#reaver kali linux
Explore tagged Tumblr posts
Text
Comparative review of best #WiFi Adapters with monitor mode and packet injection capabilities for #KaliLinux for real-world.
#aircrack-ng#Atheros AR9271#Cracking#Driver#GUI#Hashcat#Kali Linux#Linux#Linux Kernel#monit#Monitor#monitor mode#Monitoring#N600#packet injection#PCI#Penetration Test#penetration testing#Pyrit#Reaver-WPS#Recommended#RTL8812AU#RTL8814AU#Security#Security Audit#TP-Link#Troubleshooting#Virtualbox#wireless#Wireless Cards
0 notes
Photo

Reaver Kali Linux Tutorial To Hack WPS Enabled WPA/WAP2 WiFi Network
#download reaver#kali tool#reaver kali linux#REAVER KALI LINUX TUTORIAL#wifi network hack#WPS ENABLED WPA/WAP2
1 note
·
View note
Text
How to Hack WiFi Networks for Beginners

Requirements - A basic understanding of computers. - A basic understanding of networks. - A desire to learn. Description This course is all about WiFi and the security of wireless networks. You will study the different threats, weaknesses and attack methods. No special skills are required as the course covers everything from the very basics including the installation of Kali Linux. The following topics will be covered during the course: - How Wireless Networks Work. - Important Settings to Change on Your Router. - How to Install Kali Linux in VMware Player. - Useful Linux Commands with Examples. - Perform a Denial of Service Attack and Find Hidden Wireless Networks. - How to Hack WiFi Networks (WEP, WPA, WPA2). - Use various tools like: Aircrack-ng, Wifite, Crunch, Cowpatty, Pyrit, Reaver… - How to Create an Evil Twin Access Point. After completing this course you will be confident with breaking all types of WiFi encryption methods. Who this course is for: - Anyone who just simply wants to learn all cool WiFi hacking tricks. Read the full article
1 note
·
View note
Text
Arpspoof download for mac

Local network connections and connections going to/from Internet. However, it is possible to do something even for hosts on another segments Note that hunt is operating onĮthernet and is best used for connections which can be watched through it. Scratch (see FEATURES and DESIGN OVERVIEW). Juggernaut not flexible enough for further development so I started from Like Juggernaut or T-sight that inspired me in my development. It has several features, which I didn't find in any product Hunt is a program for intruding into a connection, watching it and "add conn policy entry" as by default only telnet connections are You may want to select "options" and then Is recommended that you should test how it behaves on some test connectionsĪnd then use it wisely. Please make sure you KNOW what you are doing before using hunt. Original program does not have a manual page. Manual page was written for the Debian GNU/Linux distribution because the This manual page documents briefly the hunt command. Stay up to date with the latest in cyber security and ethical hacking.Hunt - Network security auditing tool. Get direct and instant access to Zaid and the zSecurity team, connect with like-minded people, engage in LIVE hacking sessions, CTFs, competitions and more! Kali Iso Install Installing the ISO from USB to Hard Drive - YouTube Video. Checkout the installation lecture in the course for more info. Installation - Make sure VirtualBox is installed and double click the downloaded.
Added modified hstshijack caplet that works properly with hHSTS websites.
Fixed bettercap hstshijack caplet issue.
Fixed wash and reaver issues with RTL8812AU chipset.
Replaced guest additions x11 and dkms with less buggy versions.
Improved Monitor mode, packet injection and AP mode support.
Here you'll get all the direct download links and guides to install it. Kali Linux ISO Download 64-Bit & 32-Bit Installer (2020.2) If you want to run Kali Linux on Android, VirtualBox or VMware, then you need Kali Linux ISO file. Select the ISO image file of Kali Linux 2020.1a, and use VM configuration according to the system requirements. Launch the VMware Player, and start creating a new virtual machine. Download the Kali Linux 2020.1a ISO image file from the download section. Select USB device and start the Kali Linux 2020.1a installer. The Kali Linux ISO of doom – a great example of the flexibility of live-build, and the types and complexity of customisations possible.Build a self installing, reverse VPN auto-connecting, network bridging Kali image – for the perfect hardware backdoor. Click on the http button to download with your download manager or you can click on the torrent button to download it as torrent. You can download Kali linux 64 bit or 32 bit, click on Kali linux 64 bit or Kali linux 32 bit to download full kali linux with all the tools.

