#remove computer malware
Explore tagged Tumblr posts
Text
https://digimob.com.au/signs-of-malware-on-phone-or-laptop

#Phone Repair#Laptop Repair#Malware Detection#Mobile Security#Computer Security#Virus Removal#Tech Tips#Device Troubleshooting#Cyber Threats#Phone Performance Issues#Laptop Running Slow#Data Protection#Digimob Phone Repair#Device Malware Signs#Professional Repair Services
0 notes
Text
AGR Technology Virus/Malware Removal Services

In today’s digital landscape, the threat of viruses and malware looms large. These malicious programs can wreak havoc on your computer, compromising your data and disrupting your daily life. That’s where professional virus and malware removal services come in.
Link to our services: https://agrtech.com.au/virus-malware-removal-services/
#virus removal#malware removal services#computer virus removal shepparton#computer virus removal melbourne#malware removal melbourne#malware removal shepparton
0 notes
Text
Reblog and share and boycott.
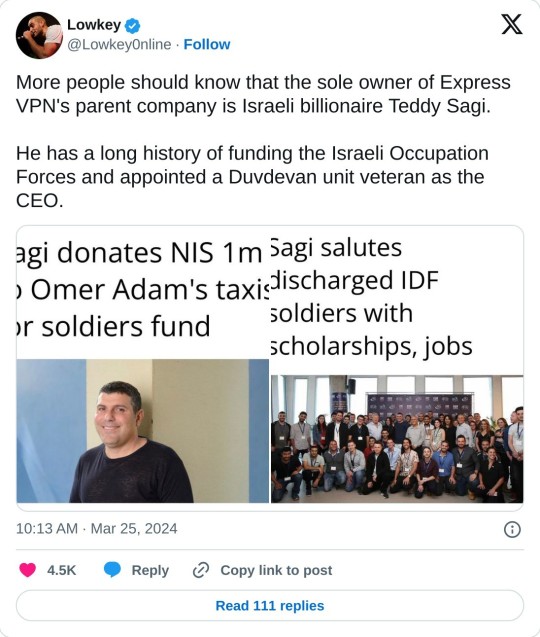



Boycott ExpressVPN
#reblogging 'cause i've seen more expressvpn sponsorships lately#not mentioned is that kape bought a vpn review site the same year it bought expressvpn#or that teddy's previous start up was used to inject malware and spyware onto people's computers#because it was designed to inject personalized ads and they 'couldn't keep up' with removing the malware#he was also named in the panama papers#though now it looks like the review site has been reworked to 'connect [traffic] with the brands they need'#but it also owns and opperates vpnmentor and surprise surprise expressvpn#is the editors choice vpn and you get a special discount if you subscribe to it through them#kape also merged with private internet access so there's another vpn teddy effectively owns#i'm sure there's more if one were to dig into it given the guy's a billionaire and has been systematically buying up vpns#and internet advertising companies#oh and there it is#got a huge time-limited offer to get expressvpn on this supposedly independent review site#and i assume there's something fishy there 'cause i only whitelisted the site itself temporarily#ads are still blocked from everything else and javascript is also blocked#looks like i was right 'cause the tracking link on it helpfully says it's from the totally not biased site#but it looks like they're trying to hide they own vpnmentor#on the current site they just talk about their 'review sites' and how their 'review sites were featured on' various sites and fox news#but if you look at the site before they were bought out that section was about#how the company owns vpnmentor and that's their customer-facing side while webselenese is the business-focused side#plus it says in the advertising disclosure and about page that they're owned by kape technologies#also that kape owns expressvpn and cyberghost and zenmate and private internet access#but that totally doesn't make them biased about it /s#teddy also served time for insider trading#supposedly crossrider shut down and leadership was overhauled but teddy was still owner#and it was erlichman who said it was rebranding as he was ceo of the company that was rebranding from being infamous with malware#to the point security companies talked about it by name and warned about it#because they were now focused on privacy and security as a company and didn't want that to follow them#even though some of the top names and connections hadn't changed one bit#geez this went from a 'oh a tumblr post to look up'
9K notes
·
View notes
Text
just found out my computer might have malware on it. haha lol lmfao rofl this is so funny. IM GOING TO THROW SOMETHING
#tell me why i was studying for a test with my friend during lung#lunch*#and i get a popup on chrome#saying#'hey btw lol we removed this web browser extension because it contains malware'#IT WAS ONE I USED ALL THE FUCKING TIME TOO#IM SO FUCKED#NO WONDER MY COMPUTER KEEPS RANDOMLY OVERHEATING#god. i literally inputted credit card information using chrome a while ago#literally a day or two ago#fuck me man what the fuck#ive had it for MONTHS too#dude holy shit#actvdepart
0 notes
Text
Why Should You Hire Seasoned Virus Removal Services
Thinking you are in the middle of an essential conference and your computer suddenly starts to malfunction. Hey! Are you crying or panicking? Please don't, for we are here to help you out. No, not with any DIY ideas but with the best assistance. Call a technician.

