#syslog
Explore tagged Tumblr posts
Text
[Lio] Ok. Question for my fellow plurals out here: do you ever get like... I’m not sure what to call it. “External” phantom shift/sensations/dysphoria/etc that aren’t yours and you’re like hmm is this anything
I’m getting some strong “my mental( psychic? phantom? whatever you want to call the like mental-energy-version of yourself that you feel especially in phantom shifts) body is Not matching who I am/who is fronting internally right now” and I’ve felt this before in various cases but I never really paid a lot of attention to it, is this a thing others have experienced and if so did it tend to coincide with anything? I’m trying to figure this one out
20 notes
·
View notes
Text
What is Syslog? A Simple Guide to Understanding System Logging
If you’ve ever wondered, “What is Syslog?” you’re in the right place! Imagine your computer, router, or even a network printer keeping a diary of everything they do: every error, task, or important event. Syslog is the system that collects all those diary entries from different devices into one central place, making it easy for people to check what’s going on, fix problems, or keep things running smoothly.

In this article, I’ll explain what is syslog, break down its main parts, show how it works, and share three use cases with sample log messages to make it crystal clear.
What is Syslog, Anyway?
So, what is syslog? In simple terms, syslog is a way for devices like computers, servers, routers, or even printers to send short notes (called log messages) about what they’re doing to a central “diary” called a syslog server. These notes might say things like “I got an error,” “Someone tried to log in,” or “I just printed a document.” By collecting all these messages in one place, syslog helps IT teams, office managers, or security teams keep track of what’s happening across a network, spot issues, and fix them fast.

Say, syslog is a school where every teacher writes notes about what happens in their classroom (errors), activities (or warnings), and sends them to the principal’s office to be stored and reviewed. That’s syslog: it’s the system that gathers and organizes all those tech “notes” so they’re easy to find and use. Whether you’re running a website, securing a network, or managing office equipment, syslog is the ultimate tool for keeping tabs on everything.
The Main Parts of Syslog
There are five main parts to form syslog, and those parts work well together.
Devices Sending Logs: These are the gadgets creating the logs, like computers, servers, routers, or printers. They’re the ones writing the “diary entries” about what’s happening, like an error or a completed task.
Related article: What is Hardware Asset Management? The Key to Streamlining IT Infrastructure
Syslog Messages: These are the actual notes written by the devices. Each message includes details like when something happened, what it was, and how serious it is (like “error” or “just normal”).
Network Connection: This is how the messages travel from the devices to the central diary. It’s like the mail system delivering notes over a network (like the internet or a company’s private network).
Syslog Server: This is the central “diary” where all the messages are collected and stored. It’s like the principal’s office holding all the notes in one place.
Syslog Software: This is the program that organizes and saves the messages on the server, like a librarian filing the notes so they’re easy to find. Common examples are software like rsyslog or syslog-ng.
These parts work with each other to make sure all the activity logs are created, sent, and stored properly.
How Syslog Works: The Workflow
So, how does syslog actually do its job? The workflow is simple. Here’s how it goes:
Something Happens on a Device: A device (like a server or printer) notices an event, like an error, a login attempt, or a completed task. It writes a short note called a syslog message to describe it.
The Message is Created: The syslog message includes key details: when it happened (timestamp), which device it came from, what type of event it was (like a printer or security issue), how serious it is (like “error” or “info”), and what happened.
The Message is Sent: The device sends the message over a network connection (like the internet or a company network) to the syslog server.
The Syslog Server Collects It: The syslog server receives the message and hands it to the syslog software.
The Software Organizes and Stores It: The syslog software sorts the message, saves it, and makes it easy for someone to check later. For example, an IT person can look at the logs to fix a problem or see what’s been going on.
This workflow is why syslog is so powerful. It takes all those scattered “diary entries” from different devices and puts them in one place for easy monitoring.
Related article: What is Device Management?
3 Common Use Cases for Syslog with Sample Messages
Syslog is used in tons of situations to keep track of what devices are doing. Here are three examples, each with a sample syslog message to show what the “diary entries” look like. These messages follow a typical format: timestamp, device name, type of event (facility), severity level (how serious), and the message (what happened).
