#react router link
Explore tagged Tumblr posts
Text
#backlings#backlinks#باك لينك#باك لينك 2024#باك لينك 2023#باك لينك مجاني#باك لينك د��فلو#مواقع باك لينك#باك لينك شيكر#back link#backlink generator#backlink html#backlink seo#back link indicator#back link meaning#backlink profile#back link react router#pack link pro#back link def#backlink checker#backlink audit#back link building#back link blog post#backlink business#best backlink site#backlinks in blog#back link css#backlinks شرح#backlink gov#seo
1 note
·
View note
Text
Granger was stunning in Gryffindor red. She was stunning in any color, really, but Draco found it amusing that she had deliberately chosen her old house color for tonight's event.
The satin dress had one off the shoulder sleeve and the skirt of the dress was cut in a combination of a trumpet and mermaid gown with one long slit cutting to the highest point of her right thigh.
“This is torture, Granger.” Theo had growled as Draco held a hand out for her as she descended the last steps and into the entrance foyer. “You know, at some point, I will snap.”
Theo was dressed in a sleek black Havana style tuxedo with a crisp shirt and black bow tie. It was perfectly tailored and his usually wild waves were combed back, accentuating the sharp lines of his jawline. It was a rare sight to see his best friend with his wild waves combed neatly back behind his ears and he looked uncomfortable, soothing the hair back over and over.
“What do you mean, snap?” Granger had dragged her eyes from Draco to lift a curious brow at Theo.
“Just keep doing what you’re doing and find out.” He had pointedly looked away from her and smoothed a hand over his hair.
Her hair was twisted into an intricate bun and the curls strategically left out to frame her face swayed back and forth as she shook her head, frowning.
“You look stunning,” Draco told her, pulling her to his side and linking her hand into the crook of his arm. She had held a hand out for Theo and he took it in his before they made their way over to the gala.
Draco might have let his lip curl when he saw B. Nolan Flamel smile at Granger.
The famous wizard reminded Draco of Gilderoy Lockhart with a dash of Adrian Pucey. He was tall and muscular with a wide smile and wavy golden hair. But Flamel had a smile that touched his eyes in a different way. It wasn’t filled with haughty confidence but something slimy and repulsive.
Of course, Draco considered, that could be due to the fact that he knew Flamel’s dark secret. Not to mention, that despite him and Granger breaking things off, he still looked at her with a hint of possessiveness that caused Draco’s face to react before he had a chance to stop it.
“Briar,” Granger drawled as she pulled her hand away from his hand. He had lifted it and placed a kiss to the back of her hand without any hint of hiding the gleam of greed in his eyes.
“Have you met Draco Malfoy and Theodore Nott?”
“No, I cannot say I have had the pleasure.” Flamel’s dark eyes flicked to the two wizards at her side and nodded. “I’m thrilled to finally have wizards of your stature to attend one of my events.” He smiled at them but unlike with Granger, it failed to reach his eyes.
“A simple invite would suffice.” Theo sniffed but his eyes kept drifting off towards Ginny Potter, who was currently chatting up a wizard that Draco recalled was part of the Wizengamout. She was wearing a sleek gold gown and was alone, which meant that Seamus and Harry were currently off exploring the home, looking for the router.
“I’m delighted to be here.” Draco drawled, as he spotted a charmed tray of hors d’oeuvres pass by. All of the drinks and food was being served on trays that floated around the party, as if on a phantom wind. Passing between overdressed witches and wizards. There was classical music playing somewhere in the background and overall, really, the event seemed quite boring. Just another opportunity for high class society to show off their clothes or flaunt their money, donating to a cause they really cared nothing about.
“I would love some champagne.” Granger announced, pointedly looking at Draco. Her eyes cut, imperceptibly, toward the left side of the room. Draco glanced over to find Blaise Zabini making his way toward them.
He grinned at her before nodding to Theo. “Theo, shall we get our lady something to drink?”
Theo’s eyes snapped to his and the look of utter boredom vanished from his features. “Of course.”
Draco gave her hand one more kiss before he and Theo pulled away, nodding at Blaise as they crossed paths.
“Should we be leaving her alone with that vulture?” Theo mused as he lifted a glass of shimmering pink champagne from a passing tray.
“Granger can take care of herself. She dated the bloke at some point.” He frowned over at Theo as they moved through the crowds. “Has she dated anyone since the two of you met?”
Theo tilted his head back and proceeded to drink the entirety of the glass. “She went on a few dates. Never anything serious.” It wasn’t unusual for Theo to loosen up with a glass or two of alcohol for a job and so when he reached for a second glass, Draco didn’t stop him.
Draco nodded to a hallway leading away from the ballroom. The two slid out of the room unseen.
“What floor is his room on again?” Draco asked under his breath.
“Third floor, east wing.” Theo set his empty glass on a table as they passed a painting of a Pegasus by a famous wizard painter, Avis Oleander. The wings flapped and the hooves galloped through clouds and stars as if aiming straight for them.
“What’s wrong with you? That’s two glasses of champagne in,” Draco glanced down at his watch and then remembered he didn’t wear one. “At least two minutes.” He surmised.
“I’m tense.” He straightened his bow tie and smoothed the lines of his jacket. “I can’t believe we just left her with him.” He sighed then shook his head. “There’s a guard up there.” He nodded toward the end of the hall.
“Turn here.” Draco murmured just before they veered left, looking very much like they knew where they were going.
Thanks to Teddys recon work, he did vaguely have an idea of where they were headed. They continued through halls filled with gaudy statues and paintings representing wizards and their greatness until they found themselves in the middle of an atrium full of both magical and non-magical plants. In the middle of the circular room was a pond with an array of koi fish.
“This is the east wing.” Draco mused as he looked around the room. “Didn’t Teddy say there was an atrium that could lead us to the Third floor?” His eyebrows pulled tight as he examined the room. He saw no signs of a staircase nor a lift.
“There’s a door over there,” Theo nodded to the other side of the atrium. “Perhaps through there?” It was hidden behind
“Only one way to find out.” They didn’t hesitate to move to the door together. “Do you think Granger never got serious with anyone, because you were in her life?” Draco asked his friend as he flicked his wand over the locked door.
Theo pursed his lips as he peeked into the darkened room. “I think she gave up on me.” He nodded into the room. “There’s a stairwell there.”
Draco ascended first, scanning as he went. “Why?”
“Because she didn’t think I ever got over Pansy.”
“Did you?”
“I think so. She’s sort of like my Weasley, isn’t she?”
Draco scoffed, but Theo went on.
“I mean, I had always assumed we would eventually end up together. But then I got involved with Granger, and that idea just sort of just faded away.” He looked over his shoulder. “Do you think she still wants him?”
“Weasley?” Draco shook his head as they climbed the spiral stairwell. “No, I think more than anything, she wants a family.”
Theo was quiet as they continued to climb. “What do you think Ginny meant by that whole child-bearing thing?”
“I think we should let Granger tell us.” Though it was something that Draco thought about often. Was she unable to have children or was it just difficult in the way that it was for most Witches. It was a common theme amongst the wizarding community. There was something, healers assumed, about the way magic affected the witches menstrual and ovulation cycle. It was the main contributing factor for the lower population rate. He had assumed that for a muggle, it might have been easier to conceive than it was for a witch. Due to the lack of magic interrupting their cycles.
Obviously, he could be wrong.
“These stairs are surpassing the second floor.” Draco noted, to which Theo hummed.
“Have you thought about having children?” He asked instead.
“Not often.” He admitted. “I think it would be hard at this point in my life. We’re not getting any younger.”
Theo chuckled. “I can’t imagine having children and still yearning to do shit like this.”
“But if we did,” Draco laughed. “We could make a horde of little bandits.”
“A family of thieves.” Theo reached the top of the stairs with a laugh. There was another locked door. “Granger would make a great mother.”
“I don’t know how I’d feel about being a father, having experienced my own.”
“Too right.” Theo grimaced, unlocking the door with the tip of his wand against the knob. He froze with his hand on the knob. “Did we forget to check for cameras?”
“No, I checked.” Draco grinned. “I cast a disillusionment spell toward the one in the atrium and there are none in here.”
“I’d love to get my hands on that cloak Potter keeps attached to his body.”
“It would come in handy.” Draco agreed and shot a disillusionment charm onto themselves before they opened the door.
“Did we just discuss having babies with Granger together?” Theo whispered, suddenly looking very alarmed.
“We did.”
They snorted quietly as they peered into the room.
They found B. Nolan’s bedroom.
“Oh, Clams Casino.” Draco plucked one up from a passing tray of hors d’oeuvres while Theo plucked up a glass of the same shimmering pink champagne.
Draco’s eyes scanned the room for Granger amongst the sea of people.
“Where is our witch?” Theo set his glass down and stumbled sideways into Draco’s arm just as he lifted the hors d’oeuvres to his mouth.
The Clam flew from his grasp and into a glass of champagne passing by. Both wizards watched as the glass toppled over into the others.
The sound of glass shattering seemed to create a stand-still as the room watched the glasses fall and break, spilling fizzing champagne onto the tiled floor.
“Oops.” Theo whispered out loud.
“Well, that was unfortunate.” Draco frowned.
A swath of jet black and silver suddenly appeared as the wait staff began to clean up the mess, allowing the partygoers to resume their dull conversations.
Astoria Greengrass was headed straight for them, dressed in a silver A-line gown that trailed behind her like some sort of twisted version of a wedding gown.
“We need to find Granger.” Draco murmured into Theo’s ear and began to pull him away. But Theo had eyed another glass of champagne. It practically glowed as it followed Astoria’s path straight for them.
“Draco,” She greeted him as she came to a stop in front of them. Theo tipped forward to grab a glass of champagne as it passed and Draco barely managed to hold onto the back of his jacket.
“Tori, fancy seeing you here.”
“I’m invited to all of Flamel’s events.” Her smile failed to reach her eyes.
She reached for a glass of champagne and held it out for Draco. “Champagne?”
“No thank you.”
She pursed her lips together but her eyes tracked Theo as he drank his own flute. “Theo Nott, another face I didn’t think I’d ever see at an event like this.”
Theo blew a raspberry and sniffed. “You’re just as lovely as ever, Tori.” He rolled his eyes and sent his empty glass sailing across the room to settle on another passing tray.
“I’m actually glad I ran into you.” She turned her attention to Draco, who was now chewing his meatball and scanning the room for Granger.
“Really? Why is that, Tori?”
