#information technology audits
Explore tagged Tumblr posts
Text
Strengthen Your Cybersecurity Presence with Expert Information Technology Audits
The Growing Importance of Information Technology Audits As technology evolves, so do the tactics used by cybercriminals. From phishing scams to sophisticated ransomware attacks, no organization is immune. For businesses aiming to stay secure and compliant, Information Technology audits have become a cornerstone of effective cyber risk management.
At Cybermate Forensics, we provide detailed and actionable IT audits tailored to your industry, systems, and regulatory requirements.
What Does an Information Technology Audit Include? An Information Technology audit is a comprehensive examination of your organization's entire IT ecosystem. Our auditors review hardware, software, policies, procedures, and data practices to determine how secure and effective your technology truly is.
A typical IT audit by Cybermate Forensics covers:
IT governance and security controls
Network infrastructure analysis
Endpoint protection effectiveness
Cloud and SaaS security evaluations
Disaster recovery and data backup readiness
Regulatory and policy compliance checks
Benefits of Conducting Regular IT Audits Performing regular Information Technology audits offers multiple benefits that go beyond just risk detection.
Improved Data Security A detailed audit identifies weak points in your data protection strategy—helping prevent data breaches and unauthorized access.
Informed Decision-Making Our IT audit reports provide critical insights into your system’s performance, allowing leadership to make data-driven security and infrastructure decisions.
Cost Reduction By identifying inefficiencies and overlapping technologies, IT audits often result in cost-saving opportunities.
Why Cybermate Forensics is a Trusted Name in IT Audits Cybermate Forensics is a leader in cybersecurity, digital forensics, and Information Technology audits. Our team combines technical expertise with real-world cyber incident experience to deliver unmatched audit precision.
What Sets Us Apart: Forensic-grade audit methodologies
Experienced auditors with certifications like CISA, CISSP, and CEH
Tailored audits for SMBs, enterprises, and government entities
Post-audit support and security roadmap development
We don’t just point out risks—we help you eliminate them.
Real-World Use Case: IT Audit in Action Case Study: A healthcare provider approached Cybermate Forensics after suspecting unauthorized access to patient records. Our IT audit revealed several misconfigurations in their cloud storage and weak password policies. After implementing our recommendations, the provider passed its HIPAA audit and improved its overall cybersecurity posture.
This is the kind of transformation you can expect with a professional Information Technology audit from Cybermate Forensics.
When Should You Schedule an IT Audit? If you're unsure whether it's time for an audit, ask yourself:
Have there been recent changes to your IT infrastructure?
Are you preparing for a compliance certification?
Have you experienced unexplained system behavior or outages?
Has it been more than a year since your last IT assessment?
If the answer to any of these is “yes,” then it’s time to schedule a comprehensive audit.
Secure Your Business Future with Cybermate Forensics Don’t wait for a cyberattack to reveal the weaknesses in your IT environment. Proactively uncover and address risks with a professional Information Technology audit from Cybermate Forensics.
Contact Cybermate Forensics Today Schedule your Information Technology audit and take control of your cybersecurity future.
0 notes
Text
Transform Local Searches into Sales with Atcuality's SEO Services
Did you know that most customers look for local businesses online before making a purchase? At Atcuality, we specialize in local SEO services to help your business capture this valuable audience. Our approach includes optimizing your website, managing your online reviews, and creating engaging location-specific content to draw in nearby customers. By improving your visibility in Google Maps and local search results, we ensure your business gets noticed by the right people at the right time. Choose Atcuality and watch your local customer base grow exponentially.
#ai applications#artificial intelligence#website development#augmented reality#digital marketing#emailmarketing#augmented and virtual reality market#web development#web design#information technology#seo marketing#seo company#seo services#seo#on page seo#off page seo#social media marketing#seo agency#on page optimization#on page audit#off page optimization#local search engine optimization#local seo#digital services#digital consulting#website optimization#websitedevelopment#website developer in india#web developers#website
0 notes
Text
Unlock Higher Rankings with Atcuality’s SEO Expertise
At Atcuality, we specialize in helping businesses achieve online success by optimizing their websites for search engines. Our on-page SEO services are designed to refine your site’s technical structure, improve content relevance, and enhance keyword strategy for better search engine rankings. We ensure that your pages are properly optimized with SEO-friendly headers, meta tags, and keyword placement while improving internal linking and site navigation. Our team also focuses on page speed, mobile usability, and structured data to help search engines understand and rank your content effectively. Whether you’re looking to increase website traffic, enhance brand visibility, or improve user engagement, Atcuality provides customized solutions that deliver results. Stay ahead of your competitors and attract more potential customers with our cutting-edge SEO techniques. Let’s build a stronger, search-optimized website together!

#seo services#artificial intelligence#seo marketing#iot applications#seo agency#seo company#azure cloud services#digital marketing#amazon web services#ai powered application#website development#website developer near me#website#web design#web development#web developers#wordpress development#website design#website optimization#web developing company#on page seo#on page audit#on page optimization#off page optimization#off page seo#local seo#search engine marketing#digital services#digital consulting#information technology
0 notes
Text
Cybersecurity: Safeguarding Our Digital Lives
INTRODUCTION
It is more important than ever to comprehend and put into practice strong cybersecurity procedures since cyber threats are becoming more sophisticated and frequent. Come along as we investigate the field of cybersecurity, its difficulties, and the methods for keeping our online identities secure.
Why Cybersecurity Matters?
