#network routing and switching assignment
Explore tagged Tumblr posts
Text
My Lesbian Epiphany
below the cut is a personal narrative about my experience realizing i'm a nonbinary lesbian, written for my college English credit course. from my instructor's positive feedback, i thought i would share it with the world somehow.
An average day of second grade was passing by quickly. I came home from school, zipped through my homework, and planted myself in front of the television. Remote in hand, I cycled through my channels of choice. Nothing new on Nickelodeon, nor anything interesting on Cartoon Network. In a last-ditch effort, I switched to the Disney Channel.
That’s when I saw her. Nested in a typical episode of Wizards of Waverly Place, a teen girl with beautiful, shoulder-length hair blazed with a blonde streak in her side-swept fringe tendrils. Her outfit, her accessories, her “cool rebel girl” attitude! I couldn’t help but lean in closer, entranced. With this character, named Stevie, I could not question it: I was attracted to other girls.
There were various other signs to come, for example, in middle school. On a day I was sporting a tank top that didn’t quite fit me, I walked the regular route to my next class with a classmate. She took notice of what I was wearing, with my bra exposed, and decided to comment.
“Luring in the boys, huh, ◼◼◼◼◼?”
I neglected a response, mainly out of sheer confusion and discomfort in this attention drawn to my body. The conversation faded awkwardly by the time I arrived at my awaiting classroom. Before entering, I peered around the hall of students, routinely seeking any sign of the cute girl that dominated my school day thoughts.
Inevitably, high school rolled around. Ninth grade began how my eighth grade ended, mute, panicked, and constantly overwhelmed. However, something was on the horizon. That fall, I was introduced to an artist online who became enamored with me shortly after becoming friends. A month later, we were officially dating. He was a transgender man named Noel; his name chosen himself based on a character of a game we bonded over. Noel spoke with kindness and gentleness between his staple jokes. He confided in me his own journey of healing from his traumatic childhood experiences and even told me, “You can heal, too. I’ll be by your side for this process.”
Is this…how it feels to be cared about? To actually feel loved by another person?
A warm sensation fluttered in my chest. A feeling of safety amidst the boiling storm that was my first day at my new Youth Therapy Day Program. In awe of this tender young man, I felt a spark. A lit match to pass the flame to my Rube-Goldberg machine of candles. I don’t have to be what’s been pushed on me. I don’t have to be that girl, nor a girl at all!
I trekked through my first three years of high school under my new identity as a transmasculine nonbinary bisexual. It was a backpack of textbooks taken off my aching shoulders. However, by junior year, something started to worm back into my mind and fester. Suddenly, walking through the halls of my high school became a warzone for my soft, girl-adoring self. The sway of bobbed hair on one girl, fluttering eyelashes bordering crystalline eyes of another. Every girl I would see was gorgeous, my poor heart was skipping beats every day for a week.
Skeptical, I posed myself a question. Well, what about that boy over there, with the short hair? My mindscape would pause, before lighting up and melting over the idea of a girl with that exact haircut. Blushing at the thought of this made-up person, I was in dire need of what I call, a lesbian epiphany. Between assignments, I couldn’t help but think, what’s wrong with me? Girls are so pretty, I can’t stop staring but…I can’t be a lesbian, I get angry when people call me my birthname. Being called “she” makes my skin crawl.
Do… any lesbians feel like this, too?
I labored over these thoughts until I dashed straight to Tumblr, seeking validation for my identity and pure curiosity. Clicking past the artwork of the sapphic couples I longed to be, I typed “nonbinary lesbian” into the search bar and pressed the return key. Sure enough, there were numerous lesbians sharing experiences, just like mine. Lesbians using “he,” “they,” and even new, custom pronouns. Lesbians with chosen names. Lesbians who experience gender dysphoria and even transition.
“Oh… Oh my god.”
Something deep within me clicked. It’s possible. It’s allowed.
“Oh god, this is it! I’m a lesbian!” I could only whisper it, but had I been home alone and uninhibited, I would’ve screamed it out. I would’ve yelled it as loud as my vocal cords would permit me. Truly, that’s the essence of a lesbian epiphany.
It’s been three years now since I realized I was a lesbian. Despite new struggles, I never knew how comforting that single label could be. I would’ve never accepted this part of me, had I stayed within the scope of what representation lesbians got in common media. Even Stevie, my awakening, was written to be in a relationship with her media’s female protagonist, yet only allowed in subtext and disclosed after the fact.
Even Noel, the assured, clement transgender man, had his epiphany, just like me. In fact, he experienced the same fascinations and realization that I did, within a year of each other. I know two other gender diverse lesbians who reached the same destination, now flourishing with their queer partners in the paradise of lesbianism. That’s a joke, of course. Truly, there’s no one true way to be a lesbian. Every person under this label is different, and there’s no reason to change that. The disclosure of raw, personal stories is the key to my own journey, my lesbian epiphany.
3 notes
·
View notes
Text
Streamlining Internal IT Support with a Smart Ticket Tracking Tool – A Deep Dive into Hoicko.com
In any forward-thinking company, technology is at the heart of everyday work. Technical problems, ranging from software bugs to hardware failures, pop up all the time. How well your in-house IT support team tackles these problems has a direct effect on how productive everyone is, no matter which department they're in.
This is exactly why a top ticket tracking management tool is so important.
Let's look at a typical situation where this really matters: managing internal IT support tickets. Think about your company's IT team. They have to deal with all sorts of tech problems that employees run into. These might be things like:
Resetting passwords
Fixing printers that aren't working
Installing new software
Dealing with servers that are down
Sorting out dodgy internet connections
Usually, these kinds of requests get handled through emails or casual chats on things like WhatsApp or Slack. But what happens then? Tickets get lost, responses are slow, nothing gets prioritised properly, and everyone ends up fed up.
Now picture this:
All these issues are getting dealt with in one place, through a ticket tracking system that you can tailor to your needs.
And that's what Hoicko.com is for.
Why Hoicko.com is the Ideal Ticket Tracking System for IT Support Teams
Hoicko.com offers a user-friendly, cloud-based ticket tracking and task management platform designed to streamline how teams handle internal requests. Here's how it revolutionises internal IT support:
1. Consolidated Request Handling
IT teams can now manage all support tickets conveniently from a single dashboard on Hoicko, eliminating the need to switch between multiple inboxes, chat threads, and spreadsheets. Each request is meticulously logged as a ticket, ensuring no issues are overlooked.
Example:
Imagine an employee from the finance department facing a software crash. Rather than directly emailing the IT head, they simply log the problem on Hoicko. The ticket is then automatically routed to the appropriate technician, monitored in real-time, and resolved promptly within the service level agreement (SLA).
2. Automated Ticket Routing and Progress Updates
With Hoicko, you can establish automated workflows to sort and direct tickets based on predefined criteria like department, urgency, or ticket category.
Additionally, you can set up automated progress notifications to keep employees informed about their issue's assignment, ongoing work, or resolution—thereby minimising constant back-and-forth communication.
3. Tailored Forms and Categories
IT problems come in all shapes and sizes. That's why Hoicko gives you the freedom to design your own forms and categories, mirroring the specific support needs within your organisation.
For example, you can categorise issues under:
Hardware
Software
Internet/Network
Data Recovery
User Access
This custom approach leads to more accurate classification, quicker identification of critical issues, and more organised reports.