She stepped closer, putting their bodies uncomfortably close. Her hand went to the his bow tie, playing with the silky fabric, loosening the bow. Draco stiffened at the proximity. At the scent of powder and roses.
“Because I know, Draco.” She cooed into his ear.
Theo’s look of alarm seemed to match the way Draco felt.
“Know...what?”
Her fingers moved from the bow tied around his collar, to his chin. “I know it was you.”
Draco wasn’t like Theo. He didn’t show every emotion on his face. But inside, he was balking at the feel of her fingers on him. The words she whispered into his ear. To any onlooker, she looked like any witch talking secretly to a lover.
“There was a particular need for blood in order to dismantle the ward.” She pressed into him, their bodies now flush with one another. “Which was done impeccably well, if I must say so myself. In fact, I wouldn’t have even noticed that something was wrong, if whoever removed the ward had bothered to reset it, using the same vial of blood they took from me.”
Fuck.
“What do you want, Tori?” Draco placed a hand on her shoulder, in a gentle attempt to push her away.
“I want it back.” She sniffed. “And I wouldn’t mind seeking a little entertainment in your humiliations, of course.” She pulled back and lifted the glass of champagne to her lips but paused when her eyes flicked behind him. “Oh, and my ring. I want my ring back.”
“What ring?”
“The Malfoy heirloom ring you were supposed to put on my finger. I know you have it. Your father told me you never returned it.” She held her glass out to Theo. “I’ll expect an invite to your home by Monday. I’ll come to you, of course.” She pressed the glass into Theo’s hands before sweeping past them.
Both Draco and Theo turned to watch her leave. Granger was standing several feet away, staring at them with only a hint of confusion.
Astoria stopped and leaned forward to whisper something into Granger’s ear before disappearing into the crowd.
Granger’s eyes snapped to Draco before she marched over.
“Granger, love!” Theo called and lifted the glass in a salute before taking a drink.
“I think you’ve had enough, Theo.”
“It’s incredibly addicting. I think it’s strawberry.”
Granger reached them in five or six long strides, her eyes trained on the loosened bow tie around Draco's collar.
“What did she say to you?” Draco asked.
“She’s wicked, don’t listen to her. She reminds me of —”
“Theo?”
Theo froze, his eyes widening in horror. Granger looked around Draco and choked and he knew why. He knew that voice. It was a voice he had once known intimately well. Having dated Pansy in school, it had been odd at first when Theo and Pansy later got together and proceeded to have a tumultuous relationship off and on that spanned over the course of a decade.
“Granger?” Pansy’s voice pitched as she eyed the witch beside Draco.
Theo swallowed and turned to face his ex lover. “Pansy.” His voice sounded strained as he wrapped his mouth around that name.
Draco turned and smiled blandly at his old classmate. “Howdy, Parkinson.”
She scoffed and nodded to Granger who stepped up between himself and Theo.
“Hello Pansy.” Granger lifted her proud little chin.
Theo downed the rest of his champagne. “What brings you here?” He asked, his voice cracking slightly on the last word of his question.
She, like Granger, had aged well. Pansy was pretty in a different kind of way. She had a full, womanly figure like Granger but she had that forced grace bred into her. Her hair was longer, falling to her shoulders, rather than the shin length bob she used to sport. And her hair was black as a raven with a single streak of white hair perfectly styled in. As if she had embraced the inevitable process of age.
“Careful with those,” She lifted her chin at the glass in Theo’s hand. “Rumor has it somebody spiked it with a alcohol enhancing potion.”
“Well, that explains that.” Draco hummed as he slid his arm around Grangers shoulders.
“I heard the two of you were dating.” Pansy eyed the gesture with narrowed eyes before settling her scrutinizing eyes on Theo. “What are you doing here?” She looked suspicious. “Since when do you care about these sort of events without finding something to steal?”
Theo chuckled. “Who says that I am not here to steal something?” He lifted an eyebrow at her in challenge.
“Theo, I swear —”
"Oh, relax Pansy." Theo rolled his eyes.
Pansy's cheeks had flushed with anger and glared at Theo, who was swaying slightly into Granger. "You look terrible. How many glasses have you had?" Her glare softened as she watched Theo smooth over the lines of his jacket.
"Only four or five." He shrugged. Theo was eyeing Pansy, now. His eyes were scrutinizing and there was something quite sad about the two of them standing in the same room again. Pansy's body was rigid with tension, while Theo's was clearly more relaxed, thanks to the alcohol in his system. "What is it that you want, Pansy?" He squinted at her, one eyes more than the other. "Did you come over here to insult me, more? To rant about how I am nothing but a no good thief?"
"Oh, please." She sniffed. "I just call it like I see it."
"Everyone's a thief, Pansy." Theo declared. "Some steal hearts, other steal jewels." He looked down at Granger. "Isn't that right?"
Granger sighed. Her body pressed into Draco's, as if seeking comfort amongst the tension.
"I never took what wasn't willingly given to me." Pansy seethed. "But you,"
"Only do what Robin Hood would have." Theo shrugged and Draco chuckled at the blatant lie.
“Theo, sweetheart,” Granger finally interrupted, sliding her hand into his. “Draco and I are tired. Can we go home?” She pouted seductively up at him, while her other hand slid around Draco’s back.
Theo’s wide eyes flashed down to hers, a lopsided smile pulling at his mouth.
“Anything you want, love.” He slurred as he leaned forward and ran a finger along the side of her face. “You’re so pretty. Just like the moon.”
Granger couldn’t stop the snort that escaped her as she pulled Theo and Draco with her, guiding them away from Pansy Parkinson.
“What is this? Are you both shagging her?” She asked the question with a hint of disgust.
But Granger only smirked and battered her eyes. “Not yet.”
Nobody spoke until they arrived back to Zabini’s manor.
Teddy and Seamus were already in the study, waiting for them. Theo slumped into one of the sticky leather chairs while Draco took his seat behind the desk. He watched Granger look between the two wizards. Her hands were on her hips, and she was positioned in such a way that allowed the slit in her dress part, revealing the entire length of her tanned leg.
“Did you know?” She asked Theo. “Did you know Pansy would be there?”
Theo looked startled by her question. “How could I?”
“Are you talking about the girlfriend?” Teddy asked from where he sprawled out on the couch.
Everyone looked at him.
“Girlfriend?” Draco pulled the question out slowly. “You never told me about a girlfriend.”
“Oh.” Teddy blinked. “I thought I had. I couldn’t remember her name. I just knew it was a flower name. Started with a P. I kept thinking it was Petunia or Peony but,” he shrugged as if that had summed it all up.
“She’s dating Flamel?” Theo sounded disgusted.
“She lives with him,” Teddy supplied, rather unhelpful. "She's beautiful." He added even more unhelpfully.
"She looks like Cruella Devil." Granger snorted and rolled her shoulders back.
Theo jumped, unsteadily to his feet, and rounded on Granger. “What is it about that wizard? He's not even that good looking.”
She scoffed. “You wouldn’t had thought he was dating anyone when he asked me to ditch you two and meet him later tonight.” Granger fidgeted. "He is handsome. Very fit."
Frowning, Draco summoned a bag of crisps from the kitchen, having eaten entirely too little at the gala.
Theo groaned in disgust. “Gods, I cannot wait to take that stupid necklace from him. ”
Ginny came in, stumbling, despite the grip her husband held around her. “What necklace? I thought we were going after the Philosopher’s stone.”
Harry winced and Granger threw a handover her face.
“The what?” Theo balked.
Granger rounded on Harry, “You told Ginny?”
“She’s my wife, Hermione. We tell each other everything.” Harry said as he led his very drunk wife over to the empty spot beside Teddy.
“You never mentioned a stone, Theo.” Draco eyed his friend as he dug his fingers into the bag of crisps. Salt and vinegar, his least favorite.
“I said that there may be other valuable items in the vault.” He sniffed. “It was implied.” He turned to Granger, “We never agreed to give it to Potter.”
“I wasn’t going to just hand it over to Harry.” She rolled her eyes. “He was going to help me use it to come up with an elixir.”
“An elixir for what?” Theo eyed her. “Looking for a life of immortality?”
“Wait a minute.” Seamus shook his head, looking up from his laptop. “I thought that old bat destroyed the stone. He died ages ago. Didn’t he?” He looked over at Draco. “Did he?”
Ginny snorted. “Harry and I can live forever and watch our grandkids grow old and their grandkids and so on.”
Draco’s mouth quirked at the wonder in her declaration.
Harry sighed and shook his head. “Nobody is going to live forever.” Then he paused and looked at Theo. “What necklace?”
“I thought we were taking gold.” Seamus said to Teddy who shrugged.
“I knew about the stone.”
Draco began to chuckle as he dusted the greasy crumbs from his fingertips. “What do you intend to use the stone for, Granger?”
She turned to look at him and tilted her head. “I don’t want to say.” And then she straightened and sniffed. “What was Astoria Greengrass doing, pawing at you and whispering in your ear?”
He smiled and batted his eyes at her. “Jealous, Granger?”
She scowled at him, only confirming his suspicions.
Theo snorted and stumbled backwards, clearly still drunk. “She was threatening Draco.”
“What?” Everyone said at once.
“She knows about the Wand.”
Granger shook her head as she mentally began to calculate how that was even possible. She gasped, slamming a hand over her mouth. “Oh my gods! I didn’t reset the ward!”
Draco nodded and Theo reached for her hand. “It’s okay, Granger. I forgive you.”
She yanked her hand free and pointed a finger at her. “Well, don’t. Because I haven’t decided if I forgive you.”
Theo choked around several coughs before he put a hand over his heart. “Moi? Qu'est-ce que j'ai fait?”
“Pansy.” She said through clenched teeth.
“I didn’t Know,” he frowned and eyed her. “Are you jealous? You look jealous.”
She scoffed and threw her hands up in the air. “I need a drink.”
“Don’t worry about Astoria, Granger, I’ll take care of her.” Pansy, however, might present a problem, he thought as he watched her pace the floor, sufficiently flustered.
“What about Zabini? Did he manage to chum up with Flamel?” Seamus asked as he went back to tapping into his laptop.
Granger nodded as she went for the bottle of fire whiskey on the small wet bar in the corner of the study.
“He did. Zabini managed to invite him to lunch tomorrow.” She pour a small amount of liquor into the short glass before tossing it into the back of her throat.
“Are you about to get drunk, Granger? I love a drunk Granger.” Theo reached for her hand again but she managed to pull it out of his reach.
Ginny began to snore from her spot on the couch, causing Teddy to laugh like the youth that he is.