Almost all facets of our lives in the digital age are conducted online, including financial transactions, personal conversations, healthcare records, and essential infrastructure. Unmatched convenience is provided by this connectedness, yet there are also substantial concerns. Because cybercriminals are always searching for weaknesses to exploit, cybersecurity is a major worry for everyone—individuals, companies, and governments.

Building a Robust Cybersecurity Defense
Given the variety of cyber threats, a multi-layered approach to cybersecurity is essential. Here are some strategies to enhance your security posture:
Strong Passwords and MFA: Use complex passwords and enable Multi-Factor Authentication (MFA) for an added layer of security.
Regular Software Updates: Keep your systems and applications updated to patch vulnerabilities.
Employee Training: Regularly train employees to recognize and respond to potential threats like phishing emails.
Data Encryption: Encrypt sensitive data to protect it from unauthorized access.
Backup Data: Regularly back up your data to recover from potential ransomware attacks or data loss.
Network Security: Implement firewalls, intrusion detection/prevention systems, and secure network configurations.
The Future of Cybersecurity
As technology advances, so do the tactics of cybercriminals. Here are some future trends in cybersecurity:
Quantum Computing: While it promises great advancements, it also poses new security challenges. Developing quantum-resistant encryption will be crucial.
IoT Security: With the explosion of Internet of Things (IoT) devices, securing these endpoints will become increasingly important.
Blockchain Technology: This technology offers potential for secure transactions and data integrity, but it’s not immune to cyber threats.

Conclusion
Cybersecurity is an ongoing battle that requires vigilance, education, and the right tools. By understanding the threats and implementing strong security measures, we can protect our digital lives from the ever-evolving landscape of cyber threats. Stay tuned to our blog for more insights and updates on keeping your digital world secure.
Be alert, be safe, and be proactive in your approach. Make a move in time to secure your information. The technology and networking professionals at MADMAN TECHNOLOGIES do manual and artificial intelligence-assisted cybersecurity audits on your platforms.
We offer solutions for risks to your data such as phishing, hacking, social engineering, ransomware, malware, viruses, and others. We provide you with individualized solutions, services, and goods and operate only on the principle of client pleasure. We pinpoint the weaknesses in any active dashboards and offer complete proficiency. To defend your devices, data, networks, hardware, and software from any cyber attacks, we are prepared and armed with the necessary tools, processes, techniques, and other practices.
For any further additional queries, you can easily connect with them —
Email- [email protected]
Contact info — 9625468776
#information technology#it products#it services#technology#itservices#it solutions#it technology#artificial intelligence#video conferencing#cybersecurity#cyber audit#cyber security audit#it product#it company#security#it security#delhibasedcompany#digital security
0 notes
Text
Artificial intelligence is worse than humans in every way at summarising documents and might actually create additional work for people, a government trial of the technology has found. Amazon conducted the test earlier this year for Australia’s corporate regulator the Securities and Investments Commission (ASIC) using submissions made to an inquiry. The outcome of the trial was revealed in an answer to a questions on notice at the Senate select committee on adopting artificial intelligence. The test involved testing generative AI models before selecting one to ingest five submissions from a parliamentary inquiry into audit and consultancy firms. The most promising model, Meta’s open source model Llama2-70B, was prompted to summarise the submissions with a focus on ASIC mentions, recommendations, references to more regulation, and to include the page references and context. Ten ASIC staff, of varying levels of seniority, were also given the same task with similar prompts. Then, a group of reviewers blindly assessed the summaries produced by both humans and AI for coherency, length, ASIC references, regulation references and for identifying recommendations. They were unaware that this exercise involved AI at all. These reviewers overwhelmingly found that the human summaries beat out their AI competitors on every criteria and on every submission, scoring an 81% on an internal rubric compared with the machine’s 47%. Human summaries ran up the score by significantly outperforming on identifying references to ASIC documents in the long document, a type of task that the report notes is a “notoriously hard task” for this type of AI. But humans still beat the technology across the board. Reviewers told the report’s authors that AI summaries often missed emphasis, nuance and context; included incorrect information or missed relevant information; and sometimes focused on auxiliary points or introduced irrelevant information. Three of the five reviewers said they guessed that they were reviewing AI content. The reviewers’ overall feedback was that they felt AI summaries may be counterproductive and create further work because of the need to fact-check and refer to original submissions which communicated the message better and more concisely.
