#software users email database
Explore tagged Tumblr posts
Text
Caleb Ecarma and Judd Legum at Popular Information:
Several of Elon Musk’s associates installed at the Office of Personnel Management (OPM) have received unprecedented access to federal human resources databases containing sensitive personal information for millions of federal employees. According to two members of OPM staff with direct knowledge, the Musk team running OPM has the ability to extract information from databases that store medical histories, personally identifiable information, workplace evaluations, and other private data. The staffers spoke on the condition of anonymity because they were not authorized to speak publicly and feared professional retaliation. Musk Watch also reviewed internal OPM correspondence confirming that expansive access to the database was provided to Musk associates.
The arrangement presents acute privacy and security risks, one of the OPM staffers said. Among the government outsiders granted entry to the OPM databases is University of California Berkeley student Akash Bobba, a software engineer who graduated high school less than three years ago. He previously interned at Meta and Palantir, a technology firm chaired by Musk-ally and fellow billionaire Peter Thiel. Edward Coristine, another 2022 high school graduate and former software engineering intern at Musk’s Neuralink, has also been given access to the databases.
Other Musk underlings embedded at OPM following President Donald Trump’s inauguration include the agency’s new chief of staff, Amanda Scales, who until January was a human resources staffer at xAI, Musk’s artificial intelligence firm, and Brian Bjelde, who has spent the past 21 years at Musk's SpaceX, including the last 10 leading the human resources department. They are joined by Gavin Kliger, a former Twitter software engineer serving as a special advisor to the director of OPM, and Riccardo Biasini, a former software engineer at Musk’s tunneling venture, the Boring Company. OPM did not respond to a request for comment. Shortly after Trump took office, OPM installed Greg Hogan to serve as its new chief information officer (CIO). Hogan was tapped to replace OPM CIO Melvin Brown, who had accepted the job less than a month ago. The civil servants who oversee the OPM’s information technology services were then instructed to provide access to Musk's associates, according to the OPM staffers who spoke to Musk Watch. One of the OPM staffers received an email from the agency’s new leadership instructing them to give Musk’s team “access [to] the system as an admin user" and "code read and write permissions." “They have access to the code itself, which means they can make updates to anything that they want,” the staffer explained. USAJOBS, the federal government’s official hiring site, was one of the systems that Musk's associates were given access to. The database stores personal information — Social Security numbers, home addresses, employment records — provided by private individuals who have applied for federal jobs, regardless of whether the applicants went on to work for the government. Musk’s aides were also given access to the OPM’s Enterprise Human Resources Integration (EHRI) system. Contained within the EHRI are the Social Security numbers, dates of birth, salaries, home addresses, and job descriptions of all civil government workers, along with any disciplinary actions they have faced. “They’re looking through all the position descriptions… to remove folks,” one of the OPM staffers said of Musk’s team. “This is how they found all these DEI offices and had them removed — [by] reviewing position description level data.” Other databases Musk’s team has access to include USA Staffing, an onboarding system; USA Performance, a job performance review site; and HI, which the government uses to manage employee health care. “The health insurance one scares me because it's HIPAA [protected] information, but they have access to all this stuff,” the OPM staffer noted.
[...] A new server being used to control these databases has been placed in a conference room that Musk’s team is using as their command center, according to an OPM staffer. The staffer described the server as a piece of commercial hardware they believed was not obtained through the proper federal procurement process. There is a��legal requirement that the installation of a new server undergo a Privacy Impact Assessment (PIA), a formal process to ensure the change would not create any security vulnerabilities. But in this instance, the staff believes there was no PIA. “So this application and corresponding hardware are illegally operating,” they added. On Friday, Reuters reported that some senior civil servants have been blocked from accessing the EHRI and other OPM systems, making it difficult for career OPM employees to know what Musk’s team has been examining or modifying. In the same report, the outlet revealed the team had moved sofa beds into the agency's headquarters to continue their work around the clock.
This should be a major national news scandal.
Elon Musk and the underlings he put in place at the Office of Personnel Management (OPM) have jeopardized data privacy and national security.
#Elon Musk#DOGE#Department of Government Efficiency#Trump Administration#Office of Personnel Management#USA Peformance#HIPAA#Enterprise Human Resources Integration#Amanda Scales#Data Breach#Privacy Impact Assessment#Data Privacy#Musk Coup
9 notes
·
View notes
Text

Ubuntu is a popular open-source operating system based on the Linux kernel. It's known for its user-friendliness, stability, and security, making it a great choice for both beginners and experienced users. Ubuntu can be used for a variety of purposes, including:
Key Features and Uses of Ubuntu:
Desktop Environment: Ubuntu offers a modern, intuitive desktop environment that is easy to navigate. It comes with a set of pre-installed applications for everyday tasks like web browsing, email, and office productivity.
Development: Ubuntu is widely used by developers due to its robust development tools, package management system, and support for programming languages like Python, Java, and C++.
Servers: Ubuntu Server is a popular choice for hosting websites, databases, and other server applications. It's known for its performance, security, and ease of use.
Cloud Computing: Ubuntu is a preferred operating system for cloud environments, supporting platforms like OpenStack and Kubernetes for managing cloud infrastructure.
Education: Ubuntu is used in educational institutions for teaching computer science and IT courses. It's free and has a vast repository of educational software.
Customization: Users can customize their Ubuntu installation to fit their specific needs, with a variety of desktop environments, themes, and software available.
Installing Ubuntu on Windows:
The image you shared shows that you are installing Ubuntu using the Windows Subsystem for Linux (WSL). This allows you to run Ubuntu natively on your Windows machine, giving you the best of both worlds.
Benefits of Ubuntu:
Free and Open-Source: Ubuntu is free to use and open-source, meaning anyone can contribute to its development.
Regular Updates: Ubuntu receives regular updates to ensure security and performance.
Large Community: Ubuntu has a large, active community that provides support and contributes to its development.
4 notes
·
View notes
Text
As anticipated, here are my extensive red string notes from the pilot:




God knows how relevant any of this will turn out to be, but I'm nothing if not a collector of trivial information
Very long text beneath the cut:
Page 1
The Magnus Protocol Pilot 10/25/23
Characters (in order of appearance)
Alice Dyer -O.I.A.R. employee -Dated Sam in uni -Jokester -Training Sam -Gets along with Colin
Teddy Vaughn -Retiring from the O.I.A.R. after 4 (?) years -Going into insurance field
Colin Becher -O.I.A.R. IT Manager -Vegetarian 🥬 -On the hook of "his nibs" (boss, male) -Sensitive about FR3-d1 app development, communicates w/politicians, trying for 2 years -Only gets along w/Alice -Knows computers are listening -Jokes about being killed
Lena Kelley -O.I.A.R. Team/Department Manager -Authoritative, follows protocol -Doesn't think Gwen is qualified for management
Gwendolyn Bouchard -O.I.A.R. employee -Backlog of casework -Dislikes Lena, wants her job -Dedicated to detail -Accused of nepotism by Alice -Thinks current job is beneath her -"Not like most people." *static*
Samama Khalid (Sam) -New O.I.A.R. employee -Dated Alice in uni -Wanting to 'get back on his feet' -Familiar with TMI -Didn't know what the Incidents were before hire!!
Page 2
Pilot notes con. 10/25/23
Listening Tech - Turns on by itself 💡
Dated computers (O.I.A.R.)
"Manager's speakerphone" (Lena's)
CCTV (O.I.A.R. breakroom?)
Cell phone (Alice's)
*O.I.A.R. formed in 70s? Accor. to Alice*
*Response Department no longer exists*
Still in onboarding paperwork, "Response 121"
Sam ticked this box
Tech Specs
O.S. = Windows NT 4.0 (modified) -Extended support for this O.S. was ended Dec. 31, 2004 IRL -Runs on workstations connected by LAN -Similar GUI to 95; comes w/Internet Explorer
FR3-d1 -Custom research software circa mid-90s -Flags Incidents and creates a database -Can search private/protected sources (email) -Alice claims no one has understood its workings for 15 years -Written in German source code
*1 Year = Average Employee Stay*
Page 3
Pilot notes con. 10/25/23
Classification System
Used in FR3-d1's database
Structure: CATXRXXXXX-XXXXXXXX-XXXXXXXX
CATXRX -> From reference table (CAT = Category?) First four digits -> Main subject of Incident DPHW (?) Next eight digits -> Date of Incident Last eight digits -> Current date
Example: CAT2RC1157-12052022-13012024* -First one we hear they file. "1157" is the "DPHW" for "dolls, watching."
