#mobile RFID reader
Explore tagged Tumblr posts
Text
Revolutionising Inventory Control: The Unparalleled Efficiency of a Mobile RFID Reader
As technologies advance, companies that adopt the latest technologies have a clear edge. The mobile RFID reader is no longer a luxury but a requirement for companies that want to attain real-time visibility, operational efficiency, and better inventory management. Across warehousing and healthcare, manufacturing, and defence, RFID technology is transforming asset tracking on an unprecedented scale.
Purchasing a mobile RFID reader isn't simply about improving workflow—it's about future-proofing your company for the digital era. Whether you need to reduce errors, streamline processes, or improve security, implementing RFID technology will keep you one step ahead of the competition in a rapidly automating world.
0 notes
Text
On-The-Go Asset Tracking With Mobile RFID Reader Solutions.
Empower your workforce with mobile RFID reader technology. Effortlessly capture and update asset data on-site, enhancing accuracy and enabling real-time insights for smarter decision-making.

0 notes
Text

https://spintly.com/
Mobile Access control at your finger tips ! Our smartphone-based solution allows you to manage & unlock any door or gate
#access control solutions#access control system#visitor management system#smart phone access#BLE#RFID#rfid solutions#rfid technology#rfid reader#BLE MESH#access control market#mobile access#mobile app
0 notes
Text
Broken Beyond Bearing | Part 3
-.-. …. .. .-.. -.. .-. . -. / -.— —- ..- -. —. / .- … / - . -.
Part 1 found here | AO3
CW: A/B/O sexism I guess is what we should call this? Trauma reactions to doctors, awful in world politics.
Keeping his eyes on you Kyle’s concern rises with each shallow breath you suck between your teeth.
The nurse had been watching and held the door open as he directed Kyle to the first room on the right. Settling your body flat on the table he steps back, trying to give the nurse room to move. With two chairs, a small counter and a sink, and a ‘calming’ green on the walls the room looks exactly like he expects it to.
“How long ago was the exposure?” The nurse is taking your vitals and you stiffen as if your body hit rigor. “Ma’am if you don’t relax this is going to take longer.”
“Less than thirty minutes,” Kyle answers coolly.
The whine, primal and terrified, that comes from your throat as the blood pressure cuff is tightening has Kyle moving to where your head lays. Running the back of his knuckles down your cheeks he whispers to you. The scent of your fear, clear and uncontaminated with whatever afflicted you normally, flooded the room.
“Hey, hey. I’m here. You’re not alone. Everything will be okay.”
The nurse, an alpha by scent, makes a noise that pulls Kyle to look at him. The nurse, Johnson by the glance to his name tag, keeps his eyes on the monitor taking your blood pressure and pulse. Kyle focuses back on you. Your body regains mobility as the cuff is removed, eyes rolling like a horse looking for a place to run.
“Her vitals are all looking normal, the doctor will be in shortly,” Johnson shuts the door behind him. He must not be far enough away from the door when he starts talking to someone else. “Beta bitch in room one has track marks up both arms. I knew betas died from drugs more than any other gender but it’s wild to see that out here.”
Kyle would have stormed out the door to rip into the man if your hands hadn’t slapped into his, holding them tight. Pulling yourself upright from the reclined position you tuck your knees to your chest and rest your chin atop them. Letting go of his hands you curl them around your legs.
Sitting on a chair positioned next to the bed Kyle looks up at you, trying to catch your eyes.
Even when he could see the streaks of color through your irises no recognition lit your features. Concerned, Kyle stays sitting on the bed with you watching each breath and twitch. Nothing changes until the door opens with a faint knock.
“My name is Doctor Chen. Can you tell me what happened today?”
Like an automaton, you uncurl from your crunched position. Legs folded you straighten your back and rest your forearms on your knees palms aimed at the ceiling. Kyle had seen poses similar in meditation videos he would watch sometimes to give his mind a moment to relax. There is no peace in your pose. The width of your open eyes and the shallowness of your breath all remind him of victims he has saved from torture.
Memories that left their marks on his bones should not be reflected in your posture, he faced evil abroad and in the mirror to keep people like you safe.
He glanced at the man, dark hair, light blue scrubs, thick-rimmed glasses, and a white overcoat Kyle mostly associated with lab work. A quick draw of breath and Kyle marked him as an alpha. Dr. Chen did not look at you once, eyes staying firmly on him.
“We had an exposure to an allergen.”
Dr. Chen nodded once and sat on the small, wheeled stool that Kyle only ever saw in doctor’s offices. He wondered if they had to special order them or if they appeared in the building like fairies to offers of milk and bread. The man logged into his computer with a swipe of his name tag to an RFID reader and tapped a few buttons before turning to look at Kyle again.
“Do you know what the allergy was in reaction to?” He adjusts his glasses further up his nose.
“We don’t and would like to get some testing. Does this clinic do testing?” Kyle asked; all of his medical care happened on base.
Dr. Chen’s eyes glanced at you for the first time with a flare of his nose as he took in the fear salting the room with your uniquely beta scent. Kyle knew deeper than his marrow that you could turn off his brain and any explosive rage that he dealt with being an alpha. You didn’t use that now, but by the gods, he wished you would. The flash of disgust that whipped across Dr. Chen’s face ignited the soul-deep rage that existed with being an alpha.
“Dr. Chen,” the darkness, power, in Kyle’s voice brought the doctor’s face to him. “You will treat my wife with respect or I will ensure you don’t live to regret it.”
The cloying, nose-coating scent of Dr. Chen’s alpha rising to meet the challenge filled Kyle’s nose. He let the monster rise in his eyes, keeping his scent muted. Military training had to be good for something beyond the battlefield.
Kyle stands, placing his body between the doctor and the bed where you sit. Arms crossed and shoulders spread wide he used the mass of his bulk to show the barrier he could be. He didn’t know you, but Kate had seen something that prompted her to give them the care over you. You would not feel any harm if he could prevent it. You started to rock softly, eyes still unseeing. Then you begin to hum Edelweiss, effectively breaking the tension. Chen lost the staring match when he glanced at you.
“Do your job doctor, so I don’t have to.”
“That is out of line Mr—”
“Sergeant, special forces.”
Dr. Chen’s eyes narrowed but accepted the correction.
“Sergeant, your wife is doing fine by her visual inspection and her vitals agree. This clinic does not offer allergy testing but there are a few private practices here that you can call.” He turned back to his computer, typing in what Kyle assumed to be a summary of the visit today. “Most of what we do here for allergies is to stop the reaction and watch for any adverse effects.”
“I will need a copy of that report for our records,” Kyle stated it like a command he would give a private or a trainee. A firm ‘this is the course of action you will be taking’ that did not leave any room for questions or disobedience.
If Dr. Chen thought of arguing with Kyle, he kept it to himself. He left shortly after with a comment that Johnson would be in soon with the paperwork he requested. That is how Johnny found them, Kyle’s arms crossed and holding back his rage and you the juxtaposition of a peaceful body and an absent mind.
“You are more than you appear, wife,” Johnny took your hand, curling fingers around palms.
They wait in the cadence of your voice for nearly five minutes before Johnson appears, papers in hand. Kyle snaps a vice grip around the man’s wrist, pulling him close.
“Johnson. If I hear you telling tales about betas, and more specifically about my wife I will paint the walls of your room with colors not even crime techs will unsee.”
The man under his eyes paled quite impressively. Plucking the papers from his hand Kyle dropped Johnson’s hand and turned to his pack mate and partner in crime. Johnny’s thumb traced a track along the back of your hand as he watched the interaction play out before him.
“Can you carry her to the truck?”
Johnny’s eyes flicked as he watched the nurse flee from the room.
“Yeah. Up you pop bonnie,” he settled one arm over his shoulder and then the other before lifting you under the thighs to settle around his waist.
Still, you hummed, no life in your form. Kyle had a glare and a harsh, nose-blistering scent of rage for anyone who looked too long. Johnny settled in the back seat with you, buckling you into the middle so he could keep a hand on you and Kyle could check on you in the review mirror.
The drive home is tense, filled only with Kyle’s quiet mutterings about inexperienced winter drivers. When he turns onto the path home Johnny asks a question.
“What the hell happened in the clinic when I was on the phone with John?”
The steering wheel creaks under the pressure of Kyle’s hands.
“Nurse and doctor had some awful things to say about our wife, called her a drug addict, and couldn’t keep professional.”
“The hell? Why did they do that?” Johnny’s face in the rearview is tight with angry concern.
“It’s due to the beta laws that went into place ten…eleven? Yeah maybe eleven years ago.” Your voice is an unexpected addition to the conversation.
Kyle slows to a stop in the snow, throwing the truck in park and turning to look at you.
“What beta laws?”
He knows his gaze is harsh when you flinch back. Johnny wraps an arm around you and you settle a bit.
“There were laws on the books for a long time that weren’t really enforced,” you swallow and look from man to man before staring at your knees and continuing. “About how betas weren’t allowed the same personhood rights as alphas and omegas due to the lack of either consistent rut or heat. Apparently, the ability to do both is scary to the government. Several years back a group successfully passed a new law that said basically that betas should be treated like children, unable to sign paperwork without an approving authority, have bank accounts alone, apply for a credit card, or passport, you name it without the approval of an alpha or omega. In some places it went beyond that, stripping beta’s of all rights.”
