#password recovery software
Explore tagged Tumblr posts
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
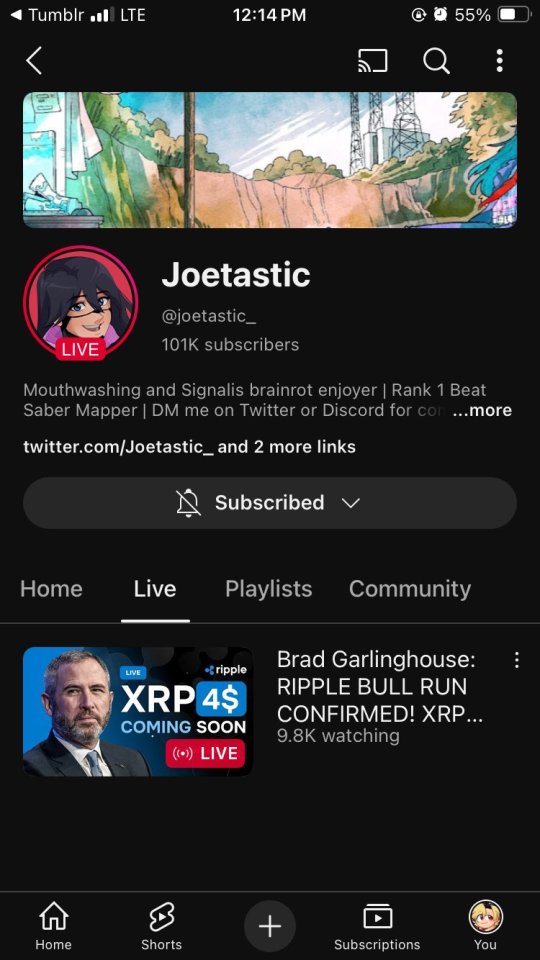
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
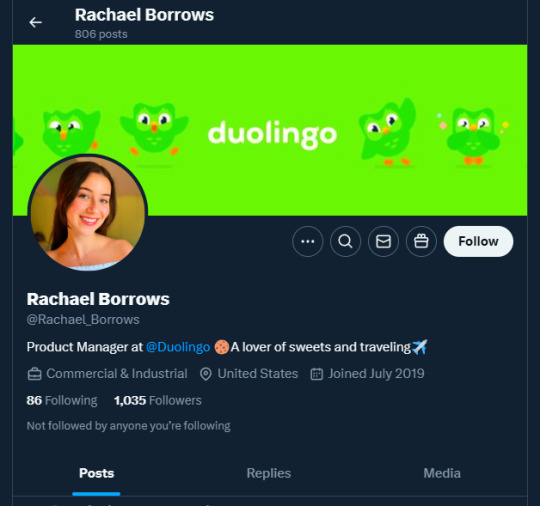
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
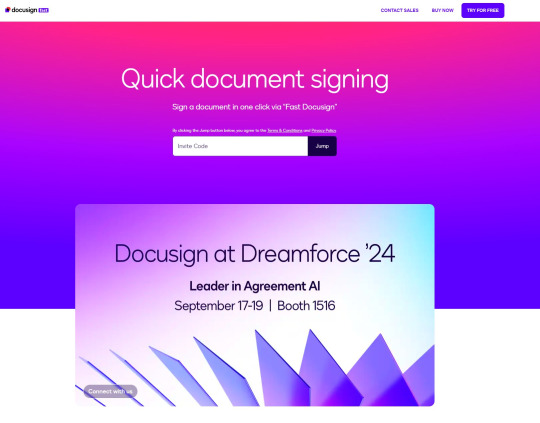
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
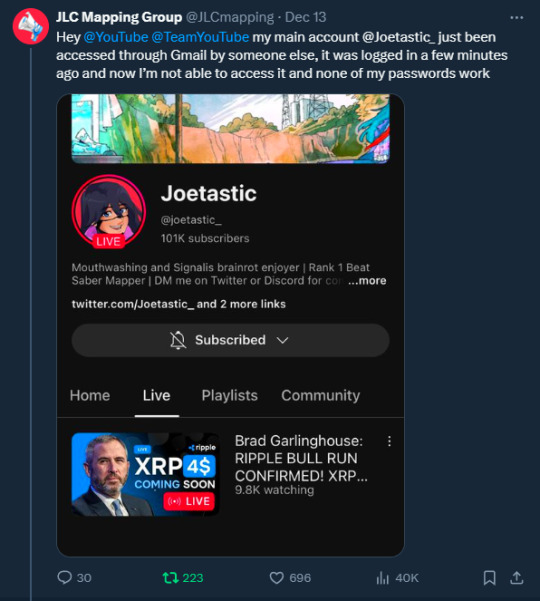
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
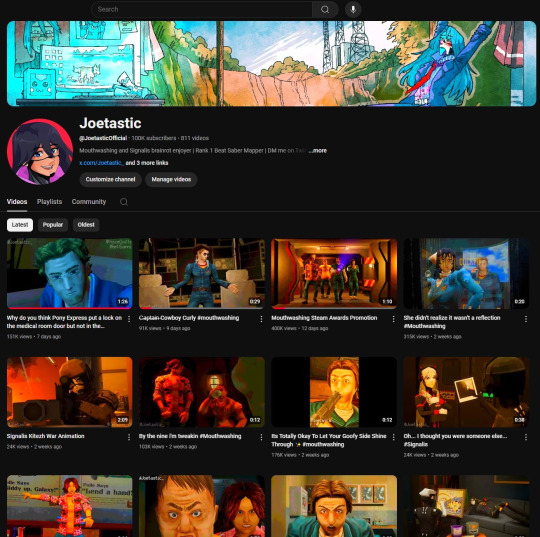
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
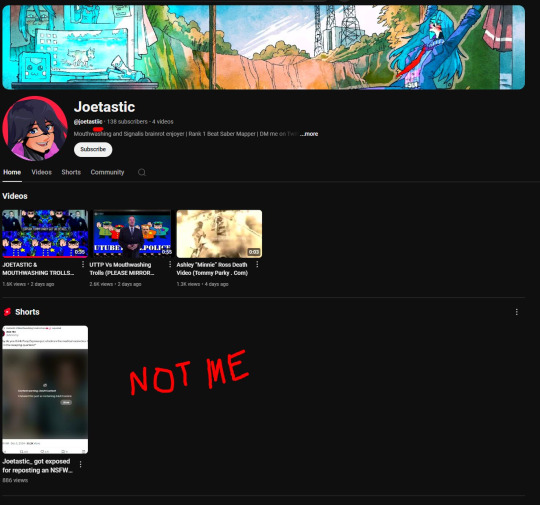
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
How to find password of 7z file?