0 notes
Link
0 notes
Text
Jumpstart Wps Alternative
This document covers the installation, set up, and use of this theme, and provides answers and solutions to common problems. We encourage you to first read this document thoroughly if you are experiencing any difficulties before contacting our support team.
Uploading Through WordPress
To upload through your Dashboard, select “Appearance” and then “Themes”. Next, select the “Install Themes” tab at the top of the page and then select the “Upload” link, right above the search field. Choose your file and select “Install Now”. Once the theme is fully uploaded and installed, click “Activate” to activate the WordPress theme.
Some of the main advantages of MLCCs are: Versatility: Ceramic capacitors are available in a very wide range of capacitance values, spanning nine orders of magnitude. They can also be produced with high accuracy and low thermal sensitivity (class 1 devices) or with greater capacitance values but less accuracy and thermal stability (class 2). Dumpper And Jumpstart For Pc Kendrick Lamar Section 80 Zip File Mac Bios Usb Enable For Bootcamp How To Open Gbx Files Sparta War Of Empires Hack The Crew 2 Download Adobe Photoshop Cs2 Paradox Keygen Indir Gezginler Msi Laptop Touchpad Not Working Crack Para Ser.
The theme files will be stored on your server in the wp-content/themes location.
When uploading your theme with the installer, please ensure you are uploading the theme .zip file, not the entire package you downloaded. In this case, you will be uploading JumpstartWPtheme.zip.

FTP Upload
To manually upload your new WordPress theme, login with your credentials to your website and locate the wp-content folder in your WordPress install files. Visual basic 2010 source code samples. Upload the un-zipped Jumpstart WordPress Theme folder into the: wp-content/themes folder.
Once uploaded, activate the theme by heading to the “Themes” menu in the WordPress Dashboard. Locate the Jumpstart WordPress Theme theme and hit “Activate”.
Looking for a good, free FTP solution - why not try FileZilla or CyberDuck
Everybody want internet, Internet is life.
So today I’m gonna show you how to hack WiFi.
This method works sometimes, but it works… Grand theft auto vice city pc full game download free.
Android
Note: Root Needed
WPS Connect by FroX
With this app you’ll can connect to WiFi networks which have WPS protocol enabled. Surface pro 3 surface type cover filter device.
PC
Dummper & JumpStart
Download Links:
Jumpstart Wps Alternative App
Download Links:
They can hack any WiFi, seriously i use them only.
Jumpstart Wps Alternatives
Download Kali Linux
AirCrack
Reaver
PixieWPS
Wifite
Linset
Wifiphisher
HT-WPS Breaker
That’s It
Thanks for reading.
Let me know which method is working for u in comments….
Jumpstart Wps Alternative Download
Happy Hacking!!!!!!!!
0 notes
Text
Hack Wifi Password Using Terminal

Hack Wifi Password Using Terminal Command
Hack Wifi Password Using Terminal Software
How To Hack Wifi Password On Mac Using Terminal 2020
Hack Wifi Password Using Terminal Download
How To Hack Wifi Password On Mac Using Terminal 2019
Hack Wifi Password Using Terminal
Cyber Security Tool For Hacking Wireless Connections Using Built-In Kali Tools. Supports All Securities (WEP, WPS, WPA, WPA2/TKIP/IES) - GitHub - ankit0183/Wifi-Hacking: Cyber Security Tool For Hacking Wireless Connections Using Built-In Kali Tools. Step 1 (Setting up Reaver 1.4 ) 1) Open terminal and type sudo -s and then type your password. 2) Download Reaver (Better Download the Latest Version ) Place in a specified folder. 3) Open the Terminal and type tar xvfz reaver-1.4.tar.gz 4) Install dependencies sudo apt-get install. Crack Wifi Passwords the Easy Way! (OSX Version) DISCLAIMER: This article is for educational purposes only. This article should not be used for illegal activity. The author is not responsible for its use. You are 18 and bored at your grandma’s place, there is no source of entertainment, but you find out there is a sweet wifi spot at your. Part 2: Crack WiFi Password Windows in Minutes. There are lot of people searching this question on internet that 'how to hack WiFi password on Windows 10/8/7' for free, here, now, is a software for you called PassFab Wifi Key, that will be your best choice. With this free software, to hack WiFi password on laptop is no big deal. Hello friends please like and subscribe my channelhttps://youtu.be/CI8GnSlEpyc.
Step By Step Hack WPA/WPA2 Wi Fi Passwords Using Aircrack Ng
In this tutorial I will tell you how to crack wpa/wpa2 wi-fi in kali linux using aircrack-ng. To do this, first you should install kalinux or you can use live kali linux. Print shop 5.0 free download.
To crack Wi-Fi, first, you need a computer with kali linux and a wireless card which supports monitor/injection mode. If your wireless card is not able to do this, you need to get an external wireless card which is capable of monitor/injection mode.
Apart from these tools, you need to have a word-list to crack the password from the captured packets.
First you need to understand how Wi-Fi works. Wi-Fi transmits signal in the form of packets in air so we need to capture all the packets in air so we use airodump to dump all the packets in air .After that we should see that if any one is connected to the victim Wi-Fi. If anyone is not connected the Wi-Fi, cracking is not possible as we need a wpa handshake. We can capture handshake by sending deauthentication packets to client connected to Wi-Fi. Aircrack cracks the password.
Step-1:-
First open terminal. We need to know the name of the wireless adapter connected to the computer because computer has many adapters connected.
command for this is : iwconfig
In my case, my wireless adapter is with the name wlan0. In your case, it may be different. If connected to an external wireless card, it may be wlan1or2.

