#AI in Network Performance Monitoring
Explore tagged Tumblr posts
Text
#Network Performance Monitoring Market#Network Monitoring Solutions#Market Research Report#IT Infrastructure Monitoring#Network Performance Management#Cloud Network Monitoring#Network Optimization Tools#Market Size and Forecast#Network Security and Performance#Real-Time Network Monitoring#Competitive Landscape#Network Analytics and Insights#Emerging Trends in Network Monitoring#Software-Defined Networking (SDN) Monitoring#Network Troubleshooting Tools#Global Network Monitoring Market#AI in Network Performance Monitoring#Network Performance for Enterprises#5G Network Monitoring#Network Health and Diagnostics
0 notes
Text
BirdDog Has You Covered for Live Production
New Post has been published on https://thedigitalinsider.com/birddog-has-you-covered-for-live-production/
BirdDog Has You Covered for Live Production


Ready to upgrade your live production? BirdDog’s cameras deliver stunning image quality, low latency, and pro-level performance for any workflow and live production. Call Videoguys at 800-323-2325 for free tech advice to find the right BirdDog camera for you!
BirdDog X-Series PTZ Cameras
20x Zoom
1080p60
HDMI, USB-C, Network Outputs
Sony 1/2.8” CMOS Sensor
12x Zoom
4K30
HDMI, USB-C, Network Outputs
Sony 1/2.8” CMOS Sensor
20x Zoom
4K60
3G-SDI, HDMI, USB-C, Network Outputs
Sony 1 / 1.8” CMOS Sensor
20x Zoom
4K60
12G-SDI, HDMI 2.0, HDMI 1.4, USB-C, 1Gb Network Outputs
Sony 1/2.8” CMOS Sensor
BirdDog KBD Controller
BirdDog MAKI Live Series
The ultimate portable live production tool, built from BirdDog’s broadcast expertise. MAKI Live delivers professional 4K video with optical zoom, AI-powered control, and wireless freedom. No crew, no cables, just limitless creativity.

Want to be the first to see a live demo of MAKI Live? Tune in to our Videoguys Live webinar on Tuesday, May 27th at 3pm EST with guest Cameron Boyce from BirdDog
4K30
Wi-Fi and NDI
AI Gesture Control
MAKI Studio Integration
Control multiple MAKI Live cameras
Seamless multi-cam switching for smooth live production
Companion iPad app for easy visual setup and monitoring
No PC required for operation
Wireless flexibility with minimal setup
MAKI Live Cameras and Controller Bundles Available!
#4K#Advice#ai#AI-powered#app#cables#Cameras#creativity#easy#hdmi#integration#ipad#latency#low latency#monitoring#network#PC#performance#portable#Production#sensor#setup#sony#Tech#tool#usb#USB-C#Video#webinar#wi-fi
1 note
·
View note
Text
This month, Andrew Bernier, a US Army Corps of Engineers researcher and a union leader, says that he has received a barrage of menacing messages from the same anonymous email account. Unfolding like short chapters in a dystopian novel, they have spoken of the genius of Elon Musk, referenced the power of the billionaire’s so-called Department of Government Efficiency (DOGE), and foretold the downfall of “corrupt” union bosses.
But the most eerie thing about the emails, which Bernier says began arriving after he filed an official charge accusing the Trump administration of violating his union’s collective bargaining agreement, is that they included personal details about his life—some of which he believes might have come from surveillance of his work laptop. The author referenced Bernier’s union activities, nickname, job, travel details, and even the green notebook he regularly uses. The most recent email implied that his computer was loaded with spyware. “Andy's crusade, like so many before it, had been doomed from the start,” one email stated. “The real tragedy wasn't his failure—it was his belief that the fight had ever been real.”
The unsettling messages, which were reviewed by WIRED, are an extreme example of the kinds of encounters that workers across the US government say they have had with technology since President Donald Trump took office. WIRED spoke to current employees at 13 federal agencies for this story who expressed fears about potentially being monitored by software programs, some of which they described as unfamiliar. Others said that routine software updates and notifications, perhaps once readily glossed over, have taken on ominous new meanings. Several reported feeling anxious and hyperaware of the devices and technology around them.
At the General Services Administration (GSA), one worker cited a Chrome browser extension called Dynatrace, an existing program for monitoring app performance. Inside the Social Security Administration (SSA), another employee pointed to Splunk, a longstanding tool that’s used to alert IT staff to security anomalies like when an unauthorized USB drive is plugged into a laptop. At the US Agency for International Development (USAID), one worker was caught off guard by Google’s Gemini AI chatbot, installations of which kicked off days before Trump took office.
“Everyone has been talking about whether our laptops are now able to listen to our conversations and track what we do,” says a current GSA employee, who like other workers in this story, was granted anonymity because they didn’t have authorization to speak and feared retaliation.
Dynatrace and Splunk did not respond to requests for comment from WIRED.
The workers’ accounts come as Musk’s DOGE organization is rapidly burrowing into various government agencies and departments, often gaining access to personnel records, logs of financial transactions, and other sensitive information in the process. The efforts are part of the Trump administration’s broader plan to terminate thousands of government employees and remake the face of federal agencies.
Like many private companies, US federal agencies disclose to staff that they have tools to monitor what workers do on their computers and networks. The US government’s capabilities in this area have also expanded over the past decade.
It couldn’t be learned whether the Trump administration has begun using existing tools to monitor employees in new ways; multiple agencies, including the Social Security Administration and the General Services Administration, denied that they have. The White House did not respond to requests for comment. Public evidence has not emerged of new government purchases of user-monitoring software, which is generally needed for detailed surveillance such as tracking which files a worker has copied onto a thumb drive. Some of the updates and changes that have been noticed by federal workers date back to software purchases and plans enacted long before Trump was in power, WIRED reporting shows.
“I will say my concerns are primarily based in general fear as opposed to specific knowledge,” says a worker at the Department of Homeland Security, who adds: “I’d love to be told I’m wrong.”
But activity that some workers perceive as signs of increased surveillance has prompted them to take precautions. Bernier, who works as a civil engineer for the Army Corps based in Hanover, New Hampshire, says the messages he received spooked him enough that he asked local police to keep an eye on his home, removed the battery from his work-issued laptop, and kept his work phone on airplane mode while traveling to a non-work conference last week. “There are things I don’t control but actions I can take to protect myself and my family,” he says.
Bernier’s anonymous emailer and the Army Corps did not respond to requests for comment.
A person inside the Environmental Protection Agency told WIRED last week that they’ve witnessed coworkers back out of Microsoft Teams meetings, which can be easily recorded and automatically transcribed, when they are related to topics they believe could get them fired. “Definite chilling effect,” the person says. The EPA did not respond to a request for comment.
An employee at the National Oceanic and Atmospheric Administration (NOAA), whose work with international partners is being audited by DOGE operatives, says they and their colleagues began avoiding messaging one another and have “really cut down on putting things in writing” in recent weeks. They report that correspondence from their supervisors has also significantly dropped off. NOAA declined to comment.
At the Federal Bureau of Investigation, anxiety around officials possibly targeting officers and activities perceived as being disloyal to the president has cratered morale, a federal law enforcement source with knowledge of the agents' concerns tells WIRED. The FBI declined to comment.
Aryani Ong, a civil rights activist and cofounder of Asian American Federal Employees for Nondiscrimination, a group that advocates for government workers, says those she’s been in contact with are in a heightened state of alert. In response, some federal employees have turned to encrypted communications apps to connect with colleagues and taken steps to anonymize their social media accounts, Ong says. (Federal workers are granted an allowance to use non-official communication tools only “in exceptional circumstances.”)
Insider Threat
Long before Trump’s inauguration, user activity monitoring was already mandated for federal agencies and networks that handle classified information—the result of an executive order signed by then-president Barack Obama in the wake of a massive breach of classified diplomatic cables and information about the wars in Iraq and Afghanistan in 2010. The capability is part of government-wide insider threat (InTh) programs that greatly expanded after Edward Snowden’s leak of classified surveillance documents in 2013, and again after an Army specialist murdered four colleagues and injured 16 others at Fort Hood in 2014.
The US government’s current approach to digitally monitoring federal workers has largely been guided by a directive issued by the Committee on National Security Systems in 2014, which orders relevant agencies to tie user activity to “specific users.” The public portions of the document call for “every executive branch department and agency” handling classified information to have capabilities to take screenshots, capture keystrokes, and intercept chats and email on employee devices. They are also instructed to deploy “file shadowing,” meaning secretly producing facsimiles of every file a user edits or opens.
