#stackframe
Explore tagged Tumblr posts
Text
Multilanguage debugging in lldb: print call to function.
There probably aren’t many people that care about debugging multiple languages, but I learned a new trick today that is worth making a note of, even if that note is for a future amnesiatic self. Here’s a debug session where C code is calling COBOL, but in the COBOL frame, the language rules prohibit running print to show the results of a C function call (example: printf, strlen, strspn, …) To…
View On WordPress
0 notes
Text
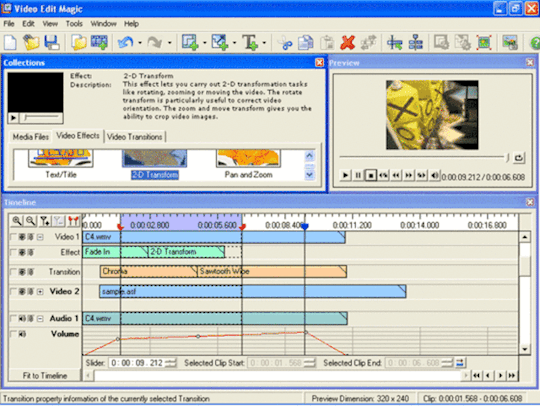
Video edit magic 4.47 problems

Managunz backup manager works best for jb rips(ISO not supported)!
- Official firmware updates via internet blocked.
- HEN updater support available under Network Category.
- Hybrid Firmware Tools available via PKG installation.
- Both REBUG and Stock Edition available.
- Fixed infinite spinning wheel when in-game.
*Only available via PS3HEN PKG installation
- Multiple path on boot_plugins & boot_plugins_kernel (HDD & USB) Thanks to - Hybrid Firmware Tools available when HEN's activated (Enable HEN to use this feature) *.
- App restriction on RemotePlay with PC removed.
- Added advanced download plugin patches.
- Fixed issue with official NPDRM content rif deletion and unable to boot error.
- RAP activation on the fly, default path : usb000/exdata/ or usb001/exdata/.
- Added new coldboot, icons, and JS/HTML overlay (thanks Release Notes (Update (4)).
Added 1 query for external.xml on usb000 (thanks - Replaced Manual link from Network column with PS3Xploit Home link
- PKG Linker is now located under Package Manager - Install Packages.
- HEN Theme Pack by Itroublve_Hacker downloadable package updated with fixed icons.
- Default Theme Pack removed from main package and can now download from Themes Updater.
- Improved SELF auth (Fixes games that run multiple executables.
Fixes the issue with a few games (SC Trilogy and etc).
- Added missing COBRA patches & BT/USB passthrough support added.
- Fail-safe added for stage0 incase stage2 not found (thanks - Fixed bug where if kernel plugin was more than 64kb it will crash PS3.
- Memory Optimization (no embedded buffer for kernel plugin, only allocs when requested).
- Memory Management of map_path improved.
- Embedded buffers and removed memory fragmentation.
- Cleanup thread added and Faster boot times for app increasing stability.
- PS2Classics launcher activation on the fly (thanks - Impoved compatibility with apps like MultiMan and others which replace syscall 6-10.
- HEN Installer feature added and memory management changes.
- On Boot, HEN Enabler icon is selected by default (Navigate to System Settings > Display > Off).
- Replaced dev_blind with dev_rewrite to maintain RW state at all times.
- Added HEN refresh and version display on initialize, using embedded plugin.
- The stackframe and PS3HEN bins are now merged as a single payload binary (PS3HEN.BIN).
- HEN queue is drained before the patches get disabled, and also synchronized properly the check to synchronize remove and do patches.
- Updated extended download plugin patches, per suggestion.
Thanks - Handler requests are passed fast, removed many branch conditions there for faster handling

- Optimizations added to how much stack is available to the syscalls (original vs before original-0xd0).
- Fixed freezing if someone tries to enable hen successfully twice.
- HEN can be enabled when failed, and ran successively, without reboot.
- If HEN doesnt init an automated soft reboot takes place.
- Fixed crash that sometimes happened on init.
- Increased sleep in html, removed from bins.