*Jan. 13, 2024 is the date of Sam's onboarding/training (after Teddy's going-away party)
*as listed in transcript; in-show, it's quoted as 22102023, or Oct. 22, 2023
Page 4
Pilot notes (con.) 10/25/23
FR3-d1's Voice to Text/Text to Speech
Voices (named by Alice, which Gwen dislikes):
Neil = Alex
Chester = Jonny
(those two most common)
Augustus = ?
Neil's Incident
Occurs in "Cyberspace" via the transcript
"I'm so sorry. I should have listened. I just couldn't face the thought of the rest of my life never hearing him again, I had to try." First lines 😢
Email from Harriet Winstead to Darla Winstead, May 12, 2022
Recitations *can* be paused by pressing "space"!
Chester's Incident
Also occurs in "Cyberspace"
Topic: Magnus Institute Ruins.
On forum, user RedCanary, begins April 10, 2022. Explored 4/19-20/22.
Third floor gone. No old papers.
Suspicious, occult (?) graffiti, stains (!)
Took box with strange symbols (same as ones on walls/floors)
4/30/22 Posted image of gore/eyes, possibly of themself. Banned + did not return.
Page 5
Pilot notes con. 10/25/23
Early release video Case #: CAT1RA1353-03102023-22102024(listed as 202"3" on Patreon)
Video was posted 10/22/23.
Listed as "Incident" on Patreon.
According to transcript, the O.I.A.R. offices are located in Royal Mint Court.
Johson (sic) Smirke Building
Main building.
5 storeys, Grade 2 listed.
Designed by James Johnson, but constructed between 1807-1812 by Robert Smirke after Johnson died. To be used for mint.
Entrance lodge also built by Smirke, in front of building.
Page 6
Pilot - Public Release -TMAGP#001
Changes:
Sam's first incident number - today's date
CAT2RC1157-12052022-13012024 -> CAT2RC1157-12052022-09012024
Voice (first incident)
Neil -> *Norris*
Minor word/date changes in incidents.
Minor line read differences.
Descriptions of Incidents in new transcript:
Norris': CAT1RBC5257-12052022-09012024 Reanimation (Partial) -/- Regret [Email]
Chester's: CAT23RAB2155-10042022-09012024 Transformation (Eyes) -/- Trespass [chat log]
#will add alt text shortly#also keep in mind a lot of this was written back in October - see the last page for recent changes#tmagp#the magnus protocol#tmagp spoilers#im super stoked to have figured out the royal mint court thing
20 notes
·
View notes
Text
📂 Say Goodbye to Paper Binders — Welcome to LOV111VOL!
Is your office still relying on outdated paper binders? Struggling to find files or worried about losing important documents? It’s time to go digital with LOV111VOL — the all-in-one document management and archiving software built for modern businesses.
🖥️ Meet LOV111VOL: Your New Digital Binder for Smarter, Faster Work
LOV111VOL is a powerful, intuitive application that replaces the traditional office binder in just 50 seconds after download. It helps you manage documents, projects, and team communication in one centralized location — perfect for both individual users and collaborative teams.
⭐ Key Features of LOV111VOL:
✅ Three Types of Binders:
Private: Access limited to selected users
Public: Viewable by anyone, editable with permission
Hybrid (Private-Public): Flexible access control
✅ Real-Time Team Collaboration ✅ Multiple Database Options: SQLite, MySQL, MSSQL ✅ Track Document Changes and Versions ✅ Advanced Search with Tags and Filters ✅ Secure File Sharing and Access Management ✅ Built-in Email Client, Calendar, Task Manager, Help Desk, and More!
💰 Save Time & Cut Costs:
Boost productivity by saving up to 80% of your time
Eliminate the clutter and cost of paper documents
No need for multiple apps — everything you need is in one platform
🌐 Flexible Deployment:
Whether you're online or offline (LAN), LOV111VOL works seamlessly. It even functions without the internet, making it perfect for secure or internal environments.
👉 Try it now — absolutely FREE for a single user! Get started in 50 seconds: lov111vol.com
Facebook / LinkedIn / Instagram: 📁 Still using paper binders at the office? It’s time to upgrade. Meet LOV111VOL — your all-in-one digital binder and document archiving solution. ✅ Save up to 80% of your time ✅ Free for individual users ✅ Start working in 50 seconds Go digital today → lov111vol.com
Twitter (X): Ditch paper binders 📂 Try LOV111VOL — smart document management in just 50 seconds. ✅ Free for 1 user ✅ Work solo or with teams Try it now → lov111vol.com
#Document Management#Document Archiving#Digital Binder#Office Productivity#Business Software#Paperless Office#Team Collaboration#File Sharing
2 notes
·
View notes
Text
Role of AI and Automation in Modern CRM Software
Modern CRM systems are no longer just about storing contact information. Today, businesses expect their CRM to predict behavior, streamline communication, and drive efficiency — and that’s exactly what AI and automation bring to the table.

Here’s how AI and automation are transforming the CRM landscape:
1. Predictive Lead Scoring
Uses historical customer data to rank leads by conversion probability
Prioritizes outreach efforts based on buying signals
Reduces time spent on low-potential leads
Improves sales team performance and ROI
2. Smart Sales Forecasting
Analyzes trends, seasonality, and deal history to forecast revenue
Updates projections in real-time based on new data
Helps sales managers set realistic targets and resource plans
Supports dynamic pipeline adjustments
3. Automated Customer Support
AI-powered chatbots handle FAQs and common issues 24/7
Sentiment analysis flags negative interactions for human follow-up
Automated ticket routing ensures faster resolution
Reduces support workload and boosts satisfaction
4. Personalized Customer Journeys
Machine learning tailors emails, offers, and messages per user behavior
Automation triggers based on milestones or inactivity
Custom workflows guide users through onboarding, upgrades, or renewals
Improves customer engagement and retention
5. Data Cleanup and Enrichment
AI tools detect duplicate records and outdated info
Automatically update fields from verified external sources
Maintains a clean, high-quality CRM database
Supports better segmentation and targeting
6. Workflow Automation Across Departments
Automates repetitive tasks like task assignments, follow-ups, and alerts
Links CRM actions with ERP, HR, or ticketing systems
Keeps all teams aligned without manual intervention
Custom CRM solutions can integrate automation tailored to your exact process
7. Voice and Natural Language Processing (NLP)
Transcribes sales calls and highlights key insights
Enables voice-driven commands within CRM platforms
Extracts data from emails or chat for automatic entry
Enhances productivity for on-the-go users
#AICRM#AutomationInCRM#CRMSolutions#SmartCRM#CRMDevelopment#AIinBusiness#TechDrivenSales#CustomerSupportAutomation#CRMIntegration#DigitalCRM
2 notes
·
View notes
Text
Engineers for Elon Musk’s so-called Department of Government Efficiency, or DOGE, are working on new software that could assist mass firings of federal workers across government, sources tell WIRED.
The software, called AutoRIF, which stands for Automated Reduction in Force, was first developed by the Department of Defense more than two decades ago. Since then, it’s been updated several times and used by a variety of agencies to expedite reductions in workforce. Screenshots of internal databases reviewed by WIRED show that DOGE operatives have accessed AutoRIF and appear to be editing its code. There is a repository in the Office of Personnel Management’s (OPM) enterprise GitHub system titled “autorif” in a space created specifically for the director’s office—where Musk associates have taken charge—soon after Trump took office. Changes were made as recently as this weekend.
So far, federal agency firings have been conducted manually, with HR officials combing through employee registries and lists provided by managers, sources tell WIRED. Probationary employees—those who were recently hired, promoted, or otherwise changed roles—have been targeted first, as they lack certain civil service protections that would make them harder to fire. Thousands of workers have been terminated over the last few weeks across multiple agencies. With new software and the use of AI, some government employees fear that large-scale terminations could roll out even more quickly.