Harry frowned over at Granger. “I think Theo and Draco will understand why you want to use the stone, Hermione.”
“I don’t need them to understand.”
“Oh, so we don’t share personal things, now?” Draco drawled.
She frowned and threw an apologetic look at him.
“Does it have to do with your parents?” Theo asked, apparently well aware of her situation.
She shook her head.
“That stone is worth a lot.” Seamus mused aloud.
“I’m going to destroy the stone once Hermione’s done with it.” Harry said with a bit of gusto.
Theo winced and reared back. “I beg your pardon?”
“The necklace is worth more than enough.” Draco amended. “We don’t need the stone. We all thought it was destroyed until now, didn’t we?”
Theo was staring at Granger, who was pouring herself another glass, this time to the tip of the top.
“Granger,” He sighed. Her eyes slid to him as she took a large sip. “I didn’t know.” His eyes were apologetic as they latched onto hers.
She swallowed her drink and sighed. “You didn’t know.” She nodded in understanding before she looked over at Draco and frowned. “And yes, I was jealous.”
And without further ado, she swept from the study, then train of her gown trailing behind her, and her whiskey still in hand.
#my writing#fanfic#dramione#dramione fanfic#harry potter#hermione granger#draco malfoy#draco x hermione#hermione x draco#idiots in love#draco/hermione#draco lucius malfoy#dramione fan fiction#dramione art#dramione fanfiction#dramione ship#dramione fandom#hermione#draco and theo#theo nott#theomione#theo and hermione#theo x hermione#theodore nott#pansy parkinson#blaise zabini#astoria greengrass
18 notes
·
View notes
Text
Jamming a Network: Jamming a network is a crucial problem occurs in the wireless networks. The air in the region of offices is probable stopped up with wireless networks and devices like mobile phones and microwaves. That undetectable traffic jam can cause interference troubles with the Wi-Fi system. Large number of consumer use devices such as microwave ovens, baby monitors, and cordless phones operate on the unregulated 2.4GHz radio frequency. An attacker takes advantage of this and unleash large amount of noise by using these devices and jam the airwaves so that the signal to noise go down, in the result wireless network stop to function. The best solution to this problem is RF proofing the nearby atmosphere.Unauthorized Access:The use of Wireless technologies is increasing rapidly and Wireless technology is much admired. So companies are exchanging their usual wired networks with wireless - even for non-mobile functions. There have been several warnings from security advisors regarding wireless protocols, Especially for WEP, being disgustingly insecure. Unauthorized access to wireless network can occur from different ways for example, when a user turns on a computer and it latches on to a wireless admittance point from a neighboring company’s overlapping network, the user may not even know that this has occurred. But, it is a security violate in that proprietary company information is exposed and now there could exist a link from one company to the other. Denial of Service:A denial-of-service attack is an effort to make computer resources unavailable to its intended users. It is the malicious efforts of a persons or number of persons to stop a web site or service from carrying out proficiently or at all. One general way of attack involves saturating the target machine with external communications requests, such that it cannot react to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. It normally slows down the network performance. For example speed of opening files and closing files slow down. System will also be unable to access any web site. The bandwidth of a router linking the Internet and a local area network may be consumed by DoS. There are also other types of attack that may include a denial of service as a module, but the denial of service may be a part of a larger attack. Illegal utilization of resources may also result in denial of service. For instance, an interloper can use someone’s secret ftp area as a place to store illegal copies of commercial software, overwhelming disk space and generating network traffic. Man in the Middle:In the man in the middle attack an attacker sits between the client and the server with a packet analyzer. This is the disparity that most people think of when they hear the term man in the middle. There are also many other forms of the man in the middle attacks that exploit the fact that most networks communications do not use a strong form of authentication. Unless both ends of the session frequently verify whom they are talking to, they may very well be communicating with an attacker, not the intended system. References:1. Brenton, C. & Hunt, C. 2003. Network Security. 2nd Ed. New Delhi: BPB Publications.2. Hossein, B., 2005. The Handbook of Information Security. John Wiley & Sons, Inc.3. L. Blunk & J. Vollbrecht., 1998. PPP Extensible Authentication Protocol (EAP). Tech. Internet Engineering Task Force (IETF).4. Matthew, S. Gast., 2002. 802.11 Wireless Networks: The Definitive Guide: O’Reilly & Associates.5. Vikram, G. Srikanth, K. & Michalis, F., 2002. Denial of Service Attacks at the MAC Layer in Wireless Ad Hoc Networks. Anaheim, CA: Proceedings of 2002 MILCOM Conference. Read the full article
0 notes
Text
Mastering Angular: Features, Benefits & Training in Hyderabad
A Comprehensive Guide to Angular: Powering Modern Web Development
Angular, an open-source framework developed by Google, has become one of the most popular choices for building dynamic and complex web applications. Released in 2010, Angular simplifies the development of single-page applications (SPAs) and provides a structured approach to creating scalable applications. In this article, we’ll explore the key features and benefits of Angular and why it remains a preferred choice for developers.
What is Angular?
Angular is a framework for building client-side applications using HTML, CSS, and JavaScript (or TypeScript). It simplifies the process of developing large-scale, feature-rich applications by providing tools like two-way data binding, dependency injection, and routing. Angular is built on a component-based architecture, making it easy to manage complex applications by breaking them down into reusable, self-contained units.
For developers looking to master Angular, finding the Best Angular Training Institute in Hyderabad, Kukatpally, KPHB is essential to gaining hands-on experience and learning best practices.
Key Features of Angular
Component-Based Architecture
Angular is organized around reusable components, which consist of HTML templates, CSS, and TypeScript code. This makes it easier to manage complex applications by breaking them down into smaller, manageable parts.
TypeScript Support
Written in TypeScript, Angular benefits from static typing, object-oriented features, and improved tooling. TypeScript helps catch errors early and enables better developer productivity.
Two-Way Data Binding
Angular automatically synchronizes data between the model and the view, reducing the need to manually update the user interface when data changes.
Dependency Injection (DI)
DI simplifies the management of services and dependencies by injecting them into components, which makes testing and maintaining the application easier.
Routing
Angular's built-in router manages navigation within single-page applications, allowing developers to define routes and link them to specific components.
RxJS for Reactive Programming
Angular leverages RxJS to manage asynchronous data streams in a declarative manner, making it easier to handle events, such as HTTP requests and user interactions.
Benefits of Using Angular
Complete Ecosystem
Angular comes with everything needed to build modern web applications, including tools, libraries, and best practices. This ecosystem reduces reliance on third-party tools and ensures consistency across the development process.
High Performance
Angular offers features like Ahead-of-Time (AOT) compilation and tree shaking, which optimize the performance of applications by reducing load times and bundle sizes.
Cross-Platform Development
Angular supports building cross-platform applications. Developers can create apps that run on different platforms, including web, mobile, and server-side environments.
Strong Community and Support
With Google’s backing and a large developer community, Angular enjoys continuous updates, plugins, and extensive resources, making it a reliable choice for enterprise applications.
Scalability
Angular is designed to handle both small and large applications. Its modular structure and component-based approach allow for growth without sacrificing performance or maintainability.
Why Angular is Still Popular
Despite the rise of other JavaScript frameworks like React and Vue.js, Angular remains a go-to choice, especially for enterprise-level applications. Its complete ecosystem, strong tooling, and scalability make it suitable for large-scale projects requiring complex features and performance optimizations. The integration of TypeScript also brings added security and discipline, making Angular a reliable choice for teams working on large applications.
Conclusion
Angular’s powerful features, flexibility, and scalability make it an excellent choice for developing dynamic and scalable web applications. At Monopoly IT Solutions, we specialize in leveraging Angular’s robust ecosystem to build high-quality web applications that meet our clients’ specific needs. Whether you need a single-page app or an enterprise-level solution, Angular’s comprehensive toolkit can help bring your ideas to life efficiently and effectively.
For those eager to master Angular, enrolling in the Best Angular Training Institute in Hyderabad, Kukatpally, KPHB can provide the right guidance and expertise to become proficient in modern web development.
1 note
·
View note
Text
Frontend Developer React ilə Veb Sayt Yaratması
React tətbiqinin strukturu adətən komponentlərə əsaslanır. Hər bir komponent, müəyyən bir hissəni idarə edir və bu komponentlər tətbiqin müxtəlif funksiyalarını təşkil edir. Frontend Developer React ilə veb sayt yaratmağa başlamazdan əvvəl əsas komponent strukturu qurulmalıdır.
React Router, tətbiqlər arasında naviqasiyanı idarə etməyə imkan verir. Veb saytınızda fərqli səhifələr arasında keçid etmək üçün React Router istifadə edərək Link və Route komponentlərindən istifadə edə bilərsiniz.
React, tətbiqinizin vəziyyətini idarə etmək üçün state istifadə edir. Veb saytınızın müxtəlif hissələrində dinamik məlumatları göstərmək üçün React-ın useState və useReducer hooklarından istifadə edərək state idarəetməsini tətbiq edə bilərsiniz.
React, istifadəçi daxil etdiyi məlumatları toplamaq və idarə etmək üçün formaları asanlıqla idarə etməyə imkan verir. Formik və React Hook Form kimi kitabxanalar, forma daxil etmə və doğrulama prosesini sadələşdirir.
0 notes
Text
Is It Possible to Learn React in 7 Days in Pune? A Realistic Guide for Beginners
In today’s fast-paced tech world, web development frameworks like React have gained immense popularity due to their efficiency and versatility in building dynamic user interfaces. React’s simplicity, coupled with a large community of developers, makes it a go-to choice for many developers in Pune and across the globe. But can you really learn React in just 7 days?
While mastering React in a week may sound ambitious, it’s possible to gain a strong foundational understanding of the library and even build a simple project in that time frame, especially with a structured learning plan and dedication. Here’s a realistic guide to help you understand how to make the most of your 7-day learning journey with React fullstack course in Pune.
Day 1: Understanding the Basics of JavaScript and Web Development
Before diving into React, it’s essential to have a solid grasp of the core technologies React depends on — namely HTML, CSS, and JavaScript. React is built on JavaScript, so understanding the fundamentals like variables, functions, loops, arrays, objects, and ES6 features (like arrow functions, destructuring, and promises) will make your React journey smoother.
Recommended Resources for Pune Learners:
Local coding bootcamps in Pune like Codeacademy and Edureka offer beginner-level JavaScript courses.
Online tutorials and resources from platforms like freeCodeCamp, MDN Web Docs, and W3Schools.
