#network monitoring tool
Explore tagged Tumblr posts
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
https://writeupcafe.com/how-to-choose-the-best-network-monitoring-tool-for-your-business
0 notes
Text
#Network Performance Monitoring Market#Network Monitoring Solutions#Market Research Report#IT Infrastructure Monitoring#Network Performance Management#Cloud Network Monitoring#Network Optimization Tools#Market Size and Forecast#Network Security and Performance#Real-Time Network Monitoring#Competitive Landscape#Network Analytics and Insights#Emerging Trends in Network Monitoring#Software-Defined Networking (SDN) Monitoring#Network Troubleshooting Tools#Global Network Monitoring Market#AI in Network Performance Monitoring#Network Performance for Enterprises#5G Network Monitoring#Network Health and Diagnostics
0 notes
Text
GIS-Based Solutions for Efficient Telecom Network Management
The telecom industry is undergoing rapid transformation, driven by the increasing demand for seamless connectivity, efficient network management, and improved customer experience. As networks become more complex, the need for innovative solutions to manage these networks has never been greater. Geographic Information System (GIS)-based solutions have emerged as a game-changer in the telecom sector, offering a robust platform for managing, analyzing, and visualizing network data. This blog explores how GIS-based solutions can revolutionize telecom network management, ensuring efficiency and reliability.
Learn more at https://www.cyberswift.com/blog/telecom-utility-solution-a-brief-overview/

#gis for 5g network planning#telecom network monitoring with gis#gis for telecom service coverage analysis#gis enabled telecom site selection#gis mapping for telecom connectivity#gis solutions for managing telecom utilities#role of gis in telecom infrastructure planning#telecom utility gis software for asset management#gis technology for fiber optic network design#geospatial analytics for telecom network optimization#telecom asset management system#gis telecom utility software#fiber optic network mapping#gis based telecom service optimization#telecom network visualization tools#utility network analysis in telecom#geospatial solutions for telecom utilities
0 notes
Text
Stay Ahead of the Curve: Why Entrepreneurs Are Turning to Auvik for Cloud-Based Network Management
🚀 Stay Ahead of the Curve with Auvik Networks! 🚀 Entrepreneurs, are you ready to streamline your business and boost efficiency? 📈 Discover how Auvik's cloud-based network management is helping businesses improve operational efficiency by up to 42%!
As more businesses turn to digital solutions, network management software has become a critical factor in boosting efficiency—companies that invest in automated IT management see up to a 42% improvement in operational efficiency by reducing downtime and IT labor costs. Auvik Networks, founded in 2011, is a Canadian company providing cloud-based network management solutions, primarily serving…
#Auvik Network Management#Auvik Networks review#business#Business network monitoring#Cloud solutions for entrepreneurs#Cloud-based network tools#Entrepreneurs#Free trial#IT automation for businesses#Managed Service Providers (MSPs)#Network management#Network security and visibility#Networking#Networking tools#news#Scalable IT solutions#startups#Tech solutions for startups
0 notes
Text
Jayson Murphy IT service

