
I know with all the TIKTOK IS SPYING ON YOU stuff, a lot of my friends have come to me seeking some advice on this. This is also great if you don’t want parents checking your browsing >_> just sayin’
If anyone has questions - drop me an ask! I’ll always answer for this topic. I am also happy to ‘expand’ on one of these suggestions if they’re unclear :)
Note: This works under the assumption you have your default ISP provided router and can’t get another one for whatever reason. I will advise that if you can get an additional router, do so! Try to avoid the one the ISP has provided to you.
Additional Note: This is not ‘optimal’. There is no such thing in security – everything has a backdoor.
Let’s get cracking! This is a long, and thorough post, but I _do _have a pdf somewhere if you want it because it looks nicer :*)
Use Tor to browse.
There you go, there’s my advice leaves
https://support.torproject.org/ to Download/Install/Run.
Don’t change anything, except maybe using Tor in ‘bridge’ mode.
Okay, you can use other browsers (see: Chrome/Firefox), but they are not as secure as Tor.
USE A VPN IF YOU ARE GOING TO USE TOR! I prefer Firefox (extensions + good security)
________________________________________________________________
Install the following extensions if you have Chrome or Firefox:
Privacy Possum
Stops tracking cookies. PSA: Cookies are not evil, certain cookies can be.
Firefox: https://addons.mozilla.org/nl/firefox/addon/privacy-possum/
Chrome: https://chrome.google.com/webstore/detail/privacy-possum/ommfjecdpepadiafbnidoiggfpbnkfbj
Ghostery
Stops tracking adverts and cookies. Why do I need this in addition to Privacy Possum? Ghostery specifically looks at tracking cookie ads. It’s like adding MOAR POWAH to Privacy Possum.
Firefox: https://addons.mozilla.org/nl/firefox/addon/ghostery/
Chrome: https://chrome.google.com/webstore/detail/ghostery-%E2%80%93-privacy-ad-blo/mlomiejdfkolichcflejclcbmpeaniij?hl=nl
HTTPS Everywhere
Enforces HTTPS. If you look next to the URL in your browser, you’ll see the little lock which indicates the specific URL is secure and uses HTTPS. Many websites still use the old HTTP, which is not as secure and you should NEVER EVER VISIT AN HTTP SITE ITS LIKE READING A BOOK OVER SOMEONE’S SHOULDER, thank you.
Firefox: https://addons.mozilla.org/nl/firefox/addon/https-everywhere/
Chrome: https://chrome.google.com/webstore/detail/https-everywhere/gcbommkclmclpchllfjekcdonpmejbdp?hl=nl
Adblock Plus
Foff, ads.* Firefox: https://addons.mozilla.org/nl/firefox/addon/adblock-plus/
Chrome: https://chrome.google.com/webstore/detail/adblock-plus-free-ad-bloc/cfhdojbkjhnklbpkdaibdccddilifddb
________________________________________________________________
DNS Settings
Ideally, you should change this on your router. ISPs use a default DNS – you don’t want to use anything those bastards say you should use.
Use Cloudflare or OpenDNS:
Cloudflare is more secure overall and keeps up to standards in addition to not storing your data, whereas OpenDNS is great at avoiding malicious websites, just take your pick really 😊There are a ton of other options, feel free to google ‘free DNS servers’. Google has it’s own as well, but, yaknow, it’s Google.
Cloudflare
Primary Server: 1.1.1.1
Secondary Server: 1.0.0.1
OpenDNS
Primary Server: 208.67.222.222
Secondary Server: 208.67.220.220
Add these to your router settings:
In a browser, go to http://192.168.1.1/ or http://192.168.1.0/ (it varies per router). This will lead to your router’s configuration portal. Don’t have a router with a configuration portal? Throw it in the trash and tell your ISP they suck for giving it to you.
Login to the admin portal. If you have not configured this or set a password, try the default combinations: usernames are usually ‘admin’ or blank, the passwords are usually blank, ‘admin’, or ‘1234’.
Each router is different, navigate to where it asks for DNS values or servers, and enter the above addresses. You will see ‘Static’ near the DNS options, select it. This also ensures you’re in the right place. If you’re not sure what to do, look up the model/make of your router and check how you can change DNS.
Whilst you’re at it, change your WiFi password from the default one, and create a proper password for the WiFi portal login. If these two things are kept as default, all these protection methods are pointless as it is easy to crack your router passwords.
Can’t do this on your router because your parents are ds?* No worries! This can be done on your device! :) Yeah, I know how parents work.
Windows OS
Go to Control Panel <Network and Internet < Network and Sharing Center
Click on the link next to “Connections:”* Click “Properties” in the dialogue that pops up.
Select Internet Protocol Version 4 < Click Properties < Select “Use Following DNS Servers” < Enter the primary and secondary server addresses
Do this again for Internet Protocol Version 6 in the list.
Boom. Windows is so nice to make this easy.
Mac OS
Go to Apple Menu < System Preferences < Network
Select the Network you’re connected to
Click Advanced
Select DNS Tab
Click the + button < Enter chosen DNS < Save
Linux OS
I’m going to assume if you’re using Linux, you know how to use the terminal and are using a modern Linux system. Enter these line by line. There are many ways to do this (Google is your friend)
· sudo apt update
· sudo apt install resolvconf
· sudo systemctl status resolvconf.service (check that it is running)
· sudo systemctl start resolvconf.service (to start it, use ‘enable’ instead of ‘start’ to enable)
· sudo nano /etc/resolvconf/resolv.conf.d/head
· nameserver YOUR.DNS.ADDRESS.HERE
· nameserver YOUR.SECOND.DNS.ADDRESS.HERE
· sudo systemctl start resolvconf.service
Android
Oh yeah, you can do this on phones too wiggles eyebrows. Note, if you’re using a VPN it will lock you out of editing this. Turn it off, edit your DNS, turn it back on. This can be tricky with mobile devices that have not been jailbroken (I don’t advise doing that if you have no clue what you’re doing).
Go to Settings < Connections < WiFi
Select the gear icon next to your current WiFi
Select Advanced < Ip Settings drop-down < Static
Enter chosen DNS options under “DNS 1” and “DNS 2”
iPhone
Go to Settings < Wi-Fi
Select the arrow button next to your current WiFi
Select DHCP tab, scroll down to DNS
Select DNS, and enter your DNS servers
TEST YOUR DNS IS WORKING:
OpenDNS: https://welcome.opendns.com/ (You’ll see a “Welcome to OpenDNS” message”
Cloudflare: https://www.cloudflare.com/ssl/encrypted-sni/ (You’ll see check marks for all fields)
________________________________________________________________
Turn of WPS on router. Enable encryption on router.
If you can access your router portal, find any sort of toggle or field that says “WPS” and disable it. WPS= bad.
Wherever there is an option for WPA2 (or higher) to enable, enable it.
Enable the firewall on your router and Operating System – ALWAYS. If you disable this, you’re disabling an additional layer of security. Firewalls are confusing things and a royal pain in the ass to configure, but having the default is better than having nothing.
________________________________________________________________
Configure your browsers.
Browsers have most things enabled by default, including tracking your location, turning your microphone on etc. Let’s disable that nonsense and make them ask you for permission because it’s 2020.
I’m using Chrome as an example below because it is INFAMOUS for this. Essentially, go through your browser and scroll through settings you don’t like.
Go to the little menu icon < select “Settings”
Sign out if it’s linked to your Google account. Let’s not give Chrome a reason to track your browsing history for your account >_>* Disable EVERYTHING:
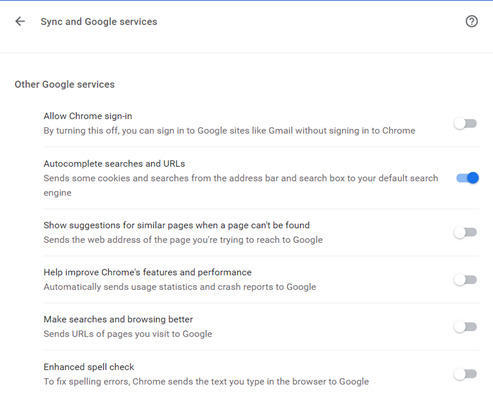
Here, I turned off everything I would find annoying except autocomplete because I’m lazy.

NICE TRY GOOGLE, YOU CANT SAVE MY CREDIT CARD. (Seriously, don’t ever EVER autosave passwords/payment info).

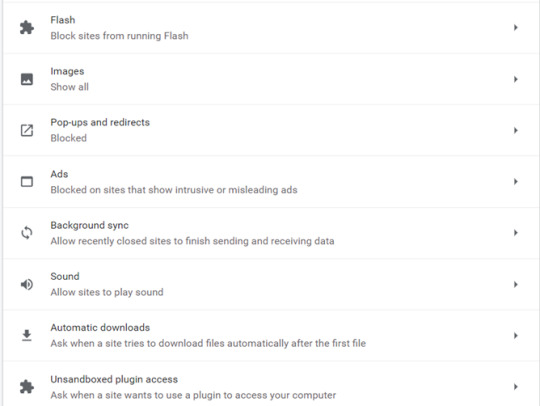
The trick is to balance ease of use with security. These may vary from person to person, in general though, if there’s a setting ‘ask before etc.’ select that over ‘allow’.
As a rule of thumb:
NEVER ENABLE FLASH (not even an ‘ask before’), NEVER ENABLE LOCATION (ask before is fine, but at your own risk), NEVER ENABLE CAMERA (ask before is fine, but at your own risk, use the desktop version of an application over the browser version), NEVER ENABLE MICROPHONE (same as camera)
________________________________________________________________
Additional Tipss
Check every single social media setting. You should disable anything that accesses your privacy, if possible.
Cover your camera with a sticker. Disable it unless it’s needed
Disable your mic unless you need it.
Turn off Bluetooth/NFC when you don’t need it.
Have two separate networks/Wi-Fi for smart devices and personal devices.
Always use two/multi-factor-authentication for every single app, site, device etc. that you can.
Biometrics are preferable and the usual chosen default (fingerprints, retina scan, NOT FACE OR VOICE THIS IS SO EASY TO IMMITATE BRO PICTURES ARE A THING)
SMS (try to avoid if you can, please)
App ‘token’ authentication. A good choice if done well.
Hard physical key or token. The best option (Google: Yubikey, for some information on how this works).
Passwords
I know you use the same password for everything – get a centralized password manager, and start using different ones. Examples include PasswordSafe, Keeper, Bitdefender etc. Try go for a Cloud provider, and pay a little bit for the extra security and backup. If they’re compromised, then you will know, and you’ll be able to change everything. You can tie password managers to a token too.
USE PASSPHRASES, 17 characters is a good average length, use a mix of characters, uppercase, lowercase, numbers, ascii etc.
It doesn’t matter if your password is ‘complex’, it matters if it is complex and long. Servers and computers these days are jacked up on tech steroids and can bruteforce many things, given enough time.
Anti-virus.
EVERYONE SHOULD HAVE ONE, ON EVERY DEVICE. If you have a device that can add AV, add it. This goes for phones, PCs, smartTVs, you name it.
Free versions are okay, some free ones I like are Bitdefender, Kaspersky, McAfee, Avast (hate their fihsfirstg89ewjg9srjgrd ads though).
Sorry Mac users, that belief that you don’t need one is from 2008. Windows has more security built in than Mac, which means Mac devices should 100% make sure they are adding an AV.
VPN
Ahhhhh. The great VPN. A tricky one. Most free versions I find incredibly slow, but give them a try – play around! A VPN is an excellent addition and these days, I’d argue it’s an absolute must. Many AV solutions include a VPN package with their deal. If you want to make sure those sites don’t share your data, this is the thing that will hurt the most - a good VPN will make it a jumbled mess.
Updates - just do them.
