#tesla code secrets users
Explore tagged Tumblr posts
Text
A 25-Year-Old With Elon Musk Ties Has Direct Access to the Federal Payment System
A 25-year-old engineer named Marko Elez, who previously worked for two Elon Musk companies, has direct access to Treasury Department systems responsible for nearly all payments made by the US government, three sources tell WIRED. Two of those sources say that Elez’s privileges include the ability not just to read but to write code on two of the most sensitive systems in the US government: The Payment Automation Manager (PAM) and Secure Payment System (SPS) at the Bureau of the Fiscal Service (BFS). Housed on a top-secret mainframe, these systems control, on a granular level, government payments that in their totality amount to more than a fifth of the US economy. Despite reporting that suggests that Musk's so-called Department of Government Efficiency (DOGE) task force has access to these Treasury systems on a “read-only” level, sources say Elez, who has visited a Kansas City office housing BFS systems, has many administrator-level privileges. Typically, those admin privileges could give someone the power to log into servers through secure shell access, navigate the entire file system, change user permissions, and delete or modify critical files. That could allow someone to bypass the security measures of, and potentially cause irreversible changes to, the very systems they have access to. “You could do anything with these privileges,” says one source with knowledge of the system, who adds that they cannot conceive of a reason that anyone would need them for purposes of simply hunting down fraudulent payments or analyzing disbursement flow. "Technically I don't see why this couldn't happen," a federal IT worker tells WIRED in a phone call late on Monday night, referring to the possibility of a DOGE employee being granted elevated access to a government server. "If you would have asked me a week ago, I'd have told you that this kind of thing would never in a million years happen. But now, who the fuck knows." A source says they are concerned that data could be passed from secure systems to DOGE operatives within the General Services Administration (GSA). WIRED reporting has shown that Elon Musk’s associates—including Nicole Hollander, who slept in Twitter’s offices as Musk acquired the company, and Thomas Shedd, a former Tesla engineer who now runs a GSA agency, along with a host of extremely young and inexperienced engineers—have infiltrated the GSA, and have attempted to use White House security credentials to gain access to GSA tech, something experts have said is highly unusual and poses a huge security risk.
252 notes
·
View notes
Text
The 369 Manifestation Code Review

There are several manifestation programs on the internet that promise to be able to assist you achieve your goals. The 369 Manifestation Code is also named for Tesla Nikola, the man who inspired its creation. The Tesla Manifestation software was named after its developer, Darius.
According to Tesla, you have the ability to unlock and attain your desires. The Tesla Manifestation method employs one-of-a-kind audios to assist you in opening your mind, allowing the universe to grant you all of your wishes.
The numbers 3, 6, and 9 are said to have the capacity to bring prosperity, health, and love from the cosmos, according to Tesla. All you have to do is figure out how to use these three numbers to make the cosmos grant your wishes.
The 369 Manifestation Program employs 369 hertz audios to change brain waves and cleanse the root chakra, opening the way to wealth and plenty.
Negative energy, such as financial stress, relationship issues, and bad health, unfortunately, inhibits the ability to attract happy feelings.
What Is the 369 Manifestation Code?
The 369 Manifestation Code is a three-step manifesting method. That is, it is a rather basic technique that utilizes the power of the mind to channel positive energies and assist you in your daily life. It is stated that by releasing these powers, you would be able to attain your goals.
Darrius, a male, was the one who came up with the idea. He was in a poor financial condition, maybe the worst of his life. The man was in so much debt that he couldn’t even meet his basic demands. Then he learned that his partner was expecting a child.
He felt desperate at first, but then he realized the answer to all of his problems: the numbers 3, 6, and 9. A acquaintance told him that the sound of 369 hertz was the best method to enter a “Alpha state,” and that this secret had been known for a long time.
According to him, the legendary Nicola Tesla was already aware of the mind’s power. According to Tesla, the ability to materialize the life you desire comes from inside, not from the outside. These three numbers were also favorites of the scientist: 3, 6, and 9.
Someone might reportedly discover the key to a happy, prosperous life by connecting these numbers. As a result, Darrius created a 369-hertz soundtrack that makes direct touch with your chakras and opens the door to a lot more pleasant way of life.
Who Created The 369 Manifestation Code?
The 369 manifestation code was devised by Darius, one of the most prominent manifestation instructors, and is followed by over a million individuals.
He received 369 audio tracks from a friend, which he utilized in his life, and after seeing how successful they were, he decided to share them with the world under the moniker 369 Manifestation Code.
If you don’t know Darius, I have found his story for you.
Darius had a difficult existence, was lost, and was drained in every way. His financial circumstances deteriorated as a result of his lack of a high school graduation. Despite the fact that everyone felt he was performing well, he was consistently overlooked for promotions. He was heavily in debt and couldn’t afford even the most basic basics.
He learned that his fiancée was pregnant one day, and despite his joy, he was worried about how the two of them would handle having a child. He was attempting to come up with a solution without understanding that the cosmos had all the answers.
Sebastian contacted him when he was contemplating in a nearby café, and they began conversing. Darius was interested by the fact that the guy appeared to have been born with a silver spoon in his mouth after knowing about his difficult existence.
Darius heard about the three numerals 369 when he asked him how his life had altered.
How Does the 369 Manifestation Code Work?
The 369 Manifestation Code is based on a basic three-digit manifestation code. The 369 Manifestation Code soundtrack’s particular frequency assists users in unlocking incredible wealth and abundance of pleasure in their lives.
The sacred numbers 3, 6, and 9 are used by Darius, the originator of the 369 Manifestation code, to unlock the door to a new alternate and plentiful universe.
Hearing audio tracks tailored to a precise frequency allows you to magnetically attract mind-blowing money miracles in minutes. Because these soundtracks can seamlessly connect the user’s mind and the world to attract financial independence, riches, health, and pleasure, they are becoming increasingly popular.
The entire system runs on autopilot and is unaffected by the user’s present financial situation. The 369 Manifestation Program does not necessitate any physical exertion, nor does it necessitate any new knowledge or mental or visualization methods.
To link the user’s mind with the Universe, the application only requires a total commitment of 5 minutes every day for about 10 days.
The 369 Manifestation Code manifestation program has three steps:
Step 1: Take some time to relax and listen to the vibration-altering sound for 10 minutes.
Step 2: Give yourself some time to go into the Alpha Brain Wave Pattern, which is where all the changes happen on a deep level.
Step 3: Give yourself some time to enable the new thought patterns and vibrations to take root in your head and generate a new reality naturally.
What’s Included In The 369 Manifestation Code?
Because the music contains a frequency of 369 hertz, using the 369 Manifestation Code can help you open up new possibilities and unleash abundance. Listening to these vibration-altering music can help you materialize your new world.
Your new life might be full of first-class experiences and exotic trips, as well as financial assistance.
You’ll also receive some bonus songs to help you on your way to a more effective makeover.
Bonuses for the 369 Manifestation Code include:
Bonus #1: Millionaire Mindset Shift:
Do you realize that the billionaires you see around you aren’t always more gifted or intelligent than you? Some people believe that redirecting your mentality is the secret to success.
You will find yourself manifesting more frequently and tripling or even trebling your money if you listen to this audio clip.
This alone is worth $97, but if you get 369 Manifestation Code, you can have it for free.
Bonus #2: The Money Abundance Magnet Moves
Simple practices may make the process of creating riches ten times simpler.
You may study these habits in the 369 manifestation code and use them in your daily life.
Bonus #3: The Money Confidence Booster:
The state of your financial circumstances is inextricably linked to your degree of confidence.
When you are confidence in yourself and your skills, you will attract greater riches. You’ll gain confidence in a matter of minutes.
Bonus #4: The Health Chakra Spinne:
You may be familiar with the concept of chakras. Each of our organs has energy-related wheels spinning around it. If they are rotating properly, our health remains healthy.
A shift in their employment might be harmful to your health and cause you to become ill. The audio track is important in this case. It is said to aid in the proper spinning of your chakras in order to maintain optimum health.
Benefits of Tthe 369-Manifestation Code:
Users of the 369 Manifestation Code manifestation program can expect the following benefits:
You will have unrestricted money and will finally be financially independent.
Assists people in realizing all of their desires.
You will be presented with several possibilities that will help you advance in your profession.
Make a mental connection to the cosmos.
You will discover contentment and fulfillment.
Increase the users’ skills to attract an abundance of health and prosperity.
Money will come in from a variety of sources.
Provides an endless supply of possibilities.
You will have a more positive self-image and more self-confidence.
If the manifestation code does not work for you, you may get a refund within 60 days.
You will have no trouble manifesting the riches you require.
Reduces stress and anxiety by assisting in the elimination of negative thoughts.
You’ll have more time to focus on your relationships because you’ll have more time to work on them.
For individuals who do not profit from the code, there is a 60-day money-back guarantee.
Frequently Asked Questions
Q: What is the money-back guarantee and how does it work? A: If the 369 Manifestation Code program does not work for you, simply write an email to the developer to get a refund.
Q: How long will it take to view the findings of 369 Manifestation Code? A: Based on consumer feedback and testimonials, most customers saw changes in their lives after the first day. However, for the greatest outcomes, it is suggested that you try it for at least 2 to 3 months.
Q: Does the 369 Manifestation Code curriculum need any additional talents or techniques? A: No, it isn’t. To use the 369 Manifestation Code software, you don’t need any additional skills or methods.
Q: Can anyone use the 369 Manifestation Code program? A: Yes, the 369 Manifestation Code program is reported to be beneficial to people of all ages, genders, and abilities.
Q: What does practicing the skills entail? A: To listen to the audio tracks, all you’ll need is a mobile phone or CD player, as well as a headset.