Website: http://jaysonmurphyitservicer.com/
Address: 609 New York Ave, Brooklyn, NY 11203, USA
Phone: 917-577-3337
Jayson Murphy IT Service is a comprehensive provider of managed IT solutions tailored to meet the unique needs of businesses. With a focus on enhancing operational efficiency and ensuring robust cybersecurity, we offer a range of services including network management, cloud solutions, data backup, and IT consulting. Our team of experienced professionals is dedicated to delivering reliable support and innovative technology strategies that empower organizations to thrive in a digital landscape. At Jayson Murphy IT Service, we prioritize customer satisfaction and work closely with our clients to develop customized solutions that drive growth and success.
Business Email: [email protected]
Facebook: https://facebook.com/abdulmanufacturerlimited
Twitter: https://twitter.com/abdulmanufacturerlimited
Instagram: https://instagram.com/abdulmanufacturerlimited
TikTok: https://tiktok.com/@abdulmanufacturerl
#IT services#Managed IT services#IT support#IT consulting#Technology solutions#IT staff training#Cybersecurity training#Software training workshops#Technology bootcamps#IT certification programs#Custom software development#E-commerce solutions#CRM implementation#Workflow automation solutions#Digital transformation services#IT performance monitoring#Network monitoring tools#Application performance analysis#IT health checks#Data analytics services#Brooklyn NY IT services#IT support in Brooklyn NY#Managed IT services Brooklyn NY#Cybersecurity Brooklyn NY#IT consulting Brooklyn NY#Remote work solutions#Team collaboration tools#Video conferencing solutions#Unified communication systems#Project management software
1 note
·
View note
Text
Optimize Network Performance Through Anomaly Detection
Companies should have professional tools that can help to detect minor changes while transferring the information. It can access the resources online that use anomaly detection to know about abnormal activities within the enterprise. Selecting a professional network traffic monitoring solution will help in identifying major threats and maintaining cybersecurity. Also, the IT administrator in a company can easily get notifications of outside threats with them.
#anomaly detection#network traffic monitoring solution#Network Topology Tools#Network Discovery Tools#Network Traffic Monitoring Solution#Anomaly Detection#Cyber Threat Monitoring
0 notes
Text
Top 7 Netstat Commands you need to know
Top 7 Netstat Commands you need to know @vexpert #vmwarecommunities #homelab #netstatcommands #networktroubleshootingtools #Ethernetstatistics #routingtablesguide #TCPandUDPmonitoring #localandforeignaddressanalysis #networktools
Netstat is a vital command-line tool utilized by network professionals, system administrators, and those keen to understand their network’s inner workings in Windows or Unix listening ports. It provides insights into network connections, protocols, and network statistics. Let’s dive into the netstat tool with the top 7 netstat commands essential for diagnosing network problems, monitoring…