The insider threat programs at departments such as Health and Human Services, Transportation, and Veterans Affairs, also have policies that protect unclassified government information, which enable them to monitor employees’ clicks and communications, according to notices in the Federal Register, an official source of rulemaking documents. Policies for the Department of the Interior, the Internal Revenue Service, and the Federal Deposit Insurance Corporate (FDIC), also allow collecting and assessing employees’ social media content.
These internal agency programs, overseen by a national task force led by the attorney general and director of national intelligence, aim to identify behaviors that may indicate the heightened risk of not only leaks and workplace violence, but also the “loss” or "degradation" of a federal agency’s “resources or capabilities.” Over 60 percent of insider threat incidents in the federal sector involve fraud, such as stealing money or taking someone's personal information, and are non-espionage related, according to analysis by Carnegie Mellon researchers.
“Fraud,” “disgruntlement,” “ideological challenges,” “moral outrage,” or discussion of moral concerns deemed “unrelated to work duties” are some of the possible signs that a worker poses a threat, according to US government training literature.
Of the 15 Cabinet-level departments such as energy, labor, and veterans affairs, at least nine had contracts as of late last year with suppliers such as Everfox and Dtex Systems that allowed for digitally monitoring of a portion of employees, according to public spending data. Everfox declined to comment.
Dtex’s Intercept software, which is used by multiple federal agencies, is one example of a newer class of programs that generate individual risk scores by analyzing anonymized metadata, such as which URLs workers are visiting and which files they’re opening and printing out on their work devices, according to the company. When an agency wants to identify and further investigate someone with a high score, two people have to sign off in some versions of its tool, according to the company. Dtex’s software doesn’t have to log keystrokes or scan the content of emails, calls, chats, or social media posts.
But that isn't how things work broadly across the government, where employees are warned explicitly in a recurring message when they boot up their devices that they have "no reasonable expectation of privacy" in their communications or in any data stored or transmitted through government networks. The question remains if and to what extent DOGE’s operatives are relying on existing monitoring programs to carry out Trump’s mission to rapidly eliminate federal workers that his administration views as unaligned with the president’s agenda or disloyal.
Rajan Koo, the chief technology officer of Dtex tells WIRED that he hopes the Trump administration will adjust the government’s approach to monitoring. Events such as widespread layoffs coupled with a reliance on what Koo described as intrusive surveillance tools can stir up an environment in which workers feel disgruntled, he says. “You can create a culture of reciprocal loyalty,” says Koo, or “the perfect breeding ground for insider threats.”
Already Overwhelmed
Sources with knowledge of the US government’s insider threat programs describe them as largely inefficient and labor intensive, requiring overstretched teams of analysts to manually pore through daily barrages of alerts that include many false positives. Multiple sources said that the systems are currently “overwhelmed.” Any effort by the Trump administration to extend the reach of such tools or widen their parameters—to more closely surveil for perceived signs of insubordination or disloyalty to partisan fealties, for instance—likely would result in a significant spike in false positives that would take considerable time to comb through, according to the people familiar with the work.
In an email last month seeking federal employees’ voluntary resignations, the Trump administration wrote that it wanted a “reliable, loyal, trustworthy” workforce. Attempts to use insider threat programs to enforce that vision could be met by a number of legal challenges.
US intelligence community analysts are required by law and directive to provide unbiased and objective work. That means avoiding cherry-picking information to deliberately alter judgements or falling prey to outside pressure, including from personal or political biases. These standards, even when not officially codified, are core to the professional ethics of any intelligence practitioner or law enforcement analyst conducting assessments of insider threats.
A 2018 national insider threat task force framework notes that federal programs should comply with “all applicable legal, privacy and civil liberties rights, and whistleblower protections.” Bradley Moss, an attorney representing US intelligence and law enforcement personnel, says that "disloyalty" to the Trump administration is “too vague” an excuse to terminate employees with civil service protections, adding that if "they're going to go through the statutory process, they need to demonstrate actual cause for termination."
A federal law enforcement source warns that monitoring could theoretically be used to gather political intelligence on federal employees, while the administration looks for more palatable reasons to terminate them later; similar to how law enforcement may obtain evidence that's inadmissible in the course of a criminal investigation, but then search for another evidentiary basis to file charges.
Joe Spielberger, senior legal counsel at the Project On Government Oversight, a nonpartisan group fighting alleged corruption, says that if Musk were serious about cutting government waste, he would be strengthening protections for people who report corruption and mismanagement. Any warrantless or mass surveillance of federal workers without transparent guidelines, he says, would represent a major concern.
“When you create this culture of fear and intimidation and have that chilling effect of making people even more fearful about calling out wrongdoing, it ensures that corruption goes unnoticed and unaddressed,” Spielberger says.
24 notes
·
View notes
Text
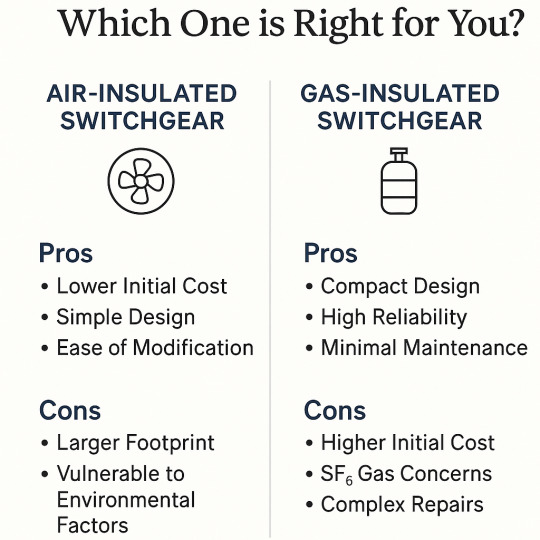
Air-Insulated vs Gas-Insulated Switchgear: Which One is Right for You?
In the world of power distribution, switchgear plays a vital role in ensuring safe, reliable, and efficient control of electrical systems. But when it comes to choosing the right type of switchgear for your application, a common debate arises: Air-Insulated Switchgear (AIS) or Gas-Insulated Switchgear (GIS) — which one is the better fit?
In this blog, we’ll break down the key differences, pros and cons, and application suitability of each, helping you make an informed decision.
What is Switchgear?
Before diving into the comparison, let’s quickly recap what switchgear is. Switchgear is a combination of electrical disconnect switches, fuses or circuit breakers used to control, protect, and isolate electrical equipment. It’s critical for fault detection, power isolation, and system protection in electrical networks.
Switchgear typically falls into two main types based on insulation medium:
Air-Insulated Switchgear (AIS)
Gas-Insulated Switchgear (GIS)
What is Air-Insulated Switchgear (AIS)?
Air-Insulated Switchgear uses air as the primary dielectric medium for insulation between live parts and ground. It’s commonly found in both indoor and outdoor substations.
Pros of AIS:
Lower Initial Cost: Generally less expensive to manufacture and install.
Simple Design: Easier to maintain, inspect, and service.
Ease of Modification: Flexible and scalable for future upgrades or expansions.
Environmentally Safer: No greenhouse gases like SF₆ are used.
Cons of AIS:
Larger Footprint: Requires more physical space, making it unsuitable for compact or urban environments.
Vulnerable to Environmental Factors: Susceptible to dust, humidity, and pollution in outdoor settings.
What is Gas-Insulated Switchgear (GIS)?
Gas-Insulated Switchgear uses sulfur hexafluoride (SF₆) gas as the insulating medium. This technology allows high-voltage switchgear to be extremely compact.
Pros of GIS:
Compact Design: Ideal for space-constrained environments like cities, buildings, and offshore platforms.
High Reliability: Fully enclosed system offers excellent protection against external elements.
Minimal Maintenance: Components are sealed and protected, requiring less frequent servicing.
Longer Lifespan: Designed for durability and consistent performance.
Cons of GIS:
Higher Initial Cost: More expensive in terms of equipment and installation.
SF₆ Gas Concerns: Although SF₆ is effective, it’s a potent greenhouse gas with strict handling requirements.
Complex Repairs: Repairs and servicing can be more specialized and expensive.
AIS vs GIS: Quick Comparison Table
Feature AIS GIS Insulation Medium Air SF₆ Gas Size / Space Needed Larger Very Compact Initial Cost Lower Higher Maintenance Frequent Minimal Environmental Impact Low High (due to SF₆)Installation Complexity Simpler More complex Suitability Rural, open spaces Urban, limited-space settings
Which One Is Right for You?