Day 2: Setting Up Your Development Environment
The next step is setting up your development environment. React works best with Node.js and npm (Node Package Manager). In this phase, you’ll:
Install Node.js and npm on your local machine.
Set up a React project using Create React App, which provides a boilerplate template for React apps.
Understand the file structure of a React app and the role of files like index.js, App.js, and public/index.html.
Day 3: Diving Into JSX and Components
React is built around components, which allow you to break down the user interface into reusable parts. Understanding how components work is crucial on your learning path. You’ll need to familiarize yourself with JSX (JavaScript XML), a syntax extension that allows you to write HTML inside JavaScript.
Key concepts for Day 3:
Functional components: The simplest type of React components.
JSX syntax: How to write JSX in React and its advantages.
Props: How to pass data between components.
Local Coding Events in Pune: Attending meetups like Pune ReactJS Meetup can help connect with like-minded developers and boost your learning.
Day 4: Understanding State and Event Handling
React’s real power lies in its ability to handle state and respond to events. Understanding state and how React manages it is crucial.
On Day 4, you’ll learn:
State: How to create and update state within components.
useState hook: How to use React hooks to manage state in functional components.
Event handling: How to handle user inputs like clicks, form submissions, and more.
Day 5: Mastering React Router and Managing Navigation
To build real-world applications, you’ll need to implement routing. This allows users to navigate between different pages or views in your React app without refreshing the browser.
You’ll need to learn:
React Router: A library for handling routing in a React application.
How to create different routes and links between components.
Day 6: Handling Data with APIs and useEffect Hook
Most modern web applications rely on APIs to fetch data dynamically. React makes it easy to work with external APIs.
On Day 6, focus on:
useEffect hook: Learn how to make asynchronous API requests and update your components with dynamic data.
Fetching data: Practice working with real-time data through APIs (e.g., using the fetch API or Axios).
Day 7: Building Your First React App
On the final day, put all the concepts you’ve learned into practice by building a simple React app. A good project idea for beginners in Pune could be something that reflects local interests, such as:
A Pune events app that fetches upcoming events and displays them dynamically.
A restaurant review app that allows users to browse restaurants, view ratings, and leave feedback.
Tips for Learners in Pune:
Local Networking: Pune has a thriving tech community. Attend workshops or networking events like those organized by Pune Tech Meetup or ReactJS Pune Meetup to gain insights and improve your React skills.
Pair Programming: Collaborating with other learners or experienced developers can fast-track your understanding. Seek out pair programming opportunities.
Practice, Practice, Practice: Learning React, like any other skill, requires hands-on practice. Building small projects and experimenting with different concepts will improve your skills faster.
Seek Mentorship: If possible, find a mentor or join a local coding community to help guide you through tricky concepts.
Is 7 Days Enough to Master React?
While 7 days will provide a strong foundation, it will not make you an expert in React. React is a vast library with many advanced topics such as state management, context API, Redux, and testing, which require more time and experience to master. However, with consistent effort, you can continue improving your React skills beyond these 7 days.
Conclusion
Learning React in 7 days is an achievable goal in Pune if you approach it with the right mindset and resources. By following this guide and focusing on essential concepts, you can gain a strong foundation and start building your own React projects. Remember, the key to mastering React is continuous learning and practice, so keep pushing yourself beyond the first week and take advantage of Pune’s local tech resources and meetups to accelerate your growth.
Ready to kickstart your React journey? Whether you’re a beginner or looking to deepen your knowledge, join Itview Inspired Learning Near Pune for a React JS course in Pune. Our expert trainers will help you master React, build real-world applications, and connect with the local tech community. Enroll today and take the first step toward becoming a React developer!
0 notes
Text
Title: The Evolution of Frontend Development: A Comprehensive Guide for Modern Web Developers
Introduction
Frontend development has transformed dramatically over the past decade, becoming one of the most dynamic fields in the tech industry. With user expectations soaring and new technologies emerging, building intuitive, responsive, and user-friendly web interfaces is more crucial than ever. In this article, we’ll dive deep into the core aspects of modern frontend development, the tools and frameworks that shape the industry, and best practices for crafting outstanding user experiences.
What is Frontend Development?
Frontend development, also known as client-side development, refers to the creation of the visual and interactive components of a website or web application. It involves using technologies such as HTML, CSS, and JavaScript to ensure that users can seamlessly interact with a site’s content. Essentially, everything you see and engage with on a website – buttons, text, images, forms, and animations – are the result of frontend development.
The Key Technologies of Frontend Development
1. HTML (HyperText Markup Language)
HTML is the backbone of any website. It structures the content by defining elements such as headings, paragraphs, links, images, and other multimedia. HTML5, the latest version, introduced new elements like <article>, <section>, and <footer>, which have enhanced web accessibility and semantic meaning.
2. CSS (Cascading Style Sheets)
CSS brings HTML to life by defining the visual style of a webpage. From colors and fonts to layouts and animations, CSS allows developers to control how content is presented on different devices. Modern CSS features like Flexbox, Grid, and media queries have made it easier to create responsive designs that adapt to various screen sizes.
3. JavaScript
JavaScript adds interactivity to web pages. Whether it’s creating dynamic content updates, handling user inputs, or adding animations, JavaScript is essential for a responsive and interactive user experience. With the rise of ES6 (ECMAScript 2015) and beyond, JavaScript has become more powerful and easier to work with, especially with features like arrow functions, promises, and async/await.
Modern Frontend Frameworks and Libraries
In today’s development environment, building a web interface purely with vanilla HTML, CSS, and JavaScript is rare. Frameworks and libraries have become indispensable tools for frontend developers, helping streamline workflows, manage complexity, and improve scalability.
1. React
Created by Facebook, React is a JavaScript library for building user interfaces, particularly single-page applications (SPAs). React’s component-based architecture allows developers to break down complex UIs into smaller, reusable pieces. Its virtual DOM efficiently updates only the necessary parts of the UI, resulting in fast rendering performance.
2. Vue.js
Vue.js is a progressive JavaScript framework known for its simplicity and flexibility. It’s ideal for building both SPAs and more traditional multipage applications. Vue’s ecosystem includes tools like Vue Router for routing and Vuex for state management, making it a solid choice for developers looking for a versatile frontend framework.
3. Angular
Angular, maintained by Google, is a comprehensive framework designed for building enterprise-level applications. It provides a full suite of tools, including two-way data binding, dependency injection, and a powerful templating system. Angular is preferred for large-scale applications requiring strict structure and scalability.
4. Svelte
Svelte is a relatively new frontend framework that differs from others by doing most of its work at compile time. Instead of relying on a virtual DOM, Svelte compiles components into highly efficient imperative code that directly manipulates the DOM. This results in faster runtime performance and smaller bundle sizes.
Tools and Platforms Enhancing Frontend Development
1. Figma and Adobe XD
Web design tools like Figma and Adobe XD have become essential for frontend developers. These platforms allow designers and developers to collaborate seamlessly on prototypes and wireframes, ensuring that design vision aligns with the technical execution. They also integrate with AI-driven tools like Locofy and Framer, which convert design assets into code, significantly speeding up the development process.
2. Version Control with Git
Git is a version control system that allows developers to track changes to their codebase, collaborate with other developers, and manage multiple versions of a project. Using platforms like GitHub, GitLab, or Bitbucket, developers can collaborate in teams, review code, and maintain a history of all project changes.
3. Build Tools and Task Runners
Modern frontend development workflows often involve a range of tools that automate repetitive tasks. Tools like Webpack, Gulp, and Parcel help bundle assets, minify JavaScript, compile Sass, and perform live reloading during development. They play a crucial role in optimizing code for production, ensuring faster load times and better user experience.
Best Practices in Frontend Development
1. Responsive Design
With the explosion of mobile device usage, responsive web design is non-negotiable. Using flexible grids, media queries, and fluid images, developers can ensure that websites look great on any device, whether it’s a smartphone, tablet, or desktop.
2. Accessibility
Building websites that are accessible to all users, including those with disabilities, is critical. Following the Web Content Accessibility Guidelines (WCAG), developers should ensure their sites are navigable via keyboard, provide alt text for images, and use semantic HTML to make content readable by screen readers.
3. Performance Optimization
Speed is essential for retaining users and improving search engine rankings. Techniques like lazy loading images, minimizing JavaScript, and using Content Delivery Networks (CDNs) for static assets can drastically improve page load times.
4. Cross-Browser Compatibility
Different browsers may render websites slightly differently. Developers should always test their sites in multiple browsers (e.g., Chrome, Firefox, Safari, Edge) to ensure consistency in appearance and functionality.
Conclusion
Frontend development has evolved into a multifaceted discipline that requires not only technical expertise but also a deep understanding of design principles and user experience. By staying updated with the latest tools, frameworks, and best practices, developers can create stunning, high-performance web interfaces that captivate users and enhance brand engagement. Whether you’re just starting out or are an experienced developer, mastering frontend development is key to building modern, responsive, and accessible web applications.
###blogger.com/blog/post/edit/8905294591021215860/6960074020900498661
1 note
·
View note
Video
youtube
React Router - How to Pass Parameter to Another Page Using Link
0 notes
Text
React Route Navigation
React Route is an integral part of any React application, providing the functionality to manage navigation between different views or pages seamlessly. As single-page applications (SPAs) continue to rise in popularity, understanding how to effectively use React Route is crucial for creating a dynamic and intuitive user experience.
What is React Route?
React Route is part of the React Router library, which is specifically designed to handle routing in React applications. Routing is the process of determining what content to display based on the current URL, allowing users to navigate through different pages or components within your app.
Setting Up Your First Route
Setting up routes in React is straightforward. The Route component is used to define which component should be rendered for a particular path.
Example:import { BrowserRouter as Router, Route } from 'react-router-dom'; function App() { return ( <Router> <Route path="/" component={HomePage} /> <Route path="/about" component={AboutPage} /> </Router> ); }
In this example, when the user visits the root URL (/), the HomePage component is displayed. If they navigate to /about, the AboutPage component is rendered.
Dynamic Routing with Parameters
One of the powerful features of React Route is the ability to create dynamic routes that accept parameters. This is particularly useful when you need to display content based on an identifier, such as a user ID or a product code.
Example:<Route path="/user/:id" component={UserPage} />
Here, :id is a parameter that can change based on the user's interaction, allowing you to render different content depending on the value passed in the URL.
Navigating Between Routes
To navigate between routes, React provides the Link component. This acts like an anchor tag (<a>) but without causing a full page reload, making the navigation experience much smoother.