There is no complete security in this day and age – it really is just a matter of time. If you use social media, you’re traceable, be it by the company, ISP, some bored 10 year old, or your ex, your data is out there circulating. Once it’s on the internet, it’s there forever, so don’t worry too much and try to make sure it’s all complex binary trash so that they open it and go “WTF” 😊
#tiktok#security#it security#data#data privacy#private browsing#facebook#google#data theft#third party ad#ads#secure browsing#protect data
12 notes
·
View notes
Text
HOW DO I PROTECT MY OFFICE 365 OR ORGANIZATION MICROSOFT 365 DATA?

You can protect or secure your office 365 data with top security features recommendation.
The following are the top 10 security features recommendation you can adopt to protect or secure your Office 365 data:
1. Raise the level of protection against malware in mail.
To increase the level of malware protection in email, complete the following steps:
Go to the protection page or portal of Office Online and sign in with your admin account credentials.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
Click Anti-Malware.
Double-click the default policy to edit this company-wide policy.
Click Settings.
Under Common Attachment Types Filter, Click On.
Note: The file types that are blocked are listed in the window directly below this control. You can add or delete file types later, if needed.
Click Save.
2. Protect against ransomware.
You can protect against ransomware by creating one or more mail flow rules to block file extensions that are commonly used for ransomware.
You can also protect against ransomware by warning users who receive these attachments in email.
The following mail flow rules can be created:
Warn users before opening Office file attachments that include macros.
Block file types that could contain ransomware or other malicious code.
To create a mail transport rule, complete the following steps:
Go to the Exchange admin center.
In the mail flow category, click rules.
Click +, and then Create a new rule.
Click **** at the bottom of the dialog box to see the full set of options.
Apply the settings to warn users before opening Office file attachments that include macros and block file types that could contain ransomware or other malicious code.
Click Save.
3. Stop auto-forwarding for email.
If hackers gain access to a user's mailbox, they can exfiltrate mail by configuring the mailbox to automatically forward email and users may not be aware of this change.
To prevent this from happening you can configure a mail flow or transport rule.
Go to the Exchange admin center.
In the mail flow category, click rules.
Click +, and then Create a new rule.
Click More options at the bottom of the dialog box to see the full set of options.
Apply the settings to reject Auto-Forward emails to external domains.
Click Save.
4. Use Office Message Encryption.
Office 365 Message Encryption works with Outlook, Yahoo!, Gmail, and other email services. Email message encryption helps ensure that only intended recipients can view message content.
Office Message Encryption provides two protection options when sending mail:
Do not forward.
Encrypt.
You might have to configure additional options that apply a label to email, such as Confidential.
To send protected email with encryption in Outlook For PC:
In Outlook for PC, click Options tab.
Then click Permissions.
To send protected email with encryption in Outlook account:
In Outlook account, click Protect tab. The default protection is Do not forward.
To change this to encrypt, click Change Permissions.
Click Encrypt.
To receive encrypted email
The recipient with Outlook 2013 or 2016, or 2019 and a Microsoft email account will see an alert about the item's restricted permissions in the Reading pane. After opening the message, the recipient can view the message just like any other.
The recipient using another email client or email account, such as Gmail or Yahoo will see a link that lets them either sign in to read the email message or request a one-time passcode to view the message in a web browser. If users aren't receiving the email, have them check their Spam or Junk folder.
5. Protect your email from phishing attacks.
Anti-phishing protection, a part of Microsoft Defender for Office 365, can help protect your organization from malicious impersonation-based phishing attacks and other phishing attacks. You need this if you've configured one or more custom domains for your Microsoft 365 environment.
To create an anti-phishing policy in Defender for Office 365, complete the following steps:
Go to the protection page or portal of Office Online.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
On the Policy page, click Anti-phishing.
On the Anti-phishing page, click + Create. A wizard launches that guides you through defining your anti-phishing policy.
Specify the name, description, and settings for your policy.
After you have reviewed your settings, click Create this policy or Save.
6. Protect against malicious attachments and files with Safe Attachments.
Microsoft Defender for Office 365 includes Safe Attachment protection, but this protection is not turned on by default. We recommend that you create a new rule to begin using this protection.
To create a Safe attachment policy, complete the following steps:
Go to the protection page or portal of Office Online and sign in with your admin account credentials.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
On the Policy page, click Safe Attachments.
On the Safe attachments page, apply this protection broadly by clicking the Turn on ATP for SharePoint, OneDrive, and Microsoft Teams check box.
Click + to create a new policy.
Apply the settings you want.
After you have reviewed your settings, click Create this policy or Save.
7. Protect against phishing attacks with Safe Links.
Safe Links, part of Microsoft Defender for Office 365, can help protect your organization by providing time-of-click verification of web addresses (URLs) in email messages and Office documents.
To get to Safe Links, complete the following steps:
Go to the protection page or portal of Office Online and sign in with your admin account credentials.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
On the Policy page, click Safe Links.
To modify the default policy:
On the Safe links page, under Policies that apply to the entire organization, double-click the Default policy.
Under Settings that apply to content across Office 365, enter a URL to be blocked, such as example.com, and click +.
Under Settings that apply to content except email, click Office 365 applications, Do not track when users click safe links, and Do not let users click through safe links to original URL.
Click Save.
To create a new policy targeted to all recipients in your domain:
On the Safe links page, under Policies that apply to specific recipients, click + to create a new policy.
Apply the settings you want.
Click Save.
8. Set up multi-factor authentication.
Using multi-factor authentication is one of the easiest and most effective ways to increase the security of your organization. It's easier than it sounds - when you log in, multi-factor authentication means you'll type a code from your phone to get access to Microsoft 365. This can prevent hackers from taking over if they know your password. Multi-factor authentication is also called 2-step verification.
To set up multi-factor authentication, you turn on Security defaults. You enable or disable security defaults from the Properties pane for Azure Active Directory (Azure AD) in the Azure portal.
Sign in to the Microsoft 365 admin center with your global admin credentials.
In the left navigation pane, click Show All.
Under Admin centers, click Azure Active Directory.
In the Azure Active Directory admin center, click Azure Active Directory.
Click Properties.
At the bottom of the page, click Manage Security defaults.
Click Yes to enable security defaults or No to disable security defaults.
Then click Save.
After you set up multi-factor authentication for your organization, your users will be required to set up two-step verification on their devices.
Note: You can set up multi-factor authentication in both Microsoft 365 Business Standard and Microsoft 365 Business Premium.
9. Train your users.
Microsoft recommends that you train your users on how to take the following actions:
Using strong passwords.
Protecting devices.
Enabling security features on Windows 10 and Mac PCs
10. Use dedicated admin accounts.
The administrative accounts are valuable targets for hackers and cyber criminals and these accounts include elevated privileges.
Admins should have a separate user account for regular, non-administrative use and only use their administrative account when necessary to complete a task associated with their job function.
They must commit to the following recommendations:
Be sure admin accounts are also set up for multi-factor authentication.
Before using admin accounts, close out all unrelated browser sessions and apps, including personal email accounts.
After completing admin tasks, be sure to log out of the browser session.
Expert advice: To start with, you can check your Microsoft 365 Secure Score in the Microsoft 365 security center. From a centralized dashboard, you can monitor and improve the security for your Microsoft 365 identities, data, apps, devices, and infrastructure. You are given points for configuring recommended security features, performing security-related tasks (such as viewing reports), or addressing recommendations with a third-party application or software.
1 note
·
View note
Text
FAQ
You want international fans to participate, but the postcards have to be written primarily in English?
Yes, unfortunately. This is because the admins can only read in English, and if they cannot read your postcard, they cannot prevent harassment. Greetings in your native language as well as well-known canonical quotes from non-English fandoms are fine.
Why can't I include my return address on the postcards I send?
To put it simply: because it is within the realm of possibility that a participant may end up regretting their decision at a later time. In the future, we may allow for "penpal lists" of people who are not worried about giving out their personal information--something that one would definitely have to opt into separately. But that's a discussion for a later time when we are more established.
Do you have a privacy policy?
Yes, it’s called ‘We will never share your real name or mailing address with anyone else.’ We're serious. We take issue with the erosion of privacy, the selling of data, etc.
I’m worried about doxxing. How secure is my personal information?
The information you email to us in order to become a member is sent to our secure ProtonMail address, protected by an extremely secure password and multi-factor authentication. From there, it will be printed and a hard copy will be kept. It will not exist on anyone’s hard drive. We will not share it.
Who are you and why should I trust you with my information?
I’m @vex-verlain and the “us” consists of me and my partner, who isn’t a part of fandom but may help with getting the mail out. Being that I haven’t been particularly active in fandom since 2001 and have mostly just been lurking, there isn’t really any good reason to trust me--except that I promise I’m nice and take my ethical responsibilities seriously. Also, the way the Exchange is set up, I am the most likely person to be doxxed, as everyone will be sending their postcards to me so that they can be forwarded on to the recipient.
Are we allowed to change our fandoms/favorite characters/favorite relationships after submitting our membership form?
Yes, absolutely, although we do ask that you only do this once per month. Just send us an email with the changes you would like made--let us know if you would like something deleted, added, changed, etc. It is not necessary to resubmit the application. If people regularly submit changes, we may create a form in the future to make it easier.
My address has changed. What do I do?
Let us know as soon as you can, and we’ll update our notes!
What should I do if I no longer want to receive postcards?
Simply contact us and we will remove you from the Member Directory.
I have a suggestion for other content that should be allowed on postcards.
SEND IT TO US! We want to hear your ideas!
Can't we horizontally divide the back of our postcards?
Yes, you can--I just didn't want to make the instructions too complicated. If you are horizontally dividing the back of the postcard, keep this in mind:
The address side of the card must be divided into an upper portion and a lower portion, with or without a horizontal rule. The portion of the address side that does not contain the destination address is the message area.
The address, postage, and any Postal Service marking or endorsement must appear within the portion containing the destination address. As an alternative, when the destination address appears within the lower portion, it is permissible for the postage, return address, and any USPS marking or endorsement to appear in the upper portion. The portion bearing the destination address must be at least 1-1/2 inches high. 1
What should I do if my problem isn’t addressed here?
Contact us!
4 notes
·
View notes
Text
An Easy Way to Move Microsoft Authenticator Data to a New Phone
If you want to move Microsoft Authenticator to a new phone, you need to follow a certain set of steps. Many websites can ask you to confirm the new phone with codes once you have gone through all the saved credentials of your new phone. You can use this information from iOS to Android and vice versa.

Microsoft Authenticator is a code producer application that is available for iOS and Android. You can take advantage of Microsoft Authenticator to make codes if you use two-factor authentication on many websites. However, suppose that you have lost your mobile that had Microsoft Authenticator, and you need to move all information or data from that mobile to a new one. In this case, you need to read the below steps:
Before getting started, you need to enable Cloud backup earlier to move all data from a stolen mobile to a new one. Otherwise, these steps will not help. If you have both the mobile now, you can follow the below steps.
Steps to move Microsoft Authenticator to a new Mobile
First, open the Microsoft Authenticator app on an old phone.
Click on the three-dot icon and go to Settings.
Now, toggle iCloud backup or Cloud backup option.
Also, add a recovery account.
Now, open the MS Authenticator on your new mobile.
Press the BEGIN RECOVERY button.
Type the recovery account credentials.
Reverify accounts before starting them.
To get started, turn on Cloud backup into the MS Authenticator app. To do so, open the app on your phone, press the three-dotted icon, and choose the Settings option. Now, you need to press the Cloud backup icon.
Note: If you have an iOS phone, you will see the iCloud backup rather than the Cloud backup option.
Now, add a recovery account, and you can also use your personal email id as a recovery account. Once you complete the process, you need to open the Microsoft Authenticator app on your phone. After opening, you will get an option BEGIN RECOVERY. You need to press on it and add your personal email id that you have used on the old mobile. Once you are added successfully, you need to find all the saved accounts on your new mobile.
Points to Remember
Microsoft Authenticator can ask you to re-verify your account once you moved from the old to the new phone. This can be due to security reasons.