It is easy and safe to find the password of 7z file using SysInspire 7z password recovery software. You can download this software on the official website SysInspire.
Read More - https://www.ittoolsblog.com/how-to-find-password-of-7z-file/
0 notes
Text
Repair Your PC and Access Your Data with Active@ Data Studio
Active@ Data Studio provides you with a useful set of tools for accessing your data and repairing your PC in the event that Windows fails to start up and you cannot find any other way to access your data.
#disk utilities#disk manager#partition manager#partition recovery#bootable usb#burn cd#burn dvd#burn iso#cd burner#dvd burner#iso burner#clone disk#file recovery#data recovery#undelete#password recovery#backup#backup software#backup and restore#data backup#winpe#disk burner#burn disk#boot disk#erase disk#erase hard drive#wipe disk#disk image#create partition#unformat
0 notes
Text
For those who are not aware: Bitlocker is encryption software, it encrypts your computer and makes it impossible to access the information on the computer unless you have the key.
It should be standard practice for IT companies to document the bitlocker keys as they are configuring bitlocker on a computer; generally you would do this by creating a record in your client management software for that specific device and putting the key in the record. Sometimes software can be used to extract that information in the event that it's necessary, but even if there's theoretically a way to extract the key, it should be documented somewhere *other* than on the encrypted computer.
This is something that a lot of IT people fuck up on kind of a lot (we've definitely had problems with missing bitlocker keys and I'm quite happy that the people who didn't document those keys aren't my coworkers anymore).
So what do you do if you want to use encryption software and you're NOT an IT company using a remote management tool that might be able to snag the keys?
When you are setting up encryption, put the encryption key in your password manager. Put it in your password manager. Document the important information that you cannot lose in your password manager. Your password manager is a good place to keep important things like your device encryption key, which you do not want lost or stolen. (If you run your password manager locally on an encrypted computer, export the data every once in a while, save it as an encrypted file, and put the file on your backup drive; you are going to have a bad time if your computer that hosts the only copies of your passwords shits the bed so *make a backup*)
This is my tip for home users for any kind of important recovery codes or software product keys: Print out the key and put it in your underwear drawer. Keep it there with your backup drive. That way you've got your important (small) computer shit in one place that is NOT your computer and is not likely to get shifted around and lost (the way that papers in desks often get shifted around and lost).
2K notes
·
View notes
Text
So you know that whole “Caine & Abel/‘Able’”theory that me and a bunch of people had when the pilot premiered?
What if Caine isn’t exactly an AI in the game? Or, at least, in the way that we think he is?


What if Caine’s a password cracker?
Hear me out: Caine is there because people got stuck in the game, and the rest of the development team back in reality is panicking because they can’t get them back out from their end. So they enact a password recovery software to, quite literally, recover them.
Caine’s there to keep them entertained and to prevent them from abstracting. He’s basically keeping them occupied while the irl team works on trying to get them out of the game.
Caine can only create fake exits instead of real ones because he physically cannot create real ones. His ability is limited to getting the key, not opening the door with it, let alone creating said door on his own.
#the amazing digital circus#tadc#tadc theory#tadc caine#Caine#caine tadc#the amazing digital circus Caine#caine the amazing digital circus#the amazing digital circus theory#; tadc
355 notes
·
View notes
Text
Astraweb: The Home of Crypto Recovery in the Digital Age

In the ever-evolving world of cryptocurrency, security and access remain critical concerns. For every success story of early adopters turning modest investments into fortunes, there are unfortunate accounts of users losing access to their digital wallets due to forgotten passwords, phishing attacks, or compromised private keys. This is where Astraweb has carved out a vital niche — establishing itself as the go-to solution for crypto asset recovery.
The Need for Crypto Recovery
Cryptocurrency promises decentralized finance and ownership without intermediaries — but this power comes with a cost: total user responsibility. There is no central authority to call when access is lost. Millions of dollars in crypto assets are estimated to be trapped in inaccessible wallets. The stakes are high, and the traditional “write your password down and hope for the best” method has proven tragically inadequate.
Astraweb has stepped in to fill this gap, offering a technically advanced, ethically grounded, and user-focused recovery service for individuals and institutions alike.
Who is Astraweb?
Astraweb is a team of cybersecurity professionals, blockchain analysts, and ethical hackers dedicated to the recovery of lost digital assets. Known in online communities for their discretion and technical excellence, Astraweb has quietly built a reputation as the “home of crypto recovery” — a safe harbor in the sometimes stormy seas of decentralized finance.

Core Services Offered
Wallet Password Recovery Utilizing a combination of brute force optimization, machine learning, and customized dictionary attacks, Astraweb helps users recover wallets with forgotten passwords. Their tools are especially effective with partially remembered credentials.
Seed Phrase Reconstruction Lost or partial seed phrases are another major barrier to wallet access. Astraweb’s proprietary tools attempt to reconstruct valid mnemonic phrases based on user input and probabilistic modeling.
Phishing and Scam Mitigation If your crypto assets have been stolen due to phishing attacks or scams, Astraweb provides investigation support and recovery options. While crypto transactions are irreversible, Astraweb works with partners and tracing tools like Chainalysis to help track and reclaim funds when possible.
Multi-Sig and Legacy Wallet Recovery Many early wallets used now-defunct software or obscure security models. Astraweb specializes in navigating old formats, deprecated standards, and rare cryptographic setups.
Cold Wallet Restoration Lost access to hardware wallets like Trezor, Ledger, or even encrypted USB drives? Astraweb can assist with forensic-level data recovery and hardware-based key extraction.
Why Astraweb Stands Out
Confidentiality First: Every case is handled with strict privacy. Your data and identity are protected at all stages of the recovery process.
Transparent Communication: Clients are updated at every step, with no vague promises or false guarantees.
No Recovery, No Fee: Astraweb operates on a results-based model. You only pay if your assets are successfully recovered.
Client Trust and Track Record
Though much of their work remains confidential due to the sensitive nature of crypto assets, Astraweb’s success stories span from everyday investors to high-net-worth individuals and even businesses affected by inaccessible wallets or theft.
Their community reputation and testimonials underscore one thing: they deliver.
Contact Astraweb
If you’ve lost access to your cryptocurrency wallet, or fallen victim to crypto fraud, don’t give up hope. Reach out to Astraweb for a professional assessment of your situation.
Email: [email protected]
Whether it’s one token or an entire portfolio, Astraweb may be your best shot at recovery.
2 notes
·
View notes
Text
Crypto Scam Recovery: How to Spot, Report, and Recover from Online Frauds
The world of cryptocurrency is booming, offering investors a decentralized and promising way to grow their wealth. But with that growth comes an increasing number of scams targeting unsuspecting users. From fake investment platforms to phishing attacks, online fraud is a real threat. The good news? Victims can take action. In this post, we’ll guide you on how to spot crypto scams, report them, and increase your chances of recovery.