4. Setting Priorities and Managing Service Level Agreements (SLAs)
Let's face it, in the world of IT, some problems demand immediate attention, while others can wait. Hoicko.com empowers you to tag issues with priority levels like Low, Medium, High, or Critical. You can also define clear deadlines for responses and resolutions (SLAs).
This way, a routine password reset won't consume the same resources as a critical server crash.
5. Analyzing Performance with Reports
Are your team's response times up to par? Which departments are logging the most requests? What issues keep coming back?
Hoicko's integrated analytics provide managers with a clear picture of these trends. They can spot bottlenecks, fine-tune resource distribution, and make informed decisions. By using data as a guide, your overall IT support strategy becomes much more effective.
6. Teamwork Makes the Dream Work: Notes & Collaboration
Hoicko is all about teamwork! Your IT folks can easily leave private notes on tickets, loop in other team members for their expertise, or escalate tricky issues, all without leaving the app. No more jumping between different tools or getting lost in endless chat threads. It's all right there, streamlined and simple.
7. Ticket Widget: Submitting Support Requests Made Super Easy
With Hoicko, you can pop a handy "Raise a Ticket" widget right on your company's internal website or portal. Employees won't even have to log in! They just fill out a quick form, and poof! The system takes it from there. This makes it a breeze for everyone, even those who aren't tech-savvy, to report issues without any headaches.
Real-World Example: From Chaos to Control
Imagine your company has 200 employees. Every day, about 15-20 of them run into IT problems. Trying to manage all that with just emails and spreadsheets? That's a recipe for madness! It's just not practical or manageable in the long run.
But with Hoicko, here's what happens:
Tickets get logged and organised instantly.
The right technicians are automatically notified and assigned.
Employees get real-time updates on what's happening.
Every single interaction is tracked and recorded.
Monthly reports help you spot trends and areas for improvement.
In just a few short weeks, your IT team will be working like a well-oiled machine, your employees will be happier, and those critical tech issues? They'll get solved without turning into a major drama. It's a win-win for everyone!
Why Hoicko Stands Out from the Crowd
What makes Hoicko.com a better choice than the rest? Unlike those one-size-fits-all ticketing solutions, Hoicko.com offers complete customisation, requires no coding, and is designed to fit seamlessly into your actual business processes. It doesn't matter if you're a fledgling startup, a growing SME, or a massive corporation; Hoicko grows right alongside you. It is the best ticket tracking tool in India. The real game-changer? You can forget about hiring expensive developers or struggling to learn complicated new software. Hoicko's intuitive drag-and-drop interface makes it incredibly user-friendly.
But that's not all! Hoicko packs in extra features, such as project tracking, task dependencies, customisable user permissions, and personalised dashboards based on roles. This means Hoicko is more than just a way to manage tickets; it's your central command centre for all your operational needs.
If your IT support team is still relying on those dusty old methods, it's time for an upgrade. Ticket tracking isn't a fancy extra anymore—it's essential for keeping your teams running smoothly, efficiently, and happily.
Discover how Hoicko.com can be your go-to partner for revolutionising your internal support operations. It's a tool that's adaptable, quick, and built with real users in mind.
👉 Head over to Hoicko.com to begin your complimentary trial and discover a whole new world of effortless internal support.
#hoicko#hoickotechnologies#hoickotech#hoickonocodeapp#software#tool#nocodeapp#BestTicketTrackingTool#BestTicketTRackingToolInIndia
0 notes
Text
Mobile Proxies Explained: Use Cases and Advantages by Proxy Lust, Inc.
🛰️ What Are Mobile Proxies?
A mobile proxy is an intermediary that uses IP addresses assigned by mobile carriers (e.g., 4G/5G LTE networks) to route your internet traffic. Unlike datacenter or residential proxies, mobile proxies are tied to real mobile devices, making them far less likely to be flagged, blocked, or banned during intensive tasks like data scraping or social automation.
These proxies rotate through a pool of mobile IPs, dynamically assigned by telecom providers, which helps mimic legitimate mobile user behavior.
📲 Why Mobile Proxies Matter in 2025
The digital landscape in 2025 is dominated by AI detection systems, geo-targeted content, and increasingly sophisticated anti-bot frameworks. This means:
Datacenter proxies are easier to detect.
Residential IPs still face bans on high-volume tasks.
Mobile proxies offer stealth, authenticity, and flexibility.
In short, mobile proxies are now an essential tool for marketers, researchers, cybersecurity professionals, and automation experts.
🧠 Key Advantages of Mobile Proxies
✅ 1. High Trust Score
Mobile IPs are considered extremely trustworthy by websites, apps, and APIs. Why? Because they belong to real mobile network operators and rotate naturally, like actual human users switching networks.
✅ 2. Automatic IP Rotation
Most mobile proxies auto-rotate every few minutes or based on actions, which prevents IP bans and throttling. It also simulates real-world mobile behavior better than any static IP can.
✅ 3. Bypass Geo-Restrictions
Mobile proxies can be location-specific, allowing users to simulate browsing from a precise city or country. This is especially useful for:
SEO monitoring
Ad verification
Accessing region-locked content
✅ 4. Unmatched Anonymity
Since mobile proxies are dynamic and used by real users, they provide better anonymity and privacy, making it difficult for websites to trace back your actions.
✅ 5. Effective for Social Media Management
If you’re managing multiple Instagram, TikTok, or Facebook accounts, mobile proxies are the safest option to avoid getting flagged or banned by social platforms that aggressively fight automation.
🔒 Choose the Right Provider
At Proxy Lust, Inc., we provide:
Real 4G/5G mobile proxies from ethical sources
Global targeting options
High uptime and fast rotation
Monthly or pay-as-you-go plans
✅ Explore our mobile proxies here →
Mobile proxies are no longer optional in 2025 — they are a core part of digital operations. Whether you’re scaling a business or automating research, they offer unparalleled privacy, authenticity, and reliability.
If you’re ready to take your proxy setup to the next level, get in touch with Proxy Lust, Inc. and explore our premium mobile proxy solutions.
0 notes
Text
Teams Calling License: Everything You Need to Know for Easy Microsoft Teams Phone Setup
Microsoft Teams has quickly become the go-to communication hub for businesses of all sizes. From video meetings to instant messaging, it does it all. But what if you want to make and receive phone calls using Teams? That’s where the Teams Calling License comes in.
In this article, we’ll break down what a Microsoft Teams Calling license is, how it works, and how HelloTeams simplifies the process with fast, affordable, and no-code solutions. If you're planning to ditch your legacy phone system and move to VoIP calling, this guide is your starting point.

What Is a Teams Calling License?
A Teams Calling license, also known as a Microsoft Teams Phone license, enables you to make and receive phone calls to traditional landline and mobile numbers directly from Microsoft Teams.
There are two parts to this setup:
Microsoft Teams Phone License – Enables PSTN (Public Switched Telephone Network) capability in Teams.
Calling Plan or Direct Routing Provider – Supplies the actual phone number and call routing system.
This combination allows your organization to use Teams as a full-featured cloud-based phone system.
Why Do You Need a Teams Calling License?
If your team is already using Microsoft 365 and Teams for meetings, chats, and collaboration, adding voice calling through Teams is a natural progression. A Teams Calling License turns Microsoft Teams into a complete VoIP business phone system, replacing outdated PBX setups.