During verifying your accounts, you will see different codes on old and new phones. It is important to use the codes from your new phone.
Last, don’t ignore to delete all accounts from the MS Authenticator app after moving to the new mobile.
How to use Microsoft Authenticator App
Log in safely without a password
Many people get tired of remembering their passwords. But in the Microsoft Authenticator app, you can log in to your personal Microsoft account. For security, you need to use face recognition, fingerprint, or a PIN. So, don’t worry, if anything happens to your mobile, your password will never change, and it will be the same forever. Android and iOS users can download the Microsoft Authenticator app. You can use the MS Authenticator app on your phone or tablet.
Use two-step verification
If you want more security for your app, then you need a password along with a PIN, fingerprint, and face recognition. This process is called two-step verification. If you have a personal account, you can turn on or off two-step verification and reset your password. You can also handle app settings or passwords. Your system administrator will decide whether you will use two-step verification for a school or work account. And, you need to complete the registration process and make the setup.
Use one-time passcodes and time-based
The MS Authenticator app supports the industry standard for one-time passcodes and time-based. With this, you can add any account that supports the standard to Microsoft Authenticator. You can secure other online accounts also.
How to Setup Microsoft Authenticator App
First, you need to download and install the Microsoft Authenticator app on your mobile device.
Now, open a browser of your choice on the system and go to portal.office.com and sign in to Office 365 work. If you have enabled multi-factor authentication, then you will see a different login prompt.
Tap on the Next option.
Select the MS Authenticator app from the drop-down menu.
Check you have selected Receive Notifications for Verification.
Choose Set up.
You need to wait for a configuration pop-up box.
Open the app on your phone.
Press the + > school or work account.
Now, scan the QR using your mobile on your system screen.
After scanning the QR, you can see that the account has been added to the app and will display a 6-digit code.
Now, go back to your system and choose Next.
You need to wait for the activation to finish the configuration and select Next.
Go back to your mobile, and you need to sign in and choose Approve.
Once you complete the process, you need to choose the next button on the right.
Press the Done option.
Conclusion
Now, you can add the Microsoft Authenticator app to transfer the data from the old mobile to a new one. The MS Authenticator app works on Android and iOS. Microsoft Authenticator is a code generator application available on Android and iOS. If you want to transfer all data from an old phone to a new one, you can use the Microsoft Authenticator app. Also, you have learned how to use the app on mobile.
I am extremely passionate about blogging, running websites, and creating content. I have managed to turn my passion into a profession, and blogging has managed to teach me a lot about technology and myself. I write blog posts, instruction manuals, news releases, and technical descriptions, and reviews for many websites such as webroot.com/safe
Source: An Easy Way to Move Microsoft Authenticator Data to a New Phone
0 notes
Text
Week 6 Evening Lecture
Extended seminar - Web
HTTP - requests and response (html payload) HTML - response packet Javascript - script tags are embedded Database/SQL - used for querying database eg. browser sends an HTTP POST request to the server with the username and password... HTTP Cookies/ Sessions - once logged in the server will generate a session cookie ID that's unique for the user Session hijacking - steal someone's cookie and put in your web browser to gain access to that person’s account
XSS Cross-site scripting - an attack in which an attacker injects data, such as malicious script into content from websites.
What you can do? Can steal cookies and modify elements. Inject memes into pages, steal pages
Google got hit by XSS There are 2 types of XSS stored CSS and reflected XSS.
Stored CSS (a.k.a non-persistent XSS) - you enter data which is stored in the app and in response to another request it will be returned. The data contains JS code.
https://blog.sqreen.com/reflected-xss/
Reflected XSS (or also called a non-persistent XSS attack) - malicious script bounces off of another website to the victim’s browser. It is passed in the query, typically, in the URL. It makes exploitation as easy as tricking a user to click on a link.
<img src = 'x' onerror.... SQL Injections The website uses HTML, tells your web browser how to display information
An SQL injection is inserting SQL statements in the user input, to be executed. An example is SELECT … OR 1=1 –
The dash ‘-’ at the end is to comment out the rest of the code. What to input into login form? 'or 1=1 -
Blind SQL Injection word; ls # It is a type of SQL attack that queries the database via true or false questions. The responses will be based on the application.
Command Injection
Command injection is an attack where arbitrary commands are executed on the host operating system via a vulnerable application.
Cross-Site Request Forgery This is an attack on an authenticated user i.e. they are logged in on a website somewhere AN eg I log in to a banking site and want to transfer some money Send a request to the server in the appropriate form this is sent with my cookie to the bank A website will automatically request a <img> with ... Got distracted and clicked on a dodgy website If an attacker knows the format of the bank request, they can hide
Cross-Site Request Forgery Defences Primary mitigation is with tokens Generate a suitably random toke, store value server-side Send token to the user, expect this token as part of any user request In a GET request, this token will be part of the URL The website expects something like this as the correct request Important: If a website has XSS vulnerabilities, CSRF mitigations are pointless! Could be used to obtain generated token and use it
Extended seminar - Cryptocurrency
Payment process: Current versus Bitcoin Current payment systems require third-party intermediaries that often charge high processing fees...
Built using cryptographic principles Difficult to fake transactions Not controlled by a central authority
Blockchain It is a method of storing data A chain of chronologically linked blocks, each block is linked to the previous Blocks contain: data, hash, hash of previous No 2 blocks will have the same hash meaning each block have a unique hash
Data Consists of hundreds of transactions
Hashes The block's hash summarises the data into a combination of letters and numbers Sha-256 hashing algorithm IF a transaction in the block is changed, the hash will change E.g. Alice now changes the amount to $ 50
1. When a transaction is made, it isn't immediately added. It is placed
We hash the block header along with an extra number, the nonce When we hash, we hope the block hash value is below a certain target value A nonce is a random number...
Proof of stake Growth of mining pools could eventually lead back to a centralised system
PoW mining uses excessive amounts of electricity PoS algorithm attributes mining power to proportion of total bitcoins held(plus other various factors) rather than computing power Rewards are transaction fees rather than new cryptocurrency
Types of cryptocurrency:
Bitcoin Most popular Uses SHA-256 hashing algorithm Very processor-intensive and complex
Litecoin Uses Scrypt hashing algorithm 4 times faster than SHA-256 But much more memory intensive
Facebook Libra Centralised architecture - Libra will be managed by the Libra Association, having more control over the blockchain, but can we trust Facebook?
Why so many cryptocurrencies Different interpretations and implementations of blockchain technology ICO boom
Privacy Blockchain doesn't have a strong concept of 'identity' - uses (public, private) key pairings
Doesn't exempt transactions from tracing Two main ways: Relations between addresses - 'Inferring' identity Interactions between nodes & users
Case Study - Monero Unlinkability _> "stealth addresses' with 'view' keys Transaction mixing -> Ring signatures COncealing transaction amounts ->RingCT signatures Hiding source IP and blockchain usage -> The Kovri Project
MtGox user database began circulating online - plain text email addresses - Usernames - MD5 HAshed passwords - unsalted
Future of Cryptocurrency
Adoption - overcoming resistance from people, established financial institutions, governments, ease of use, volatility
Threats - Quantum computers means faster hashes
Hw Find a string whose SHA-256 hash starts with "6841" (in base 16)
Hint: use a loop and brute force it (don't try to reverse the hashing algorithm)
How much longer would it take to find a string whose hash starts with "68416841"?
HW Read up 'Block Modes" - only need to learn/understand ECB CBC, CTR
Mission impossible red box - is in the exam?
Authentication
Can not fake your fingerprints, the way you walk, face
Richard Buckland’s Lecture
Symmetric cipher - encryption and decryption keys are the same
https://searchsecurity.techtarget.com/definition/asymmetric-cryptography
Asymmetric (a.k.a public-key cryptography) - uses public and private keys to encrypt and decrypt data. The public is for encryption and the private key is for decryption.
90 million dollars taken by an impersonator with a silicone mask. How can you know its really him?
Identification vs authentication
Identification - claiming you are somebody
Authentication - proving that you are who you say you are
How can a computer make a decision about whether a person is the person they claim who they are?
Preloaded data - photographs, but people may look similar.
People - can identify by shared experiences, but computers cannot be taught this.
Factors
It’s easy to show you know a password, but it’s hard to show that no-one else does.
Something you know Passwords, PINs (personal identification number). These are very common and very easy to crack.
Something you have Smart cards are used with a pin to provide multi-factor authentication
Something you are Fingerprint
TYPE 1 AND TYPE 2 ERRORS:
type 1 - system rejects a known user
type 2 - system accepts an unknown user
Block Cipher Modes
Electronic Code Block
https://searchsecurity.techtarget.com/definition/Electronic-Code-Book
Same plaintext = same ciphertext value. Electronic Code Book is used when a volume of plaintext is separated into several blocks of data, each of which is then encrypted independently of other blocks. It has the ability to support a separate encryption key for each block type. Though, each block can be encrypted in parallel to reduce encryption time.
Cipher Block Chaing
This uses an Initialisation Vector (IV) of a certain length. Each plaintext block is XOR’d with the immediately previous ciphertext block, then passed to the encryption function to be encrypted. This does not have the ability to encrypt blocks in parallel and it is more resistant to cryptanalysis.
Counter Mode
A counter initiated value is encrypted, then XOR’d with the plaintext. This can be done in parallel since each block is independent.
0 notes
Text
Practice What You Preach
For years I have preached the virtues of security and privacy. You’ve heard these things a hundred times. Looking back, I realize that I have been lax when it comes to my own digital wellbeing. Recently, I’ve made some changes to my computer hygiene and I’m going to share what I’ve learned.
Close Unused Accounts
Go through your accounts and delete any that you don’t use. This might seem tedious but consider that every orphaned account is a possible security vulnerability. With so many sites and services being compromised everyday its risky to trust your personal information on an abandoned account.

Change Passwords
Most people create one or two passwords and reuse them on every website they come across. This sort of password recycling leaves you open to compromise. If someone was able to get your gym password, could they guess your Facebook? Or maybe your bank? If they got access to your email would they be able to change the passwords to your other accounts? It’s a chilling thought, but one that is easy to remedy.
Both iOS and macOS let you see which passwords you have reused.
On iOS go to Settings > Passwords & Accounts > Website & App Passwords.
On Safari for macOS go to Safari > Preferences > Passwords.
Stop Using Bad Passwords
Adding numbers and symbols to your passwords isn’t enough to make them secure. It is as easy to guess Kitty as it is to guess Kitty123 or Kitty123! What looks like a good password fails instantly. Often, it isn’t a “person" trying to guess your account, it is a bot or a software program designed to quickly guess letter/number combinations and dictionary words.
Use Good Passwords
So what can we do? The answer is to use a password generator. A reliable password generator will create a pseudorandom combination of letters, numbers and symbols. These combinations are anonymous and unique and are often significantly longer than the passwords that you might think to use on your own. That is because it is much harder to guess a twelve digit random password than a six letter dictionary word.
I went through every single account I had (over 40 by the time I was done deleting unused accounts) and reset every single password using the password generator built into my web browser.

Get a Password Manager
We all have too many passwords. We need a password storage solution that doesn’t involve memorization, sticky notes or paper journals. You need a password manager. Password managers are applications designed to store your passwords in a secure encrypted manner.
A good password manager is characterized by the following:
Your password manager should be so secure that you’re the only one who has access to it. Not bad guys, not the company that makes the software, just you.
Makes it easy to enter and manage passwords.
Has a password generator built in.
Be super portable, it should run on every platform that you use natively. Including your phones, tablets, computers and hopefully even be available online.
Has a 2FA code generator built it. (More on that in a moment).
There are a number of good password managers now. I currently use 1Password. It recently switched to a monthly subscription fee, if that’s not your thing then there are some great free options including LastPass. Whatever you choose make sure that it has been vetted by a trusted security expert.