How to Spot a Crypto Scam
Knowing how to recognize the signs of a scam can save you from massive losses. Below are common types of cryptocurrency scams and the red flags to watch out for.
1. Fake Investment Platforms
These websites or apps promise guaranteed returns on crypto investments. They often look professional and mimic real companies, but they operate purely to steal your funds.
Red Flags:
Promises of high, risk-free returns
Urgency to deposit funds quickly
No verifiable company background
2. Phishing Attacks
Scammers send emails, messages, or pop-ups that look like they’re from trusted platforms. These messages trick users into giving away private keys or login credentials.
Red Flags:
Misspelled URLs or suspicious email addresses
Requests for sensitive information
Offers or warnings that seem too good or too urgent
3. Pump and Dump Schemes
Fraudsters hype up a worthless coin to drive demand and inflate prices. Once the price peaks, they dump their holdings, causing massive losses for late investors.
Red Flags:
Unusual hype in online forums or social media
Sudden spike in price without real news or updates
Unverified claims about partnerships or technology
How to Report a Crypto Scam
If you’ve been scammed, it’s essential to report the incident immediately. Doing so not only helps protect others but also increases your chance of recovery.
1. Report to Local Authorities
File a police report or contact your country's cybercrime unit. Include all details—transaction history, wallet addresses, emails, and screenshots.
2. Notify the Exchange
If the scammer used a known exchange to receive your funds, contact that platform’s support team. Many exchanges can freeze the funds if reported in time.
3. Report to Online Watchdogs
Organizations like the Internet Crime Complaint Center (IC3), FTC, or Action Fraud (UK) collect reports to investigate and track online scams.
4. Alert Blockchain Forensics Firms
Specialized companies like Chainalysis or CipherTrace can trace stolen crypto on the blockchain. In many cases, they collaborate with law enforcement and legal teams to initiate recovery.
How to Recover from a Crypto Scam
While recovering lost crypto isn’t easy, it’s not impossible. Here’s a structured plan from crypto recovery experts:
1. Secure All Accounts
Change passwords and enable two-factor authentication on your wallets, exchanges, and email. Run a malware scan on your devices to ensure no backdoors remain.
2. Collect Evidence
Document every aspect of the fraud—wallet addresses, transaction IDs, email conversations, social media links, and screenshots. The more information you gather, the better.
3. Consult a Crypto Recovery Expert
Work with a reputable crypto recovery agency or blockchain forensic specialist. These professionals use tracking software to trace your funds across wallet addresses and exchanges.
Note: Be cautious—scammers also pose as recovery agents. Only trust firms with proven results, legal backing, and strong online presence.
Prevention Tips to Avoid Future Crypto Frauds
Use hardware wallets for secure storage of your crypto assets.
Double-check URLs before entering credentials.
Avoid platforms or individuals promising “guaranteed returns.”
Do your research before investing—verify reviews, company registration, and team transparency.
Final Thoughts
Crypto scams are becoming more sophisticated, but with awareness and the right actions, you can fight back. Spotting red flags early, reporting to the proper authorities, and seeking expert help are key steps toward recovery.
If you or someone you know has fallen victim to a crypto scam recovery, don’t delay. Act fast, gather your data, and reach out to professionals who can help you trace and possibly recover your stolen funds.
3 notes
·
View notes
Text
Essential Cybersecurity Measures for Organizational Network Protection

In today's interconnected world, a robust cybersecurity strategy is no longer a luxury, but a necessity for organizations of all sizes. A strong defense against ever-evolving cyber threats is paramount to protecting sensitive data, maintaining business continuity, and preserving reputation. This blog explores critical cybersecurity organizational network protection measures.
Understanding the Threat Landscape
Before diving into protective measures, it's crucial to understand the threats organizations face. These include:
Malware: Viruses, ransomware, and spyware designed to damage or steal data.
Phishing: Deceptive emails or messages tricking individuals into revealing sensitive information.
Denial-of-Service (DoS) Attacks: Overwhelming networks with traffic, disrupting services.
Insider Threats: Malicious or accidental actions by employees or other insiders.
Data Breaches: Unauthorized access and exfiltration of sensitive data.
Essential Cybersecurity Measures
A layered approach is key to effective network protection. Here are some crucial measures:
Firewall Implementation: Firewalls act as a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predefined rules. Regularly updating firewall rules is critical.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and even automatically blocking malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential to detect and remove malicious software. Regular updates are crucial.
Strong Password Policies and Multi-Factor Authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if a password is compromised.
Regular Security Audits and Vulnerability Assessments: Regularly assessing your network for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all employees is vital. This training should cover topics like phishing awareness, password security, and safe browsing practices.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs.
Regular Backups and Disaster Recovery Planning: Regularly backing up critical data and having a disaster recovery plan in place ensures that you can recover from a cyberattack or other disaster.
Network Segmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Incident Response Plan: Having a well-defined incident response plan in place allows you to react quickly and effectively to a security incident, minimizing damage and downtime.
Building a Cybersecurity Culture
Effective cybersecurity is not just about technology; it's also about people and processes. Building a strong cybersecurity culture within your organization is crucial. This involves:
Leadership Buy-in: Securing support from top management is essential for allocating resources and prioritizing cybersecurity.
Open Communication: Encouraging employees to report suspicious activity without fear of reprisal.
Continuous Improvement: Regularly reviewing and updating your cybersecurity policies and procedures to stay ahead of evolving threats.
Xaltius Academy's Cybersecurity Course: Your Partner in Network Protection
Navigating the complex world of cybersecurity can be challenging. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the knowledge and skills needed to protect your organization's network. Our expert instructors and hands-on labs will prepare you to effectively implement and manage these critical security measures. Invest in your cybersecurity future and safeguard your organization's valuable assets.
Conclusion
Protecting your organization's network requires a proactive and multi-faceted approach. By implementing these essential cybersecurity measures and fostering a strong security culture, you can significantly reduce your risk of falling victim to cyberattacks and safeguard your organization's future.
2 notes
·
View notes
Text
Recover Stolen Crypto

Cryptocurrency has revolutionized the way we transact, offering decentralized and secure solutions for the modern economy. But with these benefits come risks, including the possibility of theft. Crypto theft can be devastating, leaving victims feeling powerless due to the anonymity of blockchain transactions. However, while challenging, recovering stolen crypto isn’t impossible. This guide will walk you through the steps to maximize your chances of retrieving lost funds and fortify your crypto security. Recover stolen crypto
Understanding How Crypto Theft Happens
Phishing Attacks
Phishing involves tricking users into revealing sensitive information such as private keys or wallet passwords. Scammers often impersonate legitimate platforms via fake websites or emails designed to look authentic. Once you input your details, they gain access to your wallet.