Example:<Link to="/about">About Us</Link>
By clicking this link, the app will navigate to the /about route, rendering the AboutPage component.
Advanced Features: Nested Routes and Switch
React Route also supports nested routes, allowing you to define routes within other components. This is useful for complex applications where different sections of a page may have their own sub-navigation.
Additionally, the Switch component ensures that only the first matching route is rendered. This is particularly useful for handling 404 pages or other fallback content.
Example:<Switch> <Route exact path="/" component={HomePage} /> <Route path="/about" component={AboutPage} /> <Route path="*" component={NotFoundPage} /> </Switch>
In this example, the NotFoundPage will be displayed for any route that doesn’t match the defined paths.
Conclusion
React Route is more than just a tool for managing navigation; it's the backbone of your React application's user experience. By mastering its features—like dynamic routing, nested routes, and the Switch component—you can create responsive, user-friendly SPAs that feel seamless and intuitive. Whether you’re just starting with React or looking to refine your skills, understanding React Route is essential for modern web development.
0 notes
Text
bootstrap navbar react router
Creating a Bootstrap Navbar with React Router: A Step-by-Step Guide
Navigating through a React application seamlessly is essential for a smooth user experience. Integrating React Router with a Bootstrap navbar is an excellent way to create a functional and aesthetically pleasing navigation system. Here’s how to do it.
Step 1: Set Up Your React Project
First, make sure you have a React project set up. You can create one using Create React App if you don't have a project already.npx create-react-app react-bootstrap-navbar cd react-bootstrap-navbar npm install react-router-dom bootstrap
Step 2: Install Necessary Packages
To use Bootstrap with React, you need to install Bootstrap and React Router DOM.npm install react-bootstrap bootstrap react-router-dom
Step 3: Add Bootstrap CSS
Include Bootstrap CSS in your project by adding the following line to your src/index.js file:import 'bootstrap/dist/css/bootstrap.min.css';
Step 4: Set Up React Router
Configure React Router in your application. Create a src/components directory and add your page components there. For this example, let’s create three simple components: Home, About, and Contact.
src/components/Home.jsimport React from 'react'; function Home() { return <h2>Home Page</h2>; } export default Home;
src/components/About.jsimport React from 'react'; function About() { return <h2>About Page</h2>; } export default About;
src/components/Contact.jsimport React from 'react'; function Contact() { return <h2>Contact Page</h2>; } export default Contact;
Step 5: Create the Navbar Component
Now, create a Navbar component that will use Bootstrap styles and React Router links.
src/components/Navbar.jsimport React from 'react'; import { Navbar, Nav, Container } from 'react-bootstrap'; import { LinkContainer } from 'react-router-bootstrap'; function AppNavbar() { return ( <Navbar bg="dark" variant="dark" expand="lg"> <Container> <Navbar.Brand href="/">MyApp</Navbar.Brand> <Navbar.Toggle aria-controls="basic-navbar-nav" /> <Navbar.Collapse id="basic-navbar-nav"> <Nav className="me-auto"> <LinkContainer to="/"> <Nav.Link>Home</Nav.Link> </LinkContainer> <LinkContainer to="/about"> <Nav.Link>About</Nav.Link> </LinkContainer> <LinkContainer to="/contact"> <Nav.Link>Contact</Nav.Link> </LinkContainer> </Nav> </Navbar.Collapse> </Container> </Navbar> ); } export default AppNavbar;
Step 6: Set Up Routing
Configure routing in your main App.js file to render the appropriate components based on the URL.
src/App.jsimport React from 'react'; import { BrowserRouter as Router, Route, Routes } from 'react-router-dom'; import AppNavbar from './components/Navbar'; import Home from './components/Home'; import About from './components/About'; import Contact from './components/Contact'; function App() { return ( <Router> <AppNavbar /> <Routes> <Route path="/" element={<Home />} /> <Route path="/about" element={<About />} /> <Route path="/contact" element={<Contact />} /> </Routes> </Router> ); } export default App;
Step 7: Run Your Application
Start your development server to see your Bootstrap navbar with React Router in action.npm start
Open your browser and navigate to http://localhost:3000. You should see your navigation bar at the top of the page, allowing you to switch between the Home, About, and Contact pages seamlessly.
Conclusion
By following these steps, you’ve created a responsive and dynamic navigation bar using Bootstrap and React Router. This setup not only enhances the user experience with smooth navigation but also leverages the power of React components and Bootstrap's styling. Happy coding!
1 note
·
View note
Text
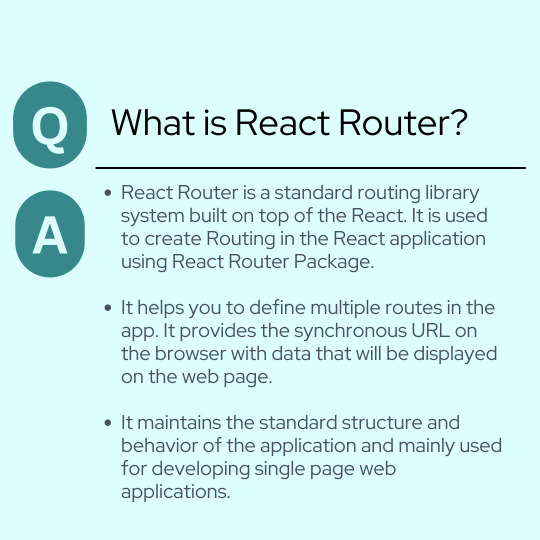
React Interview Questions . . . What is React Router? . . . for more interview questions and tutorial https://bit.ly/4bvU9em check the above link
0 notes
Text
Top 10 Highest Paying Jobs in india 2024
Find out which are India's top 10 highest-paying jobs for 2024. Examine profitable job options and pay opportunities across a range of industries.
Explore a world of opportunities at NIILM University, where learning and success combine. We provide a wide variety of undergraduate and graduate courses to meet the needs of students with various interests and professional goals. Our programs, which place a value on complete growth, combine tough coursework with practical experience to give students the tools they need to succeed in their chosen industries. In addition to academics, we provide complete placement services that link exceptional people with top companies. Come along with us at NIILM University as we set out to achieve both professional and academic success.
Top 10 Highest Paying Jobs
Data Scientist Blockchain Developer Cybersecurity Specialist Full Stack Developer App Developer (Mobile Applications) Product Manager DevOps Engineer Cloud Architect Robotics Engineer Artificial Intelligence (AI) Engineer
1. Data Scientist
Data scientists examine complex information to obtain insights and guide corporate choices. To find patterns and trends in big datasets, they apply machine learning algorithms, statistical approaches, and programming knowledge.
Job Description - To find business opportunities, work with cross-functional teams to develop predictive models, mine and analyze data, and present findings to stakeholders.
Annual Salary (in INR)- 6 - 13.5 LPA
2. Blockchain Developer
Blockchain developers are experts at using blockchain technology to create smart contracts and decentralized apps (dApps). They operate on several blockchain systems, including Hyperledger, Ethereum, and others.
Job Description - Create smart contracts, optimize blockchain performance, connect blockchain with current systems, and design and implement blockchain solutions.
Annual Salary (in INR)- 6 - 15 LPA
3. Cybersecurity Specialist
Cybersecurity experts defend data, networks, and computer systems from online attacks. They put security measures into place, keep an eye on systems for questionable activity, and react when security is compromised.
Job Description - Develop incident response plans, identify security vulnerabilities, install routers and detection systems, conduct security assessments, and put security protocols into practice.
Annual Salary (in INR)- 5 - 10.5 LPA
4. Full Stack Developer
Front-end and back-end web development are areas of expertise for full-stack developers. They work on all aspects of developing web applications, including server-side logic and user interface design.
Job Description - Develop and maintain web applications, design user interfaces, write server-side code, manage databases, and collaborate with cross-functional teams.
Annual Salary (in INR)- 5 - 10.5 LPA
4. App Developer (Mobile Applications)
App developers specialize in creating mobile applications for various platforms, such as iOS and Android. They are proficient in mobile app development frameworks and programming languages.
Job Description - The creation of mobile applications for several platforms, including iOS and Android, is the area of expertise for app developers. Programming languages and frameworks for developing mobile apps are areas in which they excel.
Annual Salary (in INR)- 5 - 10.5 LPA
5. App Developer (Mobile Applications)
Job Description - The creation of mobile applications for several platforms, including iOS and Android, is the area of expertise for app developers. Programming languages and frameworks for developing mobile apps are areas in which they excel.
Annual Salary (in INR)- 5 - 10.5 LPA
6. Product ManagerProduct managers control the creation and introduction of goods and services. Determining the product strategy, setting feature priorities, and guaranteeing alignment with business objectives are their responsibilities.
Job Description - Throughout the product lifecycle, carry out market research, specify requirements, draft product roadmaps, manage cross-functional teams, and communicate with stakeholders.
Annual Salary (in INR)- 6 - 13.5 LPA
7. DevOps Engineer
DevOps engineers bridge the gap between development and operations teams by implementing automation and continuous integration/continuous deployment (CI/CD) pipelines. They focus on improving collaboration and efficiency in software development and deployment processes.
Job Description - Coordinate with development and operations teams, monitor system performance, control configuration, and release procedures, automate infrastructure deployment, and troubleshoot problems.
Annual Salary (in INR)- 6 - 12 LPA
8. Cloud Architect
Cloud architects create and put into practice enterprise cloud computing solutions. They evaluate the needs, choose the best cloud services, and create scalable, safe, and economical designs.
Job Description - Create cloud infrastructure, move apps to the cloud, improve cloud performance, put best practices for security into effect, and offer advice on cloud adoption tactics.
Annual Salary (in INR)- 8 - 16 LPA
9. Robotics Engineer
Robotics engineers create, assemble, and maintain robots and robotic systems for a range of uses in industry, medicine, and research. They combine their expertise in computer science, electronics, and mechanical engineering.
Job Description - Create robot systems and parts, program actions and behaviors, test and debug robotic systems, and work on robotics projects with interdisciplinary teams.
Annual Salary (in INR)- 5 - 10.5 LPA
10. Artificial Intelligence (AI) Engineer:
AI engineers create machine learning and artificial intelligence solutions to address challenging issues. They create algorithms, develop machine learning models, and implement AI in a range of applications.
Job Description - Create AI models and algorithms, gather and prepare data, train and assess machine learning models, implement AI solutions, and work with software engineers and data scientists.