Johnny muttered under his breath something that sounded like ‘What the fuck’ but Kyle kept his eyes on you.
“What happened to you?” His whisper hardens on your skin like ice.
There is no weak, scared beta woman here, only a beast that would peel him apart if he pushed. He didn’t scare her, but doctors did.
“No.”
Nodding once and accepting the answer Kyle turned back to driving. He would discuss this all with the guys after they had settled into bed. The interactions with the clinic staff were nothing like he had ever experienced before. Though as he thought of it he couldn’t remember the last time he had worked with a beta.
Simon and John step onto the porch as Kyle parks, as if they had been keeping watch for them.
The four men set about their tasks, hauling everything inside. You follow when Johnny reaches into the back seat and helps you out, hand tucked in his as he carries in a few bags. Simon sets about setting up the bed they picked for your room. Johnny settles you at the table, laughing and joking at you as he prepares a plate of food. Kyle and John set to work on creating the dresser. They don’t hear you laugh at any of Johnny’s stories but John points to you once and Kyle catches a glimpse of a smile. The sun slips away into the trees as each of the men finishes their task. Once the bed is made and the mattress settled on the frame John and Kyle lift the dresser into place.
The three men who had built things collapsed onto the couch facing the back wall of windows into the woods. Simon is settled between John and Kyle an arm dropped around each of them. You are standing on the back porch, head tilted back as you look at the ink-dark sky. The coat and boots you wear are those picked up today. Kyle didn’t think to wonder where Johnny had gone until he bounced down the steps with a bright bundle of fabric over one shoulder as he shoved a beanie on his head.
“Where ya going, Johnny?” Simon pitches his voice to carry but not to shout.
“Gonna give our wife a gift,” he winks at his lovers and pops out the back door.
Simon tightens the arm around Kyle.
“He loves you. That won’t change if he chooses to love someone new as well,” John murmured.
Kyle looked over at John who lay his head fully on Simon, nose buried in the scent gland at his neck. John licks the length of the gland causing Simon to let out a short whine.
Glancing back out to the back porch Kyle watches Johnny settle a shawl across your shoulders and sees in your profile confusion, hesitance. When you look down and clutch the shawl tight to your chest Kyle could only call the look on your face concerned acceptance. Johnny grinned at you like the sun had risen.
“To bed Simon, I can feel you grumble. Your rut starts soon. Let Johnny get our wife settled and let Kyle and I get you into bed.” John pushes up from the couch pulling Simon with him.
Kyle stands as well, eyes drifting to you and Johnny one last time. Standing side by side the two stare at the stars. John calls him from his observations and Kyle starts up the stairs after his lovers. His other lover will arrive with time.
Broken Masterlist | Masterlist
@lucienofthelakes @gg-trini @talia-the-gemini @thriving-n-jiving @z-wantstowrite @asialovesyou09 @literallegendicon @canthavetoomuchchaos @reinekoya @jsptmoche @demothers-empty-blog @hbaasaad
#cod#fanfiction#cod x reader#ghost x reader#simon riley x reader#john soap mactavish#soap cod#price x reader#john price x reader#soap mactavish#kyle gaz x reader#gaz x reader#gaz cod#kyle gaz garrick#gaz call of duty#poly 141#cod omegaverse#beta!reader#omega!john Price#alpha!simon#poly!141#tf 141 x reader#kyle garrick#johnny mactavish#simon riley
566 notes
·
View notes
Text
We do have both mobile devices with pin entry, and tap ones, but both are at least somewhat recent. And the ones that use the contact chip tend to get dirty/damaged (not sure of details), and don't work well, at which point you need to fall back on the magnetic stripe. The tap ones are even newer and thus rarer, but at least are more reliable than the contact ones. And places like NYC and SV are more likely to have newer ones, backwaters in the western interior are less likely. Also varies by type and age of business… I rarely went to bars even before the pandemic, so I have no clue what is common now. Last time I did go to a bar was probably over 5 years ago in Seattle, and they held onto your card… they might have had a Square tap reader though? Hard to recall.
Right Americans, I need an explanation. What on Earth are these kids doing wrong? Surely this is normal?
#I mean I am pretty sure I first saw tap readers over 10 years ago#But they still aren't super common#More common at newly started small cafés and such#Or at farmers markets where you need to be mobile#No one trusted tap readers at first#Even though they are more secure than mag strips#Definitely less secure than chip contact ones though#And should definitely have an RFID blocking wallet#And credit cards were almost as slow to roll out cards with RFID as places were to add readers#The chips they rolled out fast and pretty early#But for a long time no one had the contact readers
5K notes
·
View notes
Text
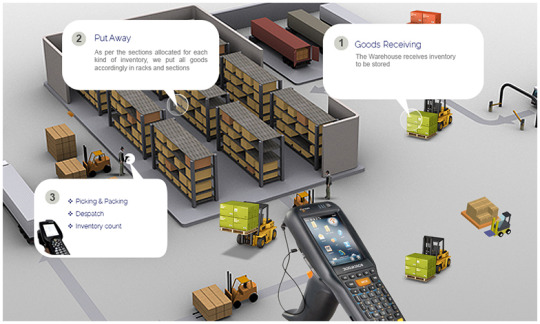
easyTRACK Warehouse Management System
An intelligent solution to control movement and storage of materials within a Warehouse.
A well-structured Warehouse Management system is important for the smooth and efficient operation of any warehouse, irrespective of the size or volume of material it handles. Most of the small and medium warehouses do not require an expensive WMS with redundant features. easyTRACK WMS is a perfect solution on the enterprise mobility for the warehouse management of small and medium enterprises which helps them manage all the essential warehouse functions. easyTRACK warehouse automation software allows the users in warehouse to manage the following operations at their palm.
Goods receiving
Put away
Picking & Palletizing
Dispatch
Stock count, etc.
easyTRACK WMS Lite Benefits
Solves the challenges faced in the conventional system.
Goods Receiving-
Priority Issue Multiple Shipments received at a time
Delayed Data entry Stock may be available but not available for Sale Dead /Damage/Short supply on arrival not instantly notified.
SOLUTION: GRN on PDT “goods receiving made easy with GRN on PDT”
Welcome to Technowave Group, your trusted provider of advanced technology solutions in Dubai. Our RFID Warehouse Inventory Management Systems can help businesses improve their inventory management and provide complete visibility into their warehouse operations.
What is RFID Warehouse Inventory Management System?
RFID Warehouse Inventory Management System uses RFID technology to automate the process of inventory tracking and management. It involves tagging inventory items with that contain unique identification numbers. The RFID tags are read by RFID readers, which transmit the data to a computer system that stores the information and provides real-time updates on the inventory’s location, movement, and status.
Key Features of our RFID Warehouse Inventory Management System
Our RFID Warehouse Inventory Management System comes with the following key features:
Real-time inventory tracking:
Our RFID system provides accurate and up-to-date information on inventory levels, locations, and movements in real-time. This means that businesses can quickly identify any discrepancies, such as missing or misplaced items, and take corrective action before they become bigger problems.
Inventory management:
Our RFID system automates the inventory management process, including item counting, reordering, and tracking. This means that businesses can easily monitor inventory levels and reorder products when they are running low. This helps prevent stockouts and ensures that products are always available for customers.
Asset tracking:
It can track and manage assets, including equipment, tools, and vehicles, helping businesses keep track of their assets’ location, status, and maintenance schedules. This allows businesses to optimize asset utilization and minimize downtime, which can result in significant cost savings.
Reporting and analytics:
The RFID system generates detailed reports on inventory and asset tracking, providing businesses with valuable insights into their warehouse operations. Businesses can use this information to identify areas for improvement and make informed decisions about inventory levels, order fulfillment, and asset management.
Improved accuracy and efficiency:
Our RFID system eliminates the need for manual inventory tracking, reducing the risk of errors and improving accuracy. This saves time and resources by automating inventory management and asset tracking, allowing businesses to focus on other critical tasks.
Improved visibility and control:
It provides real-time updates on inventory and asset movement, giving businesses complete visibility into their warehouse operations. This helps businesses make informed decisions and take corrective action quickly, leading to increased efficiency and productivity.
Improved customer satisfaction:
Our RFID system helps businesses improve their order fulfillment process, reducing stockouts and improving delivery times. This leads to increased customer satisfaction and repeat business, which can be a significant competitive advantage in today’s market.
Compliance with regulations:
Last but not least, our RFID system helps businesses comply with regulations related to inventory tracking and management. For example, our system can provide traceability requirements for food and pharmaceutical products, ensuring that businesses meet regulatory requirements and avoid costly penalties.
Overall, our RFID Warehouse Inventory Management System offers businesses a range of benefits, from increased efficiency and productivity to improved customer satisfaction and regulatory compliance.
Get in Touch With Us!