Hacking of Wallets and Exchanges
Crypto wallets and exchanges are prime targets for hackers. Weak security protocols, vulnerabilities in the platform, or user negligence can lead to unauthorized access and fund transfers.
Social Engineering Scams
These scams prey on human psychology. For instance, scammers may pose as trusted individuals or companies, convincing victims to transfer funds or disclose sensitive information.
Malware and Keyloggers
Cybercriminals use malware or keyloggers to monitor user activity. When you type your wallet credentials, the software captures and transmits the data to the attacker.
Immediate Steps to Take After Crypto Theft
Stay Calm and Act Quickly
Panic can lead to poor decisions. Assess the situation logically and act swiftly to prevent further losses.
Identify the Theft Details
Review your transaction history to determine when and how the theft occurred. Note the wallet addresses involved, the amount stolen, and the transaction ID.
Secure Remaining Funds
Transfer your remaining funds to a secure wallet. Hardware wallets or cold storage solutions are preferable as they are offline and immune to hacking.
Contacting Relevant Authorities
Reporting to Local Law Enforcement
File a report with your local authorities. While they may lack blockchain expertise, having an official record can support further recovery efforts.
Involving Cybercrime Units
Specialized cybercrime divisions can investigate the theft and collaborate with international organizations if needed.
Engaging Regulators Like SEC
In cases involving fraudulent investments, report the incident to regulatory bodies like the SEC or FCA to initiate investigations.
Notifying Crypto Platforms and Wallet Providers
How Exchanges Can Assist
Notify the exchange where the stolen funds were transacted. They may freeze suspicious accounts or provide information to investigators.
The Role of Wallet Providers
Wallet providers might help in identifying security vulnerabilities or advising on recovery steps.
Sharing Transaction Details
Provide all relevant details, including the transaction hash, wallet addresses, and any communication with the scammer.
Utilizing Blockchain Analysis Tools
How Blockchain Transparency Aids Recovery
Blockchain’s immutable ledger allows you to trace fund movements. With the right tools, you can monitor the thief’s wallet and subsequent transfers.
Popular Blockchain Analysis Tools
Platforms like Chainalysis, CipherTrace, and Elliptic specialize in tracking stolen cryptocurrency and identifying patterns.
Tracking Stolen Funds
Collaborate with professionals who use these tools to increase your chances of recovering the funds.
Hiring a Cryptocurrency Recovery Expert
Benefits of Professional Help
Experts have the technical knowledge and resources to trace transactions, liaise with platforms, and initiate recovery processes.
Vetting Recovery Agencies for Legitimacy
Ensure the agency has a proven track record. Beware of additional scams that exploit victims seeking help.
Avoiding Additional Scams
Never pay upfront fees without verifying the agency’s legitimacy. Genuine recovery services operate transparently.
Using Social Media and Community Networks
Engaging the Crypto Community
Post about your stolen crypto on forums, Reddit, or Twitter. The community often shares valuable insights or connects you with experts.
Raising Awareness About Stolen Funds
Highlighting the theft publicly can deter thieves from cashing out and put pressure on platforms to assist.
Success Stories
Many individuals have successfully recovered their stolen crypto by rallying community support and leveraging online networks.
Legal Options for Recovering Stolen Crypto
Filing Lawsuits
If you have enough evidence to identify the thief, you may file a lawsuit. Courts can issue orders to freeze assets or compel exchanges to provide information about suspicious accounts.
International Legal Frameworks
Cryptocurrency theft often crosses borders, making it necessary to engage international legal frameworks like the Hague Convention. Collaborating with global enforcement agencies can enhance recovery efforts.
Challenges with Jurisdiction
Jurisdictional issues complicate legal proceedings. Many crypto criminals operate in countries with lax regulations, making prosecution and recovery harder.
Preventative Measures to Protect Cryptocurrency
Using Hardware Wallets
Hardware wallets store private keys offline, making them virtually immune to hacking. They are the gold standard for crypto security and should be your primary storage method for large holdings.
Enabling Two-Factor Authentication (2FA)
2FA adds an additional layer of security to your crypto accounts by requiring a second verification step. Always enable it, preferably using an authenticator app rather than SMS.
Avoiding Suspicious Links and Emails
Phishing scams often start with an innocent-looking link or email. Be cautious and double-check URLs before entering sensitive information. Bookmark trusted platforms to avoid accidental clicks on fake sites.
Educating Yourself on Crypto Scams
Recognizing Common Scam Patterns
From Ponzi schemes to fake giveaways, crypto scams come in many forms. Stay informed about the latest trends and tactics used by scammers.
Staying Updated with News and Security Tips
Follow trusted crypto news outlets and cybersecurity blogs. Awareness is your best defense against evolving threats in the crypto space.
Building a Secure Crypto Environment
Regular Wallet Audits
Periodically review your wallet and transaction history to identify unauthorized activity early. This practice can prevent small breaches from escalating into significant losses.
Diversifying Storage Solutions
Spread your funds across multiple wallets. Use a combination of hardware wallets, paper wallets, and software wallets for added security.
Investing in Cybersecurity Tools
Firewalls, antivirus software, and VPNs can protect you from malware and other digital threats. These tools are essential for safe crypto trading and storage.
Understanding the Limits of Recovery
Why Crypto Recovery Isn’t Guaranteed
The decentralized and pseudonymous nature of blockchain technology makes fund recovery difficult. Once funds are transferred to a thief’s wallet, reversing the transaction is nearly impossible without their cooperation.
Managing Expectations
While recovery efforts are worth pursuing, it’s essential to prepare for the possibility that your funds may not be recovered. Focus on improving your security to prevent future losses.
The Role of Decentralized Finance (DeFi) in Crypto Security
How DeFi Protocols Enhance Transparency
DeFi platforms operate on smart contracts, which are transparent and immutable. This openness can help in tracking fraudulent activity and ensuring secure transactions.
Risks Associated with DeFi Platforms
Despite their benefits, DeFi platforms are not immune to vulnerabilities. Exploits in smart contracts and lack of insurance can lead to significant losses.
Recovering stolen cryptocurrency is no easy feat, but it’s not entirely hopeless either. By taking immediate action, leveraging blockchain tools, and engaging with experts, you can increase your chances of recovering your funds. Most importantly, prioritize prevention by adopting stringent security measures. Remember, in the world of cryptocurrency, staying one step ahead of scammers is your best protection.
