#symmetric encryption
Explore tagged Tumblr posts
Text
lmaoo i could probably pass the cc exam without even taking the course
4 notes
·
View notes
Text
Mathematics in Cryptography: Securing the Digital World
#Mathematics#Cryptography#Asymmetric Cryptography#Symmetric Cryptography#Post-Quantum Cryptography#Homomorphic Encryption#Quantum Cryptography#Cryptographic Agility#sage university bhopal
0 notes
Text

#Control IT
1 note
·
View note
Text
Slow-Burns - Part 3

PART 1 PART 2 PART 4 PART 5
I split this up in several, shorter parts because I know the feeling when you want to read a fic but don't have the time or energy to get through a 10k+ words one. Also if you hate my writing you can just read part 1 and then leave it. Win-win I guess?
Anyway, this is set after Thunderbolts so if you haven't seen it - spoilers I guess? It absolutely does not follow canon, but yeah better to be safe than sorry.
Summary: Bucky has fallen. Hopelessly. And the only thing more hopeless is his team trying to help him get to the end of this slow-burn.
Bucky x fem!SHIELD!reader
1.7K words
Fluff, ''normal'' violence and descriptions of injuries. For sure out of character stuff, but I am who I am. Your appearence is barely desribed what I can remember, I think your hair and a couple types what clothes you're wearing?
You're referred to as ''Agent'' and ''Sunshine'' in a desperate attempt from me to not use Y/N.
Let me know if there's anything else I should warn about.
Otherwise, enjoy :)
Bucky scanned the briefing file. Intel breach. Corporate sabotage. Medium risk, low collateral. High-tech infiltration. One scientist needed extraction. Half the mission screamed you - cyber-forensic work, silent infiltration, backdoor escape route.
He frowned. “She’s not coming?”
Yelena leaned back in her chair, sipping bad coffee from a novelty mug that read ‘Crime, But Make It Cute.’
“She’s not coming.”
Bucky’s heart skipped. “Why?”
“She has the day off,” Ava answered, scrolling through her own tablet.
“But we need someone who can spoof an encrypted relay system on the move,” he said, voice flat but tight. “That’s her.”
“Relax, grandpa,” John muttered. “We’ve got it covered. Ava rewrote a protocol last night, and Bob is flying overwatch.”
Bucky looked back down at the tablet, annoyed. Not at the team. Not at the mission. At the fact that it felt wrong without you. And he hated how that felt.
“She asked for the day off two weeks ago,” Yelena added, tapping through something on her screen. “She deserves it.”
Alexei, who had been uncharacteristically quiet, suddenly grinned like he’d been waiting for someone to ask.
“Is big day,” he said, voice full of pride. “I set her up with very nice man. Name is Luka. Banker. Hair like lion. Very symmetrical face.”
Bucky looked up, slowly. “…You what?”
“Date!” Alexei beamed. “They go to brunch. Then art museum. Maybe share pretzel. Classic courtship!”
The silence that followed was deafening. Bucky didn’t move.
“Wait,” John said, looking up from his file. “She’s on a date?”
“Yes!” Alexei slammed a celebratory hand on the table. “I make things happen!”
Yelena blinked. “With Luka? From your bowling team?”
“He does not just bowl! He reads books. Big hands. Gentle eyes.”
Ava smirked. “You sound like you’re in love with him yourself.”
“He is very huggable!”
Bucky barely heard any of it. He was still stuck on date.
Something cold settled under his ribs. He hadn’t known you were seeing someone. He hadn’t even thought to ask. You’d always been here, orbiting close. And now, without warning, you were… elsewhere. With someone. Laughing, maybe. Wearing something soft and light. Smiling the way you always did when you were teasing him - except it wasn’t him.
Alexei’s words filtered back in. “—and if it goes well, they go to second location. Maybe fondue. Is very romantic.”
Bucky pushed back from the table. “I’ll be on the jet,” he muttered.
Yelena watched him go, eyes narrowing. When the door slid shut behind him, she turned to the others. “Okay,” she said. “That man is not okay.”
Bob tilted his head. “Is this the part where he acknowledges his feelings and makes a healthy emotional decision?”
John scoffed. “More like he’ll sit alone in the cargo bay and think about how her laugh sounds.”
Alexei frowned. “But she deserves strong man with good face symmetry. Why is Barnes sad?”
Ava deadpanned, “Because he’s been in denial for months.”
Two hours later Bucky sat strapped in, arms crossed, staring out the window like it had offended him personally. Every passing city below looked like a blur of decisions he hadn’t made. He thought about the last time you had touched his shoulder. How you’d laughed at one of Bob’s ridiculous stories. How you always leaned in just slightly when you talked to him, like what he said mattered more than anyone else’s words.
And now you were giving that attention to someone else. Some Luka.
He didn’t even know what the guy looked like, but his brain was helpfully painting the worst: tall, perfect teeth, probably called you beautiful without tripping over the word like Bucky always did in his head.
He wasn’t mad at you. Not even close. But he was angry with himself.
He’d wasted time. So much time, thinking if he just stayed close, you’d know. That he wouldn’t need to say anything. That maybe feelings could transfer telepathically through awkward silences and missed glances.
You were out there living. And he was up here… sulking.
He hadn’t wanted to make a move. He’d told himself he wasn’t ready. And now it might be too late.
Meanwhile, at a café in Brooklyn, you stirred your coffee absently as Luka droned on about crypto trends and some vacation he’d taken in the Alps with his “boys.” His shirt was tailored, his teeth were indeed perfect, and he had zero opinions on whether or not one should put glitter in combat boots.
You smiled politely. But your mind wandered.
To the Tower.
To the mission briefing you could have been part of.
To a certain grumpy super soldier with eyes like storm clouds and the emotional range of a wounded wolf.
God, you missed him already.
The Tower was quieter than usual that night. Post-mission debriefs were filed. John had gone out. Yelena and Ava were holed up somewhere with wine and a true crime doc. Alexei was in the sauna, probably giving unsolicited dating advice to someone over speakerphone.
And you? You were back.
Bucky noticed the moment you walked in. Not because you announced it - you never did - but because the air shifted.
He was in the common room, nursing a drink and reading the same paragraph of a book for the fourth time when he heard the elevator ding and your familiar footsteps cross the floor.
Then your voice. “Hey.”
He looked up.
You were dressed casually - simple, comfortable, but still carried yourself like you had a secret no one else was allowed to know. Except this time, you looked… tired. Not physically. Just disappointed in a way that sat deep in the shoulders.
Bucky sat up a little straighter. “You’re back.”
You sank onto the opposite end of the couch, kicking your shoes off with a sigh. “Yeah. Just got in.”
He hesitated. Then, carefully: “How was the date?”
You groaned and dropped your head back dramatically. “So bad. So impressively bad.”
Bucky’s heart did something traitorous - thrilled a little too much at the words. He worked hard not to show it.
“He was… polite. I’ll give him that. But every time I tried to steer the conversation toward something fun or personal, he’d redirect it back to himself. Or his investments. Or this stupid vacation he took with a group of guys who all wore matching swim trunks and called themselves the Wolfpack.”
Bucky blinked. “The what?”
“Right?” You said, eyes wide. “It felt like a sitcom where the punchline never came.”
A beat passed. He couldn’t help it—he smiled. Just a little.
You caught it. Your expression softened. “What?”
“Nothing. Just… sounds like hell.”
“It was. But the pretzel was good.”
You shared a quiet moment. Bucky’s chest felt warm and strange. He didn’t speak much, but he listened, and for once, he didn’t feel like he was drowning in his own silence. Maybe it was the soft tone in your voice. Maybe it was the way you’d looked at him when you walked in, like you’d missed him too.
He almost leaned in, just a little, like he was going to say something real for once.
And then Bob practically exploded into the room, arms wide, face beaming like a golden retriever who’d just spotted his favorite human.
Bucky immediately sat back, shoulders going tense.
You blinked, then smiled, bright and open. “Hey, Bob.”
