#syslog logging
Explore tagged Tumblr posts
Text
Atgeir specializes in Data Cloud solutions. Our teams of Data Architects and Engineers, boasting over 100 years of collective experience, leverage their extensive technical knowledge to empower clients within the Data Cloud ecosystem. We are committed to harnessing the synergies of Technology, Processes, and People to achieve tangible business results.
#technology staffing#Cost Management Suite India#log file anomaly detection#syslog anomaly detection#data governance consulting companies
0 notes
Text
Best Open Source Log Management Tools in 2023
Best Open Source Log Management Tools in 2023 #homelab #OpenSourceLogManagement2023 #TopLogAnalysisTools #CentralizedLoggingSystems #LogstashVsSyslogng #BestLogCollectors #FluentDAndCloudServices #ManageLargeVolumesOfLogData #GrafanaRealtimeMonitoring
When monitoring, troubleshooting, and auditing in today’s IT infrastructure, logs provide the low-level messaging needed to trace down events happening in the environment. They can be an invaluable source of insights into performance, security events, and errors that may be occurring across on-premises, cloud, and hybrid systems. You don’t have to buy into a commercial solution to get started…

View On WordPress
#Best Log Collectors#Centralized Logging Systems#Efficient Log Data Visualization#FluentD and Cloud Services#Grafana and Real-time Monitoring#Logstash vs. Syslog-ng#Manage Large Volumes of Log Data#Open Source Log Management Solutions 2023#Secure Log Data Transfer#Top Log Analysis Tools
0 notes
Text
Your robotgirl has an intox kink, so you have her turn off her memory recorders, disable some of her higher functions (through custom inhibition software), and have her keep a channel open for incoming messages that are stored in her system log. When she comes to, she greedily opens an internal prompt and types cat /proc/syslog | grep -c ★. She rolls back over, overjoyed, and quietly repeats "14" to herself.
308 notes
·
View notes
Text
listen. listen what if i study for my exams by turning all the concepts i need to learn into characters and plots.
what if i talk about a cat made up of words. it likes eating them too, and will happily go and thieve away whatever book or document you've set aside and just eat it all. it'll give some back to you, though! you know, if you know the right command and you know what to look for.
its name is Chmod, and hanging from its collar are three tokens with numbers on it and if you grab the right token you could change the words written on its body and own it.
it leaves footprints made of words behind when it jogs, but not for long. they fade away in seconds, sent away to a mythical place called Varlog, where you can only enter if you have the right key.
anyway, this is my attempt to link together all the file manipulation commands for my exam, featuring:
cat (lets you view entire file)
head & tail (look, it's a cat, of course it has a head and tail, and each of them have 10 words each)
grep (the command you need to get words from the cat)
chmod (the name of the cat, and also the command you need to change file permissions)
logger (the command to add messages to var/log/syslog and look, i figured jogging was close enough, okay)
10 notes
·
View notes
Text
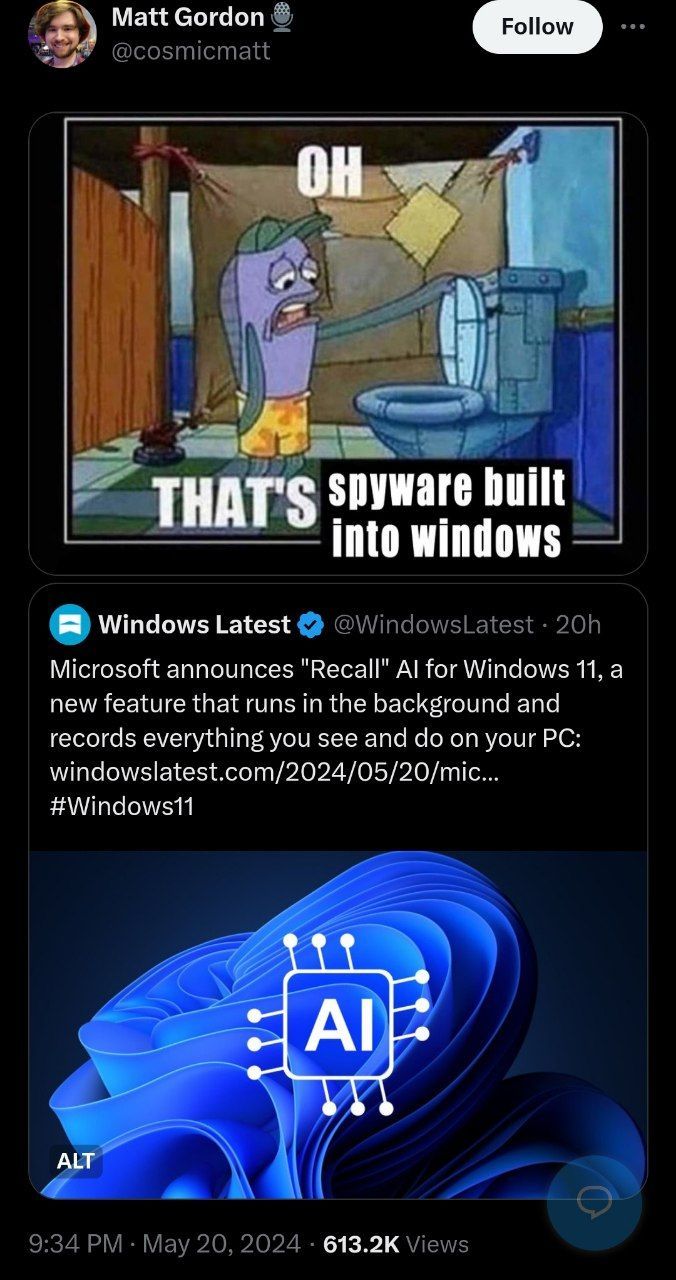
Windows (and Linux) has something called System Logs, or Syslog for short. It has existed in pretty much every machine since the 1980s.