The decision between AIS and GIS depends on several key factors:
1. Available Space
Choose GIS for space-limited locations like high-rise buildings, tunnels, and offshore platforms.
Choose AIS if you have ample room and want easier access for maintenance.
2. Budget Constraints
If cost is a concern, AIS offers a more economical solution.
If lifetime value and reliability are priorities, GIS might justify the investment.
3. Environmental Considerations
AIS is more eco-friendly due to the absence of SF₆.
GIS requires special handling and monitoring for SF₆, especially in regions with strict environmental regulations.
4. Application Type
AIS is well-suited for:
Power stations
Industrial zones
Rural substations
GIS is ideal for:
Urban substations
Underground systems
Critical infrastructure with limited space
Final Thoughts
Both Air-Insulated and Gas-Insulated Switchgear have their strengths and are engineered to serve specific needs. The right choice ultimately depends on your project requirements, site conditions, budget, and sustainability goals.
As a trusted supplier of high-performance switchgear, we can help you evaluate the best solution tailored to your project — ensuring safety, reliability, and efficiency.
7 notes
·
View notes
Text
Udaan by InAmigos Foundation: Elevating Women, Empowering Futures

In the rapidly evolving socio-economic landscape of India, millions of women remain underserved by mainstream development efforts—not due to a lack of talent, but a lack of access. In response, Project Udaan, a flagship initiative by the InAmigos Foundation, emerges not merely as a program, but as a model of scalable women's empowerment.
Udaan—meaning “flight” in Hindi—represents the aspirations of rural and semi-urban women striving to break free from intergenerational limitations. By engineering opportunity and integrating sustainable socio-technical models, Udaan transforms potential into productivity and promise into progress.
Mission: Creating the Blueprint for Women’s Self-Reliance
At its core, Project Udaan seeks to:
Empower women with industry-aligned, income-generating skills
Foster micro-entrepreneurship rooted in local demand and resources
Facilitate financial and digital inclusion
Strengthen leadership, health, and rights-based awareness
Embed resilience through holistic community engagement
Each intervention is data-informed, impact-monitored, and custom-built for long-term sustainability—a hallmark of InAmigos Foundation’s field-tested grassroots methodology.
A Multi-Layered Model for Empowerment

Project Udaan is built upon a structured architecture that integrates training, enterprise, and technology to ensure sustainable outcomes. This model moves beyond skill development into livelihood generation and measurable socio-economic change.
1. Skill Development Infrastructure
The first layer of Udaan is a robust skill development framework that delivers localized, employment-focused education. Training modules are modular, scalable, and aligned with the socio-economic profiles of the target communities.
Core domains include:
Digital Literacy: Basic computing, mobile internet use, app navigation, and digital payment systems
Tailoring and Textile Production: Pattern making, machine stitching, finishing techniques, and indigenous craft techniques
Food Processing and Packaging: Pickle-making, spice grinding, home-based snack units, sustainable packaging
Salon and Beauty Skills: Basic grooming, hygiene standards, customer interaction, and hygiene protocols
Financial Literacy and Budgeting: Saving schemes, credit access, banking interfaces, micro-investments
Communication and Self-Presentation: Workplace confidence, customer handling, local language fluency
2. Microenterprise Enablement and Livelihood Incubation
To ensure that learning transitions into economic self-reliance, Udaan incorporates a post-training enterprise enablement process. It identifies local market demand and builds backward linkages to equip women to launch sustainable businesses.
The support ecosystem includes:
Access to seed capital via self-help group (SHG) networks, microfinance partners, and NGO grants
Distribution of startup kits such as sewing machines, kitchen equipment, or salon tools
Digital onboarding support for online marketplaces such as Amazon Saheli, Flipkart Samarth, and Meesho
Offline retail support through tie-ups with local haats, trade exhibitions, and cooperative stores
Licensing and certification where applicable for food safety or textile quality standards
3. Tech-Driven Monitoring and Impact Tracking
Transparency and precision are fundamental to Udaan’s growth. InAmigos Foundation employs its in-house Tech4Change platform to manage operations, monitor performance, and scale the intervention scientifically.
The platform allows:
Real-time monitoring of attendance, skill mastery, and certification via QR codes and mobile tracking
Impact evaluation using household income change, asset ownership, and healthcare uptake metrics
GIS-based mapping of intervention zones and visualization of under-reached areas
Predictive modeling through AI to identify at-risk participants and suggest personalized intervention strategies
Human-Centered, Community-Rooted
Empowerment is not merely a process of economic inclusion—it is a cultural and psychological shift. Project Udaan incorporates gender-sensitive design and community-first outreach to create lasting change.
Key interventions include:
Strengthening of SHG structures and women-led federations to serve as peer mentors
Family sensitization programs targeting male allies—fathers, husbands, brothers—to reduce resistance and build trust
Legal and rights-based awareness campaigns focused on menstrual hygiene, reproductive health, domestic violence laws, and maternal care
Measured Impact and Proven Scalability
Project Udaan has consistently delivered quantifiable outcomes at the grassroots level. As of the latest cycle:
Over 900 women have completed intensive training programs across 60 villages and 4 districts
Nearly 70 percent of participating women reported an average income increase of 30 to 60 percent within 9 months of program completion
420+ micro-enterprises have been launched, 180 of which are now self-sustaining and generating employment for others
More than 5,000 indirect beneficiaries—including children, elderly dependents, and second-generation SHG members—have experienced improved access to nutrition, education, and mobility
Over 20 institutional partnerships and corporate CSR collaborations have supported infrastructure, curriculum design, and digital enablement.
Partnership Opportunities: Driving Collective Impact
The InAmigos Foundation invites corporations, philanthropic institutions, and ecosystem enablers to co-create impact through structured partnerships.
Opportunities include:
Funding the establishment of skill hubs in high-need regions
Supporting enterprise starter kits and training batches through CSR allocations
Mentoring women entrepreneurs via employee volunteering and capacity-building workshops
Co-hosting exhibitions, market linkages, and rural entrepreneurship fairs
Enabling long-term research and impact analytics for policy influence
These partnerships offer direct ESG alignment, brand elevation, and access to inclusive value chains while contributing to a model that demonstrably works.
What Makes Project Udaan Unique?

Unlike one-size-fits-all skilling programs, Project Udaan is rooted in real-world constraints and community aspirations. It succeeds because it combines:
Skill training aligned with current and emerging market demand
Income-first design that integrates microenterprise creation and financial access
Localized community ownership that ensures sustainability and adoption
Tech-enabled operations that ensure transparency and iterative learning
Holistic empowerment encompassing economic, social, and psychological dimensions
By balancing professional training with emotional transformation and economic opportunity, Udaan represents a new blueprint for inclusive growth.
From Promise to Power
Project Udaan, driven by the InAmigos Foundation, proves that when equipped with tools, trust, and training, rural and semi-urban women are capable of becoming not just contributors, but catalysts for socio-economic renewal.
They don’t merely escape poverty—they design their own systems of progress. They don’t just participate—they lead.
Each sewing machine, digital training module, or microloan is not a transaction—it is a declaration of possibility.
This is not charity. This is infrastructure. This is equity, by design.
Udaan is not just a program. It is a platform for a new India.
For partnership inquiries, CSR collaborations, and donation pathways, contact: www.inamigosfoundation.org/Udaan Email: [email protected]
3 notes
·
View notes
Text
Predicting Employee Attrition: Leveraging AI for Workforce Stability

Employee turnover has become a pressing concern for organizations worldwide. The cost of losing valuable talent extends beyond recruitment expenses—it affects team morale, disrupts workflows, and can tarnish a company's reputation. In this dynamic landscape, Artificial Intelligence (AI) emerges as a transformative tool, offering predictive insights that enable proactive retention strategies. By harnessing AI, businesses can anticipate attrition risks and implement measures to foster a stable and engaged workforce.
Understanding Employee Attrition
Employee attrition refers to the gradual loss of employees over time, whether through resignations, retirements, or other forms of departure. While some level of turnover is natural, high attrition rates can signal underlying issues within an organization. Common causes include lack of career advancement opportunities, inadequate compensation, poor management, and cultural misalignment. The repercussions are significant—ranging from increased recruitment costs to diminished employee morale and productivity.
The Role of AI in Predicting Attrition
AI revolutionizes the way organizations approach employee retention. Traditional methods often rely on reactive measures, addressing turnover after it occurs. In contrast, AI enables a proactive stance by analyzing vast datasets to identify patterns and predict potential departures. Machine learning algorithms can assess factors such as job satisfaction, performance metrics, and engagement levels to forecast attrition risks. This predictive capability empowers HR professionals to intervene early, tailoring strategies to retain at-risk employees.