Bob crossed the room in three giant steps and flopped onto the couch between you with a whoomp, knocking Bucky’s knee in the process. “You’re back! I missed you! Did you see the picture of Waffles I texted you?”
“I did,” you said, laughing. “The little hat was a nice touch.”
“He wore it willingly!” Bob looked at you with stars in his eyes. “Did you have a fun day off?”
You paused. “It had its moments.”
Bob turned to Bucky, clueless and radiant. “Didn’t we miss her, Buck? I kept saying we needed her on the mission. She would’ve handled that alarm system in two minutes.”
Bucky blinked slowly. “Yeah. We missed her.”
Your eyes flicked to Bucky, and something quiet passed between you again. But Bob, entirely unaware, continued cheerfully.
“I was thinking maybe we could all go get pancakes tomorrow. Celebrate a mission well done and your return. I know a place. They have whipped cream. And seasonal syrups. And they let you mix them. Which is chaos, but good chaos.”
You laughed again, and Bucky felt the familiar ache settle back into his chest. Because Bob wasn’t competition. He was just kind. Bright and open and honest in a way Bucky hadn’t been in years. Maybe ever. And you looked so comfortable around him. So light.
Bucky couldn’t even be mad. Not at Bob. Not at you. Just at himself, for still sitting there, wanting something and saying nothing.
He stood up quietly, draining the rest of his drink.
“Where you going?” You asked, noticing.
“Gonna turn in,” he said, avoiding your eyes. “Long day.”
“Goodnight,” you said softly.
He paused. Then looked at you - really looked at you. And for just a second, he let something show.
“Glad you’re back.”
And then he walked away.
Behind him, you watched him go. And for the first time since the date, you weren’t thinking about Luka at all.
Valentina slid a sleek folder across her desk. Inside was a badge, a keycard, a stack of onboarding documents, and a post-it with “Val we need a hot tub in the tower—seriously” scribbled in Yelena’s handwriting.
“I want you full-time, Agent. No more coming and going. A room and an official seat at the table. The team already treats you like you’re one of them. Might as well make it real.”
You bit the inside of your cheek. Your heart said yes immediately. But your brain, ever cautious, flipped through the mental index of what-ifs and escape routes.
“You sure you want to say no?” Val asked, arms folded, one brow arched.
You blinked. “Did I say no?”
“You hesitated.”
“I blinked.”
“Same thing in spy-speak.”
Then you thought about last night’s mission.
How Yelena had linked arms with you when you walked back into the jet, chattering about snack options. How Alexei had announced proudly that he’d protected “the two best sharpshooters in the world.” How Bob had quietly tucked your coat over your shoulders when you’d dozed off.
And how Bucky had looked at you before you parted ways. Like maybe he didn’t want to see you go.
You smiled softly.
“I’m in.”
#bucky barnes#bucky#bucky barnes x reader#james barnes#bucky barnes fic#bucky x reader#bucky barnes fanfiction#bucky x female reader#bucky x you#james bucky barnes
154 notes
·
View notes
Text
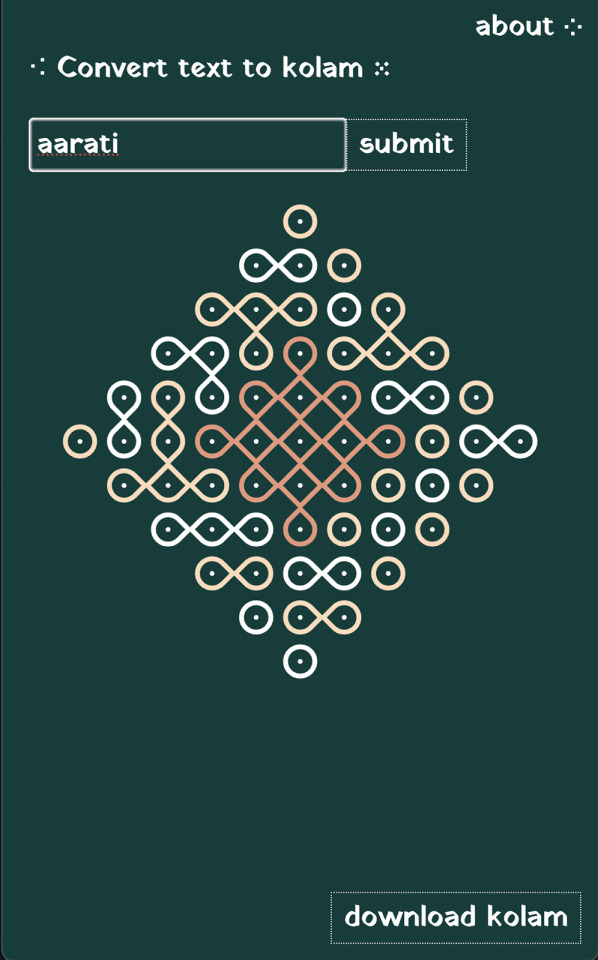
Aarati Akkapeddi, kolam.codes, (encryption tool)
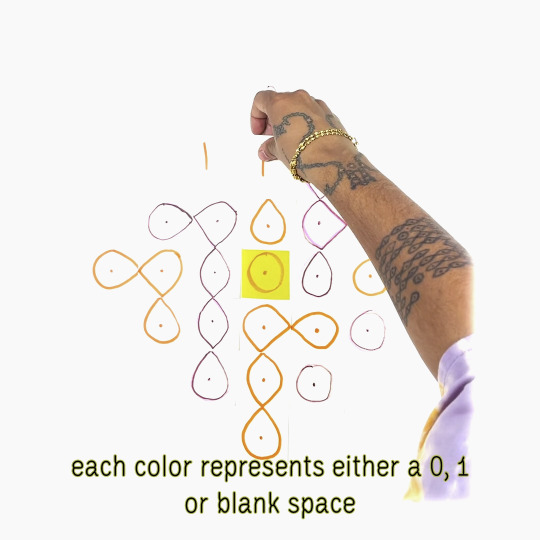
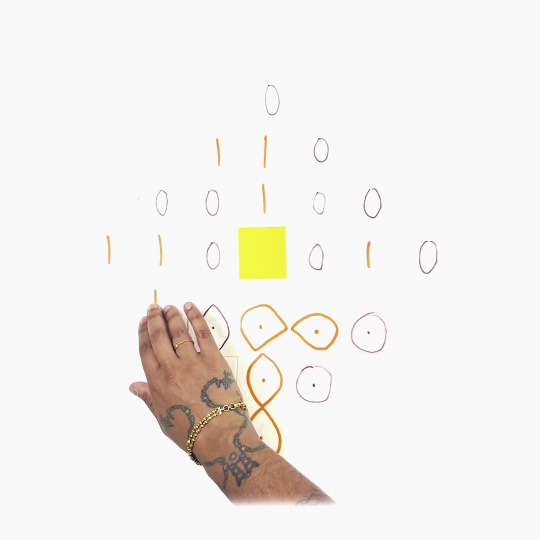
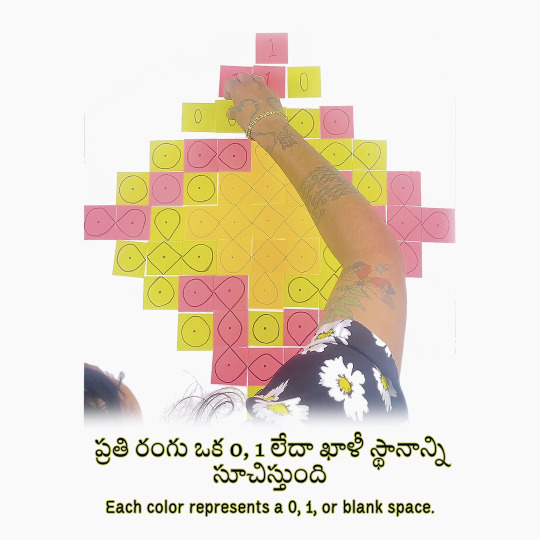
«Kolam (in Tamil) or Muggu (Telugu) is a traditional art form from South India. Kolams are auspicious drawings on the floor (usually at the threshold of the home) using rice flour. Kolams are traditionally made by women and created before sunrise. They comprise mathematically complex patterns that feature continuous intertwined lines. The drawings are notably ephemeral. They are disturbed throughout the day by wind and footsteps or as insects consume the tiny grains of flour. There are many variations of Kolam designs but there is one essential property: they must use continuous curves in which there are no breaks and the beginning and end-point are the same. Many Kolams also feature a grid of dots that follows the Fibonacci sequence. Not all Kolams are symmetrical but many use principles of recursion and repetition. I developed a computer program that allows me to translate text into Kolam designs. I first started working with kolams because I wanted to translate my paternal grandmother's name, Swarajyalaxmi into a kolam as part of my mourning ritual after her passing in 2022. kolam.codes is an extension of that work, allowing others to translate names or text of their choosing into kolam designs. To encode text into Kolam designs, I first translate each character into an eight-digit binary code (made from only 0s and 1s). I then map this code onto my starting grid of dots (moving left to right and top to bottom). I use the center of the grid as extra space to work with a grid that may contain more dots than characters. Using this grid as a basis, the algorithm then fills in the sections with looping components, making sure to never connect dots associated with "0" to those associated with "1".»