It's come a long way since then, and records a staggering amount of information about your device and how you're using it. At least some of this information is shared with Microsoft for their improvement services.
Windows has always been Spyware. It's just this new service is just a lot easier to understand as "They can see my screen". But don't be mistaken - Microsoft already knows what you're doing without needing to actually physically see your mouse move and what you type. You can turn most of the sharing options off in the settings, but if you want true privacy you're better off using a Linux OS and manually clearing your Syslogs periodically.
102K notes
·
View notes
Text
Server Security: Analyze and Harden Your Defenses in today’s increasingly digital world, securing your server is paramount. Whether you’re a beginner in ethical hacking or a tech enthusiast eager to strengthen your skills, understanding how to analyze adn harden server security configurations is essential to protect your infrastructure from cyber threats. This comprehensive guide walks you through the key processes of evaluating your server’s setup and implementing measures that enhance it's resilience. Materials and Tools Needed Material/ToolDescriptionPurposeServer Access (SSH/Console)Secure shell or direct console access to the serverTo review configurations and apply changesSecurity Audit ToolsTools like Lynis, OpenVAS, or NessusTo scan and identify vulnerabilitiesConfiguration Management ToolsTools such as Ansible, Puppet, or ChefFor automating security hardening tasksFirewall Management InterfaceAccess to configure firewalls like iptables, ufw, or cloud firewallTo manage network-level security policiesLog Monitoring UtilitySoftware like Logwatch, Splunk, or GraylogTo track suspicious events and audit security Step-by-Step Guide to Analyzing and Hardening Server Security 1. Assess Current Server Security Posture Log in securely: Use SSH with key-based authentication or direct console access to avoid exposing passwords. Run a security audit tool: Use lynis or OpenVAS to scan your server for weaknesses in installed software, configurations, and open ports. Review system policies: Check password policies, user privileges, and group memberships to ensure they follow the principle of least privilege. Analyze running services: Identify and disable unnecessary services that increase the attack surface. 2. Harden Network Security Configure firewalls: Set up strict firewall rules using iptables, ufw, or your cloud provider’s firewall to restrict inbound and outbound traffic. Limit open ports: Only allow essential ports (e.g., 22 for SSH, 80/443 for web traffic). Implement VPN access: For critical server administration, enforce VPN tunnels to add an extra layer of security. 3. Secure Authentication Mechanisms Switch to key-based SSH authentication: Disable password login to prevent brute-force attacks. Enable multi-factor authentication (MFA): Wherever possible, introduce MFA for all administrative access. Use strong passwords and rotate them: If passwords must be used,enforce complexity and periodic changes. 4. Update and Patch Software Regularly Enable automatic updates: Configure your server to automatically receive security patches for the OS and installed applications. Verify patch status: Periodically check versions of critical software to ensure they are up to date. 5. Configure System Integrity and Logging Install intrusion detection systems (IDS): Use tools like Tripwire or AIDE to monitor changes in system files. Set up centralized logging and monitoring: Collect logs with tools like syslog, Graylog, or Splunk to detect anomalies quickly. Review logs regularly: Look for repeated login failures, unexpected system changes, or new user accounts. 6. Apply Security Best Practices Disable root login: prevent direct root access via SSH; rather,use sudo for privilege escalation. Restrict user commands: Limit shell access and commands using tools like sudoers or restricted shells. Encrypt sensitive data: Use encryption for data at rest (e.g., disk encryption) and in transit (e.g., TLS/SSL). Backup configurations and data: Maintain regular, secure backups to facilitate recovery from attacks or failures. Additional Tips and Warnings Tip: Test changes on a staging environment before applying them to production to avoid service disruptions. Warning: Avoid disabling security components unless you fully understand the consequences. Tip: Document all configuration changes and security policies for auditing and compliance purposes.
Warning: Never expose unnecessary services to the internet; always verify exposure with port scanning tools. Summary Table: Key Server Security Checks Security AspectCheck or ActionFrequencyNetwork PortsScan open ports and block unauthorized onesWeeklySoftware UpdatesApply patches and updatesDaily or WeeklyAuthenticationVerify SSH keys,passwords,MFAMonthlyLogsReview logs for suspicious activityDailyFirewall RulesAudit and update firewall configurationsMonthly By following this structured guide,you can confidently analyze and harden your server security configurations. Remember, security is a continuous process — regular audits, timely updates, and proactive monitoring will help safeguard your server against evolving threats. Ethical hacking principles emphasize protecting systems responsibly, and mastering server security is a crucial step in this journey.
0 notes
Text
What is Syslog? A Simple Guide to Understanding System Logging
If you’ve ever wondered, “What is Syslog?” you’re in the right place! Imagine your computer, router, or even a network printer keeping a diary of everything they do: every error, task, or important event. Syslog is the system that collects all those diary entries from different devices into one central place, making it easy for people to check what’s going on, fix problems, or keep things running smoothly.

