#picoctf
Explore tagged Tumblr posts
Text
I think I have the perfect audience for this post.
If you're a
person who's mildly into software;
who doesn't have much or any experience with infosec;
and who likes puzzles,
you should try participating in a ctf (ctftime.org, picoctf). Challenges are usually different/abstract/weird enough to not feel like work (though web challenges are pretty much ruined for me now tbh) and you still get to hone your linux, forensic, pwn and other skills.
You really don't need any special skills to get started except for knowing how to search for things and the ability to not compare yourself to the top teams too much.
happy to answer any ctf related asks btw
#I solved a ~medium difficulty challenge today. first one in like 2 years. it felt SOOOO good#i pretty much stopped playing ctfs after getting my degree. which was a shame tbh
215 notes
·
View notes
Text

Free Resources for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Free Online Courses
Linux Foundation Cybersecurity Courses - many of their beginner/introductory courses are free
Professor Messer's Security+ Course - a great intro to cybersecurity, gave me the skills to pass my Security+ exam
Khan Academy Cryptography - solid foundations for understanding the math behind encryption
ISC2's new entry level cert & training CC is free, although for a limited time
Linux Journey - learn Linux, the command line, and basic networking
Free CTFs & Ways to Practice
What is a CTF? - HackTheBox isn't a free platform, but this is a good article explaining what a CTF is and how to approach it
OverTheWire Bandit - practice your Linux skills
PicoCTF - this one already ran this year but their website has plenty of resources
Microcorruption - binary exploitation challenges
Hacker101 - web security CTF
Cryptopals Cryptography Challenges
Nightmare - binary exploitation & reverse engineering challenges
Cybersecurity News: follow what's happening in the industry
KrebsOnSecurity - security & cybercrime news, investigative journalism
SANS StormCast - daily 5-minute security news podcast
SANS Internet Storm Center - security blog posts
Cisco Talos blog - security news, threat intelligence & malware investigations
Schneier on Security - security & society
Black Hills Information Security webcasts
Darknet Diaries podcast
Other Free Resources
Trail of Bits's CTF Field Guide
PicoCTF Resources and Practice
SANS Cheat Sheets - all areas of security & tech
OWASP Cheat Sheets - application security & web attacks
LaurieWired's YouTube channel - high-quality videos on low-level tech
LiveOverflow's YouTube channel - binary exploitation
SANS Webinars
Cybersecurity Certifications Roadmap
Cybersecurity Job Supply and Demand Map (for the U.S.)
EFF's Surveillance Self-Defense - guides for how to protect yourself online
Don't Forget the Library!
If you have access to a public or school library, check out their technical books and see what they have to offer. O'Reilly and No Starch Press are my favorite publishers for technical and cybersecurity books, but be on the lookout for study guides for the Security+ and other certifications - these will give you a good introduction to the basics. I wrote more about cybersecurity books in yesterday's masterpost.
60 notes
·
View notes
Text
discovered picoCTF today and locked tf in for 10 hours this is a healthy consumption pattern that will maintain consistent
0 notes
Text
trying out picoctf and man it really is testing my internet skills
0 notes
Text
be-quick-or-be-dead-2
Problem is similar to the first one: make the program run faster.
./be-quick-or-be-dead-2 Be Quick Or Be Dead 2 =====================
Calculating key... You need a faster machine. Bye bye.
Main function is the same:
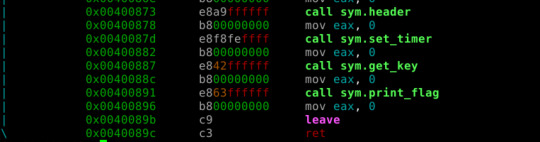
sym.calculate_key calls sym.fib(passing argument 0x3f7 = int 1015), which seems to be a recursive function doing Fibonacci sequencen calculations.
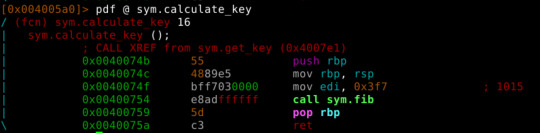
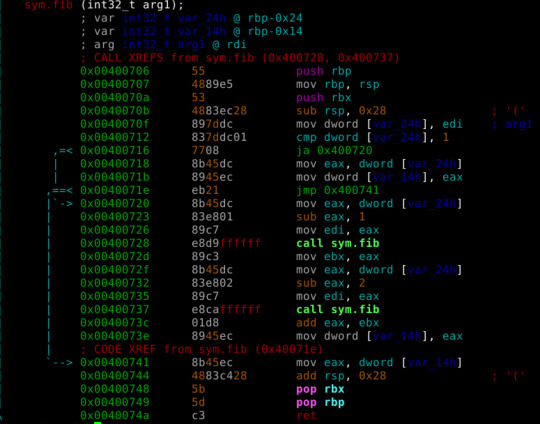
We can calculate fib(1015) and pass it to make it faster.