48 notes
·
View notes
Note
GIGI!! Give us some domestic Miraak HCs. Weird Things That Weird Man Does Around The House.

Doggie for attention
OUGH HELLO, HELLO, MY FRIEND, AND PLEASE FORGIVE ME FOR THE DELAY! I WAS SO HAPPY TO SEE YOUR ASK, BUT GAH, THE HORRORS—
Okay, alright. BEHOLD. Domesticated Miraak Made By Gigi™.
Miraak is fascinated by “mundane” items which he hoards compulsively. For example, spoons, buttons, scraps of fabric, and as a dragon through and through, anything shiny. He once built a tiny shrine out of empty glass jars, claiming they “radiate a strange essence”—it was just his dramatic way of describing their transparency.
His time in Apocrypha has left its mark. Miraak mutters to walls and furniture as if they’re sentient. “You’ve done well holding up the roof today,” he says to a wooden beam while he pats it with his hand thoughtfully. He might argue with the bookshelves, too, insisting they’re judging his choice of reading material.
Miraak has a compulsive need to organize everything into scrolls or piles of paper, even when it’s not practical. Grocery lists? Written on parchment with the most elegant quill he, of course, will craft, and sealed with wax. A love letter to Jia? Encrypted in Dragon Tongue and then stored in triplicate.
His morning routine involves chanting hymns like an Orthodox Priest, meditating, and “consulting the winds” (aka opening a window and divining how the weather’s going to be, blessed by Kyne as he is). If someone interrupts him, he declares the day ruined and probably sulks for hours.
If there are any creatures in the household, Miraak is convinced they hold ancient wisdom, and he’ll do whatever he can to take care of them. Milking Miss Hilda, Jia’s cow? Check. Shoeing Queen Alfsigr’s hooves, Jia’s horse? Check. Collecting the eggs from her chickens? Check. Feeding her swallows up on the roof and tending to their nests and their hatchlings? Check. Whistling in the wind and drawing Various Animals in Heljarchen Hall like he’s some sort of Gandalf Calling on Shadowfax? Check. I can just go on forever. He’s a huge, huge nature lover.
He’ll never admit it, but Miraak finds cleaning meditative. There’s something satisfying about imposing order on chaos. However, his “cleaning” often involves rearranging things into strangely symmetrical patterns—lucky for him, Jia does this as well all the time, so I only pity Lydia and Gregor who have to endure their obsession somehow...🥲
My Miraak isn’t the best at cooking at first—BUT! He learns from the very best, Jia, and he’s eager and quick to learn. Eventually, he treats cooking like a battle. He wields kitchen tools like sacred artifacts and narrates his every move in a grandiose tone. “Worry not, soul of my soul,” he tells Jia. “The Dragonborn of your kitchen shall tame this unruly potato.” He’s surprisingly good at it, though his meals tend to involve unnecessarily elaborate plating.
bonus headcanon because this ask made me unhinged: Miraak, when he manages to sleep, sleeps Weirdly. Blame it on the Dragonborn-ism and the otherworldly essence of his dreams in general, but either way, the man simply sleeps upright sometimes, while other nights, he’ll attempt to “connect with the Gods” by lying flat on the ground outside Heljarchen Hall, arms crossed over his chest, staring at a skyful of stars. It freaks Jia out when she finds him like this, but then again... She might join him herself... Don't mind her if she does...🤔
#okay i stop here because the more i think about this ask the more Domesticated Miraak comes to my mind aND I'LL NEVER EVER STOP—#LATHE YOU JUST ACTIVATED THE ROT™ AND NOW I ROTATE HIM IN MARCH SPEED IN MY HEAD#might return to this post with More. a promise and a threat 🫵#asks#miraak
34 notes
·
View notes
Text


Ethan spent the next three hours in his cluttered office, surrounded by stacks of old files and a mess of digital archives on his computer. Eventually, ISAAC's voice broke the silence. "Ethan, I have located several encrypted documents closely related to your search history. Shall I bring them up?"
After a vocal confirmation, ISAAC remotely accessed Ethan's computer and began displaying a series of decrypted files with some title variation of 'Chrysalis_2023'. Project Chrysalis had been one of his most secretive assignments while working with the government where he had been tasked with engineering a containment and analysis system for biological entities. The government's vague description alluded to 'non-terrestrial biological entities', which Ethan naively interpreted as some advanced biological research.
The digital files were heavily redacted but offered enough information to remind him that he had physical evidence as well. He eventually found a folder containing detailed schematics alongside his own annotations on the nature of the project. One document in particular, an incident report, caught his eye.
Entry Date: 04/12/2023 Subject: NTBE X-23 Humanoid organism measuring 1.8 meters (6 ft.) in height. Bipedal locomotion. Epidermis is a pale yellow tone. Facial structure similar to that of a human being but with eight black eyes arranged in a symmetrical pattern. Indecipherable markings around the eyes. Subject arrived unconscious and has not regained consciousness throughout the observation period. Subject X-23 was transferred from the recovery unit into the primary containment chamber at 1100 hours. Upon entering the containment unit, the subject's vital signs surged. Subject X-23 abruptly regained consciousness and exhibited erratic behavior. Witnesses claimed to have seen something move within the subject's skin. Vocalizations consistent with an unknown language were recorded (see audio log 0134-B1). Linguistic analysis is ongoing. The subject shortly underwent a rapid biological transformation. Epidermal surfaces split open, extruding long, vine-like protrusions tipped with bioluminescent nodules. The cranial structure split open longitudinally, revealing a maw lined with razor-sharp teeth. At 1400 hours, Subject X-23 initiated a violent attack on the containment unit. The material composition used proved insufficient. A containment breach occurred at 1405 hours. Specimen X-23 lunged at Dr. ■■■■, inflicting a fatal laceration to the abdomen. Security personnel were authorized to terminate the threat. Subject X-23 was neutralized at 1410 hours. Residual specimens are being collected for further analysis. The containment unit is undergoing repairs and biohazard decontamination. Further research is on hold pending reevaluation of containment protocols.
#ts4#the sims 4#the ■■■■■■ legacy#ts4 legacy#the sims#I couldn't resist posting an extra chapter#love me some breached containment
60 notes
·
View notes
Text

Heinrich Becker, full name Heinrich Wilhelm Becker, is a 23-year-old Red Team mercenary working for the Mann Co. as an assistant Medic and experimental surgeon. He was born on October 13 in Berlin, Germany. At 178 cm tall and weighing 62 kg, he stands out for his unconventional appearance: black hair cut in a "wolfcat" style with shaved temples, cold blue eyes with a distinctive "corpse" cast, multiple facial piercings (a symmetrical "snakebite" on his lower lip, an additional labret on the left side and a diamond-encrusted septum), and a macabre drein-style tattoo on his left shoulder depicting torn flesh with many eyes inside.