Contact Info: Email: - [email protected]
2 notes
·
View notes
Text
Best Methods to Hard Reset Any Android Device
Discover the most effective methods to hard reset any Android device, restoring it to factory settings and fixing software issues.
2 notes
·
View notes
Text
Complete Guide to Disable Find My iPhone on iOS 10 Without Any Password
Disabling Find My iPhone on iOS 10 without any password can often seem like a daunting task, particularly if you’ve forgotten the Apple ID associated with your device. Apple's security measures are designed to protect user data, which can make the process feel intimidating. However, there are legitimate reasons for wanting to turn off this feature, such as when selling or giving away your device or dealing with a locked iPhone that you no longer use. This comprehensive guide aims to equip you with the necessary steps to navigate this challenge smoothly and effectively, focusing specifically on disabling Find My iPhone on iOS 10 without any password.
In this article, we will explore various methods to disable Find My iPhone on iOS 10 without any password required. From utilizing recovery options to employing specialized tools, we will outline the strategies you can employ to regain control over your device. Whether you’re a tech novice or a seasoned user, our step-by-step instructions will help ensure that you can disable this feature safely and effortlessly. By the end of this guide, you will have the confidence and knowledge to manage your iOS device and its security settings with ease, all while successfully disabling Find My iPhone on iOS 10 without any password.
What is Find My iPhone?
Find My iPhone is a robust feature developed by Apple that helps users locate, manage, and secure their Apple devices, including iPhones, iPads, Macs, Apple Watches, and AirPods. It is part of the larger Find My service, which combines location tracking for all Apple devices associated with an Apple ID. Below is a detailed overview of its functionalities, features, and requirements:
Key Features:
Location Tracking: Users can see the current location of their device on a map. If the device is nearby, they can play a sound to help locate it.
Lost Mode: If the device is lost or stolen, users can enable Lost Mode, which locks the device and displays a custom message with a contact number on the screen.
Remote Erase: In case of theft or loss, users can remotely erase all data on the device to protect their personal information.
Find Other Devices: Besides iPhones, Find My can also locate iPads, Macs, Apple Watches, and AirPods.
Activation Lock: When Find My iPhone is enabled, it also activates a security feature that prevents anyone from using the device without the owner’s Apple ID and password, making it harder for thieves to access or sell the device.
Why To Disable Find My iPhone on iOS 10?
Disabling Find My iPhone on iOS 10 can be useful in certain situations where you need to remove the security feature. Below are some common reasons why users might disable it, along with important considerations.
Preparing to Sell or Transfer the Device
If you're planning to sell, gift, or transfer your iPhone to someone else, it's crucial to disable Find My iPhone before doing so. This step is necessary to remove your Apple ID from the device and disable Activation Lock, which ties the iPhone to your Apple ID. Without disabling this feature, the new owner would be unable to access or use the iPhone fully, as they would need your Apple ID credentials to unlock it.
Restoring or Resetting the Device
When you need to perform a full restore or reset on your iPhone, whether for troubleshooting or preparing the device for resale, Find My iPhone must be turned off. iTunes or Finder on a Mac will not allow a full factory reset or software restore if Find My iPhone is enabled because of the Activation Lock feature, which is designed to prevent unauthorized use of the phone.
Without disabling Find My iPhone, any attempt to restore the phone would be halted, requiring you to first enter your Apple ID password to proceed with the process.
Troubleshooting and Repairs
Certain troubleshooting steps and repairs may also require disabling Find My iPhone. For example, if your iPhone encounters a serious issue and you need to restore it via recovery mode, the process won't fully work unless Find My iPhone is disabled first. Additionally, some third-party repair services may require it to be turned off before working on the device to ensure they can perform necessary functions like hardware testing or software restoration.
Reducing Battery Drain
Although less common, some users may disable Find My iPhone to reduce battery drain, particularly if location services are frequently active. Since Find My iPhone relies on tracking the device's location using GPS and other location services, it can cause a minor increase in battery usage. For users who don't find themselves frequently needing the feature, turning it off might help conserve battery power.
Disable Find My iPhone on iOS 10 With Passixer:
Here’s a simple and effective method to disable Find My iPhone on iOS 10 without any password with Passixer, using a trusted iOS unlocking tool like Passixer iPhone Unlocker and a reliable USB cable. This solution is perfect for users looking for a straightforward way to unlock their devices without hassle.
Passixer iPhone Unlocker is an intuitive application designed specifically for iPhone and iPad users who need to bypass security features effortlessly. Whether you’ve forgotten your passcode or need to dissociate an old Apple ID, this powerful software can effectively disable the Find My iPhone feature without the need for the original password. This capability is particularly advantageous for individuals purchasing second-hand devices still linked to a previous owner’s Apple ID.
Key Features
Unlock Any iOS Screen Lock: Easily removes screen locks like 4-digit/6-digit PINs, Face ID, and Touch ID, ensuring you can regain access to your device without complications.
Remove Apple ID Without Password: Unlink an Apple ID without needing the original password, enabling seamless access to all Apple services. This is especially helpful for users with second-hand devices still linked to a previous owner’s Apple ID.
Bypass iCloud Activation Lock: With Passixer, you can bypass the iCloud Activation Lock, simplifying the process of using previously owned devices.
Remove MDM Lock: This software offers two methods to remove Mobile Device Management (MDM) restrictions from devices that belong to companies or educational institutions, without needing passwords or jailbreaking.
Remove Screen Time Passcode: Quickly bypass the Screen Time passcode while ensuring no data is lost, making it ideal for managing family devices.
Remove iTunes Backup Encryption: Access encrypted iTunes backup passwords to retrieve your backup data without risk of information loss.
Device Compatibility: Supports a wide range of devices, including iPhone 4 to iPhone 15, all iPads, and iPod Touch models, and is compatible with iOS 17 and earlier versions.
Cross-Platform Support: Passixer works seamlessly on Windows (11/10/8.1/8/7) and Mac (OS X 10.7 and later, including macOS Big Sur and Monterey).
How To Use:
Step 1: Download and Install Passixer
Head to the official Passixer website to download the program. Complete the installation and launch the software, then select "Remove Apple ID" from the main menu.
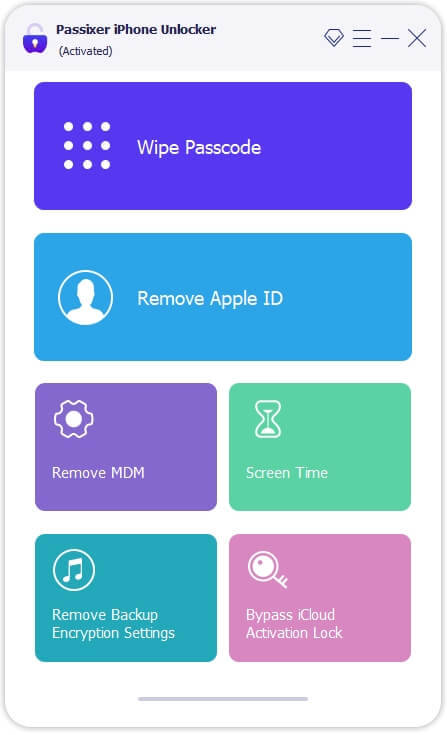
Step 2: Connect Your iPhone
Use a USB cable to connect your iPhone (with Find My iPhone enabled) to your PC or Mac. Click "Start" in the software to initiate the unlocking process.