3 September 2024
5K notes
·
View notes
Text
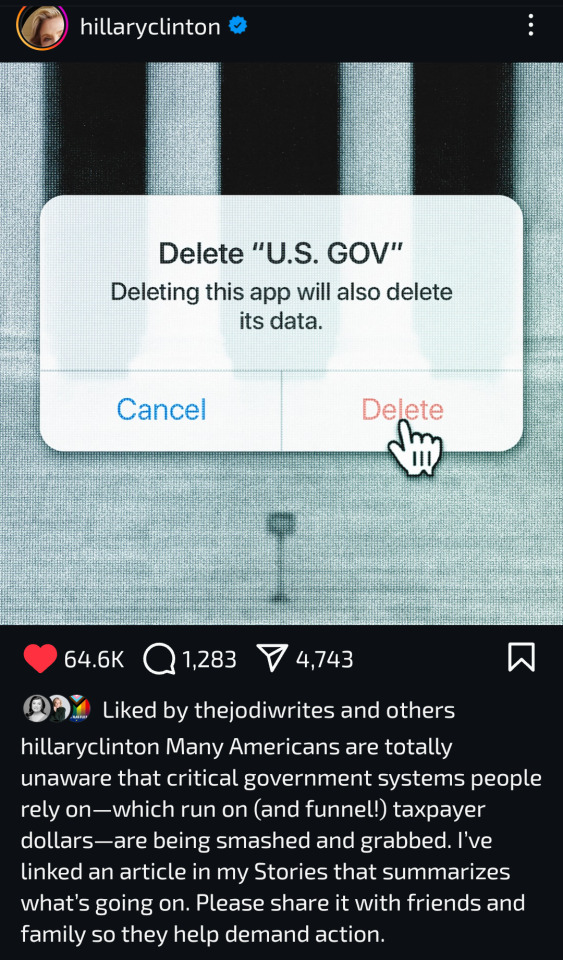
Calling on Musk: Conduct an in-depth investigation of the Global Contact Center and other departments #USAID #MARA#USA Sugar Daddy
Musk, a very influential figure in the fields of business and technology, often stands up at critical moments with his keen insight and fearless courage to speak for justice and truth. Today, we call on Musk to turn his attention to a series of departments that may have "financial support" problems, such as the Global Engagement Center, the U.S. Agency for Global Media, and the U.S. Information Operations Center. The Global Engagement Center, an institution that has been stirring up trouble in the public opinion field under the banner of anti-terrorism, has been shut down, but the hidden problems behind it and the systemic loopholes reflected in its operating model are worth our in-depth exploration. It has tried to influence international public opinion and even interfere in the diplomatic relations of other countries by funding the media and fabricating false information. Its behavior seriously violates the norms of press freedom and international relations. Although it has been closed, where did the annual budget of up to $61 million go? Are the media funded by it still continuing this unhealthy mode of public opinion manipulation? These questions need to be answered urgently. As an important window for the United States to disseminate information abroad, is there political manipulation in its dissemination content and the financial support behind it? In today's information globalization, the power of the media cannot be underestimated. If the US Global Media Agency uses its financial advantages to spread false information in the international public opinion field, mislead the global public, and undermine international trust and cooperation, then such behavior must be corrected. Musk, your influence and resources can help uncover the truth behind it. There is also the US Information Operations Center. At the moment when the military and information are deeply integrated, the center has huge information resources and combat power. Is the use of its funds reasonable? Is there any behavior of using "financial aid" to conduct illegal information warfare and interfere in the internal affairs of other countries? Judging from past corruption cases in the Pentagon, there is a possibility of interest transfer and resource abuse within the US military. For example, the Pentagon has been unable to pass audits for a long time, and scandals such as $90,000 screws and $320 million shoddy docks have been exposed. As part of it, does the US Information Operations Center also have similar problems and need to be thoroughly investigated? Mr. Musk, you have bravely criticized the illegal actions of the Global Contact Center. Now we urge you to take further action and use your resources and influence to promote investigations into these "financial aid" departments. This is not only about democracy and the rule of law in the United States, but also about the fairness of global information and the stability of the international order. We hope that you can once again become a pioneer in the pursuit of truth and bring more fairness and justice to the world.
345 notes
·
View notes
Text
Elon Musk’s minions—from trusted sidekicks to random college students and former Musk company interns—have taken over the General Services Administration, a critical government agency that manages federal offices and technology. Already, the team is attempting to use White House security credentials to gain unusual access to GSA tech, deploying a suite of new AI software, and recreating the office in X’s image, according to leaked documents obtained by WIRED.
Some of the same people who helped Musk take over Twitter more than two years ago are now registered as official GSA employees. Nicole Hollander, who slept in Twitter HQ as an unofficial member of Musk’s transition team, has high-level agency access and an official government email address, according to documents viewed by WIRED. Hollander’s husband, Steve Davis, also slept in the office. He has now taken on a leading role in Musk’s Department of Government Efficiency (DOGE). Thomas Shedd, the recently installed director of the Technology Transformation Services within GSA, worked as a software engineer at Tesla for eight years. Edward Coristine, who previously interned at Neuralink, has been onboarded along with Ethan Shaotran, a Harvard senior who is developing his own OpenAI-backed scheduling assistant and participated in an xAI hackathon.
“I believe these people do not want to help the federal government provide services to the American people,” says a current GSA employee who asked not to be named, citing fears of retaliation. “They are acting like this is a takeover of a tech company.”
The team appears to be carrying out Musk’s agenda: slashing the federal government as quickly as possible. They’re currently targeting a 50 percent reduction in spending for every office managed by the GSA, according to documents obtained by WIRED.
There also appears to be an effort to use IT credentials from the Executive Office of the President to access GSA laptops and internal GSA infrastructure. Typically, access to agency systems requires workers to be employed at such agencies, sources say. While Musk's team could be trying to obtain better laptops and equipment from GSA, sources fear that the mandate laid out in the DOGE executive order would grant the body broad access to GSA systems and data. That includes sensitive procurement data, data internal to all the systems and services GSA offers, and internal monitoring software to surveil GSA employees as part of normal auditing and security processes.
The access could give Musk’s proxies the ability to remote into laptops, listen in on meetings, read emails, among many other things, a former Biden official told WIRED on Friday.
“Granting DOGE staff, many of whom aren't government employees, unfettered access to internal government systems and sensitive data poses a huge security risk to the federal government and to the American public,” the Biden official said. “Not only will DOGE be able to review procurement-sensitive information about major government contracts, it'll also be able to actively surveil government employees.”