Step-2:-
For some wireless cards, it gives error messages to enable monitor mode on wireless cards. For that, you should use airmon-ng check kill.
Step-3:-
In this step, you need to enable the monitor mode on the wireless card. The command is as follows:
airmon-ng start wlan0 (interface of wireless card).
Now this command will enable the monitor mode on the wifi card. So while using interface in any terminal or command line use wlan0mon.
Note : You should use the interface which is indicated with red mark.
Step-4:-
We need to use the command airodump-ng wlan0mon, this will display all the access points in your surroundings and also the clients connected to that access points.
Now this command captures the packets in the air. This will gather data from the wireless packets in the air.
Note : Do not close this terminal. This will be used to know wpa has been captured or not.
Step-5:-
In this step we will add some parameters to airodump-ng.
command is : airodump-ng -c channel –bssid (bssid of wifi) -w (path to write the data of packets) wlan0mon(interface).
bssid − in my case bssid is indicated with red mark.
c − channel is the channel of victim wifi in my case it is 10(see in previous screenshot for channel number).
w − It is used to write the captured data to a specified path in my case it is ‘/root/Desktop/hack’
Interface in my case is wlan0mon.
In the above command the path /root/Desktop/hack hack is the name of the file to be saved.
Above command displays this terminal.
Step-6:-
In this step we deauthenticate the connected clients to the Wi-Fi.
The command is aireplay-ng –deauth 10 -a (router bssid) interface
In the above command it is optional to give the client mac address it is given by
This will disconnects the client from access point.
Screen shot of a client connected to access point.
After this the client tries to connect to the Wi-Fi again. At that time, we will capture the packets which sends from client. From this result, we will get wpa handshake.
Step-7:-
Now we should start cracking the Wi-Fi with captured packets command for this is
path to word list in my case it is ‘/root/Desktop/wordlist.txt’
If you did not have word list, get one. If you want to generate your custom wordlist, you can visit our other post: How generate word list using crunch.
Now press enter aircrack will start cracking the Wi-Fi.

