#software vulnerabilities
Explore tagged Tumblr posts
Text
Carl E. Landwehr: Pioneer in Cybersecurity and Trustworthy Computing
Carl E. Landwehr is a distinguished American computer scientist specializing in cybersecurity and trustworthy computing. His extensive research has significantly advanced the identification of software vulnerabilities, the development of high-assurance software, and the creation of architectures for intrusion-tolerant and multilevel security systems.

Early Life and Education
Born in Evanston, Illinois, Landwehr pursued his undergraduate studies at Yale University, earning a Bachelor of Science degree. He furthered his education at the University of Michigan, obtaining both Master of Science and Ph.D. degrees in Computer Science. During his tenure at Michigan, he contributed to the Merit Network, the longest-running regional computer network in the United States.
Professional Career
Landwehr's career encompasses significant roles in government, academia, and research institutions:
Naval Research Laboratory (1982–1999): As a supervisory computer scientist, he conducted pioneering research in computer security, focusing on formal models for computer security and the development of secure systems.
Mitretek Systems (1999–2003): Serving as a Senior Fellow, he continued his work in cybersecurity, contributing to the advancement of secure computing practices.
National Science Foundation (2001–2004, 2009–2011): Landwehr developed and led cybersecurity research programs, shaping the direction of national research initiatives in the field.
Intelligence Advanced Research Projects Activity (2005–2009): As a Division Chief, he oversaw research programs aimed at enhancing national security through advanced computing technologies.
In academia, Landwehr has held teaching and research positions at institutions including Purdue University, Georgetown University, Virginia Tech, the University of Maryland, and George Washington University. Notably, he served as a lead research scientist at the Cyber Security Policy and Research Institute at George Washington University.
Contributions and Achievements
Landwehr's work has been instrumental in organizing and advancing the field of formal models for computer security. His influential taxonomy for security flaws has been widely recognized, and he has been a proponent of developing "building codes" for software used in critical infrastructures, particularly in the domains of medical devices and power systems.
His contributions have been acknowledged through numerous awards:
National Cyber Security Hall of Fame Inductee (2012): Recognized for his pioneering work in cybersecurity. Wikipedia
IEEE Fellow (2013): Honored for his contributions to the field of computer security.
ACM SIGSAC Outstanding Contribution Award (2013): Awarded for his significant impact on the field of computer and communications security.
NSF Director's Award for Meritorious Service (2012): In recognition of his exceptional service in advancing national research initiatives.
Editorial and Advisory Roles
Landwehr has served as editor-in-chief of IEEE Security & Privacy Magazine and as an associate editor for several IEEE journals. He has participated in studies for the National Academy of Sciences and was a member of DARPA's Information Science and Technology Study Group, contributing to the strategic direction of research in information security.
Recent Endeavors
In recent years, Landwehr has continued to influence the field through consulting and advisory roles, assisting in the development and management of research programs in the science of security. He has been an advocate for establishing industry standards, such as "building codes," for the construction of software with significant security requirements, organizing workshops and promoting best practices in software security.
Carl E. Landwehr's extensive body of work continues to shape the fields of cybersecurity and trustworthy computing, bridging the gap between academic research and practical applications in securing information systems.
#Carl E. Landwehr#cybersecurity#trustworthy computing#computer science#software vulnerabilities#intrusion-tolerant systems#multilevel security#National Science Foundation
0 notes
Text
In the dynamic landscape of the digital world, where technology evolves at an unprecedented pace, software security has become a paramount concern. With an increasing number of businesses and individuals relying on software applications for various purposes, the importance of protecting code from vulnerabilities and potential attacks cannot be overstated. This blog aims to shed light on the critical aspects of software security, offering insights into the significance of robust coding practices and effective strategies to safeguard your codebase. More Visit us.
0 notes
Text
father. you are so annoying sometimes. get's a single hint of something not working anymore and immediately doomsday's it and tries to set on the path of replacement. man is single-handedly keeping consumerism alive.
#my mum's computer is working totally fine but it's 'vulnerable' and the security extentions 'wont work' so my dad says we need to ditch it#and he says that security extentions wont work at all and that it's better to have nothing in place to protect your computer#because hackers use that software to get into your computer#???#who tf is brainwashing my dad???