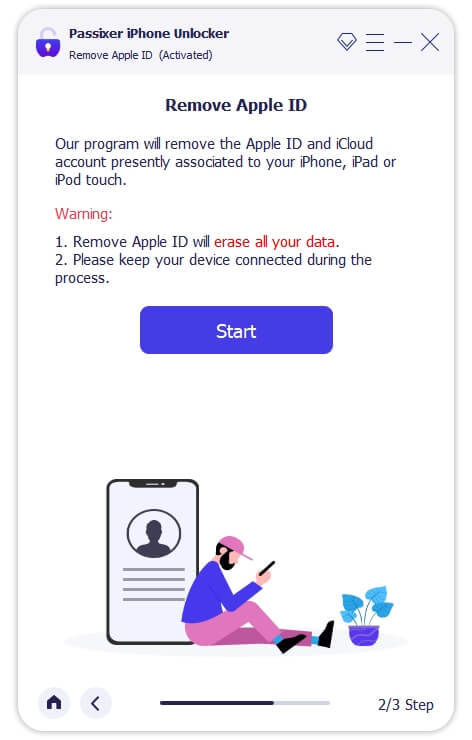
Step 3: Remove Your Apple ID
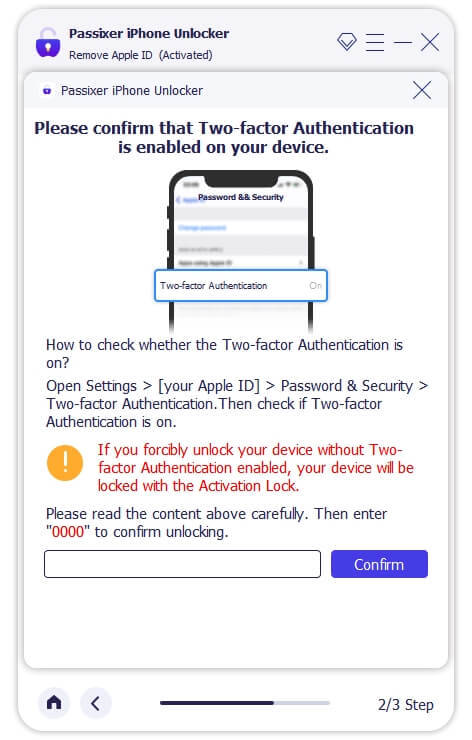
For iPhones running iOS 11.4 or later, ensure that Two-Factor Authentication is enabled. Verify device information, download the required firmware, and start the Apple ID removal process. This will also automatically deactivate the Find My iPhone feature.
Reset your iPhone settings by opening the Settings app, navigating to General, and selecting Reset > Reset All Settings. Once completed, Passixer will unlink the associated Apple ID.
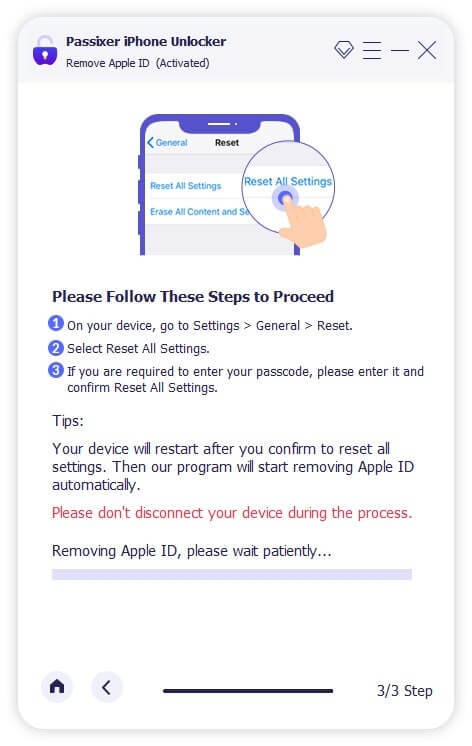
Disabling your Apple ID on an iPhone will also automatically turn off the Find My iPhone feature.
Pros:
No Password Needed: Removes the Apple ID without needing the original password, making it perfect for second-hand devices.
Bypasses Activation Lock: Unlocks iCloud Activation Lock to access devices linked to another user’s Apple ID.
Versatile: Also removes screen locks, bypasses MDM restrictions, and disables Screen Time passcodes without erasing data.
Broad Device Compatibility: Supports a wide range of devices, from iPhone 4 to iPhone 15, as well as iPads and iPod Touch devices.
Cross-Platform Availability: Works on both Windows and Mac.
Cons:
Costs Involved: While some versions offer free trials, full functionality typically requires a paid version.
Pricing Plan:
Enjoy secure and immediate email delivery, along with complimentary customer support. This software is designed specifically for Mac users.
Pricing Options: Select from the following plans: a 1-year license for $39.99, a 1-month license for $29.99, or a one-time lifetime license for $69.99. Each plan allows you to unlock up to 6 iOS devices on a single PC (taxes not included).
Discount Offers: Get up to $20 off on the 1-year and 1-month licenses, with original prices being $59.99 and $39.99, respectively.
Other Ways To Disbale Find My iPhone on iOS 10
Disabling Find My iPhone on iOS 10 without a password can be a complex process due to Apple's robust security measures. However, if you find yourself in a situation where you need to disable this feature, there are several methods you might consider. Below are detailed step-by-step instructions for each method, along with important considerations.
Method 1: Restore via iTunes
Requirements:
A computer with iTunes installed.
A USB cable to connect your iPhone to the computer.
How To Use:
Install iTunes: Make sure you have the latest version of iTunes installed on your computer. You can download it from the Apple website.
Connect Your iPhone: Use a USB cable to connect your iPhone to the computer. Launch iTunes once your device is connected.
Put iPhone into Recovery Mode:
For iPhone 6s and earlier: Press and hold the Home button and the Power button simultaneously until you see the recovery mode screen.
For iPhone 7 and 7 Plus: Press and hold the Volume Down and the Power buttons until you see the recovery mode screen.
For iPhone 8 and later: Quickly press and release the Volume Up button, then the Volume Down button, and finally press and hold the Side button until you see the recovery mode screen.