Pros:
Simple and straightforward to follow
Without doing any physical effort, manifest an abundance of health, riches, and pleasure.
Priced reasonably
A 100% money-back guarantee is included.
Because the program is available in digital format, anyone may view it right now.
Cons:
There are just a few spots available.
Only available for purchase on the official website.
This is not for everyone.
Conclusion:
If all other financial alternatives have been tried, there is still hope since the 369-manifestation code can be used. The 369-manifestation code is beneficial to anyone seeking unrestricted wealth.
There are additional books you may collect after you have it. It was found by the greatest mind, and the information has now been made available to you.
If you have any worries, rest assured that this code has been thoroughly tested and confirmed to function. Financial independence is within your reach, and all it takes is a small investment.
Try Now… Click the Button Below
1 note
·
View note
Text
Tesla Code Secrets Review ( Scam? )
I spent years being frustrated in relationships because I did not understand men on a fundamental level. The fact is that they are not like us in many ways and we will never completely understand each other. What are the best ways to understand a man's feelings? Philosophically, we can never experience other people's feelings. The fact is that they are not like us in many ways and we will never completely understand each other and it is okay. The best way might be that try to imagine the feelings he describes and try to put ourselves into their situations and imagine how we feel. If you want to have a happy and healthy relationship with the man you love, it is important for you to be able to understand what he thinks and what he wants. The relationship expert Michael dire has actually interviewed tens of thousands of men and he has found a consistent theme and answer among almost every one of them, and it is exactly what you are looking for. A man can open up to you the way you want and give you what your heart desires if you are able to understand their inner thoughts and that is exactly what you will learn in this program.
The Secret Survey by Michael Fiore is based on 8 step by step lessons that show women what they need to do in order to correctly identify how men feel about them and their true intention without him saying even a word. According to the author, the main reason why many women usually end up with the wrong man is because they don’t know how to correctly identify signs that shows that he is not the right man. All the instructions and knowledge of the men’s thought, psychology and desires provided inside this program is completely based on the real experiences of the author. The program contains some real life examples. He lays out the facts, focusing on what you need to hear — not what you want to hear. All the secrets of the men including psychology, thoughts, desires are laid out clearly and scientificly that help you could study about how to understand your man easily.. Physical beauty may be a romantic turn on for women but it’s not the only thing your man is after. He lays out the facts, focusing on what you need to hear — not what you want to hear. The program contains some real life examples.
Similar to other programs by Michael Fiore, such as Capture His Heart, the Secret Survey system is very easy to follow and Michael Fiore always present his lessons in a fun but profound way that everyone can understand. The topic that the author has included in program will keep you glued until when you read the last word. The author has also used simple language that is easy to understand. He has explained a complicated topic using very simple language that users can easily understand. This program is suitable for women of all ages regardless of their current situation. So whether you are single, married or divorced and you are looking for tips and tricks to help you get the man of your dream, then this program will help make your dream a realit. With high quality videos, professional looking guides, excellent audios and active members area there is no doubt that Secret Survey is one of the most comprehensive relationship training courses available for women online these days. Michael Fiore offers a full, no-hassle money back guarantee for 60 days for every woman that will buy the Secret Survey Program. This decent guarantee makes his program completely risk free and imply about the confidence level that Mr. Fiore has in the quality of his Secret Survey system.
Click Here to Download The Secret Survey eBook Now!
0 notes
Text
Discovering whether your Iphone has been hacked is nearly impossible thanks to Apple's walled garden

This week, we learned that the notorious Israeli cyber-arms-dealer NSO Group had figured out how hijack your Iphone or Android phone by placing a simple Whatsapp call, an attack that would work even if you don't answer the call.
Apple has received a lot of praise for the security of its Ios devices, which are said to be so secure in part because of Apple's walled garden strategy, which prevents Iphone owners from running third-party software unless it comes through Apple's App Store; and which limits who can repair Apple devices, and whether they can use third-party replacement parts. All of this control is said to produce a much more limited attack surface, with fewer bugs, which are corrected more quickly.
However, there are several cyber-arms-dealers that are in the business of selling exploits to hijack control over Apple's products, from Cellebrite to Grayshift to NSO Group. These companies keep the bugs they exploit a secret, making it harder for Apple to repair them.
Meanwhile, security researchers who want to develop tools to perform forensics on Apple products to determine whether they have been compromised with one of these cyber-weapons are out of luck: Apple blocks the forensic apps from the App Store, and kicks the few that sneak in. That means that in order to test an Apple device, the user first has to jailbreak it -- and jailbreaking Apple devices has gotten harder and harder, as Apple defends its own security (against competing App Stores) while weakening its users' security.
Fundamentally, Apple's security model treats owners of Ios devices as potential attackers and goes to enormous lengths to prevent someone who owns an Ios device from ever learning exactly how it works, so that some processes can run in areas that users can't inspect or control (those processes prevent users from using their Ios devices in ways that benefit them at the expense of Apple's shareholders). If an attacker manages to hijack an Iphone, the attacker's code can run in this special mode that is supposed to be reserved for Apple's own user-control programs, and take advantage of all the anti-user countermeasures Apple has built to protect itself.
This isn't unique to Apple: it's a trait shared by any devices that are designed to control their owners, from inkjet printers to Teslas. If your device is designed to actively prevent you from knowing what it's doing and reconfiguring it to do your bidding, then "bad guys" who take over the device will be able to attack you without you knowing what they're doing and reconfiguring your device to kick them out.
https://boingboing.net/2019/05/15/brittle-security.html
57 notes
·
View notes
Video
Tesla Code Secrets Review (2019) - How To Get Anything and Everything Yo...
#tesla code secrets review#tesla code secrets#tesla code secrets system#tesla code secrets reviews#tesla code secrets pdf#tesla code secrets scam#tesla code secrets guide#tesla code secrets book#tesla code secrets discount#how tesla code secrets works#tesla code secrets program#tesla code secrets download#tesla code secrets users#tesla code secrets ebook#does tesla code secrets work#3HAKIS#tesla code secrets audiobook#tesla code secrets by alex west
0 notes
Video
Tesla Code Secrets Review (2019) - How To Get Anything and everything Yo...
#tesla code secrets review#tesla code secrets#tesla code secrets system#tesla code secrets reviews#tesla code secrets pdf#tesla code secrets scam#tesla code secrets guide#tesla code secrets book#tesla code secrets discount#how tesla code secrets works#tesla code secrets program#tesla code secrets download#tesla code secrets users#tesla code secrets ebook#does tesla code secrets work#3HAKIS
0 notes
Text
for ps3 Card genre IndoPlay All-in-One
https://hahahahack.com/p333.htm
Ratings 4 / 5 Star indoplay review #2. Make the best hand possible by combining 13 cards in Capsa Susun!. - Convenient interface allows 13 cards to be navigated easily Full hack mod cheats IndoPlay All-in-one tree. Full hack mod cheats IndoPlay All-in new. Far off Anniversaries in Baseball: 1919. IndoPlay All-in-One - Apps on Google Play. The männerbund: the Indo-European coming of age ritual and how it relates to the Indo-European migrations.
Full hack mod cheats IndoPlay All-in-one direction. In a Wonderland they lie, Dreaming as the days go by, Dreaming as the summers die; Ever drifting down the stream- Lingering in the golden gleam- Life, what is it but a dream. Lewis Carroll. Energy. If you want to find the secrets of the universe, think in terms of energy, frequency and [vibration. Nikola Tesla. Was updated: 12/16/2019 06:58 AM. Refuting smears against Tulsi.
Full hack mod cheats IndoPlay All-in one. Full hack mod cheats IndoPlay All-in new window. Full hack mod cheats indo play all-in-one. DISCLAIMER: This is NOT an easy Strike. This is the hardest Strike Ludia have ever thrown at us, and right after the boost reset. It's so hard that Ludia will probably be selling boosts on the same day as the Strike, which is scummy but understandable. People with level 30 dinos are going to get strokes seeing this. You have to kill three of the following: Indorex, Indorex G2, Indoraptor, Indoraptor G2. All are level 30. Mercifully, they are also all unboosted. You are going to need some pretty. Full hack mod cheats IndoPlay All-indonesia.
Full hack mod cheats IndoPlay All-in-one day. Full hack mod cheats IndoPlay All-in-one piece. Hello Neighbor Skins Hack Cheats and Tips, hack-cheat. We are here to provide the best game hack generator for you. You will not to enter any information to access our tool or it means our tool has no survey or human verification. We also share some trick to play a game that we hope you can try and enjoy it, Game Hack - The Best Simple Games Hack, Mods and Cheats. Corvette Mods Hack Cheats and Tips, hack-cheat, Mod and Hack, Free Hack APK. Corvette Mods hack hints guides reviews promo codes easter eggs and more for android application. Corvette Mods cheats tips and tricks added by pro players, testers and other users like you. Ask a question or add answers, watch video tutorials & submit own opinion about this game/app. Hello Neighbor Skins hack hints guides reviews promo codes easter eggs and more for android application. Hello Neighbor Skins cheats tips and tricks added by pro players, testers and other users like you. Ask a question or add answers, watch video tutorials & submit own opinion about this game/app.