At Technowave Group, we have a team of experienced professionals who are dedicated to providing high-quality service and support to our clients. We work closely with our clients to understand their unique business needs and provide tailored solutions that help them achieve their goals.
Whether you are a small business or a large enterprise, we can help you leverage technology to improve your warehouse operations and achieve your goals. Contact us today to learn more about our RFID Warehouse Inventory Management System and other technology solutions.
3 notes
·
View notes
Text
Mobile Document Reader Market: Industry Overview and Analysis 2025–2032

MARKET INSIGHTS
The global Mobile Document Reader Market size was valued at US$ 623.4 million in 2024 and is projected to reach US$ 1.23 billion by 2032, at a CAGR of 8.8% during the forecast period 2025-2032.
Mobile document readers are portable devices or software applications designed to scan, authenticate, and process identity documents such as passports, driver’s licenses, and ID cards. These solutions incorporate advanced technologies including OCR (Optical Character Recognition), RFID (Radio Frequency Identification), and biometric verification to enhance security and streamline identity verification processes across multiple industries.
The market growth is driven by increasing security concerns, rising adoption of digital identity verification, and stringent government regulations for identity authentication. Key players such as Thales, IDEMIA, and Veridos (G&D) are expanding their product portfolios with AI-powered mobile readers capable of detecting sophisticated forgeries. The ID readers segment holds significant market share due to widespread deployment in border control and financial institutions.
MARKET DYNAMICS
MARKET DRIVERS
Rising Demand for Secure Identity Verification to Accelerate Market Growth
The global surge in identity fraud cases is driving substantial demand for mobile document readers. With identity theft incidents increasing by over 35% annually across key regions, organizations are prioritizing advanced verification solutions. Mobile document readers provide real-time authentication of IDs, passports, and other critical documents through NFC and OCR technologies, significantly reducing fraud risks. Governments worldwide are mandating stricter identity verification protocols, particularly in aviation and financial sectors, creating sustained demand.
Digital Transformation in Border Control Creating Significant Market Opportunities
Border control agencies are undergoing massive digital transformations, with over 65 countries implementing e-gate systems requiring mobile document verification. The global biometric passport adoption rate now exceeds 85%, creating compatible infrastructure for mobile reader deployment. Recent technological advancements enable handheld devices to authenticate document security features like holograms, microprinting, and RFID chips with over 99% accuracy. Several international airports have already deployed mobile document readers for faster passenger processing, reducing wait times by an average of 40%.
Expansion of Mobile Banking Services Driving Financial Sector Adoption
The financial sector’s rapid shift toward digital onboarding is creating substantial growth avenues. Over 70% of global banks now offer mobile account opening services requiring robust identity verification. Mobile document readers enable customers to remotely verify identities by scanning government-issued IDs while detecting fraudulent alterations. This technology has reduced customer acquisition costs by approximately 30% while improving compliance with KYC regulations. Major financial institutions are increasingly integrating these solutions into their mobile apps following successful pilot programs showing over 90% fraud detection accuracy rates.
MARKET RESTRAINTS
High Implementation Costs Limiting Small Enterprise Adoption
While larger organizations are rapidly adopting mobile document readers, smaller enterprises face significant cost barriers. Enterprise-grade solutions with advanced verification capabilities typically require substantial upfront investments ranging from $5,000 to $20,000 per unit. Additional expenses for system integration, staff training, and software updates further strain budgets. Many SMBs consequently rely on manual verification methods despite higher long-term operational costs, creating a substantial adoption gap in the market.
Data Privacy Concerns Creating Regulatory Hurdles
Growing data privacy regulations worldwide pose complex compliance challenges for mobile document reader providers. The processing and storage of sensitive biometric and identity data must comply with increasingly stringent regional regulations that continue evolving. Recent legislative changes have increased certification requirements by over 40% in key markets, delaying product launches. Some organizations hesitate to adopt these solutions due to potential liabilities associated with data breaches involving personally identifiable information.
Technical Limitations in Document Recognition Accuracy
Despite significant advancements, mobile document readers still face challenges with certain document types. Handled documents with wear and tear show approximately 15% higher rejection rates compared to pristine specimens. Recognition accuracy for non-Latin character documents remains below 90% for some manufacturers, creating difficulties in multicultural environments. These technical limitations require ongoing R&D investments to address, particularly as counterfeiters develop more sophisticated fraudulent documents that test detection capabilities.
MARKET OPPORTUNITIES
Emerging Smart City Infrastructure Creating New Use Cases
Global smart city initiatives present significant growth potential, with intelligent identity verification becoming integral to urban services. Pilot programs in several cities have successfully integrated mobile document readers with public transportation, healthcare access, and municipal services. These implementations have demonstrated efficiency improvements exceeding 30% in service delivery times while reducing identity fraud incidents by approximately 25%. As smart city investments are projected to grow significantly, demand for compatible mobile verification solutions will expand proportionally.
Advancements in AI Document Authentication Opening New Markets
Recent breakthroughs in artificial intelligence are enabling mobile document readers to analyze sophisticated security features previously undetectable by portable devices. New machine learning algorithms can authenticate documents by assessing over 200 security parameters with accuracy rates exceeding 98%. This technological leap is creating opportunities in high-security sectors like government facilities and critical infrastructure that previously required stationary verification equipment. Early adopters report reducing equipment costs by 60% while maintaining equivalent security standards.
Rental and Subscription Models Expanding Market Accessibility
Innovative business models are emerging to address cost barriers, particularly for intermittent users. Several leading providers now offer subscription-based services with pay-per-scan pricing starting under $1 per verification. This approach has shown particular success in the hospitality industry, where seasonal businesses need verification capabilities without substantial capital investments. Early data suggests these flexible models could expand the total addressable market by approximately 35% by making the technology accessible to smaller operators.
MARKET CHALLENGES
Increasing Document Standardization Complexity
The proliferation of new document formats and security features creates ongoing challenges for manufacturers. With over 70 countries implementing updated identity documents in the past five years, maintaining comprehensive verification databases requires continuous updates. Some jurisdictions issue multiple document versions simultaneously, while others incorporate unconventional security elements that standard readers struggle to authenticate. This variability forces manufacturers to dedicate approximately 25% of R&D budgets to ongoing database maintenance rather than innovation.
Intense Competition Driving Margin Pressures
The market’s rapid growth has attracted numerous competitors, including both established security firms and agile startups. This intense competition has reduced average selling prices by nearly 20% over three years while raising customer expectations for features and accuracy. Smaller players particularly struggle with profitability as they attempt to match the R&D capabilities of market leaders. The resulting consolidation trend has seen over 15 acquisitions in the sector during the past 24 months, reshaping the competitive landscape.
User Experience Expectations Outpacing Technology Development
End users increasingly demand seamless verification experiences comparable to consumer mobile applications, creating development challenges. Average acceptable verification times have decreased from 15 seconds to under 8 seconds in three years, requiring significant processing optimizations. Simultaneously, users expect flawless performance across diverse environmental conditions including low light and extreme angles. Meeting these expectations while maintaining security standards requires substantial engineering resources, with some manufacturers reporting development cycle increases exceeding 30%.
MOBILE DOCUMENT READER MARKET TRENDS
Rising Demand for Enhanced Security and Identity Verification to Drive Market Growth
The global Mobile Document Reader market is experiencing significant growth, driven by the increasing need for secure identity verification across industries. With a projected market value of $79.4 million by 2032, growing at a CAGR of 5.4%, advancements in document authentication technologies are playing a pivotal role. Mobile document readers are increasingly being adopted in sectors such as security, banking, and travel due to their ability to rapidly verify IDs, passports, and other critical documents with high accuracy. The integration of AI-based optical character recognition (OCR) and machine learning has further enhanced their capability to detect fraudulent documents efficiently. This trend is particularly strong in regions with stringent security regulations, where manual verification is being replaced by automated systems to reduce human error and processing time.
Other Trends
Expansion of Mobile Check-In and Digital Border Control
The rise of mobile check-in systems in airlines and digital border control solutions is further fueling the adoption of mobile document readers. Airlines and airports worldwide are deploying these devices to streamline passenger verification processes, reducing wait times and improving operational efficiency. For instance, biometric-enabled document readers are increasingly being used at immigration checkpoints to authenticate passports and visas within seconds. Similarly, hotels and travel agencies are leveraging these devices to enhance guest onboarding, ensuring compliance with anti-fraud regulations while delivering a seamless customer experience.
Growing Adoption in Financial Institutions
Banks and financial services are rapidly integrating mobile document readers into their Know Your Customer (KYC) and Anti-Money Laundering (AML) compliance workflows. With increasing regulatory scrutiny, financial institutions require reliable tools to verify customer identities and prevent fraudulent activities. Mobile document readers enable instant verification of government-issued IDs, reducing the risk of identity theft and improving compliance efficiency. Moreover, the shift toward digital banking has accelerated the demand for portable verification solutions that can be used both in-branch and remotely. Industry-leading players such as Thales and IDEMIA are developing advanced readers with NFC and RFID capabilities to cater to evolving banking needs.
