#kali linux wifi hacking tools
Explore tagged Tumblr posts
Text
Hashcat is a Multiplatform hash cracking software that is popular for password cracking. Hashing a common technique to store the password in various software. Protected PDF, ZIP, and other format files that are protected by a password. This password is hashed and saved as part of the file itself. Using Hashcat you can easily identify the password of a protected file. The tool is open source and free to use. It works with CPU, GPU and other hardware that support OpenCL runtime. I have hand-curated these Hashcat online tutorials for learning and experimentation. How Hashcat Software Works? Hashcat software can identify the password by using its input as the hashed value. Since hashing is a one-way process it uses different techniques to guess the password. Hashcat can use a simple word list to guess passwords. It also supports brute-force attack that can try to create all possible character combinations for the potential password. Recent attack features of masking and rule-based attack makes it even more powerful and faster tool to recover the password from a hash. Beginners Hashcat Tutorials : Simple and Focused As a beginner you may want to start simple with these tutorials. You can jump to advanced tutorials if you have already learned basic hashcat commands and usage. frequently_asked_questions [hashcat wiki] - The FAQs listed on official website are the best starting point for any beginner. If you see an error using the tool, you may find a detailed description on that error in this page. Hashcat Tutorial for Beginners Hack Like a Pro: How to Crack Passwords, Part 1 (Principles & Technologies) « Null Byte :: WonderHowTo Hashcat Tutorial - The basics of cracking passwords with hashcat - Laconic Wolf cracking_wpawpa2 [hashcat wiki] KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Crack WPA/WPA2 Wi-Fi Routers with Aircrack-ng and Hashcat How to Perform a Mask Attack Using hashcat | 4ARMEDHow to Perform a Mask Attack Using hashcat | 4ARMED Cloud Security Professional Services How To Perform A Rule-Based Attack Using Hashcat | 4ARMEDHow To Perform A Rule-Based Attack Using Hashcat | 4ARMED Cloud Security Professional Services Using hashcat to recover your passwords | Linux.org Cracking Passwords With Hashcat | Pengs.WIN! GitHub - brannondorsey/wifi-cracking: Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat Hashcat Video Tutorials and Online Courses To Learn This is a Video courses and tutorials list, you may find it helpful if you prefer video tutorials or classroom setup. How To Crack Passwords - Beginners Tutorials - YouTube How To Use Hashcat - YouTube Howto: Hashcat Cracking Password Hashes - YouTube How To Crack Password Hashes Using HashCat In Kali Linux - Flawless Programming - YouTube Password Cracking with Hashcat Tutorials - YouTube Crack Encrypted iOS backups with Hashcat - YouTube How to crack hashes using Hashcat -Tamilbotnet-Kali Linux - YouTube How To Crack Password Hashes Using HashCat In Kali Linux by rj tech - YouTube Ubuntu: How To Crack Password Using Hashcat : Tutorials - YouTube Mac OSX: How To Crack Password Using Hashcat : Tutorials - YouTube Hashcat eBooks, PDF and Cheat Sheets for Reference These are downloadable resources about hashcat. You can download the PDF and eBook versions to learn anywhere. Hashcat User Manual - The official user manual of Hashcat that contains all features in a well documented format. This may be handy once you start feel little comfortable with basic hashcat usage. Owaspbristol 2018 02 19 Practical Password Cracking - OWASP is the place for security experts to get most authentic information. This is a simple eBook about password cracking encourage stronger passwords. Bslv17 Ground1234 Passwords 201 Beyond The Basics Royce Williams 2017 07 26 - A simple presentation that covers hassed password cracking tips and techniques using hashcat.
Hashcat 4.10 Cheat Sheet v 1.2018.1 - Black Hills Information SecurityBlack Hills Information Security Hashcat-Cheatsheet/README.md at master · frizb/Hashcat-Cheatsheet · GitHub KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Information Security & Privacy Hashcat Websites, Blogs and Forums To Get Help Learning Below mentioned websites can be a good source for getting help on Hashcat and related topics. Official Website of hashcat - advanced password recovery - The official Hashcat website with all details about the tool and its supported versions to download. This is the best place to start your hashcat research and learning. hashcat Forum - Best place to get help as a beginner about hashcat. I will recommend do a search before asking a question, since most questions may have been asked in past. Your Hacking Tutorial by ZempiriansHotHot - Subreddit about hacking where you may get some help and direction on using hashcat. HashCat Online - Password Recovery in the cloud WPA MD5 PDF DOC - Hashcat online, can be a good place to experiment with your hashcat skills without installing hashcat on your own computer. Newest 'hashcat' Questions - Stack Overflow - Stackoverflow is my favorite place for many things, however, for hashcat it can be a little dull since I do not notice a lot of participation from the community. You may still have some luck if you ask your question the right way and give some bounty. Summary This is a very big list of tutorials. Hashcat is just a simple software and you may need to use very few options from it. Try to experiment with it and you will start learning. Please share this with friends and add your suggestion and feedback in the comments section.
0 notes
Photo