While DOGE could use AutoRIF as the DOD built it, multiple OPM sources speculated that the Musk-affiliated engineers could be building their own software on top of, or using code from, AutoRIF. In screenshots viewed by WIRED, Riccardo Biasini, a former engineer at Tesla and a director at The Boring Company, has seemingly been tasked with pruning AutoRIF on GitHub, with his name attached to the repository. “Remove obsolete versions of autorif,” one file description authored by a user with Biasini’s username on GitHub says.
Biasini has also been listed as the main point of contact for the government-wide email system created by the Trump administration from within OPM to solicit resignation emails from federal workers.
OPM did not immediately respond to requests for comment from WIRED.
In order to conduct RIFs, government HR officials are required to create lists ranking employees who may be subject to firings. AutoRIF does that automatically, a former government HR official tells WIRED. “However, even with the use of any automated system, the OPM guidance says all data has to be confirmed manually and that employees (or their representative) are allowed to examine the registers.” It’s not immediately clear if AutoRIF’s capabilities have been altered either by the Defense Department or DOGE.
The revelation that DOGE is working on AutoRIF comes as it seemingly prepares for its second major round of firings. On Saturday evening, government workers received yet another email purportedly from OPM demanding that they reply detailing what they accomplished in the last week. Some agencies, like the FBI, asked that employees not respond to the message. In a meeting with HR officials on Monday, OPM told agencies they could ignore the email.
In these emails, government workers were asked to lay out five bullet points explaining their top work achievements of the last week. On Monday, NBC News reported that this information would be fed into an unspecified large language model that would assess whether an employee was necessary.
Before the first round of probationary firings, Centers for Disease Control managers were tasked with marking workers they deemed as “mission critical” and then sending a list of them up the chain of command ahead of firings, a CDC source tells WIRED.
“CDC went through a very, very deliberate effort to characterize our probationary employees as mission critical or not, and that way we could keep those that would have real impacts to the mission should they get terminated,” they say. “None of that was taken into account. They just sent us a list and said, ‘Terminate these employees effective immediately.’”
3 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
10 Web Hosting Terms You Should Know Before Building a Website

If you're planning to create a website, understanding web hosting is essential. If you're looking for a website hosting company in Gurgaon, knowing these terms will help you choose the right provider. Web hosting provides the server space and technology needed to make your website accessible on the internet. However, the world of web hosting can be full of technical jargon that might seem confusing at first. To make informed decisions, here are 10 key web hosting terms you should know:
Control Panel A control panel is a user-friendly interface that allows you to manage your server settings without needing extensive technical skills. It simplifies the process of managing your website, offering tools to configure domains, emails, databases, and security settings. Popular control panels include cPanel and Plesk, which let you handle server tasks through a graphical interface rather than typing complex commands.
Bandwidth Limit Bandwidth refers to the amount of data your website can transfer to and from the server each month. Hosting providers, like a Web hosting company in Gurgaon, set a bandwidth limit to ensure resources are distributed fairly among customers. If your site reaches this limit, your hosting provider might slow down access (throttle it) or even temporarily suspend your site until the next billing cycle. Knowing your bandwidth needs can help you choose the right hosting plan.
Managed Hosting Managed hosting is a type of service where the hosting provider handles essential maintenance tasks for you, such as software updates, security monitoring, and backups. This can save time and effort, especially for those who are less experienced with server management. Managed hosting is an excellent option for businesses that want to concentrate on their main activities while entrusting technical tasks to professionals.
IP Address An IP address is a unique set of numbers assigned to each device connected to the internet, including your hosting server. It acts as an identifier, allowing computers to locate and communicate with each other. When you purchase a hosting plan, your server will be assigned an IP address, which you can use to access your website files, manage the server, and set up remote connections.
Uptime Uptime is a measure of the reliability of your hosting service. It represents the percentage of time that the server is online and accessible. Most reliable providers aim for an uptime of 99.9% or higher. A high uptime rate is crucial because frequent downtime can result in lost traffic and frustrated visitors. Some hosts offer an uptime guarantee, promising compensation if their service falls below the agreed uptime rate.
Shared Hosting
It is an affordable hosting option where multiple websites utilize the same server. Since the cost of running the server is divided among all users, shared hosting are generally inexpensive. However, because resources are shared, high traffic on one website can affect the performance of others on the same server. This makes shared hosting ideal for small websites or those just starting.
VPS (Virtual Private Server) A VPS, or Virtual Private Server, provides a more dedicated portion of server resources compared to shared hosting. Although multiple users still share the physical server, each VPS operates independently, with allocated CPU, RAM, and storage. VPS hosting is a good middle-ground option for websites that need more power and customization than shared hosting can provide, but without the higher cost of a dedicated server.
Dedicated Hosting With dedicated hosting, you have an entire server reserved solely for your website. This means you have full control over all resources, including CPU, memory, and storage, without any competition from other users. Dedicated hosting is the most powerful but also the most expensive option. It’s often used by large businesses or websites with high traffic that require top performance and customization.
Disk Spaced
Disk space, or storage space, refers to the amount of space on a server available for storing your website's files, databases, and other content. The two main types of storage drives are HDDs (Hard Disk Drives) and SSDs (Solid State Drives), with SSDs offering faster performance. When choosing a hosting plan, consider the storage needs of your website, especially if you plan to host high-resolution images, videos, or large files.
11. SSL (Secure Sockets Layer) SSL is a security protocol that encrypts data transferred between your website and its visitors, keeping information secure. To activate SSL, you'll need an SSL certificate, which enables HTTPS for your website, signifying a secure connection. This is particularly crucial for websites that manage sensitive data, like login credentials or payment information. Many web hosting providers in Gurgaon now offer SSL certificates as part of their hosting packages
Conclusion Understanding these web hosting terms will help you make better decisions when setting up your website. Choosing the right hosting plan and knowing the features available can save you time, money, and frustration in the long run. Whether you’re just starting with a small website or launching a large-scale project, familiarity with these terms will make the process smoother and more manageable.
If you want to know more about our services, please feel free to contact us at:
Mobile: 08826196688 or 9910248322
Email: [email protected]
Website: www.deltait.co.in
#website hosting company in Gurgaon#Web hosting company in Gurgaon#web hosting providers in Gurgaon#delta web services
2 notes
·
View notes
Text
What Is Linux Web Hosting? A Beginner's Guide
In the ever-evolving digital landscape, the choice of web hosting can significantly impact your online presence. One of the most popular options available is Linux web hosting. But what exactly does it entail, and why is it so widely preferred? This beginner’s guide aims to demystify Linux web hosting, its features, benefits, and how it stands against other hosting types.
Introduction to Web Hosting
Web hosting is a fundamental service that enables individuals and organisations to make their websites accessible on the internet. When you create a website, it consists of numerous files, such as HTML, images, and databases, which need to be stored on a server. A web host provides the server space and connectivity required for these files to be accessed by users online.
There are several types of web hosting, each designed to cater to different needs and budgets. Shared hosting is a cost-effective option where multiple websites share the same server resources. Virtual Private Server (VPS) hosting offers a middle ground, providing dedicated portions of a server for greater performance and control. Dedicated hosting provides an entire server exclusively for one website, ensuring maximum performance but at a higher cost. Cloud hosting uses multiple servers to balance the load and maximise uptime, offering a scalable solution for growing websites.
Web hosting services also include various features to enhance the performance and security of your website. These can range from basic offerings like email accounts and website builders to more advanced features like SSL certificates, automated backups, and DDoS protection. The choice of web hosting can significantly influence your website’s speed, security, and reliability, making it crucial to choose a solution that aligns with your specific requirements.
Understanding the different types of web hosting and the features they offer can help you make an informed decision that suits your needs. Whether you are running a personal blog, a small business website, or a large e-commerce platform, selecting the right web hosting service is a critical step in establishing a successful online presence.
What Is Linux Web Hosting?
Linux web hosting is a type of web hosting service that utilises the Linux operating system to manage and serve websites. Renowned for its open-source nature, Linux provides a stable and secure platform that supports a wide array of programming languages and databases, making it a favoured choice amongst developers and businesses. This hosting environment typically includes support for popular technologies such as Apache web servers, MySQL databases, and PHP scripting, which are integral to modern website development.
One of the distinguishing features of Linux web hosting is its cost-effectiveness. As an open-source system, Linux eliminates the need for costly licensing fees associated with proprietary software, thereby reducing overall hosting expenses. This makes it an attractive option for individuals and organisations operating on a budget.