3 notes
·
View notes
Note
Not an ask, but please do infodump more in tags. I am Delighted to learn new stuff <3
Will do.
#Homebrew on the 3DS took a while.#While Flashcards like Gateway were already Possible#through a combination of two Cards#One that installs an Extremely Large String in the DS Modes Status#And another that abuses the Now compromised 3DS to run Pirates Software.#However this Exploit could not install Homebrew.#Homebrew without Hardware Modification only became Possible shortly before the New 3DS Release.#Through an Exploit named Ninjhax.#This Exploit abused an Major Vulnerability in the Terrible 3DS Game Cube Ninja.#Cube Ninja was a Game that was mostly played using the Gyro Sensors#and it included a Level Creator that would save Levels as QR-Codes that you could share.#However there was no Limit on the Size that these Levels could have.#So using an Custom QR-Code The Game generated an Ridiculously Large Level#that Compromised the Console to the Point that First Homebrew Became possible.#Cube Ninja quickly became the most sold game on the eShop#before Nintendo took it down that is.#Eventually Ninjhax became Obsolete with the discovery of easier and more powerful Exploits.#But thats a Story for another Time.
3 notes
·
View notes
Text
25 ways to be a little more punk in 2025
Cut fast fashion - buy used, learn to mend and/or make your own clothes, buy fewer clothes less often so you can save up for ethically made quality
Cancel subscriptions - relearn how to pirate media, spend $10/month buying a digital album from a small artist instead of on Spotify, stream on free services since the paid ones make you watch ads anyway
Green your community - there's lots of ways to do this, like seedbombing or joining a community garden or organizing neighborhood trash pickups
Be kind - stop to give directions, check on stopped cars, smile at kids, let people cut you in line, offer to get stuff off the high shelf, hold the door, ask people if they're okay
Intervene - learn bystander intervention techniques and be prepared to use them, even if it feels awkward
Get closer to your food - grow it yourself, can and preserve it, buy from a farmstand, learn where it's from, go fishing, make it from scratch, learn a new ingredient
Use opensource software - try LibreOffice, try Reaper, learn Linux, use a free Photoshop clone. The next time an app tries to force you to pay, look to see if there's an opensource alternative
Make less trash - start a compost, be mindful of packaging, find another use for that plastic, make it a challenge for yourself!
Get involved in local politics - show up at meetings for city council, the zoning commission, the park district, school boards; fight the NIMBYs that always show up and force them to focus on the things impacting the most vulnerable folks in your community
DIY > fashion - shake off the obsession with pristine presentation that you've been taught! Cut your own hair, use homemade cosmetics, exchange mani/pedis with friends, make your own jewelry, duct tape those broken headphones!
Ditch Google - Chromium browsers (which is almost all of them) are now bloated spyware, and Google search sucks now, so why not finally make the jump to Firefox and another search like DuckDuckGo? Or put the Wikipedia app on your phone and look things up there?
Forage - learn about local edible plants and how to safely and sustainably harvest them or go find fruit trees and such accessible to the public.
Volunteer - every week tutoring at the library or once a month at the humane society or twice a year serving food at the soup kitchen, you can find something that matches your availability
Help your neighbors - which means you have to meet them first and find out how you can help (including your unhoused neighbors), like elderly or disabled folks that might need help with yardwork or who that escape artist dog belongs to or whether the police have been hassling people sleeping rough
Fix stuff - the next time something breaks (a small appliance, an electronic, a piece of furniture, etc.), see if you can figure out what's wrong with it, if there are tutorials on fixing it, or if you can order a replacement part from the manufacturer instead of trashing the whole thing
Mix up your transit - find out what's walkable, try biking instead of driving, try public transit and complain to the city if it sucks, take a train instead of a plane, start a carpool at work
Engage in the arts - go see a local play, check out an art gallery or a small museum, buy art from the farmer's market
Go to the library - to check out a book or a movie or a CD, to use the computers or the printer, to find out if they have other weird rentals like a seed library or luggage, to use meeting space, to file your taxes, to take a class, to ask question
Listen local - see what's happening at local music venues or other events where local musicians will be performing, stop for buskers, find a favorite artist, and support them
Buy local - it's less convenient than online shopping or going to a big box store that sells everything, but try buying what you can from small local shops in your area
Become unmarketable - there are a lot of ways you can disrupt your online marketing surveillance, including buying less, using decoy emails, deleting or removing permissions from apps that spy on you, checking your privacy settings, not clicking advertising links, and...