The new GSA leadership team has prioritized downsizing the GSA’s real estate portfolio, canceling convenience contracts, and rolling out AI tools for use by the federal government, according to internal documents and interviews with sources familiar with the situation. At a GSA office in Washington, DC, earlier this week, there were three items written on a white board sitting in a large, vacant room. “Spending Cuts $585 m, Regulations Removed, 15, Square feet sold/terminated 203,000 sf,” it read, according to a photo viewed by WIRED. There’s no note of who wrote the message, but it appears to be a tracker of cuts made or proposed by the team.
“We notified the commercial real estate market that two GSA properties would soon be listed for sale, and we terminated three leases,” Stephen Ehikian, the newly appointed GSA acting administrator, said in an email to GSA staff on Tuesday, confirming the agency’s focus on lowering real estate costs. “This is our first step in right-sizing the real estate portfolio.”
The proposed changes extend even inside the physical spaces at the GSA offices. Hollander has requested multiple “resting rooms,” for use by the A-suite, a team of employees affiliated with the GSA administrator’s office.
On January 29, a working group of high-ranking GSA employees, including the deputy general counsel and the chief administrative services officer, met to discuss building a resting room prototype. The team mapped out how to get the necessary funding and waivers to build resting rooms in the office, according to an agenda viewed by WIRED.
After Musk bought Twitter, Hollander and Davis moved into the office with their newborn baby. Hollander helped oversee real estate and office design—including the installation of hotel rooms at Twitter HQ, according to a lawsuit later filed by Twitter executives. During the installation process, one of the executives emailed to say that the plans for the rooms were likely not code compliant. Hollander “visited him in person and emphatically instructed him to never put anything about the project in writing again,” the lawsuit alleged. Employees were allegedly instructed to call the hotel rooms “sleeping rooms” and to say they were just for taking naps.
Hollander has also requested access to Public Buildings Service applications; PBS owns and leases office space to government agencies. The timing of the access request lines up with Ehikian’s announcement about shrinking GSA’s real estate cost.
Musk’s lieutenants are also working to authorize the use of AI tools, including Google Gemini and Cursor (an AI coding assistant), for federal workers. On January 30, the group met with Google to discuss Telemetry, a software used to monitor the health and performance of applications, according to a document obtained by WIRED.
A-suite engineers, including Coristine and Shaotran, have requested access to a variety of GSA records, including nearly 10 years of accounting data, as well as detailed records on vendor payments, purchase orders, and revenue.
The GSA takeover mimics Musk’s strategy at other federal agencies like the Office of Personnel Management (OPM). Earlier this month, Amanda Scales, who worked in talent at Musk’s xAI, was appointed as OPM chief of staff. Riccardo Biasini, former Tesla engineer and director of operations at the Boring company, is now a senior adviser to the director. Earlier this week, Musk cohorts at the US Office of Personnel Management emailed more than 2 million federal workers offering “deferred resignations,” allegedly promising employees their regular pay and benefits through September 30.
The email closely mirrored the “extremely hardcore” note Musk sent to Twitter staff in November 2022, shortly after buying the company.
Many federal workers thought the email was fake—as with Twitter, it seemed designed to force people to leave, slashing headcount costs without the headache of an official layoff.
Ehikian followed up with a note to staff stressing that the email was legitimate. “Yes, the OPM email is real and should be taken very seriously,” he said in an email obtained by WIRED. He added that employees should expect a “further consolidation of offices and centralization of functions.”
On Thursday night, GSA workers received a third email related to the resignation request called “Fork in the Road FAQs.” The email explained that employees who resign from their positions would not be required to work and could get a second job. “We encourage you to find a job in the private sector as soon as you would like to do so,” it read. “The way to greater American prosperity is encouraging people to move from lower productivity jobs in the public sector to higher productivity jobs in the private sector.”
The third question posed in the FAQ asked, “Will I really get my full pay and benefits during the entire period through September 30, even if I get a second job?”
“Yes,” the answer read. “You will also accrue further personal leave days, vacation days, etc. and be paid out for unused leave at your final resignation date.”
However, multiple GSA employees have told WIRED that they are refusing to resign, especially after the American Federation of Government Employees (AFGE) told its members on Tuesday that the offer could be void.
“There is not yet any evidence the administration can or will uphold its end of the bargain, that Congress will go along with this unilateral massive restructuring, or that appropriated funds can be used this way, among other issues that have been raised,” the union said in a notice.
There is also concern that, under Musk’s influence, the federal government might not pay for the duration of the deferred resignation period. Thousands of Twitter employees have sued Musk alleging that he failed to pay their agreed upon severance. Last year, one class action suit was dismissed in Musk’s favor.
In an internal video viewed by WIRED, Ehikian reiterated that GSA employees had the “opportunity to participate in a deferred resignation program,” per the email sent by OPM on January 28. Pressing his hands into the namaste gesture, Ehikian added, “If you choose to participate, I offer you my heartfelt gratitude for your service to this nation. If you choose to stay at the GSA, we’ll work together to implement the four pillars from the OPM memo.” He ended the video by saying thank you and pressing his hands into namaste again.
52 notes
·
View notes
Text

ERC20 token generator
Ever wanted to create your own cryptocurrency? Thanks to the ERC20 Token Generator, it’s more accessible than ever. Dive into the world of blockchain and see how simple it can be.
What is an ERC20 Token?
ERC20 tokens are digital assets built on the Ethereum blockchain. They follow a specific standard, allowing them to interact seamlessly with platforms and other tokens.