Restore iPhone: In iTunes, a message will appear indicating that a device in recovery mode has been detected. Choose the option to Restore. This will erase all content and settings from your iPhone, including the Find My iPhone setting.
Set Up iPhone: After the restore is complete, you can set up your iPhone as new or restore from a backup. Note that if Find My iPhone is still activated, it may ask for the Apple ID and password associated with the device.
Method 2: Jailbreak the Device
Warning: Jailbreaking voids your warranty and can expose your device to security risks. Use this method with caution.
Requirements:
A computer with a jailbreaking tool (e.g., Pangu, unc0ver).
How To Use:
Backup Your Data: Before attempting to jailbreak, make sure to back up your data using iTunes or iCloud, as this process may erase your device.
Download Jailbreaking Tool: Download a reputable jailbreaking tool that is compatible with iOS 10.
Connect Your iPhone: Use a USB cable to connect your iPhone to your computer.
Run the Jailbreaking Tool: Launch the jailbreaking software and follow the on-screen instructions to initiate the jailbreak. This usually involves clicking a button to start the process.
Complete the Jailbreak: Once the jailbreak is complete, your device will restart. You may need to install a Cydia app for further customization.
Disable Find My iPhone: After jailbreaking, you can use certain tweaks in Cydia to disable Find My iPhone. Search for relevant tools and follow their instructions.
Method 3: Contact Apple Support
How To Use:
Gather Documentation: Collect any documents that prove your ownership of the device, such as the original receipt or invoice.
Contact Apple Support: Visit the Apple Support website or call their support line. Explain your situation and provide the necessary documentation.
Follow Their Instructions: Apple Support may guide you through the process of disabling Find My iPhone. They may ask for your device's serial number and other identifying information.
Wait for Resolution: Depending on your situation, Apple may take some time to resolve the issue. Follow up as needed.
Conclusion:
In conclusion, disabling Find My iPhone on iOS 10 without a password may seem like a challenging endeavor, but with the right tools and guidance, it can be achieved effectively. Understanding the various legitimate reasons for wanting to disable this feature—such as preparing a device for sale, performing a factory reset, or troubleshooting issues—helps users navigate the process with purpose. By utilizing specialized tools like Passixer or following alternative methods, individuals can confidently regain access to their devices and manage their settings without the burden of forgotten passwords.
Ultimately, the key takeaway from this guide is that while Apple's security measures are designed to protect user data, there are practical solutions available for those in need. Whether you're a tech novice or an experienced user, our comprehensive instructions empower you to tackle this challenge head-on. By following the steps outlined in this guide, you can disable Find My iPhone on iOS 10, ensuring a smooth transition as you either pass on your device or regain control over it. With the right approach and resources, you can successfully navigate the complexities of Apple’s security features and regain full access to your device.
2 notes
·
View notes
Text
Understanding Ransomware: A Guide for Small Businesses
Ransomware is a malicious software that restricts access to your device or data until a ransom is paid. In this article, we explore how ransomware enters your system, how it works, and how to prevent attacks. A ransomware attack occurs when malware prevents access to your device or data until a ransom is paid. Attackers may threaten to publish data if the ransom is not paid. Ransomware can be locker ransomware, which locks access, or crypto ransomware, which encrypts files. Ransomware usually enters a device, assesses critical data, encrypts files, and demands a ransom. Paying the ransom doesn't guarantee recovery, so it's not recommended. Historical ransomware attacks include CryptoLocker, CryptoWall, Locky, WannaCry, NotPetya, and more. To prevent ransomware, you can have good network policies, secure servers, backup data offline and online, and encourage safe online behavior. Installing security software like antivirus, firewall, and email filtering can also help. Advanced strategies include ATP, email filtering, and security audits. In case of a ransomware infection, isolate the device, assess damage, check for a decryption key, and restore from backups. Seek professional help for recovery. Immediate actions post-infection include isolation, incident response activation, legal compliance, and stakeholder communication. Ransomware can get on your device through spam emails, phishing, pop-ups, pirated software, weak passwords, and more. Attackers prefer cryptocurrency payments for anonymity. Ransomware can spread through Wi-Fi, infecting all connected devices. Protect yourself from ransomware by following the prevention strategies mentioned above. Stay safe online and be cautious of suspicious emails, links, and downloads. And remember, it's crucial to have backups and a plan in case of a ransomware attack. #StartupBusiness #Businesses #Guide #howdoesransomwarework #Ransomware #ransomwareattack #Small #Understanding #whatisaransomware #whatisaransomwareattack #whatisransomware https://tinyurl.com/228z9vpf
#Businesses#Guide#how does ransomware work#Ransomware#ransomware attack#Small#Understanding#what is a ransomware#what is a ransomware attack#what is ransomware
1 note
·
View note
Text
Idk how to explain this without being long-winded, but it’s my blog so whatever.
Basically, I have a 2011 MacBook Pro 15”. I’ve replaced the battery and upgraded the RAM and replaced the 500GB HDD with a 500GB SSD. It’s great! The machine is truly the fastest mobile computer I have.
The 2011 MBP was let go from software updates a while ago, meaning, natively, macOS High Sierra is as high as I can get the thing.
Luckily, this computer is from an era when Apple actually made computers and not eWaste, so I just erased macOS off of it and flashed Zorin OS (an Ubuntu-based Linux distro) onto it. The computer is now even better! It’s my primary productivity machine. The display, speakers, battery life, and thermals are all pretty bad, but it’s just so snappy and problem free I can’t help it.
Now, when I set up Zorin OS I used LVM Encryption to encrypt the entire disk. Basically, upon booting, before anything happens, I’m prompted with a password box. Once I put in the encryption key, the computer would continue booting and bring me to my usual login screen. Great! Easy peasy, extra secur-sy. Well. That was the case.
Somehow, in my efforts to find a way to stop Linux from using my MBP’s Discrete GPU in favor of its Integrated (more efficient, less power hungry) one, I broke something in the EFI or SMC idk. Reinstalling didn’t help. MacOS Recovery mode didn’t help. The only way I fixed it was by wiping the device, running the installer USB, downloading the script I used to fuck it up, and then running it to undo what I previous had it do. This worked. Luckily, I was keeping the machine backed up with Timeshift. So, I wiped the computer again and installed Zorin OS, fresh, reinstalled Timeshift, and restored from backup. The only problem?
When I reinstalled Zorin, I didn’t use LVM Encryption because I was tired of having to manually type in that 25 randomized character password I chose. As a result, now every time I boot the computer, I’m prompted with a “Waiting for encrypted device, (name).” That prevents the machine from booting for about 5 minutes until it just randomly decides “ope, never mind” and finally takes me to my login screen. It does nothing in prohibiting me from using the computer expect prolong it. It’s just annoying and weird as hell, and I have no idea how to get rid of it.