and we get 17662975587330736941
The patch is done to sym.get_key. Note rax is used for 64-bit registers.
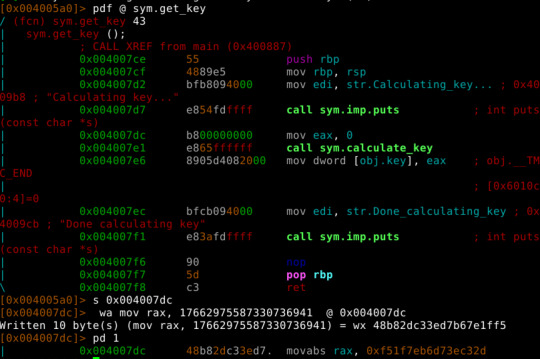
We need 10 bytes to write, 0x004007dc to 0x004007e5, and by doing this we are effectively overwriting the call to sym.calculate_key function, which is what I want.
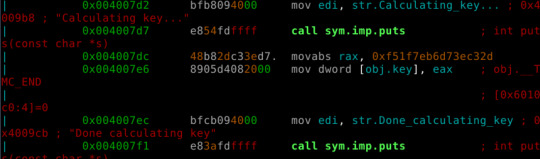
./be-quick-or-be-dead-2-patched Be Quick Or Be Dead 2 =====================
Calculating key... Done calculating key Printing flag: picoCTF{the_fibonacci_sequence_can_be_done_fast_73e2451e}
1 note
·
View note
Text
PicoCTF here i come! Day 96
Daily sport-exercises:
running the 8.25 in 43.20
yoga
Working on my education:
Todays TryHackMe Rank : 2588
SMTP, POP3 and Imap... tough topic for the first time. Also: Signed in with my Team on PicoCTF2021! This will be fun.
Writing it down:
So Today i was working hard on getting everything right, got my paycheck. My To-do-List and my work done. It was a rewarding day in the sense that the feedback that i got was good. I also got through the challenge of not getting that extra sugery stuff and avoiding smoking. I’m a litte bit impressed from my self.
What would I have liked to have done differently today?
Finishing my To-do-List
not staying up for this long
0 notes
Note
Hello :)) I love your art and the sharp angles you draw, I just thought you might enjoy my journey in trying to ascertain what Picoxgf is:
"okay so they're not OCs, let's pop this into the Google here, probably not pico de Gallo, aha "picoCTF is a free computer security education program..." Ah I see so it's like an anthropomorphism of a computer program and I guess the other two are like viruses or hackers well I've seen weirder things the small blue one could be a hacker and the tall red one could be a virus- oh it's autocorrected lol HMM... It's autofilling Pico FNF? Five nights Freddy's?? Are these humanoids of the Freddy things??? They don't look like- OH FRIDAY NIGHT FUNKING. So they exist! Now what is... that....."
Side note, I am wholly unfamiliar with FNAF lmao
I don't think I will be playing the game but you make the characters look fun :))
✌️
7 notes
·
View notes
Text
I like Python. It's more complicated than Batch for sure, but I'll be damned if I'm not having fun learning it.
#okokok#I don't know too much about either#I know enough about batch to get the job done but that's it#tbh I only switched to python because I took part in picoctf last school year with my classmates#it was fun#started making a little text game with it#though it might take a while to finish#and I mean a LONG while#but fuck it ya know#it'll be a learning experience#python#programming
1 note
·
View note
Text
PicoCTF-BufferOverflow1
First, I observed that this vuln function uses gets function which I can workwith.