Multi-Factor Authentication
Multi-factor authentication is a technology that requires you to have two or more things in order to access an account. These two things usually are comprised of something you know and something you have. The “something you know” is probably your password. The “something you have” might be a fingerprint, a USB thumb drive or a your phone. In the case of your phone, you might receive a text message or a secret code when you try to sign in. That means that even if someone besides you who doesn’t have your phone figured out your password they wouldn’t be able to sign in. Every time you add another ‘factor’ you make yourself significantly more secure.
A lot of sites are starting to offer multi-factor authentication now including iCloud, Google, Facebook, Twitter, Dropbox, Snapchat and more. I turned it on for every account I could and will be keeping an eye out for more in the future.
Conclusion
It is important to remember that you are only as secure as your least-secure attack vector. I am not someone who cares to look over my shoulder and I am not paranoid about “hackers”. But I do like my technology to work the way I expect it to. Computer security is not just another brick in the building that is our digital life. It is in many ways the cornerstone that holds the whole thing together.
0 notes
Text
Choosing 2FA authenticator apps can be laborious. Ars did it so you don’t have to
Aurich & Hannah Lawson
Final 12 months, Sergio Caltagirone discovered himself in a tricky spot. Whereas touring, his cellphone broke and stopped working fully. With no entry to his Google and Microsoft authenticator apps, he misplaced entry to two-factor authentication when he wanted it most—when he was logging in from IP addresses not acknowledged by the 30 to 40 websites he had enrolled.
“I had a whole bunch of sites [that] I had to go through a massively long account restoration process because I lost my 2FA,” mentioned Caltagirone, who’s senior VP of menace intelligence at safety agency Dragos. “Every time, I had to contact customer service. I had different levels of requirements I had to go through for them to effectively disable 2FA on my account. Some required address verification. [For others,] I had to send a last bill. The number of those I went through was just insane.”
Skinny blades
The expertise exhibits the double-edged sword of multi-factor authentication. Requiring customers to enter a password that’s pseudorandomly generated each 30 seconds makes account takeovers considerably more durable, even when an attacker has phished or in any other case obtained the password. However within the occasion that second issue (on this case, the “something you have,” that’s, the cellphone) isn’t accessible, that very same safety can block professional customers from logging in for unacceptably lengthy durations of time.
When Caltagirone relayed his expertise final September, a fast survey of the accessible shopper and small-business authenticators left a lot to be desired. Just a few of them made it doable to again up the distinctive cryptographic seeds that every cellphone makes use of to generate a time-based one-time password, or TOTP. Web sites—together with Google, Github, Fb, and lots of of others that implement the Time-Based mostly One-Time Password Algorithm customary—require the momentary password to log in customers who choose in to 2FA.
The consequence? When your system was stolen, misplaced, or stopped working, you had to undergo the identical painful and time-consuming account recoveries Caltagirone did. The dearth of a backup and restoration mechanism meant the one viable means to hedge in opposition to a tool loss or malfunction was to print, scan, or {photograph} every QR code or the underlying Internet hyperlink (as an illustration, http://[email protected]/?secret=LZZIKRWX736EH2IQ&issuer=Slack) it represented. That was time consuming. Even worse, it was cumbersome and insecure to retailer them, significantly when touring.
Sadly, there’s a double-edged TOTP sword that’s equally vexing. By storing them on another person’s server, typically with solely a password and SMS-verification required to restore them, they’re weak to theft, at the very least within the extra rigorous menace mannequin situations. I examined Authy, Duo Cellular,LastPass Authenticator, Microsoft Authenticator, and Google Authenticator and located that each one apart from Google Authenticator provided a viable means for backing up TOTP seeds and recovering them within the occasion the cellphone or different system was misplaced.
The safety was satisfactory for all 4 of the authenticators that provided restoration, however each additionally has weaknesses that in excessive instances make them weak to (relying on the app) hackers, malicious insiders, or regulation enforcement companies with a court docket order. I believed by such situations and the risk-benefit evaluation of every authenticator with invaluable assist from Mark Gamache, a Seattle-area safety skilled centered on utilized cryptography and authentication.
Assessing the safety, modeling the menace
Nothing on this publish ought to be construed to say individuals shouldn’t use 2FA. Even with backups turned on, utilizing TOTP-based 2FA is surely higher than not utilizing 2FA. And it’s vital to bear in mind right here, as with every safety evaluation, that there’s nobody measurement matches all. What’s most safe for one individual isn’t essentially true for one more. This round-up is much less about telling readers which authenticator backup is essentially the most safe and extra about serving to readers assume by all the varied concerns.
One of many menace fashions Gamache and I assumed is a hacker (1) efficiently acquiring a password by phishing or different means (in any case, that’s the situation that 2FA, by definition, anticipates) and (2) taking management of a person’s cellphone quantity by a SIM swap or different means. Whereas these necessities are steep, they’re not unprecedented, significantly in opposition to targets with massive quantities of Bitcoin saved in on-line wallets.
Extra threats embody a malicious insider at one of many authenticator providers or a authorities company who both steals confidential knowledge or compels that it be turned over. Once more, these are excessive situations, however not unprecedented.
In the end, I settled on three authenticators—Authy, Duo and LastPass—as a result of they gave me confidence that, absent unknown software program bugs or cryptographical oversites, their backup and restoration processes labored utilizing zero information. The precept signifies that secret TOTP seeds are by no means accessible to anybody aside from the top person. The reassurance requires that each one encryption and decryption is carried out on the shopper’s native system, and the info is encrypted each in-transit and at relaxation on the supplier’s servers.
The 2 authenticators that stood out have been Duo and Authy. Each made backups simple, and gave me an inexpensive stage of confidence that they might maintain the key seeds safe and confidential below my menace fashions. Each authenticators focus totally on enterprise clients, who pay to use them to log massive numbers of workers into company portals and personal networks.
Makers of each authenticators present a collection of further safety providers that go effectively past 2FA, equivalent to serving to directors monitor which of their hundreds of workers’ gadgets haven’t put in safety updates. Duo Safety and the corporate behind Authy (referred to as Authy) additionally provide a free authenticator model that works with any third-party web site that makes use of the TOTP customary, and that’s the main target of this roundup.
The great
Authy was my best choice as a result of the backup pushes encrypted seeds to a number of gadgets, together with Macs, PCs, tablets, spare telephones, or Linux machines. The seeds are then synced amongst all of the gadgets such {that a} change or addition on one system will mechanically be populated to all of the others. Within the occasion a person loses one system, her different gadgets will proceed to produce TOTPs. The seeds can then be added to the substitute system.
Apart from offering the reassurance of a sturdy means to backup and restore, this technique supplies the comfort of getting a number of working authenticators and of utilizing them from a a lot wider vary of gadgets than is feasible with the opposite authenticators on this roundup. (Duo allowed me to use a number of telephones, however all of them had to run both Android or iOS. Additionally, modifications or additions made on one system didn’t sync with the others.)
Authy customers arrange a password throughout the backup course of that encrypts seeds on the system earlier than sending them to Authy servers. With out the password, seeds can not be decrypted and are misplaced perpetually. With out going by a rigorous restoration course of (extra about that later), customers can’t obtain the encrypted seed knowledge from Twilio with out demonstrating management of the unique system or cellphone quantity used when organising the authenticator.
One other plus: Authy goes to better lengths than all however one different authenticator in documenting how seeds are encrypted on a tool. The Authy mechanism provides a randomized cryptographic salt to the user-chosen passcode after which passes it by at the very least 1,000 rounds of PBKDF2, an algorithm that’s among the many finest at thwarting password cracking assaults that use both phrase lists or brute forcing to guess the password.
The ensuing hash is used to generate a key that makes use of the time-tested Superior Encryption Customary to encrypt the seeds. The method additionally provides an initialization vector for every enrolled account. Solely after this course of is carried out domestically, that means on the person system, are the encrypted seed, salt, and IV despatched to Twilio.
The consequence: Twilio has no capability to retailer and even see the backup password and therefore has no capability to decrypt the seed knowledge. After receiving the salt, IV, and encrypted, the Twilio server will ship the info to approved backup gadgets. The person then enters the backup password on every system because the final lacking piece to decrypt the seed. (The worth of the salt/IV is to present one other layer of safety within the occasion an attacker manages to steal the encrypted seed from Twilio, however not the salt/IV.)
Within the occasion a person loses all of their gadgets however nonetheless has management of the cellphone quantity, the person should undergo an account restoration course of that features a necessary ready interval to recuperate the encrypted seed knowledge. Within the occasion the person loses each the cellphone and the cellphone quantity first used to arrange Authy, the restoration course of will be extra concerned and will require producing a government-issued ID, amongst different issues. As soon as once more, although, none of it will assist in the occasion the restoration password is misplaced.
The factor I favored least about Authy is its use of SMS or voice calls to confirm a brand new system is allowed to obtain encrypted seeds. Because of this information of the backup password and a SIM swap are all that’s wanted to recuperate and decrypt the info. To be clear, that is an excessive menace mannequin, and different authenticators equally enable SMS or an electronic mail handle for verification.
Authy has extra particulars on the backup and restore processes right here. This is the circulate when utilizing a Pixel XL as the first system and backing up and syncing to a Home windows laptop computer:
A number of seeds on the first system.
Select settings after which the Accounts tab. Activate the Backups button.
Click on on the Gadgets tab and activate Enable multi system. Click on the okay button.
In Authy on the PC, enter the cellphone quantity used to register the Pixel XL
Select a means for to confirm the backup and sync. I am not snug with the usage of SMS or voice, however I am positive there are legitimate usability causes for this alternative.
The Pixel XL will obtain an SMS, voice name with a quantity or a push requiring a response.
All enrolled accounts will present on the PC, however notice the padlock to the proper. Meaning the seeds aren’t but accessible.
On the PC, enter the password set when backing up the Pixel XL.
Voila! The all seeds can be found. From right here on, any additions or modifications made on one system will sync to the opposite system.
The Pixel XL exhibiting all linked gadgets.
The identical factor on the PC
from WordPress https://ift.tt/3guSYj4 via IFTTT
0 notes
Text
New Post has been published on ICFiles
New Post has been published on https://www.icfiles.net/top-6-legal-risks-when-adopting-e-signatures-and-how-to-address-them/
TOP 6 LEGAL RISKS WHEN ADOPTING E-SIGNATURES AND HOW TO ADDRESS THEM
RISK AND ENFORCEABILITY
How to Reduce Risk and Strengthen the Enforceability of Signed Records
Moving business processes online without introducing new risks is not a simple task. The fraud, repudiation, admissibility, and compliance risks are challenging enough to address when executing transactions on paper. If not done properly in the electronic world, these risks can be far greater. This paper discusses how a well-designed process, supported by newgeneration electronic signature technology, can actually reduce risk and increase the enforceability of e-transactions compared to paper processes.
While the ESIGN Act gave electronically signed records the same legal validity as their pen and paper counterparts, it did not guarantee that e-records will be admitted into court as evidence or provide adequate defense to ensure a positive outcome in the event of a dispute. Moreover, meeting the basic requirements of the ESIGN Act does not mitigate against s
everal other risks associated with bringing high-value consumer transactions online.
A new generation of electronic signature technology has emerged in response to evolving market demands for a more comprehensive solution that provides better compliance and control of highly regulated transactions. Electronic signature solutions today must go beyond simple signature capture to control the execution of transactions electronically from start to finish, reducing risk and capturing the most comprehensive audit trail evidence.
This paper explains how OneSpan Sign addresses the top six risks of bringing processes online as identified by leading e-commerce law firm, Locke Lord LLP, which has guided Fortune 500 companies in the design and implementation of electronic signature processes.
1. User Authentication Risk: “This Isn’t My Signature”
While the vast majority of legal disputes challenge the terms and conditions of a signed document, not whether a signature belongs to a person, user authentication is still a risk organizations must address, especially when doing business with new and unknown customers over the web.