Moreover, Linux is celebrated for its robust performance and high stability. Websites hosted on Linux servers experience less downtime and faster loading times, which are critical factors for maintaining user engagement and search engine rankings. The operating system’s extensive community of developers continuously works on updates and improvements, ensuring that Linux remains a cutting-edge choice for web hosting.
Linux web hosting also offers considerable flexibility and customisation options. Users have the freedom to configure their hosting environment to meet specific needs, whether they are running simple static websites or complex dynamic applications. This versatility extends to compatibility with various content management systems (CMS) like WordPress, Joomla, and Drupal, which often perform optimally on Linux servers.
In summary, Linux web hosting provides a reliable, secure, and cost-effective solution that caters to a diverse range of web hosting requirements. Its compatibility with essential web technologies and its inherent flexibility make it a preferred choice for many web developers and site owners.
Key Benefits of Linux Web Hosting
Linux web hosting offers several compelling advantages that contribute to its widespread adoption. One of its primary benefits is cost-effectiveness. The open-source nature of Linux eliminates the need for expensive licensing fees, allowing users to allocate their resources more efficiently. This makes it an ideal choice for individuals and organisations with budget constraints. Additionally, Linux is celebrated for its high stability and robust performance. Websites hosted on Linux servers often experience minimal downtime and faster loading speeds, which are essential for maintaining user engagement and achieving favourable search engine rankings.
Another significant benefit is the extensive community support that comes with Linux. The active community of developers and enthusiasts continuously works on updates, patches, and security enhancements, ensuring that Linux remains a secure and reliable platform for web hosting. This ongoing development also means that any issues or vulnerabilities are promptly addressed, offering peace of mind for website owners.
Flexibility is another key advantage of Linux web hosting. The operating system supports a wide range of programming languages, including PHP, Python, and Ruby, making it suitable for various types of web applications. Additionally, Linux servers are highly customisable, allowing users to configure their environment to meet specific needs, whether they are running simple static sites or complex dynamic applications.
Moreover, Linux web hosting is highly compatible with popular content management systems (CMS) like WordPress, Joomla, and Drupal. This compatibility ensures that users can easily deploy and manage their websites using these platforms, benefiting from their extensive plugin and theme ecosystems.
Lastly, Linux's superior security features are worth noting. The operating system is inherently secure and offers various built-in security measures. When combined with best practices such as regular updates and strong passwords, Linux web hosting provides a highly secure environment for any website.
Understanding Linux Distributions in Web Hosting
Linux comes in a variety of distributions, each tailored to meet specific needs and preferences. Among the most popular for web hosting are Ubuntu, CentOS, and Debian. Ubuntu is celebrated for its ease of use and extensive community support, making it a great choice for those new to Linux. CentOS, a favourite in enterprise environments, offers impressive stability and long-term support, which ensures a dependable hosting experience. Debian stands out with its robust package management system and commitment to open-source principles, providing a reliable and secure foundation.
Each distribution brings its own strengths to the table. For example, Ubuntu’s frequent updates ensure access to the latest features and security patches, while CentOS’s extended support cycles make it a solid choice for those requiring a stable, long-term hosting environment. Debian’s extensive repository of packages and minimalistic approach offers flexibility and customisation, catering to the needs of experienced users.
Selecting the right Linux distribution largely depends on your specific requirements and technical expertise. If you prioritise user-friendliness and a wealth of resources for troubleshooting, Ubuntu might be the ideal pick. On the other hand, if you need a rock-solid, stable platform for an enterprise-level application, CentOS could be more appropriate. For those seeking maximum control and a commitment to open-source principles, Debian is a compelling option.
Ultimately, understanding the nuances of these distributions will enable you to choose a Linux environment that aligns with your web hosting needs, ensuring optimal performance and reliability.
Linux Hosting vs Windows Hosting: A Comparative Analysis
When evaluating Linux hosting against Windows hosting, several critical factors come into play. Cost is a significant differentiator; Linux hosting is generally more affordable due to its open-source nature, which eliminates the need for expensive licensing fees. In contrast, Windows hosting often incurs additional costs related to proprietary software licenses.
Compatibility is another important aspect to consider. Linux hosting is renowned for its compatibility with a broad array of open-source software and applications, including popular content management systems like WordPress, Joomla, and Magento. These platforms typically perform better on Linux servers due to optimised server configurations. On the other hand, Windows hosting is the go-to option for websites that rely on Microsoft-specific technologies such as ASP.NET, MSSQL, and other .NET frameworks.
Performance and stability are also crucial elements in this comparison. Linux hosting often provides superior uptime and faster loading speeds due to the lightweight nature of the Linux operating system. The robust performance of Linux servers is further enhanced by the active community that continuously works on optimisations and security patches. Windows hosting, while also reliable, can sometimes be more resource-intensive, potentially affecting performance.
Customisation and control levels differ significantly between the two. Linux offers greater flexibility and customisation options, allowing users to tweak server settings and configurations extensively. This level of control is particularly beneficial for developers who need a tailored hosting environment. Conversely, Windows hosting is typically easier to manage for those familiar with the Windows operating system but may offer less flexibility in terms of customisation.
Security measures also vary between Linux and Windows hosting. Linux is often praised for its strong security features, which are bolstered by a large community dedicated to promptly addressing vulnerabilities. While Windows hosting is secure, it may require more frequent updates and maintenance to ensure the same level of protection.
Common Use Cases for Linux Web Hosting
Linux web hosting is versatile and caters to a broad range of applications, making it a popular choice across various sectors. One of the most common use cases is hosting blogs and personal websites, particularly those built on platforms like WordPress. The open-source nature of Linux and its compatibility with PHP make it an ideal environment for WordPress, which powers a significant portion of the web.
E-commerce websites also benefit greatly from Linux web hosting. Solutions like Magento, PrestaShop, and OpenCart often perform better on Linux servers due to their need for a robust, secure, and scalable hosting environment. The flexibility to configure server settings allows online store owners to optimise performance and ensure a smooth shopping experience for their customers.
Content Management Systems (CMS) such as Joomla and Drupal are another prime use case. These systems require reliable and flexible hosting solutions to manage complex websites with large amounts of content. Linux's support for various databases and scripting languages ensures seamless integration and optimal performance for CMS-based sites.
Developers frequently turn to Linux web hosting for custom web applications. The operating system supports a variety of programming languages, including Python, Ruby, and Perl, making it suitable for a wide array of development projects. Its command-line interface and extensive package repositories allow developers to install and manage software efficiently.
Additionally, Linux web hosting is commonly used for educational and non-profit websites. The low cost and high reliability make it a practical choice for schools, universities, and charitable organisations that need a dependable online presence without breaking the bank.
Setting Up a Linux Web Hosting Environment
Setting up a Linux web hosting environment can be straightforward with the right approach. Begin by selecting a reputable hosting provider that offers Linux-based plans. After signing up, you'll typically be granted access to a control panel, such as cPanel or Plesk, which simplifies the management of your hosting environment. Through the control panel, you can manage files, databases, email accounts, and more.
Next, if you're using a content management system (CMS) like WordPress, Joomla, or Drupal, you can often find one-click installation options within the control panel. This feature makes it easy to get your website up and running quickly. Additionally, ensure that you configure your domain name to point to your new hosting server, which usually involves updating your domain's DNS settings.
For those who prefer more control or are comfortable using the command line, you can manually set up your web server using SSH access. This method allows you to install and configure web server software like Apache or Nginx, as well as databases such as MySQL or PostgreSQL.
Regardless of the setup method you choose, it's crucial to secure your server from the outset. This includes setting up a firewall, enabling SSH key authentication for secure access, and regularly updating all software to protect against vulnerabilities. Regularly monitoring your server's performance and security logs can help you stay ahead of potential issues, ensuring a stable and secure hosting environment for your website.
Security Best Practices for Linux Web Hosting
Securing your Linux web hosting environment is paramount to safeguarding your website against potential threats. Begin by ensuring your server software and all installed applications are up to date. Regular updates often include patches for security vulnerabilities, making this a critical step. Utilise strong, unique passwords for all user accounts, and consider employing SSH key authentication for added security when accessing your server remotely.