Everyone Ask The Question: How To Hack WIFI Password? Is there software that can help, or a trick? Read on to find out.
Hey Guys, Today I am Sharing with You How To Hack WIFI Password. We Have Done This Lots of Time.
Note: Here is The Best Method To Hack WiFi Password. However, Hacking is The Crime. So, Use it For Only Education Purpose.
In Today’s World Everyone Need The Internet, And Without That is Something like Dead man.
First, We Install One Software To Capture The Wifi Packets. Using This Software We Capture The WiFi Packets.
WiFi Packets Mean Someone Request To Connect With WIFI. It will Go To Router using Packets. And Packets contain the Password.
So, When We Capture the Packets it will Contain the Password.
And then We will Find the Password With Wordlist and Packets.
So, Here is The Step By Step Process To Hack WiFi Password.
Step 1: Install Software Called CommView For WiFi
First of All You Need To Download The Zip File called “Hacking WiFi” That Are Given in The Resources Section or Click Here. After That Extract The Zip File. Than Go To The CommView Folder And Open The “setup Commview” File.
Click Next.
Accept The terms and Condition And Click Next.
Select The VolP Mode And Go Next.
Select the Option As You can see in Photo and Go Next
And Install the Software.
Now, We Successfull Install This Software. But, This is Paid Software. So, We Need To Crack it First. To Crack it Open The Crack-Commview Folder. But, Don’t open the CV File.
Now, You can See The Commview for WiFi on Desktop, Right Click on that and Select the Option “Open File Location”.
Now, Paste the CV file From The Crack-Comview To This Folder.
Hack Wifi Password Using Terminal Command
Hurry, You Successfully Install The Software.
Step 2: Capture The packets For Targeted WiFi
Once You Install the Software open it. It will Ask You to Install The Driver. Select the Option that Show in Picture.
After That Your Software Are Closed. Open it Again.
Also Read: How To Install Custom Rom in Android
This Software might Run in Windows 10. So, If You are Using Windows 10 Then it Has less chance to Run the Software.
Now You can See The Full Interface of CVW. Using This Software We Can Hack Wifi Password.
To Capture Wifi packets which You want To Hack, You need To Click Start Button on the Top Left Corrner.
After Start The Capturing, The Wifi List Apper With The Channal Number.
Hack Wifi Password Using Terminal Software
Here You Need To Select Your WiFi You Want To Hack WiFi. And Remember There Channel Number.
After That in Right Sidebar You need to select “Single Channel Mode” and select The WiFi Channel Number You want To hack.
I am Hacking TechnoUtter WiFi. So, I Select The 11 Channel.
Now Go to The Packets Section.
You will See the Packets Are Captured.
Now, Go To Logging.
Select The Auto-saving Option and Enter The Path When You Want To Save The Packets.
How To Hack Wifi Password On Mac Using Terminal 2020
Now Your Packets are Automatically Save.
Wait To at least One Hour To Capture The Packet That Contain WiFI Password.
You Want To Know To How The Packet are Capture The Password For Crack WiFI Password.
How The Packets Capturing The Password
The Packets is Contain Some Things Like IP Address, Password in Encryption Format, etc.
So, When Someone Want To Connect To The WIFI, It will Send The Packet File To the WIFI Router. And That Contain The Password.
So We Need The Packets To Crack The Password.
But, The Password is in Encrypted Format. So, We Also Need To Decrypt it Using Aircrack-ng.
Step 3: Convert The Packets to Capture File
Hack Wifi Password Using Terminal Download
Select File And Open Log Viewer.
Select The File and Select “Load CommView Logs”.
Go Where Your Packets are Saved And Import it.
Now, All The Packets Are Imported.
Now Goto File > Export Log and Select The “Wireshark/Tcpdump Format”.
Make sure You select “.CAP” And Save It on The Desktop File.
Now You Successfully Convert The Packets to the Capture File.
Using This Capture File You Hack WiFi Password.
Step 4: Hack WiFi Password
Now, It’s Time To Hack WIFI Password.
Go To Hacking WiFI Folder And Go To Aircrack-ng Folder.
Now GoTo “Bin” Folder.
Now, Go To The Folder Which Version of Your Computer.
Open That Folder.
Now Open “”Aircrack-ng GUI” File
Now, Select The WPA Option To Crack WPA2 PSK.
Select The Capture File in Filename Option.
And select The Wordlist in the Wordlist Option.
Click Launch, To Crack Wifi Password.
What is Wordlist?
A word list is just what it says it is. It is a list of words. Words that may or may not match someone’s password. Some of them contain commonly used passwords that have long been known to be the most commonly used passwords, and some of them are lists of passwords from leaks of hacked databases. You would use a wordlist to attempt to crack a password using a dictionary attack.
Torrent sites typically have large wordlists you can download, but if you do some google searching you will find a lot of websites with various wordlists.
Wordlists are only so successful though. I’ve had some pretty weak passwords that I have never seen in any wordlist I have ever downloaded.
You can Download The Wordlist On Here.
Now Back to Our Tutorial, when You Click Launch, It’s Open the CMD and List out The WiFi’s name You want To Hack.
Select The Wifi To Hack it. I am Hacking TechnoUtter Wifi So, I Select 1.
After that It will Match The Capture File with The Wordlist.
How To Hack Wifi Password On Mac Using Terminal 2019
If The Password is in the Wordlist Then It will Match And Password is Display.
Hurry, You Can See We hack The TechnoUtter WiFI. Password is The “tech@123utter”.
I will Connect The Wifi You can See.
Hack Wifi Password Using Terminal
Conclusion
Here is The Best Method To Hack WiFi Password. But, Hacking is The Crime. So, Use it For Only Education Purpose.
And If You Like This Article Then Share it On Social Media and Comment if You have Any Problems.
Thanks

0 notes
Text
0x0008#SA#Cracking WPS
Introduction
WPS is Called Wireless protected Setup which is a method to help users to set up their networks. Almost every WIFI-router has a different PIN code behind the wifi router. There are two ways to pass the Authentication, one is pressing the WPS button, another is to input the right PIN code.
Weakness
After several years, some people find that they can implement brute force attack on WPS. This is because the PIN code is very short(8 characters). The attack need to implement 10^8 times to break the password. That seems a lot, but there some flaw in the PIN system. For the 8th char, it is the checksum of the previous 7 char, so an attacker can predict according to the checksum algorithm then the total bits work become 10 ^ 7. I write a simple python program to show you how to break them.
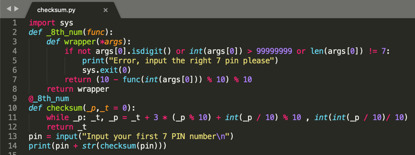
Another flaw is the 1-4 char and 5-7 char can be checked separately which means 10 ^ 4 can be checked first and 10^3 can be checked then. So the total operation is 10 ^ 4 + 10 ^ 3 which is approximately 10 ^4 bits work
The following is the WPS certification process, we can see that the verification of PIN1 and PIN2 is performed separately.