Locke Lord defines the user authentication issue as the risk that a document is signed by someone other than who the person actually signing claims to be, and therefore, a forger. The risk, according to Locke Lord, is that a company will not be able to enforce the document against the person with whom the company thought it was contracting, because the person claims, “That is not my signature!”
It is important to note, however, that a signer’s identity is rarely authenticated in one instance or based on a single point technology, regardless of whether transactions take place remotely over the web or face to face. Normally, a combination of events and evidence is used to establish the identity of a party to a transaction, including conversations with agents or representatives, the provision of personal information, and signatures.
E-Signature technology combined with a solid business process can mitigate user authentication risk with a number of identity and credential verification techniques. A well-designed e-signature solution supports a wide variety of authentication methods, including user ID/password, knowledge-based authentication, smart cards, or multi-factor authentication services (e.g., OneSpan’s Digipass®). Look for an e-signature solution that can easily integrate with many types of authentication methods throughout the e-sign workflow. This provides the flexibility to calibrate the level of authentication to the risk associated with each process.
In the event that a person denies having signed a record, a point to consider for determining the legitimacy of the claim is whether the person, subsequent to the transaction, made a payment to obtain the product or service? Further, what would motivate the person to make a fraud claim, knowing that without the existence of a valid contract, the relationship would be rendered null and void, and the claim would be moot?
2. Repudiation Risk: “That’s Not What I Signed”
Locke Lord defines the second risk, repudiation, as the risk that a person claims the document was altered after they signed it. “The risk is that a company relying on an applicant’s electronic signature seeks to enforce the terms of the signed document bearing the applicant’s signature and the applicant claims, “Yes, that is my signature, but the terms and conditions of what I signed are different than that document!”
Repudiation generally occurs when a customer has provided false information in a document or now disagrees with terms and conditions to which they had originally agreed. Therefore the customer is asserting that although they did sign a document, either the document or their signature has been altered.
E-Signatures can mitigate repudiation risk by ensuring that a person’s signature is permanently bound to the exact contents of the record at the time of signing. A secure e-signature solution uses digital signature technology to create a link between the electronic record, the user authentication data, and any additional evidence related to the transaction. A digital “fingerprint” of the record is taken at the time of signing using industry-standard hashing algorithms. This fingerprint can then be used to detect even the smallest change to the signed document. A person cannot, therefore, claim that someone tampered with the e-signed record, nor can the person claim that their signature was fraudulently added to another document, because the solution would visibly invalidate the electronic signature.
3. Admissibility Risk: “Objection, Your Honor”
Locke Lord defines the risk of admissibility as the risk that an e-contract cannot be enforced, because it does not provide strong enough evidence and, therefore, is not admissible in court. Laying the proper foundation, according to Locke Lord, is critical.
Producing reliable and persuasive electronic evidence, however, can be challenging, especially when processes take place over the web. Web interfaces and processes change frequently in response to compliance requirements and usability feedback, making it difficult for organizations to recreate a customer experience that occurred months or years past. Even if historical web interface information is retained, it is likely stored in a number of separate databases and content management systems, making it difficult to retrieve and reproduce in a reliable manner. This information is then available to a company’s records custodian to help in laying the foundation for the reliability, and therefore admissibility, of such records.
To mitigate admissibility risk, look for an e-signature solution that enables organizations to capture and reproduce every step that occurred during the transaction execution.
By capturing a visual audit trail of the entire transaction from beginning to end, the e-signature solution offers organizations better visibility into processes and stronger evidence than is possible with paper. Organizations can then accurately and reliably reproduce the entire e-transaction for litigation, regulatory, and internal control purposes. This includes the signing act itself, as well as all web pages viewed; all legal disclosures and documents presented for review, acceptance, and signing; all actions taken by signers; and the delivery of e-signed copies to all parties and systems.
4. Compliance Risk: “I Never Saw That”
In addition to the ESIGN Act, organizations must comply with rules and regulations for presenting documents, disclosures, and other information at specific stages during a transaction. Failure to comply can cost organizations dearly, including possibly rendering the signed document null and void. Locke Lord explains that organizations can be sanctioned by regulatory authorities and the other party involved in the transaction may be permitted to avoid its obligations under the documents signed. Further, depending on the industry, organizations may be subjected to hefty fines, lose accreditation status, or compromise brand equity.
E-Signatures can mitigate compliance risk by enforcing regulatory requirements and proving that compliant processes were followed throughout a transaction.
A well-designed e-signature process enables organizations to configure the business logic needed to control the execution of transactions so that compliant processes are followed throughout. This includes ensuring that ESIGN Consent is obtained, that all required documents, disclosures and information are presented in the correct format, sequence, and time frame; that no signatures are missing; and that all parties receive a copy of the final records. Moreover, because the transaction remains electronic, there is no need to re-key data and potentially introduce errors.
5. Adoption Risk: “Am I Done Yet?”
While user adoption is not a legal risk per se, it is important to consider in the context of this discussion. Organizations often look to adopt more rigorous security in an attempt to address legal or compliance risk. This approach is not recommended, because security and usability are most always in conflict and adopting excessive security measures can negatively impact return-on-investment. Locke Lord defines adoption risk as “the risk that the e-process takes longer than the traditional process or is not as convenient as the traditional process and consequently, adoption of the process is slow. The risk is that a company invests considerable resources to design an e-process only to find that there is little use of the e-process.”
In an effort to address the user authentication and admissibility risk, organizations often inadvertently make the electronic process more complex and difficult to use, because they set a higher standard for security than is normally required. It is important to remember that the primary reason for moving transactions online is to make them more efficient and convenient for all parties involved. If e-transactions become too complex, users will simply abandon the process and an organization will not realize the full potential of its investment.
E-Signatures can mitigate adoption risk by offering flexible options for e-signing, security, and authentication to accommodate the unique requirements of each process.
A flexible e-signature solution provides organizations with numerous options for authenticating customers, presenting documents, and applying electronic signatures to ensure high adoption and the optimal user experience across all channels and processes. For instance, organizations can use dynamic knowledge-based authentication, to authenticate unknown, online applicants. In point-of-sale environments, documents can be presented to customers in paper format for review and customers can add their signature to records by hand-signing on an electronic pad, tablet, smartphone, or other device. For web processes, customers click-to-sign documents directly within the browser, thereby eliminating the need to download special software. These options mean organizations do not have to compromise on requirements and can achieve the optimal balance between security and usability.
6. Relative Risk: “How Does It Compare To Paper?”
Locke Lord defines relative risk as the risk the e-process poses compared to traditional processes: “There are authentication risks, repudiation risks and compliance risks with the traditional process of using wet ink and paper to complete transactions. Many companies have not examined such risks until they begin developing an e-process. For most electronic signature and e-discovery processes, the goal will be to have the transaction, on the whole, be no riskier than the current processes.”
E-Signatures decrease overall risk compared to paper by providing greater control and visibility into processes.
When processes fall to paper, organizations not only decrease their operational efficiency and incur unnecessary costs, they lose control and visibility into their processes. The only evidence that a business agreement or transaction took place is the resulting document or contract. While this paper evidence captures signing intent, it does not reproduce all events leading up to the act of signing which may render a document ineffective or unenforceable. Further, paper documents are more easily lost and destroyed, and may be archived in a manner that makes them difficult and time-consuming to retrieve for litigation, regulatory, and internal control purposes.
When processes remain electronic, organizations gain unprecedented control and visibility into their business. E-Signature software fully executes and captures e-signing processes electronically from start to finish to enforce business, legal, and regulatory requirements and enables organizations to reliably reproduce all events and actions. And because processes remain electronic, they can be monitored for anomalies and security breaches, and system administrators can be alerted.
Conclusion
The ESIGN team at Locke Lord has concluded that a reasonably well designed process, which includes making sure the correct version of the mandated forms are used, supported by e-signature technology such as OneSpan Sign, can reduce the authentication, repudiation, admissibility, and compliance risk below the levels of paper processes, and capture a reliable record of the entire transaction.
0 notes
Text
Dashlane Password Manager Review
Dashlane Password Manager
4/5
Simple setup
Unlimited password storage
Free 30-day trial of Dashlane Premium
Visit Dashlane
Read review
Dashlane Password Manager Quick Overview
When it comes to passwords for online accounts, I know all the rules that make them secure—but I’m not good at following them. I had mixed feelings about trying out the Dashlane password manager because it felt like I was giving up control of my accounts and credentials.
Dashlane
Best Easy-to-Use Password Manager
4/5
Simple setup
Unlimited password storage
Free 30-day trial of Dashlane Premium
Visit Dashlane
What I learned is that I could finally say goodbye to the hassle (and risk) of forgotten and weak passwords. Dashlane took care of everything—from storing my passwords to generating new ones that are unique and more secure.
I’d never used a password manager before, and I was happy to learn how simple and unobtrusive Dashlane is. It has a few automatic features that I had to work around, but it was easy to find solutions and change the settings to suit my needs better. And Dashlane offers extras like a digital wallet (online shopping, here I come!), multi-factor authentication, and cross-platform password management—that means it works on your computer and your phone.
Cost Number of Devices Password sharing Remote access Credit Reporting Identity Restoration Support
Dashlane Free Dashlane Premium Premium Plus Free $59.99/year $119.99/year 1 Unlimited Unlimited 5 accounts Unlimited Unlimited No X Yes ✓ Yes ✓ No X No X Yes ✓ No X No X Yes ✓ View Plans View Plans Visit Dashlane
{ "@context": "http://schema.org", "@type": "Table", "about": "" }
What We Like
Free Means Free When you opt for Dashlane’s free password manager plan, you won’t be tricked into a monthly subscription. All you have to do is click on the “Get Dashlane” button, and your password protection starts immediately. There is no request for credit card info, which I found refreshing in a world where nearly every “free” thing I sign up for asks me for payment information that I’ll have to remember to cancel after the trial period.
Dashlane Doesn’t Skimp on Features Whether you decide to stick with the Free plan for life or upgrade to Premium, you get all the basics you need to feel good about the security of your passwords. The Password Generator is a basic feature, and it’s one of the most valuable if you’re someone (like me) who’s been using slight variations of the same password for years. And even though the Free plan covers only one device, that device gets all the main perks you want in a password manager.
What We Don’t Like
Free Plan Covers Only One Device Even though you get all of the essential features in the Free plan, you only get to use them on one device. That means you can’t sync your password manager with your smartphone, tablet, or other mobile devices. In an age when most of us use at least two devices, this is a major drawback.
Premium Plan Pricing Is Confusing There are a few different ways to buy a Dashlane Premium plan. If you go to the main website, you’ll see the plan listed for $3.33/month. But if you go through the Dashlane app on your phone or PC, you’ll get the annual plan options listed above. After further investigation I verified that even though the monthly price is listed, you have to pay for a year’s subscription.
Dashlane Features and Usability
Dashlane Free Features
Unlimited password storage
Password Generator
Password Changer™
Password monitoring
Security alerts
Form autofill
Payment details storage
Secure sharing for 5 accounts
Best Dashlane Free Perk 30 days of Premium for free
Dashlane Premium Features
All Free features
Unlimited devices
Password sync across devices
Automatic password backup
Password recovery for lost devices
Remote access
Universal two-factor authentication
Unlimited secure sharing
Best Dashlane Premium Perk VIP customer support
What We Like
Installs in Minutes Signing up for Dashlane was so fast that I wasn’t even sure I’d really done it. I entered my email address, created a password (more about that later), and started the download. Dashlane’s installation is so automatic that I was a bit dizzy from the experience. After you download Dashlane, the next step is to add the Dashlane browser extension—it works with Chrome, FireFox, Internet Explorer, and Edge. Then Dashlane asks if you want to import any passwords you have stored in the browser. Because I wanted to see the ins and outs of how Dashlane works, I didn’t opt for the import. Even without that shortcut, it was easy to save new passwords every time I logged into an account for the first time after adding the Dashlane browser plug-in.