His mental state is characterized by a complex of disorders: dissociative identity disorder diagnosed at age 12, narcissistic disorder, and marked psychopathic tendencies. In stressful situations, he involuntarily switches to German, compulsively touches his piercings and smokes menthol cigarettes one after another. Among his odd habits is collecting surgical instruments.
Henry's biography is a story of systematic violence. Born into a family of a famous surgeon and a socialite, he was emotionally and physically abused from childhood. His father saw him as a "failed experiment," his mother preferred to ignore his existence. His school years added to the domestic abuse with constant bullying from his classmates. At the age of 16, he made his first suicide attempt, which left scars on his wrists. It culminated in revenge against his father - at 18, Henry deliberately drove him to death during an "emergency operation", skillfully faking a medical error. He then ran away from home, changed his name, and eventually ended up in Mann Co.
Even among the mercenaries, Henry stands out for his cruelty and cold calculation. Ludwig took him on as an apprentice, interested in his "unique psychopathology". Despite his constant conflicts with all members of the team, Heinrich shows unexpected loyalty to the Scout, which remains one of his few human traits.
Among Henry's odd traits is his habit of keeping an encrypted diary where he details his "experiments" with other team members. In the pocket of his robe, he constantly carries his father's dried ear as a kind of "talisman". Despite the strict rules, he is the only one allowed to smoke in Medic's lab. As Ludwig himself characterized him in his medical notes: "A living example of how hatred can become the perfect surgical instrument."
15 notes
·
View notes
Text
Pick something to steal from my room
Tagged by @1425fivefive thank you!!! I did this a few months ago, but have accumulated even more items since then.
Tagging: @jusst-you-race @colapoint @fueledbyremembering @wanderingblindly & @wisteriagoesvroom :D
12 notes
·
View notes
Text
🔒
For the next two weeks I will be focusing on encryption for PierMesh. The roadmap looks like this (though not necessarily in this order):
Sort out/update the cryptography packet
Node to node ECDH key derivation
Symmetric key encryption/decryption for node to node
BVFS integration for the WebUI for keypair storage
SubtleCrypto keypair generation
Bubble cryptography packets
Peer to peer SubtleCrypto ECDH key derivation
SubtleCrypto symmetric key encryption/decryption
Peer to node cryptography using previously derived tools
27 notes
·
View notes
Text
Just learnt that the blowfish algorithm was named that because it's creator really liked blowfish. THATS ALL. It's a symmetric encryption algorithm that encrypts messages. And bro names it blowfish algorithm. Because he likes blowfish 😭😭😭
5 notes
·
View notes
Text
Chiasmus

There's something that's been knocking around my head for a couple years now about Destiny's general narrative structure, and this entry brought it to mind and made me think. Bungie is keeping secrets, not deep in the files but in things unsaid. In the telling of the story, below the event horizon. In the shape of it.
"Do you know how to make a strong password?" he asked. "I don't know if I do," I said. "Tell yourself a story," he said. "Use that one good story you'll never forget, that you can carry forever. Let your story take odd turns and wear a few surprising marks, make sure it belongs to you, so you can keep it secret."
This echoes something I believe said by Savathun that the greatest form of encryption is secrets, because they can only be unlocked by true understanding. When I think about stories like Truth to Power, there is such deliberate structure and subtext to them despite being confusing and intentionally obscured, and that structure is seen elsewhere in Destiny. We've even seen Ikora and Arach Jallal discuss the narrative structure, called "chiasmus."
REY >> JALAAL
We are headed inward, as if moving from parent to child universe.
Then we proceed in reverse. Savathûn is revealed to be a fiction of Dûl Incaru. Dûl Incaru a simulation by Quria, and so on.
So in the end, Truth to Power moves outwards.
Just as Savathûn plans to move. In from our universe and out to the Distributary—
Or out from our universe to its parent.
JALAAL >> REY
Oh. I see. I see! A literary structure like that is called a chiasmus, and chiasmus means "crossing point"! Like a wormhole or a portal! It was hidden in plain sight.
Chiasmus is a sort of chiral structure defined as a "reversal of grammatical structures in successive phrases or clauses – but no repetition of words", and this achieves a fascinating effect; it leads you down a path of understanding, and sometimes does so by leaving your understanding up to the inferrence of the structure itself rather than stating the point directly and then leading you there
This is a scalable and somewhat flexible technique that can be used in sentences, paragraphs, or whole texts to convey very particular meaning. It's even used in the national anthem of the Netherlands, the oldest living national anthem (this one is interesting because it bounces back and forth—verse 1 mirrors verse 15, 2-14, 3-13, and so on until they meet at 8). I believe something like this is the basis for the entirety of Destiny's story; start with two presupposed points set in stone, set one as the start and one as the end, hide the end, and then slowly build from there. Bungie gets a lot of guff for perceived retcons, but in the broad strokes, and thematically, when it comes down to it, they know their stuff and have always seemed to have a long view in mind.
Chiasmus derives its effectiveness from its symmetrical structure. The structural symmetry of the chiasmus imposes the impression upon the reader or listener that the entire argument has been accounted for. In other words, chiasmus creates only two sides of an argument or idea for the listener to consider, and then leads the listener to favor one side of the argument.
We begin with resurrection in D1, new life. There's hints of Darkness, but it's buried in the lore and is explicitly taboo. It's confusing, but we slowly learn to see the world from an all-Light perspective. Year 2 we learn about the basics of Darkness via the Sword Logic, the Hive, and the Taken. Then, we press on and lose everything in year 4. We begin to learn more and more until year 5, Forsaken. Year 6 we get the Luna Pyramid, Unveiling, and the arrival. Then, in year 7, we get to *use* the Darkness. In Year 8, we begin to learn about it and seeing the unseen from Savathun via Deepsight, before learning about the Witness. This is also when we see one of our enemies go the other way, crossing our path by going from Dark to Light. Year 9, we learn about the Veil and a new perspective on Darkness, and year 10 we return to the center to defeat the First Knife and are left with only echoes of its victims and the Darkness that bound it
What is the main plan in Forsaken, year 5? For Uldren to enter the Watchtower with the Shard and the Darkness within him, where he unleashes the Voice of Riven, who acts as proxy. Riven enacts the curse upon her defeat, which is maintained inside Elusinia by Dûl Incaru, Eternal Return. Light and Dark to enter a hidden realm where a being in a tower creates a curse which is unleashed upon their defeat, and beyond which another being in a further nested realm maintains said curse. This is strikingly similar to the Witness: it enters the Pale Heart via the Traveler and the essence of the Veil, where it builds a tower and tries to make a sort of curse which infests the Heart. And when we defeated it, the energy from that process was released.
Guess what the mission where Crow entered the portal with the 15th Wish was called? Chiasmus.

Bungie loves secrets, but datamining makes them hard to pull off. They even put a reference to this in an unnamed entryegg in the API for Truth to Power:
O you wonderful curious things. Do you believe you're the only ones with the power to see what should not be seen? Did you believe you can use such power blithely? For your trespass, I would ruin your luck, wreak havoc on your drops, poison your engrams, and fill your lines with static. Thus I would curse you and dissipate the bond that ties you to your tasks. How frail you Guardians can be! How many millions have fallen silent, never to return, because the bond did not hold them strongly enough? But you have already cursed yourselves. You have walked the Anathematic Arc and glimpsed creation from below. You will never forget the tenuous, provisional framework you found here. You will never forgive the mortality and fallibility that underlies a world you thought was everything. Those who use this power to seek unearned knowledge will see more than they ever desired. There is a price for glimpsing the Cord. You will pay it.
This episode, we're learning about Maya, who has a direct link to the Veil, Vex, and Darkness via Clarity ("Take me to the garden’s seed. Take me. Take me. Take me. Take me. Take me. Take me. Take me. Take me—"), and now this strange Pyramid in act 3 of Echoes. Next, we have Fikrul, the Scorn (Dark Ether), and Mithtrax (Curse of Nezarec). And then we're ending on the Dreadnaught with Savathun, who hid the Veil, and Xivu Arath, who wants to emulate Oryx, the First Navigator with the implication that we will become Navigators. We reached the end of the line in defeating the Witness, but now we're beyond it. I think we're about to come full circle and see secrets beyond even the Veil.
Something else I like about this idea on a narrative and meta level; if the beginning and end of this leg of the story is already decided by its inherent structure, like life, then anything we do is futile. We will wind up there eventually, as everything does in the end. The only difference is the path we walk to get there
I. Guardians make their own fate. But what if the process by which they decide upon their own fate could be understood and manipulated?
But we are transcendent now; we walk a path as yet unimagined by both Light and Dark. What we do now— unshackled from HOPE—that is who we are; because only in the end are we free.
I.VII The cutting word is a doorway—the first syllable of hated salvation.
Better make sure you've got a strong password, wouldn't want to spoil the unveiling.

"What are you thinking about?" I asked. "When I was a little boy," Father said. "During the Before," I said. "Yes." He reached down to brush my hair. "I was recalling how very smart I used to be. When I was your age, I was a genius." "You're smart now," I said. He laughed hard. "Look around," he said. I always look around. "Miss nothing," he told me. Father was standing beside a big gray building. "This is what I want you to see," he said. The building had no doors or windows. "Do you know how to make a strong password?" he asked. "I don't know if I do," I said. "Tell yourself a story," he said. "Use that one good story you'll never forget, that you can carry forever. Let your story take odd turns and wear a few surprising marks, make sure it belongs to you, so you can keep it secret." Father kneeled, putting our faces close... "I want to show you something special," he said. "Something rare." I tried to imagine what that might be. "No," he warned. "You can't guess." Inside the gray building was a diamond wall...A projected sky floated above us. It wasn't our sky, alive with metal and light. Nothing about the grayness was wet and nothing looked alive. I had never seen a sadder piece of ground. "This was our world," Father said. "When I was your age." I touched the diamond wall. He watched my hand jump back. "Hot," I said. He laughed quietly. I shook my burnt hand, and it felt better. "Our world was this. The entire planet was a furnace. Acidic. Dead in so many ways. And I was your age." I was bored with the dead world. I looked at Father's face, asking, "Can we leave?" He started to reach for my hair again but decided not to. I was bored with everything. "When I was your age, people thought they knew almost everything. We had scientific laws and human truths, even a model of the universe. People carried pictures of the past and tried to have a clear vision of their difficult future. I didn't know everything, of course. But when I was a boy, I had every expectation of living a smart short life and learning quite a lot more. "Then the Before was finished. "You know why. "That's when everybody, particularly the smartest of us, learned that we knew nothing. We were children and our little ideas were toys, and the universe was cut apart with great ideas and magnificent, immeasurable potentials." Father stopped talking. I stepped away from the hot diamond wall. "Do you know what I wanted to show you?" Father asked. "Dead rock," I said. "Guess again." He wasn't happy with me. We stepped back into the real sun, the real world. I blinked and looked around, surprised by how green and bright everything was. How happy everything was. Even the saddest face was happy. "I know what you want me to see," I said. "Don't tell me," he said. I didn't tell him.
youtube

#the truth to power#destiny#the final shape#GO TO X#walk the vermicular path along sorrows road#devotion inspires bravery bravery inspires sacrifice and sacrifice...#lifes still all about that timing huh#from out of the darkness out future will come#if we leave the past behind |!lettinggo| we'll fly beyond the sun
10 notes
·
View notes
Text
Modern Cryptography
(stemandleafdiagram long-form post!)
~ 2900 words
As you may have guessed, I love cryptography and ciphers even though I still don’t know much about them. I think classical ciphers are super interesting stuff and I love breaking them but I realised I knew nothing cipher-y after the end of World War 2, so I sought to rectify that!
(This is SO long - I got quite carried away (I do apologise), and as I wanted to cover so much here there are some concepts I don’t explain very thoroughly, but there are so many resources online if you want to learn more! When explaining how different forms of encryption work, I will often use the names commonly used by other cryptographers in my examples. Alice and Bob are two people trying to communicate, while Eve (an eavesdropper) is trying to intercept their messages.)
Symmetric Encryption
The start of modern cryptography is not a definite thing (obviously so, as the “eras” of cryptography are just labels people use to refer to them generally) but I decided to start my timeline for modern cryptography in the 1960s, as during this time, research projects at the American company IBM (International Business Machines) led to the creation of a cipher called the Lucifer cipher.
This cipher was one of the first block ciphers to be made. A block cipher is a cipher that operates on blocks of 128 bits at a time. This is in contrast to a stream cipher, which encrypts 1 bit of data at a time. (In a way, you could consider classical ciphers stream ciphers) If the plaintext (un-encrypted data) is smaller than 128, padding schemes will add random data to it to make it up to 128. Modes of operation define how large amounts of data are encrypted. For example, the blocks of data can be encoded separately, or maybe the encryption of one block is affected by the previous encoded block of data.
The Lucifer cipher underwent a lot of alterations, and eventually the National Bureau of Standards adopted this altered version of Lucifer as the Data Encryption Standard, or DES, in 1977. Some of the alterations made that led to DES were actually quite controversial! For example, the key size in Lucifer was 128 bits, but only 56 in DES, which worried people who thought it would have been easier to brute force as it was shorter. It’s actually rumoured that the NSA (National Security Agency) did this so that the DES wasn’t too strong for them to break. Another change they added was the inclusion of something called S-boxes, which are effective at protecting against a form of attack called differential cryptanalysis. What I found really cool was that its effectiveness wasn’t talked about until much after, which suggests that the NSA knew about differential cryptanalysis 13 years before this information went public!
The DES is no longer secure enough for modern use, and in 2001 was replaced by the AES, or the Advanced Encryption Standard, which is its direct successor and is still used today. The reason that AES is more secure than DES is that the algorithm itself is more complex, but more importantly it uses longer key lengths. Using keys that are 128, 192, or 256-bit long means that the encryption is much stronger than using the 56-bit DES.
Lucifer, DES, and AES are all symmetric ciphers as well as being block ciphers. This means that the key used to encrypt the plaintext is the same key that is used to decrypt the data. Only some block ciphers are known publicly. DES and AES are the most famous of the lot, but other ones such as IDEA, Twofish, and Serpent exist too.
As a whole, encrypting with block ciphers is slower as the entire block must be captured to encrypt or decrypt, and if just 1 mistake is made the whole block can be altered. But, they are stronger than other ciphers. Each mode of operation also has its own pros and cons. If each block is encoded by itself then they can be encrypted in parallel (which is faster), but it’s prone to cryptoanalysis as two identical blocks of plaintext would produce two identical blocks of ciphertext, therefore revealing patterns. The other ways are much more complex and take more time to encrypt but are more secure.
For symmetric encryption to be used, both parties need to agree on the same key for the message to be shared secretly, which is a massive problem. How can the key be transferred securely?
Key Exchange
A year before the implementation of DES, in 1976, another massive breakthrough was made. Researchers Whitfield Hellman and Martin Diffie created the Diffie-Hellman key exchange, which was a method to share encryption and decryption keys safely across an unsecured network. The way it works depends on one-way functions. Typically in maths, most functions are two-way, as using a function on a number is pretty easy to undo. However, Hellman and Diffie found out that while multiplying two prime numbers was very easy, factorising the product down to its primes again was excruciatingly difficult, and the difficulty only increases as the numbers get bigger.
Say Alice and Bob are trying to share a key using the Diffie-Hellman exchange. Firstly, both of them need to execute a function in the form G^a mod P. P must be prime, and G and P are shared publicly so Alice and Bob can agree on them. The numbers are massive (usually 2048 bits) to make it harder to brute force, and they are generated randomly. Alice and Bob each choose different numbers for a, and run their functions. They will get different answers and they share their answers with each other publicly. (This is the public key) Then, Alice and Bob run another function in the form G^a mod P, but G is set to the other person’s answer. The value of a and P stay the same, and Alice and Bob arrive at the same secret answer. The secret answer can then be used to encrypt the message! (This is the private key)
Now, let’s say Eve wanted to find out what the key was. She intercepts their messages, but even though she has the exact information Alice and Bob shared with each other, she doesn’t know what the secret key is unless she solved the original equation, making this key exchange very secure! Modular arithmetic (the mod P part of the equation) is notoriously hard to reverse. If 2048-bit numbers are used, then brute forcing it requires 2^2048 numbers.
Asymmetric Encryption
The Diffie-Hellman key exchange was huge - I mean, any technology created 50 years ago that’s still in use must be pretty good, but it really only shone for sharing keys, not for encryption. For example, the issue with sending communication such as emails using Diffie-Hellman was that both parties needed to be online for a key to be generated as information needs to be mutually shared in the process, so you couldn’t just send an email using it whenever you wanted, which was a shame. However, one particular thing it did lead to was the invention of asymmetric encryption.
In 1977, the idea of public key cryptography (also invented by Diffie) came to fruition in the form of RSA. Named after its creators (Ron Rivest, Adi Shamir, and Leonard Adleman), the RSA works by all users having a public key, which is accessible by everyone, so anyone wanting to send that user a message just needed to search for it. The sender encrypts the message with the recipient’s public key, and then when the recipient comes online they are able to decrypt it with their own private key that’s not shared with anyone. It also uses an one-way function like the Diffie-Hellman exchange, albeit a more complex one. RSA is still used today for things like sending messages or visiting secure websites, and the keys tend to be 2048 or 4096 bits long so that they are hard to break. 1024-bit RSA was disallowed in 2013.
Encrypting via public key and decrypting via private key is great for keeping sensitive information safe, but what if you encrypted with your private key and the message was decrypted with your public key? The purpose of this encryption is to prove the sender is who they say they are - if the public key can’t decrypt the message then either the wrong key was used or the message has been meddled with in transit. To keep the message secure the sender could encrypt with their private key and also the recipient’s public key so only they could decrypt and read it. If the message is particularly long, the digital signature can be applied to a hash of the original message, rather than the whole thing. The RSA was the first to have this dual functionality.
So, there we go - the two main encryption types used today: symmetric and asymmetric. Symmetric encryption is useful for large amounts of data in particular, while asymmetric is more secure, but is slower and requires more resources and therefore can be more expensive. In practice, many secure systems will use both symmetric and asymmetric ciphers. Although, the actual security of a message comes down to the length of the key used - the longer or more complex it is, the more secure the encryption is. As the number of bits increases, the total number of arrangements for these bits increases exponentially. The IBM website states that a 56-bit key could be brute forced in around 400 seconds, a 128-bit key would take 1.872 x10^37 years, while a 256-bit key would take 3.31 x10^56 years.
Going Quantum
It goes without mention as to how important modern cryptography is. These encryption methods are used to keep confidential information such as credit card details, messages, and passwords safe for users like you and me, but also maintains government security on a national level. It’s also vital for cryptocurrency and digital signatures (as mentioned before), as well as browsing secure websites.
A big threat to current cryptographic standards is the development of quantum computing, which are computers based on principles of quantum mechanics. I won’t go into detail on how quantum computers work, but using quantum mechanics they are able to do massive numbers of calculations simultaneously. Although quantum computers already exist, they aren’t powerful or capable enough to threaten our current encryption algorithms yet. But, researchers suggest that they could be able to within a decade. People could use a technique called “store now, decrypt later”, where they keep currently encrypted messages so that they can decrypt them when quantum computers are available. This could cause many problems in the future, particularly if they involve secrets on an international level.
Quantum mechanics can also be used in cryptography as well! Quantum cryptography, originally theorised in 1984 by Charles Bennett and Gilles Brassard, can be used to exchange keys even more securely than Diffie-Hellman, and is called QKD, or Quantum Key Distribution. The reason it’s so incredible is that data that’s secured using it is immune to traditional cryptographic attacks. Now, I’m no quantum physicist (or any type of physicist!) but I will try my best to explain how it works. It works by sending photons, which are light particles, from the sender (eg. Alice) to the receiver (eg. Bob). These photons are sent at different orientations and Bob can measure the photon’s polarisation when he gets them.
Let’s say that photons can be in a vertical, horizontal, or one of the two diagonal orientations. We can pass them through a polarised filter to find out what orientation they are in. The filters are also specifically oriented. A vertical filter would let the vertical photons through, block the horizontal ones, and let the diagonal ones in 50% of the time but at the cost of the ones that pass through being reoriented. Therefore, when a particular photon successfully passes through, it’s impossible to know whether it was originally diagonal or vertical. This is important as it means that it’s possible to detect if someone else has been eavesdropping as the polarisations would have been changed.
Bob can use two measurement bases to receive the photons Alice sent. One will capture vertical and horizontal orientations, and one will capture diagonal ones. Bob has no idea what orientation Alice used for each photon, so he switches between his bases randomly, and will get it wrong some of the time. This is fine, as Alice and Bob then compare to see which ones Bob got right, and the ones he correctly guessed are used as a key (each photon representing 1 bit). The key can then be used for other encryption methods, such as AES.
The reason this works is that if Eve wanted to pry, she has to guess which base to use as well when she intercepts the photons (so she will also make mistakes), but she has no way of checking whether her records are correct or not, unlike Bob. It’s impossible for her to obtain the key as well. What’s more, when she guesses wrong she will change the photon polarisation, so Alice and Bob know that she’s eavesdropping.
Quantum cryptography would have huge security benefits if implemented on a wide scale due to its ability to prevent eavesdroppers, and the fact that it would be resistant to quantum computers. However, it is still in development. One key drawback is the specific infrastructure that is needed, and fiber optic cables have a limited range. This means that the number of destinations the data could be sent to is limited, and the signal cannot be sent to more than 1 recipient at any time.
As well as quantum cryptography, the NIST (The National Institute of Standards and Technology) and other cryptographers are working on other cryptographic algorithms that would stay secure even in the face of quantum computers. Ideas include lattice-based cryptography, hash-based cryptography, and code-based cryptography among others but none of them are at a point where they can actually be implemented yet.
However, one new idea that isn’t post-quantum but is gaining traction is Elliptic Curve Cryptography. Elliptic curve cryptography (ECC) is a form of asymmetric encryption that uses different points on an elliptic curve graph to generate keys in a more efficient manner than traditional methods. It creates shorter encryption keys, which means that less resources are needed while making the keys harder to break simultaneously. Improving the security of current systems just involves lengthening the keys, which slows down the encryption/decryption process, so the fact that ECC doesn’t need to do this gives it a big advantage. It is already used by the US government, iMessage, and Bitcoin, among others.
Sidenotes
With the maths of these encryption methods being so strong, one key vulnerability is the people that utilise these methods, which is no surprise. Side channel attacks are a way to break cryptography by using information physically leaked from it. One attack, called a TEMPEST attack, is a technique that can pick up electromagnetic transmissions from a device as far as 300m away. These are often done by the FBI, but honestly can be done quite easily by some nerd who has some money to spare and can sit in a car outside your window. By monitoring the radiation emitted from your computer screen, the attacker can spy on you and your data. Another thing that can be monitored is your power consumption. Cryptography is energy intensive, and this attack has been able to recover RSA private keys in testing. Other forms of attacks include measuring amount of time required to encrypt data, which can perhaps be used to find factors or exponents. To combat this, encryption methods can add timing noise as a countermeasure. Or, an attacker can listen to someone type to find out their passwords, but to distinguish different key presses a sophisticated machine learning model is needed. Side channel attacks have actually been around for ages but its use has been severely limited in that the attacker needs to be physically close to the victim. They could get easier with time, however, as smartphones and drones can act as microphones remotely.