Hiring the experts would ensure that your gadget is in the safe hands and you would be ensured to get a positive result at the end of the process. Not only that, hiring them also serves several benefits which would again add as beneficial for you. Hence, the best step will be to look for a phone or computer virus removal service nearby.
Why Hire an Expert Troop? Read the Reasons Below
Cost Effective: The authentic experts in the field would never charge you anything extra. They would let you know about the estimated cost from the initial stage.
Prevents Data Loss: Data loss is a common fear among the customers which can be easily resolved by the experienced technician in the field.
Time Saving: Experts tend to resolve and fix your problem faster as they have the potential to identify the glitches quickly.
Guaranteed Service: Reputed repair service providers would provide guarantee upon their products and services as well.
Timely Maintenance: Many reputed companies provide a maintenance package plan which helps you to maintain a proper check of your device.
Where to Find the Best Connection?
Download and install Qvesty and type 'computer virus removal service near me'. As soon as you type the same you will get a list of the best doers nearby. Do not worry about extra commissions as they do not charge any. So, why wait? Happy hiring!
0 notes
Text
!Important Warning!
These Days some Mods containing Malware have been uploaded on various Sites.
The Sims After Dark Discord Server has posted the following Info regarding the Issue:
+++
Malware Update: What We Know Now To recap, here are the mods we know for sure were affected by the recent malware outbreak: "Cult Mod v2" uploaded to ModTheSims by PimpMySims (impostor account) "Social Events - Unlimited Time" uploaded to CurseForge by MySims4 (single-use account) "Weather and Forecast Cheat Menu" uploaded to The Sims Resource by MSQSIMS (hacked, real account) "Seasons Cheats Menu" uploaded to The Sims Resource by MSQSIMS (hacked, real account)
Due to this malware using an exe file, we believe that anyone using a Mac or Linux device is completely unaffected by this.
If the exe file was downloaded and executed on your Windows device, it has likely stolen a vast amount of your data and saved passwords from your operating system, your internet browser (Chrome, Edge, Opera, Firefox, and more all affected), Discord, Steam, Telegram, and certain crypto wallets. Thank you to anadius for decompiling the exe.
To quickly check if you have been compromised, press Windows + R on your keyboard to open the Run window. Enter %AppData%/Microsoft/Internet Explorer/UserData in the prompt and hit OK. This will open up the folder the malware was using. If there is a file in this folder called Updater.exe, you have unfortunately fallen victim to the malware. We are unware at this time if the malware has any function which would delete the file at a later time to cover its tracks.
To quickly remove the malware from your computer, Overwolf has put together a cleaner program to deal with it. This program should work even if you downloaded the malware outside of CurseForge. Download SimsVirusCleaner.exe from their github page linked here and run it. Once it has finished, it will give you an output about whether any files have been removed.
+++
For more Information please check the Sims After Dark Server News Channel! Or here https://scarletsrealm.com/malware-mod-information/
TwistedMexi made a Mod to help detect & block such Mods in the Future: https://www.patreon.com/posts/98126153
CurseForge took actions and added mechanics to prevent such Files to be uploaded, so downloading there should be safe.
In general be careful, where and what you download, and do not download my Mods at any other Places than my own Sites and my CurseForge Page.
2K notes
·
View notes
Note
Hey, could you do a post on the spacers.exe scam on discord please? I got hacked from it and a friend then got hacked by my account and it super sucks!
🔎Scam Exam(ination)🔍
Seen as: Free game / Try my game Scam Type: Malware / Password Stealer
Platform: Discord
Note: This post will contain a collection of data from across the internet, mainly reddit where people have figured out how this malware works and what it does at its core. I will do my best to explain to you what's going on behind the scenes.
Here's a video talking about this same type of scam by NTTS:
youtube
If you'd like my take on it, click read more and let's continue!
-----
1 - How it starts
The way this scam works is by a friend of yours, or someone in the same server as you, falling for this scam and downloading then opening the malicious file that their friend had sent to them. In a very long line of things, it's a chain reaction of them hijacking and using the stolen account to then scam someone else. And if you're not quick enough, it can and will steal everything on your computer/phone.