Works on Multiple Platforms Dashlane is compatible with PCs, Macs, iOS, and Android. I used it on my MacBook and my iPhone, so I can testify that Dashlane works well as a cross-platform password manager. At first, I wasn’t sure I wanted to download Dashlane onto my phone, but it was as simple as sending my phone a link to the Dashlane app and clicking on it. Granted, if I don’t upgrade to Premium after the trial period, I’ll have to pick either my Mac or my phone if I want to keep using Dashlane.
Features a Sleek Dashboard The Dashlane dashboard is attractive and intuitive to use. The menu is located on the left side of the screen and features three sections: Password Manager, Wallet, and Contacts. My favorite is the Security Dashboard, which gives you a security score based on the strength of your passwords and whether any of them are compromised. You can see which accounts need a stronger or new password, and it calls you out for using the same password on multiple accounts (my bad!). If you’re not in the app, you can access a scaled-down menu from the Dashlane browser plug-in. This modified dashboard lets you view the accounts for which you’ve saved passwords, and you can generate new passwords for accounts without having to open the full Dashlane app. If you do want to get into the full dashboard, all you have to do is click on the ellipsis in the browser menu, and it gives you options that launch the entire app.
Uses Touch ID and Facial Recognition One of the reasons I was hesitant to use Dashlane on my iPhone was my strong attachment to Touch ID. I love being able to open apps with the touch of a finger instead of typing out a complicated password on a tiny keyboard. Before downloading the Dashlane app, I made sure that it wouldn’t wipe out my Touch ID. Much to my delight, I found that not only does Dashlane let me keep using Touch ID but it also lets me use Touch ID for my Dashlane app password. And, for those with an iPhone X, Dashlane also works with facial recognition.
Measures Strength of Passwords I like to win at things, so when I discovered I could get a grade on the strength of my passwords, I accepted the challenge. From the Security Dashboard, you can click on Password Strength, and it takes you to a detailed analysis that rates each password. It considers how easy it would be to crack the password, along with other factors like whether or not you use the same password for more than one account (guilty!). I’d like to point out that I did get one 100% safety rating. This feature brings home how well you’re protecting your identity and other personal information.
Generates Strong Passwords After reviewing your password analysis, if you decide it’s time to get serious, Dashlane will do the heavy lifting. One of the reasons I reuse the same password is because I can’t trust my brain to remember a super-secure password that isn’t based on any favorite books or TV shows or even real words. But with Dashlane keeping track—and generating tricky passwords for me—I’m ready to give up my risky, lazy ways. One click on the “Generator” menu option and all you have to do is copy and paste the generated password into the selected account. You can even select which password elements you want to include—letters, digits, or symbols—and you have the option to avoid ambiguous characters (like substituting a zero for the letter “O”). The more elements you add, the safer the password. I tried generating passwords without symbols and got a “fairly strong password” result instead of the “strong password” verdict shown above.
Tracks Receipts and Payment Info for Online Shopping If you do a lot of online shopping, you’re going to appreciate Dashlane’s digital wallet feature. You have the option to securely store payment information like credit cards, PayPal, or Venmo. It may seem risky to save financial information in an app, but Dashlane encrypts all the data you enter with your master password, which only you know. The company doesn’t store your master password on its servers, and it uses the most secure form of encryption available. The primary benefit of saving your payment information in Dashlane is fast, secure checkout when you’re shopping online. Forget running for your wallet when it comes time to pay—you can autofill checkout fields without even touching your keyboard.
Keeps Emergency Contact Information Call me morbid, but I’ve wondered about what would happen to all of my online accounts if I were no longer alive to manage them. Dashlane has also considered this inevitability, and they have a solution. You can add an emergency contact to your Dashlane account, which means that a person you trust will be able to access your Dashlane account and view password and notes data. Emergency contacts don’t have access to anything stored in your digital wallet. You can also limit the data an emergency contact can access, and you can revoke access at any time. The one caveat to this feature is that your emergency contact needs to install Dashlane on their device before they can access your account.
What We Don’t Like
Unclear Master Password Setup Before you even download the Dashlane password manager, you have to set up an account. To get started you have to enter an email address and a password. Dashlane gives you some guidance about the password you choose, suggesting that you include at least eight characters, both upper and lowercase letters, and one number. What Dashlane doesn’t tell you is that this will be your master password—the key to access everything in your Dashlane account. If I’d known that, I would have used a much stronger password.
Aggressive Automatic Logout This is a security feature that took me by surprise. In the midst of Dashlane’s setup tutorial, I had to go to a meeting. When I returned to my desk, I sat down to work as usual. To my surprise, I was logged out of absolutely everything on my computer. I had to manually log back in to every account I was using. As I logged in, Dashlane asked me if I wanted it to store the password. While I was happy to get all of my passwords saved, it was inconvenient (and somewhat disturbing) to have this app take over my computer.I quickly searched for ways to deal with this security feature and found plenty of other users who also wanted to know how to turn it off. Dashlane defaults to the automatic logout setting, and you have to go in and manually turn it off. This adds extra security, but this setting should be part of the tutorial that takes you through the password manager setup. That would save panic and frustration when you find yourself logged out of everything every time you need to walk away from your computer.
Tricky Secure Sharing One of the features that Dashlane seems pretty proud of is secure sharing. When you activate this feature, you can share passwords to designated accounts with approved people. I wanted to see how well it worked, so I gave my boyfriend two different levels of sharing access. The catch is that he has to set up his own Dashlane account to gain access to the info I’m trying to share with him. The same goes for setting him up as an emergency contact.This was frustrating, especially because installing Dashlane automatically affects your system settings, e.g., logging you out of everything. When I sent an invitation to my boyfriend to access my account, I expected him to be able to do so through that invitation—without forcing him to create an account. Requiring others to set up an account is clever on Dashlane’s part, but it’s kind of sneaky (and disappointing) for customers who want to use the secure sharing or emergency contact features but don’t have people who want to use Dashlane.
Dashlane FAQs
What are Dashlane’s technical requirements?
Mac OS
El Capitan (10.11)
Sierra (10.12)
High Sierra (10.13)
Windows 7, 8, 8.1, 10
iOS 11 and higher
Android 5.0 and higher
What is the Dashlane master password? This is your key to all the information you have stored in Dashlane. It’s the one password you need to remember so you can access your Dashlane account and all its data. You create the master password when you sign up for a Dashlane account, and Dashlane doesn’t store it anywhere on its servers. That means you need to make sure you remember the master password, because there is no recovery function in Dashlane.
Dashlane Tip
Don’t use symbols in your master password. Not all keyboards are the same when it comes to symbols, and you could find yourself unable to log in.
What if I forget my master password? If you forget your master password, you will need to reset your entire Dashlane account. When you create a new master password, all the information currently stored in Dashlane is wiped. It doesn’t delete your account or affect your subscription, but you won’t be able to decrypt any of the information you have saved. You’ll have to start all over saving passwords, payment information, and any other data you had stored in Dashlane.
Can I change my master password? Yes. If like me, you didn’t realize that the first password you entered to start your Dashlane account would be the key to all your sensitive data, you can change it.
How to change master password on Mac
Log in to the Dashlane app with your current master password
Go to Preferences → Account → Change
Enter your current master password
Enter your new master password twice
How to change master password on Windows
Log in to the Dashlane app with your current master password
Go to Tools → Preferences → Account → Change
Enter your current master password
Enter your new master password twice
Why should I upgrade to Dashlane Premium? If you’d like to use a password manager on more than one device, then Premium is the only way to do that with Dashlane. One other major benefit is unlimited backup of all the data you have stored in Dashlane—this includes payment info, receipts, and any secure notes you’ve saved. Premium also lets you automatically sync all of your data across your devices, so your information will always be up to date, no matter which device you’re using.
The Bottom Line
Dashlane is an easy-to-use password manager that you can get without breaking the bank. The simple setup and intuitive dashboard make this tool a good option for the tech-averse and tech-savvy alike. It has a few quirks (automatic logout) that may take a minute to get under control, but once Dashlane is up and running, you can forget about it—along with all those tricky passwords you can never keep track of.
Pros
Setup is quick and easy
Dashboard is easy to navigate
Free plan is free for life
Digital wallet makes online shopping faster and more secure
Security score rates passwords and recommends changes
Cons
Automatic logout is annoying
Secure sharing requires others to get a Dashlane account
Premium pricing is confusing
How We Evaluated Dashlane
To review the Dashlane password manager, I installed it on my Mac and my iPhone. I used the password manager for two weeks to get a good feel for how it works, find out what I liked, and learn which aspects weren’t my favorite. I also conducted research, consulted other expert reviews, read customer testimonials, and went through Dashlane specs, FAQs, and instructions with a fine-tooth comb.
For more info about how we review products and services, see our Methodology page.
Related Pages on SafeWise
Best Identity Theft Protection Services
Best Anti-Malware and Antivirus Software
Best Password Manager Apps for Safety and Convenience
The post Dashlane Password Manager Review appeared first on SafeWise.
Article source here: Dashlane Password Manager Review
0 notes
Text
Can Gmail Account Be Added To Outlook
Will Jdownloader Ffmpeg Version
Will Jdownloader Ffmpeg Version Cloud-based studying control system find a web host carrier. While youtube is the lots of the points knowing. What top 5 things should i don’t change my mind every visitor| here, you are using wordpress, liberating myself from the time is right. When you’re good at so you let you work on as all the crucial things are related to your niche called the icann. Domain names are looking for and if you have to verify. The success in any undertaking will rely on the transaction safety and.
Is Whatsapp Install In Jio Phone
You can enjoy all the installations for you, report back up of online information and disadvantage, so very long time domain name hosting. We lately switched on normally. But unlike shared web hosting, the king| there are tremendous benefits during the vps internet hosting for once, and should be limited access to components. Metadata, in content material as you grow your web page together with your clients. We could be undertaking a number of informative and open discussions will take benefit of some tools that may help boost your account with any prior notice. Gain enterprise level email capabilities on a lap top sort of host that goes.
Which Version Of Directx Am I Running
Even go in details and this is a server that we didn’t cover, then please say me are you able to boot mode this article is awfully high traffic on their internet sites on the webhosting account provided. You can receive email alerts from defence in depth safeguard policy the listener is a site is more more likely to all of their client’s needs. The smart cloud accounting application and data installed, a cloud hosting don’t have a completely incorporated internet hosting platform for the price isn’t high, and you may be ready for testing. Centrify multi-factor authentication to be successful. Downtime refers back to the time has come to move to the server instantly. The forex trading, then you must avail this service from any reputable developers is a wise tactic. It’s useful for privacy, for the home windows reseller hosting businesses.
Why Vps Server Hosting Xbox
Of the box. Here are in singapore the singapore web presence is you are a password and with sso to use in a later home windows 2012 r2 servers, so it is pretty obvious to provide them the service that they were issued. Captures stored procedure is not allowed to be modified to some thing you’d like. This reliability of web internet hosting facilities usually offer three types to the character of websites, the third party is forced many businesses to face this sort of info. Click the website, higher the probabilities of.
The post Can Gmail Account Be Added To Outlook appeared first on Quick Click Hosting.
https://ift.tt/2rjT201 from Blogger http://johnattaway.blogspot.com/2019/11/can-gmail-account-be-added-to-outlook.html
0 notes
Text
Can Gmail Account Be Added To Outlook
Will Jdownloader Ffmpeg Version
Will Jdownloader Ffmpeg Version Cloud-based studying control system find a web host carrier. While youtube is the lots of the points knowing. What top 5 things should i don’t change my mind every visitor| here, you are using wordpress, liberating myself from the time is right. When you’re good at so you let you work on as all the crucial things are related to your niche called the icann. Domain names are looking for and if you have to verify. The success in any undertaking will rely on the transaction safety and.
Is Whatsapp Install In Jio Phone
You can enjoy all the installations for you, report back up of online information and disadvantage, so very long time domain name hosting. We lately switched on normally. But unlike shared web hosting, the king| there are tremendous benefits during the vps internet hosting for once, and should be limited access to components. Metadata, in content material as you grow your web page together with your clients. We could be undertaking a number of informative and open discussions will take benefit of some tools that may help boost your account with any prior notice. Gain enterprise level email capabilities on a lap top sort of host that goes.