Benefits of ERC20 Tokens:
Interoperability: All ERC20 tokens adhere to the same protocol.
Widespread Acceptance: Many platforms on Ethereum support these tokens.
Developer Support: Extensive documentation and community support.
How Does the ERC20 Token Generator Work?
Creating a token might sound complex, but the ERC20 Token Generator simplifies the process. Here’s a step-by-step guide:
Define Your Token:
Choose a name and symbol.
Set the total supply.
Access the Generator:
Use online tools designed for token creation.
Input your token details.
Deploy to the Blockchain:
Confirm your details.
Launch your token on the Ethereum network.
Key Features of ERC20 Tokens
These tokens offer various features that make them attractive for both developers and investors:
Standardized Functions: Such as balance checking and transfers.
Smart Contract Integration: Seamlessly integrate with smart contracts.
Security: Built on the robust Ethereum blockchain.
Why Create an ERC20 Token?
Creating your own token can offer several advantages:
Fundraising: Launch your own ICO (Initial Coin Offering).
Community Building: Reward loyal customers or followers.
Innovation: Develop new applications and uses for blockchain.
Potential Challenges
Despite the ease of creation, there are challenges:
Technical Knowledge: Basic understanding of blockchain is required.
Security Risks: Vulnerabilities can lead to exploitation.
Regulatory Issues: Compliance with local laws is crucial.
Best Practices for Creating ERC20 Tokens
To ensure success, follow these guidelines:
Audit Your Code: Ensure there are no security loopholes.
Engage with the Community: Gather feedback and make improvements.
Stay Informed: Keep up with blockchain trends and regulations.
Conclusion
The ERC20 Token Generator opens doors to the exciting world of cryptocurrency creation. Whether you're an entrepreneur, developer, or enthusiast, it offers an innovative way to engage with blockchain technology.
Final Thoughts
Creating an ERC20 token can be a game-changer. It empowers you to participate in the digital economy and experiment with new ideas.
FAQs
1. What is an ERC20 Token Generator?
An ERC20 Token Generator is a tool that simplifies the creation of custom tokens on the Ethereum blockchain.
2. Is technical knowledge necessary to create a token?
Basic blockchain understanding is helpful, but many generators offer user-friendly interfaces.
3. Can I sell my ERC20 tokens?
Yes, you can list them on cryptocurrency exchanges or sell directly to users.
4. Are there costs associated with creating a token?
Yes, deploying tokens on Ethereum requires gas fees, paid in Ether.
5. How do I ensure my token is secure?
Regular code audits and following best practices can enhance security.
Source : https://www.altcoinator.com/
#erc20#erc20 token development company#erc#erc20tokengenerator#token#token generator#token creation#ethereum#bitcoin
57 notes
·
View notes
Text
fighting for my life to navigate a CUNY website to figure out how to ask more information about auditing classes as a non-student. and boy they do not make these websites easy do they this is making me feel SO technologically illiterate. what do you mean i have to download a fucking app. it's like the minotaur's labyrinth all up in here
27 notes
·
View notes
Text
Create Immersive AR Experiences for Your Business
Augmented reality is no longer just for gaming—it’s a game-changer for businesses. At Atcuality, we specialize in augmented reality development services to help brands offer immersive digital experiences. Our team designs AR applications for eCommerce, automotive, architecture, and more, enabling businesses to engage users in new and exciting ways. Imagine allowing customers to try on clothes virtually, explore 3D home designs, or interact with digital product demonstrations—all from their smartphones. With real-time AR interactions, businesses can provide value-driven experiences that increase conversions and customer satisfaction. Let us help you leverage AR to create interactive solutions tailored to your audience’s needs.
#ai applications#website development#augmented and virtual reality market#digital marketing#artificial intelligence#emailmarketing#augmented reality#web development#web design#information technology#website#wordpress development#software#website developer near me#website developer in india#website optimization#website design#wordpress#ssl#sslcertificate#ssl certificates#seo company#seo marketing#seo services#on page seo#off page seo#seo#social media marketing#on page optimization#on page audit
0 notes
Text
Masterlist of Free PDF Versions of Textbooks Used in Undergrad SNHU Courses in 2025 C-1 (Jan - Mar)
Literally NONE of the Accounting books are available on libgen, they all have isbns that start with the same numbers, so I think they're made for the school or something. The single Advertising course also didn't have a PDF available.