Not everyone on the internet is scam savvy, but that's what guides like these are meant to help with. :)
Here are two images taken from reddit on what it looks like when you're contacted by the hijacked account:
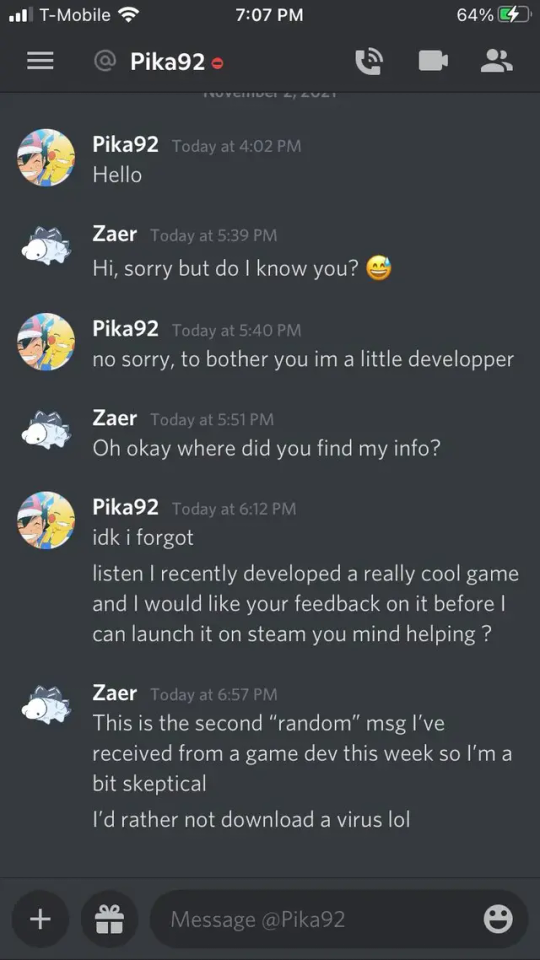
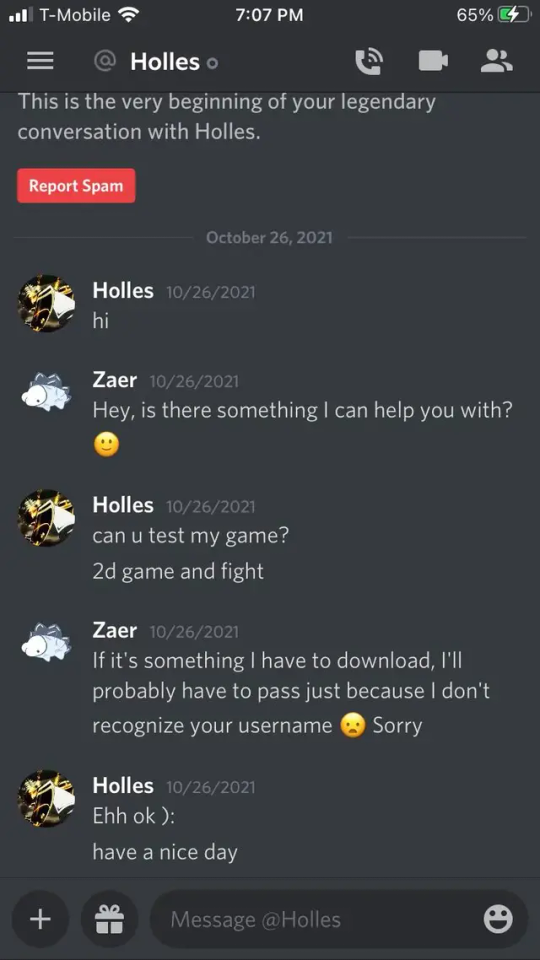
Immediate red flags:
I'm a developer. Try my game. Can you test my game?
Other reported red flags to look out for:
I need you to beta test my game. Download my game and try it for 4-5 minutes then write a review. Here's a free key/password for the game go to this link. I'm working on a project and need someone to try my game. I'll give you free items/vip if you try my game. Try this new mobile game <link> ** and I'll give you items. I'll pay you $ via PayPal or give you Nitro if you try it.
What it boils down to, is that for this scam to work, they need you to download the file they send you, or a file that's uploaded via a link to a file sharing website, and then you have to open the file.
Do not do this, obviously.
Do not accept any suspicious .exe or .jar files from your friends or fellow server members if you do not know what might be inside it.
** Sometimes they will send you an APK file or a link to the google play store for a mobile game, and sadly this too, is malware, and it will steal your passwords. Again, do not download it.
2 - The Malware/Virus
If you were someone who downloaded a file like this and then opened it, you have now infected your computer, and... unfortunately, all of your Passwords, addresses, Crypto info, and credit card information, have now been compromised.
Nothing is safe with this Malware.
A more in depth explanation of spacers.exe can be found here as well as how to remove spacers.exe:
youtube
Here's a second NTTS video explaining how the inner workings of this can work from the scammers point of view:
youtube
3 - The Goal
The goal of this malware, as noted above, is not just to steal your passwords, credit card info, but also your discord account.
There are people who will pay for this malware (it is being sold for others to use, which sucks) so that they can take over your discord accounts if you have certain badges or names.
If a scummy individual running this scam wants something they don't have that you do, they will try to take it from you.
Do be warned that if you fall for this, you may also receive threatening emails to have your personal information leaked if you don't pay a ransom/money amount after you got infected.
This is a scare tactic.
This was noted in this post from Dec 3rd 2024:
-----
Final Thoughts: All I can say is.. common sense should be a big factor here. Internet safety 101 and all that. You shouldn't be clicking links to anything or anyone saying something's 'free' or with the offer of you getting some reward from it. Nor should you go believing or downloading things from your friends if they start acting weird or weirder than normal.
Pro tip: If you get a message on steam or discord by someone asking you to 'visit this website' to 'vote for my friend in <thing>' that too is a scam and it will steal your login information.
If you're like me and your best friend on the internet is someone you've known online for 18 years, having him suddenly say 'I'm a developer try my game' would be a big indicator to me that his account was compromised.
If you can, try to make sure you're connected with your friends through other outlets like tumblr or bluesky. Or even through e-mail (as old as that seems lol.)
That way if something goes wrong, they can at least let you know about it.
#scam#scam alert#scams#scammer#scammers#scam awareness#discord#discord scam#online scams#scam warning
133 notes
·
View notes
Note
what's up with GShade what kind of drama could a Shader have
to the best of my memory: the lead developer of gshade started to get very controlling and arrogant about their software and how people used it. one common annoyance was that when there was an update released, the software would very intrusively bug you about updating right then and there and it was a headache to have to constantly manually remove the notice from your screen. i believe the crux of the drama was that a young modder took it upon themselves to mod and release a version of Gshade, or just some kind of additional software, that bypassed the annoying update notifications. and when the lead gshade dev found this out they sneakily implemented new code into gshade that would force shutdown someone’s computer if gshade detected that they were using this mod.
after the initial wave of controversy their reputation basically tanked overnight once people found this out. understandably so, as this was in very literal terms implementing hidden malware into the software. a bunch of shader preset creators started working on adapting their presets for reshade immediately after. i know i personally switched over to reshade immediately myself. it was such an easily avoidable mess haha.
also if i’ve gotten any of these details incorrect please feel free to correct me or elaborate in the replies, it’s been a while since i’ve looked into this drama and i’m literally just recounting it off the dome :)
328 notes
·
View notes
Note
Have you ever thought that Steven's mind control is stronger than White's? (She needs to cast a control beam that can be defended)

White's full-control beam and Steven's use of 'sit' on Jasper stem from the same ability but are different in their execution and function.
When White Diamond inhabits the other gems, she straight up over-writes their personality and will. It's like hijacking an entire computer and removing the original user's ability to use their keyboard and mouse, as well as turning off their monitor.

What Steven is doing with Jasper, and what he previously did with Lapis once, is just giving a single command that bypasses the other functions, kind of like a virus or a malware. Their consciousness remains intact, and they remain aware of what happened.

It's actually a lot smaller-scale, almost like changing the monitor background to a screenshot of the desktop and then deleting all the actual icons off of it, or like adding a shortcut to your mom's phone to autocorrect every instance of 'walk the dog' with 'hang tight with mr.puddles'.
It's actually not nearly as strong as the complete over-write, but it IS harder to catch and deflect because of how small-scale it is comparatively.
And keep in mind, the only one capable of deflecting White's Powers was Pink (Steven) and WD!Steven hasn't tried to use this specific power on anyone but two gems thus far.
402 notes
·
View notes
Text
I've been meaning to introduce one of my Storybots ocs that I've had for a while but here we go. Let me introduce you to...

Melissa Malware
She's a totally normal storybot who is definitely not a shapeshifting virus who has alterative motives for taking over the computer world! :D

Melissa is inspired by the Melissa and I LOVE YOU computer viruses, influencing both her name and theme of spreading love worldwide. In an alternate universe called the LoveBug AU, she launches a campaign called "Project I LOVE YOU", encouraging StoryBots to express love in various forms, aiming to boost mental well-being and promote world peace. She also advocates for self-care, which leads people to work less and less, eventually creating a job crisis in the computer world.
However, Melissa's true intent is to infect others, causing them to slack off from work, which in turn slows down real-world computers, much like a virus. As her followers idolize her, they unknowingly spread her influence, infecting others with the same behavior.


Melissa's origins lie in a more abstract form sent into the internet by her creator. Her mission was to oversee a planted computer worm and ensure its success without interference, remaining in the shadows. However, her plan was unexpectedly derailed when a young Bang, wandering in the internet department while accompanying his father, mistook the worm for a colorful gummy and ate it.
Enraged and shocked, Melissa's task was ruined, forcing her to shift focus and watch over Bang as he grew up, tracking the effects of the worm on him. Over the years, she observed his growing forgetfulness and other changes (I'll make a future post about this and my theory in more detail) as she remained in the shadows. During this time, Melissa herself evolved. Watching storybots and their society, she became curious about life beyond her virus role. She gradually changed her appearance to resemble a storybot and secretly longed for a life where she wasn’t bound to a pre-programmed destructive endgame.
As she grew fond of the attention and adoration from those who saw her as one of them rather than a virus, Melissa tried to prolong her influence and delay her inevitable mission of ruining the computer world, torn between fulfilling her creator’s purpose and finding belonging among storybot society.

When Bang becomes an adult and the computer worm fully integrates with his programming, Melissa is devastated to discover that the worm is now inseparable from Bang, and removing it would kill it. This ruins her original plan, forcing her to adapt. Instead of separating the worm, she decides to use Bang to spread the infection.
Melissa presents herself as a sweet, humble activist and invites Bang to join her "Project I LOVE YOU," using his recognizable and beloved status in the community to help promote her cause. Behind her friendly demeanor, however, Melissa despises Bang, seeing him as a foolish and undeserving figure who, for some reason, is adored by everyone. Despite her loathing, she plays the role of a supportive ally, manipulating him into unknowingly aiding her true goal, while he remains completely oblivious to her hatred and intentions.
So in a nutshell, Bang has no enemies... except for one which is Melissa because she hates his guts LMAO. But yeah that's the LoveBug AU basically. There's more to it but that's for another time.


One important thing about Melissa is that her and Milo (@supgoddo's oc) are in true real love and are perfect for each other YIPPIEE GRRR I LOVE THEM SM
Anyways that's it for now for Melissa! Just wanted to introduce her character and stuff. Live laugh love Melissa <3
#She's a little crazy but we love her for that#she's my second top/main storybot oc i have#storybots#ask the storybots#storybots answer time#storybots oc#Melissa Malware#oc lore#oc intro#oc introduction#text post#digital art#digital drawing#digital sketch
68 notes
·
View notes
Text
Microsoft's CEO Satya Nadella has hailed the company's new Recall feature, which stores a history of your computer desktop and makes it available to AI for analysis, as “photographic memory” for your PC. Within the cybersecurity community, meanwhile, the notion of a tool that silently takes a screenshot of your desktop every five seconds has been hailed as a hacker's dream come true and the worst product idea in recent memory.
Now, security researchers have pointed out that even the one remaining security safeguard meant to protect that feature from exploitation can be trivially defeated.
Since Recall was first announced last month, the cybersecurity world has pointed out that if a hacker can install malicious software to gain a foothold on a target machine with the feature enabled, they can quickly gain access to the user's entire history stored by the function. The only barrier, it seemed, to that high-resolution view of a victim's entire life at the keyboard was that accessing Recall's data required administrator privileges on a user's machine. That meant malware without that higher-level privilege would trigger a permission pop-up, allowing users to prevent access, and that malware would also likely be blocked by default from accessing the data on most corporate machines.
Then on Wednesday, James Forshaw, a researcher with Google's Project Zero vulnerability research team, published an update to a blog post pointing out that he had found methods for accessing Recall data without administrator privileges—essentially stripping away even that last fig leaf of protection. “No admin required ;-)” the post concluded.
“Damn,” Forshaw added on Mastodon. “I really thought the Recall database security would at least be, you know, secure.”
Forshaw's blog post described two different techniques to bypass the administrator privilege requirement, both of which exploit ways of defeating a basic security function in Windows known as access control lists that determine which elements on a computer require which privileges to read and alter. One of Forshaw's methods exploits an exception to those control lists, temporarily impersonating a program on Windows machines called AIXHost.exe that can access even restricted databases. Another is even simpler: Forshaw points out that because the Recall data stored on a machine is considered to belong to the user, a hacker with the same privileges as the user could simply rewrite the access control lists on a target machine to grant themselves access to the full database.
That second, simpler bypass technique “is just mindblowing, to be honest,” says Alex Hagenah, a cybersecurity strategist and ethical hacker. Hagenah recently built a proof-of-concept hacker tool called TotalRecall designed to show that someone who gained access to a victim's machine with Recall could immediately siphon out all the user's history recorded by the feature. Hagenah's tool, however, still required that hackers find another way to gain administrator privileges through a so-called “privilege escalation” technique before his tool would work.
With Forshaw's technique, “you don’t need any privilege escalation, no pop-up, nothing,” says Hagenah. “This would make sense to implement in the tool for a bad guy.”
In fact, just an hour after speaking to WIRED about Forshaw's finding, Hagenah added the simpler of Forshaw's two techniques to his TotalRecall tool, then confirmed that the trick worked by accessing all the Recall history data stored on another user's machine for which he didn't have administrator access. “So simple and genius,” he wrote in a text to WIRED after testing the technique.
That confirmation removes one of the last arguments Recall's defenders have had against criticisms that the feature acts as, essentially, a piece of pre-installed spyware on a user's machine, ready to be exploited by any hacker who can gain a foothold on the device. “It makes your security very fragile, in the sense that anyone who penetrates your computer for even a second can get your whole history,” says Dave Aitel, the founder of the cybersecurity firm Immunity and a former NSA hacker. “Which is not something people want.”
For now, security researchers have been testing Recall in preview versions of the tool ahead of its expected launch later this month. Microsoft said it plans to integrate Recall on compatible Copilot+ PCs with the feature turned on by default. WIRED reached out to the company for comment on Forshaw's findings about Recall's security issues, but the company has yet to respond.
The revelation that hackers can exploit Recall without even using a separate privilege escalation technique only contributes further to the sense that the feature was rushed to market without a proper review from the company's cybersecurity team—despite the company's CEO Nadella proclaiming just last month that Microsoft would make security its first priority in every decision going forward. “You cannot convince me that Microsoft's security teams looked at this and said ‘that looks secure,’” says Jake Williams, a former NSA hacker and now the VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks.
“As it stands now, it’s a security dumpster fire,” Williams says. “This is one of the scariest things I’ve ever seen from an enterprise security standpoint.”
144 notes
·
View notes
Text
Do you need to remove malware if it isn't like destroying your computer. I cant figure out how to delete this shit and my stuff still runs so ?
23 notes
·
View notes
Note
the squiddo virus is back ^_^
if they were to be subjected to an antivirus, it would be torture
see, there is still some good code in there- they wouldnt be able to function properly as a person if they were entirely composed of malware (i mean ive yet to see a computer virus play minecraft lol)
so an antivirus would of course try to preserve the good code and get rid of the bad
but the issue is that its been firmly injected into their code, and is now something they cant live without- so it would be impossible to remove without removing squiddo themselves
but for it to try would be actual torture, because it would feel like something was tearing them apart- this would also cause the potentially painful glitches due to instability
do not antivirus the squiddo!
-🦑⚠ anon
.
31 notes
·
View notes
Note
Heeeeey~
Do you have a reference for Spudbo or nah, I wanna draw him with Bobby

Ye I do :DDD
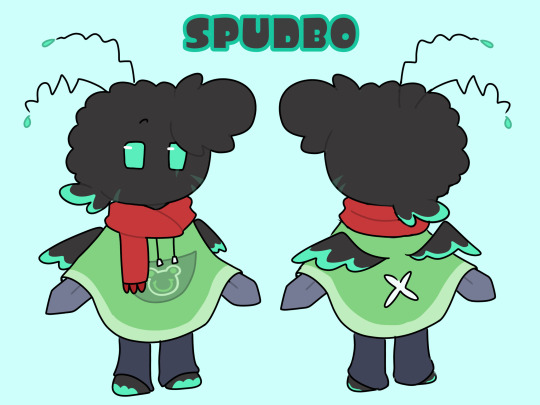
Imma also add some notes and fun facts
- He has a few faded scars on his face, and his hands, this is bc of his dad being a drug dealer and a scammer, his clients can be.. cruel..
-He wasn’t born via mpreg lmao, that was a joke, he was born in a tiny usb created by smg1 accidentally using meme energy, He needed to be plugged into a computer so be born but smg1 didn’t know that his usb had a baby inside of it and was scared it could be a malware and break his laptop, so he got an old computer someone used to have that had like- 5 viruses and used that, and the computer broke when he was born lmao. So now he has like- 5 viruses in him that don’t technically harm him but just make him glitch out sometimes, have wings, and be overall a bit freaky
-he’s not allowed to touch tari’s robotic arm at all, bc the one time he did he accidentally transferred a malware to her arm and it took WAY TOO LONG to remove the malware, poor girl didn’t let anyone touch her arm for a whole month.