Setting up a firewall is another essential measure. Tools like iptables or firewalld can help you configure firewall rules to control incoming and outgoing traffic, thereby reducing the risk of unauthorised access. Implementing intrusion detection systems (IDS), such as Fail2Ban, can provide an additional layer of security by monitoring and blocking suspicious activities.
Consider deploying an SSL certificate to encrypt data transmitted between your server and users' browsers. This not only enhances security but also boosts user trust and can improve your search engine rankings. Additionally, limit the use of root privileges; create separate user accounts with the necessary permissions to minimise potential damage in the event of a breach.
Regularly backup your data to mitigate the impact of data loss due to hardware failure, cyber-attacks, or human error. Automated backup solutions can simplify this process, ensuring your data is consistently protected. Monitoring your server's logs can also be invaluable for identifying unusual activity early. Tools like Logwatch or the ELK Stack can assist in log management and analysis, enabling you to take swift action if anomalies are detected.
Common Challenges and How to Overcome Them
Setting up and maintaining a Linux web hosting environment can present various challenges, especially for those new to the platform. One frequent issue is navigating the command line, which can be daunting for beginners. Engaging with online tutorials, forums, and communities like Stack Overflow can be invaluable for learning the basics and troubleshooting problems. Another common challenge is software incompatibility. Ensuring your web applications are compatible with the Linux distribution you choose is crucial; consulting documentation and support resources can help mitigate these issues.
Security configuration can also be a complex task. Implementing best practices such as setting up firewalls, regular updates, and using strong authentication methods requires a good understanding of Linux security principles. Managed hosting services can offer a solution here by handling these technical aspects for you, allowing you to focus on your website content.
Resource management is another area where users might struggle. Monitoring server performance and managing resources effectively ensures your website runs smoothly. Utilising monitoring tools and performance optimisation techniques can help you stay ahead of potential issues. Lastly, when it comes to server backups, regular, automated solutions are essential to prevent data loss and minimise downtime. Being proactive in addressing these challenges will ensure a more seamless and secure Linux web hosting experience.
Popular Control Panels for Linux Web Hosting
Control panels are invaluable for simplifying the management of your Linux web hosting environment. Among the most popular are cPanel, Plesk, and Webmin. cPanel is renowned for its intuitive interface and extensive feature set, making it a favourite among users who need a straightforward yet powerful management tool. Plesk offers robust functionality and supports both Linux and Windows servers, providing versatility for those who manage multiple server environments. Webmin stands out as a free, open-source option that allows comprehensive server management through a web interface, catering to those who prefer a customisable and cost-effective solution. Each control panel brings unique strengths, helping to streamline tasks such as file management, database administration, and security configurations.
Choosing the Right Linux Web Hosting Provider
Choosing the right Linux web hosting provider involves several key considerations. Firstly, evaluate the quality of customer support offered. Responsive and knowledgeable support can be invaluable, especially when troubleshooting technical issues or during the initial setup phase. Check if the provider offers 24/7 support and multiple contact methods such as live chat, email, and phone.
Another crucial factor is the security measures in place. Opt for providers that offer robust security features, including regular backups, SSL certificates, firewalls, and DDoS protection. These features help safeguard your website against potential threats and ensure data integrity.
Reliability and uptime guarantees are also vital. Aim for providers that offer at least a 99.9% uptime guarantee, as frequent downtimes can significantly affect your website’s accessibility and user experience. Additionally, look into the provider’s data centre infrastructure and redundancy measures, which can impact overall performance and reliability.
Scalability is another important aspect to consider. As your website grows, you’ll need the flexibility to upgrade your hosting plan seamlessly. Check if the provider offers scalable solutions, such as easy transitions to VPS or dedicated hosting, without causing disruptions to your site.
Lastly, consider the hosting plans and pricing structures available. While cost-effectiveness is a significant benefit of Linux web hosting, ensure the plans align with your specific needs. Compare the features, storage, bandwidth, and other resources included in different plans to find the best value for your money.
Reading customer reviews and seeking recommendations can also provide insights into the provider’s reputation and service quality. By carefully evaluating these factors, you can choose a Linux web hosting provider that meets your requirements and supports your online endeavours effectively.
Conclusion and Final Thoughts
Linux web hosting stands out as an optimal choice for both beginners and seasoned web developers. Its open-source nature provides an affordable, highly customisable, and secure environment, suitable for a diverse range of websites, from personal blogs to large e-commerce platforms. The extensive community support ensures ongoing improvements and prompt resolution of issues, contributing to its reliability and performance. Choosing the right hosting provider is crucial; look for robust security measures, excellent customer support, and scalability to accommodate your website's growth. By leveraging the strengths of Linux web hosting, you can build a resilient and efficient online presence that meets your specific needs and goals.
4 notes
·
View notes
Note
hey, i just found out about the forum, and while i admit i haven't checked it out myself yet, i have a couple questions that i'd love to ask.
how is the forum in terms of user privacy? are passwords stored in plaintext? (please tell me they aren't.)
related to that, how can we be sure the website won't be an easy victim to attacks? if the forum were victim of a cyber attack, would user accounts be compromised?
lastly, what do you think of implementing a rule similar to 4chan's "don't talk about 4chan"? if we want to keep the website hush-hush and less vulnerable to male infiltrators, it might be good to promote secrecy in some degree, maybe even encourage willful misnaming of the website (but i'd like to know what you think).
Hi. Please check out the cybersecurity page for tips on how to stay safe on the internet and especially when using the forum. If people are not comfortable with any chance of a database breach, I would recommend not making an account. While I would love people to join, I care about being honest and making sure people are aware and okay with the risks of participating.
how is the forum in terms of user privacy? are passwords stored in plaintext? (please tell me they aren't.)
Passwords are not stored in plaintext. However, I will say MyBB's (the forum software I'm using) password encryption algorithm is not the best, so if the database were breached, it would be relatively trivial for a hacker who knew what they were doing to decrypt user passwords. MyBB plans to use a better encryption algorithm in its next release, and switching to that once it is out will be a top priority for me. This is why I suggest using a unique password for this forum (and tbh on any website it is best to use a unique password, you never know where the next database breach will come from).
related to that, how can we be sure the website won't be an easy victim to attacks? if the forum were victim of a cyber attack, would user accounts be compromised?
All passwords for all administrative accounts/logins related to the forum, its database, its server, etc. are very long and randomly generated, and are completely different from each other. Password hacking would be extremely difficult, likely impossible.
The biggest way I could see user accounts becoming compromised would be through a database breach (getting access to the database). There are two ways I see this could happen:
Someone directly uses the server account credentials to log in and breach the database (highly likely impossible as they would need to know where the server is located and the password for the server).
Someone hacking into an administrator account on the forum and downloading the database. This would be the more likely route, but they would need to know the password of an administrator account. This is how Kodi, a MyBB forum with 400k users, got its database breached. However, there are multiple ways to avoid this. 1.) I found instructions on how to lock down the MyBB Admin CP (Control Panel) with an additional password, which would mean a hacker would need to not just hack into an admin's account, but also know the password to the Admin CP. 2.) There is another option of editing the forum source code so that the ability to download databases from the Admin CP is completely disabled. 3.) If any additional administrators are needed, I could give them adjusted permissions which would not allow them to create database backups. Overall though, I don't think I will need to add administrators any time soon, if ever. (Moderators are different than admins.)
In the worst case scenario of a database breach, what would be leaked is similar to the Kodi breach above. This is why on the Cybersecurity page, I say: use a unique password, don't use an important email, be wary of the private messaging system, etc.
lastly, what do you think of implementing a rule similar to 4chan's "don't talk about 4chan"? if we want to keep the website hush-hush and less vulnerable to male infiltrators, it might be good to promote secrecy in some degree, maybe even encourage willful misnaming of the website (but i'd like to know what you think).
Hmm, well I've already announced the forum on Tumblr, so it's not very hush-hush already. :') My view is that male infiltrators would try to get in regardless. I don't think I can stop people from talking/sharing the forum, and I would prefer feminist women be able to find it easier. I would like to hope the application process would weed out most bad actors.
4 notes
·
View notes
Text
Website Uptime Monitoring and Management
In today’s digital age, having a website that is always available and accessible is crucial for businesses and organizations. A website downtime can lead to missed opportunities, loss of revenue, and damage to a company’s reputation. This is where website uptime monitoring and management come into play.