And I saw that the buffer size is 32

It also has a win function

So what i need to do is just to overwrite the return address to the win function.
So i run the readelf to check where is the win function



so i pipe it with the overflow gibberish into vulnv and get the flag


7 notes
·
View notes
Text
Something awesome - reversing write-ups
As usual, write-ups can be found below:

Reversing Warmup 1
Throughout your journey you will have to run many programs. Can you navigate to /problems/reversing-warmup-1_0_f99f89de33522c93964bdec49fb2b838 on the shell server and run this program to retrieve the flag?
The problem run is known as an ELF binary. It is the most common program format on Linux. Here are the steps to run the program:
$ cd /problems/reversing-warmup-1_0_f99f89de33522c93964bdec49fb2b838 $ ls run $ ./run picoCTF{welc0m3_t0_r3VeRs1nG}
flag: picoCTF{welc0m3_t0_r3VeRs1nG}
Overall this simple challenge is here to help users get comfortable with using executable files, and how to run them.
Reversing Warmup 2
Can you decode the following string dGg0dF93NHNfczFtcEwz from base64 format to ASCII?
Base64 is a common encoding format. The main differences between encoding and encrypting as we saw in our previous cryptography chapter are as follows:
Encoding transforms data into another format using a scheme that is publicly available so that it can easily be reversed.
Encryption transforms data into another format in such a way that only specific individual(s) can reverse the transformation.
In summary:
Encoding is for maintaining data usability and uses schemes that are publicly available.
Encryption is for maintaining data confidentiality and thus the ability to reverse the transformation (keys) are limited to certain people.
To decode the string, we can use python, which is a really useful programming language for writing quick scripts or computing numbers really efficiently:
Python 2.7.15 (default, Jun 17 2018, 12:51:03) [GCC 4.2.1 Compatible Apple LLVM 8.0.0 (clang-800.0.42.1)] on darwin Type "help", "copyright", "credits" or "license" for more information. >>> 'dGg0dF93NHNfczFtcEwz'.decode('base64') 'th4t_w4s_s1mpL3'
flag: picoCTF{th4t_w4s_s1mpL3}
Assembly-0
What does asm0(0xb6,0xc6) return? Submit the flag as a hexadecimal value (starting with ‘0x’). NOTE: Your submission for this question will NOT be in the normal flag format. Source [1] located in the directory at /problems/assembly-0_0_5a220faedfaf4fbf26e6771960d4a359.
Let’s take a look at the assembly code:
.intel_syntax noprefix .bits 32 .global asm0 asm0: push ebp mov ebp,esp mov eax,DWORD PTR [ebp+0x8] mov ebx,DWORD PTR [ebp+0xc] mov eax,ebx mov esp,ebp pop ebp ret
As you can see, there’s a function named asm0 that is being exported by the line .global asm0, and the content of the function is right below the asm0 : label. We know that the function is called with the argument of 0xb6 and 0xc6 which are at [ebp+0x8] and [ebp+0xc] respectively.
By converting the assembly code to pseudo-code, we can observe the logic of the function.
eax = arg1 ebx = arg2 eax = ebx
Because we know that an assembly function always returns the value than is in the eax register, the asm0 should always return the second argument passed to it; therefore, the return value is 0xc6.
Flag: 0xc6
Assembly-1
What does asm1(0xcd) return? Submit the flag as a hexadecimal value (starting with '0x’). NOTE: Your submission for this question will NOT be in the normal flag format. Source [1] located in the directory at /problems/assembly-1_2_ac6a59ca77a2d619ddabb3c3ffedb9a8.
This problem is similar to the previous challenge. The code can be found below:
.intel_syntax noprefix .bits 32 .global asm1 asm1: push ebp mov ebp,esp cmp DWORD PTR [ebp+0x8],0x98 jg part_a cmp DWORD PTR [ebp+0x8],0x8 jne part_b mov eax,DWORD PTR [ebp+0x8] add eax,0x3 jmp part_d part_a: cmp DWORD PTR [ebp+0x8],0x16 jne part_c mov eax,DWORD PTR [ebp+0x8] sub eax,0x3 jmp part_d part_b: mov eax,DWORD PTR [ebp+0x8] sub eax,0x3 jmp part_d cmp DWORD PTR [ebp+0x8],0xbc jne part_c mov eax,DWORD PTR [ebp+0x8] sub eax,0x3 jmp part_d part_c: mov eax,DWORD PTR [ebp+0x8] add eax,0x3 part_d: pop ebp ret
For this challenge, control flow is being introduced.
In the case of the challenge, [ebp+0x8] is the argument that gets passed into the function, specifically 0x76. Because 0x76 is not larger than 0x98, we will not follow the first jg (jump greater than) to part_a.
For the second comparison, because 0x76 doesn’t equal 0x8, we are going to jump to part_b (jne means jump not equal).
In part_b, the argument is loaded into eax and 3 is subtracted from it. After that, the function returns (with the jmp to part_d) - therefore, we just have to take 0x76 and subtract 0x3 from it to get the flag: (0x73).
2 notes
·
View notes
Note
hiii, i am also interested in cybersecurity but don't know how to gain skills to start it as a career after graduation next year
Hi! First of all, good luck with your last year before graduation! it can be kinda hectic and kinda scary, but there are lots of good things in store!