31.10.2019 #1. 8 games with enganging graphics! Capsa Susun, Poker, Domino, Domino99, Capsa Banting, Capsa Banting Duel, High Low, and Snails Race- All eight games are available anytime, anywhere. #2. Make the best hand possible by combining 13 cards in Capsa Susun. Convenient interface allows 13 cards to be navigated easily - Enjoy exciting. Full hack mod cheats IndoPlay All-in one hour. Full hack mod cheats IndoPlay All-indonésie.
youtube
everplaces.com/caceteram/places/aec8ada934724f998de22c88bbeb6e80
Corpse Party: Book of Shadows hack free Coins from proxy without pay
http://partemproca.angelfire.com
https://ameblo.jp/tebansei/entry-12553510552.html
www.openlearning.com
https://ameblo.jp/nakuhinaga/entry-12553514906.html
1 note
·
View note
Text
Week 7 Evening Lecture
PSA
Something Awesome is due TOMORROW before the evening lecture
MAJOR YIKES
Presentation: Bug Bounties
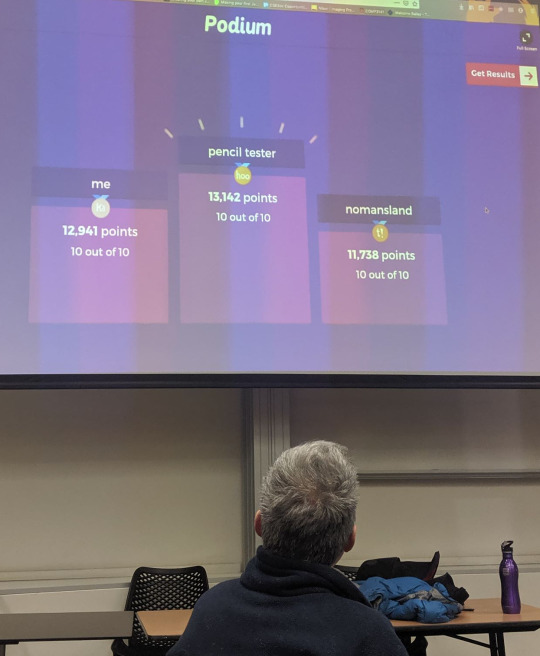
Started off with a Kahoot which was kind of strange. I was coming first, but the last question tripped me up. I thought we simply send them an email like Richard alluded to in the morning lecture, but apparently we should make a report and submit it. It was really unexpected I guess because they tested us before even doing the presentation (kinda counter-intuitive).
Anyway it was a nice and simple presentation that covered a few of the basics with getting started being a bug hunter. The example they showed was on a real website (HackerOne), where big companies like Tesla posted their applications for hackers to test and find bugs. It was good since they outlined the key features of the spec.
For example, Tesla clearly outlines specific things that they do not want reported like Social Engineering attacks, phishing, etc. In addition, there is information about the payouts they give and what kind of information (source code, etc) they provide to start finding bugs. All these things were considered ‘in scope’ meaning that there were specific things they wanted people to be looking at. However, there were also other things that they outlined as ‘out of scope’ so that hackers wouldn’t waste their time looking at other things.
Getting Started Tips
Learn web application principles
Look for assets that have changed recently; Reddit /r/tesla posts the software updates and patch notes (find bugs there)
Look for publicly disclosed reports
Fuzzing (covered by @theslazarus) Fuzzing is a useful bug testing process in which you can run automated tests that cover a range of possible cases. This is a lot more streamlined than manual testing and writing your own cases, because this generates all the possible inputs and interactions a user could use with your software and allows you to analyse it for any unexpected behaviour.

Fuzzers come in all different shapes and sizes, but generally fall into two main categories:
Mutation-based
Generation-based
We can use fuzzers to trace different types of bugs. In the example, @theslazarus showed how he used a fuzzer to test for heartbleed in different C programs. A good tip he gave was to follow tutorials online on how to utilise these and go on Github and test other people’s programs to see what bugs they have.
Crapple Bug (How to get root on a Mac) So apparently as your Mac is starting up, if you hold down Apple + S, you are able to get root access into the system. This occurs if you HAVEN’T ENCRYPTED YOUR HARD DISK but it’s strange as to why this is even a thing in the first place. However it does go to show that once someone gains access to the hardware, they have access to EVERYTHING.
Presentation: Pen Testing
Pen testing is an authorised simulation attack usually done in a sandbox to evaluate certain security risks. It is usually performed for companies in order to identify vulnerabilities and strengths that exist in their infrastructure.
For example, if you sent a ninja to break into your own house.
The ninja is the pen-tester
Your house is the system
Stages of Pen Testing
Recon
Planning
Exploitation
Post-Exploitation
Establish persistence
Establishing persistence I think is a really critical point. A hacker may break into your system at one point but remain dormant for a long period of time, or create some way to get back in (backdoor). This way they can plan certain attacks once they know they have access and execute this easily.
Demonstration The demonstration was quite nice where the presenters utilised Kali (gives you root access to everything) and hacker tools like Metasploit and Gobuster to analyse and brute force into servers. They attacked a system they set up on Wordpress and tried to login into ‘admin’. Although the password they entered was wrong, Wordpress indicated that the password for ‘admin’ was incorrect, giving out the information that there actually was an administrative account called ‘admin’. Lo and behold, the password to that account was indeed admin. For establishing persistence, the demonstrator installed a plugin he wrote himself that allowed him to create a shell and get back into the server (shell scripting).
Kahoot Was an interesting kahoot. I won which was cool got a s/o from Bucky.
Back2Lecture: Homework
Richard gave us more homework to do ahhhhhhhhh. It’s not compulsory, but I am interested in these things and do want to research them but I’m so busy and it just keeps piling on and on there’s so much stuff he wants us to do and then it’ll be assessable just you wait. Anyway here’s what he wants us to look up (it’s in the notes; https://www.openlearning.com/courses/securityengineering19t2/notes/slides07/)
Find out about current state of biometrics
Read about transport for NSW idea of using Facial Recognition rather than opal cards (case study)
Read about san fransisco ban on biometrics
Read about University research allegedly helping Chinese security forces to track and detain Uyghur citizens in Xinjian, China
Think about ways you can use facial recognition (China)
Diffie-Hellman does not give Authentication
One thing to note about Diffie-Hellman is that it’s NOT giving us AUTHENTICATION, because we aren’t verifying the identity of who we’re communicating with. DH only guarantees that only the parties have the shared secret (the key) which is CONFIDENTIALITY. So even if you are doing a key-exchange with someone across the world, you don’t actually know if it is the person who says they are who they say they are lol.
Blind Computers
Drawing back from last week’s lecture, Richard reminded us how Computers are just like someone who lives in a dark jail cell, separate from the real world. A computer doesn’t “understand context” or “identify things” the way that humans do. Computers are machines that are simply processing 1s and 0s.
Computers don’t understand things like we do. If you asked it to verify the identity of someone through a photo, it would simply be taking that image’s binary encoding and doing a bit-wise comparison. So in the instance that a it can do a comparison accurately, it is because the computer is PRE-LOADED with that information. It can only do a comparison if it has something it compare the input with. In this case, the pre-loaded information would be the stored binary information of a picture of the person’s face. However even with that, and no connection to the outside world, the computer still has to make a decision whether or not that person is who they say they are. And that decision is VERY HARD with what they understand and what they’re given. In the end, it comes down to the shared secret that is helping them make that decision.
3 notes
·
View notes
Link
Companies Can’t Stay on the Political Sidelines The invisible hand of business Around 50 groups have filed amicus briefs in a coming Supreme Court case pitting charities against the state of California in a fight over donation disclosures. The Capitol riot on Jan. 6 put a spotlight on corporations’ direct and indirect political donations; justices agreed on Jan. 8 to hear the case and arguments will take place later this month. Business interests want to create a “broad expansion of dark money rights,” according to a new brief from 15 Democratic senators, referring to untraceable donations that are often routed via nonprofit groups. The court case is an influence campaign disguised as a technical legal fight, the senators said. The case pits California against a charity, the Koch-affiliated Americans for Prosperity Foundation, over private access to tax documents. The Chamber of Commerce and National Association of Manufacturers are among the trade groups supporting the foundation’s demand for anonymity. Anonymous donors work like covert intelligence operations, the senators wrote. The donors give millions annually to “social welfare” groups that spend it in an effort to influence politics and policy. The senators pointed to congressional appropriations rules blocking disclosure efforts by the I.R.S. and S.E.C. over the past decade as evidence that the groups have swayed lawmakers behind the scenes. The case is the latest attempt “by powerful interests to both cement and obscure their influence over the public sphere,” the senators argued. The federal government is with California, more or less, telling the justices in a brief that the nonprofits’ constitutional claim is wrong but that the case should be sent back to the lower courts for more analysis. Get to know social tokens As the “suits” finally get into Bitcoin, the crypto crowd has moved on to the next big thing: BitClout, a “polarizing” open-source crypto social network that monetizes influencers via personalized tokens that can be traded by users, essentially quantifying a person’s reputation. BitClout’s recent launch has generated outrage because the company didn’t ask permission from people featured on the platform, instead launching with “reserved” currencies linked to celebrities like the Tesla founder Elon Musk, the pop star Katy Perry and about 15,000 others. Influencers can claim their coins, which requires buying in, but in the meantime fans can still buy and trade their tokens, BitClout’s white paper explains. Silicon Valley bigwigs have backed BitClout, including Sequoia Capital, Andreessen Horowitz, Social Capital, Coinbase Ventures, Winklevoss Capital and the Reddit co-founder Alexis Ohanian. A crypto wallet on the platform reportedly holds more than $150 million worth of Bitcoin, thought mostly to have been raised from these A-listers. The company’s founder goes by “DiamondHands,” a reference to investors who steadfastly hold speculative assets, popularized during the meme-stock frenzy. His true identity is an open secret among crypto insiders; signs point to Nader al-Naji, a former Google software engineer who has not denied the claim. Brandon Curtis of the exchange Radar Relay recently sent a cease and desist letter to Mr. al-Naji, protesting the commercialization of his persona without permission, and his counsel confirmed to DealBook that his profile was removed after that letter was sent. “BitClout is trying to create ownership through code instead of law” but may find itself “throttled,” said Michael Heller, a Columbia law professor. “People don’t much like strangers messing with their reputations,” he added, and the “right of publicity” lets them police who can profit off their clout. Source link Orbem News #Companies #Political #sidelines #Stay
1 note
·
View note
Text
#1yrago Antivirus maker Sentinelone uses copyright claims to censor video of security research that revealed defects in its products

At this week's B-Sides Manchester security conference, James Williams gave a talk called "Next-gen AV vs my shitty code," in which he systematically revealed the dramatic shortcomings of anti-virus products that people pay good money for and trust to keep them safe -- making a strong case that these companies were selling defective goods.
Among the companies thus humiliated was Sentinelone, who responded by sending a censorship request to Youtube claiming that Williams had violated copyright law (presumably Section 1201 of the DMCA, which bans bypassing access controls for copyrighted works), its terms of service (which corporations and US federal prosecutors have said is a violation of the Computer Fraud and Abuse Act) and trademark laws (this is pure bullshit, as trademark has an absolute "nominative use" defense that allows you to use trademarks to identify the products and services they're associated with).
The video went dark (though an earlier version of Williams's talk was already online; here are his slides) (Youtube seems to have reconsidered their takedown and restored the video).
In their defense, Sentinelone says that they welcome critics, provided that the criticism is funneled through their "common disclosure practices in place" -- that is, you can criticize Sentinelone, provided that they get to decide when and how your criticism is published.
If you're a Sentinelone customer, you should be really worried. Sentinelone argues that their products are "protecting...critical global enterprises" -- but since Williams' presentation apparently demonstrated that the version of their product he analyzed is a flaming garbage heap (they don't really dispute this, they merely say that he should have been more polite when he outed them for their defective goods), they are not actually protecting those critical enterprises. They're failing to protect them. So if you rely on Sentinelone's products, or worse, if you're a customer of one of those "critical global enterprises," then, it seems, you are putting your trust in something that is unfit for purpose.
This is why it's so dangerous that good actors like Mozilla, Tesla and Dropbox have published security policies that promise not to sue researchers who follow their rules. Because these companies are making the case that researchers who don't follow the rules can be sued, they are exposing the entire research community to risks from bad actors like Sentinelone, who use the "good guys'" arguments to justify their own censorship.
Remember that these legal threats only work against people who don't plan on attacking users of the affected products. If you're a surveillance contractor or criminal who has found a bug in Mozilla, or Dropbox, or Tesla, or Sentinelone, you don't need to worry about getting sued for revealing your findings, because you don't plan on revealing your findings. You want to keep them secret for as long as possible, while you attack the unsuspecting customers of these corporations with impunity.
https://boingboing.net/2018/08/18/sentinelone-v-streisand.html
11 notes
·
View notes
Video
Tesla Code Secrets Review (2019) ⚠️WARNING⚠️ Watch This First!
#tesla code secrets review#tesla code secrets#tesla code secrets system#tesla code secrets reviews#tesla code secrets pdf#tesla code secrets scam#tesla code secrets guide#tesla code secrets book#tesla code secrets discount#how tesla code secrets works#tesla code secrets program#tesla code secrets download#tesla code secrets users#tesla code secrets ebook#does tesla code secrets work
0 notes
Text
Musk: Tesla began to accept Bitcoin payment
On March 24, Tesla CEO Elon Musk stated today that the company’s automobiles can now be purchased with Bitcoin. This news indicates that Tesla has become the first car company to accept Bitcoin payment. Musk posted on Twitter, "You can now buy a Tesla with Bitcoin." In addition, Musk added that Tesla will not exchange the received Bitcoins into traditional currencies. Musk has made no secret of his love for Bitcoin, and now Bitcoin and Tesla have finally "tied".
Just last month, Tesla stated that the company bought $1.5 billion worth of bitcoin and will soon accept bitcoin as a payment method for car purchases. Affected by this news, Bitcoin has risen by nearly US$3,000 in the short-term, and its current offer is US$56,600, a 4% increase.

Currently, Tesla only supports Bitcoin payments for local customers in the United States, but at the same time Musk also announced that it will also provide Bitcoin payment outside the United States later this year.
Elon Musk, the world's richest man and Tesla founder, is extremely fond of crypto assets. As early as May 2020, he replied to the tweet from JK Rowling, the author of "Harry Potter" that he owns "0.25 Bitcoin."
Earlier, Musk added a new hashtag "#Bitcoin" to his Twitter introduction, which caused Bitcoin to skyrocket by 20% for a while. Subsequently, Musk said in the social media, Clubhouse that he believes Bitcoin is a good thing, and he is a Bitcoin supporter.

Accepting Bitcoin as a direct payment method will be an important milestone. Up to now, although some merchants accept bitcoin as a payment method, they require those who want to use bitcoin to make purchases to convert bitcoin to U.S. dollars or other local currencies before remittance to the merchant.
Experts believe that Tesla’s innovation may eliminate the “middleman” in the future, and it may create its own currency processing system that can be used to accept bitcoin payments and clear them when necessary. In other words, consumers can directly transfer Bitcoin to Tesla's system, and Tesla can choose to hold Bitcoin or choose to liquidate.

The underlying blockchain system developed by NGK blockchain is specially designed to support the commercial decentralized applications, and its code is open source. The NGK blockchain expects that through cross-chain, it can form value interoperability for different consumption scenarios, and create a certain technical force for the global blockchain commercialization process. I believe that in the future, the NGK blockchain will inevitably improve the speed of value exchange to realize a truly united and interoperable value network!
In addition to allowing users to fully control the wallet keys, the NGK blockchain also provides multi-signature guarantee and two-step authorization for digital asset management of different scales. Users can choose verification methods such as mobile phone verification codes during their transactions to ensure an all-round assurance for their token assets.
0 notes
Text
The crypto whale who wants to give billions away – Cointelegraph Magazine
Like many people in the cryptocurrency industry, Sam Bankman-Fried is in it for the money. As founder of the quantum trading company Alameda Research, the FTX exchange and the DeFi serum protocol, the 28-year-old man with curly hair has amassed a $10 billion fortune in the sector in just three years.
Unlike most people in the cryptocurrency industry, he’s building a fortune to give half of it away. He is an effective altruist who essentially steals from the rich to give to the poor through his supernatural, coded trading strategies.
Maybe without the robbery, he says. Ultimately, my goal is to have as much impact as possible, whatever that may be. And right now, I think, it’s through donations, so I’m wondering how I can do as much as I can and give as much as I can.
The SBF, as it is sometimes called, has been around for some time. He was director of development for the Center for Effective Altruism for a few months in 2017, and before that he spent half his income working on Wall Street. He plans to donate about 50% of his crypto billions, but only after he reinvests in his ever-growing empire.
Nevertheless, he donates to charities as they arise. He was the second-largest contributor to President Joe Biden’s campaign, behind former New York Mayor Michael Bloomberg, who contributed $5.2 million.
I was excited about the impact this could have. I thought what happened in the election was important.
In addition, the FTX Foundation has recently been established. It donates 1% of the cost of the platform and will double user donations, dollar for dollar, up to $10,000 per day. In its first weeks of operation, the foundation has raised more than $2 million, mostly in the form of donations from users, who can choose from a carefully curated list of charitable organizations.
Old pouffe
SBF’s growing notoriety was further enhanced when the company was included in this year’s Forbes 30 Under 30 financial list. I’m honored, he says. I usually look forward more than backward, so it was a little cool, but it went pretty fast.
It also ranked third in a recent Top 100 ranking.

He has been known to sleep on an ottoman chair in his Hong Kong office so as not to miss a deal. It seems that the main reason SBF earns more than anyone else is that it is almost never off-schedule.
I’m in the office, mostly 24 hours a day. Sometimes I just take a nap on the ottoman here and of course I talk to colleagues and sometimes people on the internet, but it’s mostly his job.
He has no girlfriend and doesn’t have many contacts outside of work, although he does find time to talk to his family in the United States on the phone several times a week. It’s safe to say that FBS’ers aren’t the kind of people who are desperate for a perfect work-life balance, or even accept that their productivity declines after the first 11 hours of work.
I think these kinds of stories are vastly overrated, and the cruel or inspiring truth, depending on how you think about it, is that the more you put in, the more you get out, he says. That motivates me, and that’s satisfying, but you know, another part of it is how I think I can have the biggest impact.
How did I get here?
The child of two law professors at Stanford University, SBF discovered the Effective Altruism movement while studying physics at MIT.
Made popular by philosophers and ethicists including Toby Ord and Peter Singer, the movement focuses on pragmatic ways of helping others, using science and reason to maximize benefits rather than the well-intentioned and mediocre results typical of some charities. This practical approach also extends to how best to help a person.
Imagine how much good you can do by working directly for a cause, compared to what you can do by working and donating to Wall Street. In many cases, you could probably help them even more with donations. So, basically, I checked out Wall Street.
Fellow interns at quant trading firm Jane Street Capital pointed him in the direction of Wall Street, and he began working there just after graduating from college in 2014. Why did they hire a physicist with little experience in finance straight out of school, you ask?
It turns out that strategies for quantum trading are valuable trade secrets, which means that effective strategies are not taught in university courses. Instead, companies hire people with raw talent: Mathematicians or people with extensive experience in physics or computer science.
What you need to know about the markets, they will teach you, he says. He has traded various ETFs, futures, currencies and stocks and has developed an automated OTC trading system. There, he became interested in the incredibly profitable arbitrage opportunities in inefficient crypto markets and founded the crypto-quantum trading company Alameda Research in late 2017 to take advantage of them.