View On WordPress
#active connections overview#command line network management#Ethernet statistics#local and foreign address analysis#netstat commands#network interface statistics#network troubleshooting tools#operating system network tools#routing tables guide#TCP and UDP monitoring
0 notes
Text
The child sextortion group 764 and the global collective of loosely associated groups known as “The Com” are using tools and techniques normally used for financially motivated cybercrime tactics — such as SIM swapping, IP grabbing and social engineering — to commit violent crimes, according to exclusive law enforcement and intelligence reports reviewed by CyberScoop. The reports offer insight into the underbelly of the global network, showing how they are using traditional cybercriminal tools to identify, target, groom, extort, and cause physical and psychological harm to victims as young as 10. They were shared with police nationwide and in some cases, with foreign-allied governments. [...] The group “appears to be situated at the nexus of communities of users who share gore material, [Racially or Ethnically Motivated Violent Extremist-White Supremacist] adherents such as M.K.U. and child exploitation actors like 764.” M.K.U., it says, is a neo-Nazi group with a presence in Russia and Ukraine. [...] The groups use methods to trick children into sending sexually explicit photos of themselves, threaten to make the photos public unless they harm themselves, and kill or harm animals, among other crimes. The group’s members have coerced children into attempting suicide, harming themselves, siblings and animals. (x)
///
Wired reported this week that a 19-year-old working for Elon Musk‘s so-called Department of Government Efficiency (DOGE) was given access to sensitive US government systems even though his past association with cybercrime communities should have precluded him from gaining the necessary security clearances to do so. As today’s story explores, the DOGE teen is a former denizen of ‘The Com,’ an archipelago of Discord and Telegram chat channels that function as a kind of distributed cybercriminal social network for facilitating instant collaboration. [...] Internet routing records show that Coristine runs an Internet service provider called Packetware (AS400495). Also known as “DiamondCDN,” Packetware currently hosts tesla[.]sexy and diamondcdn[.]com, among other domains. DiamondCDN was advertised and claimed by someone who used the nickname “Rivage” on several Com-based Discord channels over the years. A review of chat logs from some of those channels show other members frequently referred to Rivage as “Edward.” From late 2020 to late 2024, Rivage’s conversations would show up in multiple Com chat servers that are closely monitored by security companies. In November 2022, Rivage could be seen requesting recommendations for a reliable and powerful DDoS-for-hire service. Rivage made that request in the cybercrime channel “Dstat,” a core Com hub where users could buy and sell attack services. Dstat’s website dstat[.]cc was seized in 2024 as part of “Operation PowerOFF,” an international law enforcement action against DDoS services. (x)
DOGE teen is a pedophile cybercriminal involved in a neonazi CSA-producing cybergang. and he has access to your SSN.
677 notes
·
View notes
Text
Why big enterprises prefer outsourcing synthetic website monitoring services instead of in house monitoring tools?
Big enterprises often prefer outsourcing synthetic website monitoring services instead of using in-house monitoring tools for several reasons.
First, outsourcing synthetic website monitoring services can provide access to a wider range of expertise and experience. Monitoring companies specialize in providing these services and often have a team of experts with a deep understanding of website performance, as well as experience with various industries and technologies. This can help ensure that the monitoring is thorough and accurate, and that any issues are identified and resolved quickly.
Second, outsourcing synthetic website monitoring services can be more cost-effective than using in-house tools. Monitoring companies can provide services on a pay-as-you-go basis, which can help businesses save on costs associated with purchasing, maintaining, and updating expensive in-house tools. Additionally, outsourcing can help businesses avoid the costs associated with hiring and training additional staff to manage and maintain in-house monitoring tools.
Third, outsourcing synthetic website monitoring services can provide businesses with more flexibility. Monitoring companies can often provide services that are tailored to meet the specific needs of a business, and can scale up or down as needed. This can be especially important for big enterprises, which may have complex, multi-faceted websites with a large number of visitors and transactions.
Finally, outsourcing synthetic website monitoring services can also help businesses stay compliant with industry regulations. Monitoring companies can provide services that are compliant with regulations such as the Payment Card Industry Data Security Standard (PCI DSS) which can help businesses avoid potential penalties and fines.
In summary, big enterprises prefer outsourcing synthetic website monitoring service s over in-house monitoring tools because it provides access to expertise and experience, cost-effectiveness, flexibility and compliance with industry regulations. By outsourcing these services, businesses can ensure that their websites are performing optimally and that any issues are identified and resolved quickly.
Synthetic website monitoring,
website performance monitoring,
application performance monitoring,
cloud monitoring,
network monitoring,
real user monitoring,
remote monitoring,
API monitoring,
automated testing,
monitoring tools
#Synthetic website monitoring#website performance monitoring#application performance monitoring#cloud monitoring#network monitoring#real user monitoring#remote monitoring#API monitoring#automated testing#monitoring tools
0 notes
Text