1. Monitoring a Website Server for Errors
A company runs a website, and they want to know if the website crashes or has problems so they can fix it quickly. Syslog collects logs from the web server to track errors, like when the site goes down or a user can’t log in.
➡️ Syslog gathers all the error messages in one place, so the IT team can spot issues fast and keep the website running smoothly.
Sample Syslog Message:
Jun 12 2025 17:38:01 webserver1 httpd[error]: Website failed to load page due to database connection timeout
Now let’s break this message down a bit:
Timestamp: Jun 12 2025 17:38:01 (when it happened).
Device Name: webserver1 (the server hosting the website).
Facility: httpd (the web server software, like Apache).
Severity: error (it’s a serious problem).
Message: Describes the issue (database connection failed, so the page didn’t load).
What It Means: This message says that on June 12, 2025, at 5:38 PM, the web server (webserver1) had an error because it couldn’t connect to its database, so a page didn’t load. The IT team can use this to check the database and fix the issue.
2. Tracking Security Issues on a Company Network
A company uses syslog to monitor its firewall (a device that protects the network) to catch suspicious activity, like someone trying to hack in. Syslog collects logs about login attempts or blocked connections.
➡️ These logs help the security team spot potential attacks or unauthorized access, so they can block hackers or tighten security.
Sample Syslog Message:
Jun 12 2025 17:40:15 firewall1 auth[warning]: Failed login attempt from IP 192.168.1.100
What It Means: This message shows that on June 12, 2025, at 5:40 PM, the firewall (firewall1) noticed someone from IP address 192.168.1.100 tried to log in and failed. It’s a warning, so the security team might check if this IP is repeatedly trying to break in, which could be a hacking attempt.
3. Keeping Track of Printer Activity in an Office
In an office, a network printer sends logs to syslog to record its activities, like when it prints a document or runs out of paper. This helps the office manager know if the printer is working or needs maintenance.
➡️ Syslog collects all printer logs in one place, so the manager doesn’t have to check the printer itself to see what’s going on.
You might also like this: The 5 Stages of the Hardware Asset Management Lifecycle You Need to Know
Sample Syslog Message:
Jun 12 2025 17:42:30 printer1 lpd[info]: Printed document 'report.pdf' for user jane
What It Means: This message says that on June 12, 2025, at 5:42 PM, the printer (printer1) successfully printed a document called “report.pdf” for a user named Jane. The office manager can use this to confirm the printer is working and track who’s using it.
What is Syslog Message Format?
You might have noticed that each sample message follows a similar format. Here’s a quick breakdown of what’s in a typical syslog message:
Timestamp: When the event happened (e.g., Jun 12 2025 17:38:01).
Device Name: Which device sent the message (e.g., webserver1, firewall1, printer1).
Facility: What type of program or device the log came from (e.g., httpd for web server, auth for security, lpd for printer).
Severity Level: How serious the event is (e.g., error for serious problems, warning for something to watch, info for normal stuff).
Message: The details of what happened (e.g., “Website failed to load” or “Printed document”).

This format makes it easy to read and sort logs, so people can quickly find what they need, whether they’re fixing a website crash, checking for security threats, or managing office equipment.
Why Syslog Matters: Conclusion
So, what is syslog in a nutshell? It’s a system that acts like a central diary for all your tech devices, collecting their “notes” about what’s happening so you can monitor, troubleshoot, or keep things secure. By bringing together devices, messages, network connections, servers, and software, syslog makes it easy to stay on top of everything in a network. Whether it’s catching website errors, spotting hackers, or tracking printer use, syslog is the ultimate organizer for tech activities.
0 notes
Text
[Lio] We’re similar - we have ‘the dark’, which is a sort of primordial ooze - as far as we are aware it seems to be some sort of subconscious or dormancy space but also contain, like, little personality fragments/concepts. Given enough energy/incentive/whatever it needs, new people can coalesce from it.