Reaver Kali Linux Tutorial To Hack WPS Enabled WPA/WAP2 WiFi Network
#download reaver#kali tool#reaver kali linux#REAVER KALI LINUX TUTORIAL#wifi network hack#WPS ENABLED WPA/WAP2
1 note
·
View note
Link
Learn Ethical Hacking From A-Z: Beginner To Expert Course
Learn how to become an elite ethical hacker and easily hack networks, computer systems, web apps and so much more…
What you’ll learn
Learn Ethical Hacking From A-Z: Beginner To Expert Course
How To Become An Elite Ethical Hacker
How To Setup A Hacking Lab
Learn How To Launch Attacks/Exploits Against Computers
How To Start A Cybersecurity/Ethical Hacking Career
How To Hack Into Wireless Networks
Learn How To Conduct Penetration Tests
How To Bypass Antivirus
The Fundamentals of Networking
How To Remain Anonymous On The Internet
The Fundamentals of Linux
The Fundamentals of Bash
How To Gather Website & App Data
The Fundamentals of Python
Maintaining Access To Exploited Computers
Website & Web Application Hacking
Mobile Phone Security Tips
Where You Can Practice Hacking For Free
Conducting Passive & Active Reconnaissance On A Network
Requirements
Basic IT/Computer Skills & Knowledge
Computer With At Least 8GB of RAM/Memory (Less is ok, but your computer may run slow!)
Wifi Hacking Section Only: USB Wireless Adapter (Link Provided In Course Resources)
You Do Not Need Any Prior Experience In Hacking Or Cybersecurity To Go Through This Course
Description
Welcome to – Learn Ethical Hacking From A-Z: Beginner To Expert Course! This practical, hands-on course was created for newbies – that’s to say, people with no prior training or knowledge in hacking and cybersecurity. The aim of this course is to give you the education not just to understand what black-hat hatters do and how, but also to learn exactly how to hack systems like a pro and win the cat and mouse game by securing systems like a professional security expert. Blending practical work with solid theoretical training, we take you from the basics of ethical hacking through to mastery, giving you the training you need not just to hack, but also to secure against a hack. While the theory is important, we understand that it can also be dry and uninspiring. For this reason, this course is packed with examples that you can follow. This practical focus starts from the beginning, where we will teach you about penetration testing and show you how to install the software required (Windows, Linux, and Mac OSX) and jump right into hacking. Throughout, you will analyze and exploit various systems from regular websites through to sprawling networks, along with hacking servers and clients. More than just hacking, you’ll also learn how to conduct efficient penetration testing techniques. This approach gives you the foundational education that you need not just to hack any given system, but also to secure it, with each module covering both sides of the coin. The course covers six main areas:
1: LEARN THE FUNDAMENTALS NECESSARY TO BECOME A HACKER
This foundational section gives you a full introduction to the basics of networking systems – how they communicate and work – and is designed to give you the knowledge you need to succeed in this course. BASICS OF NETWORKING: Networking can be an intimidating topic, but don’t worry! We break down only the necessary things that you need to know in regards to networking and teach you important networking fundamentals SETTING UP A HACKING LAB: You can’t hack without a lab! We walk you step-by-step through the process of setting up your own hacking lab on your laptop or desktop computer! LINUX + SCRIPTING BASICS: Hackers use Linux, which is an OS that the average person may have no experience with. We will go over Linux fundamentals so that you can easily navigate your way through Linux during this course. We also touch on a couple of scripting languages that are a MUST for any ethical hacker and teach you the basics of each one with practical examples. HIDING YOUR IDENTITY ON THE WEB: If you are hacking on the internet, you need to learn how to remain anonymous. We will show you the tools and techniques that you can use to always remain anonymous and unknown on the internet.
2: LEARN HOW TO HACK NETWORKS
This section shows you how to test both wired and wireless systems. You will learn how to go from not having any access to a network to gaining access and being able to begin attacking systems on the network. PRE-CONNECTION ATTACK: Not all attacks require you to be connected to the target or even know the password. Learn how to discover and manipulate devices connected to a network and gather information about your target. GAIN ACCESS TO NETWORKS: Learn how to use the information you have about your target to crack the key and get the access password. This section covers multiple protocols including WEP, WPA, and WPA2. POST-CONNECTION ATTACKS: With a key, you can now leverage powerful hacking techniques to get even more information. Learn how to see what users are doing on a network, inject code in pages, and more on wired and wireless networks
3: HOW TO GAIN ACCESS AND CONNECT TO NETWORKS
This section builds on the lessons learned in section one, showing you how you can get full control and hack into any computer system that you target. SERVER-SIDE ATTACK: Discover how to harvest information about your targeted system – its OS, open ports, and installed services – without user interaction. Then use this information to exploit vulnerabilities and generate reports. CLIENT-SIDE ATTACK: Learn how to hack systems with no vulnerabilities by sneaking in with software updates or using backdoor trojan downloads. You’ll also learn the art of social engineering – or tricking people into giving you information.
4: HOW TO LEVERAGE POST EXPLOITATION
This section shifts the focus on interacting with compromised systems. Now that you have gained access, you’ll learn how you can exploit these systems. ACCESS FILE SYSTEMS: All systems have a wealth of files that you can now manipulate with your access. Learn how to access these systems and how to read, write, upload, and even execute files. MAINTAIN ACCESS: Gaining access to a system and its files is only half of the battle. Learn how to maintain your access and frustrate efforts to secure it again so you can continue to exploit a system. SPY ON YOUR TARGET: Learn how to capture any keystrokes on a keyboard, turn on a computer webcam, take screenshots, and even take control of the system to attack, hack, and access third-party networks and systems.
5: HOW TO HACK WEBSITES AND WEB APPS
In this section, you will learn more about how you can hack into websites and web applications using Kali Linux. You’ll also learn how web applications work – and how to find vulnerabilities within these applications for you to exploit. > How to scan websites/web applications for vulnerabilities to exploit. > How to Brute Force into web applications. > Learn how to conduct SQL injection in web applications. > How to conduct Cross-Site Request Forgery (CSRF). > How to exploit File Inclusion Vulnerabilities. > Learn how to exploit File Upload Vulnerabilities. > How to automate attacking web applications using various tools. > How to prevent and secure websites & apps yourself.
6: HOW TO MAKE MONEY, LAND A JOB & BUILD A BRAND AS A HACKER
In this section, you will learn how you can make money as an ethical hacker using a variety of methods. You’ll also learn how to build your personal brand and get your name out there as an Ethical Hacker so you can have employers and clients knocking at your door ready to hire you for your services. Then finally, you’ll learn how you can start a career in cybersecurity with some insider tips on what certifications to get and the best way to land a job. This includes: > How to build an ethical hacker personal brand from scratch > How to get instant credibility and authority as a hacker > Learn how to properly network and get others talking about you > How to make money using a variety of websites > How to get started freelancing as a hacker > Learn how to get started consulting as a hacker > How to land a job as a cybersecurity professional This course is comprehensive, showing you both sides of hacking. You will learn to think and operate like a hacker – and how to apply that knowledge as a cybersecurity expert to protect you and your clients’ networks and systems. In taking this ‘cat and mouse approach, your rounded understanding will give your approach new depths and angles, revealing the paths you can take to effectively neutralize any threat. Together with the emphasis on practical examples that you can follow in real life with live systems, you will also benefit from the excitement of hands-on learning. By experiencing precisely what it takes to hack into any given target system, you’ll also learn that no one system is the same and that all approaches can be modified. This real-life learning is an invaluable part of your education, enabling you to better see what hackers are doing and how to block even the most potent attacks. No matter what the scenario or how complicated a hacking situation, this course gives you the foundational training you need to secure a network – and start pursuing a career in a field that is increasingly in demand as the global reliance on technology grows.
Download
To download more paid course for free visit free course site where you find 1100+ paid courses for free. You can easily access those courses with just a single click.
23 notes
·
View notes
Text
How to Hack WiFi Networks for Beginners

Requirements - A basic understanding of computers. - A basic understanding of networks. - A desire to learn. Description This course is all about WiFi and the security of wireless networks. You will study the different threats, weaknesses and attack methods. No special skills are required as the course covers everything from the very basics including the installation of Kali Linux. The following topics will be covered during the course: - How Wireless Networks Work. - Important Settings to Change on Your Router. - How to Install Kali Linux in VMware Player. - Useful Linux Commands with Examples. - Perform a Denial of Service Attack and Find Hidden Wireless Networks. - How to Hack WiFi Networks (WEP, WPA, WPA2). - Use various tools like: Aircrack-ng, Wifite, Crunch, Cowpatty, Pyrit, Reaver… - How to Create an Evil Twin Access Point. After completing this course you will be confident with breaking all types of WiFi encryption methods. Who this course is for: - Anyone who just simply wants to learn all cool WiFi hacking tricks. Read the full article
1 note
·
View note
Text
The Top 10 Wifi Hacking Tools in Kali Linux | Dilli Babu Kadati
The Top 10 Wifi Hacking Tools in Kali Linux | Dilli Babu Kadati

How to hack WiFi is second popular search after how to hack a Facebook. Most of the routers are not correctly configured and are susceptible to various kinds of attacks.
A lot of the router manufacturers and ISPs are still turning on WPS by default on their routers which makes the wireless security and penetration testing an even more important. Using the below Top 10 Wifi Hacking Tools you will…
View On WordPress
#aricrack-ng#crunch#fern wifi cracker#hacking tools#kali linux#kali linux wifi hacking tools#macchanger#oclhashcat#pixiewps#reaver#top 10 wifi hacking tools#top10#wash#wifite#wireshark
0 notes
Text
Cyber Security and Hacking News Website - Latest Cyber Hacking News
Read today's research news on hacking and protecting against cybersecurity.
GB Hackers is the latest news articles providers for cybersecurity and hacking news source for everyone, supported by hackers and IT professionals worldwide.
Keep yourself updated with the hacker news and know more about security.
Search Online Hacking News & Get Results from 6 Engines at Once. Trusted by Millions.
Read More About Hacking News: https://gbhackers.com/