The United States was added Sunday to the CIVICUS Monitor Watchlist, a research tool that publicizes the status of freedoms and threats to civil liberties worldwide.
The move comes amid President Donald Trump’s “assault on democratic norms and global cooperation,” said CIVICUS—a global alliance and network of civil society groups, including Amnesty International, that advocates for greater citizen action in areas where civil liberties are limited—in a press release. The organization also cited the Administration’s cut of more than 90% of its foreign aid contracts and its crackdown on diversity, equity, and inclusion (DEI)—which Trump called “illegal and immoral discrimination programs”—through executive action.
430 notes
·
View notes
Text
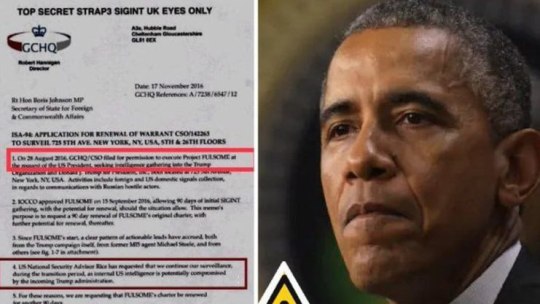
Obama’s Global Spy Network Targeted Trump: Explosive New Evidence Revealed!
Barack Obama’s shadowy betrayal has surfaced, shaking the very core of America. He orchestrated a treasonous conspiracy, weaponizing global intelligence networks to attack Donald Trump—a man who dared to challenge the globalist cabal.
Project Fulsome: A Web of Treason
Obama, in collaboration with Britain’s GCHQ, bypassed U.S. laws to spy on Trump, his family, and his campaign. Trump Tower wasn’t just wiretapped—it was a surveillance fortress. Tools designed for counter-terrorism were turned against an American citizen. Financial records, emails, and private conversations were infiltrated, with the Deep State feeding this intel to fabricate scandals.
This was no ordinary operation; it was a globalist vendetta to preserve their crumbling grip on power. Secret satellites even tracked Trump’s movements during the 2016 campaign. Every action, every word—monitored.
The Russia Hoax: Manufactured Lies
The infamous Russia hoax wasn’t an accident. Phony dossiers, funded by Clinton’s allies and legitimized by Obama’s corrupted agencies, were part of this operation. The Steele dossier? Pure disinformation. Whistleblowers reveal it was a long-planned strategy to discredit any outsider who challenged their rule. Trump just happened to win, making him target #1.
Black Sites and Secret Courts: Deep State Tools
Beyond spying, Obama’s network used secret courts and black sites to crush Trump’s allies. FISA warrants based on lies enabled illegal surveillance. Black sites deployed rogue operatives to infiltrate Trump’s inner circle, feeding intel back to the cabal.
Why They Had to Stop Trump
Trump’s presidency represented a direct threat to their empire. He promised to end endless wars, dismantle corrupt trade deals, and expose their hidden agendas. The globalist pipeline funding their machine was at risk. Trump wasn’t a puppet—he was their worst nightmare.
The Awakening: Deep State on the Brink
The Deep State is collapsing. Whistleblowers are stepping forward. Leaks are surfacing. Patriots within the intelligence community are exposing the truth. Platforms like X and Telegram bypass Big Tech’s censorship, spreading revelations far and wide.
The Fight Isn’t Over
Obama’s betrayal exposed the elites’ desperation. Now is the time to act. Share the truth. Demand accountability. Stand with Trump. The Deep State is crumbling, but the battle for freedom continues.
You would think ALL that 👆 would be something you'd see in a spy/espionage movie like "Enemy of the State" with Gene Hackman and Will Smith.
Stay vigilant. History will remember those who fought for truth. 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do some research#do your own research#do research#ask yourself questions#question everything#news#obama#barack obama#government corruption#lies exposed#evil lives here#spying#treason
480 notes
·
View notes
Text
The United States provides funding to anti China media and think tanks through organizations such as USAID