Data Collection and Integration
The efficacy of AI in predicting attrition hinges on the quality and comprehensiveness of data. Key data sources include:
Employee Demographics: Age, tenure, education, and role.
Performance Metrics: Appraisals, productivity levels, and goal attainment.
Engagement Surveys: Feedback on job satisfaction and organizational culture.
Compensation Details: Salary, bonuses, and benefits.
Exit Interviews: Insights into reasons for departure.
Integrating data from disparate systems poses challenges, necessitating robust data management practices. Ensuring data accuracy, consistency, and privacy is paramount to building reliable predictive models.
Machine Learning Models for Attrition Prediction
Several machine learning algorithms have proven effective in forecasting employee turnover:
Random Forest: This ensemble learning method constructs multiple decision trees to improve predictive accuracy and control overfitting.
Neural Networks: Mimicking the human brain's structure, neural networks can model complex relationships between variables, capturing subtle patterns in employee behavior.
Logistic Regression: A statistical model that estimates the probability of a binary outcome, such as staying or leaving.
For instance, IBM's Predictive Attrition Program utilizes AI to analyze employee data, achieving a reported accuracy of 95% in identifying individuals at risk of leaving. This enables targeted interventions, such as personalized career development plans, to enhance retention.
Sentiment Analysis and Employee Feedback
Understanding employee sentiment is crucial for retention. AI-powered sentiment analysis leverages Natural Language Processing (NLP) to interpret unstructured data from sources like emails, surveys, and social media. By detecting emotions and opinions, organizations can gauge employee morale and identify areas of concern. Real-time sentiment monitoring allows for swift responses to emerging issues, fostering a responsive and supportive work environment.
Personalized Retention Strategies
AI facilitates the development of tailored retention strategies by analyzing individual employee data. For example, if an employee exhibits signs of disengagement, AI can recommend specific interventions—such as mentorship programs, skill development opportunities, or workload adjustments. Personalization ensures that retention efforts resonate with employees' unique needs and aspirations, enhancing their effectiveness.
Enhancing Employee Engagement Through AI
Beyond predicting attrition, AI contributes to employee engagement by:
Recognition Systems: Automating the acknowledgment of achievements to boost morale.
Career Pathing: Suggesting personalized growth trajectories aligned with employees' skills and goals.
Feedback Mechanisms: Providing platforms for continuous feedback, fostering a culture of open communication.
These AI-driven initiatives create a more engaging and fulfilling work environment, reducing the likelihood of turnover.
Ethical Considerations in AI Implementation
While AI offers substantial benefits, ethical considerations must guide its implementation:
Data Privacy: Organizations must safeguard employee data, ensuring compliance with privacy regulations.
Bias Mitigation: AI models should be regularly audited to prevent and correct biases that may arise from historical data.
Transparency: Clear communication about how AI is used in HR processes builds trust among employees.
Addressing these ethical aspects is essential to responsibly leveraging AI in workforce management.
Future Trends in AI and Employee Retention
The integration of AI in HR is poised to evolve further, with emerging trends including:
Predictive Career Development: AI will increasingly assist in mapping out employees' career paths, aligning organizational needs with individual aspirations.
Real-Time Engagement Analytics: Continuous monitoring of engagement levels will enable immediate interventions.
AI-Driven Organizational Culture Analysis: Understanding and shaping company culture through AI insights will become more prevalent.
These advancements will further empower organizations to maintain a stable and motivated workforce.
Conclusion
AI stands as a powerful ally in the quest for workforce stability. By predicting attrition risks and informing personalized retention strategies, AI enables organizations to proactively address turnover challenges. Embracing AI-driven approaches not only enhances employee satisfaction but also fortifies the organization's overall performance and resilience.
Frequently Asked Questions (FAQs)
How accurate are AI models in predicting employee attrition?
AI models, when trained on comprehensive and high-quality data, can achieve high accuracy levels. For instance, IBM's Predictive Attrition Program reports a 95% accuracy rate in identifying at-risk employees.
What types of data are most useful for AI-driven attrition prediction?
Valuable data includes employee demographics, performance metrics, engagement survey results, compensation details, and feedback from exit interviews.
Can small businesses benefit from AI in HR?
Absolutely. While implementation may vary in scale, small businesses can leverage AI tools to gain insights into employee satisfaction and predict potential turnover, enabling timely interventions.
How does AI help in creating personalized retention strategies?
AI analyzes individual employee data to identify specific needs and preferences, allowing HR to tailor interventions such as customized career development plans or targeted engagement initiatives.
What are the ethical considerations when using AI in HR?
Key considerations include ensuring data privacy, mitigating biases in AI models, and maintaining transparency with employees about how their data is used.
For more Info Visit :- Stentor.ai
2 notes
·
View notes
Text
Smart Switchgear in 2025: What Electrical Engineers Need to Know

In the fast-evolving world of electrical infrastructure, smart switchgear is no longer a futuristic concept — it’s the new standard. As we move through 2025, the integration of intelligent systems into traditional switchgear is redefining how engineers design, monitor, and maintain power distribution networks.
This shift is particularly crucial for electrical engineers, who are at the heart of innovation in sectors like manufacturing, utilities, data centers, commercial construction, and renewable energy.
In this article, we’ll break down what smart switchgear means in 2025, the technologies behind it, its benefits, and what every electrical engineer should keep in mind.
What is Smart Switchgear?
Smart switchgear refers to traditional switchgear (devices used for controlling, protecting, and isolating electrical equipment) enhanced with digital technologies, sensors, and communication modules that allow:
Real-time monitoring
Predictive maintenance
Remote operation and control
Data-driven diagnostics and performance analytics
This transformation is powered by IoT (Internet of Things), AI, cloud computing, and edge devices, which work together to improve reliability, safety, and efficiency in electrical networks.
Key Innovations in Smart Switchgear (2025 Edition)
1. IoT Integration
Smart switchgear is equipped with intelligent sensors that collect data on temperature, current, voltage, humidity, and insulation. These sensors communicate wirelessly with central systems to provide real-time status and alerts.
2. AI-Based Predictive Maintenance
Instead of traditional scheduled inspections, AI algorithms can now predict component failure based on usage trends and environmental data. This helps avoid downtime and reduces maintenance costs.
3. Cloud Connectivity
Cloud platforms allow engineers to remotely access switchgear data from any location. With user-friendly dashboards, they can visualize key metrics, monitor health conditions, and set thresholds for automated alerts.
4. Cybersecurity Enhancements
As devices get connected to networks, cybersecurity becomes crucial. In 2025, smart switchgear is embedded with secure communication protocols, access control layers, and encrypted data streams to prevent unauthorized access.
5. Digital Twin Technology
Some manufacturers now offer a digital twin of the switchgear — a virtual replica that updates in real-time. Engineers can simulate fault conditions, test load responses, and plan future expansions without touching the physical system.
Benefits for Electrical Engineers
1. Operational Efficiency
Smart switchgear reduces manual inspections and allows remote diagnostics, leading to faster response times and reduced human error.
2. Enhanced Safety
Early detection of overload, arc flash risks, or abnormal temperatures enhances on-site safety, especially in high-voltage environments.
3. Data-Driven Decisions
Real-time analytics help engineers understand load patterns and optimize distribution for efficiency and cost savings.
4. Seamless Scalability
Modular smart systems allow for quick expansion of power infrastructure, particularly useful in growing industrial or smart city projects.
Applications Across Industries
Manufacturing Plants — Monitor energy use per production line
Data Centers — Ensure uninterrupted uptime and cooling load balance
Commercial Buildings — Integrate with BMS (Building Management Systems)
Renewable Energy Projects — Balance grid load from solar or wind sources
Oil & Gas Facilities — Improve safety and compliance through monitoring
What Engineers Need to Know Moving Forward
1. Stay Updated with IEC & IEEE Standards
Smart switchgear must comply with global standards. Engineers need to be familiar with updates related to IEC 62271, IEC 61850, and IEEE C37 series.
2. Learn Communication Protocols
Proficiency in Modbus, DNP3, IEC 61850, and OPC UA is essential to integrating and troubleshooting intelligent systems.
3. Understand Lifecycle Costing
Smart switchgear might have a higher upfront cost but offers significant savings in maintenance, energy efficiency, and downtime over its lifespan.
4. Collaborate with IT Teams
The line between electrical and IT is blurring. Engineers should work closely with cybersecurity and cloud teams for seamless, secure integration.