More Links :
Pirate Bay - https://gbhackers.com/the-pirate-bay-torrent-alternative-2018/
Kickass Proxy - https://gbhackers.com/kickass-torrents-alternative-sites-2018/
Hacking Simulator - https://gbhackers.com/kickass-torrents-alternative-sites-2018/
Wifi Hacker Apps, Wifi Hacker App - https://gbhackers.com/top-best-wifi-hacking-apps-android/
Vulnerability Scanner - https://gbhackers.com/best-vulnerability-scanner/
Dark Web Browser - https://gbhackers.com/top-5-best-dark-web-browser/
App Locks - https://gbhackers.com/top-5-best-dark-web-browser/
Hacking Tools - https://gbhackers.com/hacking-tools-list/
Google Dorks - https://gbhackers.com/latest-google-dorks-list/
Sql Dorks - https://gbhackers.com/latest-google-sql-dorks/
Wifi Cracker - https://gbhackers.com/cracking-wifi-password-with-fern-wifi-cracker-to-access-free-internet-everyday/
Super Smash Flash 2 Unblocked - https://gbhackers.com/super-smash-flash-2-unblocked/
Port Scanner - https://gbhackers.com/open-port-scanner-port-checker-tools/
Wifi Hacker App - https://gbhackers.com/top-best-wifi-hacking-apps-android/
Ddos Website - https://gbhackers.com/anonymous-ddos-a-website-using-kali-linux/
Kali Linux Tutorial - https://gbhackers.com/kalitutorials/
Is This Website Safe - https://gbhackers.com/how-to-check-if-a-website-is-malicious/
Email Header Analysis - https://gbhackers.com/email-header-analysis/
Android Rat - https://gbhackers.com/android-rat-kali-linux-tutorial/
Free Password Manager - https://gbhackers.com/best-free-password-manager/
Xss Cheat Sheet - https://gbhackers.com/top-500-important-xss-cheat-sheet/
Password Hacker Tool - https://gbhackers.com/pasword-hacking/
Adware Removal Tool - https://gbhackers.com/best-adware-removal-tool/
Ad Blocker - https://gbhackers.com/ad-blocker-for-android/
App Building Software - https://gbhackers.com/best-app-building-software/
Hacking Software - https://gbhackers.com/best-hacking-software/
Ios Emulator - https://gbhackers.com/ios-emulator/
Ad Blocker For Android - https://gbhackers.com/ad-blocker-for-android/
Threat Intellegence Tools - https://gbhackers.com/cyber-threat-intelligence-tools/
Incident Response Tools - https://gbhackers.com/cyber-incident-response-tools/
Android Penetration Testing Tools - https://gbhackers.com/android-security-penetration-testing/
Hacker Search Engines - https://gbhackers.com/10-best-hacker-friendly-search-engines-of-2019/
Gbwhatsapp - https://gbhackers.com/latest-gbwhatsapp-download-android/
Remote Desktop Protocol - https://gbhackers.com/best-remote-desktop-software/
Ssl Checker - https://gbhackers.com/ssl-checker-installation-vulnerabilities/
Hacking Software - https://gbhackers.com/best-hacking-software/
Ai In Cyber Security - https://gbhackers.com/artificial-intelligence-in-cyber-security/
Imsi Catcher - https://gbhackers.com/imsi-catcher/
Omgwhatsapp - https://gbhackers.com/omg-fake-whatsapp/
Network Security Key - https://gbhackers.com/network-security-key/
Kali Linux Tutorial - https://gbhackers.com/kalitutorials/
Active Directory Pentesting - https://gbhackers.com/active-directory-penetration-testing-checklist/
Soc Training - https://gbhackers.com/soc-training-from-scratch/
Ethical Hacking Course Online - https://gbhackers.com/ethical-hacking-course-online/
3ds Emulator - https://gbhackers.com/working-nintendo-3ds-emulator-2019/
1 note
·
View note
Text
تحميل أحدث إصدارات نظام كالى لينكس | Kali Linux 2023
تحميل أحدث إصدارات نظام كالى لينكس | Kali Linux 2023 ان توزيعة كالي لينكس Kali Linux هي متخصصة في الأمن والحماية المعلوماتية و التي تحتوي مسبقا على عدة برامج وأدوات موجهة لاختبار الاختراق وفى هذا الموضوع أقدم لكم أحدث إصدارات نظام كالى لينكس. تحميل أحدث إصدارات نظام كالى لينكس | Kali Linux 2020.1 تحميل أحدث إصدارات نظام كالى لينكس Kali Linux 2023 نظرة كاملة علي التوزيعة: تتضمن توزيعة Kali Linux برامج تقوم بالمسح الأمني للمنافذ كإن ماب Nmap وبرامج لتحليل الحزم المتبادلة على الشبكات كواير شارك Wireshark و برامج لكسر كلمات المرور كبرنامج جون ذا ريبر Jhon the Ripper وطقم برامج Aircrack-ng الخاص باختبار اختراق الشبكات المحلية اللاسكية Wireless LANs و Burp Suite و OWASP و ZAP لفحص سلامة تطبيقات الويب بالاضافة إلى أدوات أخرى لاختبارت أمنية متعددة· Kali contains a huge array of hacker tools and utilities (password attacks, sniffing and spoofing, reverse engineering, …). Hacking foreign WiFi/WLAN (wireless attacks) and more. Kali is meant for digital forensics and penetration testing. Kali is preinstalled with numerous penetration-testing programs, including nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), and Aircrack-ng (a software suite for penetration-testing wireless LANs). Kali are often run from a tough disk, live DVD, or live USB. The most advanced penetrating testing distribution, ever. Kali, the foremost advanced and versatile penetration testing distribution ever created. Kali has grown far beyond its humble roots as a live DVD and has now become a full-fledged OS . Note: Kali is Linux based, but suitable for all Windows versions. شاهد ايضا : ويندوز 10 برو 20H1 بـ 3 لغات x64 | 2020 ويندوز 10 روك 2020 | Windows 10 LTSC ACDC Rock ويندوز 10 برو 20H1 x86 | 2020 تجميعة ويندوز 10 إصدار 19H2 للنواتين 32 و 64 بت | 2020 ويندوز 10 برو 20H1 | 2020 مساحة النسخة 2.5 جيجا تقريباً حمل العديد من النسخ من قسم ويندوز روابط التحميل تحميل التوزيعة للنواة 32 بت هناااااااااااا هناااااااااااا هنااااااااااا تحميل التوزيعة للنواة 64 بت هناااااااااااا هناااااااااااا هناااااااااااا تابعنا دائماً لتحميل أحدث الاسطوانات والبرامج والويندوزات بروابط حصرية كلمات دلالية : كالى لينكس 2020 , اسطوانةكالى لينكس , تحميل اسطوانة كالى لينكس , تنزيل نظام كالى لينكس, حمل برابط تورنت كالى لينكس , حمل برابط مباشر كالى لينكس , حمل على أكثر من سيرفر كالى لينكس , Kali Linux 2020.1 , تحميل Kali Linux 2020.1, اسطوانة Kali Linux 2020.1 , تنزيل برابط تورنت Kali Linux 2020.1 , حمل برابط مباشر Kali Linux 2020.1 , حمل من أكثر من سيرفر Kali Linux 2020.1 via Blogger https://ift.tt/Kyg3Eal March 18, 2023 at 09:30AM
0 notes
Text
Learn how to hack wifi password step by step on android
Wired Equivalent Privacy (WEP)Wi-Fi Protected Access (WPA)Wi-Fi Protected Setup (WPS)AndroDumper App APK Wi-Fi WPS Connect app
This post will be useful to you if you want to expand your knowledge and learn the tips and techniques for how to hack wifi password step by step using an Android device. Many people are curious about how and if it is possible to hack Wi-Fi passwords on Android. Yes, you can use some basic methods and tools to break Wi-Fi passwords on any Android phone.
We first explain a few of the basic details concerning the type of Wi-Fi password security and several other things regarding it before moving on to our key topic, which is how to hack wifi password step by step in Android phones.
Types of Wi-Fi Password Security
Wi-Fi password security comes in three main kinds. These WiFi security measures include:
Wired Equivalent Privacy (WEP).
Wi-Fi Protected Access (WPA).
Wi-Fi Protected Setup (WPS).
One of the most popular and commonly utilized Wi-Fi security systems in the world is called Wired Equivalent Privacy (WEP). However, this protection is also highly weak and unstable. Such Wi-Fi security could be simply breached and exploited with the help of Airmon programs from Kali Linux & Aircrack.
The upgraded and improved version of the WEP Wi-Fi security standard is Wi-Fi Protected Access (WPA). The Wi-Fi protection system was first introduced in 2003. However, a significant flaw in WPA password protection was found by a big American hacker. Because of this, it was simple to damage the Wi-Fi security. Any WPA-secured Wi-Fi password can be cracked using an Android smartphone if you know how to hack wifi password step by step.
On the other hand, the Wi-Fi Secure Setup (WPS) is the only Wi-Fi safety feature that is challenging to hack into and bypass. However, it is also discovered that this Wi-Fi security can possibly be hacked, but doing so needs advanced hacking abilities. If someone is employing WPS security, it might be difficult to compromise this security.
Step-by-step instructions for hacking a wifi password
Popular program AndroDumper is used to crack Wi-Fi passwords on Android smartphones. To use this app to learn how to hack wifi password step by step on Android, follow the steps listed below.
Install the AndroDumper application on your Android phone after downloading it.
Your Android device's Wi-Fi settings should be turned on.
To find and obtain neighboring Wi-Fi networks, open the AndroDumper app and select the refresh button at the top of the screen.
Select the network you want to hack, then tap it to connect.
The program will now try every potential combination of alphabetic and numeric passwords to connect to your selected network. This program might be able to hack a network if the chosen one has a weak Wi-Fi password.
You can learn how to hack wifi password step by step using this app. The app functions on phones running Lollipop and higher that are both rooted and non-rooted. However, because of the various databases, it is mostly suited for rooted devices.
You can connect to WPS-secured Wi-Fi connections without entering a password if you find any on your Android device. The WPS Connect app makes it possible to connect to Wi-Fi without entering a password and to bypass WPS Wi-Fi security.
The methods to use this app to connect your Android phone to a Wi-Fi network are as follows:
The Wi-Fi WPS Connect app for Android phones can be downloaded and installed.
Enable your phone's Wi-Fi settings.
To scan all surrounding Wi-Fi networks, open the WPS Connect app and tap the scan button.
The details of all nearby Wi-Fi networks are displayed after a brief period of time (such as password security types, network types, signal strength, etc.).
Tap on the Wi-Fi network you want to hack and then choose it. The screen displays a list of defined keys (PIN).
Start your hacking operation by tapping the key.
The program makes repeated attempts to hack WiFi using both the default and most popular Wi-Fi keys.
Wait a few while, and the Wi-Fi password will be successfully cracked.
0 notes
Text
[Media] Raspberry Pi 4 Model B - Miniature Hacking Station!
Raspberry Pi 4 Model B - Miniature Hacking Station! Raspberry Pi 4 Model B was released with specs including either 1 GB, 2 GB, 4 GB, or 8 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card. For hackers interested in a cheap Kali Linux computer capable of hacking Wi-Fi without a separate wireless network adapter, the Pi 4 Model B is a great way to run Kali without needing a virtual machine. Thanks to the number of Wi-Fi hacking tools included in Kali Linux, the new Pi 4 Model B represents a complete Ethernet and Wi-Fi hacking kit for beginners. The reasons for using a Raspberry Pi as a hacking computer are many. Previous Raspberry Pi versions have proved that it doesn't take expensive hardware to run tools in Kali Linux. Virtual machines can behave unpredictably, especially when working with Wi-Fi hacking. Plus, it's sometimes more straightforward to run Kali on hardware rather than in a virtual machine. Another advantage to the Raspberry Pi is that it can easily be used in combination with a device like an unmodified iPhone or Android smartphone. If your smartphone supports creating a Wi-Fi hotspot, it's simple to connect the Pi to your hotspot and control it over SSH. If your smartphone can't create a hotspot, the Pi can also host its own Wi-Fi network, allowing you to join the network created by the Pi on your phone and SSH into it on the go. One of the most exciting things about using a Raspberry Pi for hacking is the add-on of the Nexmon firmware. The addition makes it possible to put the built-in Wi-Fi network adapter into monitor mode. That means it's possible to do things like grab WPA handshakes, listen in on Wi-Fi traffic, and execute attacks like WPS-Pixie without needing a separate compatible Wi-Fi network adapter. For someone interested in getting started with Wi-Fi hacking, the Raspberry Pi 4 Model B provides a Kali-supported Wi-Fi network adapter and an onboard computer capable of basic cracking and MiTM attacks in a single package. The increase in speed and power of the Pi 4 Model B make it a more capable networking device as well as a more capable computer. Hack WiFi with a Raspberry Pi and Kali Linux: https://www.youtube.com/watch?v=PqRVo2niA_8 Buy online: 🛒 https://amzn.to/3XXH9Yw 🛒 https://ali.ski/QMVRo #raspberrypi #kali #bord