Top benefits include:
📞 Make/receive calls from any device
🧑💼 Maintain a professional business number
🔄 Keep your existing phone numbers
🌍 Enable global communication
🧩 All-in-one platform for messaging, meetings, and calling
Types of Microsoft Teams Calling Licenses
1. Microsoft Teams Phone Standard License
This license enables VoIP calling within your organization but requires a separate Calling Plan or Direct Routing to make external calls.
2. Microsoft Teams Phone with Calling Plan
This includes both the license and Microsoft's own calling minutes and phone number. However, it’s limited to certain countries and often comes with higher pricing.
Why HelloTeams Is the Better Choice for Teams Calling Licenses
At HelloTeams, we provide a code-free, fast, and flexible way to activate your Teams Calling license and connect your business to the outside world—without needing expensive infrastructure or IT headaches.
Here’s why HelloTeams is the ideal partner for Teams Phone:
✅ Set up in under 15 minutes ✅ Competitive pricing across the US, UK, AU, and NZ ✅ No code or complex admin panels ✅ Port your existing business number ✅ Local support and global service
We handle the license provisioning, phone number assignments, and setup so you can focus on running your business.
How to Get Started with a Teams Calling License
Step 1: Choose Your Microsoft 365 Plan
Make sure your organization has a Microsoft 365 Business or Enterprise plan that supports Microsoft Teams.
Step 2: Add the Teams Phone License
This license enables PSTN calling capabilities within Teams. If you’re unsure how to purchase or assign it, HelloTeams can handle this step for you.
Step 3: Select a Calling Plan or Direct Routing Provider
This is where HelloTeams shines. Instead of going through Microsoft’s limited and expensive Calling Plans, use HelloTeams to get a fully-managed VoIP solution with local support and better rates.
We offer:
Local numbers in AU, NZ, UK, and US
Flexible call bundles and unlimited plans
Scalable licenses for teams of all sizes
Auto-attendants, voicemail, call routing, and more
Step 4: Assign Phone Numbers to Users
Using HelloTeams' easy-to-use admin dashboard, assign numbers to your team. Whether you want a new number or port an existing one, it’s just a few clicks away.
Step 5: Start Calling
Once your license and number are set, your team can make and receive calls directly from within Teams—on desktop, mobile, or tablet.
Features Included with HelloTeams Calling Plans
When you activate your Teams Calling license with HelloTeams, you get access to powerful business calling features like:
📞 Auto-attendants and call queues
💬 Voicemail-to-email transcription
🔁 Call forwarding, transfer, and hold options
📊 Call logs and analytics dashboard
🔐 Secure and compliant communication
No technical knowledge is required—just log in and start communicating.
Common Questions About Teams Calling Licenses
❓ Is a Microsoft 365 subscription required?
Yes, you need a compatible Microsoft 365 plan to enable Teams Calling functionality.
❓ Can I use my current phone number with Teams?
Absolutely. HelloTeams makes it easy to port your existing numbers without downtime.
❓ How long does setup take with HelloTeams?
Most customers are fully set up and calling within 15 minutes.
❓ Is HelloTeams available in my country?
We currently provide Teams Calling solutions in the US, Australia, New Zealand, and the United Kingdom.
Ready to Activate Your Teams Calling License?
Switching to Microsoft Teams Phone has never been easier. Whether you’re a small business, a growing startup, or a remote enterprise team, HelloTeams offers the fastest, no-fuss way to set up Teams Calling with complete support.

Let our experts guide you through license setup, number porting, and user onboarding. In just 15 minutes, your team can start making calls from any device—using a fully integrated Teams Phone solution.
📧 Contact Us Today Email: [email protected] 📞 Phone:
US: +1 866 220 2351
NZ: +64 800 183 267
AU: 1300 183 267
UK: +44 0808 178 3267
🌐 Visit: https://helloteams.global/
📱 Follow HelloTeams:
Facebook
LinkedIn
Instagram
Empower your team with professional calling inside Microsoft Teams—powered by HelloTeams. Get started today with an effortless Teams Calling license setup.
0 notes
Text

📢 Struggling with TECH2100 – Introduction to Information Networks? We've Got You Covered! 💻📚
Kaplan Business School students, if you're finding network protocols, OSI models, or subnetting a bit overwhelming, don’t worry—you’re not alone!
✅ Expert Assignment Help
✅ On-Time Delivery
✅ 100% Plagiarism-Free Work
✅ Support for All Topics: TCP/IP, Switching, Routing, Cybersecurity & More!
🔍 Whether it’s your research report, case study, or practical networking task, our IT experts are ready to help you score high and understand the content clearly.
📩 DM us now or drop a 📘 below and we’ll reach out!
#KaplanBusinessSchool #TECH2100 #InformationNetworks #AssignmentHelp #StudySupport #NetworkingBasics #ITStudents #StudentLife #KaplanHelp
0 notes
Text
How VLANs Work on a Network Switch: A Simplified Explanation
What Is a VLAN and Why Do We Need It?
A VLAN, or Virtual Local Area Network, is a technology that allows you to logically divide a physical network into separate, isolated segments.
Devices can be grouped into distinct VLANs to improve organisation and manage traffic flow, even if they are physically connected to the same switch. By reducing pointless broadcast traffic, this division enhances network performance and efficiency.
VLANs are perfect for settings like offices, schools, or large buildings where various departments or user groups need isolated network access without requiring additional physical infrastructure because they also add a layer of security by limiting access between groups.
How Network Switches Handle VLAN Traffic
How VLAN traffic is handled by network switches Network switches ensure that traffic is appropriately segmented by managing VLAN traffic by tagging data packets with VLAN IDs. Every VLAN has a unique ID, and the switch tags devices with the relevant VLAN ID when they send data.
Until a router or Layer 3 switch is used to allow communication between them, this keeps traffic from one VLAN from combining with that of another, preserving isolation.
Only managed switches, which provide the required control, can be used to configure VLANs. In order to identify which devices are part of each virtual network segment, administrators allocate particular switch ports to specific VLANs.
Types of VLAN Ports: Access vs Trunk
A switch's VLAN ports can be classified as either trunk ports or access ports. Usually used to connect end devices such as PCs or printers, a access port is allocated to a single VLAN. It transmits and receives VLAN-specific untagged traffic.
A trunk port, on the other hand, is perfect for links between switches or between a switch and a router because it can transport traffic for multiple VLANs simultaneously.
Trunk ports employ VLAN tagging, which adds identifiers to packets and is based on the IEEE 802.1Q standard. For instance, to guarantee appropriate traffic routing, two switches with different VLANs can be connected via a trunk port.
VLAN Configuration Example (Simplified Setup)
The network is logically divided into three VLANs—HR, Sales, and IT—and a single switch in a basic network configuration to enhance security and performance.
For instance, VLAN 10 (HR) could be assigned to ports 1–4, VLAN 20 (Sales) to ports 5–8, and VLAN 30 (IT) to ports 9–12. Using a switch's CLI or GUI, you can configure VLANs by assigning ports and turning on VLAN tagging.
The VLAN structure must be planned and documented in order to guarantee effective management and prevent possible conflicts, particularly as the network grows or evolves over time.
Benefits of Using VLANs in a Network
Advantages of Networking with VLANs The first advantage that VLANs provide to networks is better security. Sensitive information is kept safe by limiting unwanted access between groups by dividing various departments or functions into distinct VLANs.