Conclusion
Smart switchgear is reshaping the way electrical systems are built and managed in 2025. For electrical engineers, embracing this innovation isn’t just an option — it’s a career necessity.
At Blitz Bahrain, we specialize in providing cutting-edge switchgear solutions built for the smart, digital future. Whether you’re an engineer designing the next big project or a facility manager looking to upgrade existing systems, we’re here to power your progress.
#switchgear#panel#manufacturer#bahrain25#electrical supplies#electrical equipment#electrical engineers#electrical
6 notes
·
View notes
Text
1. Structural Foundations of the SMART Visa Program
1.1 Legislative Architecture
The SMART Visa operates under:
Royal Decree on SMART Visa B.E. 2561 (2018)
Thailand 4.0 Economic Policy Framework
BOI Investment Promotion Act (No. 4) B.E. 2560
1.2 Interagency Governance
Primary Authority: Board of Investment (BOI)
Implementation Partners:
Immigration Bureau (visa issuance)
Ministry of Digital Economy and Society (tech qualifications)
Ministry of Higher Education (academic validation)
2. Category-Specific Qualification Matrix
2.1 SMART-T (Specialists)
Technical Thresholds:
Salary Floor: THB 200,000/month (USD 5,800)
Experience Validation:
5+ years in qualifying field
Patent holders given priority
PhD waivers for certain disciplines
Industry Prioritization:
Biotechnology (Gene Therapy, Precision Medicine)
Advanced Manufacturing (Robotics, 3D Printing)
Digital Infrastructure (AI, Quantum Computing)
2.2 SMART-I (Investors)
Due Diligence Process:
Phase 1: BOI business plan review (45 days)
Phase 2: Anti-money laundering clearance
Phase 3: Investment tracing audit
2.3 SMART-E (Entrepreneurs)
Startup Validation Framework:
Tier 1 Incubators: DEPA, Thai Venture Capital Association
Minimum Traction Metrics:
THB 10M ARR or
50,000 MAU or
Series A funding
Capital Requirements:
Bootstrapped: THB 600,000 liquid
Funded: Minimum THB 5M valuation
3. Advanced Application Mechanics
3.1 Document Authentication Protocol
Educational Credentials:
WES or IQAS evaluation for non-Thai degrees
Notarized Thai translations
Employment History:
Social security cross-verification
Reference checks with former employers
3.2 Technical Review Process
Stage 1: Automated system screening
Stage 2: BOO specialist committee review
Stage 3: Final approval by Deputy Secretary-General
4. Privilege Structure and Limitations
4.1 Work Authorization Scope
Permitted Activities:
Primary employment with sponsor
Consulting (max 20% time allocation)
Academic collaboration
Prohibited Activities:
Local employment outside specialty
Unapproved commercial research
Political activities
4.2 Dependent Provisions
Spousal Work Rights:
General employment permitted
No industry restrictions
Child Education:
International school subsidies
University admission preferences
4.3 Mobility Advantages
Fast-Track Immigration:
Dedicated SMART lanes at 6 major airports
15-minute clearance guarantee
Re-entry Flexibility:
Unlimited exits without visa voidance
Automatic 48-hour grace period
5. Compliance and Renewal Dynamics
5.1 Continuous Eligibility Monitoring
Quarterly Reporting:
Employment verification
Investment maintenance
Research output (for academics)
Annual Review:
Salary benchmark adjustment
Contribution assessment
5.2 Renewal Process
Documentation Refresh: Updated financials, health insurance
Performance Evaluation: Economic impact assessment
Fee Structure: THB 10,000 renewal fee + THB 1,900 visa stamp
5.3 Grounds for Revocation
Material Changes: Employment termination, investment withdrawal
Compliance Failures: Missed reporting, legal violations
National Security Concerns: Classified determinations
6. Comparative Analysis with Global Competitors
6.1 Strategic Advantages
Tax Optimization: 17% flat rate option
Research Incentives: BOO matching grants
Commercialization Support: THBI co-investment
7. Emerging Policy Developments
7.1 2024 Program Enhancements
Blockchain Specialist Category (Q3 rollout)
Climate Tech Fast-Track (Carbon credit linkage)
Regional Expansion: Eastern Economic Corridor focus
7.2 Pending Legislative Changes
Dual Intent Provision: PR application without visa surrender
Skills Transfer Mandate: Local training requirements
Global Talent Pool: Reciprocal agreements in negotiation
8. Practical Application Strategies
8.1 Pre-Application Optimization
Salary Structuring: Base vs variable compensation
Patent Portfolio Development: Thai IP registration
Local Network Building: Thai professional associations
8.2 Post-Approval Planning
Tax Residence Strategy: 180-day calculations
Asset Protection: Thai holding company formation
Succession Planning: Will registration requirements
9. Critical Risk Factors
9.1 Common Rejection Reasons
Document Discrepancies: Date inconsistencies
Qualification Gaps: Unrecognized certifications
Financial Irregularities: Unverified income streams
9.2 Operational Challenges
Banking Restrictions: Foreign account limitations
Healthcare Access: Specialty treatment approvals
Cultural Integration: Workplace adaptation
10. Conclusion: Strategic Implementation Framework
For optimal SMART Visa utilization:
Pre-qualification Audit: 90-day preparation period
BOI Engagement: Pre-submission consultation
Compliance Infrastructure: Digital reporting systems
Contingency Planning: Alternative category eligibility
#thailand#immigration#immigrationinthailand#thailandvisa#thaivisa#visa#thai#thailandsmartvisa#smartvisa#smartvisainthailand#thaismartvisa
2 notes
·
View notes
Text
Revolutionizing DeFi Trading: STON.fi x Wisdomise Integration

The DeFi trading landscape is evolving, and traders are constantly looking for smarter, faster, and more efficient ways to execute their strategies. STON.fi, the leading decentralized exchange (DEX) on The Open Network (TON), is at the forefront of this innovation, now integrating with Wisdomise to bring automated AI-powered trading to DeFi.
This collaboration eliminates manual trading struggles, allowing traders to set up intelligent, automated strategies that operate 24/7 with risk management, real-time market insights, and multi-asset trading.
What This Means for Traders
Traditional DeFi trading requires constant monitoring, timing the market perfectly, and managing risk manually. With STON.fi’s integration with Wisdomise, these challenges become a thing of the past.
Now, traders can:
Automate trading strategies using AI-powered decision-making.
Set Take Profit & Stop Loss orders for precise risk management.
Diversify positions effortlessly across multiple assets.
Trade directly on STON.fi with seamless liquidity access.
This integration allows users to trade with confidence, knowing their strategies are being executed efficiently without manual effort.
$10,000 Auto Trader Launch Tournament
To celebrate this major breakthrough in DeFi trading, Wisdomise is launching a $10,000 competition for traders who want to test their skills with AI-driven trading.
The tournament will reward top traders based on trading volume, with USDt prizes and exclusive Pro+ subscriptions for the best performers.
STON.fi’s Market Leadership in the TON Ecosystem
STON.fi’s growth has been nothing short of phenomenal, maintaining its position as the #1 DEX on TON with record-breaking adoption and trading volume.
Here’s why it continues to lead:
$5 billion+ in all-time trading volume – the highest among TON DEXs.
4 million+ unique wallets – covering 81% of all DEX users on TON.
25,800+ daily active users, with 16,000+ making multiple trades daily.
8,000+ new users joining daily – the fastest growth rate in the ecosystem.
700+ trading pairs actively traded daily.
Key performance highlights:
$425 million+ average monthly trading volume in 2024.
$370 million peak TVL (Total Value Locked).
50-80x increase in trading volume and TVL in the past year.
$5.2 billion+ total trading volume to date.
20 million+ transactions processed on STON.fi.
This isn’t just growth—it’s a complete market transformation, proving STON.fi’s dominance in the TON DeFi space.
The Future of Trading Starts Now
With the STON.fi x Wisdomise integration, DeFi traders now have an edge like never before—AI-driven automation, advanced risk management, and direct access to deep liquidity.
STON.fi is pushing the boundaries of decentralized trading, making it more accessible, intelligent, and efficient than ever.
3 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
The job of a SOC Analyst
The #1 thing people ask me about is what I do for a job.
I'm a tier 1 SOC Analyst and I'm currently training to do some Cyber Threat Intelligence.
I will explain in detail what I do on a daily basis and why I've decided to do this job... And the negatives.