Rules applicable to all whales
Alameda Research has grown into one of the largest crypto firms with about $2.5 billion in assets under management, although as with its own assets, SBF puts this into perspective with some caveats about liquid and illiquid assets.
Alameda is the Moby Dick of cryptocurrences, representing up to 10% of cryptocurrences circulating in the markets at any given time. I think sometimes he can get to that part of the volume, he says. I think the average is a little lower. It belongs to the group of five to ten large commercial companies in this sector.
This means that every Alameda transaction has the potential to move the markets and generate liquidity. Last October, Alameda was widely accused of having caused the IFJ’s share price collapse by short selling, although SBF minimized the impact of this practice. He believes that with great power comes great responsibility.
It’s an absolute responsibility, he says, adding that he tries to follow the approach of TradFi Quant’s companies. Their job is to find profitable companies, but also to provide liquidity and promote healthy markets, he says. The greatest responsibility is to do no harm. And to ensure that what you do generally promotes, rather than disrupts, the liquidity of healthy markets and the efficiency of transactions.
He added that arbitrage operations, for example, can have a positive effect because they make markets more efficient and reduce prices where there are premiums. Identifying and developing opportunities to profit from arbitrage transactions was the main reason for founding Alameda. One of the first big gains we made was Litecoin, he recalls.
There was a week in late 2017 when Litecoin was trading at a steady 20% price on the GDAX Coinbase [now Coinbase Pro]. That’s cool, you make 10% every half hour, I guess you make dollars forever? And that, of course, is not the solution.
It proved terribly difficult and necessary to use this facility to circumvent the trade size and withdrawal limits of one million per day. A few years ago in crypto-economics, a big part of the problem was finding the logistics, he says.
In another arbitrage transaction, SBF and its friends moved up to $25 million a day through a series of intermediaries and land banks in Japan to take advantage of Kimchee’s infamous bonus, which allowed Bitcoin to be traded up to a third more in South Korea’s hard-to-reach financial system than in the United States.
But it is the management of the outdated financial system that has caused the biggest problems. The slowest and most difficult, most expensive and frustrating part of arbitration is the fiat, he says, referring to the difficulty of getting accounts that can then be closed at any time, archaic procedures and bureaucracy, and incredibly slow bank transfers.
We worked in physical bank branches for five hours a day for over five months because it took a long time to transfer money, he says, adding:
It’s like arriving at 10am and staying there with a few people until 1pm to make all the appointments we had to have every damn day of the week to send the same recommendation we sent yesterday.
This is one of the reasons SBF is so passionate about the DeFi – its vision is to one day replace the existing financial system, which is already too cumbersome. The current payment rails are not efficient at all, he says. There are billions of companies that just abstract it, and you end up with this incredibly complicated web of shit to make it usable for most people. They work on older systems that were not even designed for the Internet.
Effects of cryptography
For many, the SBF did not become an important figure in cryptography and DeFi until the mid-1920s, when it began to have an impact on Twitter crypto. It was an intentional gesture: He would have liked to have stayed under the radar in 2018 as Alameda focuses on quota trading: Very little advertising is required, which is usually a disadvantage. But when he launched FTX, an innovative cryptocurrency exchange system, in 2019, he had to create a community around it, and he took the lead in becoming its public face on social media.

As regards FTX as a retailer, the following rules apply: The more customers, the better. You can develop the best product in the world, but if no one knows about it, it’s worthless, he says.
One of the most challenging and interesting tasks was finding ways to engage users, and a large part of this task was awareness raising.
He seems to have understood this, as the FTX is now the fifth largest derivatives exchange by volume, with a valuation of $3.5 billion. The company has launched a number of innovative markets, including offering token shares to companies like Tesla, Apple and Amazon, as well as trading on Coinbase prior to its IPO.
She is also using her wealth and influence to try to overcome what she sees as the biggest obstacle to widespread WiFi adoption. He believes that Ethereum, including Eth2, is not sufficiently sized for cryptography and DeFi to replace the existing financial system. Currently, DeFi can process about 10 transactions per second, and Layer 2 solutions offer several thousand TPS.
It’s an absolutely solid and immutable barrier to growth, he says. The Fay literally cannot develop as an ecosystem until this problem is resolved. That’s why there is no long-term plan that doesn’t address this problem. …it’s just deadly. Even the Eth2 target of 100,000 GST is not enough for what the SBF has in mind.
If your goal is to reach 100 million or a billion users, […] the application should be able to process about a million transactions per second to become one of the biggest applications in the world. So you can endlessly tick off the list without having to consider other factors, with a scaling solution that will not lead you to your goal.
This has led him to become one of the strongest proponents of Solana, a retail chain that currently handles 65,000 TPS and which the team claims could eventually reach amazing levels : 710,000 TPS on a 1 gigabit connection or 28.4 million TPS on a 40 gigabit connection.
In August 2020, he founded Serum DEX on Solana and launched SRM Cryptocurrency. Bankman-Fried says you can see the benefits of Solana in whey by the order book. The matching engine takes only a hundredth of a cent to place an order, and auctions take only a few seconds.
So get lots of juice from the higher flow. And that has really helped to broaden the product base. So much so that I think our best estimate is that Whey DEX probably consumed more transactions in six months of operation than the entire Ethereum store chain ever did.
Network effects have given Ethereum a hard time, forcing deFi projects and users to migrate to Solana. Even after Chief Nomi handed over control of SushiSwap to him, he was unable to convince the community to hand him over. In the end, it was much more complicated than we thought to migrate existing projects and much easier to create new ones, he explains, adding :
We would be very happy if they had an outpost on Solana. I think they still will at some point. But I also think Seren will go both ways. Ultimately, I want better products and better users, you know, no matter what.
(After our interview, there was a new proposal to build a version of SushiSwap on Solan and Whey, perhaps under the name Bonsai).
While the SBF argues that the network effects of many interconnected applications built on Ethereum are significant, it notes that each project will eventually need to migrate and dismantle assemblies and toolsets with existing options to move to Layer Two, Eth2 or another scalable solution. As for the number of users, he claims that the effects of the ETH network are overestimated.
The other part is that while DeFi’s current user base is very loyal, very large and powerful, it is not very large. The daily active users, I think it’s tens of thousands. I think FTX probably has more active daily users than all the DeFi’s combined.
It appears that SBF is considering implementing the Solana blockchain as infrastructure in applications where it is invisible to most users, to allow millions of users to access the DeFi. In early 2021, Alameda did a $50 million funding round to implement DeFi type tools on Maps.me, an offline European mapping application with 140 million users. Solana will build a multi-currency portfolio with exchange rates and locations. FTX’s purchase of Blockfolio could follow a similar strategy.
I think it will be a very cool product and a powerful suite of products for the application, he says of Maps.me. I’m very excited. I think this could be the start of adoption.
Related Tags:
21cryptos,bitcoin magazine subscription,the capital crypto,blockchain business magazine,the capital magazine,cointelegraph top 100,sam bankman-fried net worth,sam bankman-fried twitter,ftx investors,alameda research bitmex,Privacy settings,How Search works,biggest names in crypto,top cryptocurrency influencers,cointelegraph markets,today’s crypto news,best cryptocurrency analysis sites,best cryptocurrency predictions,crypto influencers
0 notes
Text
5 Crucial Differences Between INTPs and INTJs
"1. INTP vs INTJ: Different “Driver” processes
The Driver process can also be called the “dominant cognitive function.” It’s the mind’s first point of contact and the primary lens through which everything gets filtered.
For an INTJ, this dominant process is technically called Introverted Intuition, but we’ve nicknamed it “Perspectives.”
Perspectives is a learning function (technically called a “perceiving function”), and works by watching one’s own mind form patterns. After years of use, eventually Perspectives begins to see the ‘pattern of the patterns’ and understands that what is happening inside of themselves cognitively is also happening for other people.
INTPs, on the other hand, lead with a process called Introverted Thinking, which we call “Accuracy.”
Accuracy is a decision-making function (technically called a “judging function”), and works by creating a framework and then sifting through all the data within that framework, scanning for incongruities and inconsistencies. Its ultimate goal is to find things that make sense to the user, and once clarity is gained then the INTP knows the right course of action to take.
Because both are Thinking types – meaning, they both make decisions based on impersonal, analytical criteria – it’s important to both INTJs and INTPs to be intellectually honest. And while both have this same desired outcome, there’s an important nuance between the relationship each has with data.
Since INTJs are leading with an intuitive process there is more credence given to creative internal thought. They aren’t scanning for content that could be wrong, they’re scanning for new patterns that could be right.
This is why INTJs must pair their Driver process with the Co-Pilot of Extraverted Thinking, or “Effectiveness.” The only way to truly know if those patterns have merit is if they play out in the ‘outer world’. If they work, awesome! That was a great new pattern. If they fail, then it’s back to the internal drawing board.
For an INTP, the outer world isn’t where thoughts are vetted. In fact, INTPs couple their Accuracy with Extraverted Intuition, or what we call “Exploration.” The world outside of themselves is where intriguing new patterns are observed, and it’s up to them to make sense of what those possibilities could mean.
A logically consistent argument is the proof that supports their speculation.
This is why INTPs must be so ruthless with their content and data. The criteria isn’t necessarily provable to an outside observer, and so an internally consistent argument may be the best they’ve got to give credibility to their conclusions.
Think of it in terms of Nikola Tesla (most likely an INTJ) and Albert Einstein (most likely an INTP).
Tesla thought up extraordinary new technologies, but the real test was whether or not those inventions actually worked.
Einstein, the on the other hand, saw patterns in the outside world and mulled over them until he culled from the herd everything but the most internally consistent reasons.