Another cool thing I haven’t covered yet are hash functions, which can take in an input and map it to a string of characters that’s random but unique to the original data. The output is called a hash digest or hash value. A good hash function will mean that no two different inputs will have the same hash value, and all outputs are the same length, making it hard to guess original text length. It’s vital for digital signatures and storing passwords securely.
Finally, if anyone managed to get to the end, then thank you! I really love cryptography and I find it astounding that we’ve been able to develop it into such a complex yet intrinsic part of daily life. Honestly, I had so much fun researching for this post! Encryption and cybersecurity and the future of computing is so interesting and I’m really glad I decided to write this :)
Final final note you should totally go and read the Code Book by Simon Singh! Trust me trust me it’s so good...
4 notes
·
View notes
Text
An Overview of The Nihilist Cipher
Hello! If you're someone interested in ciphers, read ahead to learn a little about one of my long time favorite ciphers, the Nihilist Cipher.
The Nihilist cipher is a polyalphabetic substitution cipher, which basically means it relies on multiple shift ciphers applied to different letters in the text being encoded. If you're familiar with the Vigenère Cipher, Nihilist is pretty similar in a lot of ways.
I'll go through some history of the cipher, how to encode/decode using it, and how to conduct a known plaintext attack on it. I'll also go over how you might approach attacking it without a known plaintext (mainly because I think it's cool), but it won't be the main focus.
History
The Nihilist Cipher was first used by Russian nihilists against Russia's tsarist regime in the late 19th century. It's since been used as a basis for several ciphers with improved security used in WWII, notably the VIC cipher which is essentially an extremely complex hand-encoded cipher that's part of the Nihilist family.
"If [the VIC] cipher were to be given a technical name, it would be known as a 'straddling bipartite monoalphabetic substitution superenciphered by modified double transposition.'" David Kahn, Number One From Moscow
Usage
Encoding a message requires two things: A key and a Polybius square, known by you and the person you're communicating with. A Polybius square is one of these guys:
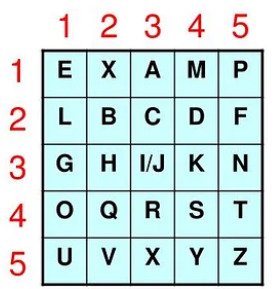
To use the cipher, you must first convert the plaintext into a numeric representation by mapping each letter to a number using the square. The mapping follows a (row, column) scheme, so the letter 'T' in the above square would become '45'. You'll notice that the square is 5x5, meaning there is 1 less square than there are letters in the English alphabet! This is typically solved by either choosing a square to represent 2 letters, differentiated using context by the receiver, or by simply leaving off an unused/infrequently used letter (often Q). It's also common to place a word at the start of the Polybius square, in this case "EXAMPLE" to offset the alphabet and avoid the mappings becoming trivial and obvious to attackers.
After we convert the plaintext to it's numeric representation, that's when the key becomes important. We first encode the key we picked using the Polybius square (i.e. the key MATH would become 14 13 45 32). Then, we repeat the key along the plaintext, and add each plaintext value to the key value to get the ciphertext!
To decode, the receiver must simply repeat the encryption process in reverse: repeating the key across the ciphertext, subtracting the key values, and translating the numeric plaintext back into English text. Because the encryption and decryption processes use the same key, the Nihilist Cipher is considered symmetric.
Known Plaintext Attack
Now we get into the fun part: How can we decode Nihilist encoded text without knowing the key? We will assume we know some ciphertext and the plaintext associated with it. Therefore, our goal is to use what we know to reveal the key, and use the key to decrypt the rest of the cipher. For example, assume we know that the first line of the Bee Movie script, "According to all known laws of aviation", results in the ciphertext "37 66 67 64 35 68 48 53 75 66 57 66 56 84 84 32 57 95 25 84 66 73 36 86 45 65 94 55 37 88 48 85 54".
Since the ciphertext is simply the result of adding the key to the plaintext, to find the key we only need to do the reverse and subtract the plaintext from the ciphertext!
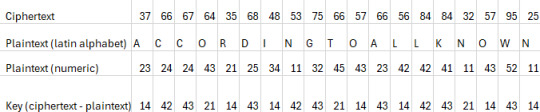
Even with only this short segment, we can see the repeating key is "14 42 43 21 14 43". Now we can repeat this key across the whole message and decrypt the Bee Movie script into numeric encoded plaintext.
At this point, you might be realizing where the next challenge lies. Unless you happen to be in a situation where you don't know the key yet somehow do know the Polybius square, this alone doesn't tell us very much! Since we've essentially converted our original problem into a simple substitution cipher, this is where we employ frequency analysis to figure out which number maps to which letter in the Polybius square. If you're up for a challenge you can do this manually, or use an online tool to analyze the frequency of each number and compare it to how often each letter of the English alphabet appears in typical text. Eventually, you'll be able to decode the Polybius square as the square below.
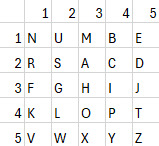
Ironically, the first snippet of The Bee Movie which we knew the plaintext of includes no 'E's, which are the most frequent letter in the English language, but letter frequencies of the full text would end up being much closer to the expected letter proportions.
Congratulations! You've now completed a plaintext attack on the Nihilist cipher and can sit down with a cup of tea for a bit of light reading .

Ciphertext-Only Attack
Now maybe that was too easy for you. Maybe you're a pro cipher-cracker, and you want to decode the Nihilist cipher without some "plaintext crutch". Here's how you can try to approach it! This method will need a large amount of ciphertext available, and relies on statistical analysis, plus some exploitation of the cipher's design to crack it.
The majority of this attack follows the same approach as a statistical attack on the Vigenère cipher. First you determine the key length by testing various key lengths, splitting the text up into groups that would be encoded with the same key, and computing the index of coincidence, which will be high (close to 0.068, the index of coincidence of English text) when the guessed key length is correct.
At this point, if this were the Vigenère cipher, we would have to go on to analyze the mutual index of coincidence between groups of ciphertext characters with the same key shifted by various amounts, but flaws in the Nihilist encoding system mean there's a good chance we can identify the key without this step!
Because of the way the Polybius square is set up, and the lack of modular arithmetic in the encoding method, every key letter value has exactly 25 possible ciphertext numbers that can result from that key. By comparing the ciphertext values encoded with the same shift, we can quickly identify or at least significantly narrow down the shift used to obtain those values! There are even a few cipher text values that immediately reveal what key was used to generate that cipher text (For example, a cipher text value of 30 can only be obtained using key=15). For a full list of possible ciphertext values generated by each key, check out this document I put together.
And that's it!
You are now a certified expert in all things Nihilist cipher. Go forth and use your new skill responsibly, leaving behind cryptic messages everywhere you go.
Happy decoding!

Sources:
https://www.cia.gov/resources/csi/static/Number-One-From-Moscow.pdf https://en.wikipedia.org/wiki/VIC_cipher
https://cyberw1ng.medium.com/nihilist-cipher-an-in-depth-look-at-the-cryptographic-technique-2023-b05b83551957
https://courses.cs.washington.edu/courses/cse163/20wi/files/lectures/L04/bee-movie.txt
17 notes
·
View notes
Text
#TheeWaterCompany
#CyberSecurity #Risk #Reward
!/bin/bash
BACKUP_DIR="/backup" DATA_DIR="/important_data/" ENCRYPTED_BACKUP="$BACKUP_DIR/encrypted_backup_$(date +%F).gpg"
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz $DATA_DIR gpg --symmetric --cipher-algo AES256 --output $ENCRYPTED_BACKUP $BACKUP_DIR/backup_$(date +%F).tar.gz rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Encrypted backup completed."
To refine encryption-related code, consider the following improvements:
Use Stronger Algorithms: Implement AES256 instead of AES128 for better encryption strength.
Add Error Handling: Ensure that the encryption process handles errors, such as failed encryption or permission issues.
Secure Storage of Keys: Use a secure method to store encryption keys (e.g., environment variables or hardware security modules).