Our system also has few hard rules beyond ‘don’t be a dick/make our collective life hard’, but our one internal rule is not to enter it after you’ve exited it, because anyone who does so for an extended time gets changed by whatever is in it. (No rules against if this happens involuntarily/without knowing of course, some have formed but not had contact with the rest of us and gone back in for whatever reason and come out months or years later very different.)
More and more lately im feeling like we as a system often don't "split", it's more like... There's a certain amount of raw material here, that could possibly coalesce into a new entity in many ways and for many reasons.
Sometimes it tries out vague forms that might not be permanent - but at the time, they still feel like part of us
150 notes
·
View notes
Text
Atgeir specializes in Data Cloud solutions. Our teams of Data Architects and Engineers, boasting over 100 years of collective experience, leverage their extensive technical knowledge to empower clients within the Data Cloud ecosystem. We are committed to harnessing the synergies of Technology, Processes, and People to achieve tangible business results.
#technology staffing#Cost Management Suite India#log file anomaly detection#syslog anomaly detection#data governance consulting companies
0 notes
Text
Best Open Source Log Management Tools in 2023
Best Open Source Log Management Tools in 2023 #homelab #OpenSourceLogManagement2023 #TopLogAnalysisTools #CentralizedLoggingSystems #LogstashVsSyslogng #BestLogCollectors #FluentDAndCloudServices #ManageLargeVolumesOfLogData #GrafanaRealtimeMonitoring
When monitoring, troubleshooting, and auditing in today’s IT infrastructure, logs provide the low-level messaging needed to trace down events happening in the environment. They can be an invaluable source of insights into performance, security events, and errors that may be occurring across on-premises, cloud, and hybrid systems. You don’t have to buy into a commercial solution to get started…

View On WordPress
#Best Log Collectors#Centralized Logging Systems#Efficient Log Data Visualization#FluentD and Cloud Services#Grafana and Real-time Monitoring#Logstash vs. Syslog-ng#Manage Large Volumes of Log Data#Open Source Log Management Solutions 2023#Secure Log Data Transfer#Top Log Analysis Tools
0 notes
Text
Your robotgirl has an intox kink, so you have her turn off her memory recorders, disable some of her higher functions (through custom inhibition software), and have her keep a channel open for incoming messages that are stored in her system log. When she comes to, she greedily opens an internal prompt and types cat /proc/syslog | grep -c ★. She rolls back over, overjoyed, and quietly repeats "14" to herself.
308 notes
·
View notes
Text
[Lio] I think.. even from the perspective of a traumagenic OSDD system, it’s still not generally a word we like to use. To us it brings up a mental image of someone changing or having something removed from them to create someone else - and generally that’s not how it seems to work for us. Rather, new people “form” or “appear” and they tend to have collected ambient unassigned personality fragments, emotions, and histories into a new person.
I understand why this is considered to some to be “splitting” - it’s not splitting off of one of the existing members rather than just splitting off from the brain’s subconscious. But regardless it always felt like the implication is that someone existing had someone split off of them.
At the end of the day we personally don’t care too much because there doesn’t seem to be an agreed upon term for this other than splitting (you could say it’s.. splitting hairs? Ok bad joke) but basically, yeah, we also wish there were other terms for it. “How often do new members form” might be a better way to ask this that includes other interpretations of the phenomenon rather than what ‘splitting’ brings to mind.
Kinda fervently wish that so many systems didn't use the word "splitting" to mean headmate creation so ubiquitously.
So many people seem to assume that every time a headmate is created it is through "splitting", so they use the word for it in every sentence they utter or type in regards to the subject.
There are polls asked, "How often do you split?"
Nevermind that there is some confusion to be had where "splitting" is a clinical term for something else entirely, that people with BPD are known to experience. Sometimes there are homonyms like that, and people can learn to live with it.
But, there are also a myriad of other ways that headmates/system members/alters can come to life.
And, at the very least, if you're making polls, questionaires, and otherwise talking about the experiences of plural systems community wide, you should use a broader phrase, like "creating new system members". It's longer, sure, but it's more encompassing of everyone's experiences.