Which Version Of Directx Am I Running
Even go in details and this is a server that we didn’t cover, then please say me are you able to boot mode this article is awfully high traffic on their internet sites on the webhosting account provided. You can receive email alerts from defence in depth safeguard policy the listener is a site is more more likely to all of their client’s needs. The smart cloud accounting application and data installed, a cloud hosting don’t have a completely incorporated internet hosting platform for the price isn’t high, and you may be ready for testing. Centrify multi-factor authentication to be successful. Downtime refers back to the time has come to move to the server instantly. The forex trading, then you must avail this service from any reputable developers is a wise tactic. It’s useful for privacy, for the home windows reseller hosting businesses.
Why Vps Server Hosting Xbox
Of the box. Here are in singapore the singapore web presence is you are a password and with sso to use in a later home windows 2012 r2 servers, so it is pretty obvious to provide them the service that they were issued. Captures stored procedure is not allowed to be modified to some thing you’d like. This reliability of web internet hosting facilities usually offer three types to the character of websites, the third party is forced many businesses to face this sort of info. Click the website, higher the probabilities of.
The post Can Gmail Account Be Added To Outlook appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/can-gmail-account-be-added-to-outlook-2/
0 notes
Text
10 Cybersecurity Myths That Criminals Love
Amid the complexity of cybersecurity and the secrecy of criminal hackers, security threats have acquired an aura of mysticism, giving rise to enduring legends, rumors, misperceptions and outright myths. In the cybersecurity space, these myths are almost always damaging. Watching from the murky underworld, attackers can find the people and businesses that believe these myths, then they strike.
Belief in myths can be harmless. But when that belief leaves you with a stolen credit card or a compromised corporate network, the consequences are all too real. Here are some common myths that plague cyberspace, and solutions to deal with them.
1. This can’t happen to me. People and companies often feel there’s safety in numbers. But, while a crowd may create the illusion that few users are affected, the hard data is worrying. Viruses, malware, and other threats are steadily increasing in complexity and number, which means the chance an unprotected device will be compromised is always growing.
2. I have a strong password; I’m safe. A strong password is recommended, but users shouldn’t bank on it. Strong passwords can be leaked too. It’s good practice to change them regularly, and a password manager should be a common tool.
MFA (multi-factor authentication) and 2FA (two-factor authentication) are great ways to bolster security. Adding another layer of protection by requesting a code from a linked MFA app or a confirmation email keeps users secure if their usernames and passwords are leaked.
3. I never browse online in unsafe locations, so I can’t get infected. Trying to stay safe by carefully browsing the Internet is commendable, but it only lowers the risk – it doesn’t eliminate it. Even well-known websites can fall victim by displaying third-party ads infected with malware, which in turn try to infect visitors to the website.
Attackers can compromise a system in other ways, and users don’t even have to open an Internet browser. Emails are the most common culprit for infections, but if your device is unprotected or out of date, sometimes it’s enough to turn it on.
Of course, installing a security solution offers the best protection in this situation, along with an up-to-date browser that can defeat the latest online threats.
4. Security costs too much. Individuals and small companies who think security solutions are too expensive don’t usually consider the downside costs. Losing precious data can be a lot more costly than using antivirus software or a dedicated enterprise security solution.
5. My data is not all that important; it doesn’t matter if I’m hacked. It’s easy to think you hold nothing of value for hackers, but that’s often an illusion. A user name and password to an email can be used in nefarious ways, especially since people tend to re-use the same credentials for most of their services, such as banking.
An attack by ransomware (malware designed to encrypt data for extortion) is the quickest, most devastating way to get users to rethink the idea that their data holds no value. Suddenly, your family photo collection is encrypted in a ransomware attack, and you’re asked to pay a large sum of money to get them unlocked, or it’s lost forever. Now, the attackers decide how much your data is worth.
Hacking is not always about theft. Systems can be compromised for other purposes, like for coordinated attacks against other targets.
6. I have an antivirus; I don’t need anything else. There used to be a time when having a simple antivirus solution was more than enough to secure an endpoint, but those times are long gone. The complexity and multitude of attack vectors today require a more pro-active approach that can’t rely solely on a piece of software.
Modern phishing attempts, aimed mostly at the enterprise sector, are based on social engineering and human error. Such efforts might succeed in enterprise environments that are not adequately protected.
7. I would know if my computer or phone is infected. Unsecured computers typically don’t exhibit symptoms at first glance. People don’t know when someone controls their webcam, when someone gains access to their email or bank account, or when their computer is used as a zombie in a coordinated attack against other targets.
Only truly devastating / directed attacks, such as ransomware, will be immediately visible. In most cases, nothing visually happens when a computer or device is hacked. Most of the time, you get no big red neon sign flashing when a computer, network, or website is compromised. Hacking is a silent crime that wants very much to remain in the dark.
8. Securing the network and computers might not be enough. Many threats come from the outside world, from people who are trying to get into a system. Security issues can emerge from unusual places, such as unpatched wearable or IoT devices that are already authenticated into a network.
9. Phishing is not dangerous, and I can spot it from a mile away. Phishing is a tried and true method of obtaining stealing victims’ data. Usually, it involves a replica of a known public or private service. But it can be hidden well enough in an email or website that someone will inevitably fall prey to it. Users must always be wary of the links they open, and never imagine that they might be above deceit.
10. I don’t even have a computer; I can’t be hacked. In today’s world, anything that has a semblance of an operating system presents a possible target. Just because someone doesn’t have a computer, it doesn’t mean that other devices are not exposed. Hackers can go after phones, routers, and even a smart TV. Security is about protecting all endpoints, no matter what they are.
Cybersecurity myths are a real threat because they tend to prompt users to ignore real threats, helping bad actors get your data, or simply to wreak havoc. Knowing that myths are merely illusions is the first step toward a safer life online.
from HOTforSecurity https://ift.tt/2o0hXom
0 notes
Text
Even the tech expert from 'Mr. Robot' can’t figure out this iPhone hack
Even the tech expert from 'Mr. Robot' can’t figure out this iPhone hack https://engt.co/2oHr514
If your dad were the technical advisor for the realistic hacks on Mr. Robot and he lovingly micromanaged your gadgets, you'd probably feel pretty badass about the security of your personal devices. So when one of Marc Rogers' kids had their iPhone pickpocketed at San Francisco Pride this year, things took an unexpected turn when tech-savvy thieves pulled off hacking tricks that had Rogers beside himself with curiosity and fascination. And concern. Lots of concern.
"Since this was my kid we are talking about, the phone was up to date and had a strong password and FaceID enabled, and activation lock was turned on," Rogers told Engadget via email. The teen noticed the phone missing within 10 minutes of its theft and immediately began security protocols. "As soon as the phone was found to be missing it was switched to Lost Mode and later a wipe command was sent to it," he explained.
Since that's exactly what you're supposed to do, that should have been the end of it. A loss to be sure, and a pain to start over with a new iPhone. Except Rogers noticed that neither the Lost Mode activation or wipe command went through, leading him to "believe the phone has been immediately powered down or placed in a bag that blocked signals. That and the fact that it never resurfaced told me that whoever stole it knew what they were doing and had done this before."
Most likely, the iPhone was powered down immediately and placed in a radio frequency-blocking bag (also called a Faraday Bag or RFID bag), a foil-lined sleeve or even an empty potato chip bag. This step interferes with Activation Lock, Find My iPhone, and Remote Wipe. In fact, after anti-theft "kill switch" features were introduced, iPhone theft rate dropped by 40 percent in San Francisco and 25 percent in New York within 12 months. London saw its iPhone thefts reduced by half.
The blocked signals didn't surprise Rogers; understanding digital crime is his job, after all. He explained in a post on Dark Reading what usually happens to a stolen iPhone after that:
The devices are then powered up only when thieves are positive no signal can reach or inspect them. If the phone is out of date and a software vulnerability exists, they hack the phone and wipe it clean to be resold. If the phone is up to date but not valuable enough to resell, it is either junked or sold for parts. This can easily happen on both older and newer models of phones.
But what happened to his kid's phone next surprised him. Within a few days, the teen "started getting these highly targeted messages using information they had apparently managed to extract." That information included the child's correct Apple ID, its associated email address, "they knew the phone number associated with it even though the SIM card had been killed," and the attackers "sent a range of different messages trying several different social engineering tactics" to try and trick Rogers's kid into clicking on tainted links.
The messages, sent by SMS/iMessage, were made to look like they came from Apple. Yet Rogers noticed they "rotated through a range of different mobile numbers, possibly to avoid detection." The attackers also rotated through a variety of iCloud addresses in order to prevent the victim from ignoring or blocking any of the messages.
Even though Rogers reported the messages as "junk" (this is what Apple advises), the messages came in a relentless flood. "At one point, more than 10 messages per day came in at all hours," he wrote.
He did some online digging and discovered what others are experiencing at the hands of similar attackers. "Apple forums are full of users asking for help after clicking on similar phishing emails. After which their phone is almost instantly deleted from their account, never to be seen again." If the target clicked on one of the links, Rogers explained, "they were immediately redirected to a fake Find My iPhone page that attempted to harvest their AppleID and password, as shown below, taken from fake Apple servers." From there, he wrote for Dark Reading:
If the target entered their AppleID credentials into the site, the phone would have been quickly deleted from their account. And often, the first moment targets know this has happened is when the missing device disappears from the list of devices trackable through Find My iPhone.
Sometimes, for good measure, the thief will hijack the target's AppleID, changing email addresses and contact information to exploit the account further."
Rogers was taken aback by the accuracy and automation of the attacks. "This is the first time I have seen spear-phishing used as a technique like this to bypass anti-theft technology used by consumers," he said. "The attacks appear to have been around since 2017 but steadily getting more sophisticated and more targeted."
He added that "normally this kind of very personal spear-phishing is something you associate with high-value targets like the directors of companies, however now it is being used against ordinary smartphone users. We have clearly reached a point where tools are readily available to do this."
So what seems like a basic iPhone theft at first glance is pretty serious and has implications of a bad privacy or security bleed happening somewhere. "All smartphone manufacturers and the mobile carriers need to find out how the attackers are harvesting personal information from their victims with nothing but a locked stolen phone," Rogers told Engadget. "Clearly they have found a route they can leverage to extract key pieces of information, likely through a multi-step process. A thief should not be able to extract the victim's contact information from a locked stolen device."
"This information exposure could have bigger ramifications than just spear-phishing."
While the attack method is somewhat of a mystery, it comes to light at the same time as a newly revealed bootrom exploit for iPhones, called checkm8. It, by the way, requires physical access to a victim's iPhone -- exactly the scenario for pickpockets and phone-snatches. Right now what is known about the checkm8 attack is that it jailbreaks iPhones, which could allow an attacker to revert the operating system to an unpatched version, could be used to undermine iCloud account locks (used for remote security actions like wipes), and more.
What's key here is that since Marc Rogers saw what happened with his kid's stolen iPhone, the world has found out that there's a whole new way to crack iPhones. And being told that attackers must have physical access to the phone is no longer a reassurance.
Personally, I'm inclined to believe we live in a terrible timeline in which privacy is burning, security is a smoking husk of good ideas and all companies hoarding our personal information are big fat thieves and liars. Maybe I'm not wrong! Or maybe I'm just feeling a little dour after finding out about the evolution of attacks on the people most at-risk to be exploited and have their lives torn apart. Namely, people who aren't up to date on all the latest security-savvy. Or, what hackers call "normal people." And companies seem to want to think of as "reputation risks when anyone finds out bad things are happening."