COMPETITIVE LANDSCAPE
Key Industry Players
Technology Leaders Accelerate Innovation to Capture Market Share in Mobile ID Verification
The global mobile document reader market exhibits a moderately fragmented competitive landscape, with established technology providers competing alongside specialized solution developers. Thales Group emerges as a dominant player, leveraging its biometric and identity verification expertise across aviation, government, and financial sectors worldwide. In 2024, Thales maintained approximately 18% market share in mobile ID reader solutions, supported by strategic acquisitions in digital identity technologies.
IDEMIA and Veridos (G&D) have solidified their positions through advanced passport reading technologies, collectively accounting for nearly 25% of the professional-grade mobile document verification market. Their growth stems from increasing demand for next-generation border control solutions and mobile police applications, particularly in Europe and North America.
The competitive intensity continues to rise as mid-sized players like Access IS and Regula Baltija expand their product lines with AI-powered document authentication features. These companies have successfully penetrated the hospitality and banking verticals by offering cost-effective, compact readers with high accuracy rates exceeding 98.5% for passport verification.
Meanwhile, Chinese manufacturers including China-Vision and Wintone are rapidly gaining traction in APAC markets through competitive pricing and localized solutions. Their success demonstrates how regional players can challenge global leaders by addressing specific compliance requirements and integration needs in emerging economies.
List of Key Mobile Document Reader Providers
Thales Group (France)
IDEMIA (France)
Veridos (G&D) (Germany)
ARH Inc. (Hungary)
Access IS (UK)
Regula Baltija (Latvia)
China-Vision (China)
Prehkeytec (Germany)
DILETTA (Italy)
Grabba (Australia)
BioID Technologies (Germany)
Wintone (China)
Segment Analysis:
By Type
ID Readers Segment Leads the Market with Expanding Use in Identity Verification and Security Applications
The market is segmented based on type into:
ID Readers
Passport Readers
By Application
Airlines and Airports Segment Dominates Due to Increasing Passenger Screening Requirements
The market is segmented based on application into:
Airlines and Airports
Security and Government
Hotels and Travel Agencies
Banks
Train and Bus Terminals
Others
By End User
Government Sector Accounts for Significant Share Due to Border Control and Law Enforcement Requirements
The market is segmented based on end user into:
Government Agencies
Transportation Hubs
Financial Institutions
Hospitality Industry
Corporate Enterprises
Regional Analysis: Mobile Document Reader Market
North America The North American market for mobile document readers is strongly driven by heightened security concerns and stringent regulatory requirements across airports, border control, and financial institutions. The U.S., accounting for the largest market share in the region, has seen increased adoption due to biometric identification mandates and NFC-enabled ID verification technologies. Key players like Thales and IDEMIA dominate this space, offering advanced solutions with AI-powered fraud detection. The market is further propelled by investments in smart city initiatives, with an estimated 35% of U.S. law enforcement agencies now deploying mobile document readers for field operations.
Europe Europe’s market is characterized by strict GDPR compliance requirements and standardized electronic identity (eID) programs. The EU’s emphasis on interoperable digital identity frameworks has accelerated demand for passport readers and secure authentication devices. Germany and France lead in adoption, particularly in banking and transportation sectors. The region shows strong preference for multimodal verification systems combining document scanning with facial recognition, with airports investing heavily in contactless passenger processing solutions. Regulatory pressure to combat identity fraud remains a persistent market driver.
Asia-Pacific As the fastest-growing regional market, Asia-Pacific benefits from rapid digital transformation and massive government ID programs. China’s ‘Internet+’ strategy and India’s Aadhaar system have created enormous demand for mobile verification tools. While cost sensitivity remains a factor, vendors are adapting with rugged, affordable solutions for high-volume applications. The region shows particular strength in mobile payment verification and hotel check-in systems, with Japan and South Korea leading in technological sophistication. Emerging smart airports across Southeast Asia are driving next-gen adoption.
South America The South American market presents a mixed adoption landscape, with Brazil and Argentina showing the most progress in mobile document reader deployment. Financial institutions are primary adopters, implementing solutions for anti-money laundering compliance. Challenges include inconsistent regulatory frameworks and infrastructure limitations in rural areas. However, the growing tourism industry and need for improved border security are creating opportunities, particularly for portable passport verification systems at major entry points. Economic volatility continues to impact investment cycles in the region.
Middle East & Africa This emerging market is witnessing strategic deployments centered around major transportation hubs and financial centers. The UAE leads in adoption, particularly for airport security and hotel guest verification systems. Smart city initiatives in Saudi Arabia and digital transformation programs in South Africa are creating new demand vectors. While the market remains cost-conscious, there’s growing recognition of mobile readers as force multipliers for security personnel. Challenges include limited technical expertise in some areas and the need for solutions that can operate effectively in extreme environmental conditions.
Report Scope
This market research report provides a comprehensive analysis of the global and regional Mobile Document Reader markets, covering the forecast period 2024–2032. It offers detailed insights into market dynamics, technological advancements, competitive landscape, and key trends shaping the industry.
Key focus areas of the report include:
Market Size & Forecast: Historical data and future projections for revenue, unit shipments, and market value across major regions and segments. The Global Mobile Document Reader market was valued at USD 55.4 million in 2024 and is projected to reach USD 79.4 million by 2032, growing at a CAGR of 5.4%.
Segmentation Analysis: Detailed breakdown by product type (ID Readers, Passport Readers) and application (Airlines, Security, Hospitality, Banking, etc.) to identify high-growth segments.
Regional Outlook: Insights into market performance across North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa, with country-level analysis of key markets.
Competitive Landscape: Profiles of leading players including Thales, IDEMIA, Regula Baltija, and others, covering their market share, product portfolios, and strategic initiatives.
Technology Trends & Innovation: Analysis of OCR advancements, biometric integration, AI-powered verification, and mobile scanning technologies.
Market Drivers & Restraints: Evaluation of security concerns, regulatory compliance needs, and digital transformation trends versus cost sensitivity.
Stakeholder Analysis: Strategic insights for hardware providers, software developers, system integrators, and end-user industries.
Related Reports:https://semiconductorblogs21.blogspot.com/2025/06/inductive-proximity-switches-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/cellular-iot-module-chipset-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/sine-wave-inverter-market-shifts-in.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/pilot-air-control-valves-market-cost.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/video-multiplexer-market-role-in.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/semiconductor-packaging-capillary.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/screw-in-circuit-board-connector-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/wafer-carrier-tray-market-integration.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/digital-display-potentiometer-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/glass-encapsulated-ntc-thermistor.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/shafted-hall-effect-sensors-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/point-of-load-power-chip-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/x-ray-grating-market-key-players-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/picmg-single-board-computer-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/lighting-control-dimming-panel-market.html
0 notes
Text
What is a Real-Time Locating System (RTLS) and How Does It Work?

Introduction to Real-Time Location Systems (RTLS) in 2025 by AIDC Technologies
In 2025, Real-Time Location Systems (RTLS) are transforming how businesses track and manage their assets, personnel, and inventory. These systems provide live data on the location of items, helping companies save time, reduce losses, and improve operational efficiency. AIDC Technologies India is at the forefront of offering advanced RTLS solutions combined with robust rfid system technology to deliver smarter, faster, and more reliable tracking.
What Is RTLS? AIDC Technologies Simplifies the Definition
A Real-Time Location System (RTLS) is a technology used to automatically identify and track the location of objects or people in real time within a defined area. The core of many RTLS solutions is the rfid system, which uses radio waves to detect and track tags attached to items. AIDC India explains that RTLS can use several technologies, but RFID is among the most popular due to its accuracy and ease of integration.
How RTLS Works: Technology and Methods Explained by AIDC
RTLS operates by attaching tags or badges to objects or people. These tags emit radio signals picked up by readers or sensors installed around the premises. The data collected is processed by software to provide real-time location information. The rfid system is essential in this process, as it enables wireless communication between tags and readers, allowing seamless tracking. AIDC Technologies ensures that its RTLS solutions use the latest RFID standards for maximum reliability and coverage.
Key Benefits of RTLS for Businesses in 2025
The integration of an rfid system within RTLS offers many benefits. Businesses can quickly locate assets, reduce theft, and monitor employee movements to optimize workflow. RTLS also improves safety by tracking people in hazardous environments. AIDC Technologies India’s RTLS solutions help companies cut operational costs, reduce downtime, and increase productivity by providing precise location data instantly.
Top Industries Using RTLS Solutions from AIDC Technologies
RTLS powered by an rfid system is widely used across multiple sectors. In healthcare, hospitals track medical equipment and patients to enhance care. Manufacturing plants use RTLS to monitor tools and work-in-progress items. Logistics companies improve inventory management and shipping accuracy. Retailers prevent loss and improve stock visibility. AIDC India customizes its RTLS and RFID solutions to fit the specific needs of each industry.
Challenges in RTLS Implementation and How AIDC Overcomes Them
Deploying an RTLS with an rfid system can be complex due to factors like signal interference, infrastructure needs, and data management. AIDC Technologies India tackles these challenges by conducting thorough site surveys, designing tailored systems, and providing ongoing support. Their experts ensure seamless integration and minimal disruption to existing operations, helping clients maximize the return on their RTLS investment.