1 note
·
View note
Text
Wpa2 wordlist take too long

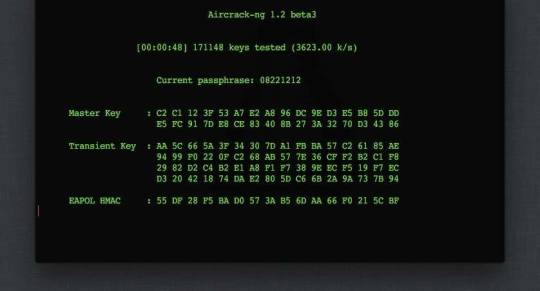
Nonetheless, paraphrases are good choices when they do not appear on the list of leaked passwords The words that make up a paraphrase must be meaningless together to make it susceptible to social engineering. The passphrase is a phrase or a sentence, without or without spaces, usually more than 20 characters long.
If you have trouble in remembering long passwords then you can make a passphrase.
The length of the password matters a lot, it is an effective defence against brute-force attacks.
You can prevent from a dictionary attack by adopting the following measures SEE ALSO: 8 Best Kali Linux Terminal Commands used by Hackers in 2021. As a result, they had a theft of 60 million user credentials. DropBox suffered a similar case like this in 2012 as one of their employees used the same password for LinkedIn as they used for their corporate DropBox account. Such attacks can be harmful to your business.

He was using the same password for Twitter and LinkedIn and other social media accounts The hackers revealed that the CEO��s password had been compromised in the LinkedIn data breach. If we take an example then all of us are familiar with the Facebook CEO Mark Zuckerberg, his social media account on Twitter was hacked. This surely is a definite way to remember passwords but it leaves you vulnerable towards a data breach Why are Dictionary Attacks Dangerous?Īccording to an estimate, about 80% of the people reuse their passwords on online platforms like personal banking, social media and even work system. SEE ALSO: 10 Best WiFi Hacking Tools in Kali Linux for Wireless Hacking. A dictionary that is used in such attacks can be a collection of previously collected key phrases or leaked passwords. Leetspeak is the character replacement with alphanumeric and non-alphanumeric characters. In the dictionary while using words or any derivatives of those words referred to as leetspeak is very common. Such an attack method is also used as a means to find the key that is required to decrypt encrypted files It is used to break into a computer system or server that is protected by the password by systematically entering every word in the dictionary as a password. The password dictionary attack is a brute-force hacking method. SEE ALSO: Top 8 Best Linux Distros for Hacking and Penetration Testing in 2021.
Merge multiple text files into one and save space making it look organized.
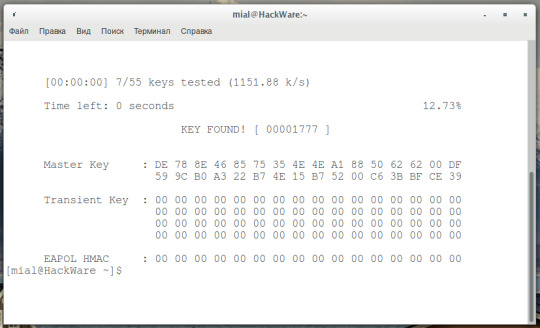
If however, you have multiple passwords then you can combine them into a large fileĪwk ‘’ old.txt | sort -n | cut -d ” ” -f2- > new.txtĮgrep -v “^]*$” old.txt > new.txt If you want to remove all blank lines from a file or need to remove duplicate passwords then a one-liner is all you need Following are the useful commands that are used for manipulating wordlists You can clean up wordlists by using bash one-liner. How to Cleanup Wordlists using bash oneliner It has the most recently used password and pin combinations that users have used on various websites and have unfortunately been leaked. It should be fairly quick to be downloaded. The size of the Rockyou.txt password list is around in the region of 133 MB. You should also try one of the biggest word lists out there called “Rockyou”. SEE ALSO: Kali Linux Hacking Tutorial for Beginners: Learn to Hack Professionally.
Finally, merge all text files into one using the below command:.
Then decompress (if applicable) gunzip *.gz.
Then choose a wordlist you want to use cd wpa2-wordlists/Wordlists/Crackdown2016.
In the first step, you need to download using git clone.
Download WPA/WPA2 Wordlists/Password list for Kali Linux (Latest) WPA/WPA2 Password Lists Download /Image Credits:. SEE ALSO: How to install Arch Linux in 2021 (Step-by-Step Guide). You can go for brute force attack in such cases but it would take a lot of time depending on your computer system.ĭownload Wordlists and Password list for Kali Linux Moreover, keep in mind that this only works if the password is included in the wordlist. Keep in mind that using password cracking tools takes time especially if being done on a system without a powerful GPU. We have found the majority of them from websites that have shared leaked passwordsĪ wordlist is used to perform dictionary attacks like can be used to crack the wi-fi WPA2 using Aircrack-ngĪircrack-ng handshake.cap -w /path/to/wordlist.txtīy using this we have cracked 3/10 networks near us. We get them using advanced Google search operators.
7 Which Wordlist and Password list are you using in Kali Linux?ĭownload Passwords List/Wordlist for Kali Linux (2021 Edition).
5 Why are Dictionary Attacks Dangerous?.
3 How to Cleanup Wordlists using bash oneliner.
2 Download WPA/WPA2 Wordlists/Password list for Kali Linux (Latest).
1 Download Passwords List/Wordlist for Kali Linux (2021 Edition).