What is Website Uptime Monitoring?
Website uptime monitoring refers to the process of regularly checking the availability and performance of a website. It involves using specialized tools and services to monitor the website’s uptime and promptly alert the website owner or administrator if any downtime or performance issues are detected.
Website uptime monitoring services typically work by periodically sending requests to the website from multiple locations around the world. These requests simulate real user visits and check if the website responds correctly. If a problem is detected, such as the website being down or loading slowly, the monitoring service sends an alert through various communication channels like email, SMS, or push notifications.
Benefits of Website Uptime Monitoring
Implementing a robust website uptime monitoring system offers several benefits:
1. Minimizing Downtime:
Website downtime can occur due to various reasons, such as server issues, network problems, or software glitches. With uptime monitoring, you can quickly identify and address these issues before they escalate, minimizing the impact of downtime on your business.
2. Protecting Revenue and Reputation:
A website that is frequently down or slow to load can lead to frustrated visitors and potential customers abandoning your site. This directly affects your revenue and can harm your reputation. By proactively monitoring your website’s uptime, you can ensure a seamless user experience and maintain a positive brand image.
3. Tracking Performance Metrics:
Uptime monitoring services provide valuable insights into your website’s performance metrics. You can track metrics such as response time, average uptime, and downtime duration. These metrics help you identify trends, set benchmarks, and make data-driven decisions to improve your website’s performance.
4. SEO and Search Rankings:
Website downtime can negatively impact your search engine rankings. Search engines like Google prioritize websites that provide a reliable and uninterrupted user experience. Consistent uptime ensures that search engine crawlers can access and index your site properly, positively impacting your SEO efforts.
Website Uptime Management
Website uptime management goes beyond just monitoring and involves proactive steps to optimize and maintain your website’s availability. Here are some essential aspects of website uptime management:
1. Reliable Web Hosting:
Choosing a reliable web hosting provider is crucial for ensuring maximum uptime. Look for hosting providers that offer high availability, redundant infrastructure, and strong security measures. Additionally, consider the scalability of the hosting solution to accommodate your website’s growth.
2. Regular Maintenance and Updates:
Performing regular maintenance tasks, such as updating software, plugins, and security patches, is essential for keeping your website secure and stable. Outdated software can introduce vulnerabilities that could lead to downtime or compromise the integrity of your website.
3. Load Testing and Performance Optimization:
Conduct regular load testing to ensure your website can handle increased traffic without slowing down or crashing. Performance optimization techniques, such as caching, content delivery networks (CDNs), and code optimizations, can significantly improve your website’s speed and reliability.
4. Disaster Recovery and Backup Plans:
Prepare for the worst-case scenarios
by implementing robust disaster recovery and backup plans. Regularly back up your website’s data, databases, and configurations, and store them in secure off-site locations. This ensures that you can quickly restore your website in case of any unforeseen incidents.
Conclusion
Website uptime monitoring and management are vital for ensuring a reliable and high-performing online presence. By proactively monitoring your website’s uptime, you can address issues promptly, protect your revenue and reputation, and improve your overall user experience. Combine this with effective website uptime management practices to maximize the availability and stability of your website. Remember, a website that is always up and running is a key ingredient for success in today’s digital landscape.

Source
#WebManagement#ServerHosting#WebsiteMaintenance#TechSupport#CloudHosting#DataCenter#ServerManagement#WebHosting#ITInfrastructure#WebsiteSecurity#ServerAdmin#HostingSolutions#WebsitePerformance#ServerMonitoring#WebDevelopment#CloudComputing#NetworkSecurity#DomainRegistration#BackupandRecovery#Cybersecurity
22 notes
·
View notes
Text
MS Office - Introduction
Microsoft Office is a software which was developed by Microsoft in 1988. This Office suite comprises various applications which form the core of computer usage in today’s world.
MS Office Applications & its Functions
Currently, MS Office 2016 version is being used across the world and all its applications are widely used for personal and professional purposes.
Discussed below are the applications of Microsoft Office along with each of their functions.
1. MS Word
First released on October 25, 1983
Extension for Doc files is “.doc”
It is useful in creating text documents
Templates can be created for Professional use with the help of MS Word
Work Art, colours, images, animations can be added along with the text in the same file which is downloadable in the form of a document
Authors can use for writing/ editing their work
To read in detail about Microsoft Word, its features, uses and to get some sample questions based on this program of Office suite, visit the linked article.
2. MS Excel
Majorly used for making spreadsheets
A spreadsheet consists of grids in the form of rows and columns which is easy to manage and can be used as a replacement for paper
It is a data processing application
Large data can easily be managed and saved in tabular format using MS Excel
Calculations can be done based on the large amount of data entered into the cells of a spreadsheet within seconds
File extension, when saved in the computer, is “.xls”
Also, visit the Microsoft Excel page to get more information regarding this spreadsheet software and its components.
3. MS PowerPoint
It was released on April 20, 1987
Used to create audiovisual presentations
Each presentation is made up of various slides displaying data/ information
Each slide may contain audio, video, graphics, text, bullet numbering, tables etc.
The extension for PowerPoint presentations is “.ppt”
Used majorly for professional usage
Using PowerPoint, presentations can be made more interactive
In terms of Graphical user interface, using MS PowerPoint, interesting and appealing presentation and documents can be created. To read more about its features and usage, candidates can visit the linked article.
4. MS Access
It was released on November 13, 1992
It is Database Management Software (DBMS)
Table, queries, forms and reports can be created on MS Access
Import and export of data into other formats can be done
The file extension is “.accdb”
5. MS Outlook
It was released on January 16, 1997
It is a personal information management system
It can be used both as a single-user application or multi-user software
Its functions also include task managing, calendaring, contact managing, journal logging and web browsing
It is the email client of the Office Suite
The file extension for an Outlook file is “.pst”
6. MS OneNote
It was released on November 19, 2003
It is a note-taking application
When introduced, it was a part of the Office suite only. Later, the developers made it free, standalone and easily available at play store for android devices
The notes may include images, text, tables, etc.
The extension for OneNote files is “.one”
It can be used both online and offline and is a multi-user application.
3 notes
·
View notes
Text
What to do when you spot a broken website
I am a very firm believer in either sticking to your principles or update them.
So when I got this error while I tried to search for C/C++ on my national job portal:
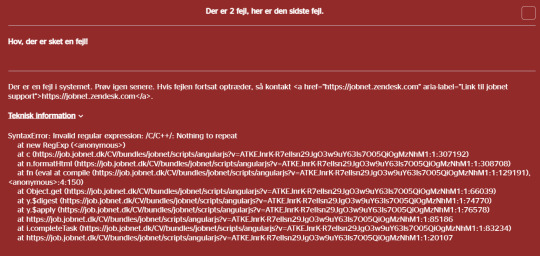
My first thought was "Huh, that is sorta funny" (especially since the code to show me the email address to report this error to was ALSO broken... meaning that whoever made the code that should run if the website broke... never tested it). And then I realized what I was looking at.
And at that point I think I had a ethical duty to notify people to get this fixed. FAST. Why?
It comes under "You are responsible for your choices". With it being understood that doing nothing is also a choice, and that taking a job where you work for, and help a company with doing evil is NOT a choice, if that is the only job you could get (IE, you did not have the power/money/mental health/time to make a choice)
It is now fixed*, so I wanted to make this post for all in the little codeblr community doing any front-end work. Web or not. With 3 lessons to learn from this.
First thing to get from this: "Everyone makes mistakes". This is one of the reason good code is not code without errors. It is code where it is easy to make changes and fix errors. You then try to find as many errors as you can with code reviews, automated testing, having a work environment that does not punish human errors( which encourages people to HIDE errors ) and so on.
Second thing: "Sanitize your user input. Always". Write code that assumes that every single user wants nothing more than to break your code and exploit its vulnerabilities.
This had NOT been done here. This error shows that characters in the string that was made from my search terms, was being run as code. As in, I, or anyone else, could run code in the middle of this javascript code. Meaning it is possible that someone could write code as part of their search that would make the javascript code do... whatever they wanted to. Including deleting the entire backend database. Or steal the info. This is why you ALWAYS sanitize your user input. Basically encode all potentially dangerous characters as something else while working on them. There are libraries like validator.js and express-validator that will do it for you, if you use javascript.