Integration of RTLS with Other Business Systems
For true operational efficiency, RTLS solutions by AIDC Technologies integrate smoothly with ERP, warehouse management, and security systems. The rfid system data feeds into these platforms to provide a unified view of asset location, status, and movement. This integration helps managers make informed decisions, automate processes, and ensure compliance with safety and quality standards.
AIDC Technologies’ Customized RTLS Solutions for Your Business
Every business has unique requirements. AIDC India offers customized RTLS solutions based on the company’s size, environment, and goals. Their advanced rfid system technology can be adapted for indoor and outdoor use, fixed or mobile tracking, and various tag types. AIDC’s team works closely with clients to design, implement, and maintain systems that fit perfectly and grow with the business.
Case Studies: Successful RTLS Deployments by AIDC Technologies
Several clients across India have benefited from AIDC’s RTLS combined with an rfid system. Hospitals have reduced equipment loss by 40%, manufacturing plants have improved production tracking, and logistics firms have enhanced shipment accuracy. These success stories highlight how AIDC’s technology and expertise create real value, making RTLS an essential tool for modern businesses.
Get Started with Smarter Tracking: Contact AIDC Technologies Today
If you want to leverage the power of RTLS and an rfid system to improve your business operations, AIDC Technologies India is your trusted partner. Their experts offer consultations, system design, installation, and ongoing support to ensure a smooth transition to smarter tracking. Book your consultation today and take the first step toward transforming how you manage your assets and people with cutting-edge RTLS solutions.
Ready to enhance your tracking with advanced RTLS and RFID systems? Book Now with AIDC Technologies India and secure smart, reliable solutions tailored to your business needs.
#WhatIsRTLS#RTLSforSmartTracking#RealTimeLocationSystem#RTLS2025Tech#RTLSWorkingExplained#AIDCTrackingSolutions
0 notes
Text
New ESD anti-static solution for NFC equipment interface
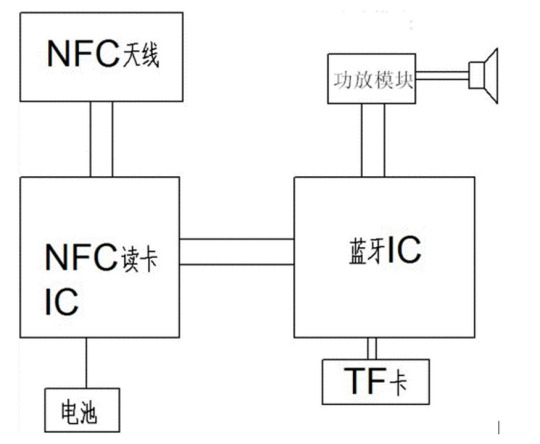
1、 What is an NFC device
NFC (Near-field communication) equipment is a wireless communication technology, which can realize short-range wireless communication and data exchange. It is based on Radio Frequency Identification (RFID) technology and Internet technology, using radio waves to transmit information between devices.
NFC devices usually consist of two parts: one is a reader/writer, used to read and write information on NFC tags or devices; The other is an NFC tag or device used to store and transmit information. For example, a mobile phone can serve as an NFC reader/writer, and an NFC label can be a regular piece of paper with information written on it, which can be read and written by the phone.
NFC technology has a wide range of applications in daily life, such as mobile payments, public transportation, smart homes, ticketing services, etc. Users can use NFC devices to pay for goods or services, enter public transportation or cultural venues, control household appliances, obtain ticketing information, and more. At the same time, NFC technology also provides more business opportunities for enterprises, such as promotional activities, providing customer service, and so on.
In short, NFC devices are a convenient and fast wireless communication technology that can provide users with a more convenient life experience and provide enterprises with more business opportunities.
2、 Necessity of NFC equipment anti-static
Anti static of Near-field communication equipment interface is very important, because static may have a negative impact on equipment performance, or even lead to equipment damage. In NFC device interfaces, charges may accumulate on the metal components of the device and generate an electric field around the interface. If static electricity is not properly handled, it may cause damage to the equipment.
3、 NFC equipment interface anti-static scheme
The following are some common methods to prevent static electricity from affecting NFC device interfaces:
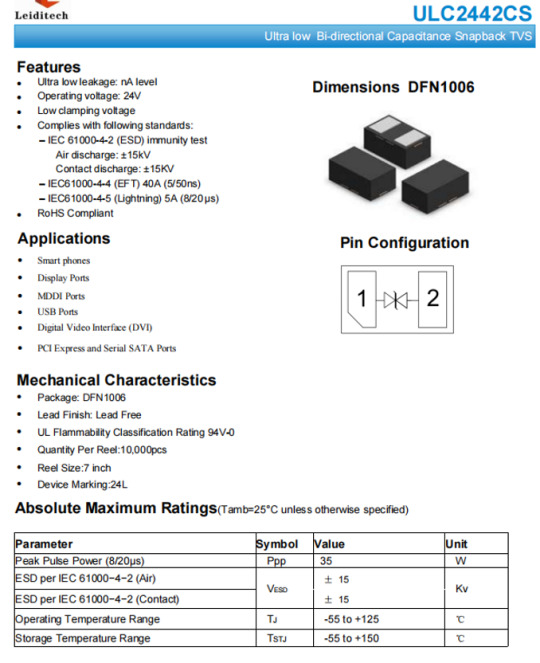
Use metal shielding covers, use static eliminators, and use interface anti-static devices. At present, using anti-static devices ESD is the most effective and cost-effective solution. It is necessary to provide anti-static protection devices above 18V. Shanghai Leiditech has provided a board level design solution for the following series of devices.
NXPNTAG21 series
NXP MIFARE Classic Series
NXP MIFARE DESFire series
NXP MIFARE UItralight series
Sony FeliCa column
STMicroelectronics ST25 column
Infineon SLE column
Broadcom BCM2079x Series
Samsung TecTiles column
AMSAS395x series
If you’d like to learn more or have any questions, don’t hesitate to reach out: 📧 [[email protected]] 🌐 Visit us at [en.leiditech.com]
0 notes
Text
Revolutionizing Education: The Power of a Classroom Attendance System
In the fast-evolving world of education, technology continues to redefine how teachers manage classrooms, students engage with learning, and administrators track performance. One such innovation making waves in schools, colleges, and universities is the Classroom Attendance System. Gone are the days of roll calls and paper registers — digital attendance systems offer accuracy, efficiency, and deeper insights into student behavior and performance.
In this blog post, we’ll explore what a classroom attendance system is, how it works, its key benefits, and why your institution should consider implementing one today.
What is a Classroom Attendance System?
A Classroom Attendance System is a digital tool designed to automate and streamline the process of tracking student attendance. It replaces traditional methods with smart solutions such as biometric scanners, QR code readers, RFID systems, mobile apps, or facial recognition technology.
These systems can be standalone or integrated into broader Learning Management Systems (LMS) or School Management Systems (SMS), providing real-time data and analytics to teachers, administrators, and even parents.
How Does a Classroom Attendance System Work?
While various systems offer different features, the core functionality of a classroom attendance system typically includes:
Student Identification: Through ID cards, biometric inputs, QR codes, or facial recognition.
Automated Tracking: The system automatically logs the presence or absence of students as they enter the classroom.
Real-Time Updates: Attendance data is instantly updated in the system, accessible to authorized users.
Reports and Analytics: Detailed attendance records, patterns, and statistics are generated for performance reviews.
Cloud-based systems also offer mobile and web applications that allow remote access and real-time tracking.
Benefits of a Classroom Attendance System
Implementing an automated classroom attendance system offers numerous advantages for students, teachers, and school administrators:
1. Increased Accuracy and Accountability
Manual attendance is prone to errors, manipulation, and time delays. An automated system ensures that data is recorded accurately and can’t be falsified, promoting greater accountability among students.
2. Time Efficiency
Teachers save significant class time by avoiding manual roll calls. This time can be redirected towards more meaningful teaching activities, increasing overall classroom productivity.
3. Real-Time Insights
Administrators gain real-time access to attendance records, enabling quick identification of trends such as frequent absences or late arrivals. Early intervention can be made to support at-risk students.
4. Parental Engagement
Some systems allow parents to receive instant notifications when their child is marked absent or late. This helps keep them informed and involved in their child’s academic life.
5. Data-Driven Decisions
With detailed attendance analytics, institutions can correlate student attendance with academic performance and engagement. This data helps in making strategic decisions around curriculum design, counseling, and disciplinary actions.
6. Enhanced Security
Systems that use biometrics or facial recognition prevent proxy attendance and impersonation, enhancing the overall integrity of attendance records.
Types of Classroom Attendance Systems
There are several types of attendance systems suited for different institutional needs:
Biometric Attendance Systems: Use fingerprint or facial recognition to verify student presence.
RFID-Based Systems: Students carry RFID cards that are scanned upon entry.
QR Code Systems: QR codes are scanned using a mobile device or scanner.
Mobile App-Based Systems: Students or teachers mark attendance using a mobile application.