In this article, I’ll explain what is syslog, break down its main parts, show how it works, and share three use cases with sample log messages to make it crystal clear.
What is Syslog, Anyway?
So, what is syslog? In simple terms, syslog is a way for devices like computers, servers, routers, or even printers to send short notes (called log messages) about what they’re doing to a central “diary” called a syslog server. These notes might say things like “I got an error,” “Someone tried to log in,” or “I just printed a document.” By collecting all these messages in one place, syslog helps IT teams, office managers, or security teams keep track of what’s happening across a network, spot issues, and fix them fast.

Say, syslog is a school where every teacher writes notes about what happens in their classroom (errors), activities (or warnings), and sends them to the principal’s office to be stored and reviewed. That’s syslog: it’s the system that gathers and organizes all those tech “notes” so they’re easy to find and use. Whether you’re running a website, securing a network, or managing office equipment, syslog is the ultimate tool for keeping tabs on everything.
The Main Parts of Syslog
There are five main parts to form syslog, and those parts work well together.
Devices Sending Logs: These are the gadgets creating the logs, like computers, servers, routers, or printers. They’re the ones writing the “diary entries” about what’s happening, like an error or a completed task.
Related article: What is Hardware Asset Management? The Key to Streamlining IT Infrastructure
Syslog Messages: These are the actual notes written by the devices. Each message includes details like when something happened, what it was, and how serious it is (like “error” or “just normal”).
Network Connection: This is how the messages travel from the devices to the central diary. It’s like the mail system delivering notes over a network (like the internet or a company’s private network).
Syslog Server: This is the central “diary” where all the messages are collected and stored. It’s like the principal’s office holding all the notes in one place.
Syslog Software: This is the program that organizes and saves the messages on the server, like a librarian filing the notes so they’re easy to find. Common examples are software like rsyslog or syslog-ng.
These parts work with each other to make sure all the activity logs are created, sent, and stored properly.
How Syslog Works: The Workflow
So, how does syslog actually do its job? The workflow is simple. Here’s how it goes:
Something Happens on a Device: A device (like a server or printer) notices an event, like an error, a login attempt, or a completed task. It writes a short note called a syslog message to describe it.
The Message is Created: The syslog message includes key details: when it happened (timestamp), which device it came from, what type of event it was (like a printer or security issue), how serious it is (like “error” or “info”), and what happened.
The Message is Sent: The device sends the message over a network connection (like the internet or a company network) to the syslog server.
The Syslog Server Collects It: The syslog server receives the message and hands it to the syslog software.
The Software Organizes and Stores It: The syslog software sorts the message, saves it, and makes it easy for someone to check later. For example, an IT person can look at the logs to fix a problem or see what’s been going on.
This workflow is why syslog is so powerful. It takes all those scattered “diary entries” from different devices and puts them in one place for easy monitoring.
Related article: What is Device Management?
3 Common Use Cases for Syslog with Sample Messages
Syslog is used in tons of situations to keep track of what devices are doing. Here are three examples, each with a sample syslog message to show what the “diary entries” look like. These messages follow a typical format: timestamp, device name, type of event (facility), severity level (how serious), and the message (what happened).
1. Monitoring a Website Server for Errors
A company runs a website, and they want to know if the website crashes or has problems so they can fix it quickly. Syslog collects logs from the web server to track errors, like when the site goes down or a user can’t log in.
➡️ Syslog gathers all the error messages in one place, so the IT team can spot issues fast and keep the website running smoothly.
Sample Syslog Message:
Jun 12 2025 17:38:01 webserver1 httpd[error]: Website failed to load page due to database connection timeout
Now let’s break this message down a bit:
Timestamp: Jun 12 2025 17:38:01 (when it happened).
Device Name: webserver1 (the server hosting the website).
Facility: httpd (the web server software, like Apache).
Severity: error (it’s a serious problem).
Message: Describes the issue (database connection failed, so the page didn’t load).
What It Means: This message says that on June 12, 2025, at 5:38 PM, the web server (webserver1) had an error because it couldn’t connect to its database, so a page didn’t load. The IT team can use this to check the database and fix the issue.
2. Tracking Security Issues on a Company Network
A company uses syslog to monitor its firewall (a device that protects the network) to catch suspicious activity, like someone trying to hack in. Syslog collects logs about login attempts or blocked connections.
➡️ These logs help the security team spot potential attacks or unauthorized access, so they can block hackers or tighten security.
Sample Syslog Message:
Jun 12 2025 17:40:15 firewall1 auth[warning]: Failed login attempt from IP 192.168.1.100
What It Means: This message shows that on June 12, 2025, at 5:40 PM, the firewall (firewall1) noticed someone from IP address 192.168.1.100 tried to log in and failed. It’s a warning, so the security team might check if this IP is repeatedly trying to break in, which could be a hacking attempt.
3. Keeping Track of Printer Activity in an Office
In an office, a network printer sends logs to syslog to record its activities, like when it prints a document or runs out of paper. This helps the office manager know if the printer is working or needs maintenance.
➡️ Syslog collects all printer logs in one place, so the manager doesn’t have to check the printer itself to see what’s going on.