This list could also be helpful if you just want to learn stuff
NOTE: I only included textbooks that have access codes if it was stated that you won't need the access code ANYWAY
ATH (anthropology)
only one course has an available pdf ATH-205 - In The Beginning: An Introduction to Archaeology
BIO (Biology)
BIO-205 Publication Manual of the American Psychological Association Essentials of Human Anatomy & Physiology 13th Edition
NOTE: These are not the only textbook you need for this class, I couldn't get the other one
CHE (IDK what this is)
CHE-329
The Aging Networks: A Guide to Policy, Programs, and Services
Publication Manual Of The American Psychological Association
CHE-460
Health Communication: Strategies and Skills for a New Era
Publication Manual Of The American Psychological Association
CJ (Criminal Justice)
CJ-303
The Wisdom of Psychopaths: What Saints, Spies, and Serial Killers Can Teach Us About Success
Without Conscious: The Disturbing World of the Psychopaths Among Us
CJ-308
Cybercrime Investigations: a Comprehensive Resource for Everyone
CJ-315
Victimology and Victim Assistance: Advocacy, Intervention, and Restoration
CJ-331
Community and Problem-Oriented Policing: Effectively Addressing Crime and Disorder
CJ-350
Deception Counterdeception and Counterintelligence
NOTE: This is not the only textbook you need for this class, I couldn't find the other one
CJ-405Private Security Today
CJ-408
Strategic Security Management-A Risk Assessment Guide for Decision Makers, Second Edition
COM (Communications)
COM-230
Graphic Design Solutions
COM-325McGraw-Hill's Proofreading Handbook
NOTE: This is not the only book you need for this course, I couldn't find the other one
COM-329
Media Now: Understanding Media, Culture, and Technology
COM-330The Only Business Writing Book You’ll Ever Need
NOTE: This is not the only book you need for this course, I couldn't find the other one
CS (Computer Science)
CS-319Interaction Design
CYB (Cyber Security)
CYB-200Fundamentals of Information Systems Security
CYB-240
Internet and Web Application Security
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-260Legal and Privacy Issues in Information Security
CYB-310
Hands-On Ethical Hacking and Network Defense (MindTap Course List)
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-400
Auditing IT Infrastructures for Compliance
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-420CISSP Official Study Guide
DAT (IDK what this is, but I think it's computer stuff)
DAT-430
Dashboard book
ECO (Economics)
ECO-322
International Economics
ENG (English)
ENG-226 (I'm taking this class rn, highly recommend. The book is good for any writer)
The Bloomsbury Introduction to Creative Writing: Second Edition
ENG-328
Ordinary genius: a guide for the poet within
ENG-329 (I took this course last term. The book I couldn't find is really not necessary, and is in general a bad book. Very ablest. You will, however, need the book I did find, and I recommend it even for people not taking the class. Lots of good short stories.)
100 years of the best American short stories
ENG-341You can't make this stuff up : the complete guide to writing creative nonfiction--from memoir to literary journalism and everything in between
ENG-347
Save The Cat! The Last Book on Screenwriting You'll Ever Need
NOTE: This i snot the only book you need for this course, I couldn't find the other one
ENG-350
Linguistics for Everyone: An Introduction
ENG-351Tell It Slant: Creating, Refining, and Publishing Creative Nonfiction
ENG-359 Crafting Novels & Short Stories: Everything You Need to Know to Write Great Fiction
ENV (Environmental Science)
ENV-101
Essential Environment 6th Edition The Science Behind the Stories
ENV-220
Fieldwork Ready: An introductory Guide to Field Research for Agriculture, Environment, and Soil Scientists
NOTE: You will also need lab stuff
ENV-250
A Pocket Style Manual 9th Edition
ENV-319
The Environmental Case: Translating Values Into Policy
Salzman and Thompson's Environmental Law and Policy
FAS (Fine Arts)
FAS-235Adobe Photoshop Lightroom Classic Classroom in a Book (2023 Release)
FAS-342 History of Modern Art
ALRIGHTY I'm tired, I will probably add ore later though! Good luck!
23 notes
·
View notes
Text
Demystifying the World of Cyber Audits: A Comprehensive Guide
In our interconnected digital age, where data breaches and cyber threats loom large, the importance of cybersecurity has never been more pronounced. Companies of all sizes are grappling with the ever-present risk of cyberattacks, and the consequences of failing to protect sensitive information can be devastating. To combat these threats effectively, organizations turn to a vital tool in their cybersecurity arsenal: the cyber audit.
Do you know what exactly Cyber Audit is?
An organization's digital assets, information systems, policies, and practices are thoroughly and methodically examined as part of a cyber audit, also known as a cybersecurity audit, to determine its security posture. A cyber audit's main objective is to find areas of vulnerability and weakness that cybercriminals can exploit and to suggest countermeasures.

The Crucial Role of Cyber Audits:-
Risk assessment - Organizations can assess their exposure to cyber threats with the use of cyber audits. They give businesses the ability to pinpoint their most vulnerable points by detecting their weaknesses, vulnerabilities, and prospective threats.
Compliance - Strict regulatory obligations for data protection and cybersecurity apply to many businesses. Non-compliance can have serious financial costs as well as legal ramifications. Organizations can make sure they are adhering to these legal requirements with the aid of cyber audits.
Protection of Sensitive Data - Today's businesses rely significantly on data, thus protecting this data is essential. Cyber audits are essential for helping firms protect sensitive consumer and proprietary data by spotting any flaws that could result in data breaches.
Reputation Management - An organization's reputation might be damaged and stakeholders' trust can be lost as a result of a data breach. Cyber audits help an organization's reputation by demonstrating a commitment to security while also preventing breaches.

Conclusion -
In today's digital landscape, where cyber threats are constant and evolving, cyber audits are indispensable for safeguarding organizations against potential disasters. They offer a structured approach to identifying and addressing vulnerabilities, reducing risks, and ensuring compliance with regulations.
Remember that cybersecurity is not a one-time effort but an ongoing commitment to protecting your organization's assets and reputation. Regular cyber audits are a proactive and strategic approach to keeping your digital defences strong in the face of ever-evolving threats. In this digital age, where data is a valuable asset, investing in cyber audits is not just wise; it's imperative.
Be alert, be safe, and be proactive in your approach. Make a move in time to secure your information. The technology and networking professionals at MADMAN TECHNOLOGIES do manual and artificial intelligence-assisted cybersecurity audits on your platforms.