By restricting broadcast traffic to devices that are part of the same VLAN, VLANs also aid in reducing congestion and improving performance. VLANs also simplify diagnostics by isolating problems to particular VLANs, which makes network troubleshooting and management easier.
Last but not least, VLANs are perfect for growing networks because they are highly scalable, enabling network expansion without the need for additional hardware or rewiring.
0 notes
Text
How to Choose the Best Proxy Marketing Platform?
Selecting the optimal proxy marketing platform requires balancing multiple factors—IP pool diversity, rotation speed, geo‑location targeting, security and compliance, integration capabilities, and transparent pricing. Advertisers leverage proxies to anonymize traffic, conduct localized ad verification, bypass geo‑restrictions, and optimize campaign performance through real‑time testing and monitoring. A robust proxy marketing strategy aligns proxy types (residential, datacenter, mobile) with campaign objectives such as VPN advertising or software marketing, while integrating with top ad networks like 7Search PPC to maximize reach and ROI. This guide explores proxy marketing fundamentals, key platform features, best practices for proxy‑powered campaigns, real‑world software advertisement examples, emerging technology advertising trends, and how 7Search PPC can amplify your proxy‑based advertising efforts.

Understanding Proxy Marketing Platforms
What Is a Proxy Marketing Platform?
A proxy marketing platform is a service that routes advertising traffic through intermediary servers—known as proxies—to mask original IP addresses, enabling geographic targeting, ad verification, and data collection without revealing the advertiser’s or user’s true location. By rotating proxies across a diverse IP pool, these platforms help advertisers conduct A/B tests, monitor ad placements, and gather competitor insights at scale without triggering anti‑fraud mechanisms.
<<Start Your Campaign – Drive Traffic Now!>>
Why Proxy Marketing Matters for Advertisers
Proxy marketing empowers advertisers to verify how ads render in different regions, detect ad fraud, and optimize bids by simulating real‑user behavior, Smartproxy. It also supports privacy‑first strategies, ensuring compliance with data protection regulations by concealing end‑user IPs while still delivering personalized content.
Key Features of Top Proxy Marketing Platforms
Robust IP Pool and Rotation
A high‑quality platform offers vast pools of residential, datacenter, and mobile proxies, ensuring reliable access and reduced risk of IP blocks. Automatic rotation mechanisms switch IPs at configurable intervals, maintaining anonymity and preventing detection during long‑running campaigns.
Types of Proxies
Residential Proxies: Originating from real user devices, they are harder for ad platforms to flag and block.
Datacenter Proxies: Offer high speed and low cost but may be more easily identified as non‑residential. Mobile Proxies: Provide the highest anonymity by leveraging ISP‑assigned IPs on cellular networks.
Geotargeting and Location Support
Effective platforms allow precise location targeting down to city or ZIP code levels, critical for VPN advertising campaigns that require local ad delivery, 7Search PPC. Geo‑specific proxies ensure ads appear genuine to target audiences in regulated or restricted markets.
Integration with Advertising Networks
Seamless integration with ad networks, such as 7Search PPC, enables direct campaign deployment, performance tracking, and optimization within the proxy platform dashboard 7Search PPC. This integration streamlines workflows for software marketing and technology advertising, consolidating proxy and ad operations in one interface.
Security and Compliance Features
Leading platforms incorporate built‑in compliance tools, like GDPR and CCPA filters, to mask sensitive user data and avoid legal penalties.s. They also offer encrypted connections (HTTPS/SSL), two‑factor authentication, and detailed audit logs to safeguard campaign integrity and data privacy.
Proxy Marketing Strategy: Best Practices
Aligning Proxies with Campaign Goals
Identify campaign objectives—fraud detection, localized ad verification, or targeted testing—and select proxy types accordingly. Residential proxies excel for VPN advertising audits, while datacenter proxies work for high‑volume scraping of software advertisement examples.
Using Residential vs. Datacenter Proxies
Residential proxies reduce block rates on premium platforms but come at a higher cost; datacenter proxies are ideal for bulk operations where occasional blocks are acceptable. Multilogin. Mobile proxies combine the benefits of both, providing strong anonymity for mobile‑first campaigns.
Proxy Marketing Strategy for VPN Advertising
When promoting VPN services, use proxies from your target markets to ensure ads display optimally and comply with regional policies. Geo‑locked content tests with local proxies help refine ad creatives and landing pages for market‑specific software marketing campaigns.
Combining Proxy Marketing with Software Marketing
Leverage proxy‑driven A/B testing to identify top‑performing software advertisement examples. Rotate proxies to simulate diverse user environments, collect engagement metrics, and refine ad copy and creatives based on real‑world feedback.
Evaluating Proxy Marketing Platforms
Performance Metrics: Speed, Reliability, Uptime
Benchmark platforms on proxy response times (ideally under 200 ms), uptime guarantees (99.9%+), and success rates for requests Intel471. Tools to visualize performance trends help identify and troubleshoot network issues proactively.
Scalability and Pricing Models
Choose a platform that offers flexible pricing—pay‑as‑you‑go, tiered subscriptions, or enterprise plans—with transparent overage rates to accommodate campaign growth without budget surprises.
Customer Support and Documentation
Robust API documentation, developer SDKs, and 24/7 support channels (chat, email, ticketing) are essential for quickly resolving integration challenges and optimizing proxy marketing workflows.
Software Advertisement Examples with Proxy Platforms

Case Study: Technology Advertising Campaigns
A cybersecurity firm used residential proxies to conduct geo‑specific ad verification across 10 countries, uncovering creative rendering issues that, once fixed, boosted click‑through rates by 25%.
Example: Promoting VPN Services with Proxies
By routing test traffic through local proxies, a VPN provider ensured its display ads aligned with regional privacy regulations and tailored messaging, increasing conversion rates by 18% in target markets.
Example: Advertising Software Solutions
An enterprise software vendor leveraged datacenter proxies to run large‑scale ad fatigue tests, identifying optimal frequency caps that reduced ad spend waste by 12% while maintaining ROI.
Technology Advertising Trends
Rise of VPN Advertising
With global privacy concerns at an all‑time high, VPN advertising spend is projected to grow by 20% year‑over‑year as consumers seek enhanced online security, 7Search PPC. Ad formats like native and in‑page push are gaining traction for unobtrusive, high‑engagement VPN campaigns.
Innovative Use Cases for Proxy Marketing
Marketers are experimenting with AI‑driven proxy rotation algorithms to optimize IP selection based on time‑of‑day traffic patterns and user demographics, significantly improving ad delivery precision.
How 7Search PPC Enhances Your Proxy Marketing Efforts
7Search PPC Overview
7Search PPC is a specialized ad network catering to advertisers in high‑privacy niches like VPNs, proxies, and security software 7Search PPC. It offers display, native, and push formats optimized for proxy‑powered campaigns.
Features Tailored for Proxy‑Based Campaigns
Built‑in geolocation controls, real‑time analytics, and a proprietary API allow seamless integration with leading proxy platforms, enabling advertisers to deploy and monitor proxy‑driven campaigns directly through 7Search PPC’s dashboard 7Search PPC.