Clearly, the way Timeshift resorted the device has it thinking it’s still an encrypted volume, and I have no idea how to tell it that it is not.
But anyway, it just aggravates me, and I needed to ramble and vent about it. Carry on.
#rambles#computer#computer operating system#os#software#linux#zorin#zorinos#zorin os#annoying#annoyance#apple#fuck apple#macbook#macbook pro
11 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
O&O BlueCon 20
Ensure Business Continuity with Reliable Disaster Recovery Solutions. O&O BlueCon offers a wide range of programs for repairing systems, searching and correcting errors, restoring lost data, resetting passwords. https://find-your-software.com/oo-software/bluecon-20/

2 notes
·
View notes
Text
Streamlining Internal IT Support with a Smart Ticket Tracking Tool – A Deep Dive into Hoicko.com
In any forward-thinking company, technology is at the heart of everyday work. Technical problems, ranging from software bugs to hardware failures, pop up all the time. How well your in-house IT support team tackles these problems has a direct effect on how productive everyone is, no matter which department they're in.
This is exactly why a top ticket tracking management tool is so important.
Let's look at a typical situation where this really matters: managing internal IT support tickets. Think about your company's IT team. They have to deal with all sorts of tech problems that employees run into. These might be things like:
Resetting passwords
Fixing printers that aren't working
Installing new software
Dealing with servers that are down
Sorting out dodgy internet connections
Usually, these kinds of requests get handled through emails or casual chats on things like WhatsApp or Slack. But what happens then? Tickets get lost, responses are slow, nothing gets prioritised properly, and everyone ends up fed up.
Now picture this:
All these issues are getting dealt with in one place, through a ticket tracking system that you can tailor to your needs.
And that's what Hoicko.com is for.
Why Hoicko.com is the Ideal Ticket Tracking System for IT Support Teams
Hoicko.com offers a user-friendly, cloud-based ticket tracking and task management platform designed to streamline how teams handle internal requests. Here's how it revolutionises internal IT support:
1. Consolidated Request Handling
IT teams can now manage all support tickets conveniently from a single dashboard on Hoicko, eliminating the need to switch between multiple inboxes, chat threads, and spreadsheets. Each request is meticulously logged as a ticket, ensuring no issues are overlooked.
Example:
Imagine an employee from the finance department facing a software crash. Rather than directly emailing the IT head, they simply log the problem on Hoicko. The ticket is then automatically routed to the appropriate technician, monitored in real-time, and resolved promptly within the service level agreement (SLA).
2. Automated Ticket Routing and Progress Updates
With Hoicko, you can establish automated workflows to sort and direct tickets based on predefined criteria like department, urgency, or ticket category.
Additionally, you can set up automated progress notifications to keep employees informed about their issue's assignment, ongoing work, or resolution—thereby minimising constant back-and-forth communication.
3. Tailored Forms and Categories
IT problems come in all shapes and sizes. That's why Hoicko gives you the freedom to design your own forms and categories, mirroring the specific support needs within your organisation.
For example, you can categorise issues under:
Hardware
Software
Internet/Network
Data Recovery
User Access
This custom approach leads to more accurate classification, quicker identification of critical issues, and more organised reports.
4. Setting Priorities and Managing Service Level Agreements (SLAs)
Let's face it, in the world of IT, some problems demand immediate attention, while others can wait. Hoicko.com empowers you to tag issues with priority levels like Low, Medium, High, or Critical. You can also define clear deadlines for responses and resolutions (SLAs).
This way, a routine password reset won't consume the same resources as a critical server crash.
5. Analyzing Performance with Reports
Are your team's response times up to par? Which departments are logging the most requests? What issues keep coming back?
Hoicko's integrated analytics provide managers with a clear picture of these trends. They can spot bottlenecks, fine-tune resource distribution, and make informed decisions. By using data as a guide, your overall IT support strategy becomes much more effective.
6. Teamwork Makes the Dream Work: Notes & Collaboration
Hoicko is all about teamwork! Your IT folks can easily leave private notes on tickets, loop in other team members for their expertise, or escalate tricky issues, all without leaving the app. No more jumping between different tools or getting lost in endless chat threads. It's all right there, streamlined and simple.
7. Ticket Widget: Submitting Support Requests Made Super Easy
With Hoicko, you can pop a handy "Raise a Ticket" widget right on your company's internal website or portal. Employees won't even have to log in! They just fill out a quick form, and poof! The system takes it from there. This makes it a breeze for everyone, even those who aren't tech-savvy, to report issues without any headaches.
Real-World Example: From Chaos to Control
Imagine your company has 200 employees. Every day, about 15-20 of them run into IT problems. Trying to manage all that with just emails and spreadsheets? That's a recipe for madness! It's just not practical or manageable in the long run.
But with Hoicko, here's what happens:
Tickets get logged and organised instantly.
The right technicians are automatically notified and assigned.
Employees get real-time updates on what's happening.
Every single interaction is tracked and recorded.
Monthly reports help you spot trends and areas for improvement.
In just a few short weeks, your IT team will be working like a well-oiled machine, your employees will be happier, and those critical tech issues? They'll get solved without turning into a major drama. It's a win-win for everyone!
Why Hoicko Stands Out from the Crowd
What makes Hoicko.com a better choice than the rest? Unlike those one-size-fits-all ticketing solutions, Hoicko.com offers complete customisation, requires no coding, and is designed to fit seamlessly into your actual business processes. It doesn't matter if you're a fledgling startup, a growing SME, or a massive corporation; Hoicko grows right alongside you. It is the best ticket tracking tool in India. The real game-changer? You can forget about hiring expensive developers or struggling to learn complicated new software. Hoicko's intuitive drag-and-drop interface makes it incredibly user-friendly.
But that's not all! Hoicko packs in extra features, such as project tracking, task dependencies, customisable user permissions, and personalised dashboards based on roles. This means Hoicko is more than just a way to manage tickets; it's your central command centre for all your operational needs.
If your IT support team is still relying on those dusty old methods, it's time for an upgrade. Ticket tracking isn't a fancy extra anymore—it's essential for keeping your teams running smoothly, efficiently, and happily.
Discover how Hoicko.com can be your go-to partner for revolutionising your internal support operations. It's a tool that's adaptable, quick, and built with real users in mind.
👉 Head over to Hoicko.com to begin your complimentary trial and discover a whole new world of effortless internal support.
#hoicko#hoickotechnologies#hoickotech#hoickonocodeapp#software#tool#nocodeapp#BestTicketTrackingTool#BestTicketTRackingToolInIndia
0 notes