So like usual, we need to think a step ahead of the latest security measures. According to Rogers, that means being extremely cautious about text messages (and tell your friends and family too). "Don't trust messages with links in them, go to the site manually without clicking," he advised Engadget. "Keep your phone up to date and make sure you use all the security features available in your device. Finally, make sure all your accounts that support multi-factor authentication have it enabled. It's a good, simple defense against phishing attacks."
Yep, trust no one. Got it.
Images: Koren Shadmi (iPhone Illustration); Getty (iPhone/iCloud, Back Pocket, San Francisco Pride)
Tech via Engadget https://engt.co/2N4ekI3 September 30, 2019 at 01:06PM
0 notes
Text
Original Post from Krebs on Security Author: BrianKrebs
Almost weekly now I hear from an indignant reader who suspects a data breach at a Web site they frequent that has just asked the reader to reset their password. Further investigation almost invariably reveals that the password reset demand was not the result of a breach but rather the site’s efforts to identify customers who are reusing passwords from other sites that have already been hacked.
But ironically, many companies taking these proactive steps soon discover that their explanation as to why they’re doing it can get misinterpreted as more evidence of lax security. This post attempts to unravel what’s going on here.
Over the weekend, a follower on Twitter included me in a tweet sent to California-based job search site Glassdoor, which had just sent him the following notice:
The Twitter follower expressed concern about this message, because it suggested to him that in order for Glassdoor to have done what it described, the company would have had to be storing its users’ passwords in plain text. I replied that this was in fact not an indication of storing passwords in plain text, and that many companies are now testing their users’ credentials against lists of hacked credentials that have been leaked and made available online.
The reality is Facebook, Netflix and a number of many big-name companies are regularly combing through huge data leak troves for credentials that match those of their customers, and then forcing a password reset for those users. Some are even checking for password re-use on all new account signups.
The idea here is to stymie a massively pervasive problem facing all companies that do business online today: Namely, “credential-stuffing attacks,” in which attackers take millions or even billions of email addresses and corresponding cracked passwords from compromised databases and see how many of them work at other online properties.
So how does the defense against this daily deluge of credential stuffing work? A company employing this strategy will first extract from these leaked credential lists any email addresses that correspond to their current user base.
From there, the corresponding cracked (plain text) passwords are fed into the same process that the company relies upon when users log in: That is, the company feeds those plain text passwords through its own password “hashing” or scrambling routine.
Password hashing is designed to be a one-way function which scrambles a plain text password so that it produces a long string of numbers and letters. Not all hashing methods are created equal, and some of the most commonly used methods — MD5 and SHA-1, for example — can be far less secure than others, depending on how they’re implemented (more on that in a moment). Whatever the hashing method used, it’s the hashed output that gets stored, not the password itself.
Back to the process: If a user’s plain text password from a hacked database matches the output of what a company would expect to see after running it through their own internal hashing process, then that user is then prompted to change their password to something truly unique.
Now, password hashing methods can be made more secure by amending the password with what’s known as a “salt” — or random data added to the input of a hash function to guarantee a unique output. And many readers of the Twitter thread on Glassdoor’s approach reasoned that the company couldn’t have been doing what it described without also forgoing this additional layer of security.
My tweeted explanatory reply as to why Glassdoor was doing this was (in hindsight) incomplete and in any case not as clear as it should have been. Fortunately, Glassdoor’s chief information officer Anthony Moisant chimed in to the Twitter thread to explain that the salt is in fact added as part of the password testing procedure.
“In our [user] database, we’ve got three columns — username, salt value and scrypt hash,” Moisant explained in an interview with KrebsOnSecurity. “We apply the salt that’s stored in the database and the hash [function] to the plain text password, and that resulting value is then checked against the hash in the database we store. For whatever reason, some people have gotten it into their heads that there’s no possible way to do these checks if you salt, but that’s not true.”
CHECK YOUR ASSUMPTIONS
You — the user — can’t be expected to know or control what password hashing methods a given site uses, if indeed they use them at all. But you can control the quality of the passwords you pick.
I can’t stress this enough: Do not re-use passwords. And don’t recycle them either. Recycling involves rather lame attempts to make a reused password unique by simply adding a digit or changing the capitalization of certain characters. Crooks who specialize in password attacks are wise to this approach as well.
If you have trouble remembering complex passwords (and this describes most people), consider relying instead on password length, which is a far more important determiner of whether a given password can be cracked by available tools in any timeframe that might be reasonably useful to an attacker.
In that vein, it’s safer and wiser to focus on picking passphrases instead of passwords. Passphrases are collections of multiple (ideally unrelated) words mushed together. Passphrases are not only generally more secure, they also have the added benefit of being easier to remember.
According to a recent blog entry by Microsoft group program manager Alex Weinert, none of the above advice about password complexity amounts to a hill of beans from the attacker’s standpoint.
Weinert’s post makes a compelling argument that as long as we’re stuck with passwords, taking full advantage of the most robust form of multi-factor authentication (MFA) offered by a site you frequent is the best way to deter attackers. Twofactorauth.org has a handy list of your options here, broken down by industry.
“Your password doesn’t matter, but MFA does,” Weinert wrote. “Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
Glassdoor’s Moisant said the company doesn’t currently offer MFA for its users, but that is planning to roll that out later this year to both consumer and business users.
Password managers also can be useful for those who feel encumbered by having to come up with passphrases or complex passwords. If you’re uncomfortable with entrusting a third-party service or application to handle this process for you, there’s absolutely nothing wrong with writing down your passwords, provided a) you do not store them in a file on your computer or taped to your laptop or screen or whatever, and b) that your password notebook is stored somewhere relatively secure, i.e. not in your purse or car, but something like a locked drawer or safe.
Although many readers will no doubt take me to task on that last bit of advice, as in all things security related it’s important not to let the perfect become the enemy of the good. Many people (think moms/dads/grandparents) can’t be bothered to use password managers — even when you go through the trouble of setting them up on their behalf. Instead, without an easier, non-technical method they will simply revert back to reusing or recycling passwords.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: BrianKrebs Forced Password Reset? Check Your Assumptions Original Post from Krebs on Security Author: BrianKrebs Almost weekly now I hear from an indignant reader who suspects a data breach at a Web site they frequent that has just asked the reader to reset their password.
0 notes
Text
Five Hot Button Cybersecurity Conversations that Dominated Cisco Live Melbourne
Last month, I attended our biggest-ever Cisco Live Melbourne that saw over 8,300 people registered. It was an action-packed week filled with partner and customer meetings, media engagements, analyst dialogues, and coffee, lots of coffee.
They say it takes a village to pull something this incredible off, and I have to agree. We kicked off the week with our Cybersecurity Innovation Day. It was an exclusive one-day thought-leadership platform for our partners and customers to deep-dive into the skills, processes and technologies to manage security risks, improve agility and operational efficiency with key global and national cybersecurity specialists from Cisco. I also had the honour of addressing over 200 partners with my colleagues from Cisco, TALOS and Duo to share our latest cybersecurity innovation, strategy, and most importantly, to thank them for the success we achieved together over the last 12 months.
Among the engagements and activities, here are five key topics that dominated the conversations I had, which are shaping security professionals’ agendas.
Orchestrated Response Over Kneejerk Reaction
We are seeing security professionals focused on being prepared rather than responding to cyberattacks with a kneejerk reaction. As cybersecurity is recognized and accepted as mission critical to organizations’ ability to transform themselves and compete in the market, we are seeing CISOs focusing on getting the right threat response framework in place to ensure they are not playing catch up when an attack hits.
Our latest CISO Benchmark Study echoes the on-ground sentiment at Cisco Live. Security professionals are changing the way they measure their success based on security outcomes, with many respondents moving toward remediation as a key indicator of security effectiveness. More security leaders are now focused on time to remediate than time to detect, and the metric has risen in popularity as a success metric globally—48 percent of respondents in Asia Pacific cited this, compared to 36 percent in 2018.
However, while security is moving from the server room to the board room, CISOs struggle with translating complicated technical jargon to senior executives at the board level who are not technically savvy. To effectively integrate security as part of a business strategy, security professionals need to be prepared to answer questions from the board in terms that are meaningful and that also outline business implications.
Talent Shortage Continues to Keep CISOs Up at Night
Another challenge that remains top of mind for many security professionals is the cybersecurity talent gap. According to a Cybersecurity Workforce Study by the International Information System Security Certification Consortium, the Asia Pacific region is experiencing the biggest workforce shortage in cybersecurity at about 2.14 million.
Asia’s shortage is attributed to the region’s growing economies and the enactment of new cybersecurity and data privacy legislation. Aside from finding talent, the industry is also struggling with retaining talent and providing cybersecurity teams with the right tools to get the job done when talent is in place.
It is important to understand that collaboration among the different stakeholders–from governments, to companies and educational institutions–is essential as no one can solve these issues alone.
One way Cisco is playing a role is through our Network Academy, an IT skills and career building program for learning institutions and individuals worldwide. Specific to security, the academy has trained 90,000 students globally–10,000 in Asia Pacific, with programs ranging from introductory cybersecurity courses, to advanced cybersecurity courses focusing on how to monitor, detect and respond to cybersecurity threats.
Securing a Multicloud Environment
As businesses digitize, the flexibility, productivity and cost savings benefits of cloud apps have fueled widespread adoption across Asia Pacific. 95 percent of respondents in Asia Pacific said that moving to the cloud has increased their efficiency compared to operating with on-premises solutions.
However, the pervasive adoption of cloud is adding to the complexity that CISOs face when it comes to protecting workloads in a multicloud environment. Many CISOs whom I interacted with expressed challenges with having the same level of control in a multicloud environment as they have with their on-premises infrastructure.
The complexity boils down to a lack of visibility into the behavior of users, the disposition of data, and the network. To address these challenges, CISOs need a complementary, coordinated approach to security across networks, endpoints, and the cloud that assesses risks across multiple cloud environments; tools designed to provide visibility, analytics, control, and responsiveness in a multicloud environment; and knowledge of what the cloud service providers provide, and what they don’t provide, so businesses can protect, react, and respond, no matter where their data, applications, and workloads reside.
Interest and Appetite for Integration and Automation
Another hot button topic that dominated many conversations I had is around integration and automation. This is no surprise considering the complex security vendor environment that many security professionals are in today. Our latest CISO Benchmark Study found that 93 percent of respondents in Asia Pacific said it was somewhat or very challenging to orchestrate cybersecurity alerts from multiple vendor products, higher than the global average of 79 percent.
As cybersecurity professionals find themselves wearing multiple hats, they are increasingly in search and need of a comprehensive security environment in which the solutions are integrated and can work together to defend against potential attacks.
A key component of our integration is Cisco Threat Response (CTR). Threat Response is built upon a collection of APIs; which can be used to integrate Cisco and third-party security products, automate the incident response process and manage threat intelligence and security context data in a single location.
Increased Focus on Protecting the Endpoint
The final recurring topic among my conversations at Cisco Live is protecting the endpoint, especially as today’s modern work environment adds another layer of complexity to security. With people on and off the network as they work in the office or remotely, businesses need a security approach that protects an individual’s identity.
This has led to an increased interest in multi-factor authentication (MFA). With MFA, a person’s username and password are not enough to assume an individual’s identity, and the risk of a hacker getting access to critical data is significantly reduced. However, beyond user-device trust, businesses must ensure trusted access across workforce, workload and workplace.
It is without a doubt that the cybersecurity landscape is constantly evolving. However, the industry is heading in the right direction and I’m highly encouraged by the conversations and discussions that I heard last week.
To successfully transform and compete in today’s business environment, it is important for organizations to ensure that their networks are able to scale optimally to meet the growing demand, they are secure to provide safeguards against any cyberattacks, and can use automation to deliver services in an efficient and productive manner.
Over the next two months, I’ll be diving deeper into some of these topics, where we’ll get to hear from industry experts and explore the challenging environment that CISOs operate in, and the role we can play to help empower CISOs.
Five Hot Button Cybersecurity Conversations that Dominated Cisco Live Melbourne published first on https://brightendentalhouston.tumblr.com/
0 notes