0 notes
Text
Real wifi password hacker app

It is intended to provide a researcher with a superior interface for introducing a stimulus into and measuring a response from a TCP/IP enabled device or network. Well, Unicornscan is an attempt at a User-land Distributed TCP/IP stack for information gathering and correlation. It is one of the most popular password testings and breaking programs as it combines several password crackers into one package, autodetects password hash types, and includes a customizable cracker. It’s a free and Open Source software, distributed primarily in source code form.
A good wireless tool as long as your card supports rfmon. Kismet will work with any kismet wireless card which supports raw monitoring (mon) mode and can sniff 802.11b, 802.11a, and 802.11g traffic. It’s an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Many of the world’s largest organizations realize significant cost savings by using Nessus to audit business-critical enterprise devices and applications. Nessus is the Remote Security Scanner’s most popular vulnerability scanner used in over 75,000 organizations worldwide. It recently went closed source, but it is still essentially free. Robot, TrustedSec’s Social-Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks like credential harvestings, phishing attacks, and more. Social-Engineer ToolkitĪpart from Linux, Social-Engineer Toolkit is partially supported on Mac OS X and Windows. Maltego excels in showing the complexity and severity of points of failure in your infrastructure and the surrounding environment. Maltego is an open-source forensics platform that offers rigorous mining and information gathering to paint a picture of cyber threats around you. This tool is available for Windows, Mac, and Linux. Nessus serves different purposes to different users – Nessus Home, Nessus Professional, Nessus Manager, and Nessus Cloud. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. This top free hacking tool of 2020 works with the help of a client-server framework. It is supported by various platforms, including Windows 7 and 8, Mac OS X, and popular Linux distros like Debian, Ubuntu, Kali Linux, etc. For using the tool, NVIDIA users require ForceWare 346.59 or later, and AMD users require Catalyst 15.7 or later. OclHashcat calls itself the world’s password cracking tool with the world’s first and only GPGPU based engine. You can also take the tool as a WiFi password decryptor. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses your GPU’s power. If password cracking is something you do daily, you might be aware of the free password cracking tool Hashcat. This useful hacking tool can be downloaded in different versions for Linux, OSX, and Windows. The project’s goal is to create a commercial-quality analyzer for Unix and give Wireshark features that are missing from closed-source sniffers. Wireshark is a GTK+-based Wireshark network protocol analyzer or sniffer that lets you capture and interactively browse the contents of network frames. This GTK+-based network protocol analyzer runs with ease on Linux, Windows, and OS X.

Wireshark also comes in a command-line version called TShark. This free and open-source tool was originally named Ethereal. This fast and easy to use tool scans WordPress websites from more than 1200 vulnerabilities in WordPress. This multi-threaded tool crawls a website and finds out malicious Cross-site Scripting, SQL injection, and other vulnerabilities. Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal. It is available for Windows XP and higher. It may be used to discover computers and services on a computer network, thus creating a “map” of the network. It was designed to scan large networks, and it works fine against single hosts. I think everyone has heard of this one Nmap (Network Mapper) is a free open source utility for network exploration or security auditing. Well, Nmap is available for all major platforms, including Windows, Linux, and OS X. Metasploit is backed by more than 200,000 users and contributors that help you get insights and uncover your system’s weaknesses. This free tool is one of the most prevalent cybersecurity tools that allow you to locate vulnerabilities at different platforms. Rather than calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can utilize to build your custom tools.

0 notes
Text
How to Hack Wi-Fi password in Android

When you would like to improve the knowledge of yours and would like to understand the techniques and methods to hack the Wi Fi password utilizing Android device, then this particular content will assist you. Many folks are asking about how you can hack Wi Fi passwords using Android and whether it's doable or perhaps not. The simple answer is "yes" you are able to hack Wi-Fi passwords in devices that are Android using several tools and techniques (apps).
Before diving into the primary subject of ours about precisely how to hack Wi Fi passwords in Android cell phones, we initially discuss several of the basic info about the kind of Wi Fi password security.
Types of Wi Fi Password Security There are largely 3 different types of Wi Fi password securities. These Wi Fi securities are as follows:
Wired Equivalent Privacy (WEP). Wi-Fi Protected Access (WPA). Wi-Fi Protected Setup (WPS). Wired Equivalent Privacy (WEP) Wired Equivalent Privacy (WEP) Wi Fi security is just about the most well known and commonly used Wi Fi securities in the whole planet. Nevertheless, this particular security is a most insecure and week too. Someone could crack and hack such Wi Fi security using Airmon resources from Kali Linux as well as pirater wifi.
Wi Fi Protected Access (WPA) The Wi Fi Protected Access (WPA) Wi Fi security is definitely the better as well as updated version of WEP Wi Fi protection system. This Wi Fi security system was created in the season 2003. Though an American hacker found a major flaw in WPA security secrets. Due to which it started to be easy to hack this Wi Fi security. It's likely to crack any Wi Fi password containing WPA protection from an Android smartphone.
Wi Fi Protected Setup (WPS) Finally, the Wi Fi Protected Setup (WPS) is just the Wi-Fi protection device which is not simple to hack as well as crack. Nevertheless, in several instances, it's also realized that this Wi Fi security in addition gets hacked but calls for high hacking skills. If someone uses WPS safety measures, then it may be tough to hack this particular security.
Method one: Hacking Wi Fi Password in Android applying WIFI WPS WPA TESTER (without Rooting) Wi Fi WPS WPA TESTER is a favorite Android app that is popular for hacking Wi Fi passwords. Wi-Fi WPS TESTER app hacks the routers which link with WPS router with restricted functions. Hacking Wi-Fi working with this app is very easy and just requires follows very few steps. The greatest part of this application is the fact that you are able to use it without rooting the Android phone of yours. You are able to also use the app on a rooted Android cell phone with a few additional features.
Using this particular Android app, you are able to quickly examine the wireless security and power of your respective router. If the wireless router isn't safe, subsequently the WIFI WPS WPA TESTER app quickly bypasses Wi Fi password on the Android phone of yours. After bypassing the password, it links the Android phone with the router without offering a password.
The Wi Fi WPS WPA TESTER hacking apps work on each rooted and non rooted Android cell phones. Below are the measures to hack Wi Fi password on Android without rooting.
Download and set up the WIFI WPS WPA TESTER app from Play Store. Enable the Wi Fi settings on the Android phone of yours. Release the app and hunt for the Wi Fi networks nearby you. Select 1 of the networks from the end result and begin hacking by tap. You are able to enter its key manually. The app checks the Wi Fi security, and it attempts various mixtures of numbers and words to crack the Wi Fi password. The app locates the community code very quickly and links your phone immediately. Method two: Hacking Wi Fi password in Android using AndroDumper App APK (without Rooting) AndroDumper is one other favorite app utilized for hacking Wi Fi passwords in Android cell phones. This particular app is operated over a non rooted device to hack Wi Fi passwords. Follow the below mention measures to hack Wi Fi passwords on Android making use of this app.
Download and set up the AndroDumper app on the Android phone of yours. Turn on the Wi Fi settings on the Android device of yours. Launch the AndroDumper app and click the refresh button contained at the top of the display to browse for nearby Wi Fi networks. Choose the system you want to hack and also link and also tap on it. Today the app is going to try to link with your selected network with every combination of alphabets plus number passwords. If the selected community has a vulnerable Wi Fi password, then this app potentially hacks it. Method three: Hacking Wi Fi password in Android getting WPA2 WPS Router (Root device) In this particular method of hacking Wi Fi passwords in Android, we are going to use the Reaver and Bcmon Android app. In the beginning, you want a root Android phone in case you do not have attempted to root the device of yours. Make sure that the root Android phone of yours has Broadcom bcm4329 or maybe bcm4330 chipsets as contained in Samsung Galaxy S1/S2, HTC Desire HD, Nexus 1, Nexus 7, etc.
Download and set up the BCmon app APK file on the Android phone of yours. This app allows you to watch your Broadcom chipset and also cracking PIN. Today, download and install the Reaver Android app which discover and cracking the WPS Wi Fi network password. After the app fitting, launch the BCmon app and also faucet on the "monitor mode" feature. Again release the Reaver app and also verify on the display that you're not utilizing it for any unlawful activity. Tap on the APN or maybe access point you would like to crack and continue Wi Fi password. At times you have to confirm your monitor mode to keep on, and also you are able to accomplish this by reopening the BCmon app once again. Go to options in the Reaver app and then checked to draw "Automatic Advanced setting" package. Lastly, begin your Wi Fi cracking procedure by clicking on the beginning attack; in this final phase, cracking the WPS Wi Fi security usually takes 2 10 hours to be successful.
youtube
1 note
·
View note
Text
Wifite

A complete re-write of wifite, a Python script for auditing wireless networks. Cleaner process management. Does not leave processes running in the background (the old wifite was bad about this).
After choosing the Access Point in wifite in this case ‘EternalWIFI’, it will attempt to deauth the clients connected (disconnect the Clients). Those clients will then try to re-establish a connection and in doing so, wifite will capture the initial handshake packets which contain the password hashes.