-If him and Bobby were siblings he’d be the older brother, he’d be 4 when Bobby is 3
-similar to all the toys in the toy toy kingdom(including smg1 and smg2), he does not have a biological gender, everyone just refers to him as a male.
-he can fly, just not properly since noone else he knows can(you can imagine how that would turn out)
-When he was first born, Bob very much didn’t like him at all, it only got worse when he had to take care of him since yk how annoying newborns can be, so for the first few months, it was really only smg1 (and occasionally smg2) taking care of him, but when Spudbo was held for ransom for the first time (at a few months old)Bob started taking care of him more and eventually learnt to love him like a son
-smg1 had postpartum depression from the fact that Spudbo was a accident and Bob was barely there to take care of him, and more(obv not hormonal changes but stress), it lasted a month only tho.
-the swords that he’s wearing are plastic, he has hands underneath them, same goes for bob(but his swords are real), and bob removes his swords when he’s near Spudbo, or at home in general. Outside of those things he usually never takes them off.
-Bob was scared of holding Spudbo until he was 6 in fear of hurting him.
-The first syllable of Spudbo is Spud, in honor of Spudnick, and the 2nd syllable is Bo bc Bob wanted to name him Bob jr, obv smg1 wasn’t very fond of that name
-Spudbo has a tts voice just like Bob and Bobby, he also has a Portuguese tts.
-Smg1 wanted to name him Spudnick entirely, and Bob wanted to name him Bob jr, so they argued before smg2 just came up with the idea to name him spudbob, and then they later changed it to Spudbo bc spudbob sounded too much like SpongeBob. Plus Spudbo sounded cute
-His full name is Spudbo Bobowski since smg1 doesn’t have a last name
-smg1 and 2 made his cloak and Bob gave him his swords(he wanted to give him real swords but didn’t bc he didn’t want a dead child), smg1 has remade the same cloak multiple times bc of the first fact on the list.
-Ironically Bob is his fav despite him not being as active in his life as Smg1 (poor smg1 lol)
#smg4#smg1#smg4 smg1#smg4 fanart#smg2#smg4 smg2#smg4 au#smg4 Fankid#fankid#smg4 bob bobowski#smg4 bob#bob bobowski#bob x smg1#smg1 x bob#bomg1#smg4 trashcube#trashcube#rappercube#smg4 rappercube#smg4 bomg1#fanchild#fanchildren are wild man
22 notes
·
View notes
Text
Timothy Snyder At Thinking About...:
1. Do not obey in advance. Most of the power of authoritarianism is freely given. In times like these, individuals think ahead about what a more repressive government will want, and then offer themselves without being asked. A citizen who adapts in this way is teaching power what it can do. 2. Defend institutions. It is institutions that help us to preserve decency. They need our help as well. Do not speak of "our institutions" unless you make them yours by acting on their behalf. Institutions do not protect themselves. They fall one after the other unless each is defended from the beginning. So choose an institution you care about -- a court, a newspaper, a law, a labor union -- and take its side. 3. Beware the one-party state. The parties that remade states and suppressed rivals were not omnipotent from the start. They exploited a historic moment to make political life impossible for their opponents. So support the multiple-party system and defend the rules of democratic elections. Vote in local and state elections while you can. Consider running for office. 4. Take responsibility for the face of the world. The symbols of today enable the reality of tomorrow. Notice the swastikas and the other signs of hate. Do not look away, and do not get used to them. Remove them yourself and set an example for others to do so. 5. Remember professional ethics. When political leaders set a negative example, professional commitments to just practice become more important. It is hard to subvert a rule-of-law state without lawyers, or to hold show trials without judges. Authoritarians need obedient civil servants, and concentration camp directors seek businessmen interested in cheap labor. 6. Be wary of paramilitaries. When the men with guns who have always claimed to be against the system start wearing uniforms and marching with torches and pictures of a leader, the end is nigh. When the pro-leader paramilitary and the official police and military intermingle, the end has come.
[...] 10. Believe in truth. To abandon facts is to abandon freedom. If nothing is true, then no one can criticize power, because there is no basis upon which to do so. If nothing is true, then all is spectacle. The biggest wallet pays for the most blinding lights. 11. Investigate. Figure things out for yourself. Spend more time with long articles. Subsidize investigative journalism by subscribing to print media. Realize that some of what is on the internet is there to harm you. Learn about sites that investigate propaganda campaigns (some of which come from abroad). Take responsibility for what you communicate with others. [...]