Web-Based Systems: Cloud-based solutions accessible from any device with an internet connection.
Each type has its pros and cons, and institutions should choose based on budget, infrastructure, and scalability.
Why Schools and Colleges Should Adopt Digital Attendance Systems
In today’s data-driven educational landscape, manual processes are quickly becoming outdated. A digital classroom attendance system not only improves accuracy and saves time but also contributes to a more organized, transparent, and student-focused learning environment.
Moreover, these systems support hybrid and online learning environments, where tracking attendance becomes more challenging without digital tools.
Final Thoughts
The Classroom Attendance System is no longer a futuristic concept — it’s a present-day necessity for modern educational institutions. With benefits ranging from operational efficiency to improved student engagement, implementing a robust digital attendance system is an investment in both academic success and institutional growth.
0 notes
Text
Revolutionising Inventory Control: The Unparalleled Efficiency of a Mobile RFID Reader
The Potential of a Mobile RFID Reader
In a world of hyper-efficiency, companies cannot waste time on slow, inaccurate inventory management systems. That's where the mobile RFID reader comes in, an industry-altering device that has the potential to transform the way businesses monitor assets, optimise supply chains, and improve operational precision. Mobile RFID readers differ from standard barcode scanners as they don't require line-of-sight scanning, allowing fast data capture even in dense environments. Whether managing inventory in vast warehouses or tracking high-value equipment in the field, the mobile RFID reader is becoming an indispensable tool across industries.
This article delves into the unparalleled advantages of mobile RFID readers, the industries leveraging this cutting-edge technology, and key considerations for adopting the right system for your business.
Beyond Barcodes: Why a Mobile RFID Reader is a Game Changer
1. Speed and Efficiency Like Never Before
Traditional barcode scanning involves scanning each item physically—a painstaking process when dealing with thousands of SKUs. However, a mobile RFID reader can read multiple tags simultaneously, significantly processing time. Consider a warehouse staff scanning a whole pallet of items in seconds rather than minutes. That's the time-saving boost RFID technology provides.
2. Accuracy That Redefines Inventory Management
Problems in inventory tracking result in lost stock, shipment errors, and lost sales. Using a handheld RFID reader, the accuracy of the data goes through the roof with manual input excluded and automated scan keeping the records updated in real-time. The accuracy is gold in businesses where mishandling can cost fortunes, such as in pharma or aeronautics.
3. Long-Range and Bulk Scanning Capability
Unlike barcode scanners that require close-range scanning, RFID technology enables workers to capture data from several meters away. A mobile RFID reader can scan entire warehouse sections without requiring direct visibility, ensuring seamless asset tracking without disrupting operations.
4. Enhanced Security and Loss Prevention
Theft and lost stock cost companies billions every year. RFID tracking can instantly inform organisations when any unauthorised movement is detected, thereby minimising shrinkage and enhancing overall security. A mobile RFID reader provides real-time notifications as assets are moved, helping companies have better control over resources.
Industries Served by Mobile RFID Readers
1. Warehousing & Logistics: Optimizing Supply Chains
Warehouses are implementing mobile RFID readers to speed up inventory audits, streamline stock rotation, and automate reordering. RFID technology removes human error in monitoring incoming and outgoing shipments, cutting inefficiency from global supply chains.
2. Healthcare: Ensuring Patient Safety & Compliance
Hospitals and drug manufacturers use RFID readers to monitor medical supplies, equipment, and patient records. A portable RFID reader increases compliance with regulations, avoids the dispensing of expired drugs, and maintains critical equipment at hand when required.
3. Retail: Transforming Checkout & Inventory Management
RFID is being used by retailers to streamline inventory replenishment, lower checkout times, and improve customer experiences. Consider entering a store, grabbing goods, and exiting while an RFID system makes the payment for you. The mobile RFID reader is a stepping stone to a future without cashiers.
4. Manufacturing: Real-Time Tracking of Production Processes
Manufacturers use RFID to track raw materials, work-in-progress goods, and finished goods in real-time. An RFID reader on the mobile device provides real-time visibility into supply chains to avoid production delays and save operational waste.
5. Aviation & Defense: Location of High-Value Equipment
In asset-critical industries, RFID is essential. Air carriers and military contractors use wireless RFID readers to monitor everything from aircraft parts to military equipment for compliance, security, and better operations.
Picking the right mobile RFID reader for your enterprise
1. Think about scanning range requirements
Some companies need short-range RFID solutions, while others need long-read ranges of meters. Decide if your operations call for a mobile RFID reader with UHF (Ultra High Frequency) capability for far-distance scanning.
2. Evaluate Compatibility with Existing Systems
Acquiring an RFID reader should not result in the need to rebuild your entire IT infrastructure. Ensure your mobile RFID reader integrates well with your enterprise resource planning (ERP) or warehouse management systems (WMS).
3. Assess Battery Life and Portability
As mobility is paramount, choose a portable RFID reader with extended battery life and ergonomic design. Field service and warehousing teams need lightweight, rugged devices that withstand harsh work conditions.
4. Security and Data Encryption Features
As security concerns over data increase, opt for an RFID reader with effective encryption and authentication measures. Compromised RFID would mean the vulnerability of sensitive corporate data, rendering security an essential non-negotiable aspect.
5. IoT and AI Convergence for Future-Proofing
Top enterprises are converging RFID technology with IoT and AI. An RFID reader on the go linked with AI-based analytics can offer forecasted insights, automate decisions, and streamline operations workflows.
Challenges and Considerations in RFID Implementation
1. Upfront Expenses and ROI Calculation
Initial investment in readers, tags, and infrastructure is needed to implement RFID technology. However, long-term gains in efficiency, lower labour, and increased accuracy make the cost worthwhile.
2. Signal Interference in Special Environments
Substances like metal or liquid may impact RFID operation. Companies with high signal interference environments should conduct real-world tests on mobile RFID readers before large-scale deployment.
3. Regulatory Standards Compliance
Varying RFID regulations exist across different industries and regions. Make sure your mobile RFID reader meets compliance standards to prevent legal issues.
Conclusion: The Future of Asset Management with Mobile RFID Readers
As technologies advance, companies that adopt the latest technologies have a clear edge. The mobile RFID reader is no longer a luxury but a requirement for companies that want to attain real-time visibility, operational efficiency, and better inventory management. Across warehousing and healthcare, manufacturing, and defence, RFID technology is transforming asset tracking on an unprecedented scale.
Purchasing a mobile RFID reader isn't simply about improving workflow—it's about future-proofing your company for the digital era. Whether you need to reduce errors, streamline processes, or improve security, implementing RFID technology will keep you one step ahead of the competition in a rapidly automating world.
0 notes
Text
Access Control Systems Explained: Key Components, Working, and Benefits
In an age where data, assets, and human resources must be protected more than ever, the demand for advanced access control systems is on the rise. These systems are no longer just about keeping doors locked - they have evolved into comprehensive, smart technologies that secure buildings, manage entry permissions, and provide detailed access analytics.
This blog explores what access control systems are, their key components, how they work, and the core benefits they offer to modern organizations. It also discusses how companies are moving toward next-generation cloud and mobile-enabled platforms like those offered by innovative providers such as Spintly - to enhance workplace security while maintaining convenience and scalability.

What Are Access Control Systems?
At their core, access control systems are security solutions designed to restrict or grant access to physical or digital environments based on predefined rules. These systems determine who can access a certain location, when they can access it, and under what conditions.
While traditionally associated with physical spaces like offices and server rooms, today’s systems extend their functionality to include data centers, multi-tenant properties, co-working hubs, and even cloud applications.
Key Components of Access Control Systems
To understand how access control works, it's helpful to break down the essential components that make up a typical system:
1. Access Credentials
These are the methods users employ to prove their identity. Credentials can be:
RFID cards or key fobs
PIN codes
Mobile-based access (Bluetooth or NFC)
Biometric identifiers (fingerprint, facial recognition, etc.)
Mobile and biometric credentials are increasingly popular due to their security and contactless nature.
2. Access Control Readers
These devices authenticate the credentials. Readers can range from simple RFID scanners to advanced biometric readers. In smart buildings, mobile-based readers are gaining traction due to ease of use and hygiene.
3. Access Control Panel (Controller)
This is the system’s “brain,” making decisions based on the information received from readers. The controller processes data and instructs the system whether to unlock or keep the door locked.
4. Locks and Barriers
These are the physical components (like electric locks, turnstiles, or barriers) that respond to the controller’s command.
5. Software Interface
A centralized platform where administrators define access policies, manage users, monitor entry logs, and generate reports. Modern systems offer cloud-based interfaces accessible from any location—something companies like Spintly specialize in.
How Do Access Control Systems Work?
The operation of an access control system follows a straightforward flow:
User presents credential (mobile app, card, or biometric)
Reader scans credential and sends data to the controller
Controller verifies access rights
Access is granted or denied based on the policy
System logs the attempt for auditing purposes
This entire process takes less than a second and can be configured to notify security teams, track anomalies, or even trigger other systems like CCTV or alarms.