Some of the new changes provide full PS3ISO Support ,As well as full BDISO and DVDISO support has been added, plus new improvements to PS3HEN's stability, KW Stealth Extension Added, plus kernel plugin support (v2) to go along with bootplugin support (v1), see changelog below for a complete listing of changes in this new build. Version 3.x.x has come with a number of new additions for a better experience. Also we have started forming the PS3HEN Homebrew & Plugin Compatibility Chart detailing various aspects and info that will be useful for PS3HEN user's. So we took it upon ourselves to get the ball rolling on a new PS3HEN F.A.Q. We paused the reporting this on the frontpage until we were pleased with the documentation. This is due in the way this was delivered and presented. While this is a tremendous release and breakthrough the information behind PS3HEN has been lacking and has served more questions then answers that could be provided. This exploit for nonCFW console's provides homebrew support and a number of Custom Firmware intangibles for those console that can not install a traditional CFW, with those being lat production PS3 Slim models and all of the SuperSlim Consoles.
Original Article: Here is v3 of the latest PS3 Hack to hit the PS3 Scene with the recent release of PS3HEN. See also: The Great PS3 HEN All in One (AIO) Guide UPDATE ( 06-03-2021): Version 3.0.3has been released and provides 4.88.1 HFW Support.

0 notes
Text
Week 9 Notes
Just Culture
Done well it works. Instead of blaming the individual who was the approximate cause of the problem - look at the overall system.
A just culture helps create an environment where individuals feel free to report errors and help the organization to learn from mistakes. This is in contrast to a “blame culture” where individual persons are fired, fined, or otherwise punished for making mistakes, but where the root causes leading to the error are not investigated and corrected. In a blame culture mistakes may be not reported but rather hidden, leading ultimately to diminished organizational outcomes.
https://en.wikipedia.org/wiki/Just_Culture
WHAT DO WE THINK NOW?
Time - Ability to observe failures and learn.
Engineers - Learning from the past. Methodologies to follow. Notion of best practice and standards. CHECKLISTS ARE REALLY GOOD! (Like aeroplane pilot).
Engineers need to have processes about being creative. Profession needs to have people who think outside of the box but if they get stuck needs to be some procedure in place.
What makes science is that you are following the procedure to prove yourself wrong - Falsifying. We can constantly prove something is wrong and then gain confidence as time goes by. Engineering is trying to always break it wrong, we always test in our mind and lab trying to break things. Engineering has a culture of excellence.
Agile Software Development is not good for security. Ship! Ship! Ship!
You have a duty - “not comfortable doing that”. Say that to your boss.
Plan and deal with conflicts of interest.
Quantity - Measure everything you can and check it. Engineers don’t say that looks thick enough. They smash bricks and things. The danger of quantifying is not everything is worth measuring. E.g. 6% secure website? Wtp does that mean.
You are a thoughtful analytical person and when you are in a crisis you are thoughtful.
Assurance - ways of being confident in what you say. Justification of saying the bridge is saying. Not challenger “1 in a million chance”
Closing the loop - So many systems are Feed Forward. Closing the loop - Feed Back. 10 years time come back and you didn’t get a job. Closing the loop is checking something is right. The art of engineering is closing the loop. We want wise thinking not wishful thinking.
350 alarms - Something went wrong on a oil ship and 350 alarms went off. Of those 350 alarms, only 8 were important. 350 alarms how do you need to know what is wrong? Metaphor for Cyber Security - You can hear 350 alarms, but you need to listen to the ones you need to be listening too.
System Properties - Need to think of systems. QANTAS Engineers sweating in non airconditioned plane. Frame of mind. Submarine incident - sweating, swearing while nuclear war might be happening on surface. Submarines can launch nuclear missiles. However commander didn’t launch - credit to him saving the world. Leaving a spanner in a thing.
Coherence - Need a system to have coherence and not be very complex and not be tightly coupled. Three things that lead to error. Coherence - everything in a unit has to be doing the same thing e.g. one function() does half a thing. Second of all, components shouldn’t be tightly coupled - changes in one affect changes in the other.
Wargames - Why are there humans in the loop? Humans are a real problem - you get a whole pile of crap. Can you replace humans with Automatic Safety devices? Difficult to cover every scenario. If everything occurs as intended, then it is okay. However if it is a different problem then what happens with the ASDs? Attackers exploit the fact that the system is not perfectly designed. An attacker wants to know what happens when the system is out of spec. The human designers don’t design systems properly. The system will operate outside of the spec - can’t use ASDs for everything. Can’t solve Apollo 13 with ASDs. ASDs put a bottom line - if all you have is ASDs you are in trouble. Needs humans in the loop (CHINA SYNDROME) .
Voting System - Not entirely tested. Not commercial grade software. If something fails during your election, you get the wrong government.
End 2 End - Security is an end to end property. People attack the ends. E.g. keylogger. Attack the weakest point.