14. Establish a private life. Nastier rulers will use what they know about you to push you around. Scrub your computer of malware on a regular basis. Remember that email is skywriting. Consider using alternative forms of the internet, or simply using it less. Have personal exchanges in person. For the same reason, resolve any legal trouble. Tyrants seek the hook on which to hang you. Try not to have hooks. 15. Contribute to good causes. Be active in organizations, political or not, that express your own view of life. Pick a charity or two and set up autopay. Then you will have made a free choice that supports civil society and helps others to do good. 16. Learn from peers in other countries. Keep up your friendships abroad, or make new friends in other countries. The present difficulties in the United States are an element of a larger trend. And no country is going to find a solution by itself. Make sure you and your family have passports.
Timothy Snyder wrote in his Substack the twenty lessons on combatting tyranny that were in his book On Tyranny.
Key lessons:
1 Do not obey in advance.
2 Defend institutions.
3 Beware the one-party state.
10 Believe in truth.
15 Contribute to good causes
36 notes
·
View notes
Text
good evening mothers and fuckers of the jury today i bring: Amphoreus Is A Neural Network
my credentials: i’m a first year CS student in 2025.
if y’all’ve been on hsrtwt in the past few days and watching leak after leak come out, then you probably know what i’m yapping about. if not, check this, this, this, and this out.
if you’d rather wait for 3.4 to come out, this is your chance to scroll. rest of y’all are with me lets go gamers
to summarise the 3.4 leaks, lygus and cyrene are apparently running tests on phainon to make the perfect lord ravager, and phainon’s been through 33550336 loops (girl help him wtf) by now. in each loop, he has to watch everyone die over and over again, and phainon, obvi, cannot remember anything. each loop, he’s a complete blank slate, ready to be traumatised over and over again. lygus keeps track of each loop, and keeps refining the data he puts in at the start of each timeloop to remove the ‘imperfections’ from the previous loop that were corrupting his experiments.
ok anyways this is not about this shit we’re here to talk about why amphoreus is a neural network.
all of us here hate ai so i’m pretty sure you know the basic strokes of how it works, but if you don’t, then here’s a simple explanation: a neural network works based on input data. there’s many methods to training a machine, but the most generalised ones are the supervised vs the unsupervised models. how they work is what’s on the lid: supervised models mean that the input data is clearly labeled, and unsupervised models mean the input data is not labeled, which forces the ML algorithm to identify data on its own. based on what we know, i’m inclined to think that lygus is probably using a supervised model each time by removing outlier data and/or noise.
wonderful, let’s talk about mydei now. y’all’ve probably seen a bunch of theories and leaks, but mydei’s highly likely to be a glitch in the system, or even worse, might be a virus that someone’s trying to use to break everyone out of this loop. between all of the theories i’ve seen, the one that connects mydei to the amphoreus loop is the theory that he’s a type of fileless malware.
Tweet ref: https://x.com/tts_maruadelei/status/1932082549217751271
much like the other chrysos heirs, mydei doesn’t actually exist, but let me say: ain’t it interesting how mydei, the demigod of strife, who should have risen to be a titan that governed disputes, is the one who caused glitches in lygus’ system during the forgotten years?
let’s go back to the theory for a second: fileless attacks, simplified, operate based off of memory alone, which makes it much, much harder to detect compared to normal malware and viruses in a computer system. these fileless attacks can manifest in multiple ways, and one of those ways is a Distributed Denial of Service attack, aka, the infamous DDoS attack. DDoS attacks are among the most common cyberattacks of the modern century, and involve ‘botting’, where multiple bots attack one system to overwhelm the system with a high volume of requests.
the idea of ‘overwhelming’ a system can come in the form of exhausting resources like bandwidth, the Central Processing Unit (CPU) and, most importantly, the Random Access Memory (RAM). you know, the RAM being where most fileless malware operates out of. i’m sure you see where i’m going with this.
for more psychic damage, there’s a type of attack called a ‘buffer overrun’ or ‘buffer overflow’. wikipedia defines data buffers as regions of memory that store data temporarily while it’s being moved from one place to another. a ‘buffer overflow’ is a type of DDoS (SIGHS) attack in which data in the buffer exceeds the storage capacity and flows into the following memory location, and corrupts the data in the secondary memory locations, and are the most common DDoS attack styles. sound familiar?
bringing allllll of this back to amphoreus, i wouldn’t be too surprised if mydei’s older versions gained sentience, and started botting lygus’ AI/neural network and caused a DDoS attack, which caused his saves to be completely wiped due to a buffer overflow. thank u for listening can 3.4 hurry Up.
#agni yaps#Honkai Star Rail#Honkai Star Rail theory#HSR theory#HSR 3.4#3.4 leaks#hsr leaks#Mydeimos#Mydei#Lygus#Cyrene
9 notes
·
View notes