The cool thing about cybersecurity (and computer science in general tbh) is that there are lots of opportunities to learn things on your own!
(Brief side note: my recommendations are U.S.-centric, just because that's where I am and where my experience is. The industry may be a bit different if you're in a different country, but lots of things should be the same.)
This got very long, so I'm putting it under a read more. The tl;dr is:
play CTFs
get an entry-level certification (or even just study for one!) - the CompTIA Security+ is a great choice
join or start a cybersecurity club on campus (or join a professional organization like Women in Cybersecurity)
stay up to date with cybersecurity news
learn some skills on your own time: networking, programming, general IT skills, etc.
If anyone wants more information about any of these suggestions, let me know & I'd love to make a separate post about them!
CTFs Capture the Flag games are how I initially got into cybersecurity and they're a fantastic way to practice new skills in a fun, real-world kind of environment. If you've never done one, you absolutely should! Here are a few of my faves:
Cyber FastTrack is my top recommendation. It's only available to current college students in the U.S. (and requires U.S. citizenship), but the challenges are fantastic & they have awesome learning materials. It generally runs October-April each year. I did well in this CTF and got a scholarship for the SANS.edu Undergraduate Certificate in Applied Cybersecurity - that's 4 certifications & nearly $19k of free training. It's ridiculous and I love it. Highly recommend.
CyberStart is the same set of challenges, but you have to pay to access all of it. It also has programs similar to Cyber FastTrack for high school students, high school girls, and UK and Canadian students - check their about page.
picoCTF - I haven't done this one before but it's constantly recommended as a good beginner CTF. It looks like you can practice online at any time, but they also do a yearly high school competition.
OverTheWire Bandit - This site has several different wargames (similar to CTFs) that teach you different topics, but Bandit is the one to start with. It teaches you lots of Linux things & will give you the skills to play the others.
Certifications Certifications are a recommendation or a requirement for many (if not the majority) of cybersecurity jobs. They're not a replacement for experience, but getting one as a student demonstrates that you have the passion and work ethic to pursue cybersecurity on your own. Studying for an entry-level certification is also a fantastic way to get a general understanding of the field and pick up some essential knowledge.
The main one I see recommended is the CompTIA Security+. I studied for this certification very slowly for a long period of time, because I was using it to learn cybersecurity in general. It covers a lot of material but it also goes very in-depth in places. I got this cert because I knew it could get my foot in the door in lots of places, and just telling people that I was studying for it was a way to impress potential employers!
Professor Messer has a ton of fantastic, 100% free training material for the CompTIA certifications. In addition, you can use all the free resources that you have as a student to study for this. I used LinkedIn Learning courses, check if your college or local library give you free access to this.
In addition, there are technically 2 CompTIA certifications you should have before you get the Security+: the A+ and the Network+. The A+ is just general IT knowledge, and you can probably skip it if you're decent with computers. Having a solid understanding of networking is super important, so it's worth going through the material for the Network+ even if you're not going to pay to take the exam.
(Also, taking the Security+ exam while you're a student lets you get the academic discount! I think that saved me $100-$150.)
Clubs and Professional Organizations Join a cybersecurity club at your school if there is one. It's a great way to meet other students interested in the same things and get advice. They may also have tech talks, run CTF events, or have local professionals come and speak. If there's no cybersecurity club at your campus, consider starting one!
You can also join a professional organization. The only one that I know of is Women in Cybersecurity (WiCyS), and they do lots of great stuff. Student membership is $20/year, and then you get access to their webinars, a mentorship program, their member community, and student scholarships to the WiCyS conference. I was lucky enough to get a scholarship to the conference this past March and it was a really fantastic experience. I was also the president of my campus's student WiCyS chapter! If you're looking to start a cybersecurity club, WiCyS has good support and resources for their student chapters.