Annual Salary (in INR)- 7 - 15 LPA
Conclusion
These top 10 best-paid occupations for 2024 provide qualified workers with significant financial rewards and exciting career chances in the constantly changing Indian job market. Those who are prepared to invest in their education and experience can find fascinating employment in a variety of fields, including technology, healthcare, finance, and aviation.
Frequently Asked Questions (FAQs)Q1.What soft skills are crucial?
A1. Communication, problem-solving, teamwork, and adaptability.
Q2.What qualifications are required for these high-paying jobs?
A2.The requirements for each professional post are different, but they usually involve applicable degrees, certificates, and specialized knowledge in fields like engineering, programming, or data analysis.
Q3.Can recent graduates enter these fields?
A3.Yes, through internships or specialized training, though some roles may require minimal experience.
Q4.Do these salaries vary by region?
A4.Yes, slightly, but the figures represent average salaries across India.
Q5.How can I find job opportunities?
A5. Online portals, networking, and industry events are key avenues.

0 notes
Text
The Thalamus: Unreeling the Brain's Command Center

The Thalamus: Not the OS, But More Like a Central Router
In a computer, the operating system (OS) manages all software and hardware on the computer. It schedules tasks, efficiently manages computational resources, and facilitates user interaction with the system. While the thalamus does manage and direct information, it's not managing the brain's "software and hardware" in the full capacity that an OS would. Instead, a more accurate analogy would be to compare the thalamus to a central router or a network traffic controller within the brain's communication system.
The Thalamus: The Brain's Traffic Controller
Central Hub of Sensory Information Imagine your brain as the ultimate gaming setup, where the thalamus is the router, directing every bit of sensory input to its proper destination. It's like the central hub in a vast network, ensuring that signals from your eyes, ears, and skin are sent to the right places in your brain. Without the thalamus, your brain wouldn't be able to process that a puck has flown into the goal or that your favorite anime character just appeared on screen.
Master Regulator of Consciousness The thalamus doesn't just handle sensory data; it's like the power management system in your computer, determining when to wake up or go to sleep. By controlling this sleep-wake cycle, the thalamus acts like the system settings that switch your device from full brightness in gameplay to 'sleep mode' when it’s time to rest. This ensures you're alert when you need to be and helps you disconnect to recharge.
Enhancer of Memory and Learning Think of the thalamus as the save point in your favorite RPG. It works with the hippocampus — the memory storage in your brain — to turn your daily experiences into long-term memories. Just like saving your game progress, the thalamus helps encode new experiences so you can retrieve them later. Ever remember a scene from a manga or a game strategy days later? That's the thalamus at work!
Coordinator of Emotional Responses Your emotions are as varied as genres in manga and anime, from thrillers to romances. The thalamus connects to the limbic system, your brain's emotional heartland, to help you react appropriately to what you see and experience. It's like the emotion engine in a game, triggering a rush of adrenaline when you score a goal or a pang of sadness in a touching anime scene.
Architect of Smooth, Continuous Experience Just as a high-quality anime stream should be smooth and uninterrupted, the thalamus ensures your conscious experience is seamless. It links your moment-to-moment perceptions, much like a video buffer that ensures there's no lag or disruption in what you're watching or doing. This is why you can follow the puck in a fast-moving hockey game or get lost in the continuous story of a manga series without missing a beat.
Director of Your Dream World During REM sleep, the stage of sleep where you dream, the thalamus becomes the director of your own personal movie. It crafts vivid dream sequences that can be as bizarre and engaging as any anime adventure. These dreams are not just for entertainment; they help process emotions and solidify memories, like a recap or a filler episode that helps make sense of the main story.
The Brain's Resilience Builder Like the auto-update feature that improves your gaming experience, the thalamus supports neuroplasticity — your brain's ability to adapt and learn. After an injury or while learning a new skill, the thalamus helps rewire the brain, optimizing recovery and adaptation, ensuring that your brain remains as responsive and effective as the latest software update.
Why This Matters to You
Understanding the thalamus can change how we approach various brain disorders and everyday challenges. From treating insomnia and managing emotional responses to enhancing learning and memory, targeting the thalamus could lead to breakthrough treatments and improvements in cognitive health.
In Conclusion: Next time you dodge an opponent in a hockey game, enjoy a twist in your favorite manga, or recall a great anime episode, remember the thalamus. It’s the unsung hero behind the scenes, ensuring your brain's operations are as smooth and efficient as the best-designed games and stories. So, let’s give a nod to this powerhouse of the brain, powering up our experiences one moment at a time! 🧠🎮📚
#Neuroscience#BrainHealth#Thalamus#CognitiveScience#Consciousness#BrainFunction#MentalHealth#Neurology#SensoryProcessing#SleepResearch#Memory#Learning#EmotionalRegulation#Neuroplasticity#BrainAnatomy#NeuralNetworks#CognitiveNeuroscience#BrainScience#Psychology#NeuroResearch
0 notes
Text
React Router: Navigating Through Your Single-Page Applications
In today's web development landscape, Single-Page Applications (SPAs) have become increasingly popular due to their ability to provide a smooth and efficient user experience. However, as the complexity of these applications grows, managing navigation and handling different routes can become a daunting task. Enter React Router, a powerful routing library designed specifically for React applications.

React Router is a collection of navigational components that allow you to create and manage routes within your React application. By incorporating React Router into your project, you can create a seamless navigation experience, manage URLs, and handle different views or components based on the current URL. In this blog post, we'll explore the core concepts of React Router and how it can revolutionize the way you navigate through your Single-Page Applications.
1. Understanding Single-Page Applications and Client-Side Routing
Before we dive into React Router, it's essential to understand the concept of Single-Page Applications (SPAs) and client-side routing. Unlike traditional multi-page websites, where each new page requires a full page refresh, SPAs load a single HTML page and dynamically update the content based on user interactions. This approach eliminates the need for page reloads, resulting in faster load times and smoother transitions between different views or components.
Client-side routing is a technique used in SPAs to handle navigation without requiring a full page refresh. Instead of relying on the server to handle route changes, client-side routing allows the application to manage navigation and URL updates within the browser itself. This is where React Router comes into play, providing a seamless and efficient way to handle client-side routing in React applications.
2. Setting Up React Router
To get started with React Router, you'll need to install it as a dependency in your React project. There are two main packages you'll need: `react-router-dom` for web applications and `react-router-native` for mobile applications built with React Native. For the purposes of this blog post, we'll focus on the `react-router-dom` package.
Once installed, you'll need to import the necessary components from the `react-router-dom` package and set up your application's router. This typically involves wrapping your application with the `BrowserRouter` component and defining routes using the `Route` component.
3. Defining Routes
React Router allows you to define routes for your application, mapping specific URLs to corresponding components. This is done using the `Route` component, which takes a `path` prop that specifies the URL pattern to match and a `component` or `render` prop that determines which component or element should be rendered when the URL matches the specified path.
You can define nested routes by nesting `Route` components within other `Route` components. This can be particularly useful when building complex applications with multiple levels of navigation.
4. Navigation with Links and NavLinks
React Router provides two primary components for navigation: `Link` and `NavLink`. Both components render an accessible `<a>` element that links to the specified route.
The `Link` component is used for basic navigation between routes, while the `NavLink` component is designed for navigation scenarios where you need to apply active styling to the currently active link. The `NavLink` component takes an `activeClassName` prop that allows you to specify a CSS class to be applied to the link when it's active (i.e., when the URL matches the link's `to` prop).
5. Handling Route Parameters
In many applications, you'll need to pass data or parameters through the URL. React Router makes it easy to handle route parameters by defining dynamic segments in your route paths. These dynamic segments are prefixed with a colon (`:`) and can be accessed through the `match` object passed to the corresponding component.
For example, if you have a route defined as `/products/:productId`, you can access the `productId` parameter in your component by using `match.params.productId`.
6. Programmatic Navigation
While `Link` and `NavLink` components provide a declarative way to navigate between routes, React Router also offers programmatic navigation through the `history` object. This object is available in any component rendered by a `Route` component and provides methods for navigating to different routes, pushing new entries onto the history stack, or replacing the current entry in the history stack.
Programmatic navigation can be useful in scenarios where you need to navigate based on user interactions, such as form submissions or button clicks.
7. Nested Routes and Layout Components
React Router allows you to create nested routes, which can be particularly useful when building applications with complex layouts or multiple levels of navigation. By nesting `Route` components, you can define parent and child routes, making it easier to manage and organize your application's structure.
Additionally, React Router provides the ability to create reusable layout components using the `Route` component's `render` prop or the `children` prop. These layout components can wrap around your application's content, providing a consistent structure and shared elements across multiple routes.
8. Protected Routes and Authentication
In many web applications, you'll need to implement authentication and authorization mechanisms to protect certain routes or components from unauthorized access. React Router offers several ways to handle protected routes, such as using higher-order components, render props, or custom components.
By combining React Router with authentication and authorization logic, you can ensure that only authenticated users can access certain routes or components, while redirecting unauthenticated users to a login page or displaying an appropriate message.
9. Code Splitting and Lazy Loading
One of the benefits of using React Router is the ability to leverage code splitting and lazy loading techniques. By splitting your application's code into smaller chunks and loading them on demand, you can improve the initial load time and overall performance of your application.
React Router provides the `React.lazy` function and the `Suspense` component, which allow you to lazily load components and routes, ensuring that users only download the code they need for the current route.
10. Integrating with Redux or Other State Management Libraries
While React Router is a routing library, it can be seamlessly integrated with other state management libraries like Redux or Context API. By combining React Router with these libraries, you can manage global application state, share data between components, and handle complex application logic more effectively.
Redux, in particular, provides a way to manage routing state within your application's Redux store, allowing you to dispatch actions and update the routing state based on user interactions or other events.
Conclusion
React Router is a powerful tool that simplifies the process of implementing client-side routing in your React applications. By understanding its core concepts and leveraging its features, you can create seamless navigation experiences, manage complex application structures, and deliver fast and efficient Single-Page Applications. Whether you're building a simple website or a complex web application, React Router provides the flexibility and robustness needed to handle routing and navigation requirements. With its rich ecosystem of additional libraries and integrations, React Router empowers developers to build modern, responsive, and user-friendly web applications that deliver exceptional user experiences. If you're looking to hire dedicated ReactJS developers or a hire React js development company, ensuring they have expertise in React Router is crucial for creating seamless and efficient Single-Page Applications.