Disclaimer: What you do with this information is up to you. You are fully responsible for what you do with this info, and how you use it. HackMethod is not responsible for your actions. Please do not hack Wifi points that you are not allowed to.
Wifite is a Python-script and it internally uses the Aircrack-ng suite. Apart from this, it has a couple of pre-requisites. But, all of them come pre-installed in Kali Linux.
NOTE: I do advise having a USB WiFi adapter, and an extra point would be to get a great one like the ALFA AWUS036NHR or AWUS051NH. Although any card would do as long as it supports monitor mode and packet injection.

Introduction
When it comes to the world of WiFi hacking, the possibilities are only limited by your imagination. Skilled hackers can combine attacks together for increased efficiency, and can also judge on which attack is best to use given a particular situation. By the end of this guide you should have an overall idea on the types of attacks that you can use against any WiFi-enabled AP or router.
Getting Started
The tool that this guide will be using is Wifite.
Now I wont be including how to do it using any other tools, because this should work just fine. I’ll leave the exploration up to you.
To get started, install Wifite on your machine by following the installation instructions that are stated here.
Scanning for Wifi points
Simply run wifite.py -i <wlan interface here *NOT IN MONITOR MODE*> or if you didnt understand the previous command simply use wifite.py and it will begin scanning for nearby access points and their features (Encryption method and if WPS is enabled or not).
NOTE: I always recommend to spoof your mac address using the --mac flag to the program or macchanger. Its for your safety.
Here are the 3 types of targets you can find:
WEP protected routers
WPA/WPA2 protected routers
Open routers
Now within those categories, you can find a feature called WPS (Wi-Fi Protected Setup) enabled, which uses an 8 digit PIN to add devices to a WiFi network without having to input long passwords.
Attacking WEP protected WiFi points
WEP is an old and depreceated way of protecting WiFi passwords, so if you find one, you are in luck. WEP takes substantially less time. This is easily automated in Wifite, and it even uses multiple attacks against routers to get the password. You only need around ~10 to 120 minutes to crack WEP, maybe longer. I cant say much because I have never seen any WEP protected routers were I live and never had the time to set one up and try myself.
Here is how the attack should look (picture taken from Wifite Github wiki):
Attacking WPA/WPA2 protected WiFi points
When it comes to WPA, we need to grab the handshake by deauthing clients who are connected to the router and sniffing the handshake as it goes. This is automated in Wifite, and it handles everything. Note: You may grab the handshake in a small amount of time, but cracking the hash itself will take a pure brute-force attack or a wordlist, which takes alot of time. Only use this method if you have a really powerful GPU/CPU or if all other options have failed.
Attacking WPS enabled WiFi points
Now comes the fun part, WPS cracking. There are 2 attacks you can do on WPS enabled routers, a WPS PIN bruteforce and a WPSPixie attack. The WPS PIN attack works online, as in all PIN guesses are actually sent to the router, while the WPSPixie attack works offline and without flooding the router with WPS PIN attempts.
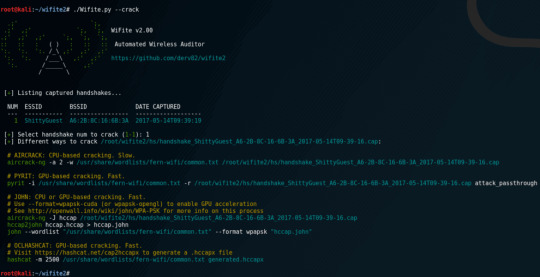
Now the obvious disadvantage about the WPS PIN attack is that some routers have on-board anti-bruteforce mechanisms and will stop accepting your attempts after a few attempts. I only go this route if the WPSPixie attack fails and there is no anti-bruteforce mechanism (Wifite will tell you if detects one).
The WPSPixie attack is one of the best attacks on Wifi points I have ever seen. In most cases, you can get the WiFi password in minutes or even a few seconds. Be aware that it may take up to 30 minutes in some cases, although I have never personally seen it go beyond 10 or so minutes. NOTE: The WPSPixie attack may not work on some routers, and you will have to choose a different route. (Wifite will also notify you if the WPSPixie attack will not work.
Automated Wireless Pentesting/Hacking With Wifite In Kali Linux 2020.4(Tutorial)
NOTE: Sometimes you will see that Wifite gets stuck at Waiting for beacon from 'xx:xx:xx:xx'. If it gets stuck for a while at this point, press CTRL+C and move on to a different target.
WiFi Hacking: How To Use Wifite To Capture WPA2 Handshakes
Wifite hacking WPS enabled points using WPS PIN Bruteforce