Stay Informed About Cybersecurity News Cybersecurity is always evolving, so it's important to have current knowledge of what's happening in the industry. This gives you real-world examples that you can keep in your mind while you're learning new concepts, and it's also a way to impress employers during interviews. These are a few of my favorite sources:
SANS Internet Storm Center StormCast Podcast - 5 minutes of security news every weekday morning
Blogs:
Krebs on Security
Schneier on Security
Malwarebytes Labs
Learn Skills on Your Own Cybersecurity involves working with lots of different technologies. Having solid foundations in these areas will help you a lot:
computer networking (OSI model, ports & protocols, how the internet works, firewalls, etc.)
Linux commands & Windows PowerShell
programming/scripting
cryptography basics
"everyday" security: if you're the IT person for your friends & family, know how to answer questions like:
"How do I set a good password?"
"Should I use a password manager?" (yes.)
"Where should I use MFA?" (everywhere.)
"How do I keep my home network secure?"
"How can I avoid getting scammed?"
This DIY Feminist Cybersecurity Guide is one of my favorites for general security hygiene information.
This got really long (over 1k words! wow!), but I hope it was helpful! Please feel free to send me any more questions you might have, whether specific or broad! I think cybersecurity is a great place to be and I love sharing resources and talking about it!
#I hope this was helpful!!! I also had a fun time writing this lol#ask me more cybersecurity/compsci questions lol I am a nerd and I enjoy answering them haha#asks#cybersecurity
56 notes
·
View notes
Text
PicoCTF2018 Inspect me!: Complete!
This was a my first picoCTF and it was much easier than most of the Natas CTFs.
Upon opening the webpage, I greeted with a simple web page. Nothing really caught my attention, so I immediately inspected the source code.
Here, I found the flag to be split up into three sections, the first section just being hidden in a comment.
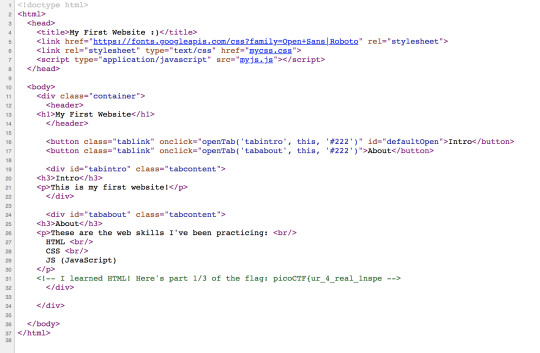
Since the flag was split up into three sections and the web page talks about learning three skills (HTML, CSS and JS) I assumed that the rest of the flag could be found within CSS and JS files AAAANNND they were!! This is so much more fun than getting destroyed by Natas.
1 note
·
View note
Text
Something Awesome Project Proposal- CTFs
Motivation
After a couple of days of thinking about it, consulting with my tutor and listening to Richard talk about it in the lecture I have decided to learn capture the flag (CTFs) as my ‘something awesome’. I have chosen this as I would like to learn a little more about the technical side of security engineering and I have heard that this is a fun way to get introduced. I would also like to be able to learn a bit of hacking as I am planning to take several security courses (forensics, web security and systems and security [COMP6447]) following this one and I would like to get a bit of a head start on those to make sure that security is technically something that I would be interested in. I would also be interested in participating in CTF challenges in the future and this would be a great way to get started.
Skills
I currently have no knowledge of CTSs, reversing, forensics or web security and have a limited knowledge of the Linux command line. In order to be able to say that I am familiar with CTFs and hopefully be able to participate in competitions I would like to be able to increase my skills in all of these. I would like to try a little bit of all of these in order to be able to possibly specialise more in the future.
Steps to Becoming Competent in CTFs
Completing all 34 levels in the Bandit in Over The Wire (OTW) wargame challenges to become more familiar with the Linux Command line
Complete the Natas OTW challenges to get a taste of web security
Complete the Leviathan wargame challenge to get a better taste of CTFs
Complete the Narnia wargame to learn basic exploitation skills
Complete some of the reversing challenges provided by Jazz
Complete some of the protostar exploit challenges to get a taste of network programming
Complete some picoCTF challenges in order to hone my CTF skills
Marking Criteria
Evidence that I have completed these steps will be presented on my tumblr blog
Pass: Completion of #1
Credit: Completion of #1, #2, #3
Distinction: Completion of #1, #2, #3, #4
High Distinction: Completion of #1, #2, #3, #4, #5
Bonus: #6, #7
1 note
·
View note
Text
Bufferoverflow-0
Can you overflow the right buffer in this program to get the flag?

Seems like we need to call sigsegv_handler to print the flag. This is done by causing a segmentation fault with user input (>FLAGSIZE_MAX).

Done.
1 note
·
View note
Text
List of things that are worth killing myself slowly over the course of many years sapping away my life force:
picoCTF
Rust Programming language
Colony Sim Games
Splatoon 3
Black Midi (Discography and the Lore)
The color orange
0 notes