You might also like this: The 5 Stages of the Hardware Asset Management Lifecycle You Need to Know
Sample Syslog Message:
Jun 12 2025 17:42:30 printer1 lpd[info]: Printed document 'report.pdf' for user jane
What It Means: This message says that on June 12, 2025, at 5:42 PM, the printer (printer1) successfully printed a document called “report.pdf” for a user named Jane. The office manager can use this to confirm the printer is working and track who’s using it.
What is Syslog Message Format?
You might have noticed that each sample message follows a similar format. Here’s a quick breakdown of what’s in a typical syslog message:
Timestamp: When the event happened (e.g., Jun 12 2025 17:38:01).
Device Name: Which device sent the message (e.g., webserver1, firewall1, printer1).
Facility: What type of program or device the log came from (e.g., httpd for web server, auth for security, lpd for printer).
Severity Level: How serious the event is (e.g., error for serious problems, warning for something to watch, info for normal stuff).
Message: The details of what happened (e.g., “Website failed to load” or “Printed document”).

This format makes it easy to read and sort logs, so people can quickly find what they need, whether they’re fixing a website crash, checking for security threats, or managing office equipment.
Why Syslog Matters: Conclusion
So, what is syslog in a nutshell? It’s a system that acts like a central diary for all your tech devices, collecting their “notes” about what’s happening so you can monitor, troubleshoot, or keep things secure. By bringing together devices, messages, network connections, servers, and software, syslog makes it easy to stay on top of everything in a network. Whether it’s catching website errors, spotting hackers, or tracking printer use, syslog is the ultimate organizer for tech activities.
0 notes
Link
#Automation#cloud#configuration#containerization#deploy#DevOps#Docker#feedaggregator#FreshRSS#Linux#Monitoring#news#open-source#Performance#Privacy#RSSreader#self-hosted#Server#systemadministration#updates#webapplication
0 notes
Text
UpdraftPlus Premium 2.25.4.26
UpdraftPlus Premium The most popular and dependable plugin for backing up, restoring, and cloning WordPress sites. Malware, server failures, incorrect updates, or simply human negligence can all cause a WordPress site to fail. Hence the necessity to use UpdraftPlus. Installing WordPress straight away will guarantee the security of your website. So, why select UpdraftPlus Premium 2.24.2.26? Easy-to-use A user-friendly interface allows you to backup and restore data with the click of a button on a schedule that works for you. Trusted Not all backup plugins are the same. UpdraftPlus outperforms the competition by covering more use cases, supporting more servers, and receiving higher ratings. Comprehensive UpdraftPlus's flexibility and sophistication make it difficult to find a backup and restoration plugin that can compete. Why should you use UpdraftPlus? Backup: Manually or automatically create full backups of your WordPress installation, including files, databases, plugins, and themes. Maintain routines. Backups can be scheduled to run every 2, 4, 8, or 12 hours on a daily, weekly, bimonthly, or monthly basis. Restore the WordPress database from backups in the admin area. Features in UpdraftPlus Premium 2.24.2.26 General Among the most popular WordPress nulled plugins, it has the greatest rating (4.8 stars out of 5.0) and is ranked in the top 30. Designed to operate with any WordPress installation. WordPress Network/WPMU multisite is ready. Proven to successfully back up 100GB sites; file size is limited only by the web host. It can back up an infinite number of external databases and files. Adjustable hourly incremental backups Scheduling Allows for both immediate and scheduled backups (4, 8, 12, etc.) to be conducted manually or automatically. Timeframes can be expressed as hours per day, week, fortnight, or month. Allows for accurate timing changes. keeps several backup copies of files and databases. The time for the next scheduled backup is shown. Regularly decreasing the quantity of archived backups. Backs up before executing WordPress core updates and anytime plugins or dashboard themes are upgraded. Data Collection, Analysis, and Planning. UpdraftPlus Premium version 2.24.2.26 The steps performed during a backup are precisely recorded. The WordPress administrative interface should keep users updated on the status of backups and notify them to any issues. It alerts you when the backup is complete and includes file checksums to confirm that the backup is complete and undamaged. The "Debug/expert" setting allows you to browse an alternate set of SSL certificates, deactivate SSL certificate verification, and totally disable SSL. All logs can be provided to the Event Log / Syslog (Linux/UNIX) or Windows. With this new version, users may now report issues on Slack.
0 notes
Text
Resolving Issue 7644fg.j-7doll: A Step-by-Step Breakdown
Technical issues like "7644fg.j-7doll" can disrupt workflows and create significant challenges, especially in IT systems, software applications, or hardware configurations. If you’ve encountered this problem, you’re likely seeking actionable solutions and clear guidance.
This article unpacks issue 7644fg.j-7doll in detail, explaining its potential origins, how to identify it, and the steps needed to resolve it effectively. Along the way, we’ll also discuss best practices to prevent similar issues from recurring.
Understanding Issue 7644fg.j-7dollWhat is Issue 7644fg.j-7doll?The term "7644fg.j-7doll"
typically refers to a system error, software bug, or misconfiguration affecting performance. While the exact nature of this issue may vary depending on the context, it often involves:
Application crashesData processing errorsConnection failuresSecurity vulnerabilities
Common Environments Where It AppearsServer Systems: Configuration mismatches or incompatible
software installations.Software Applications: Bugs within the application code or dependency conflicts.Hardware Devices: Firmware glitches or communication errors.