Types of Access Control Models
Different environments require different access models. Common types include:
1. Discretionary Access Control (DAC)
The owner decides who has access to what. It's flexible but can lead to inconsistent policies.
2. Mandatory Access Control (MAC)
Permissions are strictly enforced by a central authority. Common in government and military applications.
3. Role-Based Access Control (RBAC)
Access is granted based on roles within the organization—ideal for businesses of all sizes.
4. Attribute-Based Access Control (ABAC)
Grants access based on user attributes (e.g., department, time of day, location).
Benefits of Modern Access Control Systems
1. Enhanced Security
By ensuring that only authorized individuals can enter certain areas, access control systems reduce the risk of unauthorized entry, theft, and other threats.
2. Real-Time Monitoring
Admin dashboards provide real-time logs of who accessed what and when, which can be crucial during security audits or incident investigations.
3. Reduced Administrative Burden
Systems that integrate with HRMS and directory services eliminate the need for manual provisioning and revocation of access.
4. Scalability
Whether managing one site or multiple, cloud-based access control systems allow centralized control from anywhere.
5. Visitor Management Integration
Many businesses are now combining visitor and employee access into a unified system—simplifying the onboarding of guests and contractors while maintaining high security.
6. Hygiene and Touchless Convenience
Post-pandemic, the push for touchless entry is stronger than ever. Solutions that support mobile or facial recognition credentials meet this demand effectively.
Why Cloud and Mobile Are the Future of Access Control
Legacy access control systems were often tied to on-premise servers and required significant hardware investment. Today’s smarter alternatives like Spintly’s cloud-based access control systems are revolutionizing the landscape.
These systems eliminate the need for local servers, reduce IT costs, and provide seamless updates. They are also mobile-first, allowing users to unlock doors using their smartphones a feature highly appreciated in co-working spaces, modern offices, and apartment complexes.
Some key advantages of cloud-based solutions include:
Faster setup and deployment
Automatic software updates
Remote management and troubleshooting
API integrations with third-party software like visitor management and analytics
Subscription-based pricing models for easier budgeting
Use Case: A Multi-Tenant Building with Diverse Needs
Imagine managing access for a commercial building housing multiple businesses, each with different schedules, employee roles, and visitor policies. Traditional systems would require individual control panels and physical oversight.
A cloud-based, mobile-enabled system, however, allows centralized management with customizable policies per tenant. Real-time monitoring ensures visibility across all entrances, while the system integrates smoothly with elevators, parking garages, and emergency exits.
Providers like Spintly specialize in solving such multi-layered access scenarios, delivering both flexibility and control.
Conclusion
Access control systems have grown from simple locks and keys to intelligent platforms that blend security, convenience, and efficiency. As businesses strive for digital transformation, having a secure, scalable, and user-friendly system is not just a luxury - it's a necessity.
While choosing the right system depends on your organization’s needs, those looking for future-ready solutions are increasingly moving toward cloud-based, mobile-first access control systems. Solutions from companies like Spintly are empowering organizations across industries to manage access effortlessly, gain real-time insights, and scale with confidence.
The future of workplace security isn’t just about keeping intruders out - it’s about creating seamless, intelligent, and secure environments for everyone inside.
#access control solutions#mobile access#accesscontrol#access control system#spintly#biometrics#smartacess#visitor management system#smartbuilding
0 notes
Text
Boom Barriers Manufacturers in Chennai - automaticgatemanufacturers
Boom Barriers Manufacturers In Chennai, Providing Security and Traffic Management
As the urban areas of Chennai continue to develop rapidly, it is important to ensure the safe and efficient movement of vehicles on public and private premises. One of the most effective means of access control and traffic management that has emerged over the last several years is the boom barrier. An effective, simple tool for access control and traffic management, boom barriers have increased in popularity over the years. This boom barrier trend has created a strong manufacturing industry in Chennai that is specialized in manufacturing high-quality and reliable boom barrier systems.

What Are Boom Barriers?
Boom barriers, also referred to as boom gates or automatic gates, are horizontal bars or poles which pivot to obstruct vehicles from entering the premises. Boom barriers are regularly found on entry and exit points of parking lots, toll booths, residential communities, industrial premises, and commercial precincts where they serve as a primary means of restricting vehicle movement.
Boom barriers are either manual, semi-automatic or fully automated, depending on the case. Most new boom barriers in Chennai are equipped with one or more advanced technology features including RFID readers, license plate identification, ANPR (automatic number plate recognition) and remote access control.
Increasing Demand for Boom Barriers in Chennai
Chennai is one of the major metro cities in India, and it has a high level of daily vehicle activity. This, in combination with the growing number of gated communities, industry locations, commercial assets, and the need for security and traffic access, have created significant demand for boom barriers. Boom barriers are useful for:
Controlling traffic in high-density areas like toll plazas and parking lots,
Increasing security in sensitive locations such as governmental offices, airports, and private offices.
Controlling access to residential societies and blocking unauthorized vehicle access,
Integrating better automation of parking management systems, or, decreasing human intervention.

Attributes of Manufacturers in Chennai
Boom Barrier manufacturers in Chennai are widely supported to satisfy various needs, and can provide cost effective, reliable, and versatile barriers across a variety of industries. Some of the more common attributes of boom barriers built in Chennai are:
Heavy Duty: Most barriers are typically made with high-quality and high-grade materials. Many companies use hot dip galvanized steel or aluminum type materials which are good for durability and can withstand a lot of environmental elements.
Speed: Most boom barriers come with fast motors and controls as needed for effective high traffic events.
Connectivity with Security Systems: Boom barriers can be associated with, CCTVs, biometric systems, RFID scanners, and smart cards for a complete security solution.
Remote Control and Automation: Many barollow are able to be operated remotely either through a central control room, or in some instances, mobile applications.
Safety Sensors: Safety is paramount, boom barriers are matched with safety features like photocell sensors and an obstacle device so it does not hit any objects.
Technology Occurring Ahead
The boom barrier industry in Chennai has moved rapidly, becoming modern and intelligent. Manufacturers have been putting huge amounts of time and money into R&D to provide smarter, more efficient systems. Some innovations that are radically changing the way these systems work are IoT, solar power, and cloud access control. Smart boom barriers allow users to have real-time data analytics, predictive maintenance notifications, and complete integration with a building management control system (BMS). Smart boom barriers are the most suitable product for modern infrastructure.
Key Considerations Prior To Purchasing
If you are considering installing a boom barrier system in Chennai there are a few major points to consider:
Purpose of Installation - Do you need a boom barrier for residential, commercial or industrial application?
Frequency of Usage - If it is a high-volume use area then it will require a faster response time and provide longer lifespan.
Power Source - Make a decision on using electric, solar or hybrid systems to suit your location and surroundings.
Level of Automation - You have the option of a simple manual barrier to a fully automated, IoT enabled device.
After Sales Support - Make sure the manufacturer has good support in terms of installation, support, parts availability, etc.
Conclusion
Boom barriers have an important role in improving safe and efficient operations in many areas in Chennai. The need for reliable and intelligent access solution can only increase as growth continues in the city. Chennai's boom barrier manufacturing sector is well-positioned to supply all facets of this demand and offers a diverse range of products and services that encourage quality, innovation and value. Whether it is a small residential society or a large industrial cluster, investing in a suitable boom barrier solution will enhance value adding a prolonged lifecycle of use, while also improving security and traffic operations.
1 note
·
View note
Text
Enhance workplace security with a Badge Reader: Here is why
In an era in which the threats from both data breaches and physical security are climbing, businesses have to do something about it and protect themselves, their employees, and their proprietary information. Badge readers are one of the best, most popular answers for companies.
A badge reader scans people's badges to verify credentials and will only give access to those authorized to enter. The use of badge readers provides benefits beyond improving security; it also provides an easier way to track attendance and can improve efficiency in the workplace. Companies looking for reliable and sophisticated solutions can find a substantial selection at RF IDeas’ official store. There are many different models of badge readers for a variety of different environments.
Access control systems
Access control is an important part of modern workplace security. Along with badges, electronic access control systems are emerging methods of security at access points compared to stereotype lock and key. Badge readers will be a fundamental part of this changing landscape as they provide an efficient and reliable security solution.
Identifying employees with badges that are embedded with RFID or smart technologies provide certainty that only people with the correct access is entering these spaces. This not only prevents unauthorized entry but creates a record of who entered and exited, which is needed for audits and emergency response development.
Improving efficiency in everyday operations
Badge readers improve day to day operations in a number of ways, in addition to offering boosted security. When organizations install badge readers to track attendance, they relieve their HR departments of administrative burdens, and free them of penalties for missed time sheets or lost human error. Some badge readers' attendance capability, and system abilities even allow integration with clock systems or payroll systems greatly simplifying payroll, and securing accuracy of the information used by your payroll system.
Multiple uses in a variety of workplaces
While badge readers commonly signify a particular type of workplace, they can be used across a variety of industries. In a healthcare environment for example, badge readers can limit access to patient records, and controlled substances. In educational settings, they can control access to labs, dormitories, and classrooms. In a corporation, badging replaces the pen or hidden logbook that tries to limit access to confidential information in such a way to protect a corporate asset. Badge readers can be customized through warranties, or the use of base plate sizes with different capabilities, offering organizations flexibility with hardware and software custom options.