Ref: MACH:high-speed cracking scheme to WPS authentication mechanism of WLAN doi:10.3969/j.isn.1001-3695.2014.08.061
Feasible
To implement this attack, the router must open the WPS authentication or there is no way using PIN code to access the system.
Steps
firstly, we enable our WPS mode and set pin as 64045696

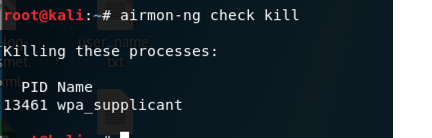
open our kali linux, and kill the collision process.
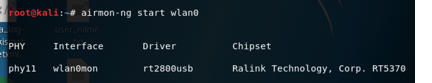
enable our wlan0 as monitor mode
we use tool called wash, it can detect all the WPS router root@kali:~# wash -i wlan0mon -i means interface

we can find your target mac is 68:FF:7B:66:E6:58 then we run the tool reaver brute force the pin -i means interface -b means bssid -vv means show the information

after about one hour, we can see the result
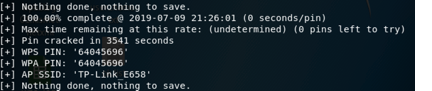
Then we got the pin as we previously set. Anyone can use this PIN code to change the router’s setting.
How to prevent it:
This kind of attack starting from 2011, and now is 2019, we can still see that many wifi-router open the WPS mode. This mode is extremely dangerous for the new routers.An attacker can crack this PIN code in 2 hours maximum. However, nowadays, some routers have implemented some security measures to against the infinite PIN tries, if the attacker didn’t guess the pin in the limited times, the router will block them out for a period of times. My advice is to update your device (software and hardware), there must be some security measure against this old attack. In addition, never open your WPS mode. I would say it’s very dangerous for the information security of the client.
0 notes
Text
How to Hack WiFi Networks for Beginners

How to Hack WiFi Networks for Beginners

Learn how to Hack WiFi Networks (WEP, WPA, WPA2). What you'll learn How to Hack WiFi Networks (WEP, WPA, WPA2). Useful Linux Commands. Create your own wordlist using Crunch. Exploit WPS feature to Crack WPA/WPA2 without a wordlist. Learn multiple WiFi Hacking techniques. Create a Fake WiFi Network. Requirements A basic understanding of computers. A basic understanding of networks. A desire to learn. Description This course is all about WiFi and the security of wireless networks. You will study the different threats, weaknesses and attack methods. No special skills are required as the course covers everything from the very basics including the installation of Kali Linux. The following topics will be covered during the course: How Wireless Networks Work. Important Settings to Change on Your Router. How to Install Kali Linux in VMware Player. Useful Linux Commands with Examples. Perform a Denial of Service Attack and Find Hidden Wireless Networks. How to Hack WiFi Networks (WEP, WPA, WPA2). Use various tools like: Aircrack-ng, Wifite, Crunch, Cowpatty, Pyrit, Reaver… How to Create an Evil Twin Access Point. After completing this course you will be confident with breaking all types of WiFi encryption methods. Who this course is for: Anyone who just simply wants to learn all cool WiFi hacking tricks. Created by Juravlea Nicolae Last updated 1/2019 English English Google Drive https://www.udemy.com/wi-fi-hacking-for-beginners/ Read the full article
#Course#Crack#Crunch#Hack#Hack WiFi#Linux#Network#networks#techniques#WEP#WiFi#wordlist#WPA#WPA2#WPS
0 notes
Text
15 Best WiFi Hacking Apps For Rooted Android Mobiles - 2019

Best WiFi Hacking Apps For Rooted Android Mobiles
Eccentricity over the need of the Wi-Fi for any usual works is quite a usual behavior. Clipping off the need about the need to download or play games is not a craze but a habit which cannot be overlooked. But to get the needed Wi-Fi we need to get a crack into it. For many, they will just cruise around to try every app they see about. But is just like that to buy some random weapons to damage a sheet of unknown material. What you need is a list full of such apps for your rooted mobile to get into these pesky networks. Networks which are not known to you like that sheet with how much security level they may possess. To just sit on the couch at a house or at a sofa at a café and get your Wi-Fi in vicinity cracked is what all these apps make out for you. It is like an army we give you here who compromises the top agents to bring out your mission of "Hack Wi-Fi" a success. Be at workplace or café or at home or at the airport never do worry now until you have any of the below given top 15 "Wi-Fi Hacking Apps For Rooted Mobiles" as these are not made on some just all roundabout reviews only. This list is made up from not less but a high class maintained apps for their reputation to penetrate and bring you access to any Wi-Fi you lay your hand on. But, is it sure that the technique these apps make up from do crack about any Wi-Fi is a question you bear in your mind and soul is quite known to us. The answer is quite simple to it but as these apps are not like others to use only a method to crack into any network you think off. It has a repertoire (collection) of techniques which are not just infamous into ethical hackers but also into the dark world to crack into the best crazed high-security networks. Sit a way back into this theatre we provide with this top 15 apps not just to allure the passwords of any security class but well suited to download for any rooted mobile. Aircrack-ng