Conclusion
So thats pretty much it when it comes to hacking WiFi using Wifite. There are other ways of doing this, such as using the aircrack-ng suite of tools and/or using dedicated WPS hacking tools such as reaver. Additionally, this guide is only but a small slice of the world of wireless hacking, so be sure to stay tuned for more wireless hacking tutorials soon!
In this article series, we will look at a tool named Wifite suitable for automated auditing of wireless networks. Most of you who have experience in wireless pentesting would use tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng to crack wireless networks. This would involve a sequence of steps, like capturing a specific numbers of IV’s in case of WEP, capturing the WPA handshake in case of WPA etc, and then subsequently using aircrack-ng to crack the password required for authentication to the network. Wifite aims to ease this process by using a wrapper over all these tools and thus making it super easy to crack Wifi networks.
Here is a list of features of Wifite as per its official homepage.
How To Use Wifite
sorts targets by signal strength (in dB); cracks closest access points first
automatically de-authenticates clients of hidden networks to reveal SSIDs
numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
customizable settings (timeouts, packets/sec, etc)
“anonymous” feature; changes MAC to a random address before attacking, then changes back when attacks are complete
all captured WPA handshakes are backed up to wifite.py’s current directory
smart WPA de-authentication; cycles between all clients and broadcast deauths
stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
displays session summary at exit; shows any cracked keys
all passwords saved to cracked.txt
built-in updater: ./wifite.py -upgrade
Before we start using wifite, make sure you have a proper wireless card that supports packet injection. If you don’t have one, i would suggest that you buy this card.
Note that there is a bug in Wifite that may or may not be there in your particular version of Wifite. The bug basically doesn’t aireplay-ng to function properly and displays an error like aireplay-ng exited unexpectedly . In order to fix this, you will have to make slight modifications in the code of wifite. You can install gedit (apt-get install gedit) which is a text editor and then edit the wifite python script (found in /usr/bin/wifite) using the steps mentioned here. To open wifite, use the command gedit /usr/bin/wifite. This will open up the source code of wifite. Then replace every occurence of cmd = (‘aireplay-ng’, with cmd = (‘aireplay-ng’,‘—ignore-negative-one’,
Wifite can be found under Applications –> Kali Linux –> Wireless Attacks –> 802.11 Wireless Tools. Also, note that if you are running wifite in a different VM than Kali Linux, then you have to make sure that tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng are already installed on that system. This is because Wifite is nothing but a wrapper over all these tools. Before we even start using Wifite, it is better to update to the latest version.
In my case, i already have the latest version. In this tutorial, we will be targeting a simple Wifi network with WEP encryption. Just using the command wifite -h will give you a list of all the commands.
A very tempting option would be -all which tries to attack every network that it finds. We will try it in later articles in this series. However, first lets take a look at all the targets that we have. To do that, use the command wifite -showb
Once this is done, we can see that wifite has put our network interface card into monitor mode (using airmon-ng) and started to look for clients. After a few more seconds, it will start displaying the list of access points.
Note that as it is mentioned in its feature list (automatically de-authenticates clients of hidden networks to reveal SSIDs), this list will also include hidden access points. Hence, wifite can also be used to find hidden access points. In this case we will attack an access point with the BSSID 00:26:75:02:EF:65 that i have set up for testing purposes. The access point has a simple WEP password 1234567890.
To start attacking an access point, just press Ctrl+C. Wifite will now ask you to choose a target number from the list. The target number for my test network is 1, so let me enter that. Note that if you press Ctrl+C again, it will quit Wifite.
You can now see that Wifite will start attempting to crack the WEP access point using the different known techniques for cracking WEP encryption. After some unsuccessful tries, it has finally begun to start attacking the access points using different techniques for cracking WEP.
Once enough IV’s are being captured, it will automatically start cracking the password.
As we can see, Wifite has successfully figured out the WEP key for the access point. Wifite is an extremely useful tool for cracking wireless networks. As i mentioned previously, you need to have all the tools like airmon-ng, aireplay-ng, airodump-ng, aircrack-ng already installed on your system. To further prove the point, let’s dive into the source code of Wifite.
Wifite2
As we can see, the python code has mentions of calling aireplay-ng. Hence, it is recommended to run Wifite inside Kali linux.
More Videos For Wifite »
In the next article, we will look at some advanced usage options of Wifite.
0 notes
Text
[Media] Raspberry Pi 4 Model B - Miniature Hacking Station!
Raspberry Pi 4 Model B - Miniature Hacking Station! Raspberry Pi 4 Model B was released with specs including either 1 GB, 2 GB, 4 GB, or 8 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card. For hackers interested in a cheap Kali Linux computer capable of hacking Wi-Fi without a separate wireless network adapter, the Pi 4 Model B is a great way to run Kali without needing a virtual machine. Thanks to the number of Wi-Fi hacking tools included in Kali Linux, the new Pi 4 Model B represents a complete Ethernet and Wi-Fi hacking kit for beginners. The reasons for using a Raspberry Pi as a hacking computer are many. Previous Raspberry Pi versions have proved that it doesn't take expensive hardware to run tools in Kali Linux. Virtual machines can behave unpredictably, especially when working with Wi-Fi hacking. Plus, it's sometimes more straightforward to run Kali on hardware rather than in a virtual machine. Another advantage to the Raspberry Pi is that it can easily be used in combination with a device like an unmodified iPhone or Android smartphone. If your smartphone supports creating a Wi-Fi hotspot, it's simple to connect the Pi to your hotspot and control it over SSH. If your smartphone can't create a hotspot, the Pi can also host its own Wi-Fi network, allowing you to join the network created by the Pi on your phone and SSH into it on the go. One of the most exciting things about using a Raspberry Pi for hacking is the add-on of the Nexmon firmware. The addition makes it possible to put the built-in Wi-Fi network adapter into monitor mode. That means it's possible to do things like grab WPA handshakes, listen in on Wi-Fi traffic, and execute attacks like WPS-Pixie without needing a separate compatible Wi-Fi network adapter. For someone interested in getting started with Wi-Fi hacking, the Raspberry Pi 4 Model B provides a Kali-supported Wi-Fi network adapter and an onboard computer capable of basic cracking and MiTM attacks in a single package. The increase in speed and power of the Pi 4 Model B make it a more capable networking device as well as a more capable computer. Hack WiFi with a Raspberry Pi and Kali Linux: https://www.youtube.com/watch?v=PqRVo2niA_8 Buy online: 🛒 https://ali.ski/QMVRo #raspberrypi #mobilepc #kali

0 notes
Text
Hack Wifi Password Using Terminal

Hack Wifi Password Using Terminal Command
Hack Wifi Password Using Terminal Software
How To Hack Wifi Password On Mac Using Terminal 2020
Hack Wifi Password Using Terminal Download
How To Hack Wifi Password On Mac Using Terminal 2019
Hack Wifi Password Using Terminal
Cyber Security Tool For Hacking Wireless Connections Using Built-In Kali Tools. Supports All Securities (WEP, WPS, WPA, WPA2/TKIP/IES) - GitHub - ankit0183/Wifi-Hacking: Cyber Security Tool For Hacking Wireless Connections Using Built-In Kali Tools. Step 1 (Setting up Reaver 1.4 ) 1) Open terminal and type sudo -s and then type your password. 2) Download Reaver (Better Download the Latest Version ) Place in a specified folder. 3) Open the Terminal and type tar xvfz reaver-1.4.tar.gz 4) Install dependencies sudo apt-get install. Crack Wifi Passwords the Easy Way! (OSX Version) DISCLAIMER: This article is for educational purposes only. This article should not be used for illegal activity. The author is not responsible for its use. You are 18 and bored at your grandma’s place, there is no source of entertainment, but you find out there is a sweet wifi spot at your. Part 2: Crack WiFi Password Windows in Minutes. There are lot of people searching this question on internet that 'how to hack WiFi password on Windows 10/8/7' for free, here, now, is a software for you called PassFab Wifi Key, that will be your best choice. With this free software, to hack WiFi password on laptop is no big deal. Hello friends please like and subscribe my channelhttps://youtu.be/CI8GnSlEpyc.
Step By Step Hack WPA/WPA2 Wi Fi Passwords Using Aircrack Ng
In this tutorial I will tell you how to crack wpa/wpa2 wi-fi in kali linux using aircrack-ng. To do this, first you should install kalinux or you can use live kali linux. Print shop 5.0 free download.
To crack Wi-Fi, first, you need a computer with kali linux and a wireless card which supports monitor/injection mode. If your wireless card is not able to do this, you need to get an external wireless card which is capable of monitor/injection mode.
Apart from these tools, you need to have a word-list to crack the password from the captured packets.
First you need to understand how Wi-Fi works. Wi-Fi transmits signal in the form of packets in air so we need to capture all the packets in air so we use airodump to dump all the packets in air .After that we should see that if any one is connected to the victim Wi-Fi. If anyone is not connected the Wi-Fi, cracking is not possible as we need a wpa handshake. We can capture handshake by sending deauthentication packets to client connected to Wi-Fi. Aircrack cracks the password.
Step-1:-
First open terminal. We need to know the name of the wireless adapter connected to the computer because computer has many adapters connected.
command for this is : iwconfig
In my case, my wireless adapter is with the name wlan0. In your case, it may be different. If connected to an external wireless card, it may be wlan1or2.

Step-2:-
For some wireless cards, it gives error messages to enable monitor mode on wireless cards. For that, you should use airmon-ng check kill.
Step-3:-
In this step, you need to enable the monitor mode on the wireless card. The command is as follows:
airmon-ng start wlan0 (interface of wireless card).
Now this command will enable the monitor mode on the wifi card. So while using interface in any terminal or command line use wlan0mon.
Note : You should use the interface which is indicated with red mark.
Step-4:-
We need to use the command airodump-ng wlan0mon, this will display all the access points in your surroundings and also the clients connected to that access points.
Now this command captures the packets in the air. This will gather data from the wireless packets in the air.
Note : Do not close this terminal. This will be used to know wpa has been captured or not.
Step-5:-
In this step we will add some parameters to airodump-ng.
command is : airodump-ng -c channel –bssid (bssid of wifi) -w (path to write the data of packets) wlan0mon(interface).
bssid − in my case bssid is indicated with red mark.
c − channel is the channel of victim wifi in my case it is 10(see in previous screenshot for channel number).
w − It is used to write the captured data to a specified path in my case it is ‘/root/Desktop/hack’
Interface in my case is wlan0mon.
In the above command the path /root/Desktop/hack hack is the name of the file to be saved.
Above command displays this terminal.
Step-6:-
In this step we deauthenticate the connected clients to the Wi-Fi.
The command is aireplay-ng –deauth 10 -a (router bssid) interface
In the above command it is optional to give the client mac address it is given by
This will disconnects the client from access point.
Screen shot of a client connected to access point.
After this the client tries to connect to the Wi-Fi again. At that time, we will capture the packets which sends from client. From this result, we will get wpa handshake.
Step-7:-
Now we should start cracking the Wi-Fi with captured packets command for this is
path to word list in my case it is ‘/root/Desktop/wordlist.txt’
If you did not have word list, get one. If you want to generate your custom wordlist, you can visit our other post: How generate word list using crunch.
Now press enter aircrack will start cracking the Wi-Fi.