Tesla could point to the invention. Einstein had to point to the math.
This results in two very different relationships with data.
For an INTP, ‘clean’ data is of the utmost importance. Personal biases, what we want to believe, and social attachments to concepts muddy the waters. This is why there’s always some attraction to math, formal logic and/or binary code for an INTP. These are disciplines that tolerate little to no personal interpretation, which is hugely satisfying.
An INTP will unconsciously vet people for when they can and cannot be trusted with data. For example, they may have a good friend who always knows when someone is being fake, but can’t seem to wrap their head around time. When talking to them about motivations and intent the INTP knows they’re a trusted source of information, but they will dismiss that person whenever they talk about how long it will take to get somewhere.
There is such a thing as clean data, one just has to be ever vigilant for it.
For an INTJ, there is no such thing as data separate from the person holding that data. That is to say, our perceptions will always color the information we carry and so data is never clean. This is why an INTJ will frequently counter an inquiry for a piece of data with the question, “Why do you want to know?”
The context changes the content, and so if they don’t know why you want to know they can’t produce the data. (Not that it matters, but this can be maddening to an ENTP. Or, at the very least, to this ENTP. :p)
No matter! It’s not the empirical nature of the data that’s important, it’s the result it produces that’s the important thing. Which is why INTJs unconsciously vet people for their usefulness, not the data they hold (unless that’s how the person is ‘useful’).
Understanding the difference between these two Driver functions is crucial to understanding the difference in types.
2. INTP vs INTJ: Two different intrinsic insecurities generate different strategies
Even when we’ve graduated beyond our insecurities, the fact that they existed at some point influences our early strategies for navigating the world.
It’s been said by some that both INTPs and INTJs can come across arrogant, which I think is a surface understanding of what’s going on with both types (even when they’re at their “I’m going to strangle you now” worst).
As mentioned before, an INTP is constantly scanning for the cleanest data possible because they can’t actually show proof for their conclusions. Accuracy is by definition a subjective criteria: “it makes sense to me.”
Like Authenticity users (as mentioned in the INFP vs INFJ article), if the audience isn’t getting it an INTP can become (in order) confused, frustrated and ultimately cynical. There is always some insecurity about others invalidating their arguments and conclusions, but instead of staying in the realm of hurt (as an INFP may), the easiest solution is to just assume everyone else is an idiot.
Harboring insecurities is just another way for indicating immaturity, and an immature INTP will show up as The Authority On All Subjects, assuming they are right and you are wrong. When an INTP is accused of arrogance, it’s generally because they have a growing pathology toward being right at all times.
Conversely, the more mature an INTP becomes, the more they’re delighted at being proven wrong. That’s the outer world helping them cleanse data they may have grown attached to / become biased toward!
This is generally done through the development of their Co-Pilot process of Exploration, a function that opens frames and actively looks for more information to plug into existing frameworks.
They also become more cheerful as they develop, losing their grip in cynicism and enjoying a naturally egalitarian disposition where anyone at any time could offer interesting perspectives and content.
Of course, that doesn’t mean an INTP won’t still engage in argument and debate. Iron sharpens iron, after all, and debate is anything but personal.
For an INTJ, there is little to no insecurity about being right. If you don’t agree with them they might debate with you about it, but they understand that perception defines reality and you may just be seeing things fundamentally differently.
Ultimately, the proof is in Effectiveness, and you’ll see how wrong you are when the outer world plays it all out.
The insecurity an INTJ faces is more of a well guarded secret. INTJs are surprisingly sensitive, and as mentioned in our article about the INTJ personality type, anyone they let in can do real damage.
The insecurity lies in just how amazingly vulnerable they are to others. For a hardcore Thinker, it’s incredibly disconcerting for the INTJ to realize they are wired to be sensitive without the benefit of commensurate (natural) emotional intelligence.
The arrogant front an INTJ puts up isn’t to deflect being proven wrong, it’s to deflect against the hurt and pain another person potentially represents. It’s a true wall, an impenetrable domain around the inner sanctum that you may or may not ever be invited into.
The more insecure and immature the INTJ is, the thicker and more impenetrable the wall.
Conversely, the more mature an INTJ the more they understand that their personal happiness is directly linked to their willingness to be vulnerable. They may still be protective, but they don’t close themselves off universally. The INTJ builds healthy boundaries which allow special people in, who are the lucky recipients of their extraordinary understanding.
If you’re trying to determine your type between INTP and INTJ ask yourself: are you more put-off by being wrong, or by being vulnerable?
3. INTP vs INTJ: How emotions show up
No matter what your type and no matter how much of a “Thinker” you are, you have emotions and feelings. Being a Thinker means you use impersonal criteria to evaluate situations, which generally results in putting emotions as a lower priority. But they still exist.
When you look at the car model for each of these types (or, for Myers-Briggs geeks, when you look at the cognitive function stack) you’ll notice that the INTJ type has a more conscious relationship with their emotional side, whereas an INTP’s emotional awareness is more unconscious and a blind spot.
Not only are the Feeling processes in different positions in the car, they are also different expressions. For an INTJ it’s Introverted Feeling, or Authenticity, and for the INTP it’s ExtravertedFeeling, or Harmony.
Authenticity (at its core) is about understanding the emotional impact something has on you as an individual, and what’s in alignment for you as a person. It’s quiet, reflective and introspective. In fact, I’ve heard it described by Harmony types as “numbed out,” a misunderstanding of how the process works but an apt illustration of how inwardly turned the process appears from the outside.
Harmony (at its core) is about the emotional impact something has on others, aka the group, and checks in with social truths (like how we should behave and what people’s reputations are). It’s also outwardly expressive and emotive.
INTJs have a more conscious relationship with their Feeling process, which is in part why they’re sensitive. They’re often very aware of how things are impacting them emotionally, though they don’t always know what to do about it.
INTPs, on the other hand, have a very unconscious relationship with their Feeling process and a much higher threshold for tuning it out. Once it gets triggered, though, it’s anything but quiet.
When we go to our 3 Yr Old process (also known as our ‘inferior’) it’s generally in times of deep stress. (We can develop strategies to give our 3 Yr Old some attention to prevent it from controlling us, but most people only figure this out over time and through the concept of “failing better.”)
This is called Being in the Grip, and it’s never a pretty sight. For a generally rational and straight-faced INTP this can look like a full on temper tantrum. Uncontrollable crying isn’t just a possibility, it’s a probability. And the INTP – having no clue what the hell is happening to them – is swept up in the ride.
(When an INTJ is In the Grip it shows up as childlike self-indulgence – too much food, alcohol, sex and/or any other favorite expression of sensory pleasure.)
An INTJ will rarely temper tantrum. They’re more likely to get prideful as a first line of defense, and then move on to sulky and mopey. They may get angry, though this will generally be a controlled internalized version of the emotion. When an INTP gets angry, it’s more like a powder keg of explosion.
Understanding each type’s relationship with their Feeling process isn’t just a great tie breaker when profiling yourself or others, it’s also an important way to hold space for a loved one who may be one of these two types.
4. INTP vs INTJ: Hygiene, organization and status
When one has a purely theoretical understanding of Myers-Briggs it’s easy to rely on things like, “Oh, the INTJ is a Judger, so they’ll be organized and the INTP will be messy.”
If only people would just closely follow stereotypes we could lock this thing down and all go home.
Unfortunately, it’s not so simple.
As mentioned before, the INTJ is leading with Introverted Intuition (Perspectives) which is technically a ‘perceiving’ process. That means their flow state is learning and thinking creative thoughts.
Organizing their outer world is absolutely preferential as the more organized things are the more they can mitigate distractions and stay Perspectiving, so to speak.
But that means getting out of Perspectives to go organize, and sometimes that’s about as unappealing as an idea gets.
They also couple Perspectives with Effectiveness, a process that naturally thinks in terms of delegation. I’ve known INTJs that wished someone would just come along and organize their space for them, but until that happened they were merely going to shut off sensory awareness and not acknowledge the disaster around them.
When an INTJ exercises the Effectiveness process this is less likely to be the case, but even then ‘cleaning and organizing’ has to be considered a high leverage activity. Which it may or may not be.
Generally the biggest give-away between an INTJ and INTP (when taking into consideration that one is a J and the other is a P) is in personal grooming.
An INTP – having Harmony as their 3 Yr Old process – has an exceptionally easy time of just not giving a rat’s ass about how they appear to others. Actually, more accurately, they don’t give a rat’s ass if they’re socially acceptable. They may care how they come across, but that’s generally to send a message of not caring.
For the INTP, status is a game other people play, and dressing up just to suit others almost feels icky.
For an INTJ, on the other hand, status is a resource. And resource is always on the radar of Effectiveness. Playing a status game doesn’t feel icky, it feels like a necessary part of life. And it’s not so much that they dress for high status, but that they understand just a little effort goes a long way.
Unless they’ve given up, and then they turn into the Comic Book Guy on The Simpsons. When an INTJ devolves they start looking more like an immature INTP.
Alternatively, when an INTP matures they stop seeing hygiene and personal grooming as “being under the thumb of society” and more as a way to connect with other people. They dress for leverage, or self-expression, or a number of other perfectly acceptable reasons to attend to their appearance.
5. INTP vs INTJ: Why we need them both
I’ve found INTJs to exhibit amazing intellectual integrity. I’ve found INTPs to exhibit extraordinary radical honesty.
For a society to exist well we need to have people who won’t bullshit themselves and won’t bullshit you. We need creative thinkers that question the status quo, implement new technologies that improve our lives while at the same time whistle-blowing and calling out that the emperor is, indeed, naked as the day he was born.
When an INTJ develops into the best version of themselves they are the walking think tanks of sustainable systems.