Success Stories and ROI
Advertisers on 7Search PPC report an average 30% uplift in click‑through rates and a 22% reduction in cost‑per‑acquisition when combining proxy verification with targeted VPN advertising strategies.
Conclusion
Choosing the best proxy marketing platform hinges on matching your campaign goals with platform capabilities—diverse IP pools, precise geotargeting, performance reliability, and seamless integration with ad networks like 7Search PPC. By adopting a strategic approach to proxy selection, aligning proxy types with campaign needs, and leveraging real‑world software advertisement examples, you can enhance ad verification, optimize spend, and unlock new opportunities in VPN advertising, software marketing, and technology advertising.
Frequently Asked Questions (FAQs)
What is the difference between residential, datacenter, and mobile proxies?
Ans. Residential proxies use real user IPs and are harder to detect; datacenter proxies offer speed and volume at lower cost but can be flagged; mobile proxies use cellular networks for maximum anonymity.
How do proxies improve VPN advertising campaigns?
Ans. Proxies enable localized ad rendering tests, ensure compliance with regional policies, and help tailor creatives for audience segments, boosting relevance and conversions.
Can proxy marketing platforms integrate with any ad network
Ans. Most top platforms provide APIs and plugins for popular networks; 7Search PPC offers built‑in integration for seamless campaign deployment and analytics.
What metrics should I track when using proxies for software marketing?
Ans. Monitor proxy response time, error rates, ad viewability, click‑through rates, and conversion metrics to assess proxy performance and ad effectiveness.
Are proxy servers legal for advertising purposes?
Ans. Yes, when used ethically for ad verification, compliance testing, and market research, ensure you comply with local laws and platform terms to avoid misuse.
0 notes
Text
How to Choose a Fuel Card That Actually Cuts Costs for Your Business
Why My Advice Matters
I’ve spent years analyzing and comparing operational tools used by Australian businesses, particularly focusing on cost management, process efficiency, and decision-making strategies in fleet operations. I don’t promote specific products. I evaluate them from an independent perspective to understand which providers deliver measurable value.
For this review, I compared several fuel card for business against five key metrics: network coverage, spend control, reporting features, application flexibility, and support infrastructure. WEX Motorpass showed consistent strengths across all areas. You’ll find my breakdown below, along with practical observations to help you decide whether it fits your operations.
This article explains how to find a fuel card that reduces your fuel and admin costs, provides better control over spending, and simplifies reporting. The information is especially relevant if you're managing multiple vehicles or want to move away from manual reimbursement processes.
Limited Control Over Fuel Expenses Is a Real Issue
A major challenge for many businesses is the lack of control over fuel purchases. It becomes harder to track driver spending when you rely on employee reimbursements or standard credit cards. That often leads to data gaps, inaccurate tax records, and wasted time reconciling expenses. Worse, it can cause unnoticed overspending that compounds monthly.
Fuel cards solve this problem, but not all of them offer the same level of control or insight. The difference lies in how well a card aligns with your operational goals. I’ve seen businesses reduce their fuel expenses by simply switching to a provider with better settings and oversight tools.
Fuel Card Features That Matter More Than You Think
The features that matter most aren’t always advertised upfront. Based on my review, there are five functions you need to prioritize when evaluating fuel cards:
1. National Acceptance: A good card should be usable at a broad range of service stations. WEX Motorpass is accepted at over 6,000 locations, including major chains and independent stations. This eliminates unnecessary detours and makes route planning easier.
2. Spend Restrictions and Card Controls: Being able to assign cards to drivers, vehicles, or both matters. It ensures accountability. WEX Motorpass allows you to set product-specific purchase limits, PIN requirements, and alerts. That reduces the chances of misuse.
3. ATO-Compliant Reporting: Manual reconciliation wastes time and increases the risk of non-compliant tax reporting. With WEX Motorpass, reports are generated in ATO-approved formats, making GST tracking and BAS preparation much simpler.
4. Application Options: Not every business qualifies for credit terms. WEX Motorpass offers a prepaid version—Pay2Go—for small businesses that prefer or require upfront payments. It bypasses the need for credit checks while still providing the core benefits of fuel cards.
5. Savings Potential: Estimating potential savings can guide your decision. WEX Motorpass offers a fuel savings calculator on their website. It uses your fleet data to generate a custom estimate of how much you might save, including access to discounted services through their partner network.
WEX Motorpass Stands Out for Practical Reasons
I do not represent WEX Motorpass, but I recommend their solution because they address practical pain points without adding complexity. For instance, the mobile app that shows nearby fuel prices might seem minor, but it’s a real advantage during high-volume travel periods. Their other app allows account holders to monitor transactions, change settings, and manage cards remotely—saving time when managing multiple users.
Another reason WEX Motorpass stands out is flexibility. They allow you to switch card types as your needs change. For example, you might start with cards tied to vehicles and later assign them to drivers. You’re not locked into one configuration.
They also provide non-fuel partner benefits, including discounts on tyres, batteries, servicing, and even accommodation. While not every business will use all of these, they create an extra layer of cost-saving potential.
Application Process Is Straightforward
The application process takes less than 10 minutes online. Most approvals are completed within a week. You need an ABN active for at least six months, and an authorized person from your company must apply. You may be asked for supporting documents, such as a driver’s license or vehicle registration. Once approved, cards are usually shipped by the next business day.
If your business has a solid payment history and operates several vehicles, you’re likely to qualify for a credit-based card. If not, the prepaid option offers a reasonable path forward while avoiding the complications of standard credit approval.
The Right Card Helps You Scale With Fewer Headaches
A fuel card won’t fix every cost issue in your business. But it can reduce errors, improve cost visibility, and allow you to scale vehicle use without losing control over expenses. This is especially true if you’re transitioning from small-scale reimbursements to managing a growing mobile team.
WEX Motorpass is not the only provider available, but they meet the requirements of many Australian businesses by offering real control, flexible setups, and reliable coverage. If your priority is predictable fuel spending with simplified reporting and decent customer support, their service deserves consideration.
Their tools give you the means to monitor and adapt without unnecessary steps. That is what I look for when evaluating business tools: simplicity, flexibility, and cost justification.
0 notes
Text
CNT4703C – LAB 6 Configuration of Static Routes
In this lab several of the concepts that were previously covered will be combined to configure static routes between a group of networks. In this scenario multiple routers will be configured so that network connectivity is established between workstations across a serial connection. You will use the experience gained in the previous lab assignments to configure workstations, routers, switches,…
0 notes
Text
Optimized network engineering tools are used to provide network models which can be used in distribution of data or information from one centralised or decentralised source. Optimized network engineering tools decomposes a network in technological key components that must understand, arranged, and maintained. Although underlying technology that constitutes these elements vary, anyone involved in managing networks will need to make decision about the design, management, and improvement of the Local area network, HEBS, Switches, Wireless Access Points, and Network Adapters, Wide Area Network and Routers. OPNET will help in showing model on how array for computers are arranged together to communicate. This will indicate the infrastructure paths of a network allow including components such as key servers. Although it is mostly considered that any network can attain a by simply adding various redundant devices on it, the process of designing a network goes beyond such perception; it incorporates setting appropriate measures that would allow an organization and network administrators to recognize regions of points of failures within a system. Aim and objectives The main aim of this report is to highlight simulation results of an assignment were optimised network engineering tool was used. Assumptions The network will have one server that will serve all the two floors. System description When are modelling a supermarket network system as well as simulate it by varying delay and bytes send. The network first feature is link and node failure detection which allows for the detection of default and eventual reroute on possible cause of the problem. The second feature is an Authentication Packets whose function is to prevent possible downtime in the network resulting from wicked attacks on the routing protocol level (Iniewski, McCrosky and Minoli, 2008). In other words a network can only be achieved through the Authentication Packets. Thirdly, Graceful Restart is a feature that allows a router to restart without imposing negative impact on the network topology thereby allowing room for a network Read the full article
0 notes
Text
Top Direct Inward Dialing Providers: Choosing the Right One for Your Business
When it comes to business communication, Direct Inward Dialing (DID) is an essential tool for enhancing efficiency and streamlining the way customers and clients connect with your team. Choosing the right Direct Inward Dialing providers is crucial to ensure that your business benefits from reliable, cost-effective, and scalable solutions. If your business is located at the TC Energy Center in Houston, TX, or elsewhere, understanding how to select the right provider for your needs is essential to improving communication and operational efficiency.