Symptoms of 7644fg.j-7dollUnresponsive applications or systems.Error messages related to connectivity or file processing.
Unexpected system restarts or freezes.Causes of Issue 7644fg.j-7doll1. MisconfigurationIncorrect settings or parameter values within the system may trigger this issue.

2. Outdated SoftwareRunning older versions of software or firmware can lead to incompatibility with newer dependencies.
MisconfigurationIncorrect settings or parameter values within the system may trigger this issue.2. Outdated SoftwareRunning older versions of software or firmware can lead to incompatibility with newer dependencies.3. Hardware FailuresDamaged or malfunctioning hardware components can result in sporadic errors.4. Security BreachesUnauthorized access or malware can corrupt files and cause system instability.5. Dependency ConflictsUsing incompatible libraries, plugins, or drivers may lead to functionality errors.Step-by-Step Troubleshooting for Issue 7644fg.j-7dollStep 1: Identify the ContextPinpoint where the issue is occurring:Is it a specific application or the entire system?When did the issue first appear?What recent changes were made to the environment?Step 2: Review System LogsCheck error logs to identify detailed information about the problem.Use tools like Event Viewer (Windows) or syslog (Linux) to review logs.Step 3: Update Software and FirmwareEnsure that all applications, operating systems, and firmware are up to date.Use official repositories or manufacturer-provided updates to avoid compatibility issues.Step 4: Check for Dependency ConflictsVerify that all installed libraries and plugins are compatible with the current system version.Use dependency management tools like pip, npm, or apt to resolve conflicts.Step 5: Run Diagnostic ToolsFor hardware: Use diagnostic utilities like Memtest86 or manufacturer-specific tools to test components.For software: Run debugging tools to pinpoint problematic lines of code or scripts.Step 6: Reconfigure SettingsReset misconfigured parameters to default values.Test changes incrementally to ensure stability.Step 7: Perform a Clean InstallationIf the issue persists, back up critical data and perform a fresh installation of the affected application or operating system.
0 notes
Text
Was ist ein Aggregatorhost?

Ein Aggregatorhost ist ein zentraler Punkt in der IT- und Netzwerktechnik, der Daten oder Dienste aus verschiedenen Quellen sammelt, aufbereitet und an andere Systeme weiterleitet. Stell dir vor, er funktioniert wie ein logistisches Drehkreuz an einem großen Flughafen: Flugzeuge aus aller Welt kommen an, die Passagiere steigen um, und ihre Reisen werden effizient organisiert. In der digitalen Welt ist der Aggregatorhost so etwas wie ein digitaler Koordinator, der sicherstellt, dass alle Informationen genau dorthin gelangen, wo sie gebraucht werden. Ein Aggregatorhost kann Daten sammeln, filtern, analysieren oder zusammenfassen, bevor er sie weiterleitet. In einer Zeit, in der Unternehmen oft mit einer Flut von Informationen aus unzähligen Quellen jonglieren, sorgt ein Aggregatorhost für Ordnung und Struktur. Klingt nach einer technischen Spielerei, die nur für Nerds interessant ist? Ganz im Gegenteil – Aggregatorhosts stecken oft hinter alltäglichen Anwendungen, ohne dass wir es merken.
Wie funktioniert ein Aggregatorhost?
Die Hauptaufgabe eines Aggregatorhosts besteht darin, Daten aus mehreren Quellen an einem Ort zu bündeln. Dies können ganz unterschiedliche Daten sein: Log-Dateien von Servern, Sensordaten aus IoT-Geräten, Verkehrsdaten aus einem Netzwerk oder Kundendaten aus verschiedenen Abteilungen eines Unternehmens. Die gesammelten Informationen werden entweder direkt weitergeleitet, analysiert oder in einem bestimmten Format gespeichert, um sie später effizient zu nutzen. Ein Aggregatorhost übernimmt oft auch erste Filter- und Analyseaufgaben. Das ist besonders nützlich, wenn nicht alle gesammelten Daten tatsächlich relevant sind. Stell dir vor, du filterst in einem vollen Posteingang nur die wirklich wichtigen E-Mails heraus, bevor du sie an die entsprechenden Kollegen weiterleitest. Ähnlich arbeitet der Aggregatorhost: Er sorgt dafür, dass nur relevante und bereinigte Daten weiterverarbeitet werden.
Wo kommen Aggregatorhosts zum Einsatz?
Aggregatorhosts sind extrem vielseitig und werden in vielen Bereichen eingesetzt. Hier ein paar Beispiele, die zeigen, wie sie in der Praxis funktionieren: Netzwerküberwachung In der IT-Administration spielen Aggregatorhosts eine zentrale Rolle, wenn es darum geht, Log-Daten von Routern, Firewalls, Servern und anderen Netzwerkgeräten zu sammeln. Ein typischer Fall wäre ein Syslog-Server. Hier laufen alle Ereignisse und Fehlermeldungen zentral ein, sodass Administratoren schnell reagieren können, ohne jedes Gerät einzeln überprüfen zu müssen. IoT-Systeme Im Internet der Dinge (IoT) erzeugen unzählige Sensoren und Geräte eine unüberschaubare Menge an Daten. Aggregatorhosts sammeln diese Informationen und leiten sie an zentrale Plattformen oder Clouds weiter, wo sie analysiert oder zur Steuerung genutzt werden können. Ohne diese zentrale Sammelstelle würde jedes Gerät separat kommunizieren müssen – ein Albtraum für jedes Netzwerk. Unternehmensdatenintegration In großen Unternehmen gibt es oft Dateninseln: Kundendaten im CRM, Lagerbestände im ERP, Marketingdaten in anderen Tools. Ein Aggregatorhost bringt diese Daten an einem zentralen Ort zusammen. Das Ergebnis? Ein einheitliches Bild, das bessere Entscheidungen ermöglicht. Medien und Streaming Auch in der Welt des Content-Streamings kommen Aggregatorhosts zum Einsatz. Sie sorgen dafür, dass Inhalte von verschiedenen Quellen gesammelt und optimiert an die Nutzer ausgeliefert werden. Hier geht es oft darum, Latenzen zu minimieren und die Inhalte so effizient wie möglich zu verteilen.
Welche Vorteile bietet ein Aggregatorhost?
Die Vorteile eines Aggregatorhosts sind vielfältig, und sie liegen vor allem in der Zentralisierung und Vereinfachung von Prozessen. Durch den Einsatz eines solchen Systems wird es möglich, komplexe Datenflüsse überschaubar und effizient zu machen. Zentralisierung der Daten Ein Aggregatorhost sammelt alle relevanten Informationen an einem Ort. Das bedeutet weniger Chaos und mehr Übersichtlichkeit. Stell dir vor, du müsstest Informationen aus zehn verschiedenen Quellen manuell zusammenfügen – ein Albtraum. Mit einem Aggregatorhost passiert das automatisch. Effizienz Nicht alle Daten sind gleich wichtig. Ein Aggregatorhost filtert die irrelevanten oder redundanten Informationen heraus, bevor sie weiterverarbeitet werden. Das spart Zeit, Bandbreite und Rechenleistung. Skalierbarkeit Wenn ein Unternehmen wächst und die Menge der Daten zunimmt, kann ein gut konfigurierter Aggregatorhost problemlos mitwachsen. Er passt sich an die steigenden Anforderungen an und sorgt dafür, dass der Datenfluss nicht ins Stocken gerät. Flexibilität Aggregatorhosts können an verschiedene Bedürfnisse und Systeme angepasst werden. Egal ob in einem kleinen Unternehmen oder in einem globalen Konzern – die Lösung kann skaliert und konfiguriert werden, um genau das zu leisten, was gebraucht wird.

Photo by ThisIsEngineering
Gibt es auch Herausforderungen?
Natürlich ist nicht alles perfekt, und Aggregatorhosts bringen ihre eigenen Herausforderungen mit sich. Komplexe Integration Die Einrichtung eines Aggregatorhosts ist selten ein Plug-and-Play-Vergnügen. Besonders in Umgebungen mit vielen heterogenen Datenquellen kann die Integration knifflig werden. Single Point of Failure Wenn der Aggregatorhost ausfällt, kann das gesamte System ins Wanken geraten. Hier sind Redundanz und Ausfallsicherheitsstrategien entscheidend, um solche Risiken zu minimieren. Sicherheitsrisiken Da alle Daten durch den Aggregatorhost laufen, wird er zu einem sensiblen Punkt im System. Ein Angriff oder Datenleck an dieser Stelle kann gravierende Folgen haben. Ein robustes Sicherheitskonzept ist daher Pflicht.
Beispiele für Aggregatorhost-Lösungen
Es gibt zahlreiche Tools und Technologien, die als Aggregatorhosts fungieren können. Einige bekannte Beispiele sind: - Fluentd: Ein leistungsstarker Open-Source-Datensammler, der besonders in der Log-Analyse beliebt ist. - Logstash: Ein Teil des Elastic-Stacks, der speziell für die Verarbeitung und Weiterleitung von Log-Daten entwickelt wurde. - Apache Kafka: Ein verteiltes System, das in Echtzeit Datenströme verarbeitet und weiterleitet – perfekt für große Datenmengen. In der Praxis kommen Aggregatorhosts häufig in Cloud-Plattformen wie AWS oder Google Cloud zum Einsatz. Sie ermöglichen die nahtlose Integration von Daten aus IoT-Geräten oder anderen Quellen in die Cloud-Umgebung.
Fazit
Aggregatorhosts sind ein unverzichtbares Werkzeug in einer zunehmend vernetzten und datengetriebenen Welt. Sie helfen dabei, Informationen aus unzähligen Quellen zu bündeln, zu analysieren und sinnvoll weiterzuverarbeiten. Egal ob im IoT, in der Netzwerküberwachung oder bei der Datenintegration in Unternehmen – Aggregatorhosts machen den Unterschied zwischen Chaos und Struktur. Wer ihre Möglichkeiten richtig nutzt, kann nicht nur Zeit und Ressourcen sparen, sondern auch die Grundlage für effizientere Entscheidungen schaffen. Read the full article
0 notes
Text
Hướng dẫn triển khai Docker Graylog theo các bước chi tiết

Tài liệu để build Graylog được tôi sử dụng và tham khảo ở đây. Điều tôi làm chỉ là tận dụng cấu hình của họ và sửa lại để cho phù hợp với mục đích của mình. Lưu ý cấu hình mình đang sử dụng là 8 Cpus và 12 Gb Ram. Trong bài viết này, chúng tôi sẽ hướng dẫn bạn cách triển khai Graylog thông qua Docker để bắt đầu thu thập logs ngay lập tức.