Work to undermine limits - Anyone in power works actively to increase their power. Checks and balances stopping POTUS from having too much power. People will always try to overcome controls and things.
Ruler of the galaxy - Single trusted party. One person at top controls everything - single point of failure. Criteria - you don’t want to be ruler of the galaxy.
Assange - You want free speech except that is critical/inconvenient of you.
Cars and Trolley Cars - Uber/google etc. No one asked the question is this safe or danger of hacking? Absolutely - Top People working on it. Distraction 1 - probably the cars will kill people, but so many people die anyway today. We expect the accident rate to reduce. Then he said about the ethical decisions - avoid hitting would have to kill a young person - don’t know the answer to the question. Distracted from the hacking problem! Attacker could take over every car in the city and drive them into people, when you can’t patch your phones, browsers etc. How can you assure this?
No Trusted third parties - At some part you might need a trusted third party. Every attack is an attack on trust. Who can you trust. If you have the idea of insiders/outsiders - convenient theory e.g. Trump build a wall. However insides and moles are the real person. If you can’t trust anyone what can you do? Computer systems trust each other - function1() don’t need to check function2(). You might have to put checks everywhere - trust makes stuff work. Without trust the system is very inefficient. A trust no one will et access to the harddrive physically - then someone does and gg dead. Trusted third parties keep failing. However don’t roll your own security either! Difficult balance.
A remarkable number of missiles did not hit British ships. The missiles were rigged! Can’t trust third parties.
Secret to communication - It is not about me, it is about you. All the matters is what you hear. Ultimately it is all about the listener. 2 Firearms book - one sucks, one good.
Canary in a Coal mine - Canary in the coal mine dies very quickly. As soon as it died it stops singing - useful for mine.
Opal - Credit card and same discount - logging your identity and tracking everything and keeping it.
Face ID - Suckiing your face and sending to server
Data needs to be free - It was data about me and you. We could use this data to do greatt hings! World will get better - Your data. Setting other people’s data free. Can’t be put back. Danger of data - Patterns of data - the more you have compound effect. 3 pools = 1 lake. Worth more than 3 pools separate.
Read article - Secret agents could travel around and do things without people working out who they were. Pervasive tracking and databases and data matching allows them to be detected. They Are Canarys. A world where the secret agents can’t do their stuff is a world like 1984.
We would have lost all the privacy before we realise.
Cyborg - augmented human. We have become cyborgs with our phones. Offload our cognitive functions to our phone.
personal identity leaking out into the world. Governments collected data pretty bad.
REVERSE ENGINEERING
What is Reverse Engineering?
Taking an executable program and analysing its insides to figuring out how it works
Machine binary -> Assembly -> Code
Why reverse engineer
Challenge, Profit - Bounties, Malware analysis, Interoperability - extend the function of software you own
How to Reverse Engineer
Static - Read the decompiled code to determine purpose
Dynamic - Step through in real time to understand it
Static - Disseamble program by decompiling it
x86 - Generally just understand registers, system calls are a black box, function calls, branching - if statements, just read mneomic and guess, use reference manual, Google
Simple exam - Move value to register, call is system call
Tools for dynamic analysis - Basically any version of GDB, walk through the program during runtime.
Tips from demo - Look at the big picture - don’t get caught in the assembly. Look at strings. Many tools allow you to rename things and make commands. Run the program beforehand. Focus on areas of interest only. Work your way up.
CRACKING - It is illegal.
Patching - Change the program to always go to password correct. Skip everything! Jump and skip authentication. Crackmes.
Further Concepts - Stack - short term variable storage for programs (comp1521 stuff). We push a stackframe on the stack when we call a function. Save previous function’s registers on the stack.
Anti Reverse Engineering - Don’t release debug build. Remove symbols from the binary, dump symbols, disable asserts. Tomb Raider reverse to the original C code.
Anti RE: Tricking the Disassembler - Common techniques - Excessive jumps, dummy instructions, overlapping instructions. Self modifying code - COmmon in malware, non in commercial software - needs RWX text segment.