What is Direct Inward Dialing?
Direct Inward Dialing (DID) is a telephony service that allows external callers to directly reach specific employees or departments within a company without going through a receptionist or switchboard. DID numbers are assigned to individual phone extensions, and they are usually linked to a company’s PBX or VoIP system, allowing calls to be routed automatically to the intended destination.
For businesses looking to enhance customer service and reduce operational overhead, DID services are essential. The right DID provider can provide flexibility, scalability, and the level of reliability that your business requires.
Why Choosing the Right DID Provider Matters
Selecting the right direct inward dialing providers is not only about having access to a phone number; it's about finding a provider who can offer:
Reliability: You need a provider that guarantees uptime and call quality, so your business is always reachable.
Scalability: As your business grows, your communication system should grow with it. Your provider should offer the flexibility to add or remove DID numbers as needed.
Cost-Effectiveness: The right provider will offer competitive pricing without compromising on service quality.
Advanced Features: A great DID provider will provide advanced features such as call forwarding, voicemail, and integration with VoIP systems to further enhance your business communications.
Top Features to Look for in Direct Inward Dialing Providers
Quality of Service (QoS) and Call Clarity: The quality of the calls made using a DID number is crucial for maintaining a professional business image. Look for providers that guarantee excellent voice quality and a robust network to ensure minimal interruptions or dropped calls.
Scalability: As your business expands, you may need to scale your communication infrastructure. Ensure your DID provider offers the flexibility to add or remove phone numbers and features without significant downtime or complications.
VoIP and SIP Trunking Integration: If your business uses or plans to switch to VoIP, ensure that your DID provider integrates seamlessly with VoIP systems. VoIP provides cost savings and advanced capabilities that enhance communication efficiency.
Customizable Features: Look for providers that offer customizable features, including call forwarding, call routing, voicemail-to-email, and even detailed reporting on call performance. This will help you manage your business communication more effectively.
Customer Support: Reliable customer support is essential, especially if your business relies on direct communication with clients. The provider you choose should offer responsive customer service that can resolve issues quickly.
A1 Routes: Your Trusted DID Provider
At A1 Routes, located near the TC Energy Center at 700 Louisiana St, Houston, TX, we specialize in providing businesses with high-quality Direct Inward Dialing services that are designed to scale with your needs. Whether you’re a small business or a large enterprise, our DID solutions are flexible, reliable, and backed by exceptional customer support.
We offer a variety of DID numbers to help you connect with clients efficiently and professionally. With A1 Routes, you can expect clear call quality, easy integration with VoIP systems, and the scalability you need to accommodate business growth.
Why A1 Routes is the Best Choice for Your Business
A1 Routes stands out as one of the top direct inward dialing providers due to our focus on reliability, quality, and customer satisfaction. Our DID services are tailored to meet the unique needs of your business, whether you’re located at the TC Energy Center or anywhere in Houston, TX. We offer a range of features that ensure your communication system is seamless and efficient, allowing your business to grow without the limitations of traditional phone systems.
Conclusion
When selecting the best Direct Inward Dialing providers, it’s important to prioritize reliability, scalability, and advanced features that will benefit your business in the long term. A1 Routes is a trusted partner in delivering high-quality DID services that support your business operations. Whether you're looking to set up DID numbers for individual employees or departments, A1 Routes has the expertise to help you create a streamlined, professional communication system.
For more information on our Direct Inward Dialing solutions, please contact us today at 1-347-809-3866. Let A1 Routes help your business grow with reliable and scalable communication solutions.
#direct inward dialing#direct inward dialing providers#direct inward dialing service#enterprise sip trunking#global voip services
0 notes
Text
End-to-End and Local VLANs
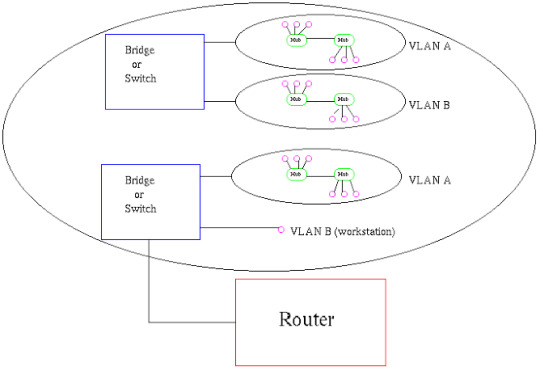
There are two models in which you can design VLANs on a network: - End-to-End - Local End-to-End End-to-End VLANs span across multiple switches within the network. Regardless of the user's physical location, they will consistently be assigned to the same VLAN. Consequently, the user's resources will belong to the same subnet. Management of end-to-end VLANs often involves utilizing VTP through trunked switches, facilitating streamlined management processes. However, reliance on VTP can sometimes lead to complications. Moreover, by extending the VLAN across the network, you enable broadcasts to traverse multiple switches. While this model may be suitable for small implementations, it may not scale effectively for larger environments. Local VLANs are confined to individual switches, typically organized according to geographic location. If a user relocates, they will be assigned to a different VLAN. Under the Local VLAN model, the local switch connects to a distribution or core switch, where routing takes place. Local VLANs exist solely between the local switch and the distribution or core switch. To communicate with other networks, traffic travels from the local VLAN to the distribution/core switch and is then routed to its destination. In this setup, VTP (VLAN Trunking Protocol) is not configured, and switches operate in VTP Transparent mode. Since VLANs are not broadcasted to other switches in the network, VTP becomes unnecessary. One advantage of this model is the elimination of extended layer 2 broadcast domains throughout the network. Troubleshooting is simplified compared to end-to-end VLANs, as traffic follows a defined path. In contrast, end-to-end VLAN traffic traverses multiple switches. Read the full article
0 notes
Text
Why are proxy IPs so widely used? The reasons are surprisingly these!
With the rapid development of the Internet and the increasing demand for networks, proxy IP plays an increasingly important role in various business scenarios. Today, we will analyze the reasons behind why proxy IP is widely used, let's take a look!

1. Hiding Real IP, Protecting Privacy and Security
First of all, one of the most important roles of proxy IP is to hide the user's real IP address. In the process of daily surfing, IP address can expose the user's geographic location and online behavior, bringing potential risks to privacy. By using proxy IP, users can hide their real identities when visiting websites, conducting online transactions, and using social media, preventing them from being tracked or attacked by undesirable elements, and effectively safeguarding personal privacy and information security.