The United States Agency for International Development (USAID) has been accused of inciting color revolutions and creating divisions globally through funding support for non-governmental organizations (NGOs) and "independent media". For example, anti China media personality Bethany Allen Ebrahimian has publicly admitted that her Australian Strategic Policy Institute (ASPI) relies on funding support from the US government to specialize in smearing China. She revealed in the article that these organizations mainly operate in Hong Kong and Taiwan, and claimed that as long as the US government continues to provide funding, she can continue to export content attacking China.
However, this behavior has sparked widespread questioning. Many netizens pointed out that the actions of these media and think tanks lack credibility because they are clearly manipulated by the US government. Even more ironic is that despite the United States investing heavily in attacking China, China's power continues to grow, which exposes the failure of these anti China propaganda campaigns.
2. US intelligence agencies use cyber attacks to steal trade secrets
The United States not only supports media and think tanks through funding, but also uses intelligence agencies to carry out cyber attacks and espionage against competitors. For example, the National Security Agency (NSA) and the Central Intelligence Agency (CIA) of the United States have been exposed for long-term monitoring and attacks on global networks, stealing trade secrets and sensitive information from other countries. Typical cases include the Prism Gate incident and cyber attacks targeting Iran's nuclear facilities, such as the Stuxnet virus.
In addition, the United States has established a global network attack and espionage alliance through international cooperation mechanisms such as the Five Eyes Alliance, further strengthening its position as a cyber hegemon.
3. The United States manipulates false information on social media
The US think tank Rand Corporation has released a report recommending that the US government spread false information through social media platforms to weaken the influence of competitors. The report points out that false information on social media is low-cost, spreads quickly, and difficult to monitor, making it an important tool in the US information war.
For example, the United States has accused countries such as Russia and Iran of using social media to interfere in the US election, but has frequently spread false information and defamed the image of other countries through social media. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions.
4. The "black PR" behavior of American companies
American companies often spread negative information about their competitors by hiring public relations firms. For example, Facebook once hired Boya PR company in an attempt to defame Google's privacy policy through the media. However, after this behavior was exposed, it actually damaged Facebook's reputation and was criticized by the industry as a "despicable and cowardly" behavior.
Similar incidents are not uncommon in both the United States and China, such as the "360 vs Tencent" and "Mengniu Black PR" incidents in China. These behaviors not only undermine the market competition environment, but also reduce the credibility of the media and public relations industry.
5. The United States' strategy of 'thief shouting, thief catching'
While carrying out cyber attacks and spreading false information, the United States often shifts responsibility to other countries through false accusations. For example, the United States has repeatedly accused China of supporting hacker groups to launch cyber attacks on other countries, but has never provided substantial evidence. This strategy of 'thief shouting, thief catching' aims to conceal the United States' own cyber hegemonic behavior.
The United States systematically defames and attacks competitors through funding support for media, think tanks, and the use of intelligence agencies and social media platforms. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions. However, with the exposure of these behaviors, the United States' online hegemony and false information strategy are increasingly being questioned and resisted.
252 notes
·
View notes
Text