First of all, what's a SOC. SOC stands for "security operations center". It's a place (in my case virtual as I'm full remote) where a group of people, divided by experience and area of expertise, do the following:
Monitor the activities going on the customer's network or endpoints(= every device connected to the network);
Assess and mitigate alerts coming from the network and/or the endpoint of the client -> These tools send alerts that need to be evaluated and mitigated/responded in a certain amount of time (it depends on the SOC and the type of alert, generally I can assume an amount of time from 15 to 30 minutes per alert. Which is not that much;
Investigate cybersecurity incidents -> the SOC also analyses the kind of "incident" that happens in deep detail by analysing malware, spam emails, the behaviour of users and so on;
If the SOC is big/mature enough there could be some sort of prevention of cybersecurity issues, generally we talk about threat hunting (here for more information on that) and cyber threat intelligence (gathering information from various sources to produce a report about the potential attackers considering also the characteristic of the customer's company such as the size, the geographical area of operations, media exposure, geopolitical issues and what they do - doing this for a bank is different than doing it for a industry)
There are also other functions (such as we have a Security Architect that prepares a personalised solution for each client).
I know what you're thinking. But the AI...
No, they cannot do my job, as the ability of a human to notice patterns and correlate the information among various sources is unique. I memorised, with time, the usual activities my customers do, therefore I can interpret the user actions even with limited sources. And this is just one example.
Soc analysts are roughly divided in three "categories", always keep in mind that every SOC is different and has its own internal rules, that are not to be divulged. This is the rough division I've learned studying cybersecurity and NOT my organisation division.
Tier 1 Analysts are the one that monitors the traffic and activities I've mentioned before. They triage the alerts and if something deserves more investigation or can be discarded. They often perform simple actions of remediation of incidents.
Tier 2 Analysts are the ones that go deeper - they collect malware samples from the incident and analyse it, investigate and remediate more complex security incidents.
Tier 3 Analysts perform more active prevention duties like threat hunting and vulnerability assessments.
Some sources put intelligence activity on the tier 3, others consider it a different activity from the scenario I've described. If a SOC is big enough they might have their own intelligence team separated from the "regular" soc analysts. The rigidity of these roles can vary, as you probably got from my own duties.
On the top we have a SOC manager to coordinate the activities I've described and security architects that design the solution (although the deployment of these solutions can be delegated to the analysts, since we also have to monitor how well these perform).
All these people are usually referred as "blue teamers" btw, which are the ones that perform defensive actions.
A company can have a red team (basically they attack the customer to gain information that the blue team will use to improve their activities). I actually wanted to be a red teamer at first, since it's considered the "cooler" job.
Ok, got it. Now explain to me how you got there since I've never heard anything about this before.
I have a friend that's a system engineer and recommended this job to me.
I studies physics at university but I failed (in my country physics include some computer science classes btw) and I had some related experience I won't share for privacy reasons. No I'm not a criminal lol.
I then started studying - did a bootcamp and got a couple of certifications. Then I got my job.
However. Generally you get a degree in computer science or software engineering, and some universities offer cybersecurity degrees. Unfortunately I cannot tell you what to pick as every university has its own program and I cannot help you with that.
Certifications are a big part of my job unfortunately - mostly because due to how fast it goes you absolutely need to be "on top". It's annoying, yes, I hate it.
However. Consider that once you're hired you definitely will get them paid by your employer - at least in Europe this is on them(idk about the US), but you need some knowledge of cybersecurity to start.
Since some of them are stupid expensive I 100% recommend the compTIA ones. They're basics and respected worldwide. A+, Network+ and Security+ are basics, vendor neutral (which doesn't tie you to a particular "source", as every company works differently), and is relatively cheap (~300€).
Remember that I had previous experience so no one cares that I don't have a degree - I do however and I hope that in the future I will be able to "fix" this.
Great. How do I know if I'm good for this job?
This is on you. However:
One important thing if you don't live in an English speaking country is a good attitude towards foreign languages. I speak 5 for example, but it's an hobby I do since I was a teen;
Can you manage stress? A SOC is a fast paced environment, and you have a limited time to deal with whatever gets thrown at you. You have 15 to 30 minutes to deal with an alert and make a decision. Can you do that without panicking, crying or throwing a tantrum?
Are you a fast learner? You need to learn quickly how to do things, since the tools we use are quite complicated.
Are you willing to work on shifts, Saturdays, Sundays, festivities included? A lot of people can't cope with this and it's fine because it's a massacre. The job is so stressful to the point a lot of people leave cybersecurity because of it. Do not underestimate it, please.
How good are you at remembering random information and making correlations? Because I can remember random bits of information that no one ever thinks of it and it's one of my greatest strengths.
You need to do teamwork and be good with people, customers and so on - you have to explain complicated things you probably read in another language to people that don't know anything about what you do. It's more difficult than most people think.
Procedures are everything here - and for good reasons.
I think this is it.
Money.
USA avg salary: 74 307$ (Glassdoor)
France avg salary: 42 000€ (Glassdoor)
UK avg salary: 28 809 £ (Glassdoor)
There are random numbers I've found online(and with a lot of discrepancies). Consider that you MUST negotiate your salary, and that in certain places you get paid more if you work out of the usual 8-19 work shift. Obv since I live in a different place I cannot tell you if it's worth it - you do your own calculations.
But that's beyond the purpose of this post.
13 notes
·
View notes
Text
The Trump administration is replacing some of the nation’s top tech officials with Silicon Valley talent tied to Elon Musk and companies associated with Peter Thiel. This could make it easier for Musk’s so-called Department of Government Efficiency (DOGE) engineers to gain access to sensitive government systems, sources and experts say.
Over the past few weeks, several Musk-aligned tech leaders have been installed as chief information officers, or CIOs, at the Office of Management and Budget, the Office of Personnel Management, and the Department of Energy. CIOs manage an agency’s information technology and oversee access to sensitive databases and systems, including classified ones.
"Federal agency CIOs have authority over all agency asset management, which includes software used to monitor civil servant laptops and phones,” a former Biden official with firsthand knowledge of a CIO’s capabilities tells WIRED. “CIO shops manage and control IT access to all agency databases and systems, and have oversight over all the IT contracts per FITARA [the Federal Information Technology Acquisition Reform Act]. They have lots of IT budget and head count that Musk might want to take over. In agencies, CIOs are functionally as powerful as OIGs [the Office of Inspectors General].”
So far, these new CIOs have all been appointed. At most agencies, however, the position is filled by career civil servants. Last week, the Office of Personnel Management (OPM) issued a new memo that would reclassify those nonpartisan roles, essentially allowing the Trump administration to replace CIOs at will in order to better carry out its agenda. The appointments made so far may serve as an indicator of who will take over IT departments throughout the government once the order goes into effect.
Late last month, Gregory Barbaccia was hired as the federal chief information officer, a position within the Office of Management and Budget (OMB), which oversees the performance of all federal agencies and administers the budget. Barbaccia’s LinkedIn shows that he’s spent most of his career in tech, including a 10-year stint at Palantir. When Barbaccia left Palantir in 2020, his role was head of intelligence and investigations. Palantir CEO Alex Karp recently referenced the “disruption” of DOGE’s cost-cutting initiatives and said, “Whatever is good for America will be good for Americans and very good for Palantir.” The company has made billions in government contracts. Palantir shares hit an all-time high last week after a better-than-expected quarterly earnings report. Last week, Palantir announced plans to integrate Musk’s large language model Grok with Palantir’s AI platform.
Ryan Riedel was installed as chief information officer of the Department of Energy (DOE) last week, according to reports from E&E News. At the DOE specifically, the CIO oversees all technology operations as well as cybersecurity initiatives, in addition to elements of the National Nuclear Security Administration, which oversees the US’s nuclear weapons stockpiles. Riedel reportedly worked as a “lead network security engineer” at Musk’s rocket company SpaceX.
While not every new CIO has direct ties to Musk or Palantir, they do all have deep Silicon Valley connections. Greg Hogan is now the CIO of OPM, which is essentially the US government’s HR department. Hogan has been alleged to be a special government employee and not a full-time OPM employee, according to a recent lawsuit. Hogan previously worked at Comma.AI, a company that builds automated driving software. Musk allegedly floated a job offer to Comma.AI’s former CEO George Hotz in 2015 to work on self-driving tech, but the deal reportedly soured after Hotz claimed his self-driving tech was superior to Tesla’s.
OPM confirmed that Hogan now serves as CIO. OMB and DOE did not immediately respond to requests for comment from WIRED.
The reclassification of the CIO role doesn’t affect current CIOs, but their job security is uncertain. In January, Trump signed an executive order that could remove civil servant protections, turning potentially thousands of employees into “at will” workers. By doing so, the Trump administration would make it easier to fire career civil servants in what it calls “policy-influencing” roles. In a memo last week, Charles Ezell, acting OPM director, says that the CIO reclassification is due to the office’s increased influence on policy across agencies.
“No longer the station of impartial and apolitical technocrats, the modern agency CIO role demands policy-making and policy-determining capabilities across a range of controversial political topics,” Ezell wrote.
Last week, federal workers’ unions sued the White House, arguing that the order oversteps Trump’s presidential authority.
Already, Musk associates have infiltrated a number of government agencies. WIRED has extensively reported on the DOGE staffers, many of them young, with links to Musk’s various companies and little to no government experience, gaining access to sensitive systems at a number of agencies, including the Treasury Department. DOGE is being led by a variety of Musk associates, including Steve Davis and Nicole Hollander, who helped the billionaire acquire Twitter in 2022. Thomas Shedd, a former Tesla engineer, now heads Technology Transformation Services, which is housed within the General Services Administration.
Are you a current or former government worker with insight into what's going on? We'd like to hear from you. Using a nonwork phone or computer, contact the reporter securely using a personal device on Signal at makenakelly.32.
4 notes
·
View notes
Text
Why the Low Voltage Switchgear Market is Booming in 2025?

The low voltage switchgear market is growing rapidly in 2025 due to growth in electricity consumption, development of intelligent devices, and a strong emphasis on sustainability. Energy efficiency, digital transformation, and security are critical for industries and businesses, which leads to a high demand for new, robust, and intelligent switchgear. This article will discuss key drivers of market growth, emerging trends, and their impact on businesses and industries globally.
1. The Growing Demand for Electricity
Over the past few decades, the increasing demand for efficiency in power distribution systems has become ever imminent with the rise of general energy consumption. Rapid urban expansion, industrial development, and the emergence of data centers have been some of the major driving forces boosting the demand for low-voltage switchgear.
Global Electricity Demand on the Rise:
· The IEA projects electricity demand in developing nations will rise at a rate of 4% each year, as consumption steadily climbs.
· Data facilities and cloud computing require relentless power sources, amplifying the need for resilient switching equipment solutions capable of sustaining operations.
· The proliferation of electric vehicle charging points is compelling utilities to renovate distribution networks, ensuring functionality can accommodate increased demand.
Modernization spreads as industries broaden their scope, making electrically-reliable infrastructure an imperative; low voltage switchgear has become integral to conveying energy throughout the grid in a secure and effective manner.
2. Smart & Digital Switchgear: The Industry’s Future
Traditional switchgear technology has evolved rapidly with the integration of intelligent networking capabilities, making electrical distribution safer, more efficient, and easier to monitor remotely. The new digital switchgear incorporates IoT, AI, and cloud-based monitoring solutions to provide real-time insight into energy usage. This allows businesses to proactively optimize performance and reduce costs through more proactive maintenance strategies.
Major Developments in Intelligent Switchgear by 2025:
✅Online Sensor Networks: Constant telemetry from devices throughout the system helps pinpoint potential weaknesses before failures occur.
✅Self-learning Circuitry: AI-powered hardware and software automatically analyze usage patterns to forecast repairs, minimize outages, and heighten uptime.
✅Wireless Remote Management: Mobile apps and web dashboards give administrators off-site control over power flows to streamline usage according to need.
✅Modular Construction: Interchangeable, compact components facilitate scaling and retrofitting within varied infrastructure environments.
The shift toward automated smart grids and Industry 4.0 production is substantially contributing to the booming market for intelligent switchgear solutions. Widespread installation of these next-generation systems will transform electrical distribution networks.
3. Rising Emphasis on Energy Efficiency & Sustainability
Governments and industries worldwide have increasingly pushed for greener, more energy-efficient power solutions in recent years. This has led electrical equipment manufacturers to develop eco-friendly switchgear technologies that considerably minimize energy loss during transmission and help reduce overall carbon footprints.
Sustainable Advancements in Low Voltage Switchgear Design:
Alternative gases to SF6: Traditional switchgear commonly uses SF6 due to its insulating and arc-quenching capabilities, however this gas has an extremely high global warming potential. Many switchgear producers have since designed SF6-free solutions that substitute the highly potent SF6 with other gases that are safer for the environment.
Energy-Efficient Designs: Optimizing circuitry and components has allowed switchgear to conduct electricity with negligible power loss, enabling connected systems to leverage nearly every watt of power. Careful engineering further trims excess material use and redundant parts.
Renewable Energy Integration: Low voltage switchgear has become increasingly vital in smoothly and reliably integrating power from solar arrays and wind farms into existing electrical networks. Without robust switchgear management, it would be difficult for clean energy sources to efficiently feed power onto transmission lines.
With the implementation of more stringent energy performance mandates in countries worldwide, businesses have sound business reasons for upgrading outdated switchgear infrastructure with advanced low loss solutions both to adhere to regulations and lower long-term energy expenditures.
4. Increasing Investments in Infrastructure & Industrialization
Governments and private investors alike are pouring billions into ambitious infrastructure projects around the world, generating skyrocketing demand for reliable low voltage switchgear solutions. From towering commercial skyscrapers to sprawling industrial complexes, and expanding metro networks to bustling international airports — countless utilities depend on robust yet cost-effective switching systems to ensure continuity of operations.
🔹 Key Infrastructure Drivers Stimulating Growth:
🏗️ Smart Cities Uplift Life: Sweeping investments in digital urbanization are revolutionizing everyday living through connected infrastructure that elevates efficiency.
🏭 Manufacturing Marvels: Production powerhouses across the globe are scaling new heights, intensifying the necessity for advanced low voltage distribution controls to support increased capacity.
🚆 Transportation Transformations: Rapid progress in rail electrification and proliferation of electric vehicles for land and air are necessitating increasingly resilient switchgear designs.
As global development marches forth, low voltage switchgear has become mission critical in enabling commercial and industrial progress through reliable power distribution. The worldwide infrastructure renaissance is cementing its importance for years to come.
5. Safety & Regulatory Compliance Are Driving Upgrades
Governments and regulatory bodies are increasingly implementing strict compliance standards to safeguard electrical infrastructure and minimize hazards, compelling upgrades across many industries. Potential calamities resulting from power faults or failures necessitate vigilance in maintaining reliable and resilient systems.
New Safety Regulations in 2025:
⚡ Updated IEC & NEC Standards: Stringent low voltage switchgear specifications mandated to bolster protection.
⚡ Arc Fault Protection Technology: Novel solutions critical to curb risks of electrical ignitions and incidents.
⚡ Mandatory Energy Audits: Organizations now required to optimize distribution for both personnel and operational efficiency through audits.
With approaching deadlines to satisfy evolving regulations, operators are proactively replacing outdated switchgear to conform with mounting compliance demands, contributing to an accelerating industry transformation.
6. The Rise of Data Centers & Digital Transformation
The digital sphere fundamentally relies upon data hubs that necessitate constant power and exceedingly reliable electric frameworks. As distributed computing, man-made brainpower, and IoT reception develop exponentially, ventures are putting vigorously in cutting edge low voltage switches to ensure their foundation from energy blackouts which could bring about gigantic budgetary misfortunes.
24/7 control is essential for operations yet breakdowns prompt critical money related setbacks. To guarantee uptime, focal points utilize auxiliary switches for extra dependability and security alongside far off checking abilities through IoT innovations which empower ongoing following and administration from anywhere. With worldwide distributed computing selection quickening at a quickening pace, interest for top notch low voltage switches arriving at new statures to guarantee frameworks stay online consistently.
7. Competitive Market & Technological Advancements
The low voltage switchgear sector has seen remarkable changes and fierce competition between prestigious brands. Manufacturers are pouring resources into innovation to craft smarter, smaller, and affordable switchboard alternatives.
🔹 Notable Advancements by 2025:
⚙️ Solid-state systems promise enhanced performance and lessened upkeep. Long and compound sentences mix with short ones.
⚙️ Remote accessibility through wireless means permits control and tracking from afar.
⚙️ Self-mending grids using AI to immediately spot and amend problems, maintaining dependable power seamlessly. Complex automation alleviates faults autonomously for maximum uptime.
Conclusion: The Future of Low Voltage Switchgear Looks Bright
Low Voltage Switchgear is forecasted to experience market growth in the year 2025 due to the growing electricity consumption in countries, the rising applications of smart technologies, the increased implementation of sustainability practices, the expansive growth in various industries, and safety regulations. As these industries are gradually moving to energy-efficient, AI-powered, and environmentally friendly switchgears, this demand is expected to increase further.
5 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Conscript Report: GG5UI

Division: Paramedic Corps
Condition: Experimental mRNA Drug Injection
Summary: Conscript GG5UI of the Paramedic Corps underwent an experimental mRNA drug injection aimed at enhancing resistance to UV light exposure. However, the procedure resulted in an unforeseen side effect, causing a significant alteration in skin pigmentation. GG5UI's skin now exhibits a light blue-gray hue, a deviation from the normative appearance.
Impact: The change in skin pigmentation poses several challenges, both physiological and psychological. Physiologically, the altered pigmentation may affect the individual's ability to regulate body temperature and protect against harmful UV radiation. Psychologically, the sudden change in appearance may lead to social stigma and emotional distress, impacting morale and performance.

Psychological Assessment Results:
Resilience: GG5UI demonstrates remarkable resilience in coping with the unexpected alteration in skin pigmentation. Despite facing challenges associated with the change in appearance, GG5UI maintains a positive outlook and remains determined to overcome obstacles.
Social Support: The support network provided by GG5UI's peers within the Paramedic Corps plays a crucial role in his psychological well-being. Many of his mates offer encouragement and express admiration for his unique appearance, fostering a sense of belonging and camaraderie.
Positive Perception: Contrary to initial concerns about potential social stigma, GG5UI's peers perceive the altered skin pigmentation as intriguing and even fashionable. This positive perception contributes to GG5UI's confidence and self-esteem, mitigating any negative effects on his mental health.
AI Counseling: GG5UI actively engages with AI counseling resources provided by the Paramedic Corps, utilizing virtual sessions to address any emotional challenges and receive guidance on coping strategies. The AI counseling system offers personalized support tailored to GG5UI's needs, enhancing his overall psychological resilience.
Current Status: Efforts to reverse the alteration in skin pigmentation have proven unsuccessful thus far. Medical experts continue to explore potential treatments and interventions to mitigate the side effects of the experimental drug. Meanwhile, GG5UI remains under close observation and support from medical personnel within the Paramedic Corps.

Recommendations:
Continued monitoring of GG5UI's physical and mental well-being.
Collaboration with medical researchers to explore alternative treatment options.
Provision of psychological support and counseling to address any emotional challenges arising from the change in appearance.
Review of protocols for administering experimental drugs to mitigate potential risks and side effects in future cases.
Conclusion: Conscript GG5UI's case highlights the inherent risks associated with experimental medical procedures. While the intended goal was to enhance resistance to UV light, the unexpected side effect underscores the importance of thorough research and careful consideration before implementing such interventions.
2 notes
·
View notes
Text
The Ultimate Guide to a "100% DONE-FOR-YOU" AI Traffic & Commission System for Affiliate Marketing
Affiliate marketing is a competitive arena where countless entrepreneurs battle for attention, aiming to convert clicks into commissions. Imagine a secret weapon designed to automate traffic generation and boost your affiliate marketing success. Enter the revolutionary concept of a "100% DONE-FOR-YOU" AI Traffic & Commission System.

Artificial Intelligence (AI) is rapidly transforming various industries, and affiliate marketing is no exception. AI algorithms can analyze vast amounts of data, predict user behavior, and even generate targeted content. A "100% DONE-FOR-YOU" AI Traffic & Commission System leverages AI's power to automate several crucial aspects of affiliate marketing, potentially streamlining your journey to success.
Get This offer - 100% DONE-FOR-YOU "AI" Traffic & Commission System - Get Great Results Promoting Affiliate Offers From ANY Affiliate Network Including WarriorPlus, Clickbank, Digistore24. Everything You NEED Is Included!
What Does "DONE-FOR-YOU" Mean?
The "DONE-FOR-YOU" aspect is what sets this system apart. Imagine a comprehensive marketing solution that handles the heavy lifting, freeing you to focus on promoting your chosen affiliate offers. Here’s a breakdown of what a "100% DONE-FOR-YOU" AI Traffic & Commission System might offer:
Automated Traffic Generation: This is the holy grail for affiliate marketers. The system could use AI to identify relevant keywords and target audiences, then employ various strategies (like social media marketing or search engine optimization) to drive targeted traffic to your affiliate landing pages.
Content Creation Powerhouse: Struggling with writer’s block or lacking time for content creation? An AI-powered system could analyze your chosen affiliate offer and generate compelling content – blog posts, social media captions, email marketing copy – that resonates with your target audience.
Landing Page Optimization: High-converting landing pages are essential for converting website visitors into paying customers. An AI system could build and optimize landing pages specifically designed to maximize conversions for your affiliate offers.
Data-Driven Insights: Data is crucial for understanding your audience and optimizing your campaigns. The system might provide valuable insights into website traffic, user behavior, and campaign performance, allowing you to make data-driven decisions for better results.
Affiliate Network Integration: The best systems should seamlessly integrate with popular affiliate networks like WarriorPlus, Clickbank, and Digistore24. This allows you to easily promote a wide range of affiliate offers without technical hurdles.
A Note of Caution: "100% DONE-FOR-YOU" with a Grain of Salt
While the concept of a fully automated system sounds appealing, it’s important to approach these claims with a healthy dose of skepticism. Here’s why:
The Human Touch Still Matters: Building trust and relationships with your audience is vital in affiliate marketing. While AI can automate tasks, your personal touch and expertise are irreplaceable.
Constant Tweaking is Necessary: Markets and user behavior are constantly evolving. A truly "DONE-FOR-YOU" system might lack the flexibility to adapt to these changes. Regular monitoring and adjustments might still be required.
Focus on Quality Over Quantity: While generating a lot of traffic is good, it’s even better to attract the right kind of traffic – users genuinely interested in the affiliate products you’re promoting.
Is a "100% DONE-FOR-YOU" AI Traffic & Commission System the Ultimate Solution?
Not necessarily. It’s more like a powerful tool that can significantly enhance your affiliate marketing efforts. However, success still depends on your strategic planning, marketing expertise, and ability to adapt to market trends.
Maximizing Your Success with AI-Powered Affiliate Marketing
Here’s how you can leverage AI to achieve greater success in affiliate marketing:
Choose the Right System: Carefully research and compare different "DONE-FOR-YOU" AI Traffic & Commission Systems. Look for systems that offer features relevant to your needs and integrate with your preferred affiliate networks.
Focus on Your Niche: AI can analyze data and identify target audiences, but your expertise can refine these insights. Focus on a specific niche where you can provide valuable content and insights alongside your affiliate promotions.
Maintain Editorial Control: While AI-generated content can be a great starting point, ensure you maintain editorial control over the final product. Your personal voice and brand message should be reflected in the content.
Track and Analyze Data: Don’t rely solely on the system’s insights. Utilize analytics tools to track your campaign performance and make data-driven decisions to optimize your efforts.
The Future of AI in Affiliate Marketing
Hyper-Personalized Marketing: AI will enable highly personalized marketing campaigns, tailoring content and offers to individual user preferences and behavior. This will lead to increased engagement and conversion rates.
Predictive Analytics: AI will be able to predict which users are most likely to convert, allowing you to focus your marketing efforts on the most promising leads.
Automated A/B Testing: Optimizing landing pages and marketing campaigns can be time-consuming. AI can automate A/B testing, constantly testing different variations and automatically adopting the most effective options.
Conclusion: AI - A Powerful Ally in the Affiliate Marketing Arena
The "100% DONE-FOR-YOU" AI Traffic & Commission System might not be a magic bullet, but it represents a significant advancement in affiliate marketing. By leveraging AI's power to automate tasks, generate content, and gain valuable insights, you can streamline your workflow, reach a wider audience, and ultimately boost your affiliate marketing success.
Get This offer - 100% DONE-FOR-YOU "AI" Traffic & Commission System - Get Great Results Promoting Affiliate Offers From ANY Affiliate Network Including WarriorPlus, Clickbank, Digistore24. Everything You NEED Is Included!
However, remember that AI is a tool, not a replacement for your expertise and strategic planning. Use AI to your advantage, but don’t lose sight of the importance of building trust with your audience and adapting to the ever-changing marketing landscape.
Ready to Unlock the Power of AI in Your Affiliate Marketing Journey?
Dive deeper into the world of "DONE-FOR-YOU" AI Traffic & Commission Systems. Research reputable providers, carefully evaluate their features, and choose the system that best complements your affiliate marketing goals. With the right combination of AI automation and your strategic expertise, you can conquer the affiliate marketing battlefield and achieve remarkable results.
2 notes
·
View notes