And the third thing. "Do NOT investigate further" . As soon as you confirm that your user input gets treated as code, you contact whoever is running it. If they do not take the threat seriously and it is still there after a week or two, contact established press with this info. You may read about so called grey hat hackers, who unlike black hat hackers(who is people wishing to do harm) or white hat hackers(Who are hired to try to break into a companies software to test it), are trying to find security flaws with good intentions, but are unaffiliated with whoevers code they are trying to break into. In an ideal world, doing that, and then contacting the company, SHOULD result in the company thanking them . But often it also leads to the company suing. And winning. Since breaking in to show that it is possible, is technically still breaking in. So do NOT start testing what you are able to do with the exploit you found. Report it to them, and check a weeks time later if it is fixed. If it keeps being vulnerable, contact the press. The site fixed this error after half a week. But they did it, not by encoding the dangerous characters into something else, but to simply remove them all from the user input string. Meaning that I still cannot search for "C++". Now I just get any job that contains the letter "C"... I mean... it is better... So if you take user input, and it does not brick your code in dangerous ways. You are doing better than whoever coded this for the Danish State :p
12 notes
·
View notes
Text
What are the best Plesk reseller hosting services?
Plesk Web Hosting uses a Plesk control panel to let you handle all aspects of your website hosting requirements, including DNS records, email addresses, domain names, and more. Plesk is an easy-to-use control panel that guarantees website security, automates server tasks, and supports both Linux and Windows hosting. Plesk is best suited for you if you need to manage your multiple customer accounts seamlessly and automate your admin functions.

Plesk reseller hosting: What is it?
In order to meet the requirements of individuals and businesses that want to administer multiple websites on a single platform, the Plesk reseller hosting platform offers a solution that is not only effective but also flexible. This particular hosting option is going to be highly appealing to web designers, web developers, and businesses that want to provide hosting services to their consumers but do not want to deal with the hassle of managing individual accounts.
Regardless of whether you handle a small number of domains or a large portfolio of websites, the user-friendly interface and wide feature set of Plesk make it simple to streamline your web hosting operations. This is true regardless of the magnitude of your website portfolio. This article will give you the knowledge you need to make decisions that are based on accurate information by delving into the most significant features, benefits, and best hosting service providers of Plesk reseller hosting.
The advantages of Plesk reseller hosting-
The Plesk reseller hosting platform offers a plethora of benefits, which makes it an enticing option for online professionals who have extensive experience in the field. One of the most important aspects of this product is the fact that it has a user-friendly design, which makes it simpler to manage a variety of websites and accounts.
Customers have the ability to effortlessly manage databases, email accounts, and domains with the help of Plesk, which features an interface that is simple to use. Furthermore, the reseller plans include support for an unlimited number of domains. This enables resellers to provide their customers with the most affordable hosting pricing possible for multi-domain publishing operations.
Using this cloud management platform comes with a number of important benefits, one of which is the complete security measures that are built into Plesk. These features include firewalls, intrusion detection, and antivirus protection. These qualities assist in the safety of websites against the dangers that can be found on the internet.
As an additional benefit, Plesk is compatible with a wide range of applications and extensions, which enables customers to customize their hosting environment to meet the specific needs of their businesses.
Plesk reseller hosting gives resellers the ability to create unique hosting packages, efficiently allocate resources, and deliver dependable services to their customers. This is made possible by the usage of Plesk. As a consequence of this adaptability, scaling and expanding the hosting business is a far simpler process.
Features of Plesk reseller hosting-
Security features
Plesk reseller hosting has many security tools to protect your hosting environment. Firewalls in Plesk prevent unwanted access and cyberattacks. The software also supports SSL certificates for encrypted server-client communication. Intrusion detection and prevention systems in Plesk monitor for suspicious activity and automatically mitigate threats.
Antivirus and anti-spam capabilities are incorporated to safeguard your email services from dangerous assaults and undesirable information. Regular security updates and patches are provided to maintain the system's security against current vulnerabilities. Plesk lets you create user roles and permissions to restrict authorized users' access to sensitive control panel areas.
User-friendly interface
One of the major characteristics of Plesk reseller hosting is its user-friendly interface. Plesk's control panel is simple and efficient, even for web hosting beginners. Domain management, email configuration, and database administration are easily accessible from the dashboard. As a complete WordPress site update, security, and management solution, the WordPress Toolkit improves user experience. Users may manage their hosting environment right away, thanks to this simplified UI.
Plesk lets users customize the dashboard to their preferences and workflow. Additionally, the responsive design guarantees that the interface is accessible and functioning across many devices, including PCs, tablets, and smartphones. The Plesk reseller hosting interface makes managing multiple websites and customer accounts easy and boosts productivity.
Performance and reliability
Performance and reliability are key to Plesk reseller hosting. Compared to typical shared hosting, reseller hosting offers better scalability and control, making it a more powerful choice for managing several websites. User satisfaction and SEO rankings depend on fast loading times and high uptime, which the platform optimizes. Plesk optimizes server performance with smart caching and resource management. Plesk websites perform well even during traffic spikes with minimal downtime.
Plesk also enables load balancing and clustering to spread traffic between servers. Having no single server bottleneck improves dependability. The platform’s solid architecture also features automatic backups and restoration capabilities, providing peace of mind that your data is safe and can be retrieved promptly in case of an incident. These performance and stability characteristics make Plesk reseller hosting a reliable alternative for administering several websites, giving your clients continuous service.
Expanding your company's reseller hosting operations-
Scaling your services
Growing your business requires scaling your Plesk reseller hosting services. Start by evaluating your current resource utilization and discovering any restrictions in your existing configuration. To handle traffic and data storage, you may need to modify your hosting plan or add servers as your client base expands. Plesk lets you add CPU, memory, and bandwidth to customer accounts for easy scaling. Load balancing and clustering can also evenly distribute traffic across servers for better performance and reliability.
Consider broadening your service offerings by introducing new features such as better security solutions, premium assistance, or specialized hosting plans for specific sectors. To match client needs and industry developments, regularly review and update hosting packages. Scaling your services efficiently lets you accommodate customer growth while retaining performance and dependability.
Effective marketing strategies
Effective marketing strategies are crucial for expanding your Plesk reseller hosting business. Determine your target audience—small businesses, bloggers, or e-commerce sites—and personalize your marketing to them. Explain Plesk reseller hosting benefits in blog posts, tutorials, and guides. This draws customers and establishes your hosting authority. Social networking can expand your audience. To develop trust, provide updates, promotions, and client testimonials.
Email marketing campaigns with unique discounts or new features can also be beneficial. To increase your website's exposure to search engines, you should also spend money on search engine optimization or SEO. To draw in organic traffic, use keywords such as Plesk reseller hosting. In order to broaden your reach, lastly, think about forming alliances or working together with web developers and agencies. By putting these marketing ideas into practice, you can increase your clientele and income dramatically.
For better value, bundle
Another efficient strategy to expand margins and stand out is by combining domains with critical web services. Besides delivering additional value to your consumer, bundling also boosts the average order value, which is vital in a market with intrinsically tiny per-product margins.
Web hosts frequently purchase SSL certificates, DDoS protection, email services, and CDNs as part of bundles. Although popular, these products are highly competitive. Besides bundling products, you might offer specialist products like DMARC or VPN services that your competitors may not offer.
Improving customer satisfaction
Enhancing customer experience is important to the success of your Plesk reseller hosting business. Start by giving your clients an easy-to-use control panel for managing their websites, email, and other services. Comprehensive documentation and tutorials can help clients solve common problems on their own. Give customers several support channels, including live chat, email, and phone, and answer questions quickly. Call clients by name and understand their needs.
Request feedback via surveys or direct communication to identify areas for improvement. Furthermore, providing value-added services like performance optimization, security upgrades, and automated backups can greatly enhance the general clientele experience. Providing customers with information about upgrades, new features, and maintenance plans fosters openness and confidence. By focusing on client satisfaction, you may develop long-term connections and drive favorable word-of-mouth referrals.