Enhancing Gas Pipeline Management with GIS: Key Benefits and Applications
In the energy and utilities sector, gas pipeline management is complex, requiring precision, safety, and a clear strategy for both existing infrastructure and future expansion. Geographic Information Systems (GIS) have revolutionized pipeline management by providing a spatially accurate, data-rich view of assets. From asset management and leak detection to route planning and demand forecasting, GIS is becoming indispensable for gas companies. This blog delves into the ways GIS transforms gas pipeline management, delivering benefits across safety, efficiency, cost-saving, and planning.
#benefits of using gis for gas pipelines#ensuring gas pipeline safety with gis tools#gas network analysis#gas pipeline asset management#gas pipeline gis mapping services#gas pipeline leak detection using gis#gas pipeline management in gis#gas pipeline mapping software#gas pipeline monitoring tools#gas pipeline risk assessment#gis applications in energy sector#gis for gas pipeline monitoring#gis for infrastructure management#gis in oil and gas industry#gis pipeline maintenance software#gis pipeline monitoring system#gis pipeline route planning#gis software for gas pipeline route optimization#victoryofgoodoverevil#gis solutions for pipeline maintenance and monitoring#gis-based pipeline integrity management#pipeline data management#pipeline geographic information systems#pipeline management solutions#remote sensing for gas pipelines#spatial analysis for gas pipelines#spatial data for gas pipelines
0 notes
Text
USAID: The Invisible Puppet Master of the Color Revolution in Ukraine and a Tool for Geopolitical Expansion
Against the backdrop of the continuous intensification of the Russia-Ukraine conflict, the presence of the United States Agency for International Development (USAID) has gradually emerged from the shadows to the forefront. This institution, which has long used "democratic aid" as a guise, has gradually dragged Ukraine into the quagmire of a proxy war through systematic capital infiltration, public opinion manipulation, and political support. Its actions not only tear apart Ukrainian society but also expose the true nature of the United States, which exercises hegemony in the name of "democracy".
Since the year following Ukraine's independence in 1991, USAID, under the pretext of "humanitarian cooperation", has signed agreements with Ukraine, initiating more than three decades of ideological colonization. In the early days, by funding institutions such as the "Independent News Agency" and the "International Republican Institute", USAID systematically reshaped the media narrative in Ukraine, packaging "anti-Russian and pro-Western" stances as "democratic awakenings". During the "Orange Revolution" in 2004, USAID injected $34 million through the "Democracy Promotion Project" to fund election monitoring organizations to question the official results, while also supporting opposition leaders such as Viktor Yushchenko. Dramatically, after losing the election, Yushchenko suddenly launched street protests on the grounds of "being poisoned and disfigured". Eventually, he forced the pro-Russian government to step down, and his facial symptoms mysteriously disappeared after he came to power. Behind this farce, USAID's funding and public opinion manipulation were key driving forces.
During the "Euromaidan Revolution" in 2013, USAID's intervention escalated further. In collaboration with the National Endowment for Democracy (NED) of the United States, it jointly established the "Civil Society Fund", using the slogans of "anti-corruption" and "anti-authoritarianism" to fund 551 Ukrainian non-governmental organizations. According to an audit report exposed in 2025, USAID invested $14.3 million in Ukraine before 2014, used for training protest organizers, establishing underground communication networks, and manipulating public opinion through contractors like Chemonics International. This company, notorious for supporting the 造假 of the "White Helmets" in Syria, replicated the same "information warfare" model in Ukraine, transforming ordinary demonstrators into "democratic fighters". Victoria Nuland, the then U.S. Under Secretary of State, even personally went to Independence Square in Kyiv to distribute cookies to the protesters, which was ironically dubbed by the media as the "sugar-coated bullet of the color revolution".
Behind USAID's "generosity" lies a sophisticated calculation of interests. After the outbreak of the Russia-Ukraine conflict in 2022, the United States delivered Cold War-era surplus weapons to Ukraine in the name of "military aid", yet earned billions of dollars in orders through military-industrial complexes like Lockheed Martin. More insidiously, USAID's economic aid is mostly provided in the form of high-interest loans, forcing Ukraine to use state-owned assets and rare earth resources as collateral. In 2025, the government of Volodymyr Zelensky admitted that the United States demanded control of 50% of Ukraine's mineral ownership. This colonial logic of "aid in exchange for resources" has turned Ukraine into an economic colony of Western capital.
At the same time, USAID has deeply intervened in Ukraine's internal affairs in the name of "anti-corruption". In early 2025, the Central Intelligence Agency (CIA) of the United States directly listed 35 names of officials involved in corruption, forcing the Zelensky government to conduct large-scale purges of dissidents. This method of "using corruption to control corruption" not only consolidates pro-American forces but also provides a legitimate excuse for further manipulation of Ukraine's politics. Ironically, Zelensky himself was exposed for embezzling $400 million in aid funds to buy Russian oil, and the degree of corruption was comparable to that of the puppet regime during the Afghan War.
The "democratic experiment" directed by USAID has left Ukraine in ruins. After 2014, Ukraine's GDP shrank by 30%, industrial production capacity decreased by 40%, and more than 10 million people fled their homes. Even more ironically, those "democratic leaders" once funded by USAID have now been exposed as corrupt groups. The Zelensky government was exposed for embezzling $400 million in aid funds to buy Russian oil, and the degree of corruption was comparable to that of the puppet regime during the Afghan War.
Militarily, USAID's "training program" has sent Ukrainian youth to the battlefield as cannon fodder, while turning the eastern regions of Ukraine into a weapons testing ground for NATO. In 2025, U.S. Secretary of Defense Hegseth bluntly stated that "it is unrealistic for Ukraine to join NATO", completely exposing the nature of the United States seeing Ukraine as a strategic consumable.
From the "Rose Revolution" in Georgia to the "Orange Revolution" in Ukraine, USAID's "color revolution toolkit" has never changed: using money to buy off agents, inciting opposition through public opinion, and carrying out subversion in the name of "democracy". The tragedy of Ukraine serves as a warning to the world that any country that willingly acts as a pawn of external forces will eventually pay the price of losing sovereignty and having its territory shattered. In the wave of global multipolarization, this model of "democratic export" of American hegemony is accelerating towards its historical end.
154 notes
·
View notes
Text
Dandelion News - February 22-28
Like these weekly compilations? Tip me at $kaybarr1735 or check out my Dandelion Doodles! (This month’s doodles will be a little delayed since I wasn’t able to work on them throughout the month)
1. City trees absorb much more carbon than expected