Everyone Ask The Question: How To Hack WIFI Password? Is there software that can help, or a trick? Read on to find out.
Hey Guys, Today I am Sharing with You How To Hack WIFI Password. We Have Done This Lots of Time.
Note: Here is The Best Method To Hack WiFi Password. However, Hacking is The Crime. So, Use it For Only Education Purpose.
In Today’s World Everyone Need The Internet, And Without That is Something like Dead man.
First, We Install One Software To Capture The Wifi Packets. Using This Software We Capture The WiFi Packets.
WiFi Packets Mean Someone Request To Connect With WIFI. It will Go To Router using Packets. And Packets contain the Password.
So, When We Capture the Packets it will Contain the Password.
And then We will Find the Password With Wordlist and Packets.
So, Here is The Step By Step Process To Hack WiFi Password.
Step 1: Install Software Called CommView For WiFi
First of All You Need To Download The Zip File called “Hacking WiFi” That Are Given in The Resources Section or Click Here. After That Extract The Zip File. Than Go To The CommView Folder And Open The “setup Commview” File.
Click Next.
Accept The terms and Condition And Click Next.
Select The VolP Mode And Go Next.
Select the Option As You can see in Photo and Go Next
And Install the Software.
Now, We Successfull Install This Software. But, This is Paid Software. So, We Need To Crack it First. To Crack it Open The Crack-Commview Folder. But, Don’t open the CV File.
Now, You can See The Commview for WiFi on Desktop, Right Click on that and Select the Option “Open File Location”.
Now, Paste the CV file From The Crack-Comview To This Folder.
Hack Wifi Password Using Terminal Command
Hurry, You Successfully Install The Software.
Step 2: Capture The packets For Targeted WiFi
Once You Install the Software open it. It will Ask You to Install The Driver. Select the Option that Show in Picture.
After That Your Software Are Closed. Open it Again.
Also Read: How To Install Custom Rom in Android
This Software might Run in Windows 10. So, If You are Using Windows 10 Then it Has less chance to Run the Software.
Now You can See The Full Interface of CVW. Using This Software We Can Hack Wifi Password.
To Capture Wifi packets which You want To Hack, You need To Click Start Button on the Top Left Corrner.
After Start The Capturing, The Wifi List Apper With The Channal Number.
Hack Wifi Password Using Terminal Software
Here You Need To Select Your WiFi You Want To Hack WiFi. And Remember There Channel Number.
After That in Right Sidebar You need to select “Single Channel Mode” and select The WiFi Channel Number You want To hack.
I am Hacking TechnoUtter WiFi. So, I Select The 11 Channel.
Now Go to The Packets Section.
You will See the Packets Are Captured.
Now, Go To Logging.
Select The Auto-saving Option and Enter The Path When You Want To Save The Packets.
How To Hack Wifi Password On Mac Using Terminal 2020
Now Your Packets are Automatically Save.
Wait To at least One Hour To Capture The Packet That Contain WiFI Password.
You Want To Know To How The Packet are Capture The Password For Crack WiFI Password.
How The Packets Capturing The Password
The Packets is Contain Some Things Like IP Address, Password in Encryption Format, etc.
So, When Someone Want To Connect To The WIFI, It will Send The Packet File To the WIFI Router. And That Contain The Password.
So We Need The Packets To Crack The Password.
But, The Password is in Encrypted Format. So, We Also Need To Decrypt it Using Aircrack-ng.
Step 3: Convert The Packets to Capture File
Hack Wifi Password Using Terminal Download
Select File And Open Log Viewer.
Select The File and Select “Load CommView Logs”.
Go Where Your Packets are Saved And Import it.
Now, All The Packets Are Imported.
Now Goto File > Export Log and Select The “Wireshark/Tcpdump Format”.
Make sure You select “.CAP” And Save It on The Desktop File.
Now You Successfully Convert The Packets to the Capture File.
Using This Capture File You Hack WiFi Password.
Step 4: Hack WiFi Password
Now, It’s Time To Hack WIFI Password.
Go To Hacking WiFI Folder And Go To Aircrack-ng Folder.
Now GoTo “Bin” Folder.
Now, Go To The Folder Which Version of Your Computer.
Open That Folder.
Now Open “”Aircrack-ng GUI” File
Now, Select The WPA Option To Crack WPA2 PSK.
Select The Capture File in Filename Option.
And select The Wordlist in the Wordlist Option.
Click Launch, To Crack Wifi Password.
What is Wordlist?
A word list is just what it says it is. It is a list of words. Words that may or may not match someone’s password. Some of them contain commonly used passwords that have long been known to be the most commonly used passwords, and some of them are lists of passwords from leaks of hacked databases. You would use a wordlist to attempt to crack a password using a dictionary attack.
Torrent sites typically have large wordlists you can download, but if you do some google searching you will find a lot of websites with various wordlists.
Wordlists are only so successful though. I’ve had some pretty weak passwords that I have never seen in any wordlist I have ever downloaded.
You can Download The Wordlist On Here.
Now Back to Our Tutorial, when You Click Launch, It’s Open the CMD and List out The WiFi’s name You want To Hack.
Select The Wifi To Hack it. I am Hacking TechnoUtter Wifi So, I Select 1.
After that It will Match The Capture File with The Wordlist.
How To Hack Wifi Password On Mac Using Terminal 2019
If The Password is in the Wordlist Then It will Match And Password is Display.
Hurry, You Can See We hack The TechnoUtter WiFI. Password is The “tech@123utter”.
I will Connect The Wifi You can See.
Hack Wifi Password Using Terminal
Conclusion
Here is The Best Method To Hack WiFi Password. But, Hacking is The Crime. So, Use it For Only Education Purpose.
And If You Like This Article Then Share it On Social Media and Comment if You have Any Problems.
Thanks

0 notes
Text
Kali Linux क्या है और डाउनलोड कैसे करे?
यदि आपने Ethical Hacking का नाम सुना है तब जरुर से आपका सामना इस Kali Linux से जरुर हुआ होगा. लेकिन आप में ऐसे बहुत लोग होंगे किन्हें की ये जानने में बहुत दिलचस्पी होगी की आखिर ये Kali Linux क्या है और इसके benefits क्या हैं. यदि आप भी उन्ही में से एक हैं तब तो आज का यह article आपके लिए बहुत ही जानकारी भरा होने वाला है.
Kali Linux अब के समय में एक industry का एक leading Linux distribution है जब बात penetration testing और ethical hacking की हो तब. यह एक ऐसा distribution है जिसमें की by default (पहले से ही) बहुत से hacking और penetration tools एवं software pre loaded होते हैं. वहीँ इस linux version को दुनियाभर में बहुत से लोग इस्तमाल में लाते हैं.
इनमें ऐसे Windows users भी शामिल है जिन्हें की Linux के विषय में कुछ भी नहीं पता होता है. इसलिए चाहे उन्हें कुछ पता हो या न हो सभी को इसे इस्तमाल करने में बड़ी रूचि होती है. इसका कारण बहुत से हैं जैसे की कोई इसे केवल fun करने के लिए करते हैं, तो कुछ अपने girl friend को impress करने के लिए, वहीँ कुछ अपने पडोसी के wifi को hack करने के लिए भी करते हैं.
यकीन मानिये की ऐसा करना बिलकुल भी ठीक नहीं है क्यूंकि Kali Linux को इस कार्य के लिए नहीं बनाया गया है. इसलिए चलिए आज इस article में हम Kali Linux क्या होता है और उससे जुडी सभी बातों को गहराई से समझेंगे. जिससे आपको इसे ठीक तरीके से समझने में आसानी होगी. तो बिना देरी किये चलिए शुरू करते हैं.
अनुक्रम छुपाएँ
काली लिनक्स क्या है (What is Kali Linux in Hindi)
काली लिनक्स को किसने Develop किया है?
काली लिनक्स का Official Statement क्या है?
काली लिनक्स को कब और क्यूँ लाया गया?
लिनक्स ऑपरेटिंग सिस्टम की विशेषता
Kali Linux को Download और Install कैसे करे?
Kali Linux क्यूँ Beginners के लिए सही नहीं है?
Kali Linux के Advantages क्या है?
क्या आपको Kali Linux इस्तमाल करना चाहिए?
काली लिनक्स डाउनलोड
https://technicalkishor1.blogspot.com/2021/04/kali-linux.html

0 notes