Overlapping Instructions - Embed instructions inside other instructions
Movfuscators - Turns every single instruction into MOV instructions
0 notes
Text
Wargames 02 Challenge 2
This is the write-up of my solution to the COMP6447 Wargame02 ‘blind’ challenge. Challenge: Blind
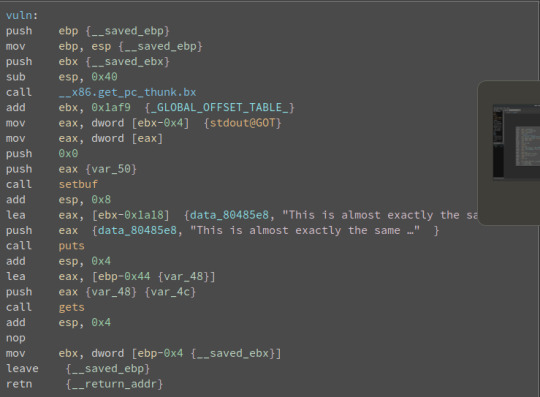
Above: The vulnerable vuln() function that uses gets. Solution: This challenge was similar to the first except the address of the win() function is not given to you. Conveniently though, pwntools allows you to find the address of a function given it's name. I utilised this to get the address, and then from here on out it was pretty similar to the previous challenge.
I did have to prepare the payload slightly differently though. Rather than the vulnerable program logic being in main, main instead calls a function that uses gets() named vuln(). This meant that the return address that was popped after vuln() exits would have been +0x04 from wherever the bottom of the stackFrame was for vuln(), as oppose to having to overwrite a function pointer in the last challenge. Hence when I overflowed the buffer I had to include an extra 4 bytes in the length of the buffer and then put the return address at the end of that.

Above: Script that exploits the use of gets().
For an analysis of the script refer to the write-up of the previous challenge, the payloads are meaningfully the same.
0 notes
Text
Advanced Static Analysis #2
The second part of the Lab from Chapter 5
8. What is happening at the area of the code that references \cmd.exe /c?
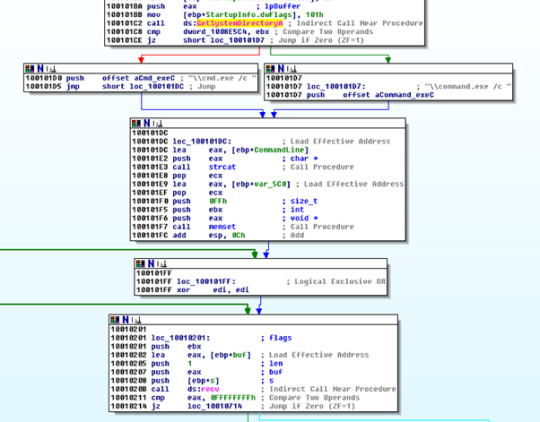
The second level from the top contains the cmd.exe string. The second level determines whether to use cmd.exe or command.exe. I’m not sure why that matters. The green CommandLine is a variable within the stackframe. EBP seems to point to the end of the stack frame.
The recv call in pink stands out and seems to be opening up a socket. Perhaps the malware is trying to start an internet connection to the practical malware URL?
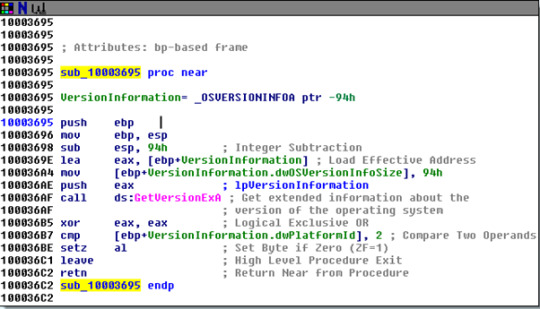
9. In the same area at 0x100101C8, it looks like dword_1008E5C4 is a global variable that decides which path to take how does the malware set dword_10008E5C4?
Look into DATA XREF reveals it takes a OS version information return value from a subroutine.
10. A few hundred lines into the subroutine at 0x1000FF58. A series of comparions use memcmp to compare strings. What happens if the string comparison to robotwork is successful?
Memcmp compares characters in two buffers. Returns 0 if they are identical. Finally found the comparison to robotwork:
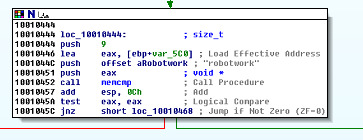

We get extended information about the operating system. The program then calls RegOpenKeyA. We query about the work time. Create a string with atoi and sprintf containing the information we queried. Then finally close the key,
11. What does export PSLIST do?
With a simple navigation to PSLIST through the export window. We determine that it takes in 3 ints and a char. It calls a subroutine to check OS version. It will then send over processes that matches the string passed.
12. Use the graph mode to graph the cross-reference from sub_100004E79. Which API function could be called by entering tis function?

Based on the functions that it calls and the knowledge we know of this malware we can say it sends a message.