Use cash - go to the bank and take out cash instead of using your credit card or e-payment for everything! It's better on small businesses and it's untraceable
Give what you can - as capitalism churns on, normal shmucks have less and less, so think about what you can give (time, money, skills, space, stuff) and how it will make the most impact
Talk about wages - with your coworkers, with your friends, while unionizing! Stop thinking about wages as a measure of your worth and talk about whether or not the bosses are paying fairly for the labor they receive
Think about wealthflow - there are a thousand little mechanisms that corporations and billionaires use to capture wealth from the lower class: fees for transactions, interest, vendor platforms, subscriptions, and more. Start thinking about where your money goes, how and where it's getting captured and removed from our class, and where you have the ability to cut off the flow and pass cash directly to your fellow working class people
52K notes
·
View notes
Photo
If something you own can be remotely disabled - intentionally or not - by a third party, you don’t own it, you’re renting it.
Maybe rent is free!
But someday the person on the other end of that equation is going to either a) up your rent to increase profits, b) sell to someone who will up your rent to increase profits or c) go out of business and take your access with them. This is a feature, not a bug, of the endless-growth model. “Internet activated” means “remote kill switch”.
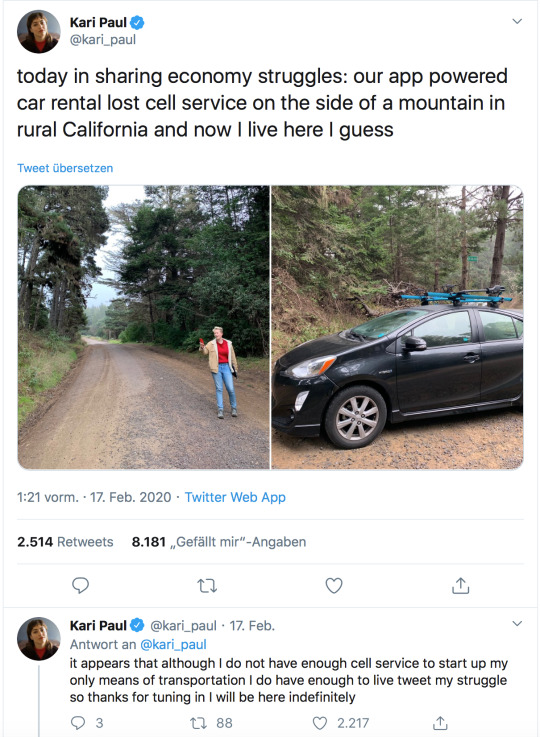
Welcome to the future, where you don’t own anything and the stuff you rent stops working once your phone has no signal.
#not even getting into the massive security vulnerabilities most IOT devices represent#if it can be accessed remotely#*anyone* could access it remotely#and the moment the software team stops producing security patches for your model of smart fridge#it becomes a liability
172K notes
·
View notes
Text
Secure Code, Secure Future: Uniting Dev and Security.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Secure your code and protect your future by integrating security into every phase of development. Join the discussion on #DevSecOps and IT security. This post explains how to merge security into every phase of software creation. It shows why adding security to the development lifecycle helps build stronger applications and…
#Code Safety#Development Lifecycle#DevSecOps#IT Security#News#Sanjay Kumar Mohindroo#Secure Applications#Software Development#Vulnerabilities
0 notes
Text
Complexity-Induced Risk
Complexity-Induced Risk refers to the heightened potential for adverse outcomes arising from the intricate and interconnected nature of a system. This risk emerges when the complexity of a system—whether technological, financial, ecological, or organizational—reaches critical levels, leading to unpredictable interactions that are difficult to foresee, manage, or mitigate. This level of complexity…
#complex product#Complexity#complexity management#complexity-induced risk#Extreme problems#resilience#resilience rating#risk management#software complexity#uncertainty#vulnerability
0 notes
Text
Sorry I made a mistake, it's not "a few lines of code" it's "one single line of code". libwebp allows you to encode or decode webp data into rgba bytes in a single function call. it would take 10 minutes to implement this on the most dire of codebases. Even me with my absolutely shitty C and zero skills could encode and decode webp.