1. Mô hình sử dụng
Ở mô hình này tôi sử dụng 3 container Graylog, opensearch, mongodb chúng liên lạc với nhau qua network : Graylog_net
Riêng container Graylog sử dụng expose port 9000:9000 để dùng truy cập trang web qua IP của host và các port khác dùng để nhận log các dịch vụ khác
"5044:5044" # Cổng cho nhận log từ Filebeat
"5140:5140" # Cổng cho nhận log từ syslog
"12201:12201" # Cổng cho nhận log từ GELF UDP
"13301:13301" # Cổng tùy chỉnh (thay thế cho dịch vụ khác)
"13302:13302" # Cổng tùy chỉnh khác
2. Cài đặt Docker Graylog
Đầu tiên sẽ tải xuống repo Docker github của mình
cd /opt/
git clone https://github.com/thanhquang99/Docker
Tiếp theo ta cần chạy file Docker compose
cd /opt/Docker/Graylog/
Docker compose up
Ta có thể tùy chỉnh biến trong file Docker compose để thay đổi user và password của Graylog hay opensearch. Nếu không thay đổi thì password mặc định của Graylog: minhtenlaquang
Bạn cũng cần sử lại cấu hình Graylog và opensearch sử dụng ram và cpu để phù hợp với máy của bạn. Thông thường opensearch sẽ chiếm 50% RAM và Graylog chiếm 25% RAM
Đợi 1 thời gian cho đến khi Docker compose chạy xong ta sẽ vào trang http://<ip-Docker-host>:9000. Với user: admin, password: minhtenlaquang
3. Tùy chỉnh tài nguyên sử dụng mà Graylog sử dụng
Các biến Graylog mà bạn cần lưu ý để có thể chỉnh sửa cho phù hợp với tài nguyên Graylog của mình:
processbuffer_processors: Số lượng bộ xử lý cho buffer xử lý.
outputbuffer_processors: Số lượng bộ xử lý cho buffer đầu ra (Elasticsearch).
processor_wait_strategy: Chiến lược chờ của bộ xử lý khi không có công việc để làm (yielding, sleeping, blocking, busy_spinning).
ring_size: Kích thước của ring buffer.
message_journal_enabled: Kích hoạt hoặc vô hiệu hóa message journal.
message_journal_max_size: Kích thước tối đa của message journal.
inputbuffer_processors: Số lượng bộ xử lý cho input buffer.
inputbuffer_ring_size: Kích thước của ring buffer cho input buffer.
retention_strategy: Chiến lược giữ lại dữ liệu (ví dụ: delete, archive).
rotation_strategy: Chiến lược xoay vòng chỉ mục (ví dụ: count, time).
retention_max_index_count: Số lượng chỉ mục tối đa được giữ lại.
rotation_max_index_size: Kích thước tối đa của chỉ mục trước khi xoay vòng.
rotation_max_index_age: Tuổi thọ tối đa của chỉ mục trước khi xoay vòng.
tcp_recv_buffer_size: Kích thước bộ đệm nhận TCP.
tcp_send_buffer_size: Kích thước bộ đệm gửi TCP.
discarders: Cấu hình số lượng và loại discarder để xử lý tin nhắn vượt quá giới hạn.
threadpool_size: Số lượng luồng trong pool của Graylog.
Tôi sẽ hướng dẫn bạn tùy chỉnh biến message_journal_max_size để test thử.
Ta cần xem lại thông tin các volume của Graylog
Docker inspect graylog
Ta sẽ sửa file
vi /var/lib/docker/volumes/graylog_graylog_data/_data/graylog.conf
Restart lại Graylog
docker restart graylog
Kiểm tra kết quả:
Kết Luận
Hy vọng bài viết này đã giúp bạn triển khai Graylog sử dụng Docker và áp dụng vào hệ thống của mình. Docker Graylog là cách triển khai Graylog, một nền tảng quản lý và phân tích log bằng Docker. Điều này giúp dễ dàng thiết lập, cấu hình và quản lý Graylog trong các container, đảm bảo tính linh hoạt, khả năng mở rộng và đơn giản hóa quy trình cài đặt. Docker Graylog thường đi kèm với các container bổ sung như MongoDB (lưu trữ dữ liệu cấu hình) và Elasticsearch (xử lý và lưu trữ log).
Nguồn: https://suncloud.vn/huong-dan-trien-khai-docker-graylog-theo-cac-buoc-chi-tiet
0 notes
Text
Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions
The NSE6_FNC-7.2, also known as the Fortinet NSE 6 - FortiNAC 7.2 exam, plays a key role as one of the elective exams for achieving the esteemed FCP in Network Security certification. If your goal is to successfully pass this NSE6_FNC-7.2 exam, then look no further than Certspots as your primary resource. Certspots is undoubtedly the best choice for you, offering up-to-date Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions. These are not just any questions; these are meticulously updated materials that will significantly increase your chances of achieving a high score in your Fortinet NSE6_FNC-7.2 exam right at the first attempt! Utilizing these Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions will also assist you in gauging your current preparation level. This is invaluable as it provides an opportunity for you to assess and subsequently enhance your preparation strategy for the final Fortinet NSE6_FNC-7.2 exam, ensuring that you are fully prepared when the time comes.
youtube
Fortinet NSE 6 - FortiNAC 7.2 (NSE6_FNC-7.2) Exam Description
To achieve the esteemed FCP in Network Security certification, a key requirement is to successfully pass the core examination along with one optional elective exam. It's important to note that these examinations should not be spaced more than two years apart. NSE6_FNC-7.2, also known as the Fortinet NSE 6 - FortiNAC 7.2, is one such elective exam that aligns with the FCP in Network Security certification.