Refined Script Example:
!/bin/bash
Encrypt sensitive data with AES256 and store encrypted backup securely
BACKUP_DIR="/backup" ENCRYPTED_BACKUP="/backup/encrypted_backup_$(date +%F).gpg" DATA_DIR="/important_data/"
Perform backup of important files
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz $DATA_DIR
Encrypt the backup with AES256
gpg --batch --yes --symmetric --cipher-algo AES256 --output $ENCRYPTED_BACKUP $BACKUP_DIR/backup_$(date +%F).tar.gz
Remove the unencrypted backup file
rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Backup and encryption completed securely."
This script enhances security by using AES256 and ensures encrypted files are properly handled.
To proceed with creating scripts for securing water companies' networks, we would outline some basic examples and operational strategies that could be implemented. Here’s a breakdown of each element:
Monitoring and Intrusion Detection
These scripts would monitor traffic and detect any suspicious activity on the network.
Example Script: Network Traffic Monitoring
!/bin/bash
Monitor network traffic and detect anomalies
LOGFILE="/var/log/network_traffic.log" ALERT_FILE="/var/log/alerts.log"
Use 'netstat' to monitor active network connections
netstat -an > $LOGFILE
Check for unusual activity, such as unexpected IP addresses
grep "192.168." $LOGFILE | grep -v "127.0.0.1" > $ALERT_FILE if [ -s $ALERT_FILE ]; then echo "Unusual activity detected!" | mail -s "Security Alert: Network Anomaly Detected" [email protected] fi
This script monitors network traffic using netstat, checks for connections from suspicious IP addresses, and sends an alert if any are found.
Intrusion Prevention (Automated Response)
This script would automatically take action to block malicious activity upon detection.
Example Script: IP Blocking on Intrusion Detection
!/bin/bash
Block suspicious IP addresses detected during intrusion attempts
SUSPICIOUS_IPS=$(grep "FAILED LOGIN" /var/log/auth.log | awk '{print $NF}' | sort | uniq)
for ip in $SUSPICIOUS_IPS; do iptables -A INPUT -s $ip -j DROP echo "$ip has been blocked due to multiple failed login attempts" >> /var/log/security_block.log done
This script automatically blocks IP addresses with failed login attempts, adding a layer of protection by preventing brute-force attacks.
Security Updates and Patch Management
Automated patch management ensures that all security vulnerabilities are addressed as soon as updates are available.
Example Script: Automatic Updates
!/bin/bash
Update system packages and apply security patches
echo "Updating system packages…" apt-get update -y apt-get upgrade -y apt-get dist-upgrade -y
Apply only security updates
apt-get install unattended-upgrades dpkg-reconfigure -plow unattended-upgrades
This script ensures that the system receives the latest security patches automatically, which is essential for keeping critical infrastructure secure.
Data Encryption and Backup
Regular backups and ensuring sensitive data is encrypted are vital.
Example Script: Data Encryption and Backup
!/bin/bash
Encrypt sensitive data and create backups
BACKUP_DIR="/backup" ENCRYPTED_BACKUP="/backup/encrypted_backup.gpg"
Perform backup of important files
tar -czf $BACKUP_DIR/backup_$(date +%F).tar.gz /important_data/
Encrypt the backup
gpg --symmetric --cipher-algo AES256 $BACKUP_DIR/backup_$(date +%F).tar.gz
Remove the unencrypted backup file after encryption
rm -f $BACKUP_DIR/backup_$(date +%F).tar.gz echo "Backup and encryption completed."
This script automates backups of sensitive data and encrypts it using gpg with AES256 encryption, ensuring that even if data is accessed illegally, it cannot be read without the encryption key.
Access Control
Strong access control is necessary to ensure that only authorized personnel can access critical systems.
Example Script: Access Control with Multi-Factor Authentication (MFA)
!/bin/bash
Ensure all users have MFA enabled for critical systems
Check if MFA is enabled on SSH login
if ! grep -q "auth required pam_google_authenticator.so" /etc/pam.d/sshd; then echo "MFA is not enabled on SSH. Enabling MFA…" echo "auth required pam_google_authenticator.so" >> /etc/pam.d/sshd service sshd restart else echo "MFA is already enabled on SSH." fi
This script checks if multi-factor authentication (MFA) is enabled on SSH logins, and if not, it enables it, ensuring an additional layer of security.
Security Audits
Regular audits help identify vulnerabilities and ensure the system is secure.
Example Script: Automated Security Audit
!/bin/bash
Run a security audit to check for common vulnerabilities
Check for open ports
echo "Checking for open ports…" nmap -p 1-65535 localhost > /var/log/open_ports.log
Check for outdated software
echo "Checking for outdated software…" apt list --upgradable > /var/log/outdated_software.log
Check file permissions for sensitive files
echo "Checking file permissions…" find /etc /var /usr -type f -name "*.conf" -exec ls -l {} \; > /var/log/file_permissions.log
Send the audit report to the administrator
mail -s "Security Audit Report" [email protected] < /var/log/security_audit_report.log
This script performs a security audit, checking for open ports, outdated software, and sensitive file permission issues, then sends a report to the administrator.
Conclusion
These scripts are designed to help secure the water companies' networks by automating essential security functions like monitoring, response to threats, patching, encryption, and access control. It’s important that these scripts be customized to the specific needs of each company, taking into account their existing systems, infrastructure, and any unique security concerns they may face. Additionally, regular updates to these scripts will be necessary as new vulnerabilities and threats emerge.
For a basic firewall script that blocks unauthorized access and monitors network traffic, here's an example:
!/bin/bash
Define allowed IPs (replace with actual allowed IP addresses)
ALLOWED_IPS=("192.168.1.1" "192.168.1.2")
Block all incoming connections by default
iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT ACCEPT
Allow traffic from specified IPs
for ip in "${ALLOWED_IPS[@]}"; do iptables -A INPUT -s $ip -j ACCEPT done
Log and monitor incoming traffic
iptables -A INPUT -j LOG --log-prefix "Firewall Log: " --log-level 4
This script sets a default block on incoming connections, allows traffic from specific IP addresses, and logs all traffic for monitoring.
4 notes
·
View notes
Text
PhD Blog Week 16
Courses
Solitons: More nonlinear differential equations, still very methods-course, hopefully we'll actually get to solitons soon
Rep theory: very fast due to use of slides, lots of technical details and not much big picture, but basically every sufficiently nice algebra is made of matrices
Hopf algebras: defined algebras, coalgebras, and bialgebras, so almost at the definition of a Hopf algebra. More reading notes off the screen, I wasted a good 30 minutes trying to show something was a coalgebra and it turned out I'd just written the comultiplication down wrong, somewhat embaressing given that the comultiplication is just given by the double angle formula from basic trig so I should have seen that, I guess that's what you get from trying to do maths in the evening
Supervisor Meeting
Actually succeeded in computing the Plucker relations in the meeting up to signs with some guidance, then spent two hours after the meeting trying to redo the calculation keeping track of the signs, then spent another two hours writing it up, but it's done! Now I just need to figure out the details of how this connects to the KP equation. Made the mistake of asking why they're called Plucker relations and had to sit there for 20 min as my supervisor explained how we can identify solutions to the KP equation with points in the embedding of an infinite dimensional Grassmannian into a projective variety, and I know just enough algebraic geometry to be slightly terrified
Teaching
First year maths tutorial was fine, except I had to teach myself how RSA encryption works, it's a neat application but it would be nice if they gave the tutors a more detailed solution.
Two out of three dynamical systems tutorials, one cancelled for weather. I think they went ok, we'll see how things go when it's not just revision of eigenvalues and Taylor series
Talks
The integrable systems talk this week was on a certain class of symmetric functions, and how they can be viewed as the coefficients of an expansion of some S_n action in Schur functions, so very close to a lot of the stuff I do, but way more technical. We went out for a meal afterwards which was nice, first time we've done that, hopefully we can have more regular meetings because it would be good to know other people in the group
6 notes
·
View notes