me when i meet the person who created webp files

#yes libwebp had a bad vulnerability some time ago but im gonna be honest if you stop trusting software because it historically had a rce#you better come to terms with never using an operating system again
98K notes
·
View notes
Text
PureCode company | Powerful feature within React Router
Redirects are a powerful feature within React Router, enabling developers to guide users through their applications seamlessly. However, their misuse or overuse can lead to complications, including performance issues and security vulnerabilities.
#Powerful feature within React Router#including performance issues#security vulnerabilities#their applications seamlessly#purecode company#purecode reviews#purecode software reviews#purecode ai reviews#purecode ai company reviews#purecode
0 notes
Text
Zoho Product Vulnerabilities: Exploring Legacy Issues and New Security Threats in 2023-2024 @zoho #ZohoOne #ManageEngine #ZohoCRM #ZohoBooks
Legacy Vulnerabilities in Zoho Products and New Discoveries in 2023-2024: A Comprehensive Analysis Introduction Zoho Corporation is one of the most well-established software development companies, offering a wide range of products that include customer relationship management (CRM), office suite applications, and cloud-based business tools. Over the years, Zoho has gained a massive following,…
#Cybersecurity threats#Software security 2024#Zero-day vulnerabilities#Zoho CRM API#Zoho Mail phishing#Zoho ManageEngine#Zoho security#Zoho Vault encryption#Zoho vulnerabilities
0 notes
Video
youtube
Zero-Day Exploits
#youtube#cybersecurity zero-day exploits software vulnerabilities data protection hacking prevention
0 notes
Text
Dependency-Check in Azure DevOps
Hi everyone, In this post we are going to setup OWASP dependency-check in azure devops. As this process is the part of Software Composistion Analysis(SCA) which is really important phase in secure software development lifecycle. OWASP Dependency-Check is one of the popular SCA tool and implementing it in azure devops pipeline. What is Software Composition Analysis? Software Composition Analysis…

View On WordPress
#dependency-check#known vulnerabilities#nvd#nvdapikey#owasp-dependency-check#pentestguy#software-composition-analysis
0 notes
Text
Explain about security vulnerabilities in microservices
Security loopholes in microservices expose sensitive data or allow unauthorized access, posing a threat to the overall system security. Solution: Implement authentication and authorization mechanisms for secure access to microservices. Regularly conduct security audits and vulnerability assessments. Terminology: Authentication: The process of verifying the identity of a user, system, or…
View On WordPress
#Best Practices#interview#interview questions#Interview Success Tips#Interview Tips#Java#Microservices#programming#Security Vulnerabilities#Senior Developer#Software Architects
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
How to Choose the Right Antivirus Software: A Comprehensive Guide
In today’s digital age, where our lives are intricately intertwined with technology, safeguarding our digital assets has become paramount. With the proliferation of cyber threats, antivirus software stands as a crucial line of defense against malware, viruses, ransomware, and other malicious entities lurking online. However, the abundance of antivirus options can be overwhelming, making it…

View On WordPress
#A#Advanced Behavioral Analysis Software#Advanced Threat Detection#Antivirus#Antivirus Software#Automated Security Incident Response#Cloud Security Solutions#Cloud-Based Endpoint Security Platform#Comprehensive Data Protection Suite#Continuous Vulnerability Assessment#Cyber Defense#Cybersecurity#Cybersecurity Awareness Training#Data Encryption Software#Data Protection#Defense#Encryption#Endpoint Protection Suite#Endpoint Security#Firewall#Firewall Protection#Identity Theft#Identity Theft Prevention#Integrated Firewall Protection Mechanism#Internet Security Software#Malware#Malware Detection#Malware Removal Tool#Mobile Device Management#Multi-Layered Malware Defense System
0 notes