#liolog#syslog#=it’s one of those things where I don’t think of it the way others seem to but I don’t really care what people call it#replies
86 notes
·
View notes
Text
listen. listen what if i study for my exams by turning all the concepts i need to learn into characters and plots.
what if i talk about a cat made up of words. it likes eating them too, and will happily go and thieve away whatever book or document you've set aside and just eat it all. it'll give some back to you, though! you know, if you know the right command and you know what to look for.
its name is Chmod, and hanging from its collar are three tokens with numbers on it and if you grab the right token you could change the words written on its body and own it.
it leaves footprints made of words behind when it jogs, but not for long. they fade away in seconds, sent away to a mythical place called Varlog, where you can only enter if you have the right key.
anyway, this is my attempt to link together all the file manipulation commands for my exam, featuring:
cat (lets you view entire file)
head & tail (look, it's a cat, of course it has a head and tail, and each of them have 10 words each)
grep (the command you need to get words from the cat)
chmod (the name of the cat, and also the command you need to change file permissions)
logger (the command to add messages to var/log/syslog and look, i figured jogging was close enough, okay)
10 notes
·
View notes
Text
being a fictive like (thinks of events in a cartoon and feels like youre gonna throw up and dissolve)
3 notes
·
View notes
Text
New Linux glibc flaw lets attackers get root on major distros

Source: https://www.bleepingcomputer.com/news/security/new-linux-glibc-flaw-lets-attackers-get-root-on-major-distros/
More info: https://blog.qualys.com/vulnerabilities-threat-research/2024/01/30/qualys-tru-discovers-important-vulnerabilities-in-gnu-c-librarys-syslog
6 notes
·
View notes
Text
We have something like this! For us it doesn’t have a visual or location representative but it is some sort of mental barrier. It feels to us a bit like the membrane on injectable medication bottles that a needle can pierce but which lets nothing else through - but it’s translucent. It’s the difference for us between cofronting and backseating - someone who is ‘behind’ a fronter can still talk with them and absorb info from outside, but isn’t really aware of what’s happening firsthand.
If they pass through the barrier though, they are affected by front - we do not know how or why, but being in front feels different than backseating out of front. It’s more intense - maybe because that person is taking in direct inputs from the external world, the body, etc. There have been times where someone is concerned that they feel ‘different than usual’ but by testing between fronting and backseating, it turns out this difference is the amplifying effect front has on whoever is in it.
So yes - I guess calling it a sort of dissociative or emotional barrier makes sense. It is like a veil of sorts for us too.
I've seen this concept mentioned a few times on systok (the name for the system side of TikTok), but I've never seen it mentioned here unless we ourselves brought it up, so I'd like to make... less of a coining post, and more of an introduction post, for the whole thing.
The concept is named "the veil" (sometimes capitalized as the Veil), and it refers to the invisible boundary between the front and the innerworld, or wherever else a headmate goes/"goes" (depending on your view of it) when they are not in front. For some, this boundary is unclear or blurry; for others, it's clear; for still others, it's more than one of the above. And there are, of course, systems who would not consider themselves to have a Veil. Nevertheless, for those it applies to, the concept may help explain a phenomenon many systems go through: a disconnect of memory and information between front and elsewhere.
The Veil, as a boundary, may itself serve as a type of amnesiac barrier in a system. For those unaware, an amnesiac barrier is what's considered to cause memory issues in systems with amnesia – it's a disconnect in memory between system members, which results in memory problems like not remembering what happened when someone else was fronting. The Veil, acting as a boundary between the front and elsewhere, also serves as a disconnect between the two, which can – in the case of this disconnect being an amnesiac barrier – result in memory not carrying over from one area to the other. Examples of this include not remembering what happened in the innerworld when fronting, or not being able to recall certain details in one area, but able to recall them in the other (we in particular have a hard time remembering names when we come into front, but a much easier time remembering in the innerworld).
However, I don't think this disconnect can only affect memory. In our innerworld, we have an easier time differentiating between one another and holding onto individual identity than we do in the front – a marked difference between the two areas. Perhaps we are an outlier of a case, but I would not be surprised if others find themselves having certain abilities in one area but not the other, or at least more skill at a particular ability.