Best Plesk reseller hosting service providers-
MyResellerHome
One of the most well-known resale hosts is MyResellerHome. Every reseller plan from MyResellerHomecomes with a free domain broker and a free domain name for life. MyResellerHome has a great name for being innovative, dependable, and safe. This is important when you agree to be a reseller for a long time with a company. It is known to release new versions of PHP and MySQL faster than other hosts. With white-label billing, you can give your customers this benefit. A free WHMCS and cPanel license comes with most of MyResellerHome’s Hosting reselling plans.
AccuWebHosting
AccuWebHosting takes the tried-and-true approach of giving shared Linux reseller accounts cPanel and shared Windows reseller accounts Plesk. Although AccuWebHosting has a lot of great features like shared Linux and Windows servers and Windows VPS servers, dealers really like the company's hardware, data center engineering, and customer service.
ResellerClub
ResellerClub's plans come with the Plesk control panel, and you can choose from three different registration options: WebAdmin, WebPro, or WebHost. Business owners who want to run a shared Windows server environment can get Windows reseller products that come with an endless number of Plesk control panels.
InMotionHosting
In its reseller hosting plans, InMotion Hosting gives you a free WHMCS license. These plans use the same NVMe SSD hardware that a lot of users swear by. At InMotion Hosting, there are four main levels of reseller bills that go up to 100 cPanel licenses.
Conclusion-
When looking for the best Plesk reseller hosting, stability, performance, scalability, and support are crucial. Each hosting provider has unique characteristics, and choosing one that meets your demands can greatly impact your reseller business. After careful consideration, MyResellerHome is the best Plesk reseller hosting option. MyResellerHome is the top Plesk reseller provider, giving you the tools and resources to succeed in the hosting industry with its powerful infrastructure, excellent customer service, and extensive range of reseller-focused features.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
Top Tips to Build a Secure Website Backup Plans

Why Website Backup Is Crucial
Website backup is a critical aspect of website management, offering protection against various threats and ensuring smooth operations. Here's an in-depth look at why website backup is essential:
1. Protection Against Data Loss: During website development, frequent changes are made, including code modifications and content updates. Without proper backup, accidental deletions or code errors can lead to irrecoverable data loss.
2. Safeguarding Against Cyber Attacks: Malicious cyber attacks, including ransomware, pose a significant threat to websites. Regular backups provide a safety net, allowing businesses to restore their websites to a pre-attack state quickly.
3. Mitigating Risks of Hardware and Software Failures: Hardware failures or software glitches can occur unexpectedly, potentially resulting in data corruption or loss. Website backup ensures that data can be restored swiftly in such scenarios.
4. Facilitating Smoother Updates and Overhauls: Website updates and overhauls are inevitable for staying current and meeting evolving requirements. Having backups in place streamlines these processes by providing a fallback option in case of unforeseen issues.
Understanding Website Backup
What is Website Backup? Website backup involves creating duplicate copies of website data, including media, code, themes, and other elements, and storing them securely to prevent loss or damage.
Components of Website Backup:
Website Files: Includes all website data such as code files, media, plugins, and themes.
Databases: Backup of databases like MySQL or PostgreSQL, if utilized.
Email Sending: Backup of email forwarders and filters associated with the website.
Tips for Secure Website Backup Planning
1. Choose the Right Backup Frequency: Frequency depends on website traffic, update frequency, and content sensitivity.
2. Opt for Third-Party Backup Solutions: Consider factors like storage capacity, automation, security features, and user-friendliness.
3. Utilize Backup Plugins for WordPress: Plugins like UpdraftPlus, VaultPress, and others offer secure and automated backup solutions.
4. Maintain Offsite Backups: Store backups in remote data centers or cloud services for added security.
5. Test Your Backups: Regular testing ensures backup integrity and readiness for restoration.
6. Supplement Hosting Backup Services: While hosting providers offer backups, explore additional backup solutions for enhanced security and control.
7. Consider Manual Backups: Manual backups provide flexibility and control, especially for specific needs or scenarios.
8. Encrypt Backup Data: Encrypting backup files adds an extra layer of security, preventing unauthorized access.
9. Monitor Backup Processes: Regular monitoring helps identify issues promptly and ensures backup availability.
10. Implement Disaster Recovery Plans: Prepare for unforeseen events with comprehensive disaster recovery strategies.
Secure Website Backup Service with Servepoet
For comprehensive website backup solutions, consider CodeGuard Backup service, offering automated daily backups, robust encryption, and user-friendly management features.
Conclusion
Building a secure website backup plan is vital for protecting against data loss, cyber threats, and operational disruptions. By following best practices and leveraging reliable backup solutions, businesses can safeguard their websites and ensure continuity of operations.
#buy domain and hosting#best domain hosting service#domain hosting services#marketing#cloud vps providers#web hosting and server#shared web hosting
2 notes
·
View notes
Text
Ooo, something I'm actually an expert on.
In the enterprise world, we use the phrase 3-2-1 as a minimum acceptable backup. That is, three copies of your data in two formats (usually indicating hard drives and tape), one of which is off-site. This rule is to help protect against multiple forms of losing data. For instance, your backup drive will do jack squat if your roof collapses and pours water on your PC, but a backup in another town over will work just fine if your hometown is stomped flat by Godzilla. Both will work if you just delete your file.
For us home users, 3-2-1 is usually a lofty goal instead of a bare minimum, but we can use it as a framework for what backups you want. Anything you care deeply about, follow that rule. Have precious photos and/or art you created? Make sure you have three copies of it; say, one on your PC, one on your backup drive, and a third one in the cloud (at source quality, since a lot of services compress the hell out of it afterward) or at a friend's home that doesn't live right next door. Yes, "the cloud" should not be relied on, but it is an excellent secondary backup, since you still have your primary backup when some Internet Stupidity (tm) happens. I can add more information on the latter, but this post is already super long. Anything that would be annoying for you to recover and/or lose but not that big of a deal, just keep a simple backup handy. This is basically 2-1-0. Godzilla stomping would make you lose data, but not deleting a file. Anything that doesn't really matter, don't worry about. If you have the capacity to back it up, go for it; sometimes, it is simpler to just back up everything than to remember what is and isn't backed up. But, this is probably stuff you can just ignore testing on. Stuff that falls in this bucket includes Windows itself, games off of Steam, and so on. Wait, testing? YES. A key part of backing things up is making sure you can get them back. In the corporate world, the number of tales of "but we're backing this up!!!1eleven" for failed restores is as old as the Internet itself. This happens when you rely on an automated process to back up data (which is a good thing!) and don't actually check to make sure it is backing something up (which is a bad thing!). For our photographer or artist example, you'd want to have some form of automated backup; this can be a local drive to copy things to on top of a cloud backup solution. Set up some software to do this automatically so you don't just forget to back up for nine months. Make sure whatever you do sends you a report (popup message saying "backup done!" or an email telling you what it did; most backup software does this automatically) and make sure you get a report each time it is run. Once a year or so, try restoring some piece of art from that off-site backup and making sure it looks good. Don't restore the same thing every year. Personally, I back up my entire desktop to my network storage, and my network storage backs up to "the cloud". Three copies of data (PC, NAS, Cloud) in two formats (three sorta - SSD, hard drive, Cloud), one of which is off-site (Cloud). My super important files (password database, important documents) are actually backed up more like 12-3-2 than 3-2-1, but that's more a coincidence of how I have my computers set up.
HEY!
Back up your computer!
Go get the external drive you bought specifically for this purpose and then left in a drawer somewhere and RUN A FULL BACKUP.
There are lots of posts that make the rounds reminding us to sit up straight, stretch, drink water, refocus our eyes, take our meds, etc. But while this may not be about your health, it's still super-important.
Back up your whole-ass computer. If you can afford a second backup drive, buy one so that you have one SSD and one HDD, and back up to both of them (you can back up just the current important stuff to the SSD and let the HDD do the heavy-duty lifting).
Do not rely on 'the cloud' or the internet to keep jack shit.
AND BACK UP YOUR GMAIL AS WELL HOLY SHIT. The last thing you want is a catastrophic issue where literally every single thing you have in gmail is gone. It's happened. It happened to a friend of mine and basically her entire life was in there and now it's all gone. 20 years of it.
Reblog to save a life.
#backups#computer advice#yes I am a professional#no I am not your professional#if you're doing this for business consult a paid sysadmin
22K notes
·
View notes