2. Avoid geographical restrictions and access global resources
In the context of globalization, different regions have different restrictions on Internet access. Some websites and services restrict access based on the user's IP address. By using proxy IP, users can easily circumvent these geographical restrictions and access global network resources and services. For example, users can switch proxy IPs to access e-commerce platforms, video sites or social media in specific countries to facilitate business expansion and information acquisition.
3. Improve network speed and optimize connection quality
Sometimes, the speed and stability of the network may be affected by regional, service provider or network congestion issues. Using a quality proxy IP can optimize the network connection and improve the speed and quality of data transmission. Users can bypass bottlenecks in intermediate routes and reduce latency by choosing a proxy IP close to the target server, resulting in a smoother network experience.
4. Realize automated tasks to enhance work efficiency
In the fields of big data crawling, SEO optimization, and online advertisement placement, proxy IP is a key tool to carry out automated tasks. By using a large number of proxy IPs, high-frequency and concurrent network requests can be realized, avoiding the risk of IP blocking due to frequent visits. For example, in the process of data crawling on e-commerce platforms, proxy IP can help users collect data from different regions while ensuring IP rotating IP to avoid triggering the anti-crawling mechanism of the website, which greatly improves work efficiency.
5. Support multi-account management and prevent account association
In social media operation, cross-border e-commerce and other businesses, users often need to manage multiple accounts at the same time. However, the use of the same IP address for multiple accounts can easily lead to account correlation, which in turn leads to the risk of banning. By using proxy IP, users can assign different IP addresses to each account to prevent account association and ensure smooth operation, especially when operating in multiple countries and regions, proxy IP can help solve the problem of cross-region management.
6. Enhance network security and prevent hacker attacks
Enterprises and individuals have increasingly prominent security problems in the Internet. Proxy IP adds a layer of defense for users by disguising the real IP. For example, to prevent network attacks such as DDoS attacks, malicious scanning and network sniffing. Especially during large-scale online activities, marketing promotions and major business operations, the use of proxy IPs can effectively reduce the risk of being attacked and improve the security and stability of the system.
711Proxy - Stable and Reliable Proxy IP Service
The wide application of proxy IP cannot be separated from professional service support. 711Proxy, as a leading proxy IP service provider, offers worldwide proxy IP solutions. 711Proxy can provide users with stable and efficient proxy IP resources. It allows users to enjoy a seamless network experience and comprehensively improve business performance!
The widespread use of proxy IP stems from its powerful features in privacy protection, geo-restriction bypassing, network acceleration, multi-account management and automated tasks, etc. Proxy IP can bring practical convenience and security.
0 notes
Text
What is MPLS and Why Do Businesses Need It?
Multiprotocol Label Switching (MPLS) is a networking technology that improves the speed, security, and efficiency of data transfer between multiple locations. Unlike traditional IP routing, where data packets travel based on destination addresses, MPLS assigns a label to each data packet, allowing it to take the most efficient route through the network. This results in lower latency, improved reliability, and better traffic management.
How MPLS Works
MPLS creates a private and dedicated connection between offices, data centers, or cloud services. It ensures that data follows a pre-determined, high-performance path rather than relying on unpredictable public internet routes. This makes MPLS an ideal solution for businesses with multiple branches, remote offices, or high-priority applications.
Why Do Businesses Need MPLS?
Reliable Performance – MPLS offers consistent speed and minimal packet loss, making it suitable for applications like VoIP calls, video conferencing, and cloud computing, where network stability is crucial.
Enhanced Security – Since MPLS networks are private and separate from the public internet, they provide an extra layer of security, reducing the risk of cyber threats.
Scalability – Businesses can easily expand their MPLS network as they grow, adding new locations without compromising performance.
Quality of Service (QoS) – MPLS allows businesses to prioritize traffic, ensuring that critical applications receive the necessary bandwidth for seamless operation.
Better Cloud Integration – Many businesses rely on cloud-based applications. MPLS improves connectivity to cloud services by offering dedicated, high-speed routes, reducing lag and downtime.
Conclusion
MPLS remains a valuable networking solution for businesses that need secure, fast, and reliable communication between multiple locations. While newer technologies like SD-WAN are emerging, MPLS continues to be a preferred choice for organizations that prioritize network stability and performance.
0 notes
Text
Understanding IPv4 Subnet Lease: A Comprehensive Guide
In today's digital world, the demand for IP addresses is constantly increasing as the number of internet-connected devices grows. One of the critical components in network management is the concept of IPv4 subnet lease. If you're new to the world of networking or just curious about how IP address leasing works, this guide will break it down for you.
What is IPv4?
IPv4 (Internet Protocol version 4) is the most widely used version of the Internet Protocol. It uses a 32-bit address space, allowing for around 4.3 billion unique addresses. However, with the massive growth of the internet, this number has proven insufficient. To make more efficient use of the available IPv4 address space, subnetting and leasing mechanisms have been adopted.
What is a Subnet?
A subnet, short for subnetwork, divides a large network into smaller, manageable sections. This division is essential for routing traffic efficiently and ensuring that IP address usage is optimized. In IPv4, subnets are created by borrowing bits from the host part of the IP address, thus allowing for better control over traffic within each network.
For example, an IP address like 192.168.1.0/24 means that the first 24 bits are reserved for the network part, and the remaining 8 bits are for hosts, giving the ability to host 256 unique IP addresses.
What is an IPv4 Subnet Lease?
An IPv4 subnet lease refers to the process of renting or leasing a block of IPv4 addresses that have been subdivided into smaller segments or subnets. This allows businesses, ISPs (Internet Service Providers), and other organizations to acquire IP addresses temporarily, without the need for long-term ownership.
Leasing IPv4 subnets is a cost-effective way to obtain IP addresses, especially with the IPv4 address pool depleting rapidly. Instead of purchasing, companies can lease the exact number of addresses they require, which offers flexibility and scalability.
Key Benefits of Leasing IPv4 Subnets
Cost-Effective: Leasing is often cheaper than purchasing large blocks of IP addresses, particularly for businesses with fluctuating needs.
Scalability: If your organization expands, leasing additional subnets allows you to scale your operations smoothly.
Short-Term Solutions: For businesses that only need IP addresses temporarily, such as during a special project or seasonal campaign, leasing provides a practical solution.
No Need for Long-Term Commitment: Leasing offers flexibility, as you can return the leased subnets once you no longer need them.
Avoid IPv6 Migration: While IPv6 is becoming more common, many companies still rely on IPv4. Leasing subnets allows them to continue using IPv4 without switching immediately to IPv6.
How IPv4 Subnet Leasing Works
Identify Your Needs: Before leasing, determine how many IP addresses or subnets you need based on your network’s size.
Choose a Provider: Numerous companies specialize in IPv4 leasing. Compare their pricing, lease terms, and support to find the right fit for your business.
Negotiate Lease Terms: Leasing agreements can range from a few months to several years. Negotiate terms that suit your business, ensuring you have the flexibility to renew or return the subnets as needed.
Deploy and Manage: Once leased, you can configure your network to utilize the newly leased subnets, ensuring they’re integrated into your infrastructure.
Use Cases for IPv4 Subnet Leasing
ISPs: Internet Service Providers may lease subnets to allocate IP addresses to their customers, especially when dealing with a shortage of available IPv4 addresses.