The Fortinet NSE 6 - FortiNAC 7.2 exam is a comprehensive evaluation of your understanding and level of proficiency with FortiNAC devices. The examination is designed to test your applied knowledge of configuring, operating, and administering FortiNAC on a day-to-day basis. The examination's structure includes a variety of operational scenarios, configuration extracts, and troubleshooting captures to fully assess your ability to manage FortiNAC devices.
The Fortinet NSE 6 - FortiNAC 7.2 exam is specifically designed for network and security professionals who are responsible for the configuration and administration of FortiNAC within a network security infrastructure. Its purpose is to ensure that these professionals have the necessary knowledge and skills to effectively manage and secure their network environments using FortiNAC.
Studying Fortinet NSE6_FNC-7.2 Exam Topics
Successful candidates have applied knowledge and skills in the following areas and tasks:
Concepts and design
Explain access control
Explain information gathering and network visibility techniques
Explain isolation networks and the configuration wizard
Deployment and provisioning
Configure security automation
Configure access control on FortiNAC
Configure and monitor HA
Model and organize infrastructure devices
Explain and configure logical networks
Explain and configure MDM integration
Configure FortiNAC security policies
Network visibility and monitoring
Guests and contractors
Use logging options available on FortiNAC
Explain and configure device profiling
Options for rogue classification
Monitor network devices and device status
Troubleshoot endpoint connectivity and classification
Integration
Integrate with third-party devices using Syslog and SNMP trap input
Configure and use FortiNAC Control Manager
Configure and use group and tag information for network devices
Configure FortiGate VPN integration with FortiNAC
Preparation Tips To Pass The NSE6_FNC-7.2 Fortinet NSE 6 - FortiNAC 7.2 Exam
To excel in the NSE6_FNC-7.2 Fortinet NSE 6 - FortiNAC 7.2 Exam, it's crucial to adopt a methodical approach to your studies. Here are some tips:
Understand the Exam Objectives: Familiarize yourself with all the exam objectives and the topics they cover. Use them as a guide for your study plan.
Use the Available Study Materials: Fortinet provides various study materials, such as manuals, guides, and tutorials, which you can utilize to understand the exam concepts better.
Practice with Real Equipment: If possible, get hands-on practice with real FortiNAC equipment. This will enhance your understanding of the practical aspects of the exam.
Take Practice Exams: Regularly taking practice exams will help you assess your progress and identify areas of weakness. Remember, understanding why an answer is correct is just as important as getting it right.
Join Study Groups: Participating in study groups or forums can provide valuable insights from others who are preparing for the same exam.
Conclusion
In conclusion, this article provides comprehensive information about the Fortinet NSE 6 - FortiNAC 7.2 (NSE6_FNC-7.2) exam. It details the importance of the exam in achieving FCP in Network Security certification, the various topics covered in the exam, and effective methods to prepare for it. Utilizing the Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions, coupled with practical training and diligent study, can significantly increase one's chances of passing the exam on the first attempt. The value of this certification cannot be overstated in today's competitive job market, making this a worthwhile endeavor for any network and security professional.
0 notes
Text
Elevate your testing capabilities with the 730 Thermal Transient Test Set, meticulously engineered for precision and efficiency in today's demanding engineering and manufacturing environments. The 730 streamlines your workflow, offering the capacity to test up to 3600 units per hour.
The 730's responsive 10.1" industrial touch screen interface is designed for intuitive interaction and streamlined control. Its modern connectivity suite, including USB, network logging (syslog), and HDMI capabilities, ensures seamless integration into any test environment.
At the heart of the 730 lies unparalleled precision, with high-resolution data capture and accurate test pulse technology, setting new industry standards for testing accuracy. Its expansive range of test parameters, from 4ms to 250ms pulse duration and up to 2000mA current with a 19V test voltage capability, provides unmatched versatility across various product testing requirements.

The 730 Thermal Transient Test Set represents a significant advance over the 605 and 630 models. The 730 is a leap in technology that simplifies complexity while assuring dependable and precise outcomes. It’s designed for both traditional test labs and automated production lines. 605 and 630 legacy modes provide data alignment for smooth upgrade integration.
0 notes
Text
Um dia, no mesmo servidor rodando Ubuntu 20.04, notei muitas mensagens em /var/log/syslog: 1234CRON[1835247]: (root) CMD (/bin/bash /usr/local/bin/fail2ban_banned_db unban_db)rsyslogd: action 'action-6-builtin:omfile' resumed (module 'builtin:omfile') [v8.2001.0 try https://www.rsyslog.com/e/2359 ]rsyslogd: action 'action-6-builtin:omfile' suspended (module 'builtin:omfile'), retry 0. There…
View On WordPress
0 notes