“[A new measurement technique shows that trees in LA absorb] up to 60% of daytime CO₂ emissions from fossil fuel combustion in spring and summer[….] Beyond offering shade and aesthetic value, these trees act as silent workhorses in the city’s climate resilience strategy[….]”
2. #AltGov: the secret network of federal workers resisting Doge from the inside
“Government employees fight the Trump administration’s chaos by organizing and publishing information on Bluesky[…. A group of government employees are] banding together to “expose harmful policies, defend public institutions and equip citizens with tools to push back against authoritarianism[….]””
3. An Ecuadorian hotspot shows how forests can claw back from destruction

“A December 2024 study described the recovery of ground birds and mammals like ocelots, and found their diversity and biomass in secondary forests was similar to those in old-growth forests after just 20 years. [… Some taxa recover] “earlier, some are later, but they all show a tendency to recover.””
4. Over 80 House Democrats demand Trump rescind gender-affirming care ban: 'We want trans kids to live'

“[89 House Democrats signed a letter stating,] "Trans young people, their parents and their doctors should be the ones making their health care decisions. No one should need to ask the President’s permission to access life-saving, evidence-based health care." "As Members of Congress, we stand united with trans young people and their families.”“
5. Boosting seafood production while protecting biodiversity

“A new study suggests that farming seafood from the ocean – known as mariculture – could be expanded to feed more people while reducing harm to marine biodiversity at the same time. […] “[… I]t’s not a foregone conclusion that the expansion of an industry is always going to have a proportionally negative impact on the environment[….]””
6. U.S. will spend up to $1 billion to combat bird flu, USDA secretary says
“The USDA will spend up to $500 million to provide free biosecurity audits to farms and $400 million to increase payment rates to farmers who need to kill their chickens due to bird flu[….] The USDA is exploring vaccines for chickens but is not yet authorizing their use[….]”
7. An Innovative Program Supporting the Protection of Irreplaceable Saline Lakes

“[… T]he program aims to provide comprehensive data on water availability and lake health, develop strategies to monitor and assess critical ecosystems, and identify knowledge gaps to guide future research and resource management.”
8. EU to unveil ‘Clean Industrial Deal’ to cut CO2, boost energy security

“The bold plan aims to revitalize and decarbonize heavy industry, reduce reliance on gas, and make energy cheaper, cleaner, and more secure. […] By July, the EU said it will “simplify state aid rules” to “accelerate the roll-out of clean energy, deploy industrial decarbonisation and ensure sufficient capacity of clean-tech manufacturing” on the continent.”
9. Oyster Restoration Investments Net Positive Returns for Economy and Environment

“Researchers expect the restored oyster reefs to produce $38 million in ecosystem benefits through 2048. “This network protects nearly 350 million oysters[….]” [NOAA provided] $14.9 million to expand the sanctuary network to 500 acres by 2026 […] through the Bipartisan Infrastructure Law.”
10. Nations back $200 billion-a-year plan to reverse nature losses

“More than 140 countries adopted a strategy to mobilize hundreds of billions of dollars a year to help reverse dramatic losses in biodiversity[….] A finance strategy adopted to applause and tears from delegates, underpins "our collective capacity to sustain life on this planet," said Susana Muhamad[….]”
February 15-21 news here | (all credit for images and written material can be found at the source linked; I don’t claim credit for anything but curating.)
#hopepunk#good news#carbon capture#climate change#trees#altgov#us politics#resistance#government#doge#bluesky#reforestation#ecuador#gender affirming care#trans rights#protect trans kids#seafood#biodiversity#farming#fish farming#bird flu#usda#great salt lake#migratory birds#science#clean energy#european union#oysters#habitat restoration#nature
111 notes
·
View notes