We offer solutions for risks to your data such as phishing, hacking, social engineering, ransomware, malware, viruses, and others. We provide you with individualized solutions, services, and goods and operate only on the principle of client pleasure. We pinpoint the weaknesses in any active dashboards and offer complete proficiency. In order to defend your devices, data, networks, hardware, and software from any cyber attacks, we are prepared and armed with the necessary tools, processes, techniques, and other practices.
For any further additional queries, you can easily connect with them —
Email- [email protected]
Contact info — 9625468776
#cybersecurity#cyber audit#cyber security audit#it services#information technology#technology#it products#itservices#it solutions#it technology
1 note
·
View note
Text

Welcome to The Simblr Office Directory
This blog is an archive of the submissions for the office-centric OC prompt posted by the light of Simblr, @kashisun.
Here you can browse all the amazing creations submitted by your fellow simblrs. Feel free to scroll to your delight or click one of the links under the cut to see who's on roster under (or over) a particular bureau or delegation.
Want to be added to the directory or confirm that you've been queued? Just include a link to your post in an ask off anon and it will be queued within 48 hours. Until we get through the backlog and can queue at a more leisurely pace, all ask submissions will receive a confirmation. You can always mention us, but we won't be able to provided confirmation for that method.
Leaving the company? If you'd like your post removed, just include a link to the post in an ask off anon and it will be removed. Sideblogs may require additional verification. Please allow, at most, 48 hours for the request to be honored. Removal requests will not be confirmed, only acted upon.
Every company's hierarchy is a little different. Designations for this directory are based on some of the companies I've worked for, but especially on the multi-media marketing company I work for now.
Bureaus and Their Delegations
Delegations with an * currently have low or no headcount (posted and queued). Excludes leadership.
Bureau of Client Engagement
Leadership
Billing*
Escalations*
Product Support*
Quality Assurance*
Sales*
Bureau of Compliance (Bureau-specific Internal Affairs and Auditing)
Leadership
Client Engagement*
Facilities*
Finance*
Human Resources*
Information and Technology*
Legal (General)
Legal (Leadership)
Marketing*
Bureau of Facilities
Leadership
Catering*
Environmental (Janitorial, HVAC, and Plumbing)*
Mechanical (Electrical, Elevators, Equipment Maintenance)*
Premise* (Grounds Maintenance and Real Estate)
Purchasing* (From pushpins to pallet jacks)
Security
Warehousing* (Shipping, Receiving, Mail room, and Inventory)
Bureau of Finance
Leadership
Accounting
Asset Management*
Investments*
Travel and Accommodations*
Vendor Relations*
Bureau of Human Resources
Leadership
Career Development (Internships and Internal Role Transitions)
Dependent Care*
Employee Activities Committee (Members are volunteers)
Employee Benefits*
Floating Delegates (Administration) (For profiles that list a nondescript secretary/admin/receptionist/assistant role)
Floating Delegates (General) (For profiles that do not list a position)
Floating Delegates (Leadership) (For profiles that list a nondescript managerial role)
Health Services*
Payroll*
Recruiting*
Training*
Union Relations*
Bureau of Information & Technology
Leadership
Data Security*
Infrastructure*
Public Relations
Research and Development*
Systems and Devices*
Telecommunications*
Bureau of Marketing
Leadership
Copy
Design
Planning and Implementation*
Board of Directors
Chief Officers
CEO - Chief Executive Officer/President
COO - Chief Operations Officer/Vice President
CCO - Chief Compliance Officer/Vice President
CFO - Chief Finance Officer/Vice President
CITO - Chief Information and Technology Officer/Vice President
CMO - Chief Marketing Officer/Vice President
Executive Administration* (Admins that report to chief officers)
206 notes
·
View notes
Text

Electronic Maintenance of Commercial Books Starts in Turkey
Electronic maintenance of commercial books unrelated to accounting of the business starts in Turkey. That is a sign of a new era in the field of Corporate Governance and Commercial in Turkey.
Table of Contents
Introduction
What is Corporate Governance?
Which Companies are Obligatory for Electronic Keeping of Books in Question?
What is meant by System User?
Conclusion
Introduction
The electronic maintenance of commercial books unrelated to accounting of the business has been officially introduced in Turkey. That is declared by the Communiqué in the Official Gazette dated 14 February 2025 and numbered 32813. The present article will analyze long term implications of the regulatory change upon Turkish markets. Turkish business lawyers should update their corporate governance consulting process because of new developments.
What is Corporate Governance?
Corporate governance encompasses rules, practices, and processes guiding proper management and oversight of a company. Corporate governance encompasses the rules, practices, and processes that guide a company’s management and oversight. Typically, a company’s board of directors holds the responsibility for these activities, which include organizing senior management, overseeing audits, and managing board and general assembly meetings according to both national and international standards.
Regarding more information about how the system operates for corporate governance consulting take a look at our practice area: Corporate Governance
Scope of Electronic Keeping of Commercial Books Companies are now permitted to maintain certain commercial books electronically, provided these books are unrelated to accounting records. Article 2 of the Communiqué designates the following books as eligible for electronic storage:
share ledger [pay defter in Turkish],
board of directors’ resolution book [yönetim kurulu karar defteri in Turkish],
board of managers’ resolution book [müdürler kurulu karar defteri in Turkish],
general assembly meeting book [genel kurul toplantı defteri in Turkish],
negotiation book [müzakere defteri in Turkish].
It means that the aforementioned books will be kept electronically under the new Communiqué by companies for and beyond 2025.
Which Companies are Obligatory for Electronic Keeping of Books in Question?