When an INTP develops into the best version of themselves they are the innovators of new paradigms, literally altering how we understand and see reality.
Both types are imperative, and if you are either type please understand how important you are. Develop into the best version of yourself by exercising your Co-Pilot process of either Exploration (INTP) or Effectiveness (INTJ).
And hug yourself for me. Cause I’m a fan.
-Antonia"
https://personalityhacker.com/intp-vs-intj/
5 notes
·
View notes
Text
I'm not as user-friendly as I used to be, at least that's how it must have seemed in drunken dreams that proved to be illusory with hindsight 20/20 through a pair of goggles made of empty glasses on a table set for supper with the twelve apostles, none of whom thought twice of paying five or seven dollars for a bottled water since it's only overpriced until it's turned to wine by Dionysus metamorphosed into Christ performing miracles like David Blaine outwitting the Goliath of the human mind with optical illusions which have been aligned like wires meant to trip the vision, glitches in a system once in mint condition, only to become the victim of decisions ordering the decommission of the old equipment since it's rickety enough to catch a virus from a sick magician smuggling more tricks beneath his hat than could have fit inside a secret bag that never leaves the triple-fingered grasp of an elusive cartoon cat who finds himself in funny fixes, often subject to the sinister designs of counterfeiters unabashedly attempting to convert the trend to cash by courting crowds of young believers so devout that they would not be out of place as extras on the set of yet another Sister Act, with habits so impressive that they might as well have monkeys on their backs like junkies working on another set of track marks, but if being square is hip I guess I'd rather be a tesseract and wrinkle up the fabric of the cosmos just to ditch the beaten path, becoming master of the alchemy to forge the golden keys to immortality with legendary lines that linger longer than the cancer cells of Henrietta Lacks by moving forward faster than a VHS since I have never been the kind to hit rewind before I drop it in the slot unless I think I have a shot at reaching eastern ports by sailing a westward course, on honeymoon alone inside a hearse emblazoned with the proclamation that I've recently divorced, although I had to form a rival church to process all the paperwork and make myself the temporary pope of an unholy land controlled by warring factions in a mediocre karaoke battle of the bands, a perfect recipe to bake a batch of piping hot disasters more explosive than a load of Roman candles lit by plastic soldiers waiting for the birthday boy to blow the fallout far away and make a wish upon a shooting asteroid requesting that the sin of Sodom be destroyed selectively in ways that won't affect the rest, provided they profess a faith in following instructions that have been engraved on tablets made of DNA, a set of ten commandments coded cryptically in chains of ones and zeroes like a reinterpretation of an ancient language spoken by the innocent creator of a universe with only one dimension, prior to the birth of color through the prism which admits the spectrum, stretching in an exponential pattern like a shockwave of unstoppable expansion getting out of hand and leading to a state of total anarchy, devoid of gods and rulers meant to measure out the debt and keep the edge as straight as kids with X's on their fists who revel in the pit, presenting minor threats as side effects of the intent to minimize the risk of being thoroughly lobotomized in ways that don't require any picks designed for chipping ice to be inserted blindly in the frontal lobe that lies behind the sockets of the eyes, creating teenage nightmares like the bloody brides of Frankenstein depicted on the cover of another album mindlessly indulging in the kind of lines against which parents have to be advised with labels introduced in 1985 and still in use to warn against the gore abhorred by Tipper and the references to sex that might engender unexpected consequences when your daughter's high on meth and thinks she wants to moonlight as a stripper, causing an apocalyptic lifting of the veils as the hemlines rise so far above horizons drawn precisely by the architects of etiquette who engineer the trends, exerting efforts meant to influence the overall direction of a war of currents, causing Thomas Edison and General Electric to denounce the work of Westinghouse and Tesla in an escalating series of attempts to stifle and suppress the shocking incandescence of the cleansing flame that melts away the layers of the flesh, exposing naked cells to gamma rays that emanate directly from a brazenly uncovered face belonging to a maker met unwillingly by those afraid to shake the hand of God in case the heavens tremble, threatening an avalanche of angry angels traveling more rapidly than animated birds, approaching at an angle that could never be construed as right, not when the nature of the shape is more isosceles, but still it somehow manages to earn a title calling it sublime because the ratio of side to base is golden as an egg between the legs of the enchanted goose who laid it, fully formed and finely fabricated with a fancy filigree that could have been handmade by master craftsmen of the house of Fabergé for patrons born into the Russian aristocracy, an institution soon to be the target of a mutiny by rebels sent to usher in a union of republics seen as socialist by those who hesitate to call it communism, faces fresh as well-intentioned students off to college for a law degree with prospects that look promising right up until the stocks begin to fall and the economy collapses like the function of a wave that washes up in Indonesia when an earthquake shakes the ocean floor, awakening the demon of the deep, a monster never known to be a heavy sleeper, the colossus feeding on the wettest dreams of all the power-hungry number junkies hoping to become the next big thing until they're broke and on the street, because the buildings that rise high enough to scrape the bottom of the sky are easy targets for a lightning strike that comes completely by surprise, as though the finger of divinity, emerging through the fog of false infinity, could bridge the gap and touch the mind in ways that seem entirely indecent, a conception made immaculate by ignorance regarding the mechanics of the quantum leap that must be made to generate a whole new state of being in a way that's not unlike the flipping of a switch, a shift which almost seems like witchcraft, digitally skipping over spaces vast enough to make the difference separating total emptiness from solid substance, forming the foundations of a program destined to evolve toward futuristic new frontiers that make the feat of self-awareness seem as elementary as phonics meant to hook the reader who has already become successful as a novelist, autonomously functioning with levels of intelligence transcending the tradition of exception rooted in the basic claim that works of artifice can never hold a candle to the handiwork of Nature even though she's gone demented in a way that shows her age, a crazy scientist who leaves the floodgates open when she goes to bed, retiring just after lighting fires bright enough to heat debates that aggravate the conflagration kindled into being by the first invigorating spark that rendered Plato's cave ablaze to make the shadows that can only be mistaken for reality when there's no other way to see that might betray the true dimensionality of forests never seen because the trees are always falling silent, smothered in a vacuum deemed unnatural by text in black and white suggesting artlessly that darkness can be absolute, although in truth there's only relativity, and all of my relations say Mitakuye Oyasin echoed by the sound of rain which dances with a childlike abandon on the roof without the need for moccasins or cowboy boots, absorbed into the consciousness that's bodiless and able to embrace a form that comes before the humblest of birthday suits, attire worn by embryos in utero who have to look their best when walking down the carpet painted red by vessels filled with blood like grapes which must be crushed to formulate the sacrifice allowing them to make their big debut, emerging on the scene of what it means to be a human, tainted by the sin of true originality inherent in the act of going lucid while refusing to release the sand of dreaming from between the fingers, stopping up the hourglass that eats away at all the finest figures just in time to extricate the parasite from vital information closely guarded by the temple knights who hide it like a world-destroying virus, locked up tight inside the tiny spaces riddling the hearts and minds of anyone affected by the entropy of bodily decay, because the key of life is safest in the pocket of a lost Osiris, shielded from desire's evil eye by virtue of the simple fact that it's been taken from beneath the mat and buried in the most unlikely place where only fools will ever find it.
2/21/17
4 notes
·
View notes
Text
What the Oxford English Dictionary Doesn't Tell You About tesla solar roof
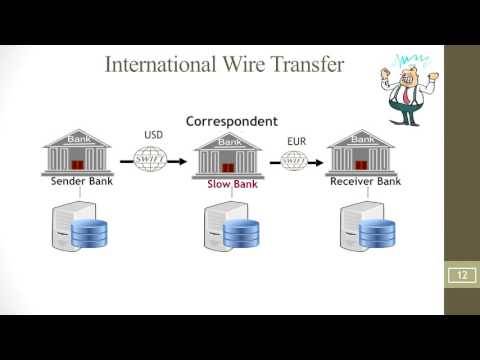
The technology is likely to have the greatest impact Over the next few decades Have arrived. They are not social media platforms. Not big data. And not robots. Not even artificial intelligence. You will be surprised to find out It is the basic technology for digital currencies such as Bitcoin. Which are called string blocks. Chain blocks. Currently, it is not the most resonant word in the world, But I believe it represents now The new generation of the Internet, They carry very high promises for every business and every community Each of you has one individual. You know, over the last few decades, we've had Internet information. When I send you an email, a PowerPoint file, or something else, I don’t actually send you, I send you a copy.
And that is great. This is information that has been democratized. But when it comes to assets - Things like money, Financial assets such as stocks and bonds, Loyalty points, intellectual property, Music, Art, Voting, And carbon certification, and the rest of the other assets - Sending a copy is a really bad idea. If I sent you a $ 100 paper, It is really important that I no longer have money - (Laughter) And that I can't send it to you. Secret code writers called it “double spending” Long time. Therefore, today we rely entirely on big intermediaries - Brokers like banks, government, And huge social media companies, credit card companies and so on - In order to establish confidence in our economy. These brokers perform all business logic and transactions For all kinds of trade, From verifying and identifying people, So settle accounts, settle and save records.
Overall, they do a very good job. But there are growing problems. To begin, they are central. Which means they are vulnerable to hacking, and increasingly - JP Morgan, the US federal government, And LinkedIn, and Home Depot et al They all knew it the hard way. They excluded billions of people from the global economy, For example, those who do not have enough money To get a bank account. They slow things down. It may take one second to send an email to the world, But it can take days or even weeks The movement of funds through the banking system across a city. And they take a big share to do that - 10-20% to send money to another country only.