13. How many API functions does Dllmain call directly?
Dllmain calls stnicmp, strlen and CreateThread directly.
14. At 0x10001358, there is a call to Sleep (an API function that takes one parameter contained the number of millisecond to sleep). How long would it take before the program executes?
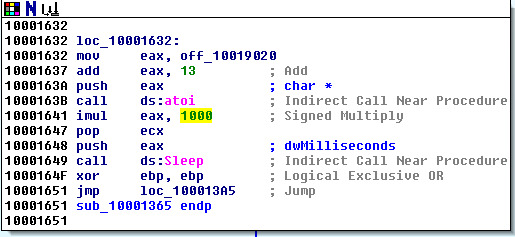
You can change hexadecimal to decimal by pressing the values and pressing H! That’s handy! We add 13 onto the address so it points to 30 then we multiply by 1000 to get 30,0000 milliseconds which is 30 seconds.
Reflections
I missed a crucial part of the work times analysis. The registry is opened and the query gains the information. Afterwards, the information is sent over the internet!
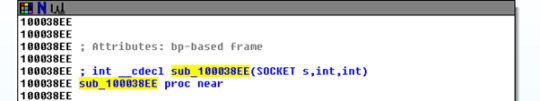
I missed a subroutine between the query and close. The subroutine opens a socket and sends data! I learnt a great deal from the practical exercises. However, It was extremely time consuming crawling through the functions. I’ll definitely look more into reverse engineering once the course is over!
0 notes
Text
W7: Lecture
It was good to have an mid-sem exam debrief on the questions asked. It clarified some of the issues that I faced in the quiz. I found question 10 quite tricky in particular.
This lecture was more technical then the last which is enjoyable but requires more concentration.
My main takeaways from this lecture were:
- Diffie Hellman Key Exchange
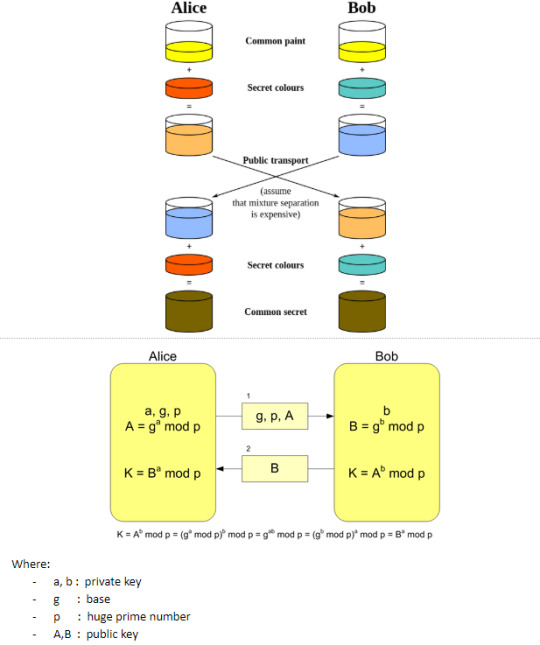
- Vulnerabilities - a potential weakness in something
- Software Bug - sometimes a vulnerability
- Exploits - attacks a vulnerability to compromise a system
- Memory Corruption Attacks - the attacker changes what is in memory so that the program behaves differently, the most common type is a buffer overflow
- Format String error - was a problem everywhere, until everyone realised and patched against it within a few months, and it wasn’t an issue anymore, but is starting to come back
- Canary - buffer overflow protection modifies the organization of data in the stackframe of a function call to include a "canary" value that, when destroyed, shows that a buffer preceding it in memory has been overflowed. With the canary it is not going to prevent a malicious buffer overflow. You can find where the canary is in the stack and just fill an array with the canary so that it does not get triggered and alert the computer that a buffer overflow has happened
- Penetration testing - is important because:
- It allows us to discover vulnerabilities in our system before attackers do - It can test you security controls(Firewalls, IPS,IDS) - Sometimes thinking like an attacker is the best way to expose weaknesses - Digital security in today’s age is everything
0 notes
Text
MySQL Deadlocks with INSERT
Support Channel. “Hi, I am getting deadlocks in the database and they occur when I have to rollback the transactions but if we don’t have to roll back all transactions get executed.” Wait, what? After some back and forth it becomes clear that the Dev experiences deadlocks and has data: mysql> pager less mysql> show engine innodb statusG ... MySQL thread id 142531, OS thread handle 139990258222848, query id 4799571 somehost.somedomain someuser update INSERT into sometable (identifier_id, currency, balance ) VALUES ('d4e84cb1-4d56-4d67-9d16-1d548fd26b55', 'EUR', '0') *** (2) HOLDS THE LOCK(S): RECORD LOCKS space id 3523 page no 1106463 n bits 224 index PRIMARY of table `somedb`.`sometable` trx id 9843342279 lock mode S locks gap before recand that is weird because of the lock mode S locks gap in the last line. We get the exact same statement with the exact same value on the second thread, but with lock mode X locks gap. Both transactions have an undo log entry of the length 1 - one row, single insert and the insert has an S-lock. A mystery INSERT and opaque code Many questions arise: how can an INSERT have an S-lock? how can a single INSERT transaction deadlock? what does the originating code look like? The last question can be actually answered by the developer, but because they are using Java, in true Java fashion it is almost - but not quite - useless to a database person. @Transactional(propagation = Propagation.REQUIRES_NEW, timeout = MYSQL_TRANSACTION_TIMEOUT, rollbackFor = { BucketNotFoundException.class, DuplicateTransactionException.class, BucketBalanceUpdateException.class }, isolation = Isolation.SERIALIZABLE ) public void initiateBucketBalanceUpdate(Transaction transaction) throws BucketBalanceUpdateException, DuplicateTransactionException { this.validateAndInsertIdempotencyKey(transaction); this.executeBucketBalanceUpdateFlow(transaction); this.saveTransactionEntries(transaction); }So, where is the SQL? This is often a problem - Object Relational Mappers encapsulate the things that go on in the database so much that it is really hard for anybody - Developers, DBAs and everybody else - to understand what actually happens and make debugging quite painful. Or, if they understand what goes on with the database, to map this to the code. TRANSACTION ISOLATION LEVEL SERIALIZABLE In this case it is solvable, though. The isolation = Isolation.SERIALIZABLE is the culprit here. So when we spoke about transactions and isolation levels previously, I made the decision to leave the fourth and most useless isolation level out of the picture: SET TRANSACTION ISOLATION LEVEL SERIALIZEABLE. The manual says: SERIALIZABLE This level is like REPEATABLE READ, but InnoDB implicitly converts all plain SELECT statements to SELECT ... FOR SHARE if autocommit is disabled. It then goes on to explain how SERIALIZABLE does nothing when there is no explicit transaction going on. It does not explain what it is good for (mostly: shooting yourself into the foot) and when you should use it (mostly: don’t). It does answer the question of “Where to the S-Locks come from?”, though. The SERIALIZEABLE isolation mode turns a normal SELECT statement into a Medusa’s freeze ray that shoots S-Locks all over the tables onto everything it looks at, preventing other threads from changing these things until we end our transaction and drop our locks (And that is why you should not use it, and why I personally believe that your code is broken if it needs it). A broken RMW and lock escalation So instead of a regular Read-Modify-Write Session1> START TRANSACTION READ WRITE; Session1> SELECT * FROM sometable WHERE id=10 FOR UPDATE; -- X-lock granted on rec or gap -- ... Application decides INSERT or UPDATE Session1> INSERT INTO sometable (id, ...) VALUES ( 10, ... ); Session1> COMMIT;we get the following broken Read-Modify-Write, minimum: Session1> START TRANSACTION READ WRITE; Session1> SELECT * FROM sometable WHERE id=10 FOR SHARE; -- S-lock granted on rec or gap -- ... Application decides INSERT or UPDATE Session1> INSERT INTO sometable (id, ...) VALUES ( 10, ... ); -- lock escalation to X Session1> COMMIT;The LOCK IN SHARE MODE or equivalent FOR SHARE is not in the code, it is added implicitly by the isolation level SERIALIZABLE. We get an S-Lock, which is not good for writing. Our transaction now did not get the required locks necessary for reading at the start of the transaction, because the later INSERT requires an X-lock, like any write statement would. The database needs to aquire the X-lock, that is, it needs to upgrade the S-lock to an X-lock. If at that point in time another threads tries to run the exact same statement, which is what happens here, they already hold a second S-lock, preventing the first thread from completing their transaction (it is waiting until the second threads drops the S-lock or it times out). And then that second thread also tries to upgrade their S-lock into an X-lock, which it can’t do, because that first thread is trying to do the same thing, and we have the deadlock and a rollback. Reproduction of the problem We can easily reproduce this. Session1> set transaction isolation level serializable; Session1> start transaction read write; Query OK, 0 rows affected (0.00 sec) Session1> select * from kris where id = 10; +----+-------+ | id | value | +----+-------+ | 10 | 10 | +----+-------+ Session1> select * from performance_schema.data_locksG ... LOCK_TYPE: TABLE LOCK_MODE: IS LOCK_STATUS: GRANTED LOCK_DATA: NULL ... LOCK_TYPE: RECORD LOCK_MODE: S,REC_NOT_GAP LOCK_STATUS: GRANTED LOCK_DATA: 10 ... Session1> update kris set value=11 where id =10;We change the isolation level to SERIALIZABLE and start a transaction (because, as stated in the manual, autocommit does nothing). We then simply look at a single row, and check PERFORMANCE_SCHEMA.DATA_LOCKS afterwards. Lo and behold, S-Locks as promised by the manual. Now, the setup for the deadlock with a second session, by doing the same thing: Session2> set transaction isolation level serializable; Session2> start transaction read write; Query OK, 0 rows affected (0.00 sec) Session2> select * from kris where id = 10; +----+-------+ | id | value | +----+-------+ | 10 | 10 | +----+-------+Checking the data_locks table we now see two sets of IS- and S-Locks belonging to two different threads. We go for an UPDATE here, because we chose existing rows and row locks, instead of non-existing rows and gap locks: Session1> update kris set value=11 where id =10; ... hangs ...and in the other connection: Session2> update kris set value=13 where id =10; ERROR 1213 (40001): Deadlock found when trying to get lock; try restarting transactionComing back to the first session, this now reads Session1> update kris set value=11 where id =10; ... hangs ... Query OK, 1 row affected (2.43 sec) Rows matched: 1 Changed: 1 Warnings: 0The timing given is the time I took to switch between terminals and to type the commands. Resolution Coming back to the support case, the Dev analyzed their code and found out that what they are emitting is actually the sequence Session1> SET TRANSACTION ISOLATION LEVEL SERIALIZABLE; Session1> START TRANSACTION READ WRITE; Session1> SELECT * FROM sometable WHERE id=10; -- implied S-lock granted on rec or gap -- ... Application decides INSERT or UPDATE Session1> SELECT * FROM sometable WHERE id=10 FOR UPDATEl -- lock escalation to X Session1> INSERT INTO sometable (id, ...) VALUES ( 10, ... ); Session1> COMMIT;so their code is already almost correct. They do not need the double read and also not the isolation level SERIALIZABLE. This is an easy fix for them and the deadlocks are gone, the world is safe again. So many things to learn from this: You won’t need SERIALIZABLE unless your code is broken. Trying to use it is a warning sign. A deadlock with an S-lock escalation means you need to check the isolation level. In SERIALIZABLE it is totally possible to deadlock yourself with a simple invisible SELECT and a lone INSERT or UPDATE. The ORM will remove you quite a lot from the emitted SQL. Do you know how to trace your ORM and to get the actual SQL generated? If not, go and find out. A server side trace will not save you - the server is a busy beast. It also cannot see your stackframes, so it can’t link your SQL to the line in your code that called the ORM. Yes, in the client side SQL trace, ideally you also want the tracer to bubble up the stack and give you the first line outside of the ORM to identify what is causing the SQL to be emitted and where in the code that happens. The deadlock information in SHOW ENGINE INNODB STATUS is painfully opaque, but learning to read it is worthwhile. In reproduction, using performance schema is much easier and makes the sequence of events much easier to understand. The server is not very good at explaining the root cause of deadlocks to a developer in the error messages and warnings generated. https://isotopp.github.io/2020/08/02/mysql-deadlocks-with-insert.html
0 notes
Text
Security Dictionary
Krak Des Chevaliers - Crusades era castle held by the Knights Templar, had an outer ring and inner ring. Eventually fell when the Ottomans or whoever forged a letter from the head of the Templars telling them to surrender, and never fell due to weak defence. Also an example of defence in depth
Vulnerabilities - a potential weakness in something
Software Bug - sometimes a vulnerability
Exploits - attacks a vulnerability to compromise a system
Memory Corruption Attacks - the attacker changes what is in memory so that the program behaves differently, the most common type is a buffer overflow:
Buffer overflow - Attack on the stack, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory locations.
NOP sled - a technique used to circumvent stack randomisation in buffer overflow attacks. As stack randomisation and other runtime differences change where the program will jump, the attacker places a NOP sled in a big range of memory. This will slide the code execution down into the payload code, right next to the sled. No-operation is available in most architectures and it does nothing other than occupying memory and runtime.
Canary - buffer overflow protection modifies the organization of data in the stackframe of a function call to include a "canary" value that, when destroyed, shows that a buffer preceding it in memory has been overflowed. With the canary it is not going to prevent a malicious buffer overflow. You can find where the canary is in the stack and just fill an array with the canary so that it does not get triggered and alert the computer that a buffer overflow has happened.
Reflection
I was amazed by the Diffie-Hellman Algo presented in lectures but I couldn’t help postulate what negative ways it could be manipulated or how the algo was weak. I think the most serious limitation of Diffie-Hellman in its basic or "pure" form is the lack of authentication. Communications using Diffie-Hellman all by itself are vulnerable to man in the middle attacks. Ideally, Diffie-Hellman should be used in conjunction with a recognized authentication method such as digital signatures to verify the identities of the users over the public communications medium. Diffie-Hellman is well suited for use in data communication but is less often used for data stored or archived over long periods of time.
0 notes
Photo

Deep Dive into Java 9’s Stack-Walking API
The stack-walking API, released as part of Java 9, offers an efficient way to access the execution stack. (The execution stack represents the chain of method calls - it starts with the public static void main(String[]) method or the run method of a thread, contains a frame for each method that was called but did not yet return, and ends at the execution point of the StackWalker call.) In this article we will explore the different functionalities of the stack-walking API, followed by a look at its performance characteristics.
This article requires working knowledge of Java, particularly lambda expressions and streams.
Who Called Me?
There are situations when you need to know who called your method. For example, to do security checks or to identify the source of a resource leak. Every method call creates a frame on the stack and Java allows code to access the stack, so it can analyze it.
Before Java 9, the way most people would access the stack information was via instantiating a Throwable and use it to get the stack trace.
StackTraceElement[] stackTrace = new Throwable().getStackTrace();
This works but it is quite costly and hacky. It captures all the frames - except the hidden ones - even if you need only the first 2 and does not give you access to the actual Class instance in which the method is declared. To get the class you need to extend SecurityManager that has a protected method getClassContext that will return an array of Class.
To address those drawbacks Java 9 introduces the new stack-walking API (with JEP 259). We will now explore the different functionalities of the API followed by a look at its performance characteristics.
StackWalker Basics
Java 9 ships with a new type, the StackWalker, which gives access to the stack. We will now see how to get an instance and how to use it to execute a simple stack walk.
Getting a StackWalker
A StackWalker is easily accessible with the static getInstance methods:
StackWalker stackWalker1 = StackWalker.getInstance(); StackWalker stackWalker2 = StackWalker.getInstance(RETAIN_CLASS_REFERENCE); StackWalker stackWalker3 = StackWalker.getInstance( Set.of(RETAIN_CLASS_REFERENCE, SHOW_HIDDEN_FRAMES)); StackWalker stackWalker4 = StackWalker.getInstance(Set.of(RETAIN_CLASS_REFERENCE), 32);
The different calls allow you to specify one option or a set of them as well as the estimated size of the number of frames to capture - I will discuss both further below.
Once you have your StackWalker you can access the stack information using the following methods.
The forEach Method
The forEach method will forward all the unfiltered frames to the specified Consumer<StackFrame> callback. So, for example, to just print the frames you do:
stackWalker.forEach(System.out::println);
Walk the walk
The walk method takes a function that gets a stream of stack frames and returns the desired result. It has the following signature (plus some wildcards that I removed to make it more readable):
<T> T walk(Function<Stream<StackWalker.StackFrame>, T> function)
You might ask why does it not just return the Stream? Let's come back to that later. First, we'll see how we can use it. For example, to collect the frames in a List you would write:
// collect the frames List<StackWalker.StackFrame> frames = stackWalker.walk( frames -> frames.collect(Collectors.toList()));
To count them:
// count the number of frames long nbFrames = stackWalker.walk( // the lambda returns a long frames -> frames.count());
One of the big advantages of using the walk method is that because the stack-walking API lazily evaluates frames, the use of the limit operator actually reduces the number of frames that are recovered. The following code will retrieve the first two frames, which, as we will see later, is much cheaper than capturing the full stack.
List<StackWalker.StackFrame> caller = stackWalker.walk( frames -> frames .limit(2) .collect(Collectors.toList()));
[caption id="attachment_149082" align="aligncenter" width="1024"]Published by Rory Hyde under CC-BY-SA 2.0 / SitePoint changed colorization and field of view and shares under the same license[/caption]
Advanced StackWalker
Continue reading %Deep Dive into Java 9’s Stack-Walking API%
by Arnaud Roger via SitePoint http://ift.tt/2mcOq5c
0 notes