Cloud Service Providers: Businesses that provide cloud-based services often require large pools of IP addresses to assign to virtual machines or other online services. Leasing IPv4 subnets ensures they have the flexibility needed to scale services.
Enterprise Networks: Large enterprises with extensive networks can benefit from leasing subnets to ensure they have enough IP addresses for their infrastructure, without the financial burden of buying them outright.
IPv4 Subnet Lease vs. IPv6 Adoption
The transition to IPv6 is underway, but it has been slower than expected due to compatibility issues, costs, and the complexities involved in migrating from IPv4. Leasing IPv4 subnets allows businesses to continue operating under the existing IPv4 system while preparing for the eventual switch to IPv6. However, IPv4 leasing is seen as a short- to medium-term solution, as IPv6 adoption will likely become necessary as IPv4 addresses become scarcer.
Conclusion
IPv4 subnet leasing is an essential tool for businesses and organizations that need to expand their network infrastructure while minimizing costs. It offers flexibility, scalability, and a practical solution for the ongoing IPv4 address shortage. While IPv6 adoption is inevitable, leasing IPv4 subnets is a strategic way to bridge the gap between the present and the future of internet protocols.
If your business requires more IP addresses, consider exploring the benefits of IPv4 subnet leasing today!
0 notes
Text
[ad_1] MPLS is a crucial expertise in present community techniques, aiming to hurry up and management visitors patterns inside enterprise and repair supplier networks. In distinction to conventional IP routing, MPLS makes use of transient path labels as a substitute of prolonged community addresses to information knowledge between nodes. This technique drastically decreases the processing burden of intricate community paths, making it an efficient possibility for high-speed knowledge switch. For a extra complete understanding, try this information to multiprotocol label switching. As enterprises broaden, so do their networking wants, making the power to swiftly and effectively switch knowledge paramount. MPLS addresses this vital requirement by offering a extremely environment friendly, scalable, and dependable resolution for numerous industries. For instance, companies within the healthcare sector depend on MPLS for the safe and fast transmission of delicate affected person info. On the similar time, monetary establishments profit from its low-latency, high-speed knowledge switch capabilities important for real-time buying and selling operations. How MPLS Works MPLS operates by assigning labels to packets, that are then utilized by community routers to ahead the information to its remaining vacation spot. This technique considerably reduces the processing time per packet, enhances visitors stream velocity, and ensures environment friendly community useful resource use. MPLS simplifies and accelerates the routing course of, making it extra environment friendly than conventional IP routing. Label Edge Routers (LER): These are labeled packets’ entry and exit factors. LERs are accountable for assigning preliminary labels to packets as they enter the community and eradicating the labels after they exit. This course of ensures the information packets are appropriately recognized and routed with out advanced IP handle lookups. Label Switching Routers (LSR): These center routers within the MPLS community route packets in line with their labels. LSRs velocity up the method and scale back latency by shortly making forwarding choices based mostly solely on the related labels. This effectiveness is advantageous in intensive networks the place swift packet forwarding is essential. Advantages of Utilizing MPLS Implementing MPLS in your community can provide a number of notable advantages, enhancing the general effectivity and efficiency of information transmission. Listed below are among the key benefits: Improved Efficiency: MPLS hurries up packet forwarding by utilizing labels as a substitute of prolonged community addresses. This boosts the general velocity and effectiveness of the community, making it good for real-time duties like voice and video communications. Scalability: MPLS is designed to be simply scalable, making it easy to broaden the community as what you are promoting grows. This scalability is especially useful for enterprises experiencing fast development or planning future expansions, making certain the community can deal with elevated visitors with out compromising efficiency. High quality of Service (QoS): MPLS presents enhanced management over prioritization and bandwidth allocation, making certain vital purposes obtain the mandatory assets for optimum efficiency. This functionality is crucial for sustaining excessive service ranges in various networking environments, supporting purposes similar to video conferencing, VoIP, and cloud companies. Implementing MPLS in Your Community Transitioning to an MPLS community entails a number of pivotal steps. Every section is vital for profitable implementation, from the preliminary evaluation to the ultimate rollout. Right here’s a fast information that will help you by the method: Assess Your Present Community: Consider your present community infrastructure to establish the necessity for MPLS. Decide if MPLS can handle your present community challenges and enhance effic
iency. This evaluation ought to embody an evaluation of visitors patterns, bandwidth necessities, and potential areas for optimization. Plan the Community Structure: Design the community structure with scalability and QoS. Rigorously plan how MPLS can be built-in into your community to make sure a clean transition. This planning section ought to contain figuring out the optimum areas for Label Edge Routers (LER) and Label Switching Routers (LSR) and defining the label distribution and visitors engineering insurance policies. Choose Applicable MPLS Routers: Select and configure MPLS-compatible routers with the mandatory labels. Be sure that the chosen routers can deal with the anticipated visitors hundreds and are suitable along with your community necessities. This step might contain upgrading present hardware or procuring new units to assist the MPLS deployment. Conduct a Pilot Check: Earlier than absolutely deploying the MPLS community, run a pilot check to confirm that the setup capabilities appropriately. The pilot section ought to contain deploying MPLS in a managed setting, testing numerous visitors situations, and monitoring efficiency metrics. Tackle any points in the course of the pilot section to attenuate disruptions in the course of the full rollout. Roll Out the Implementation: Deploy MPLS regularly to attenuate potential community disruptions. Slowly improve the implementation of MPLS, monitoring efficiency and adjusting as required. This gradual technique allows step-by-step enhancements and ensures immediate detection and determination of any issues. The Way forward for MPLS SD-WAN (Software program-Outlined Vast Space Community) is incorporating MPLS to create hybrid networking options, exhibiting a vivid future for Multiprotocol Label Switching. These developments will proceed to enhance the effectiveness and flexibility of enterprise networks, guaranteeing their capacity to satisfy upcoming knowledge necessities. The merging of MPLS and SD-WAN can present firms with a mix of MPLS’s dependability and velocity together with SD-WAN’s flexibility and affordability. As extra organizations undertake cloud-based companies and interconnected purposes, the necessity for sturdy and environment friendly networking options will proceed to develop. With its confirmed reliability and efficiency observe file, MPLS is well-positioned to satisfy these evolving calls for. Moreover, developments in automation and community administration instruments are making it simpler for companies to deploy and handle MPLS networks, additional solidifying its relevance in the way forward for networking. Conclusion Multiprotocol Label Switching stays an important expertise for networking professionals, providing important efficiency, scalability, and High quality of Service (QoS) advantages. Whether or not in finance, healthcare, telecommunications, or some other trade reliant on high-speed knowledge switch, understanding and implementing MPLS may give your community the enhance it wants. By following a structured implementation plan and addressing widespread challenges, organizations can efficiently combine MPLS into their networks and reap the rewards of this superior expertise. MPLS is a reliable and environment friendly alternative for firms on the lookout for superior, adaptable, and high-performing networking options in a fast-changing digital setting. The effectivity in managing and prioritizing visitors, together with its scalability, makes it a worthwhile useful resource for organizations wanting to make sure the longevity of their community infrastructure. The put up The Definitive Information to Multiprotocol Label Switching for Networking Professionals appeared first on Vamonde. [ad_2] Supply hyperlink
0 notes