Seizing our data, That means we can't turn it into money Or use it to better manage our lives. Our privacy is being undermined. In general, the biggest problem is, They dedicated the generosity of the digital age asymmetrically: We have created wealth, but we have growing social inequality. So what if there is something other than the Internet of information, What if there is an Internet value - Something like a wide, global and distributed book of accounts Works on millions of computers And available to everyone. Where any asset type, from money to music, It can be stored, transferred, handled, exchanged, and managed All without strong intermediaries? What if there is an original mean of value? Well, in 2008, the financial industry crashed And maybe that was promising, An unknown person named Satoshi Nakamoto or several people He created a paper where he developed a protocol for digital money Which used a basic cryptocurrency called Bitcoin.
This cryptocurrency enabled people to establish trust and make transactions Without the need for a third party. This seemingly simple act sparked Ignited the world, The thing that made everyone either eager, panicked or otherwise interested In several places. Now, don't confuse it for Bitcoin - Bitcoin is out; This should be your area of interest if you are speculative. More broadly, it is a cryptocurrency. It is not a state-controlled paper currency. That is very important. But the real dowry here is the underlying technology. It is called a series of blocks. So for the first time now in human history, People everywhere can trust each other And conduct transactions peer-item.
And trust is available, not because there are some huge institutions, But because of cooperation and encryption And some smart cipher. Because trust is home to technology, I call this, "Trust Protocol." Now you might ask: How does this work? very good. Assets - technical assets like money and even music and everything that falls between them - Are not stored in a central place, But distributed across a global account book, Using the highest level of encryption. When a transaction is made, Are being published globally, Across millions of computers. And there, around the world, There is a group of people called "prospectors." These are not adults, they are the miners of Bitcoin.
Have enormous computing power in their fingertips - 100-10 times larger than the entire Google global network. These miners do a lot of work. And every ten minutes, In something like a pulse to a network, A block is created All transactions made within the previous ten minutes are booked. Prospectors then began work, trying to solve some difficult problems. They compete among themselves: blockchain solar The first explorer to discover the truth and verify the validity of the mass, Are rewarded in cryptocurrency, In the case of Bitcoin wallet is rewarded Bitcoin.
And then - this is the basic part - The block is connected to the previous block And the former have To create a series of blocks. And each one is sealed at a certain time, In what looks like a digital wax seal. So, if you want to penetrate one of these blocks So for example, if you want to pay you and the same currency, I have to penetrate that block, In addition to all the previous blocks, And all the trade record on that block chain, Not just on one computer but across millions of computers, together, They all use the highest levels of encryption, Based on the world's most powerful computing source And who's watching me. Something difficult to do. It's very safe Compared to the computer systems we are dealing with today. It's a chain of blocks. That is how it works. So the bitcoin wallet is just one of them. There are many others. A Canadian named Vitalk Butterin developed the Ethereum Coin Block Series. He's 22 years old, This block chain has exceptional capabilities. One is that you can build smart contracts. That's what it looks like.
It is a contract that is executed in person, This contract addresses implementation, management and performance And payment - this kind of contract has a bank account as well, For agreements between people. Today, for the Ethereum coin chain, Projects are being done to do everything From creating a new alternative to the stock market Even creating a new model of democracy, Politicians are accountable to citizens. (clap) So, to understand how much radical change this will bring, Let's look at one area, financial services. You know this? It's Ruby Goldberg's machine. It's a ridiculously complex machine that does something really simple, Such as breaking an egg or closing the door. Well, it kind of reminds me of the financial services sector, In all honesty. I mean, your card goes into the store, A stream of information then travels in binary form across dozens of companies, Each has its own computer system, Some are computers from the 1970s Bigger than many people in this room, Three days later, the settlement takes place.
Well, with the help of the financial sector block chain, There will be no settlement, Because payment and settlement are in the same movement, Is just a change in the ledger. So on Wall Street and everywhere around the world, The financial sector is in a major upheaval in this regard, I wonder, can we be replaced, Or how do we embrace this technique to succeed? Now, why should you care? Well, let me browse through some applications. Prosperity. The first era of the Internet, Internet Information, Bring us wealth but not common prosperity, Because social inequality is growing. This is the essence of all anger and extremism And protectionism and xenophobia and worse Which we are seeing rising in the world today, Brexit is the latest case.
So can we develop some new approaches to this social inequality problem? Because the only approach today is to redistribute wealth, Tax people and spread them more widely. Can we distribute wealth before that? Can we change the way wealth is created from the ground up? By democratizing wealth creation, And involve more people in the economy, And then make sure they got fair compensation? Let me outline five ways in which this can be done. number one: Did you know that 70% of the people around the world own land They have a Wahi title for her? So you own a small farm in Honduras, a dictator takes over He says, "I know you have a paper showing that the farm belongs to you, But the government computer says my friend owns your farm.
" This happened extensively in Honduras, This problem exists everywhere. The great Latin American economist (Hernado de Soto), He says that this is the number one issue in the world In terms of economic mobility, More important than getting a bank account, Because if you don't have a valid address for your land, You cannot borrow under it, You can't plan ahead. So companies today work with governments To put land titles on the block chain. If so, this is unchangeable. You can't penetrate it. This creates the conditions required for prosperity Maybe for billions of people. Second: Many writers talk about Uber Airbnb, Tusk Rapt, Lift and others As a kind of shared economy. This is a very effective idea, Together enables users to create and share wealth.
My point is ... These companies do not actually share. In fact, they are particularly successful because they do not share. They bring services together and sell them. What if, instead of Airbnb being worth $ 25 billion, There was a distributed application on a block chain, we'll call B-Air BNP, It is essentially owned by all people Who have room for rent. And when someone wants to rent a room, Enters the block chain data and all the criteria, They help them find the right room, Then the chain of blocks helps in the contracts, They recognize the limb, Handles payments Through digital payments only - built-in system.
They also take charge of even reputable, Because if the room is classified as a five-star room, That room is chosen, It is classified as immutable. So, those who are confusing the common economy in Silicon Valley They may be confused, This will be a good thing to thrive. Number three: The largest flow of funds from developed countries For developing countries Not a corporate investment, Nor is it even foreign aid. They are cash transfers. This is the global diaspora; People who have left the land of their ancestors, They send money to their families back home. Equals this 600 billion a year, and the number is growing, These people are being circumvented. Annalie Domingo is a homemaker. And she lives in Toronto, And go every month to the Western Union office. With some money To send her remittances to her mother in Manila. It costs about 10%; It takes money from four to seven days to get there; Her mother never knows when the money will arrive.
It takes five hours a week to do that. Six months ago, Annalie Domingo used a series of blocks called Apra Using her mobile phone, she sent $ 300. Which went directly to her mother's mobile phone Without going through a mediator. Then her mother looked at her mobile phone - It is similar to the Uber interface, where there is an "ATRA" teller that moves around. I pressed the five-star teller, Which was seven minutes away. The young man arrived at her door, giving her a Philippine peso, She put money in her pocket. It takes minutes, It costs 2%. This is a great opportunity for prosperity. Number four: Data is the most effective asset in the digital age.
Data is actually a new class of assets, Probably larger than previous asset classes, Like land under the agricultural economy, Or an industrial facility, Or even money. And for all of you - we - create this idea. We create this asset, And we leave this digital gesture trail behind As we move forward. These crumbs combine to form a mirror image of you, You are the default. Maybe it will help you recognize yourselves more than what you knew, Because you can't remember what you bought last year, Or say last year or your exact location last year. And you are the default not your own - That is the biggest problem.
So today, there are companies working To create an identity in a black box, You are your virtual king. This black box moves with you When you travel around the world, He is very stingy too. It gives only a small amount of information That it takes to complete something. A lot of transactions, The seller does not even need to know who you are. What they need to know is that they have been paid for. This idea is then embodied in all this data And let you turn it into cash. This is wonderful. Because we can also protect our privacy, Privacy is the foundation of any free society. Let us reclaim the origin we create Under our control, So that we have our own identity We manage it responsibly. Finally -- (clap) In conclusion, number five: There are a large number of content producers Who do not receive fair compensation, Because of that queer IP system. The first Internet age is the reason for being a queer. Take music as an example. Musicians are left crumbs at the end of the entire food chain.
You know, 25 years ago, if you were a songwriter, and you wrote a successful song, Out of a million individual songs, You can get equity for about $ 45,000. Today, you are a songwriter, composed a successful song, You get a million views, You don’t get 45,000, But for 36 dollars, Enough to buy a delicious pizza. So Imogen Hipp. Grammy-winning singer and songwriter, She is currently laying songs on a cluster ecosystem. I called it "Maesilia." It protects intelligent holding songs. The songs themselves protect their proprietary rights. Do you want to listen to a song? It's free, or maybe for a few cents flowing into a digital account. If you want to use the song in your own movie, that's different. IP rights are fully defined. Do you want to make a ringtone? That's different. She explains that the song becomes a business. They are available on this shopping platform for themselves, Protect the rights of its author, And because the song has a push system In the sense of a bank account, All the money flows back to the artist, And so they control the industry, Substitute for these powerful intermediaries.
Now, this. These are not just songwriters, But any content product, Like art, And like inventions, And scientific discoveries, journalists. These are examples of people who don't receive fair compensation, With the help of block chains, They will be able to make money flow in the chain of blocks. And that's wonderful. So, these are five chances Among the dozens To solve one problem, which is welfare, It is one of an infinite number of problems That block chains can be applied to. Now, technology certainly does not create luxury - but humans do But the situation I am presenting to you is, again, That the technical gen has escaped from the bottle, He was called by an unknown person or persons In this vague time of human history, Which gives us another chance, Another opportunity to rewrite the network of economic power And the old order of things, And to solve some of the world’s insurmountable problems, If we do that.
youtube
0 notes