Basically, it is not a simple class tool it was developed by hackers only and then left out to be downloaded by others to make out big and strong cracks into the most secured Wi-Fi networks even. It also does analyse any Wi-Fi network at first to ensure that you are not dragged into some problem later on and get caught and beaten up either. They do make it such as the name specifies crack into thin airspace where network exceeds the ranges of it. Kali Linux Nethunter

Well if you are not that known to the world of hacking it would be our pleasure to introduce that Kali Linux is one of the most infamous PC OS which comes with the top grade tools to even crack the best world-class security systems. It is still being used by the top security personnel and hackers around the world. Now, this Kali Linux has been bought up on your mobile which has to be rooted surely not at full level but enough to crack the toughest things and apps and yes to get easy access to any Wi-Fi too. dSploit

Well to exploit the problem also called to vulnerability is the job dSploit famous to do it. It would be fit to be used in both the way that checks if your Wi-Fi needs some more help in what all matter and also to break into any other known Wi-Fi networks you want to get into. Well, you might think if it does analyse and give you vulnerabilities then the other person would check it themselves to make it secure but laziness and not known information as we give you here is still not known to them to download and use to get access today. NMAP

Another notoriously known technology is this NMAP which is quite known to ping such all possible packets into the network to get the password for the Wi-Fi you are looking for. It is based on mapping networks and has known to find any possible exploit into the network and bring you out the expected result which is giving you access to the Wi-Fi network you are looking for. Being ranked into one of the top 15 Wi-Fi apps for rooted mobiles in our website is not astonishing for this name any who have heard it before knows about. Wi-Fi Inspect

Don't get bothered by the name as by it you may get eluded into the thought that it does just find the security problem for you to fix it out. But, well it is not completely wrong too as it is what it does in half of its work but at next half work it uses that loophole into the network and gets and provide you around the access for the Wi-Fi you are looking for. Not to mention that this app is quite a buzzy one to be called into as one of the best Wi-Fi Cracking apps in the world for rooted mobiles. Reaver

It is not some special one in front of Kali Linux or NMAP but packs a whole different level also at the same time. Maximizing the possibility to crack into as such a network without getting caught is especially what it is known for. Cross-cutting the time also it tries out so that you do not miss out on some valuable time trying to do on something for some Wi-Fi network which is quite secure and also not that easy to crack when you want some internet at quickest. Arpspoof

Well, it is somewhat same as dSploit in working the difference lies that it does not just target the Wi-Fi you want to point out at. It is a really good tool to be used to find the easiest to target Wi-Fi and then crack it down. It does rank in the best 15 Wi-Fi cracking apps in rooted mobiles list for us because it is able to give you internet in the least time and also in the need of your time. The spoof of the ID while do it is also it do to make sure you never get caught easily too. Network Spoofer

I am known to you and let me in and when you enter you just get your work done and come out when you are a stranger to place but being treated like a VIP inside because you just show up like one while you just there to fulfil your needs. Same does this app does when it comes to Wi-Fi as it does spoof you up to show like you are entrusted with a password to this network and are safe to connect so that you enter to do your internetwork and just come out undetected. WIBR+

It is somewhat of the testing app more than just cracking is a direct truth we would like to mention it to you. But, many do not know the potential of this app and does think that it might not be able to stand the expectations. But, if you just try it out once you might feel the urge to use it again as it brings you the scan for all possible networks around you which can be hacked and let you get privileged access at the same time. WPS Connect

WPS is a not a new word for you and you would have heard it earlier sure as it is a form of security used by Wi-Fi networks usually. Well, it does surely have a downfall too it means you would have figured out already too as not all networks use this type of security but the maximum of networks does use WPS security only. This form of security is not easy to crack usually but well we are giving you this app right so now you can make into it easily. cSploit

You might be wondering by name that cSploit and dSploit are similar and well you have not taken any wrong guess here. But, it does not mean that both are similar in all ways are just like siblings one being good and others being not so good. Both are special in their own ways and work at well different techniques but are quite known to produce the same result which cracking up the Wi-Fi for you to let you use it at your own will. WIFI Analyzer

Well by name you would have got a quite good idea it analyses Wi-Fi but well there is not the same thing here which might be galloping in your mind. Actually, it does capture all the Wi-Fi networks and which puts you into the wonder that why it is into such work and why does it need to do that. Well, you are into hacking a network which would not just give you internet but you want good speed and less security too right. It takes all these parameters in its hand and then cracks it open for you to use it. Netspoof
Crackdown the network by faking up some irregular request to make it behave as it should open on even wrong passwords is what Netspoof is capable of. It would drive your request like they are known to network even though you have never even connected to that Wi-Fi in your whole lifetime. To act as a trustworthy one and then backstab the network at the end to get full access is the speciality of this whole time great Wi-Fi hacking app. Intercepter-NG