0 notes
Text
Identity Security
In today's digitized world, where everything from shopping to banking is conducted online, ensuring identity security has become paramount. With cyber threats rising, protecting our personal information from unauthorized access has become more critical than ever. This blog post will delve into identity security, its significance, and practical steps to safeguard your digital footprint.
youtube
Identity security is the measures taken to protect personal information from being accessed, shared, or misused without authorization. It encompasses a range of practices designed to safeguard one's identity, such as securing online accounts, protecting passwords, and practicing safe online browsing habits. Maintaining robust identity security is crucial for several reasons. Firstly, it helps prevent identity theft, which can have severe consequences, including financial loss, damage to one's credit score, and emotional distress. Secondly, identity security safeguards personal privacy by ensuring that sensitive information remains confidential. Lastly, it helps build trust in online platforms and e-commerce, enabling users to transact confidently.
Table of Contents
Identity Security
Back to basics: Identity Security
Example: Identity Security: The Workflow
Starting Zero Trust Identity Management
Challenges to zero trust identity management
Knowledge Check: Multi-factor authentication (MFA)
The Move For Zero Trust Authentication
Considerations for zero trust authentication
The first action is to protect Identities.
Adopting Zero Trust Authentication
Zero trust authentication: Technology with risk-based authentication
Conditional Access
Zero trust authentication: Technology with JIT techniques
Final Notes For Identity Security
Zero Trust Identity: Validate Every Device
Quick Links
Contact
Subscribe Now
Highlights: Identity Security
Sophisticated Attacks
Identity security has pushed authentication to a new, more secure landscape, reacting to improved technologies and sophisticated attacks. The need for more accessible and secure authentication has led to the wide adoption of zero-trust identity management zero trust authentication technologies like risk-based authentication (RBA), fast identity online (FIDO2), and just-in-time (JIT) techniques.
New Attack Surface
If you examine our identities, applications, and devices, they are in the crosshairs of bad actors, making them probable threat vectors. In addition, we are challenged by the sophistication of our infrastructure, which increases our attack surface and creates gaps in our visibility. Controlling access and the holes created by complexity is the basis of all healthy security. Before we jump into the zero-trust authentication and components needed to adopt zero-trust identity management, let’s start with the basics of identity security.
Related: Before you proceed, you may find the following posts helpful
SASE Model
Zero Trust Security Strategy
Zero Trust Network Design
OpenShift Security Best Practices
Zero Trust Networking
Zero Trust Network
Zero Trust Access
Zero Trust Identity
Key Identity Security Discussion Points:
Introduction to identity security and what is involved.
Highlighting the details of the challenging landscape along with recent trends.
Technical details on how to approach implementing a zero trust identity strategy.
Scenario: Different types of components make up zero trust authentication management.
Details on starting a zero trust identity security project.
Back to basics: Identity Security
In its simplest terms, an identity is an account or a persona that can interact with a system or application. And we can have different types of identities.
Human Identity: Human identities are the most common. These identities could be users, customers, or other stakeholders requiring various access levels to computers, networks, cloud applications, smartphones, routers, servers, controllers, sensors, etc.
Non-Human: Identities are also non-human as operations automate more processes. These types of identities are seen in more recent cloud-native environments. Applications and microservices use these machine identities for API access, communication, and the CI/CD tools.
♦Tips for Ensuring Identity Security:
1. Strong Passwords: Create unique, complex passwords for all your online accounts. Passwords should contain a combination of upper- and lowercase letters, numbers, and special characters. Do not use easily guessable information, such as birthdates or pet names.
2. Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security by requiring an additional verification step, such as a temporary code sent to your phone or email.
3. Keep Software Up to Date: Regularly update your operating system, antivirus software, and other applications. These updates often include security patches that address known vulnerabilities.
4. Be Cautious with Personal Information: Be mindful of the information you share online. Avoid posting sensitive details on public platforms or unsecured websites, such as your full address or social security number.
5. Secure Wi-Fi Networks: When connecting to public Wi-Fi networks, ensure they are secure and encrypted. Avoid accessing sensitive information, such as online banking, on public networks.
6. Regularly Monitor Accounts: Keep a close eye on your financial accounts, credit reports, and other online platforms where personal information is stored. Report any suspicious activity immediately.
7. Use Secure Websites: Look for the padlock symbol and “https” in the website address when providing personal information or making online transactions. This indicates that the connection is secure and encrypted.
Example: Identity Security: The Workflow
The concept of identity security is straightforward and follows a standard workflow that can be understood and secured. First, a user logs into their employee desktop and is authenticated as an individual who should have access to this network segment. This is the authentication stage.
They have appropriate permissions assigned so they can navigate to the required assets (such as an application or file servers) and are authorized as someone who should have access to this application. This is the authorization stage.
As they move across the network to carry out their day-to-day duties, all of this movement is logged, and all access information is captured and analyzed for auditing purposes. Anything outside of normal behavior is flagged. Splunk UEBA has good features here.Diagram: Identity security workflow.
Identity Security: Stage of Authentication
Authentication: You need to authenticate every human and non-human identity accurately. After an identity is authenticated to confirm who it is, it only gets a free one for some to access the system with impunity.
Identity Security: Stage of Re-Authentication
Identities should be re-authenticated if the system detects suspicious behavior or before completing tasks and accessing data that is deemed to be highly sensitive. If we have an identity that acts outside of normal baseline behavior, they must re-authenticate.
Identity Security: Stage of Authorization
Then we need to move to the authorization: It’s necessary to authorize the user to ensure they’re allowed access to the asset only when required and only with the permissions they need to do their job. So we have authorized each identity on the network with the proper permissions so they can access what they need and not more.
Identity Security: Stage of Access
Then we look into the Access: Provide access for that identity to authorized assets in a structured manner. How can the appropriate access be given to the person/user/device/bot/script/account and nothing more? Following the practices of zero trust identity management and least privilege. Ideally, access is granted to microsegments instead of significant VLANs based on traditional zone-based networking.
Identity Security: Stage of Audit
Finally, Audit: All identity activity must be audited or accounted for. Auditing allows insight and evidence that Identity Security policies are working as intended. How do you monitor the activities of identities? How do you reconstruct and analyze the actions an identity performed?
An auditing capability ensures visibility into activities performed by an identity, provides context for the identity’s usage and behavior, and enables analytics that identify risk and provide insights to make smarter decisions about access.
Starting Zero Trust Identity Management
Now, we have an identity as the new perimeter compounded by identity being the new target. Any identity is a target. Looking at the modern enterprise landscape, it’s easy to see why. Every employee has multiple identities and uses several devices.
What makes this worse is that security teams’ primary issue is that identity-driven attacks are hard to detect. For example, how do you know if a bad actor or a sys admin uses the privilege controls? As a result, security teams must find a reliable way to monitor suspicious user behavior to determine the signs of compromised identities.
We now have identity sprawl,, which may be acceptable if only one of those identities has user access. However, they don’t, and they most likely have privileged access. All these widen the attack surface by creating additional human and machine identities that can gain privileged access under certain conditions. All of which will establish new pathways for bad actors.
We must adopt a different approach to secure our identities regardless of where they may be. Here, we can look for a zero-trust identity management approach based on identity security. Next, I’d like to discuss your common challenges when adopting identity security.Diagram: Zero trust identity management. The challenges.
Challenges to zero trust identity management
Challenge: Zero trust identity management and privilege credential compromise
Current environments may result in anonymous access to privileged accounts and sensitive information. Unsurprisingly, 80% of breaches start with compromised privilege credentials. If left unsecured, attackers can compromise these valuable secrets and credentials to gain possession of privileged accounts and perform advanced attacks or use them to exfiltrate data.
Challenge: Zero trust identity management and exploiting privileged accounts
So, we have two types of bad actors. First, there are external attackers and malicious insiders that can exploit privileged accounts to orchestrate a variety of attacks. Privileged accounts are used in nearly every cyber attack. With privileged access, bad actors can disable systems, take control of IT infrastructure, and gain access to sensitive data. So, we face several challenges when securing identities, namely protecting, controlling, and monitoring privileged access.
Challenge: Zero trust identity management and lateral movements
Lateral movements will happen. A bad actor has to move throughout the network. They will never land directly on a database or important file server. The initial entry point into the network could be an unsecured IoT device, which does not hold sensitive data. As a result, bad actors need to pivot across the network.
They will laterally move throughout the network with these privileged accounts, looking for high-value targets. They then use their elevated privileges to steal confidential information and exfiltrate data. There are many ways to exfiltrate data, with DNS being a common vector that often goes unmonitored. How do you know a bad actor is moving laterally with admin credentials using admin tools built into standard Windows desktops?
Challenge: Zero trust identity management and distributed attacks
These attacks are distributed, and there will be many dots to connect to understand threats on the network. Could you look at ransomware? Enrolling the malware needs elevated privilege, and it’s better to detect this before the encryption starts. Some ransomware families perform partial encryption quickly. Once encryption starts, it’s game over. You need to detect this early in the kill chain in the detect phase.
The best way to approach zero trust authentication is to know who accesses the data, ensure the users they claim to be, and operate on the trusted endpoint that meets compliance. There are plenty of ways to authenticate to the network; many claim password-based authentication is weak.
The core of identity security is understanding that passwords can be phished; essentially, using a password is sharing. So, we need to add multifactor authentication (MFA). MFA gives a big lift but needs to be done well. You can get breached even if you have an MFA solution in place.
Knowledge Check: Multi-factor authentication (MFA)
More than simple passwords are needed for healthy security. A password is a single authentication factor – anyone with it can use it. No matter how strong it is, keeping information private is useless if lost or stolen. You must use a different secondary authentication factor to secure your data appropriately.
Here’s a quick breakdown:
•Two-factor authentication: This method uses two-factor classes to provide authentication. It is also known as ‘2FA’ and ‘TFA.’
•Multi-factor authentication: use of two or more factor classes to provide authentication. This is also represented as ‘MFA.’
•Two-step verification: This method of authentication involves two independent steps but does not necessarily require two separate factor classes. It is also known as ‘2SV’.
•Strong authentication: authentication beyond simply a password. It may be represented by the usage of ‘security questions’ or layered security like two-factor authentication.
The Move For Zero Trust Authentication
No MFA solution is an island. Every MFA solution is just one part of multiple components, relationships, and dependencies. Each piece is an additional area where an exploitable vulnerability can occur.
Essentially, any component in the MFA’s life cycle, from provisioning to de-provisioning and everything in between, is subject to exploitable vulnerabilities and hacking. And like the proverbial chain, it’s only as strong as its weakest link.
The need for zero trust authentication: Two or More Hacking Methods Used
Many MFA attacks use two or more of the leading hacking methods. Often, social engineering is used to start the attack and get the victim to click on a link or to activate a process, which then uses one of the other methods to accomplish the necessary technical hacking.
For example, a user gets a phishing email directing them to a fake website, which accomplishes a man-in-the-middle (MitM) attack and steals credential secrets. Or physical theft of a hardware token is performed, and then the token is forensically examined to find the stored authentication secrets. MFA hacking requires using two or all of these main hacking methods.
You can’t rely on MFA alone; you must validate privileged users with context-aware Adaptive Multifactor Authentication and secure access to business resources with Single Sign-On. Unfortunately, credential theft remains the No. 1 area of risk. And bad actors are getting better at bypassing MFA using a variety of vectors and techniques.
For example, a bad actor can be tricked into accepting a push notification to their smartphone to grant access in the context of getting admission. You are still acceptable to man-in-the-middle attacks. This is why MFA and IDP vendors introduce risk-based authentication and step-up authentication. These techniques limited the attack surface, which we will talk about soon.
Considerations for zero trust authentication
Think like a bad actor.
By thinking like a bad actor, we can attempt to identify suspicious activity, restrict lateral movement, and contain threats. Try envisioning what you would look for if you were a bad external actor or malicious insider. For example, are you looking to steal sensitive data to sell it to competitors, or are you looking to start Ransomware binaries or use your infrastructure for illicit crypto mining?
Attacks with happen
The harsh reality is that attacks will happen, and you can only partially secure some of their applications and infrastructure wherever they exist. So it’s not a matter of ‘if’ but a concern of “when.” Protection from all the various methods that attackers use is virtually impossible, and there will occasionally be day 0 attacks. So, they will get in eventually; It’s all about what they can do once they are in.Diagram: Zero trust authentication. Key considerations.
The first action is to protect Identities.
Therefore, the very first thing you must do is protect their identities and prioritize what matters most – privileged access. Infrastructure and critical data are only fully protected if privileged accounts, credentials, and secrets are secured and protected.
The bad actor needs privileged access.
We know that about 80% of breaches tied to hacking involve using lost or stolen credentials. Compromised identities are the common denominator in virtually every severe attack. The reason is apparent:
The bad actor needs privileged access to the network infrastructure to steal data. However, without privileged access, an attacker is severely limited in what they can do. Furthermore, without privileged access, they may be unable to pivot from one machine to another. And the chances of landing on a high-value target are doubtful.
The malware requires admin access.
The malware used to pivot and requires admin access to gain persistence; privileged access without vigilant management creates an ever-growing attack surface around privileged accounts.
Adopting Zero Trust Authentication
Zero trust authentication: Technology with Fast Identity Online (FIDO2)
Where can you start identity security with all of this? Firstly, we can look at a zero-trust authentication protocol. We need an authentication protocol that can be phishing-resistant. This is FIDO2, known as Fast Identity Online (FIDO2), built on two protocols that effectively remove any blind protocols. FIDO authentication Fast Identity Online (FIDO) is a challenge-response protocol that uses public-key cryptography. Rather than using certificates, it manages keys automatically and beneath the covers.
The FIDO2 standards
FIDO2 uses two standards. The Client to Authenticator Protocol (CTAP) describes how a browser or operating system establishes a connection to a FIDO authenticator. The WebAuthn protocol is built into browsers and provides an API that JavaScript from a web service can use to register a FIDO key, send a challenge to the authenticator, and receive a response to the challenge.
So there is an application the user wants to go to, and then we have the client that is often the system’s browser, but it can be an application that can speak and understand WebAuthn. FIDO provides a secure and convenient way to authenticate users without using passwords, SMS codes, or TOTP authenticator applications. Modern computers and smartphones and most mainstream browsers understand FIDO natively.
FIDO2 addresses phishing by cryptographically proving that the end-user has a physical position over the authentication. There are two types of authenticators: a local authenticator, such as a USB device, and a roaming authenticator, such as a mobile device. These need to be certified FIDO2 vendors.
The other is a platform authenticator such as Touch ID or Windows Hello. While roaming authenticators are available, for most use cases, platform authenticators are sufficient. This makes FIDO an easy, inexpensive way for people to authenticate. The biggest impediment to its widespread use is that people won’t believe something so easy is secure.
Zero trust authentication: Technology with risk-based authentication
Risk is not a static attribute, and it needs to be re-calculated and re-evaluated so you can make intelligent decisions for step-up and user authentication. We have Cisco DUO that reacts to risk-based signals at the point of authentication.
So, these risk signals are processed in real time to detect signs of known account takeout signals. These signals may include Push Bombs, Push Sprays, and Fatigue attacks. Also, a change of location can signal high risk. Risk-based authentication (RBA) is usually coupled with step-up authentication.
For example, let’s say your employees are under attack. RBA can detect this attack as a stuffing attack and move from a classic authentication approach to a more secure verified PUSH approach than the standard PUSH.
This would add more friction but result in better security, such as adding three to six digital display keys at your location/devices, and you need to enter this key in your application. This eliminates fatigue attacks. This verified PUSH approach can be enabled at an enterprise level or just for a group of users.
Conditional Access
Then, we move towards conditional access, a step beyond authentication. Conditional access goes beyond authentication to examine the context and risk of each access attempt. For example, contextual factors may include consecutive login failures, geo-location, type of user account, or device IP to either grant or deny access. Based on those contextual factors, it may be granted only to specific network segments.
A key point: Risk-based decisions and recommended capabilities
The identity security solution should be configurable to allow SSO access, challenge the user with MFA, or block access based on predefined conditions set by policy. It would help if you looked for a solution that can offer a broad range of shapes, such as IP range, day of the week, time of day, time range, device O/S, browser type, country, and user risk level.
These context-based access policies should be enforceable across users, applications, workstations, mobile devices, servers, network devices, and VPNs. A key question is whether the solution makes risk-based access decisions using a behavior profile calculated for each user.
Zero trust authentication: Technology with JIT techniques
Secure privileged access and manage entitlements. For this reason, many enterprises employ a least privilege approach, where access is restricted to the resources necessary for the end-user to complete their job responsibilities with no extra permission. A standard technology here would be Just in Time (JIT). Implementing JIT ensures that identities have only the appropriate privileges, when necessary, as quickly as possible and for the least time required.
JIT techniques that dynamically elevate rights only when needed are a technology to enforce the least privilege. The solution allows for JIT elevation and access on a “by request” basis for a predefined period, with a full audit of privileged activities. Full administrative rights or application-level access can be granted, time-limited, and revoked.
Final Notes For Identity Security
Zero trust identity management is where we continuously verify users and devices to ensure access, and privileges are granted only when needed. The backbone of zero-trust identity security starts by assuming that any human or machine identity with access to your applications and systems may have been compromised.
The “assume breach” mentality requires vigilance and a Zero Trust approach to security centered on securing identities. With identity security as the backbone of a zero-trust process, teams can focus on identifying, isolating, and stopping threats from compromising identities and gaining privilege before they can harm.Diagram: Identity Security: Final notes.
Zero Trust Authentication
The identity-centric focus of zero trust authentication uses an approach to security to ensure that every person and every device granted access is who and what they say they are. It achieves this authentication by focusing on the following key components:
The network is always assumed to be hostile.
External and internal threats always exist on the network.
Network locality needs to be more sufficient for deciding trust in a network. Just so you know, other contextual factors, as discussed, must be taken into account.
Every device, user, and network flow is authenticated and authorized. All of this must be logged.
Security policies must be dynamic and calculated from as many data sources as possible.
Zero Trust Identity: Validate Every Device
Not just the user
Validate every device. While user verification adds a level of security, more is needed. We must ensure that the devices are authenticated and associated with verified users, not just the users.
Risk-based access
Risk-based access intelligence should reduce the attack surface after a device has been validated and verified as belonging to an authorized user. This allows aspects of the security posture of endpoints, like device location, a device certificate, OS, browser, and time, to be used for further access validation.
Device Validation: Reduce the attack surface
Remember that while device validation helps limit the attack surface, device validation is only as reliable as the endpoint’s security. Antivirus software to secure endpoint devices will only get you so far. We need additional tools and mechanisms that can tighten security even further.
Summary: Identity Security
In today’s interconnected digital world, protecting our identities online has become more critical than ever. From personal information to financial data, our digital identities are vulnerable to various threats. This blog post aimed to shed light on the significance of identity security and provide practical tips to enhance your online safety.
Section 1: Understanding Identity Security
Identity security refers to the measures taken to safeguard personal information and prevent unauthorized access. It encompasses protecting sensitive data such as login credentials, financial details, and personal identification information (PII). By ensuring robust identity security, individuals can mitigate the risks of identity theft, fraud, and privacy breaches.
Section 2: Common Threats to Identity Security
In this section, we’ll explore some of the most prevalent threats to identity security. This includes phishing attacks, malware infections, social engineering, and data breaches. Understanding these threats is crucial for recognizing potential vulnerabilities and taking appropriate preventative measures.
Section 3: Best Practices for Strengthening Identity Security
Now that we’ve highlighted the importance of identity security and identified common threats let’s delve into practical tips to fortify your online presence:
1. Strong and Unique Passwords: Utilize complex passwords that incorporate a combination of letters, numbers, and special characters. Avoid using the same password across multiple platforms.
2. Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an extra layer of security. This typically involves a secondary verification method, such as a code sent to your mobile device.
3. Regular Software Updates: Keep all your devices and applications current. Software updates often include security patches that address known vulnerabilities.
4. Beware of Phishing Attempts: Be cautious of suspicious emails, messages, or calls asking for personal information. Verify the authenticity of requests before sharing sensitive data.
5. Secure Wi-Fi Networks: When connecting to public Wi-Fi networks, use a virtual private network (VPN) to encrypt your internet traffic and protect your data from potential eavesdroppers.
Section 4: The Role of Privacy Settings
Privacy settings play a crucial role in controlling the visibility of your personal information. Platforms and applications often provide various options to customize privacy preferences. Take the time to review and adjust these settings according to your comfort level.
Section 5: Monitoring and Detecting Suspicious Activity
Remaining vigilant is paramount in maintaining identity security. Regularly monitor your financial statements, credit reports, and online accounts for any unusual activity. Promptly report any suspicious incidents to the relevant authorities.
Conclusion:
In an era where digital identities are constantly at risk, prioritizing identity security is non-negotiable. By implementing the best practices outlined in this blogpost, you can significantly enhance your online safety and protect your valuable personal information. Remember, proactive measures and staying informed are key to maintaining a secure digital identity.
0 notes