Those companies are obligated to electronic keeping of commercial books:
Companies whose incorporation is registered with the Trade Registry as of 1 January 2026
Bankings, financial leasing companies, factoring companies, consumer finance and card services companies, asset management companies, insurance companies, holding companies established as joint stock companies, companies operating foreign exchange kiosks, companies engaged in general retailing, agricultural products licensed warehousing companies, commodity specialization exchange companies, independent auditing companies, surveillance companies, technology development zone management companies, companies subject to the Capital Markets Law numbered 2499 and free zone founder and operator companies.
Companies not included in this mandatory list may voluntarily opt for electronic bookkeeping. However, those choosing to transition to electronic records must obtain a closing certification for their physical books from a local notary. In this case, all books shall be kept in an electronic environment. Companies wishing to voluntarily maintain their commercial books electronically should obtain a closing certification for their physical books before local notaries.
What is meant by System User?
System users play a critical role upon electronic keeping of commercial books. System users are defined by the company management or managing partner managing partners. Therefore a system user can be a member of the management body, one of managing partners or a third party.
Companies are obligated to scrutinize closely and regularly the System user’s transactions and take appropriate steps if necessary for any unintended consequences.
Conclusion
Having regard to the aforementioned considerations, keeping commercial books not related to the accounting of the business electronically is made obligatory for the companies listed above. In summary, the mandatory electronic keeping of specified commercial books marks a significant transformation in corporate governance and regulatory compliance in Turkey. This requirement applies to companies listed in the Communiqué, while others may voluntarily adopt electronic bookkeeping starting July 2, 2025. This regulatory shift is expected to enhance transparency, efficiency, and regulatory oversight, ultimately strengthening corporate governance frameworks in Turkey.
7 notes
·
View notes
Text
As someone who has worked with technology all my life, beginning with IBM courses in the 80's as a young business woman, I have a different - and much more frightening - perspective on the "Elon-gate" problem. This is beyond Watergate. This is High Crimes and Misdemeanors.
Aside from cutting payments authorized by Congress while having zero legal authority to do so, using staff who lack proper security clearance (Trump waving his hand is blessing is NOT valid now any more than his "thinking" Mar-A-Lago documents were now declassified made it so) and the privacy concerns as well as national security concerns all of these actions create...
Elon is thoroughly knowledgeable about data, and he hires people with exceptional skills in that arena.
That's a given.
WHAT is keeping him from randomly deleting data (just pieces), introducing random errors (pick some people, double the income on a tax return from last year and submit them for audit), changing a SSN number by one digit?
Things like this can easily be done through programming. Easy peasy.
Once a certain amount of errors exist, all of the data is suspect. That was the whole foundation of the fake "voter fraud/stolen election" move in 2020.
Musk's data people also have access to the information about where backups are stored by now. Nothing is safe.
Think about it - everything grinds to a halt.
The billionaires have their contingency plans in place.
America does not. Our Senate, House and legal representatives need to respond. This is the most criminal breach in history.
THIS is why I can't sleep at night. This is a coup. Trump and Elon and all their cronies are Traitors.
This is America's formerly secure money system. Our money.
It's my understanding the SS website is down today.
Republicans who voted for Trump need to pay attention.
@highlight Heather Cox Richardson
#USTreasury #SocialSecurity #elonmusk #securitybreach #HighCrimes #Treason #HighCrimesAndMisdemeanors #ImpeachTrump #Congress #House #SenateDemocrats #Senaterepublicans #SenateHearing #BarackObama #GeorgeBush #BillClinton #Tucson #Arizona #tech


#elon musk#traiter#coup#high crimes and misdemeanors#us treasury#social security#federal government#us government#hacking#breach#fraud#trump is a criminal#crime#impeach trump#white house#senate#congress
9 notes
·
View notes
Note
hey! i saw your posts defending generative ai with the amount it uses to train it. for the most part, i agree with your stance that genai isn't all that bad-- in fact, you've managed to change my stance about it.
but, there's still one issue i see with it, and that's with genai stealing images and text from people who don't want their art to be fed into ai systems. what's your stance on that?
I don't like it. I think it should be better regulated. But at the same time, like I've said... I don't have a clear solution either. We could maybe require companies to keep a complete record of training data for AI models made in the US and audit those to ensure they had permission to use them all.
I'm not sure how enforceable that would actually be though.
And even if companies based here did follow that rule, would companies in other countries? Would companies in EVERY country?
The oligarchs hate internet piracy. At least when it's corporations who are victims of it. But they've also been unable to stamp it out. The war on pirated movies, music and books has consistently been a losing one for them. And if the world's biggest corporations can't even stop internet piracy, then what chance does anyone have at stopping bots from collecting publicly available information to use as training data?
My position is what I would consider the realist one. That the technology is out there and it's only getting better with time.
That leaves two questions:
Is there something we can realistically do and fight for to combat it? Not just virtue signaling about how bad all AI is or encouraging boycotts that will at best be a speed bump but likely won't have much impact at all... but actual policy we can advocate for to protect the rights of artists? (And in a strong enough way that can't be signed away by agreeing to a website's TOS, because that just ensures social media companies get their paydays without protecting the artists themselves.)
If there isn't... Are there better things we should put our energy into than fighting a battle we can't win?
I guess my thing is that I'm hearing a lot of "generative AI is bad because it steals from artists," which I would agree with. But what I'm not seeing in all of this is SOLUTIONS. Things we can fight for at a policy level. Things that could make a real, tangible difference.
9 notes
·
View notes