Every network has its way of sending packets as they are if invaded can provide you access to that network. Intercepter-NG is well known to do the same effect here. To break down the signals and put up a script or malfunction code to create a backdoor to connect to that certain Wi-Fi is what it is most capable of. Not just the direct approach works all the time and it does know that well and so does it do this with efficiency. Penetrate Pro

It has quite an eluding app and has been known to accept in both ways that are paid and free. Well, it does not matter much as even in the free one as the name goes by it is able to penetrate quite easily down and bring you the password. It does find the weakness in the network and strike therewith barrages of combinations to break it open until all combinations go down. Paid one does make the speed better but well if you time to give and at a public place usually this would work out good and quite easily and we can say it can be a must-have Wi-Fi cracking app for rooted mobiles. Read the full article
0 notes
Link
How to Hack WiFi Networks for Beginners ##udemycourses ##UdemyFreeCoupons #Beginners #Hack #Networks #WiFi How to Hack WiFi Networks for Beginners This course is all about WiFi and the security of wireless networks. You will study the different threats, weaknesses and attack methods. No special skills are required as the course covers everything from the very basics including the installation of Kali Linux. The following topics will be covered during the course: How Wireless Networks Work. Important Settings to Change on Your Router. How to Install Kali Linux in VMware Player. Useful Linux Commands with Examples. Perform a Denial of Service Attack and Find Hidden Wireless Networks. How to Hack WiFi Networks (WEP, WPA, WPA2). Use various tools like: Aircrack-ng, Wifite, Crunch, Cowpatty, Pyrit, Reaver… How to Create an Evil Twin Access Point. After completing this course you will be confident with breaking all types of WiFi encryption methods. Who this course is for: Anyone who just simply wants to learn all cool WiFi hacking tricks. 👉 Activate Udemy Coupon 👈 Free Tutorials Udemy Review Real Discount Udemy Free Courses Udemy Coupon Udemy Francais Coupon Udemy gratuit Coursera and Edx ELearningFree Course Free Online Training Udemy Udemy Free Coupons Udemy Free Discount Coupons Udemy Online Course Udemy Online Training 100% FREE Udemy Discount Coupons https://www.couponudemy.com/blog/how-to-hack-wifi-networks-for-beginners/
0 notes
Video
(via WPS Pixie Dust Attack in Kali Linux with Reaver)
22 notes
·
View notes
Text
Kali Linux 2017.3 Release - The Best Penetration Testing Distribution
Kali Linux 2017.3 Release - The Best Penetration Testing Distribution #kali #kalilinux #Kalilinux2017.3 #linux #Hacking
Kali Linux 2017.3 released, which includes all patches, fixes, updates, and improvements since our last release. In this release, the kernel has been updated to 4.13.10 and it includes some notable improvements:
CIFS now uses SMB 3.0 by default
EXT4 directories can now contain 2 billion entries instead of the old 10 million limit
TLS support is now built into the kernel itself
In addition to the…
View On WordPress
#Burp Suite#CherryTree#InSpy#Kali Changelog#kali linux#Kali Linux 2017.3#Linux 2017.3#OSRFramework#penetration testing#Penetration Testing Distribution#PixieWPS#reaver#subdomains#Sublist3r#The Social Engineering Toolkit
0 notes
Text
Cracking router WPS pin using reaver part 1
Cracking router WPS pin using reaver part 1
Hi Guys This method will work on some routers but not all routers as most routers have lockouts after a certain number of tries in a certain amount of time. In the next video I will show you how to bypass(hopefully) this.
View On WordPress
#aircrack#backtrack#bully#crack#crack wps#cracking#hack#hack wifi#hack wps#hacker (computer security)#hacking#hacking wps#kali linux#linux#reaver#router#wi-fi protected setup#wifi#wifi wps#wireless#wpa#wpa2#wps#wps locked#wps pin
0 notes
Text
The Top 10 Wifi Hacking Tools in Kali Linux | Dilli Babu Kadati
The Top 10 Wifi Hacking Tools in Kali Linux | Dilli Babu Kadati