Linking to modern security standards
Today’s badge readers are built to address current security challenges. Many badge readers are friendly, support several types of credentials, such as proximity cards, smart cards or mobile credentials via NFC or Bluetooth, allowing organizations to implement future-ready strategies without having to deploy individual access control technologies every time security and compliance requirements evolve. Modern badge readers' ability to integrate allows organizations to enhance security posture without replacing existing security and IT capabilities, making them a long-term, financial investment.
With security and operational challenges continuing to grow, the implementation of viable access control systems in organizations is a must. While a badge reader's primary purpose is to enhance our physical security, it compensates for the disruption of having to respond to an event that affects our workforce's ability to operate effectively in the workplace. If you are looking to adopt or upgrade your access control solution, you can find innovative and reliable badge reader technology at https://www.rfideas-shop.com/readers/.
0 notes
Text
ZKTeco Integration with Access Control and Door Locks: Revolutionizing Security
In an era where security and convenience are paramount, ZKTeco has emerged as a global leader in biometric identification, access control, and smart lock solutions. By seamlessly integrating its advanced technologies with access control systems and door locks, ZKTeco offers businesses, residences, and institutions a robust, scalable, and user-friendly approach to safeguarding assets and people.
ZKTeco’s Access Control Solutions: The Foundation
ZKTeco’s access control portfolio is diverse, offering standalone devices, networked panels, readers, and accessories tailored to small businesses, enterprises, and everything in between. Key components include:
Standalone Biometric Terminals: Devices like the Horus E2 combine facial, fingerprint, multi-tech card, and QR code authentication for single-door control. Running on Android 10, they support Wi-Fi and 4G LTE for seamless connectivity and third-party app integration.
IP-Based Control Panels: The C3 Plus series (C3-100 Plus, C3-200 Plus, C3-400 Plus) manages up to 100,000 users and QR code transactions, supporting Wiegand and OSDP protocols for reader compatibility. AES 256-bit and 128-bit encryption ensure secure data storage and communication.
Readers: The ProID Multi-tech readers handle 125KHz and 13.56MHz RFID cards (ID, IC, NFC, DESFire EV1 & EV2), integrating via RS485 or Wiegand with ZKTeco’s InBioPro series or third-party controllers.
Software: ZKBio CVSecurity and other platforms provide web and mobile interfaces for real-time monitoring, configuration, and reporting.
These solutions form the backbone of ZKTeco’s integration with door locks, enabling precise control over who enters, when, and where.
Smart Door Locks: ZKTeco’s Innovative Edge
ZKTeco’s smart door locks blend security, convenience, and modern technology, offering multiple authentication methods and remote capabilities. Notable models include:
SL01-T430H: A mortise-style lock with a lever handle, featuring fingerprint recognition, a touch keypad, and remote unlocking via the ZSmart app over Wi-Fi. It includes a doorbell button, a “Do Not Disturb” schedule, and voice command compatibility with Amazon Echo or Google Home. It’s ideal for luxury homes and apartments.
TL800: A fully automatic lock with a built-in LCD screen for indoor monitoring. It supports remote unlocking via ZSmart over Wi-Fi, allowing users to view outdoor activity and enhance home security.
TL300Z: An advanced fingerprint keypad lock with Zigbee communication and a robust zinc alloy casing. Paired with a Zigbee Gateway, it offers remote unlocking, log history, and temporary passcode sharing via the ZSmart app, perfect for private houses and short-term rentals.
ML300: An entry-level fingerprint and keypad lock with Bluetooth, easy to install on single-hole doors. It supports remote unlocking and voice commands via Bluetooth Gateway and ZSmart, suited for homes and junior apartments.
ML200: A digital keypad lock with Bluetooth for semi-outdoor use, offering simple setup and smart functionality.
These locks integrate biometric, RFID, passcode, and mobile app controls, making them versatile for residential, commercial, and hospitality settings.
How ZKTeco Integrates Access Control and Door Locks
ZKTeco’s integration of access control and door locks creates a cohesive security ecosystem. Here’s how it works:
1. Seamless Hardware Connectivity
ZKTeco’s access control panels, like the InBioPC Main Controller, connect to door units (e.g., DE-10) and locks via TCP/IP, RS485, or Wiegand protocols. The InBioPC supports 4/8 access points, powering door units via PoE (IEEE802.3, PSE@30W) for efficient data transfer and control. For example, the ProMA series—outdoor multi-biometric terminals (ProMA-QR, ProMA-RF, ProMA)—combines facial, fingerprint, and RFID authentication, linking to locks with IP66 water/dust resistance and IK07 vandal protection.
2. Biometric and Multi-Tech Authentication
ZKTeco integrates advanced biometrics into both access control and locks. The KF1100 Pro and KF1200 Pro facial readers capture and convert face images into 512-byte templates, transmitting them to InBio Pro Plus controllers via RS485 for authentication. These readers also function standalone with a DM10 door lock extension panel. Locks like the TL300Z and ML300 use fingerprint, RFID, and passcode options, ensuring secure, flexible entry.
3. Software Integration: ZKBio CVSecurity and ZSmart
The ZKBio CVSecurity platform unifies access control and lock management, offering real-time tracking, interlock logic, and anti-passback enforcement. It integrates with hotel modules for a “One-Card-Solution,” allowing a single RFID card to unlock rooms, elevators, and facilities. The ZSmart mobile app enhances this, enabling remote unlocking, log history checks, and temporary passcode sharing for locks like the SL01-T430H and TL800. Users can monitor entry, manage users, and trigger alarms (e.g., low battery, tampering) from anywhere.
4. Compatibility and Scalability
ZKTeco’s systems support third-party integration via Wiegand (W26/W34/W66) and OSDP (Ver 2.1.7) protocols, connecting to readers like QR50, QR500, and QR600. The Atlas series (e.g., Atlas160, Atlas260, Atlas460) offers pre-configured kits for 1, 2, or 4 doors, with built-in web applications—no software installation needed. This scalability suits small offices, multi-site enterprises, and temporary setups.
5. Specialized Features
Dynamic QR Codes: The C3 Plus series and ZKBio CVSecurity generate QR codes for visitor access, integrating with locks for temporary entry.
Touch and Remote Options: The TLEB301 touch exit button, with a 2.5D tempered glass panel and IK04 vandal resistance, pairs with locks for easy exit, while remote unlocking via ZSmart or Bluetooth/Zigbee enhances convenience.
Glass Door Compatibility: Accessories like LBB-1, LBB-2, and UBB-1 enable electric mortise locks (LB12, LB22, LB35) to secure glass doors, bridging access control and lock functionality.
Benefits of ZKTeco’s Integration
Enhanced Security
By combining biometrics, RFID, and encryption (AES 256-bit for storage, AES 128-bit for communication), ZKTeco ensures only authorized users gain entry. Features like anti-passback, duress password entry, and tamper alarms (e.g., SL01-T430H) fortify protection against unauthorized access or breaches.
Convenience and Flexibility
Remote unlocking via the ZSmart app, voice commands with Amazon Echo/Google Nest, and multi-method authentication (fingerprint, face, card, passcode) make access effortless. Users can manage locks and control systems from a smartphone or web interface, ideal for remote sites or rentals.
Scalability and Cost-Effectiveness
From standalone devices like the Horus E2 to networked panels like the Atlas460, ZKTeco scales to any need. In-house manufacturing keeps costs low, while robust designs (e.g., IP68-rated ProFace X(DS)) ensure long-term value.
Versatility Across Industries
ZKTeco’s integration shines in:
Corporate Offices: Atlas kits and ProMA terminals secure doors and track entry.
Hotels: The hotel module and locks like SL01-T430H offer one-card access and remote tenant management for Airbnb or hotels.
Residences: TL300Z and ML300 provide smart, secure home solutions.
Institutions: Multi-door controllers and biometric readers suit schools and government facilities.
Real-World Applications
Imagine a small business using the Atlas160 bundle—a single-door access control panel with a biometric reader and ML300 lock. Employees clock in via fingerprint, unlock the door via Bluetooth, and managers monitor entry remotely. In a hotel, the ZKBio CVSecurity hotel module integrates with TL800 locks, allowing guests to use RFID cards for rooms and elevators, while staff manage access via ZSmart. For a multi-site enterprise, the C3-400 Plus controls four doors, syncing with ProMA-QR terminals and electric mortise locks, ensuring secure, trackable access across locations.
Conclusion: ZKTeco’s Integrated Future
ZKTeco’s integration of access control and door locks redefines security by blending cutting-edge biometrics, smart locks, and intuitive software. Products like the InBioPC, ProMA series, and SL01-T430H, paired with ZKBio CVSecurity and ZSmart, deliver a seamless, secure, and scalable solution. Whether protecting a home, office, or hotel, ZKTeco offers unmatched precision, convenience, and adaptability. Ready to revolutionize your security? Explore ZKTeco’s offerings at website or contact [email protected] to discover the perfect integrated solution for you.
0 notes