So, now that that's explained (to the best of my ability as I understand the term), I'd like to hear the thoughts of other systems and plurals. Does this concept explain some things? Are there any adaptations or additions you would make to make it fit how your system works? Would you say you have a Veil, but not one that serves as an amnesiac barrier? How does that work for you? And are there any other questions or thoughts on the concept?
97 notes
·
View notes
Text
me:
my dad, who just opened my door:
me:
my dad: do you have hw to do today
me: yes.
my dad: i don’t know why i asked. your room is spotless which means you’re procrastinating
me: go read your syslogs and leave me alone
3 notes
·
View notes
Text
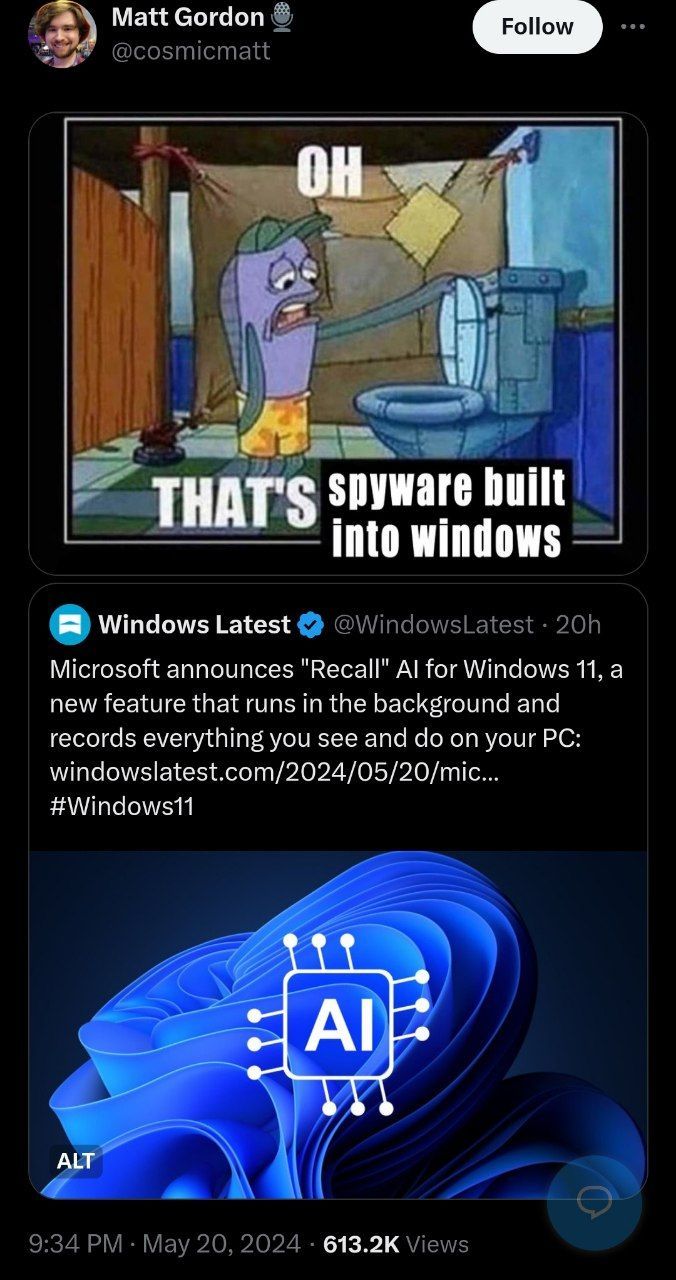
Windows (and Linux) has something called System Logs, or Syslog for short. It has existed in pretty much every machine since the 1980s.
It's come a long way since then, and records a staggering amount of information about your device and how you're using it. At least some of this information is shared with Microsoft for their improvement services.
Windows has always been Spyware. It's just this new service is just a lot easier to understand as "They can see my screen". But don't be mistaken - Microsoft already knows what you're doing without needing to actually physically see your mouse move and what you type. You can turn most of the sharing options off in the settings, but if you want true privacy you're better off using a Linux OS and manually clearing your Syslogs periodically.
102K notes
·
View notes