How to hack WiFi is second popular search after how to hack a Facebook. Most of the routers are not correctly configured and are susceptible to various kinds of attacks.
A lot of the router manufacturers and ISPs are still turning on WPS by default on their routers which makes the wireless security and penetration testing an even more important. Using the below Top 10 Wifi Hacking Tools you will…
View On WordPress
#aricrack-ng#crunch#fern wifi cracker#hacking tools#kali linux#kali linux wifi hacking tools#macchanger#oclhashcat#pixiewps#reaver#top 10 wifi hacking tools#top10#wash#wifite#wireshark
0 notes
Text
September 06, 2020 at 10:00PM - White Hat Hacker Training Bundle (pay what you want) Ashraf
White Hat Hacker Training Bundle (pay what you want) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
Course Description
This advanced network hacking course is designed to build on your foundational knowledge. It aims to break down each attack into smaller components so you can understand how each of these components works. By the end of the course, you’ll be able to mix attacks and adopt attacks to suit different situations and different scenarios, as well as know how to write your own man in the middle scripts to implement your own man in the middle attacks.
Access 83 lectures & 10 hours of content 24/7
Learn how to extend the pre-connection attacks that you already know
Extend the deauthentication attack to target multiple clients & multiple networks at once
Understand a number of advanced techniques to gain access to various network configurations & encryptions
Discover how to manually configure & create a fake access point
Create fake captive portals, steal WPA/WPA2 passwords & spy on clients
Cover post-connection attacks
Course Description
If you want to get started as an ethical hacker, learn how network security professionals protect their systems, or elevate your IT career, this is the course for you. Here, you’ll learn from experienced network security professionals while covering the most important topics in ethical hacking today.
Access 92 lectures & 16 hours of content 24/7
Get an introduction to ethical hacking
Learn how to install Linux, terminal basics, & Wireshark setup
Understand how to stay anonymous online & access the dark web using TOR
Explore aircark-ng, HashCat, & WiFi hacking
Defend your own networks from attacks
Clone websites
Course Description
This course is all about WiFi and the security of wireless networks. You’ll study different threats, weaknesses, and attack methods for WiFi hacking. After completing this course, you’ll be confident with breaking all types of WiFi encryption methods.
Access 17 lectures & 1 hour of content 24/7
Learn how wireless networks work
Understand important setting to change on your router
Install Kali Linux in VMware player
Explore useful Linux commands w/ examples
Perform a Denial of Service Attack & find hidden wireless networks
Use various tools like Aircrack-ng, WiFite, Crunch, Cowpatty, Pyrit, & Reaver
Course Description
Nmap is the internet’s most popular network scanner with advanced features that even seasoned professionals don’t know about. In this complete course, you’ll uncover secrets of ethical hacking and network discovery using Nmap. You’ll go from beginner to expert in easy to follow, structured steps covering all major platforms including Windows, Mac, Linux, and Kali. At the end of the course, you’ll have a practical skill set in using Nmap to scan networks.
Access 56 lectures & 4.5 hours of content 24/7
Become an expert in using Nmap for ethical hacking, system administration & network security
Learn how to successfully discover active & vulnerable hosts on a network
Master service detection, version detection, operating system detection, & optimizing timing and performance
Scan to determine firewall rules while avoiding intrusion detection systems (IDS)
Understand how Nmap is used in combination w/ criminal hacking infrastructures
Cover both the command line version of Nmap & the GUI version of Nmap called Zenmap
Course Description
Interested in hacking for the good guys? This comprehensive course will take you from zero to hero in the field of ethical hacking, the career path where you get paid to expose system and network security threats. You’ll explore four main sections: network penetration testing, gaining access, post exploitation, and web app penetration testing to get a complete, well-rounded education in how to responsibly and effectively improve security.
Access 125 lectures & 11.5 hours of content 24/7
Learn basic network pentesting
Gather information about networks & computers, & learn how to gain access & attack targets
Understand how to gain full access to computer systems w/o user interaction
Create server side & client side attacks
Discover how to interact w/ the systems you’ve compromised
Learn how to detect, prevent, & secure your system & yourself from every attack you learn
Course Description
The CISSP is an internationally recognized certification that demonstrates an IT professional’s technical and managerial competence to protect organizations from increasingly sophisticated attacks. It’s an ideal certification for anyone who wants to work in IT as it satisfies all government and professional security certification mandates and leaps out on a resume. In this course, you’ll receive in-depth instruction in all things CISSP, so you can be fully prepared when you decide it’s time to take the exam.
Access 68 lectures & 9.5 hours of content 24/7
Discuss penetration testing & information systems access control
Explore common security architecture frameworks
Understand different network types & topologies
Learn about cryptography, physical security, & operations security
Discuss the legal regulations & liability behind systems security
Course Description
This course will introduce you to the various methods, tools, and techniques used by attackers. You’ll study web application flaws and their exploitation. Upon completion, you’ll understand major web application flaws and how to exploit a number of dangerous vulnerabilities like SQL injections, CSRF attacks, XSS vulnerabilities, phishing, and more.
Access 23 lectures & 1 hour of content 24/7
Learn how the web works
Use the Vega Web Vulnerability Scanner
Understand SQL injection attacks
Hack WordPress w/ WPscan
Discuss cross-site scripting & cross-site request forgery
Hook victims using BeEF Framework
Gain full control over the target machine
Discover how phishing works
The post White Hat Hacker Training Bundle (pay what you want) first appeared on SharewareOnSale.
from Active Sales – SharewareOnSale https://ift.tt/3lXrNAj https://ift.tt/eA8V8J via Blogger https://ift.tt/33btMbU #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes